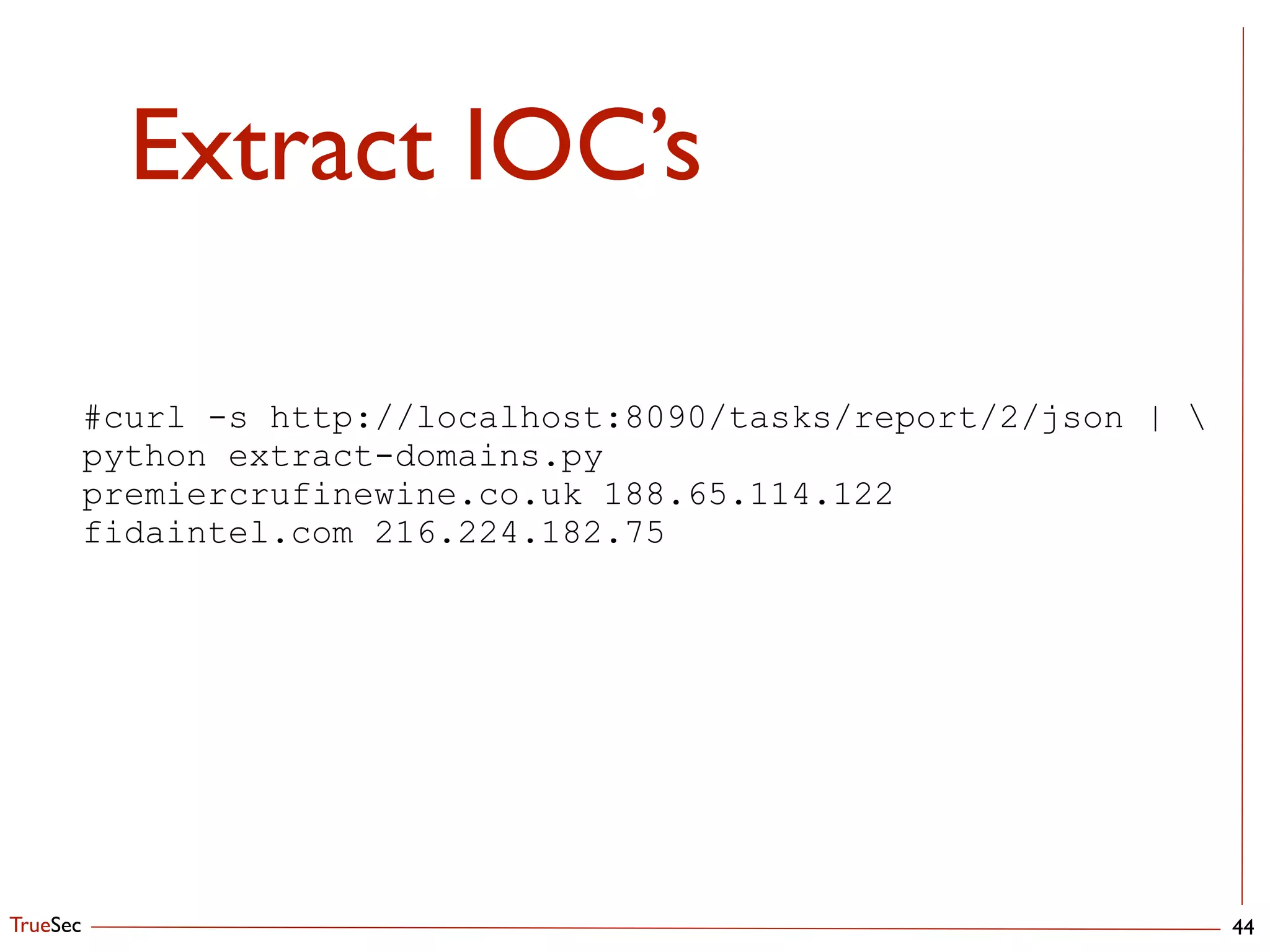
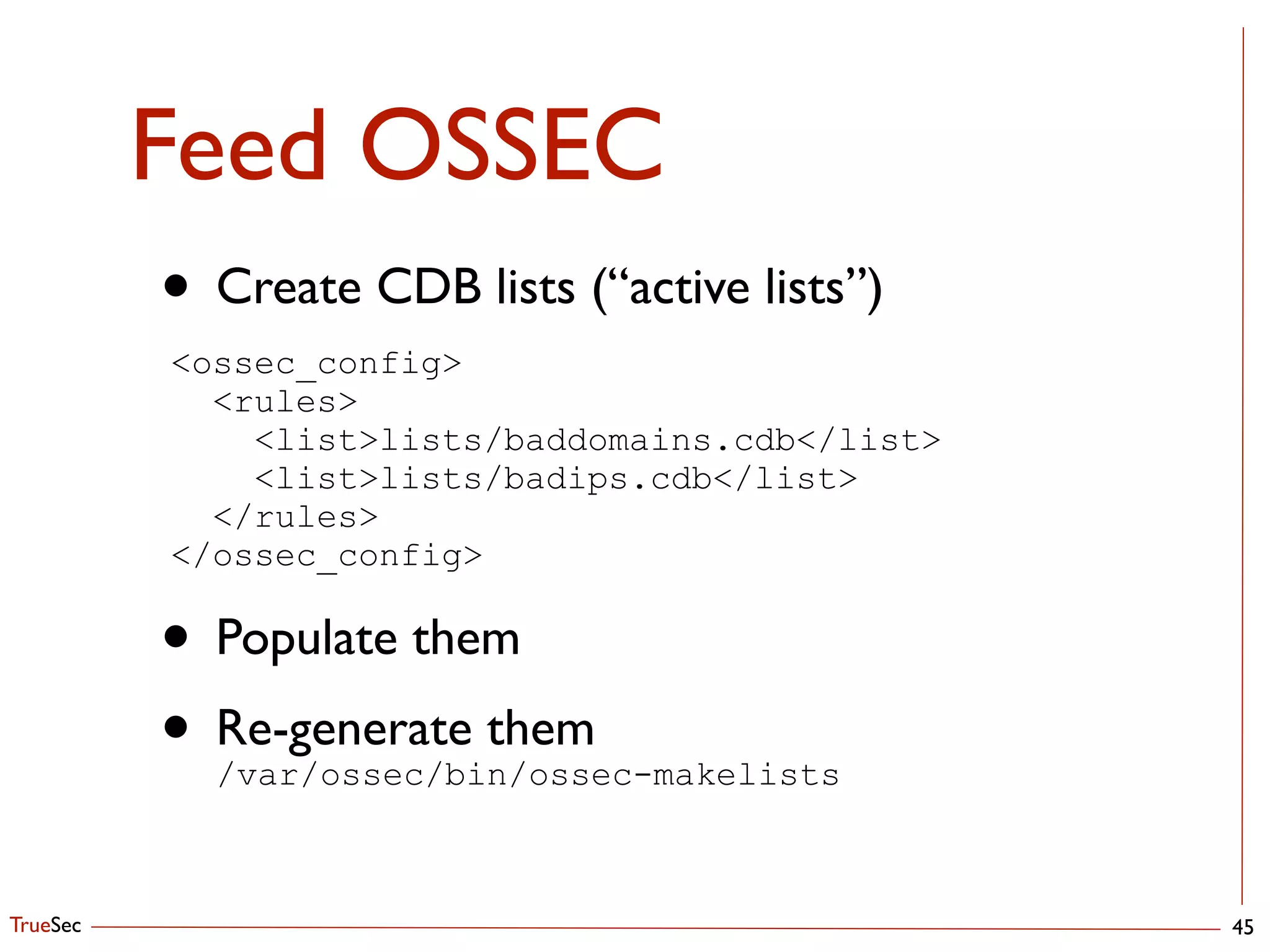
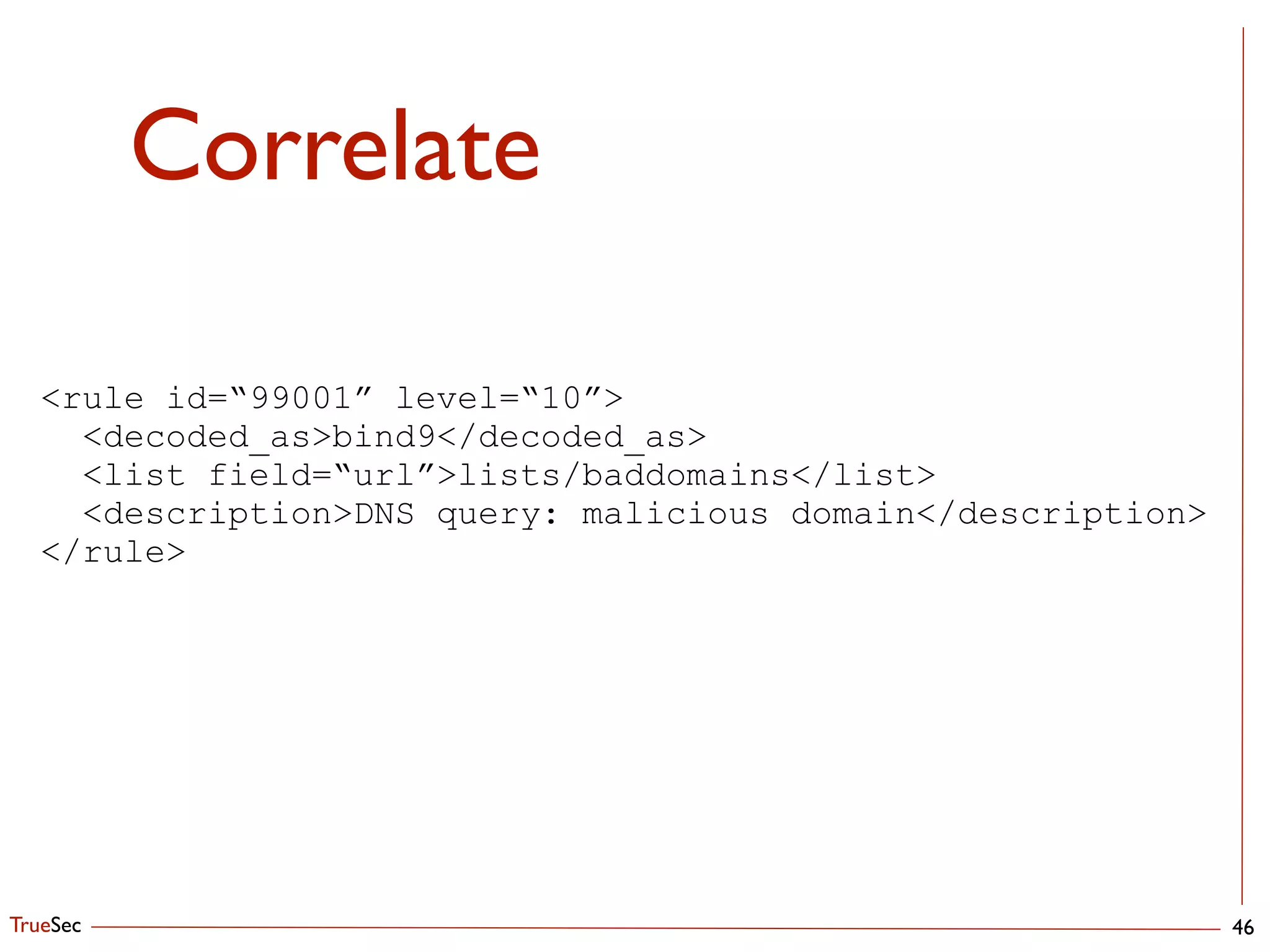
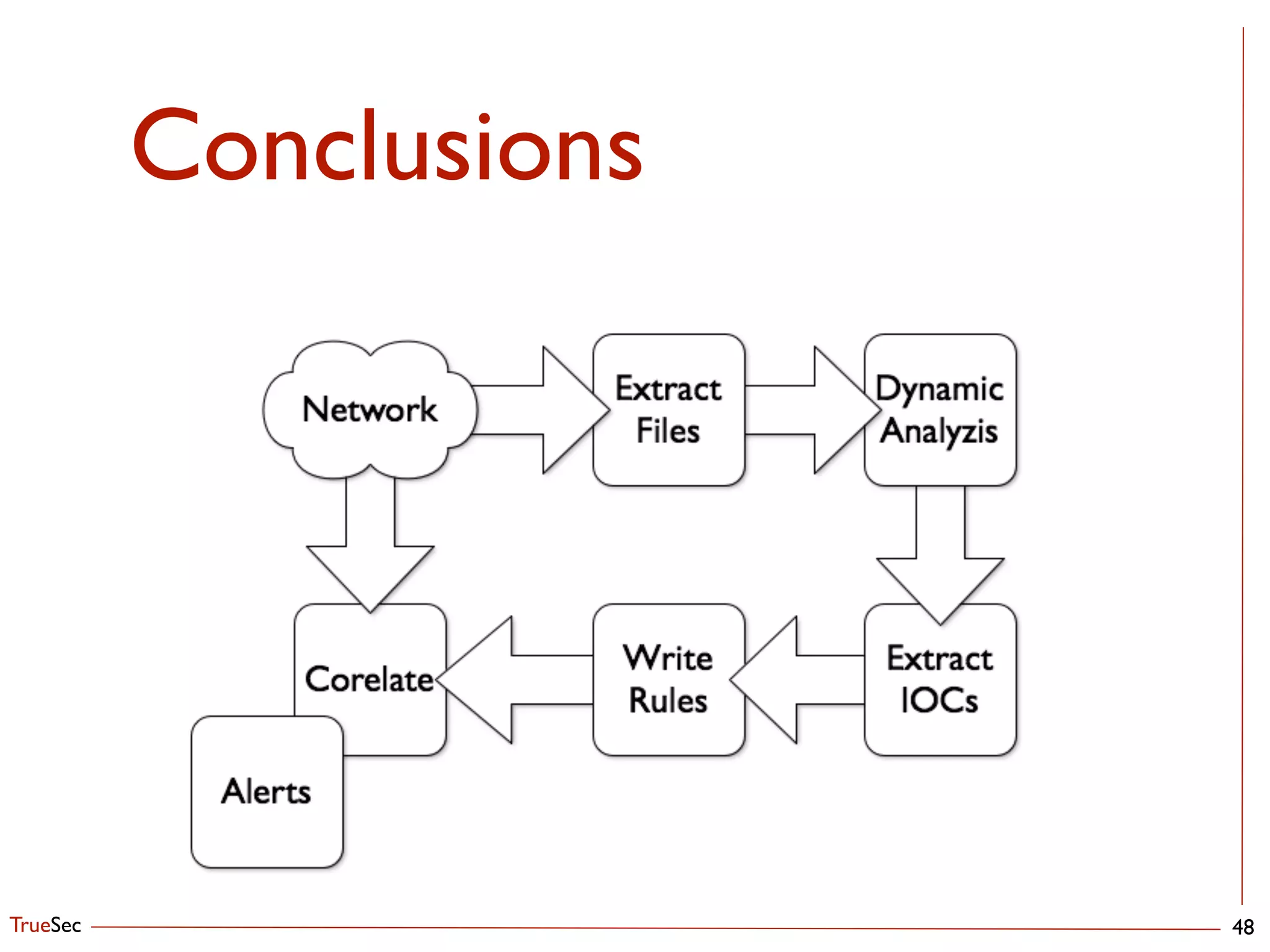
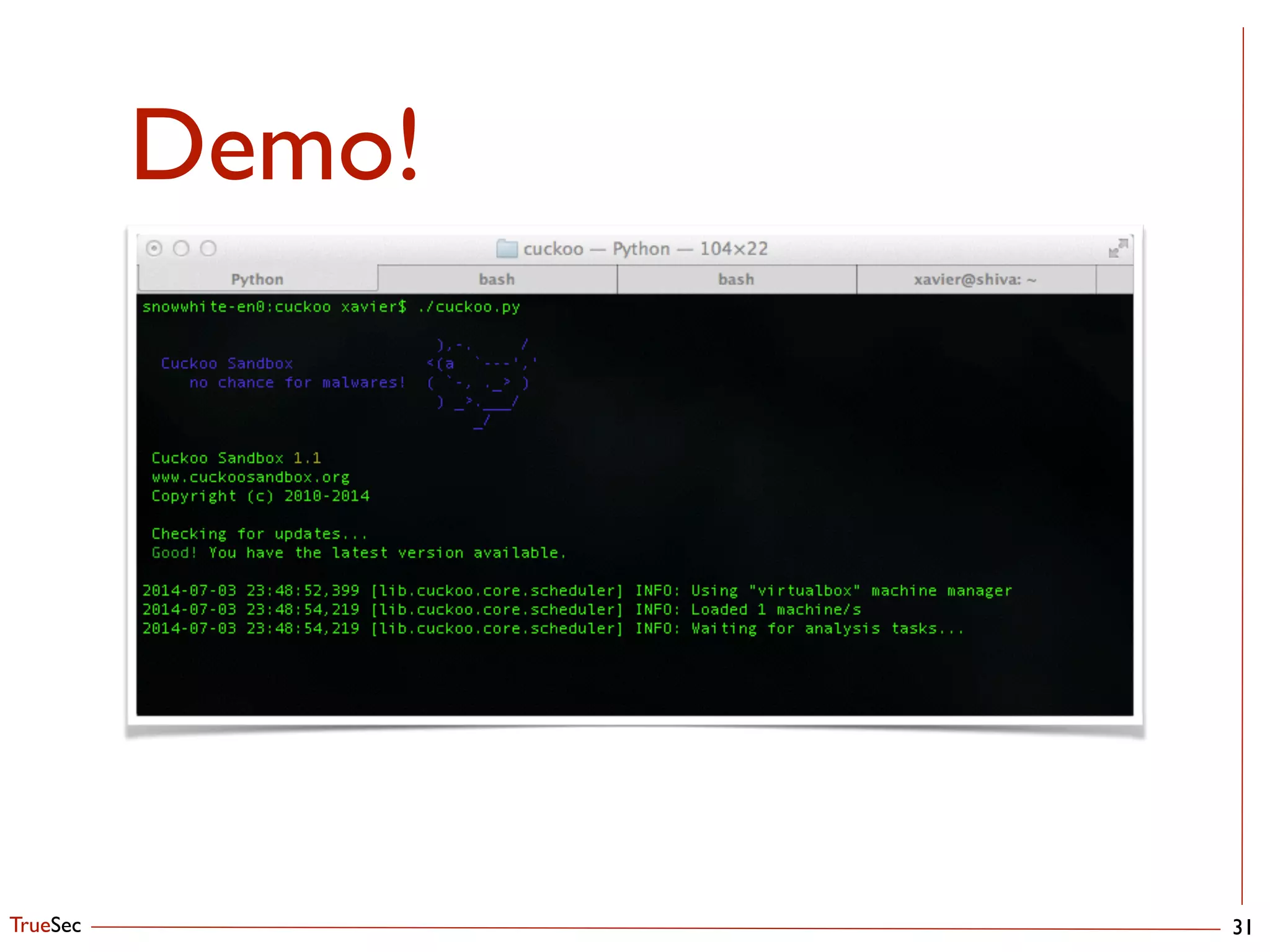
This document discusses setting up an automated malware analysis sandbox using Cuckoo and Bro. It recommends using Cuckoo to dynamically analyze malware samples and Bro to monitor network traffic and extract suspicious files. Bro scripts are shown to extract files and submit them to Cuckoo for analysis. The talk emphasizes automating the analysis workflow and correlating indicators from Cuckoo with external threat intelligence in OSSEC to aid detection.

















![TrueSec
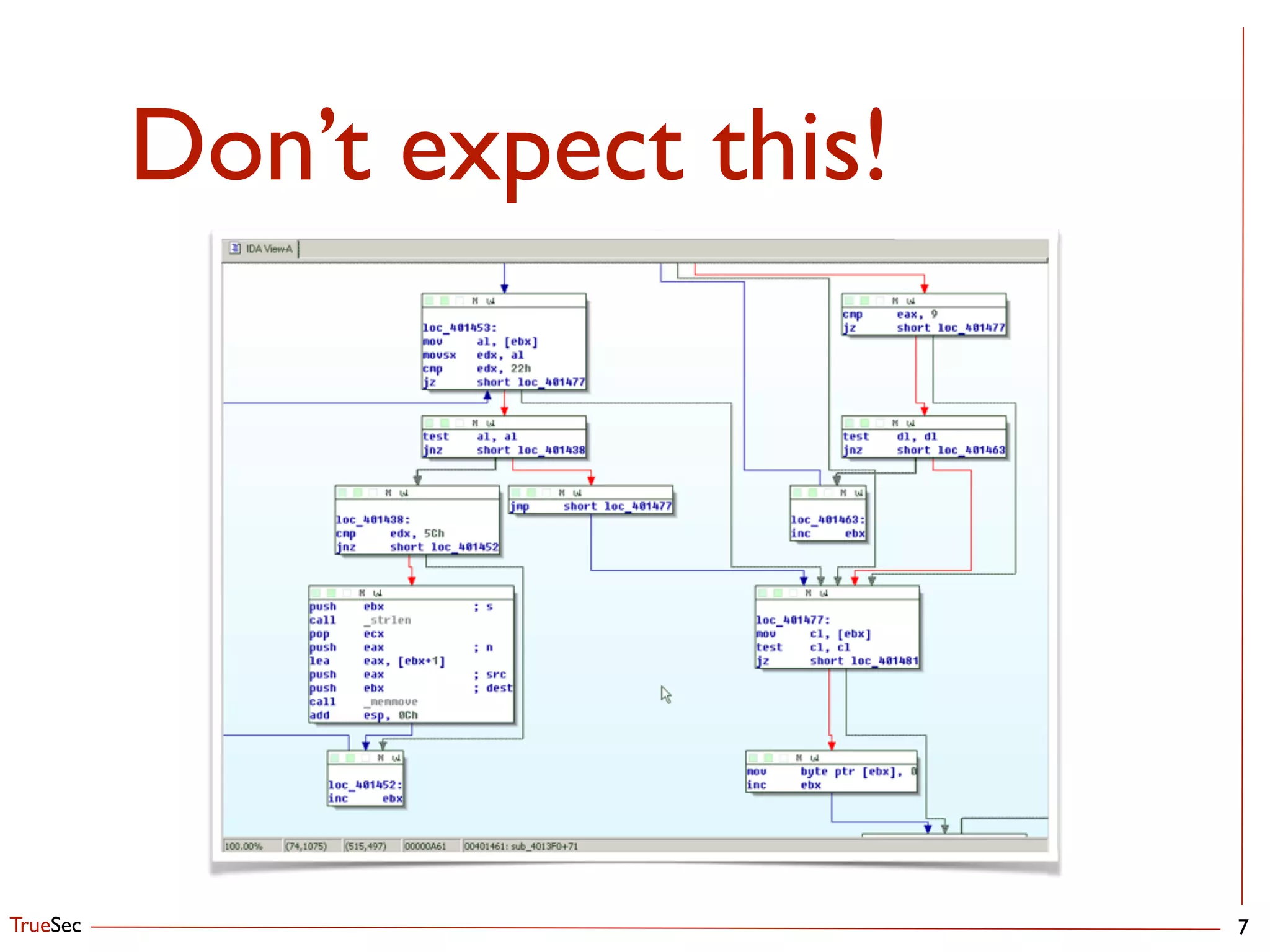
Extract Those Files!
37
global ext_map: table[string] of string = {
["application/x-dosexec"] = "exe",
} &default ="";
!
event file_new(f: fa_file) {
local ext = “data";
!
if ( f?$mime_type )
ext = ext_map[f$mime_type];
!
local fname = fmt("%s-%s.%s",
f$source, f$id, ext);
Files::add_analyzer(f, Files::ANALYZER_EXTRACT,
[$extract_filename=fname]);
}](https://image.slidesharecdn.com/malware-analysis-free-software-rmll2014-140708082623-phpapp01/75/Malware-Analysis-Using-Free-Software-37-2048.jpg)