The document discusses live memory forensics for Android devices, detailing phases like data acquisition, analysis, and presentation, while emphasizing the importance of volatile data analysis. It explains the tools and methodologies for analyzing processes, memory structures, and artifacts to detect potentially malicious activities, including malware behavior and rootkit identification. Additionally, the document describes the use of the Volatility framework and custom plugins for extracting sensitive data from Android applications, highlighting the challenges and techniques in digital forensics within a mobile context.




![Android basics (2)
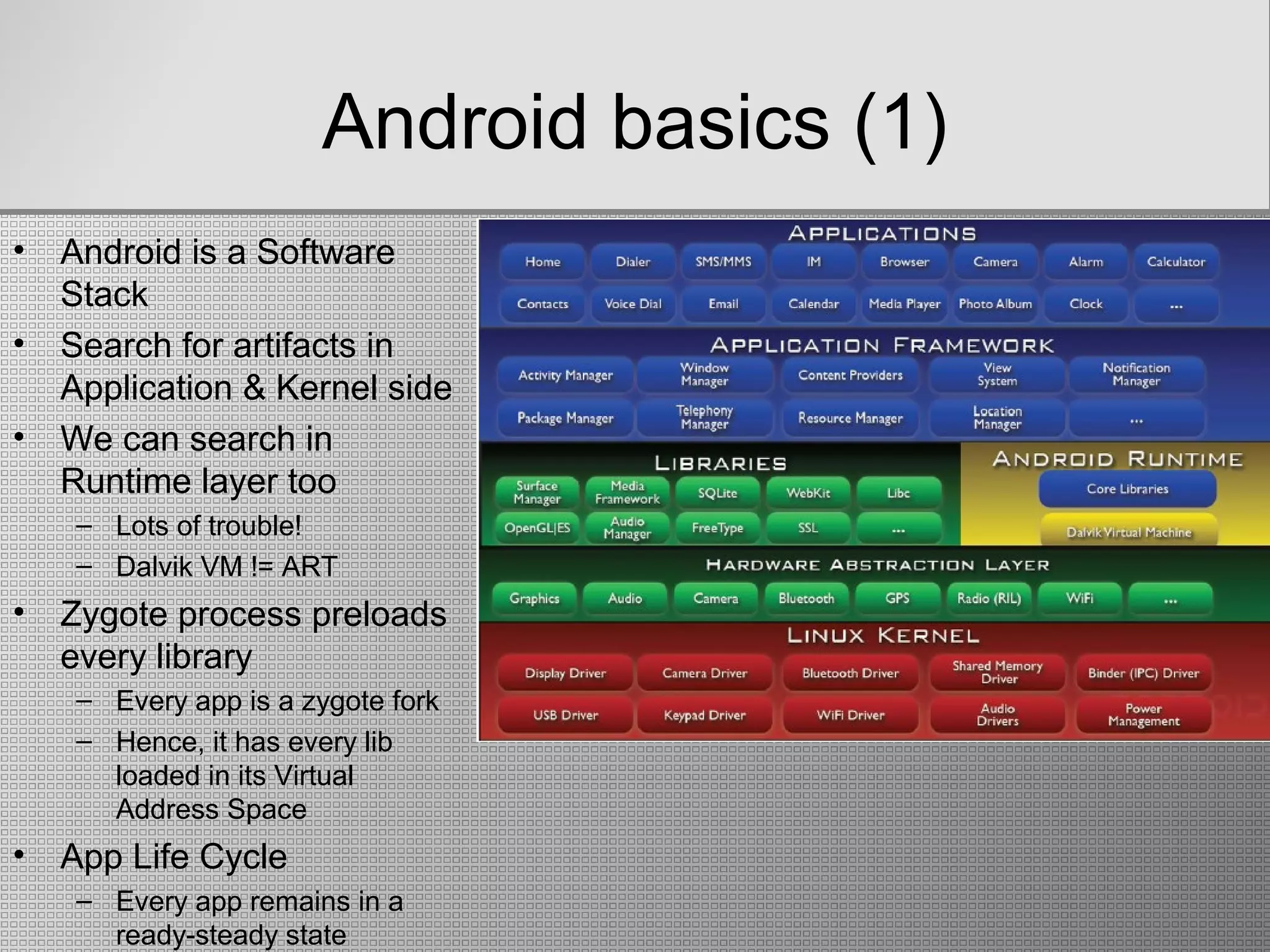
• Android apps’ .apk [Android Application
Package] file gives nice hints
• Disassemble the .apk file (apktool)
• AndroidManifest.xml: permissions, Ιntents
• classes.dex: Reversing the app
– DEX Smali assembly (Dalvik’s assembly)
– DEX Java with a decompiler
• Android’s filesystem
– data/ storage/ app-cache/ …
– One can dump the filesystem from RAM.dump](https://image.slidesharecdn.com/finalpresentation-newenglish-151026163556-lva1-app6892/75/Live-Memory-Forensics-on-Android-devices-9-2048.jpg)


![Process Analysis (2)
• Check apps’ UIDs
– Android assigns a unique UID in each app
– User installed apps have UID > 10000
– Process Hollowing could be detected
• Check Linuxes standards for process
names, environment variables
– Kernel threads must be enclosed in []
– They cannot have environment variables
– A malware could masquerade in [] but still
have environment variables](https://image.slidesharecdn.com/finalpresentation-newenglish-151026163556-lva1-app6892/75/Live-Memory-Forensics-on-Android-devices-15-2048.jpg)
![Process Analysis (3)
$ python vol.py -f ~/android-dumps/example.dump linux_psaux
Volatility Foundation Volatility Framework 2.4
Pid Uid Gid Arguments
1 0 0 /init
2 0 0 [kthreadd]
3 0 0 [ksoftirqd/0]
4 0 0 [kworker/0:0]
[snip]
468 1023 1023 /system/bin/sdcard -u 1023 -g 1023 -d /mnt/media_rw/sdcard
/storage/sdcard
474 10005 10005 android.process.media
523 10029 10029 com.android.inputmethod.latin
539 1001 1001 com.android.phone
[snip]
1138 10053 10053 com.savemebeta
1157 0 0 /system/bin/sh -
1164 0 0 insmod /sdcard/lime.ko path=tcp:12345 format=lime
1381 0 0 [kworker/0:1]](https://image.slidesharecdn.com/finalpresentation-newenglish-151026163556-lva1-app6892/75/Live-Memory-Forensics-on-Android-devices-16-2048.jpg)
![Process Analysis (4)
$ python vol.py -f ~/android-dumps/example.dump linux_psxview
Volatility Foundation Volatility Framework 2.4
Offset(V) Name PID pslist pid_hash kmem_cache parents leaders
---------- -------------------- ------ ------ -------- ---------- ------- -------
0xde81bc00 init 1 True True True True True
0xde81b800 kthreadd 2 True True True True True
0xde81b400 ksoftirqd/0 3 True True True False True
[snip]
0xde071800 zygote 65 True True True True True
0xde071400 drmserver 66 True True True False True
0xde071000 mediaserver 67 True True True False True
0xde0a7c00 installd 68 True True True False True
0xde0a7800 keystore 69 True True True False True
0xde0a7400 qemud 70 True True True False True
0xde0a7000 sh 73 True True True False True
0xde0e9800 adbd 74 True True True True True
• Requires strong internal knowledge of the Android OS
and the Linux kernel
• Tough for a rootkit to hide from every OS “spot”](https://image.slidesharecdn.com/finalpresentation-newenglish-151026163556-lva1-app6892/75/Live-Memory-Forensics-on-Android-devices-17-2048.jpg)

![Searching & Dumping files (1)
$ python vol.py -f ~/android-dumps/example.dump linux_lsof -p 1138
Volatility Foundation Volatility Framework 2.4
Pid FD Path
-------- -------- ----
1138 0 /dev/null
1138 1 /dev/null
1138 2 /dev/null
1138 3 /dev/log/main
1138 4 /dev/log/radio
1138 5 /dev/log/events
1138 6 /dev/log/system
1138 7 /system/framework/core.jar
1138 8 /dev/__properties__
1138 9 socket:[1803]
[snip]
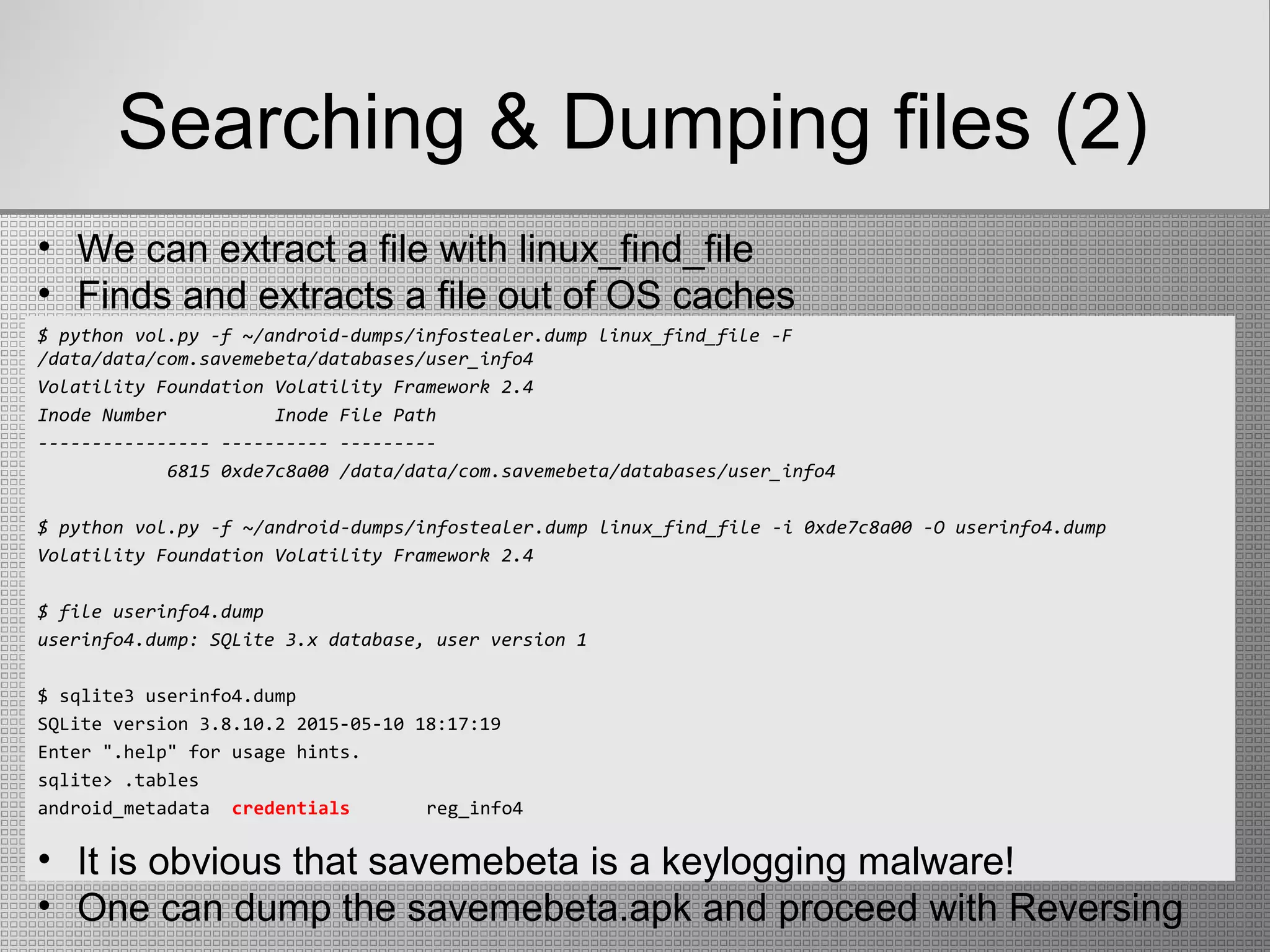
1138 47 /data/data/com.savemebeta/databases/user_info4
• linux_lsof: displays any open file (regular files, streams,
logging buffers, sockets)
• The user_info4 file looks interesting..](https://image.slidesharecdn.com/finalpresentation-newenglish-151026163556-lva1-app6892/75/Live-Memory-Forensics-on-Android-devices-19-2048.jpg)
![Searching & Dumping files (3)
$ python vol.py -f ~/android-dumps/infostealer.dump linux_enumerate_files --output=text --output-file=dump-
files
$ cat dump-files | grep "/data/app" | egrep ".apk$"
3628688208 0x5c /data/app/com.savemebeta-1.apk
3628158240 0x5a /data/app/com.android.service-1.apk
[snip]
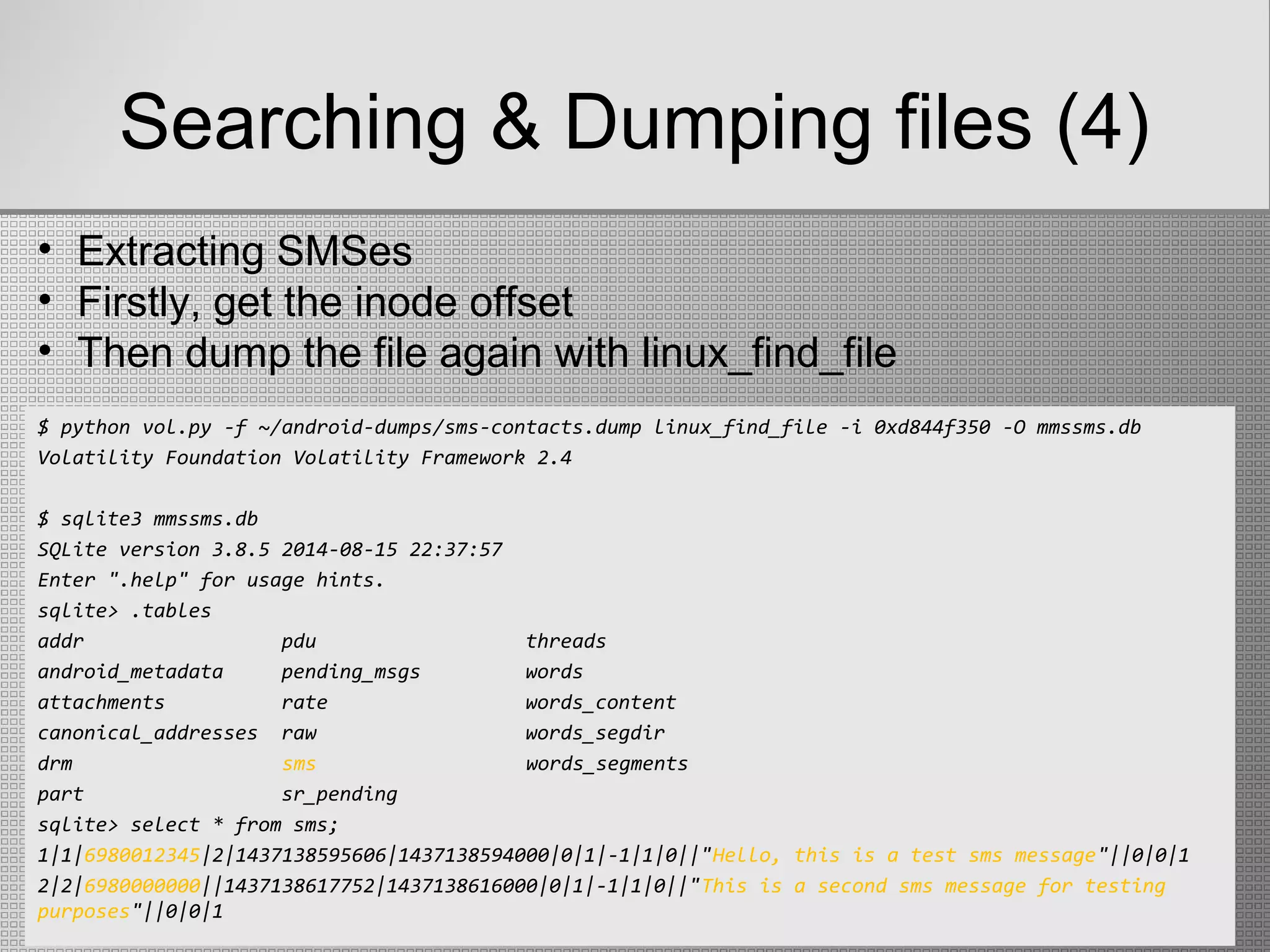
$ cat dump-files | egrep ".db$"
3628510096 0x1a23 /data/data/com.android.providers.telephony/databases/telephony.db
3628425472 0x1a09 /data/data/com.android.providers.telephony/databases/mmssms.db
3628945664 0x1a18 /data/data/com.android.email/databases/EmailProviderBackup.db
3628947776 0x1a16 /data/data/com.android.email/databases/EmailProviderBody.db
3628948304 0x1a0c /data/data/com.android.email/databases/EmailProvider.db
3628924192 0x1a3b /data/data/com.android.deskclock/databases/alarms.db
3628163328 0x19c4 /data/data/com.android.providers.settings/databases/settings.db
3628820800 0x1a42 /data/data/com.android.providers.media/databases/internal.db
3628473888 0x1a01 /data/data/com.android.providers.media/databases/external.db
3628394288 0x1a10 /data/data/com.android.launcher/databases/launcher.db
3628554224 0x1a2c /data/data/com.android.launcher/cache/widgetpreviews.db
3628536720 0x1a21 /data/data/com.android.providers.downloads/databases/downloads.db
3628406640 0x19d5 /data/data/com.android.providers.contacts/databases/profile.db
3628494176 0x19d3 /data/data/com.android.providers.contacts/databases/contacts2.db
• linux_enumerate_files: displays all files found in the
filesystem cache](https://image.slidesharecdn.com/finalpresentation-newenglish-151026163556-lva1-app6892/75/Live-Memory-Forensics-on-Android-devices-21-2048.jpg)
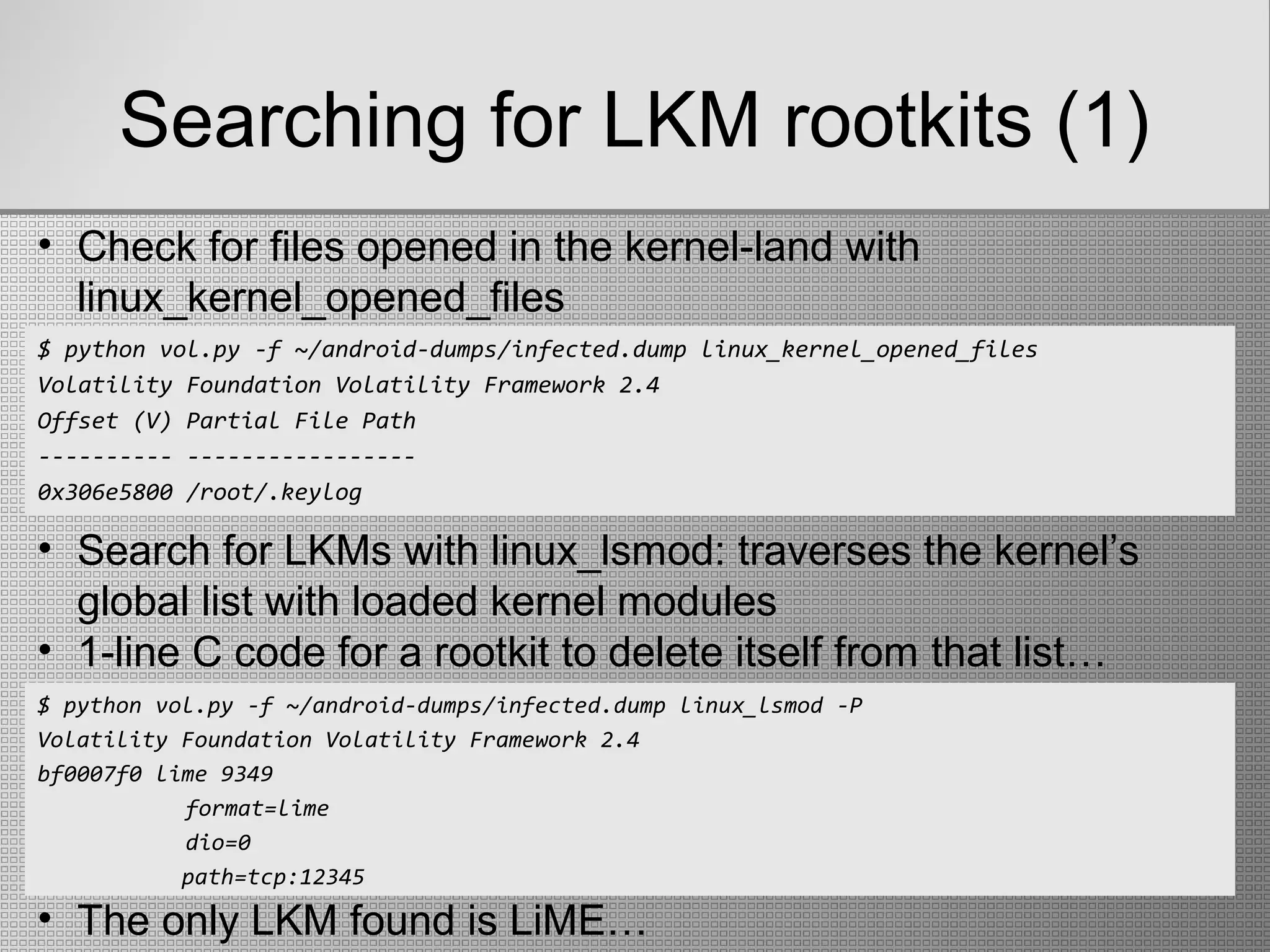


![Recovering filesystems (2)
$ sudo python vol.py -f ~/android-dumps/Evo4GRodeo.lime --profile=LinuxEvo4GARM linux_recover_filesystem –D
fs-example-output
$ cd fs-example-output/
$ echo */
acct/ app-cache/ data/ dev/ mnt/ proc/ sys/ system/
$ cd app-cache/com.android.browser/cache/webviewCache
$ sudo chmod -R 777 .
$ file *
0107b850: ASCII English text, with very long lines
19dde20c: HTML document text
28ca44b8: GIF image data, version 89a, 1 x 100
29b5cf95: JPEG image data, JFIF standard 1.02
29f711e8: JPEG image data, JFIF standard 1.02
301c338b: PNG image data, 1000 x 90, 8-bit/color RGBA, non-interlaced
[snip]
• linux_recover_filesystem: extracts part of the device’s whole
filesystem structure (the % of data that was cached in RAM)
• One then can apply traditional Digital Forensics techniques
• Android’s stock browser uses the app-cache tmpfs
filesystem to store its webviewCache ](https://image.slidesharecdn.com/finalpresentation-newenglish-151026163556-lva1-app6892/75/Live-Memory-Forensics-on-Android-devices-26-2048.jpg)

![Volatility plugin dev (1)
• Volatility framework provides some useful
API
– Quick byte sequences (needles) searching in
RAM data
– Easy data parsing, formatting and printing
• What would be a useful plugin?
– Facebook: 1.31 billion mobile users [22/4/15]
– 1.31 billion / 7.3 billion ~= 0.179](https://image.slidesharecdn.com/finalpresentation-newenglish-151026163556-lva1-app6892/75/Live-Memory-Forensics-on-Android-devices-28-2048.jpg)