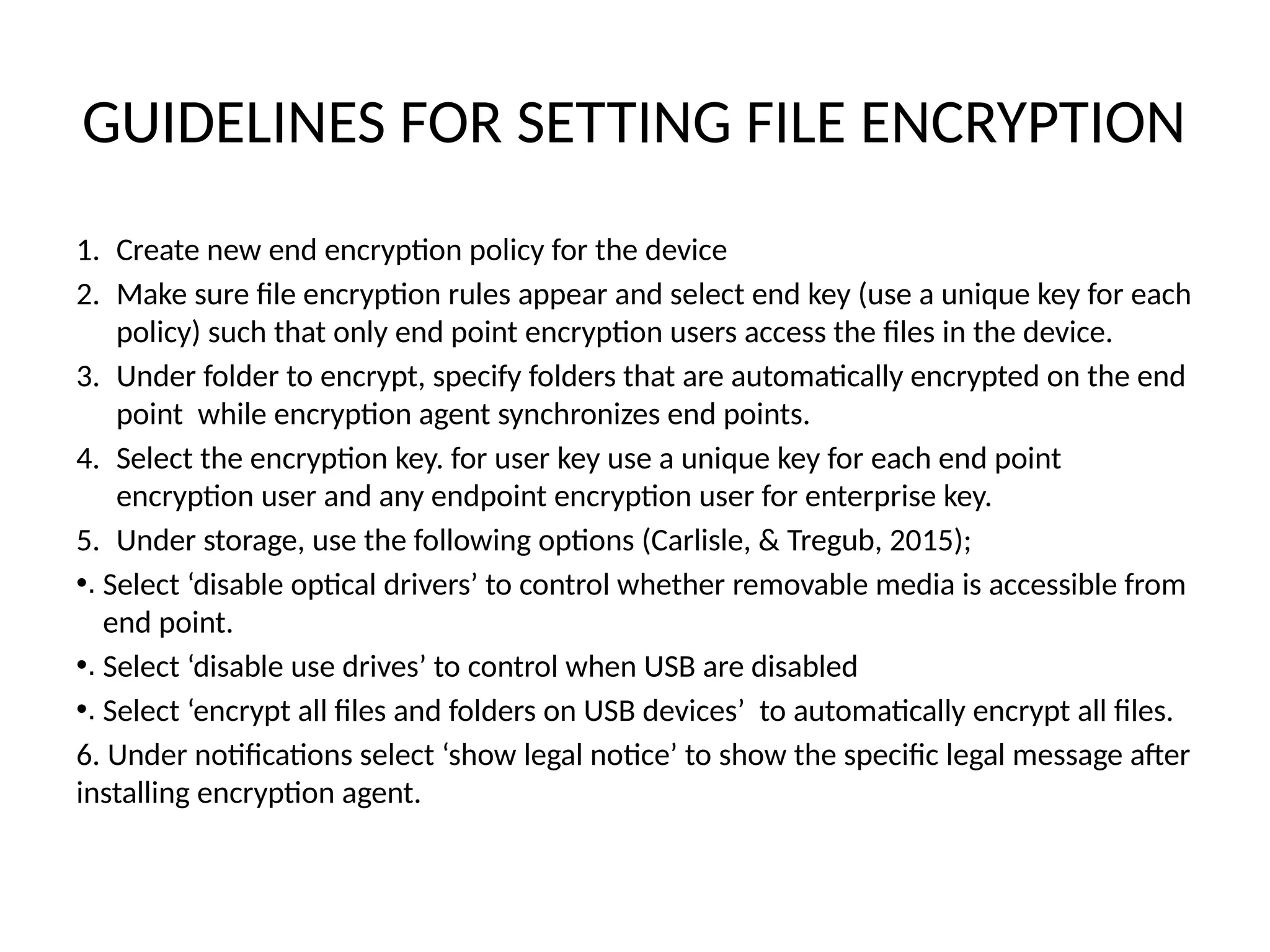
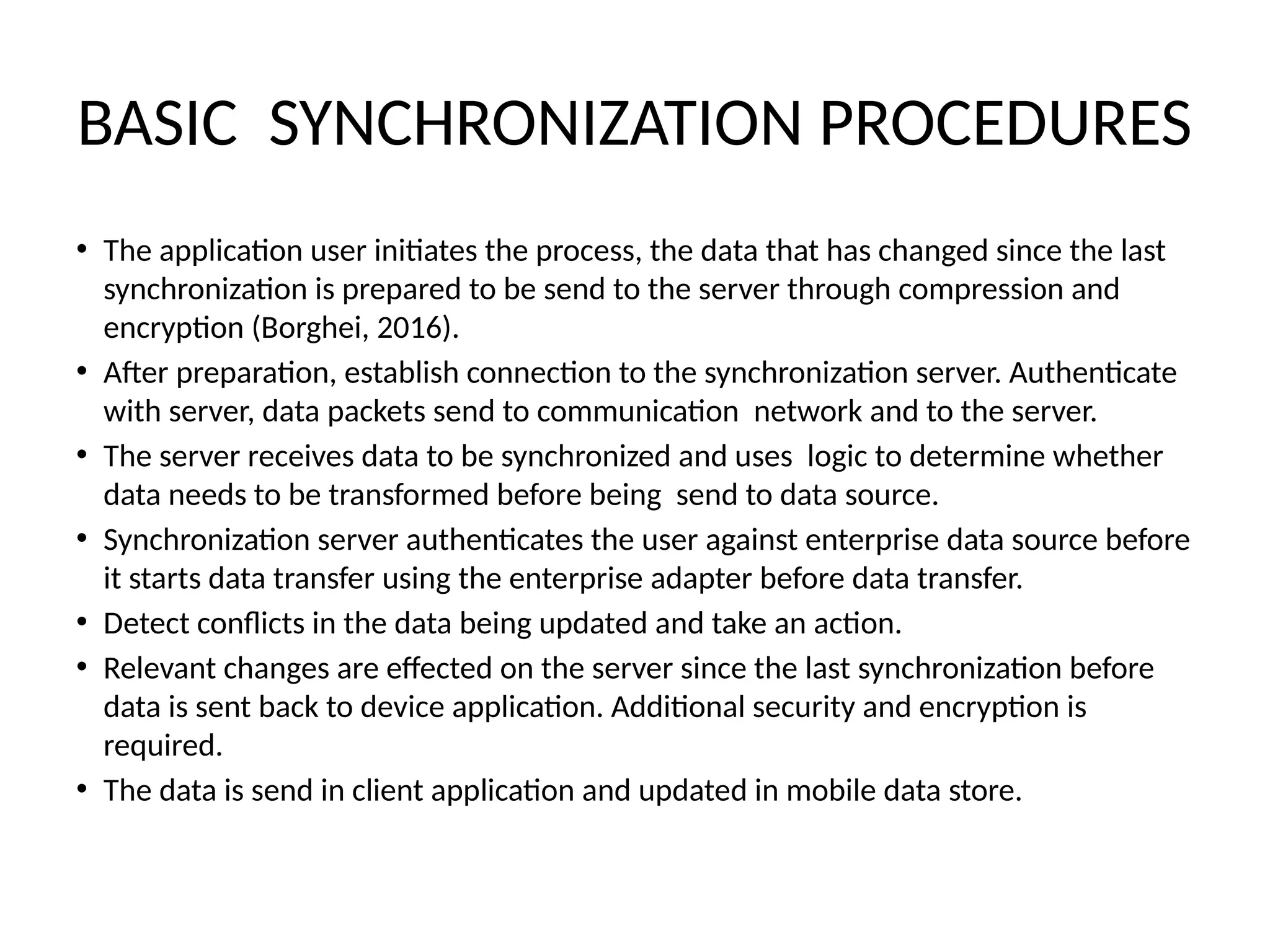
The document outlines mobile security guidelines for employees using personal and corporate-owned devices, emphasizing the need for both physical and digital security to protect corporate data. It provides practical steps such as using strong passwords, device encryption, and cautious use of public networks, as well as actions to take if a device is lost. Additionally, it describes protocols for data synchronization and compliance with organizational security standards.