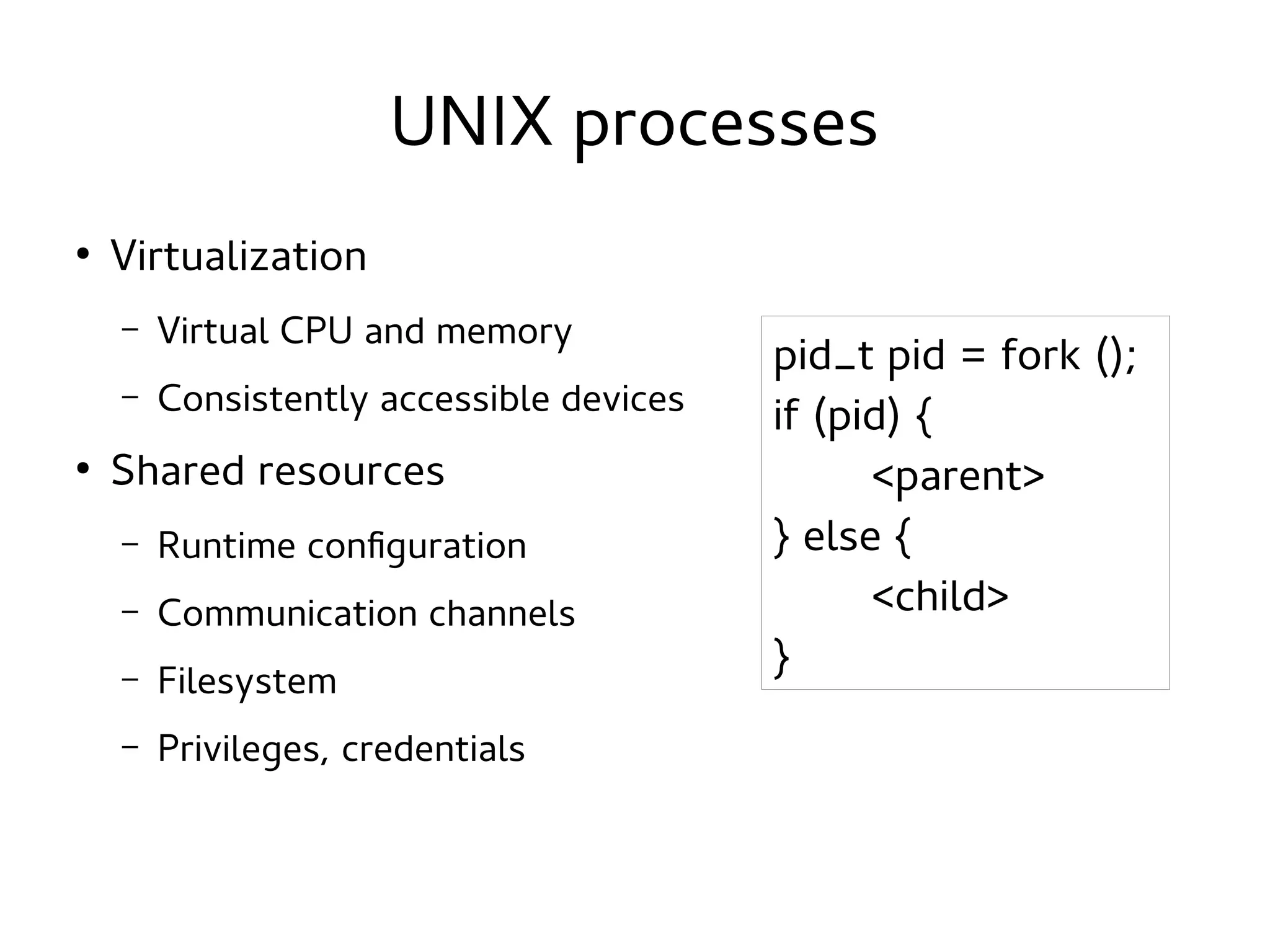
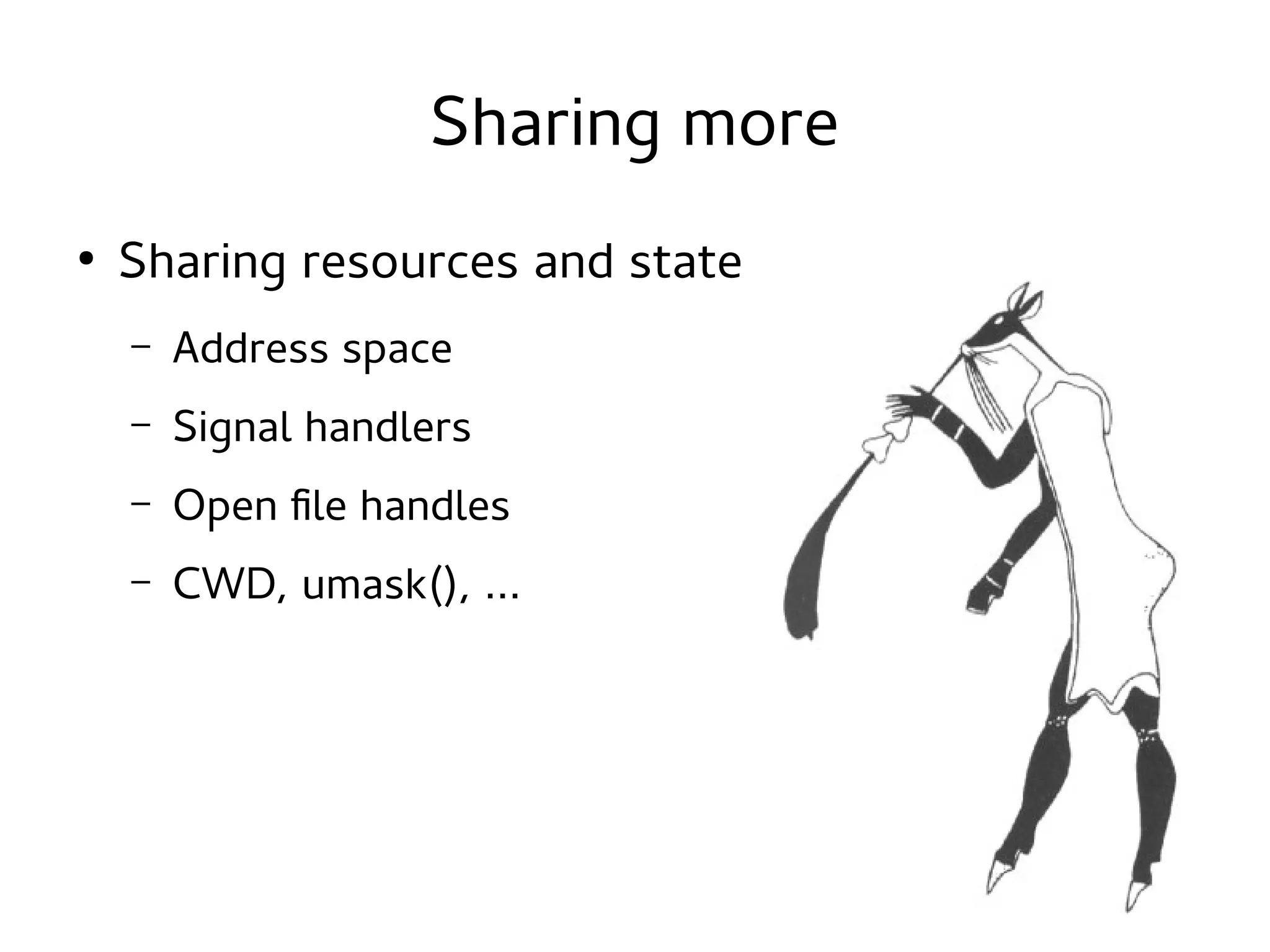
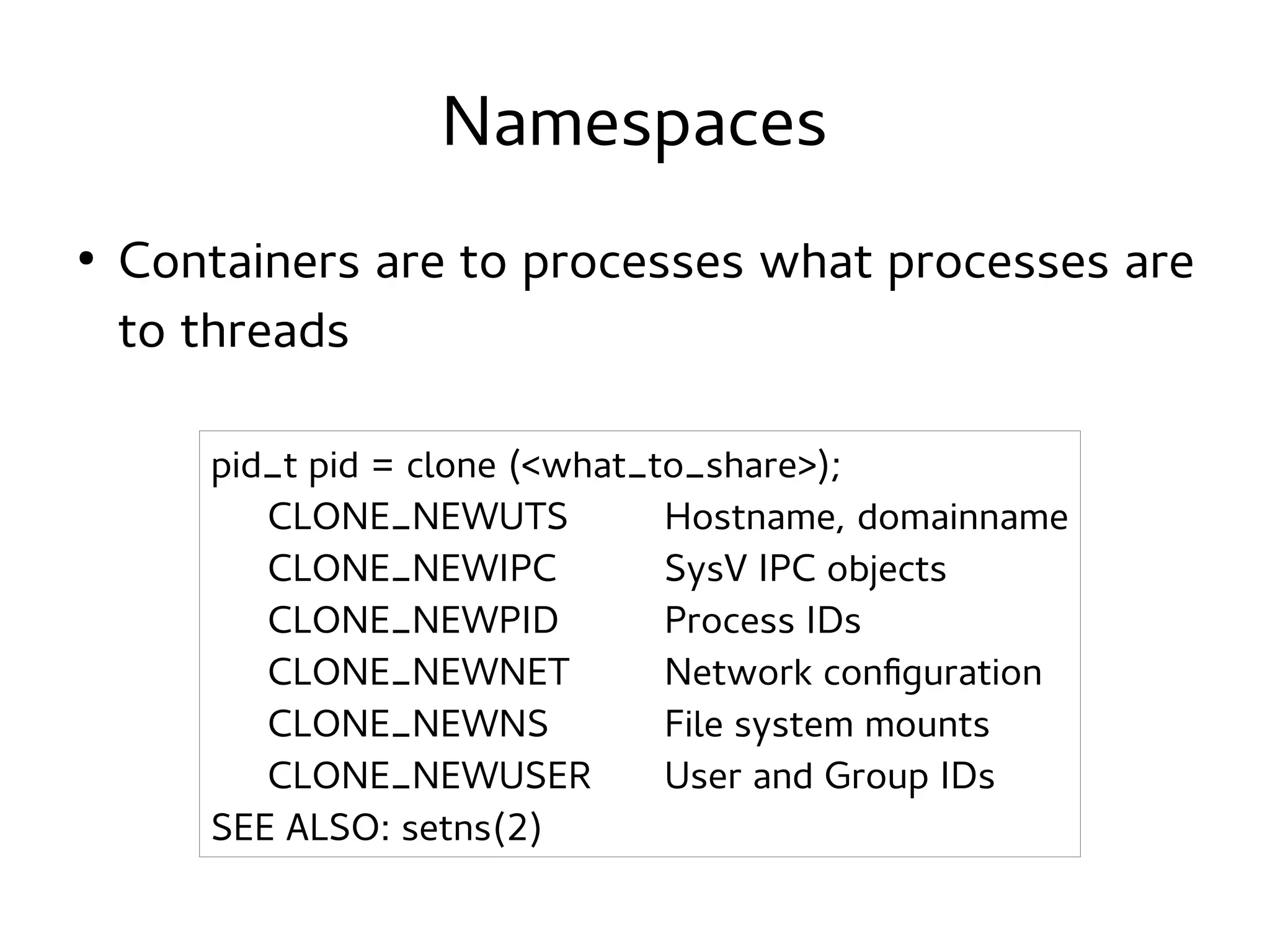
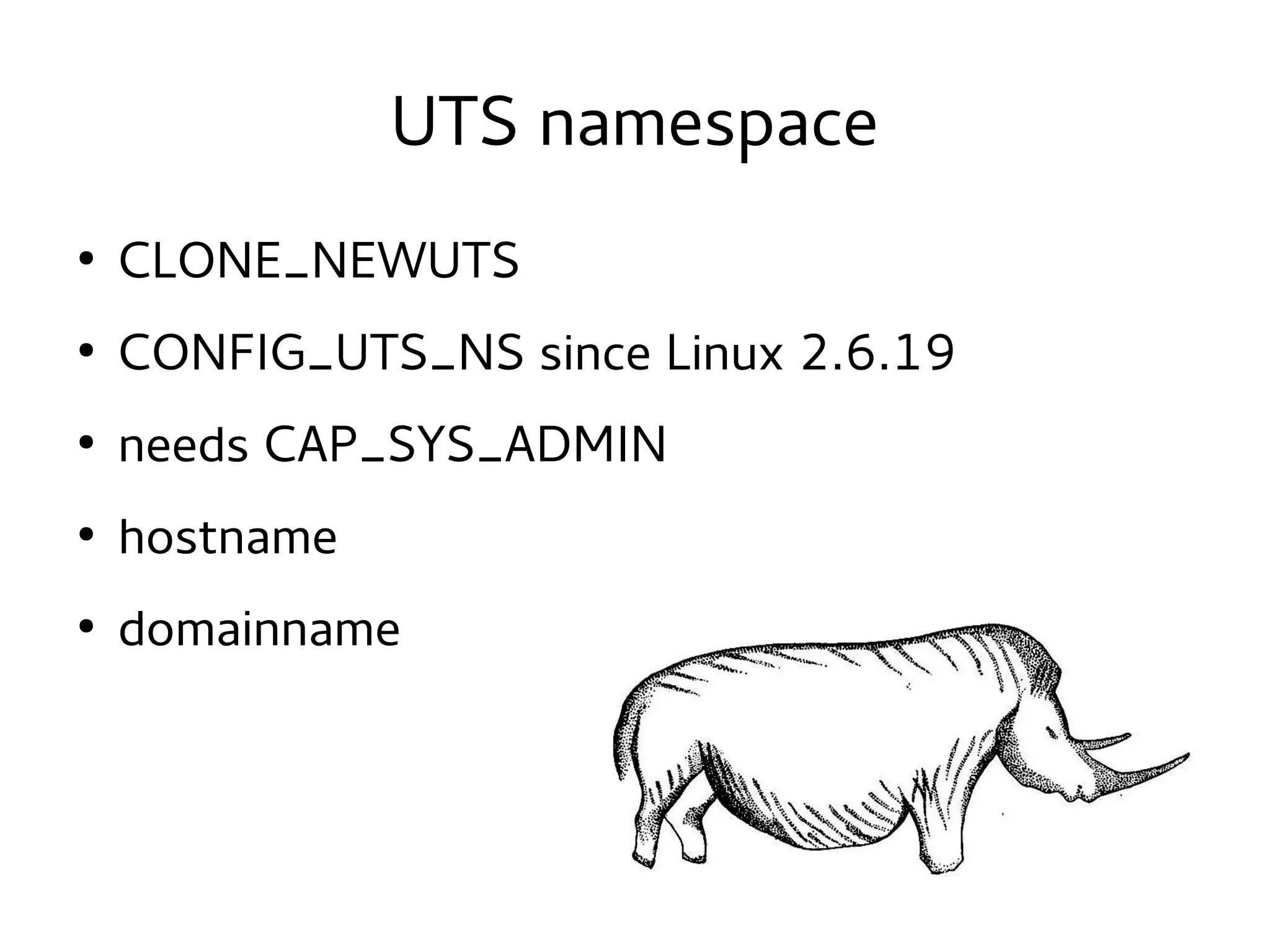
This document discusses namespaces in Linux. Namespaces allow containers to have isolated resources like processes, networking, file systems, users and more. Containers share less than virtual machines but provide more isolation than regular processes. Namespaces use the clone system call to create an isolated view of various system resources for a container. Common namespaces include UTS for hostname, IPC for shared memory, PID for process IDs, network, mount and more. Tools like LXC, Docker and systemd-nspawn make it easy to create and manage containers using namespaces and cgroups.