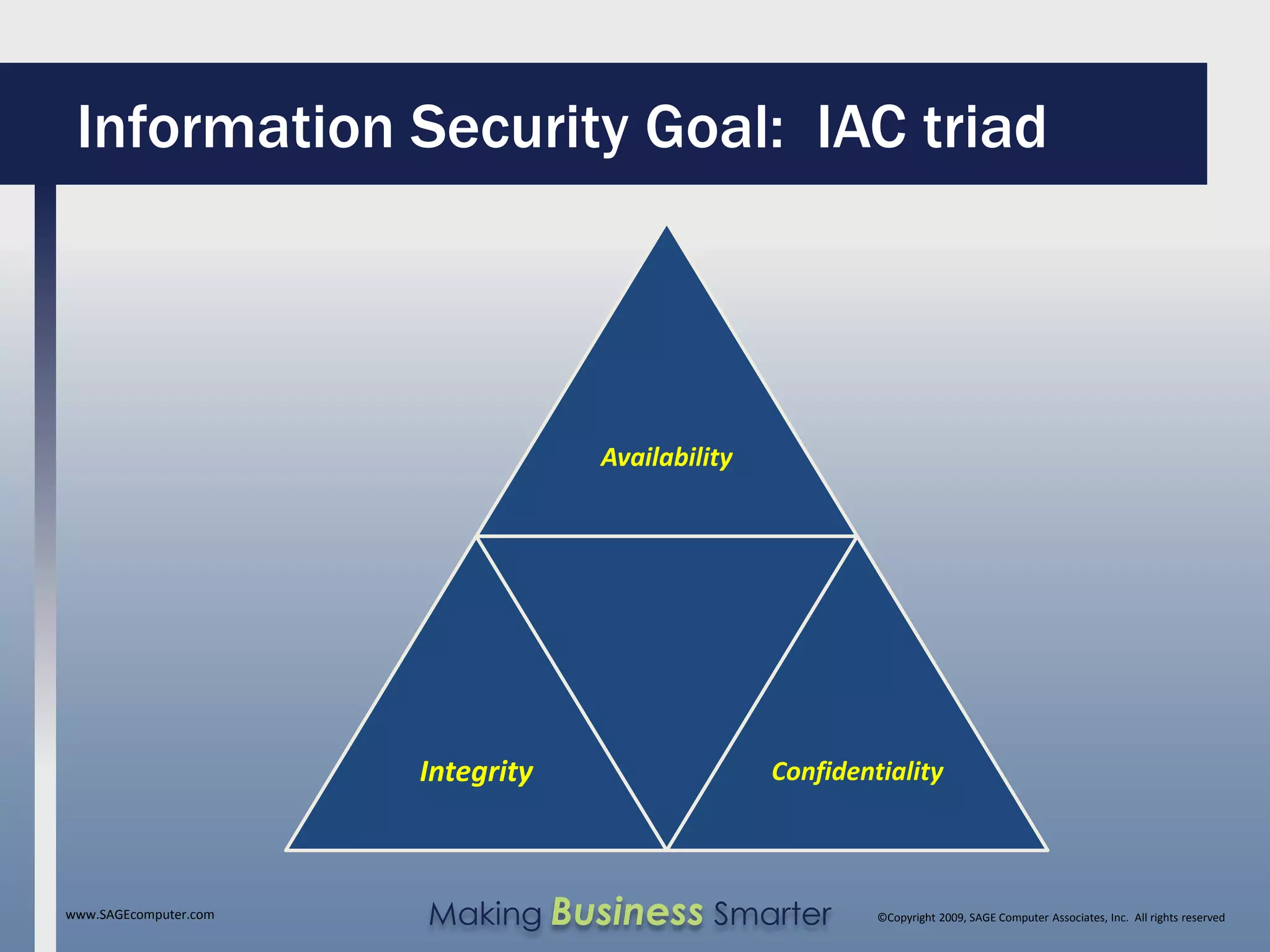
The document discusses information security as a critical mindset focusing on the protection of data rather than just technological solutions. It outlines the goals of information security, including availability, integrity, and confidentiality, while also addressing threats and best practices for organizations and users to mitigate risks. Additionally, it emphasizes the importance of formal policies and user education in maintaining a secure information environment.