Download as PDF, PPTX



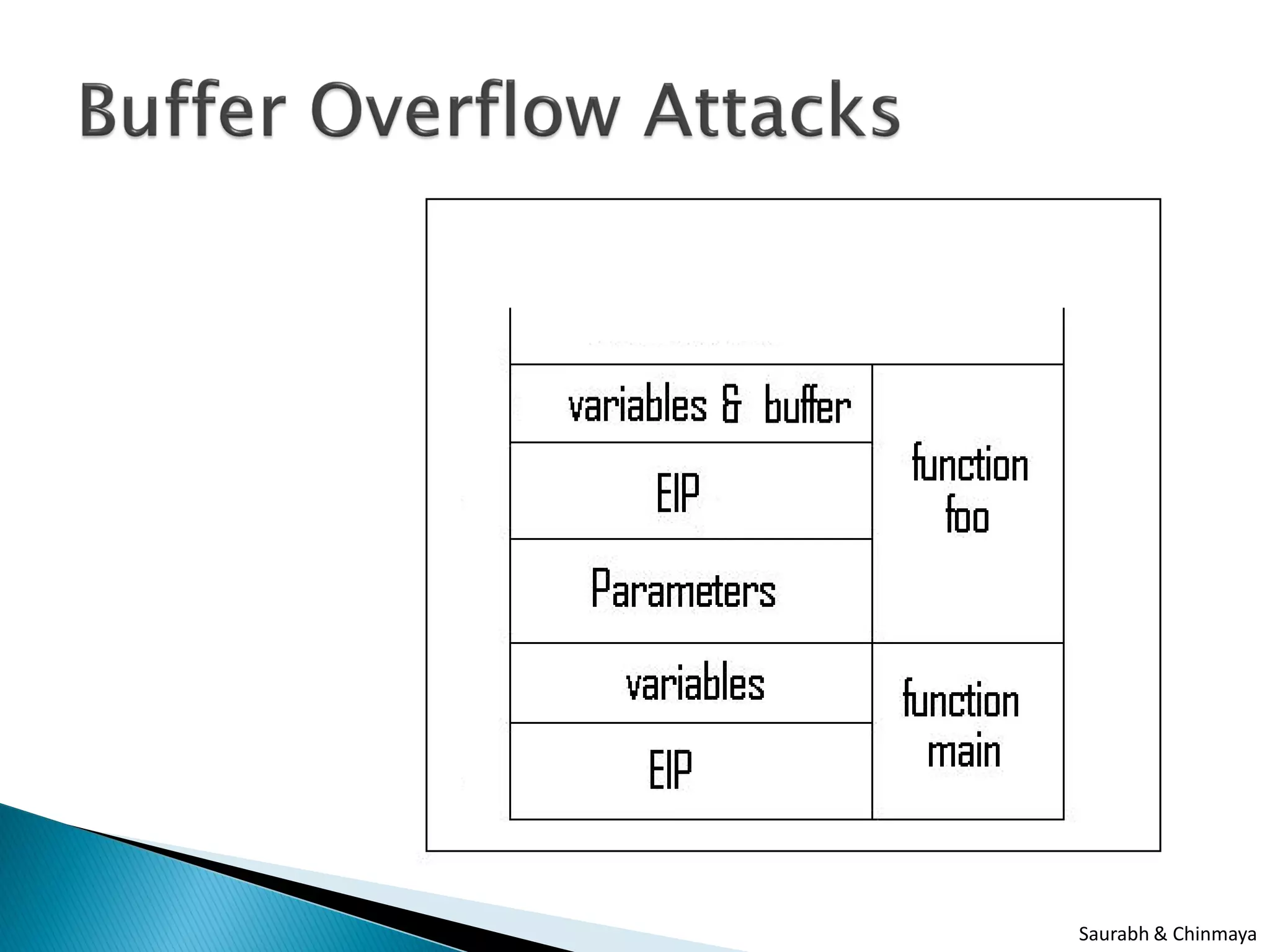

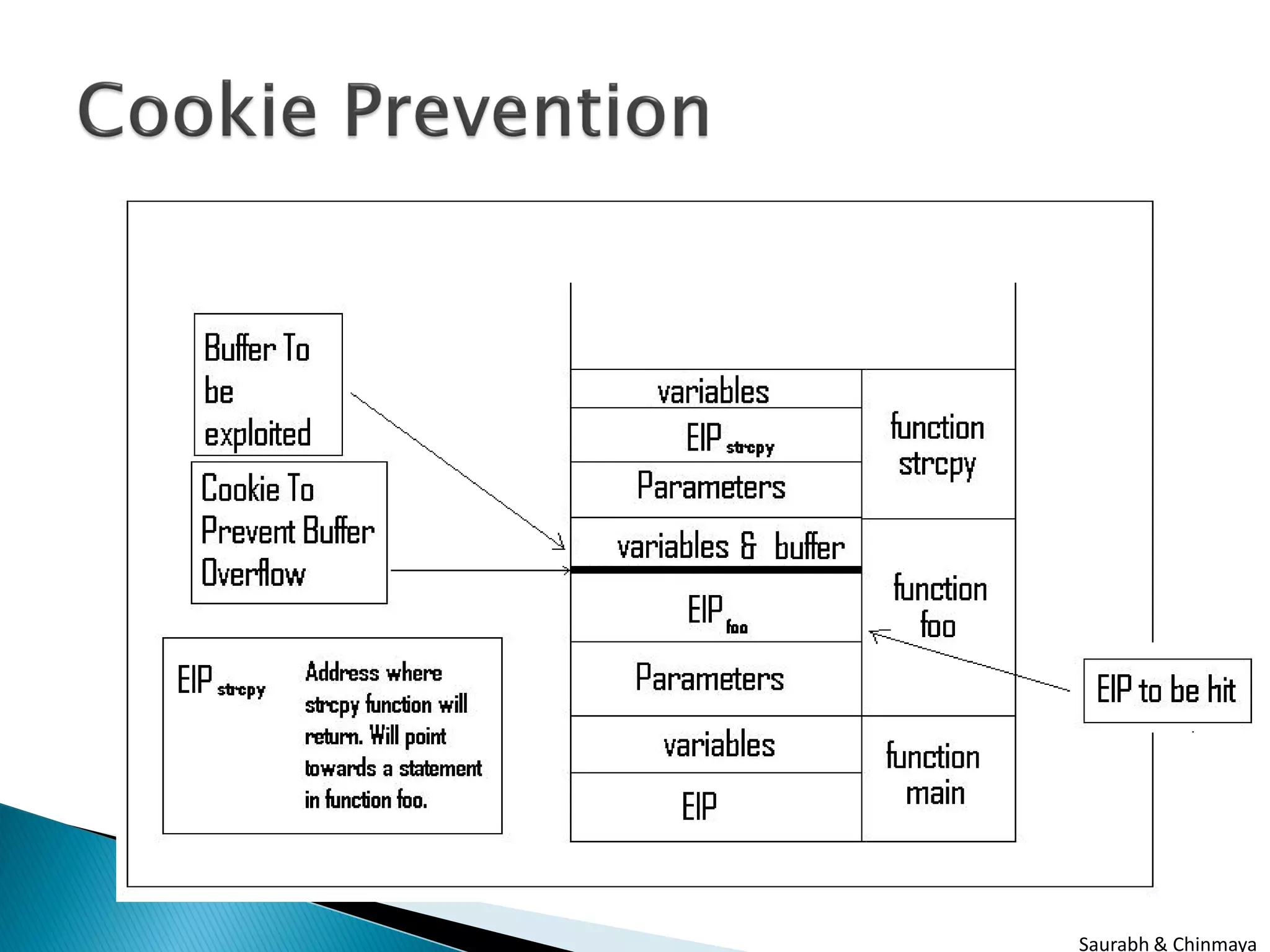
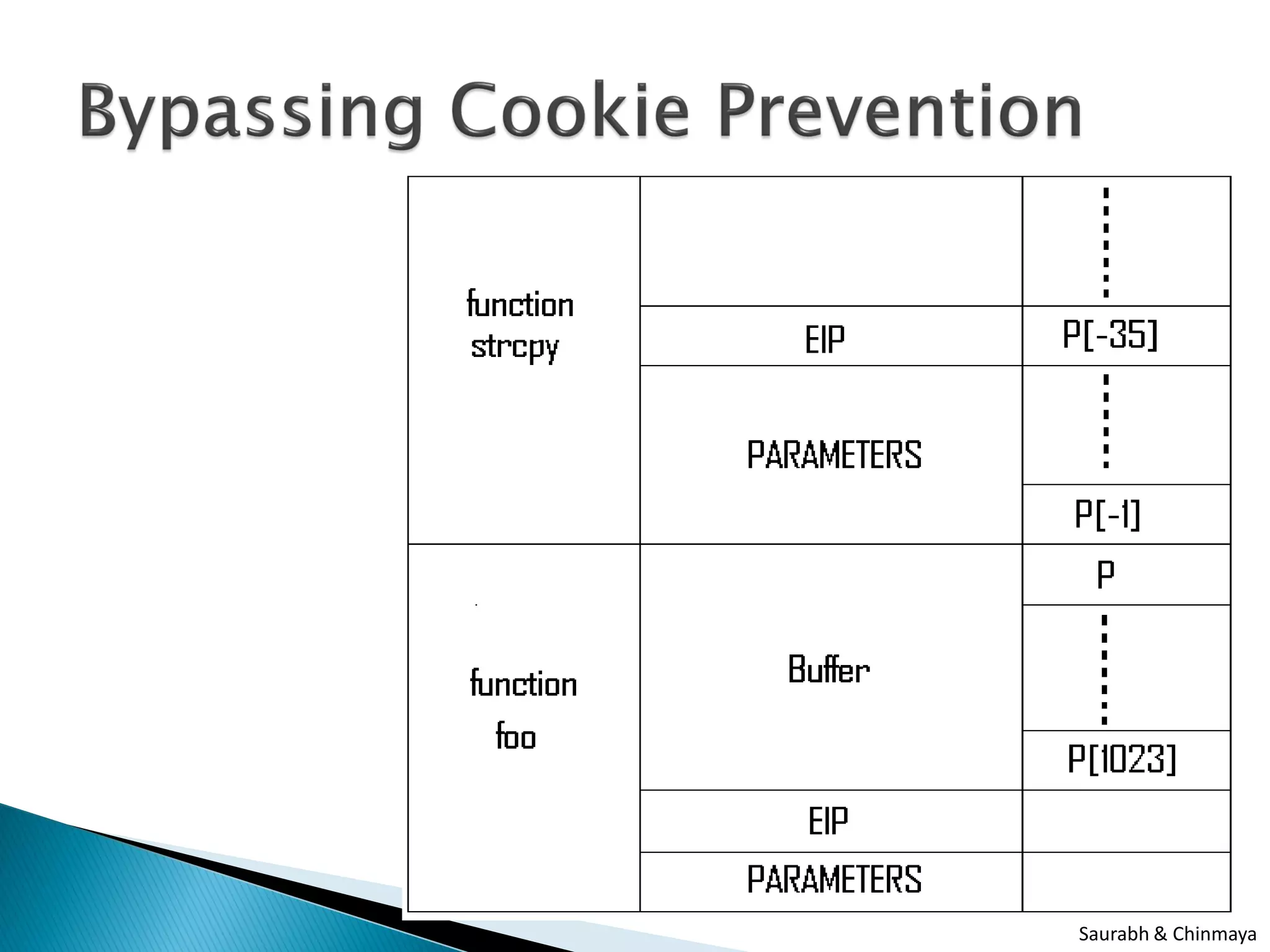


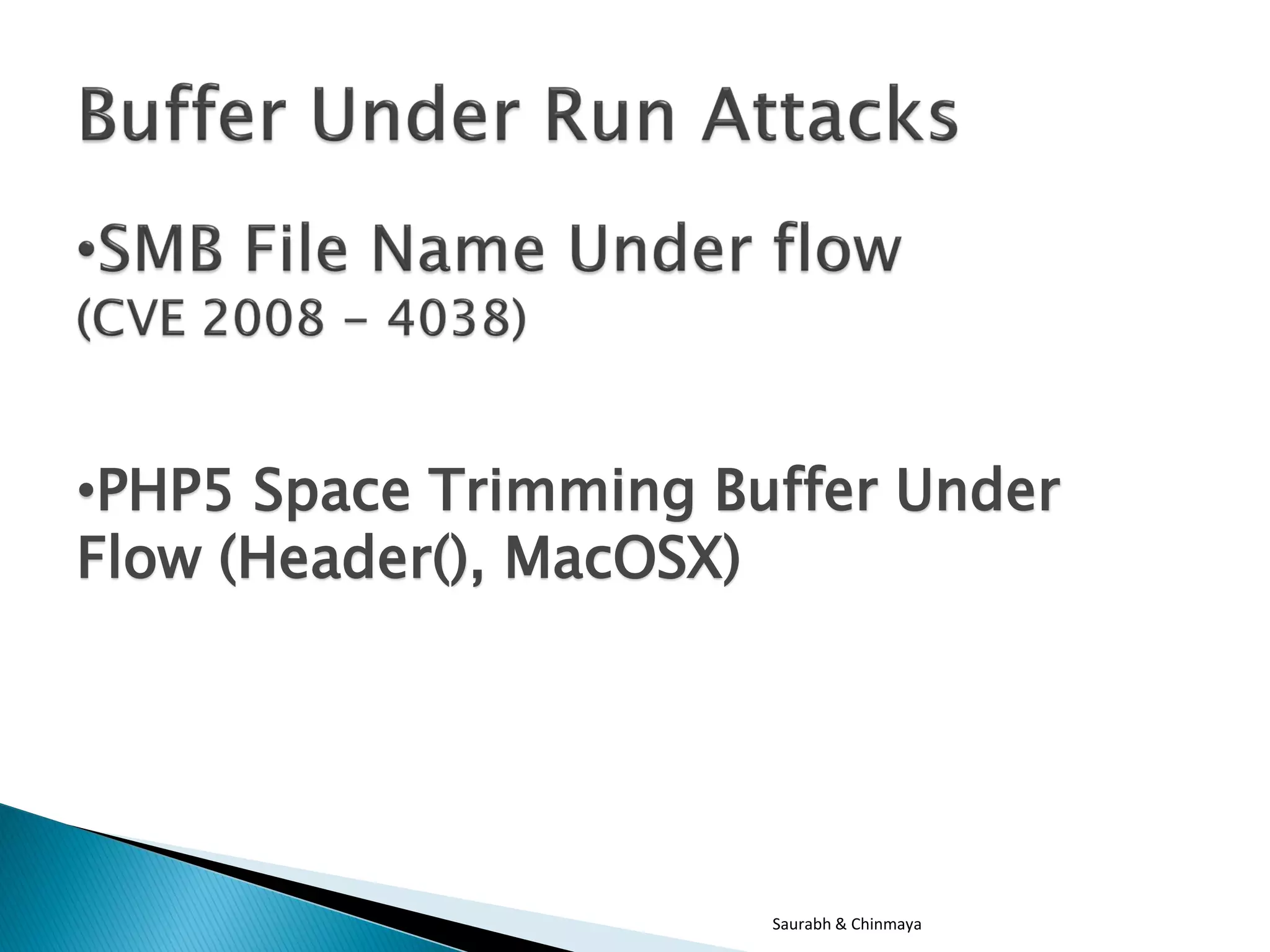



The document discusses three types of attacks: buffer overflow attacks, which occur when input data exceeds the allocated buffer size and overwrites other values; cookie prevention techniques; and buffer under run attacks, such as a PHP5 space trimming buffer underflow. It was presented by Saurabh Sharma and Chinmaya Kamal of SETLabs, Infosys.











