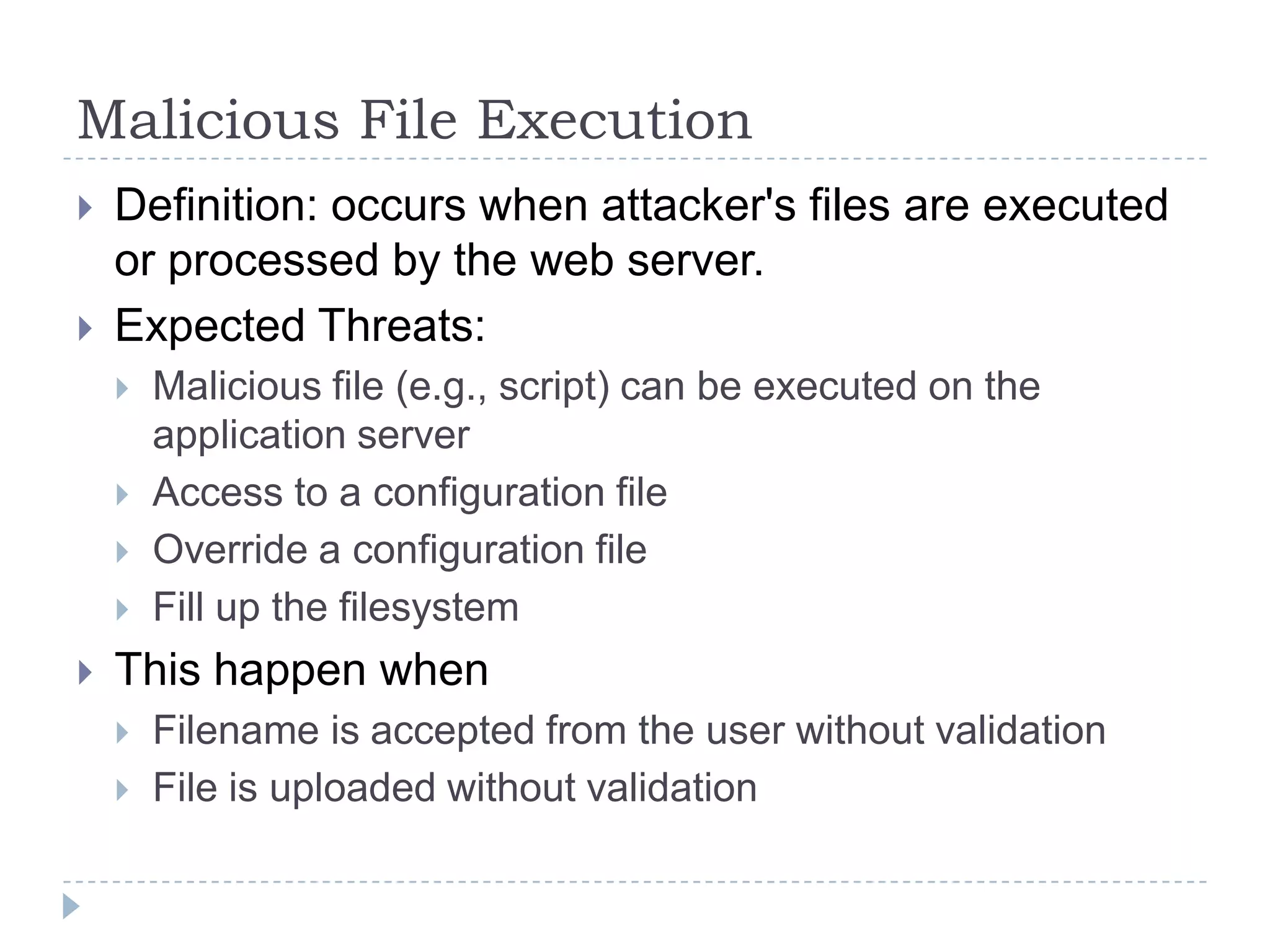
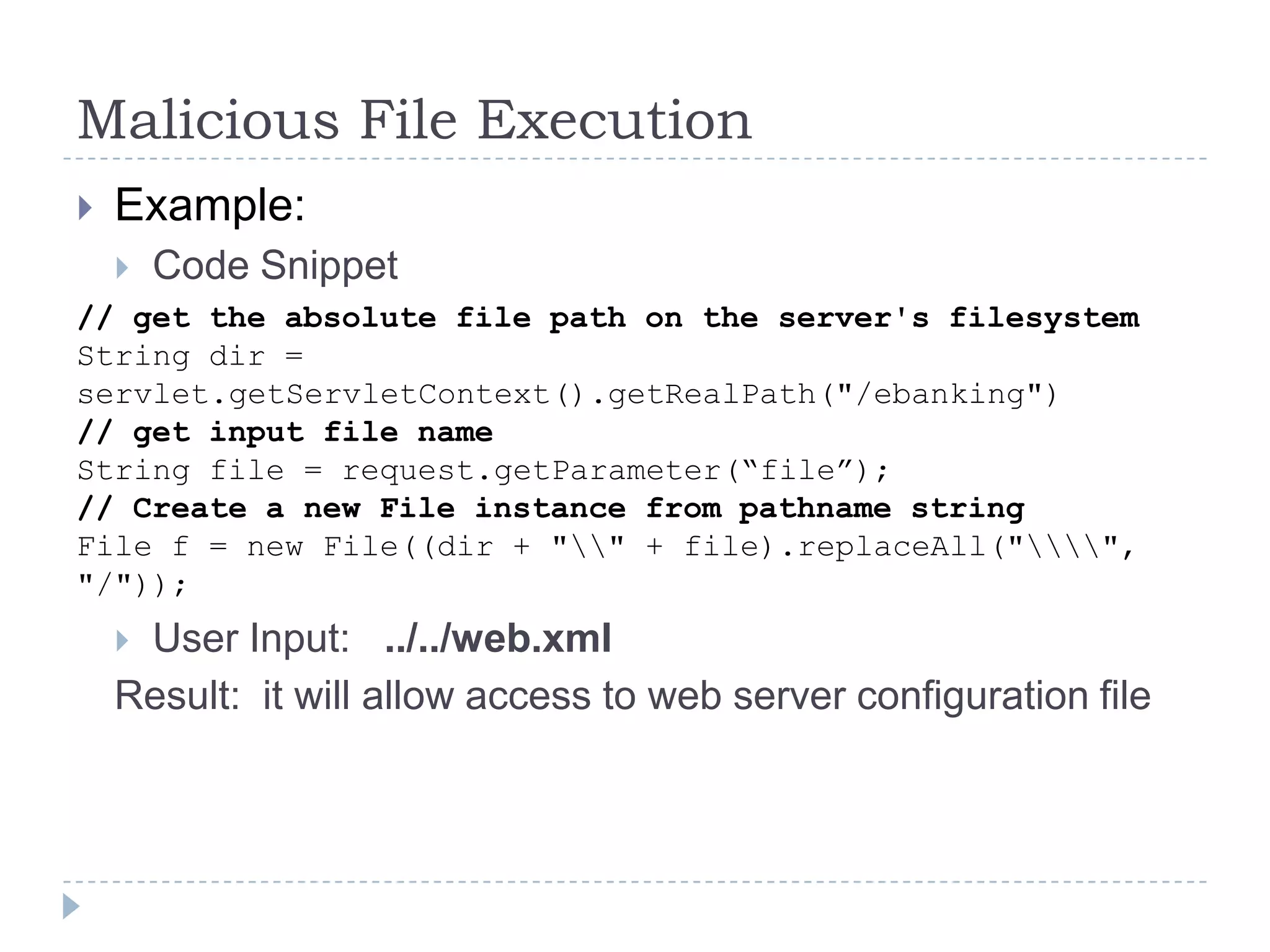
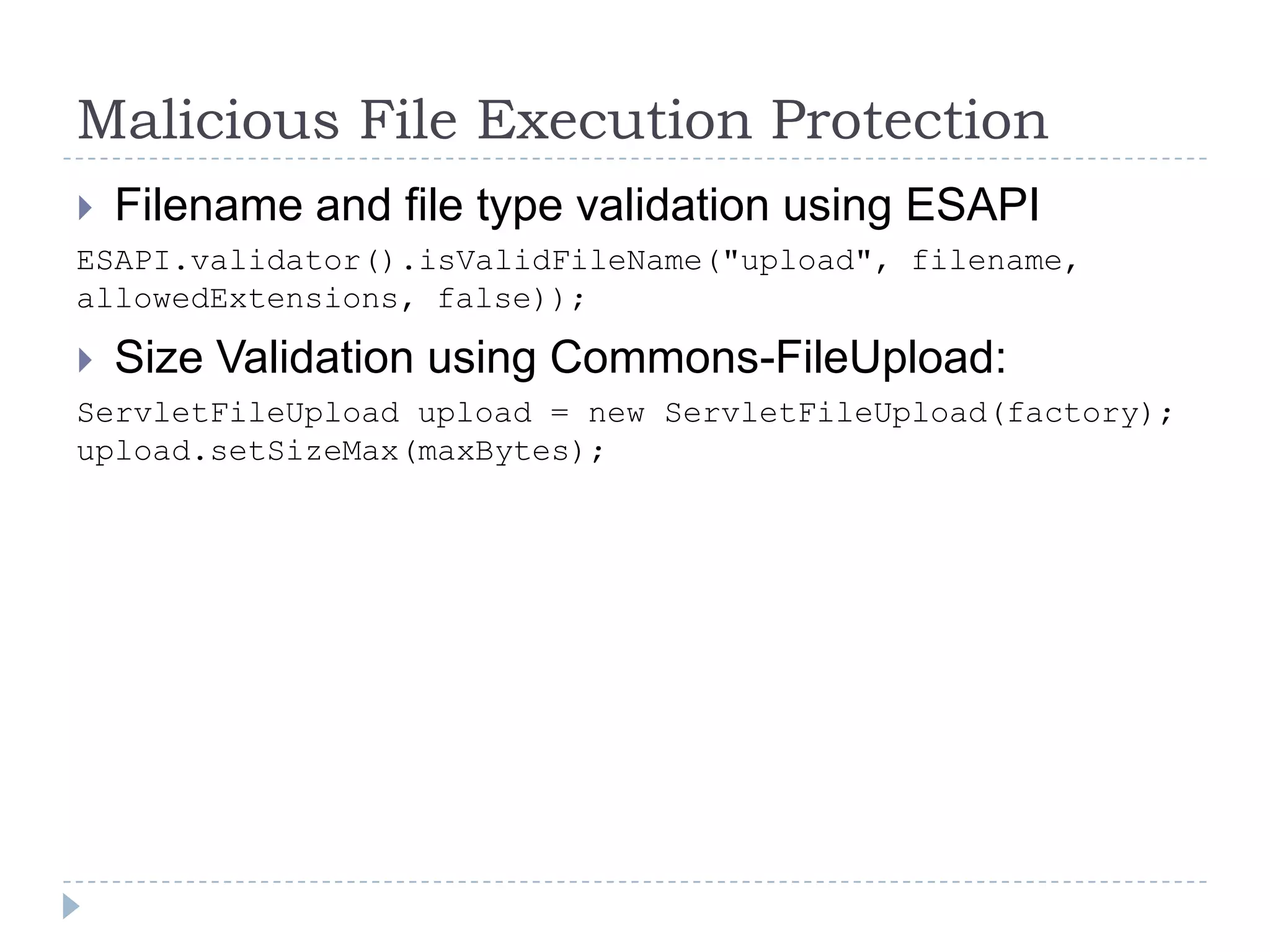
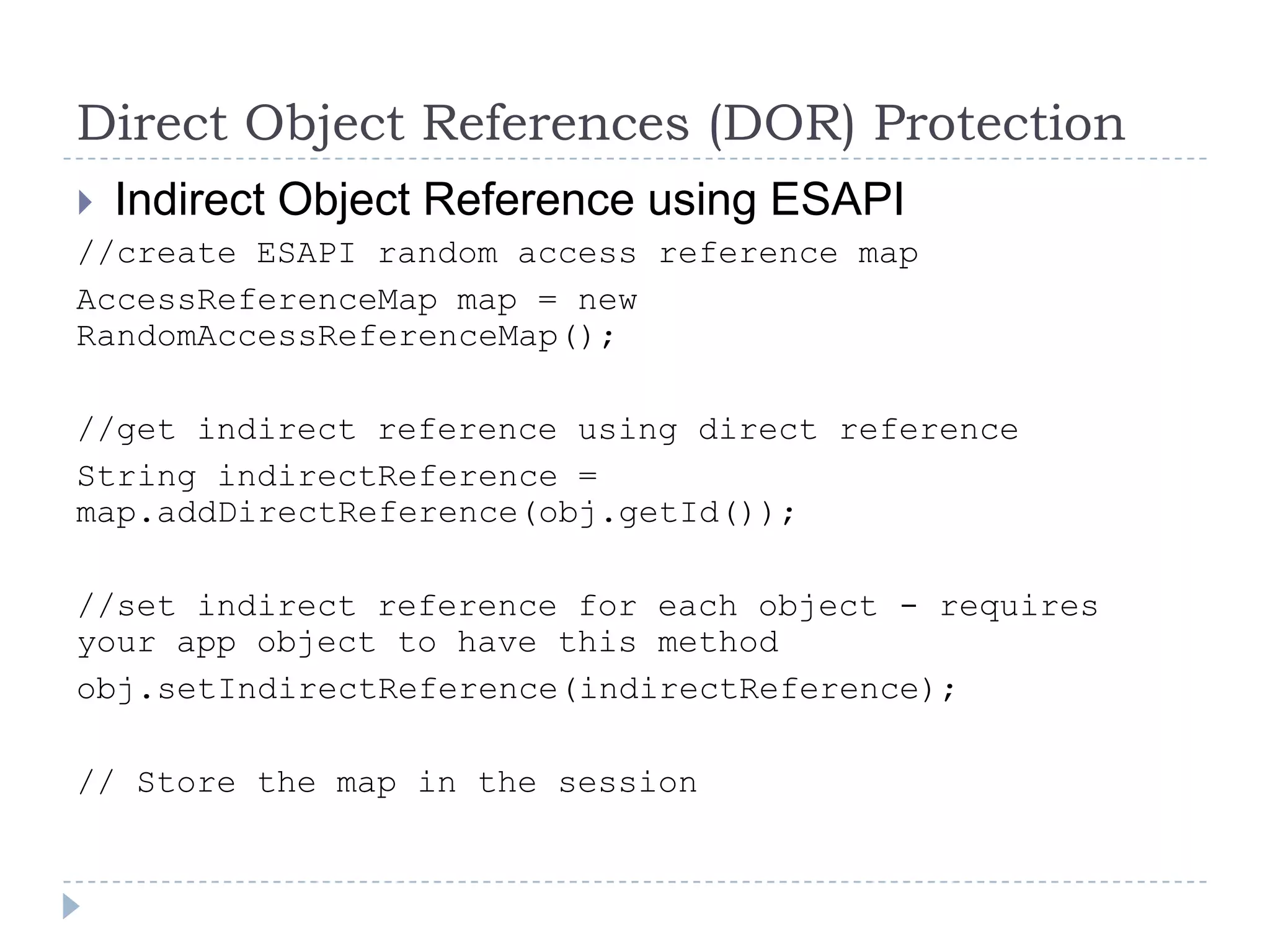
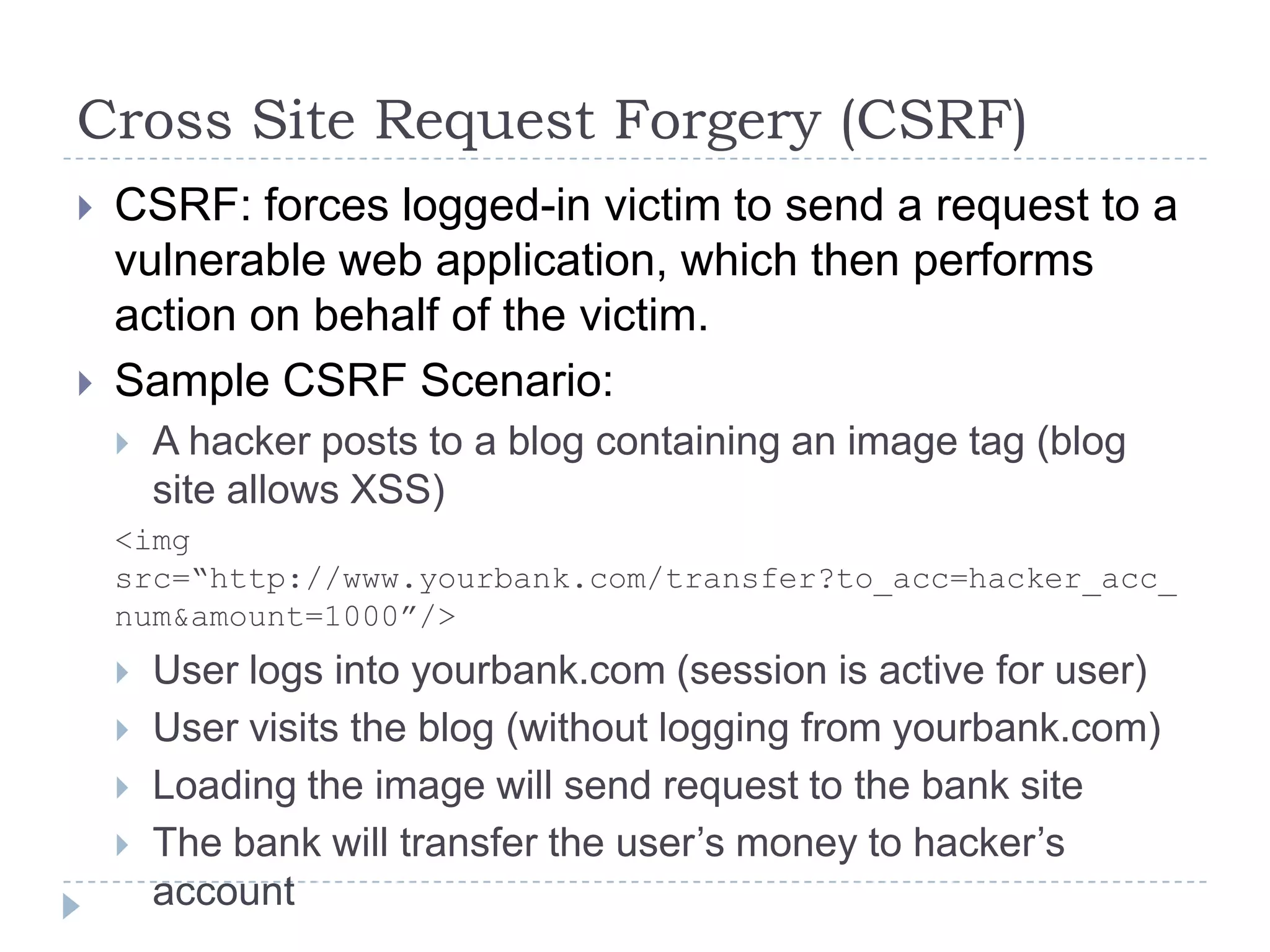
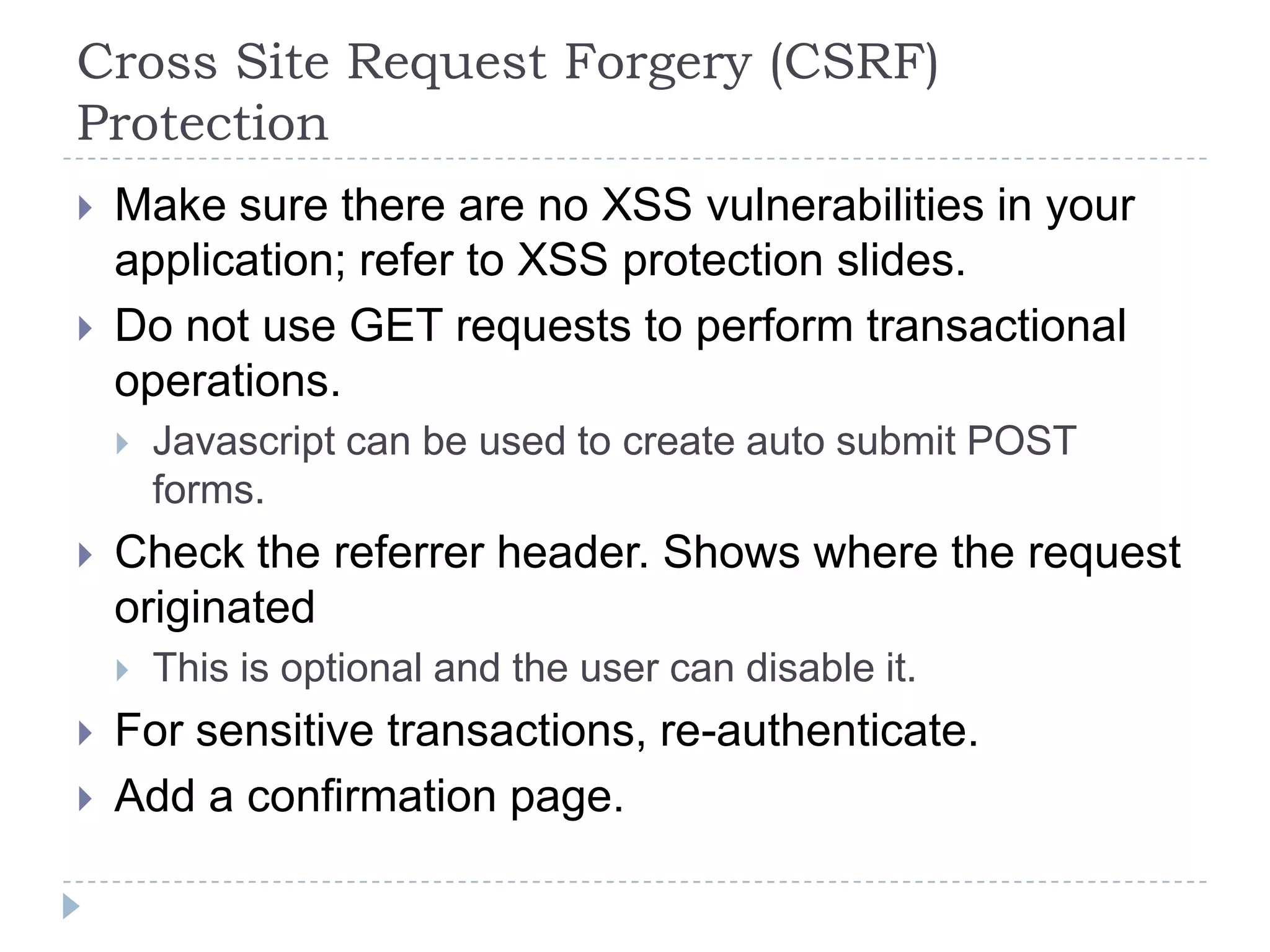
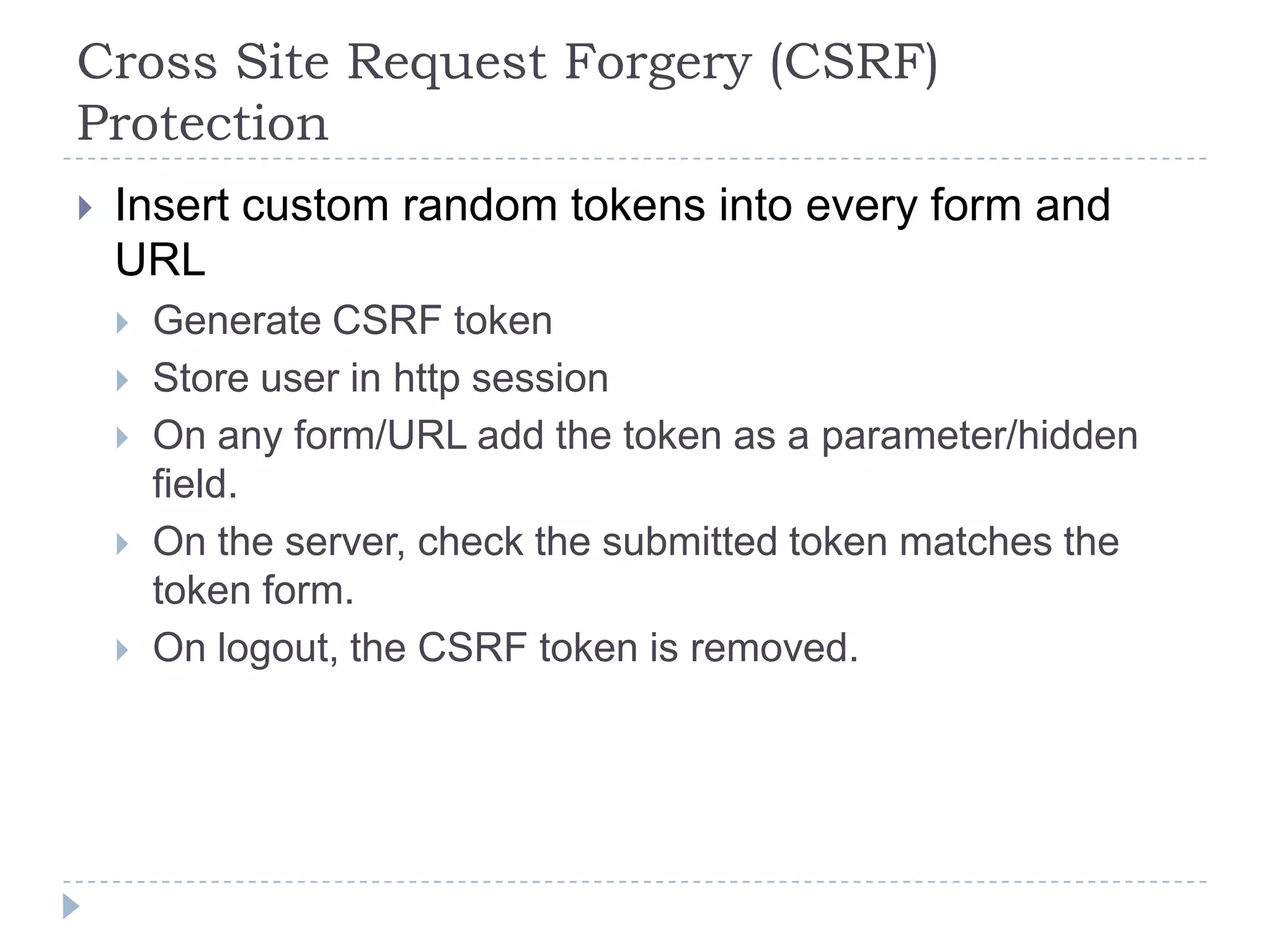
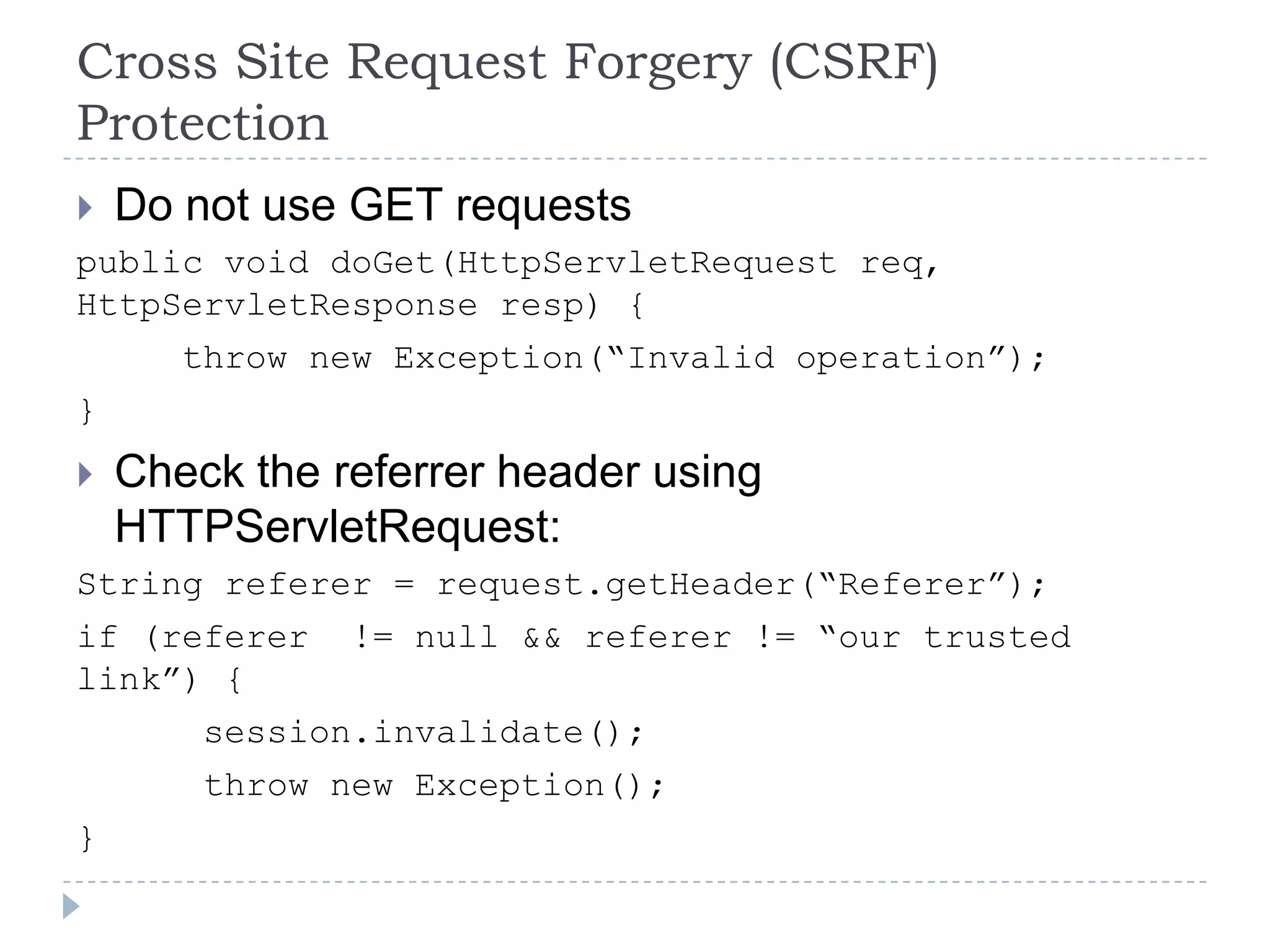
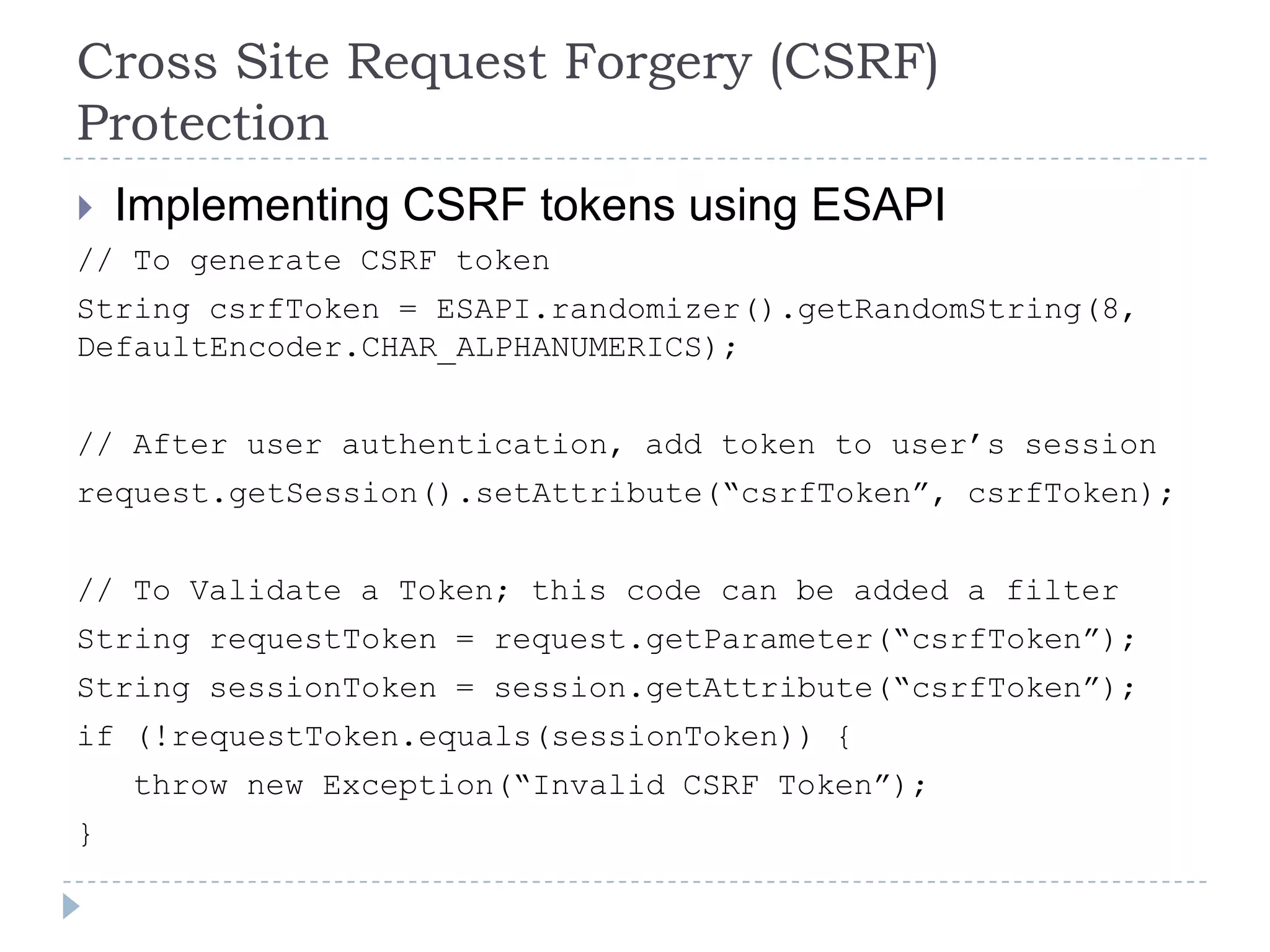
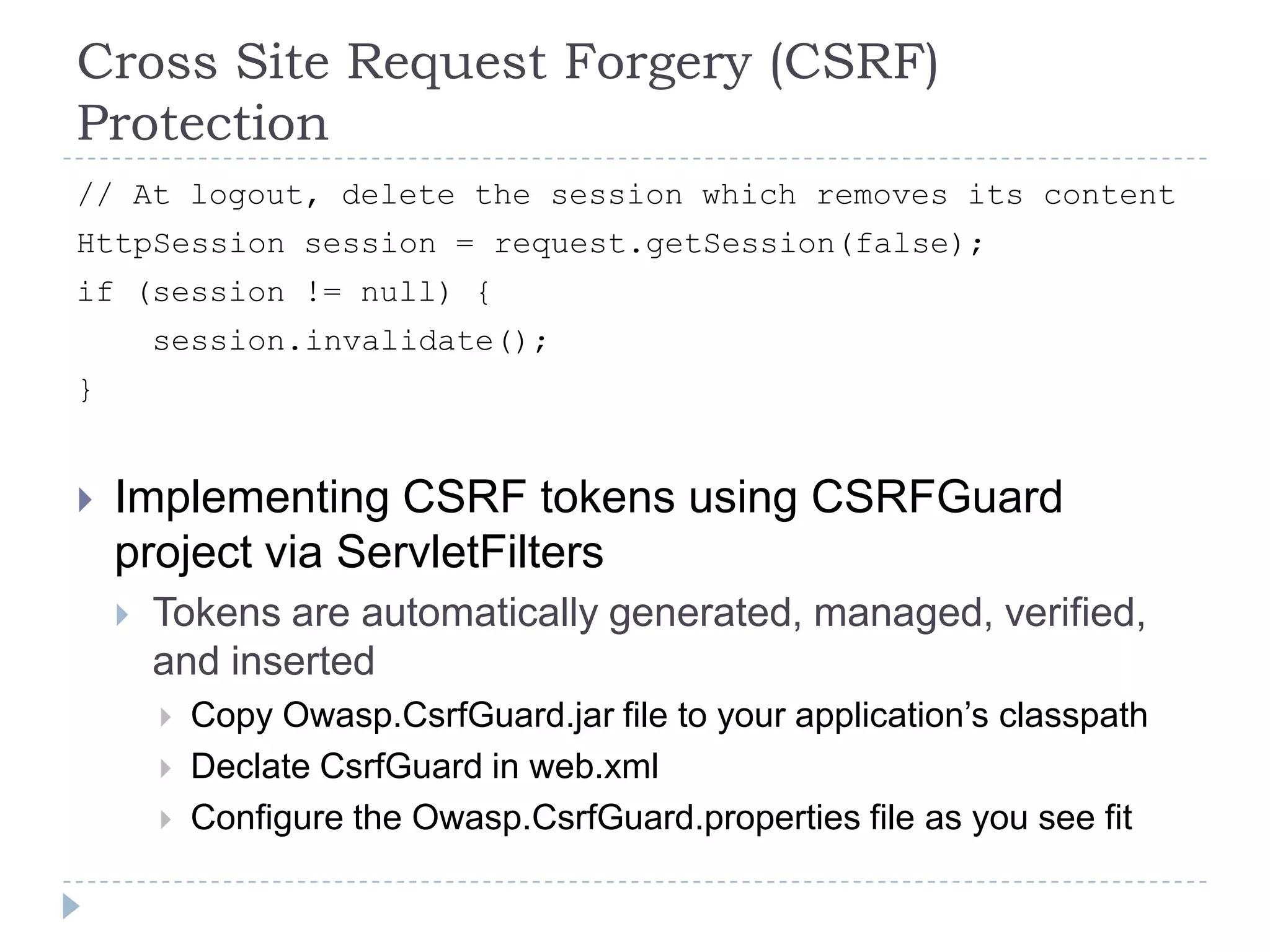
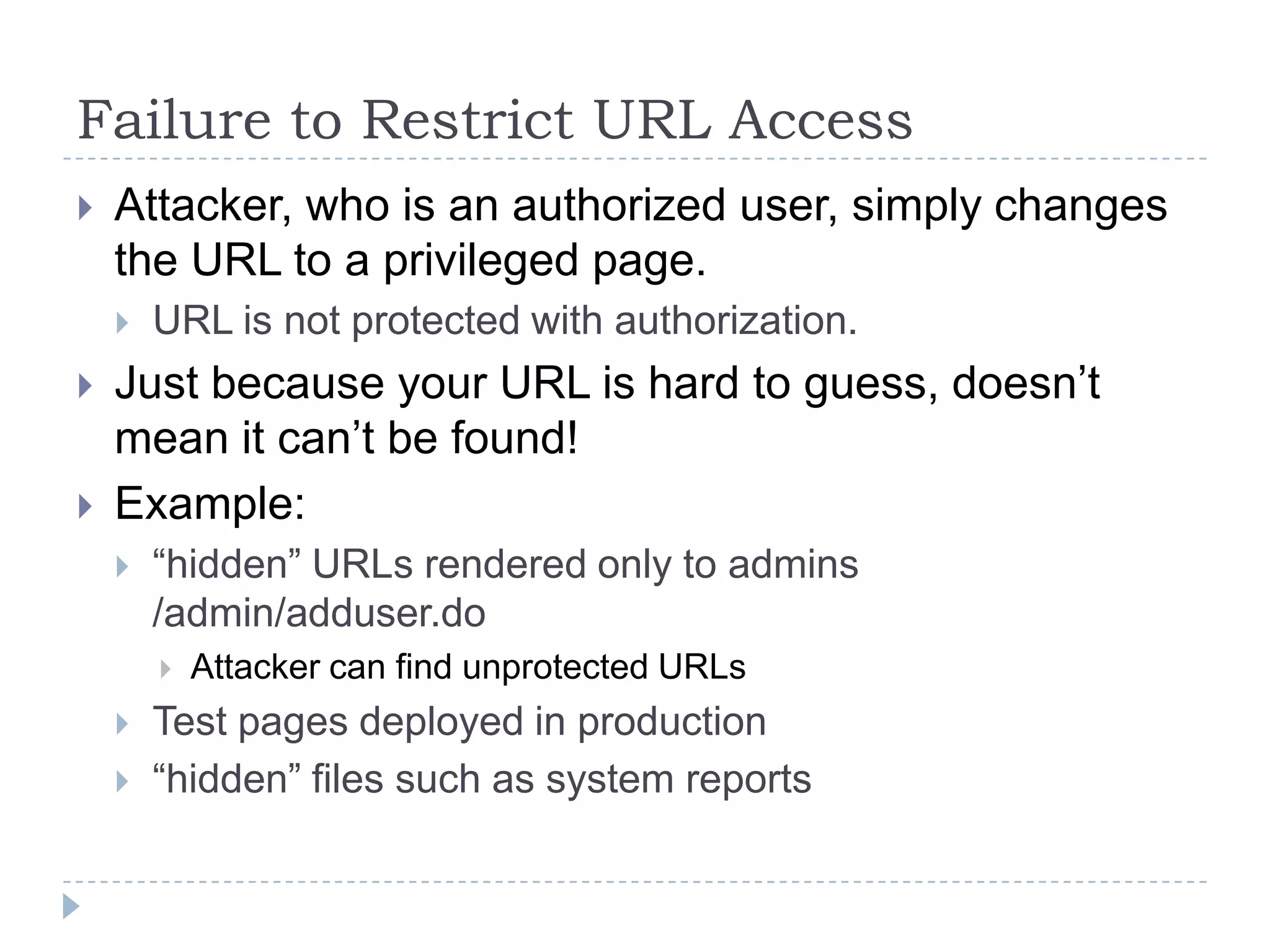
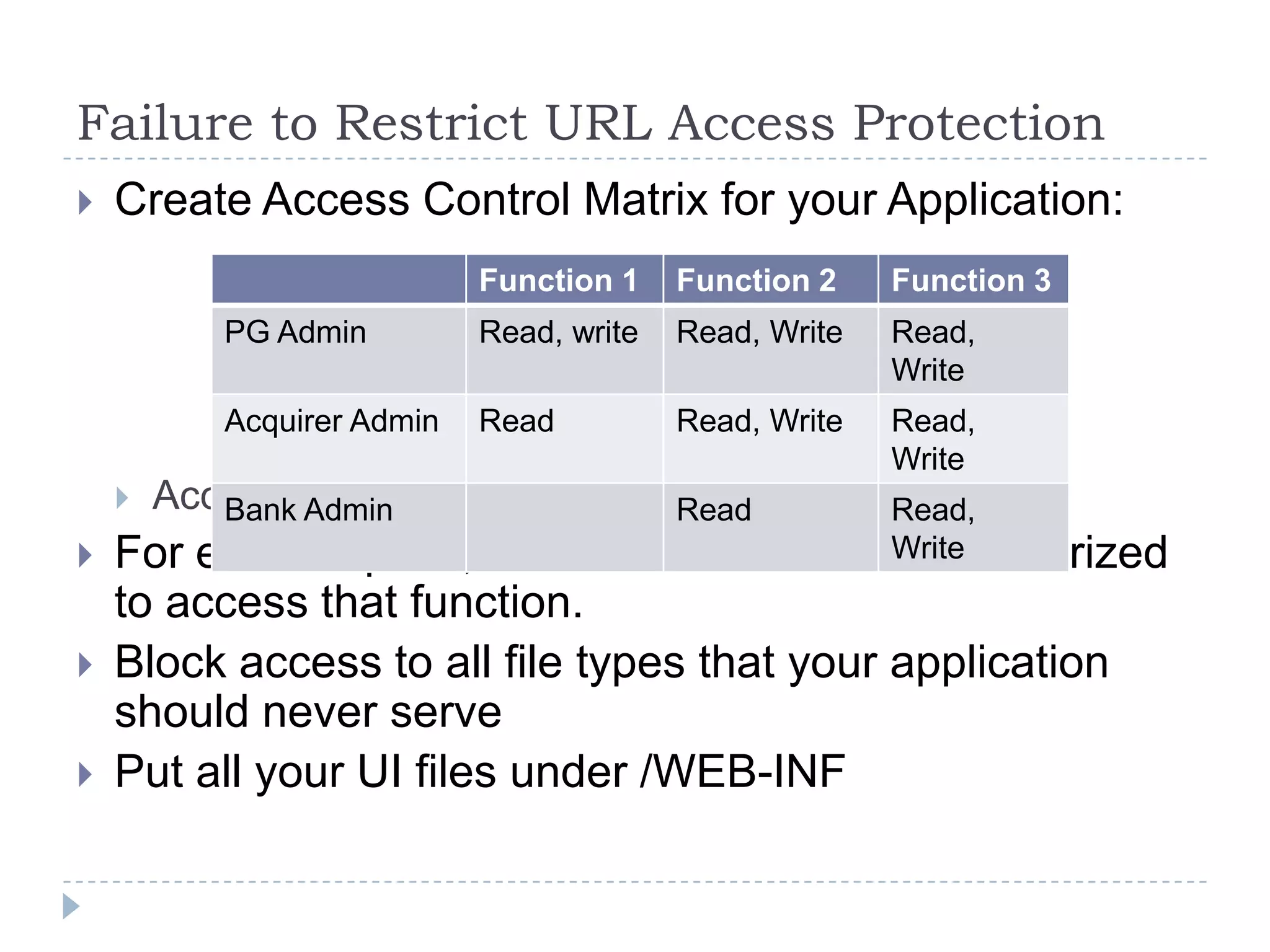
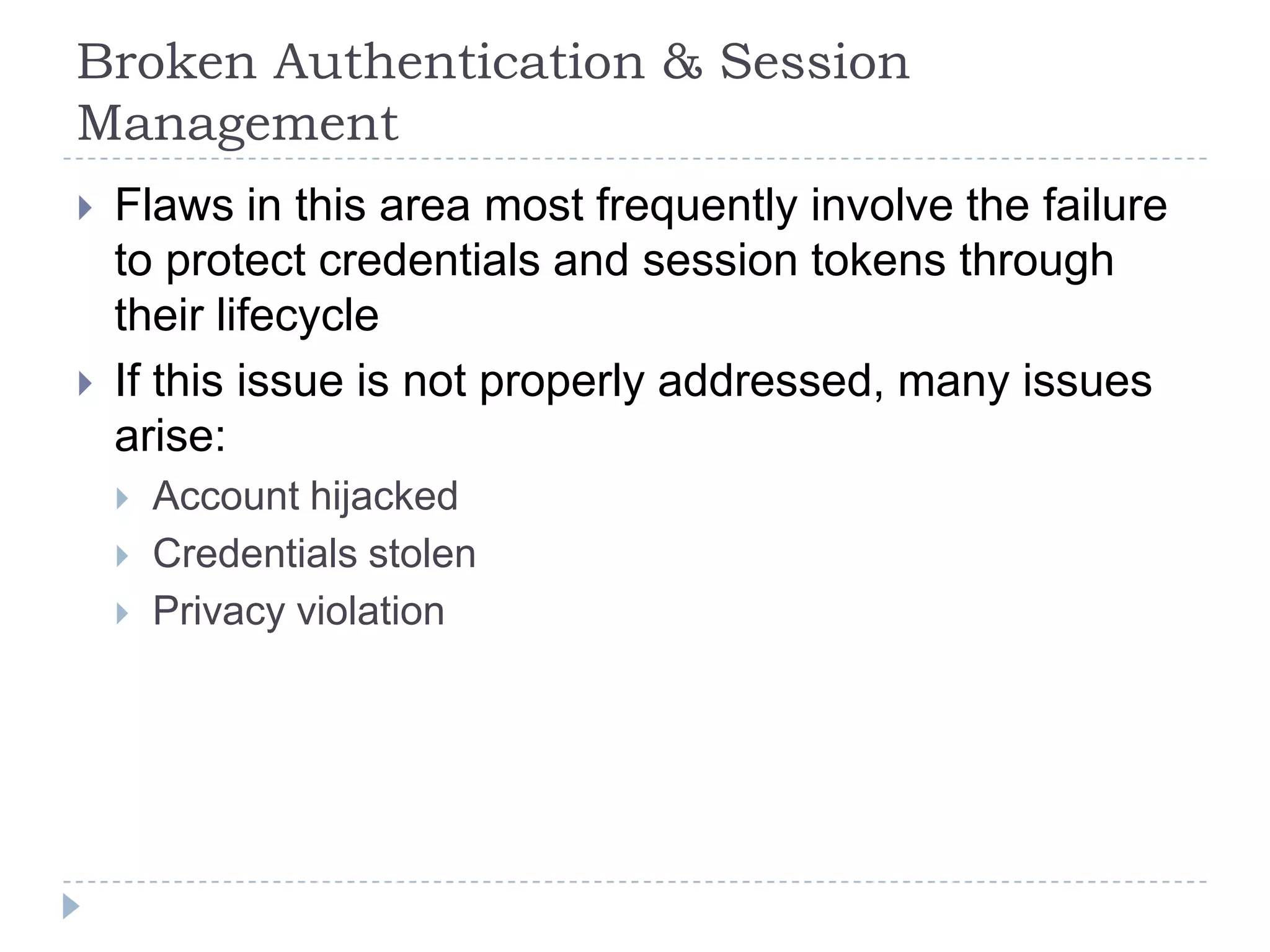
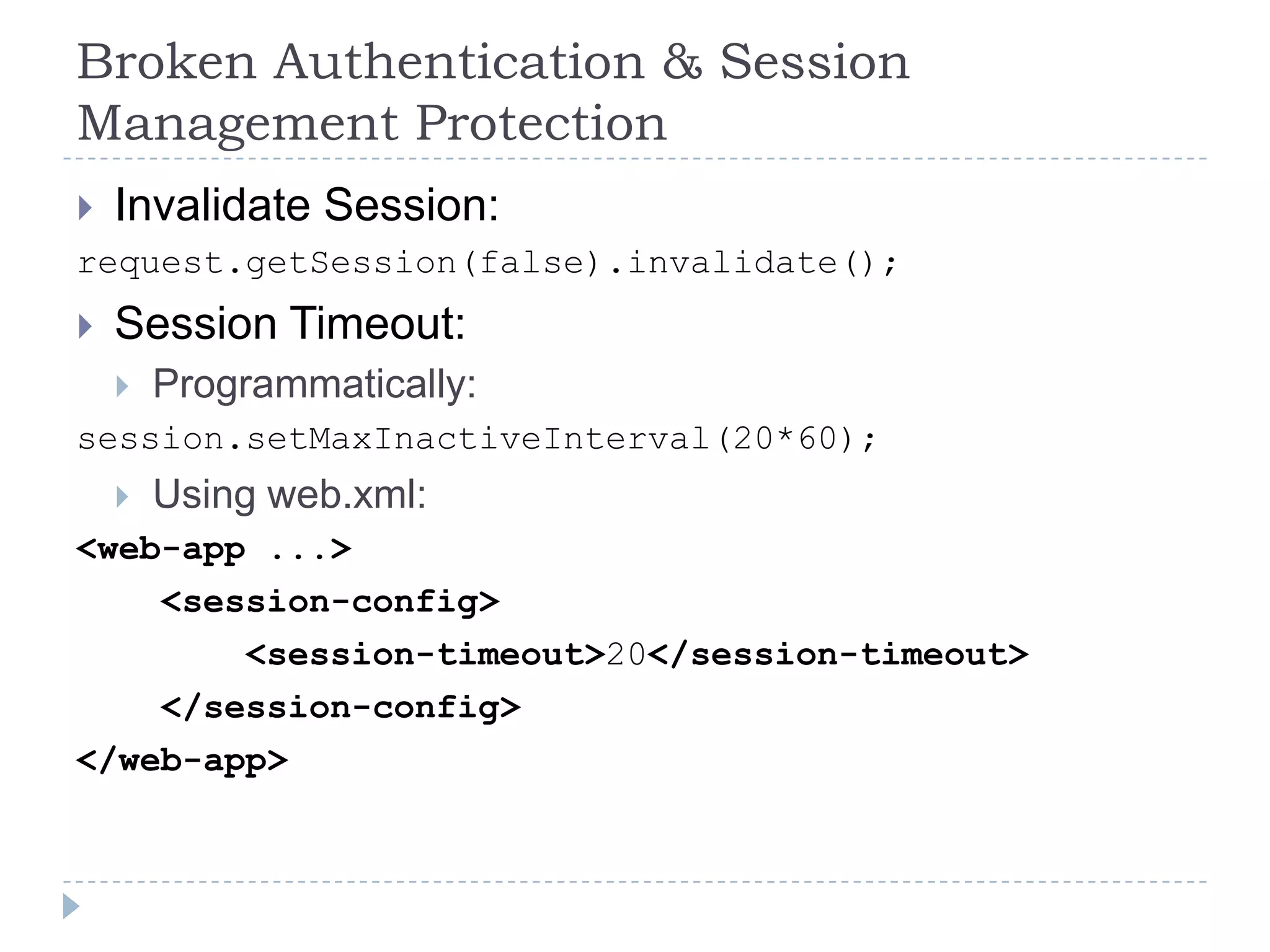
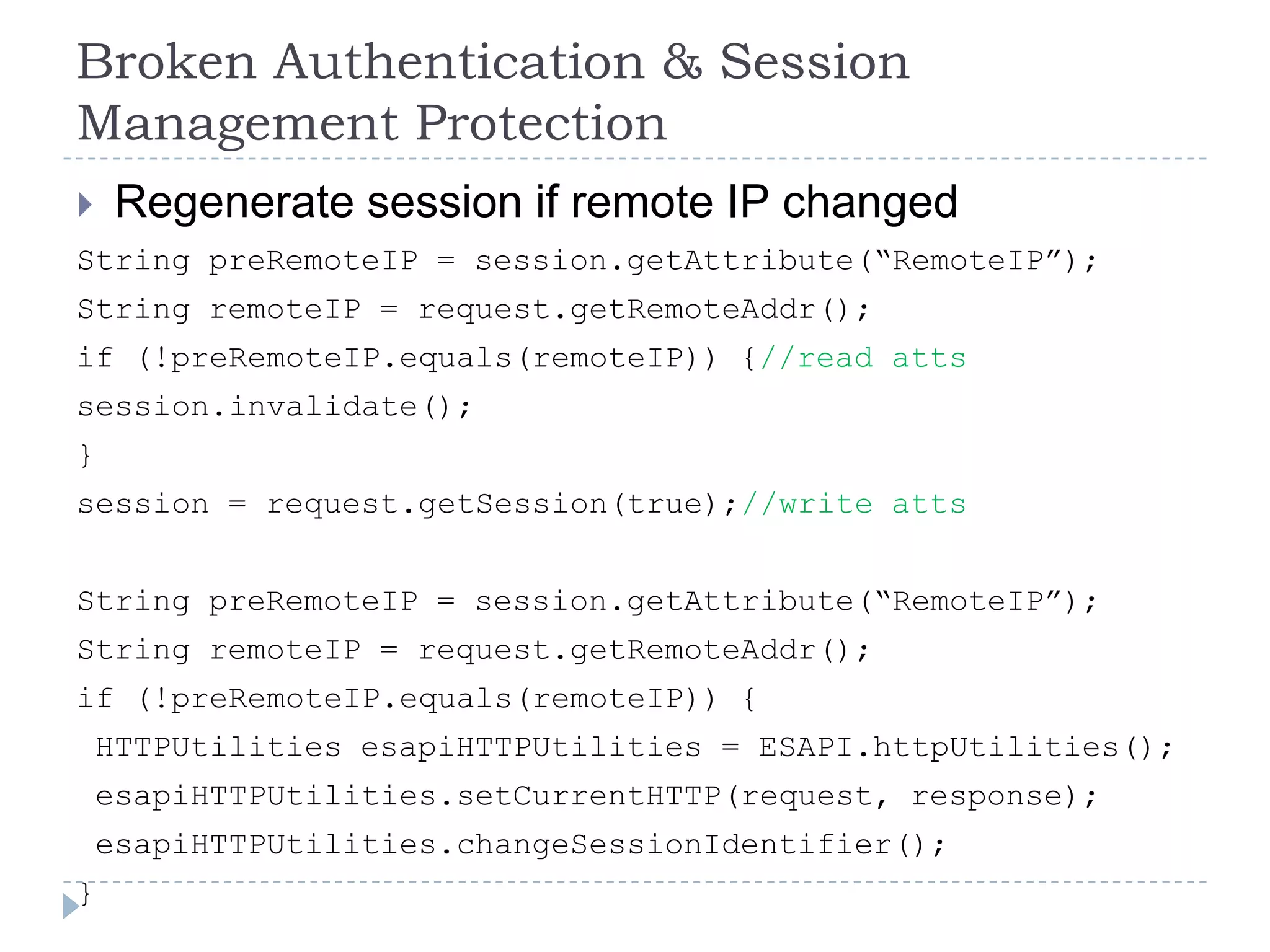
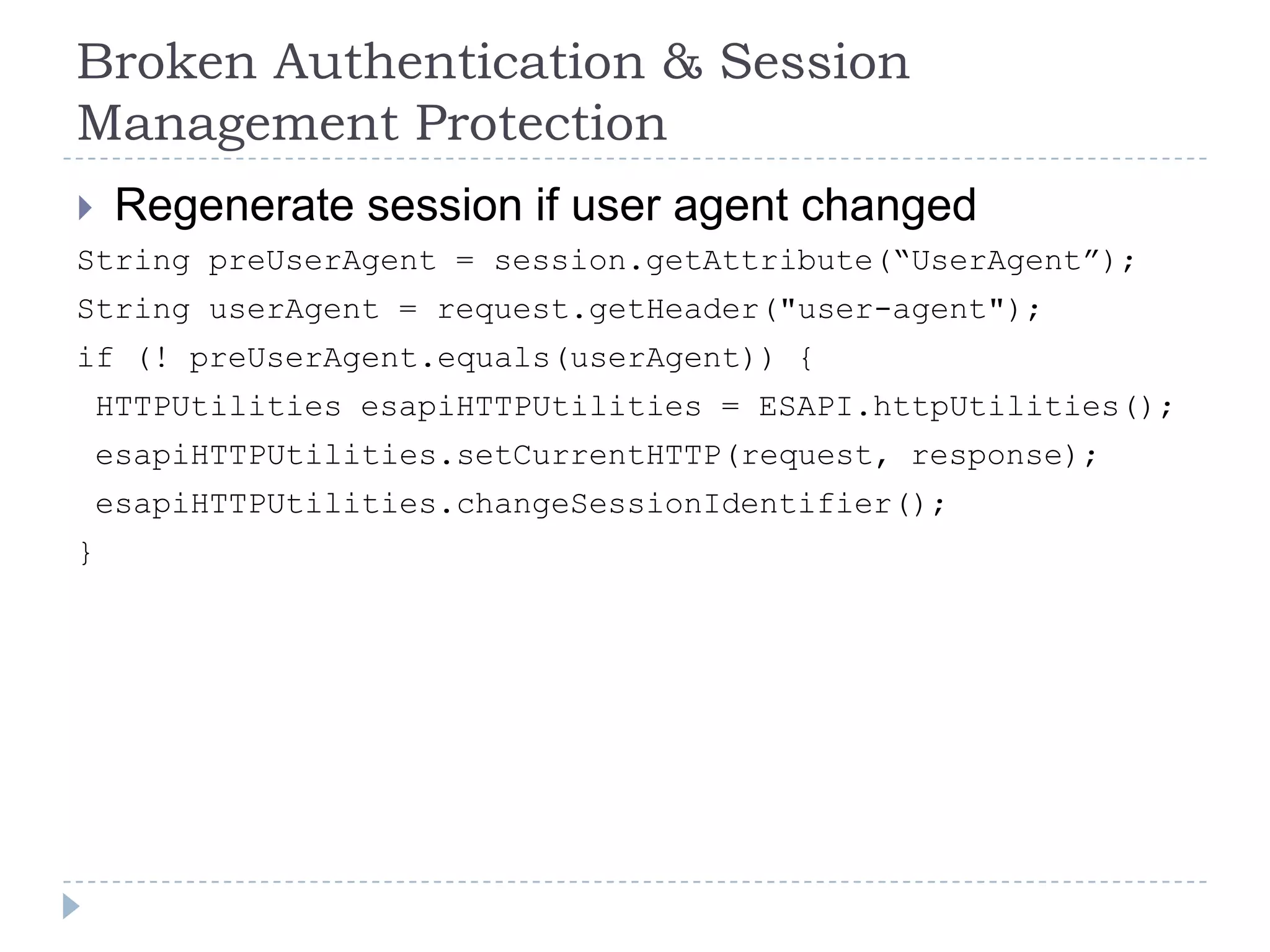
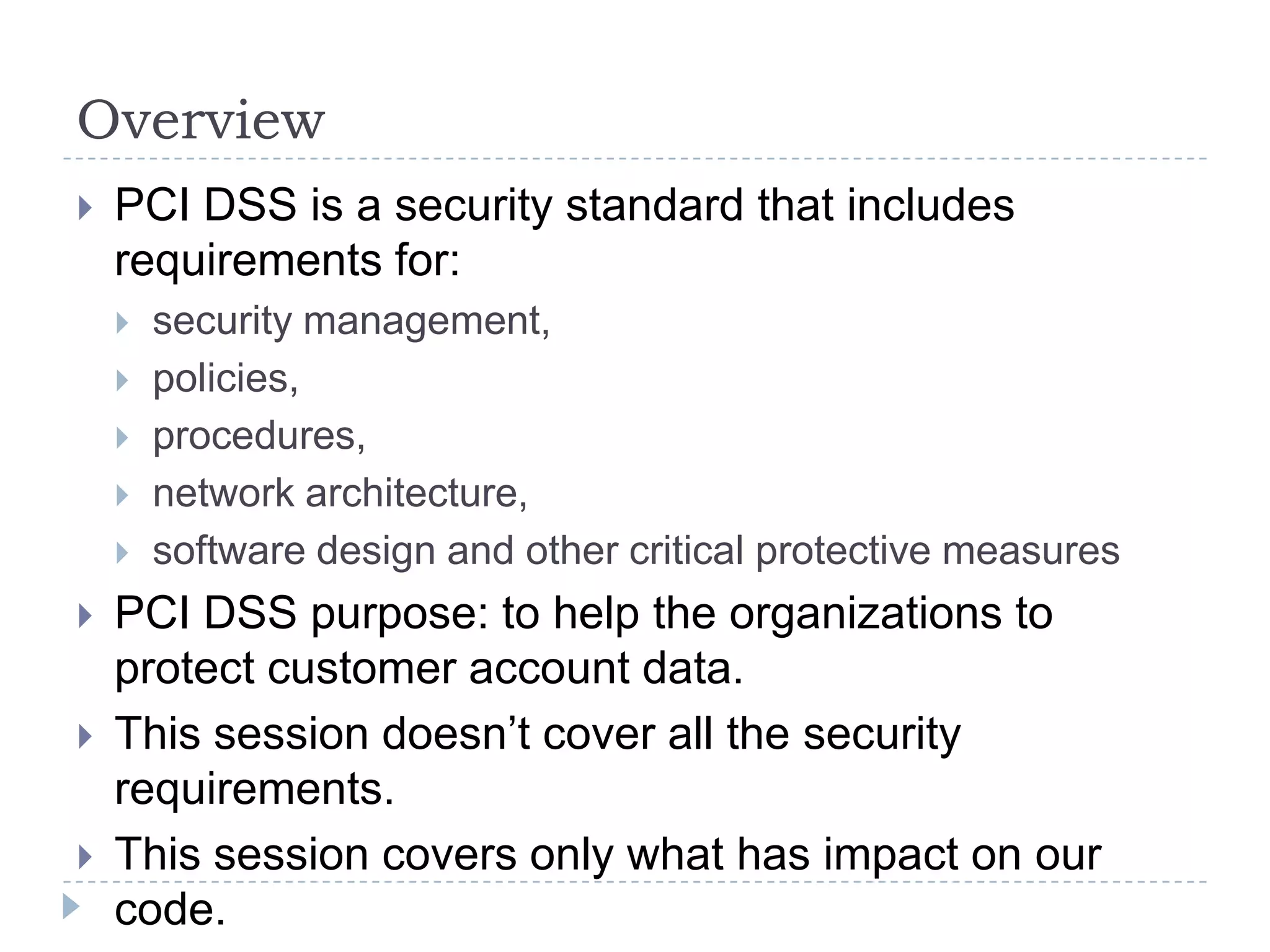
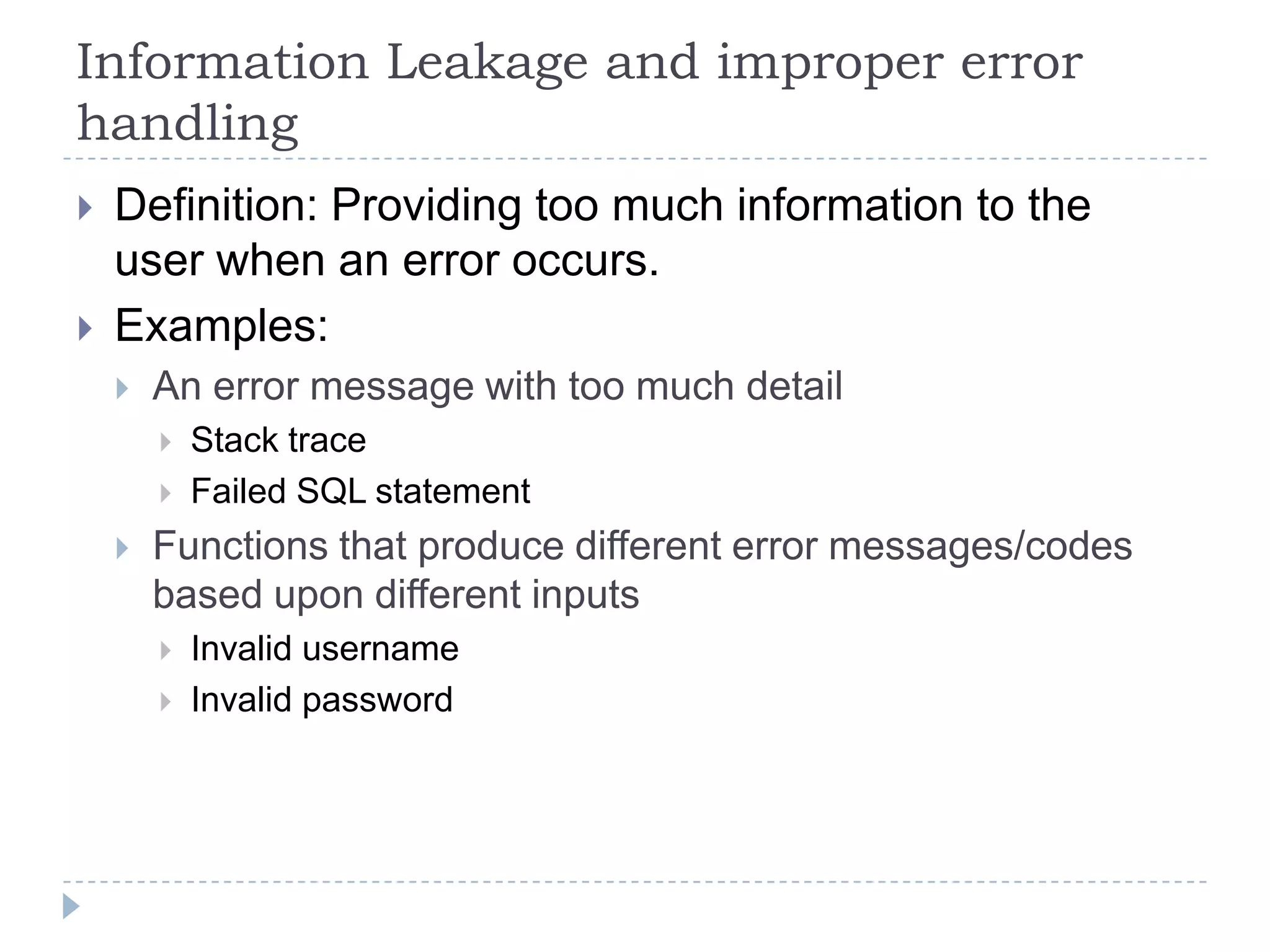
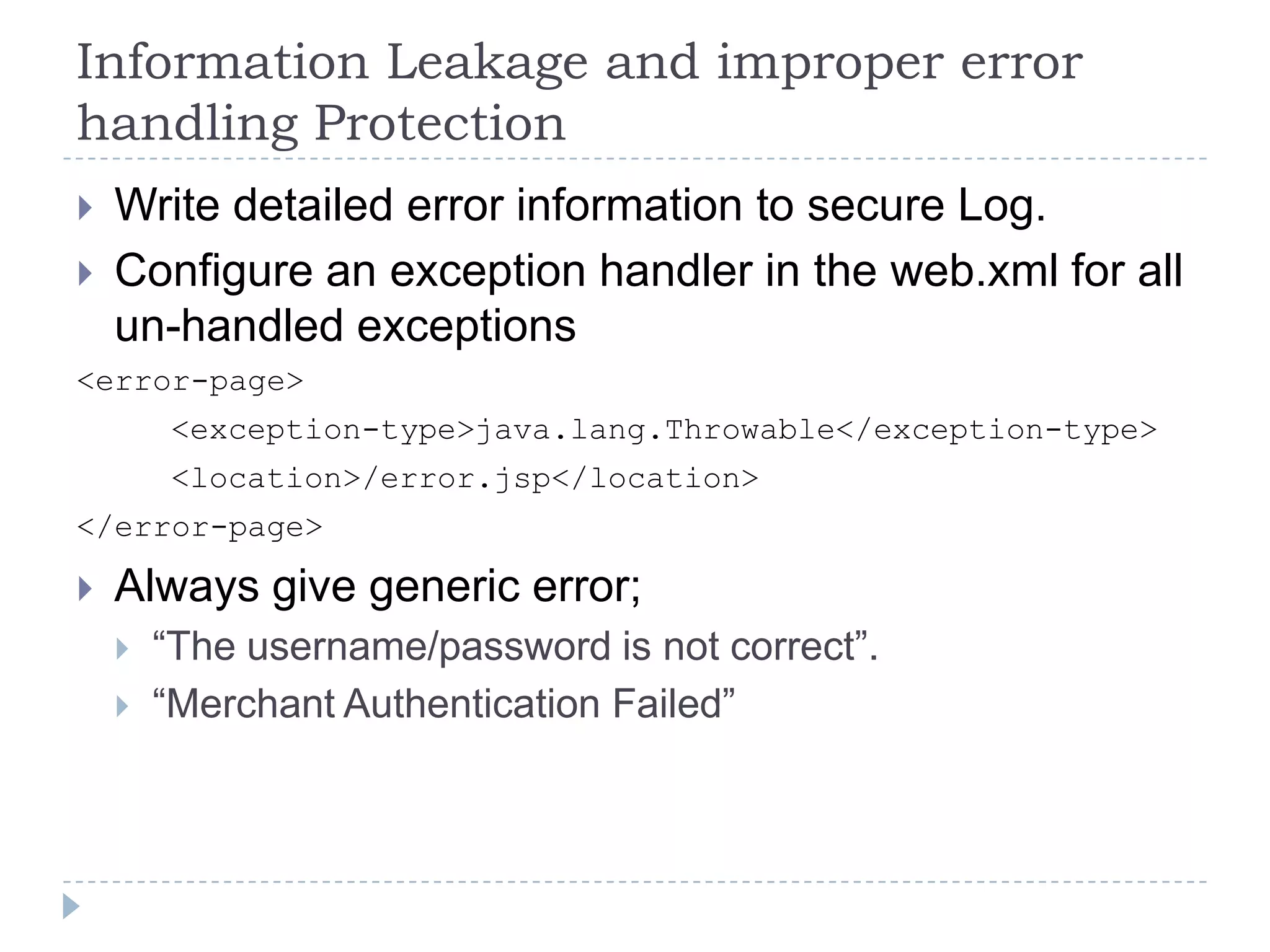
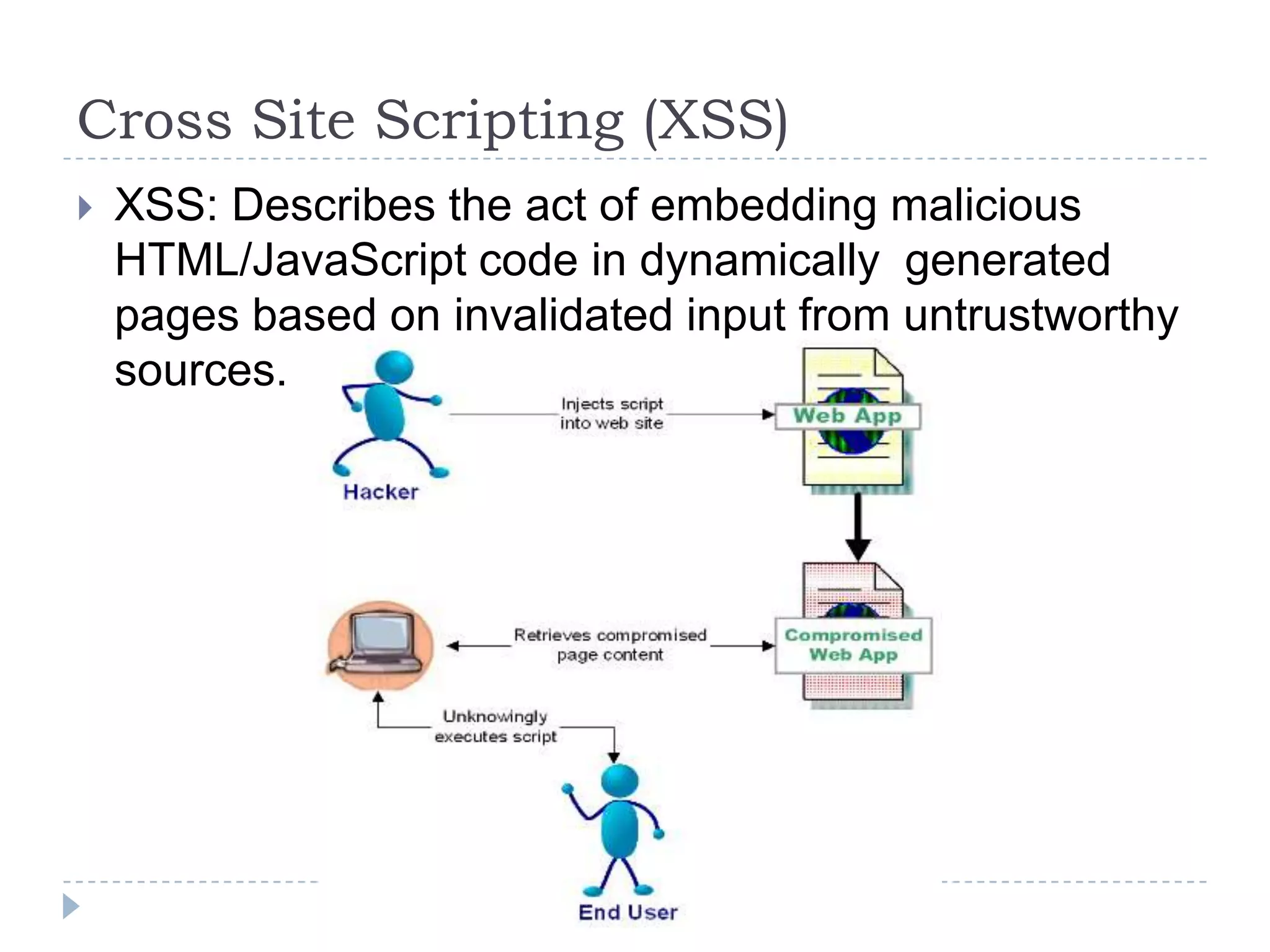
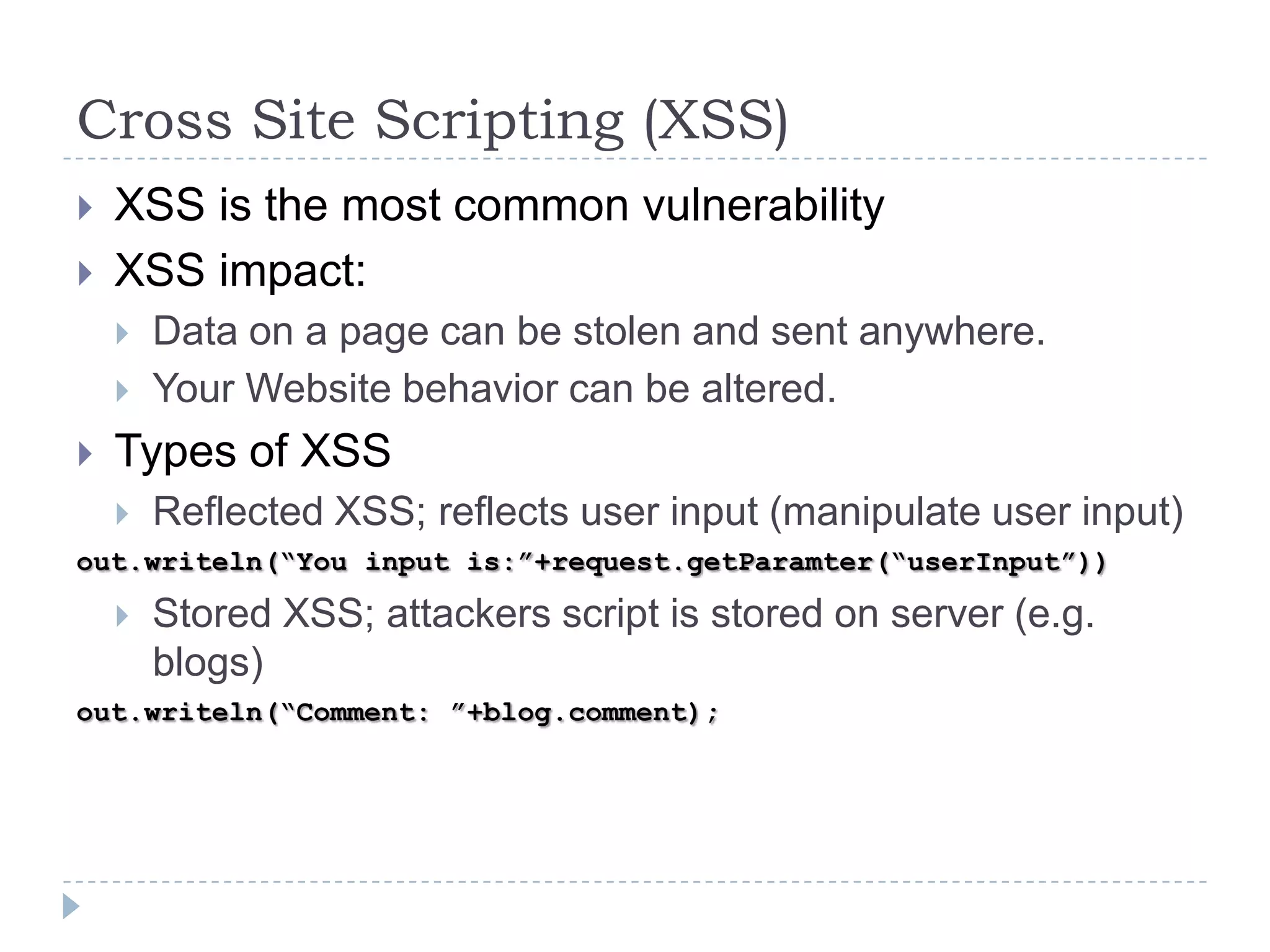
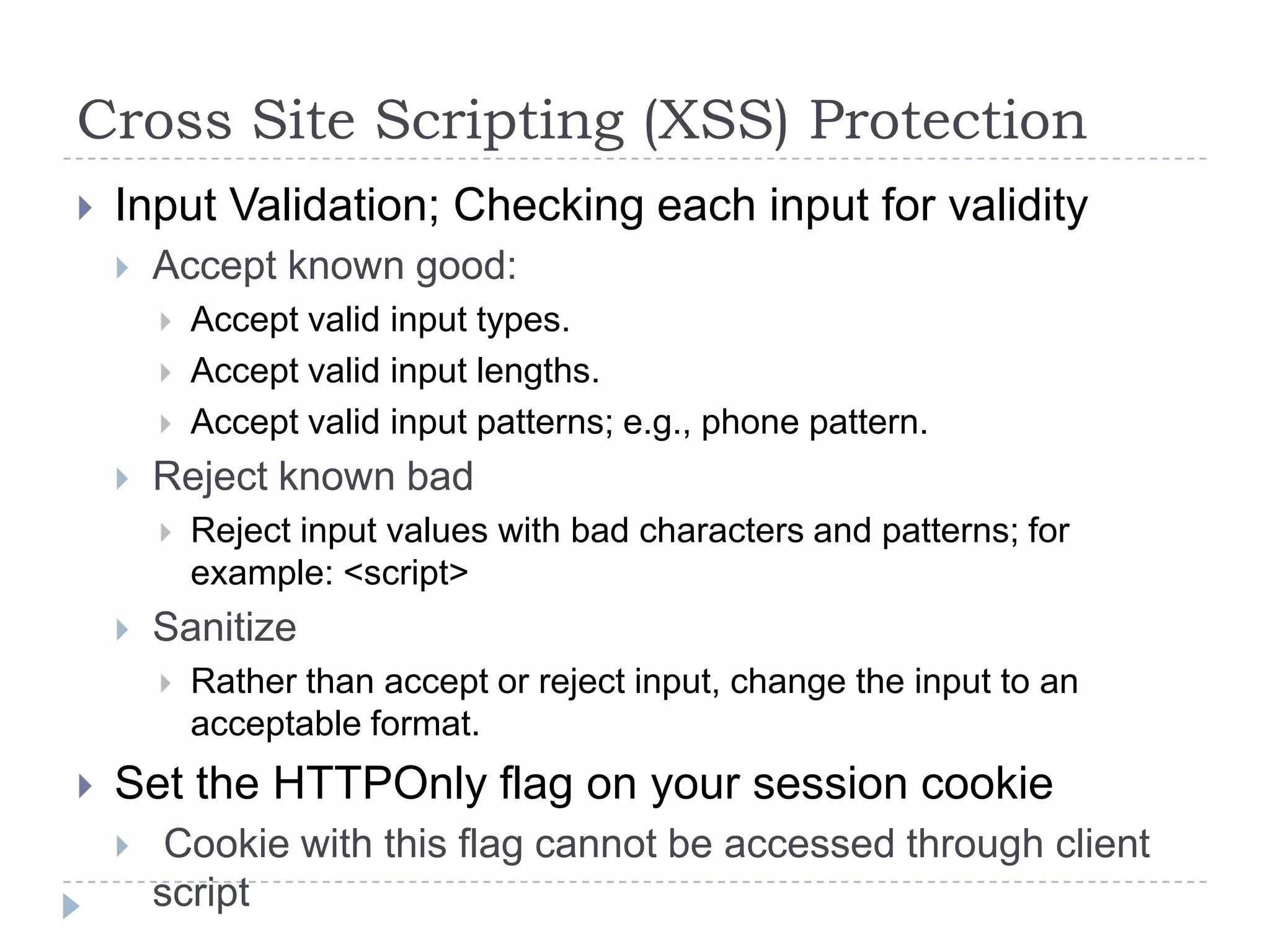
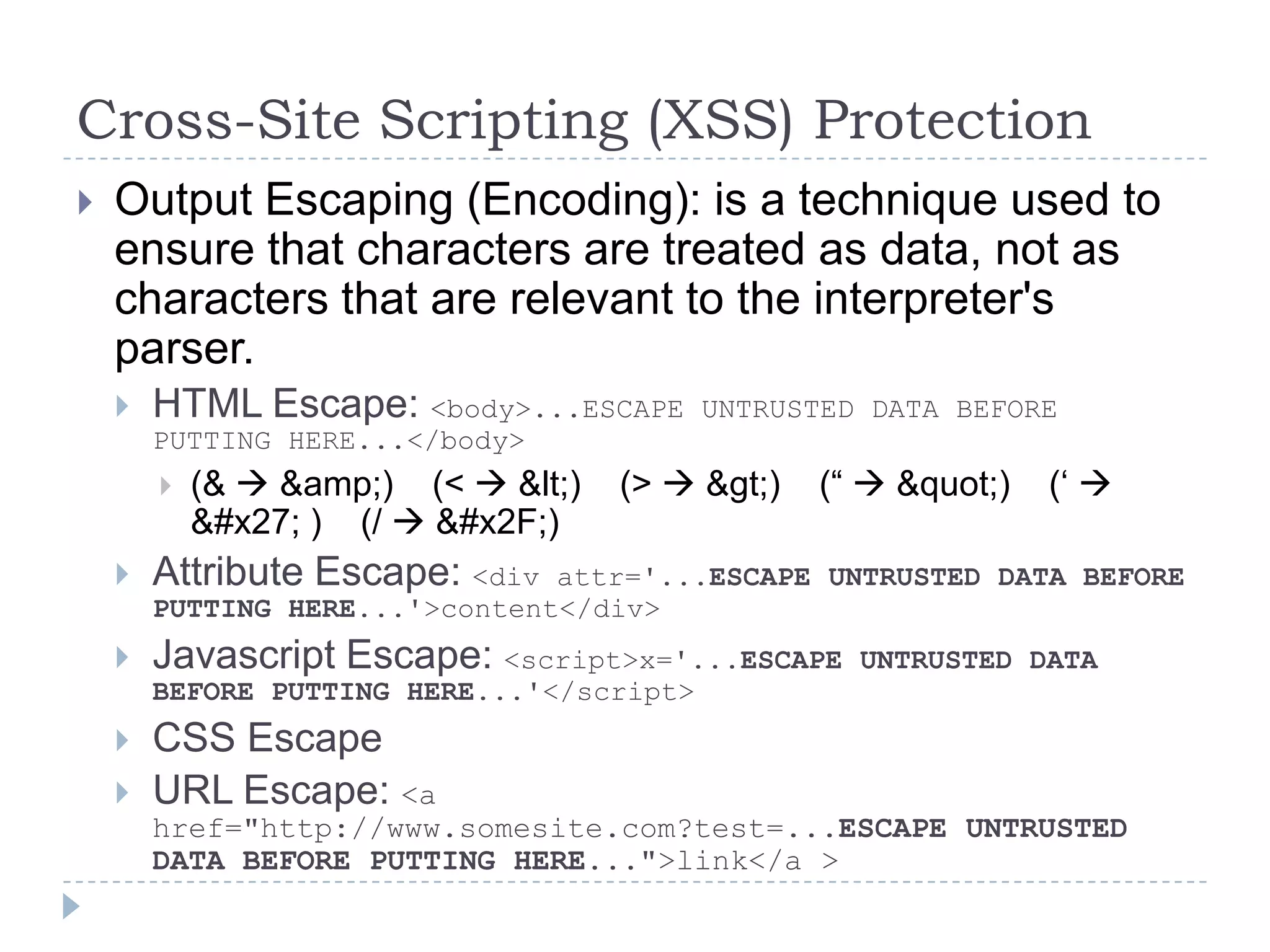
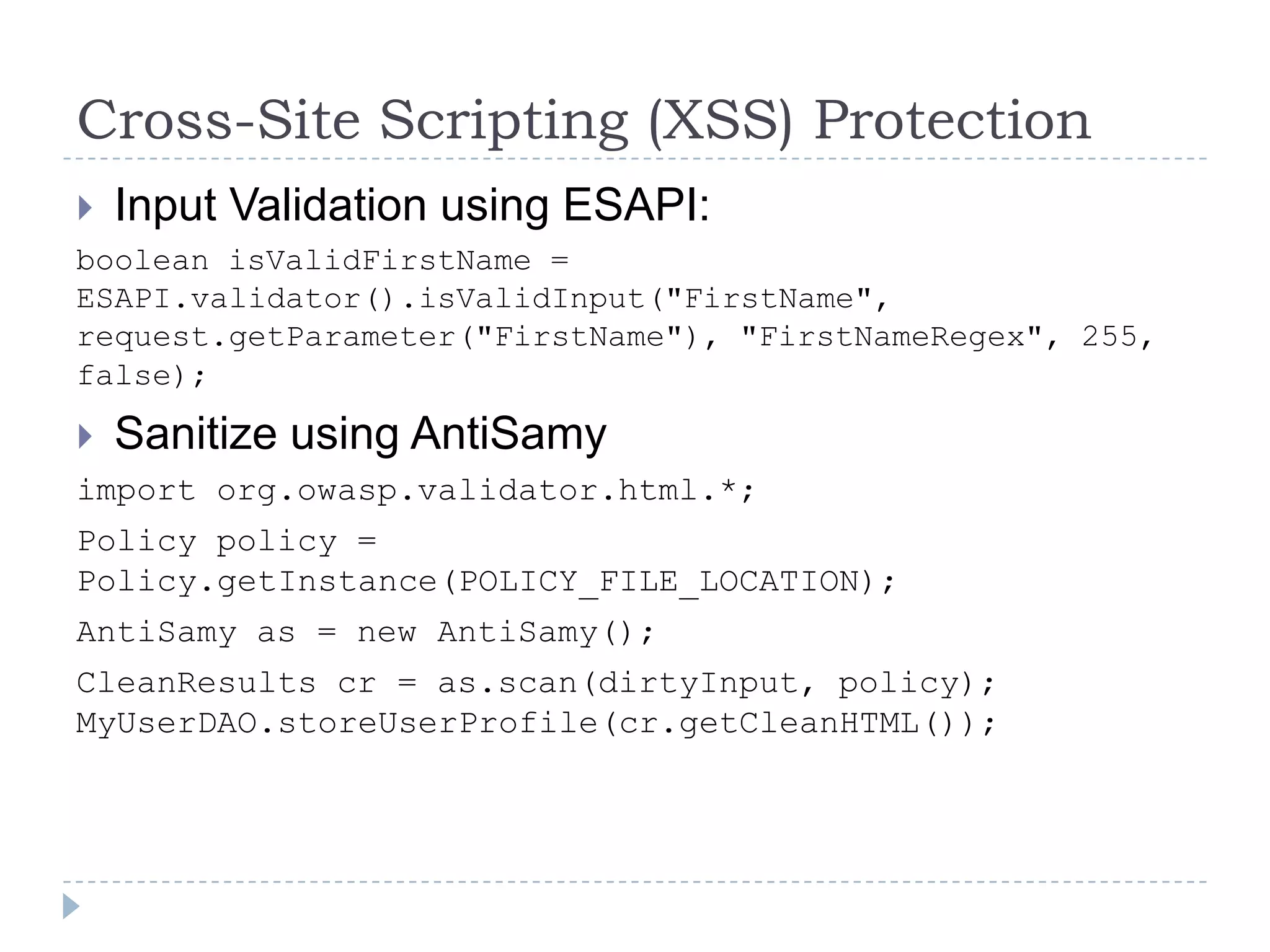
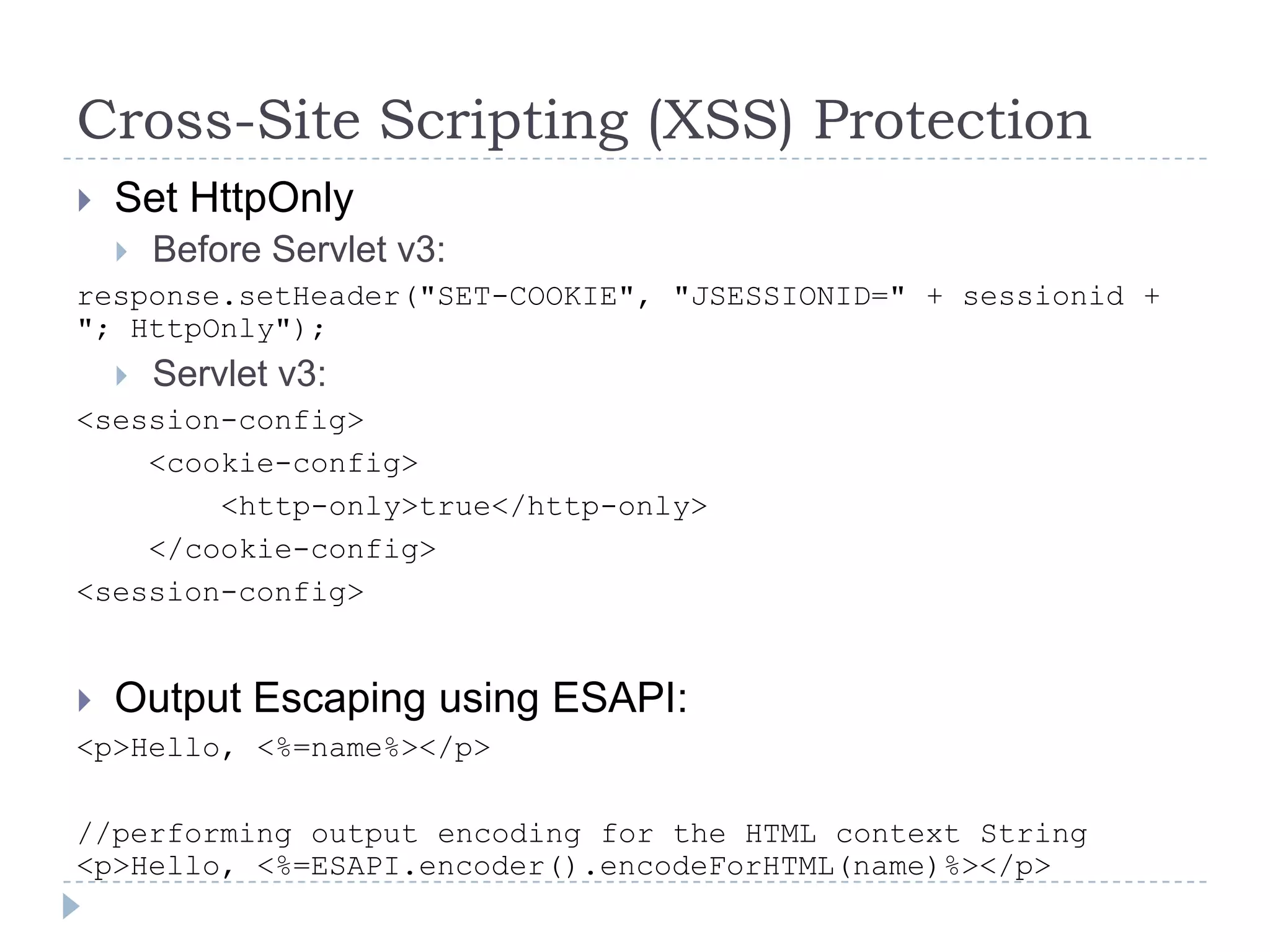
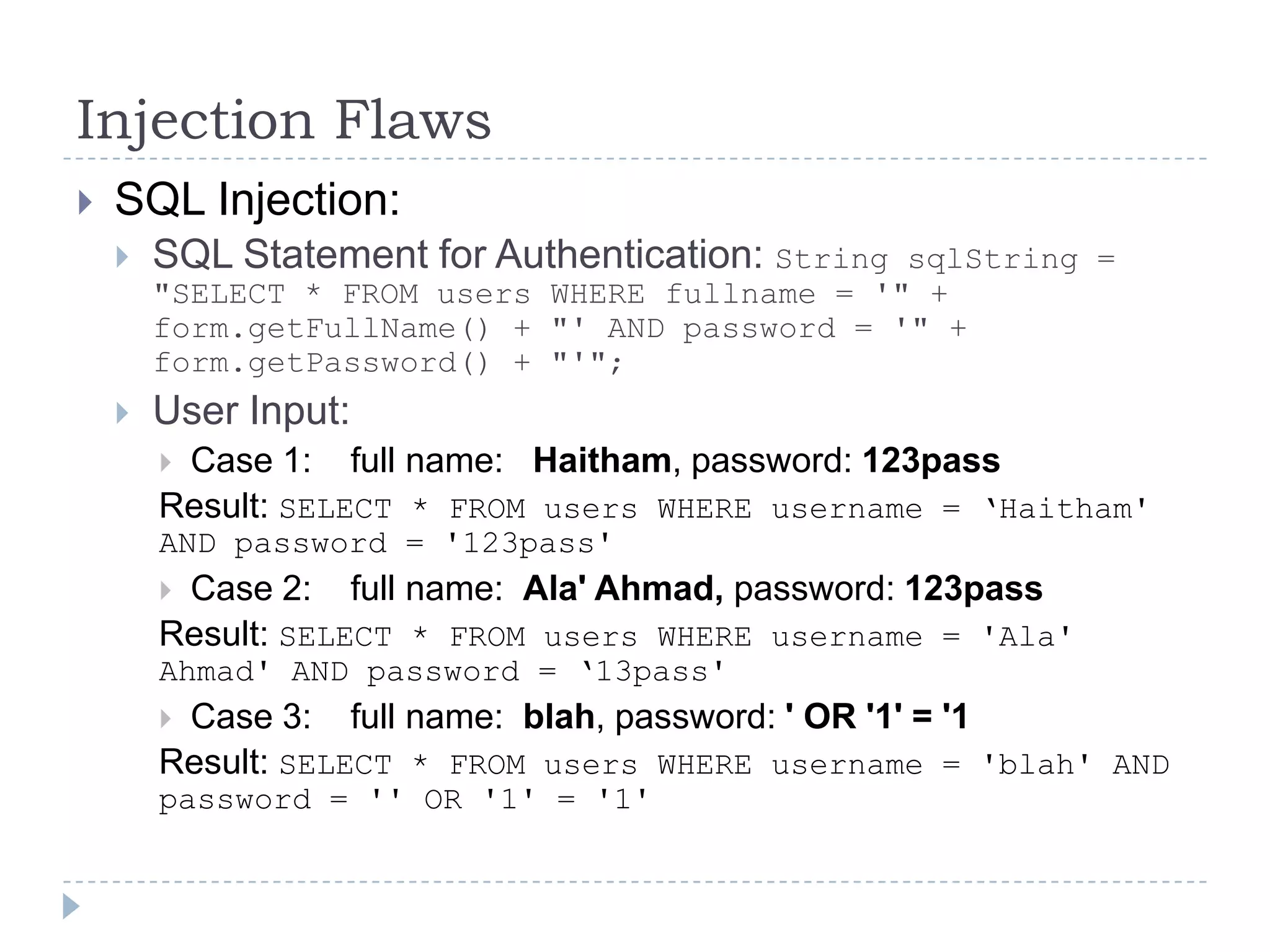
This document summarizes key PCI security requirements related to common web application vulnerabilities. It discusses requirements around proper error handling, cross-site scripting, injection flaws, malicious file execution, direct object references, and other issues. For each vulnerability, it provides definitions, examples, and recommendations for implementing controls like input validation, output encoding, prepared statements, and access control to help secure applications and protect cardholder data.


![Injection Flaws
XPATH Injection
XML file:
<?xml version="1.0" encoding="utf-8"?>
<employees>
<employee id="AS1" firstname="John" salary=“100"/>
<employee id="AS2" firstname=“Adam“ salary=“200"/>
</employees>
XPATH expression: String exp =
“/employees/employee[@id=„”+form.getEID()+”']”
User Input: Emp_ID=„ or '1'='1
Result: /employees/employee[@id=„„ or '1'='1']](https://image.slidesharecdn.com/pcisecurityrequirements-securecoding-121116113213-phpapp02/75/PCI-Security-Requirements-secure-coding-14-2048.jpg)


![Injection Flaws Protection
XPATH Injection Protection
User input must not contain any of the following
characters:
( ) = ' [ ] : , * / WHITESPACE
XPATH Injection protection using ESAPI
String exp = “/employees/employee[@id=„”+
ESAPI.encoder().encodeForXPath(form.getEID())+
”']”](https://image.slidesharecdn.com/pcisecurityrequirements-securecoding-121116113213-phpapp02/75/PCI-Security-Requirements-secure-coding-17-2048.jpg)