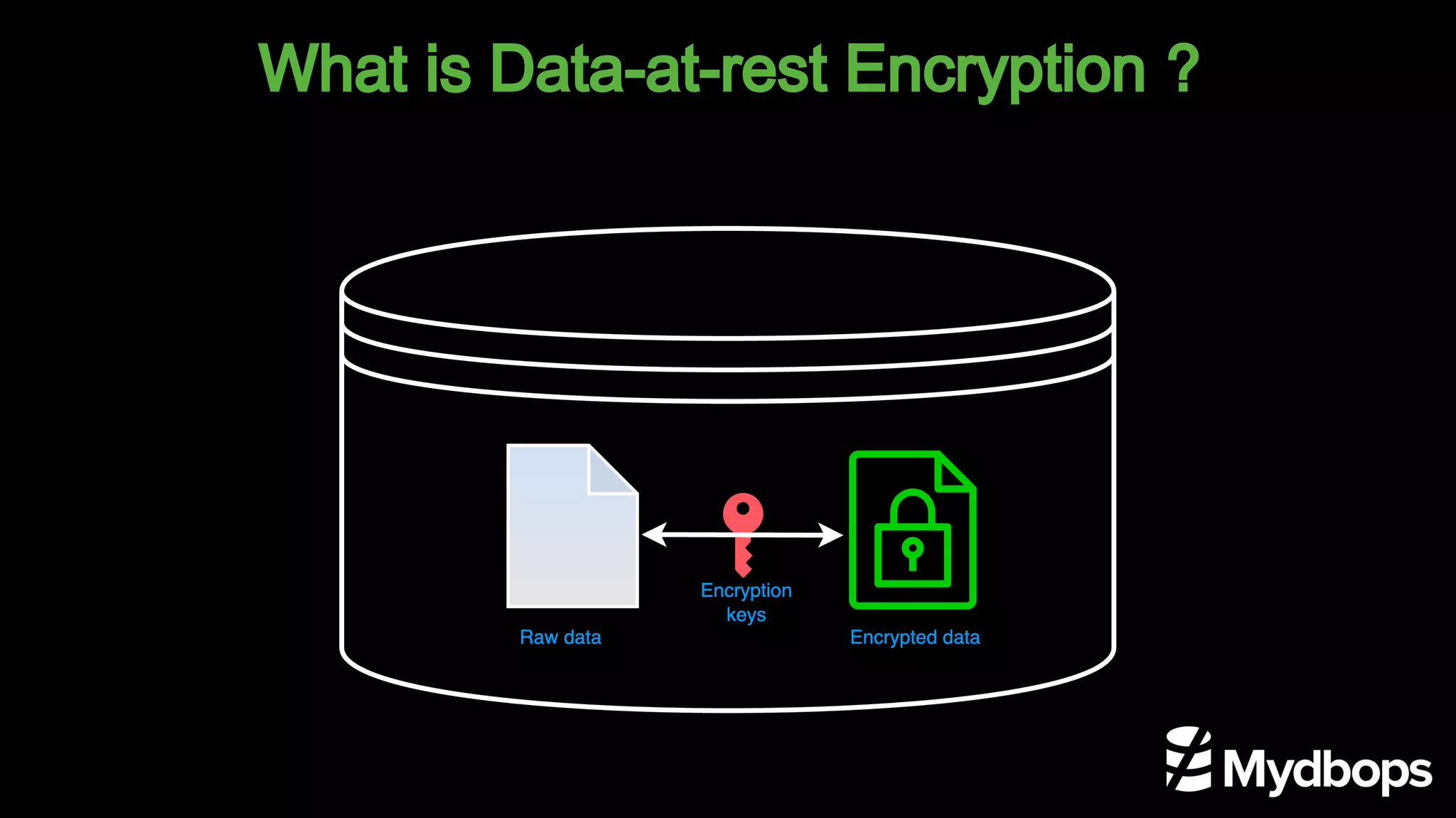
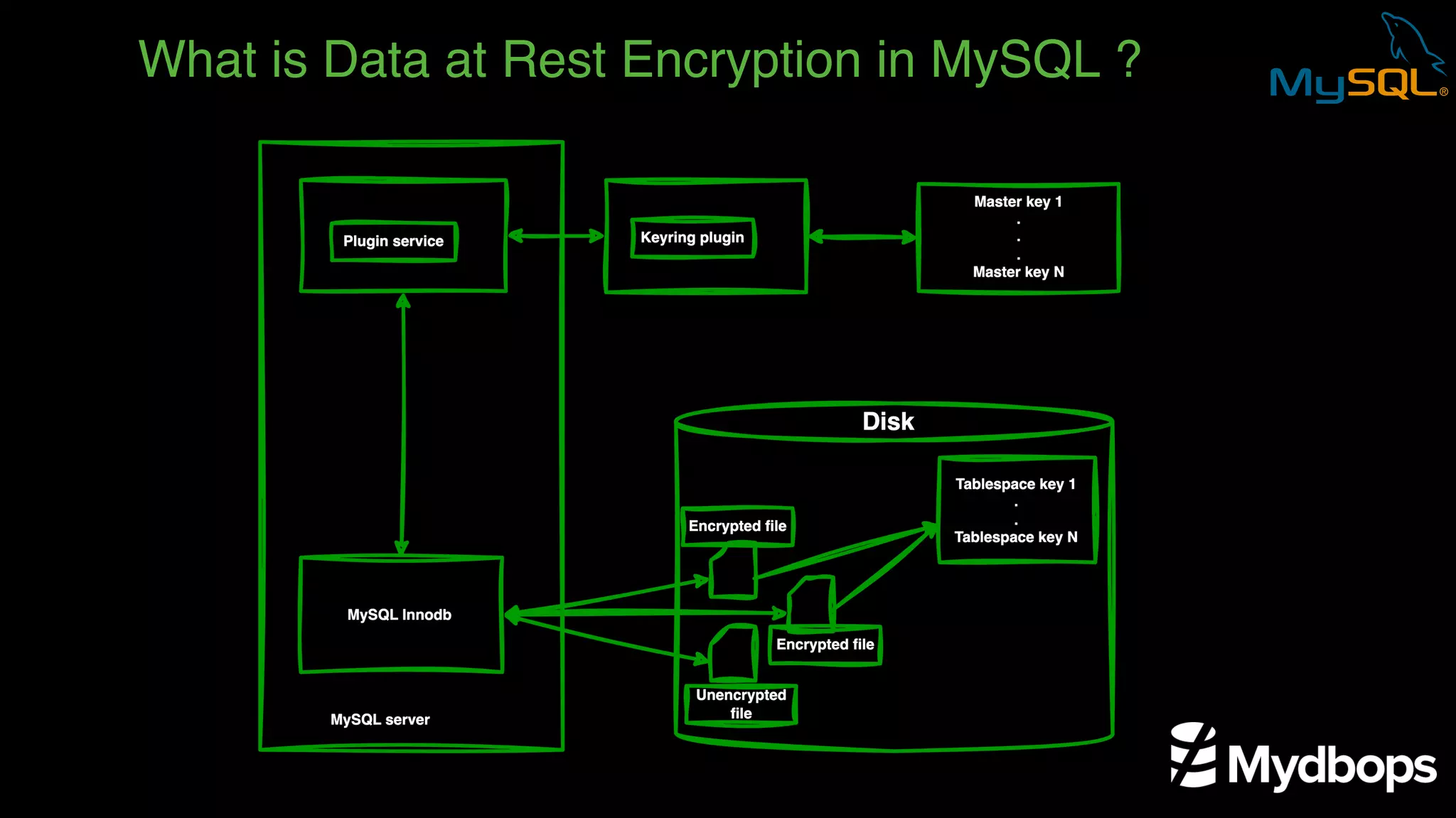
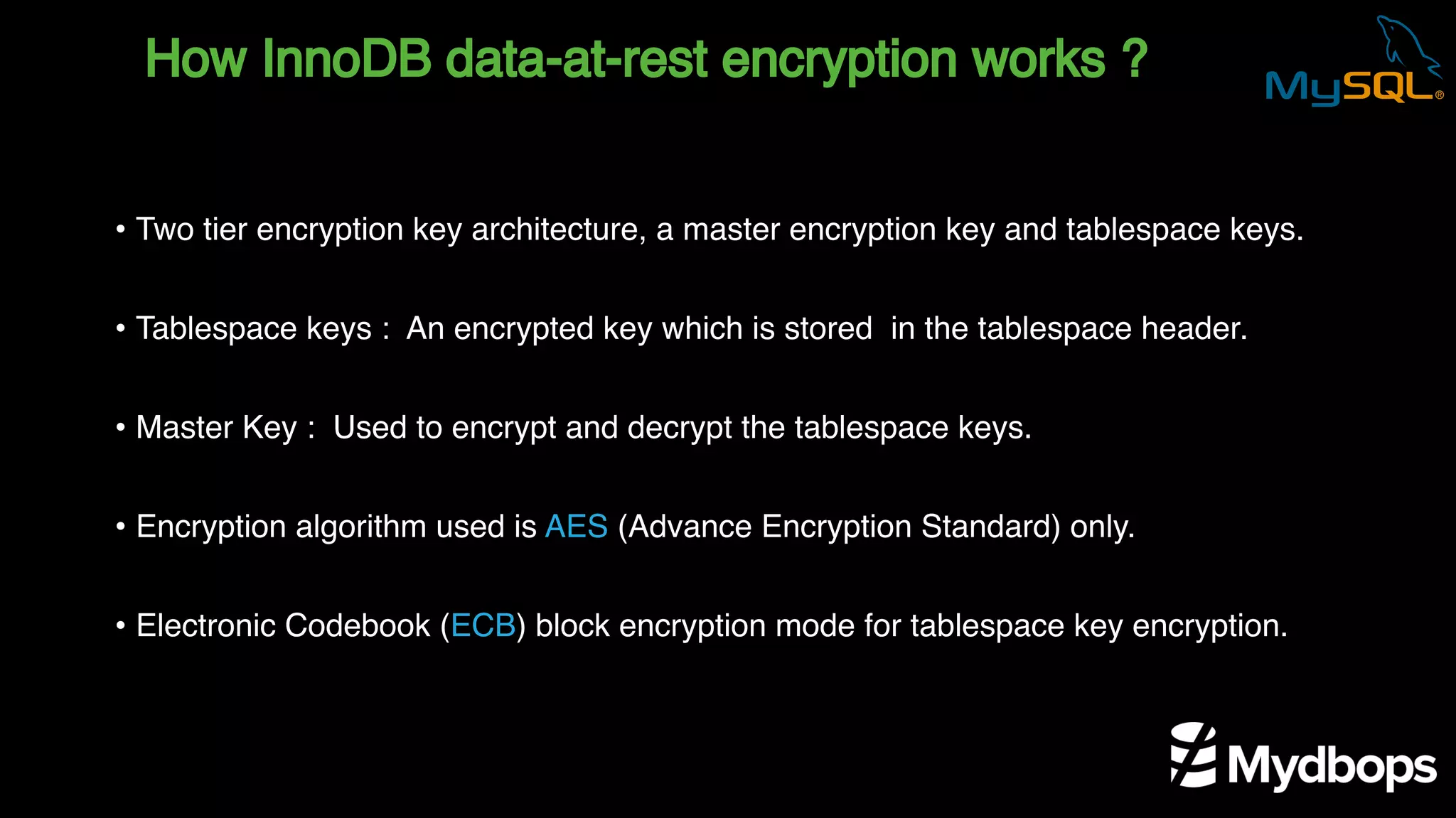
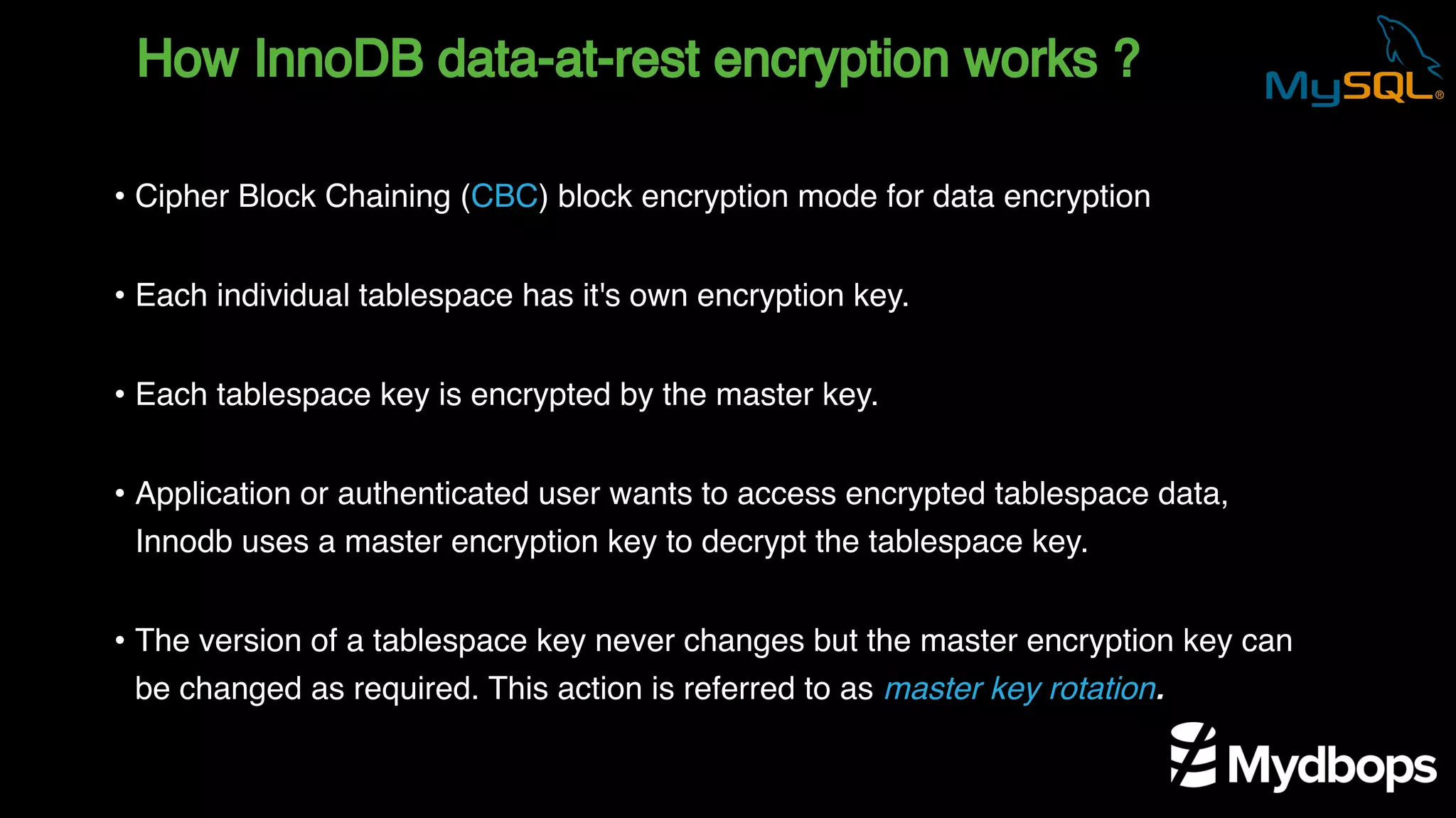
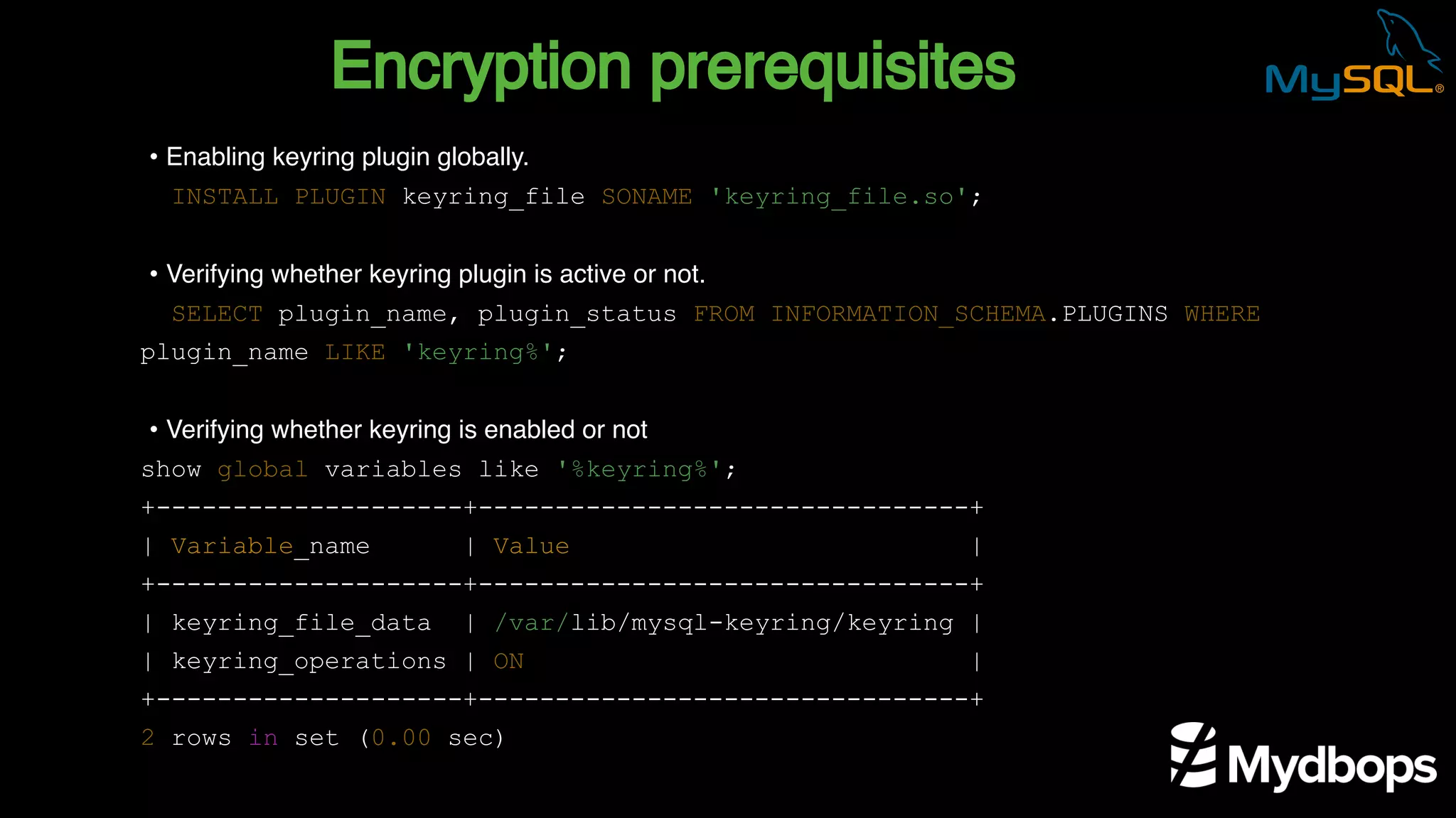
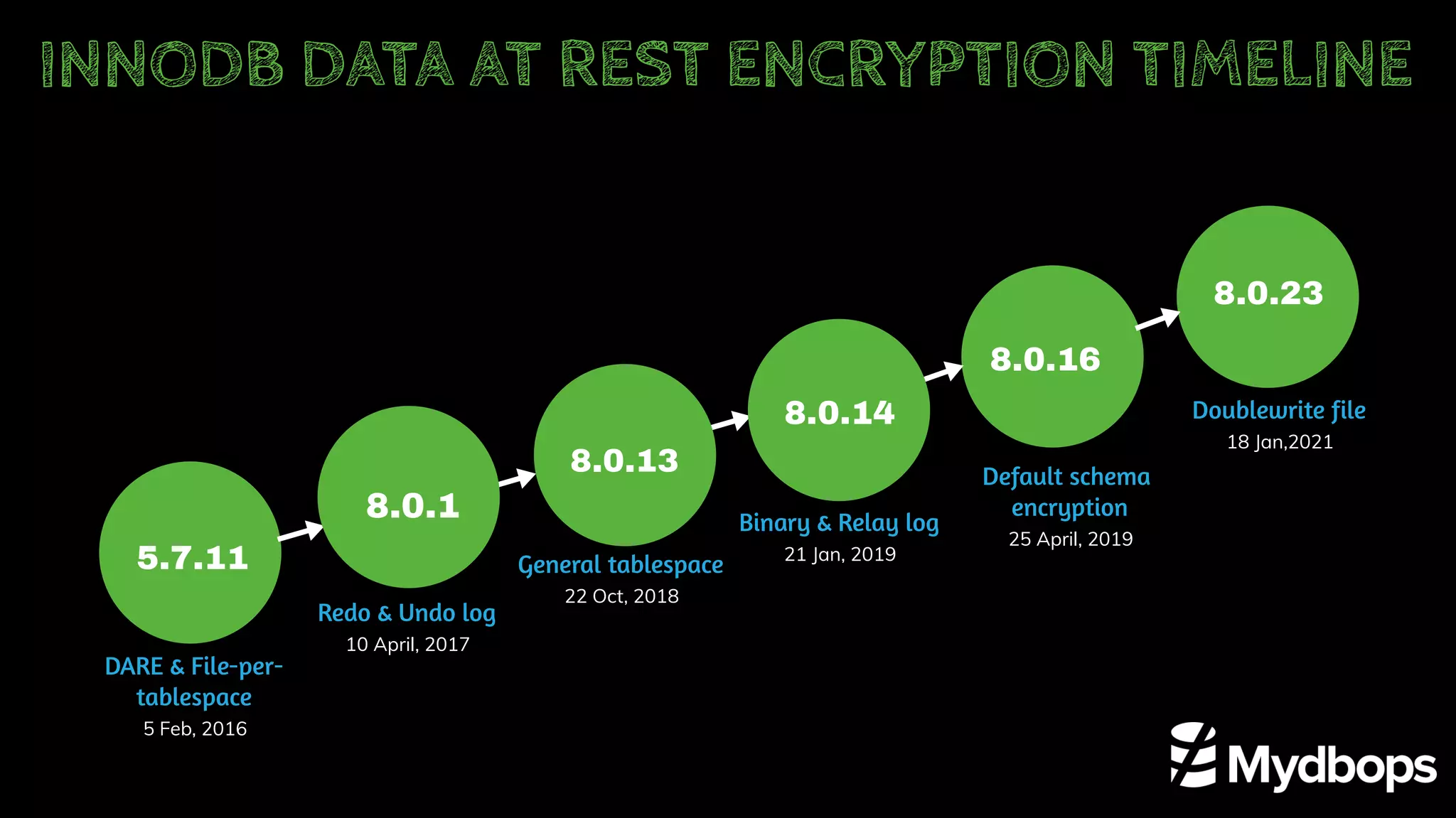
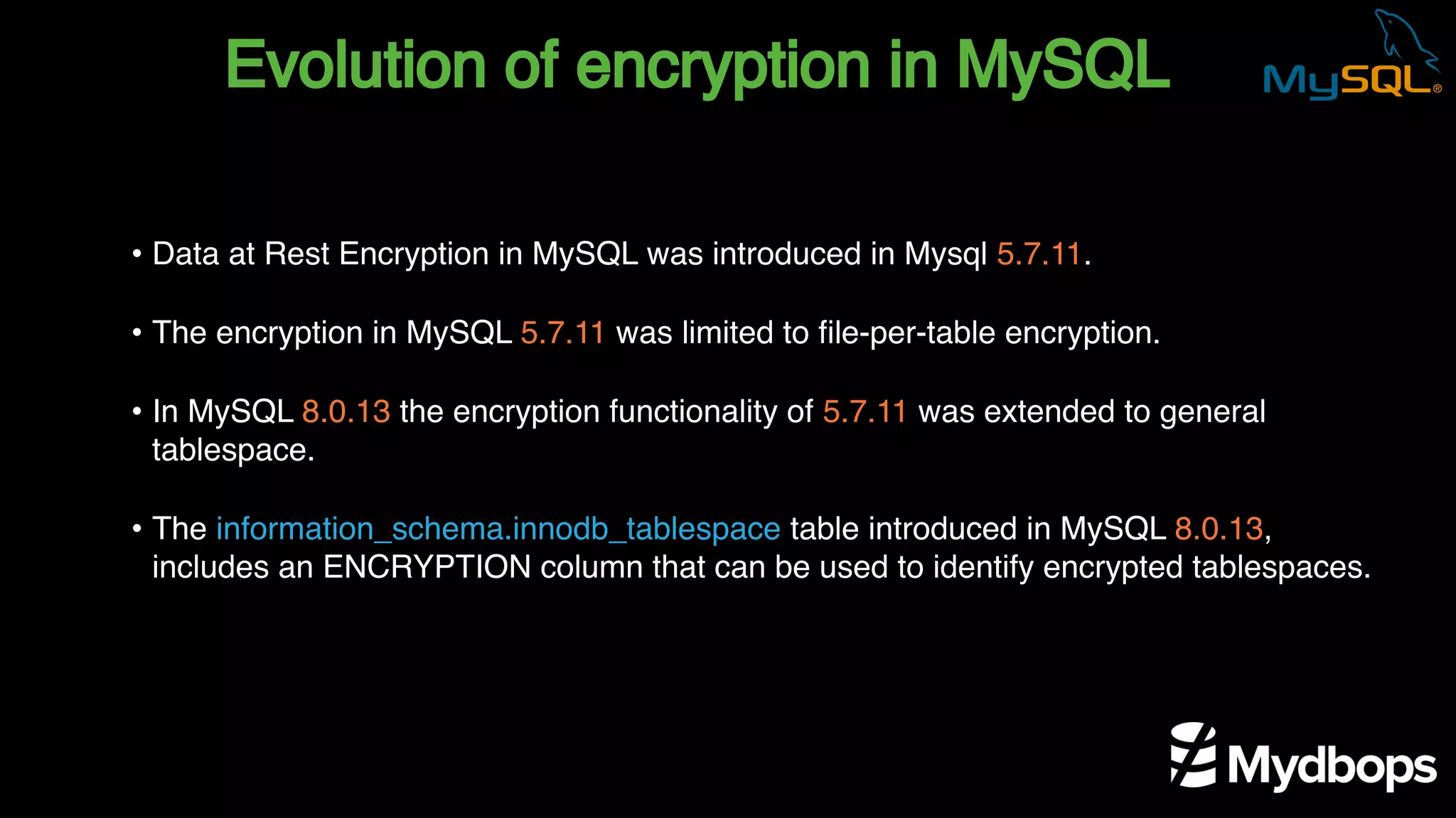
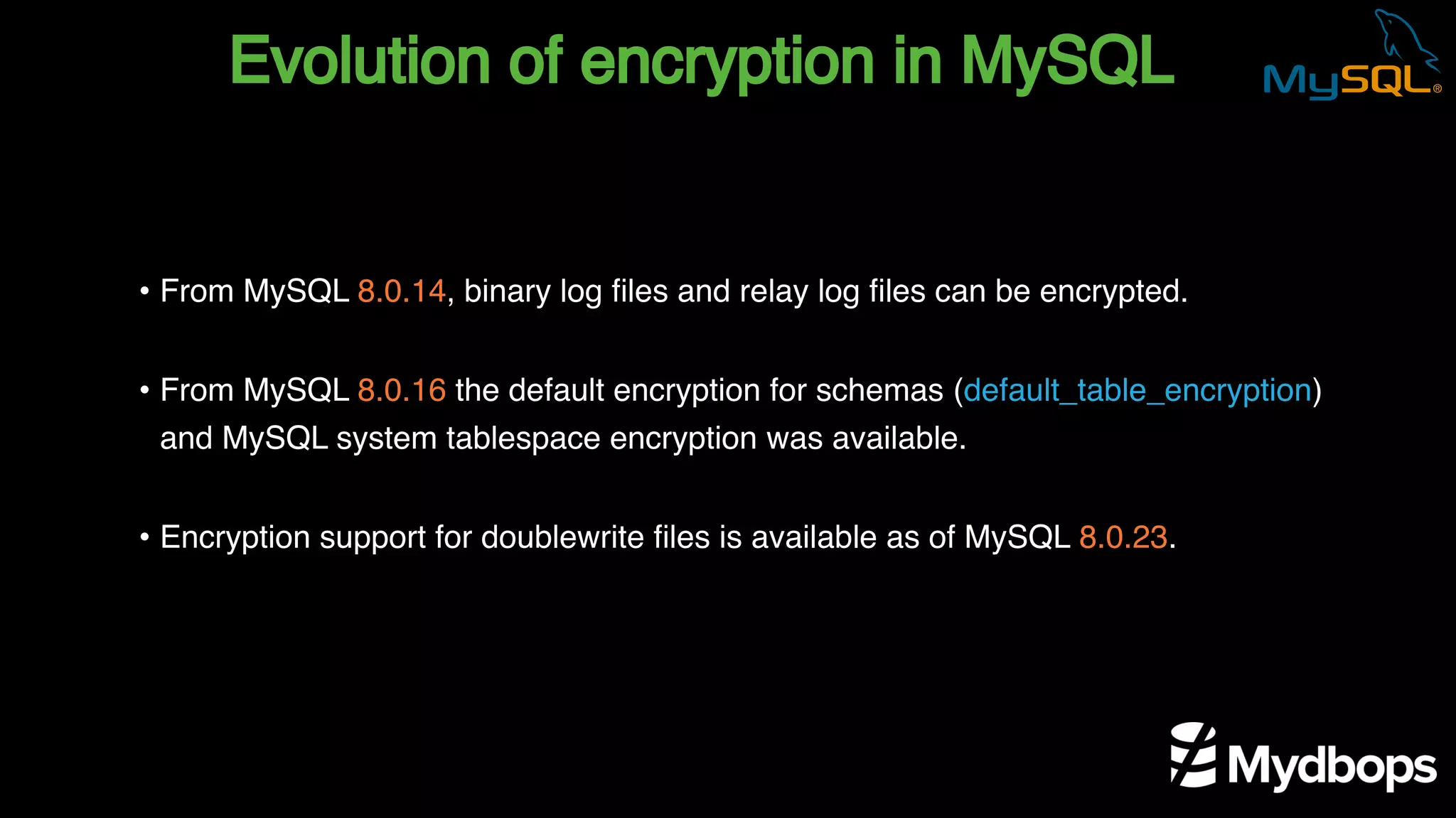
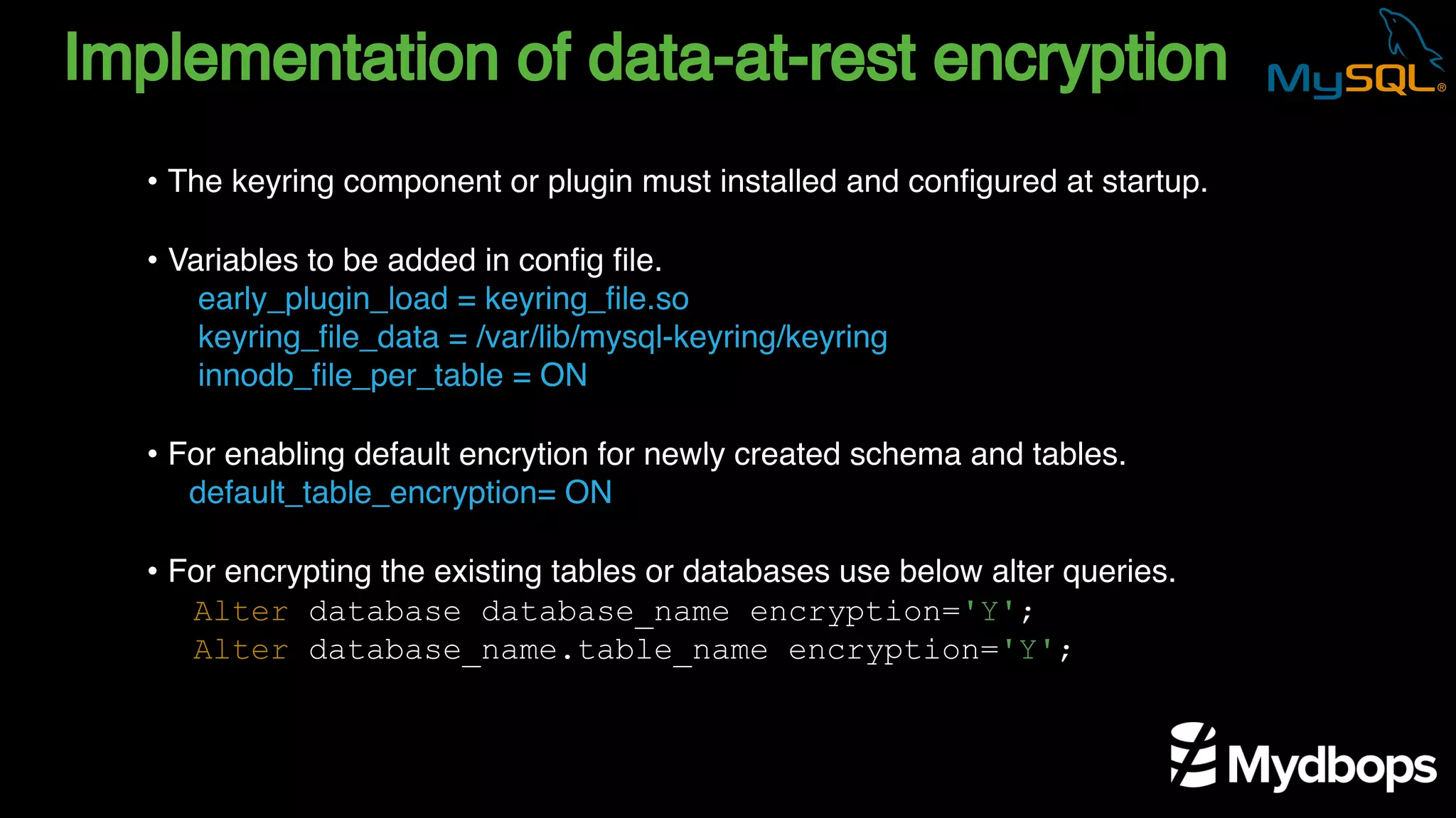
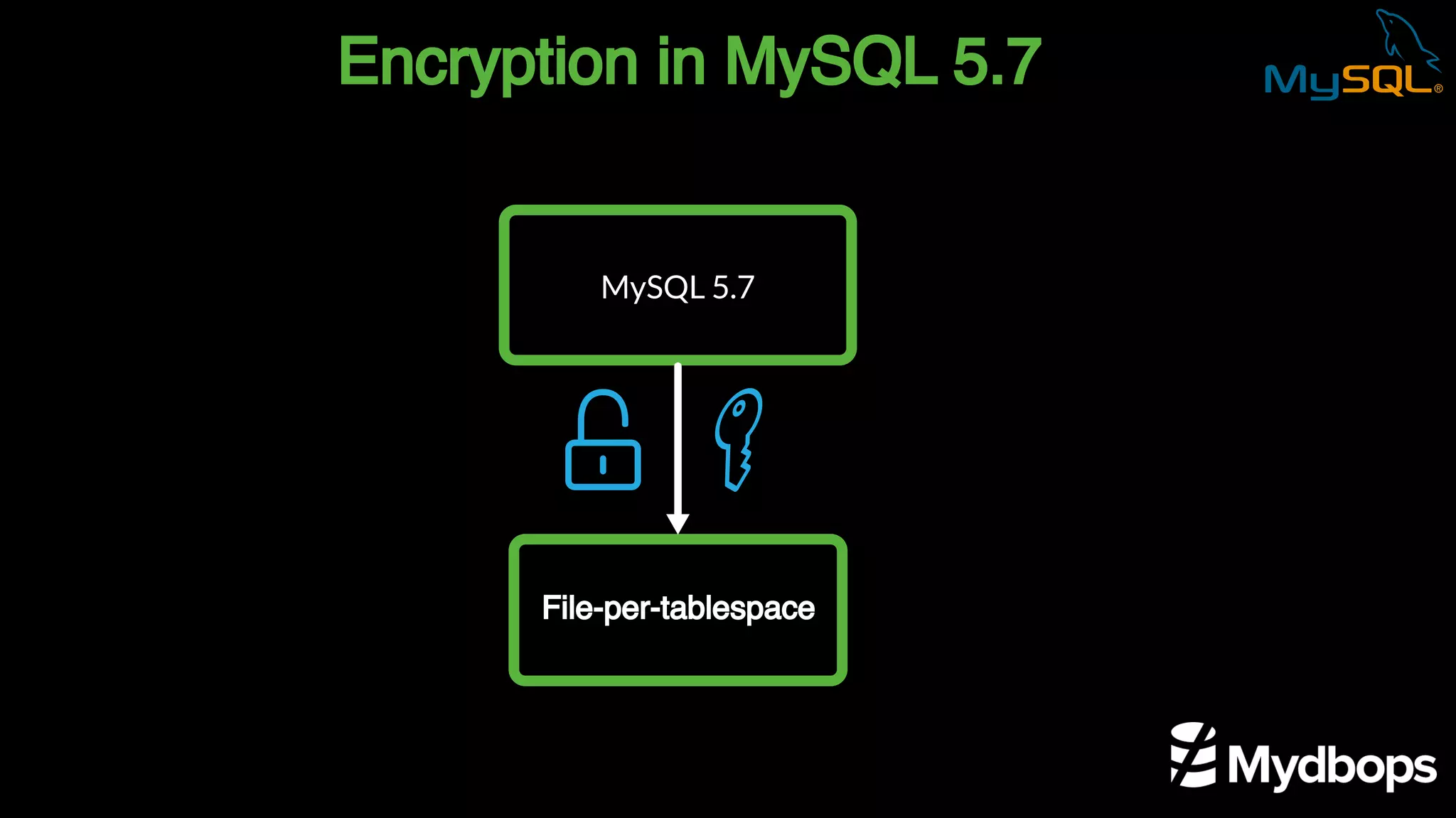
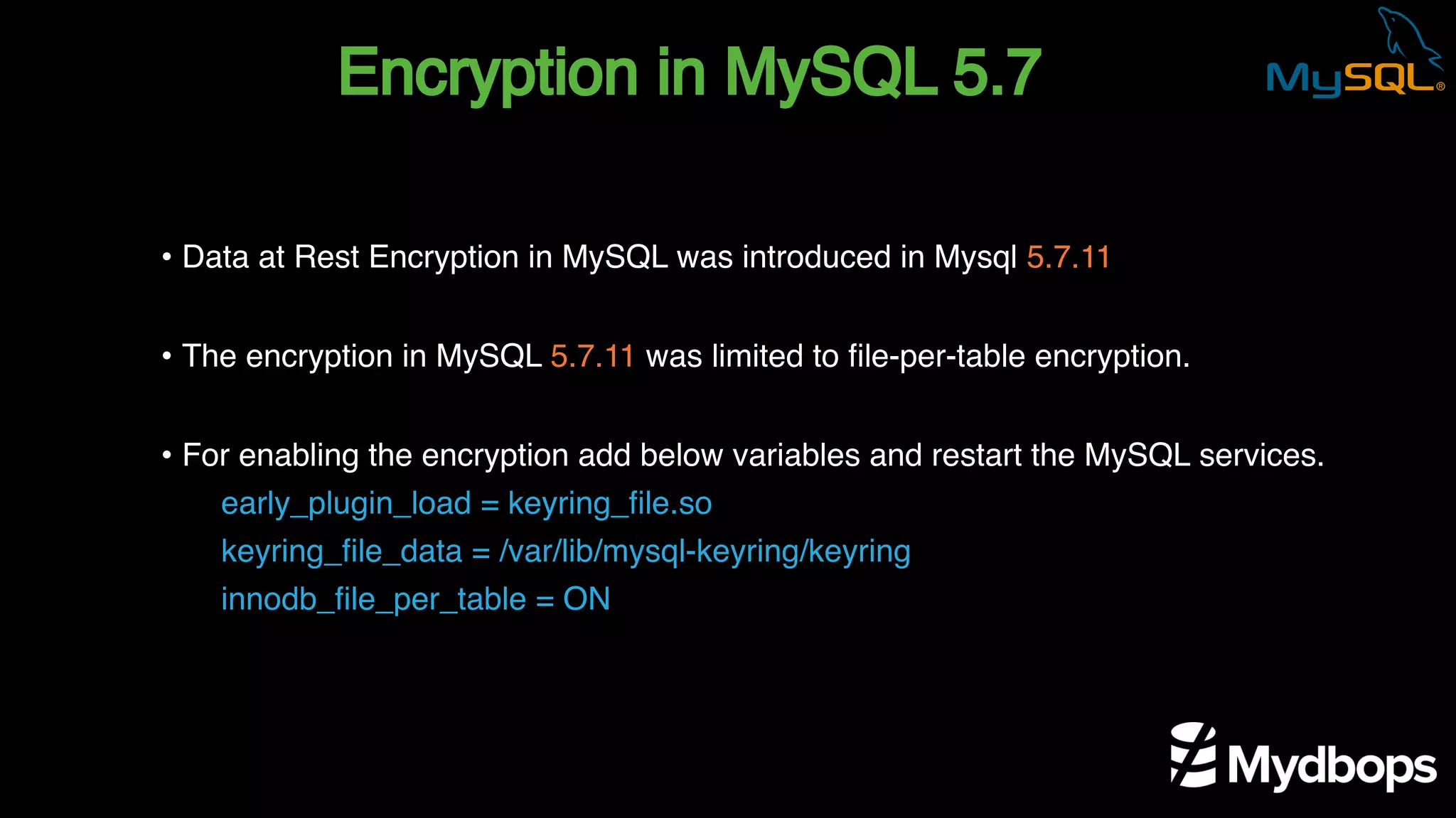
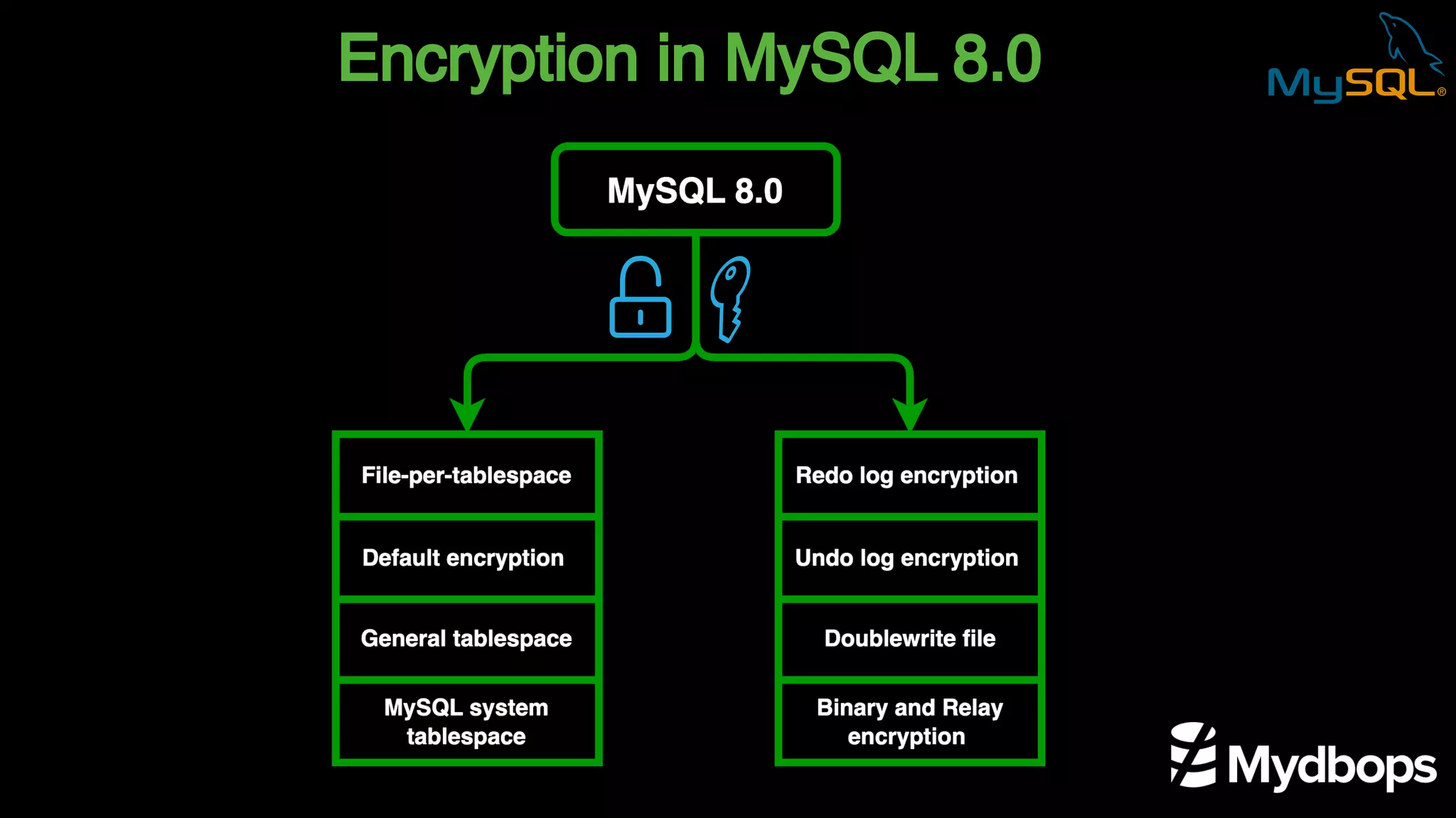
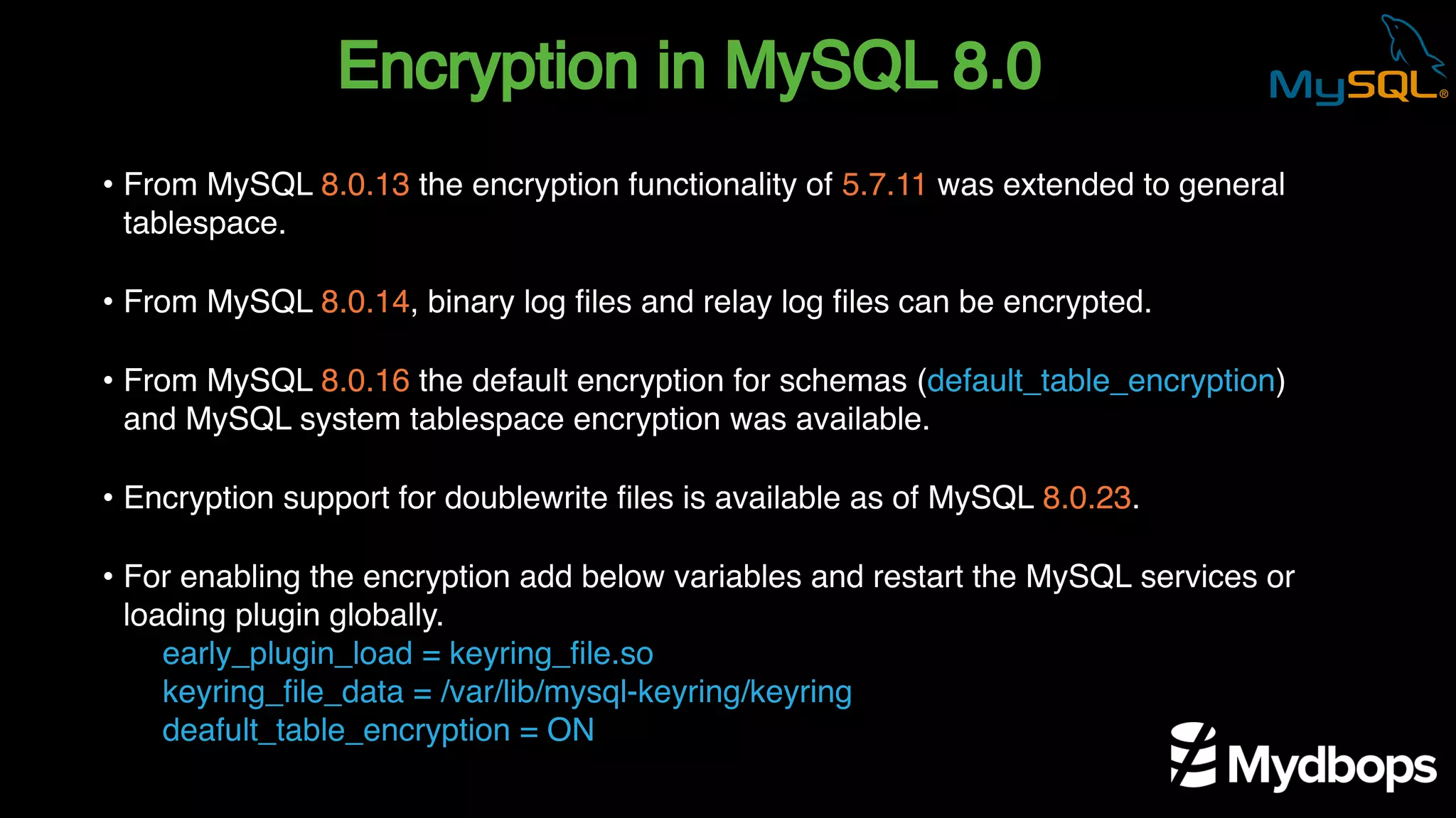
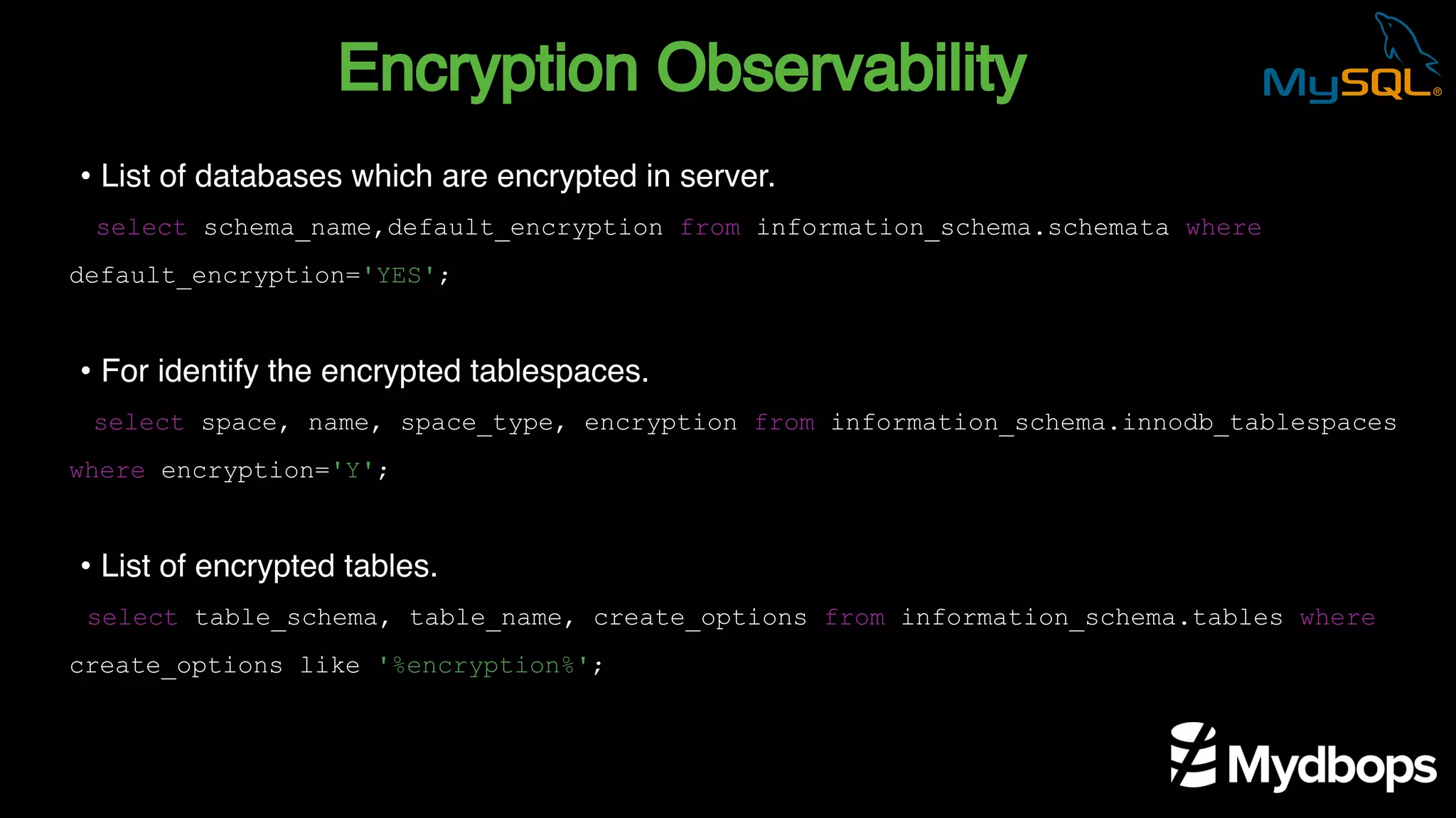
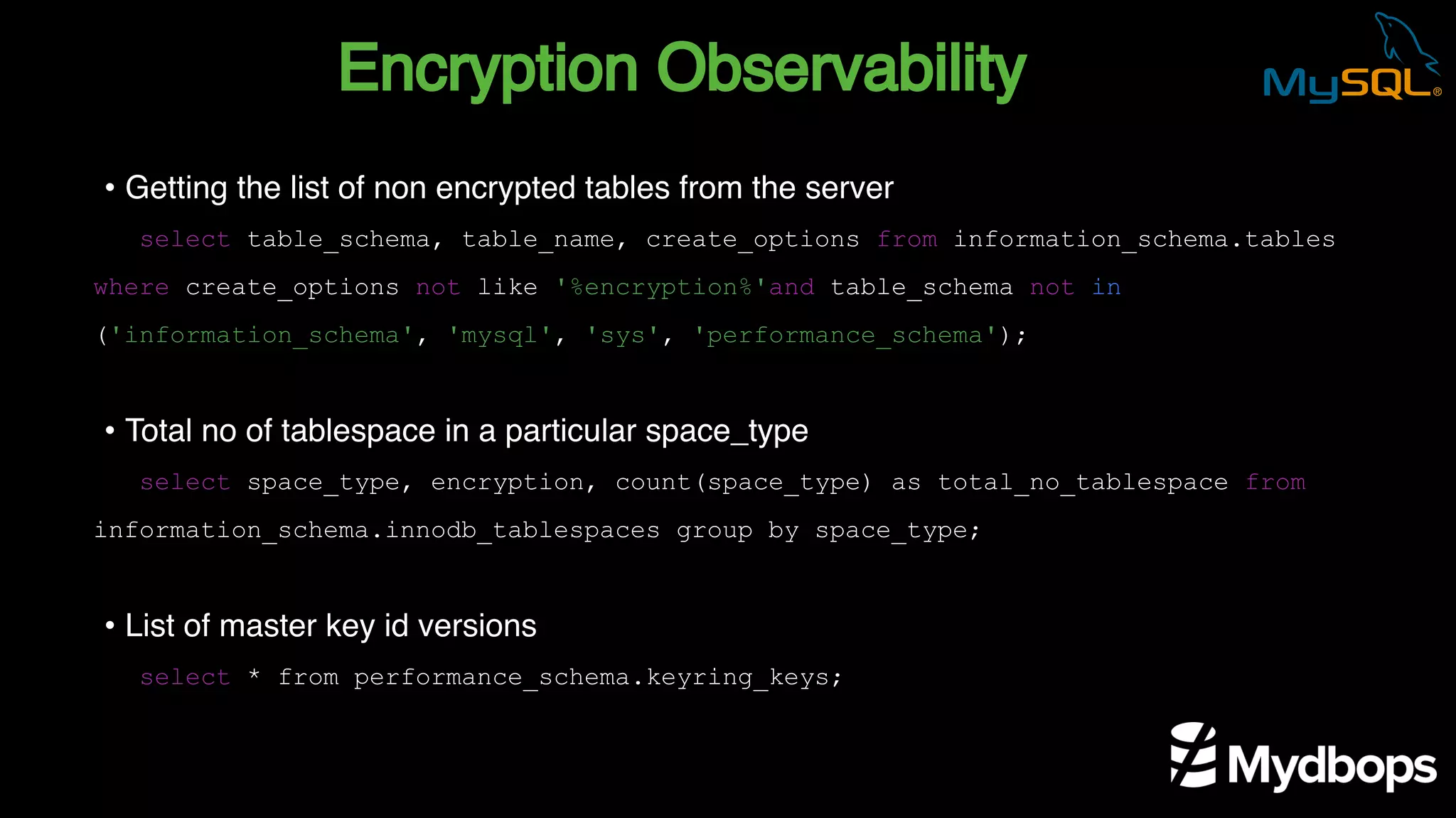
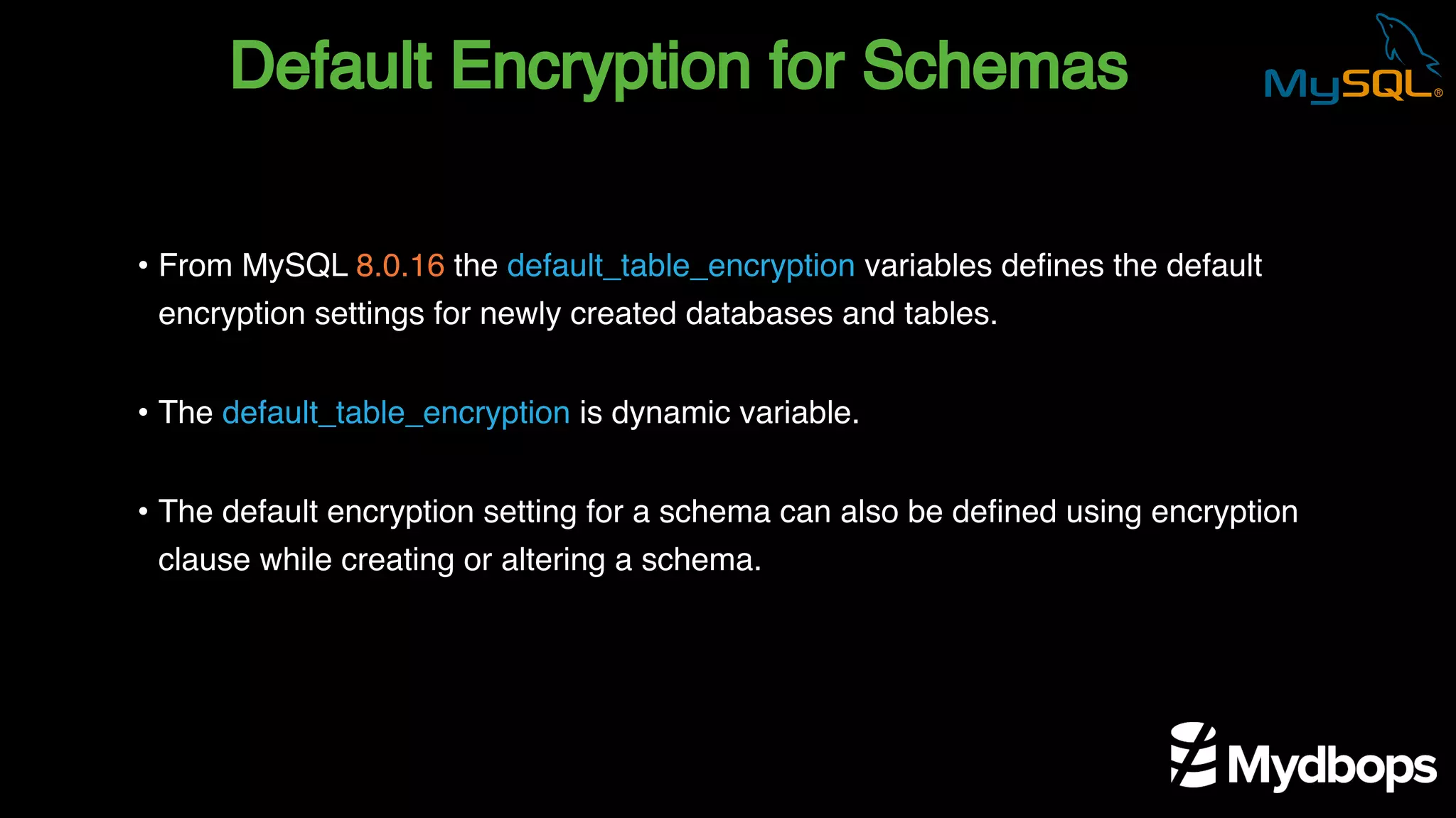
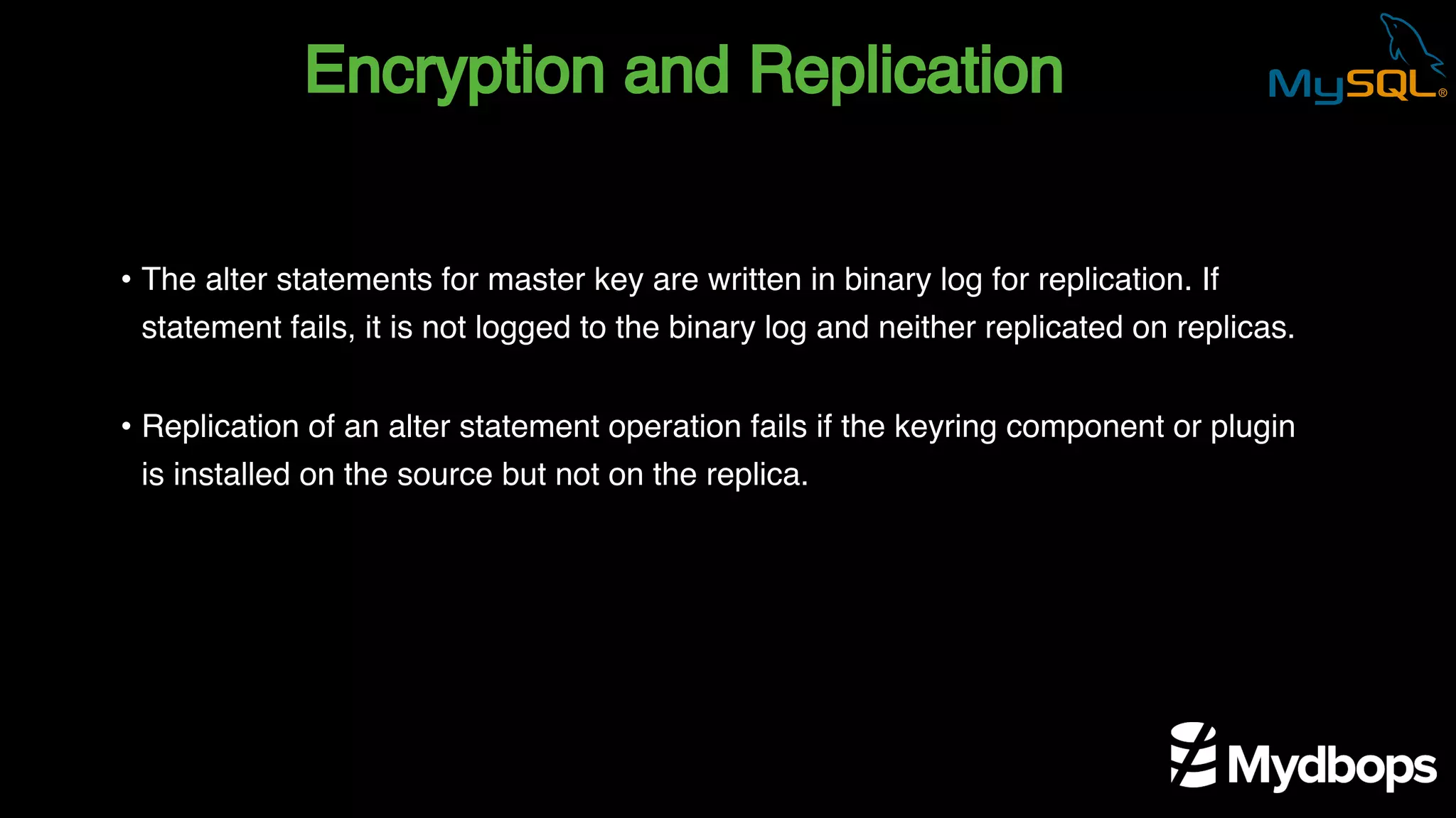
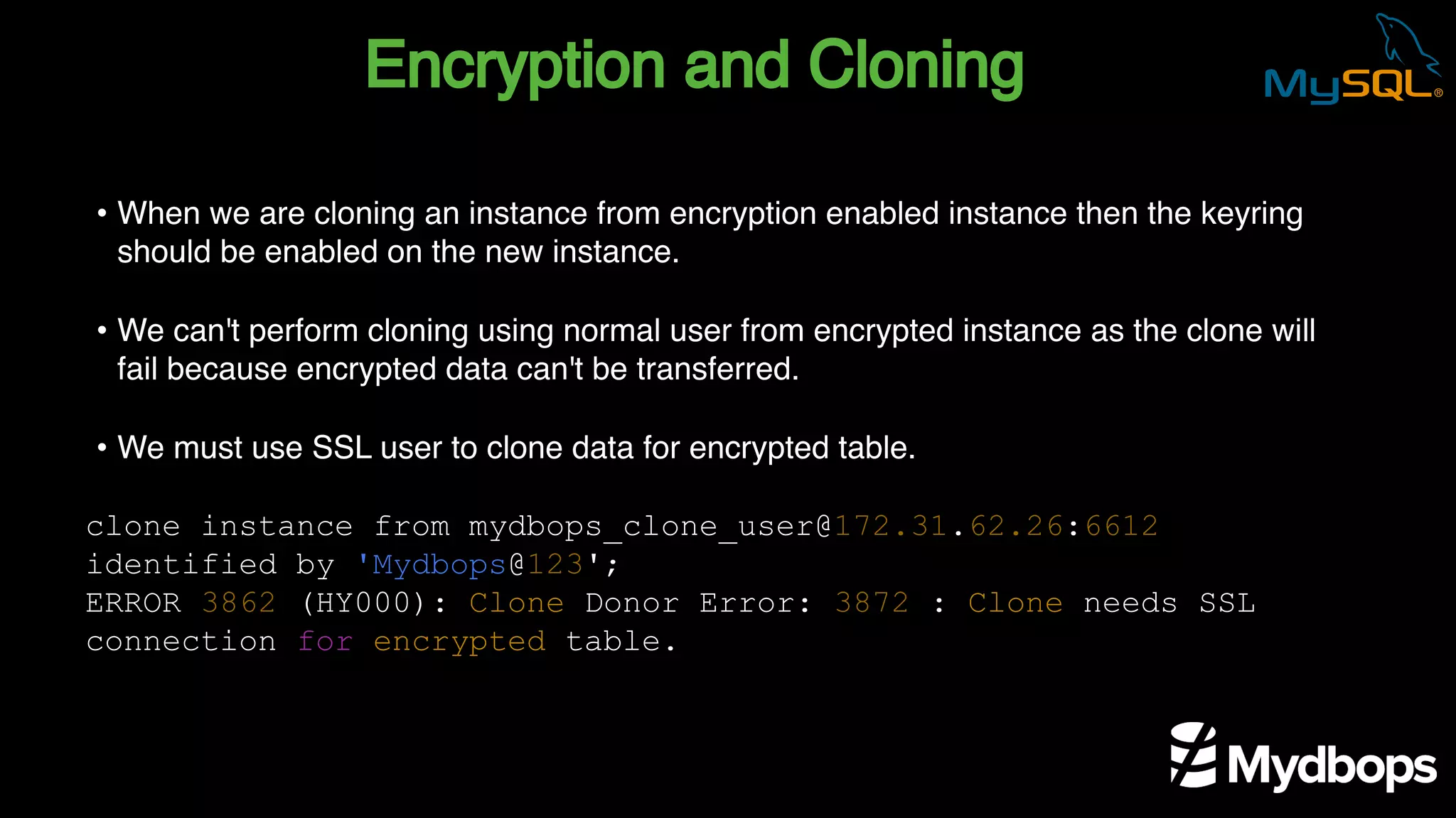
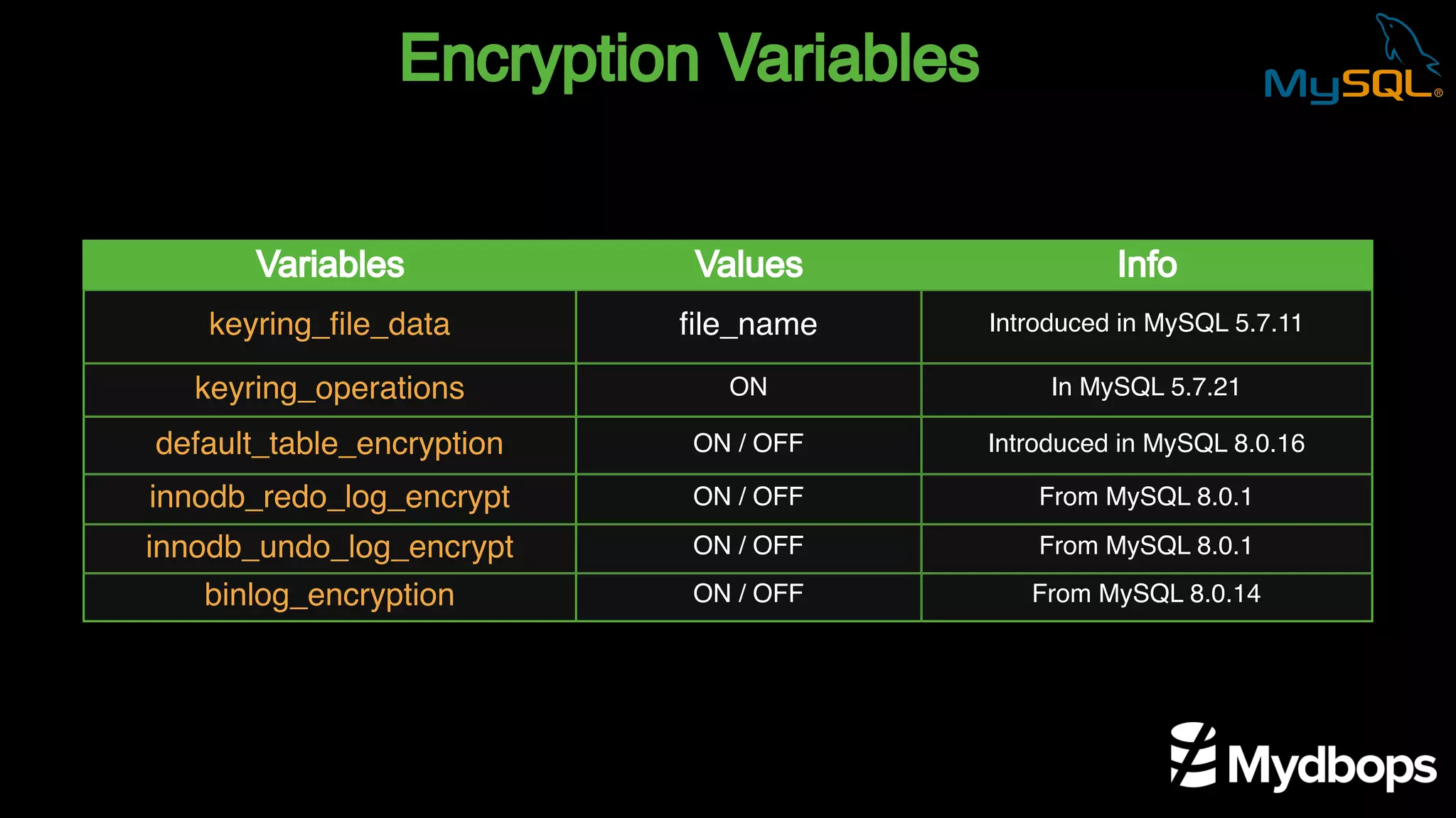
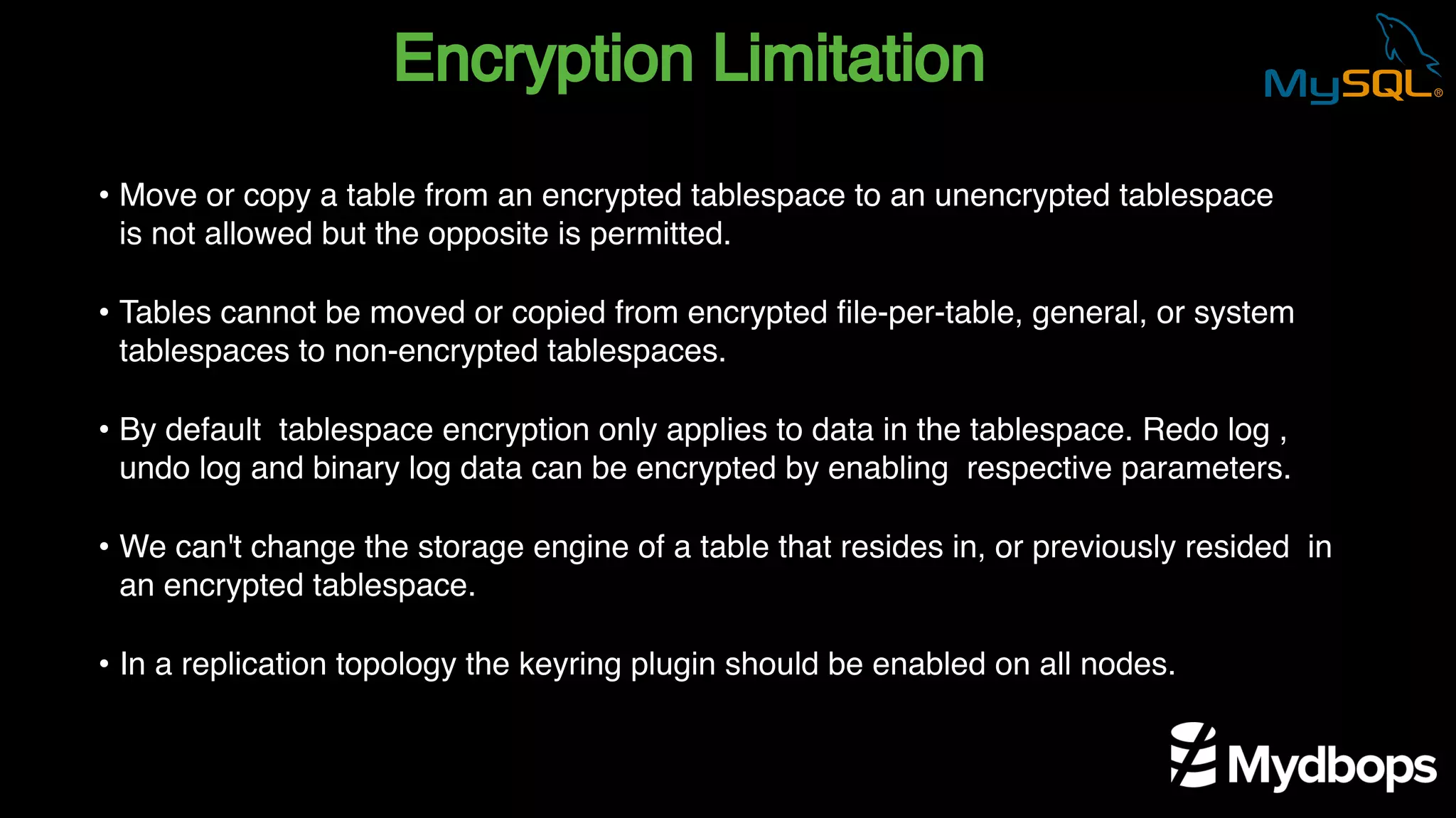
The document outlines the features and implementation of data encryption at rest in MySQL, focusing on InnoDB data encryption mechanisms introduced in versions 5.7 and 8.0. It details the architecture of encryption keys, prerequisites for setup, and highlights the evolution of encryption capabilities over various MySQL releases, including transparent data encryption (TDE) and support for general tablespace and binary log encryption. Additionally, it addresses encryption prerequisites, observability, and the implications of master key rotation in a replication environment.