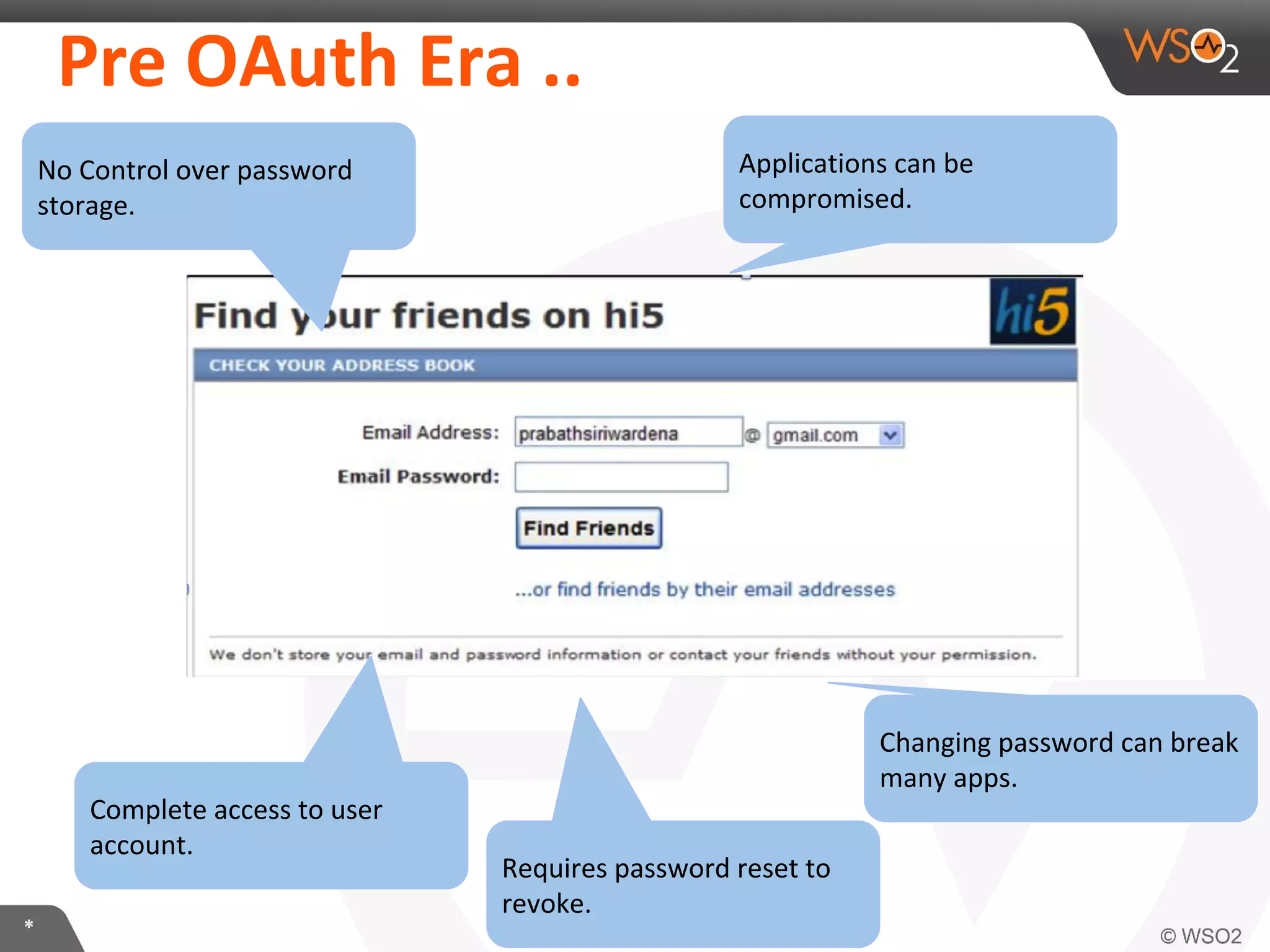
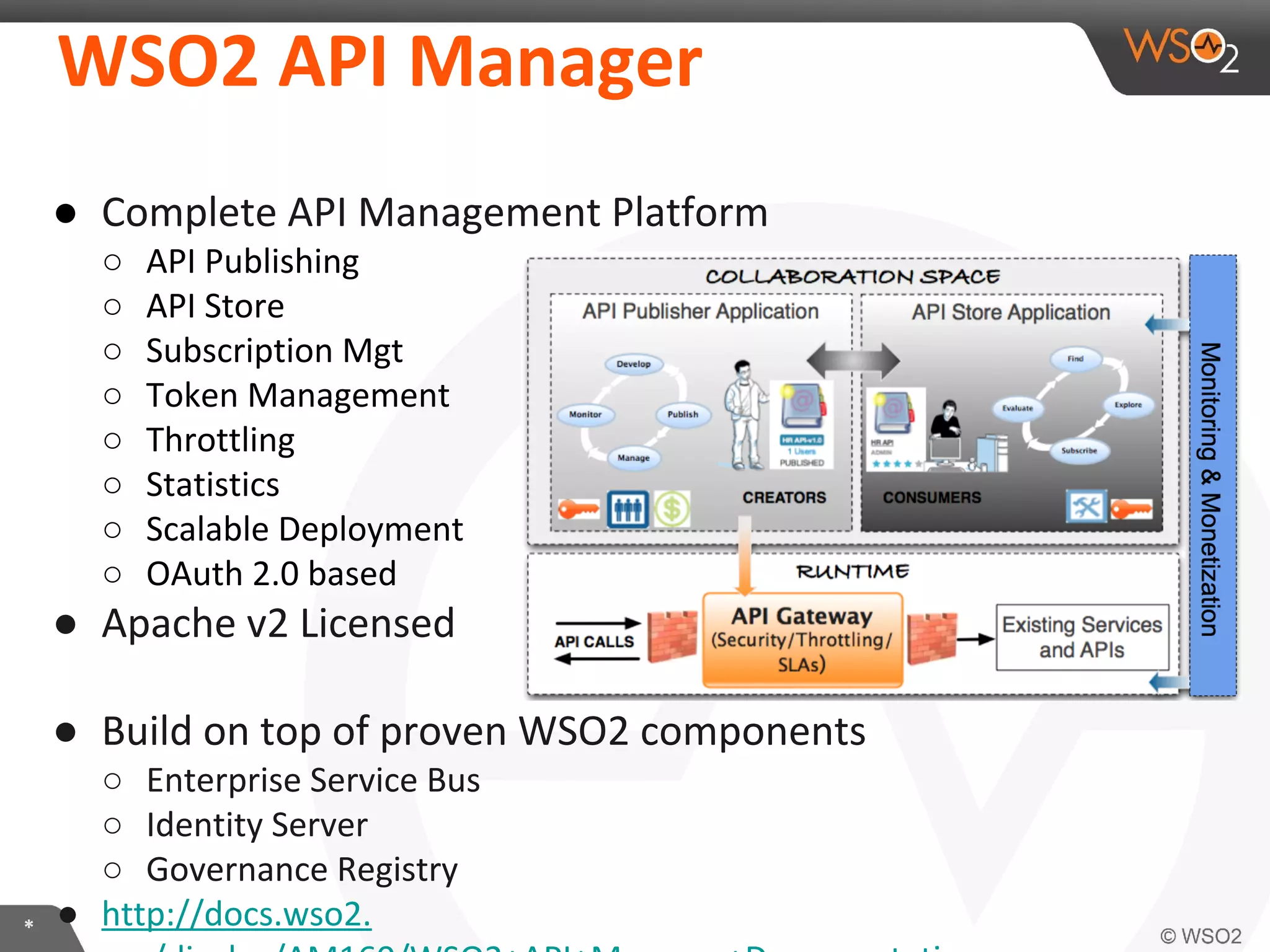
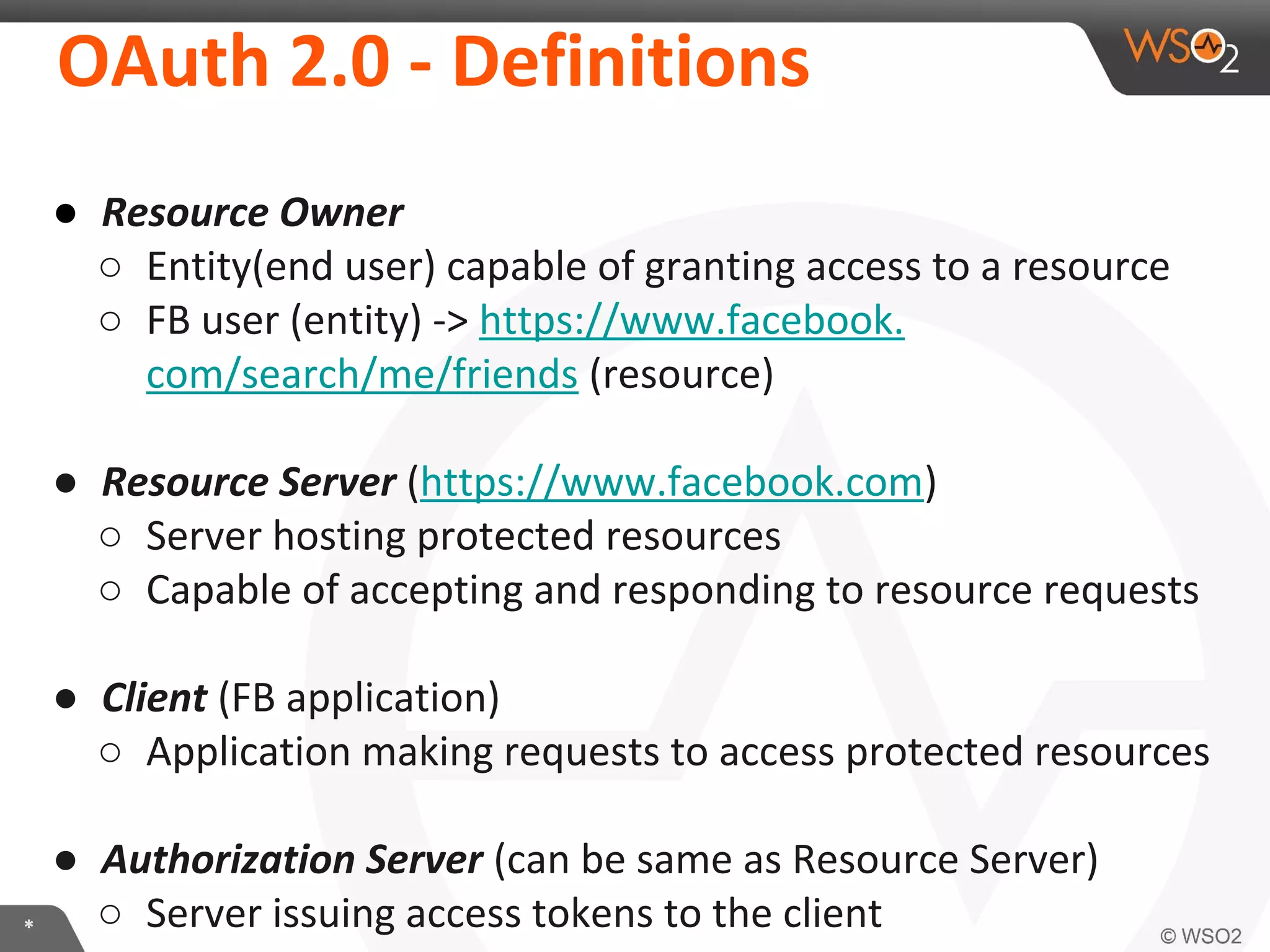
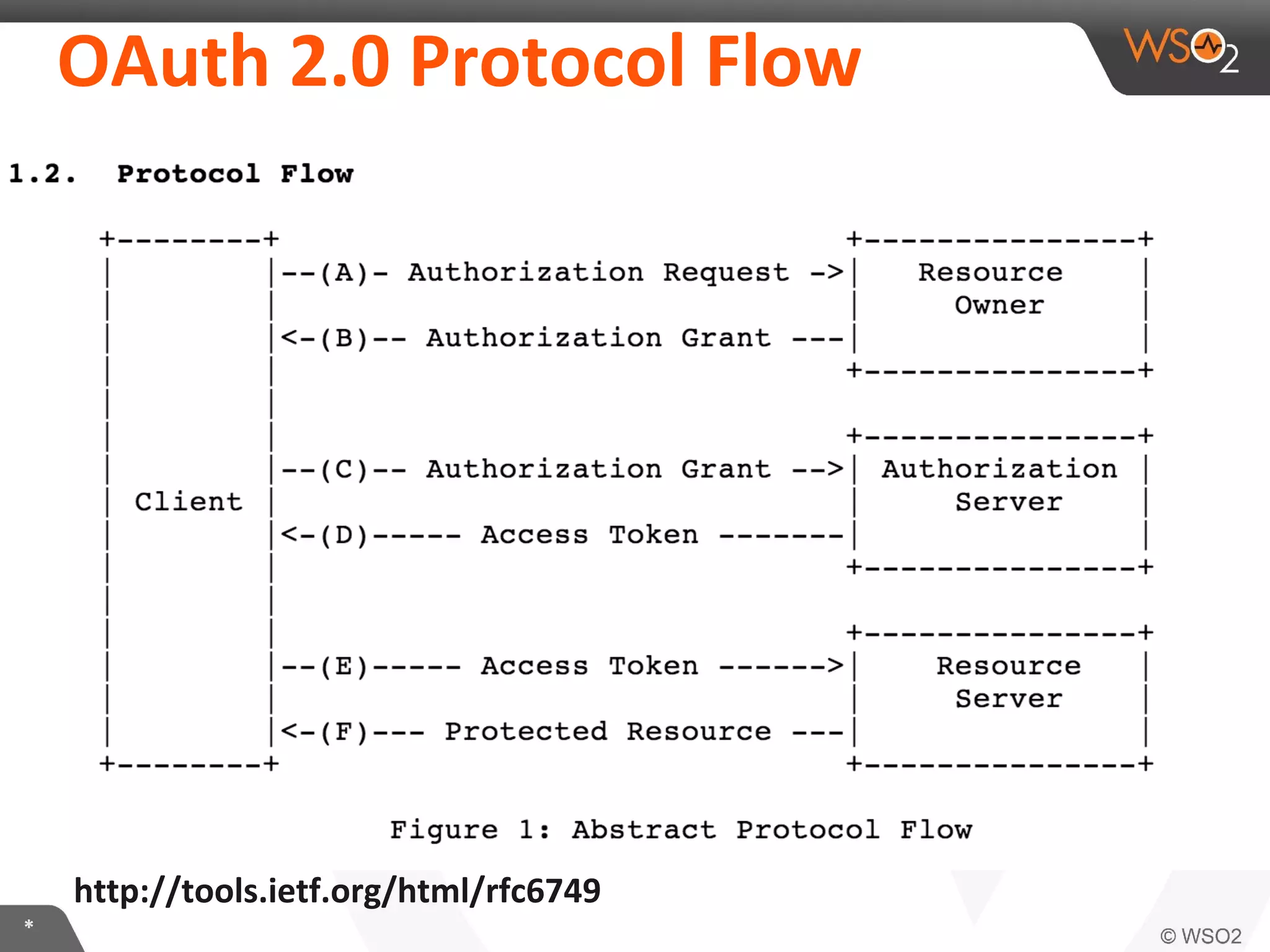
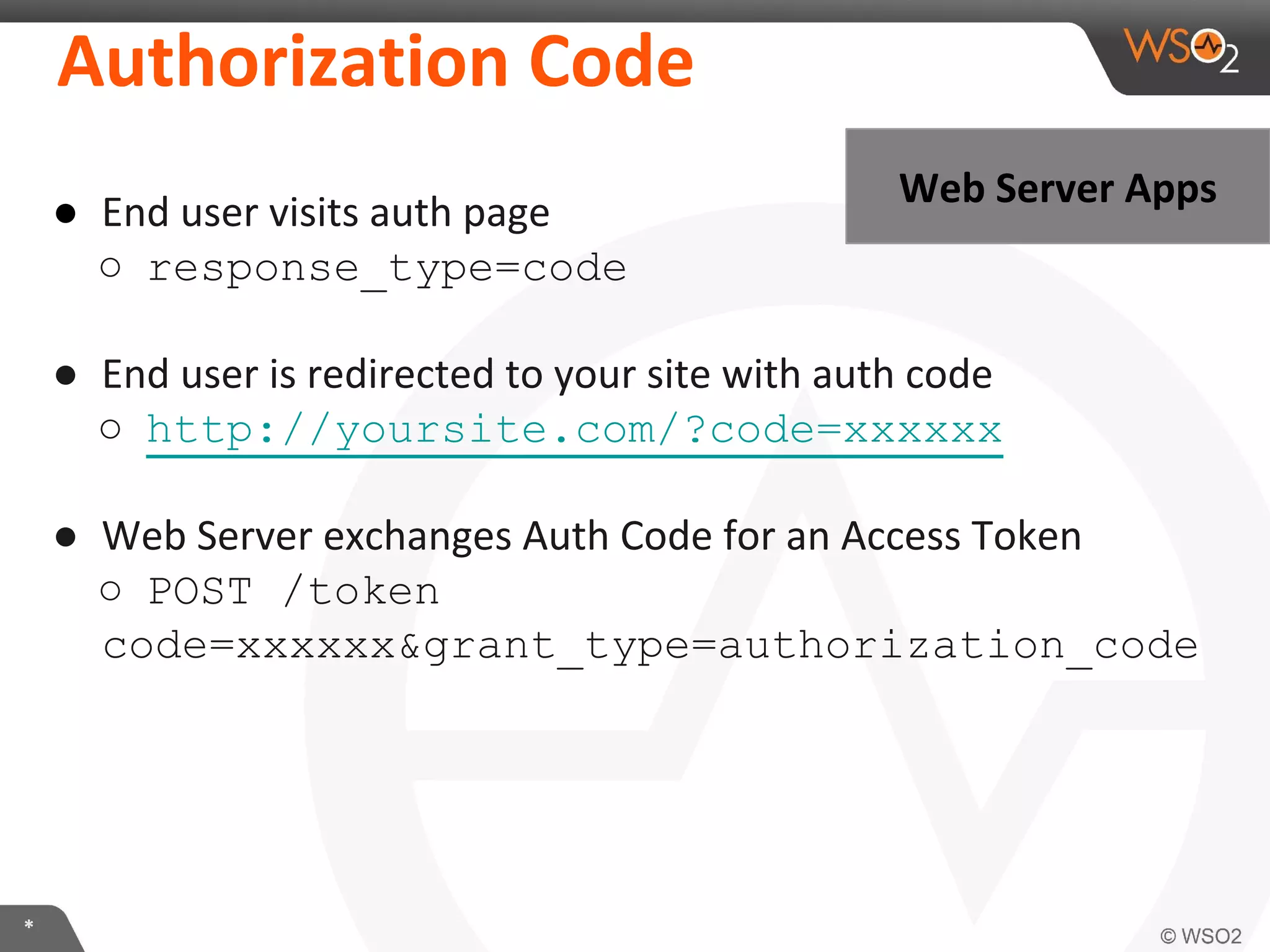
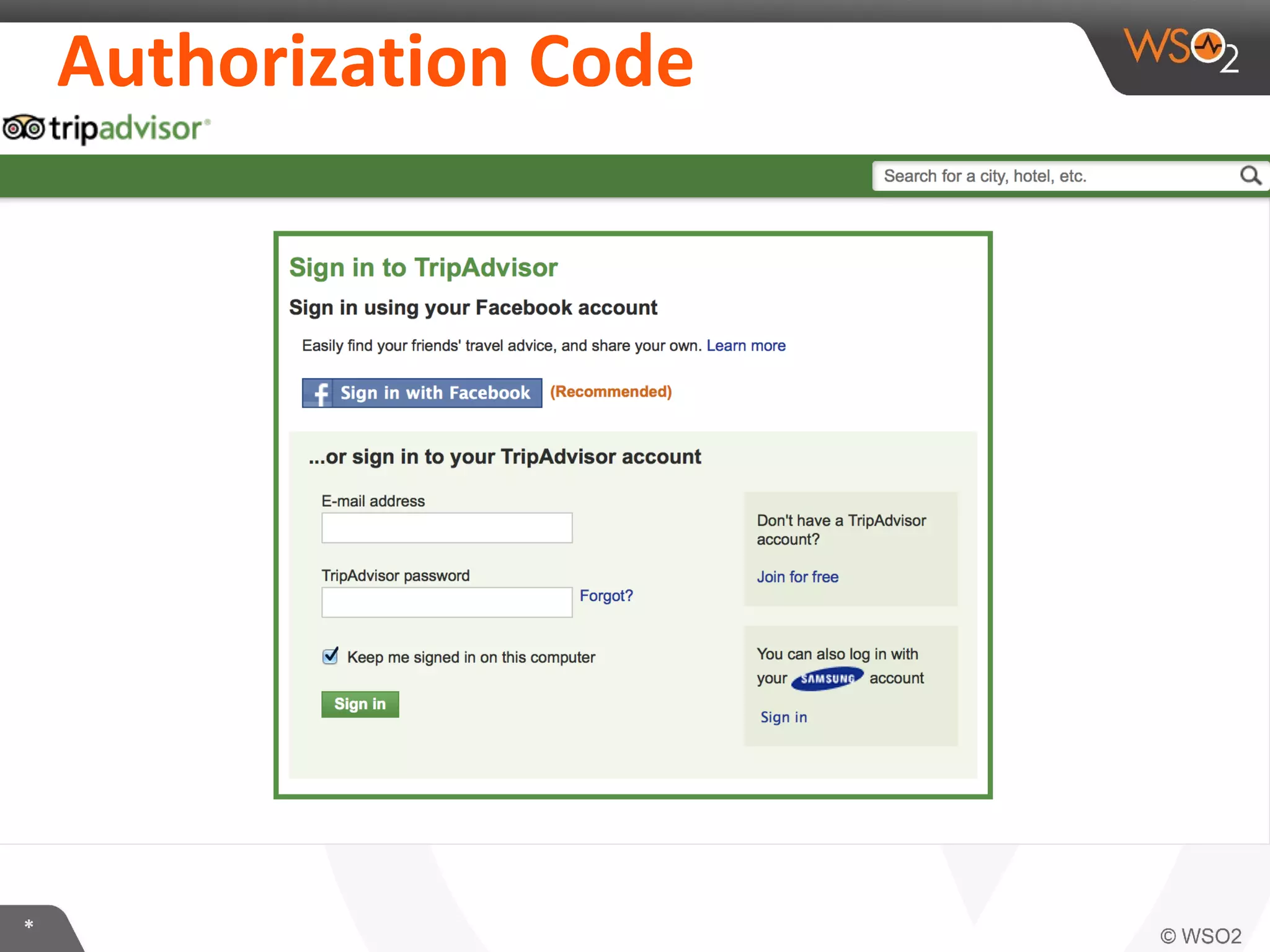
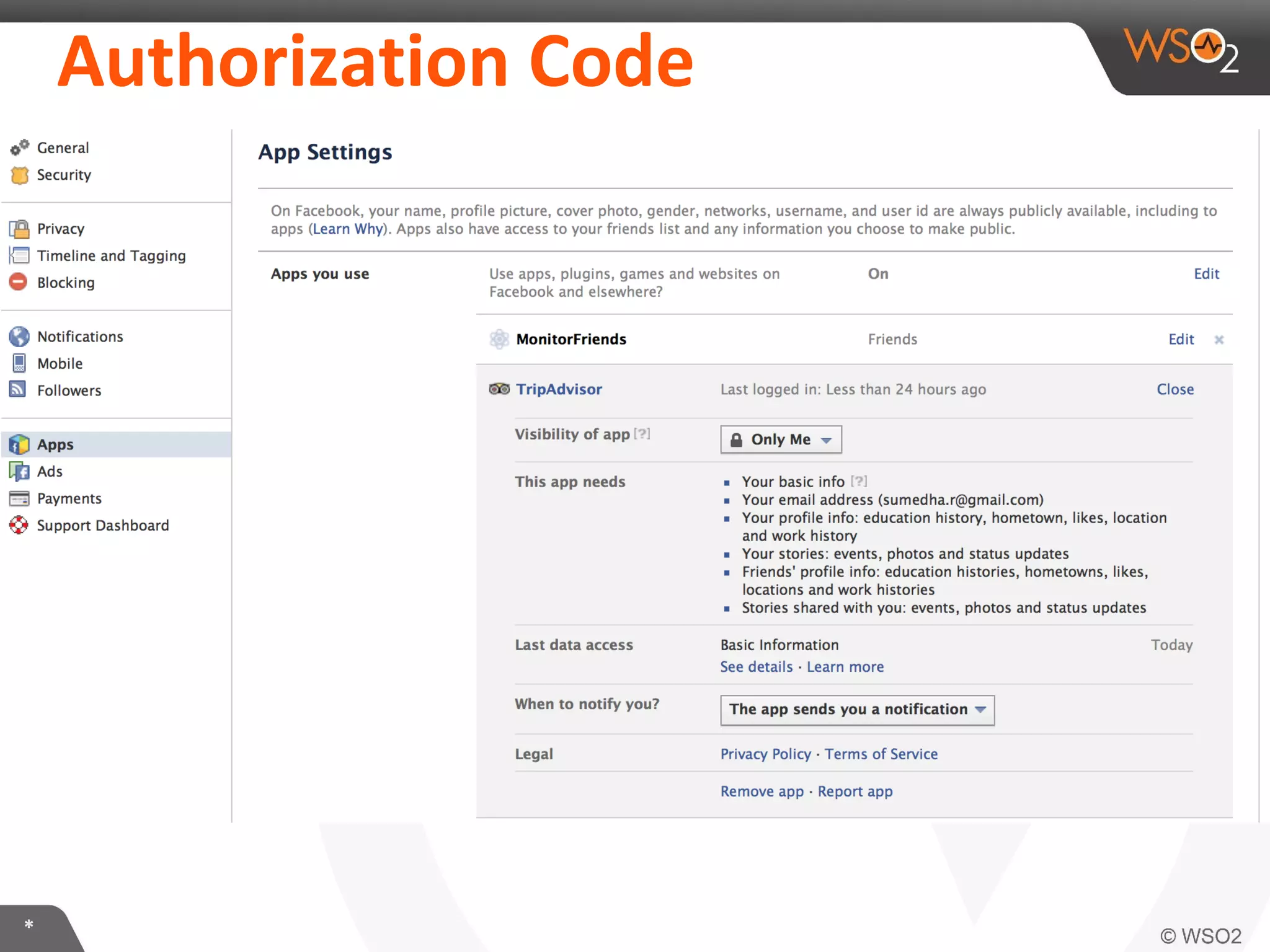
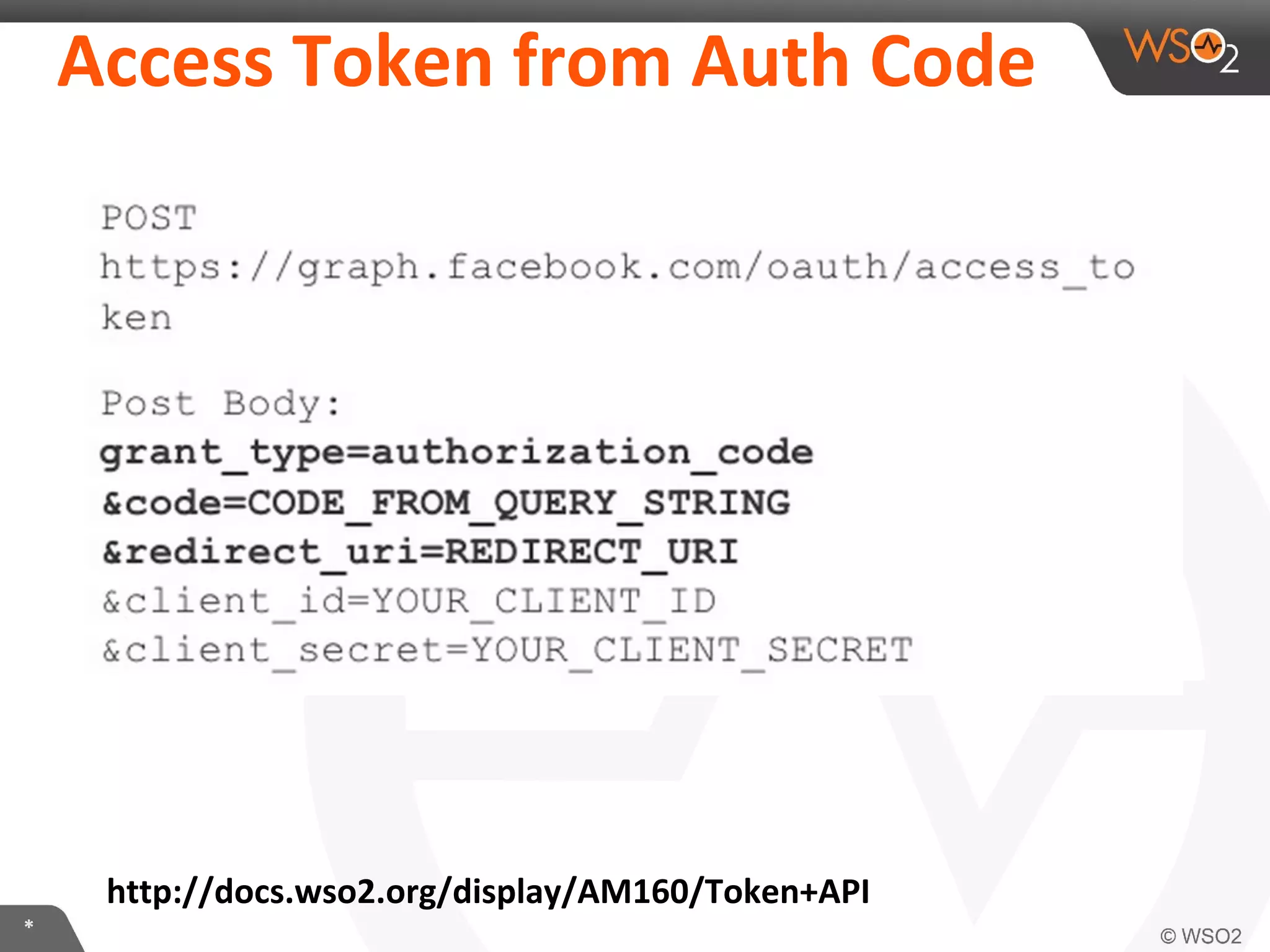
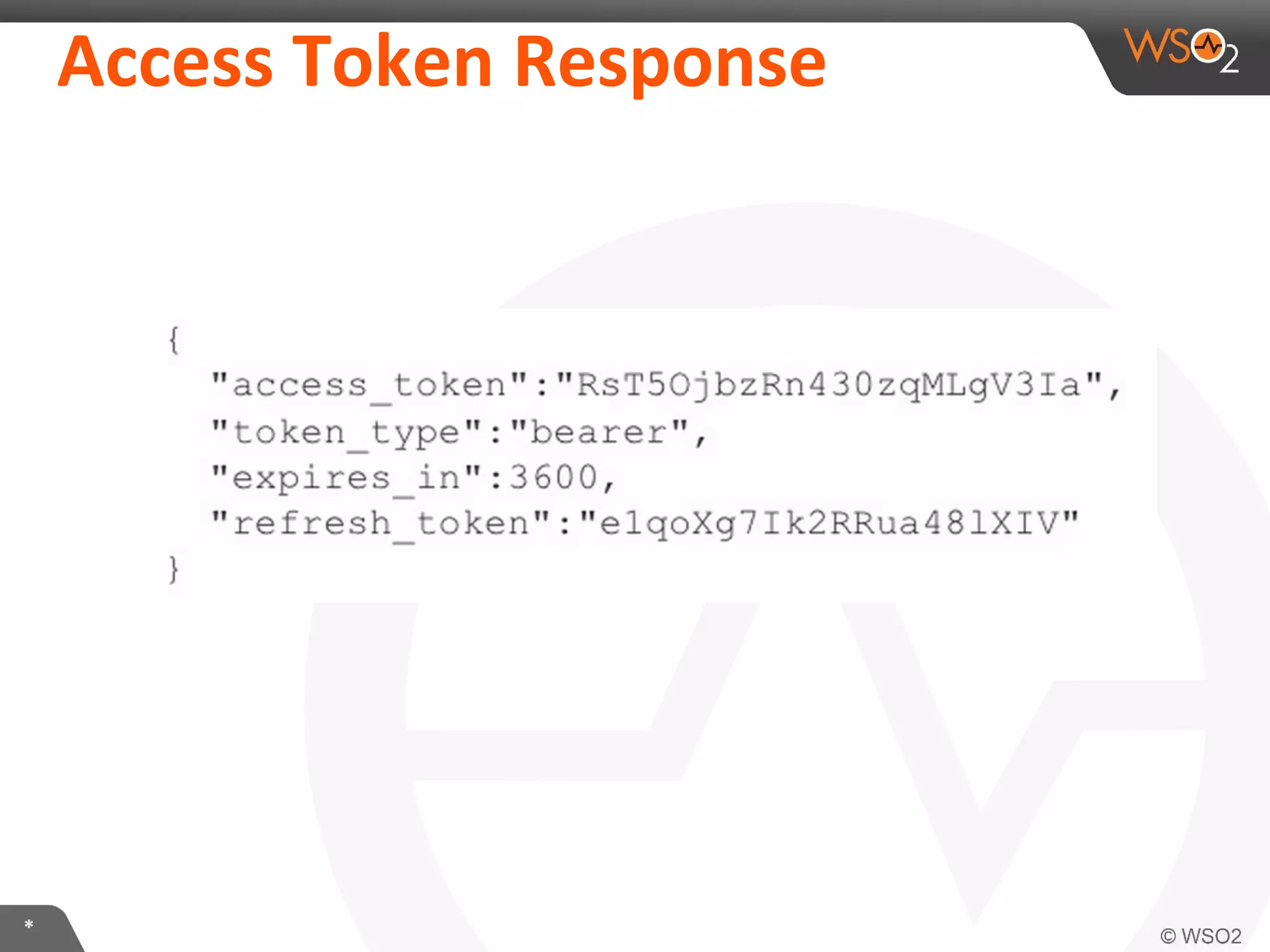
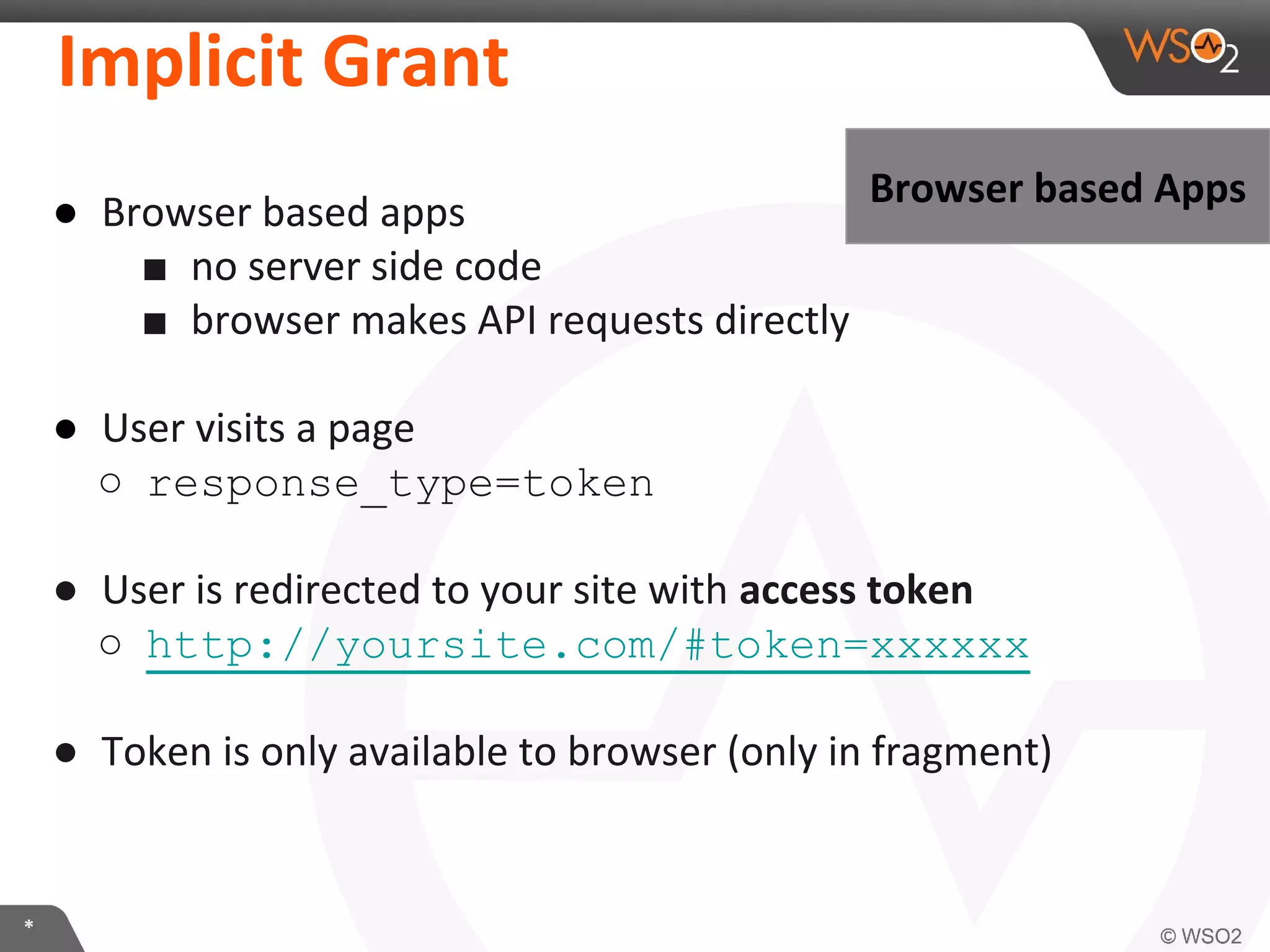
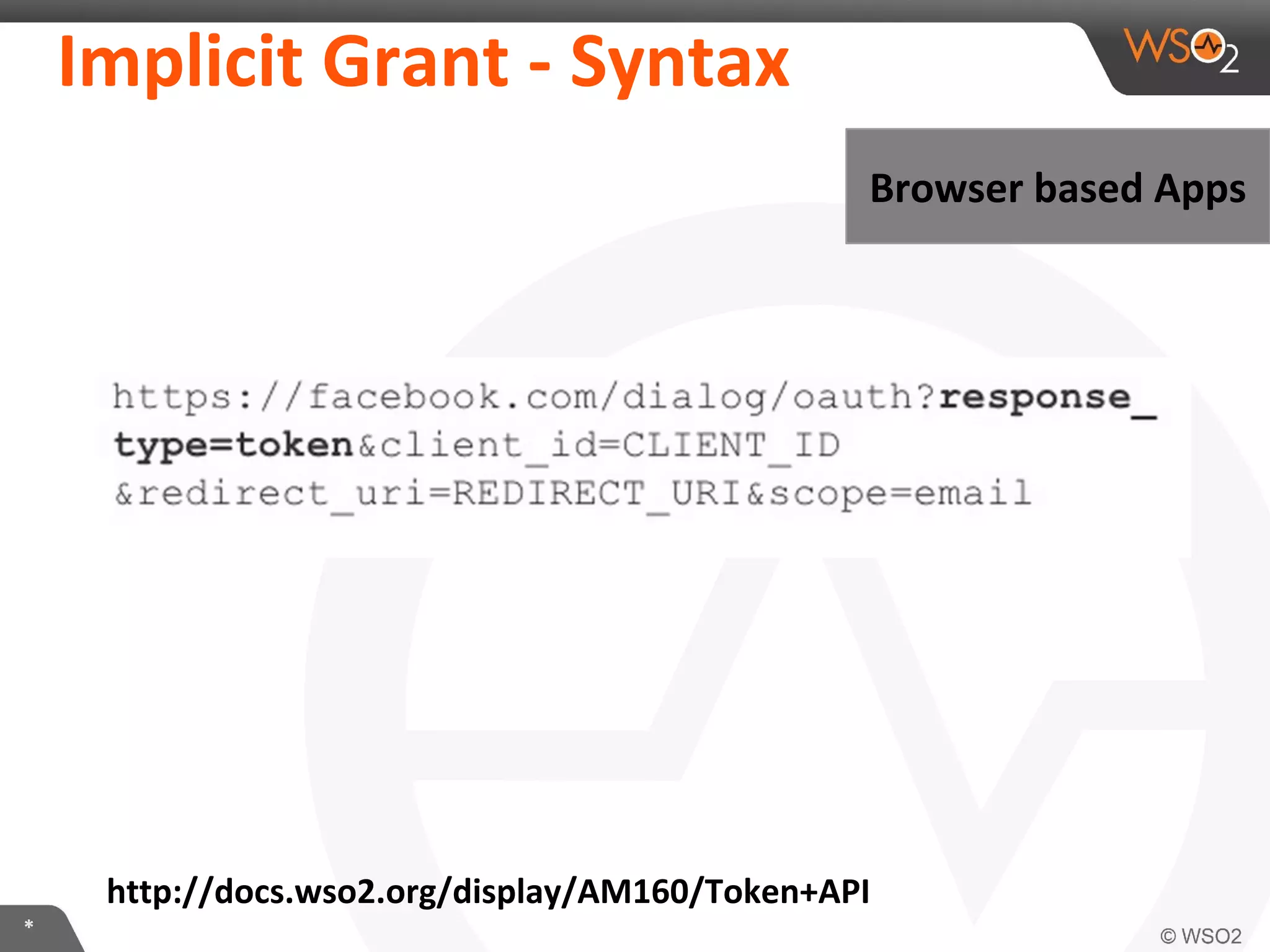
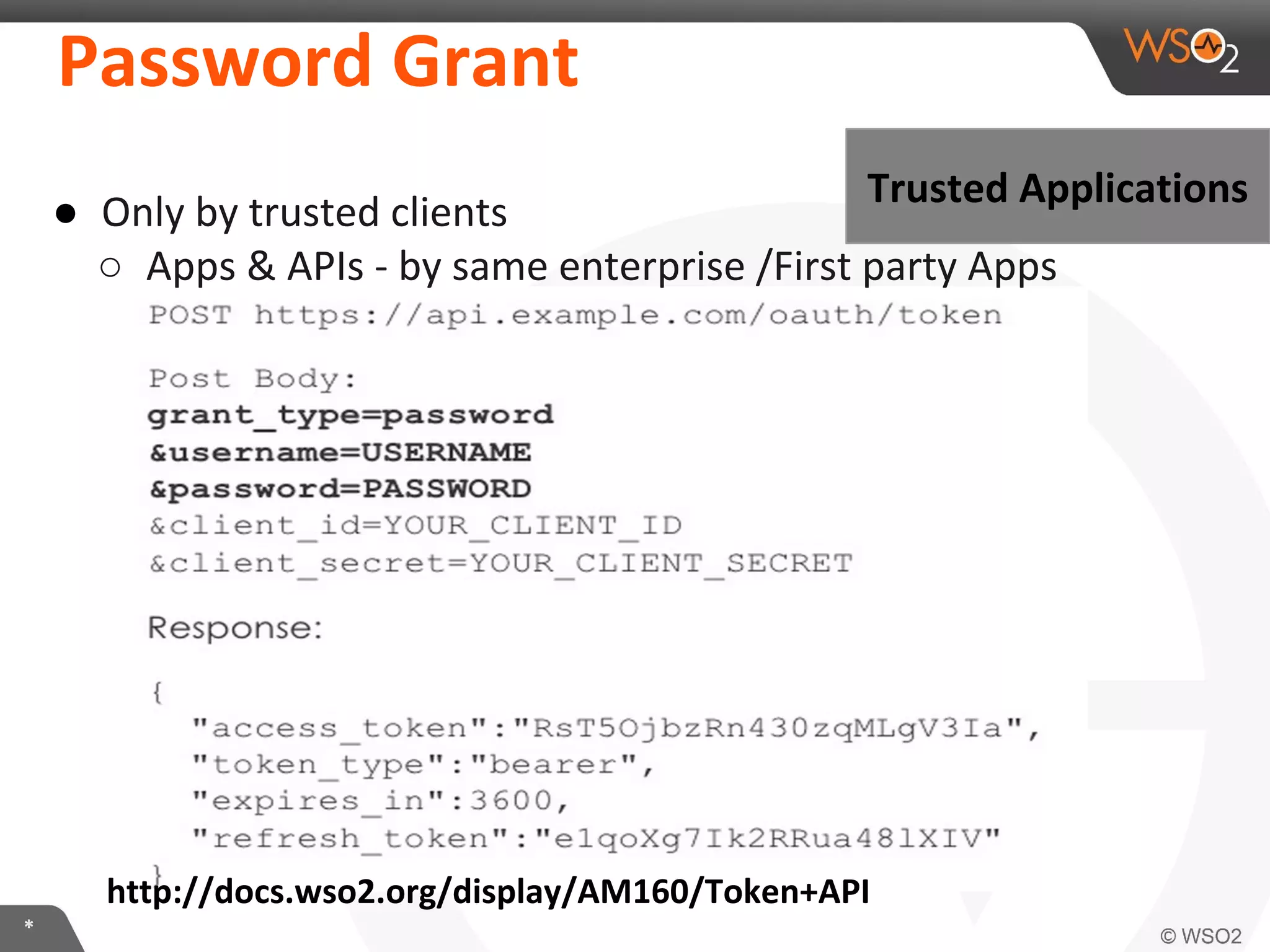
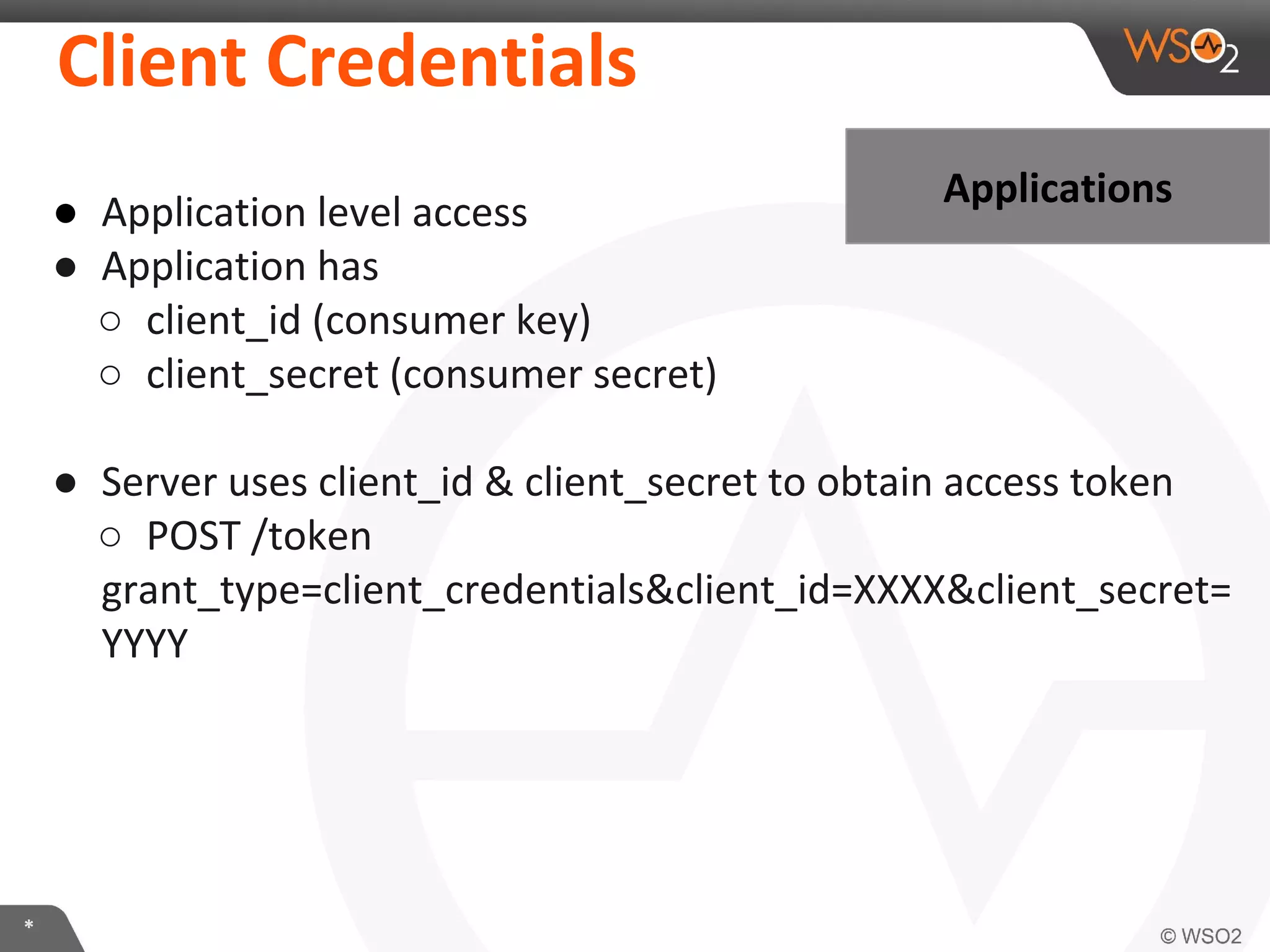
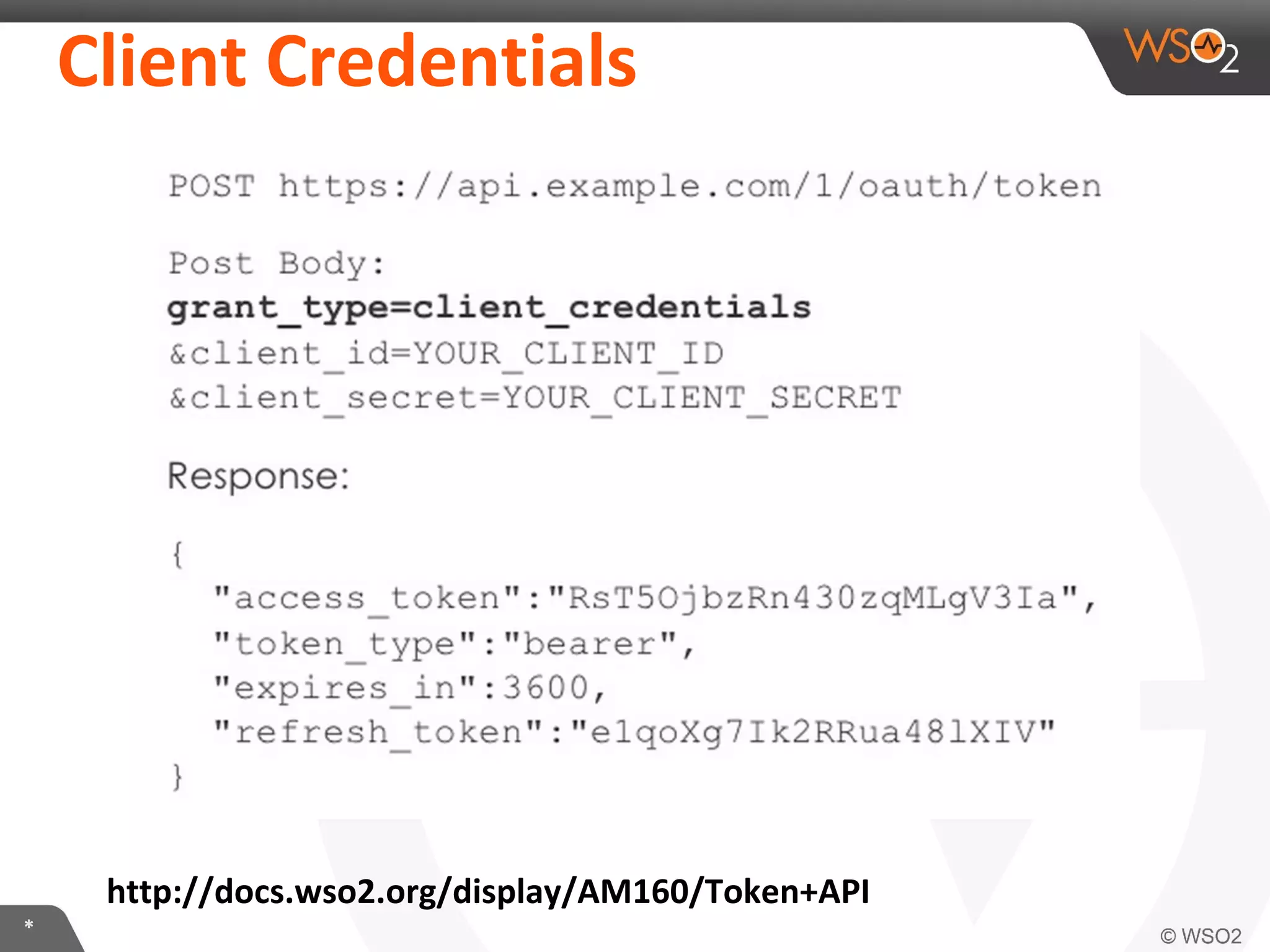
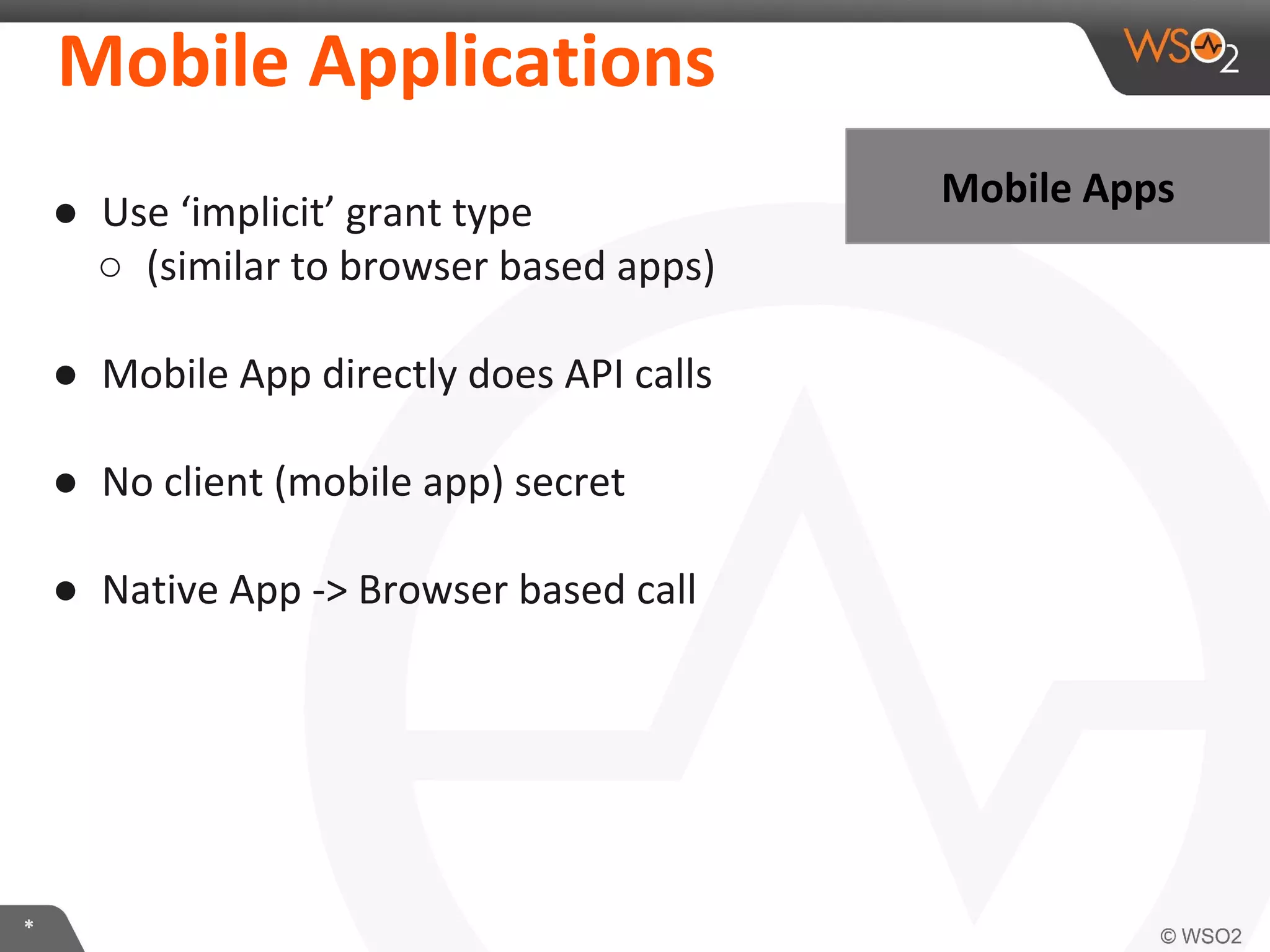
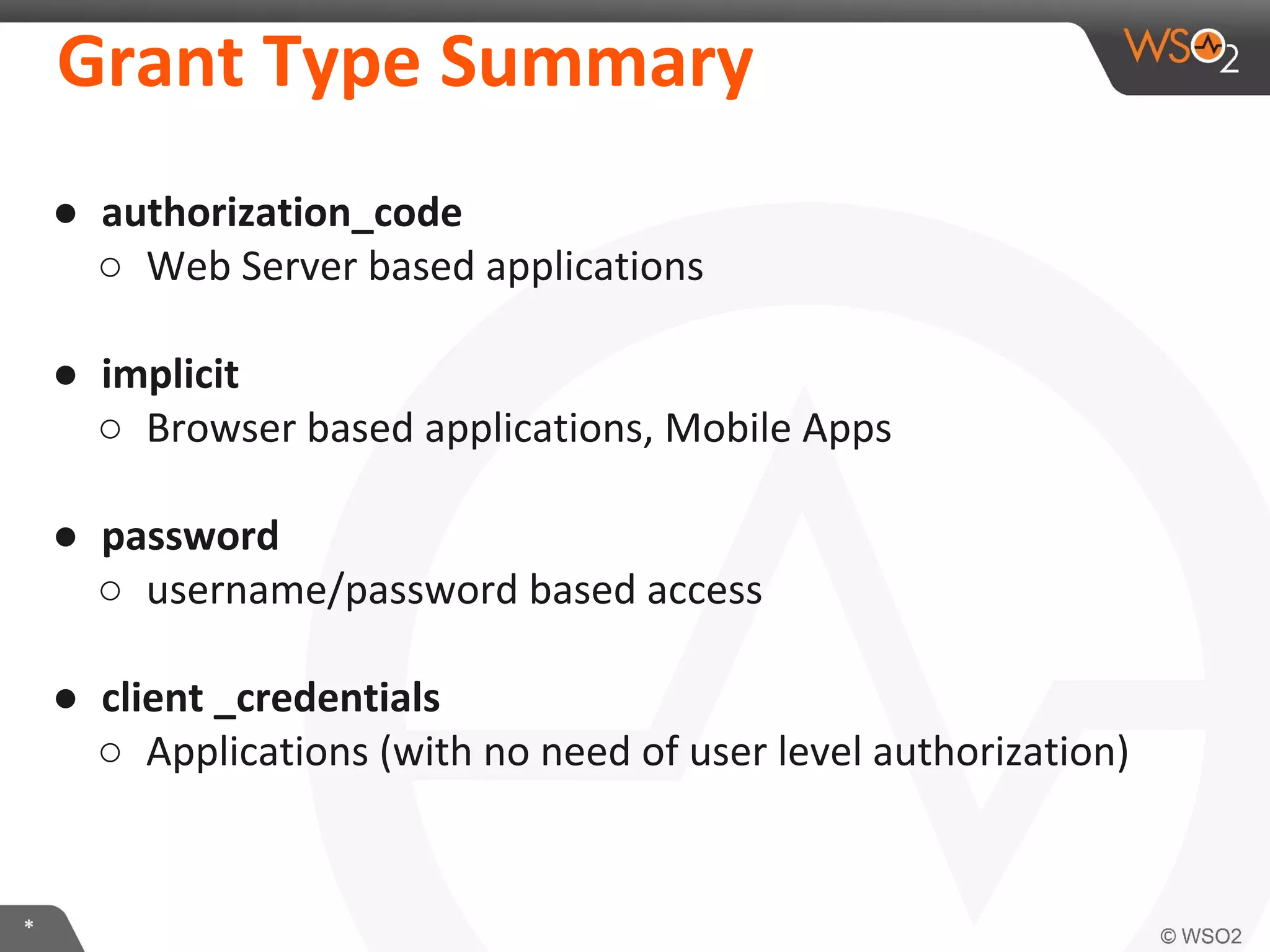
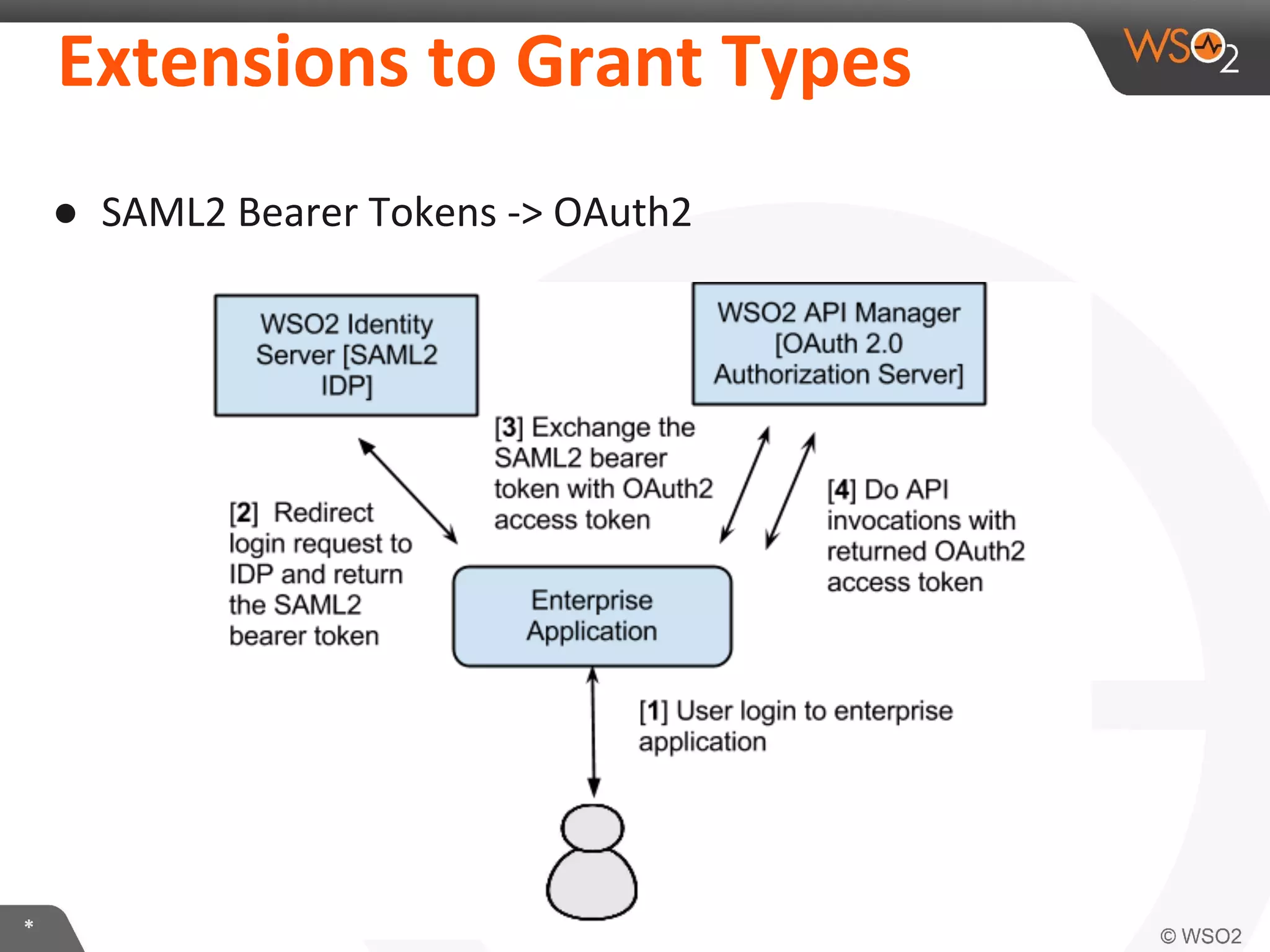
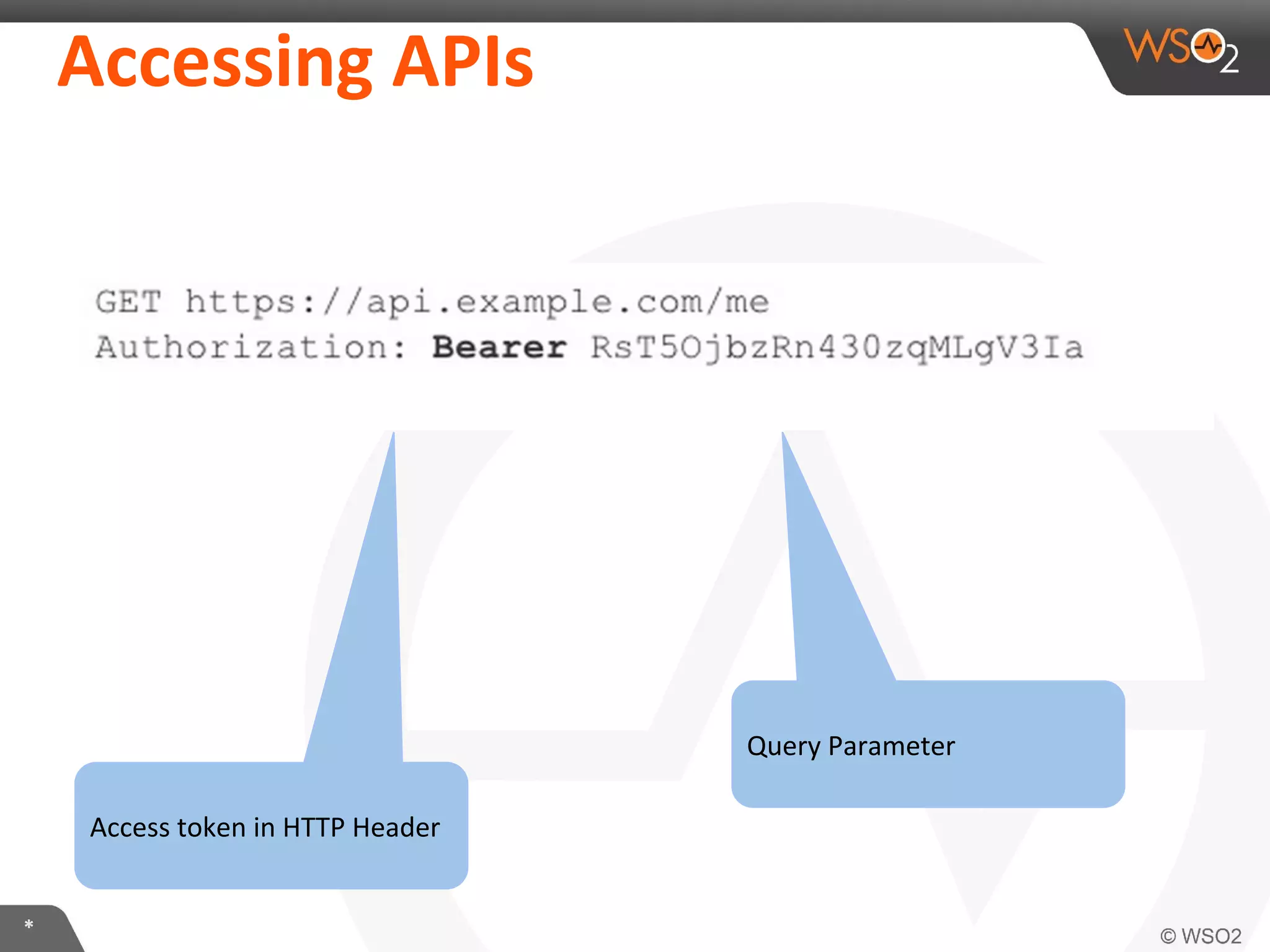
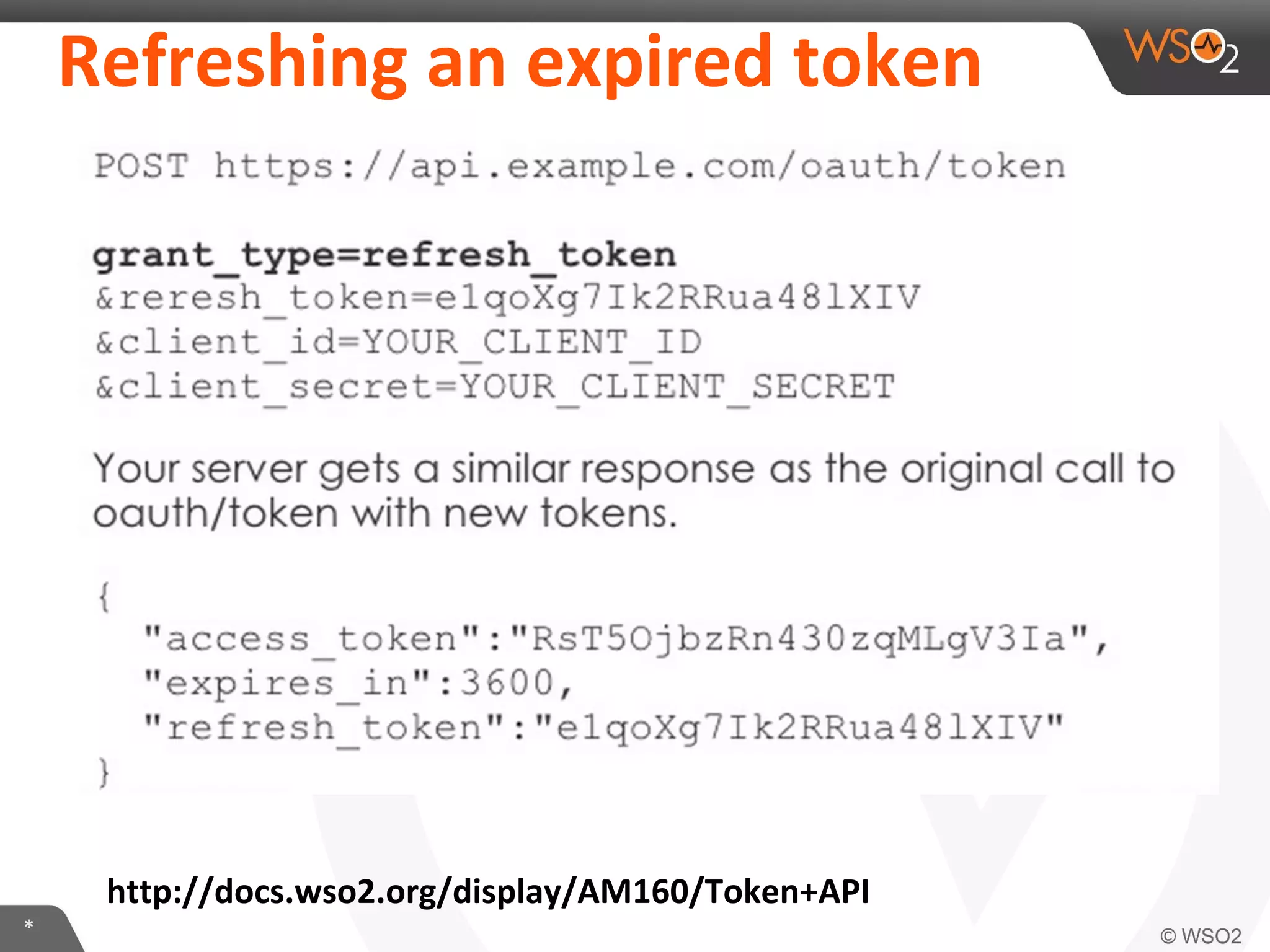
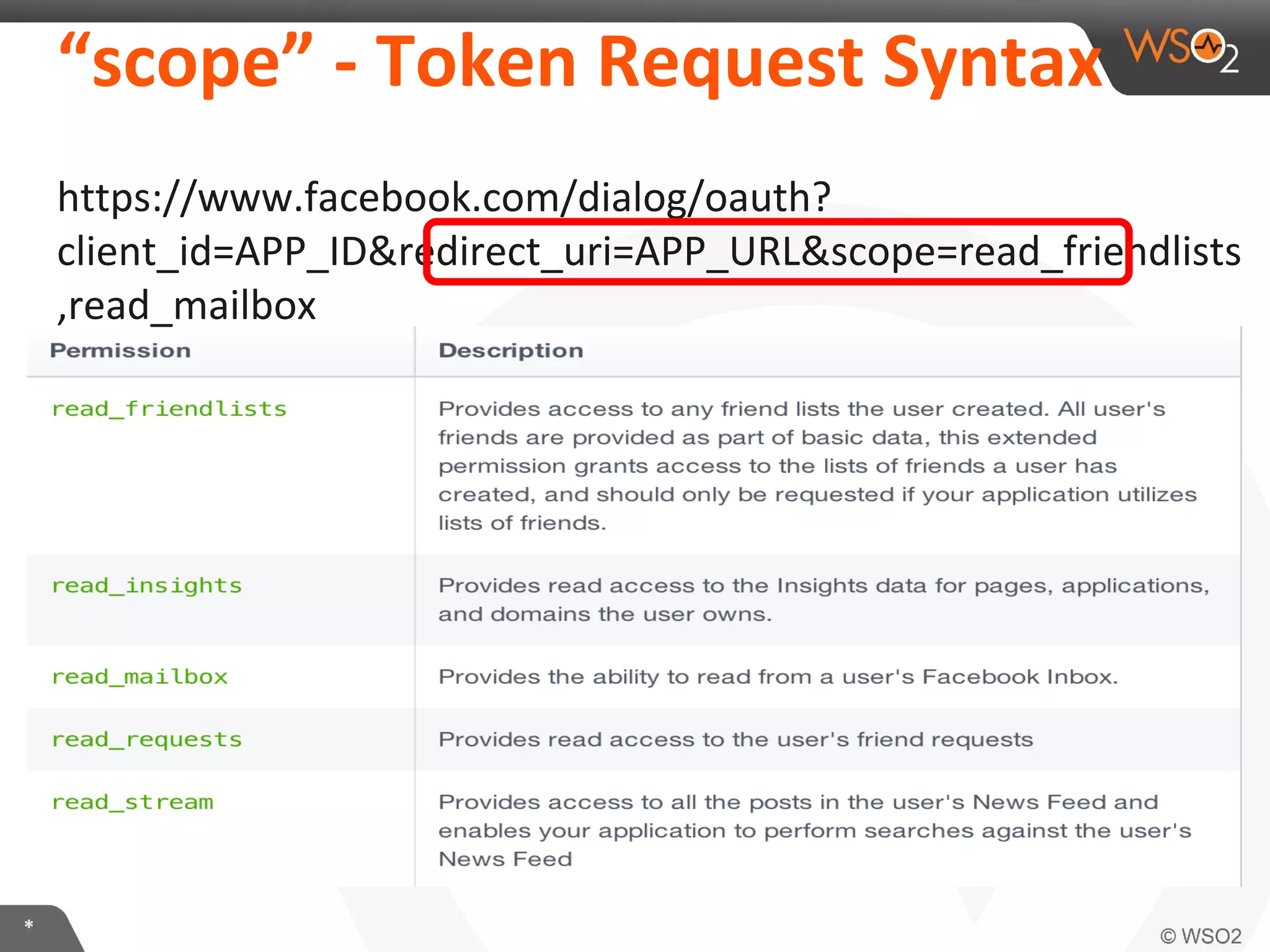
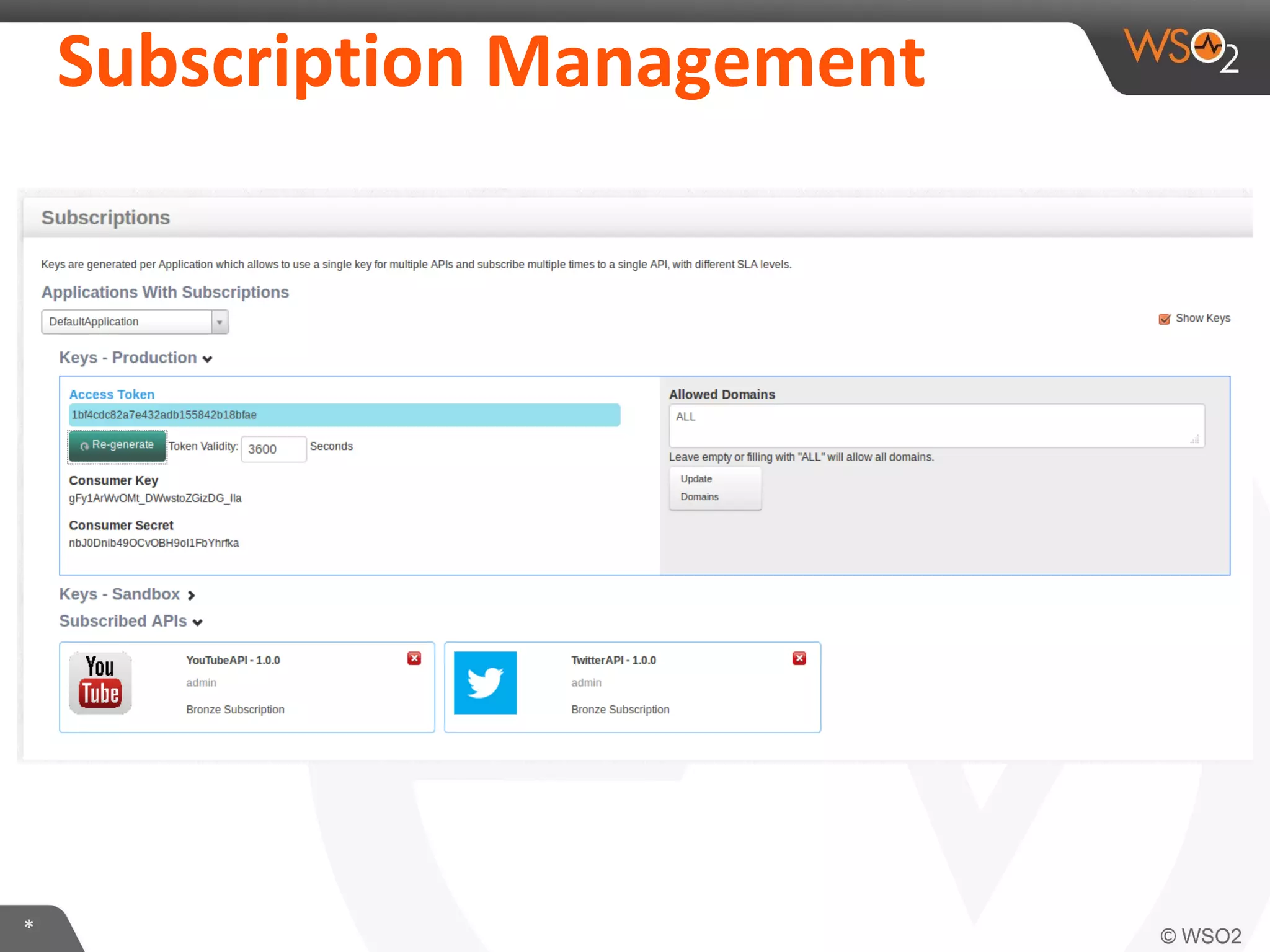
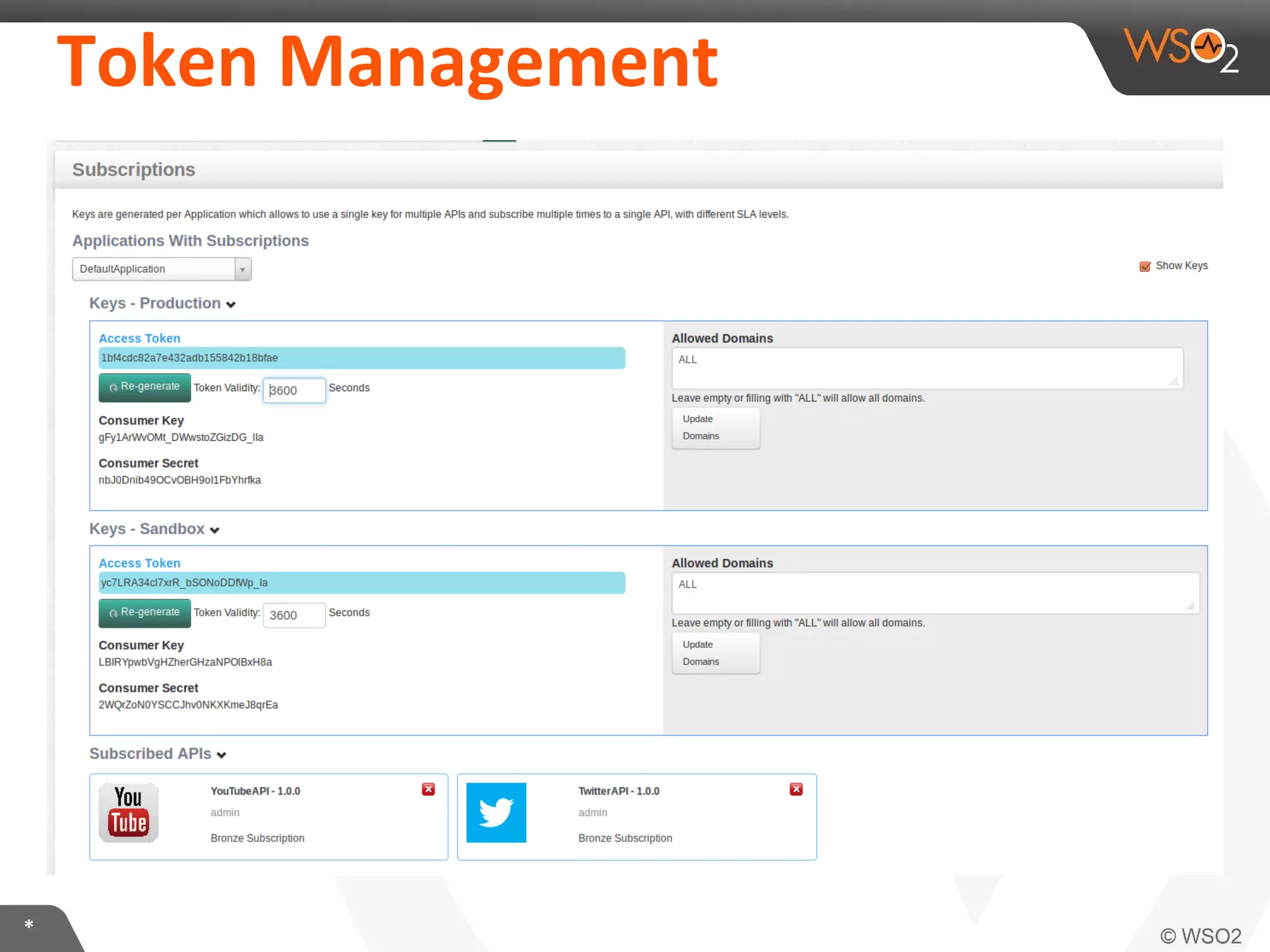
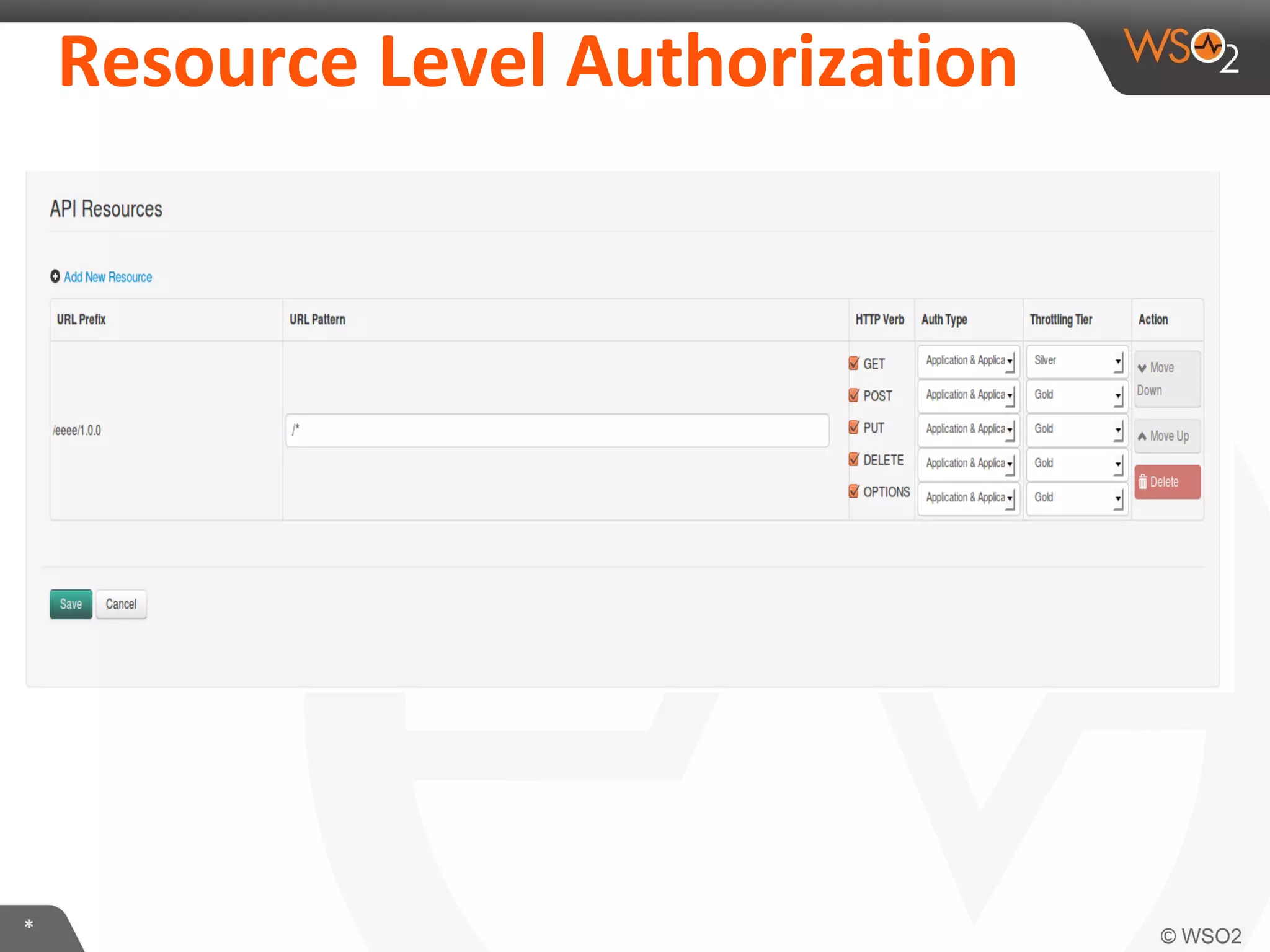
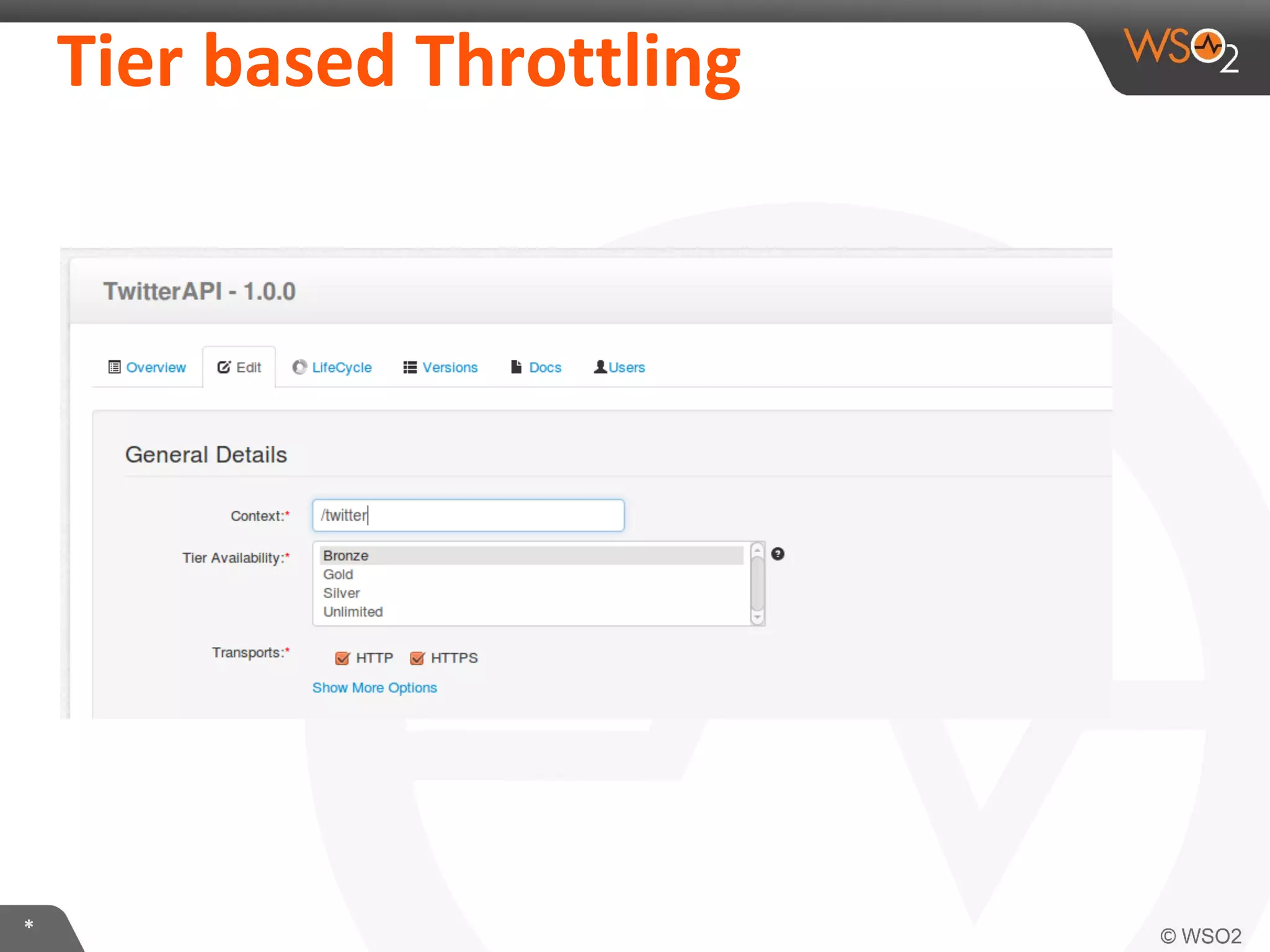
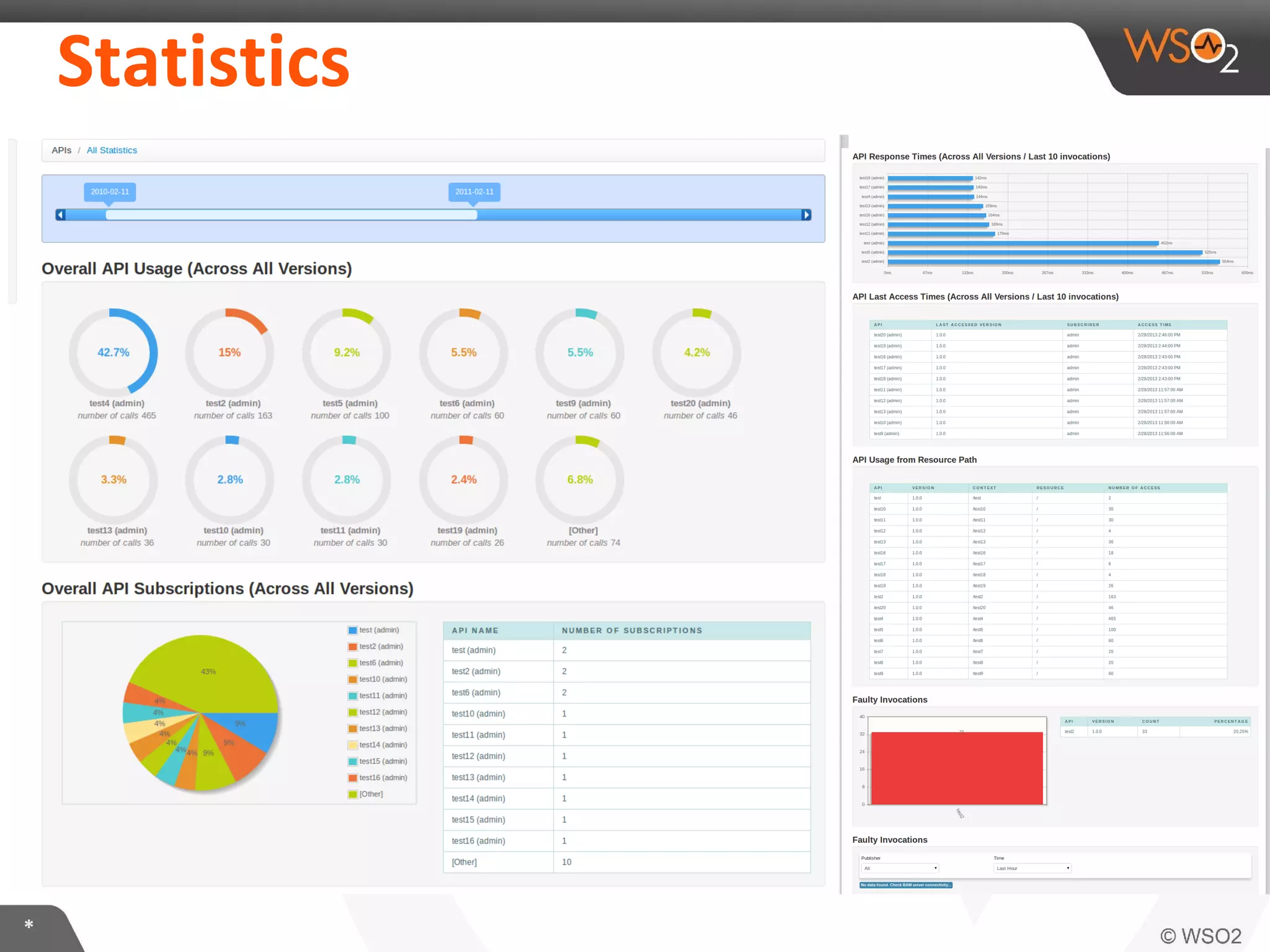
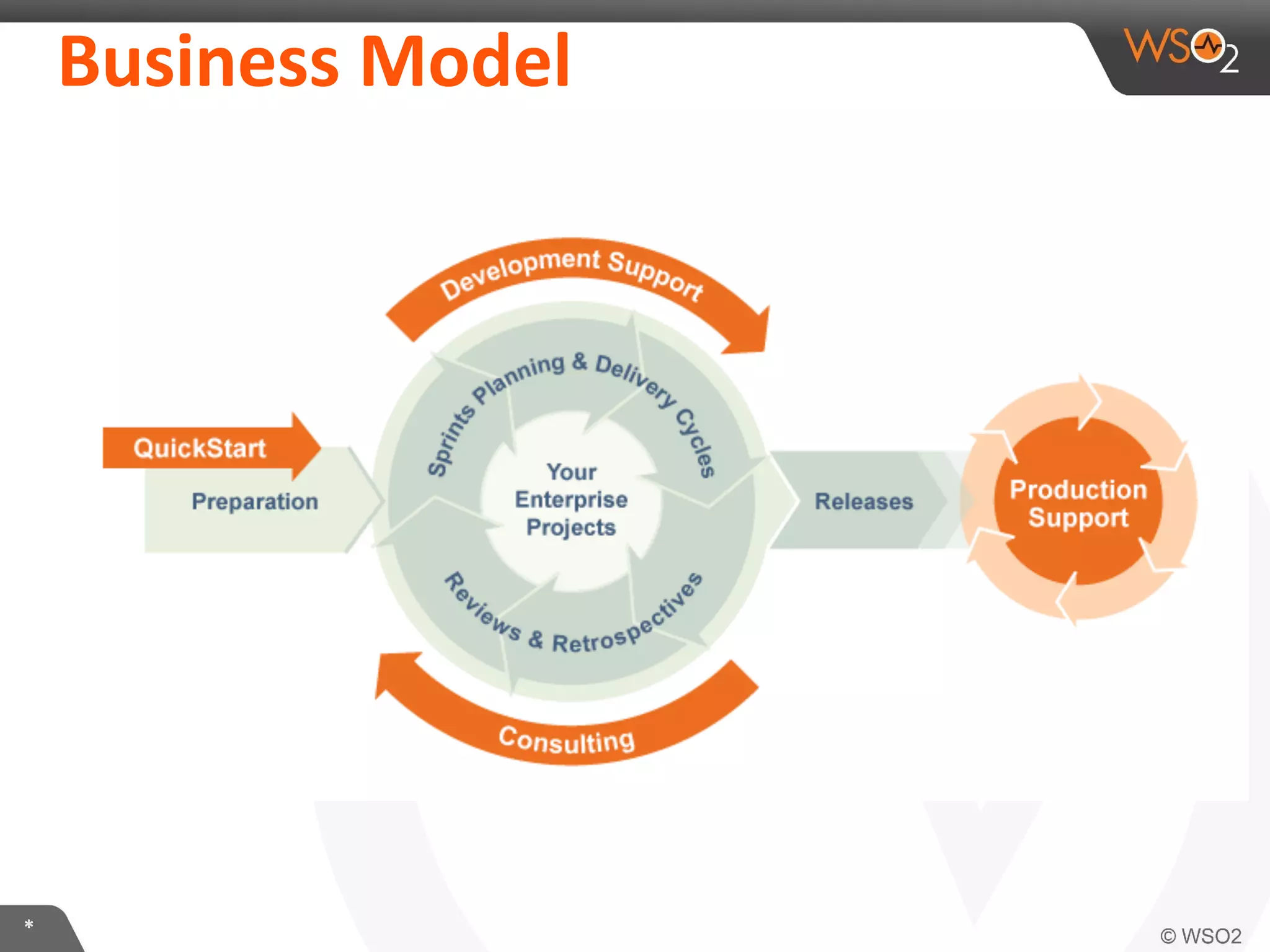
The document discusses OAuth 2.0 and how it is implemented in WSO2 API Manager. It provides an overview of OAuth 2.0 concepts like authorization grants, tokens and flows. It also summarizes how WSO2 supports the OAuth 2.0 framework for API management, including token management and authorization code, implicit and password grants. Extensions to OAuth 2.0 in WSO2 API Manager are also briefly covered.