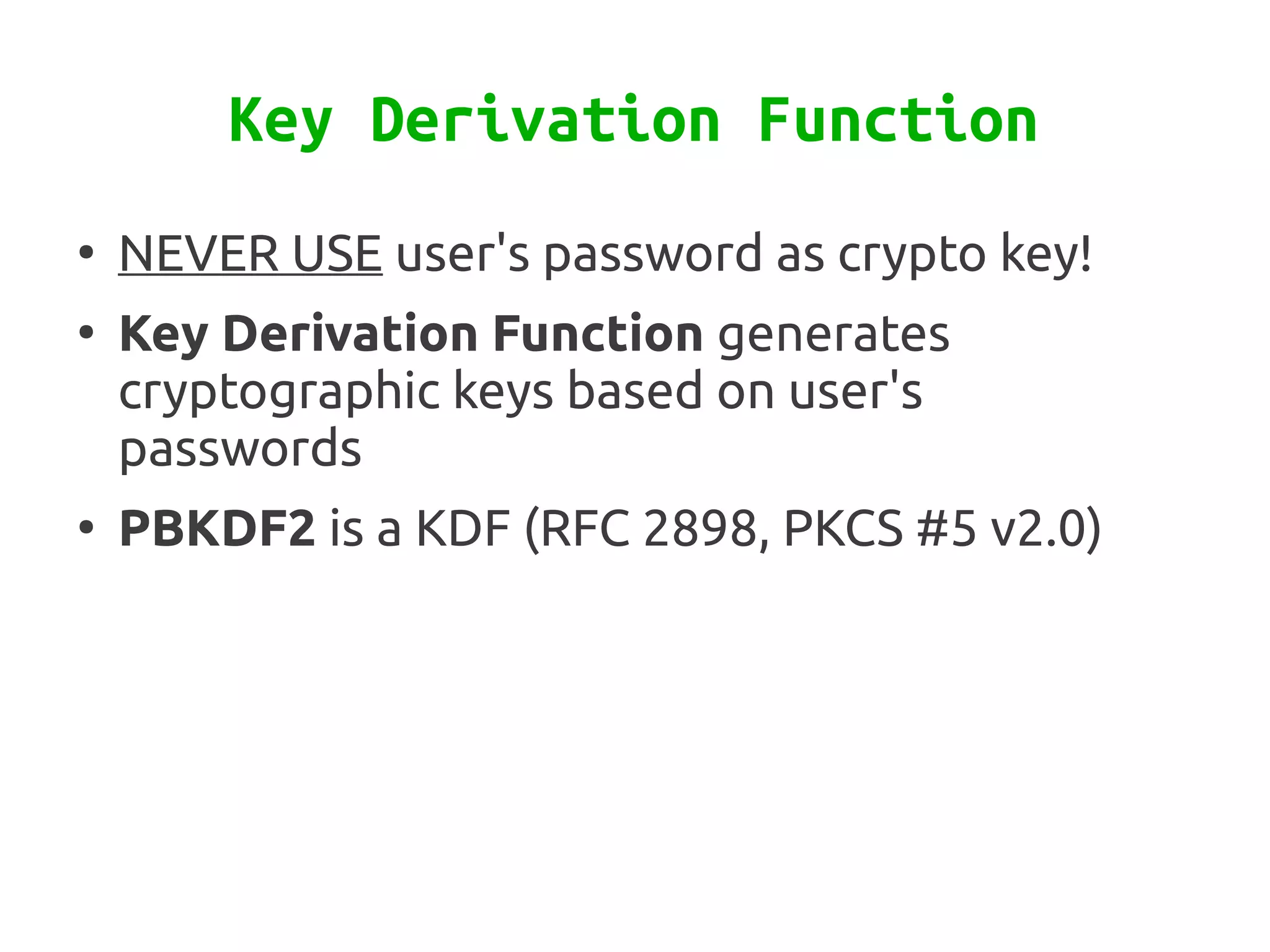
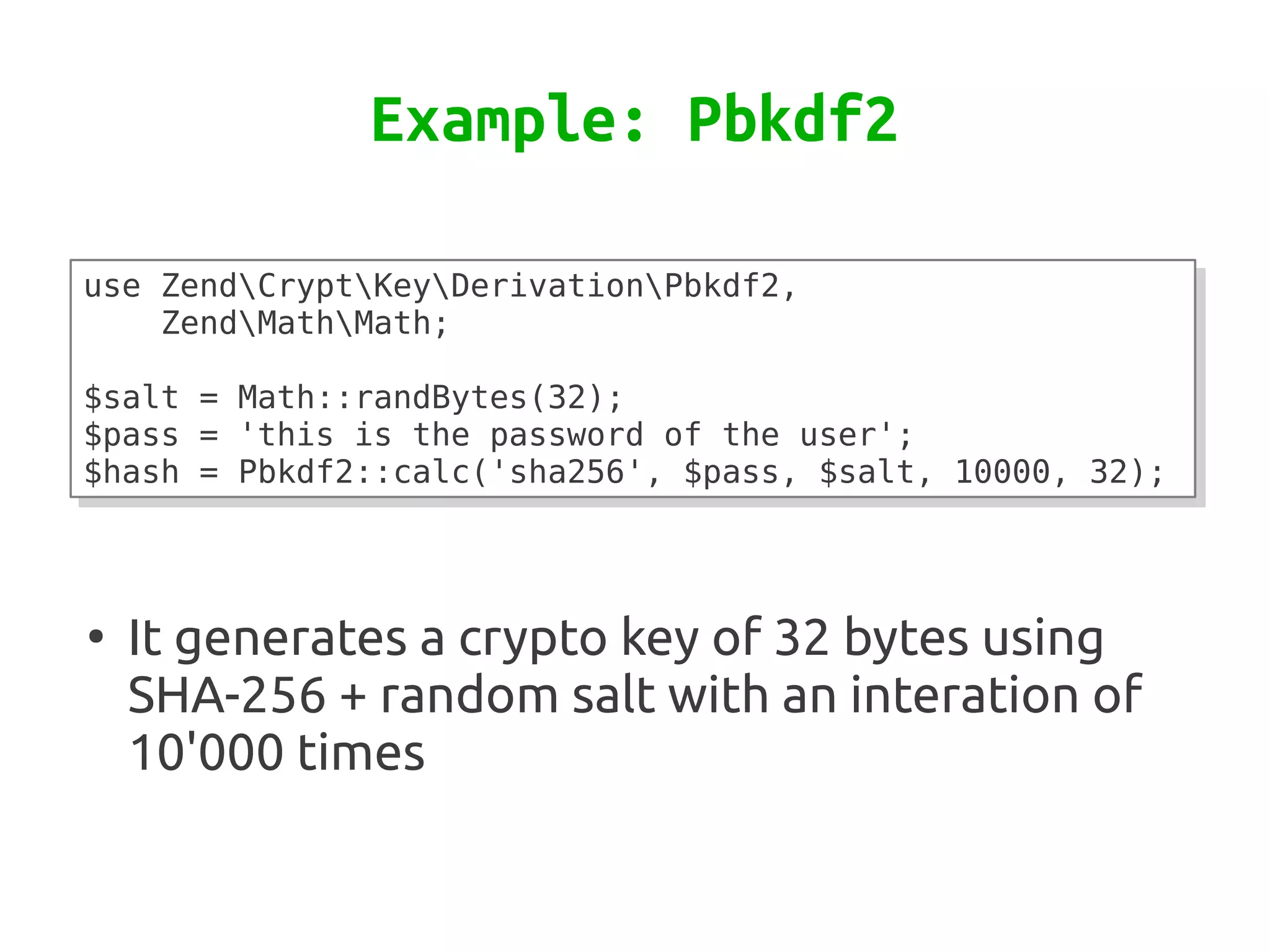
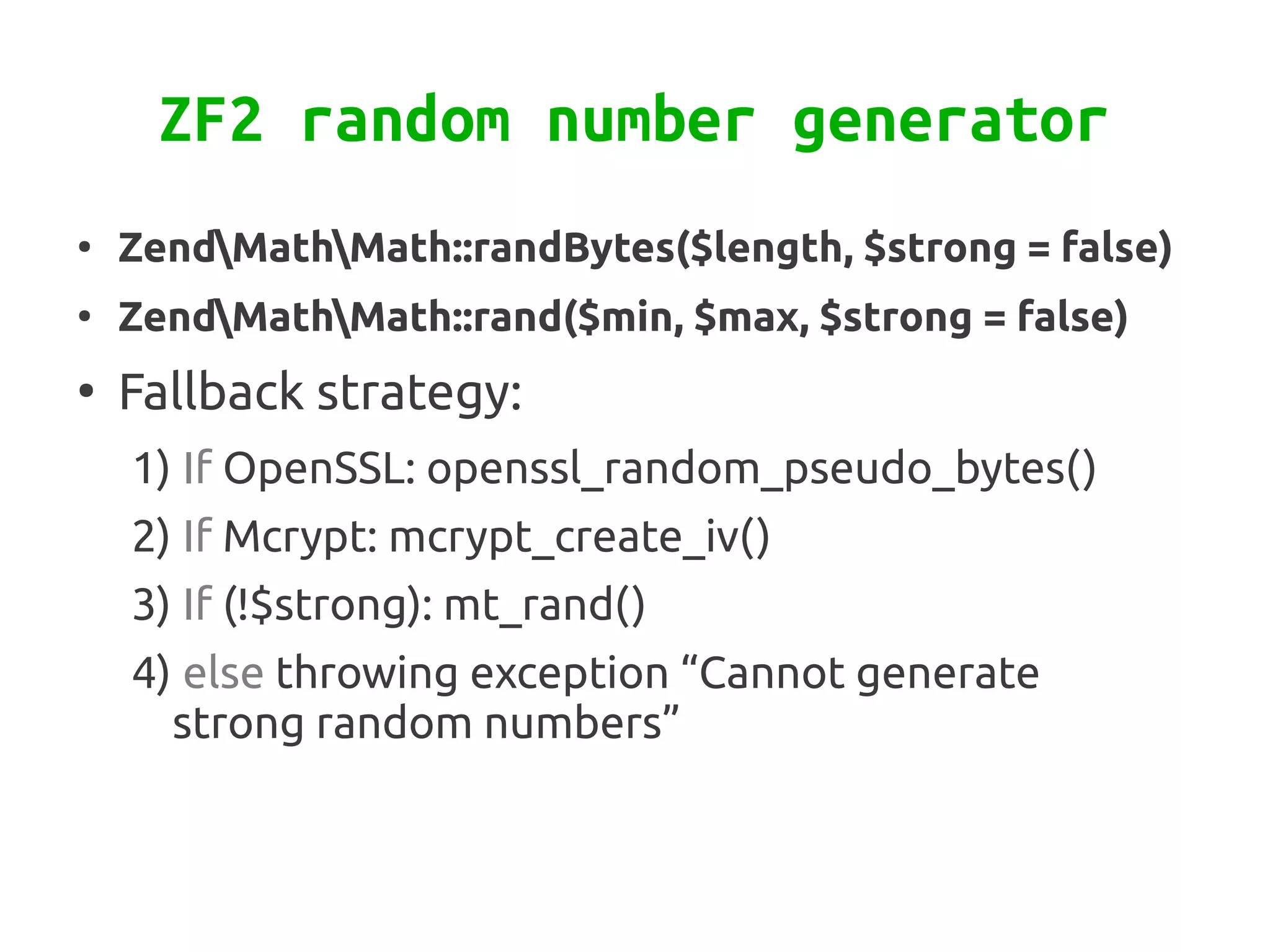
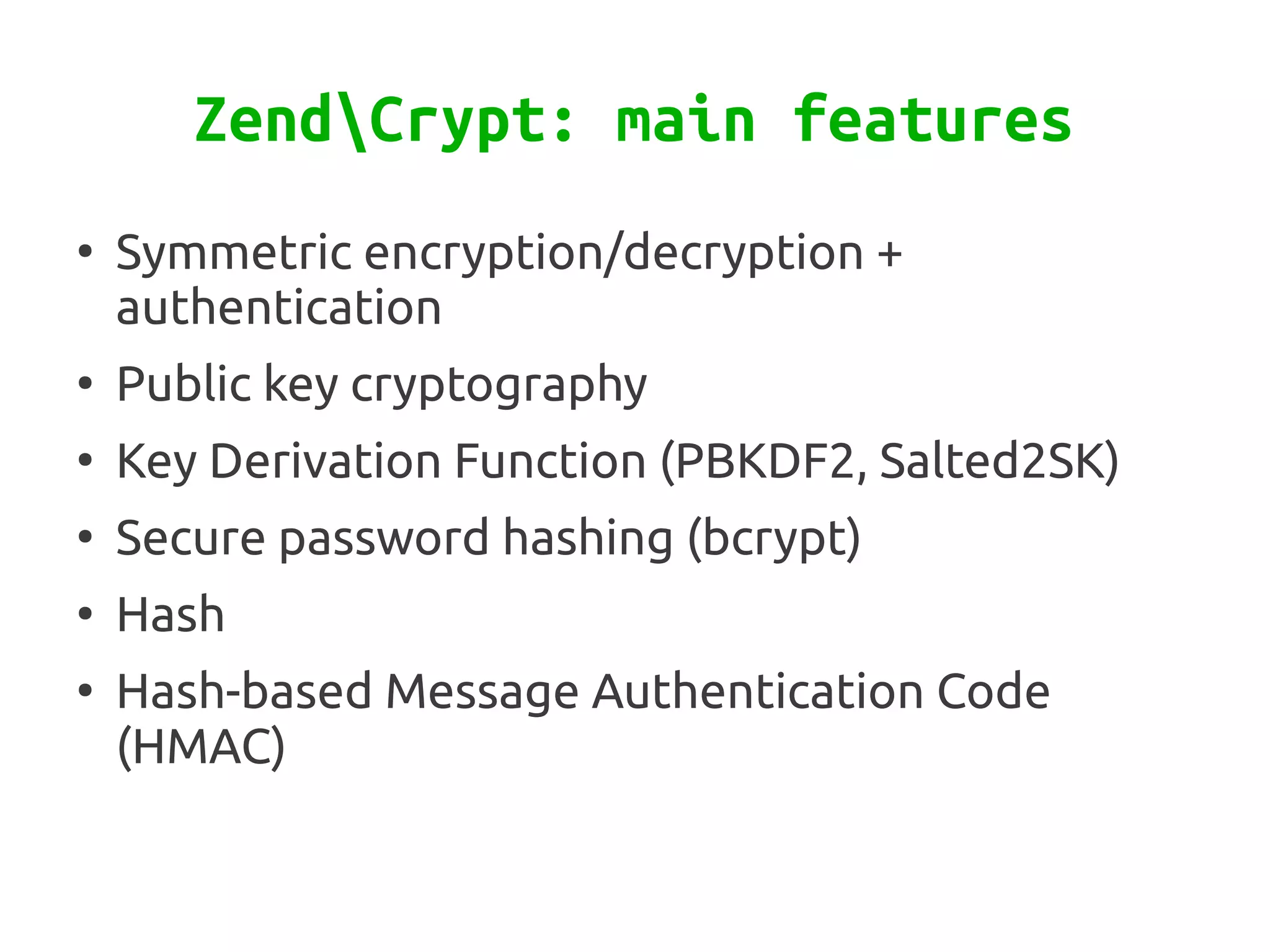
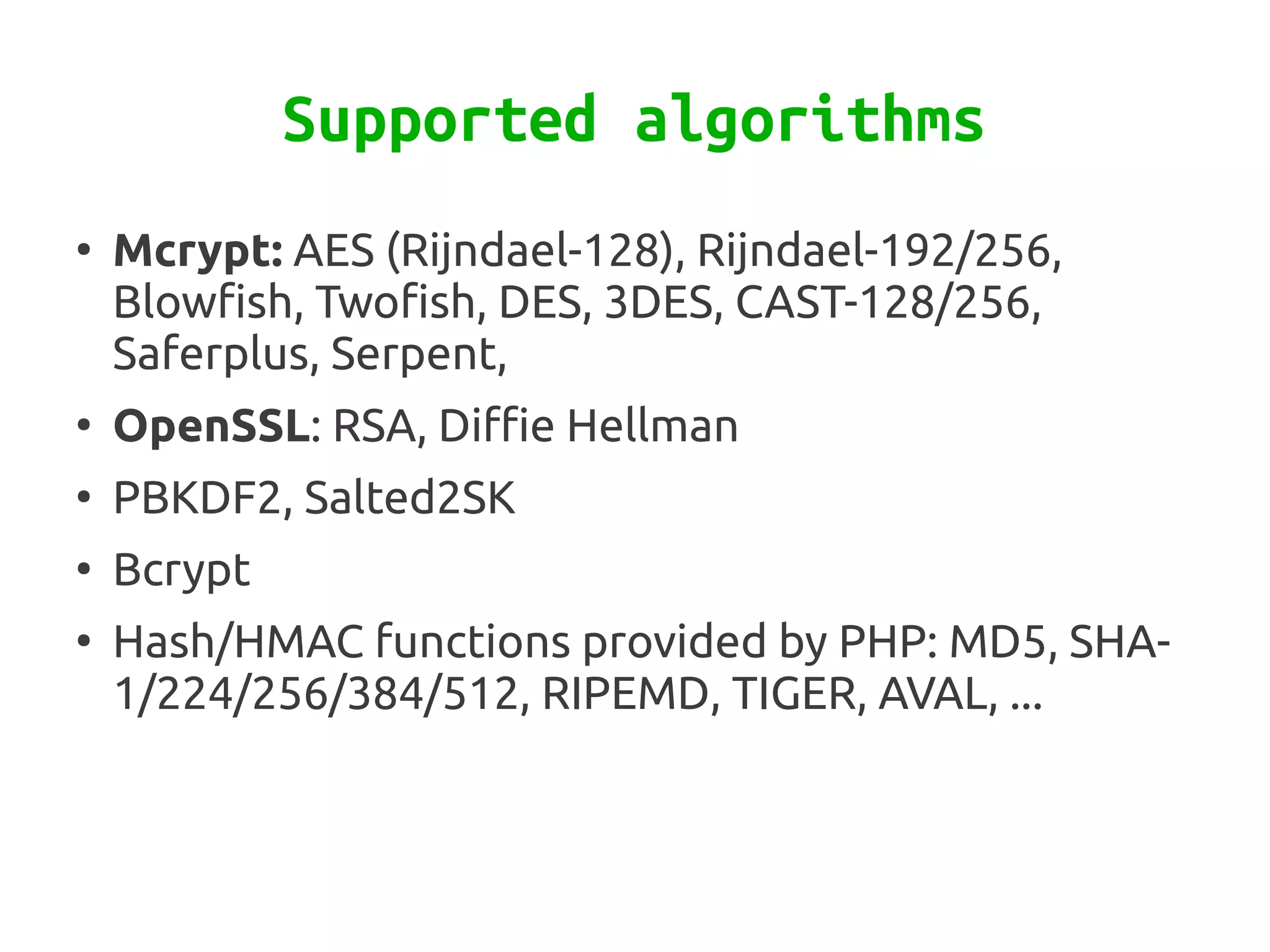
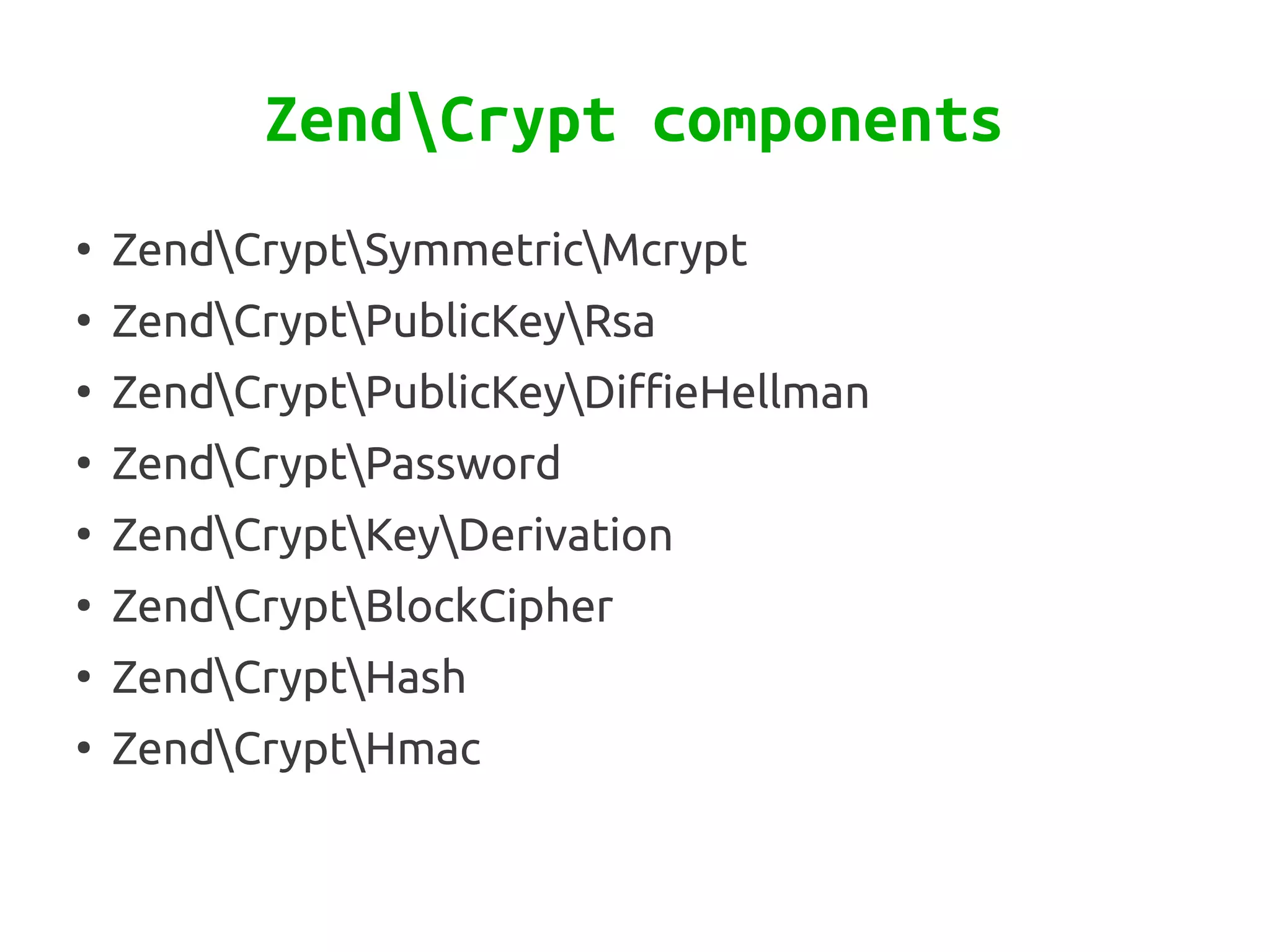
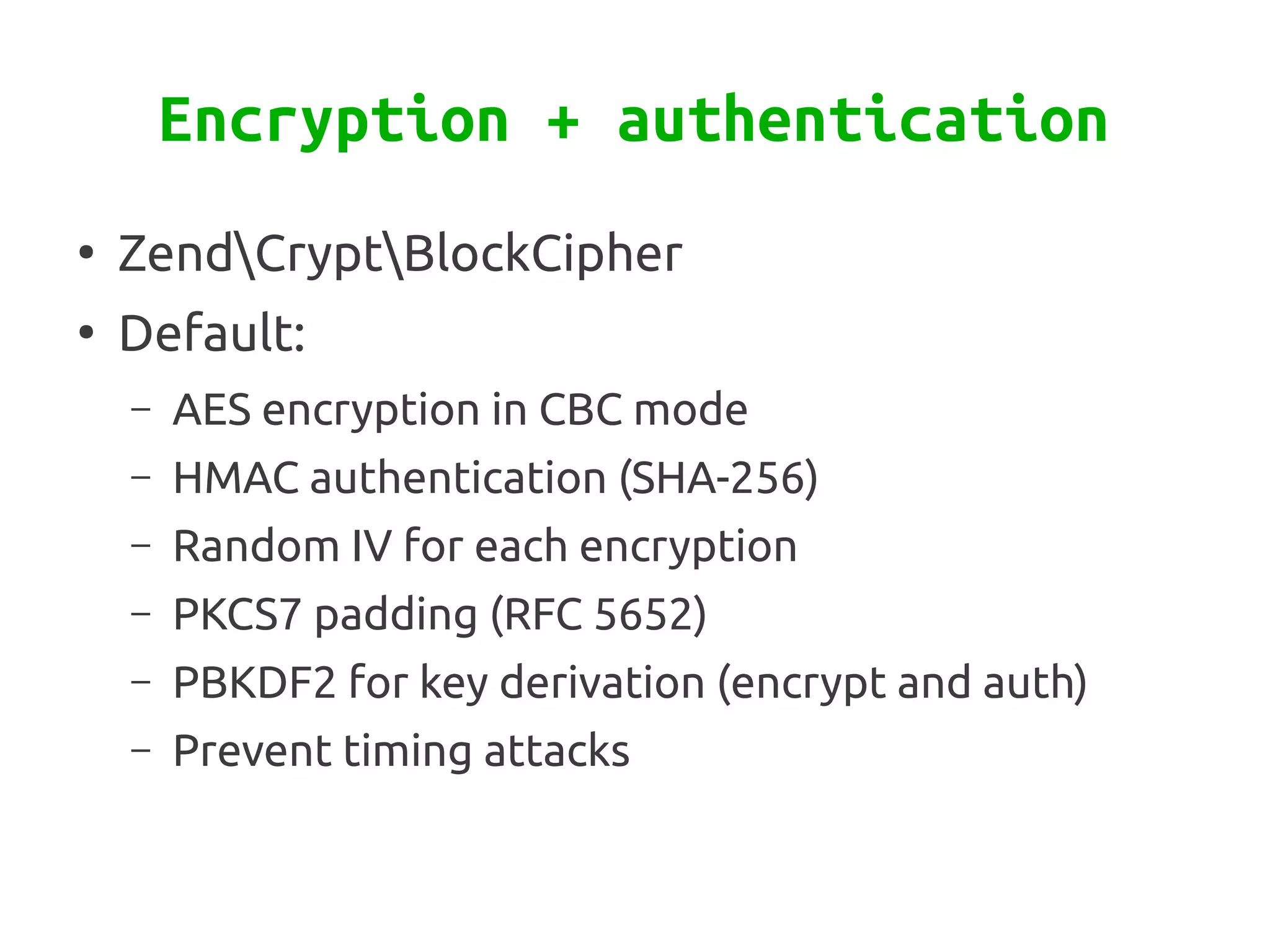
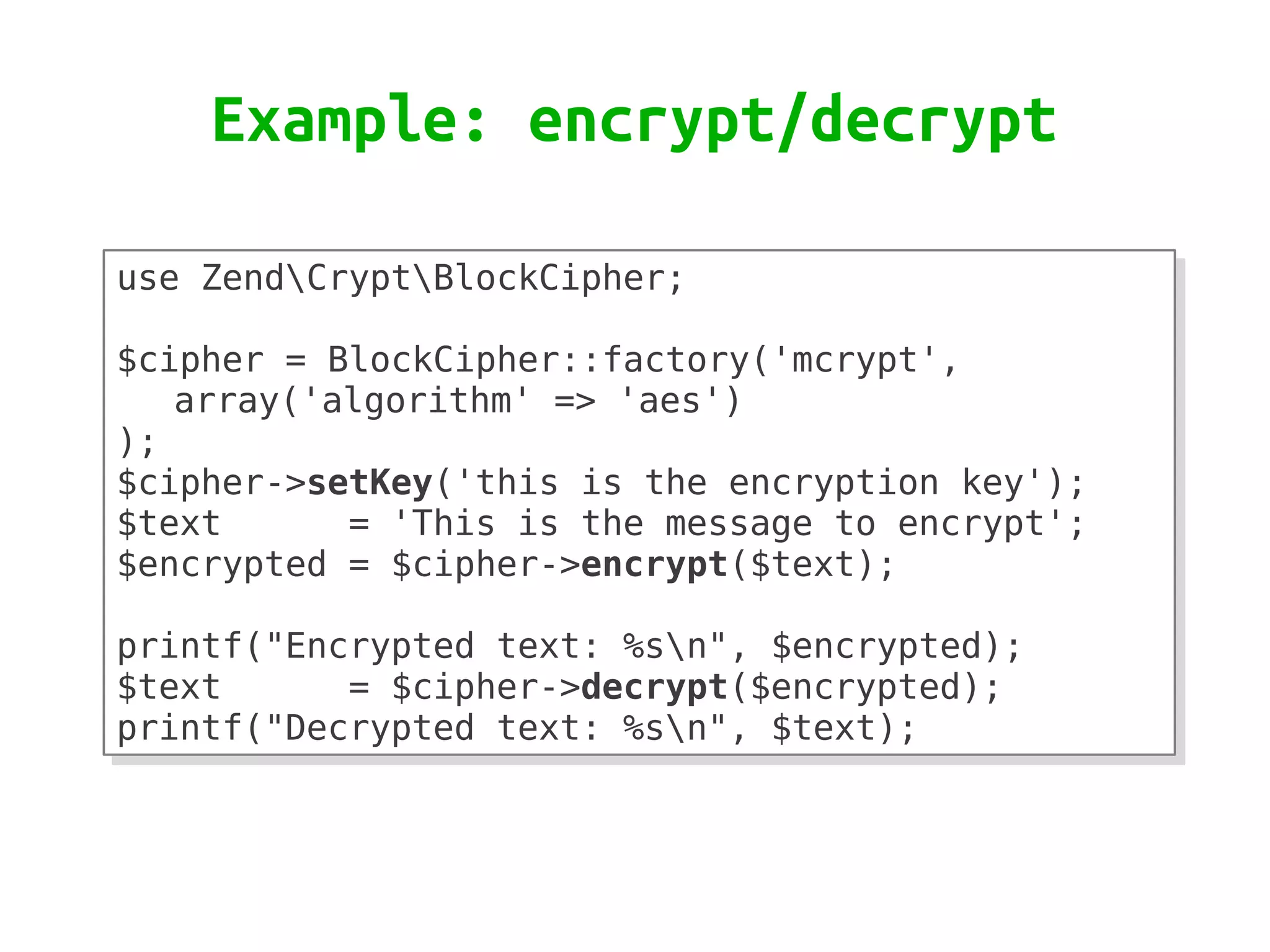
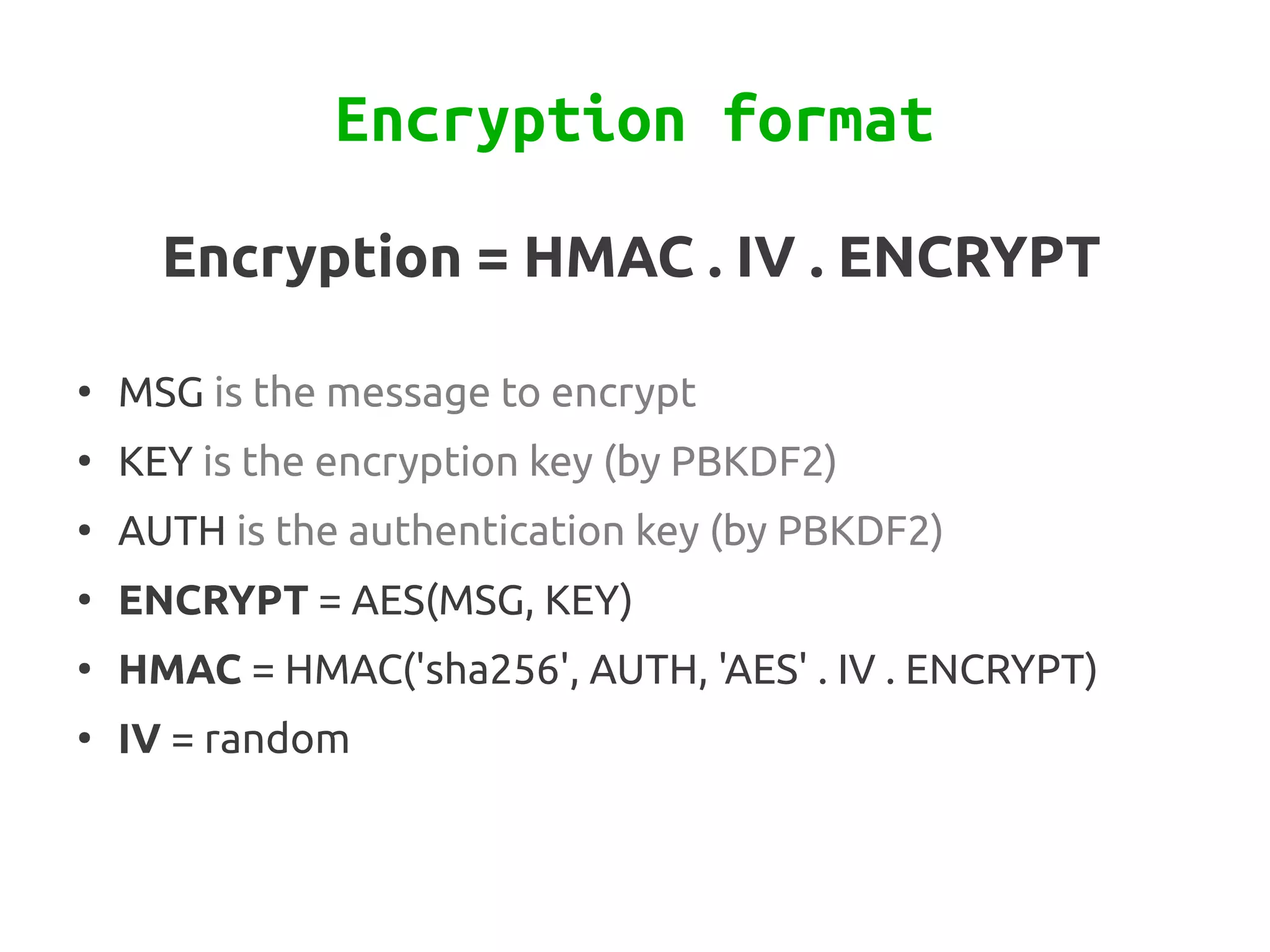
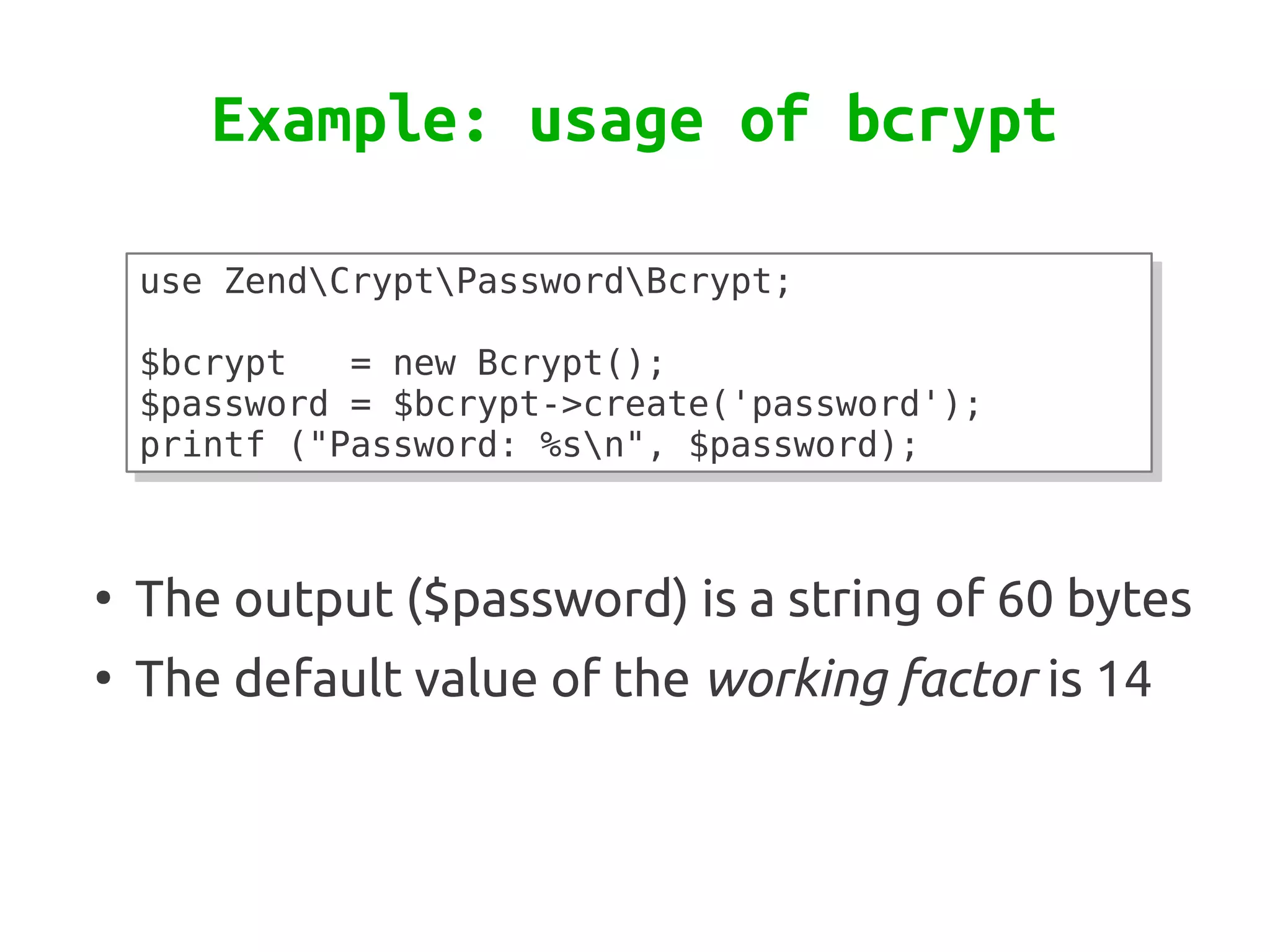
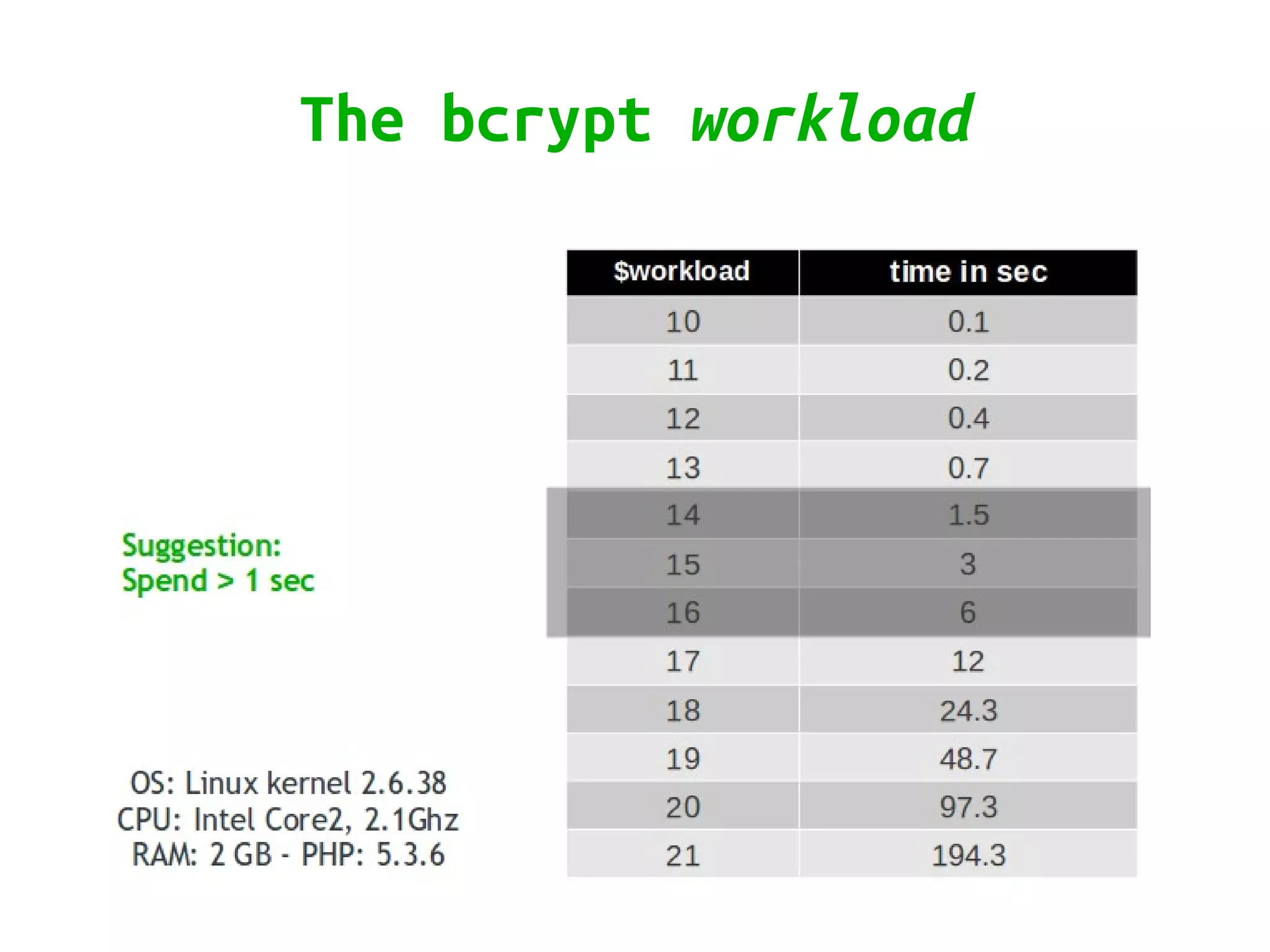
Zend\Crypt is a new component in Zend Framework 2 that facilitates cryptography in PHP projects. It supports symmetric and asymmetric encryption, hashing, key derivation functions, and other cryptographic algorithms. Some features include AES encryption, RSA and Diffie-Hellman for public key cryptography, bcrypt for secure password hashing, and PBKDF2 for password-based key derivation. The component provides classes for different algorithms and use cases like encryption, signatures, and password storage.


![Check for valid passwords
use ZendCryptPasswordBcrypt;
use ZendCryptPasswordBcrypt;
$bcrypt
$bcrypt = new Bcrypt();
= new Bcrypt();
$password = $_POST['password'];
$password = $_POST['password'];
$hash
$hash = '…'; // i.e. get from a database
= '…'; // i.e. get from a database
if ($bcrypt->verify($password, $hash)) {
if ($bcrypt->verify($password, $hash)) {
echo “The password is valid”;
echo “The password is valid”;
} else {
} else {
Echo “The password is not valid”;
Echo “The password is not valid”;
}
}](https://image.slidesharecdn.com/zendcrypt-120612034406-phpapp01/75/Cryptography-with-Zend-Framework-13-2048.jpg)