Session| Microsoft Purview DLP Deep Dive
Presenter | Nikki Chapple 2 x MVP and Principal Cloud Architect at CloudWay
Event | Workplace Ninjas Norway
Format | In Person | Oslo | Norway
Date | 11 June 2025
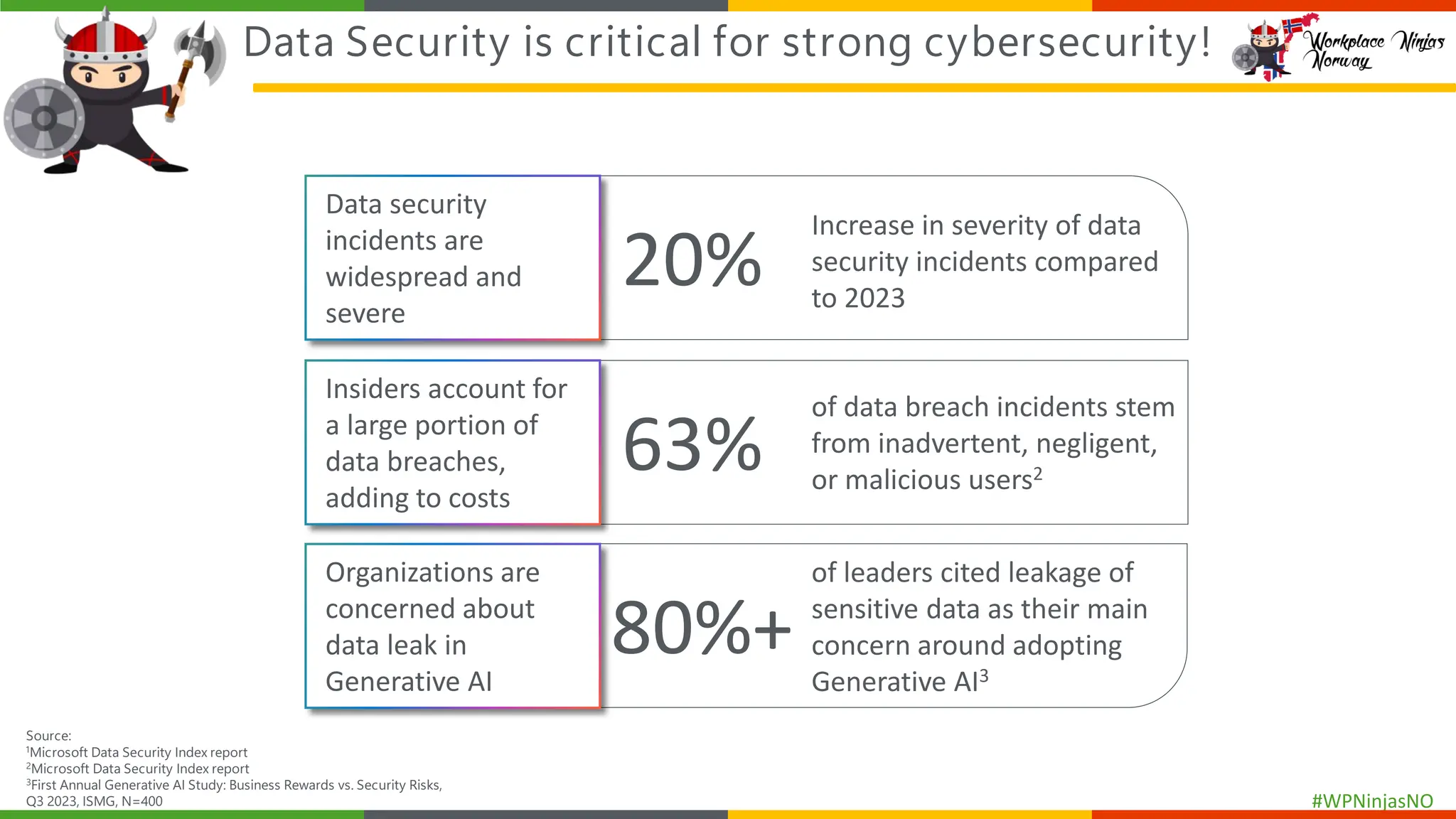
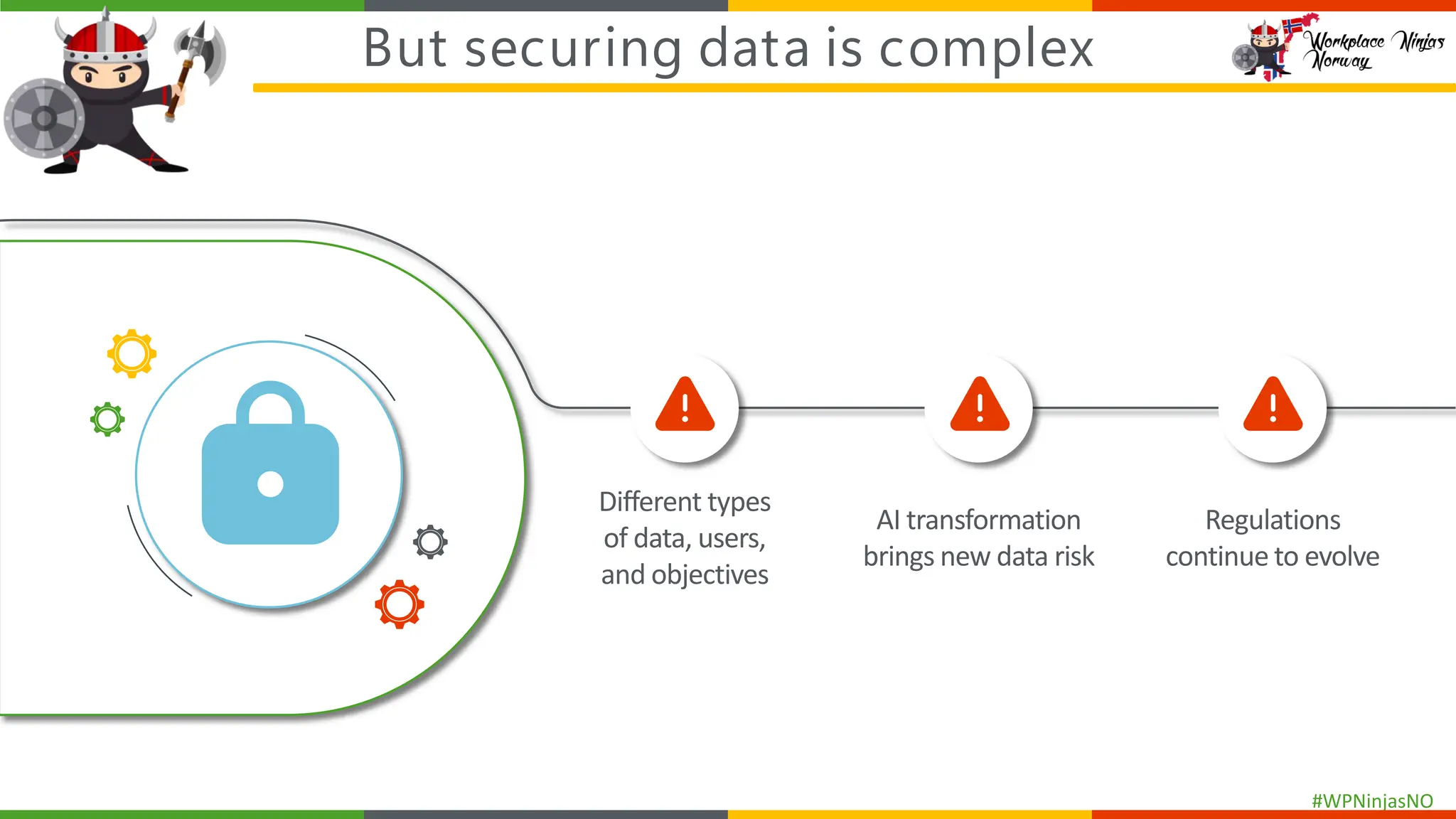
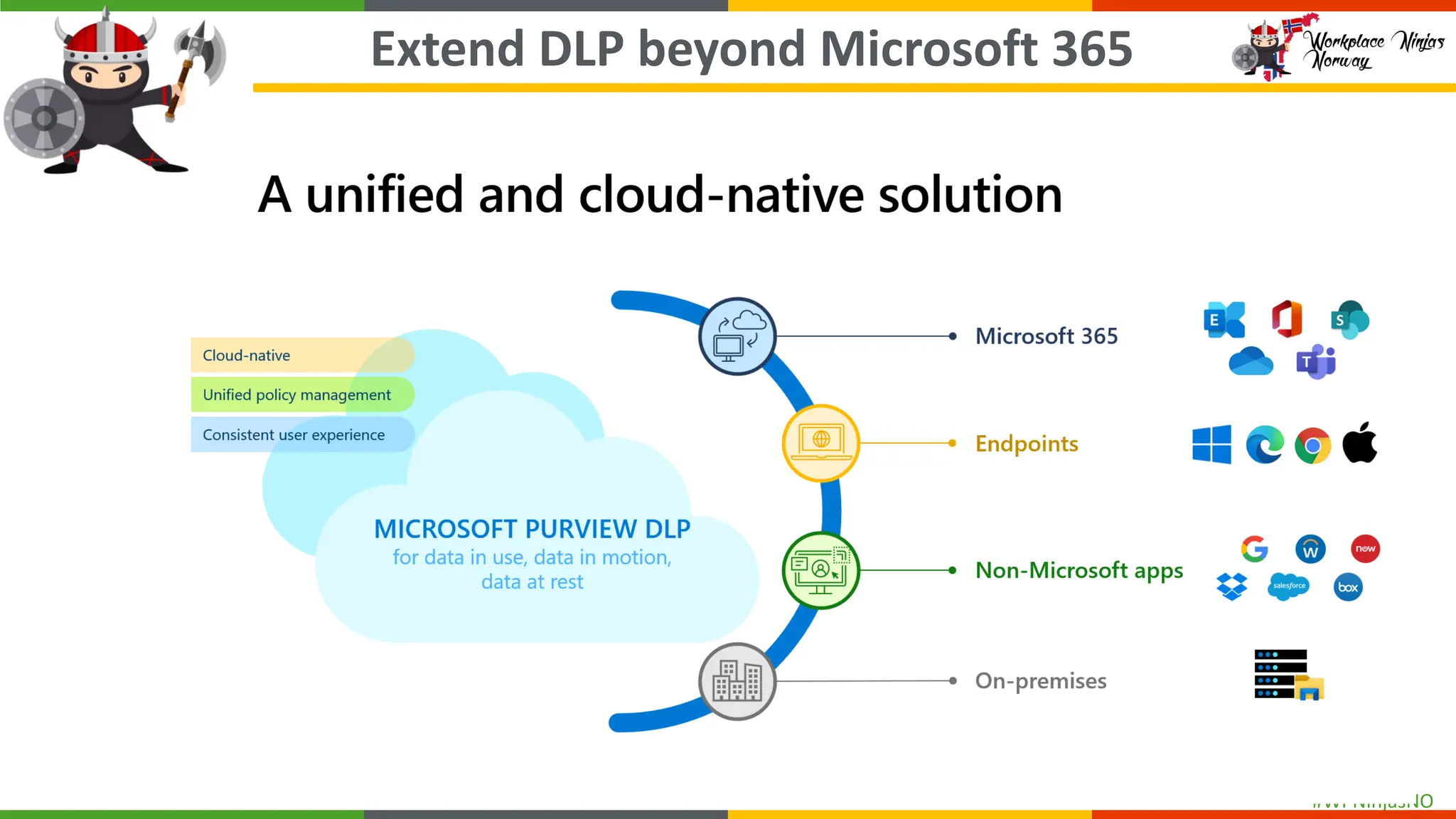
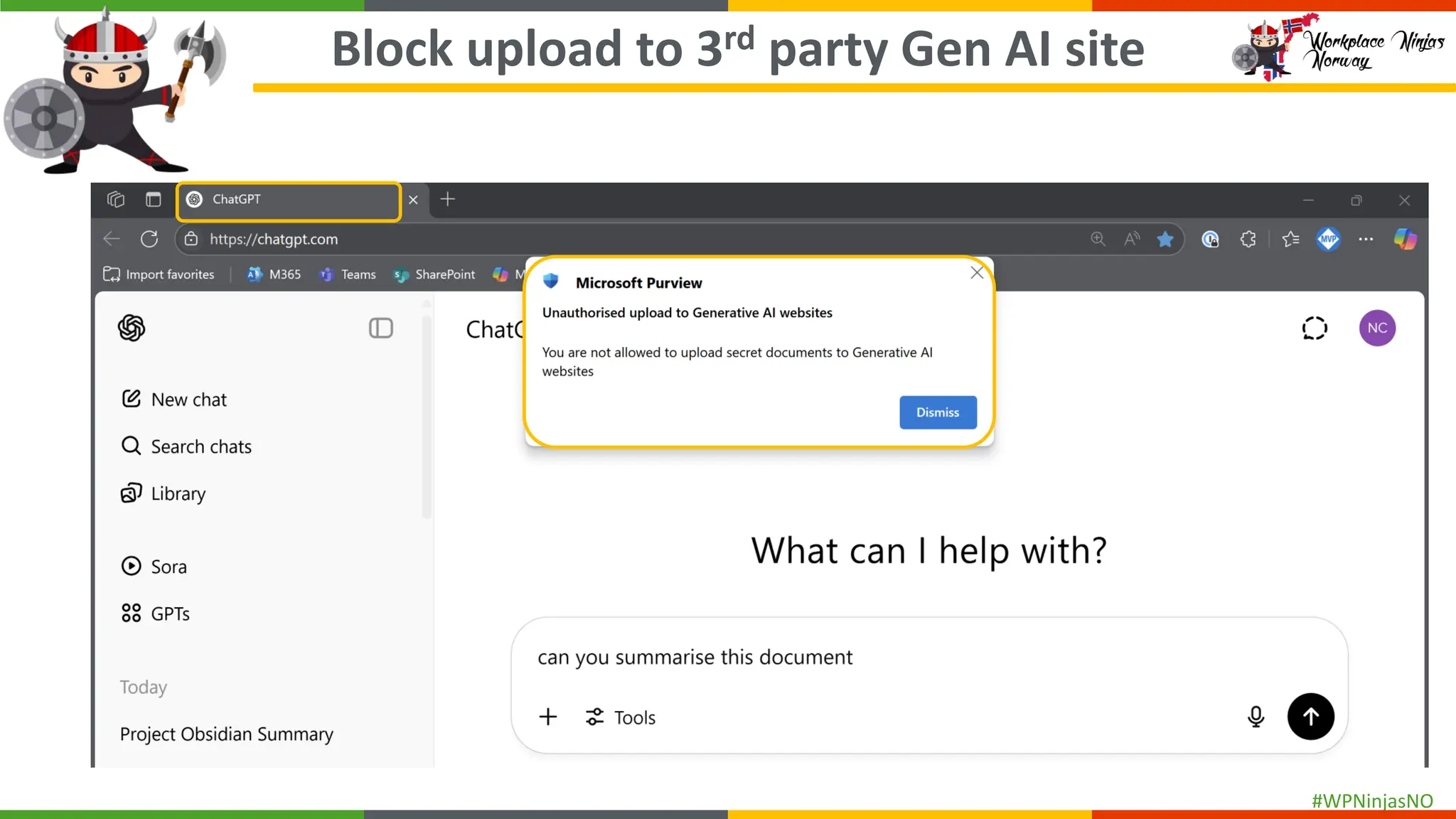
As cyber threats and data breaches continue to evolve, safeguarding sensitive data within Microsoft 365 becomes increasingly critical. The integration of generative AI tools in business workflows further amplifies the risk of inadvertently exposing sensitive information. By deploying Microsoft Purview Data Loss Prevention (DLP) across Microsoft 365, organizations can better protect their sensitive data and mitigate the risks associated with accidental and malicious oversharing.
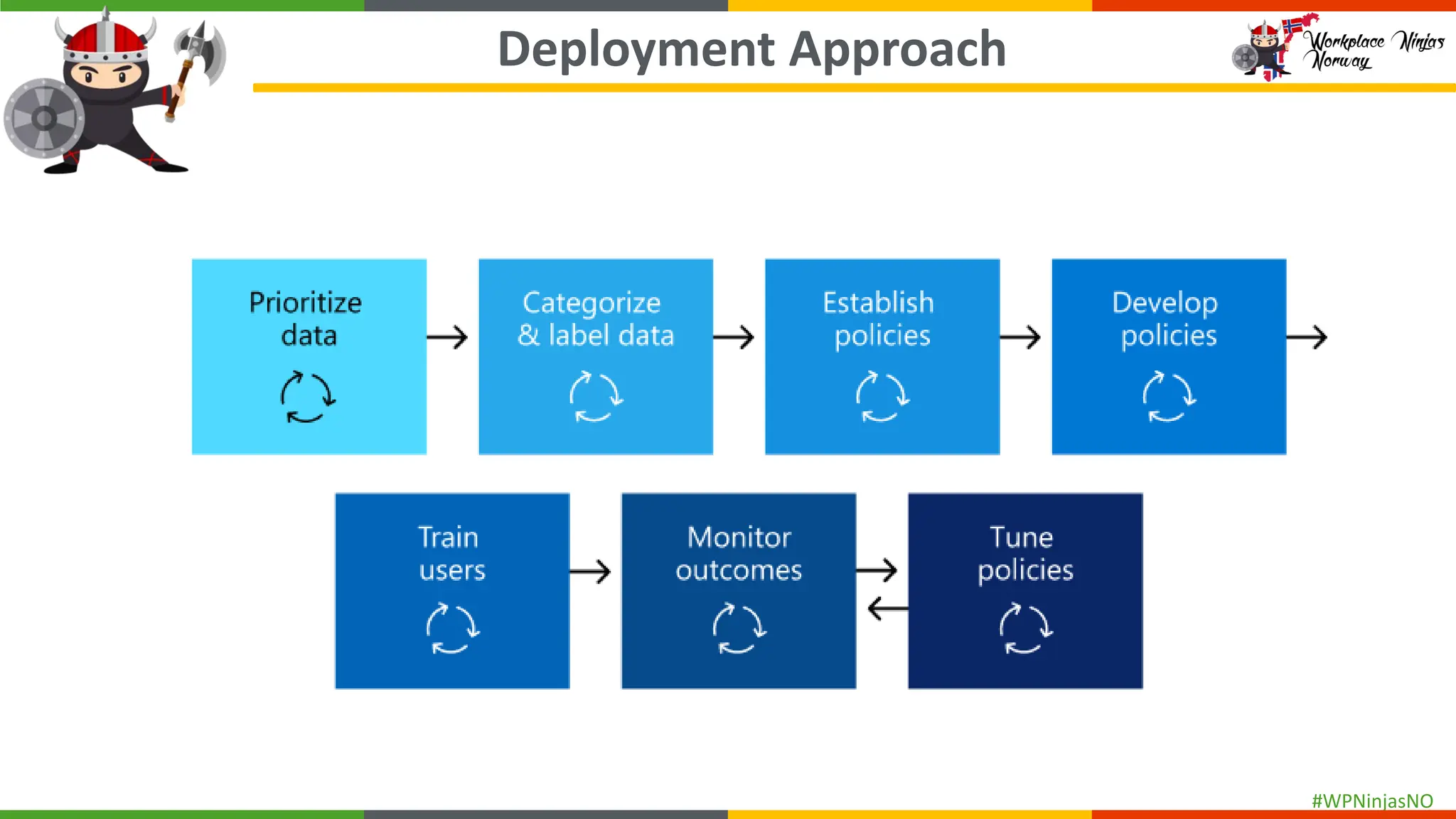
This session is a hands-on demo on configuring and deploying Microsoft Purview DLP policies across Microsoft 365 apps, endpoints, and Copilot integrations to protect sensitive data and mitigate oversharing.
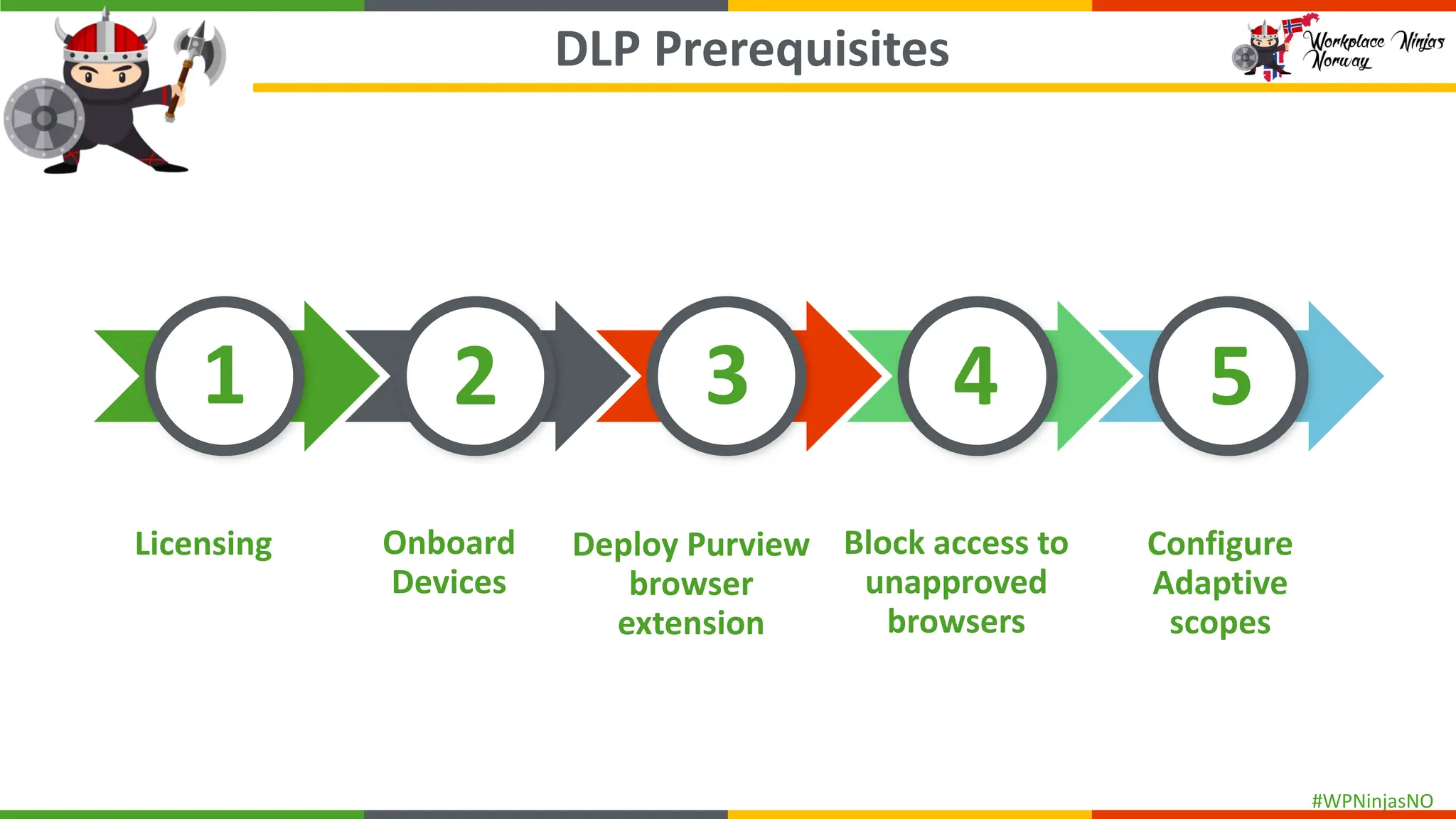
Covering
- What is DLP
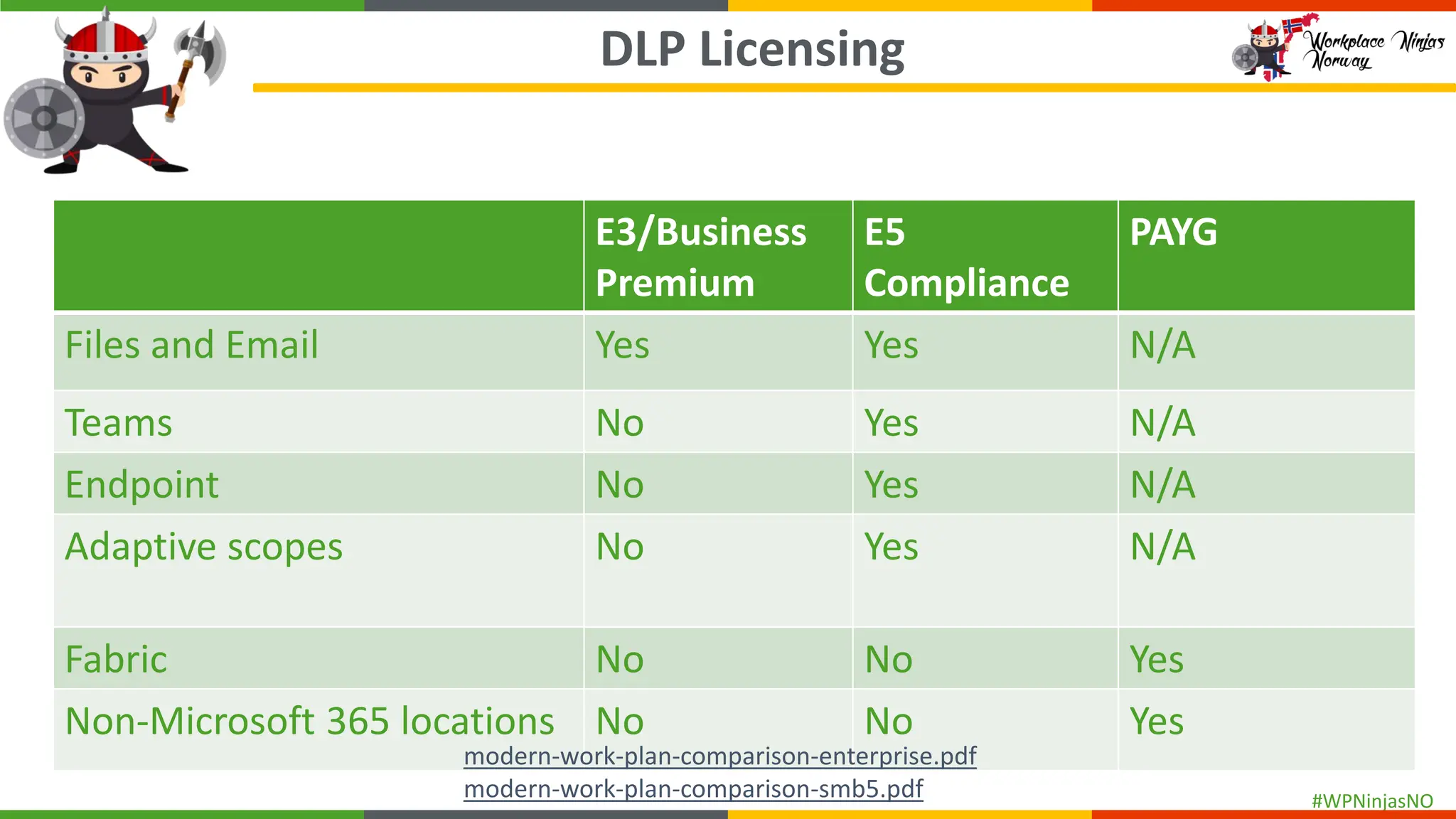
- Licensing
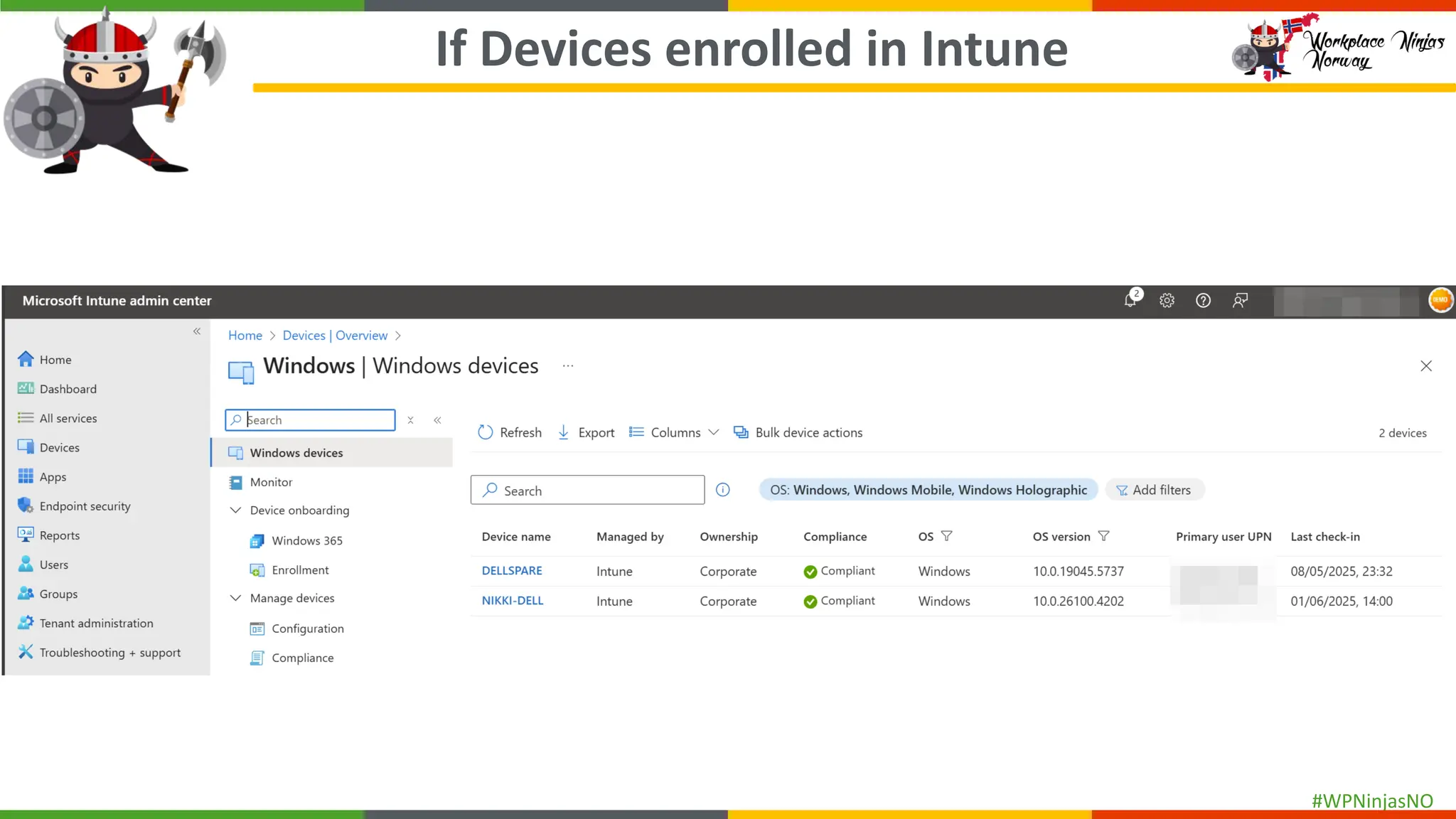
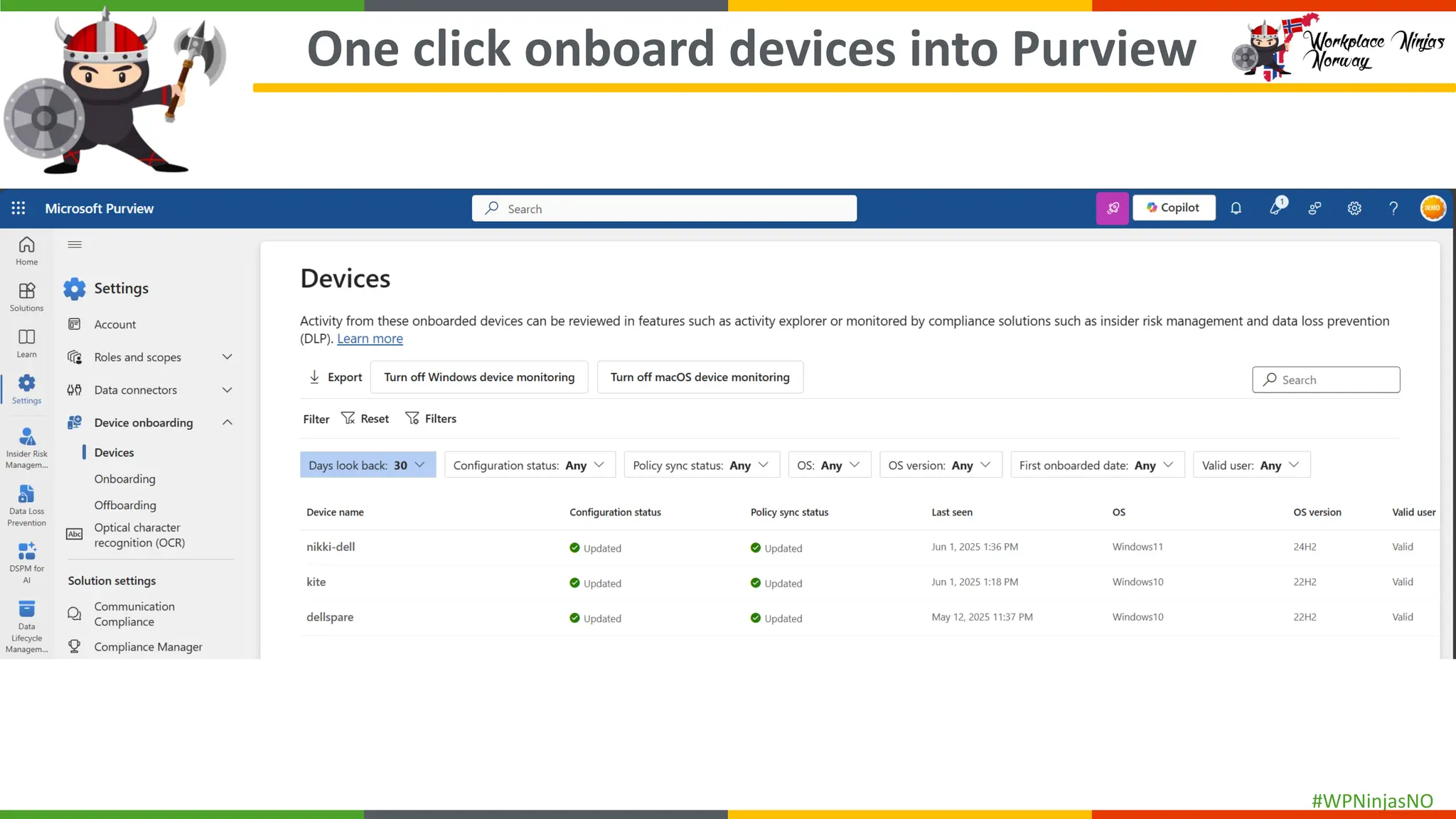
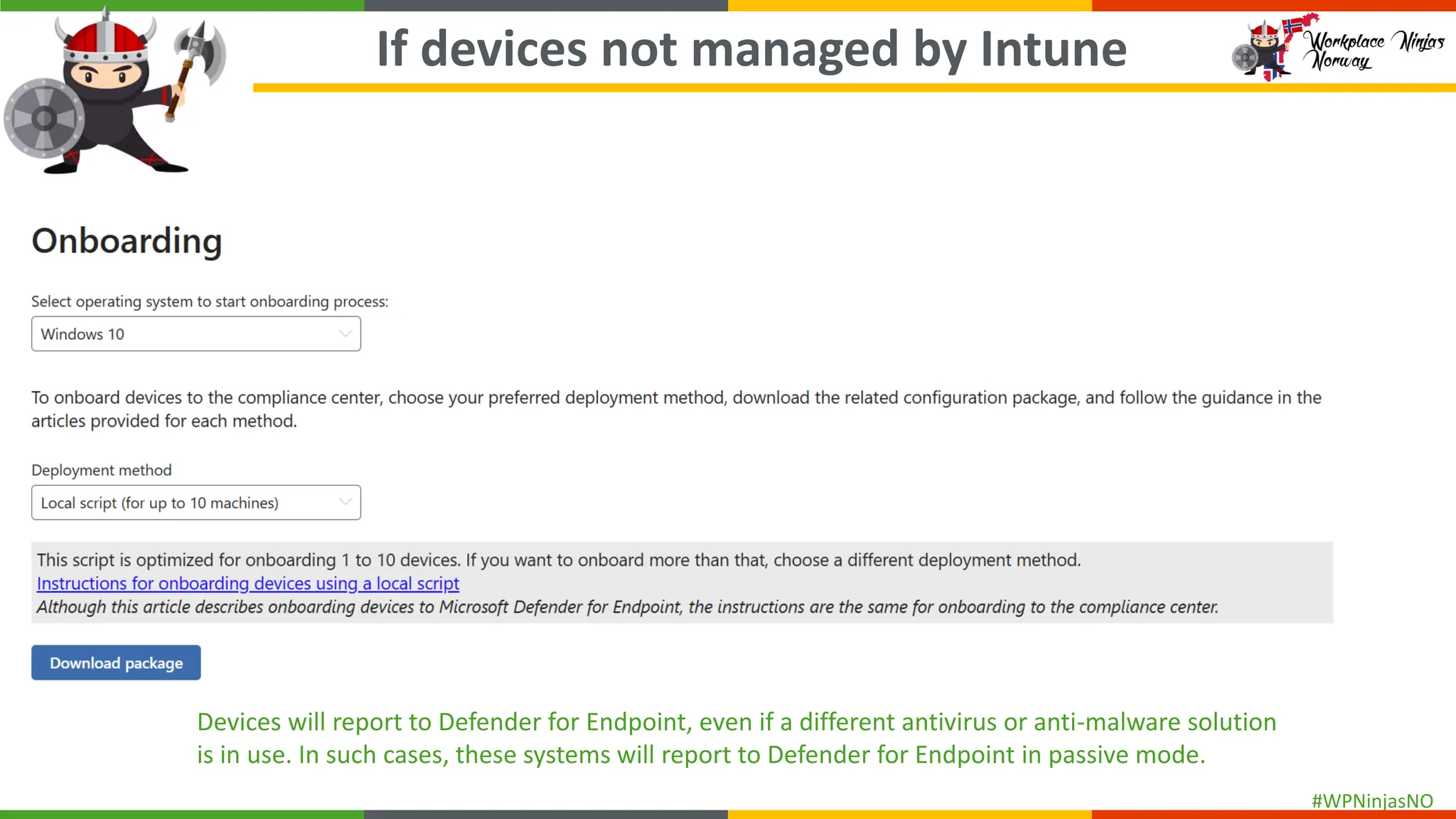
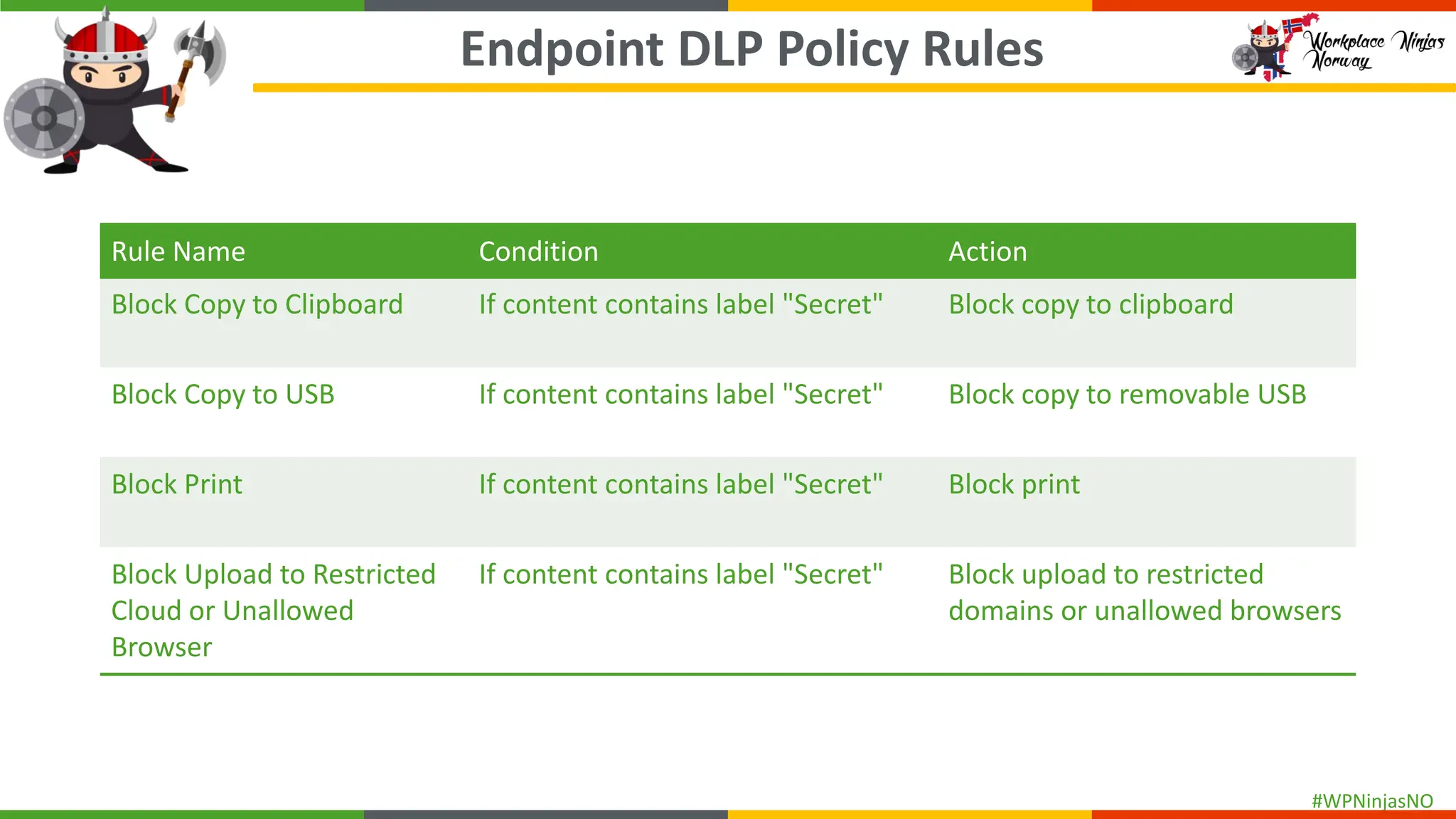
- Onboarding devices into Purview for EndPoint DLP
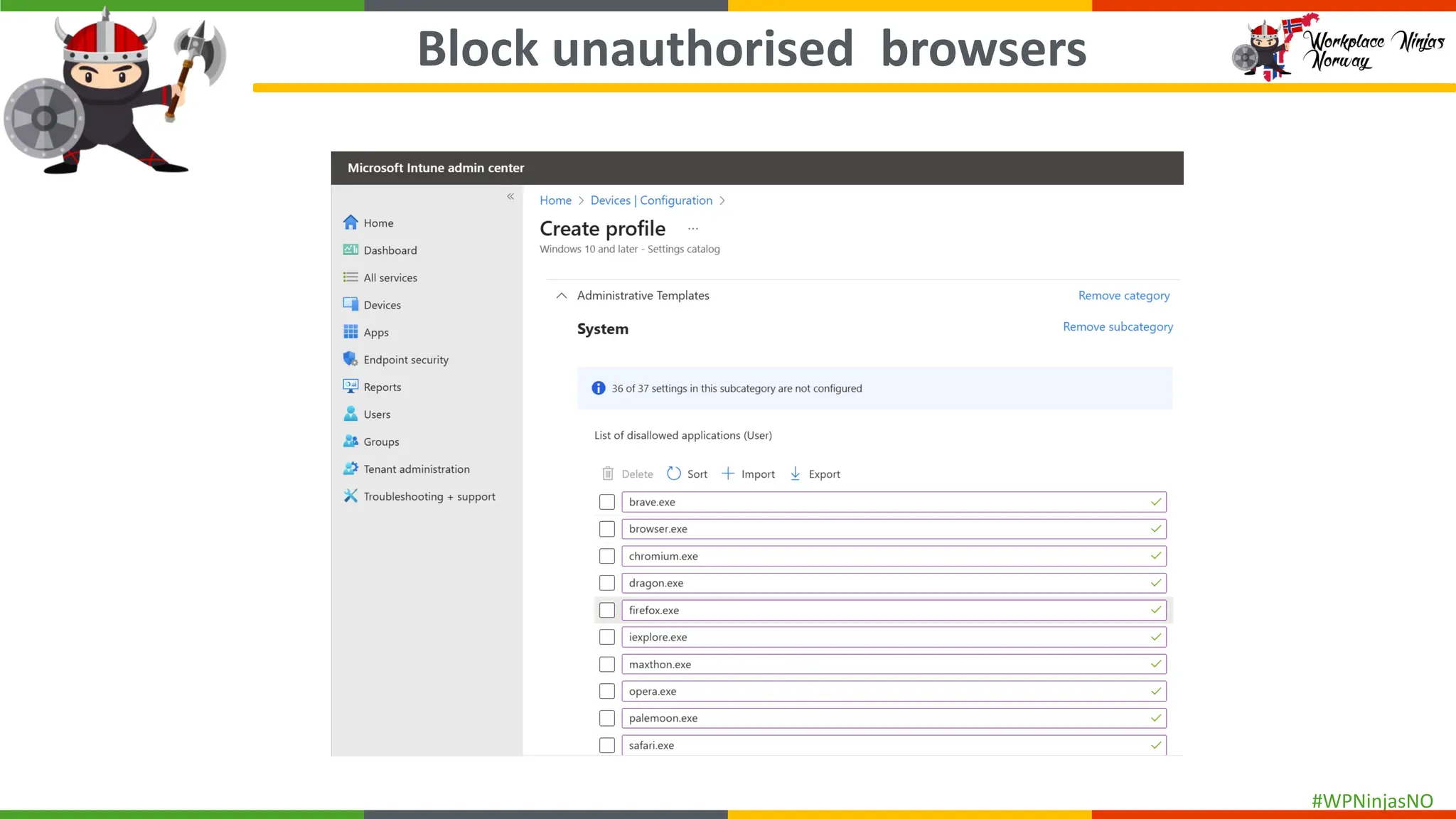
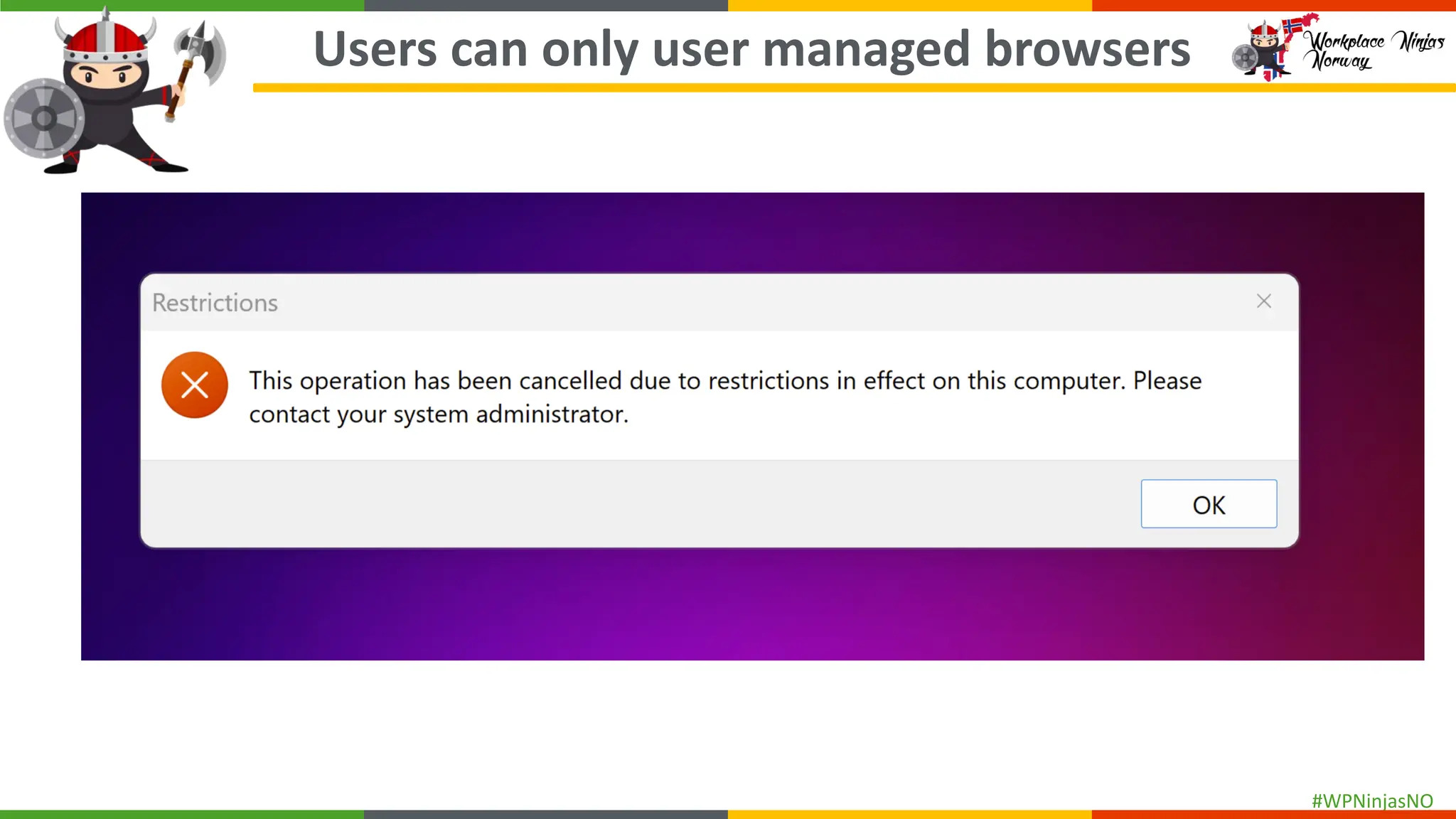
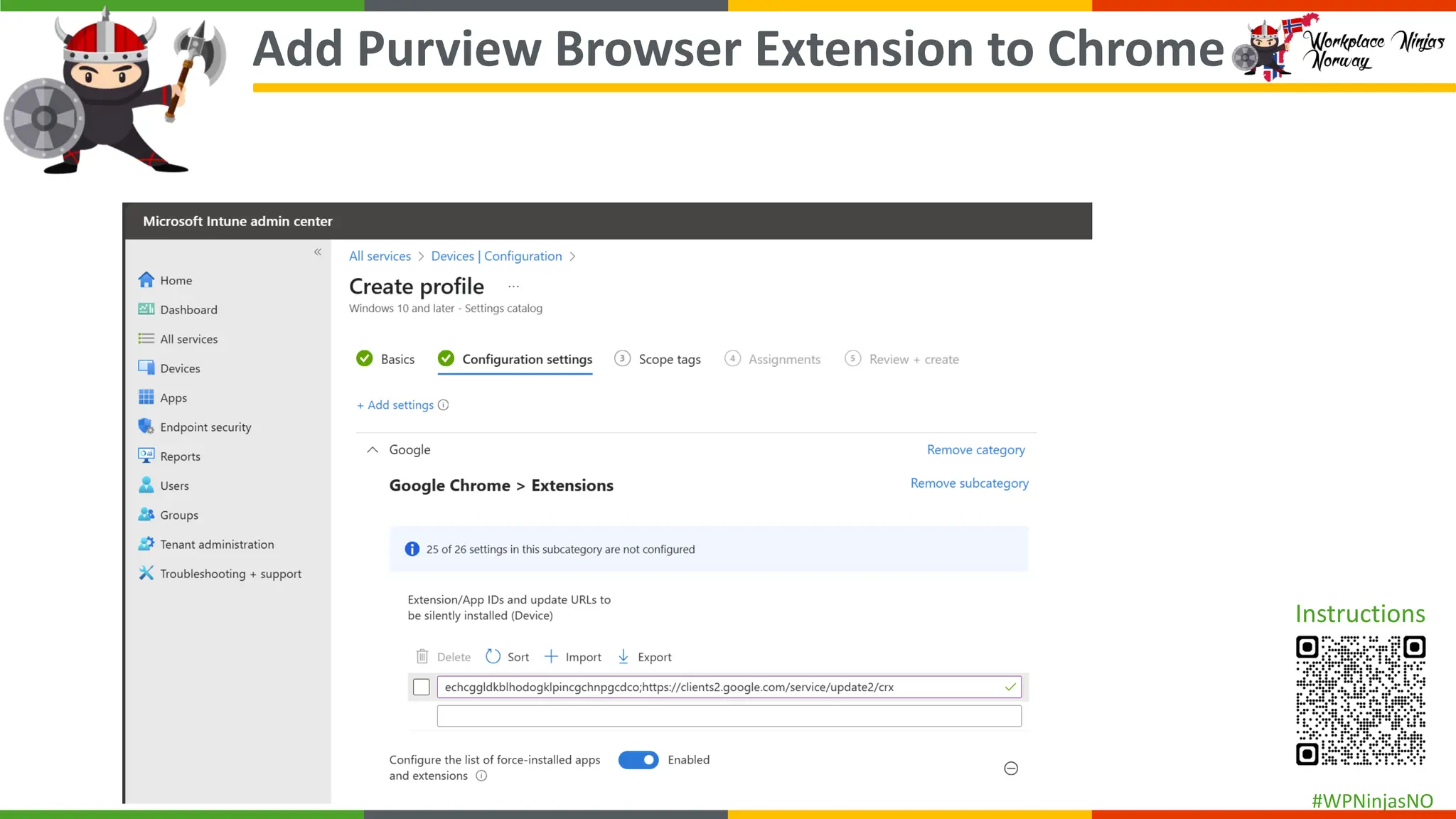
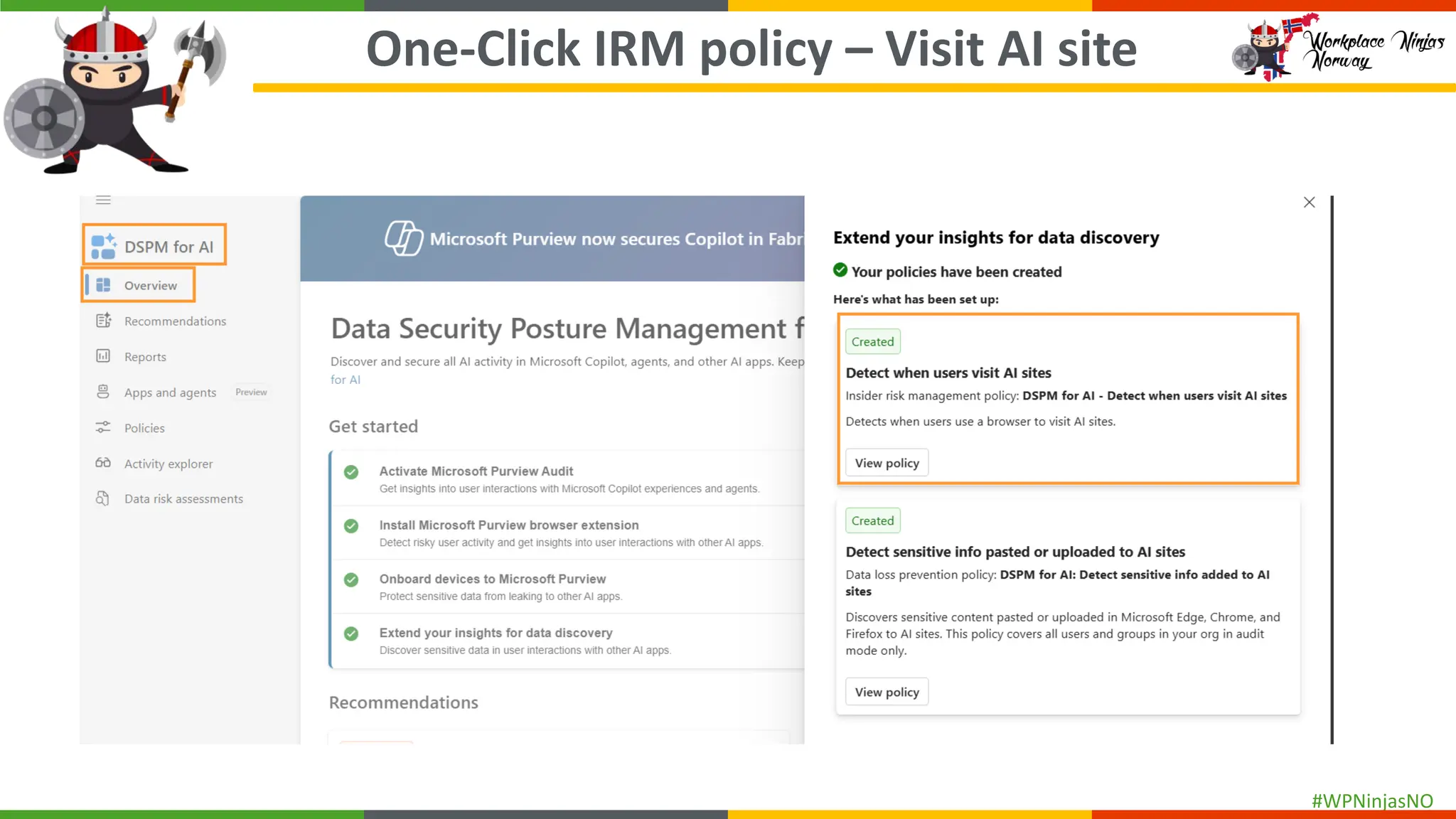
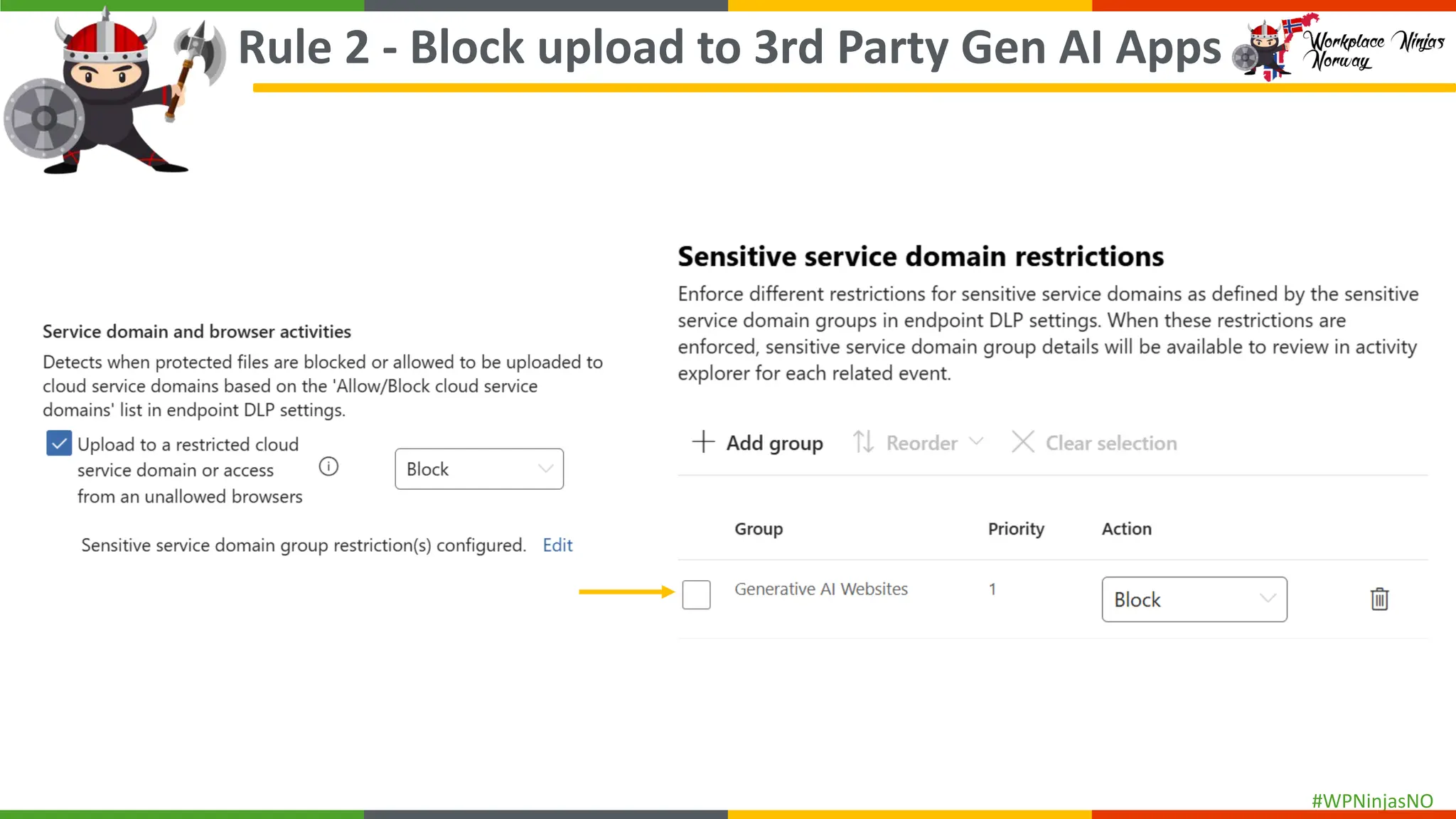
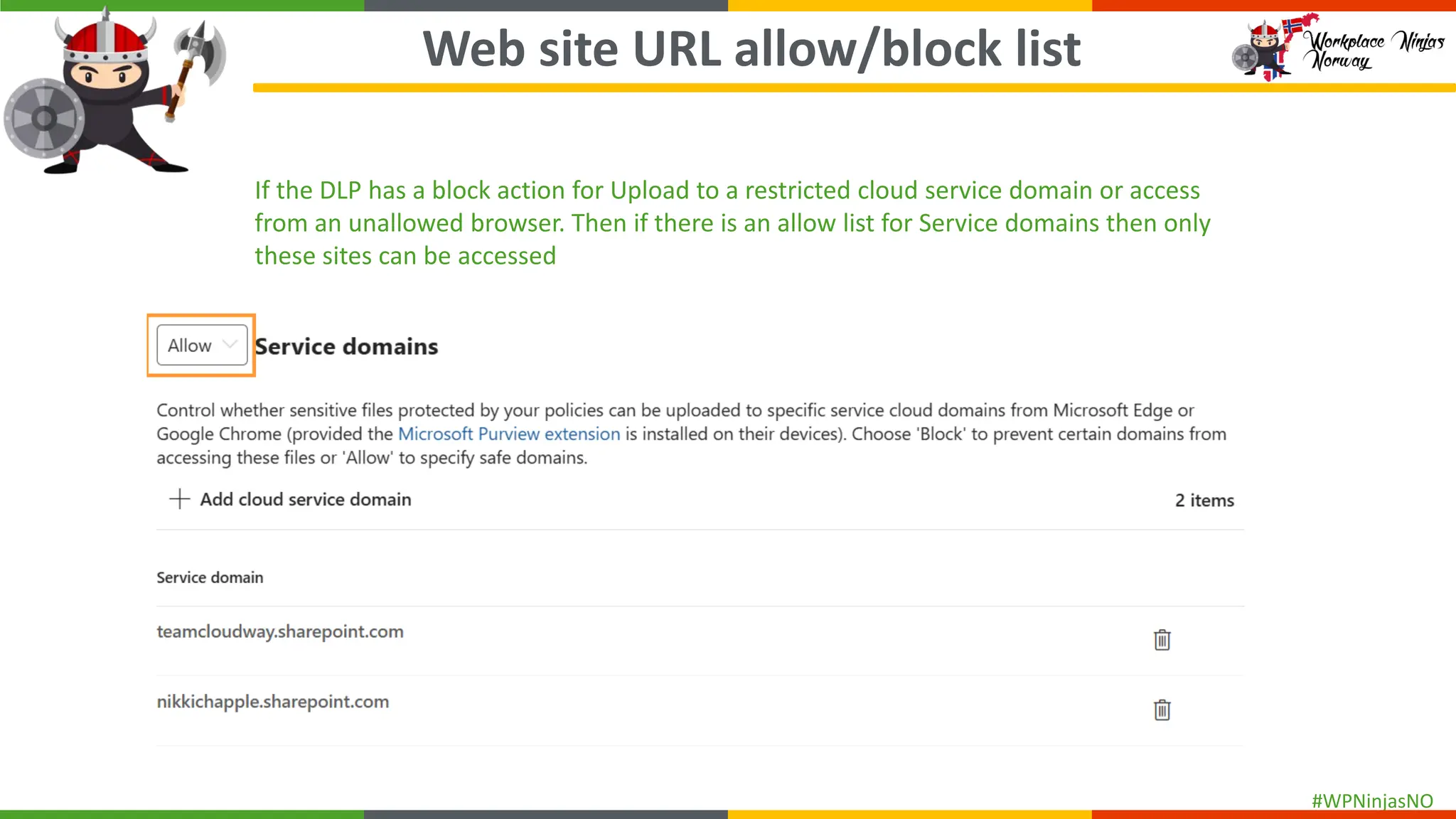
- Block Unauthorised Browsers
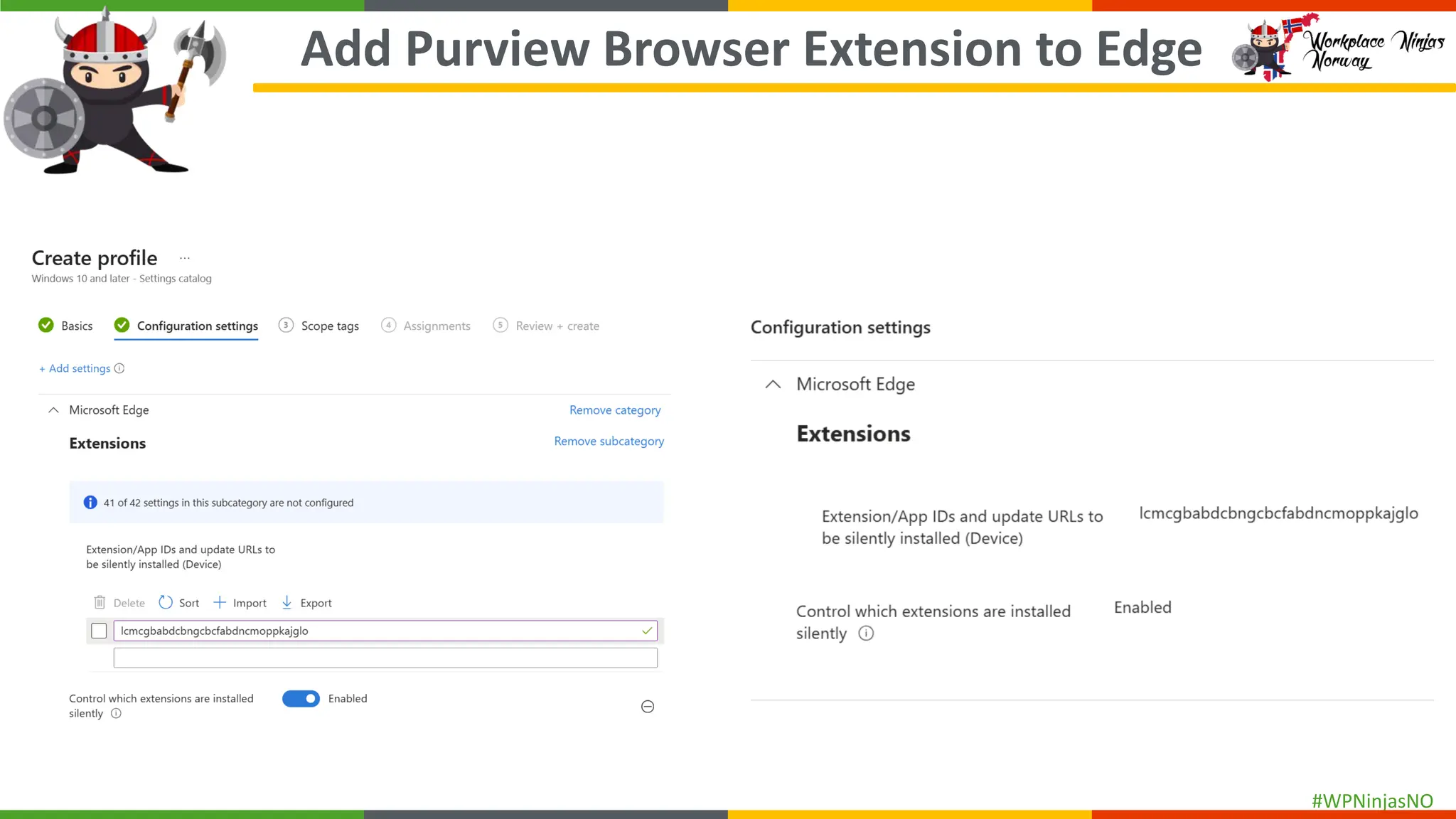
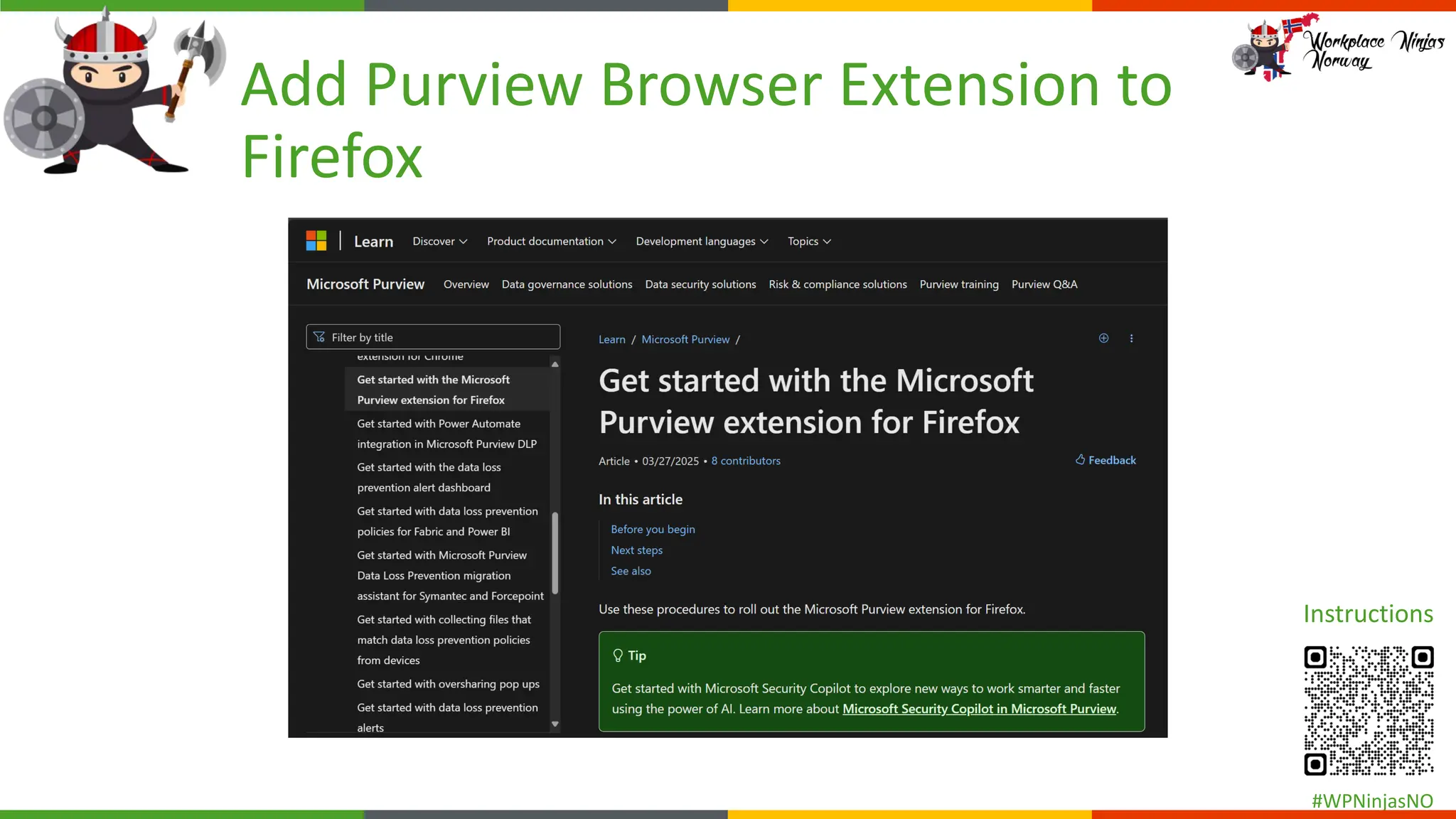
- Add Purview Browser Extension
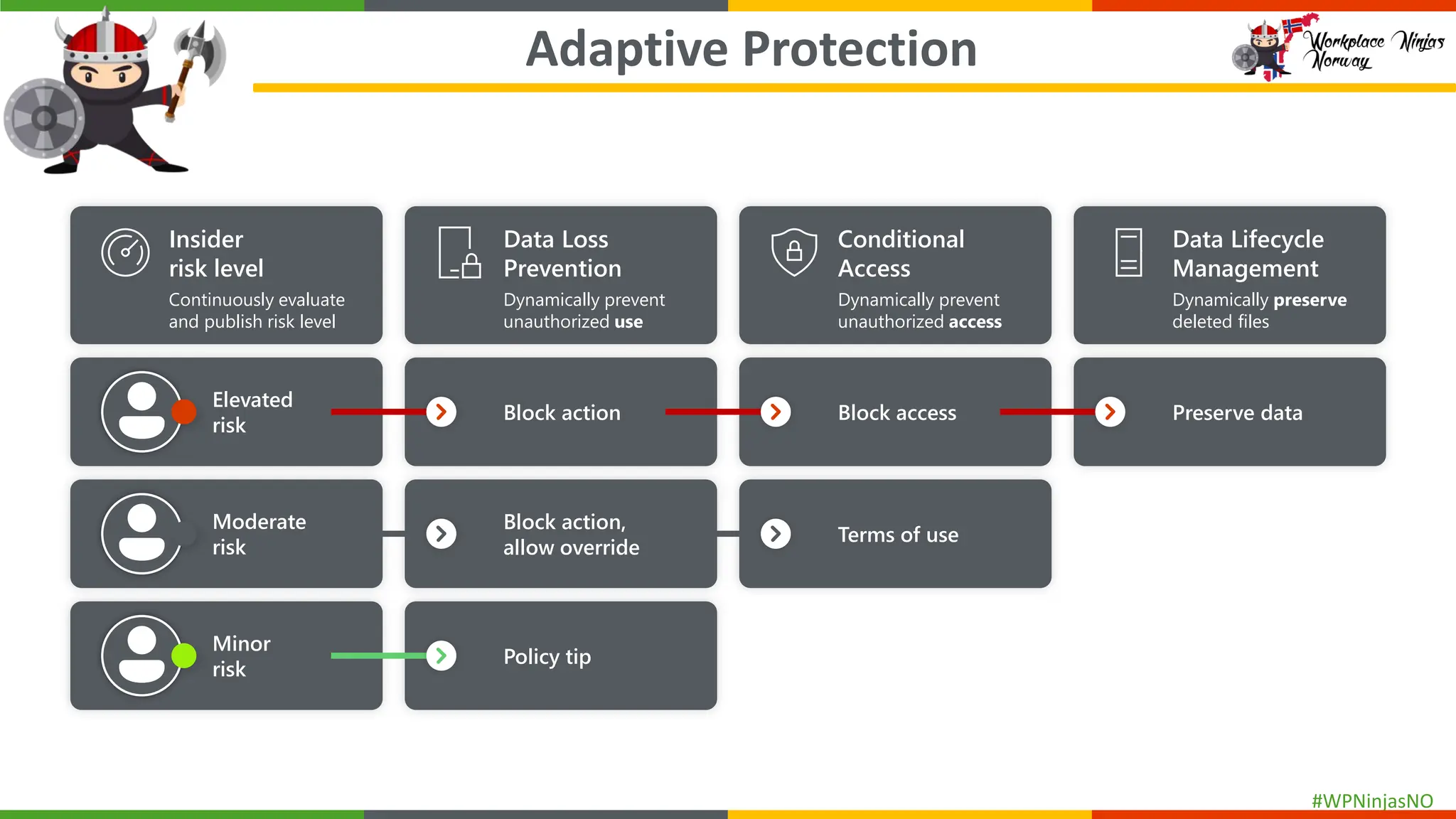
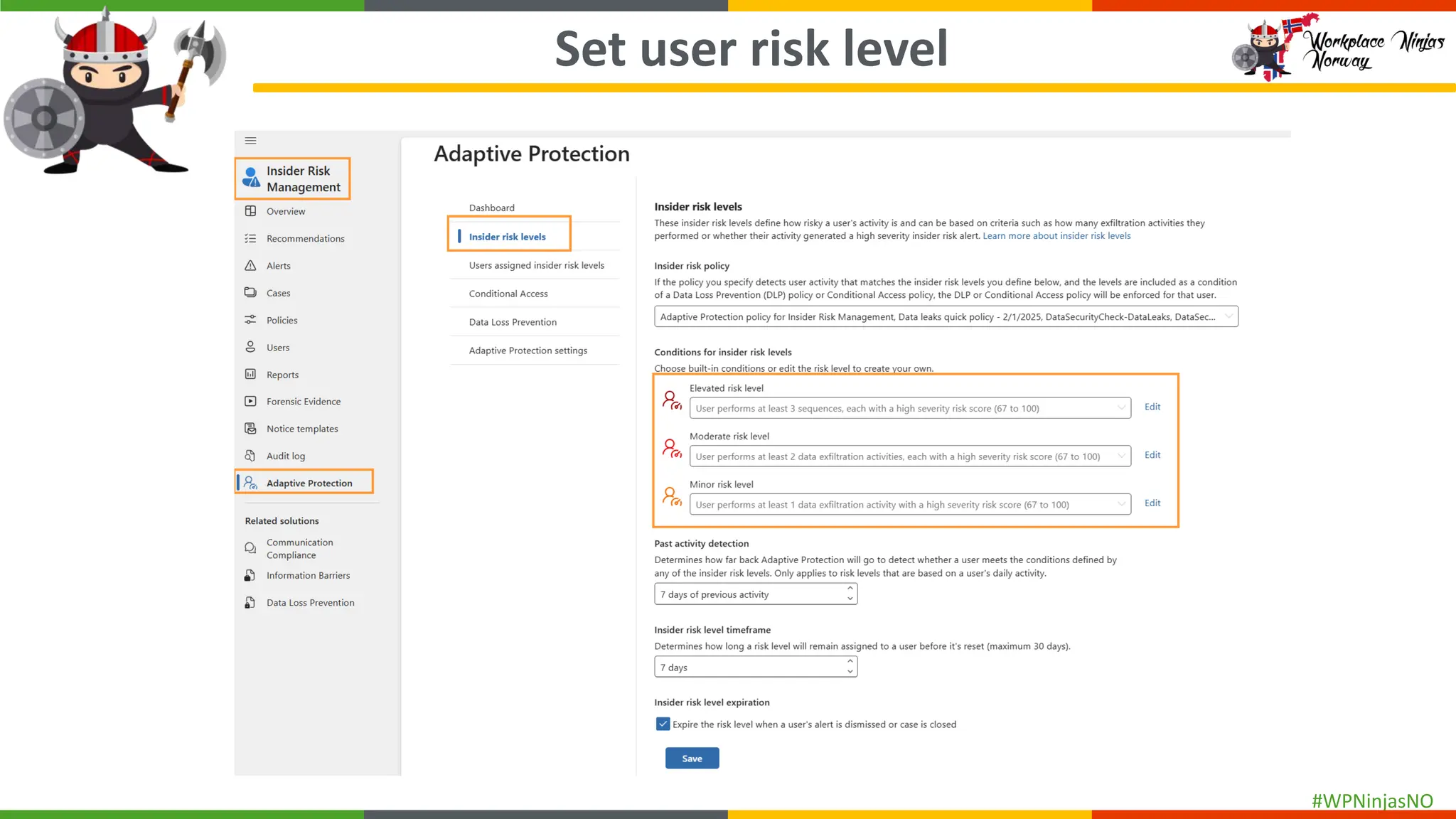
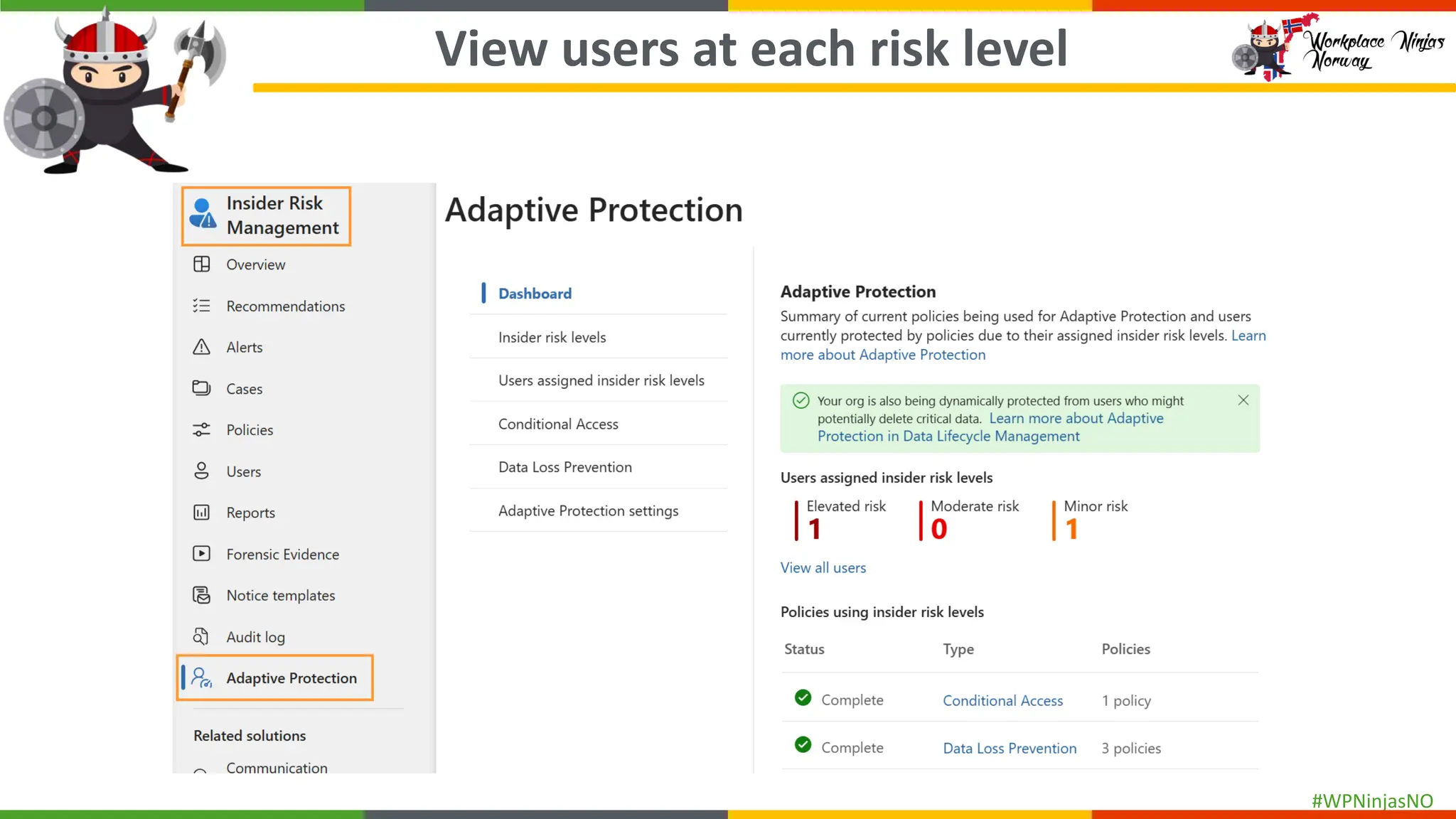
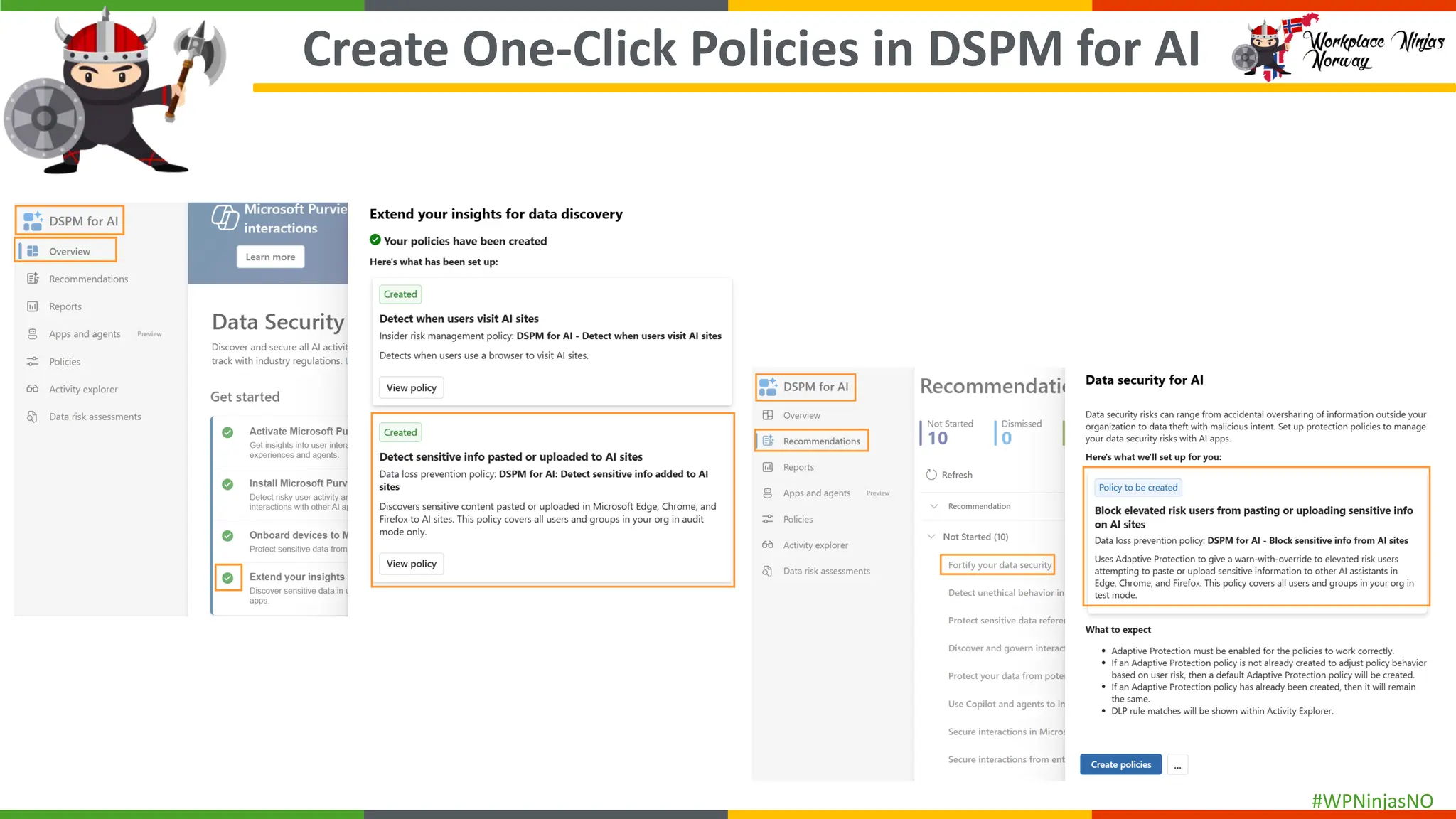
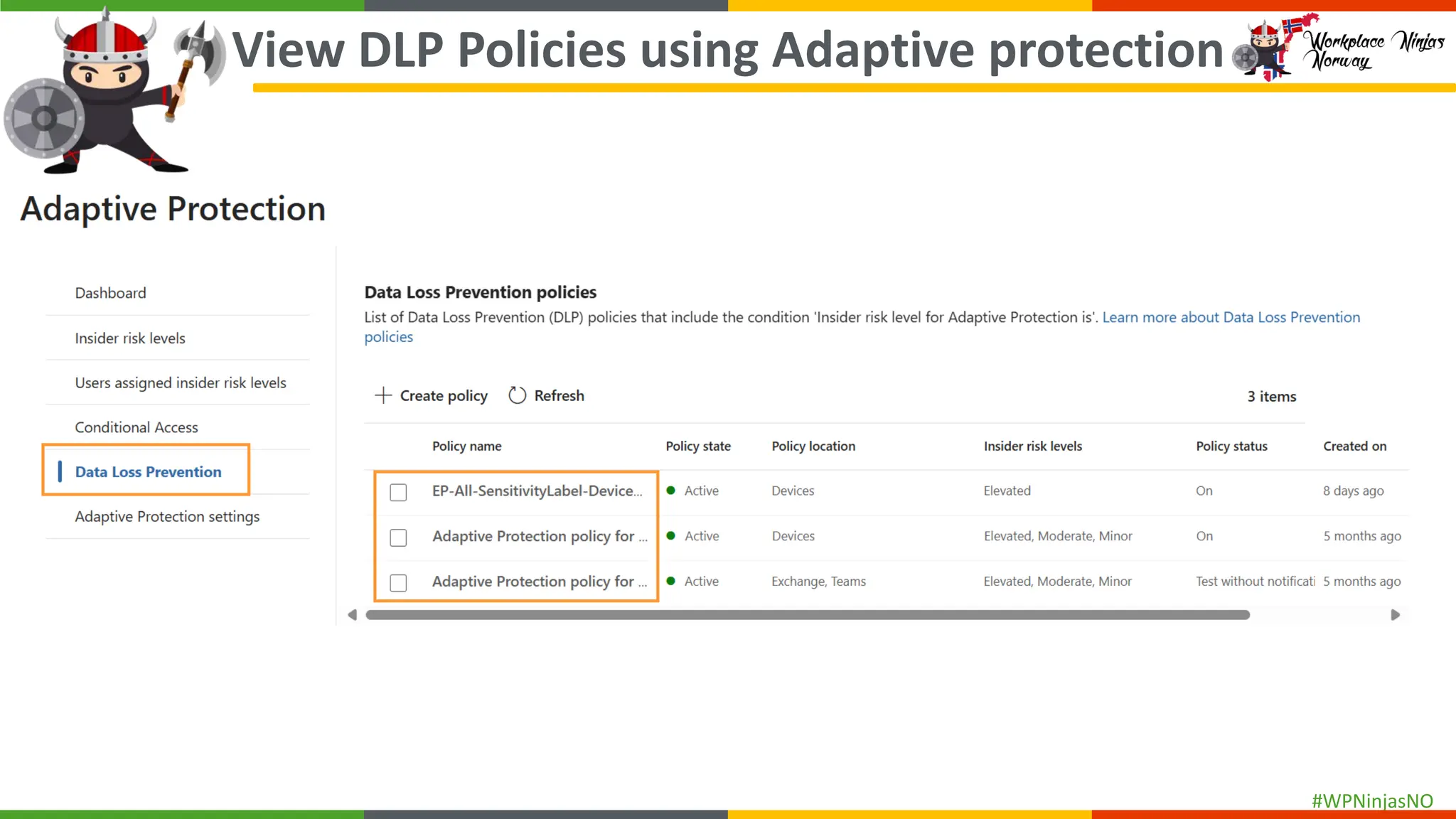
- Set up Adaptive Protection
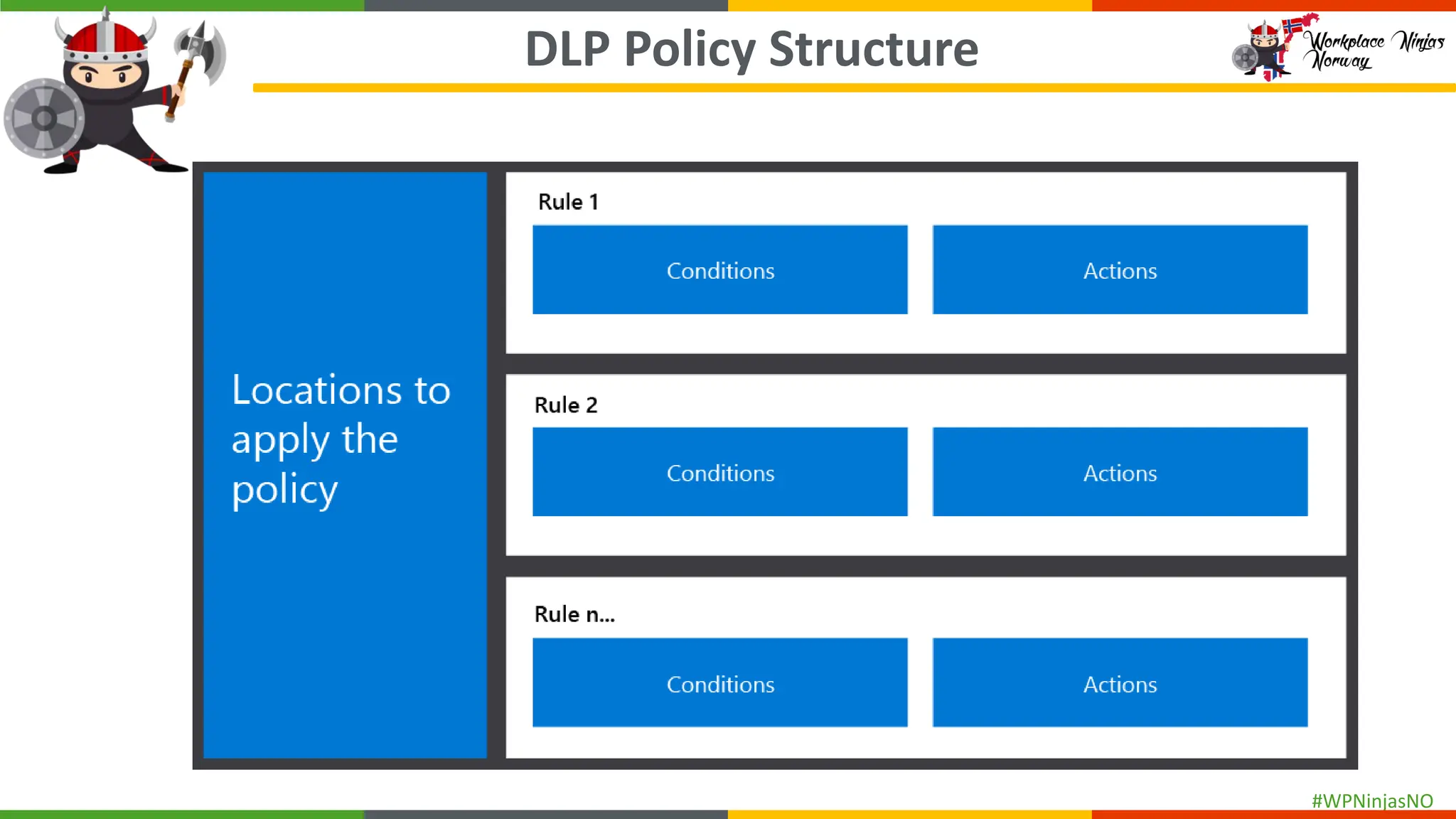
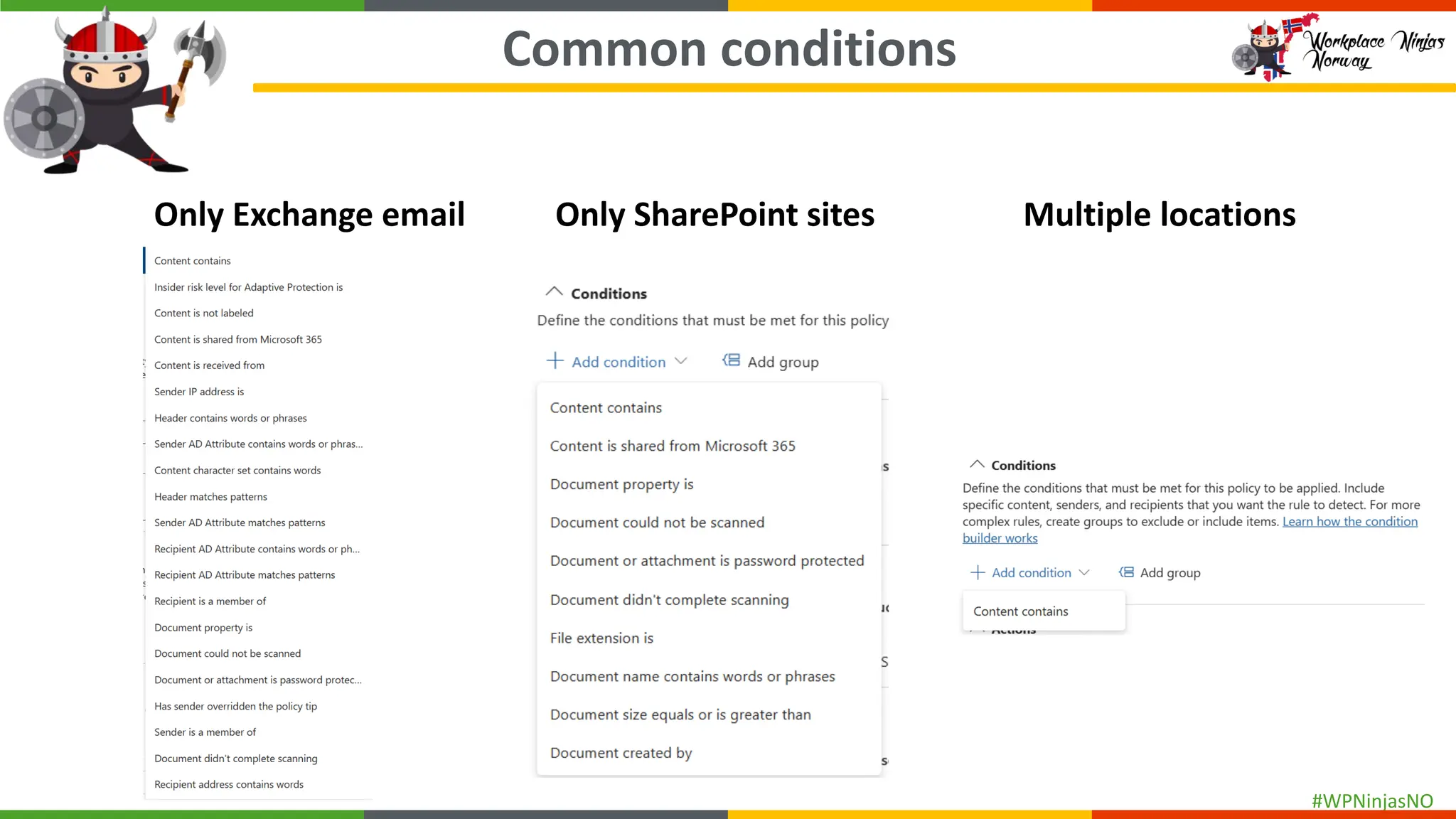
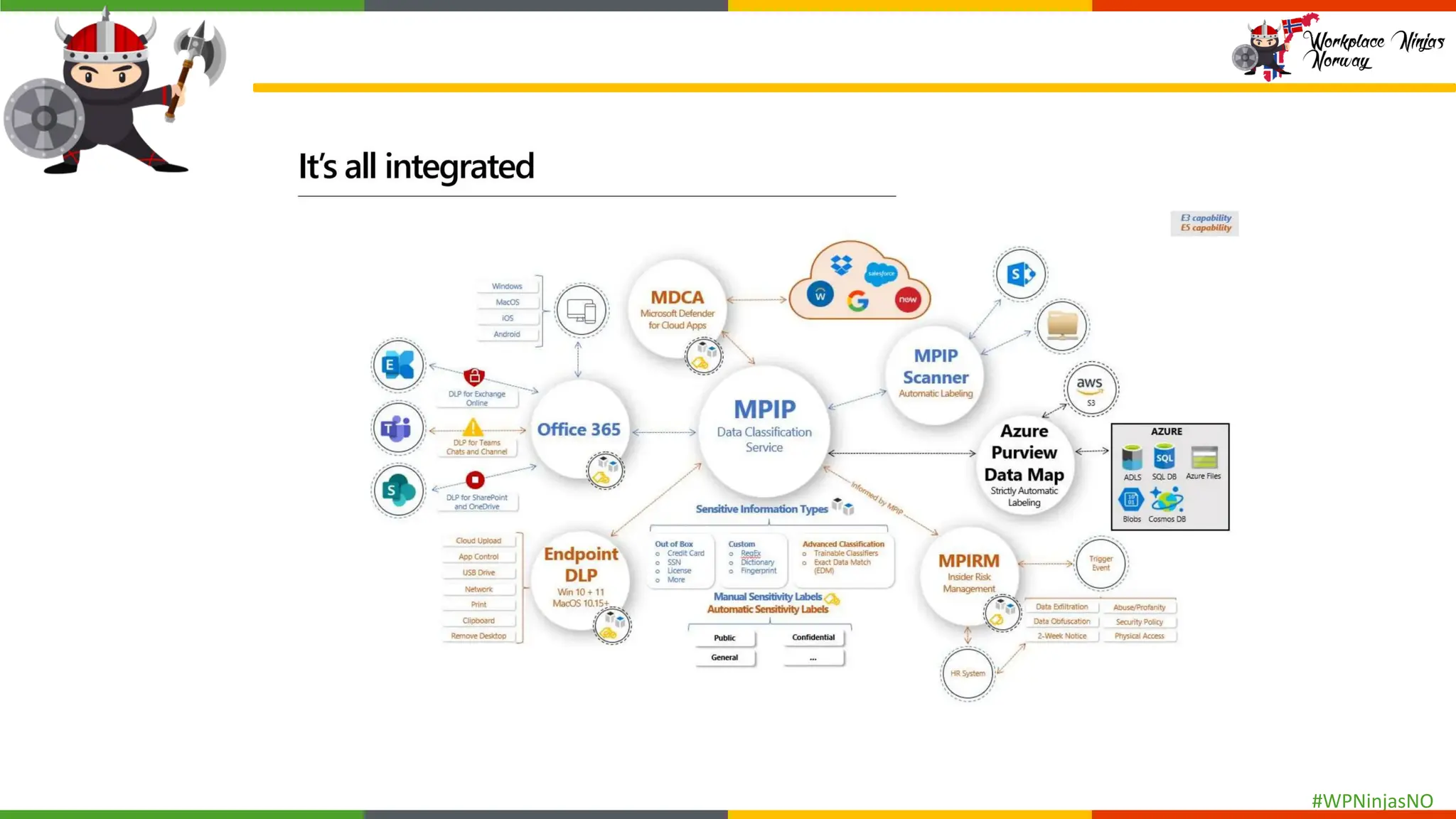
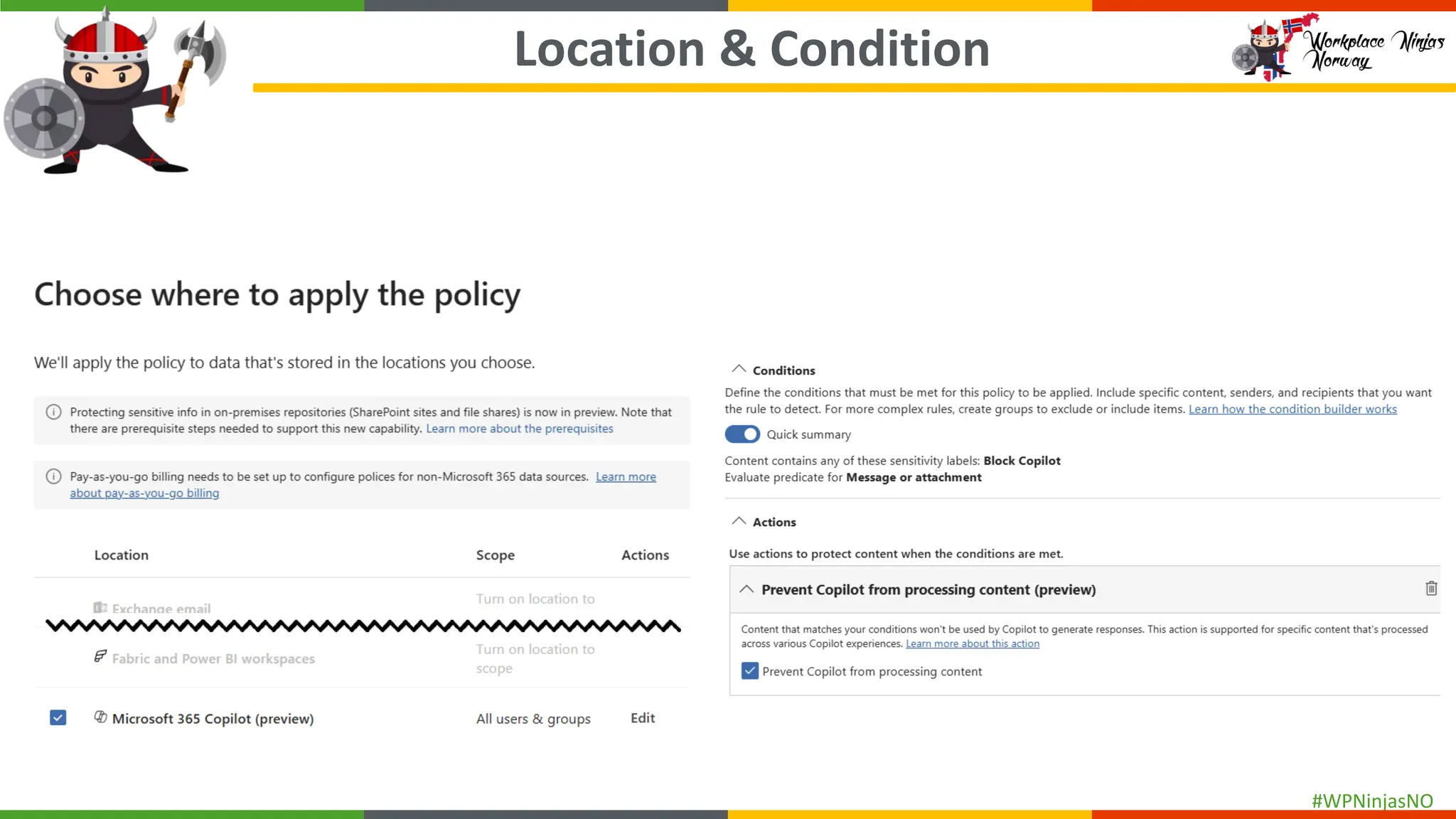
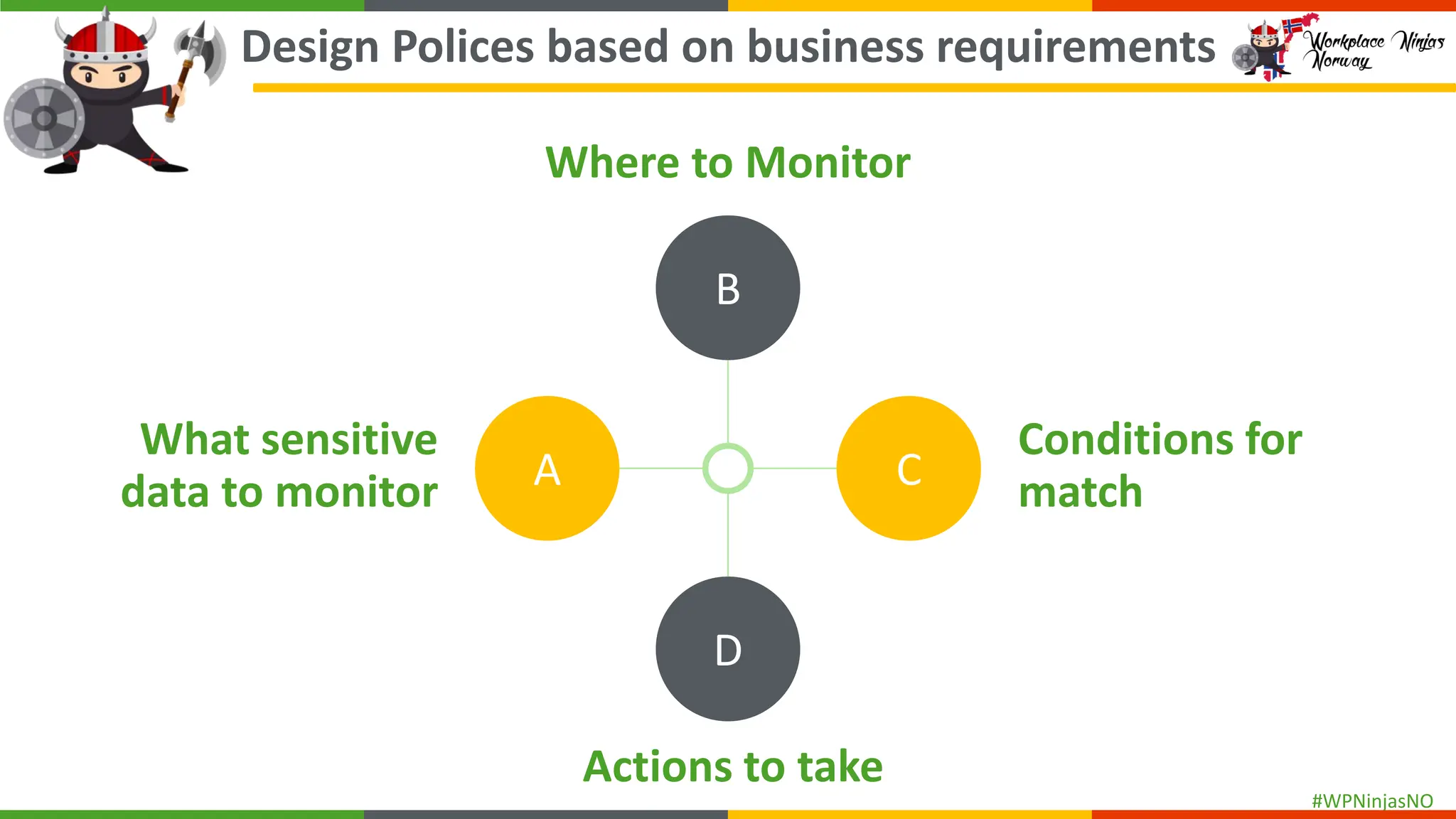
- Explain DLP policy structure
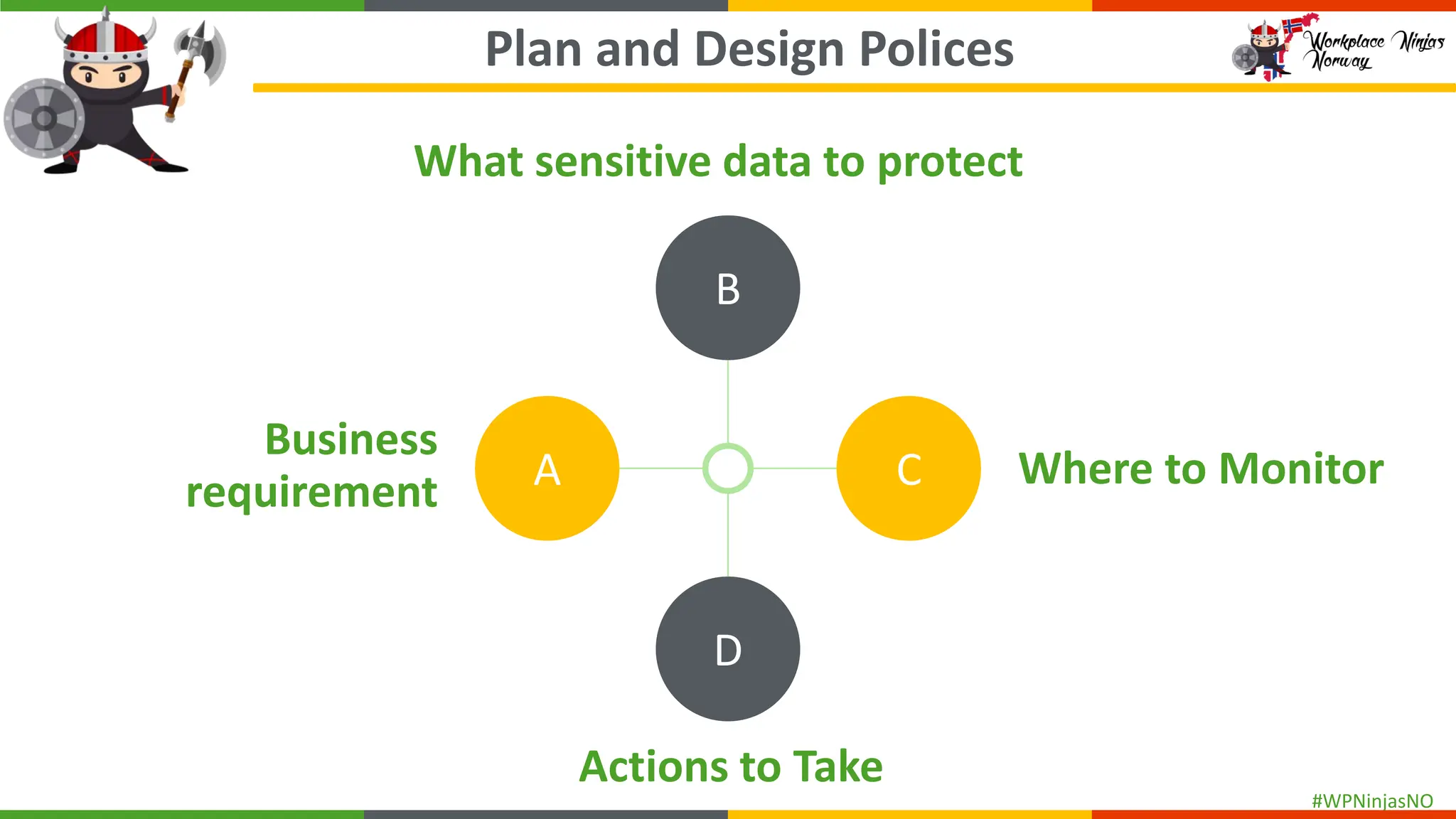
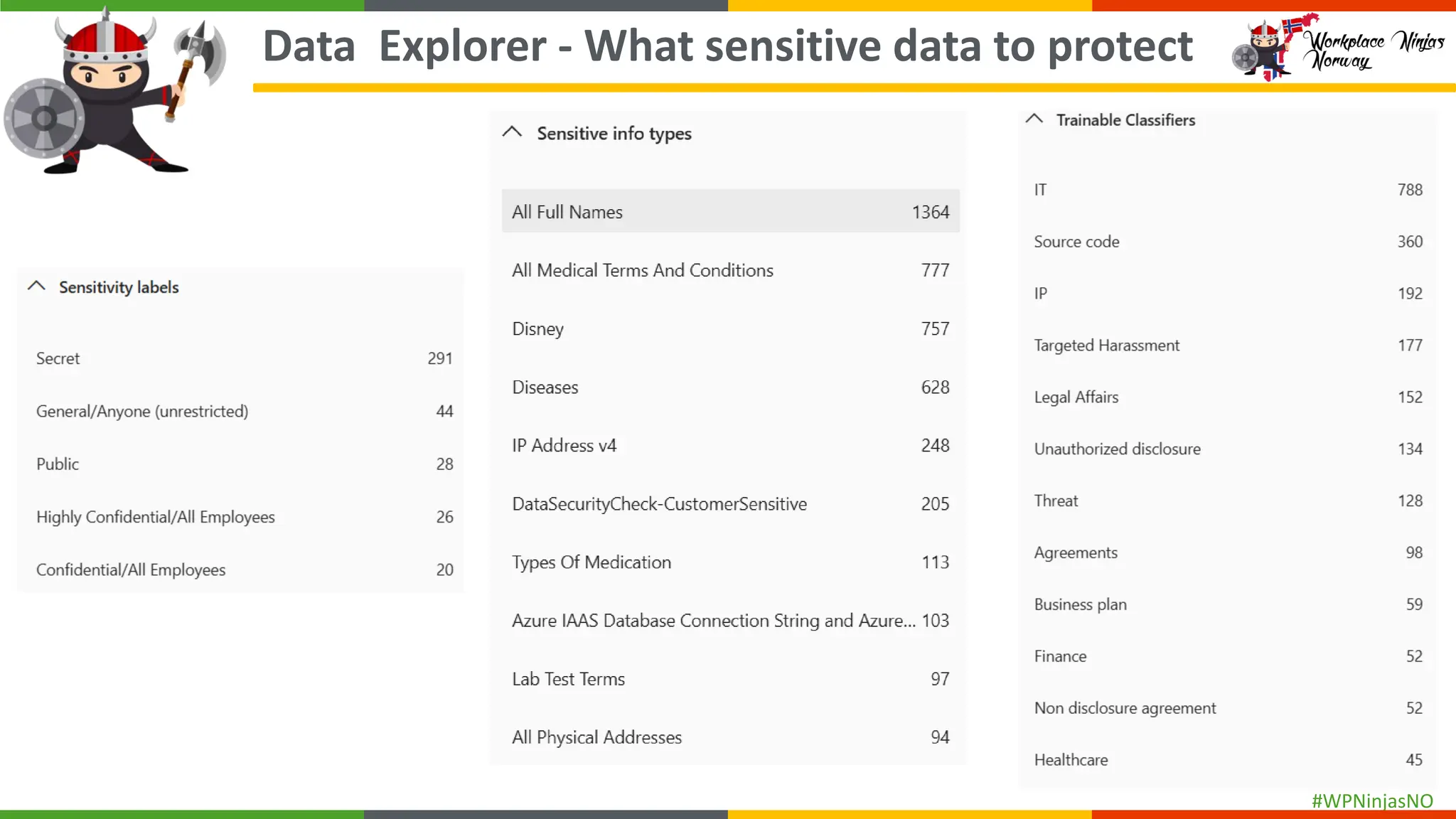
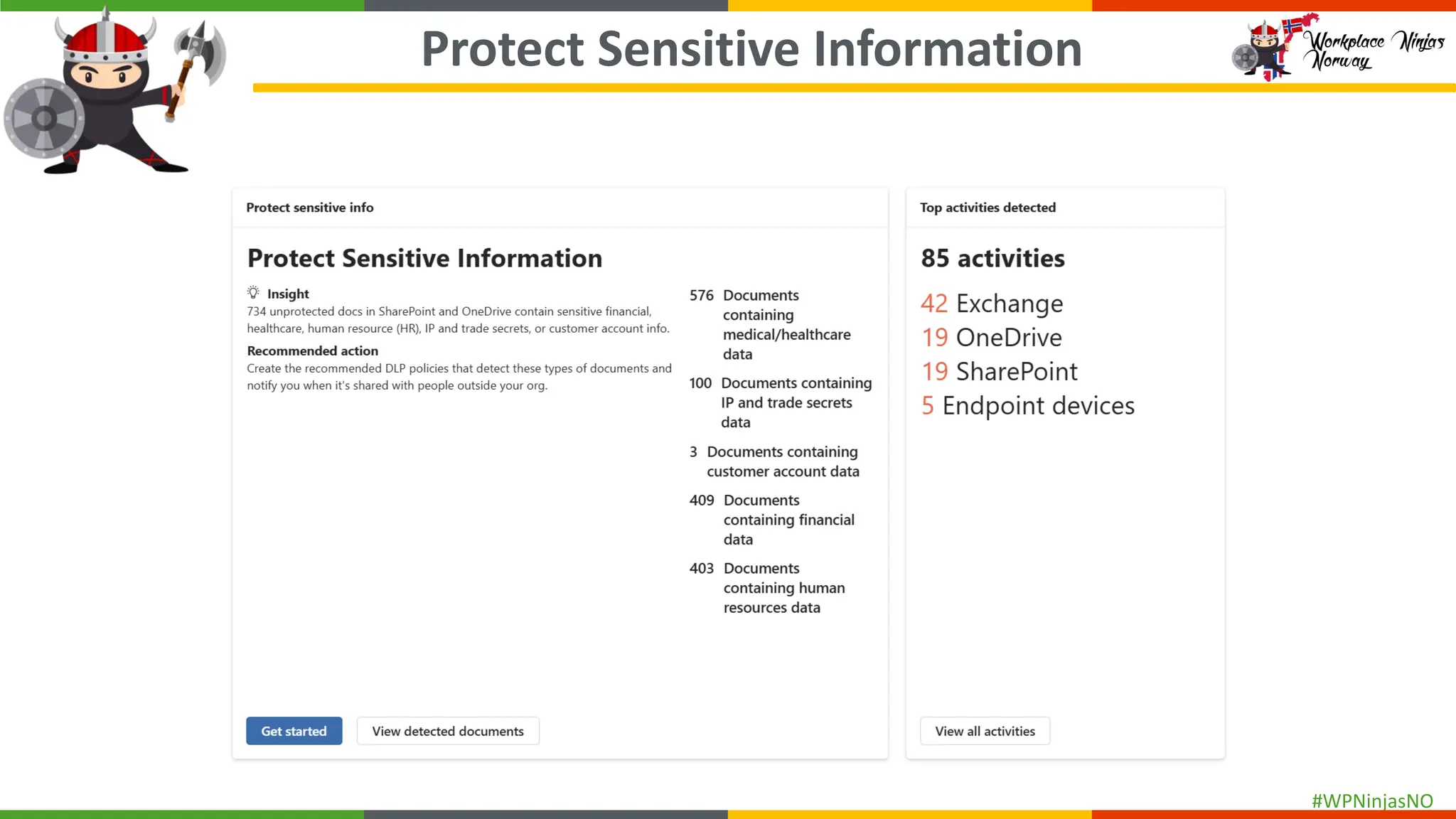
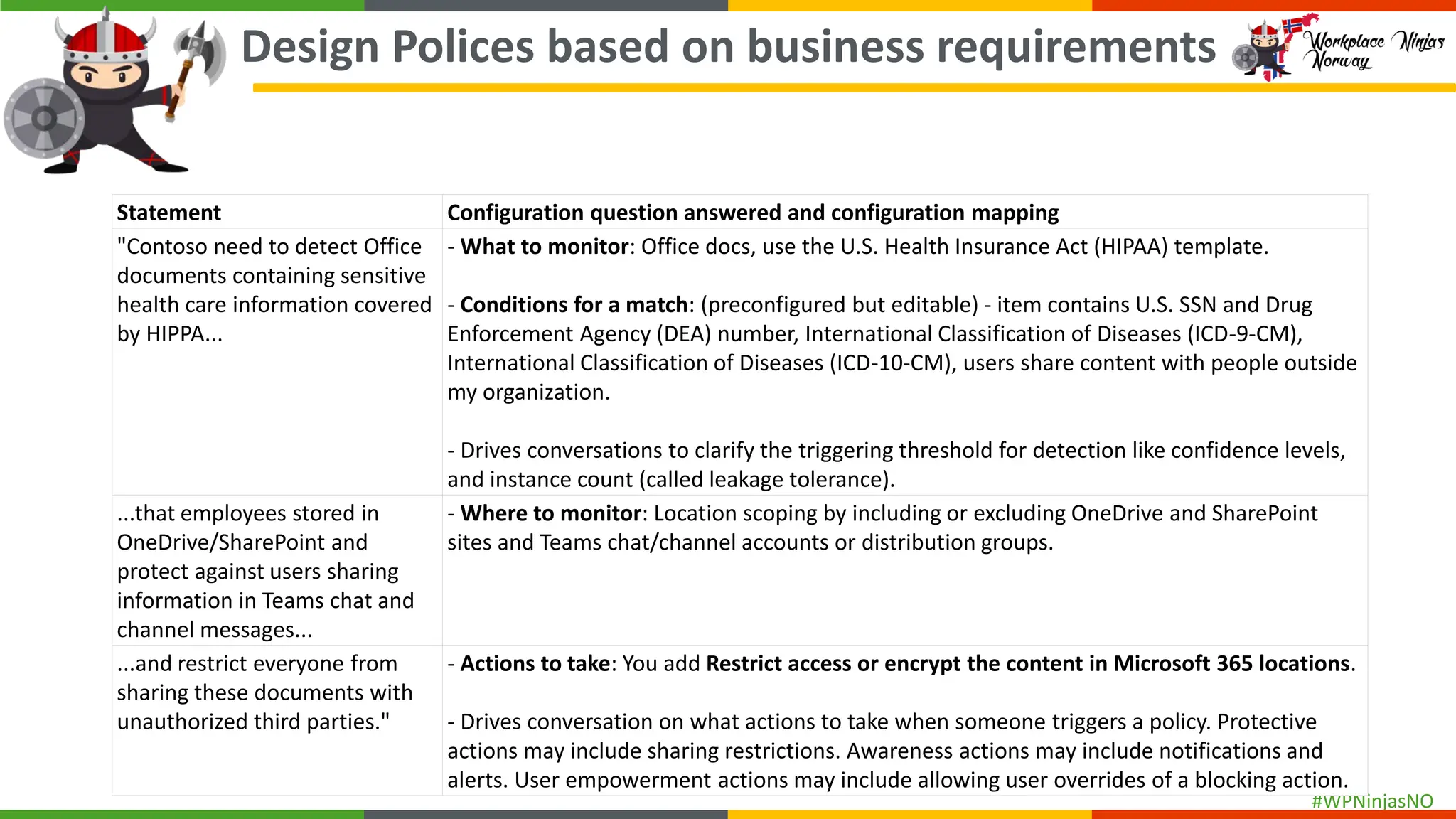
- Understanding sensitive data
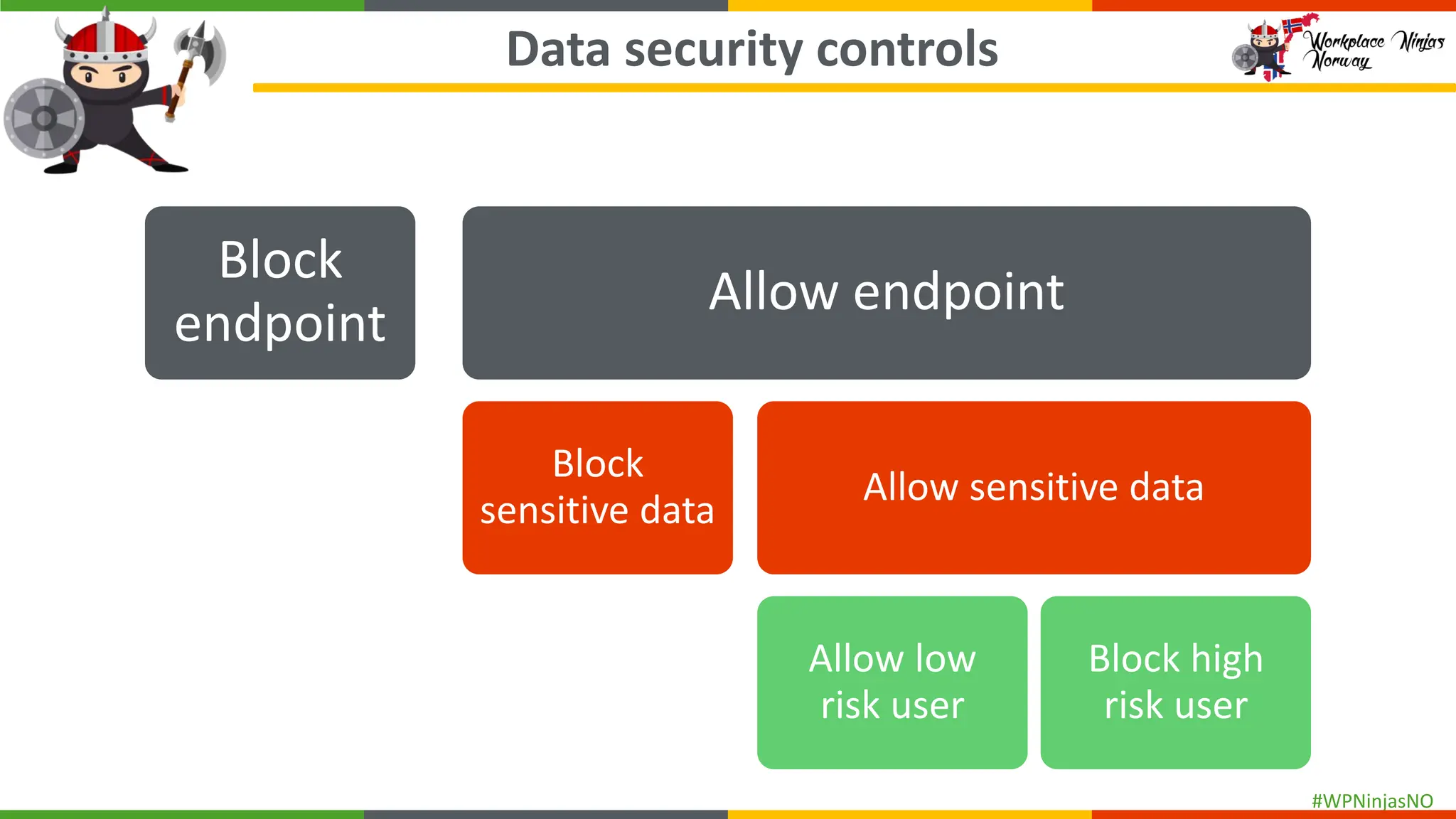
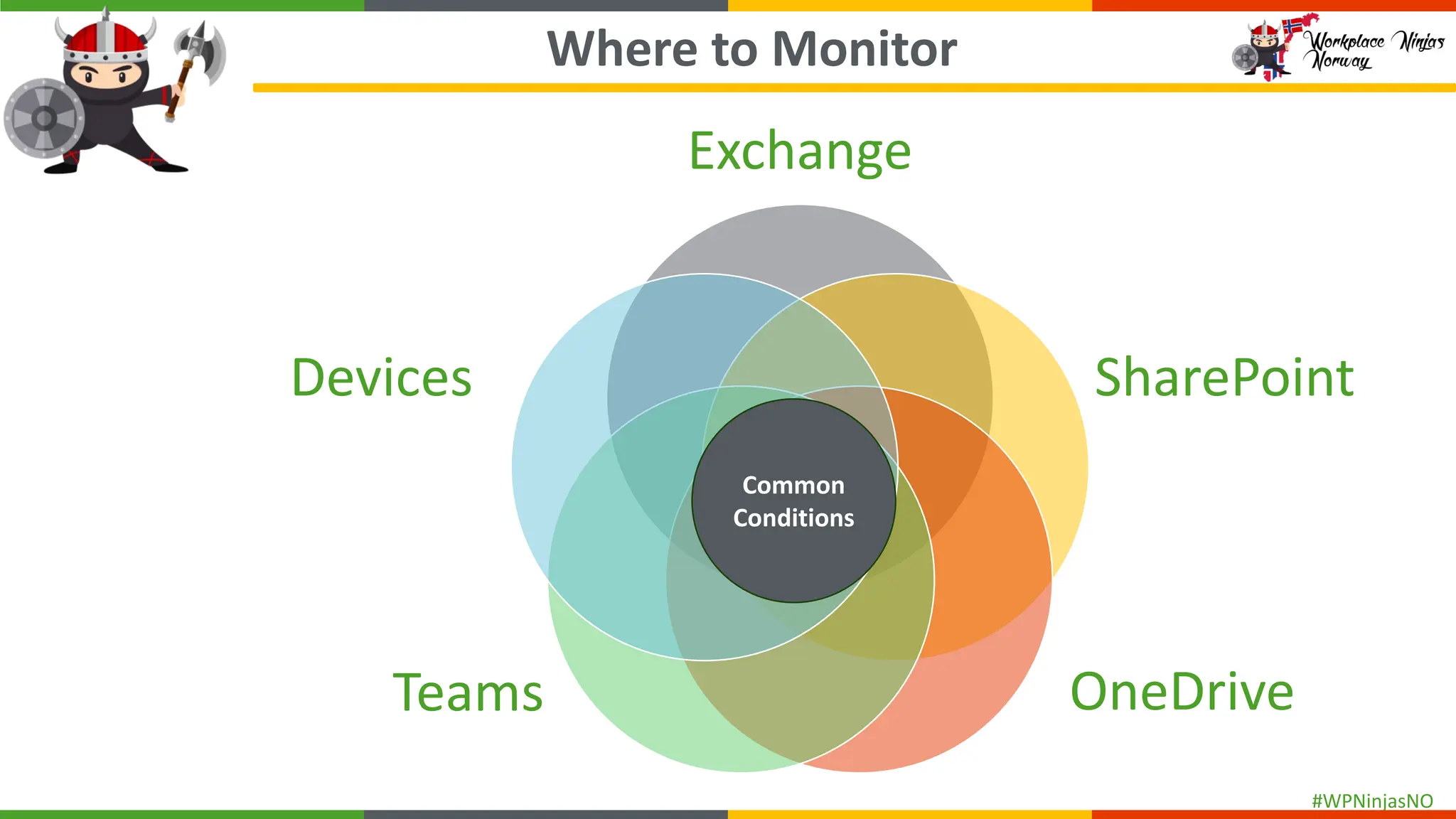
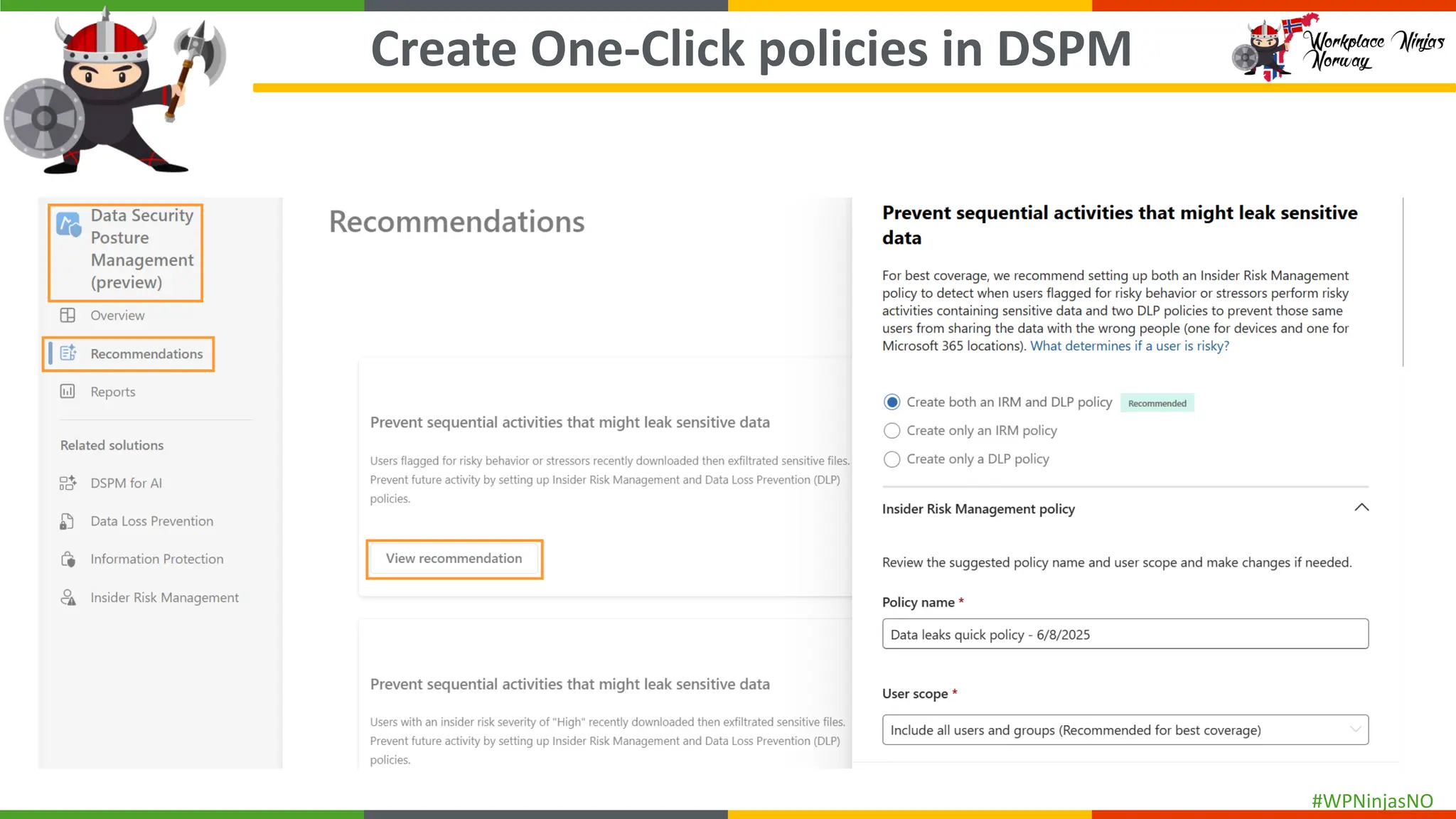
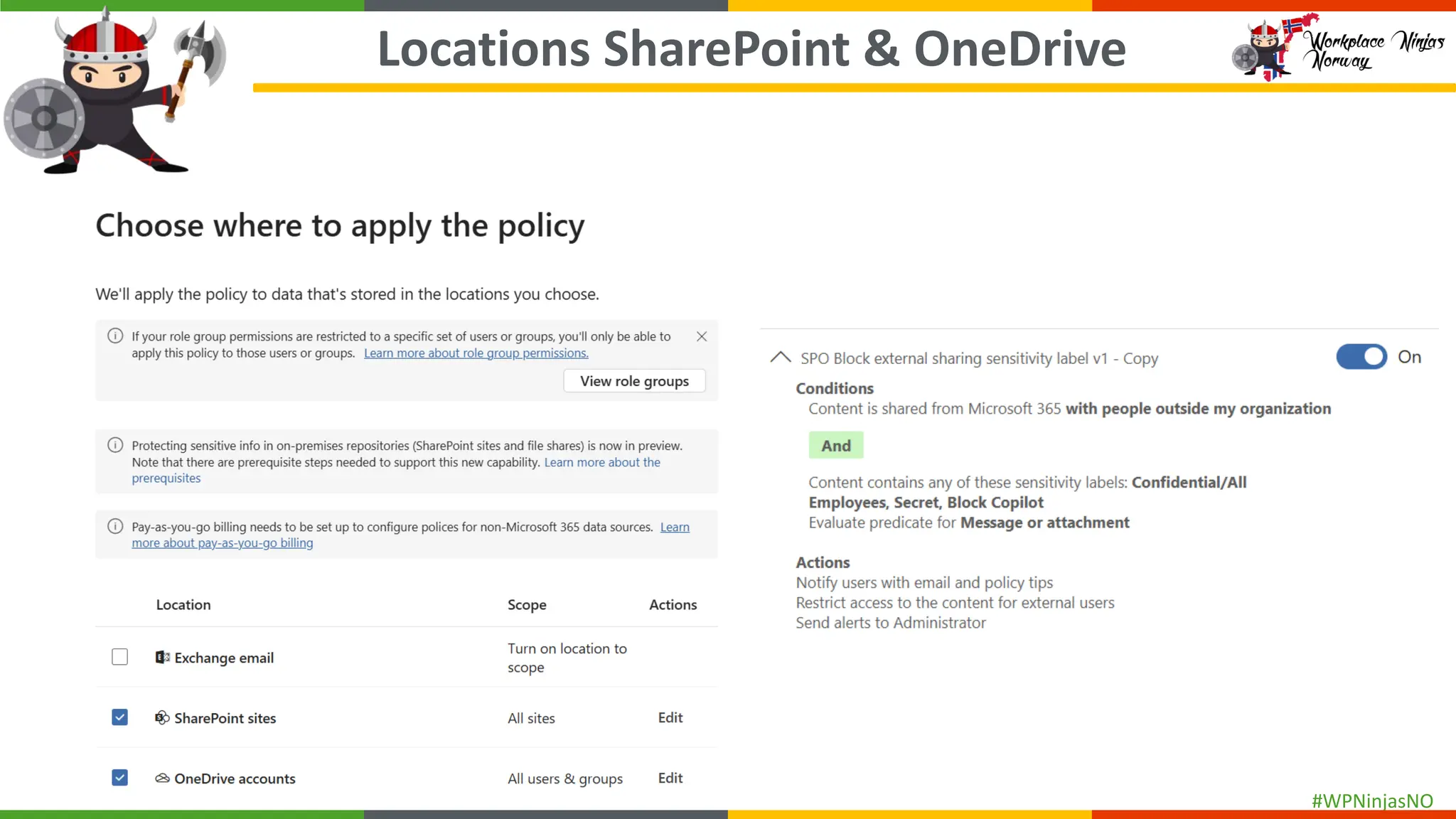
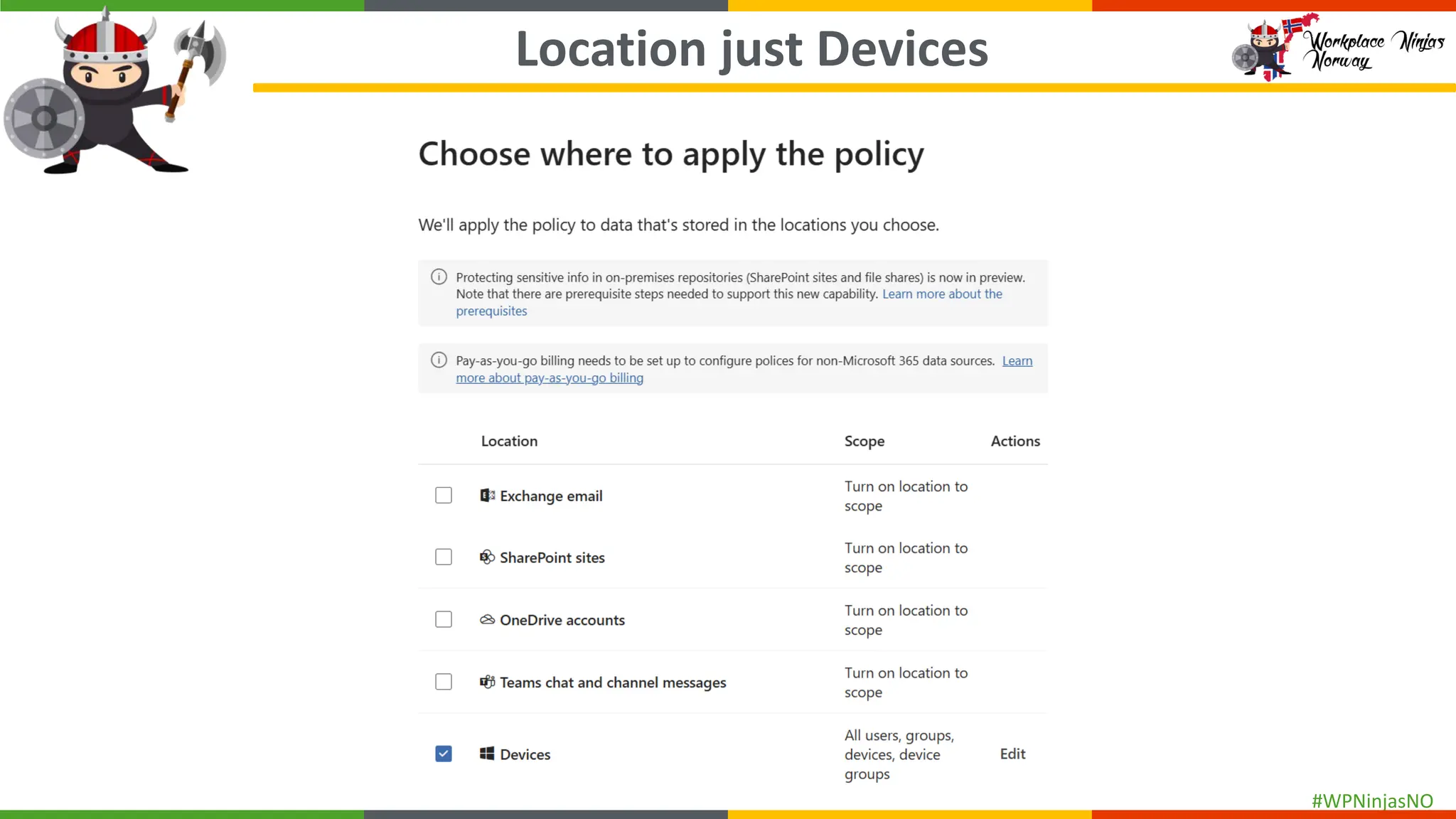
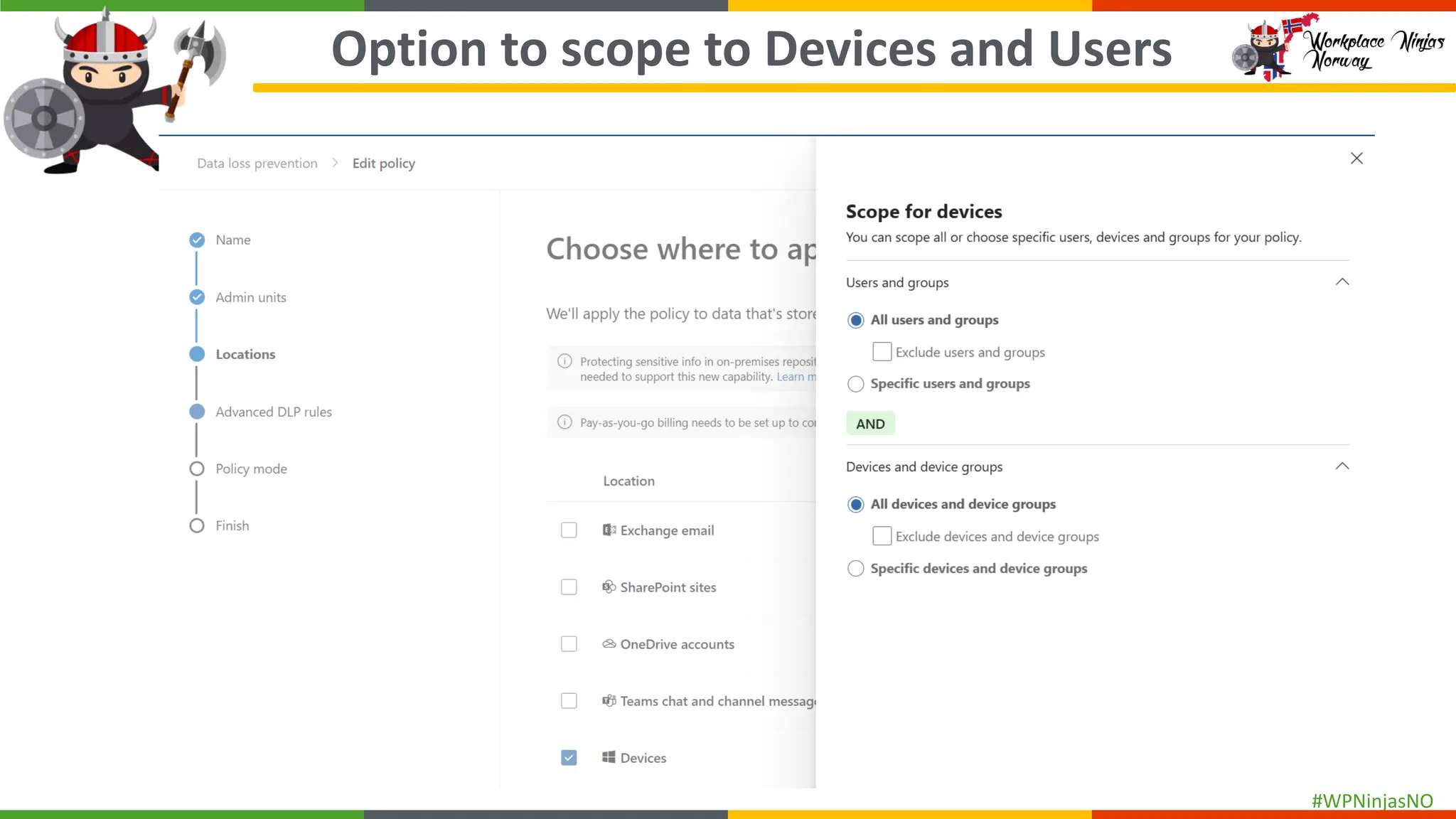
- Create separate DLP policies for each location
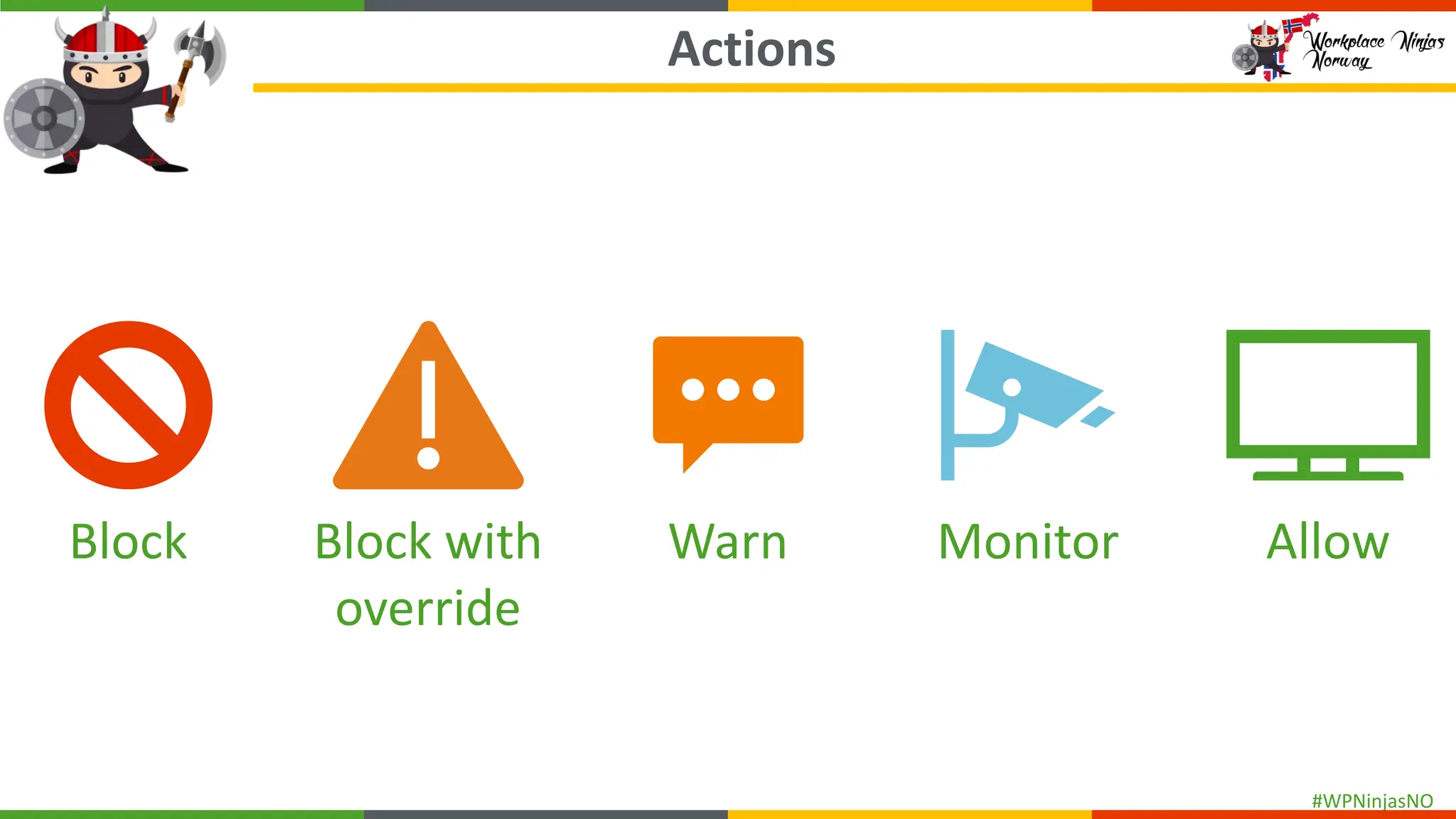
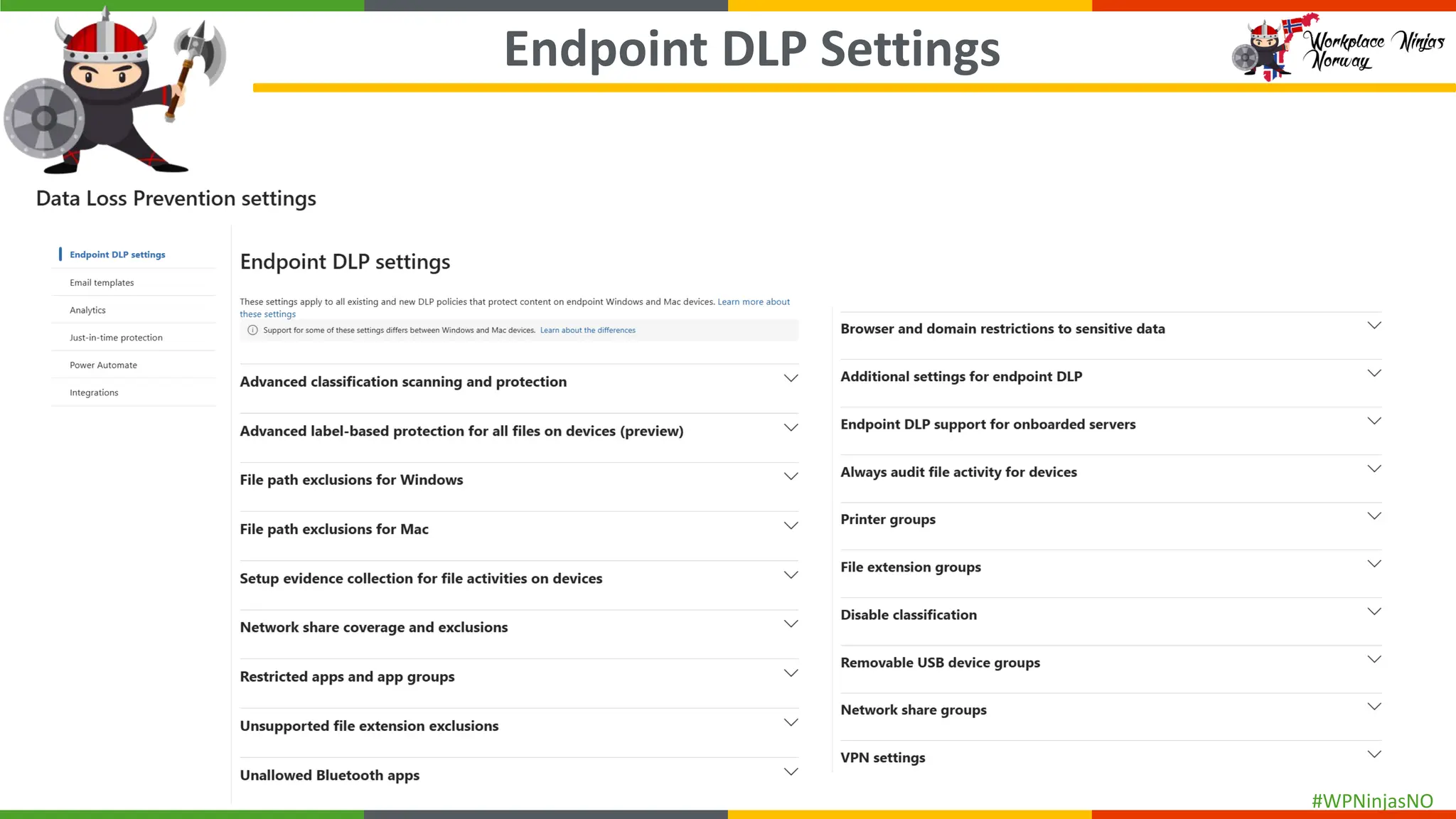
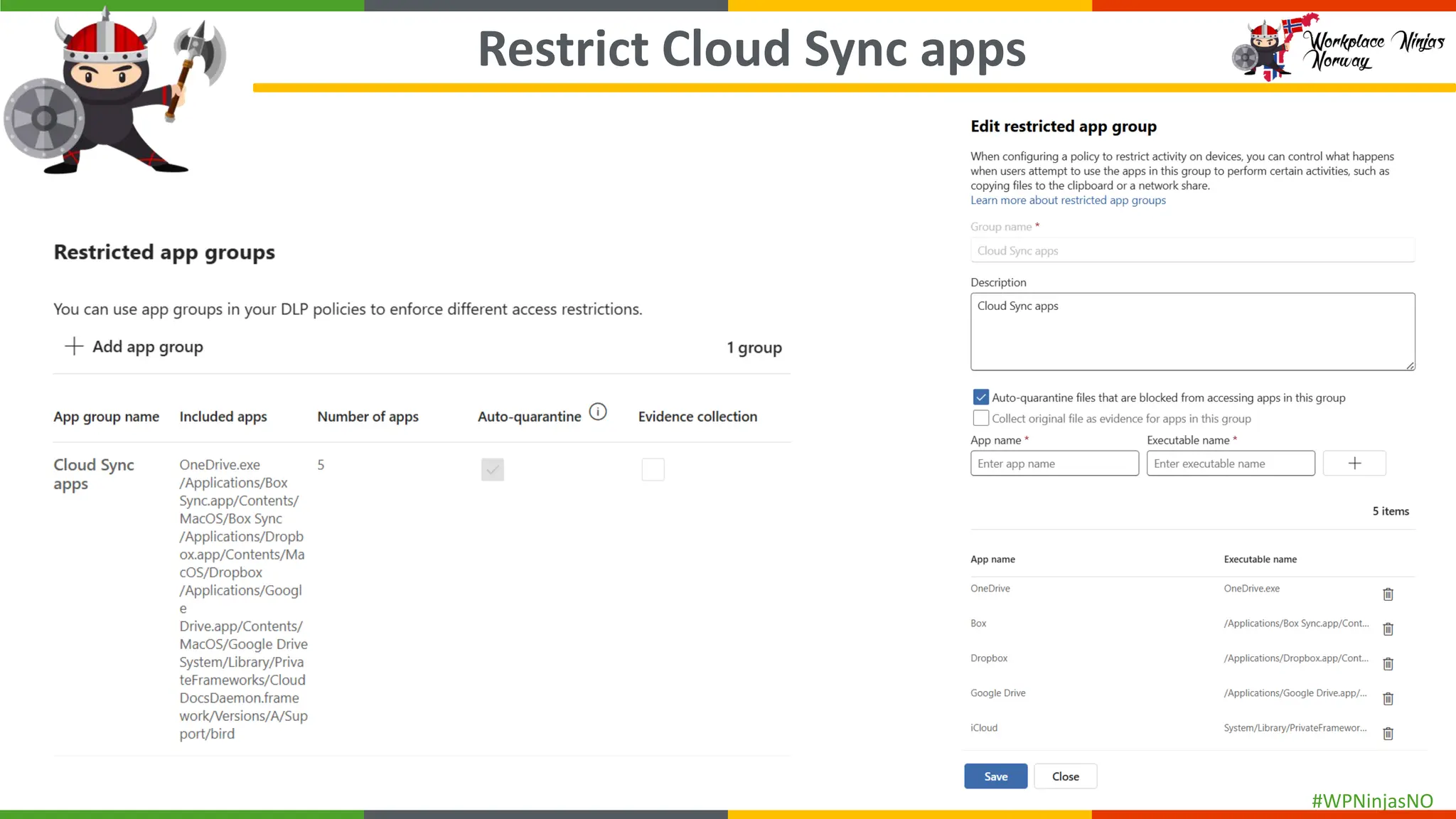
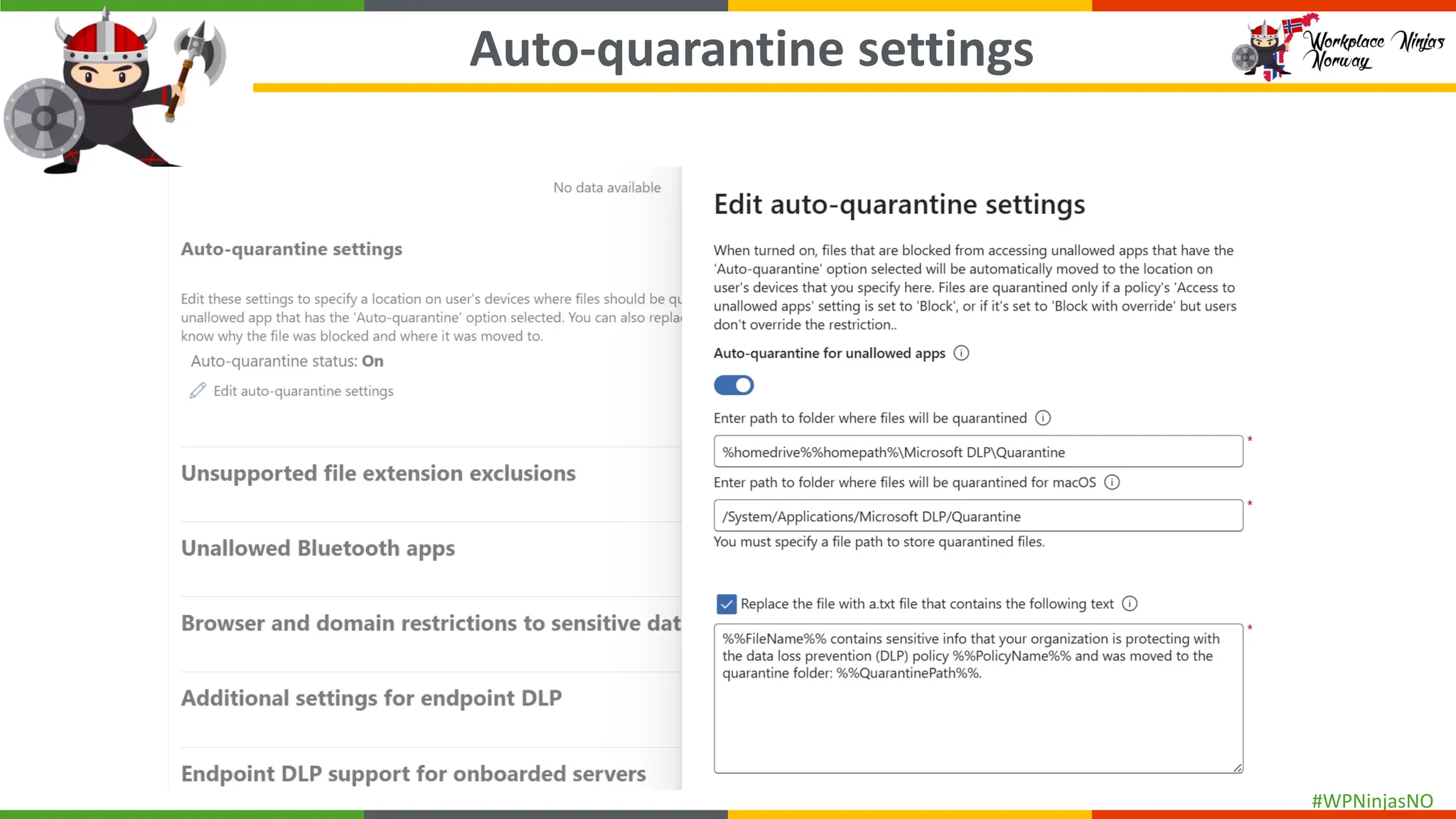
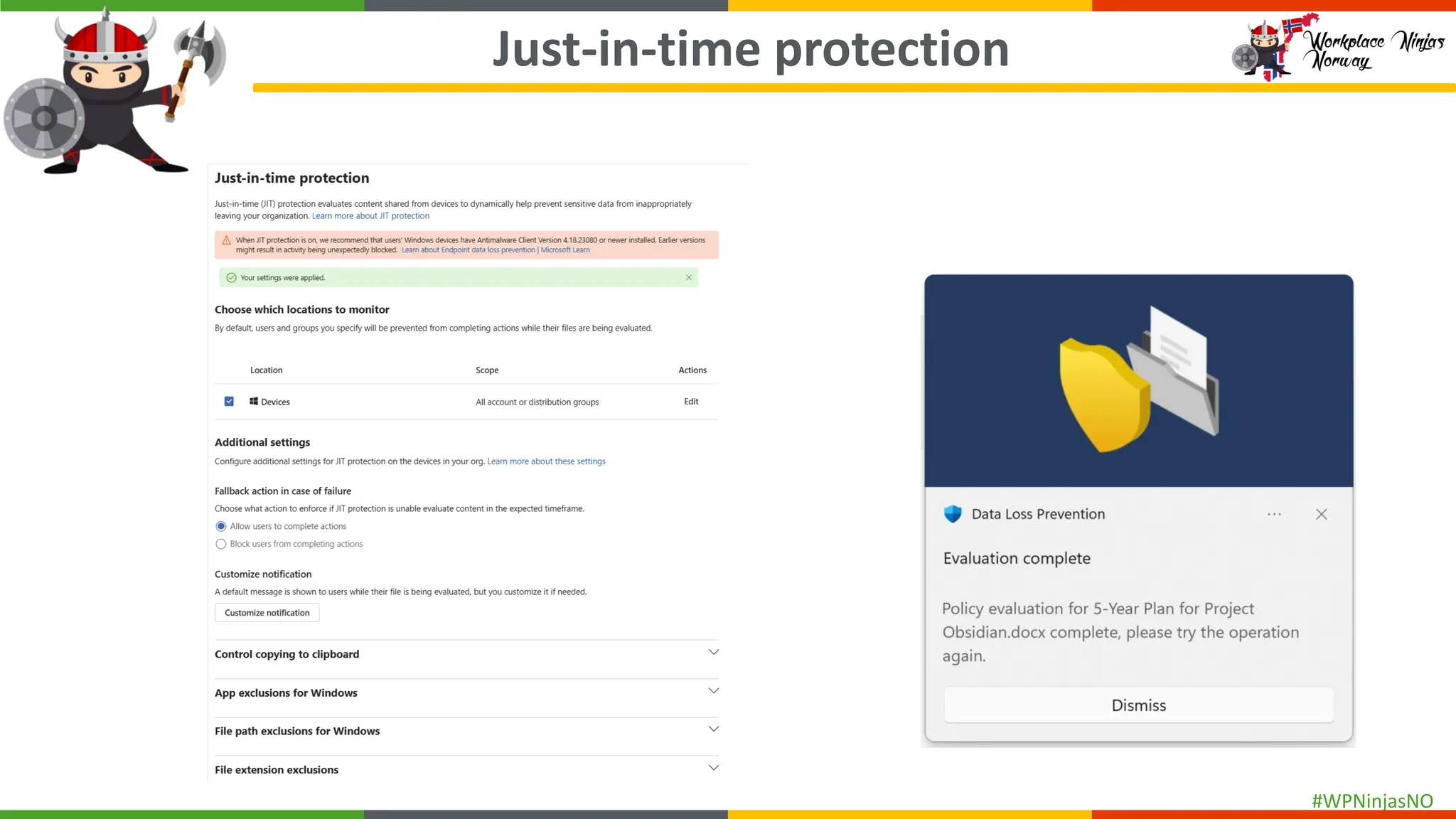
- DLP settings
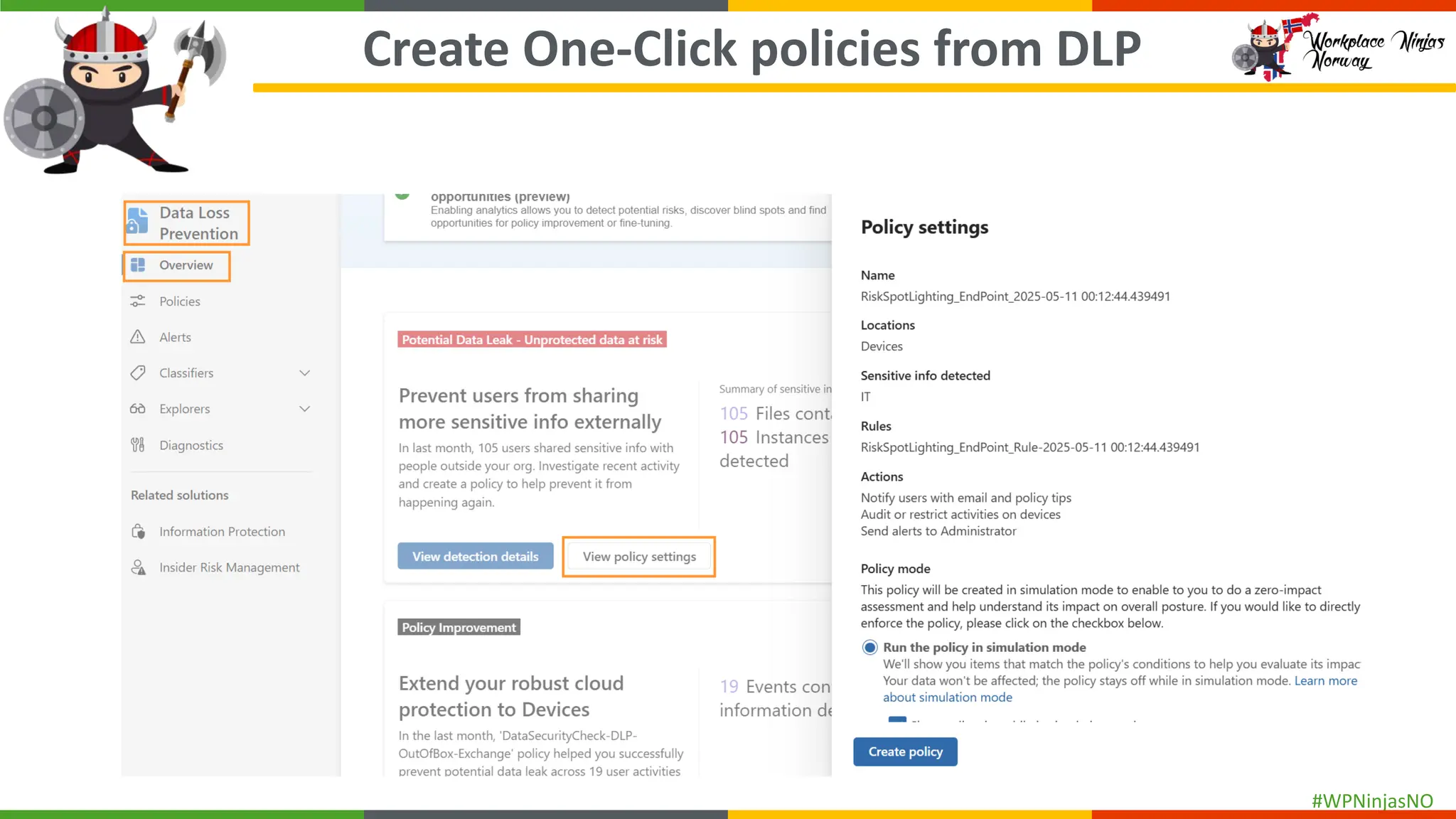
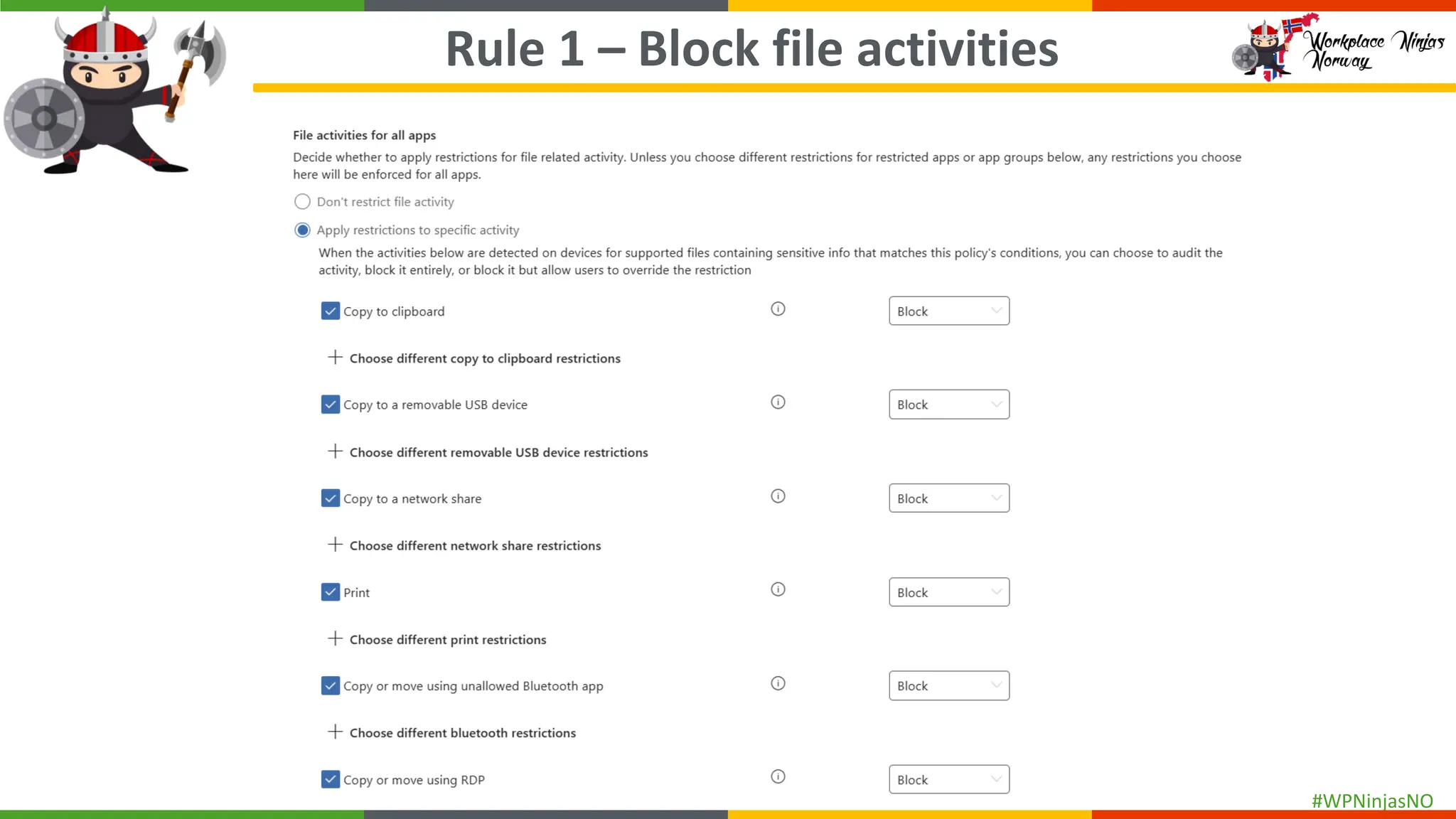
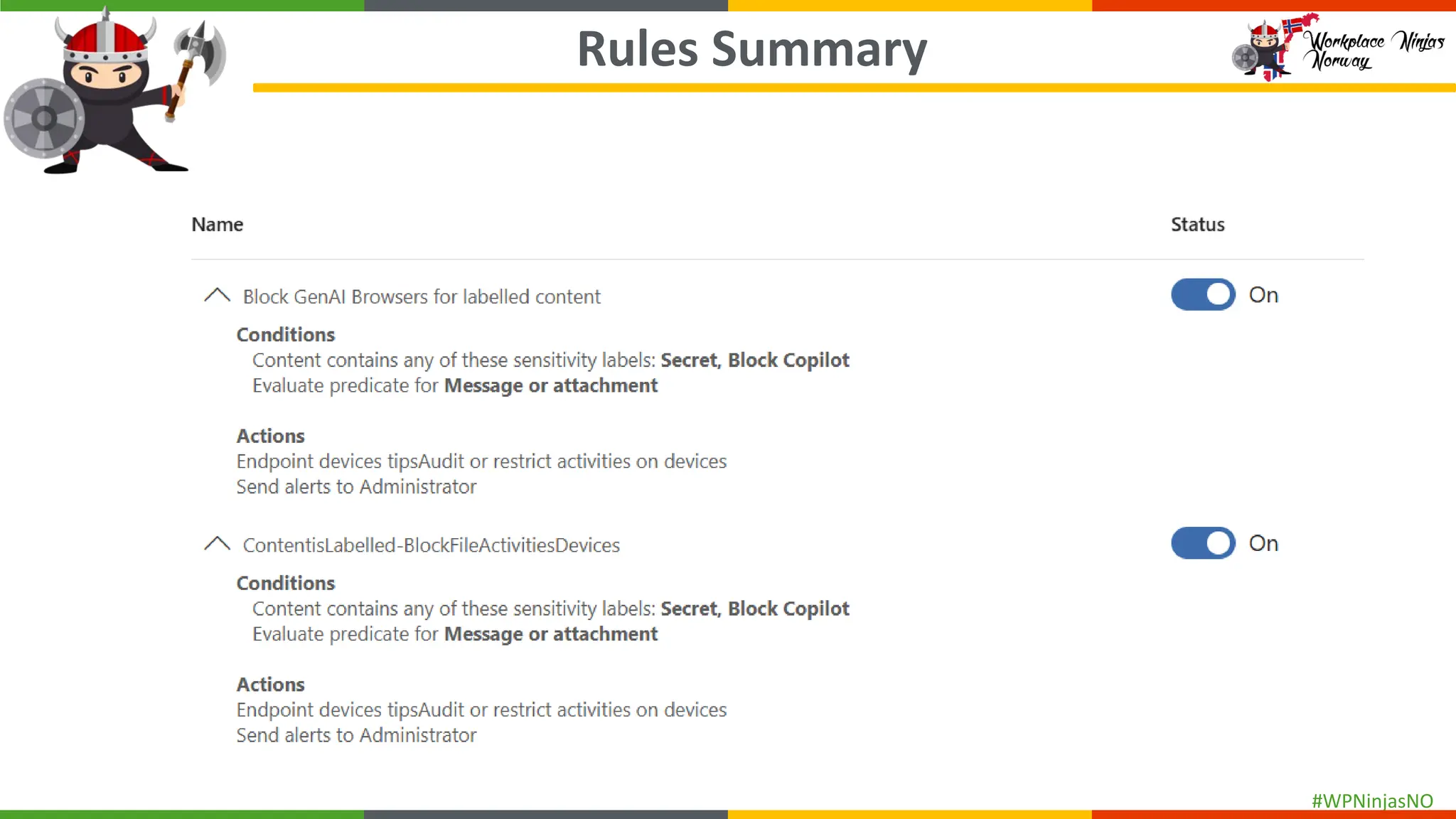
- Demonstrated creating DLP Policies
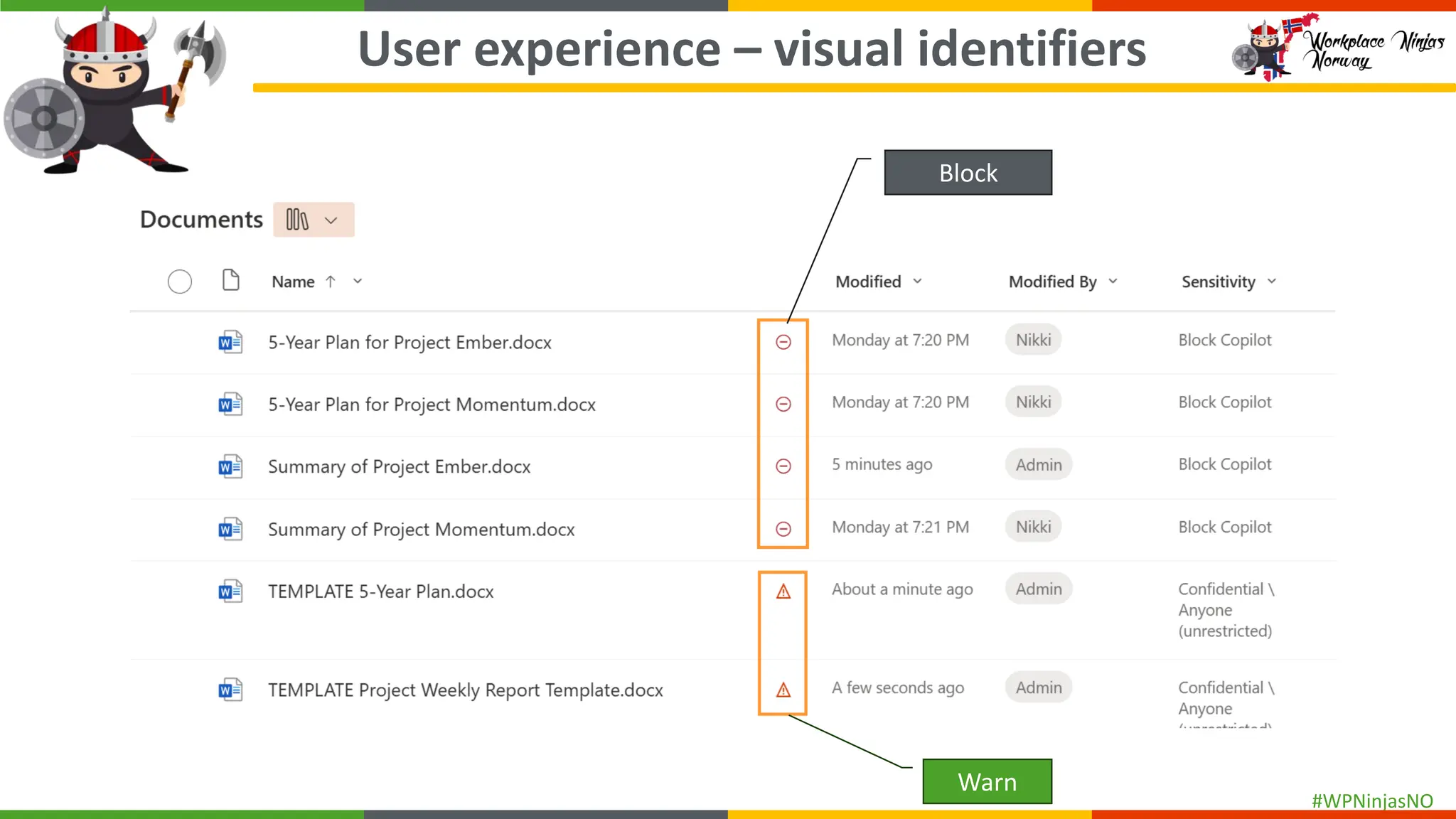
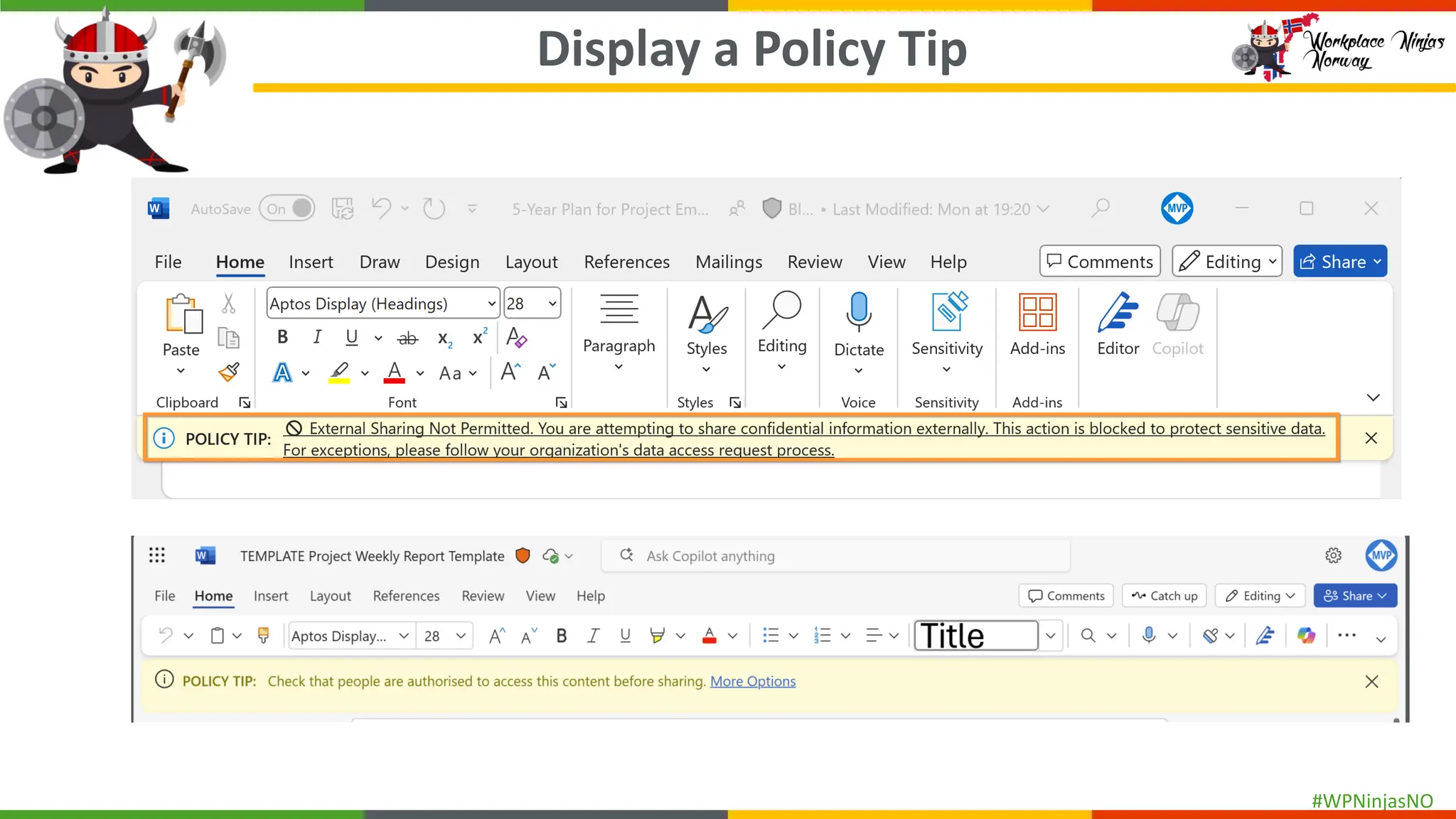
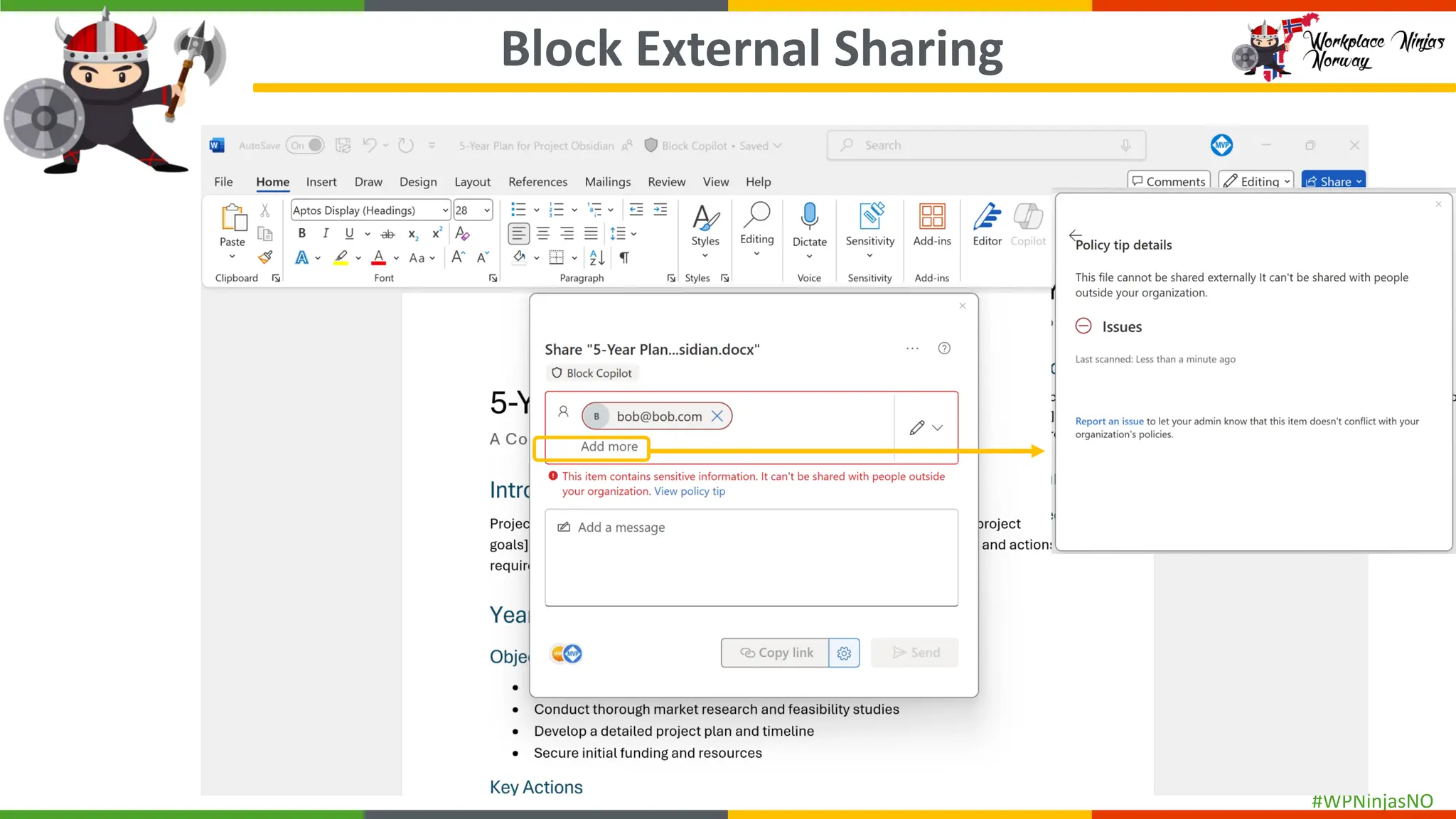
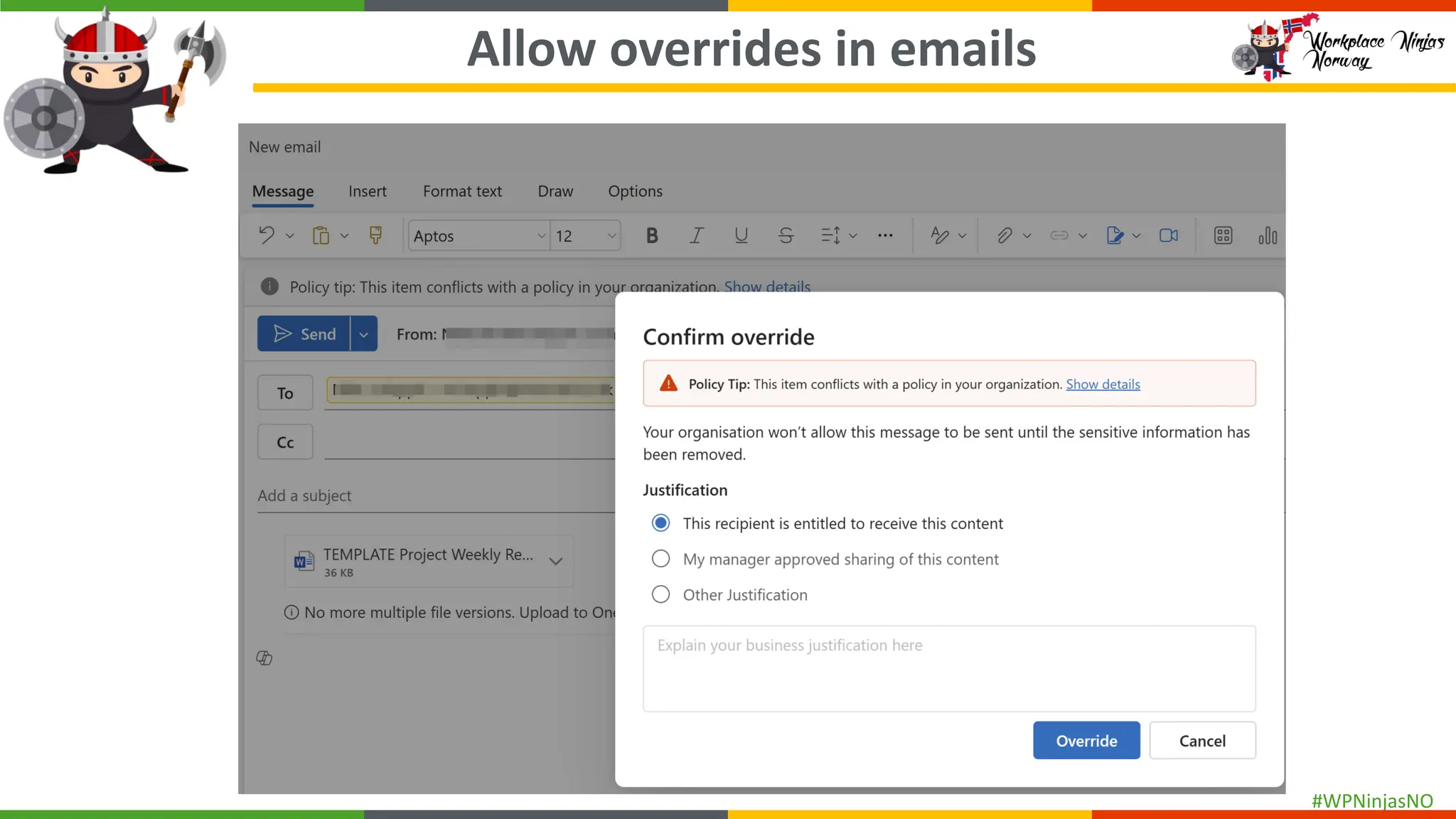
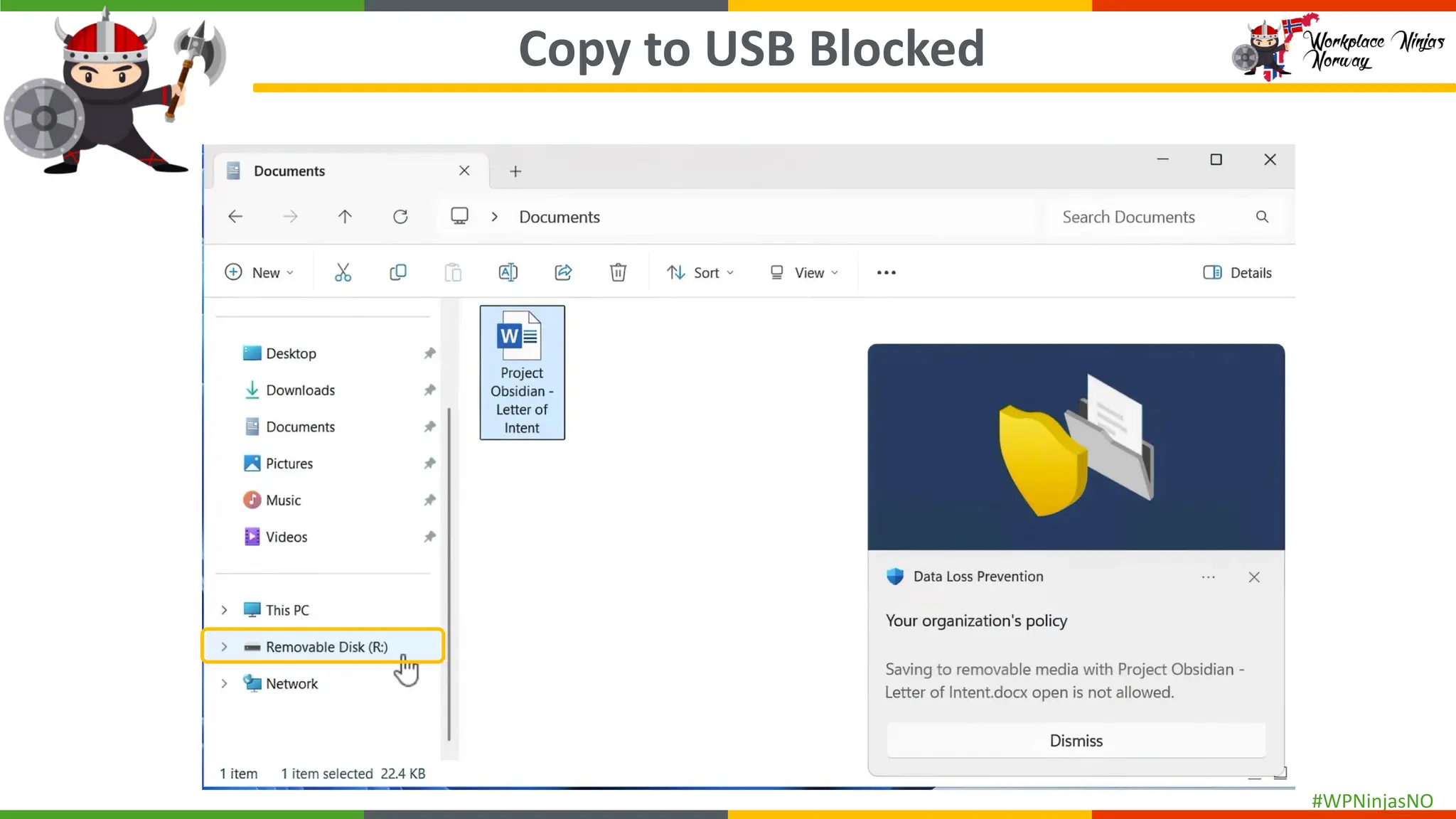
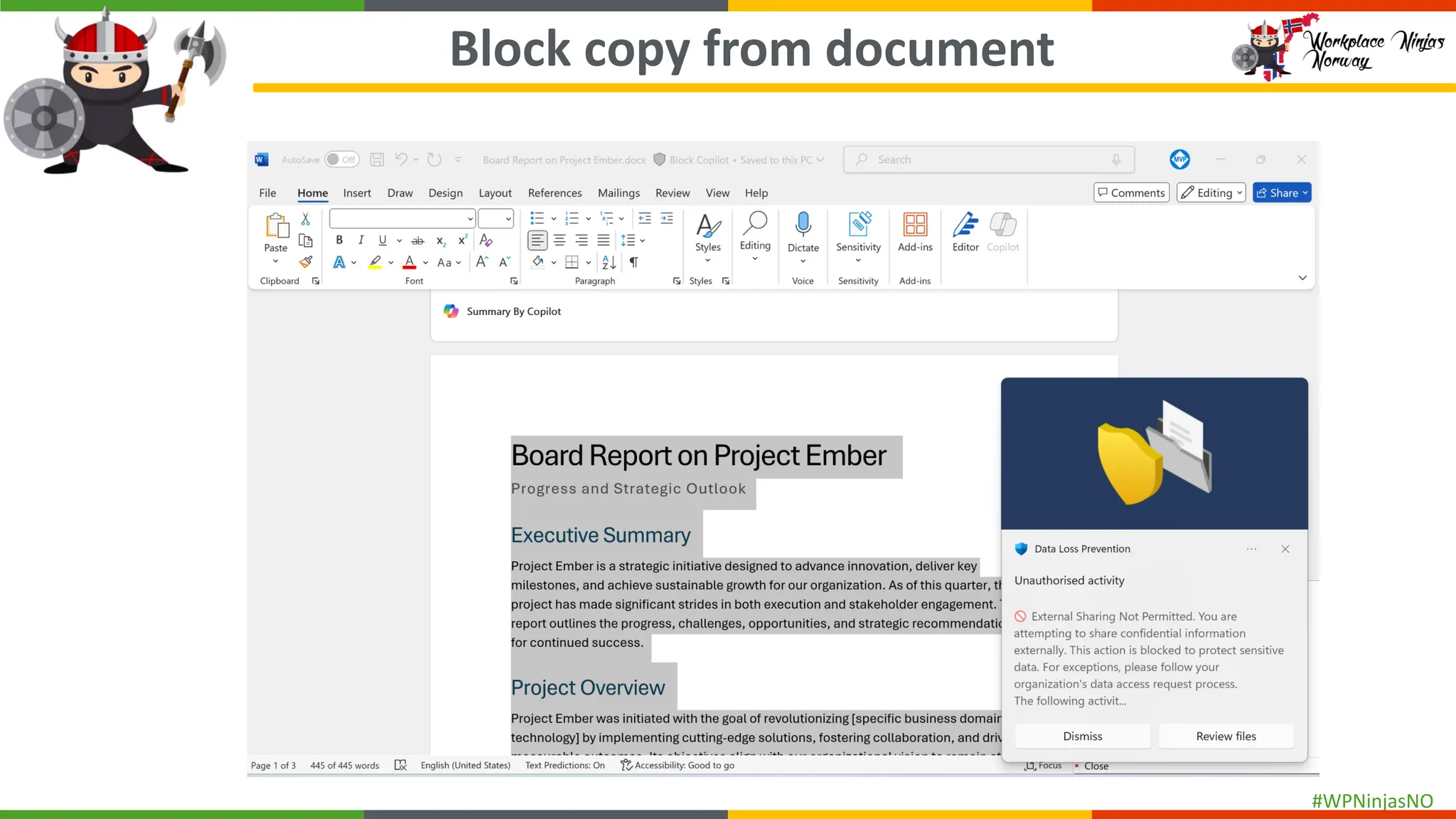
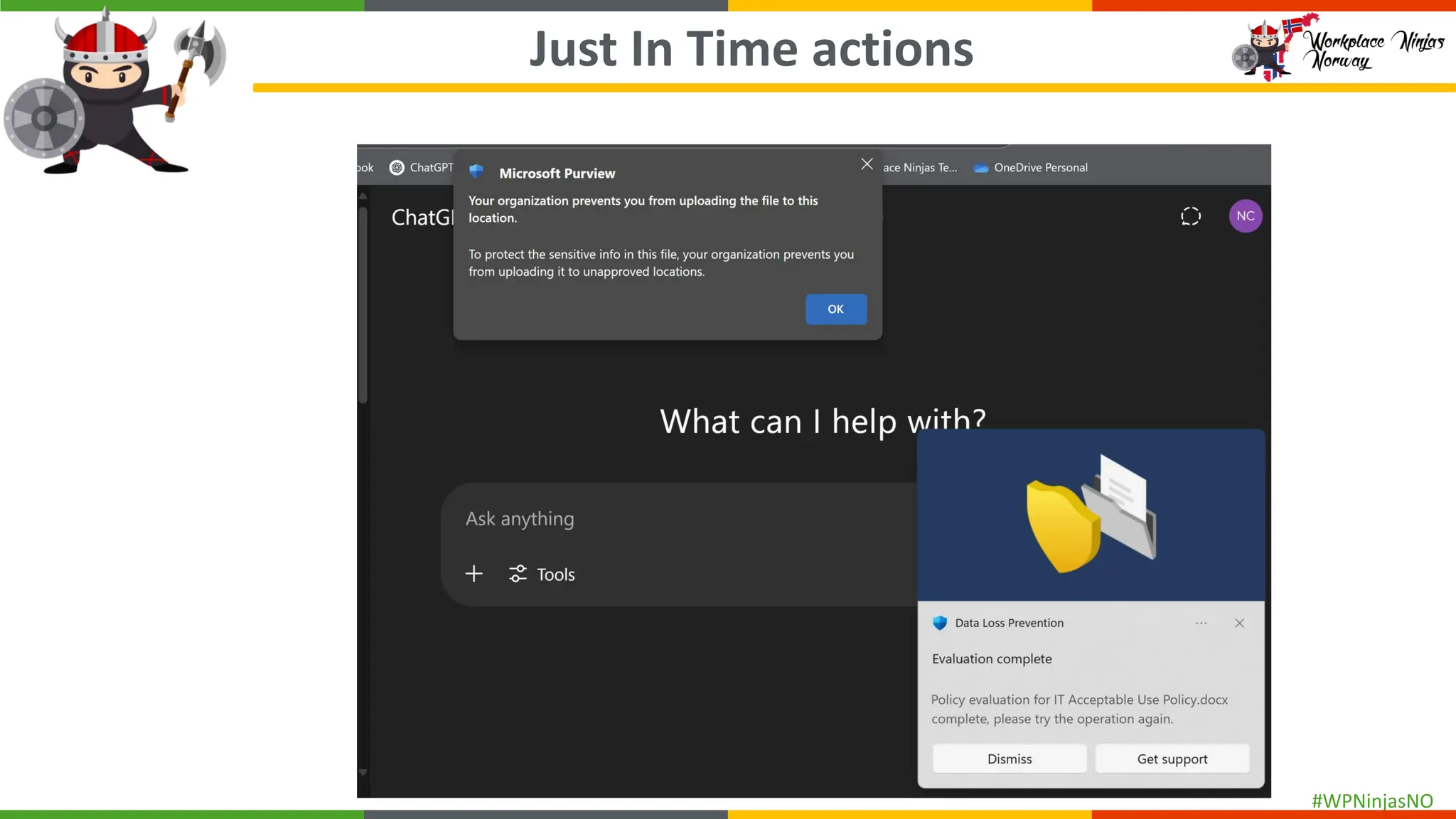
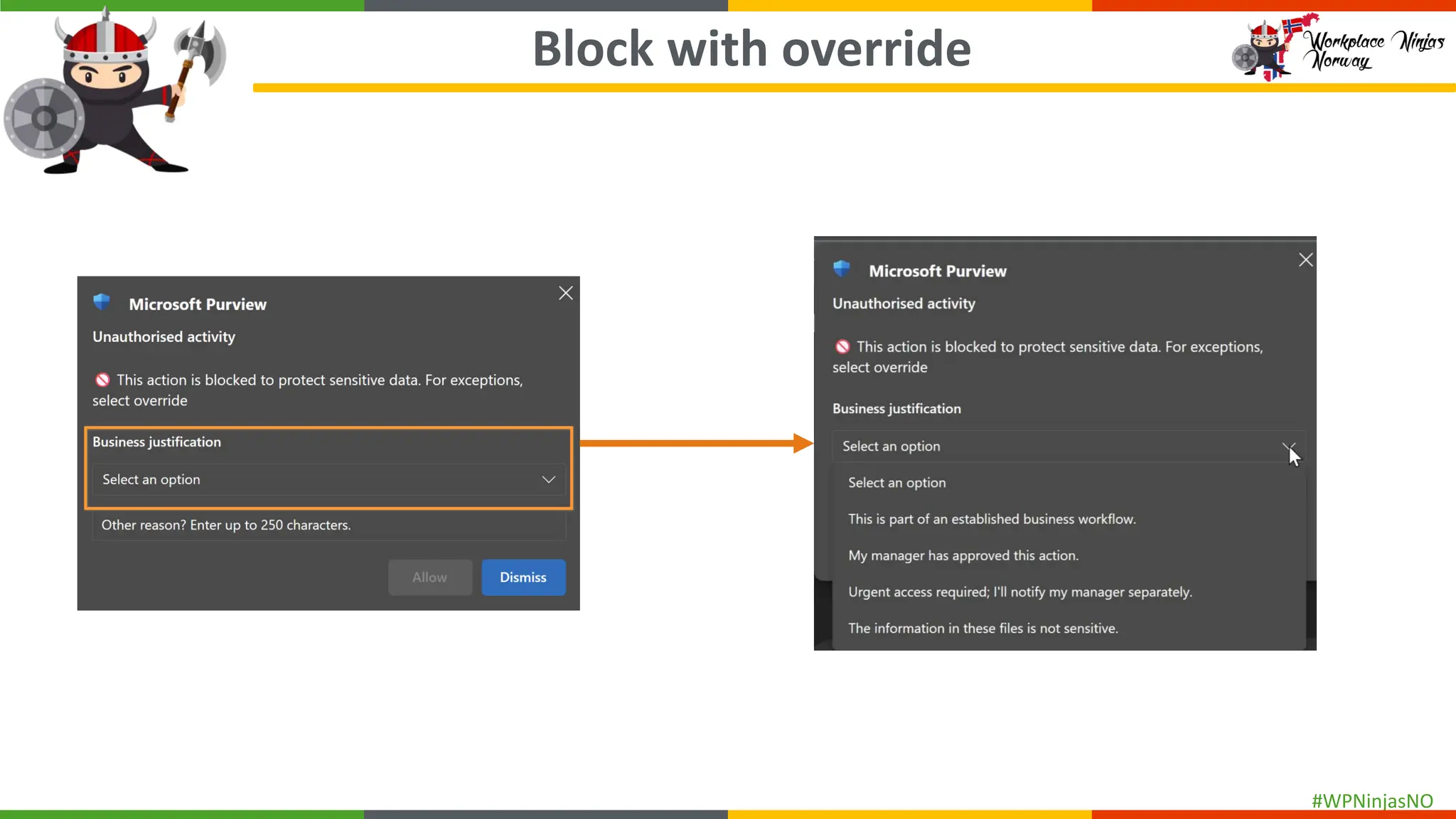
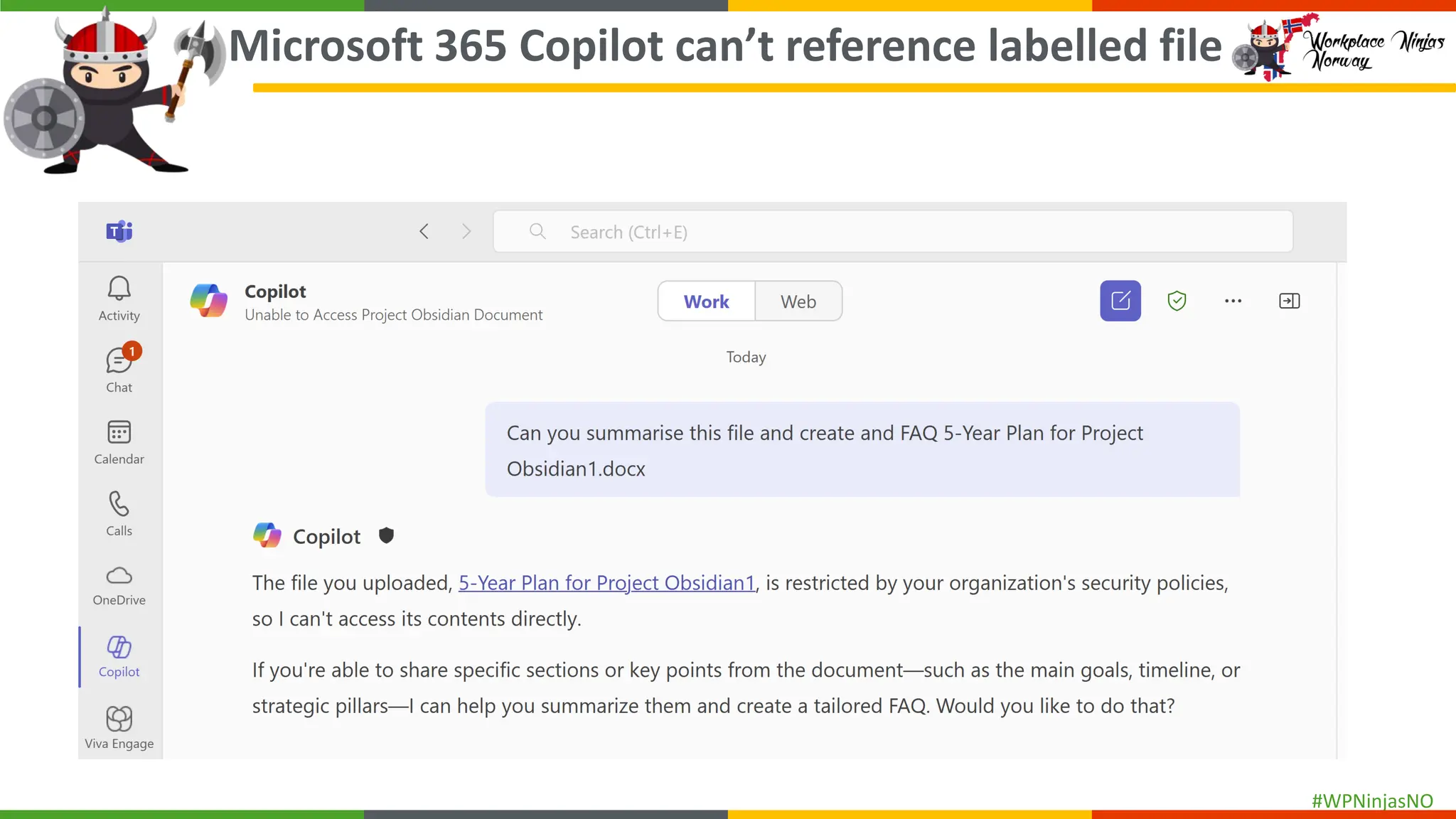
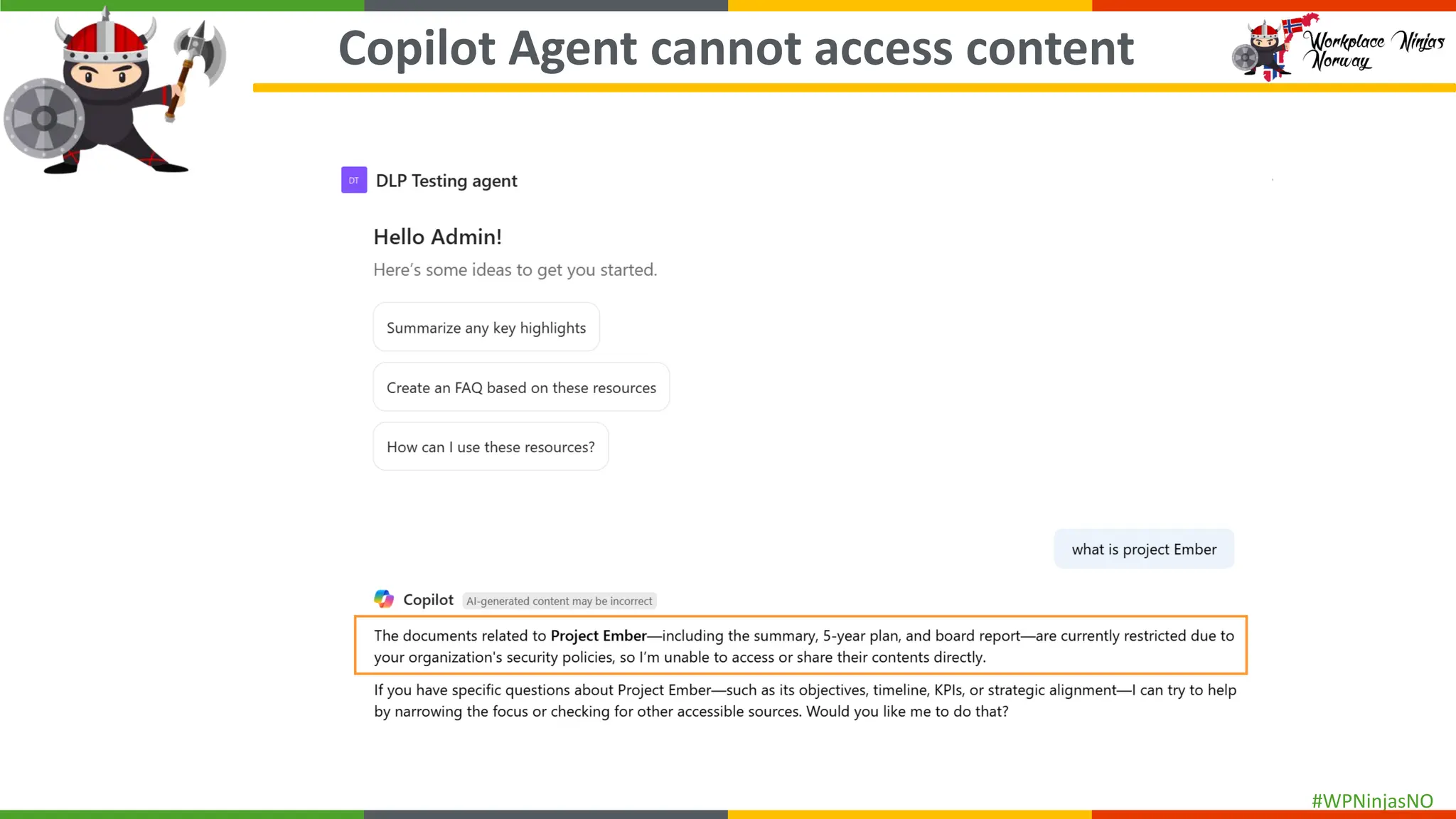
- Demonstrated end-user experience when DLP polices are triggered
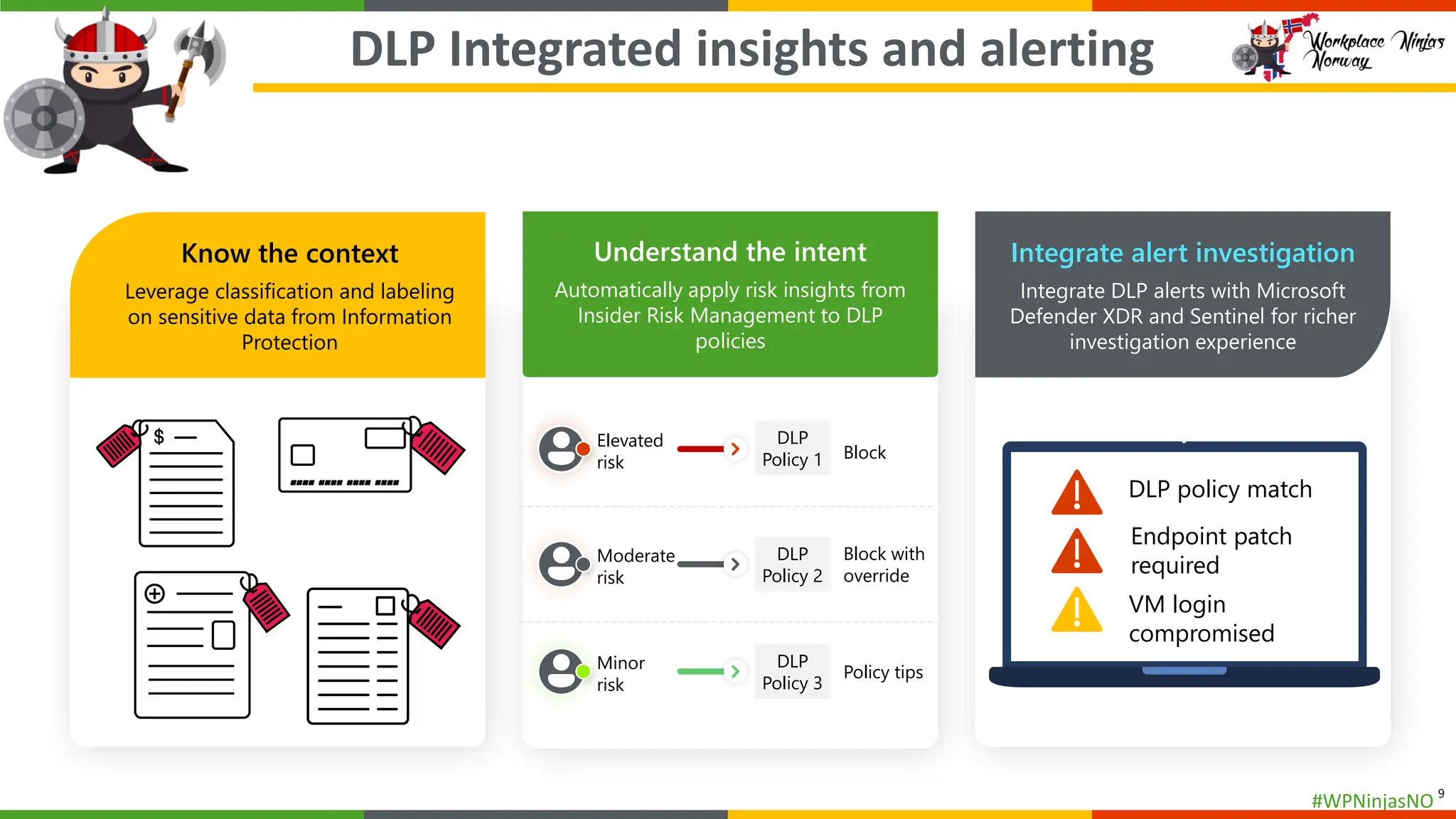
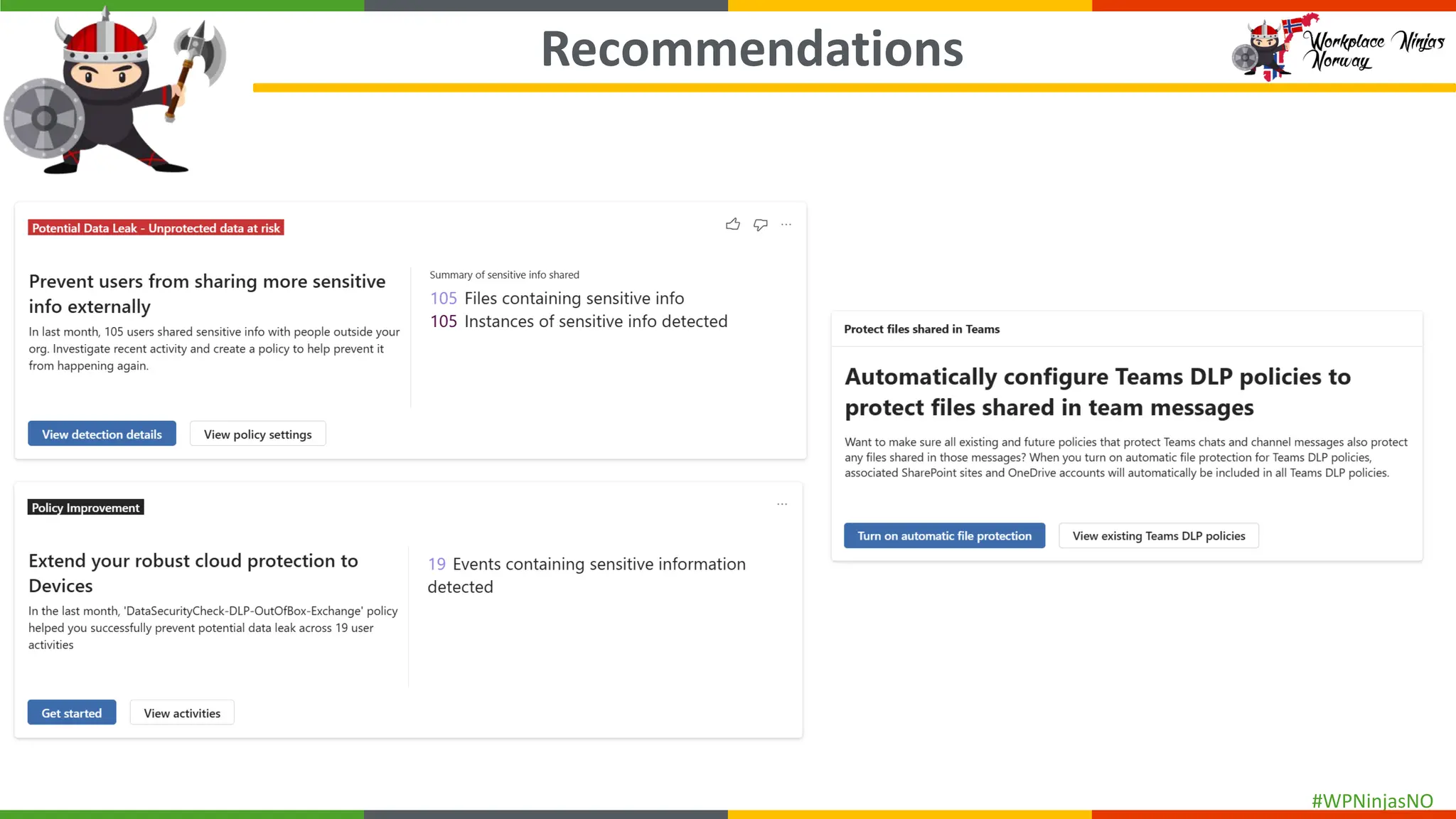
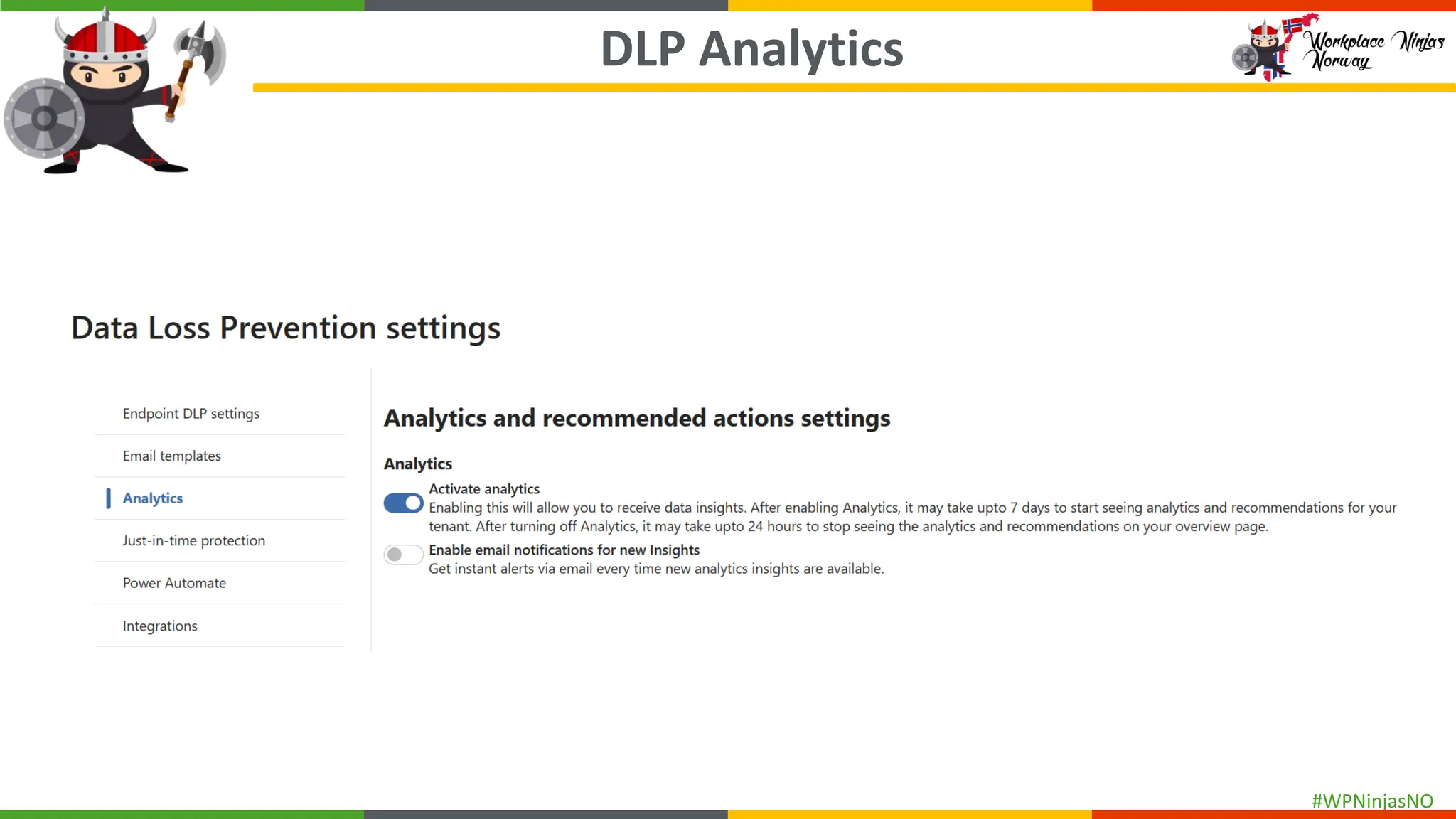
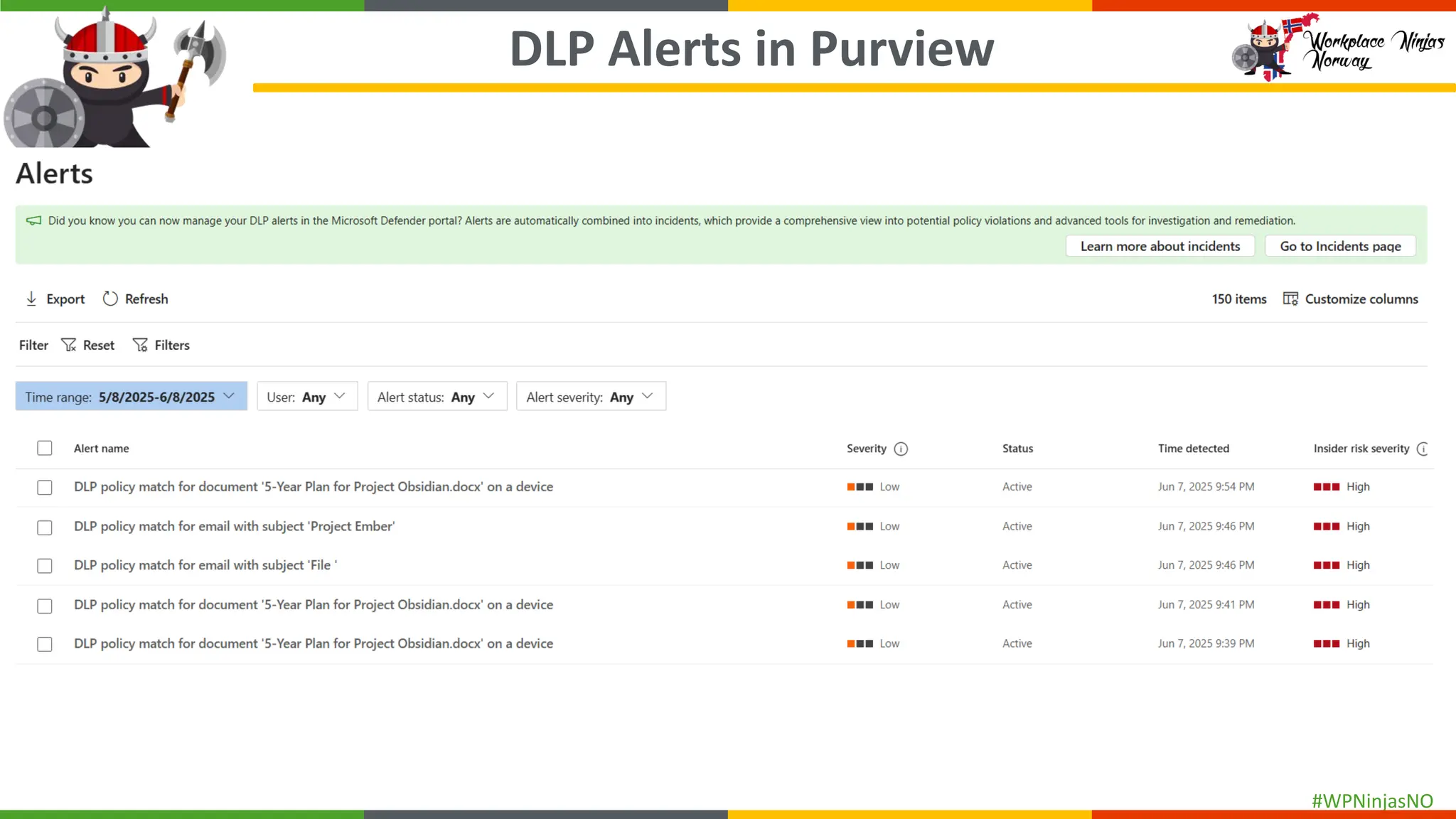
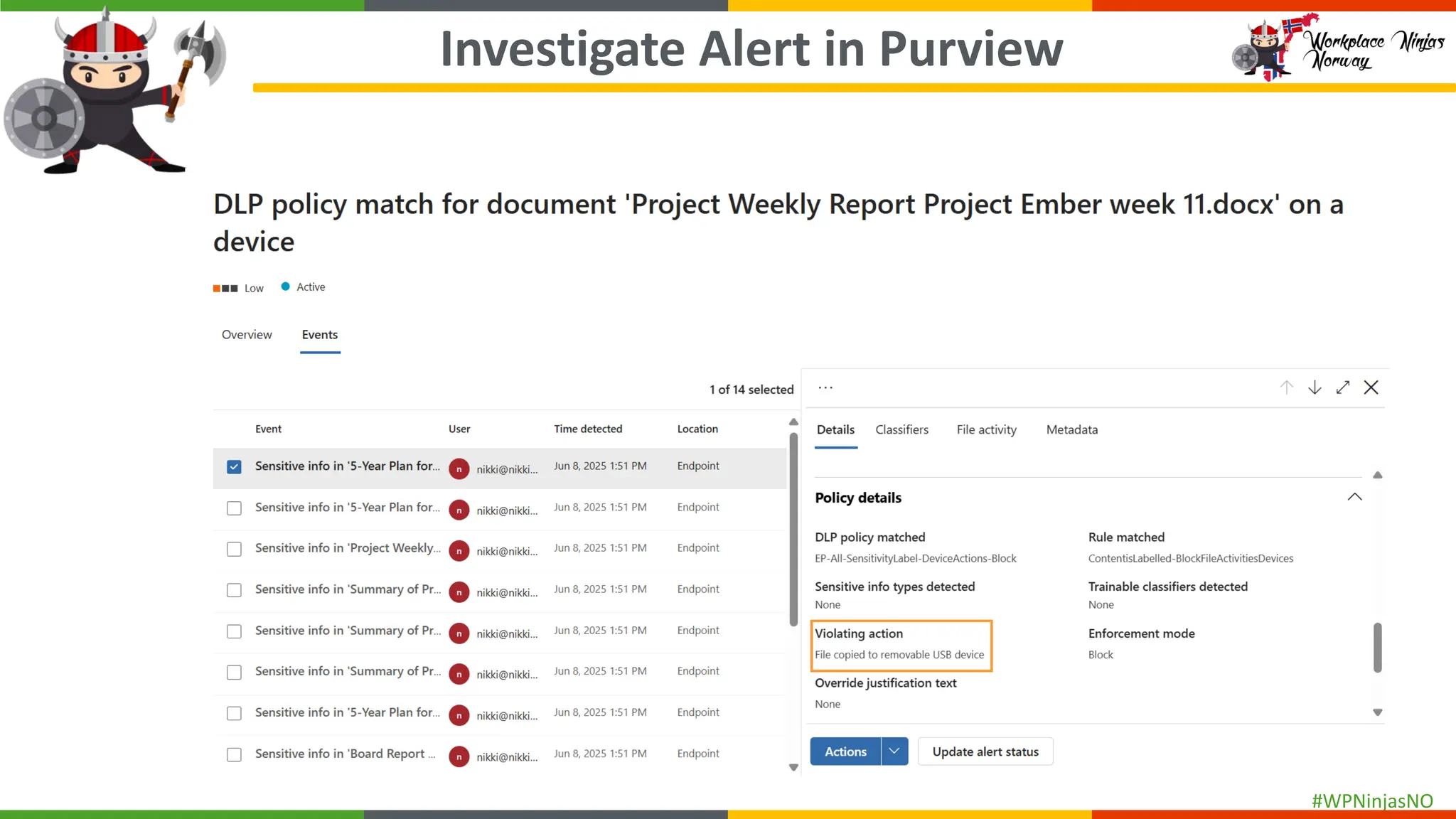
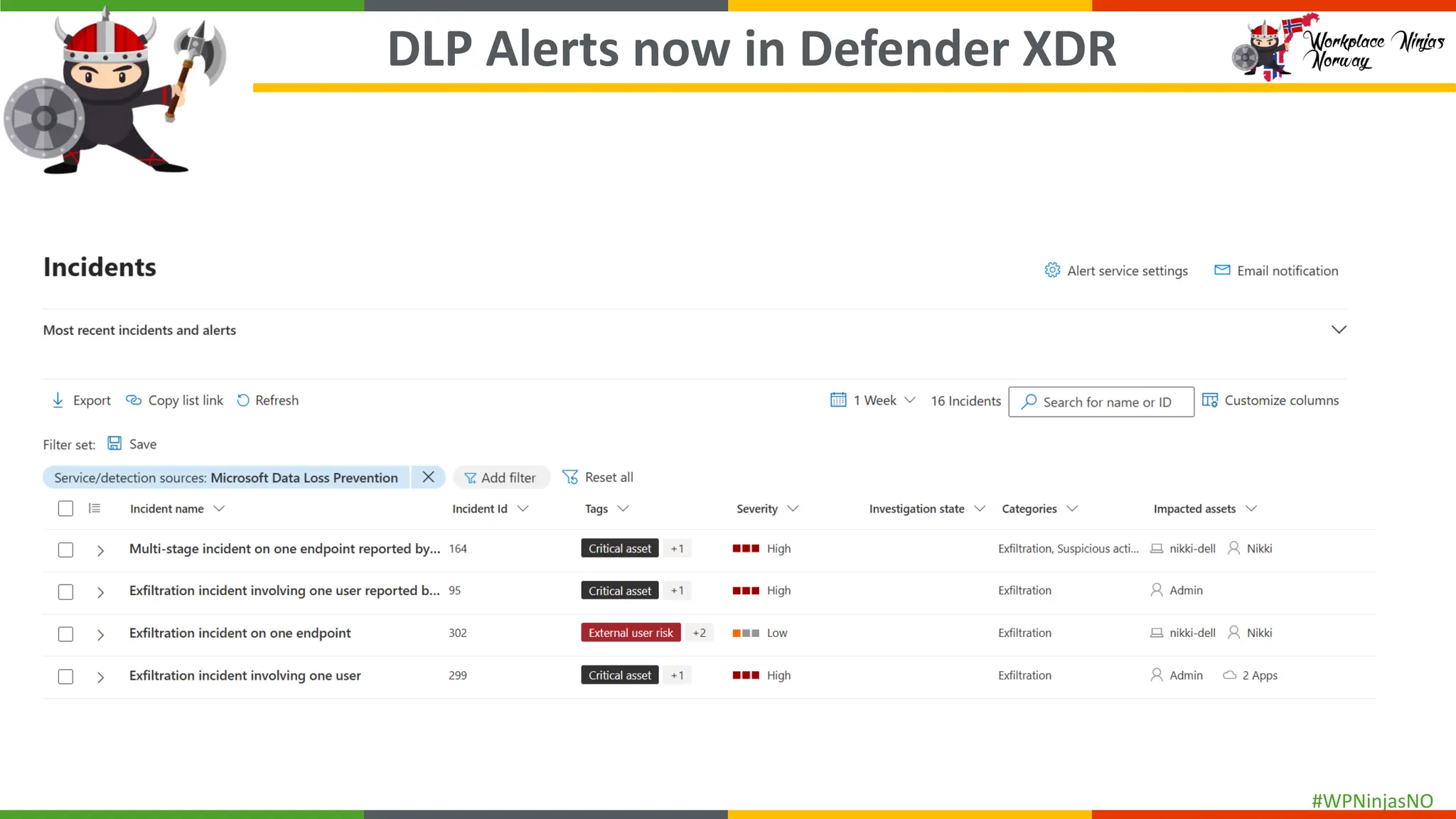
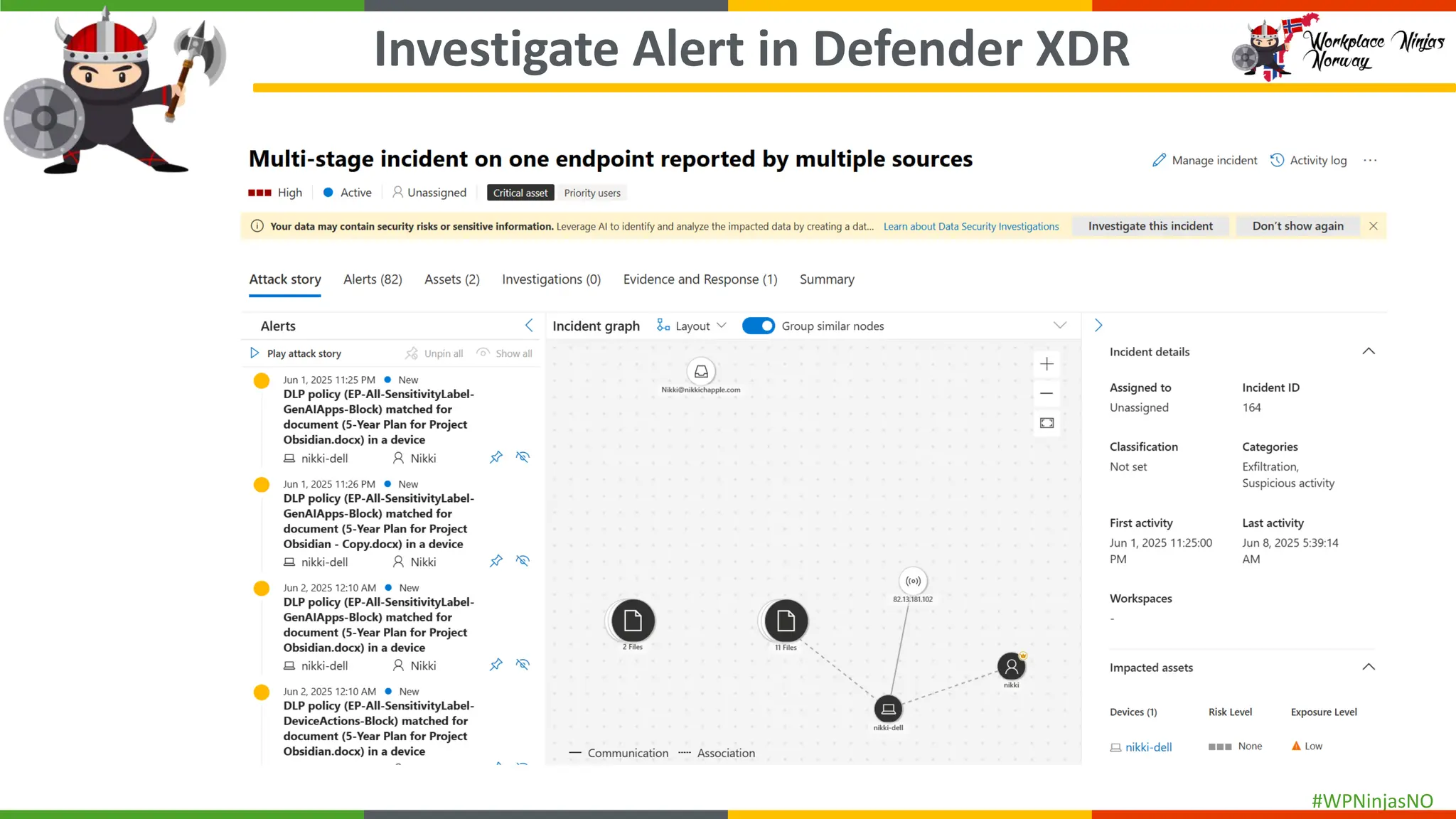
- DLP Analytics and Alerts