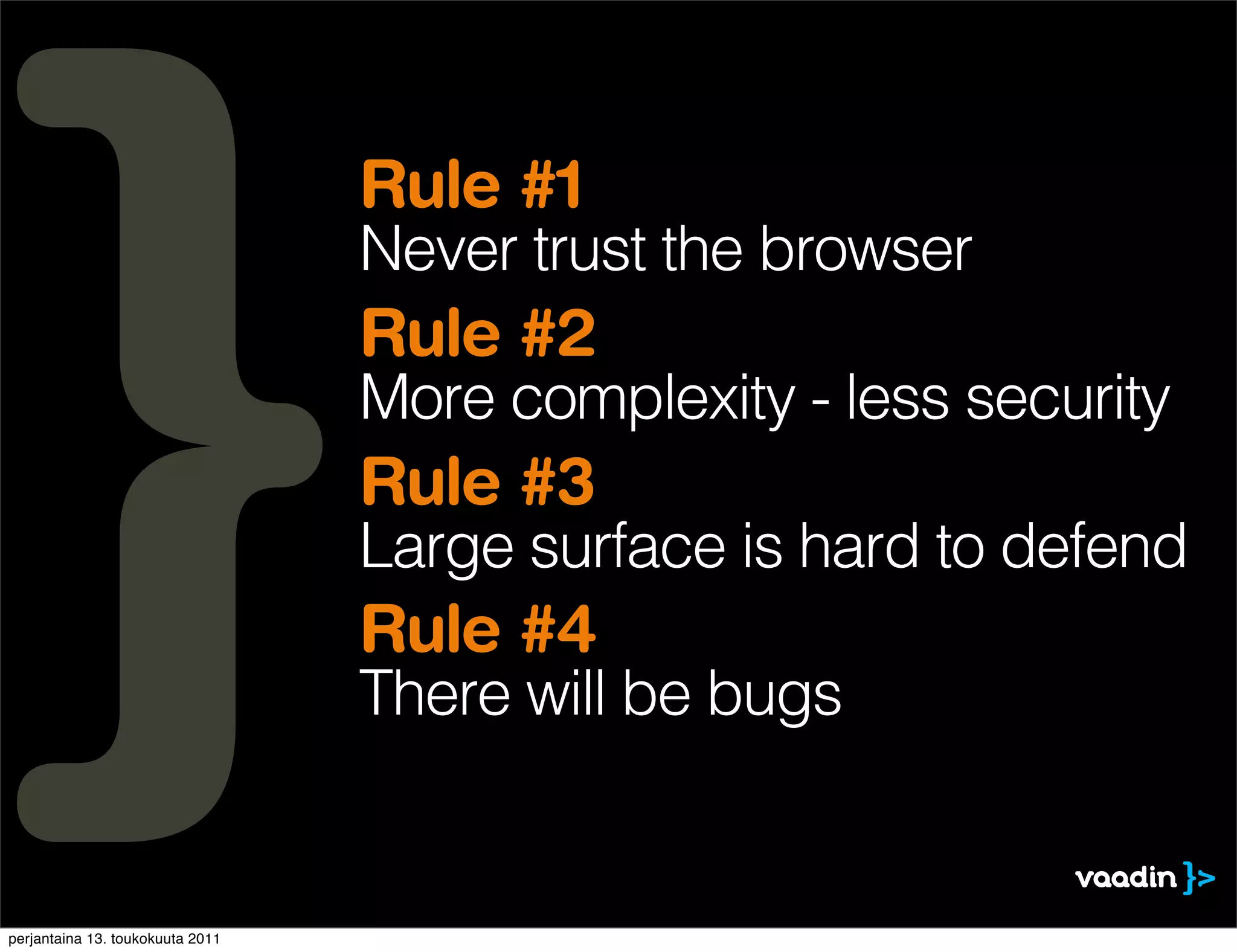
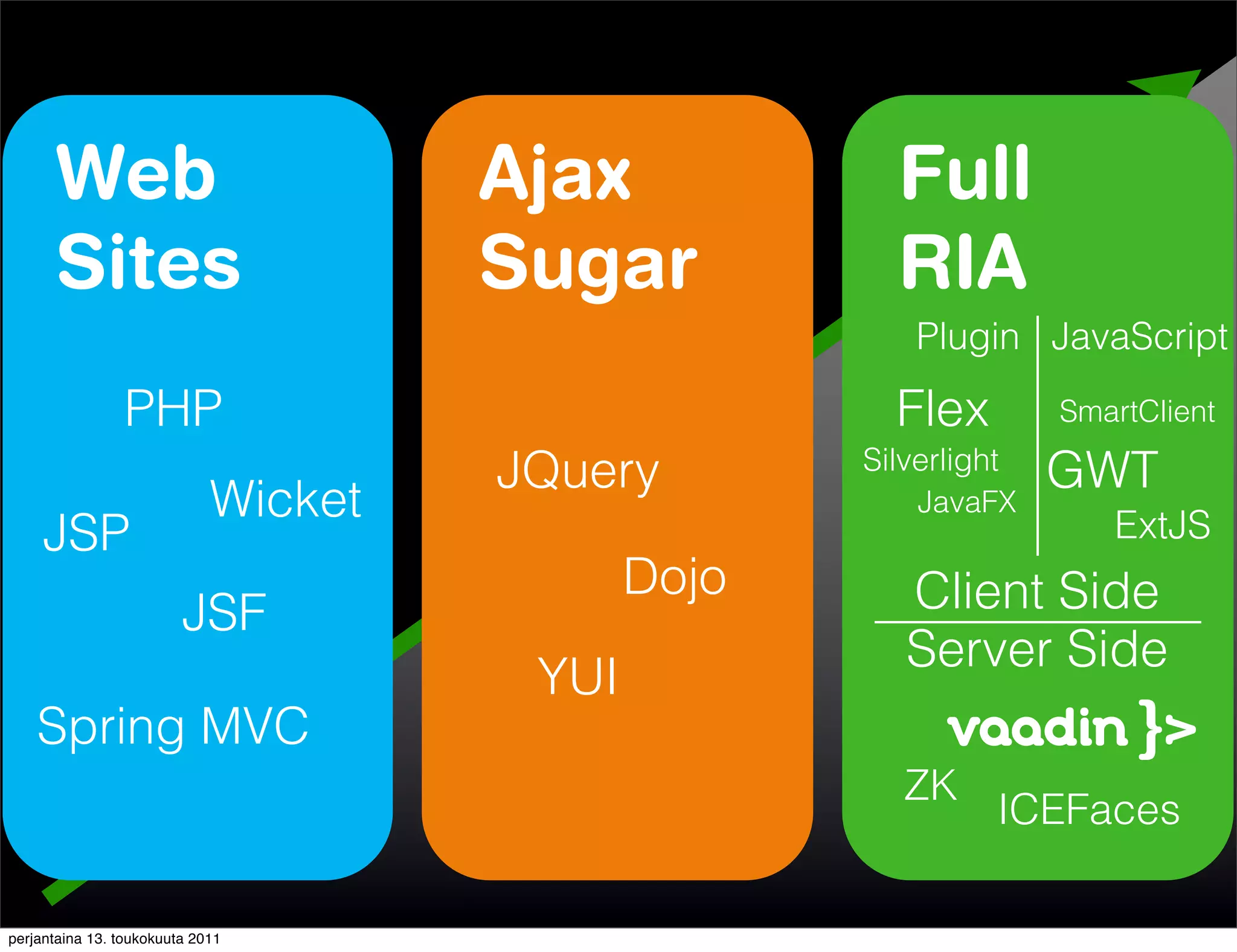
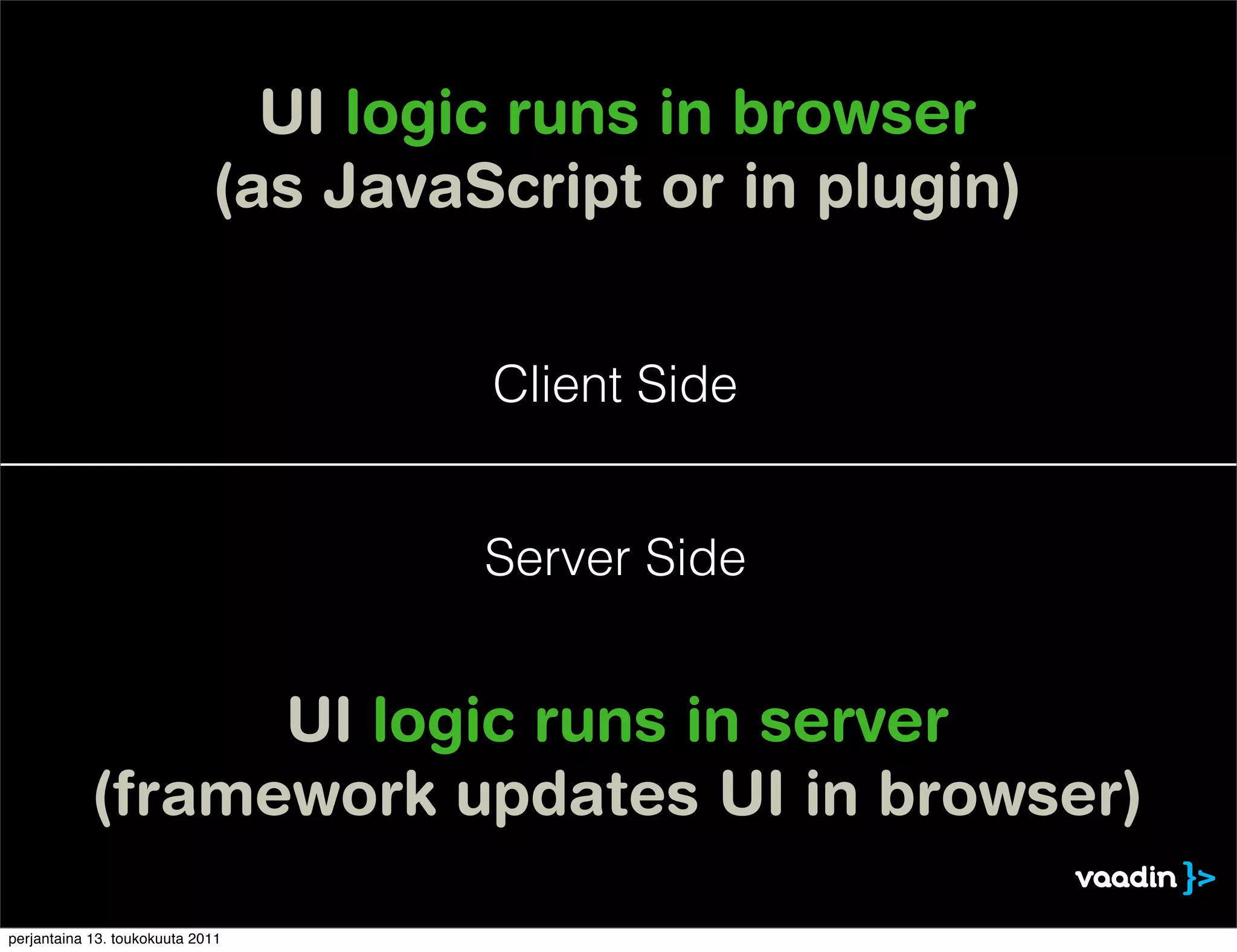
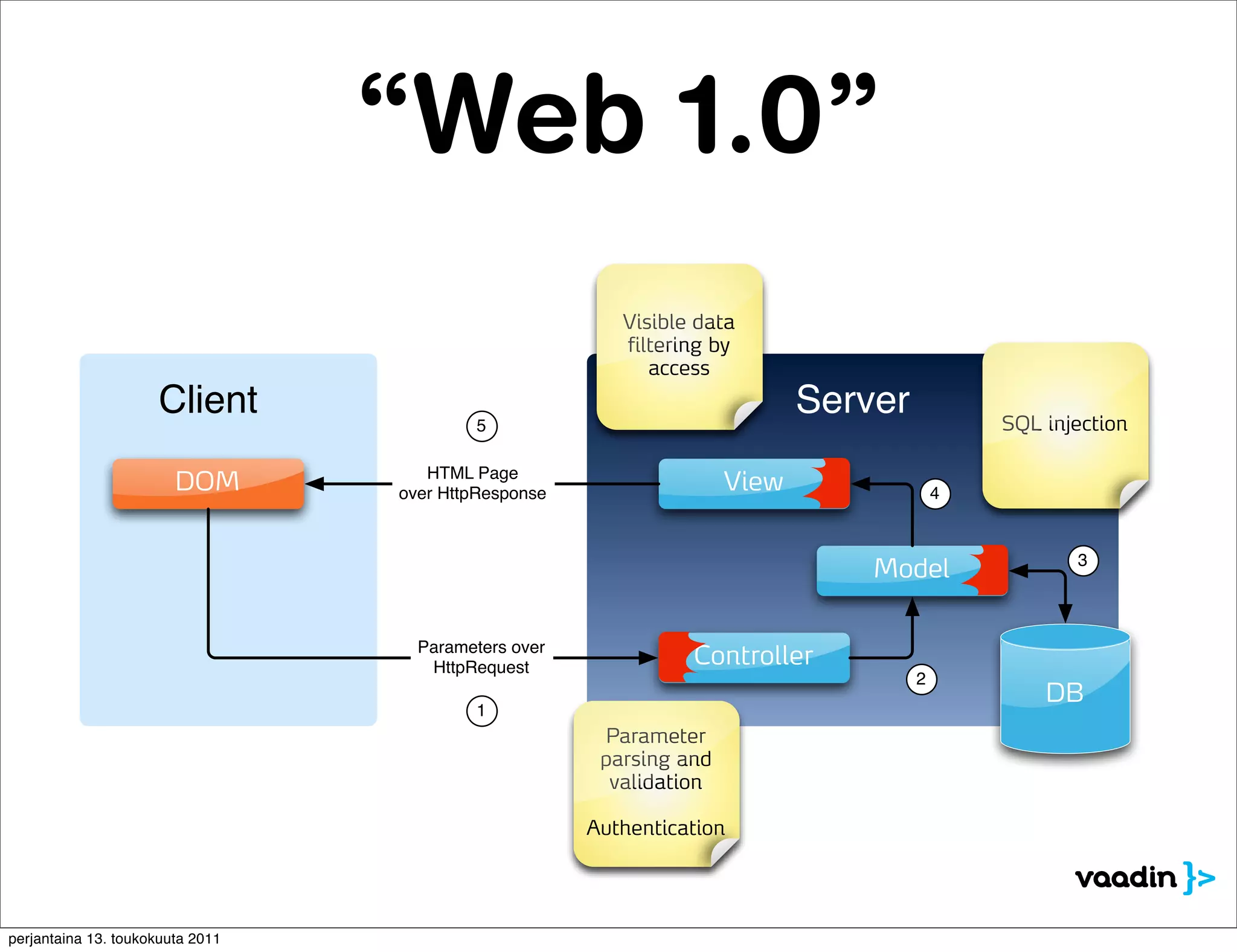
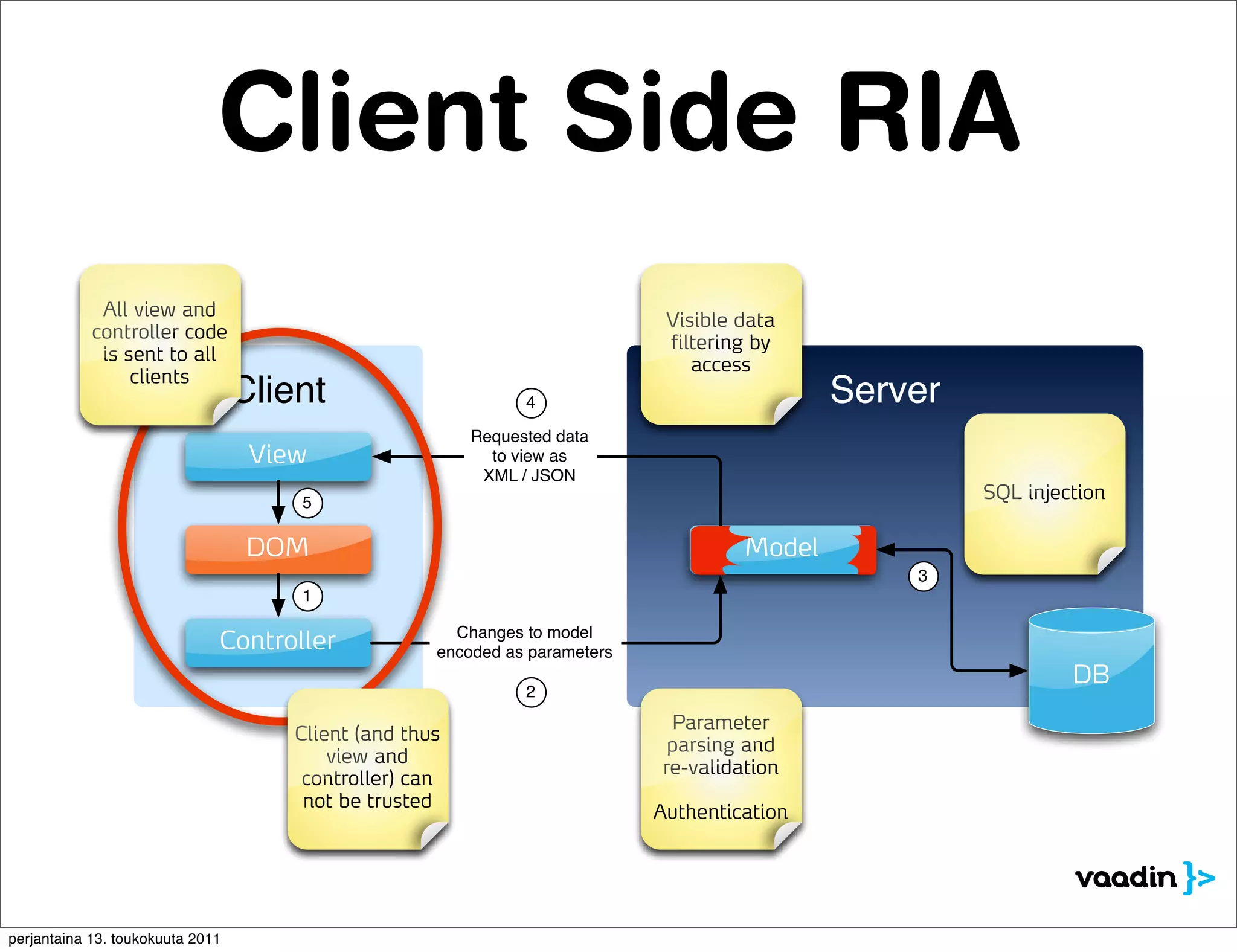
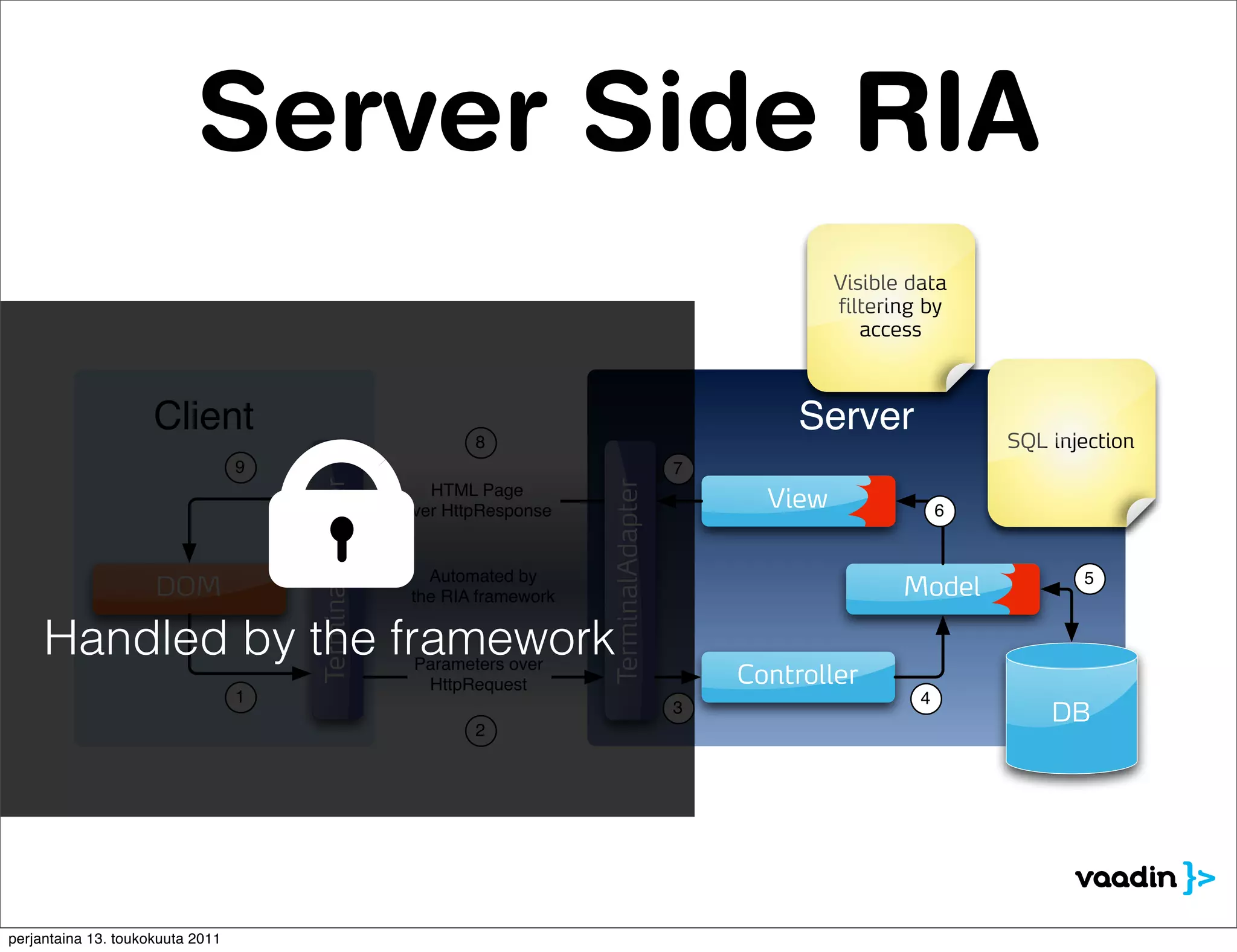
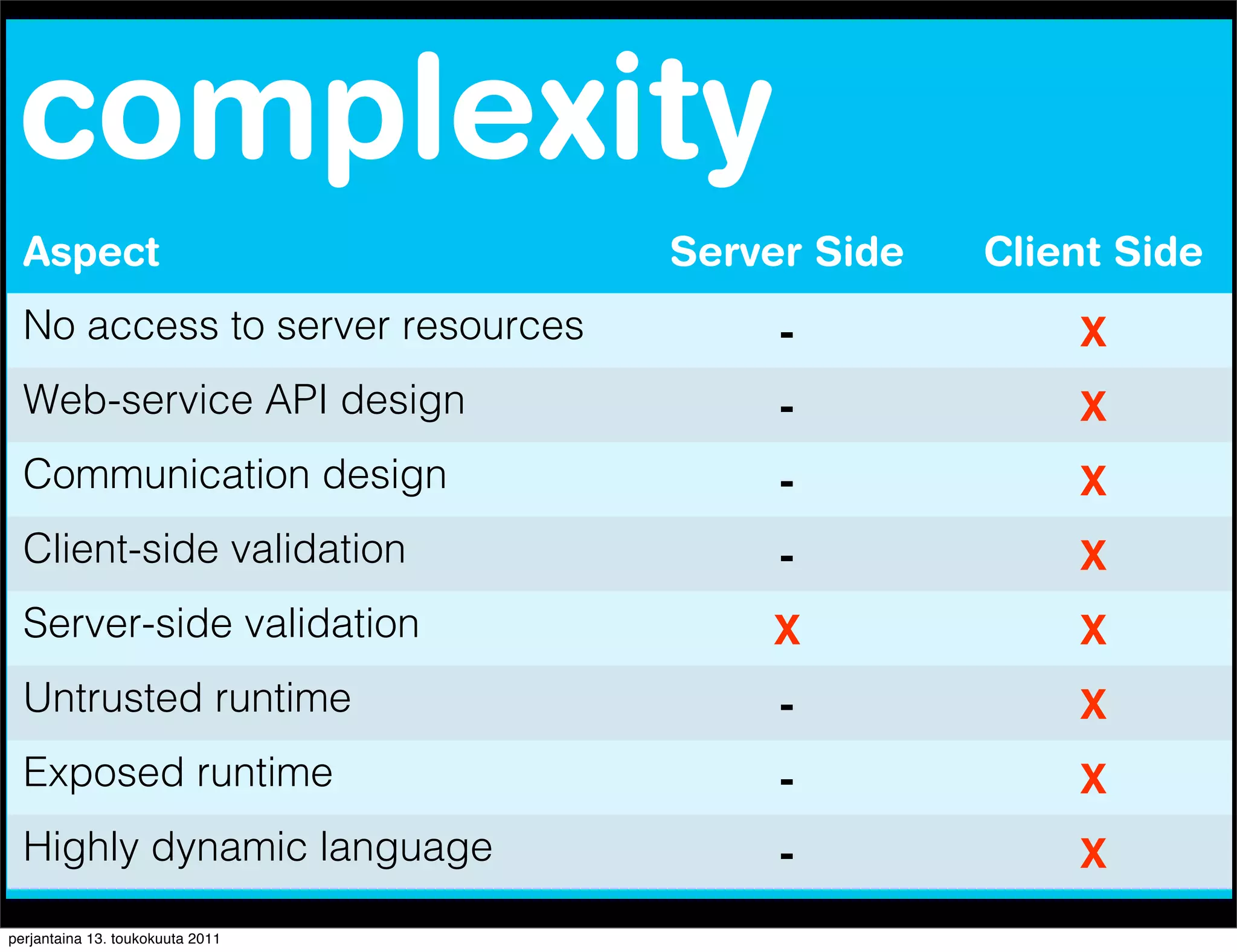
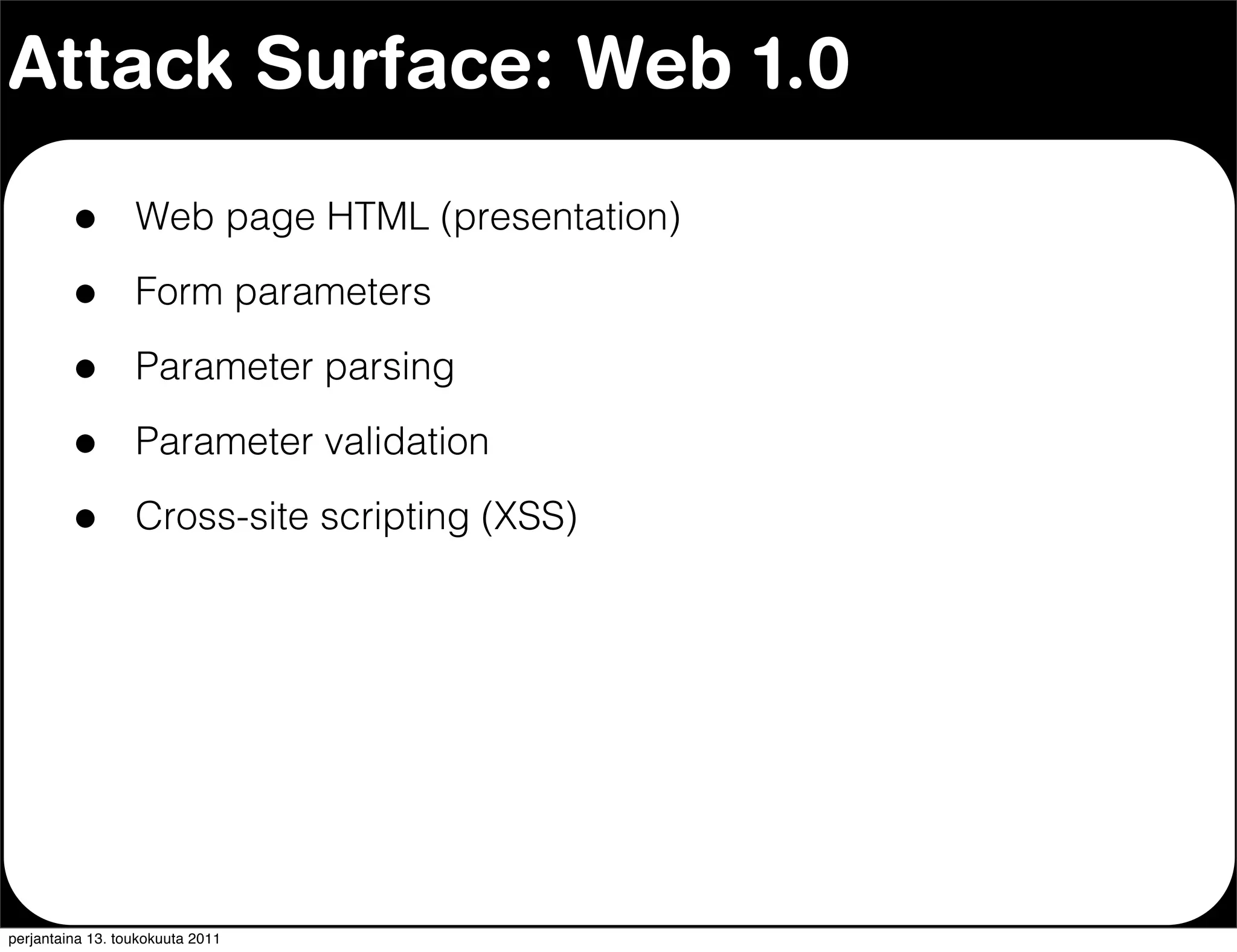
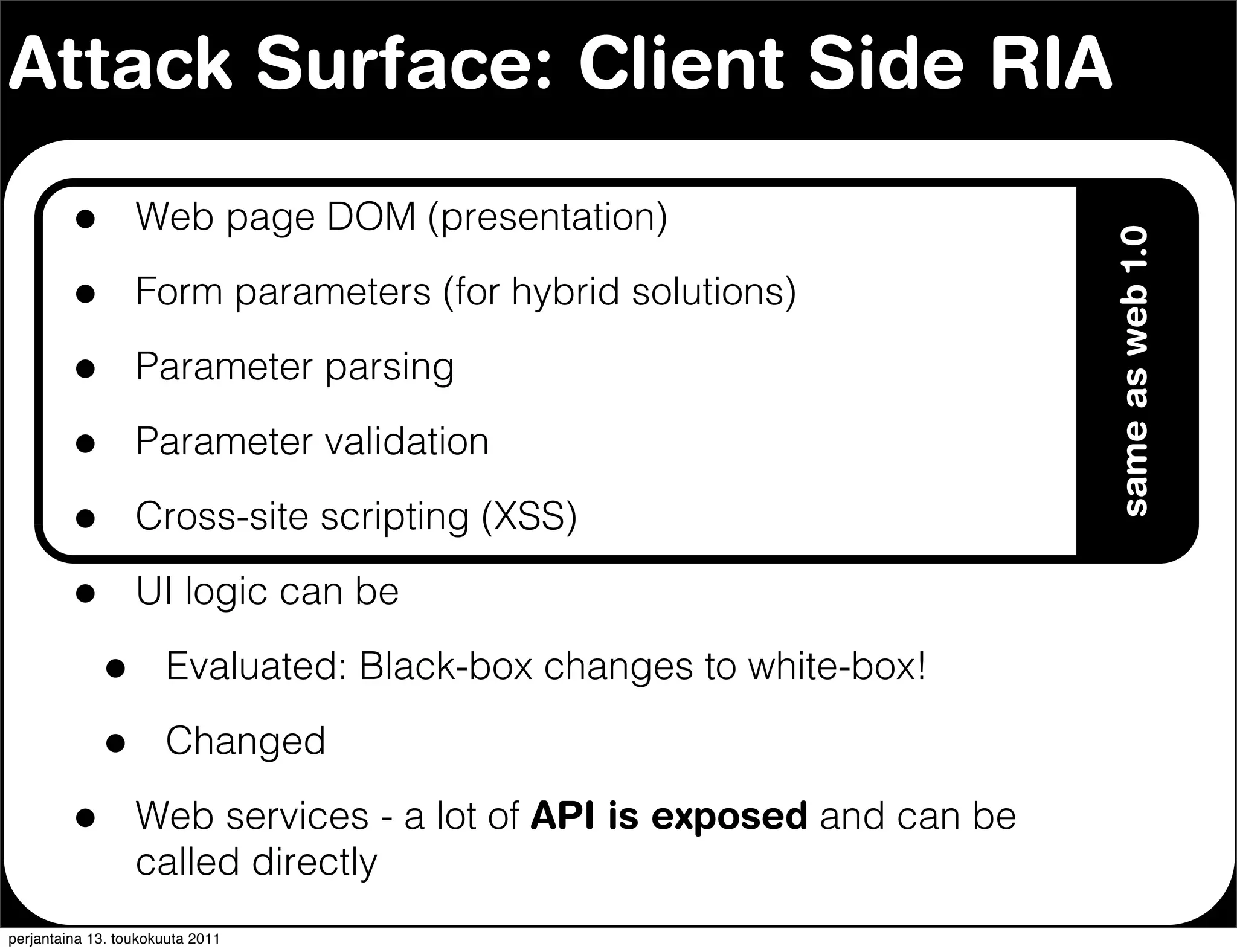
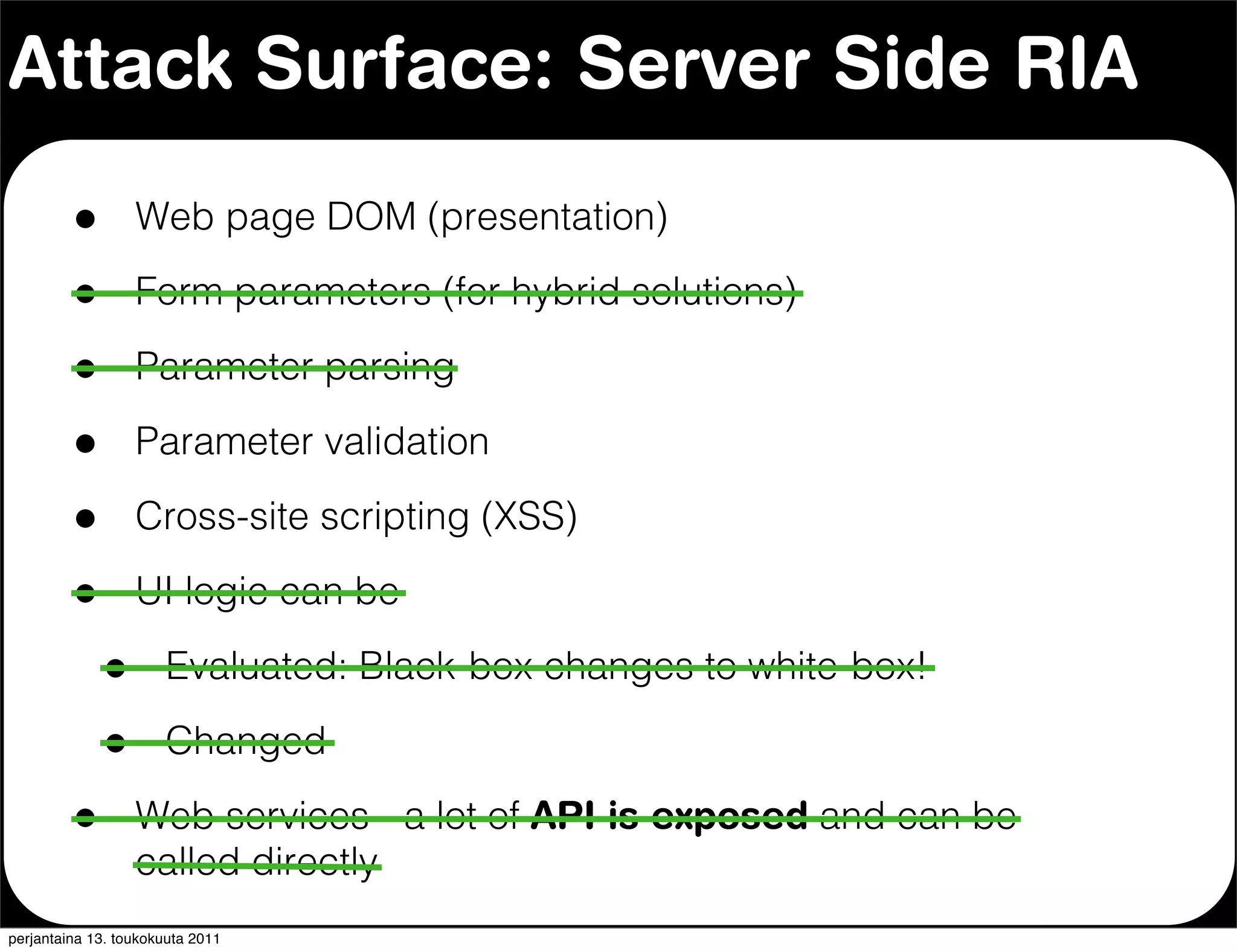
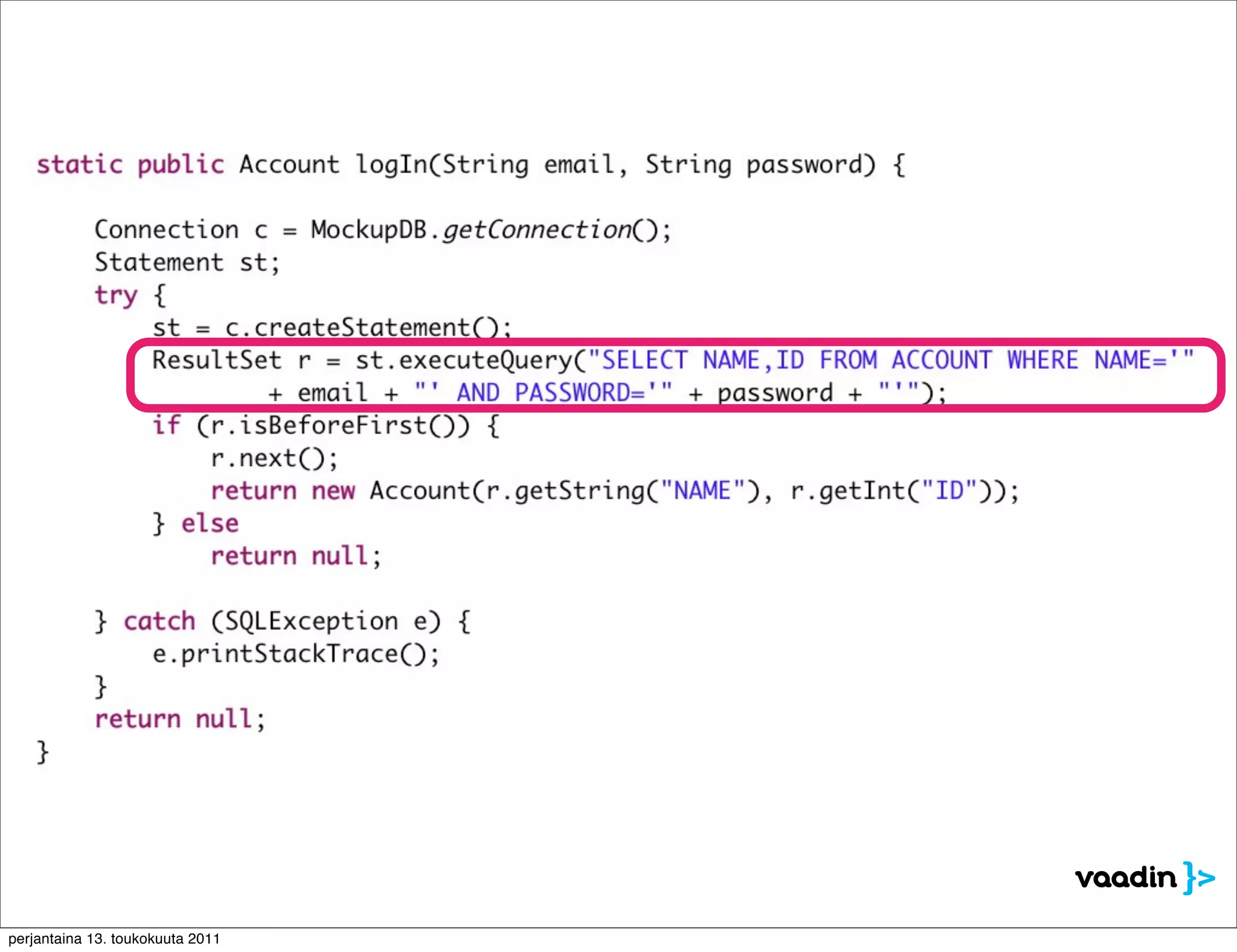
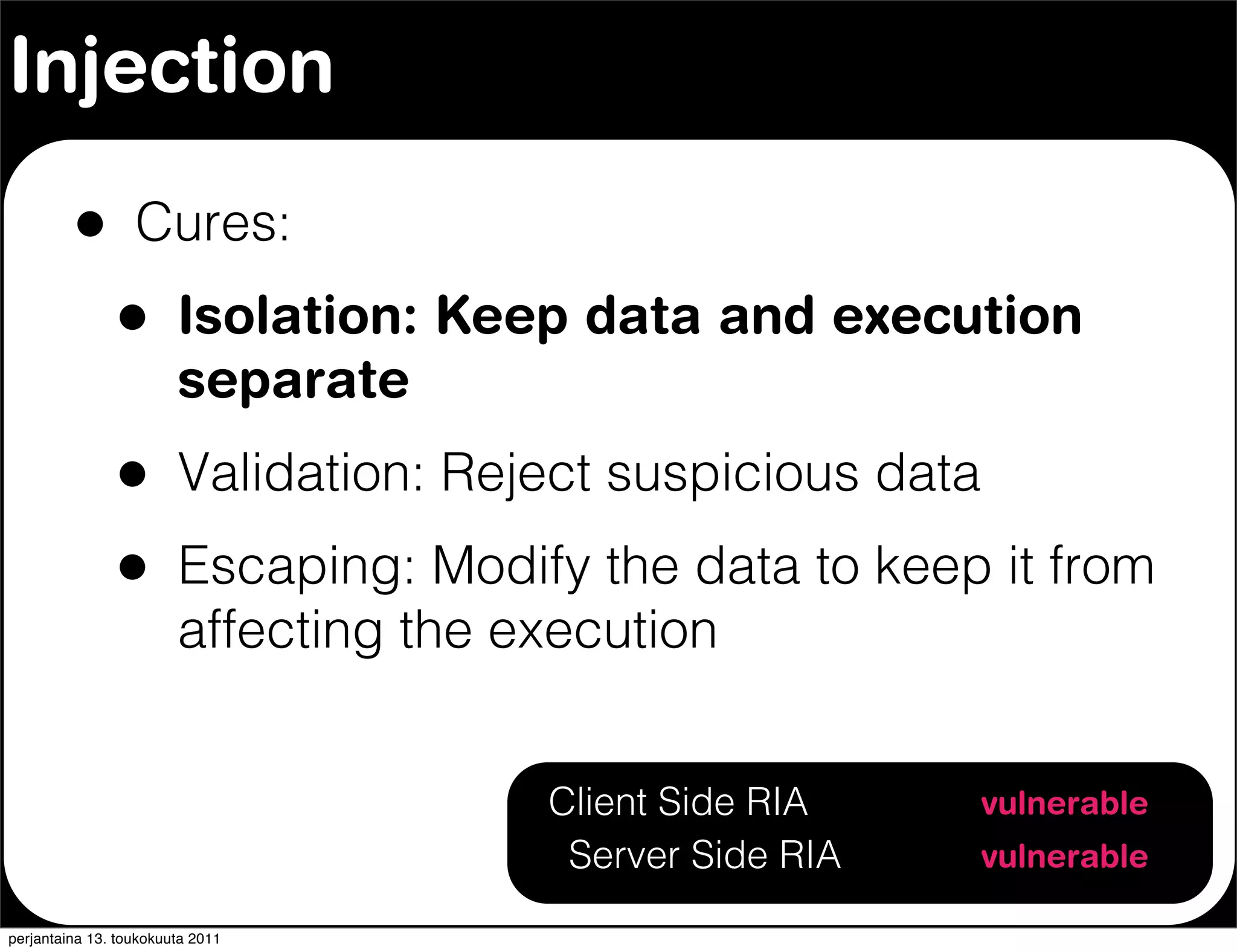
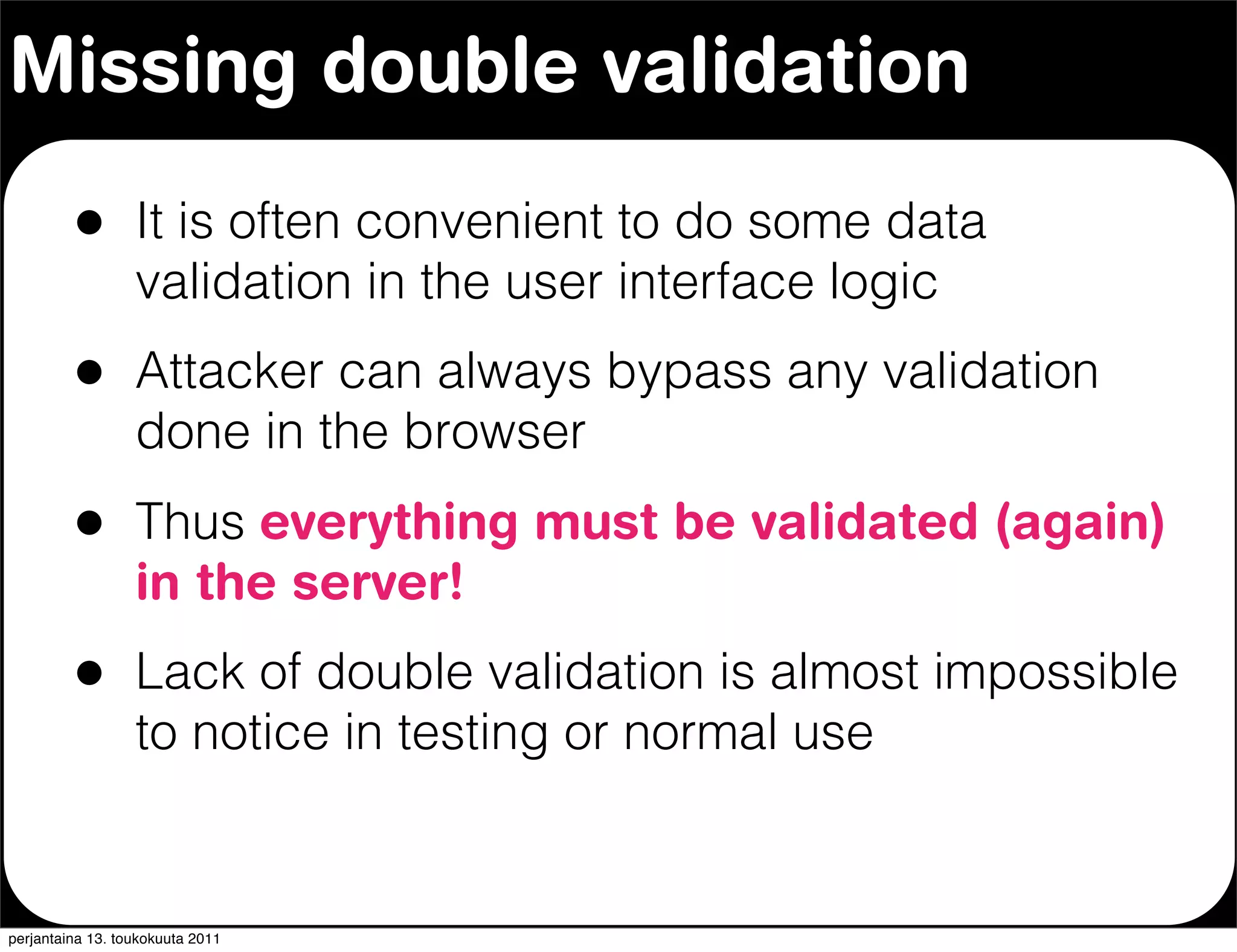
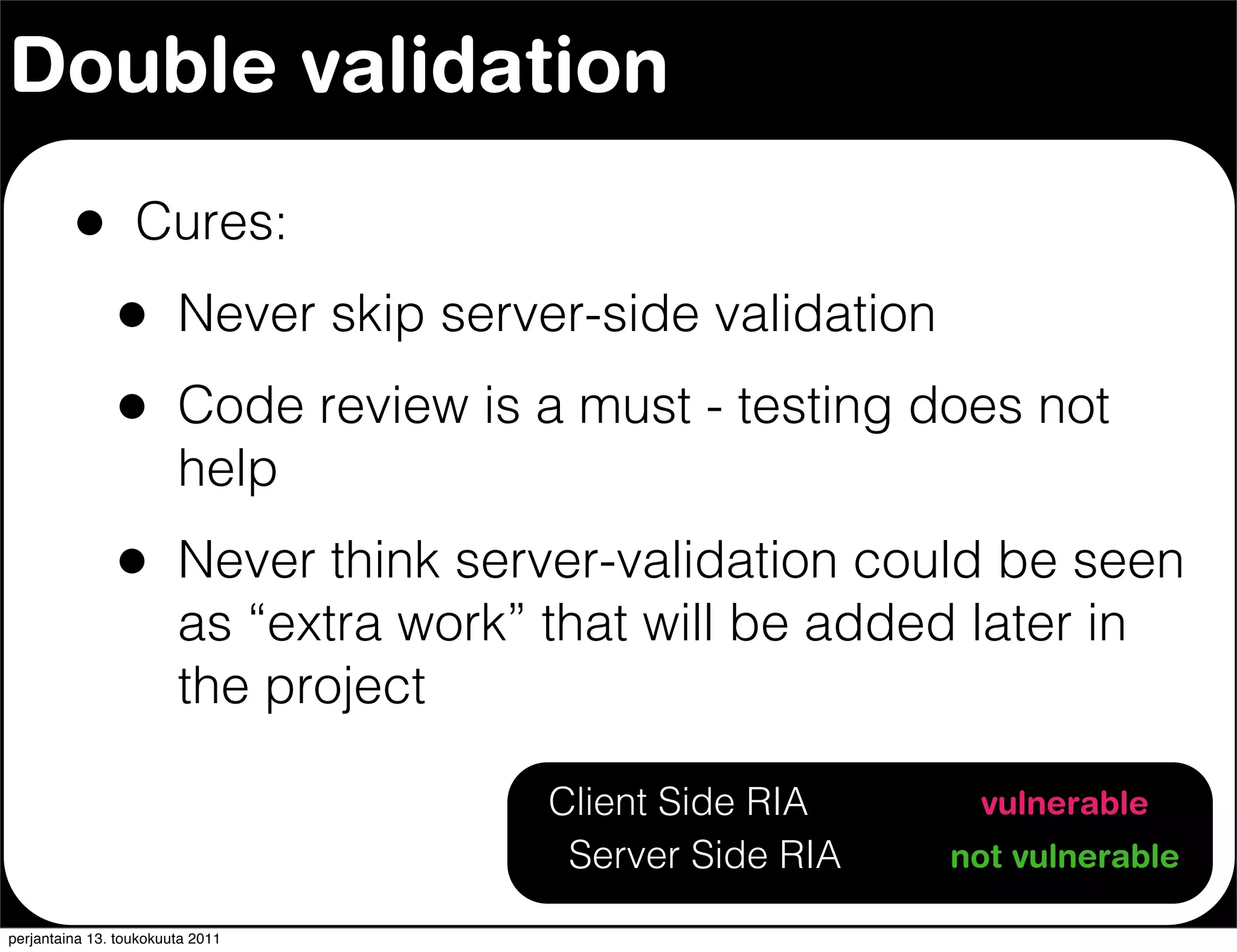
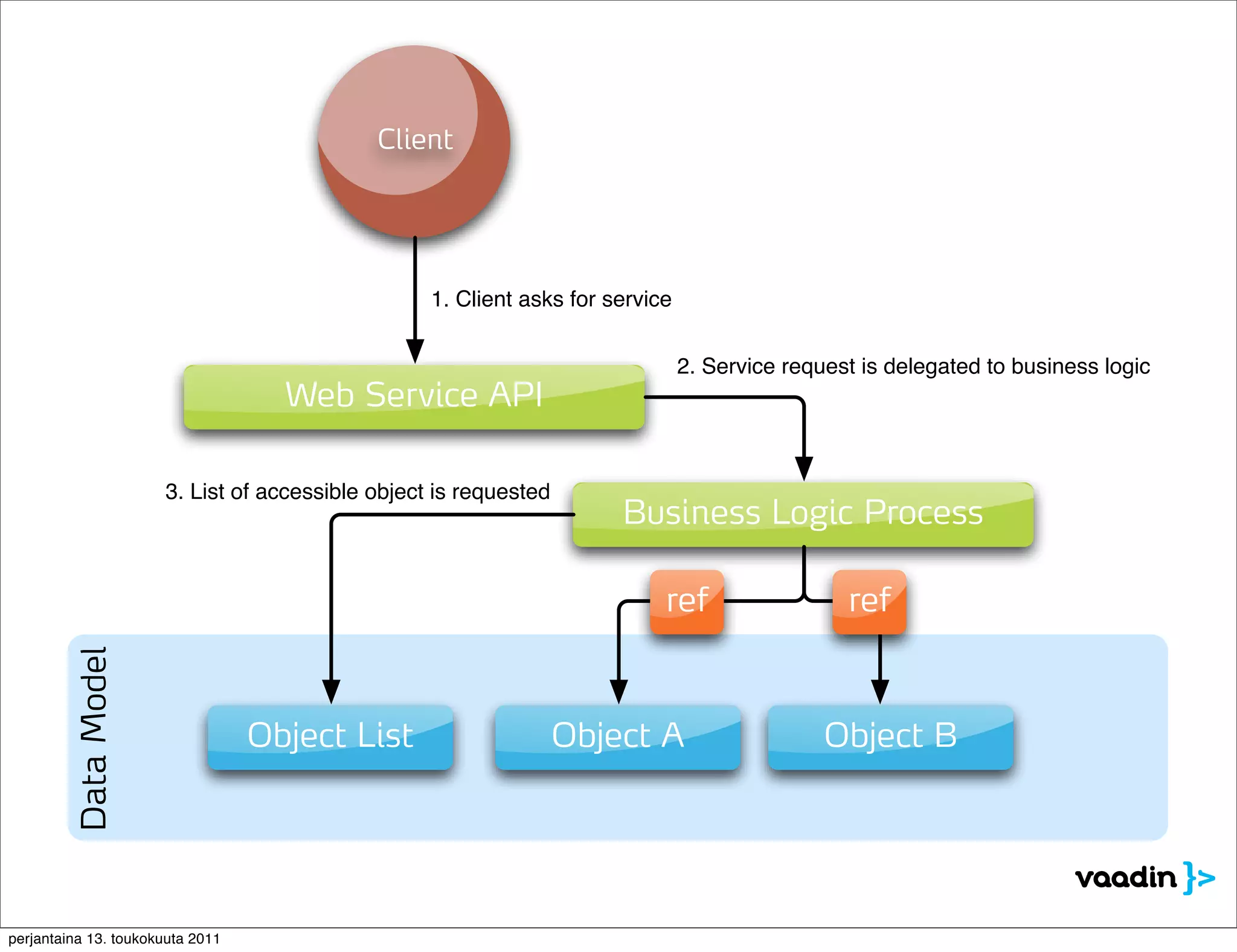
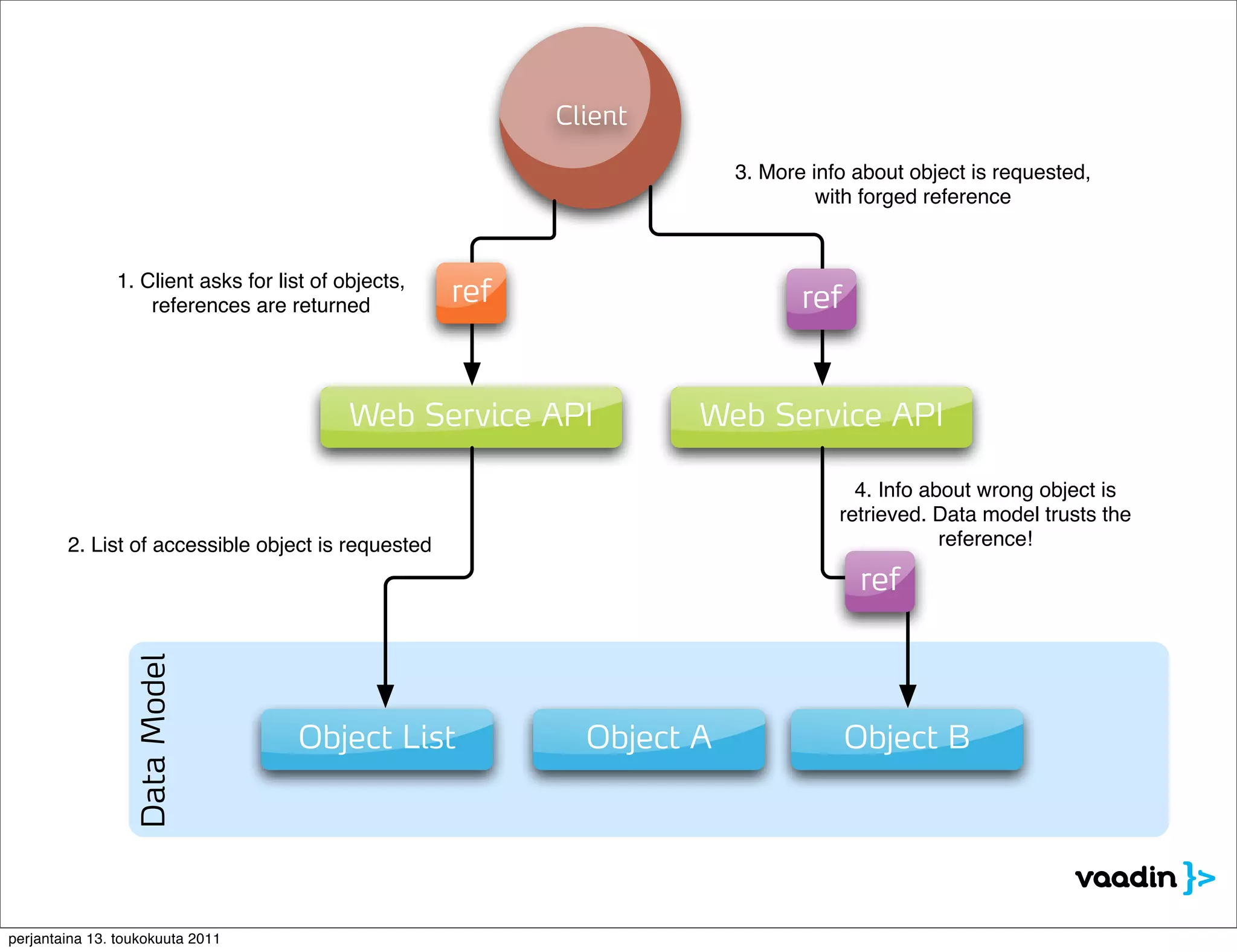
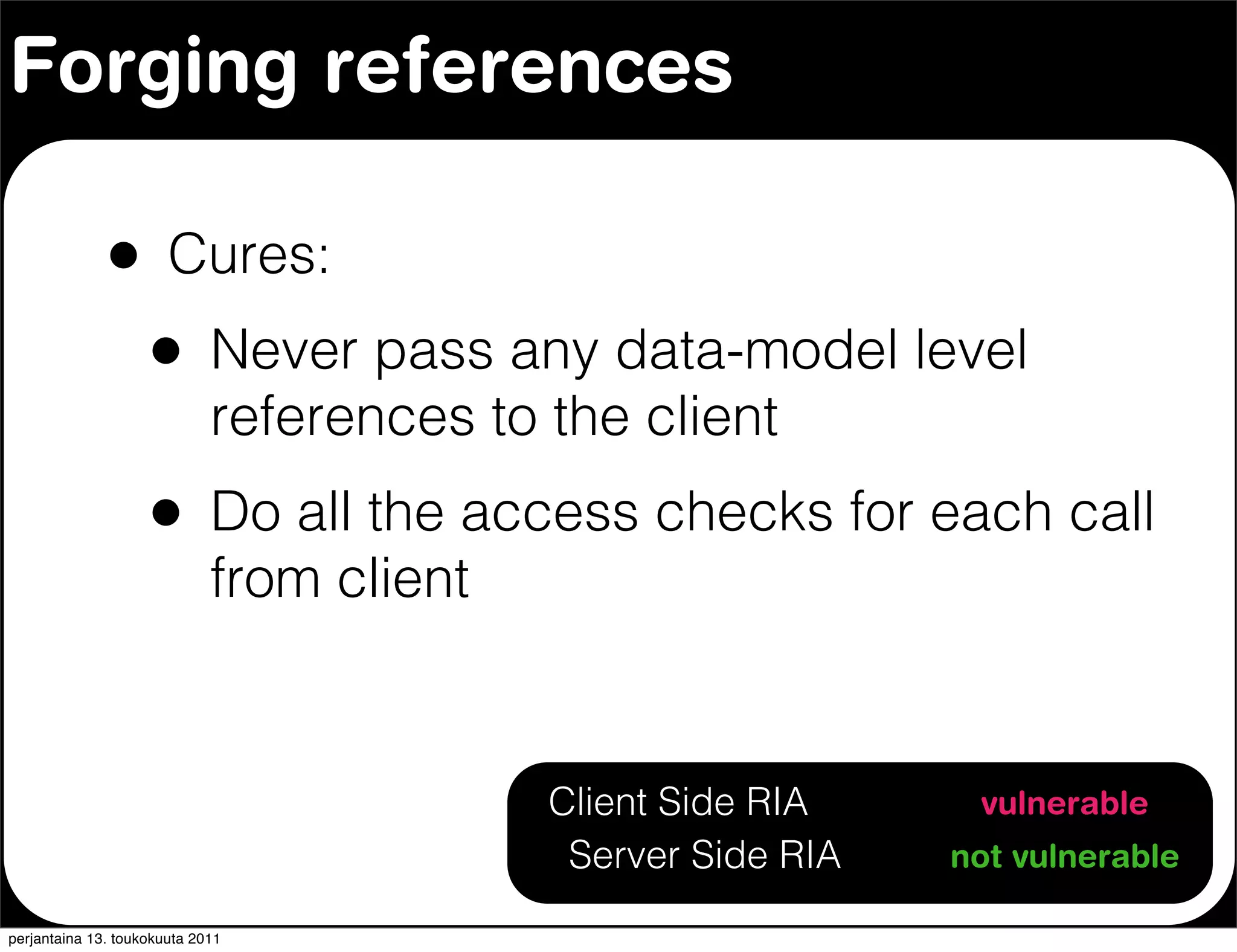
The document discusses security issues with rich internet applications (RIAs). It outlines four main rules: 1) never trust the browser, as client-side code can be manipulated; 2) more complex architectures introduce more opportunities for vulnerabilities; 3) client-side RIAs have a larger attack surface than server-side RIAs; and 4) all software will contain bugs, so architectures should be designed to minimize security risks from bugs. It provides examples of SQL injection, validation bypassing, and request forging to illustrate how client-side RIAs can be vulnerable if these principles are not followed.













![Local demo
http://localhost:8080/paymate/
Online demo
http://vaadin.com/web/joonas/wiki/-/wiki/Main/RIA%20Security
[ no relation to paymate.com.au or paypal.com ]
perjantaina 13. toukokuuta 2011](https://image.slidesharecdn.com/ria-security-handouts-110524052103-phpapp01/75/RIA-Security-Broken-By-Design-29-2048.jpg)
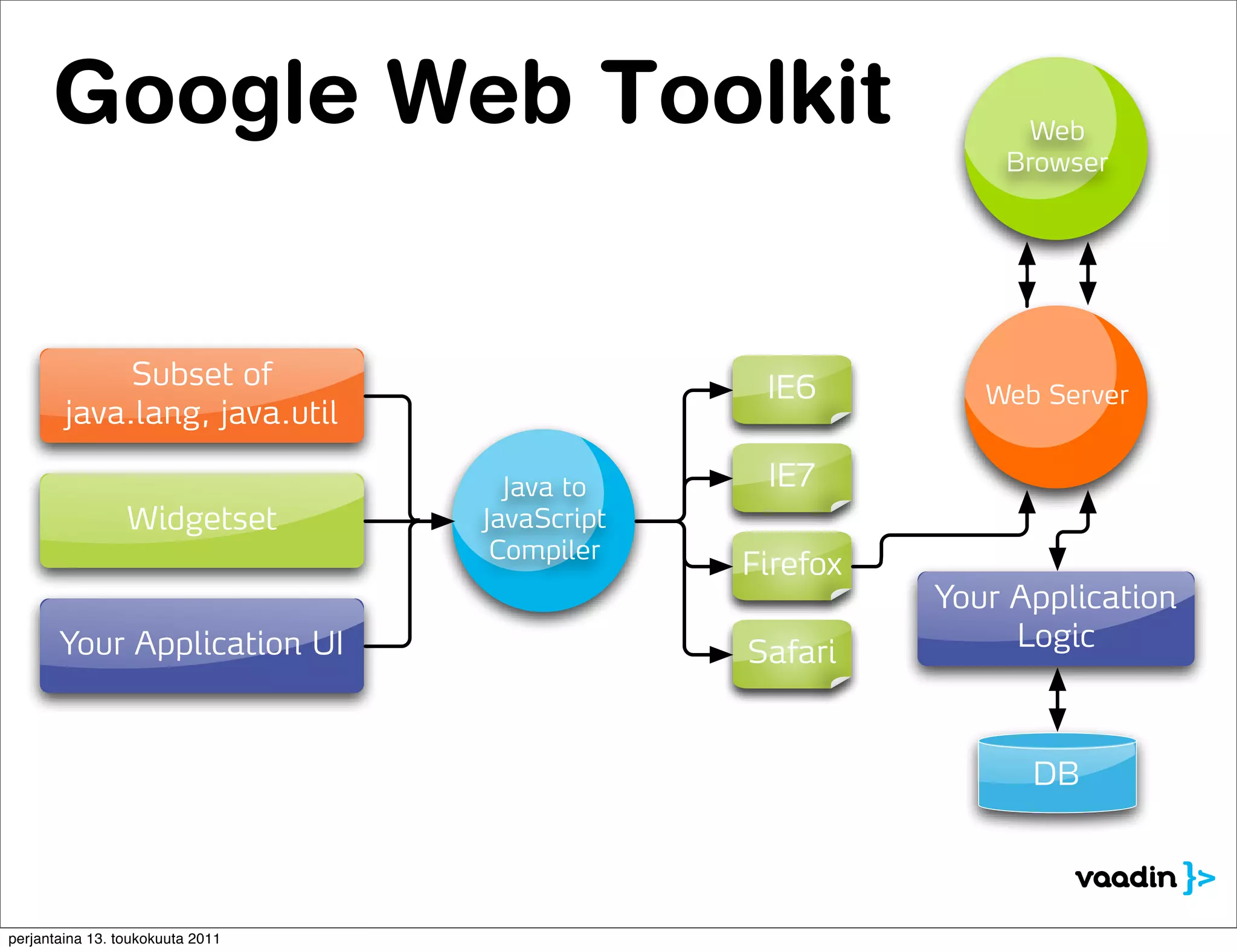
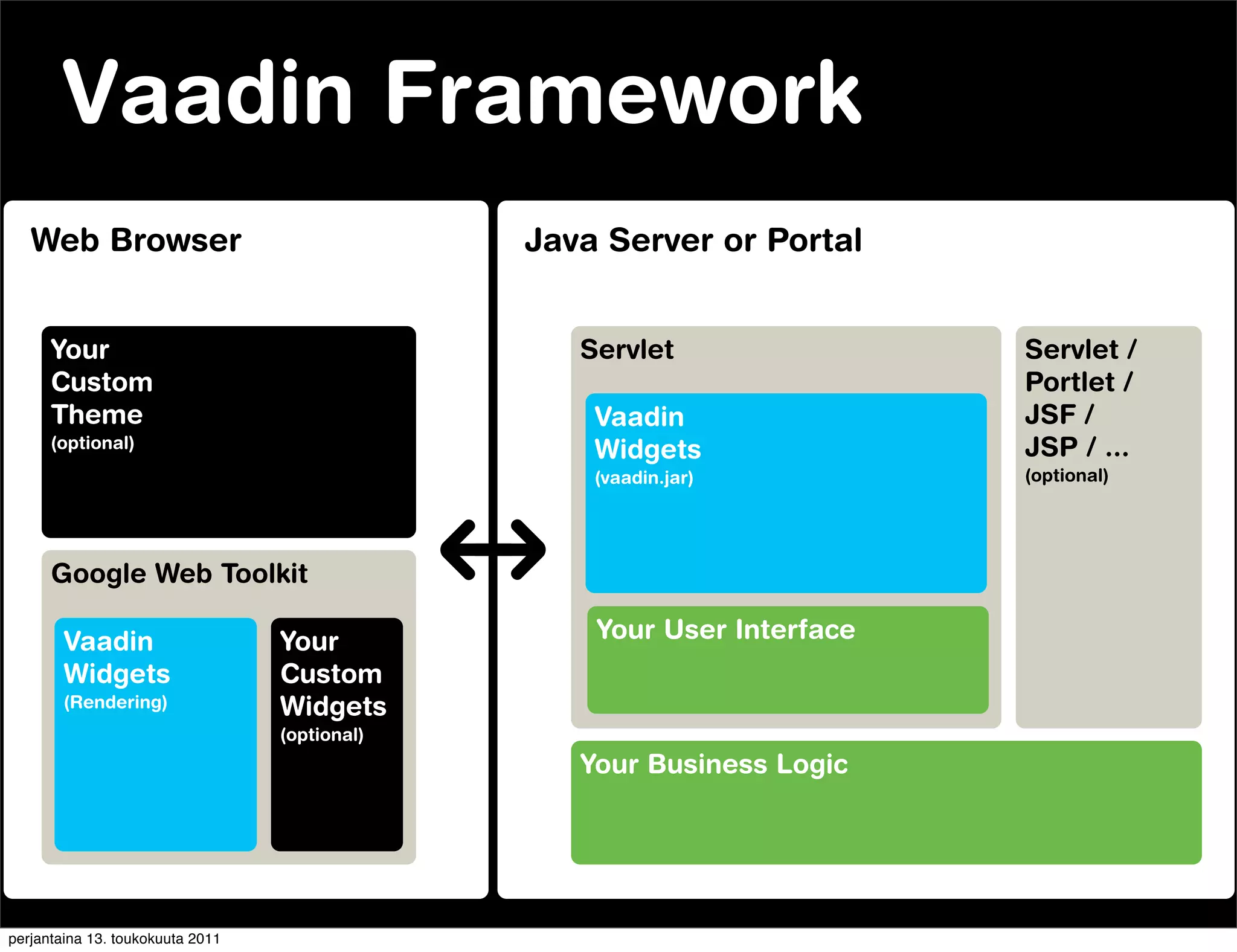
![GWT version
Client-side RIA version Vaadin version
Server-side RIA version
Running on Client Client Side Web Toolkit ]
[ Google RIA Server[Side RIA
IT Mill Toolkit ]
User Inteface
[ Custom code ]
Web Service API Async
Web Service API
Running on Server
Web Service API Impl User Inteface
[ Custom code ]
Business Logic
DB
perjantaina 13. toukokuuta 2011](https://image.slidesharecdn.com/ria-security-handouts-110524052103-phpapp01/75/RIA-Security-Broken-By-Design-30-2048.jpg)







![var xhr = document.body.childNodes[5].contentWindow.XMLHttpRequest;
Override the original XMLHttpRequest implementation
xhr.prototype.originalSend = xhr.prototype.send;
xhr.prototype.send = function(a) {
! Create UI for our hack tool
var panel = document.createElement("DIV");
! panel.innerHTML = "<textarea id='postdata' cols=80 rows=20> "+
"</textarea><br/><button id='postbutton'>Post</button>";
! document.body.appendChild(panel);
! document.getElementById('postdata').value=a;
Do the sending when the button is pressed
! var t = this; document.getElementById('postbutton').
addEventListener("click",function() {
! ! t.originalSend(document.getElementById('postdata').value);
! ! document.body.removeChild(panel);
! }, true);
};
perjantaina 13. toukokuuta 2011](https://image.slidesharecdn.com/ria-security-handouts-110524052103-phpapp01/75/RIA-Security-Broken-By-Design-41-2048.jpg)

![These bugs are
just plain stupid!
[our team is smart enough to avoid them]
perjantaina 13. toukokuuta 2011](https://image.slidesharecdn.com/ria-security-handouts-110524052103-phpapp01/75/RIA-Security-Broken-By-Design-48-2048.jpg)