This document provides instructions for modifying Android apps without source code through reverse engineering the APK file. It details the steps to:
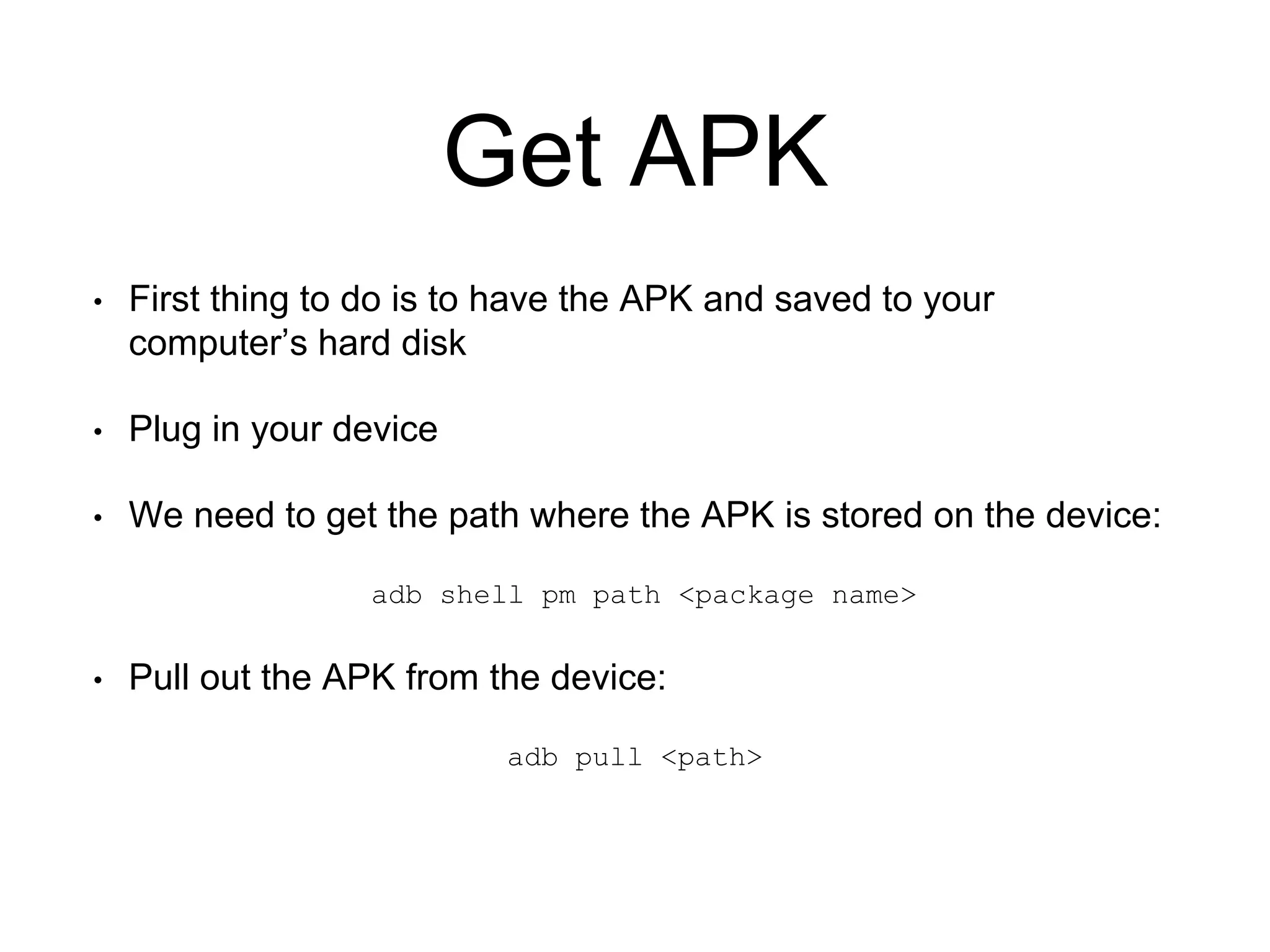
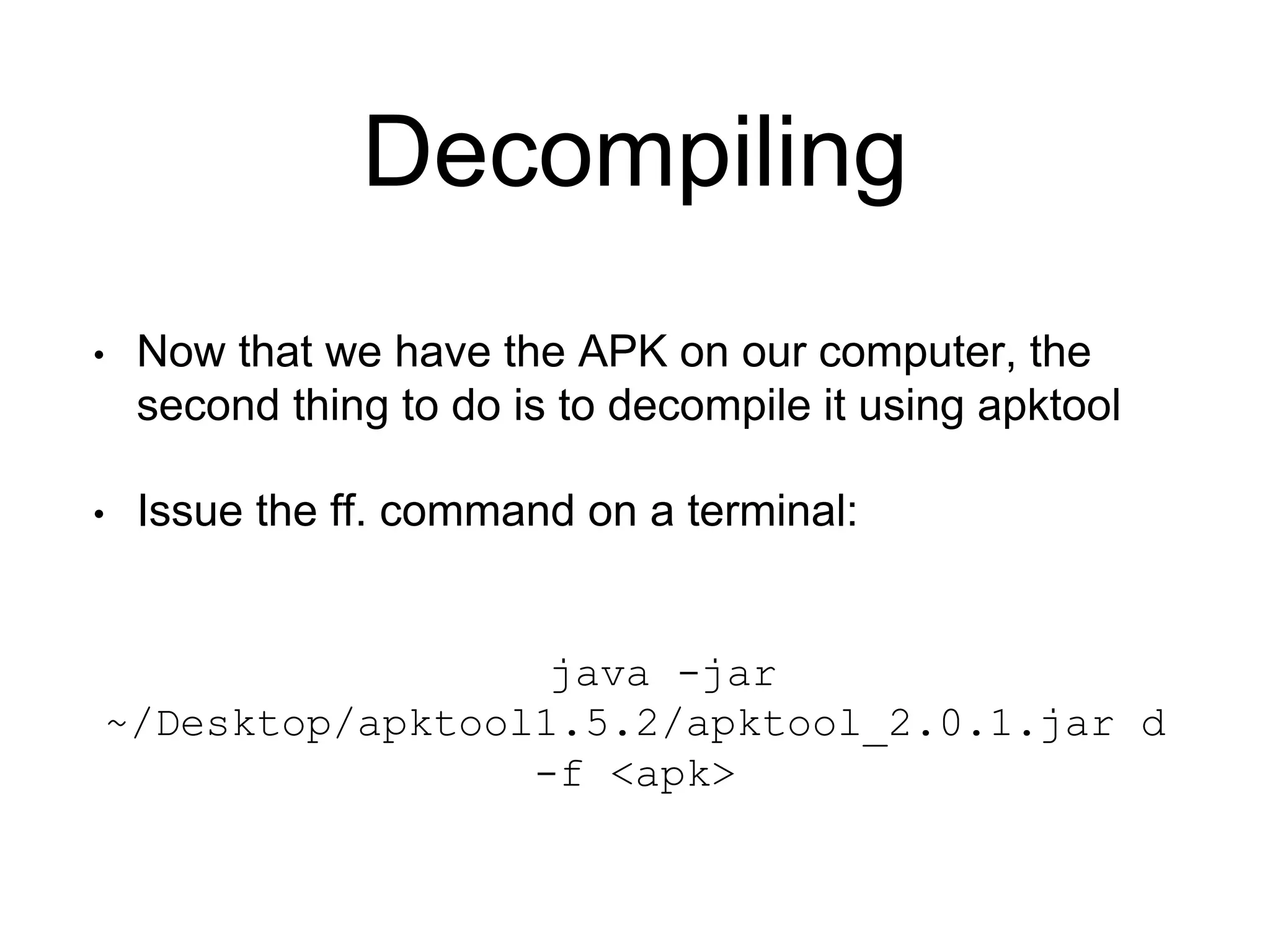
1. Decompile the APK file using Apktool to convert it to a readable format.
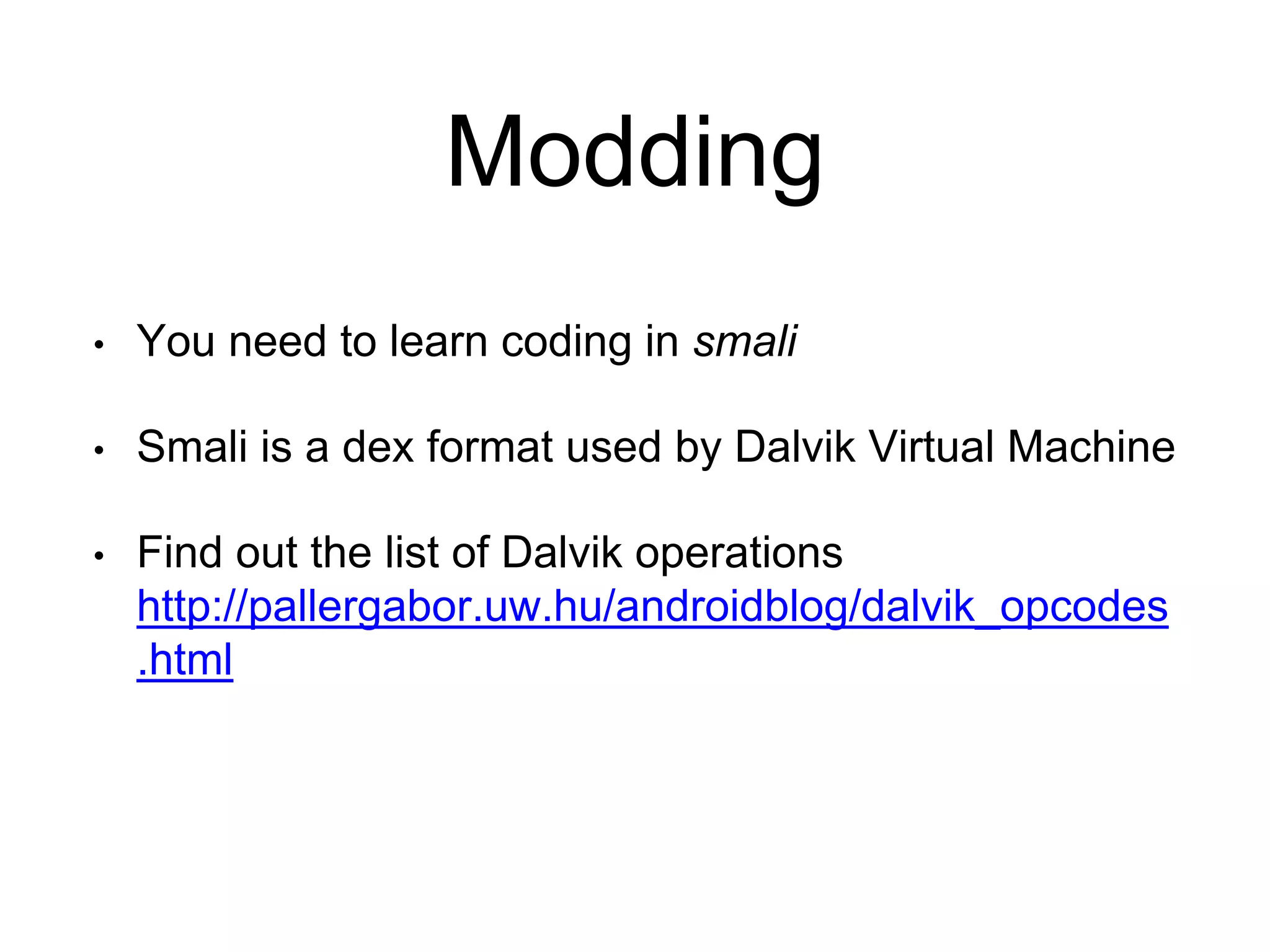
2. Modify the decompiled source code written in Smali, the dex format used by Android.
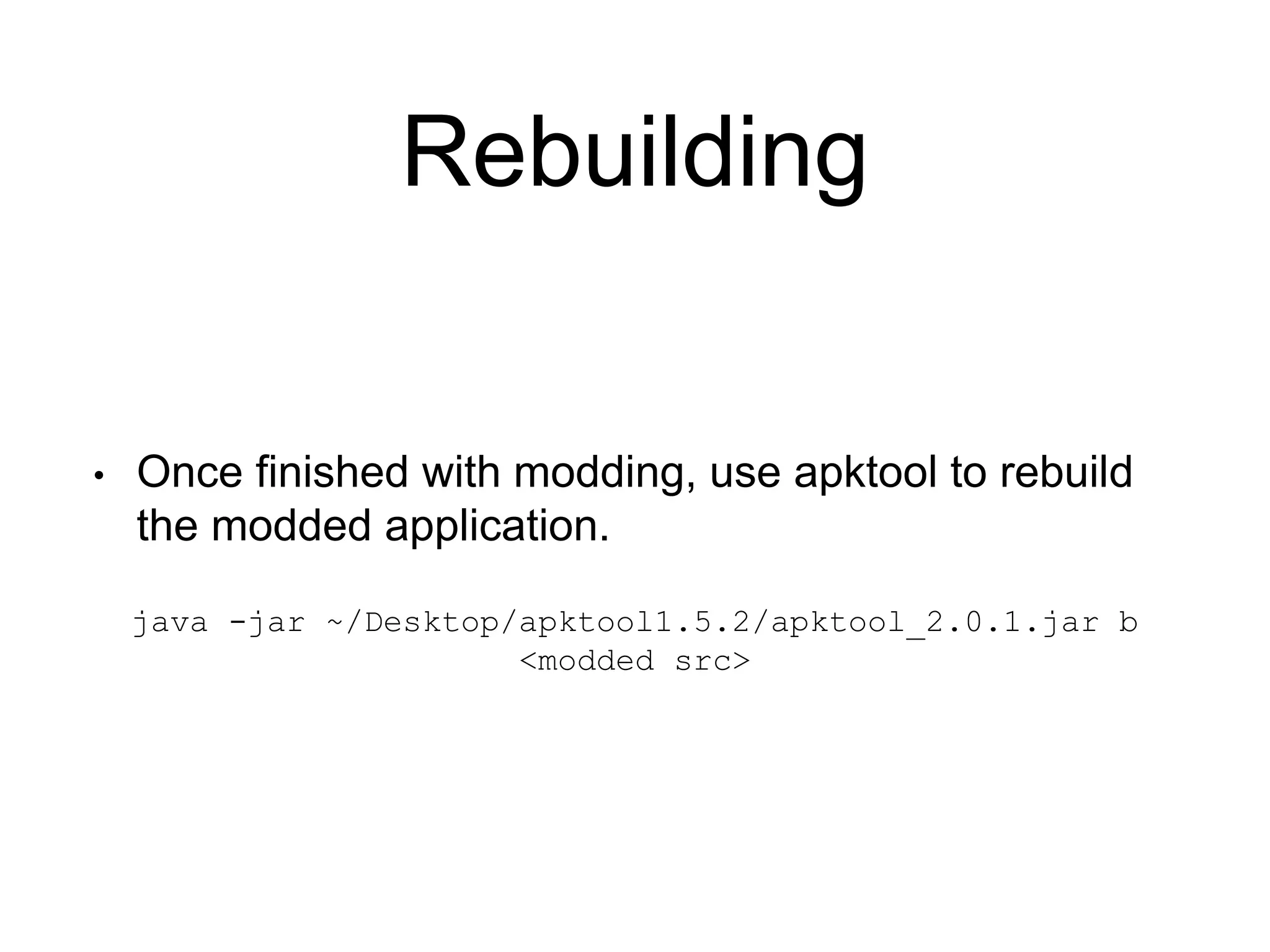
3. Rebuild the modified APK file using Apktool.
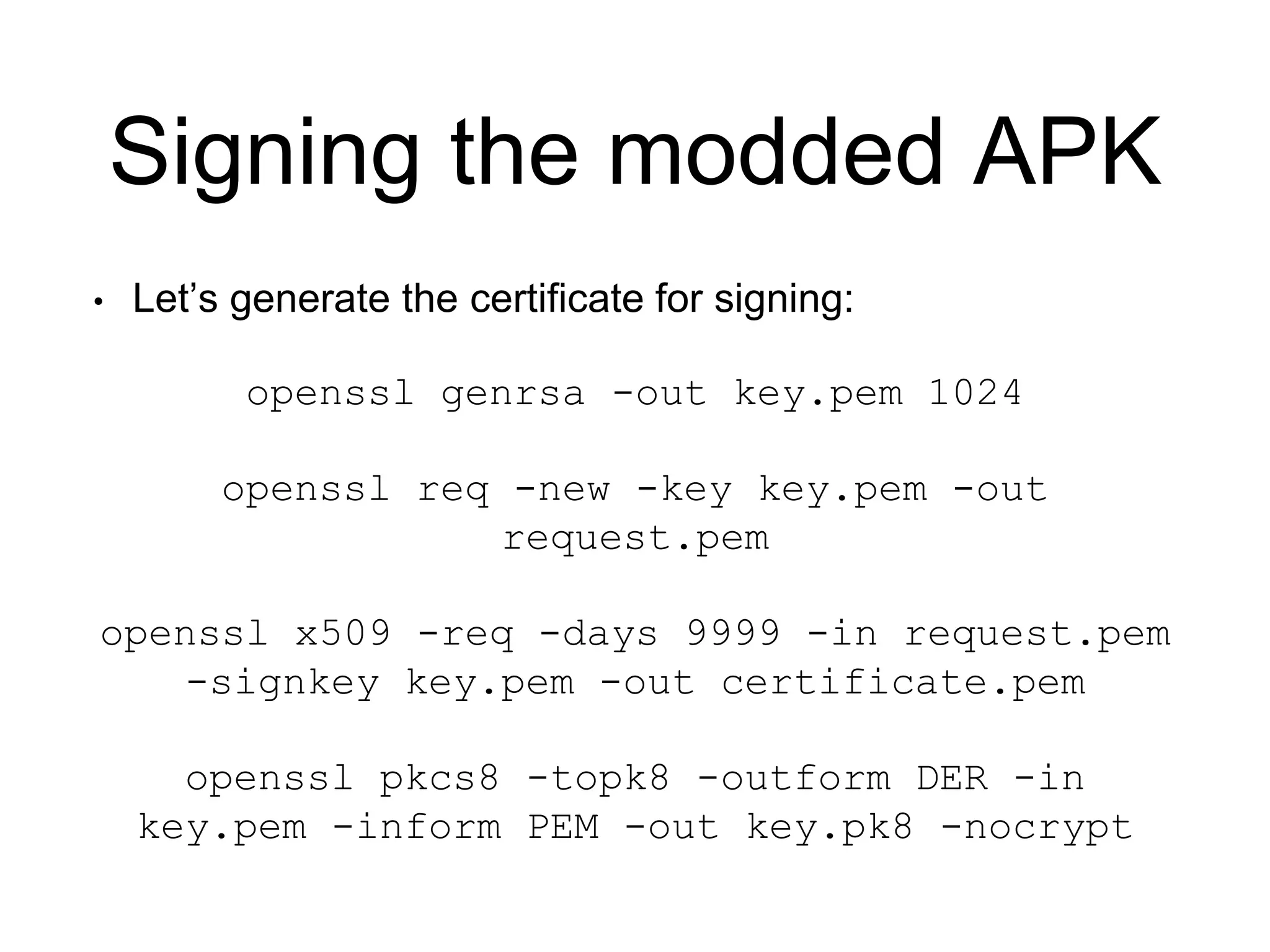
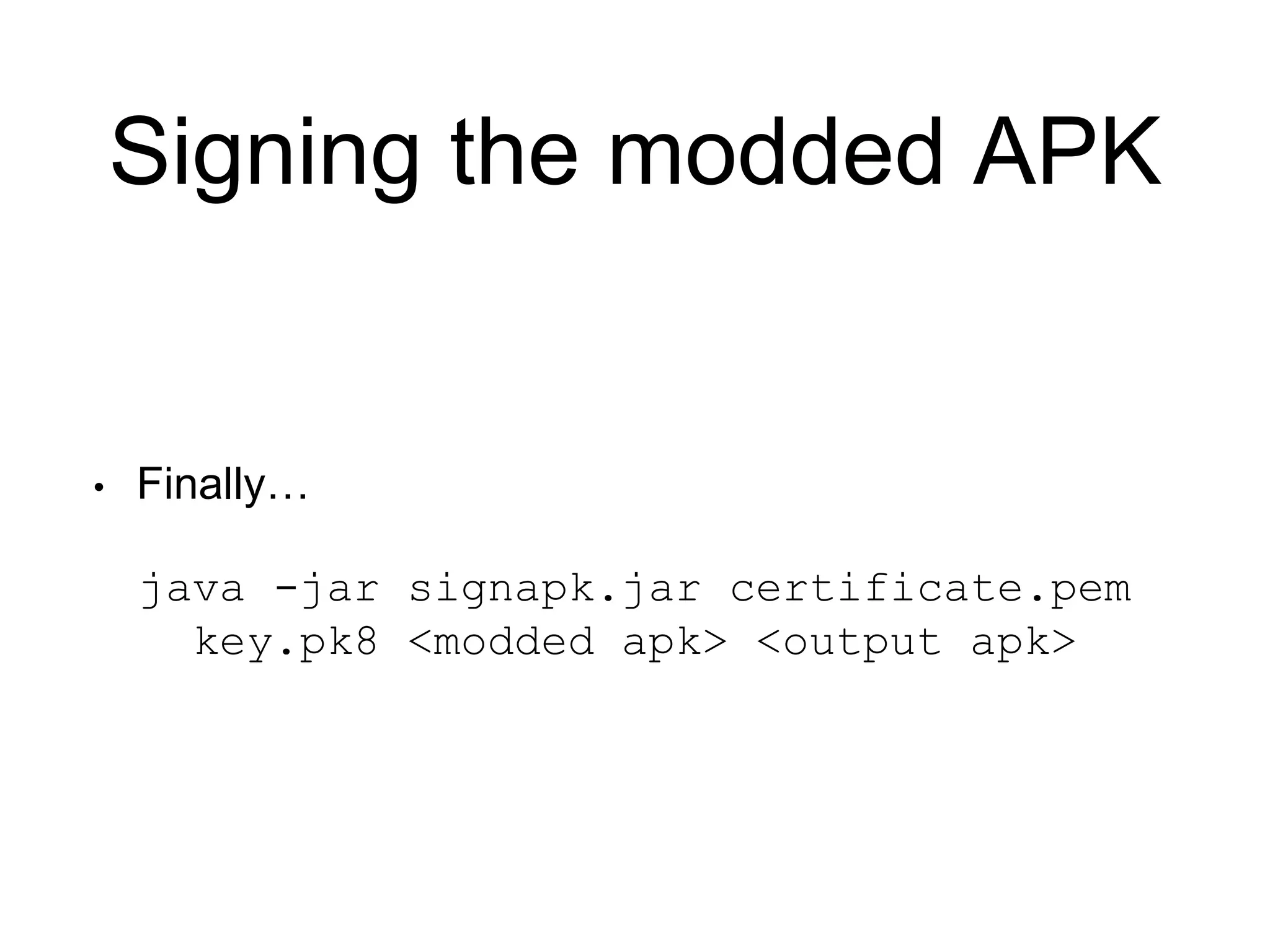
4. Sign the rebuilt APK with a generated certificate to allow it to run on devices.
Common injected code examples like adding a popup message or method profiling calls are also provided.

![Requirements
• Java SDK
[http://www.oracle.com/technetwork/java/javase/downloads/index
.html]
• Android SDK [http://developer.android.com/sdk/index.html]
• Apktool [https://bitbucket.org/iBotPeaches/apktool/downloads]
• SignApk [http://forum.xda-
developers.com/attachment.php?s=ed93891ef99dc601482f8c9b
196c8c4f&attachmentid=1846095&d=1364661948]
• Android Studio (Optional)
• OpenSSL](https://image.slidesharecdn.com/hackingandroid-151209071225-lva1-app6891/75/Modifying-Android-Apps-Without-Source-Codes-2-2048.jpg)