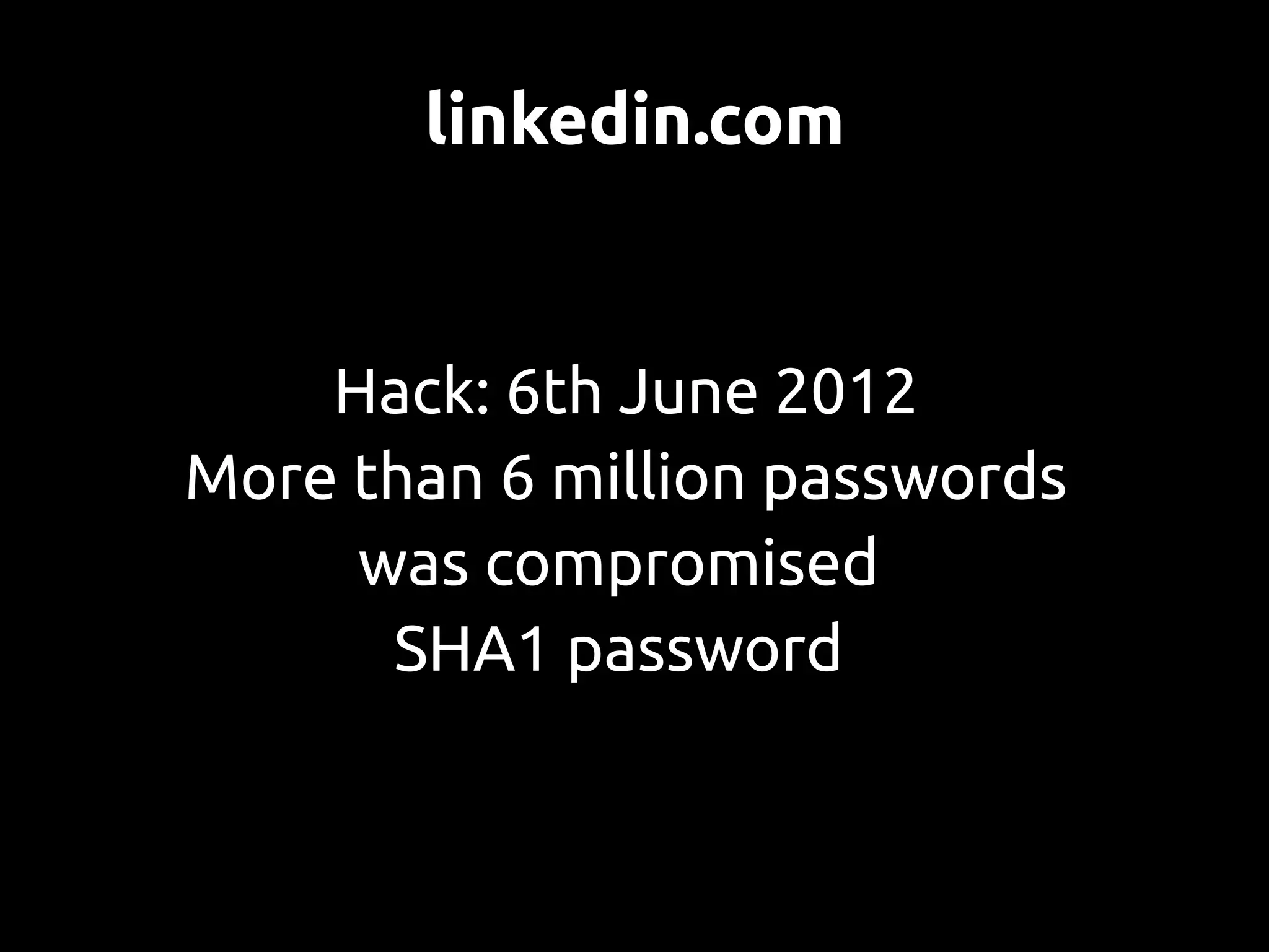
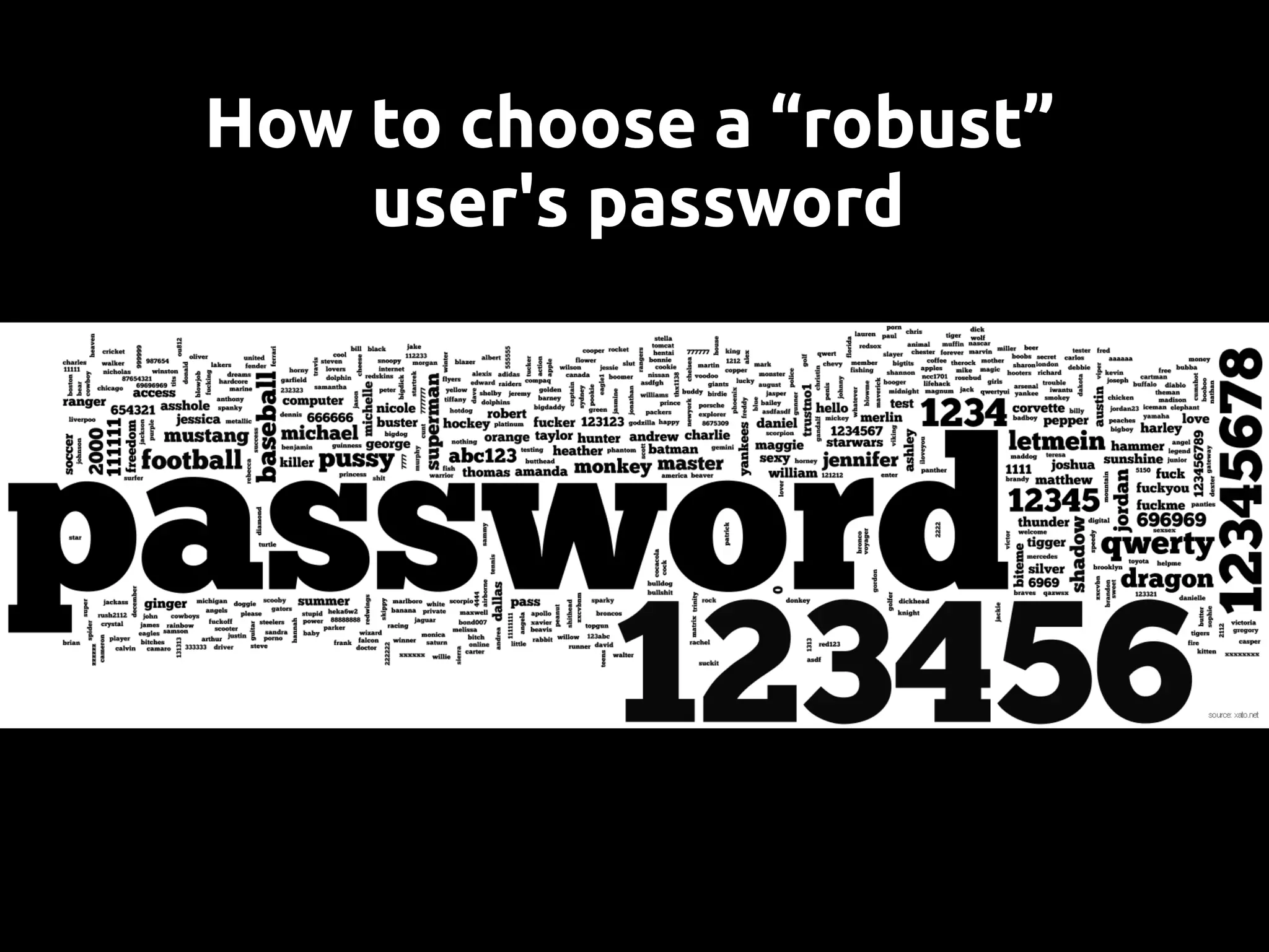
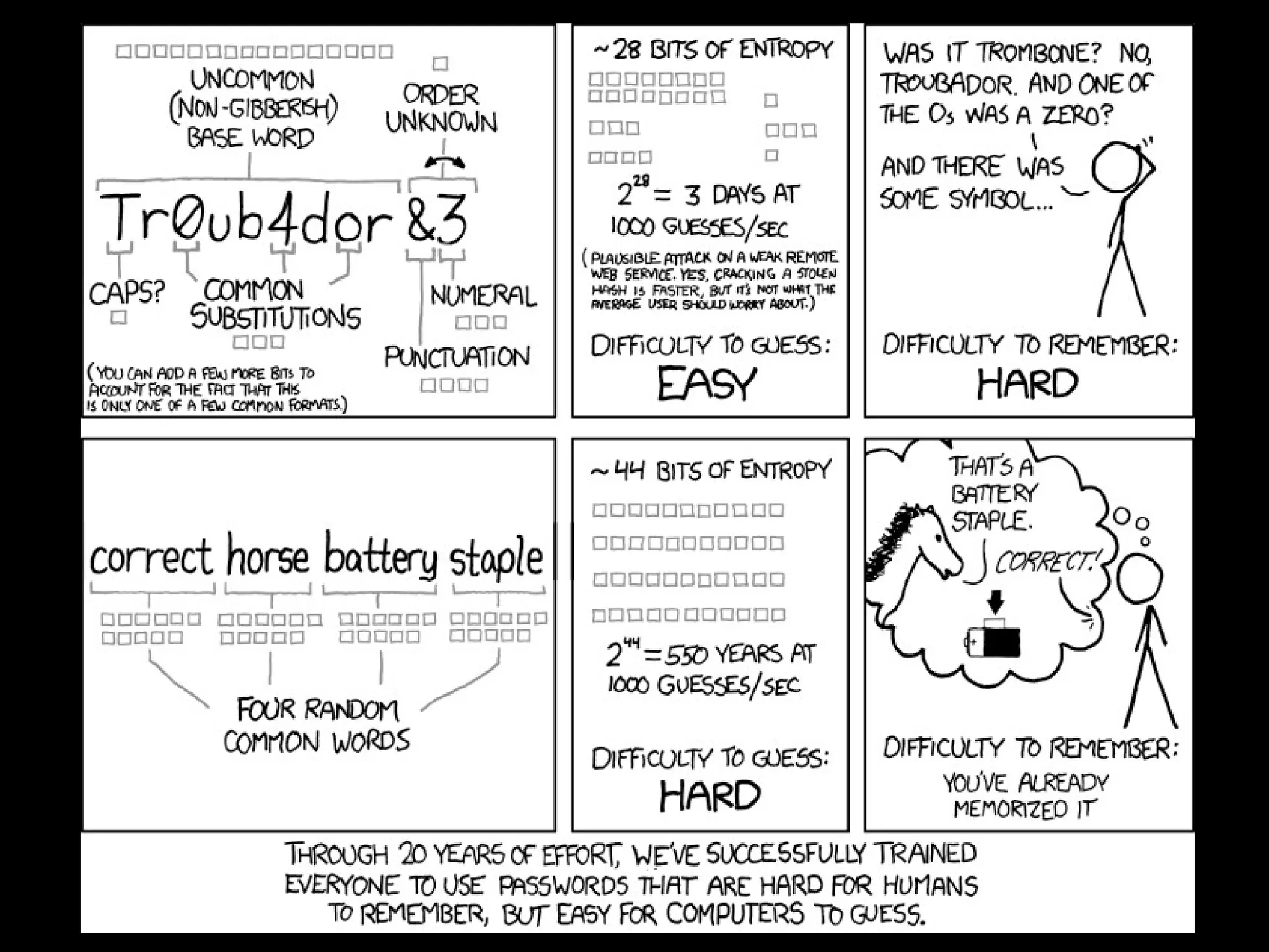
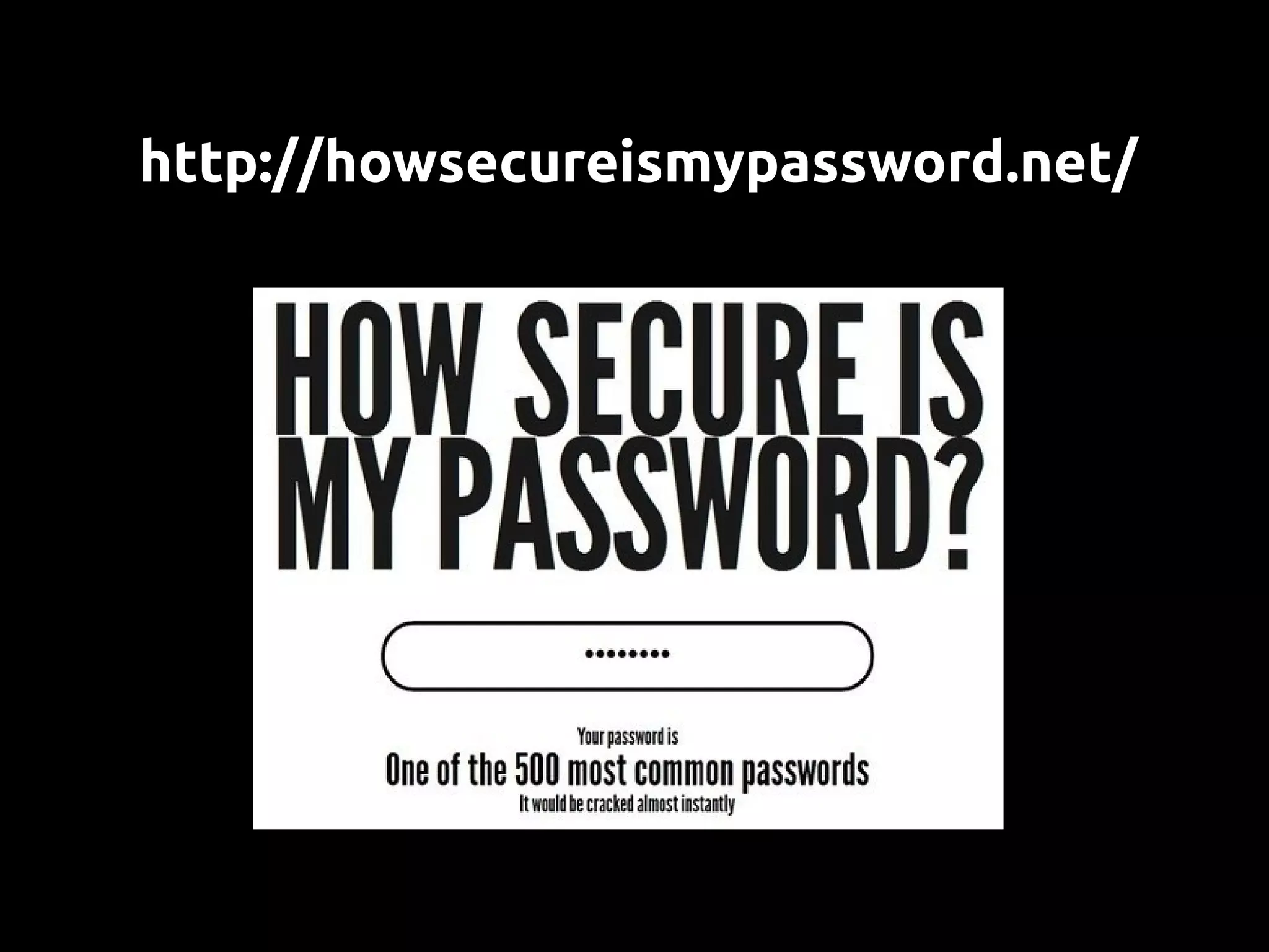
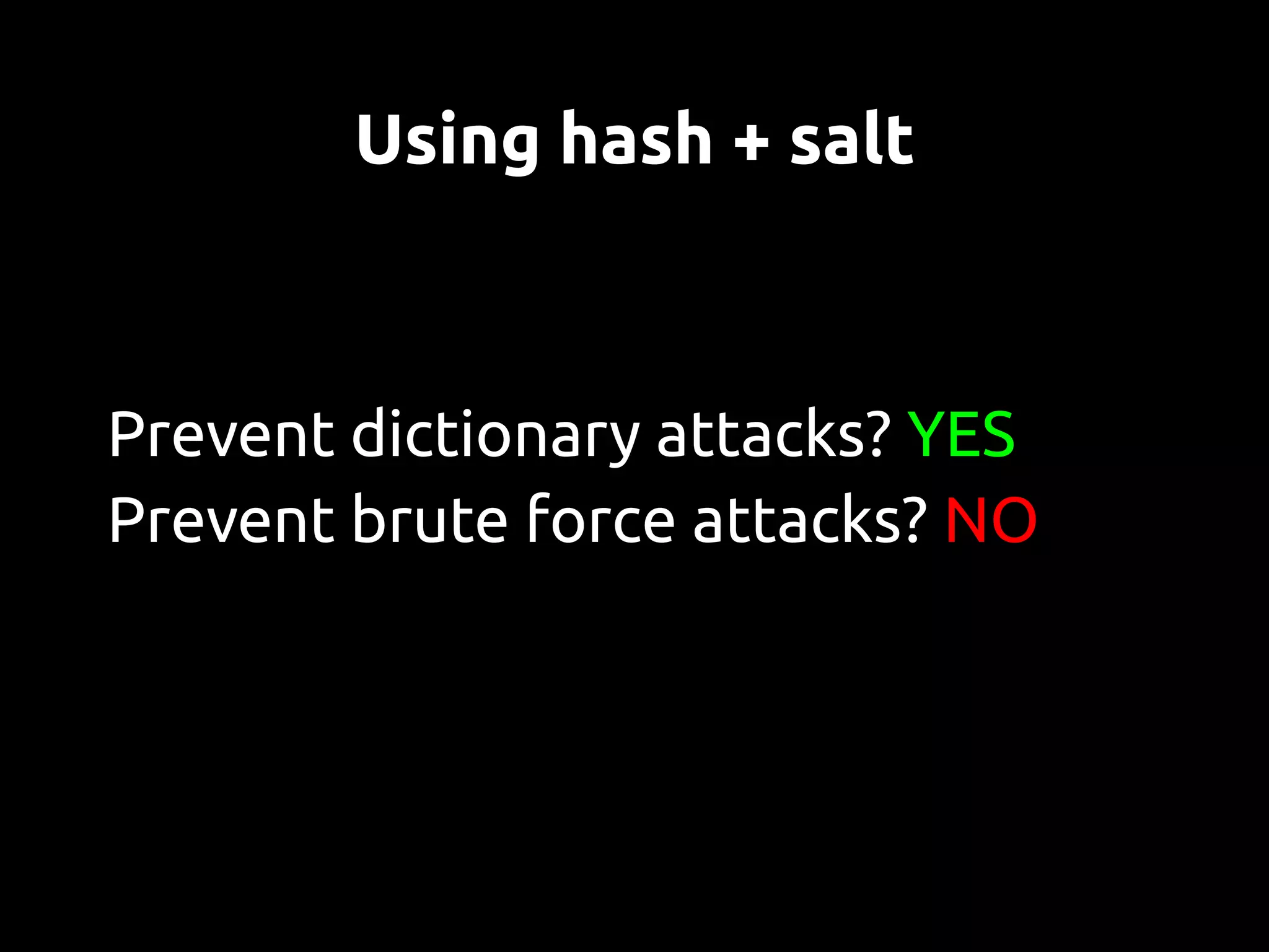
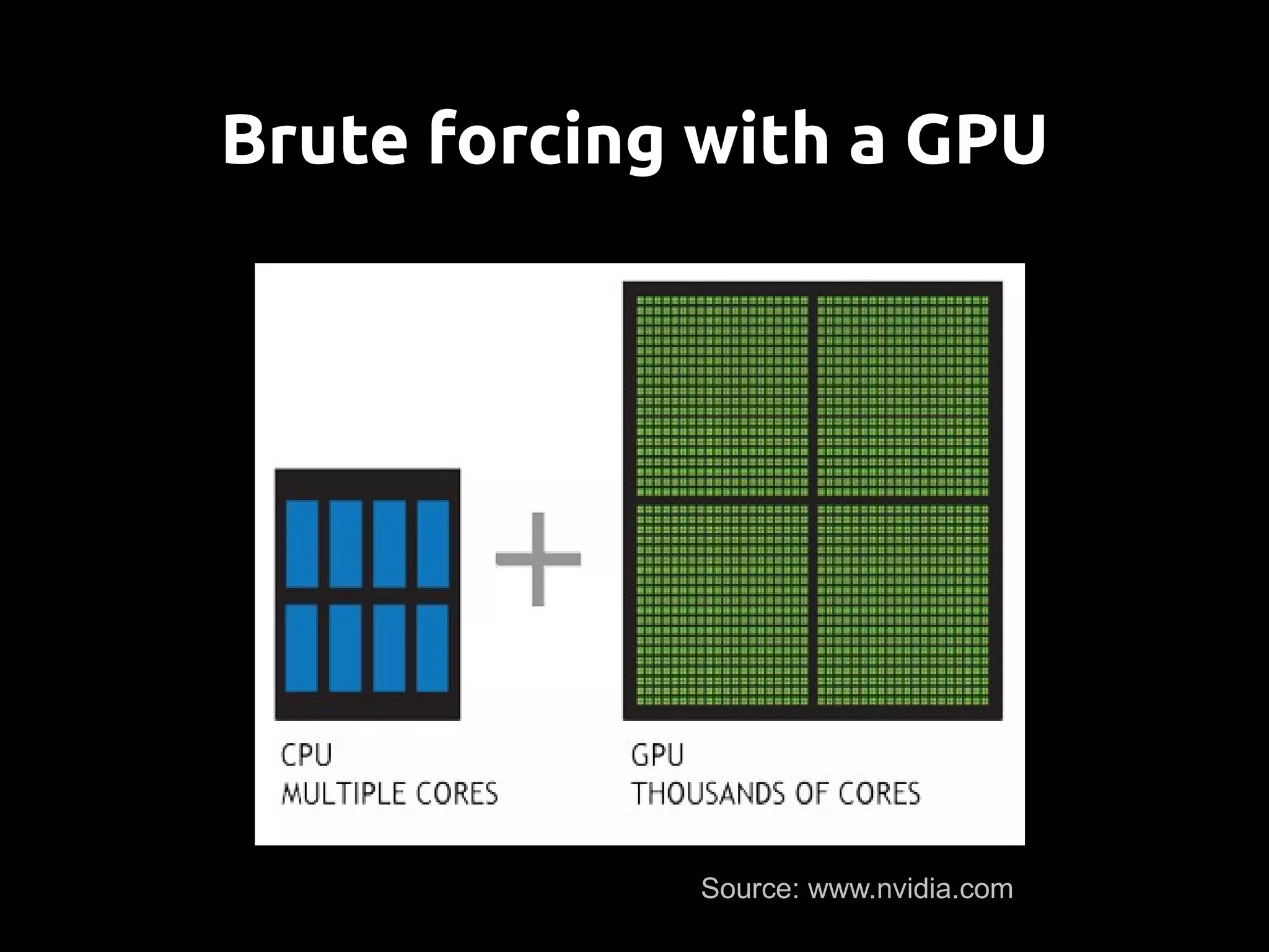
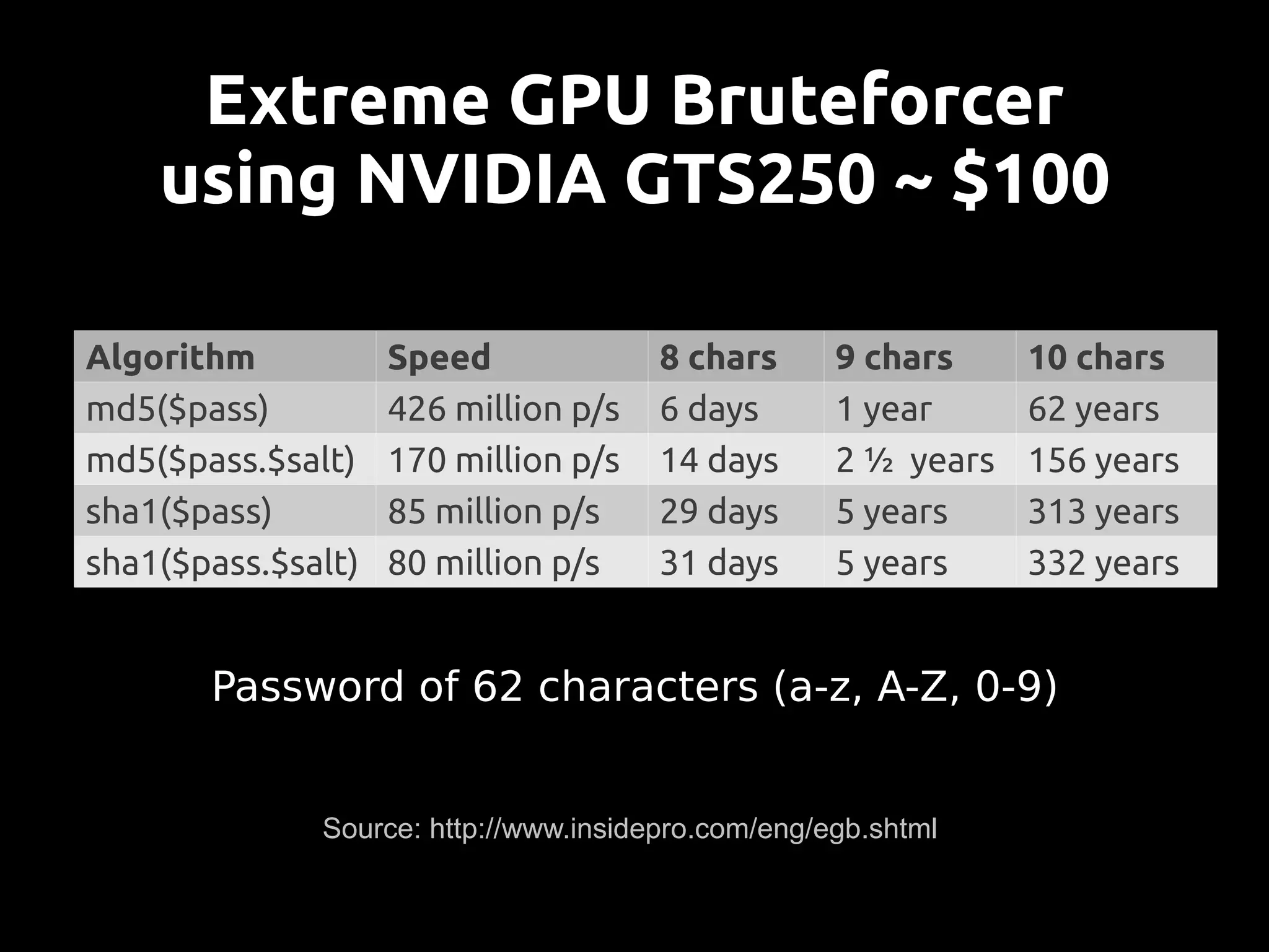
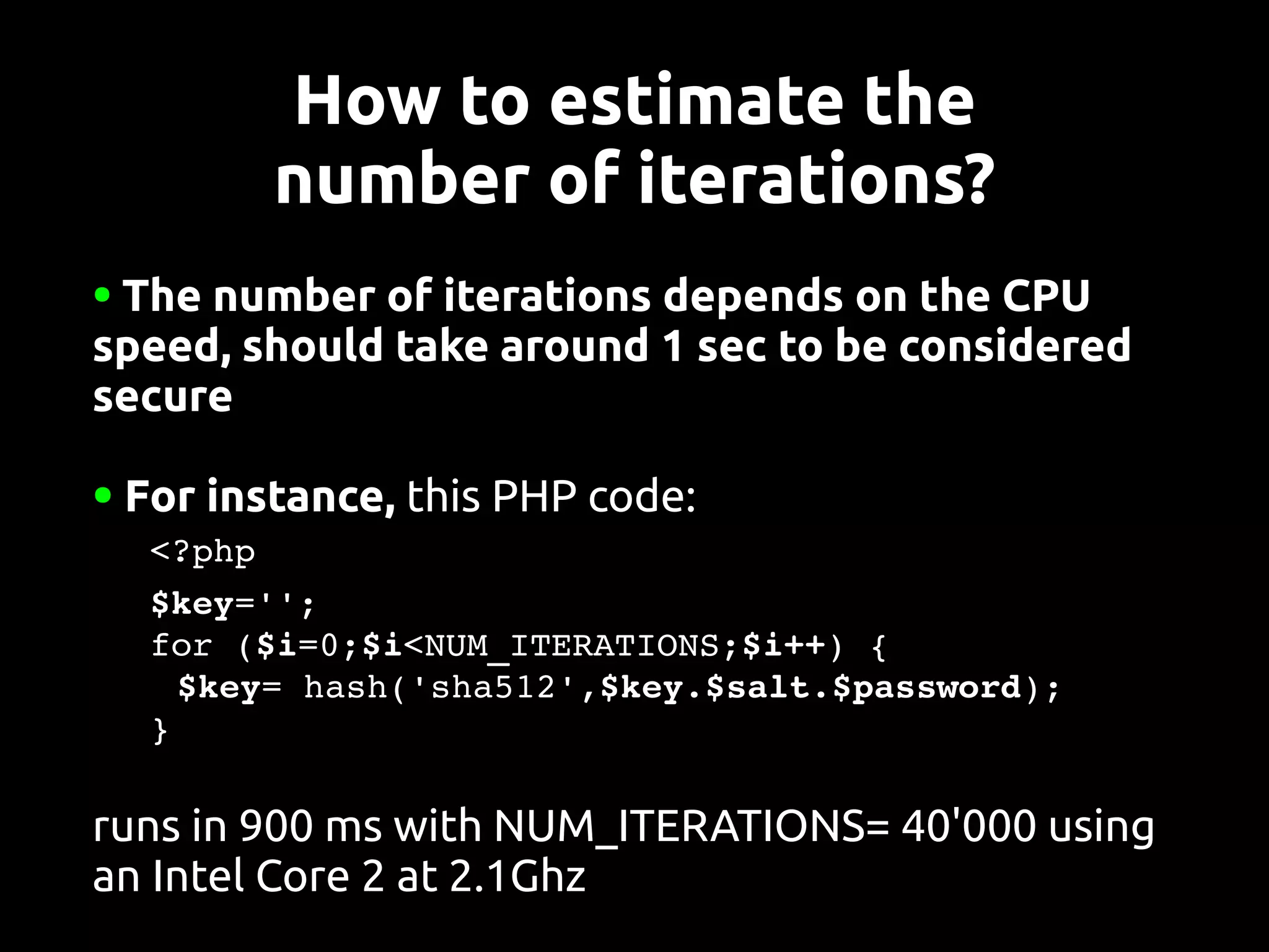
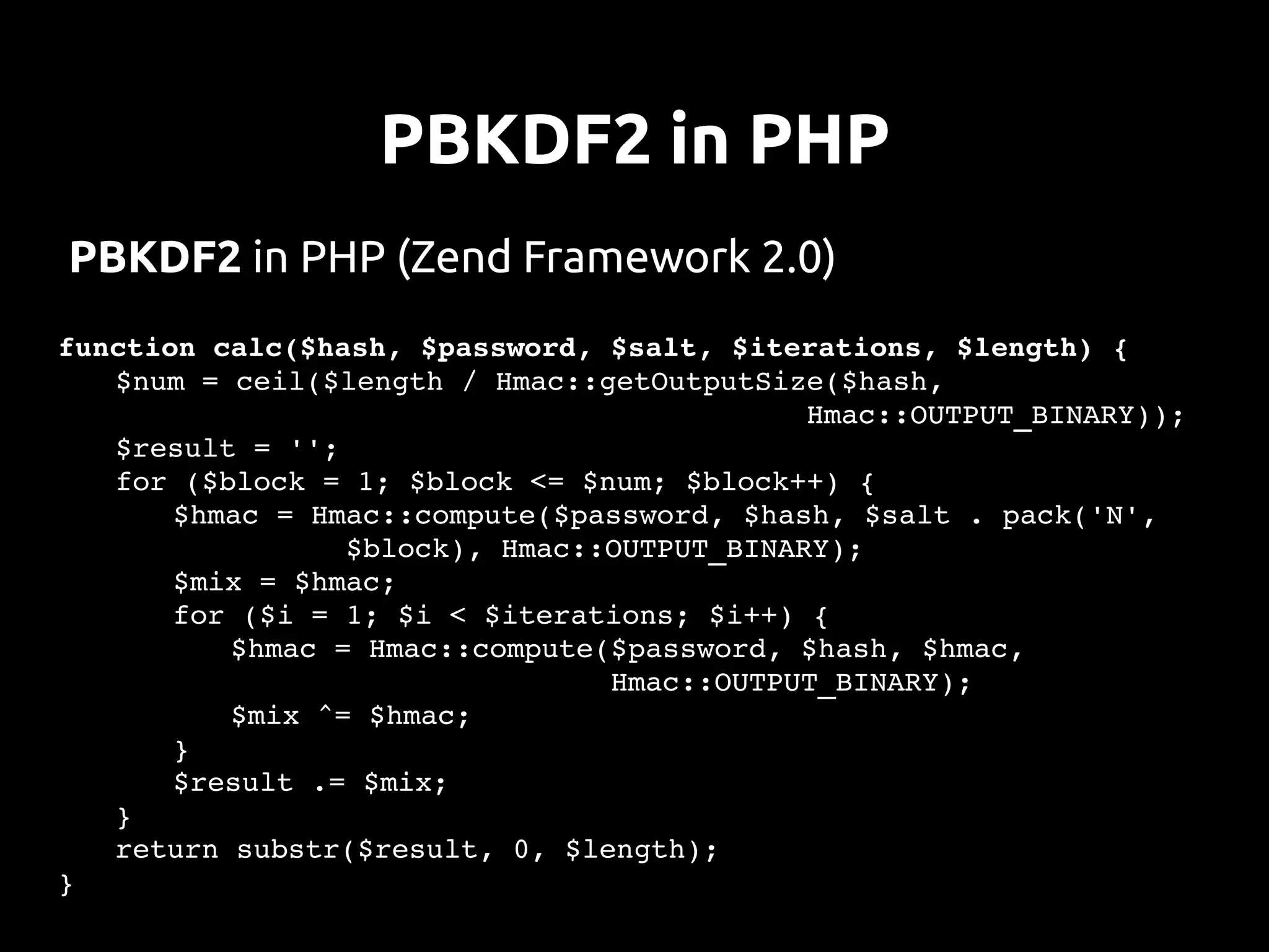
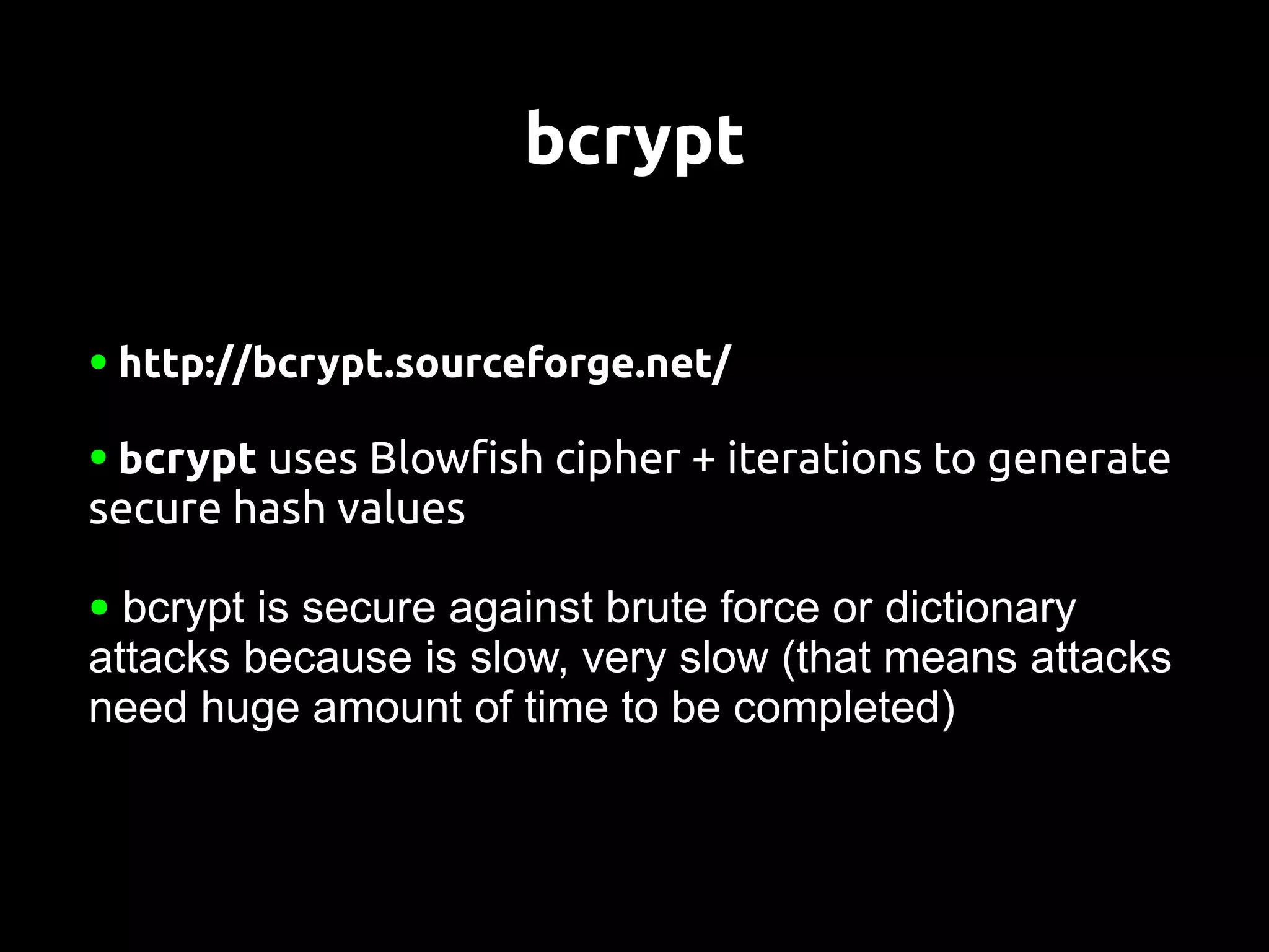
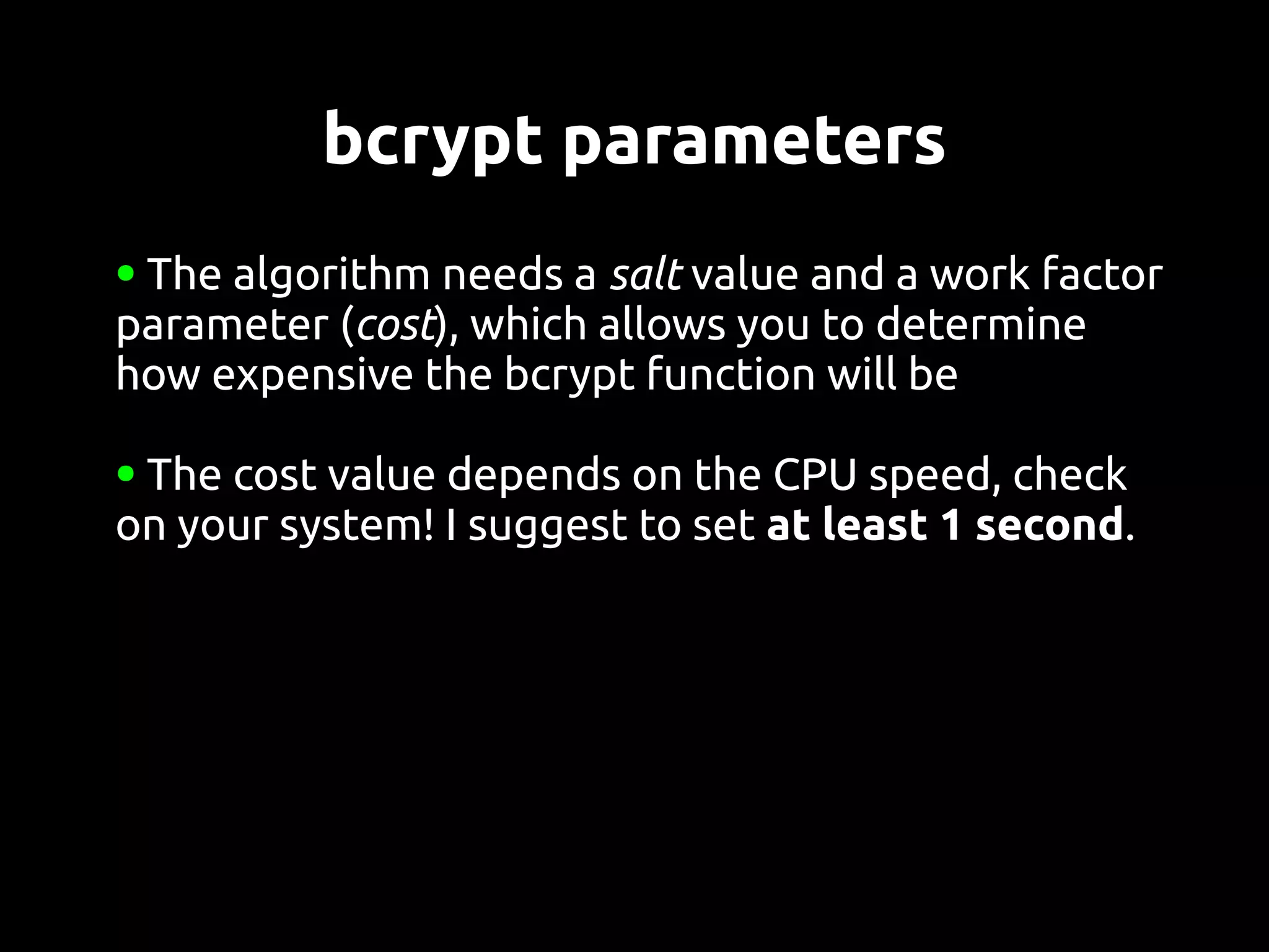
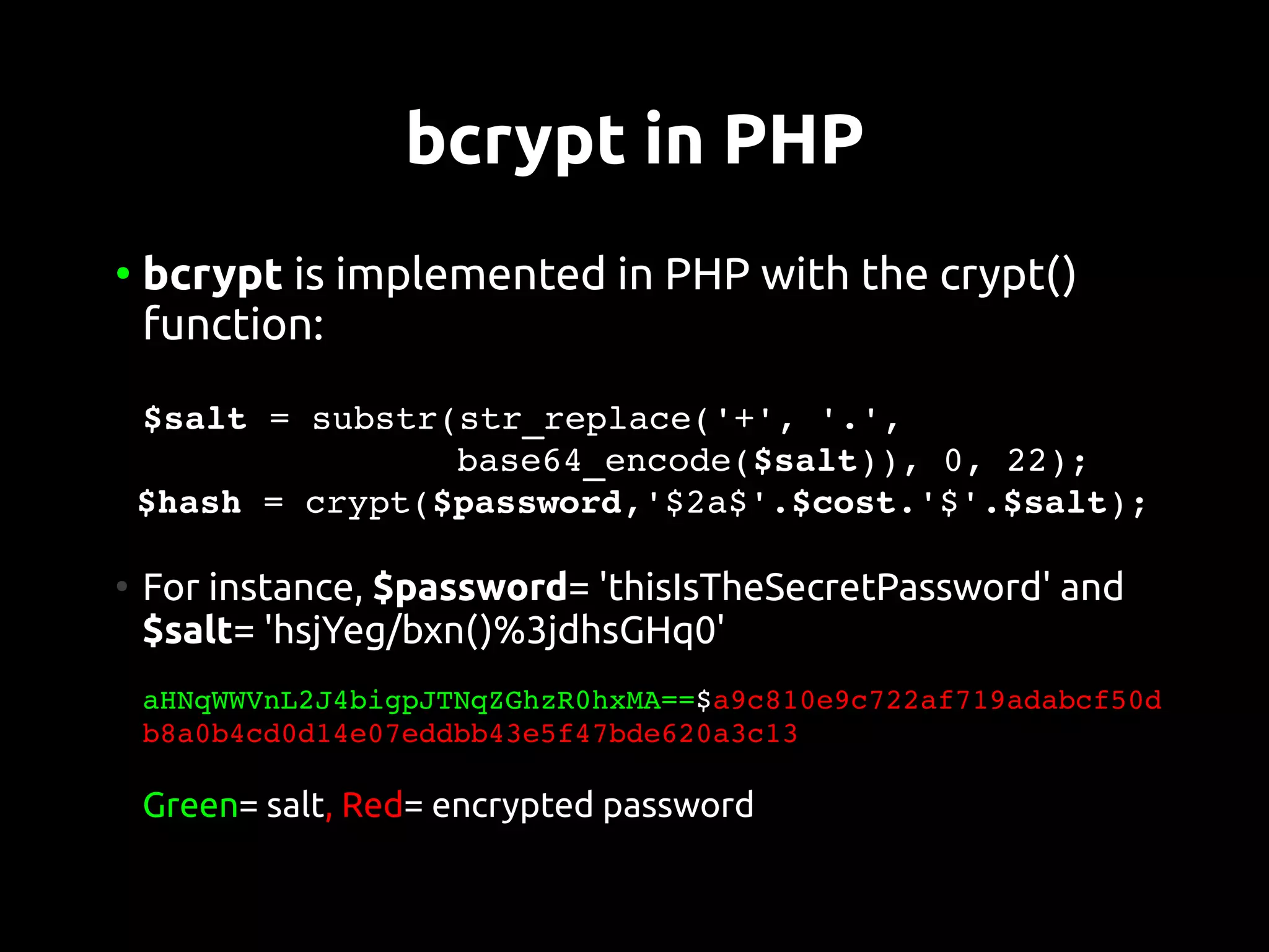
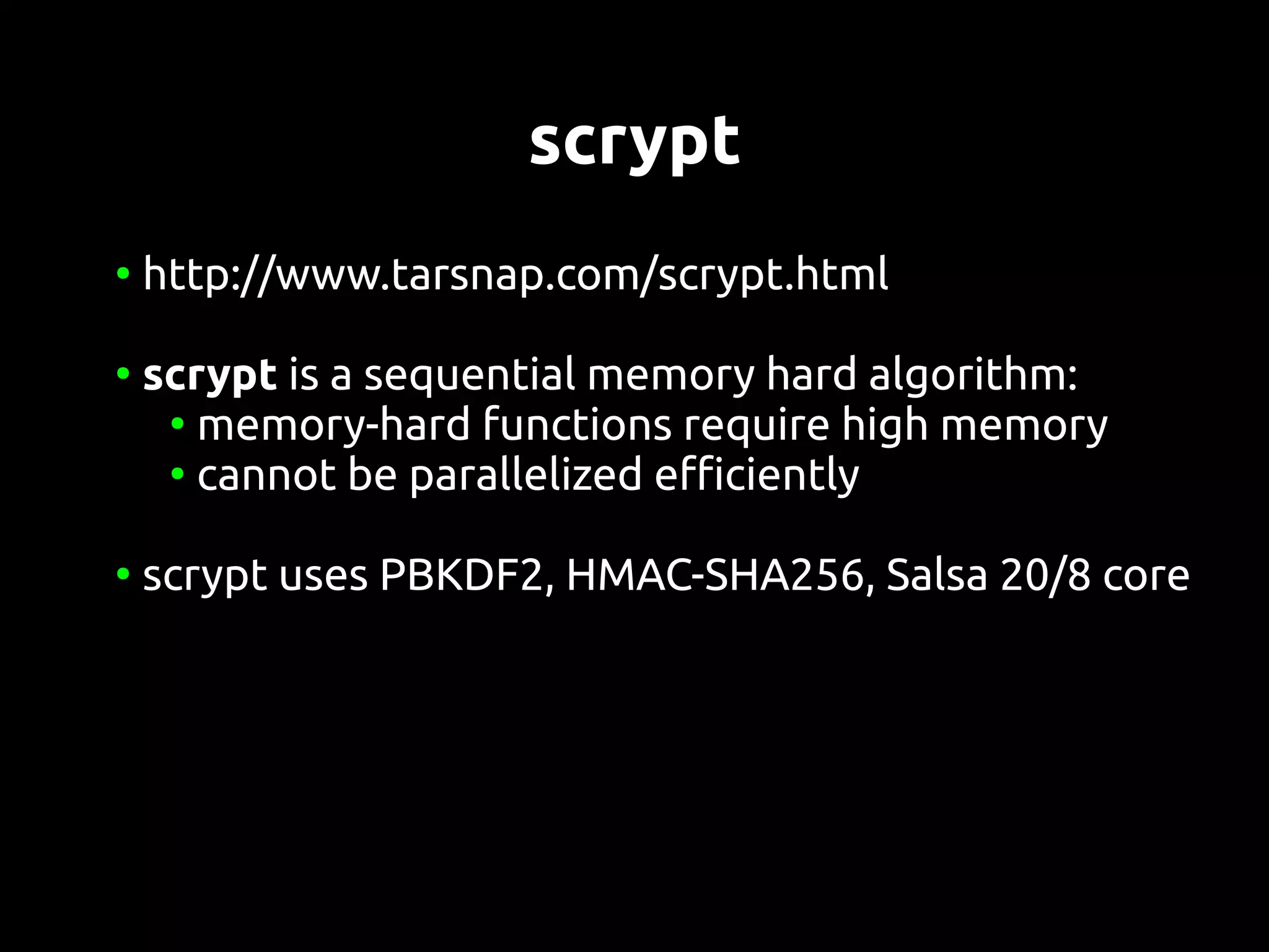
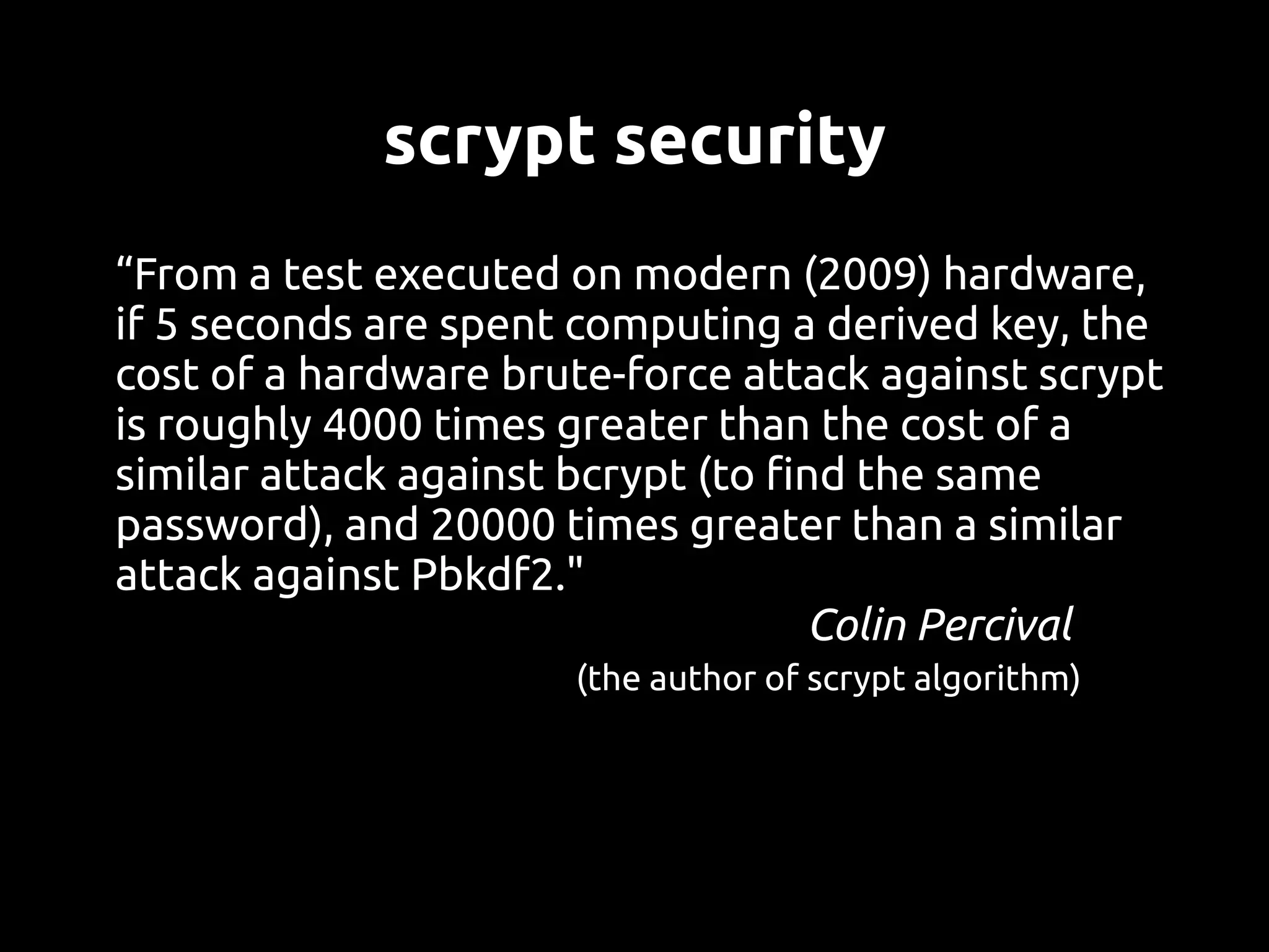
This document discusses password security from both user and developer perspectives, providing guidelines on creating and securely storing passwords. It stresses the importance of using robust passwords, such as long pass phrases, and recommends advanced hashing techniques like PBKDF2, bcrypt, and scrypt for developers. Moreover, it highlights the shortcomings of outdated methods, such as MD5 and SHA1, in protecting against modern brute force attacks.