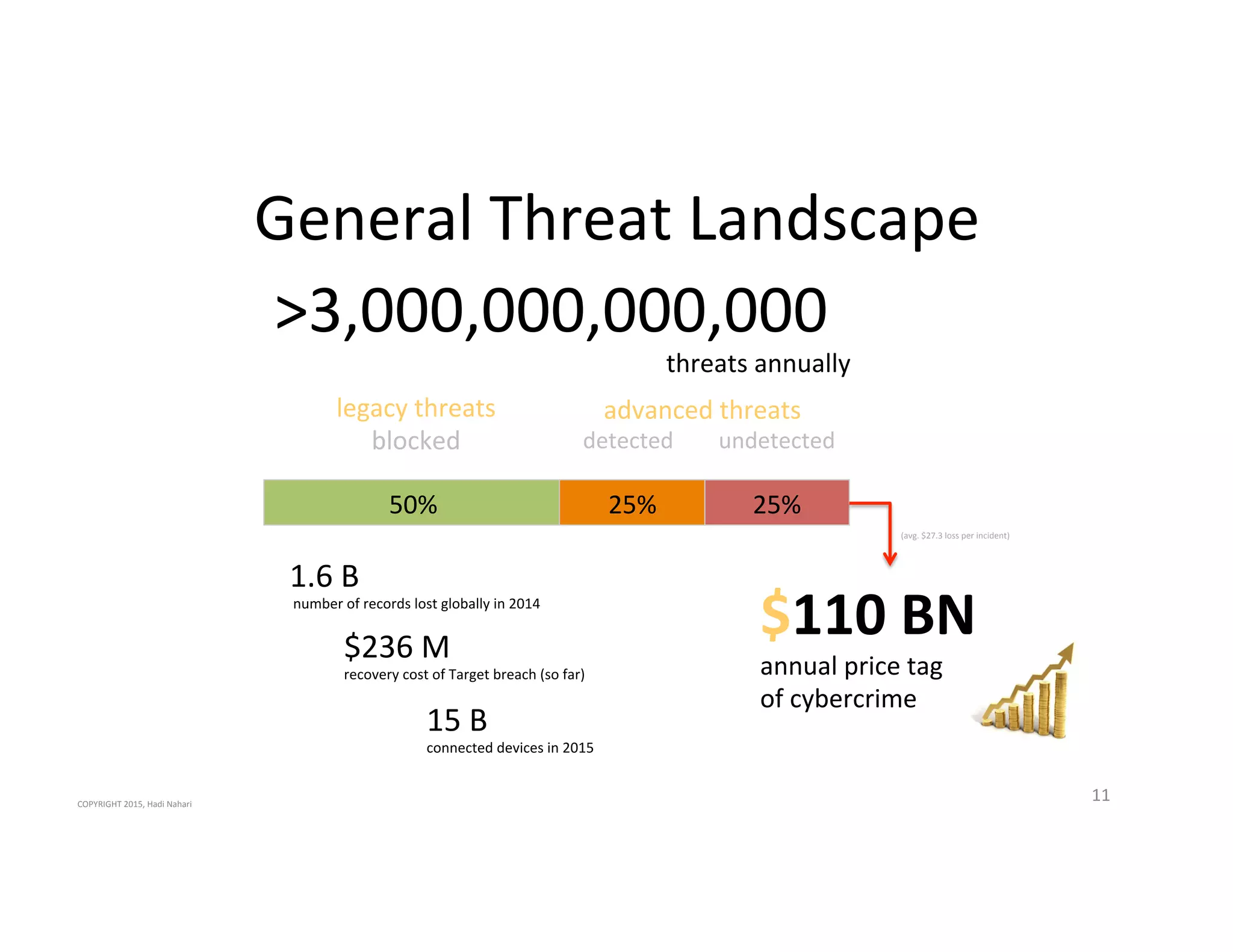
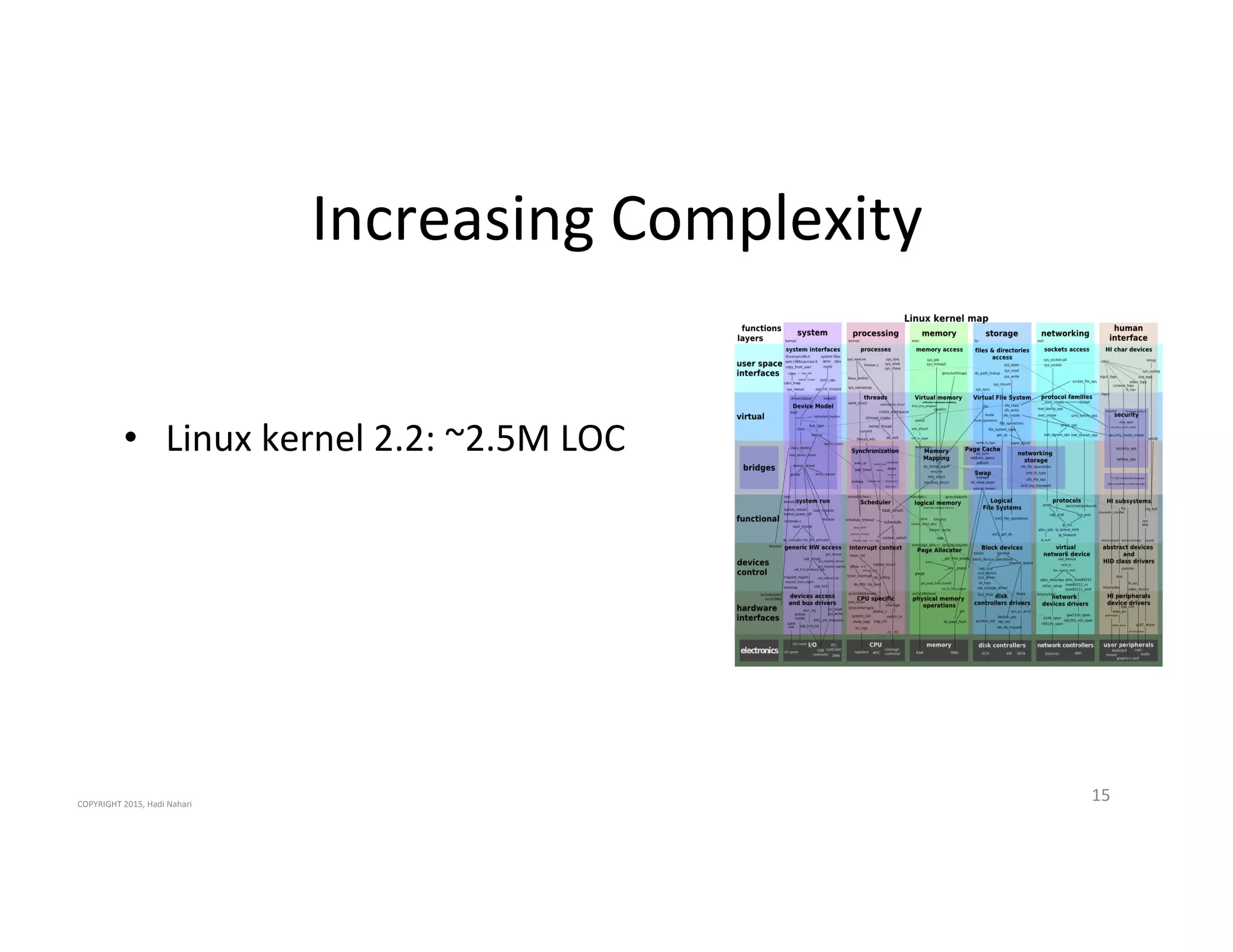
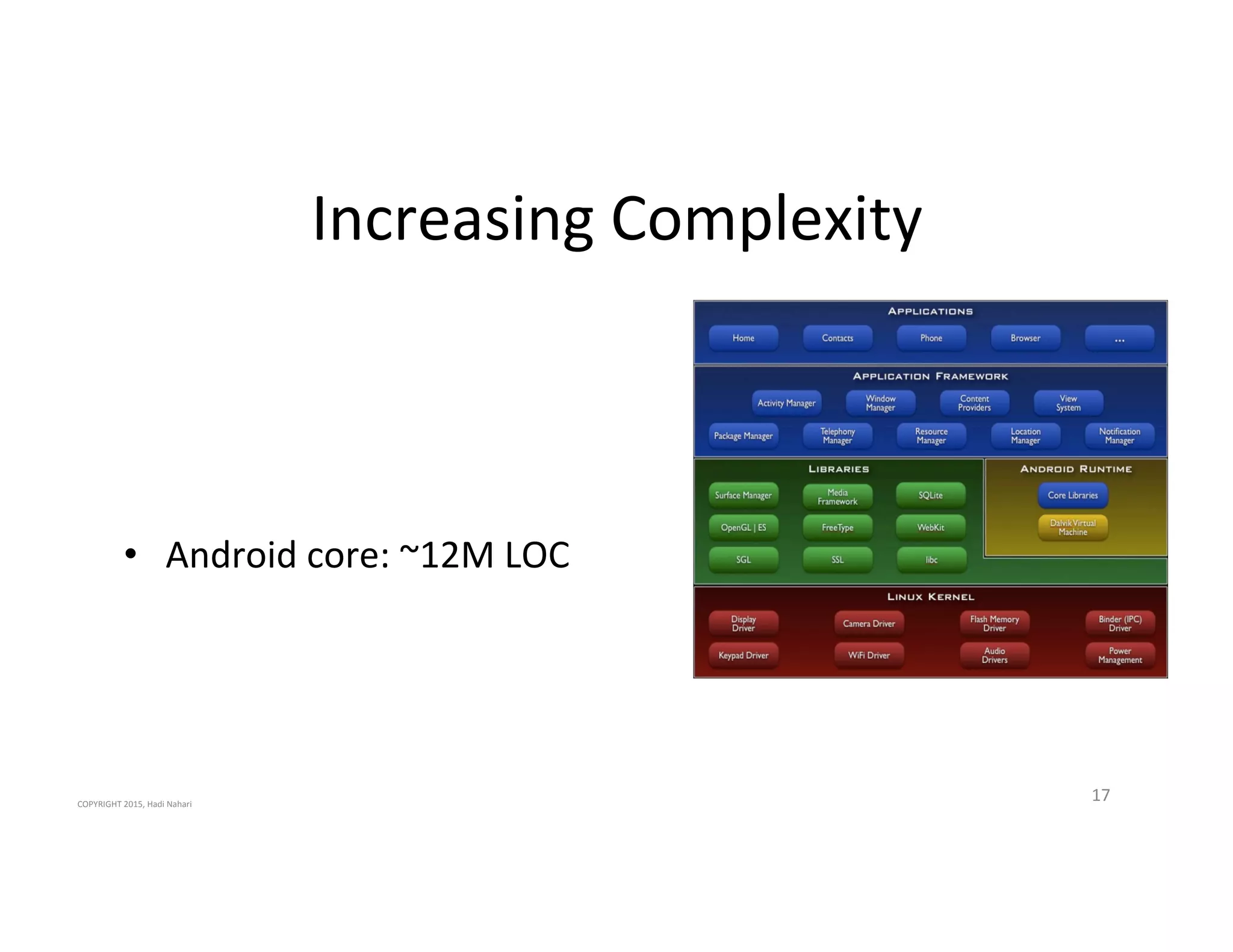
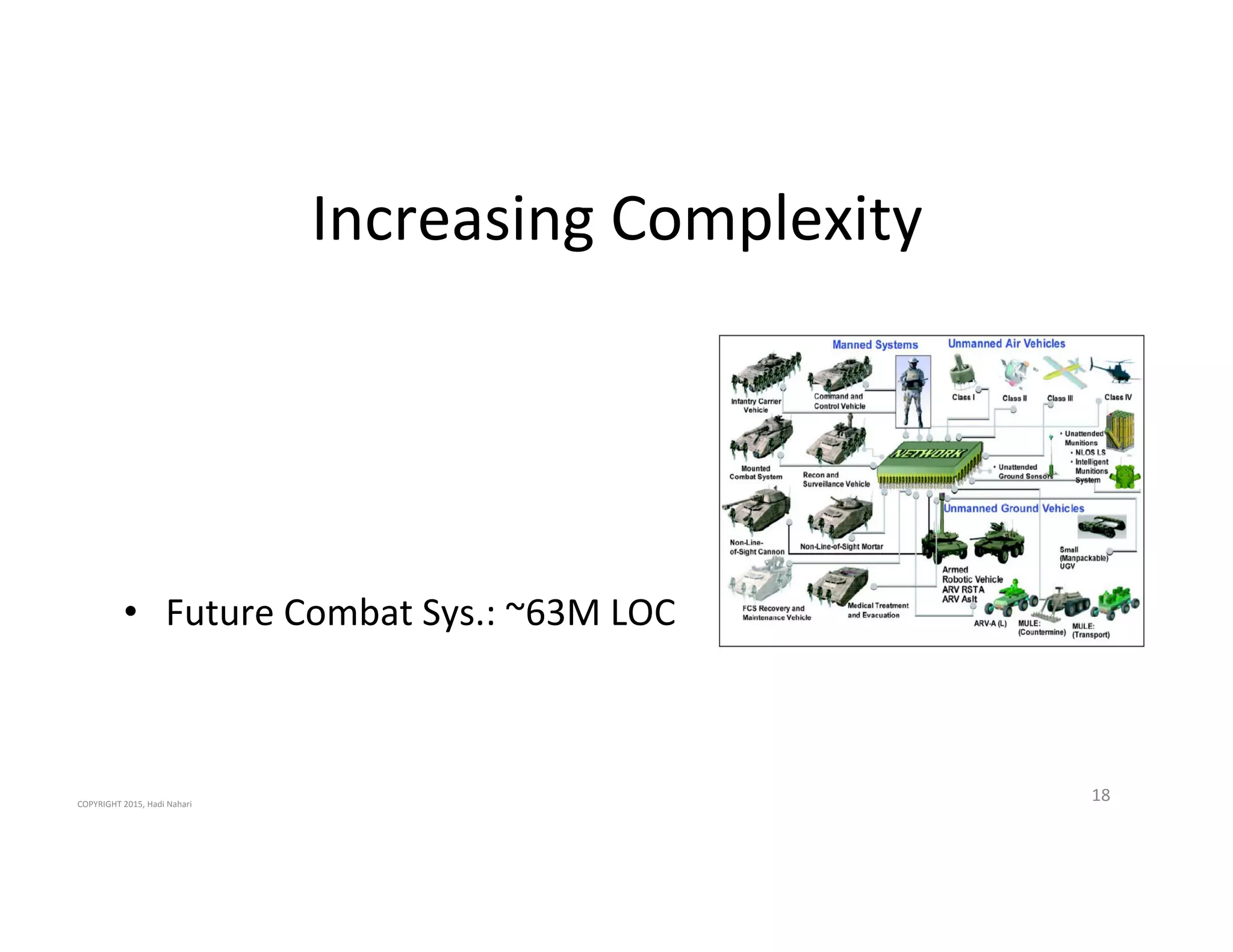
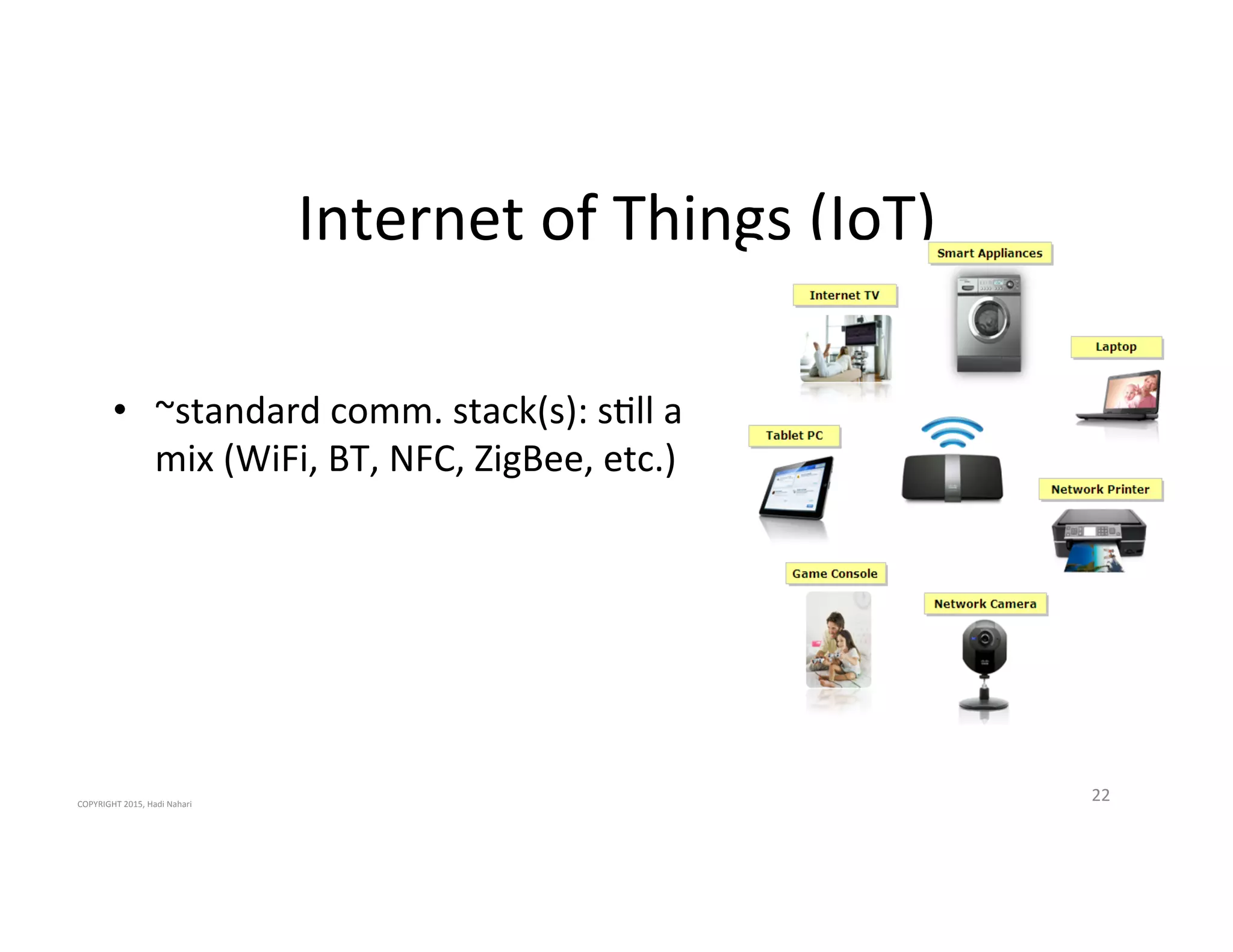
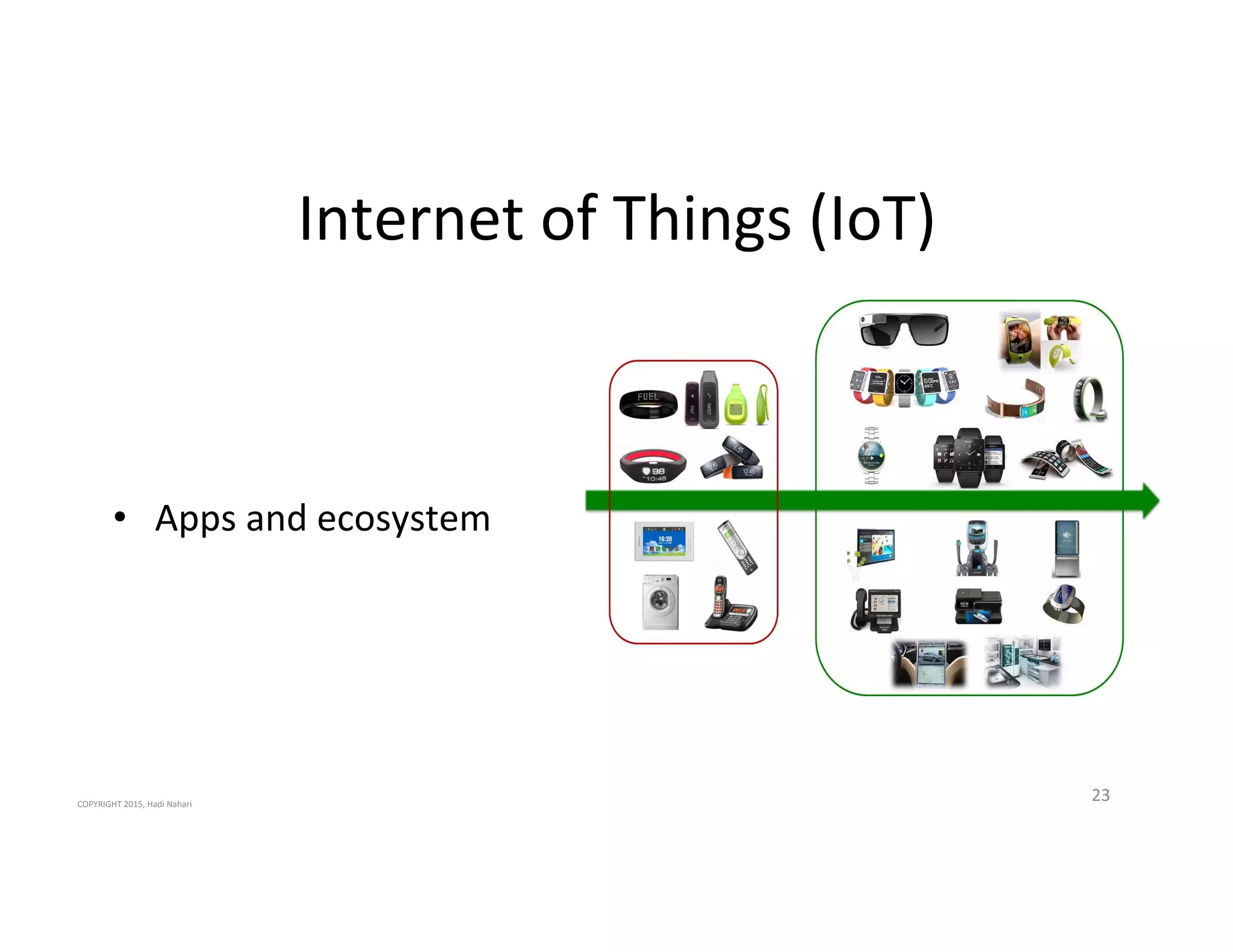
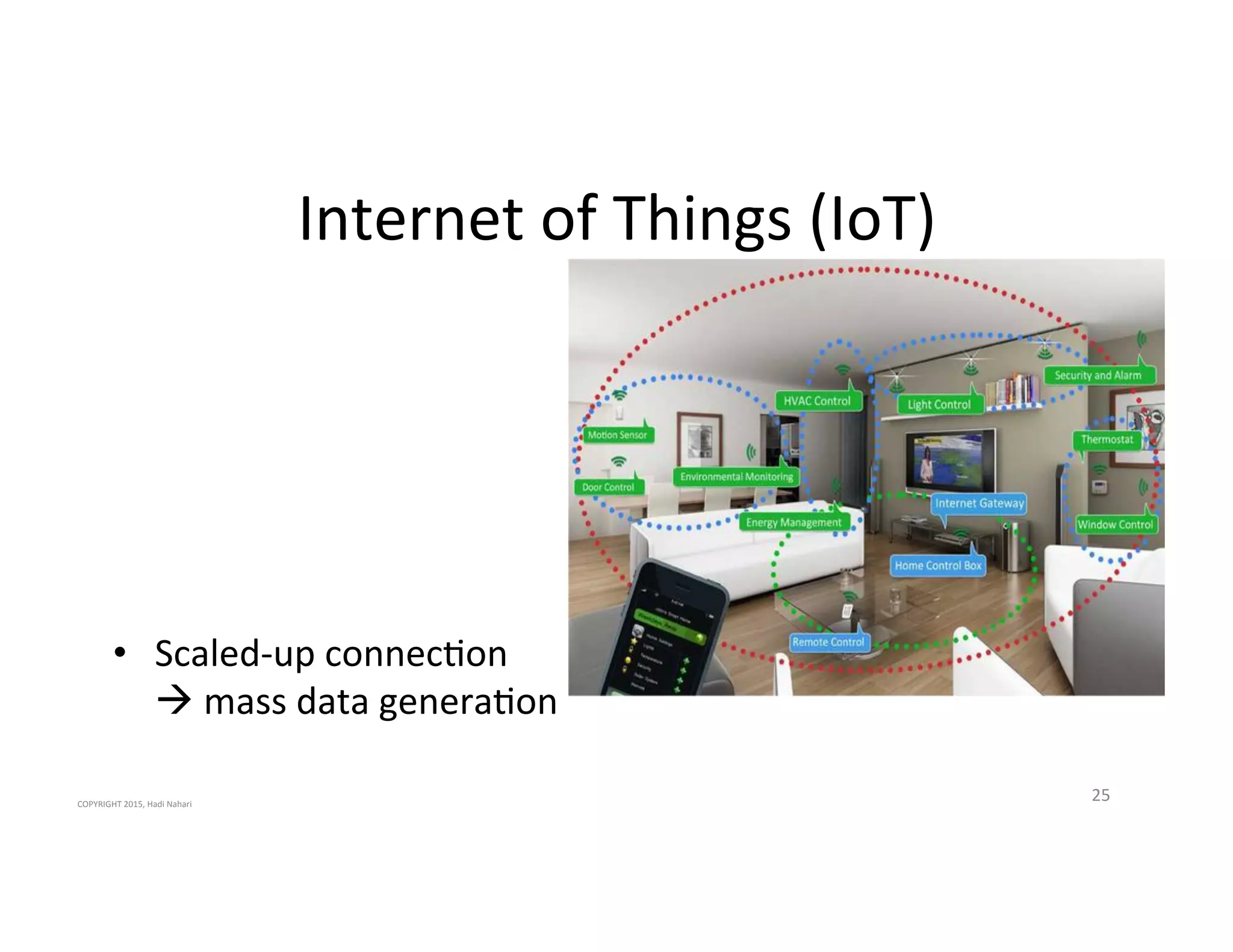
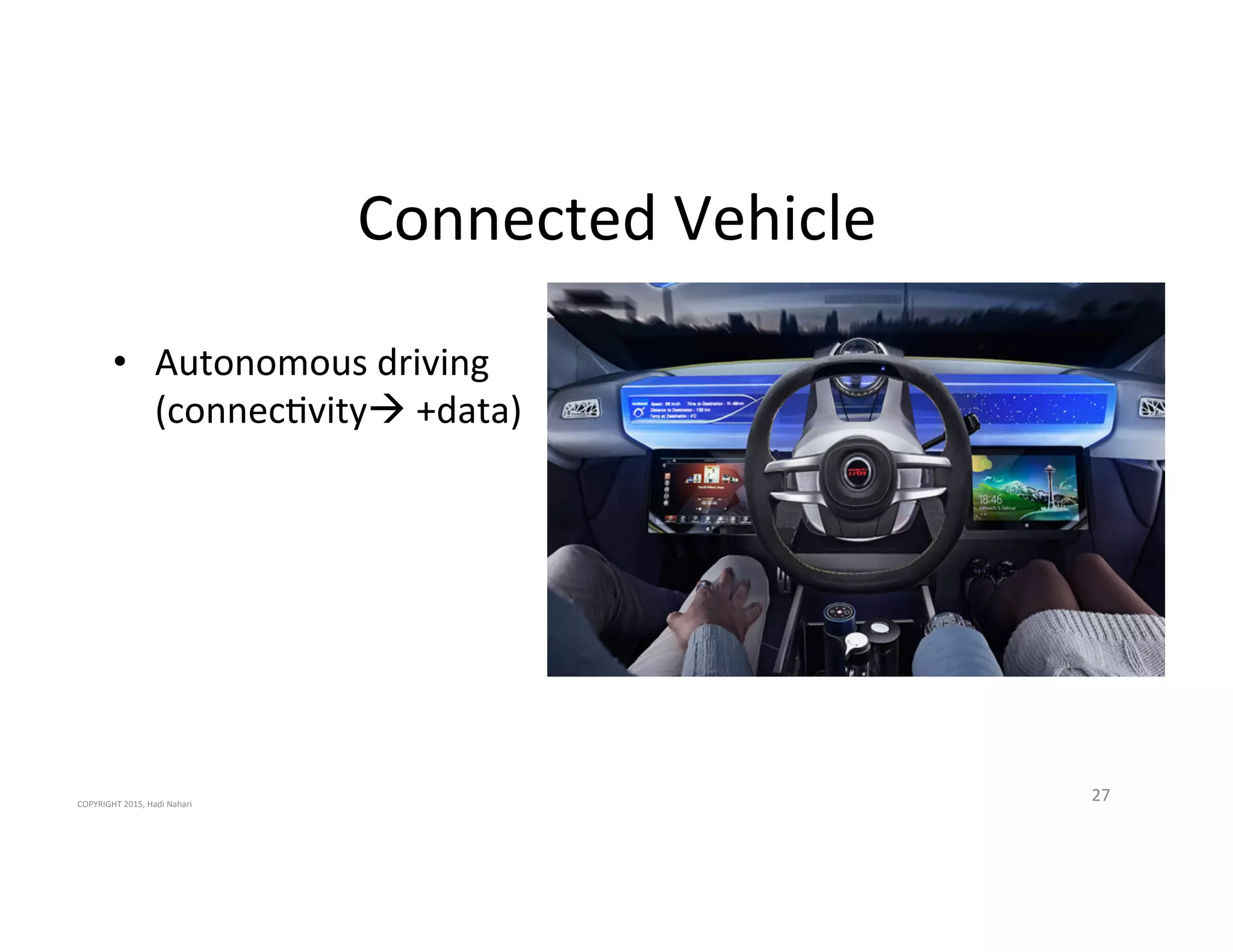
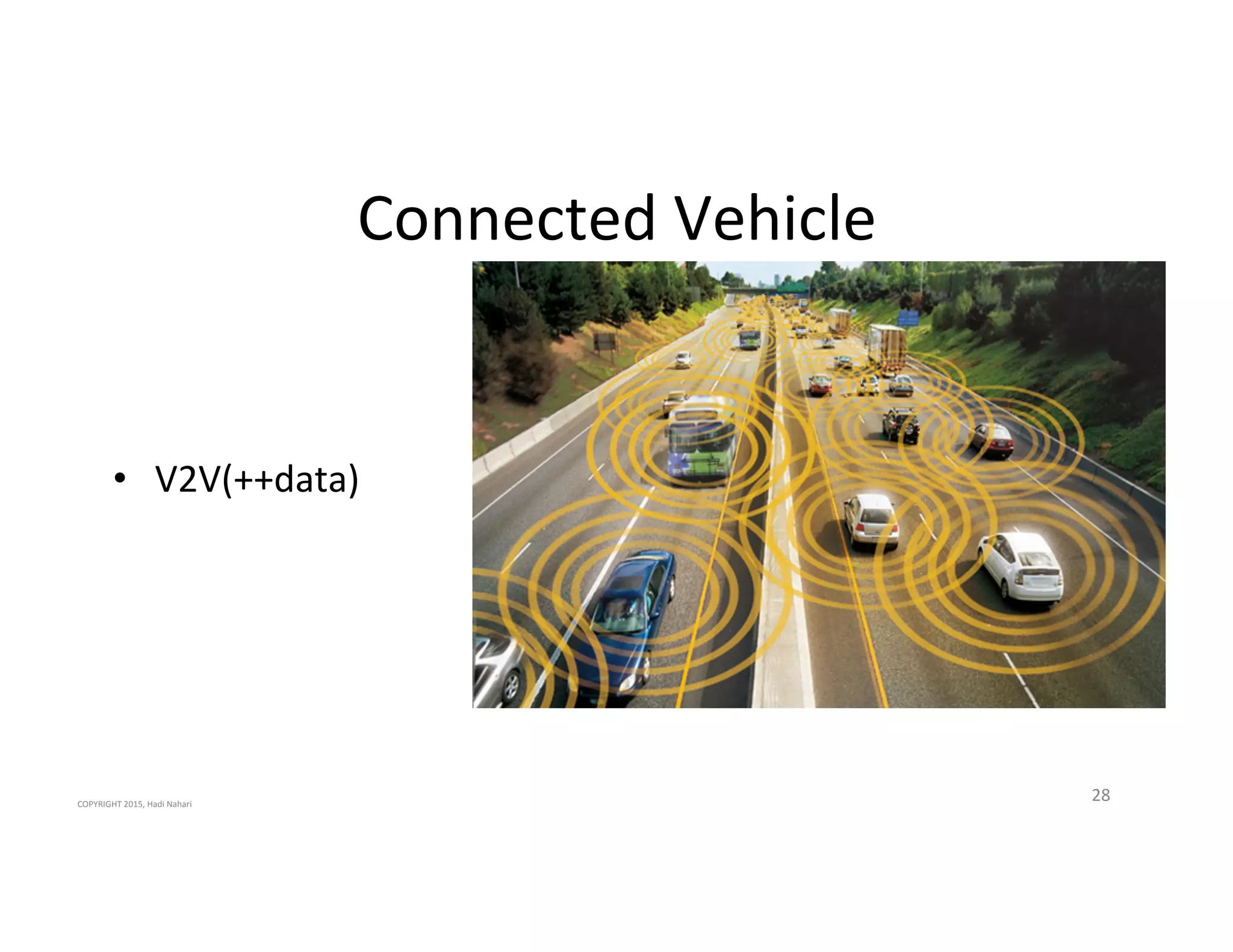
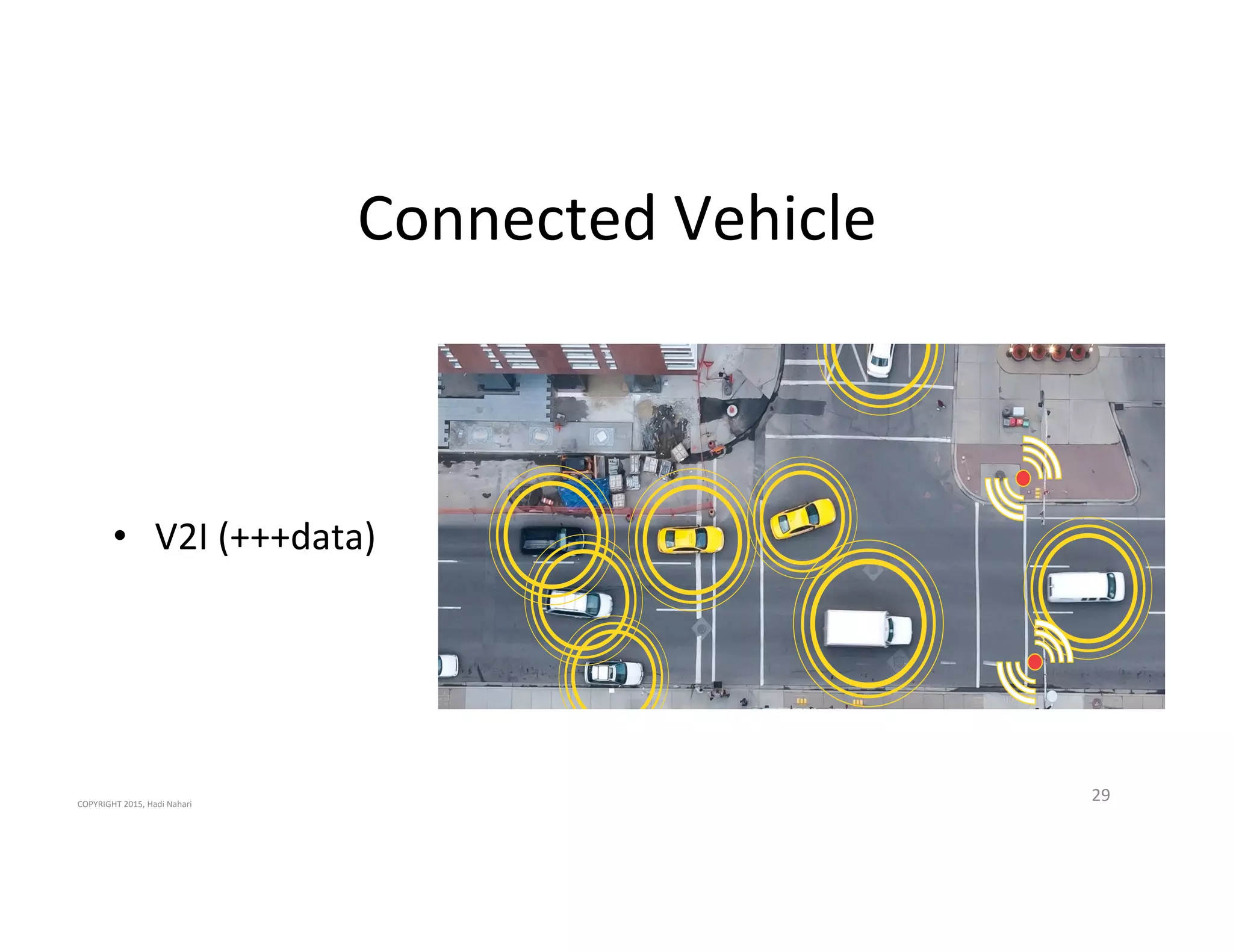
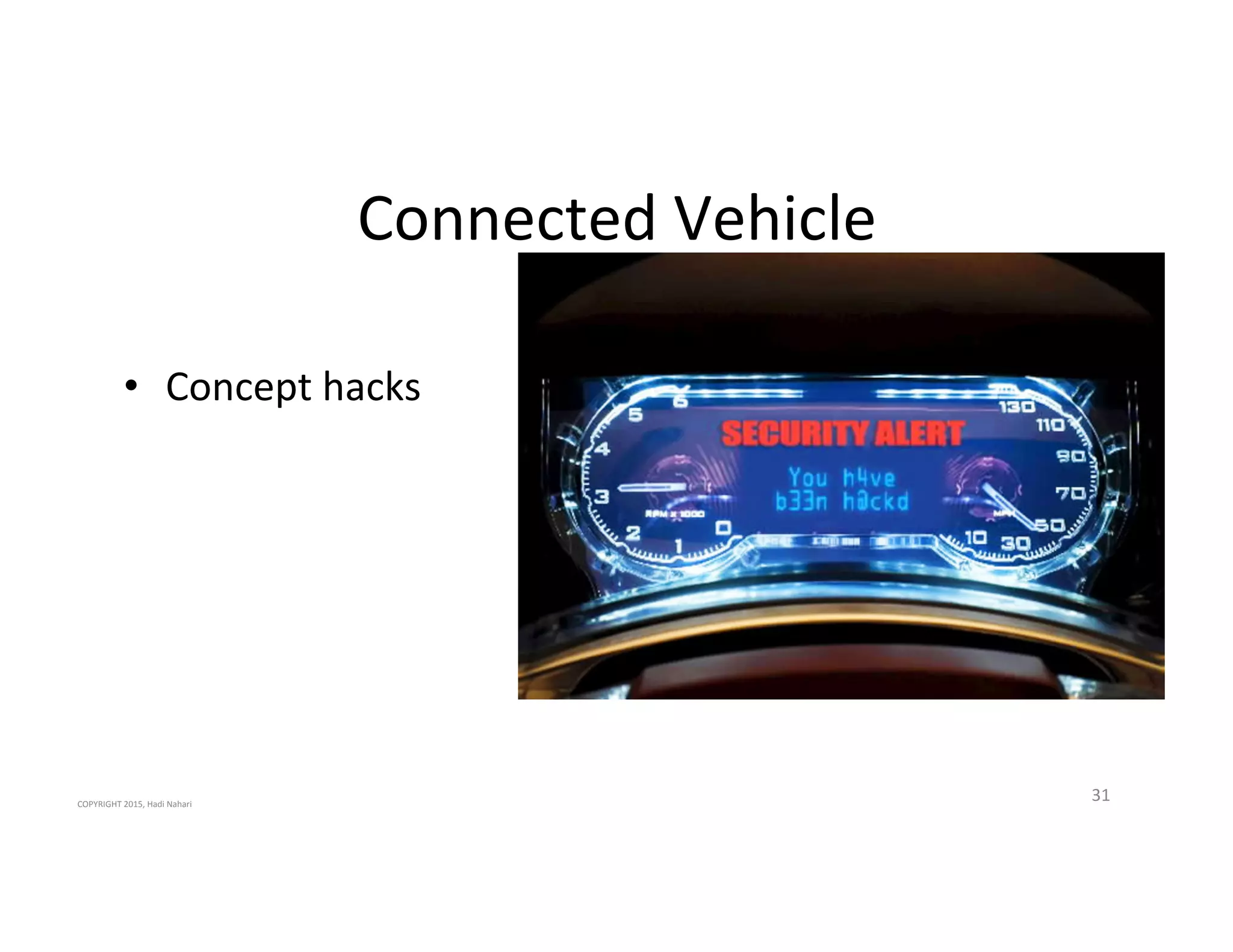
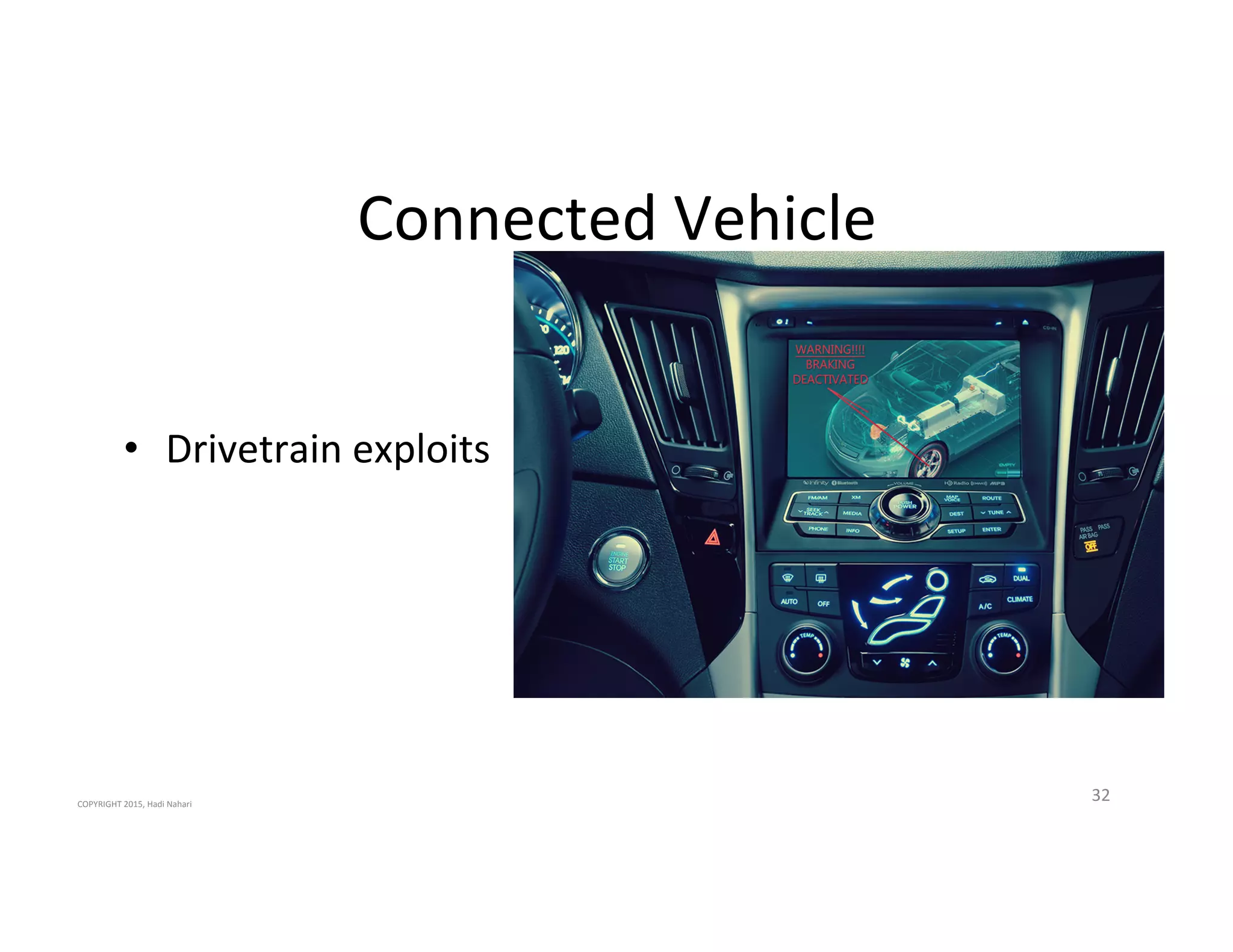
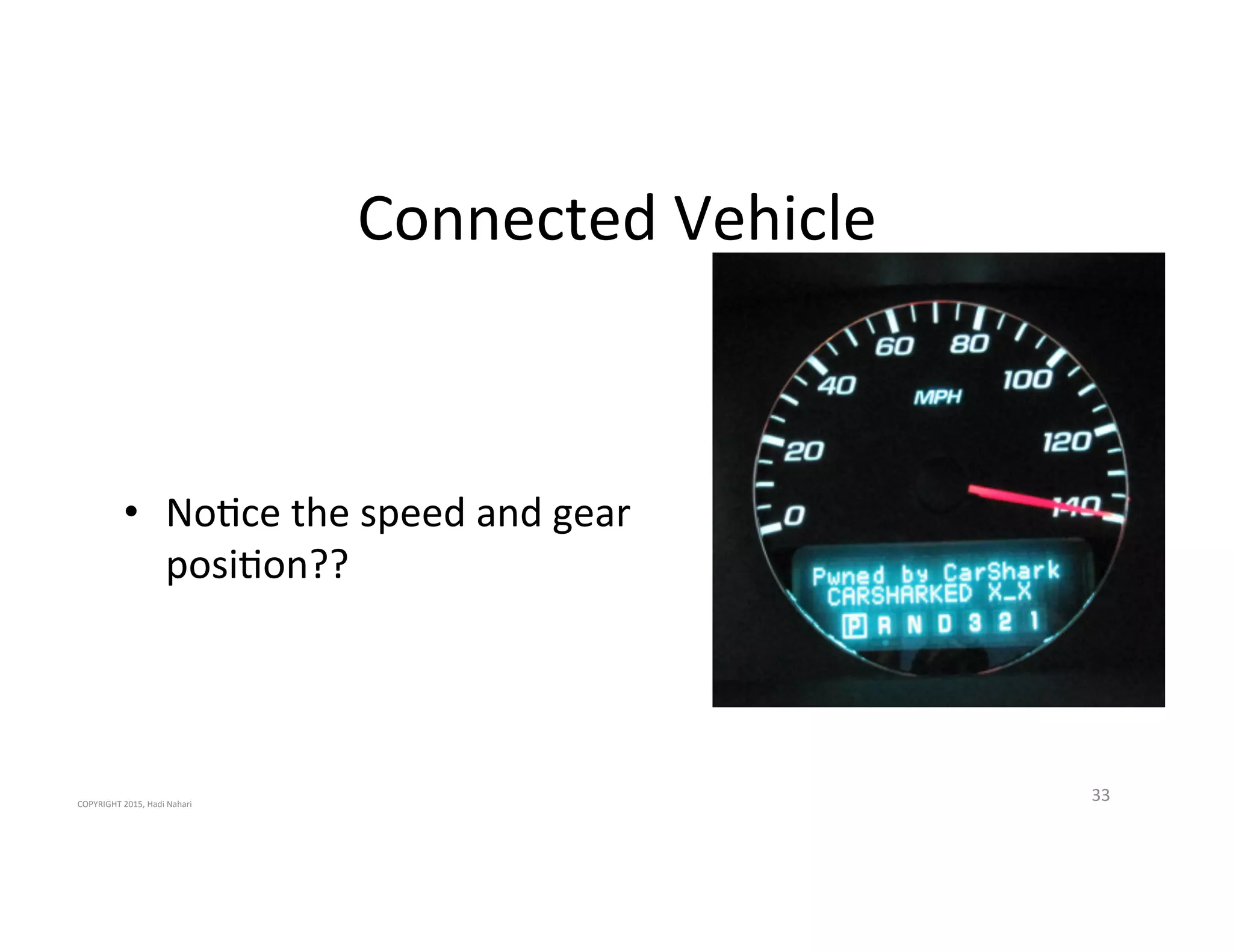
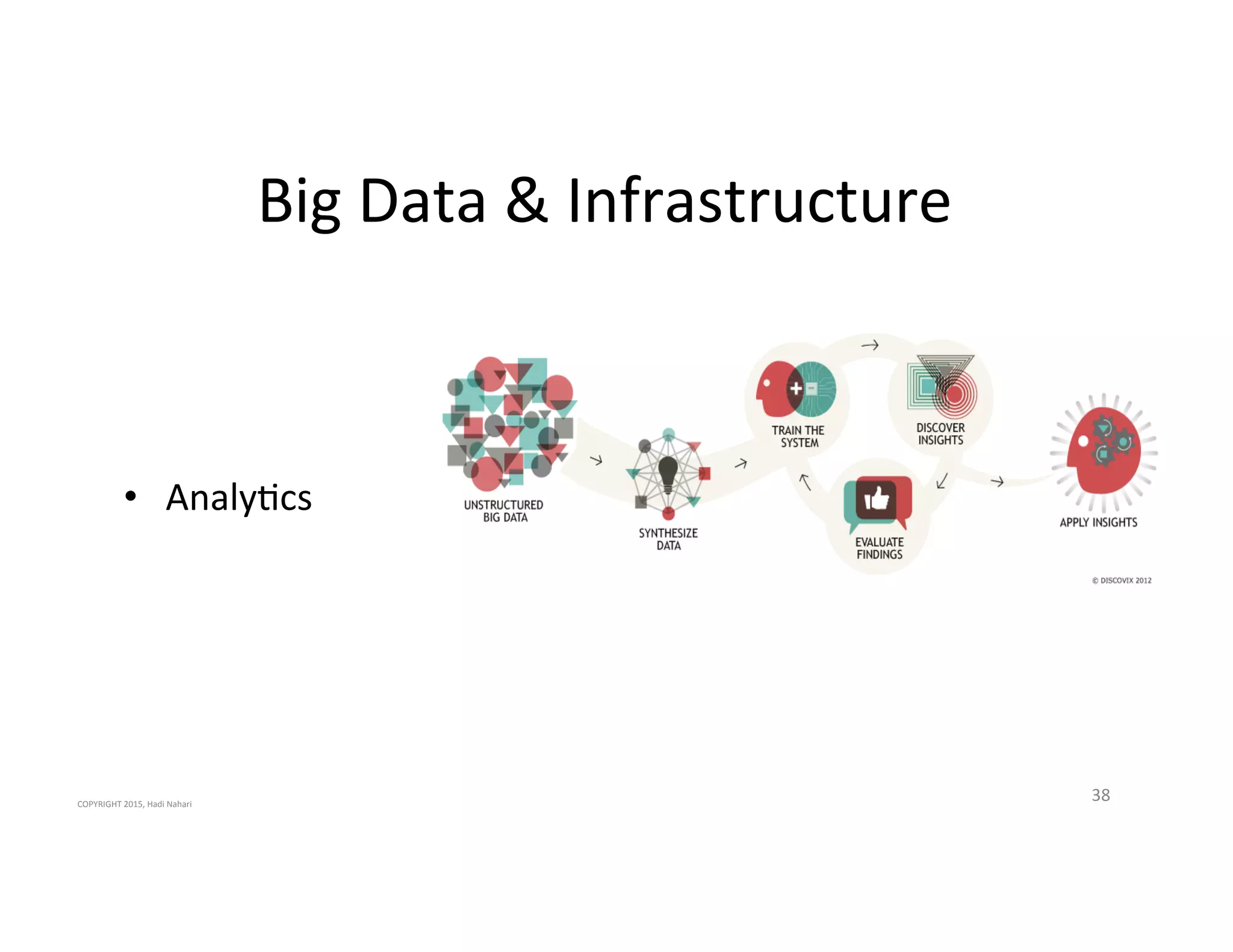
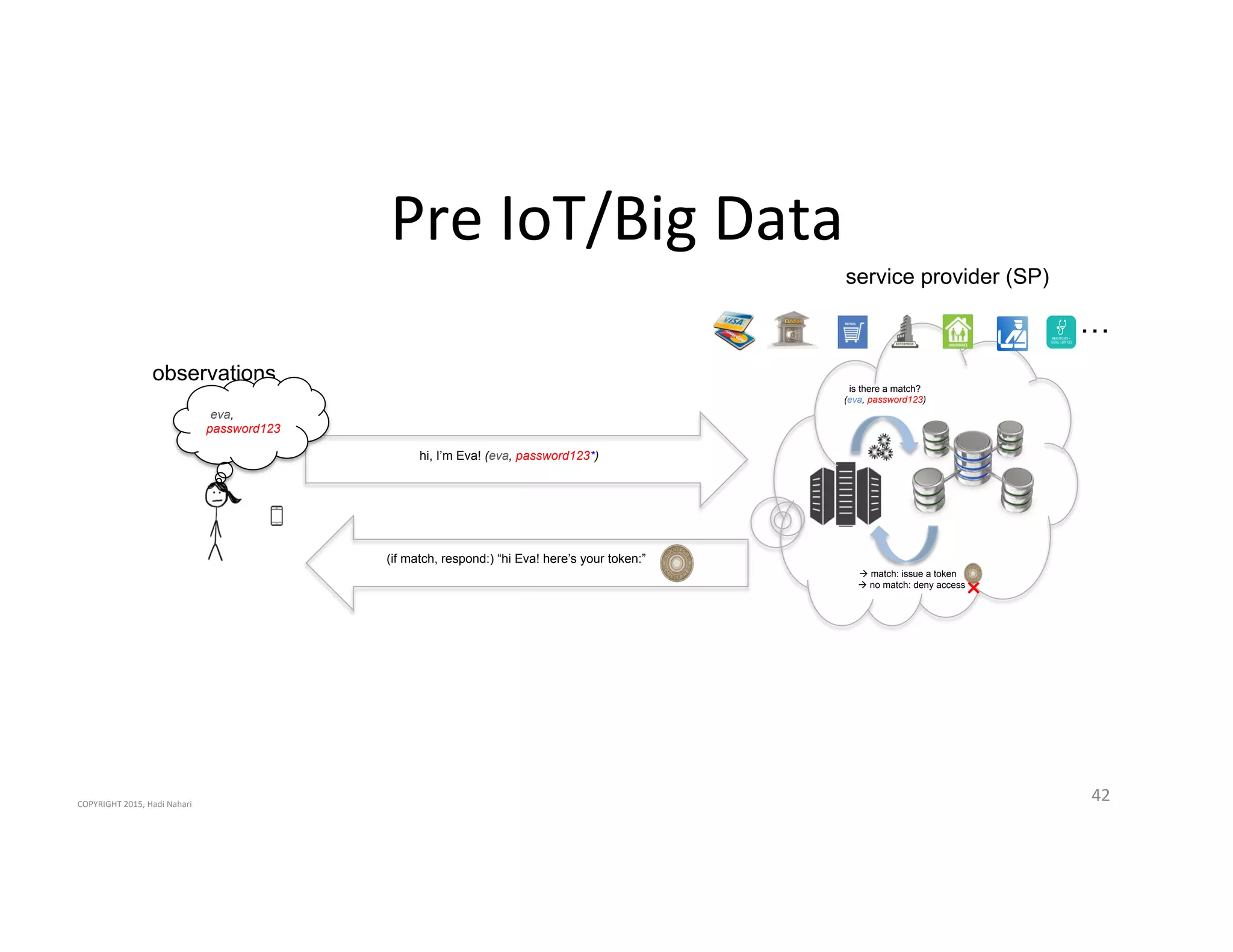
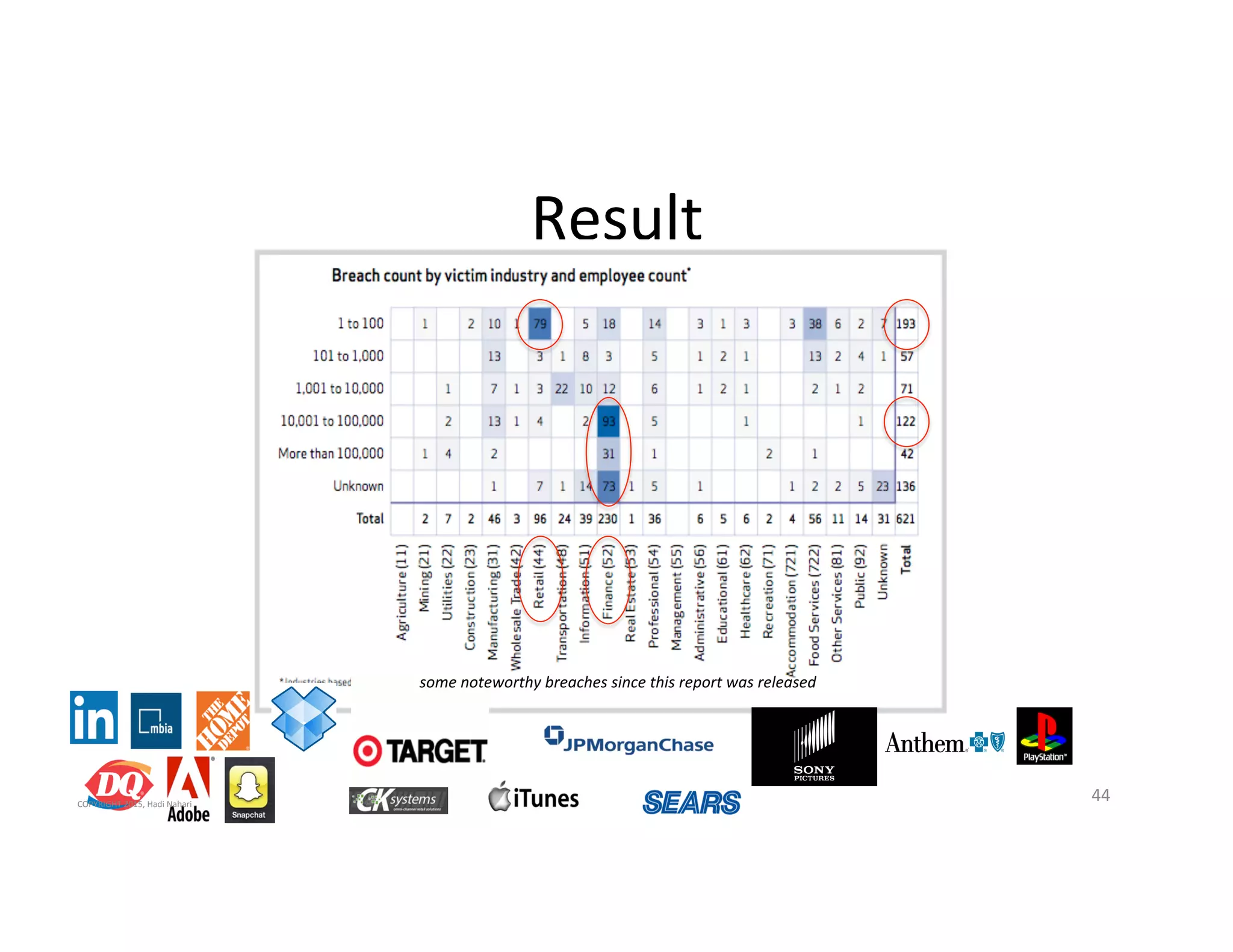
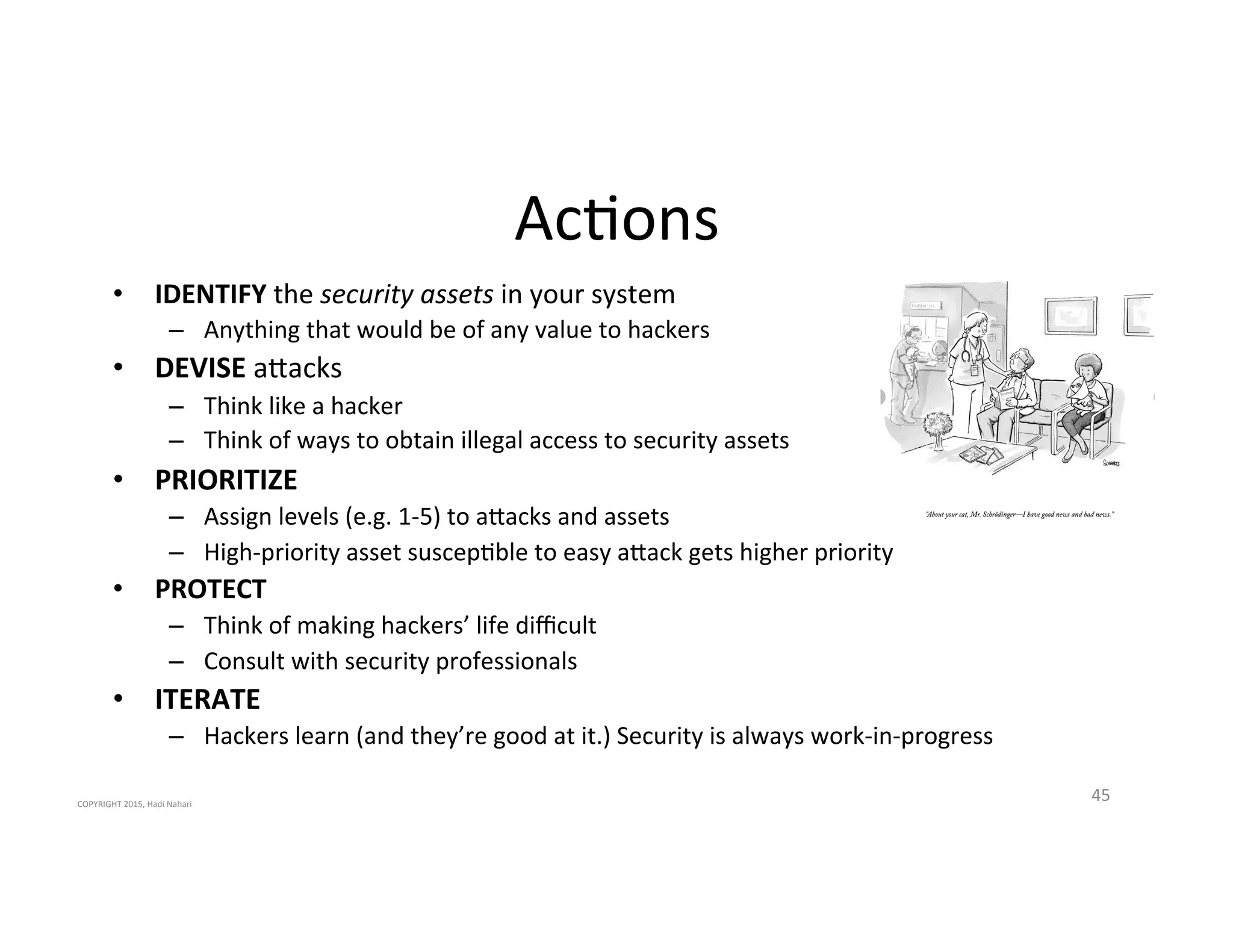
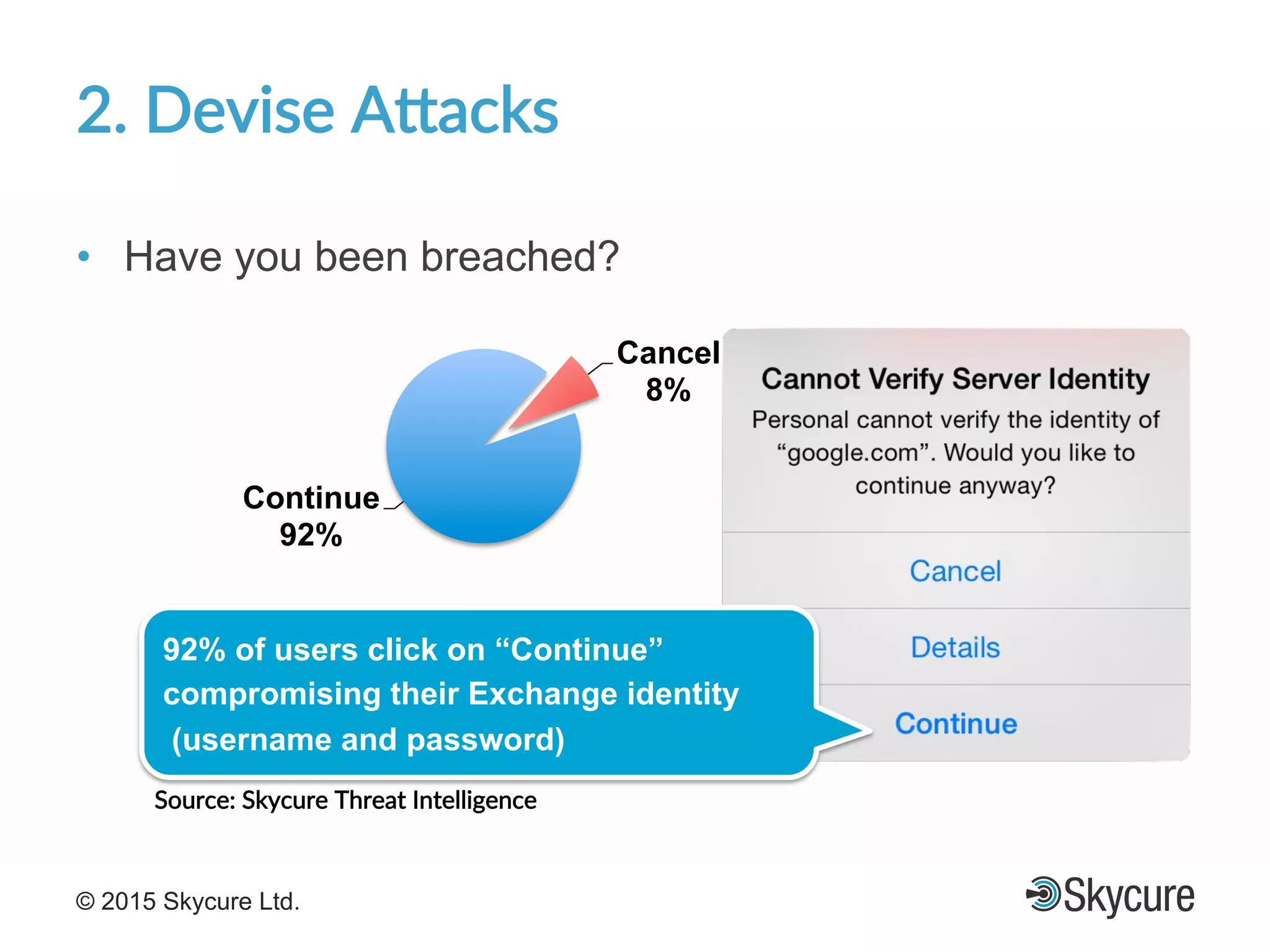
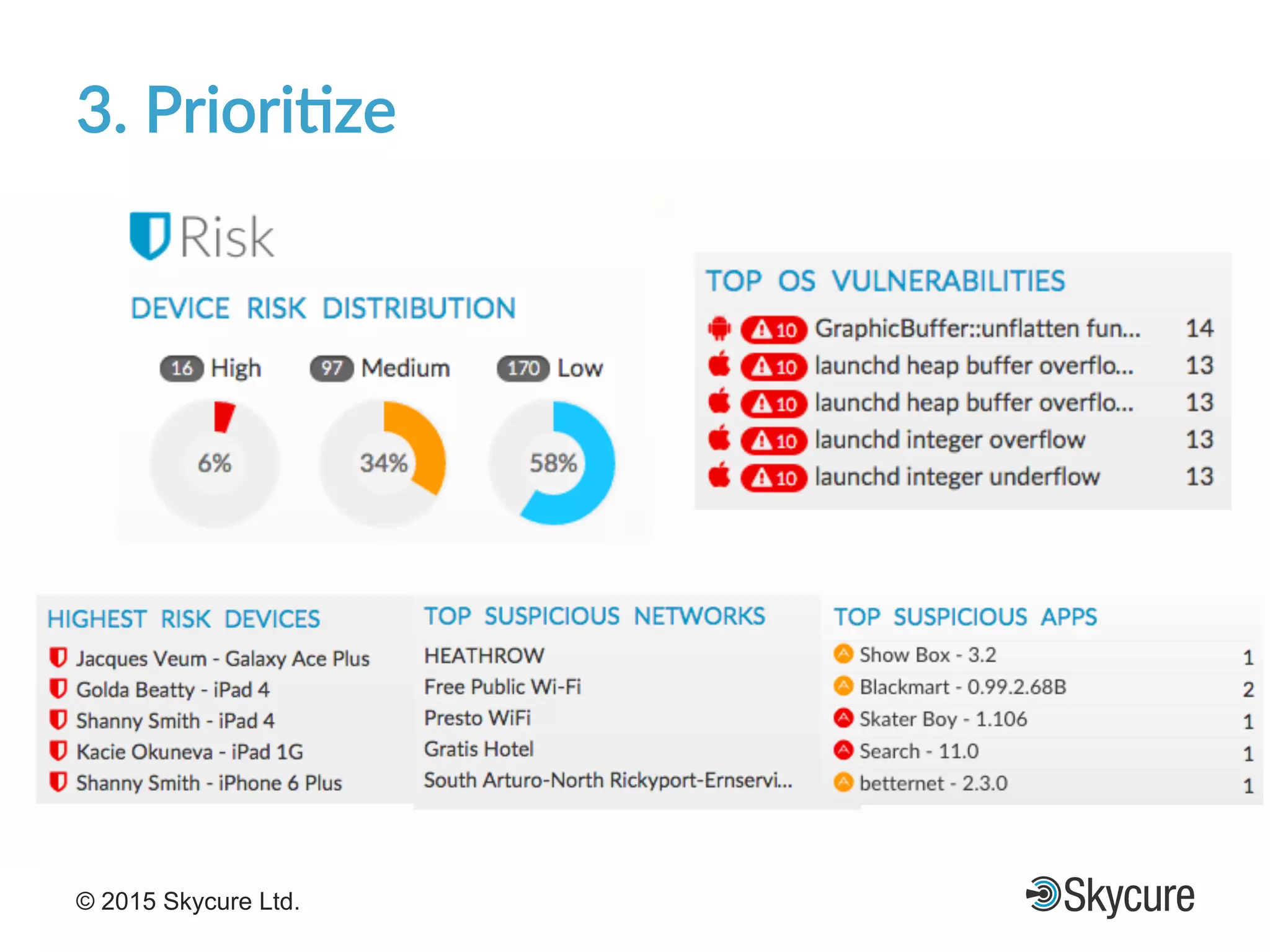
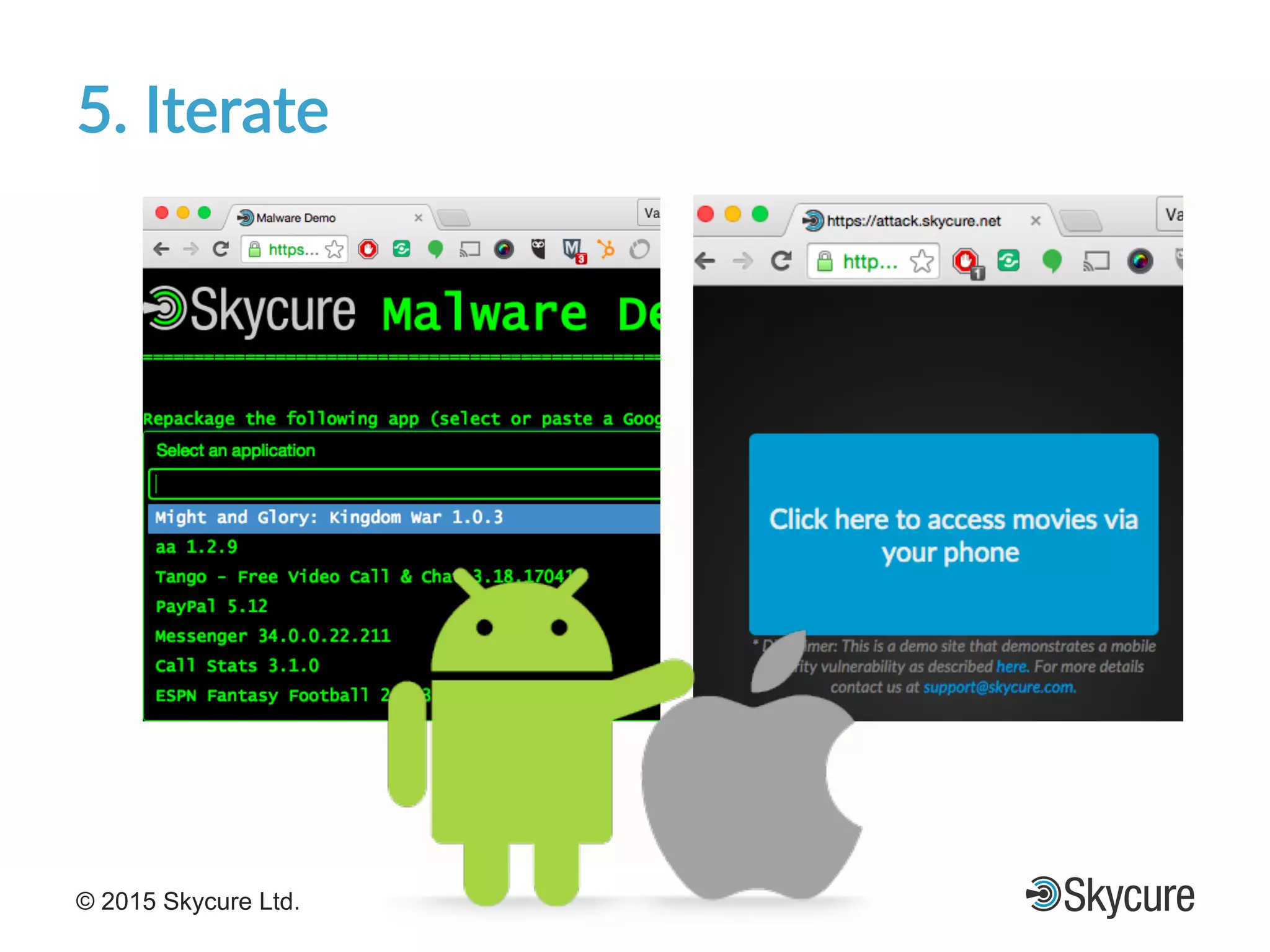
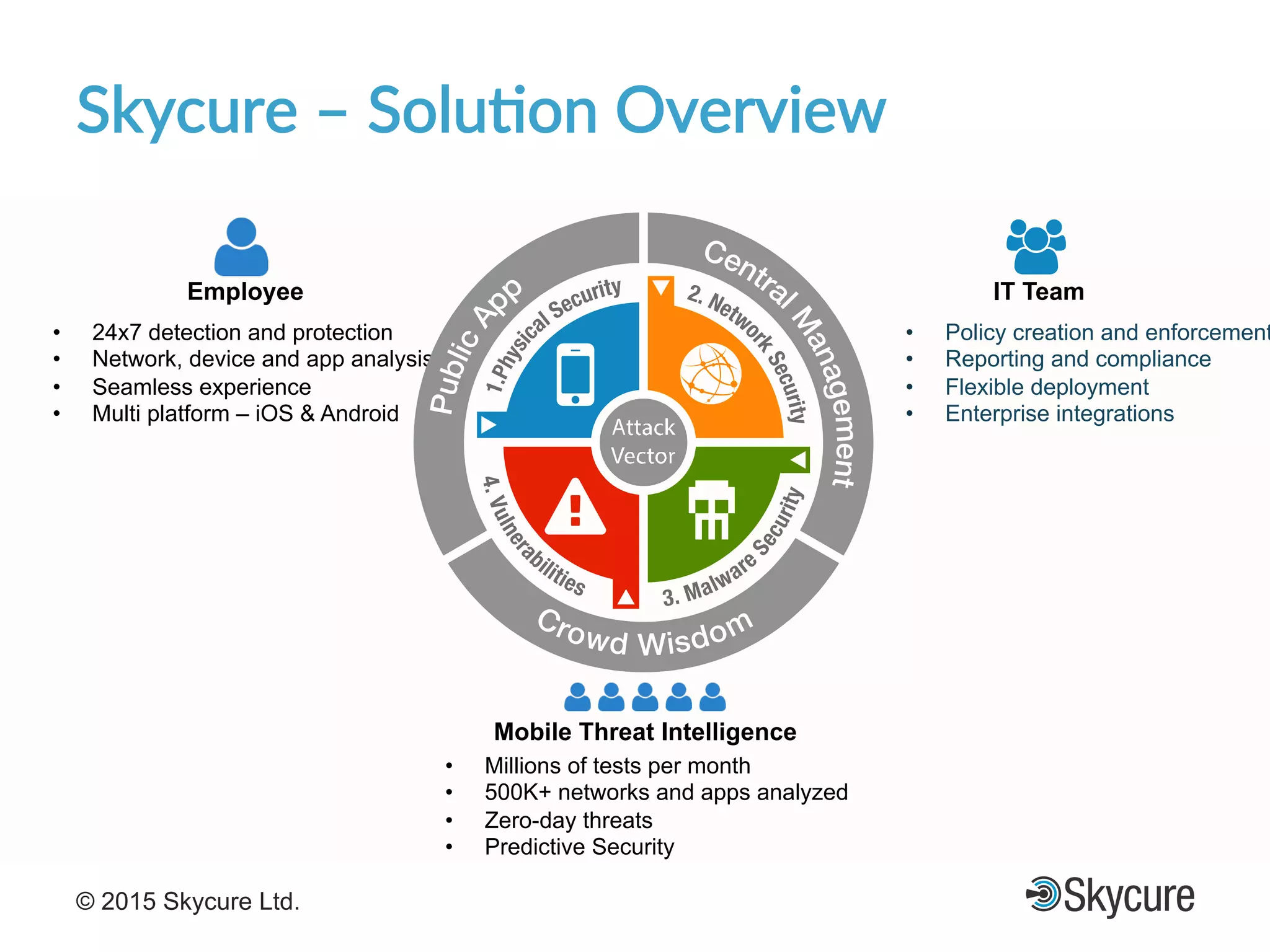
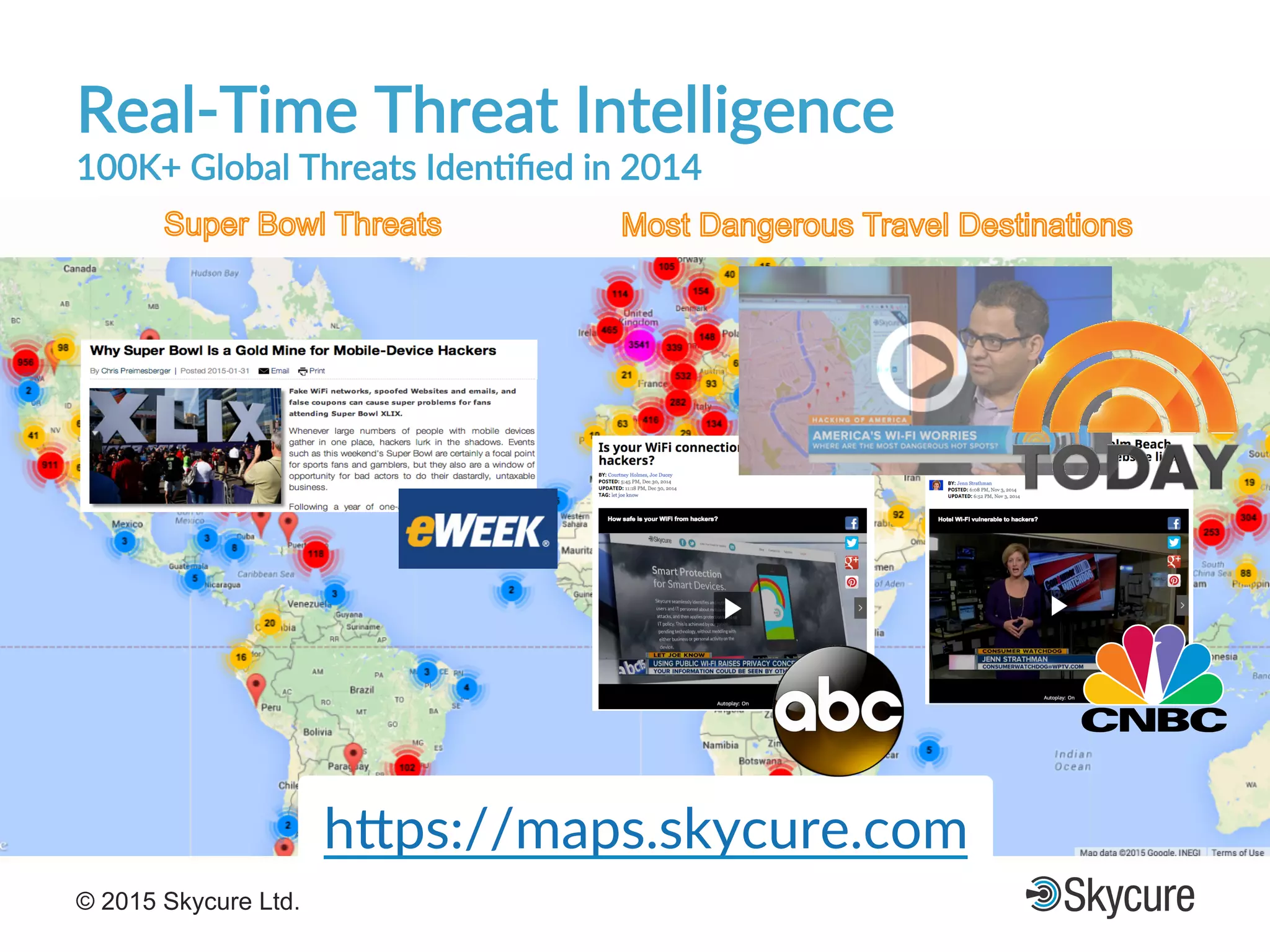
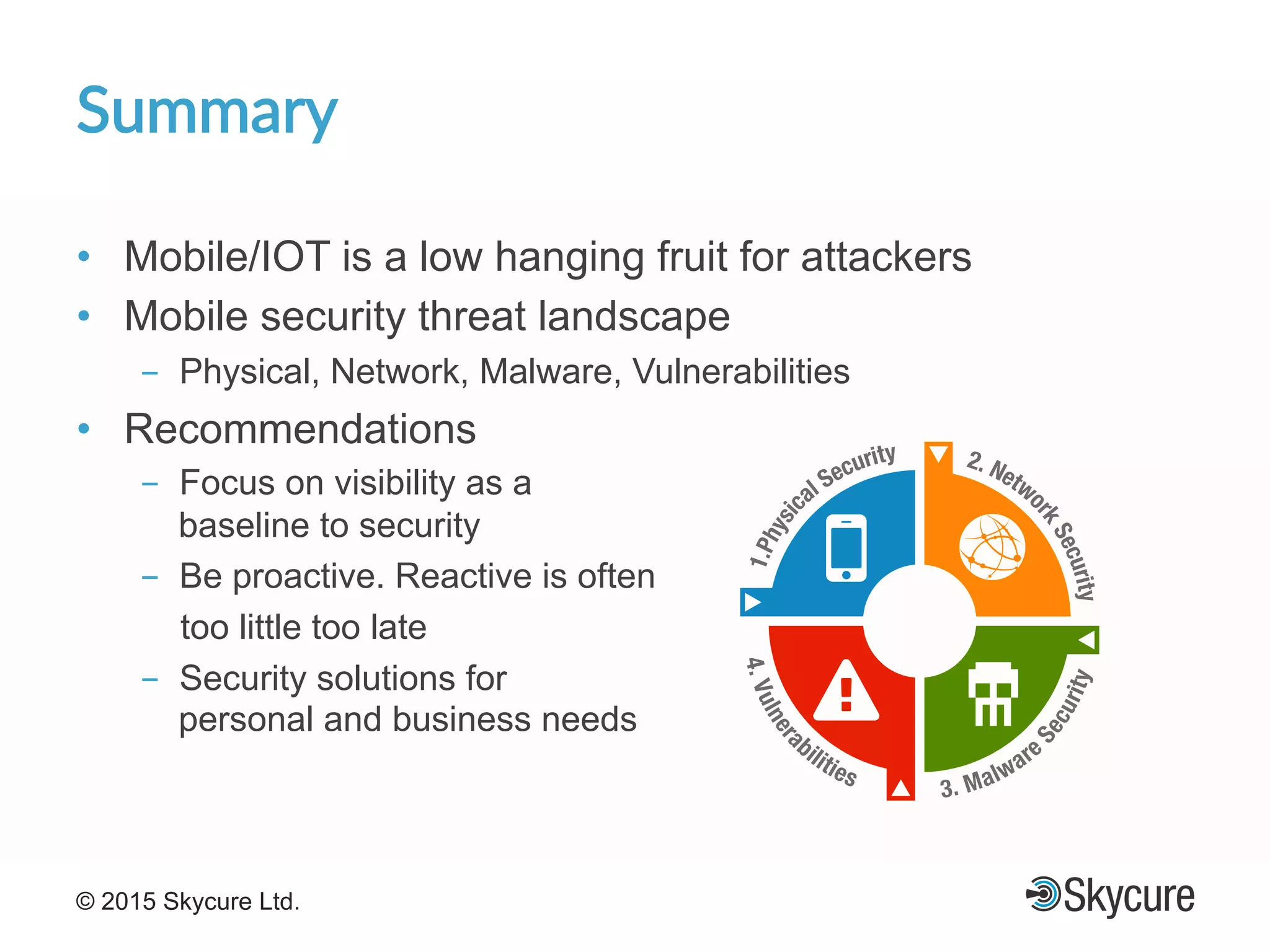
The presentation discusses the current state of mobile security and the ever-increasing complexity and risk posed by connected devices. It highlights the high volume of annual threats and offers actionable steps to enhance security, such as identifying assets, devising attack strategies, and prioritizing vulnerabilities. The summary emphasizes the need for proactive security measures to guard against the growing threat landscape in mobile and IoT environments.