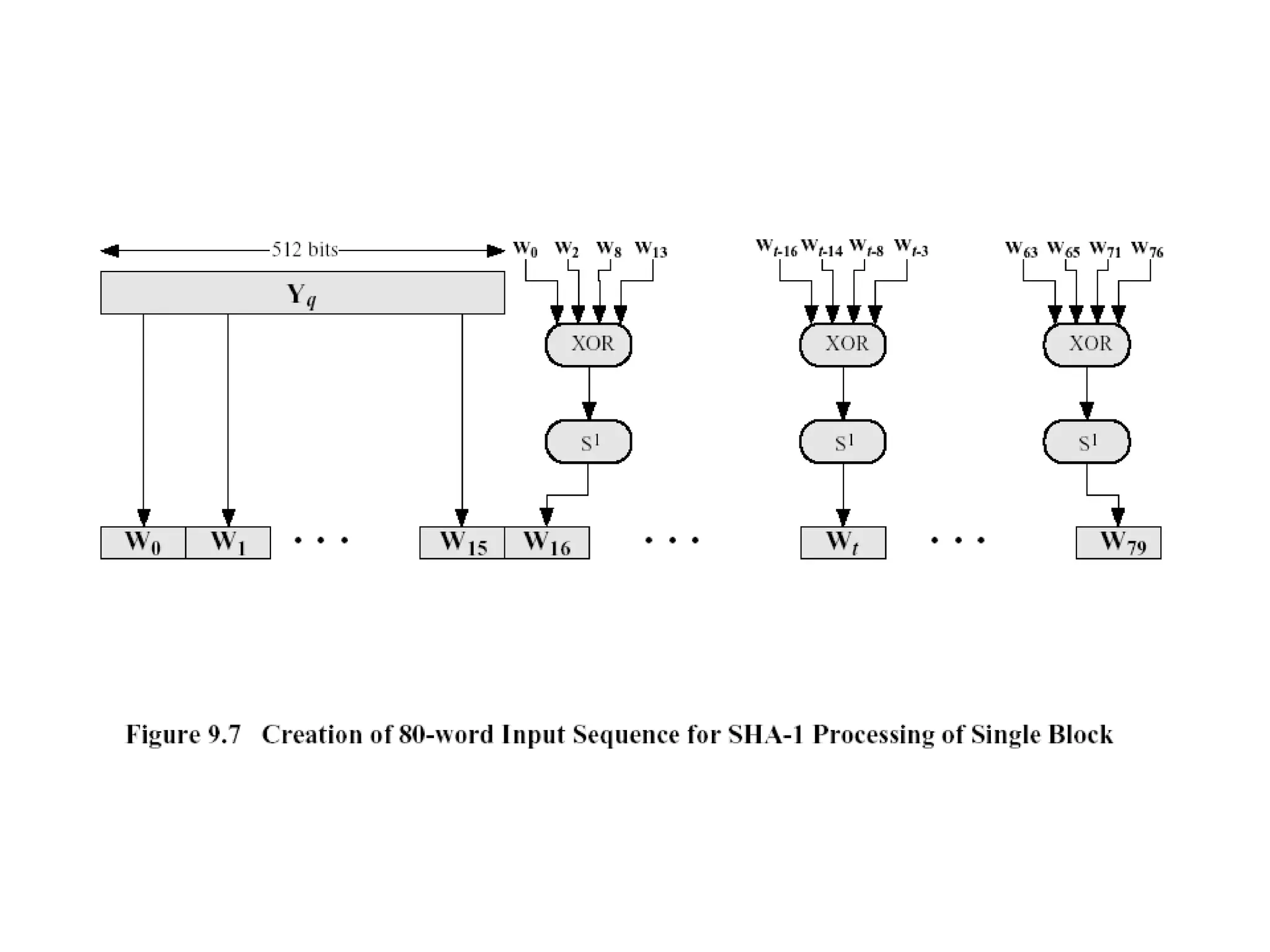
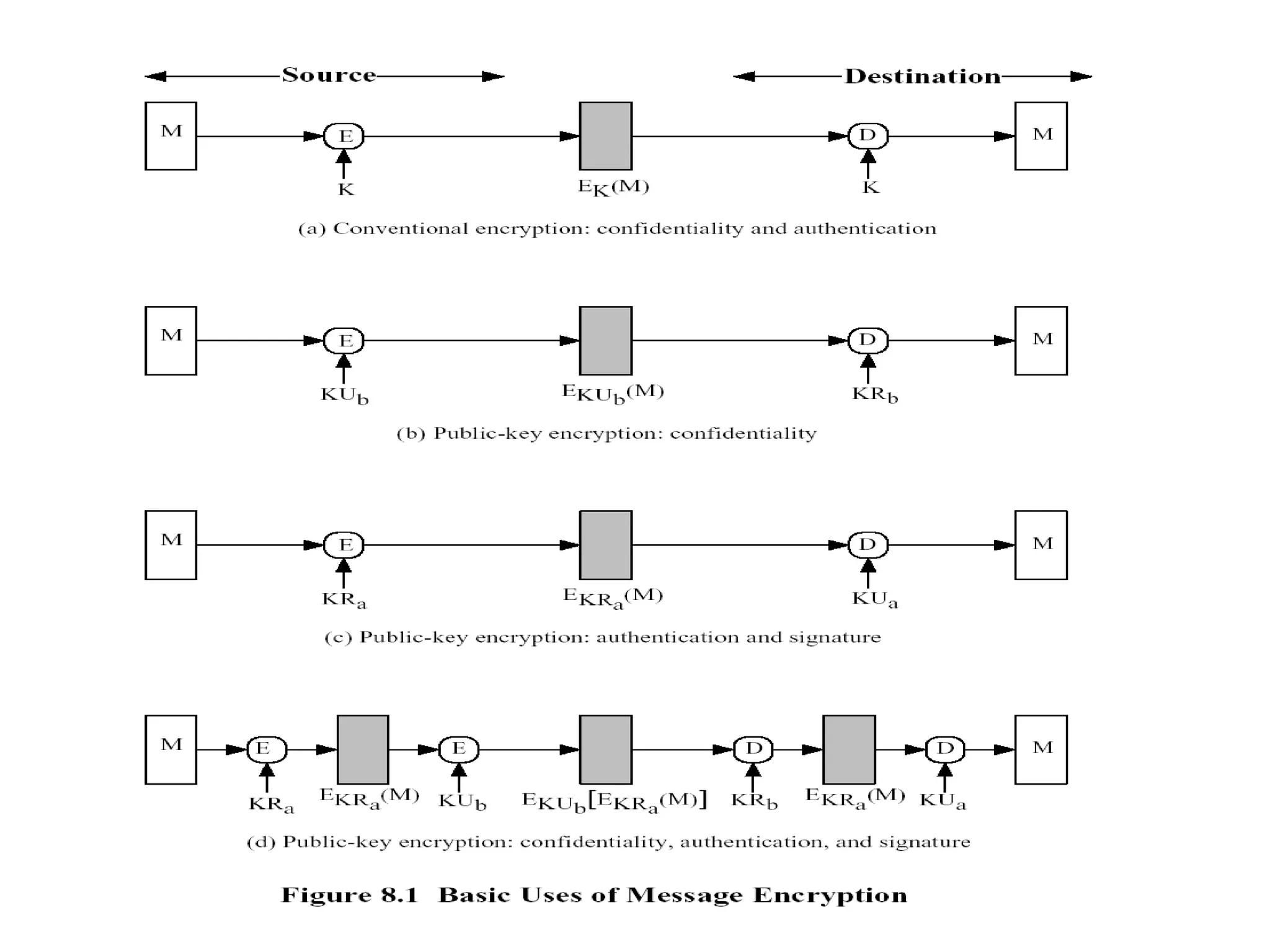
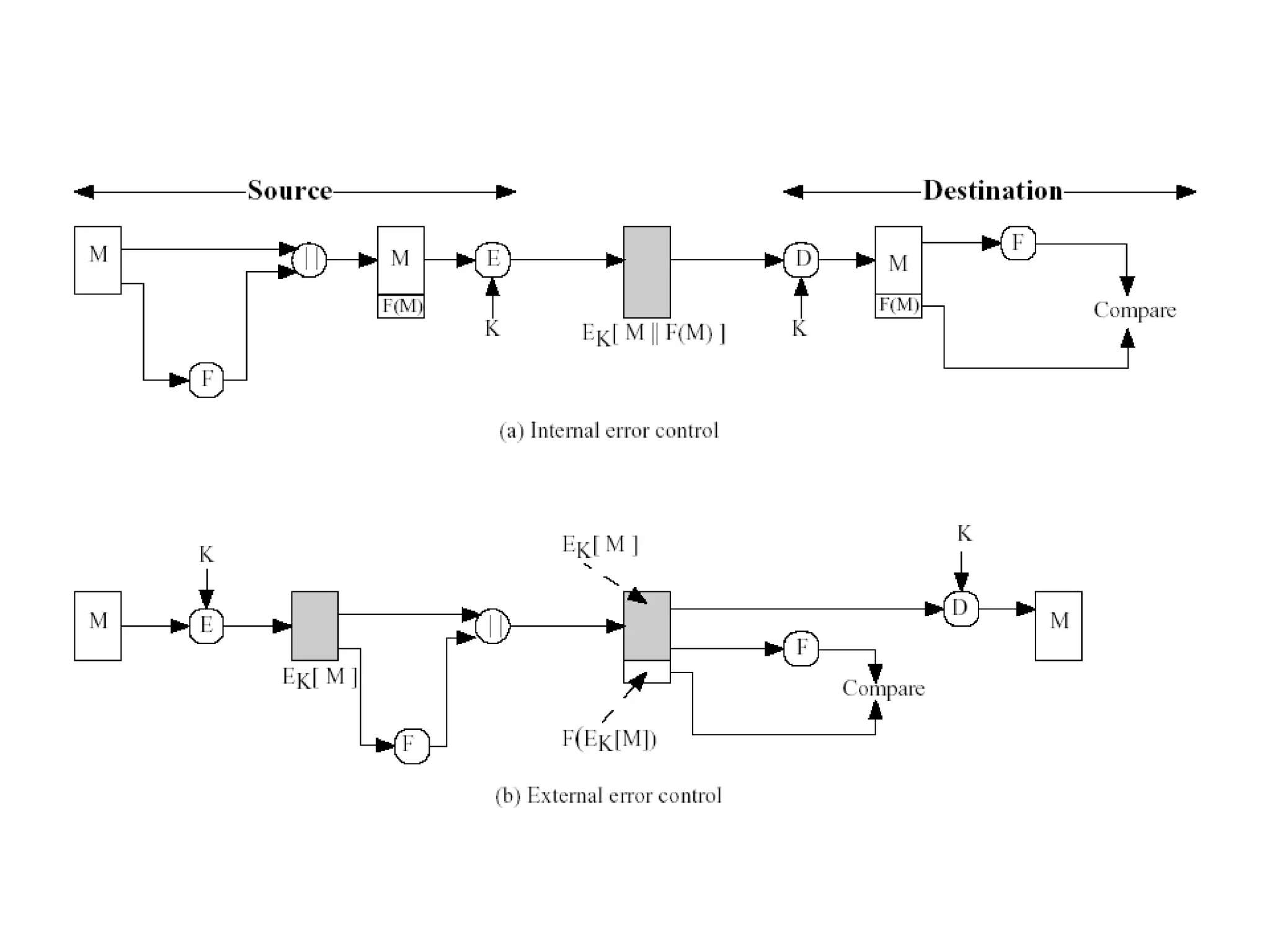
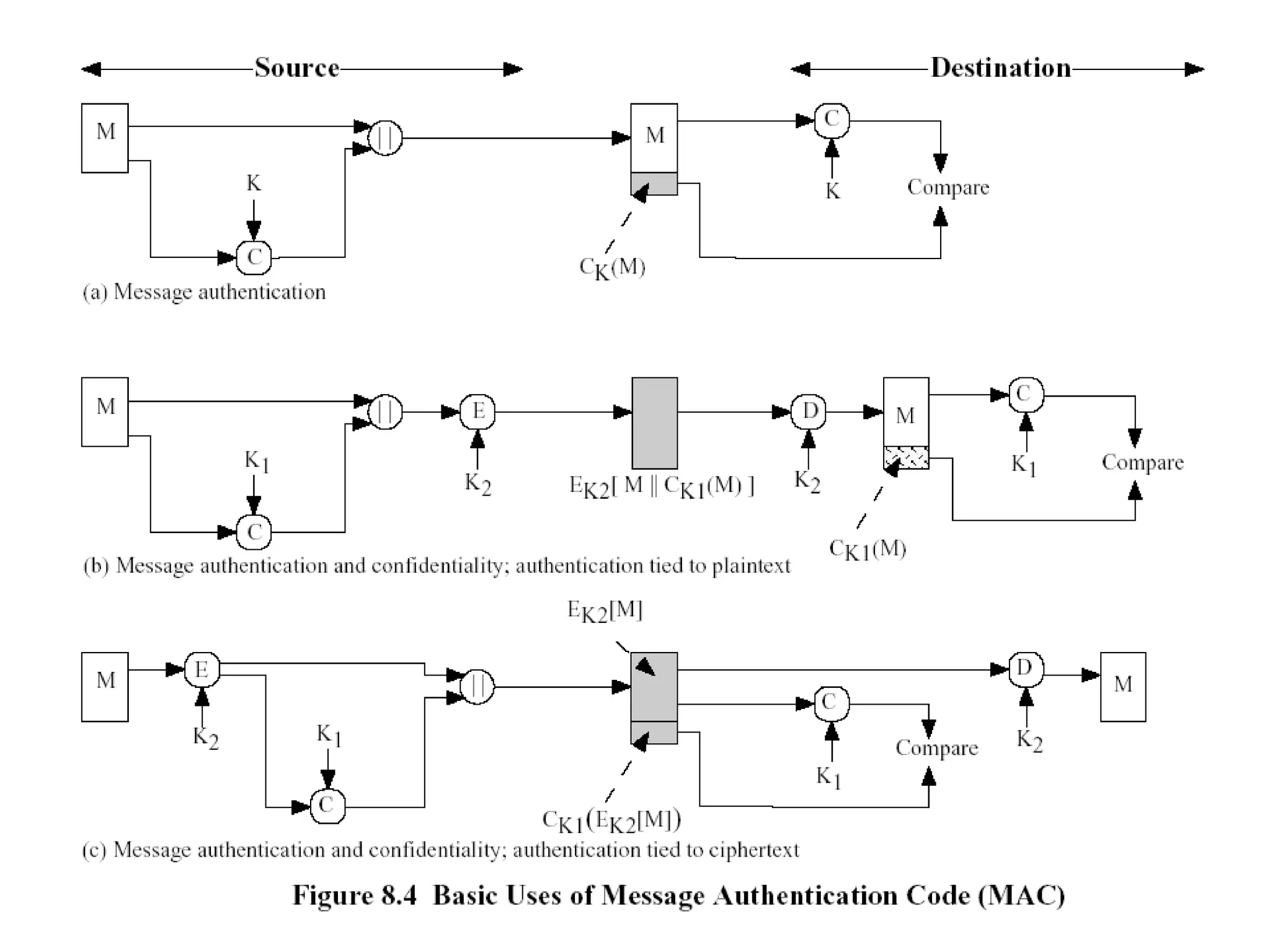
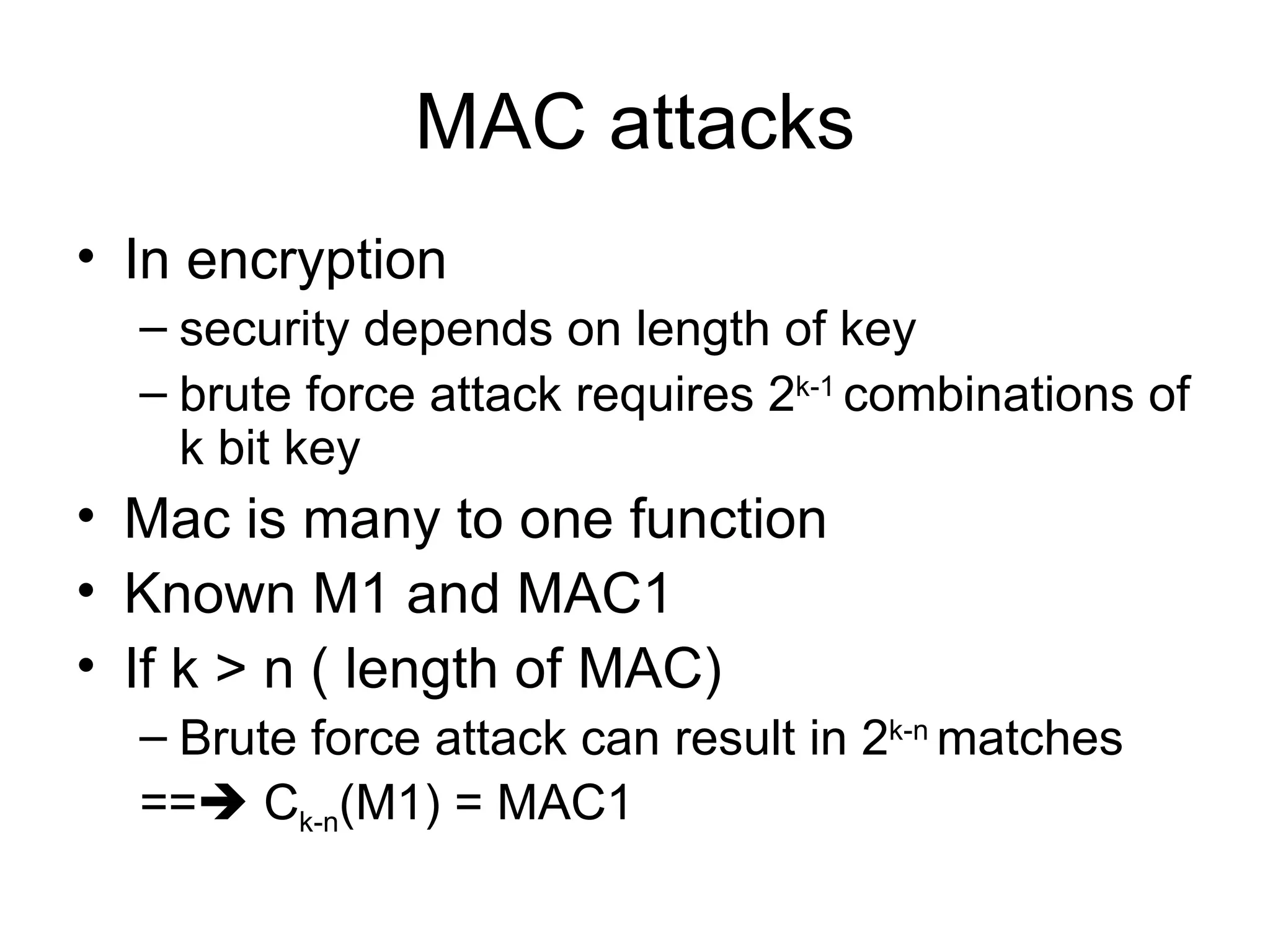
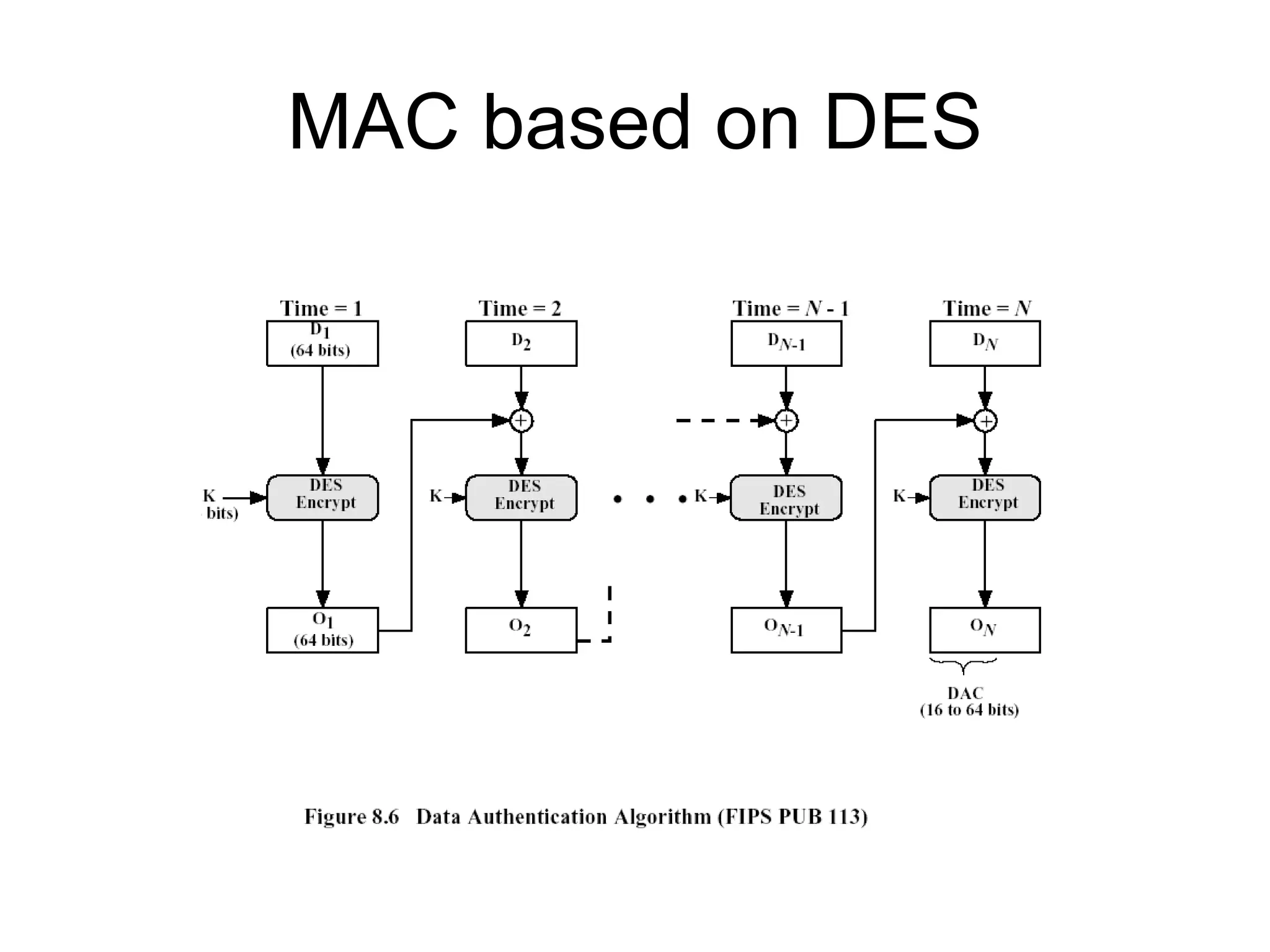
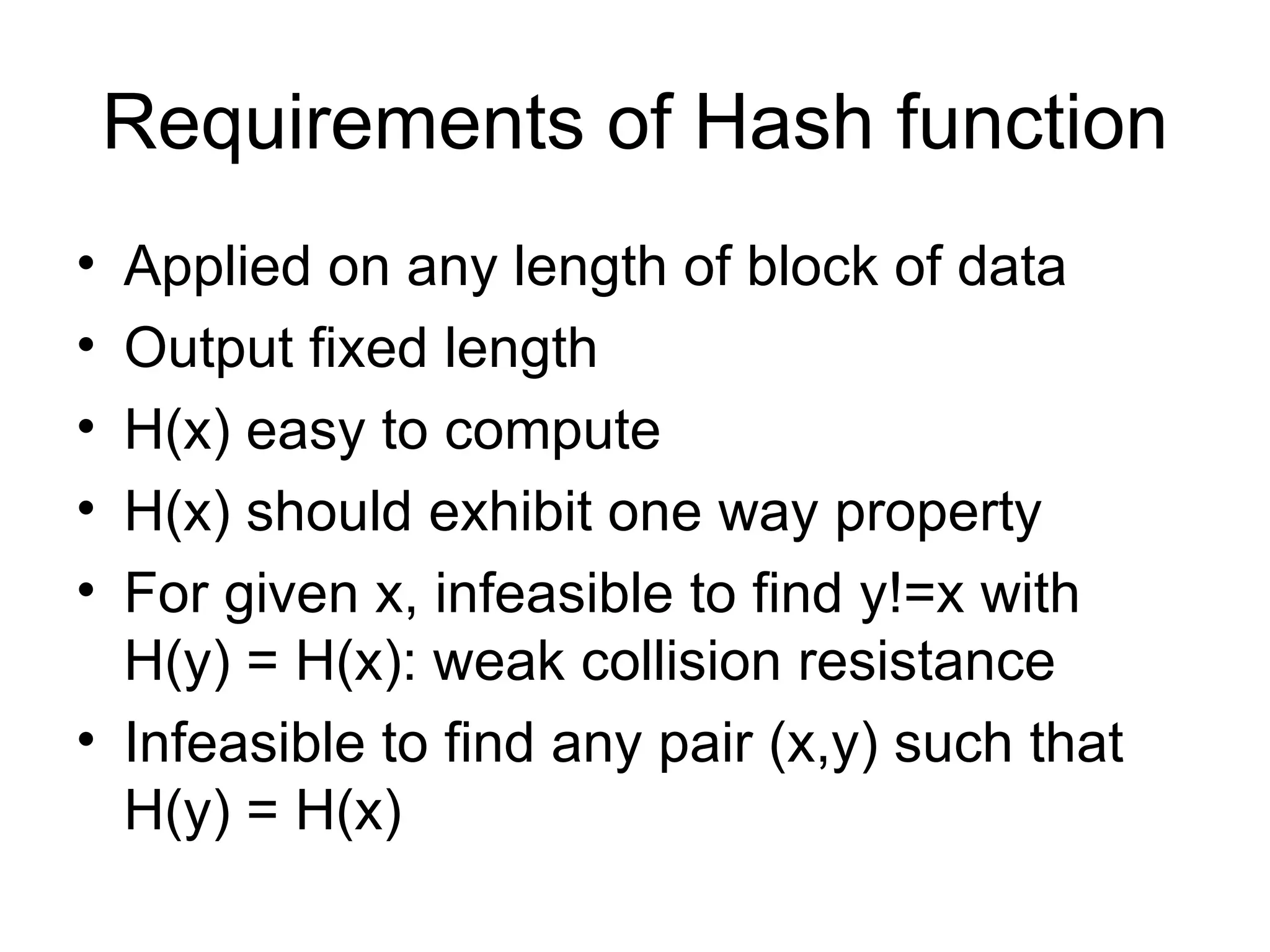
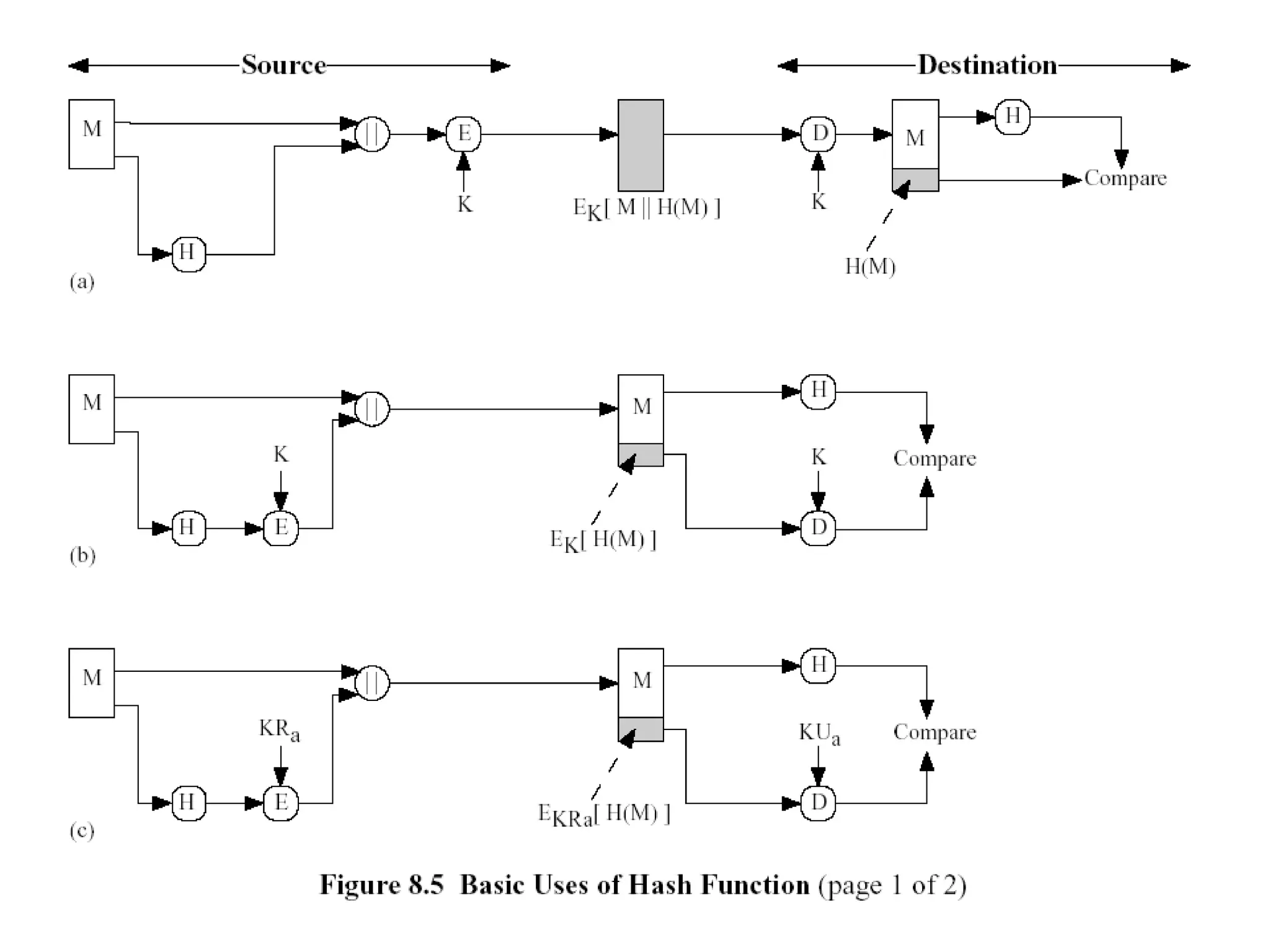
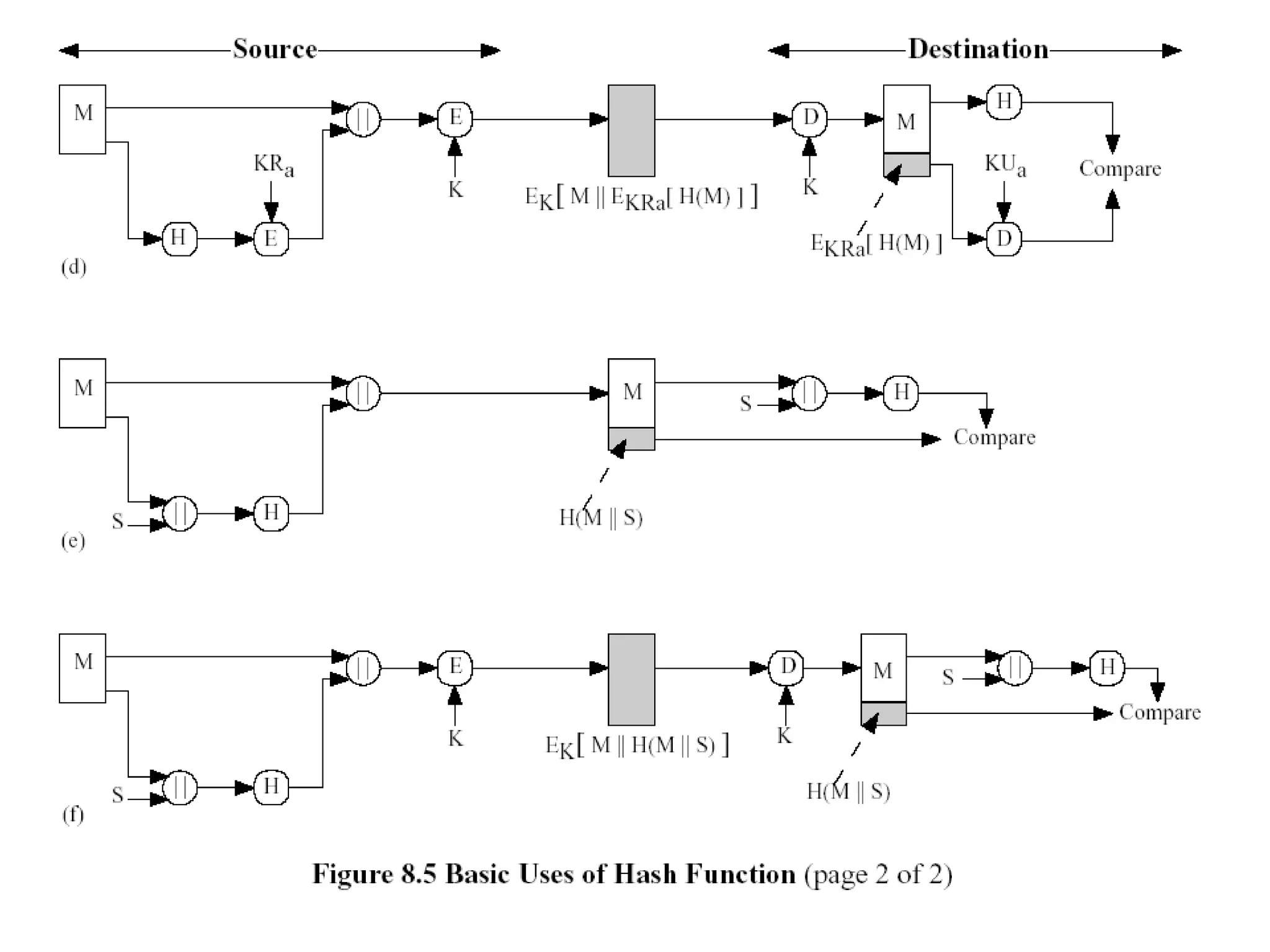
Message authentication provides a way to verify that a received message is from the alleged source and has not been altered. It includes mechanisms for non-repudiation by the source. Authentication functions include lower level authenticators and higher level functions that use authenticators to verify message authenticity. Message authentication codes are appended to messages by the sender and verified by the receiver recomputing the code. MAC attacks aim to find the key or authenticate incorrect messages without finding the key. Hash functions map messages to fixed length values to verify integrity.





![MAC requirements Knowing M and Ck(M) it should not be possible to make M’-> Ck(M’) = Ck(M) For any random M, M’; Pr[Ck(M) =Ck(M’)] should be 2 -n for n MAC bits If M’ = f(M); Pr[Ck(M) =Ck(M’)] should be 2 -n](https://image.slidesharecdn.com/messageauthentication-091201224745-phpapp02/75/Message-Authentication-11-2048.jpg)





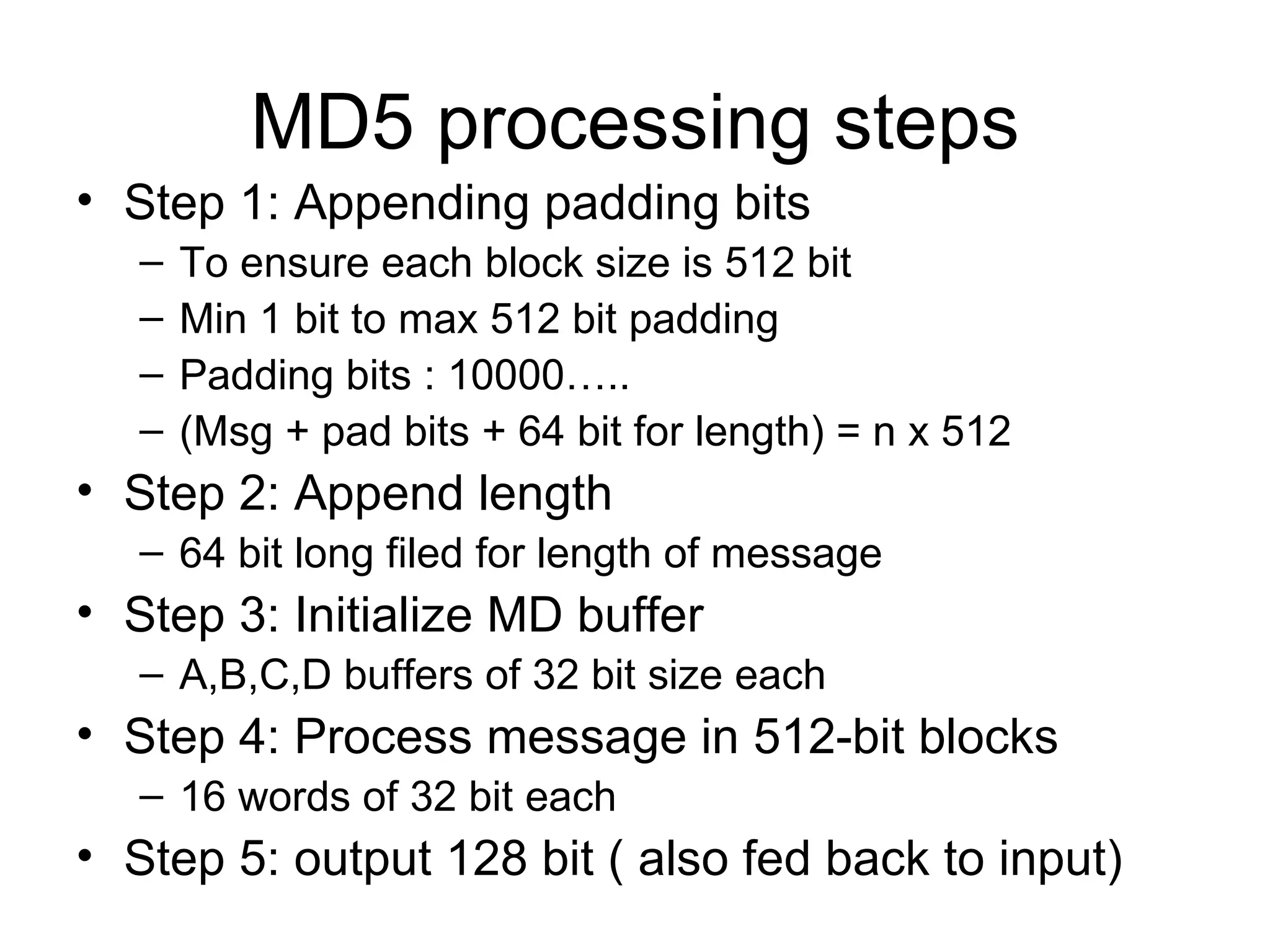
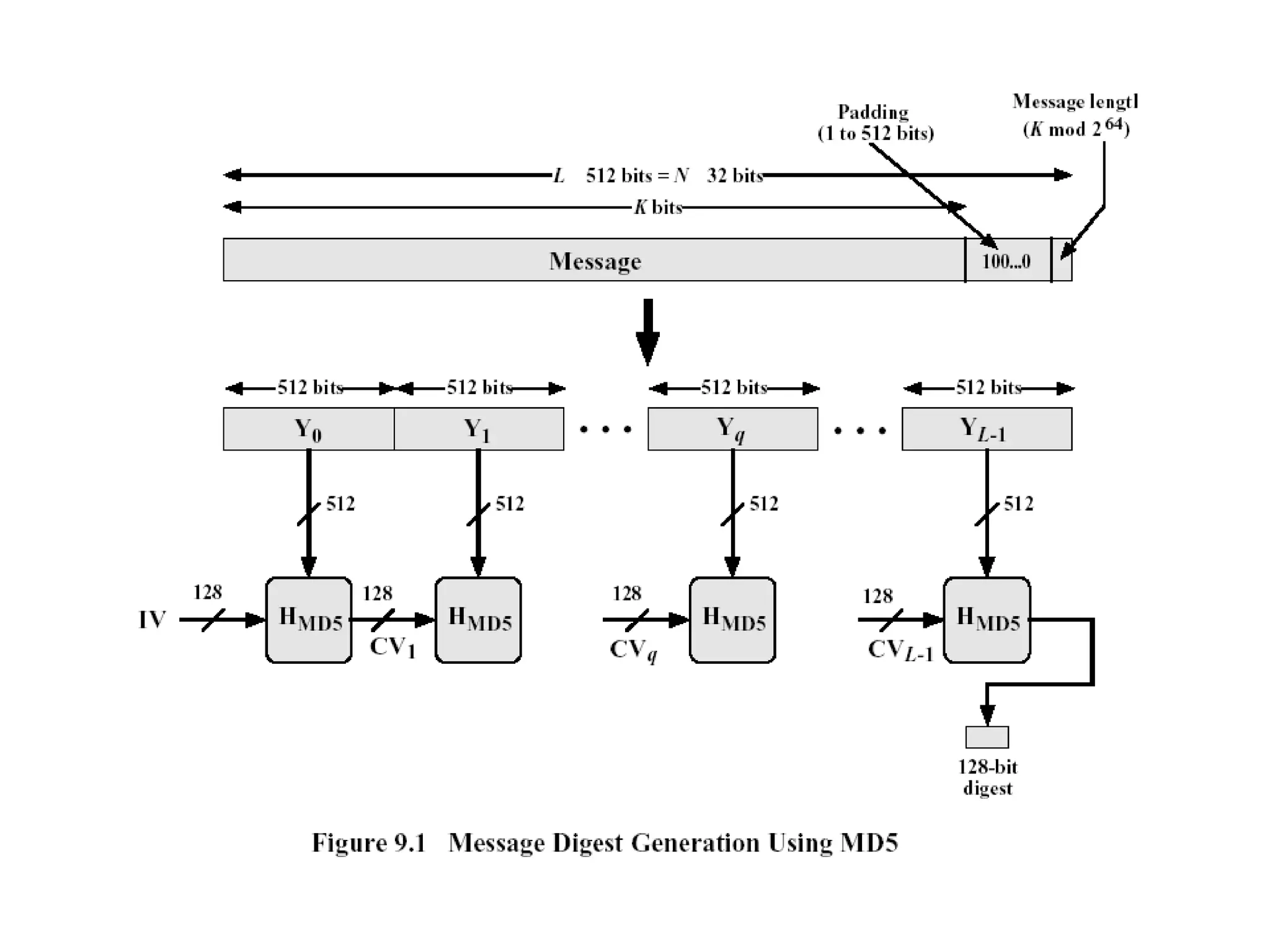
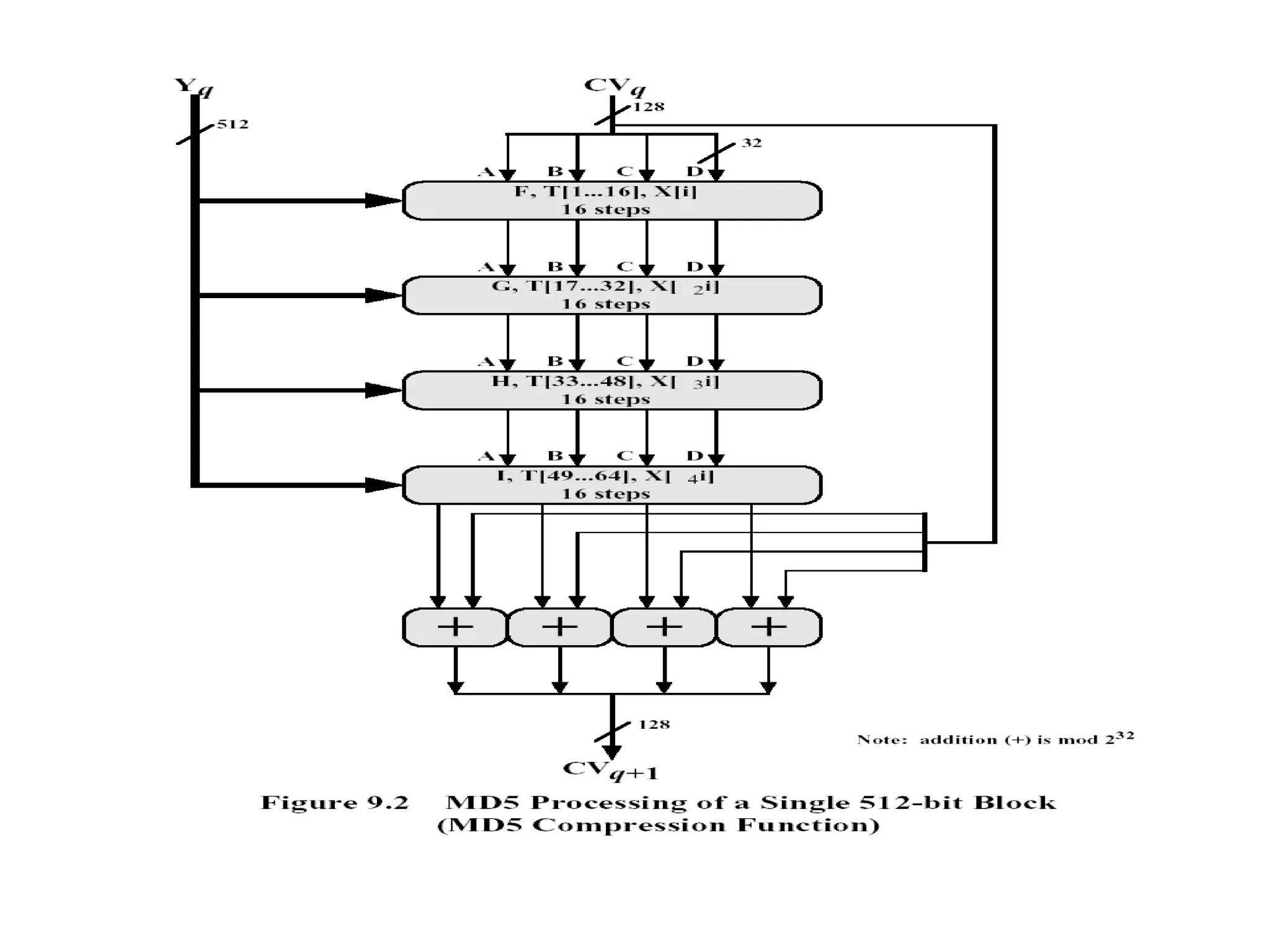
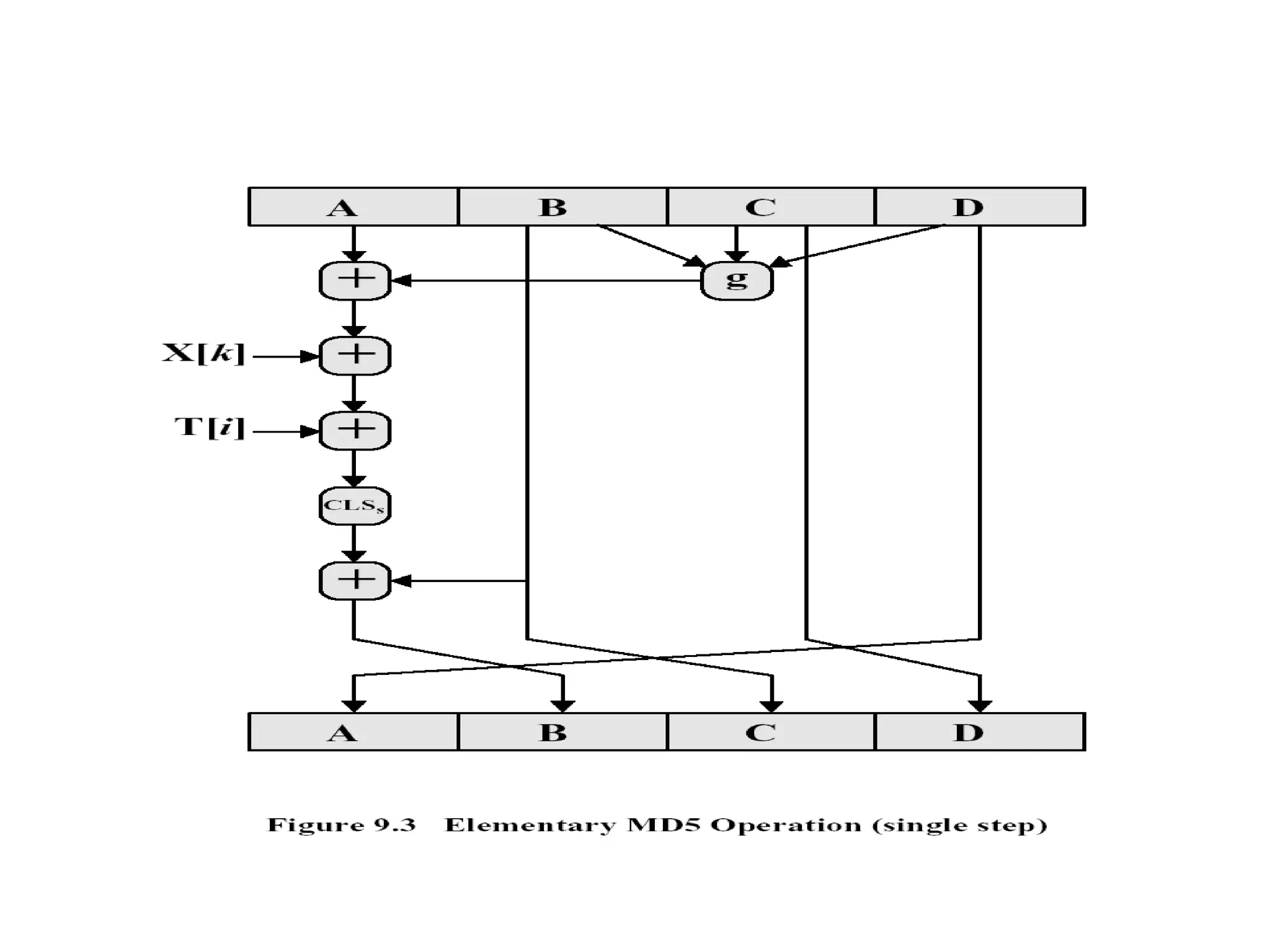
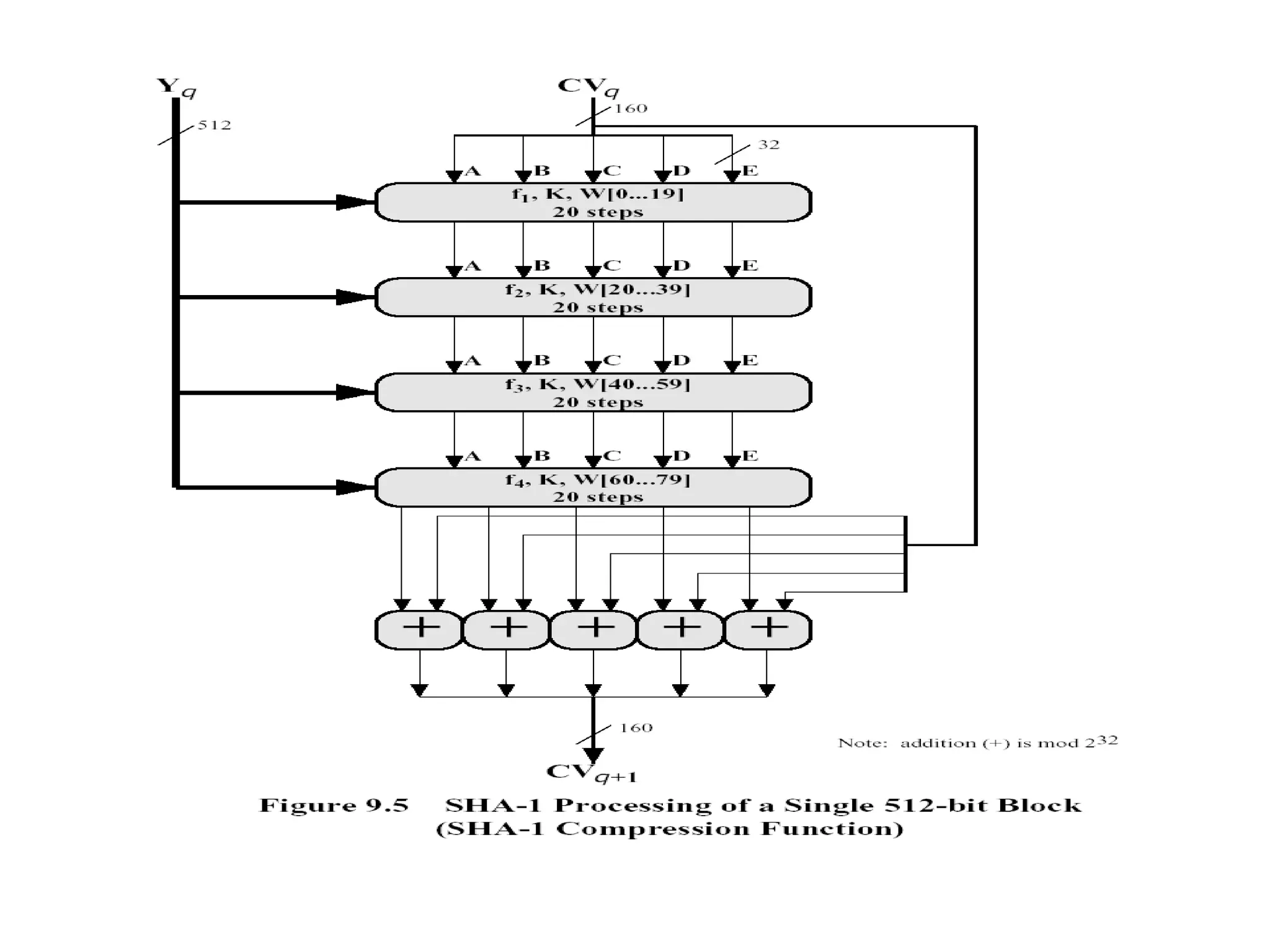
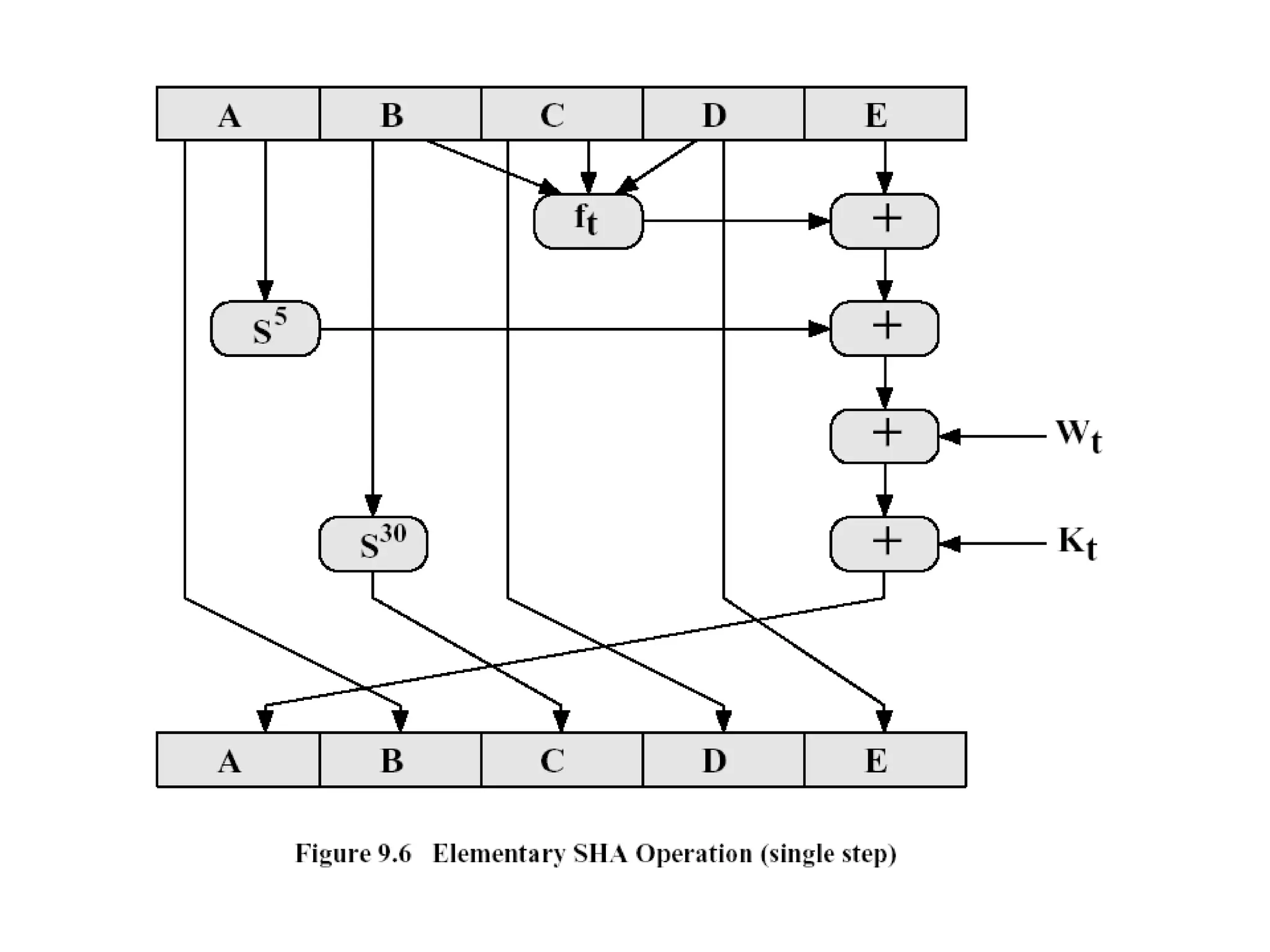
![Step 4 Four rounds 16 steps in each round Details of each round Inputs A,B,C,D ( 32 bits each) 512 bit block Message ( 16 x 32) T[ i ] 32 bit array of cont from sin value Processing F,G,H &I functions in each round Output A,B,C,D](https://image.slidesharecdn.com/messageauthentication-091201224745-phpapp02/75/Message-Authentication-23-2048.jpg)