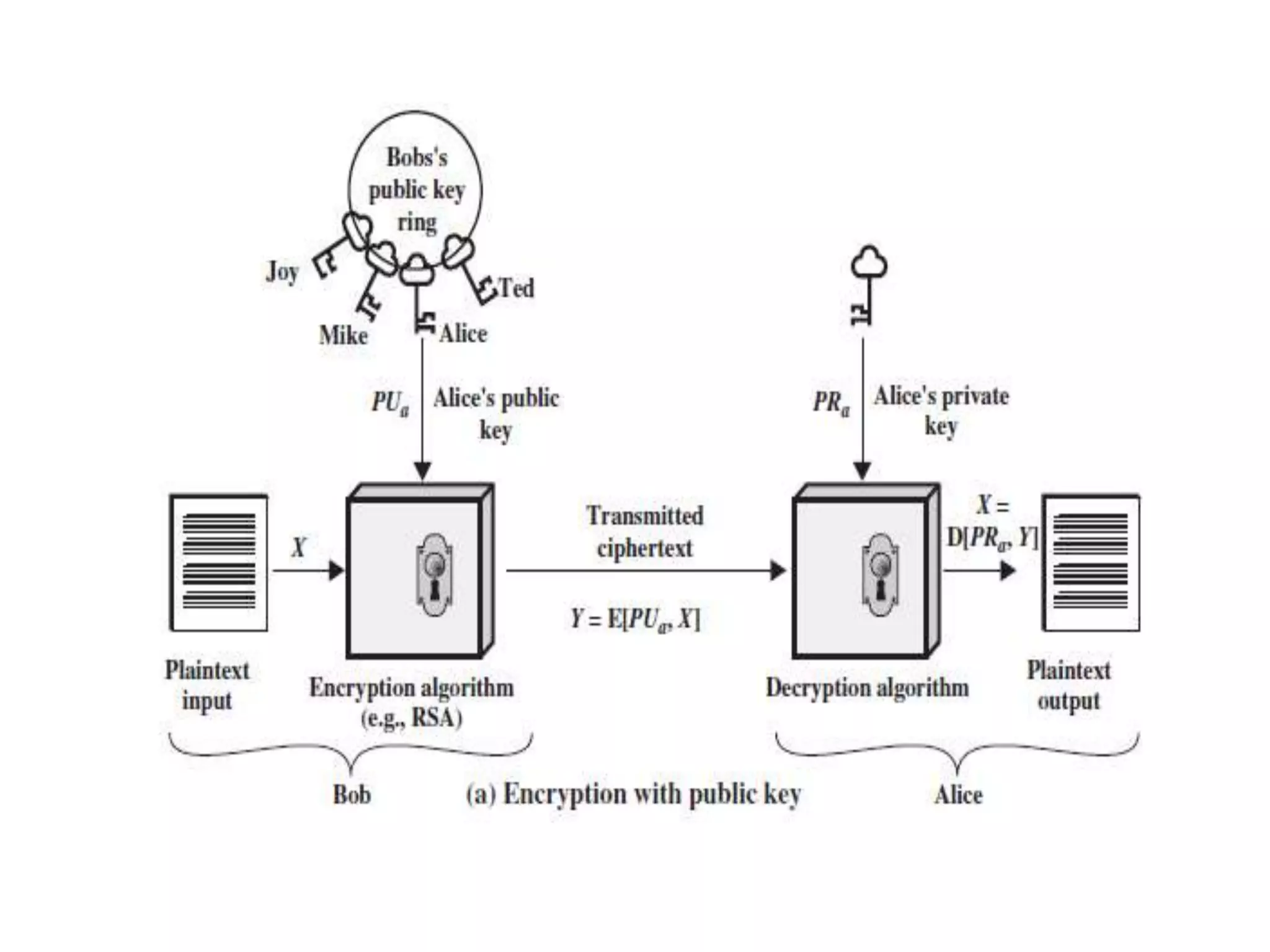
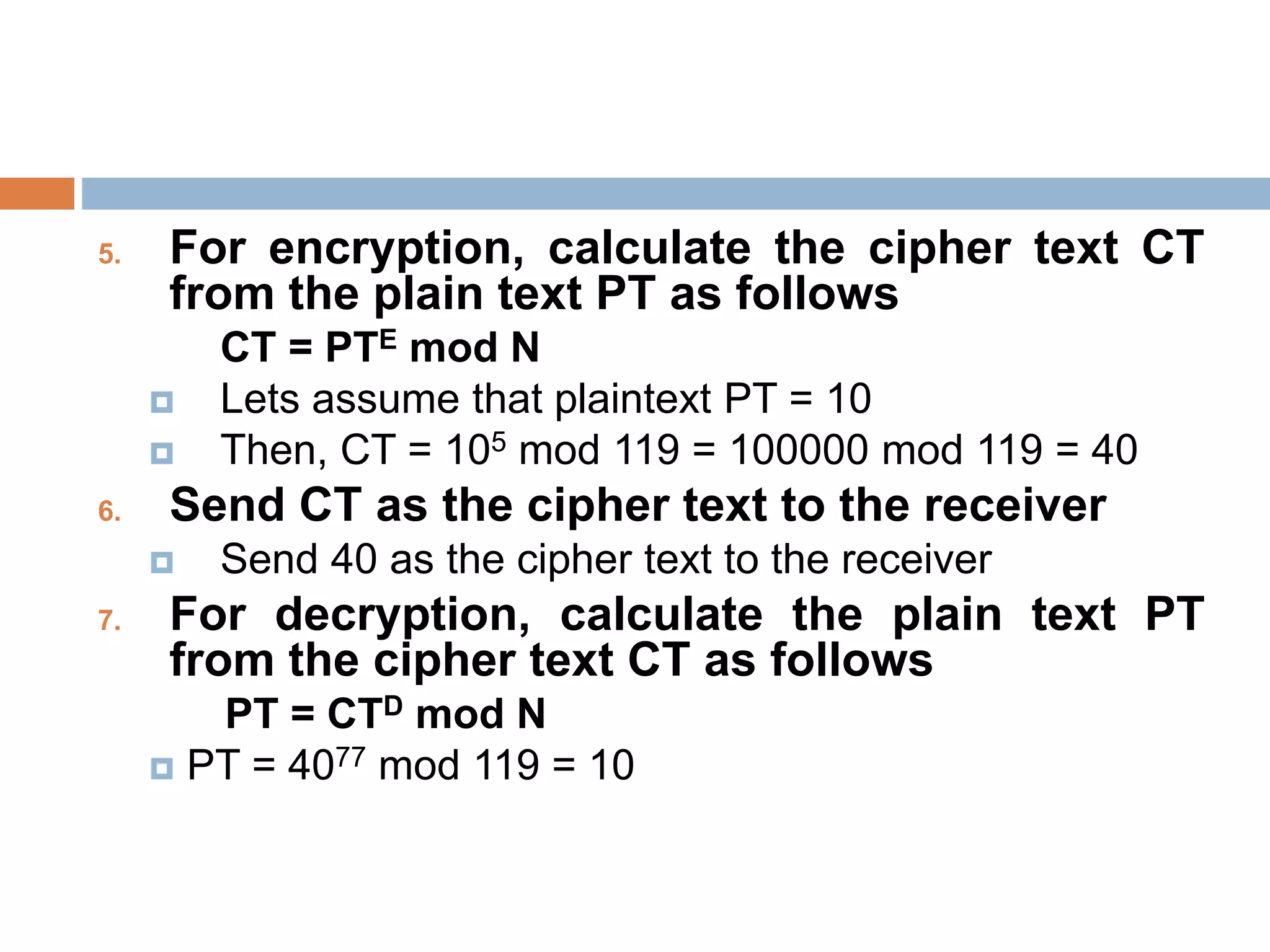
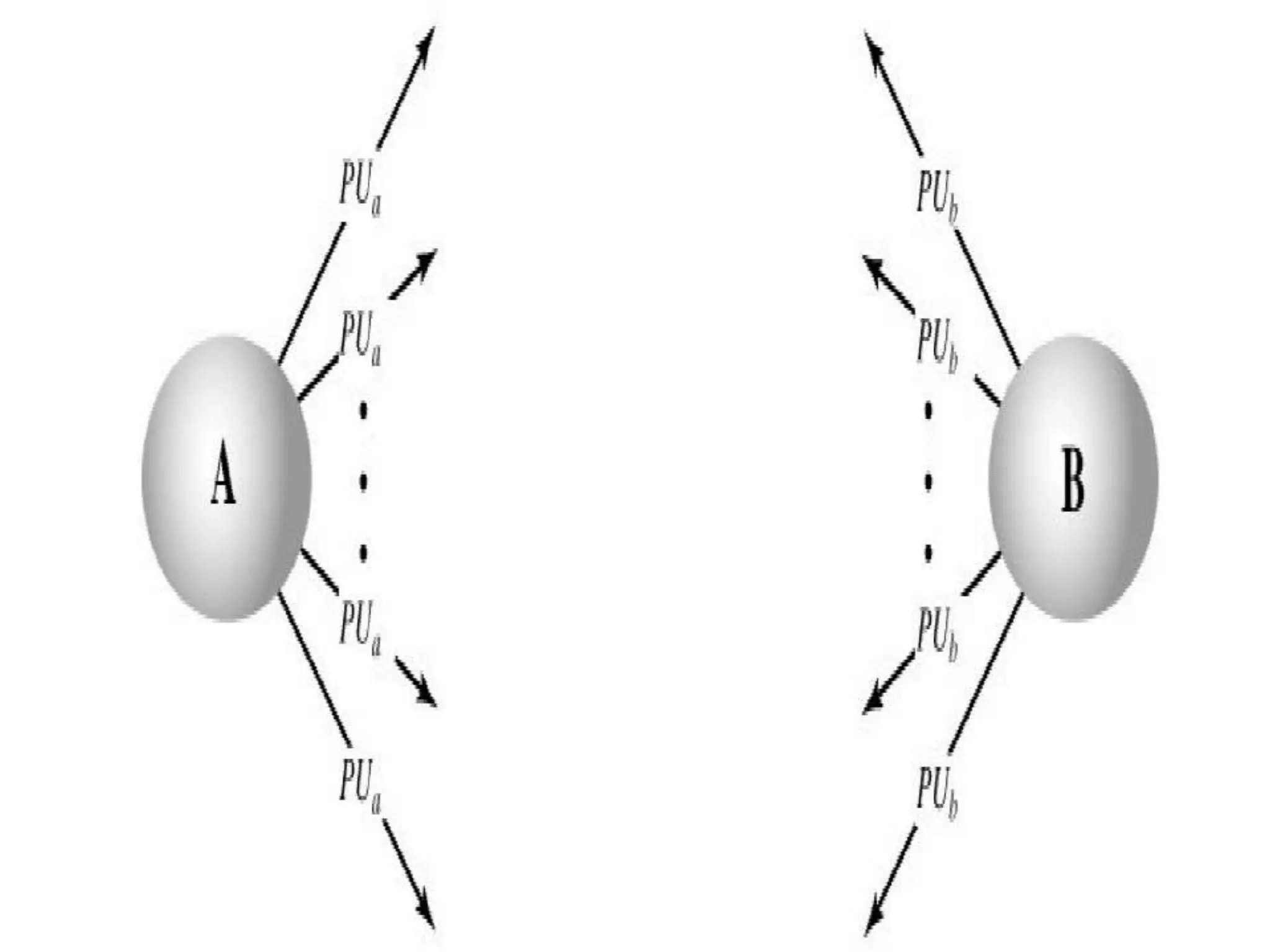
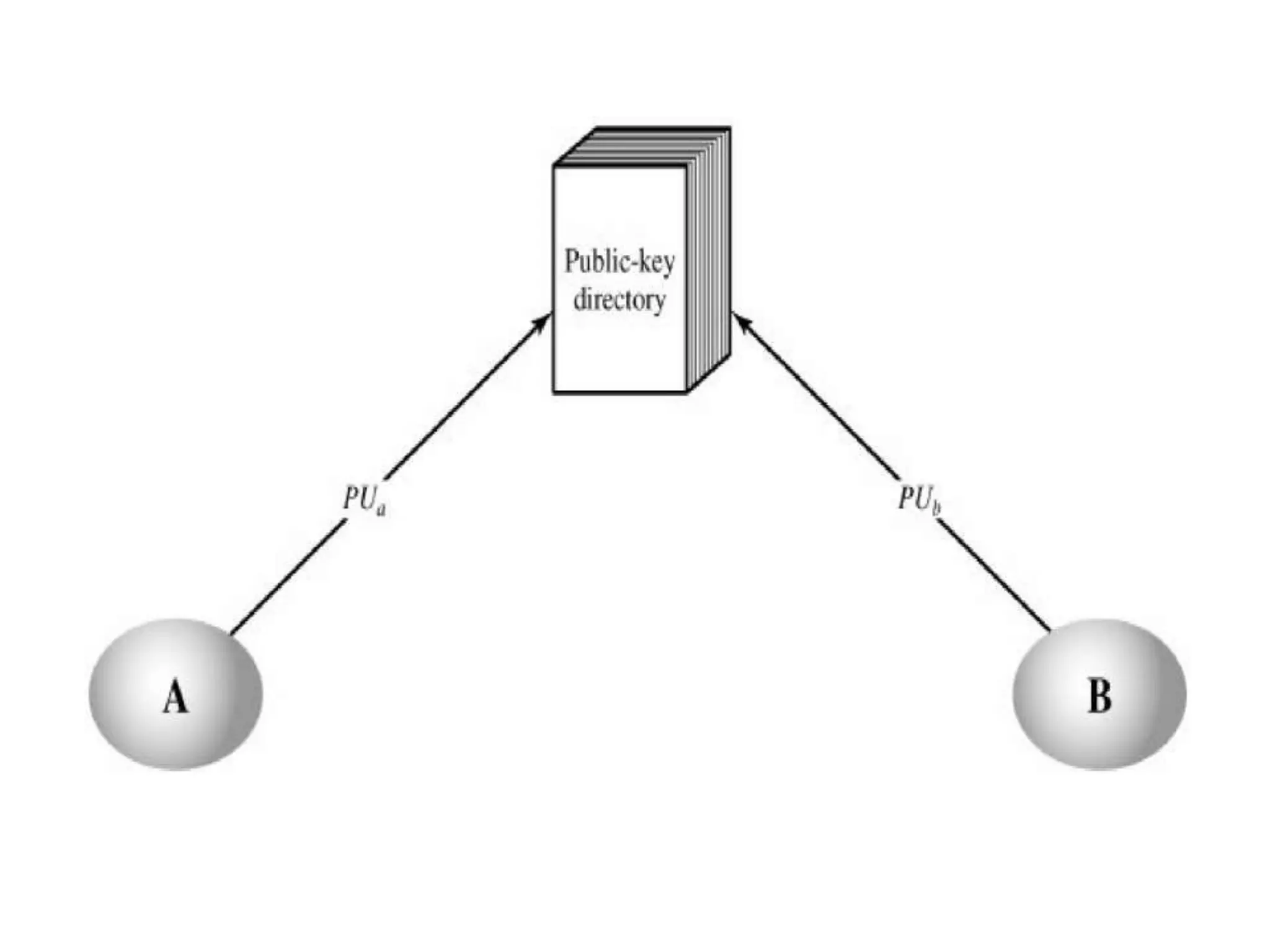
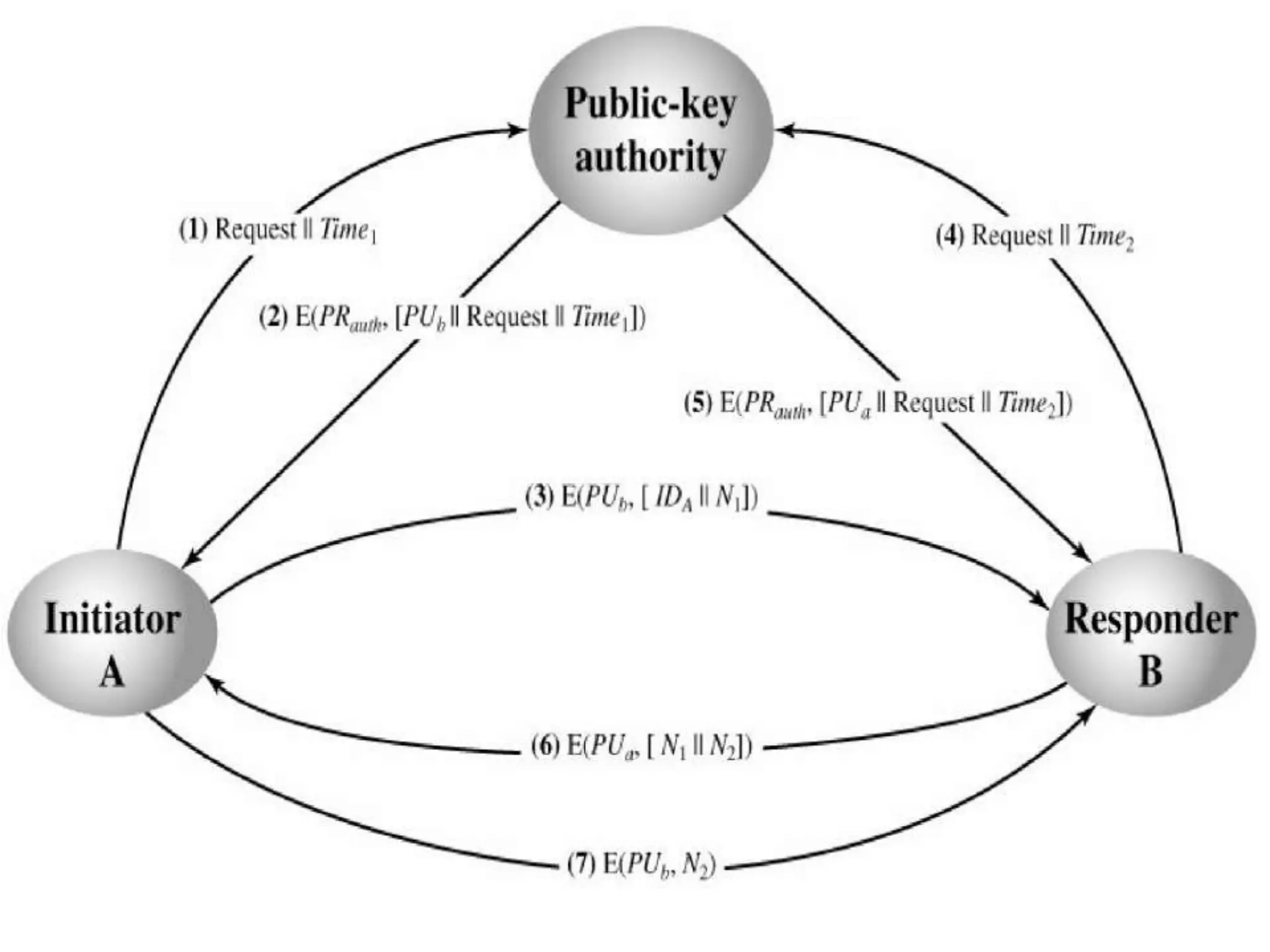
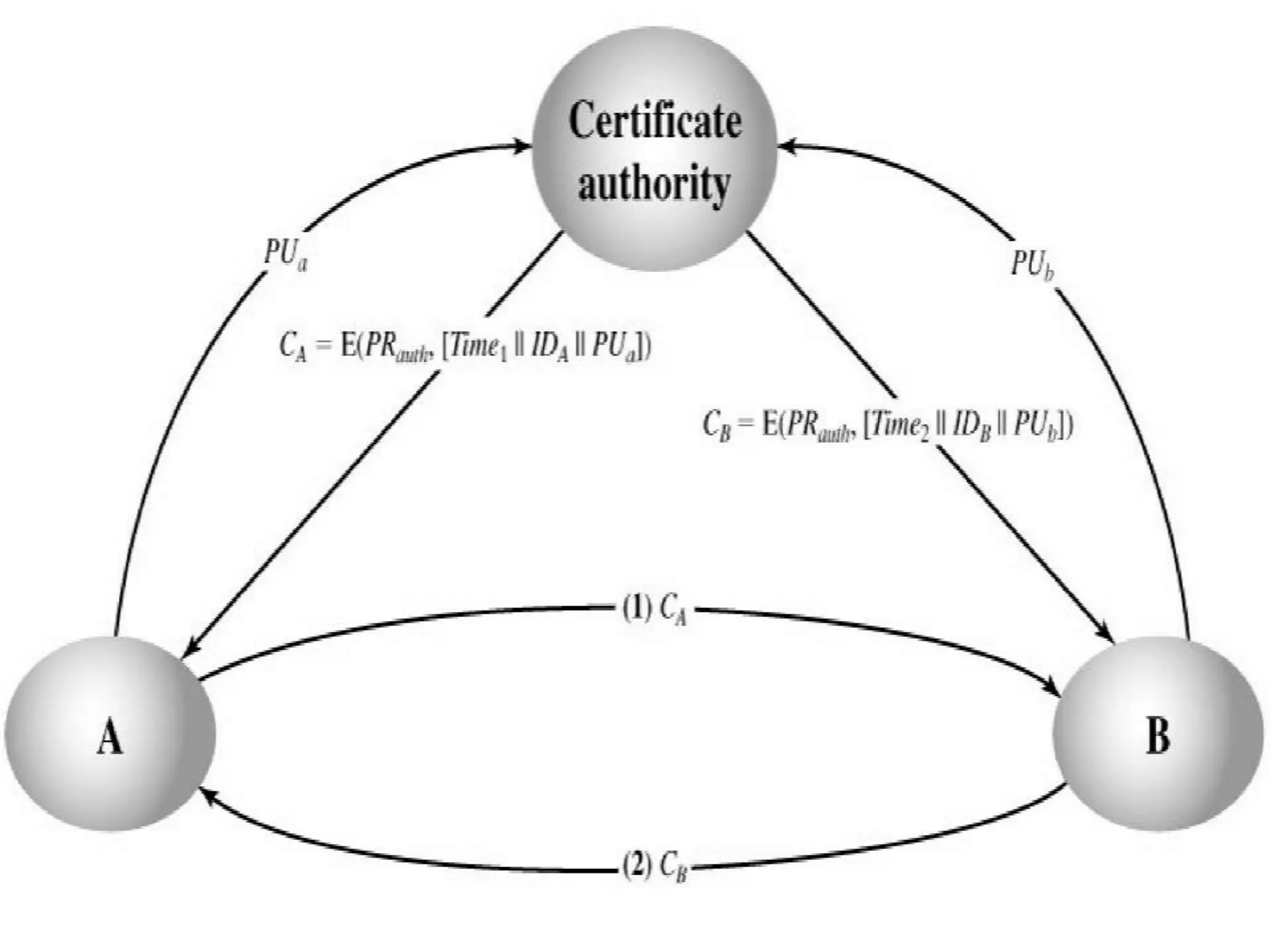
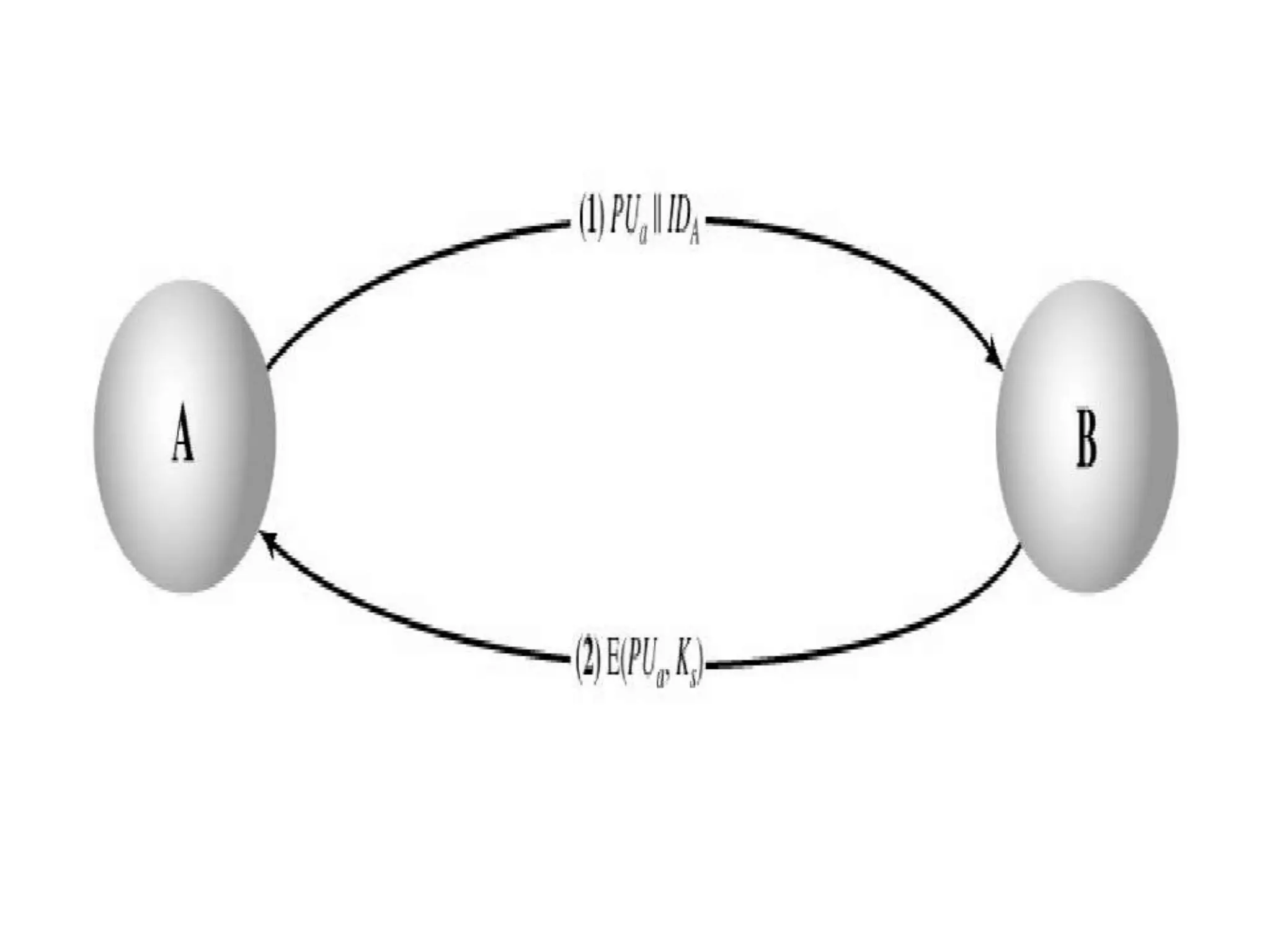
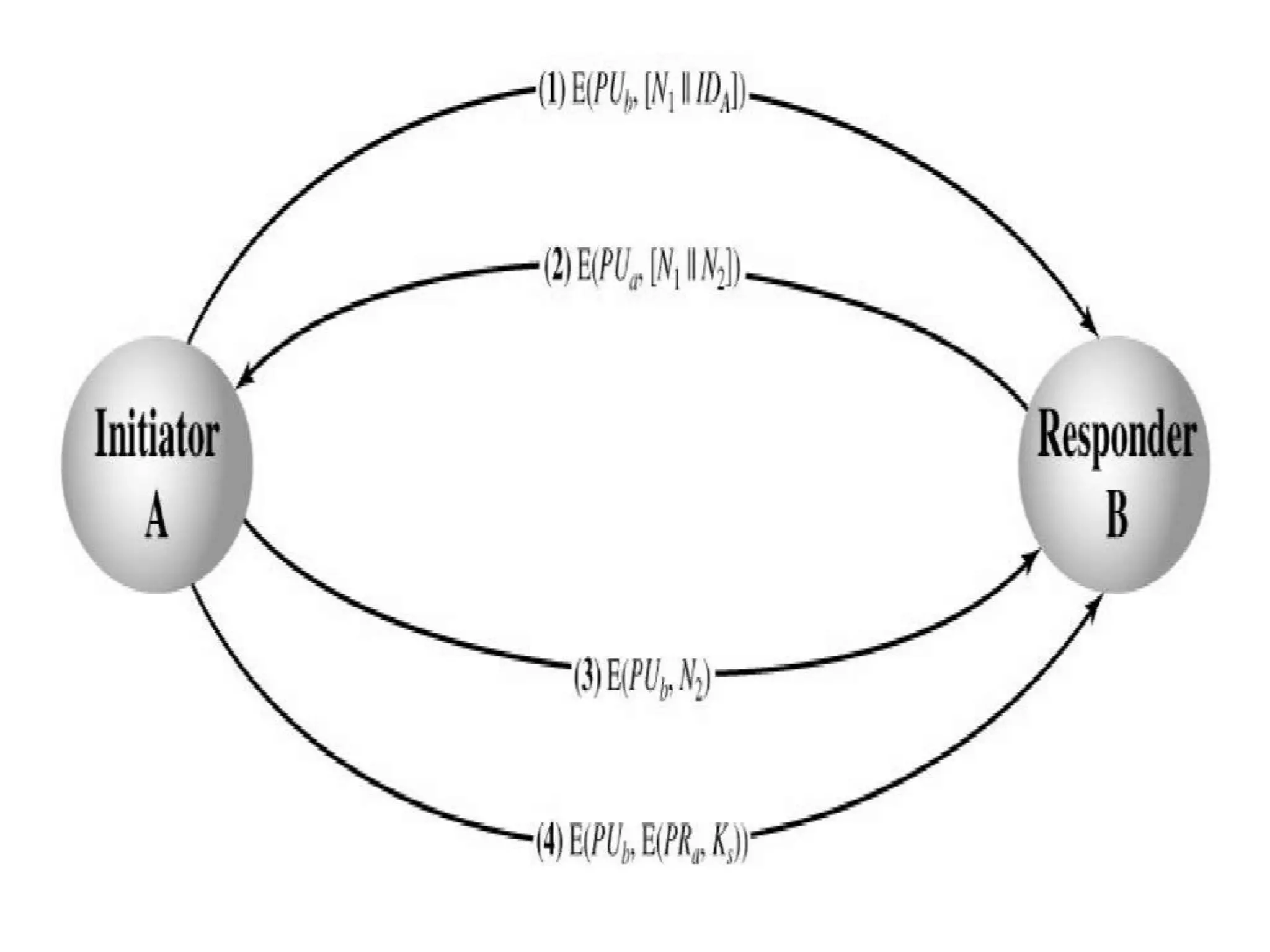
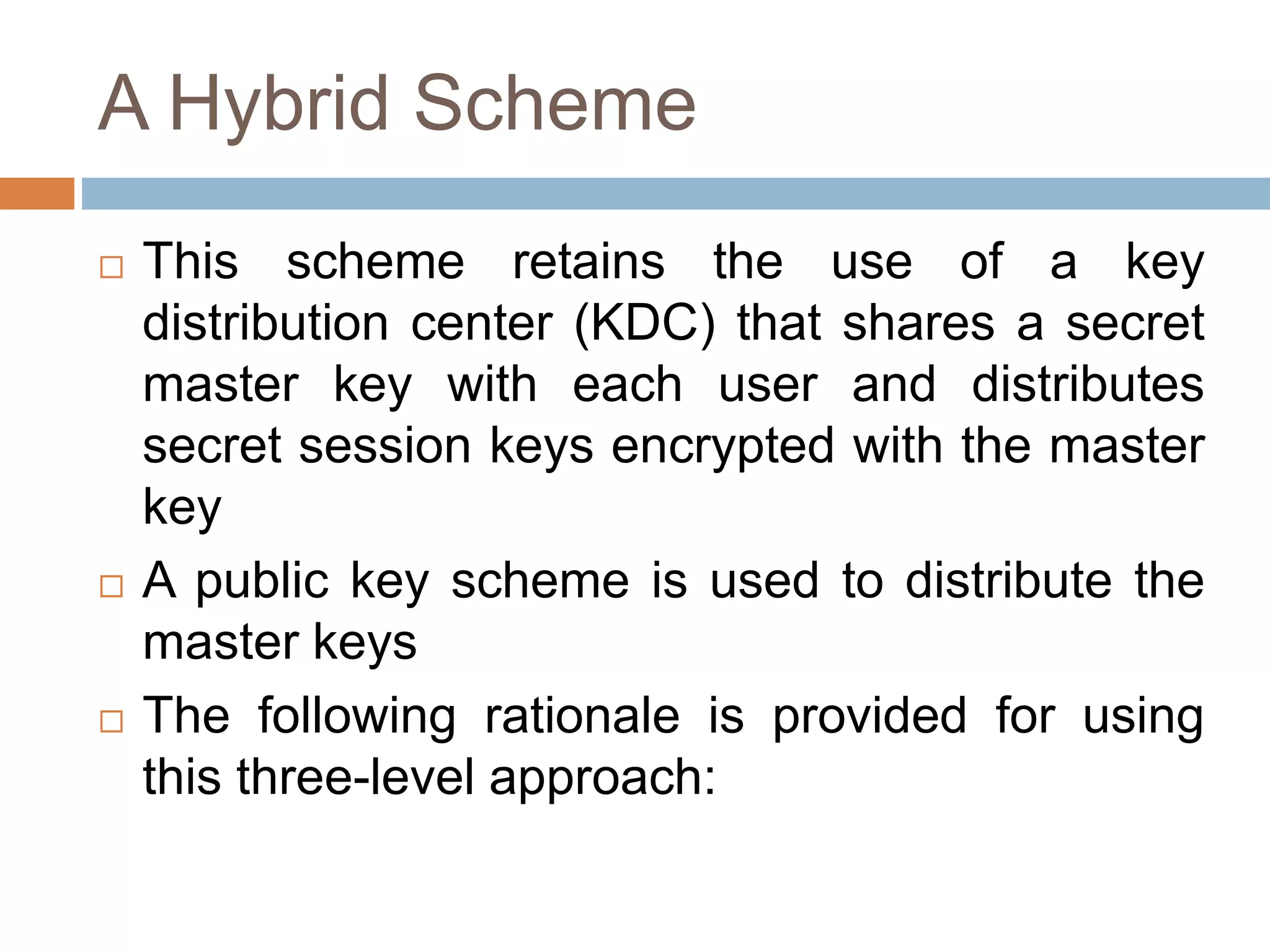
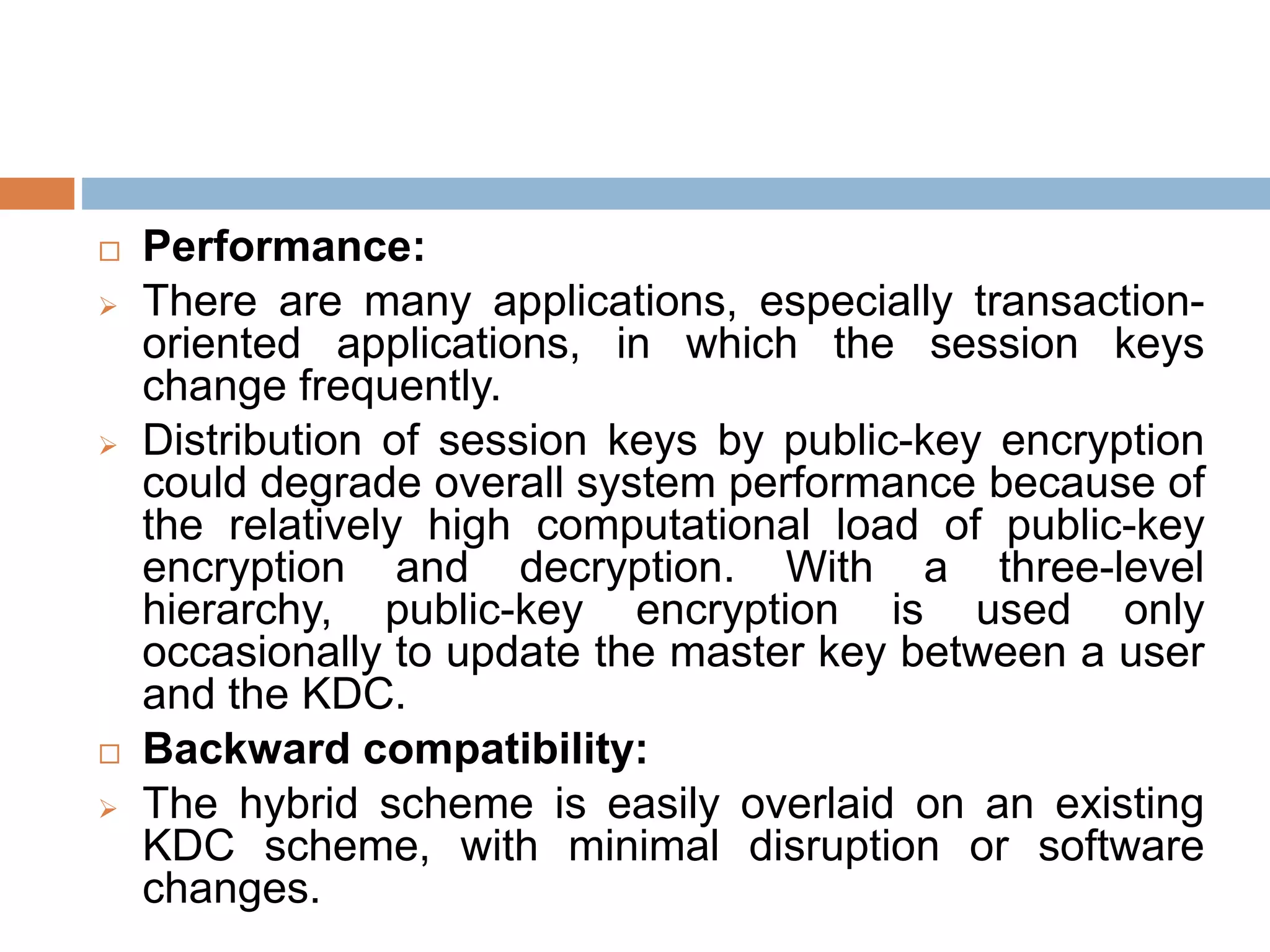
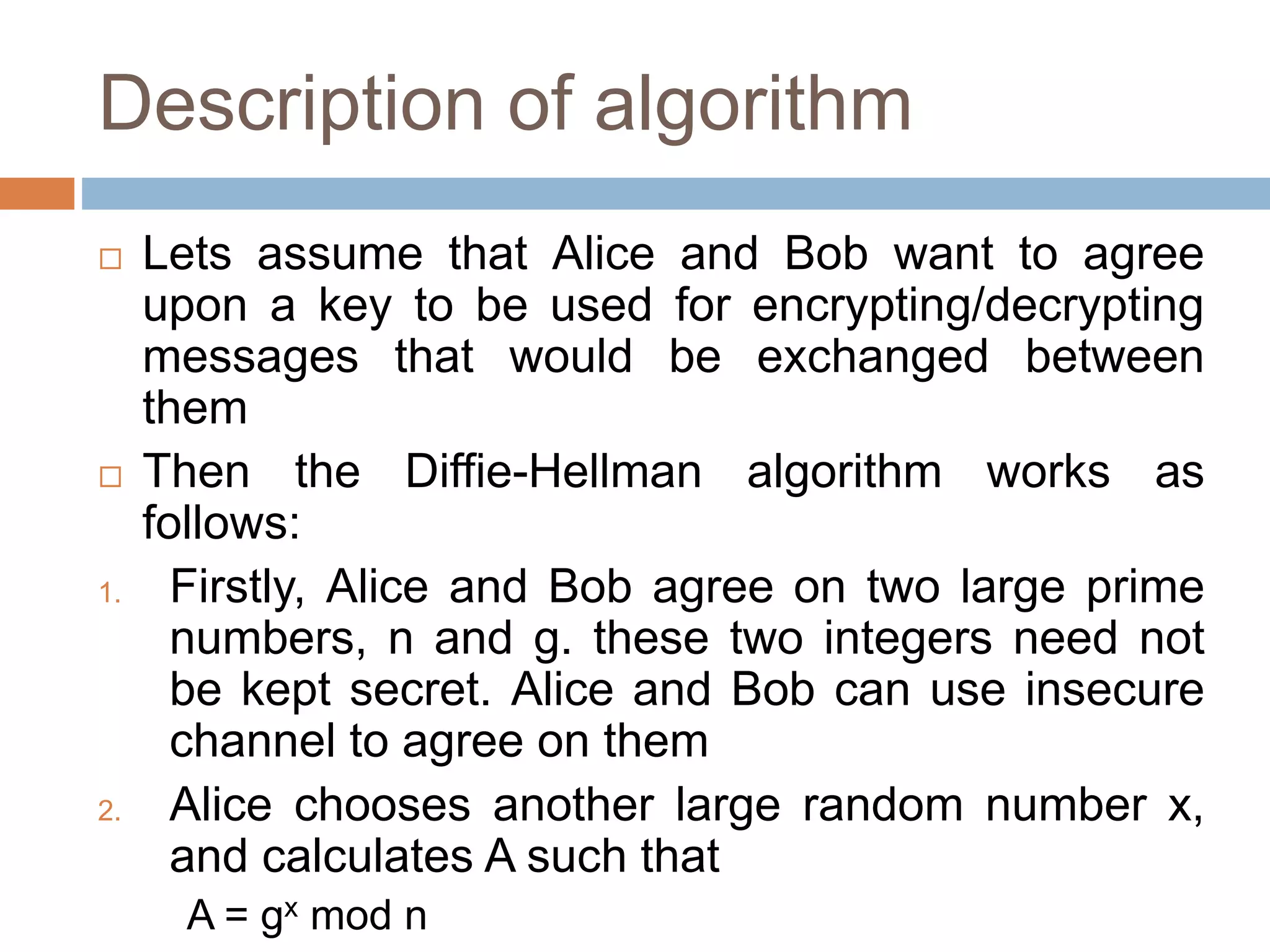
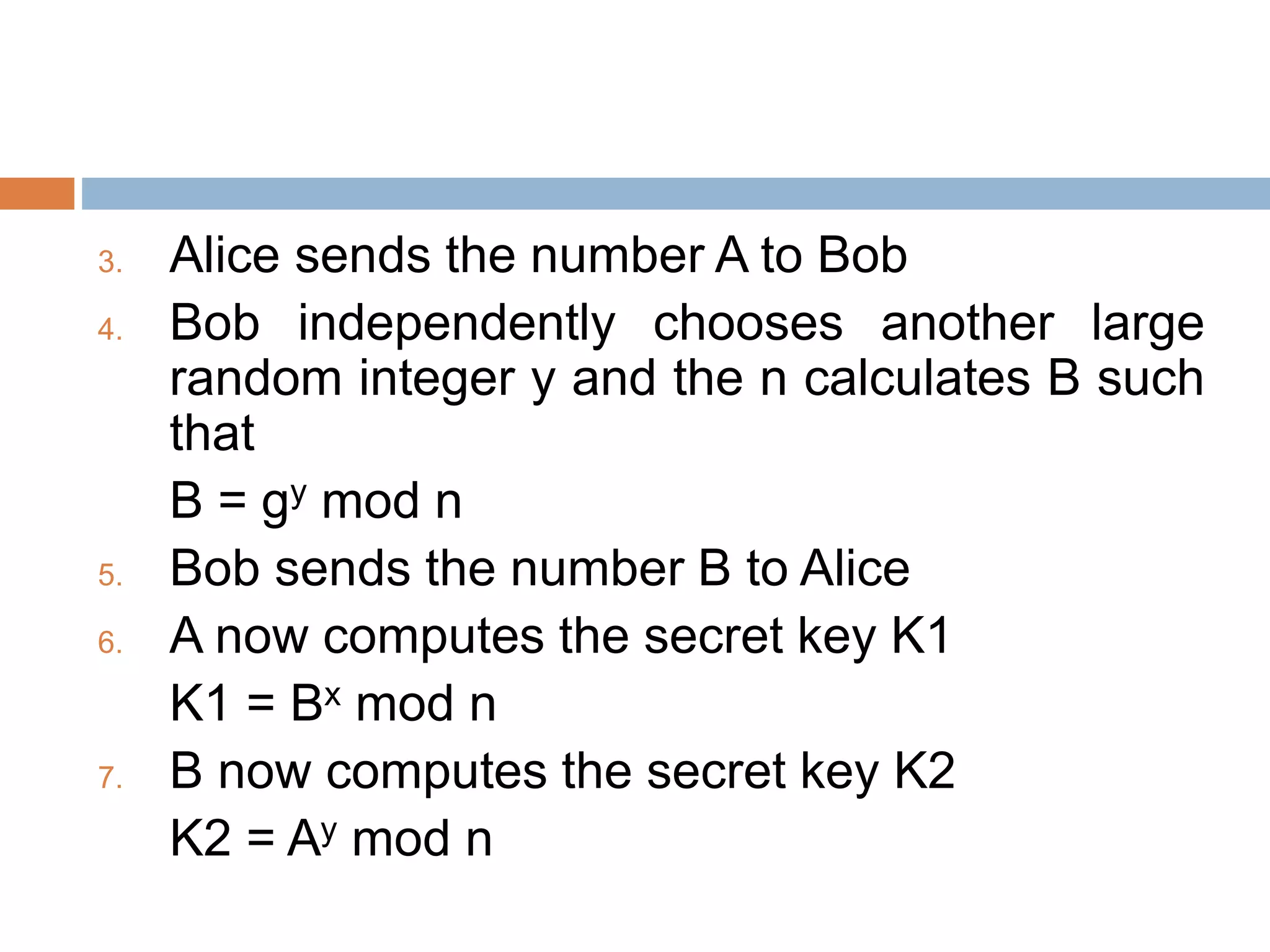
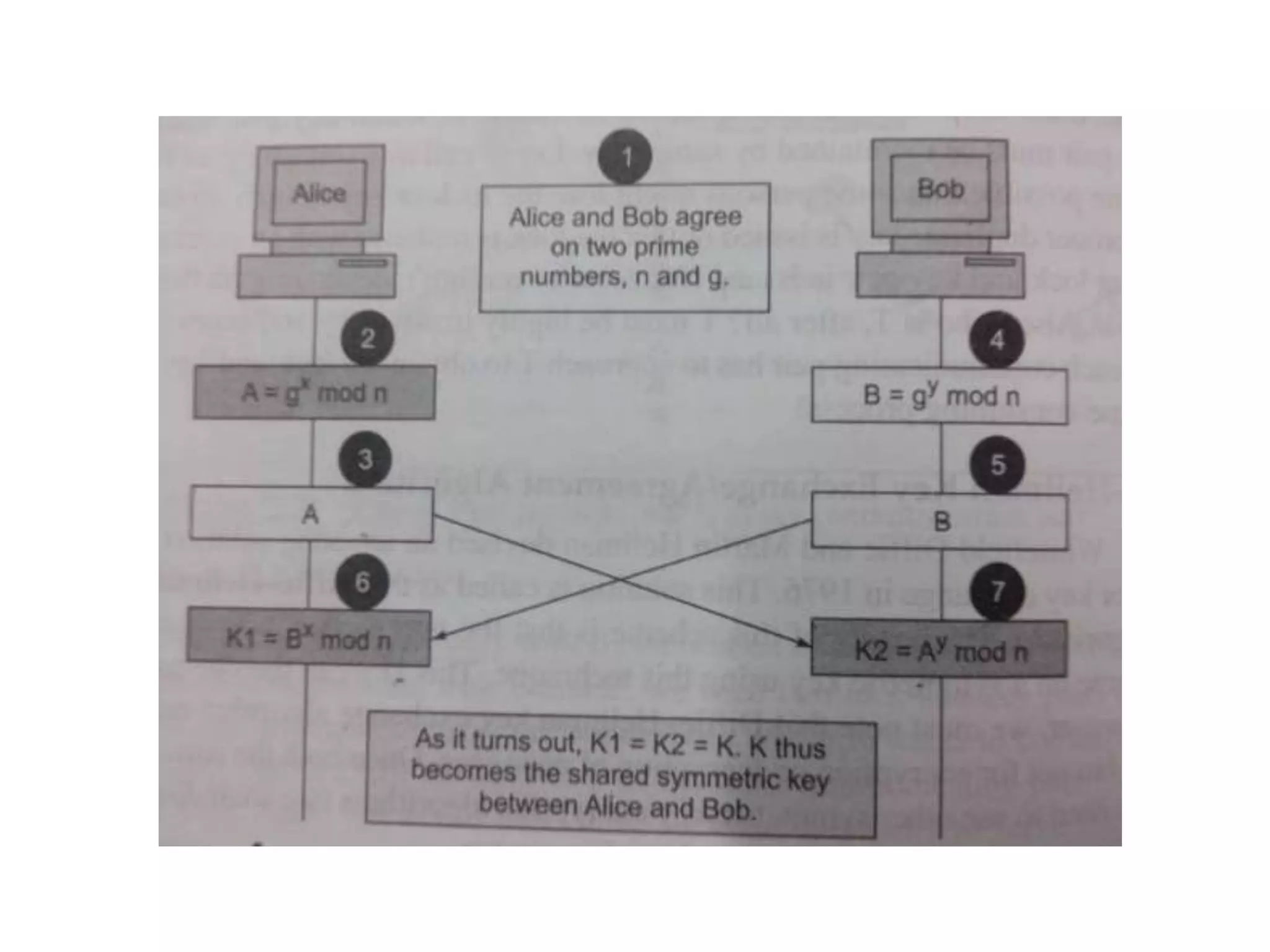
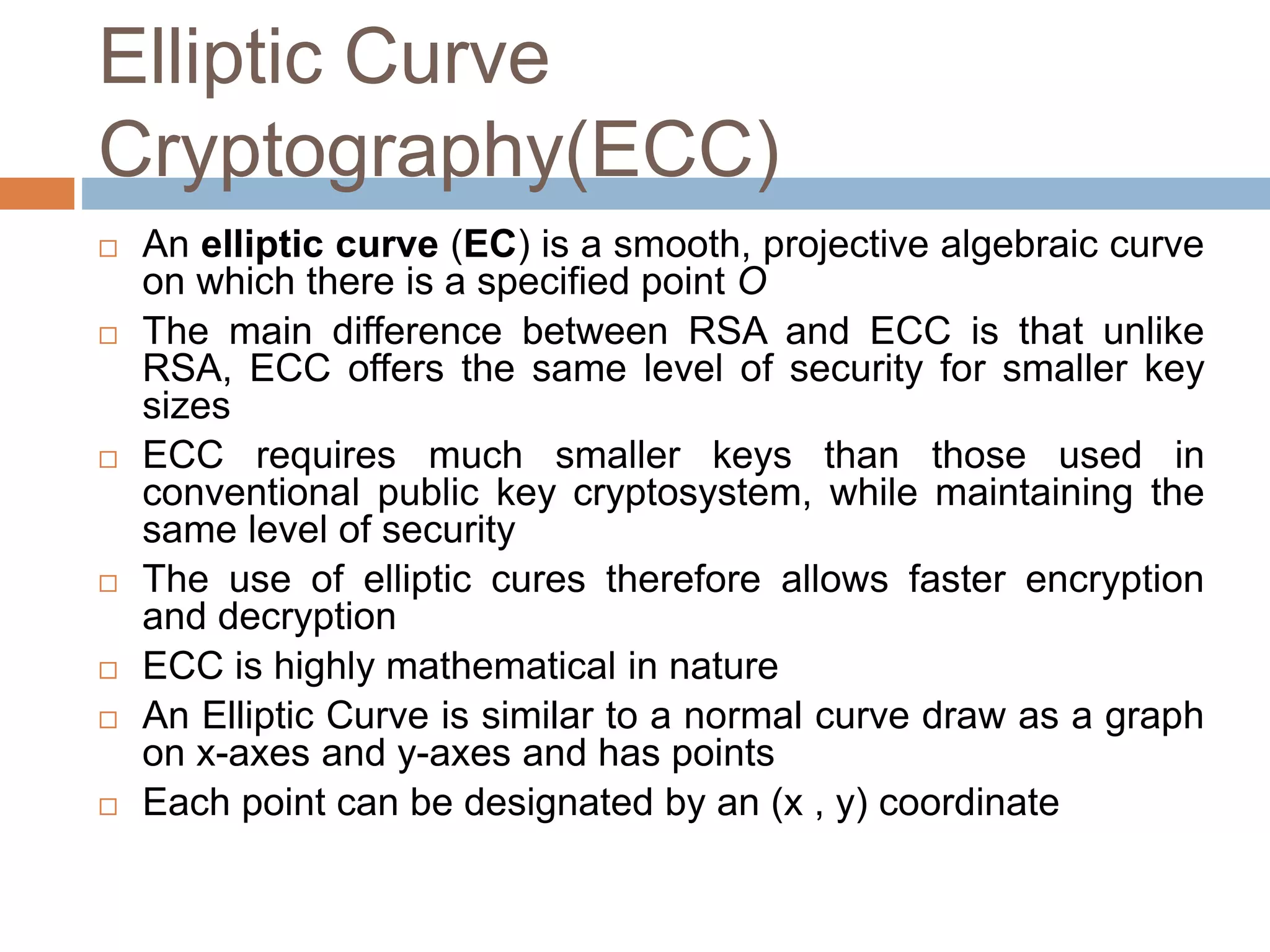
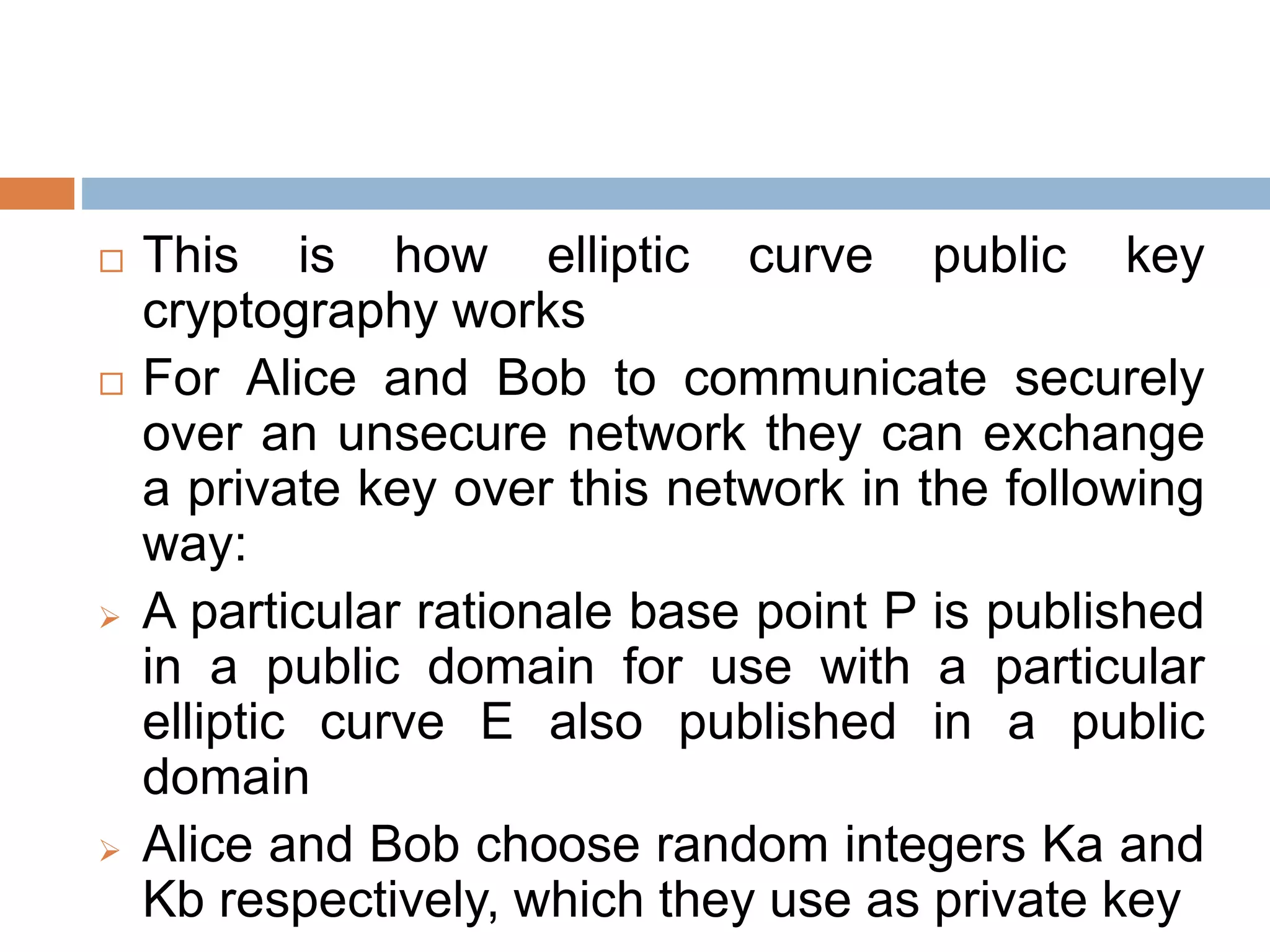
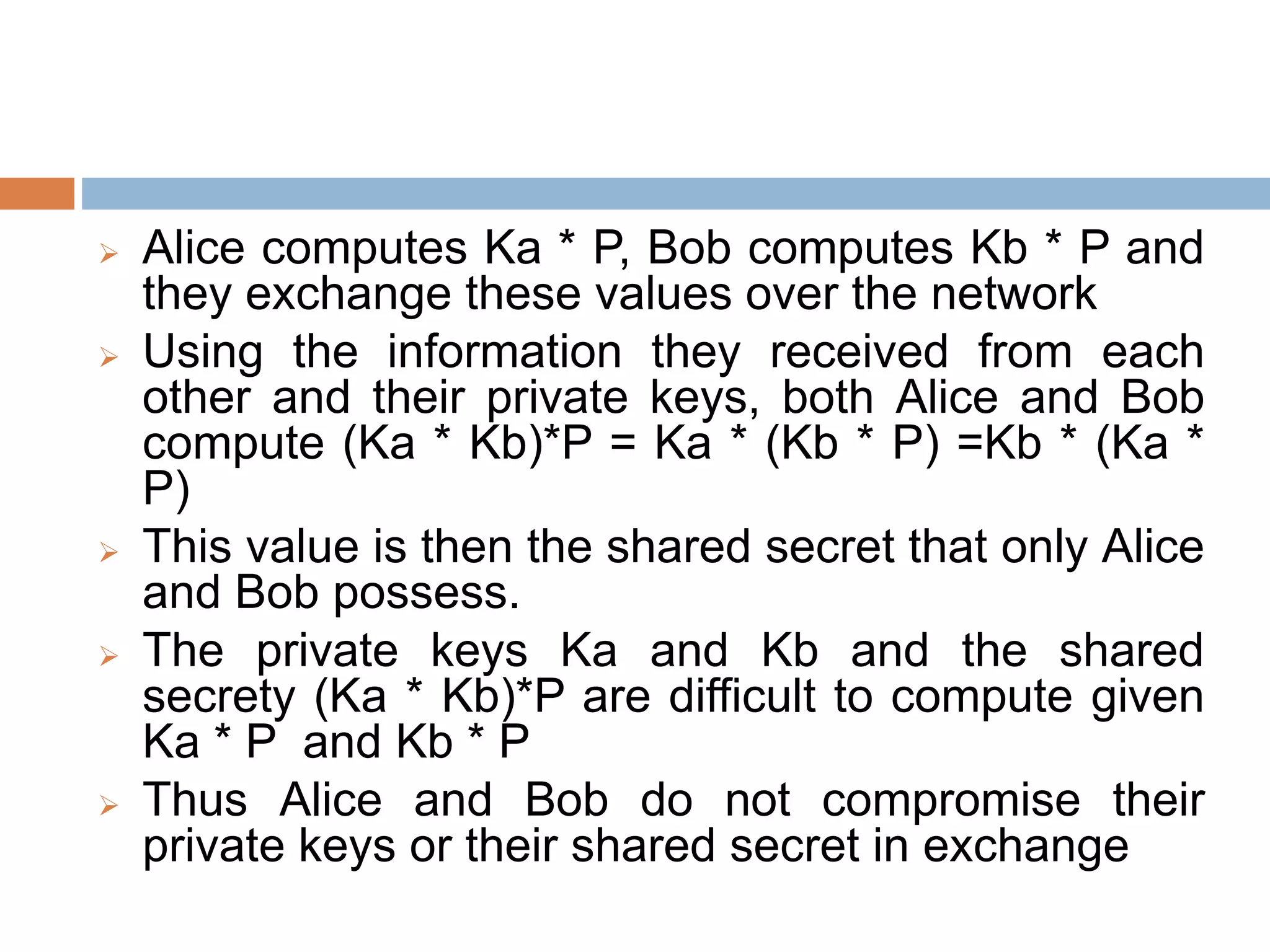
This document discusses the principles of public key cryptography. It begins by defining asymmetric encryption and how it uses a public key and private key instead of a single shared key. It then discusses key concepts like digital certificates and public key infrastructure. The document also provides examples of how public key cryptography can be used, including the RSA algorithm and key distribution methods like public key directories and certificates. It explains how public key cryptography solves the key distribution problem present in symmetric encryption.