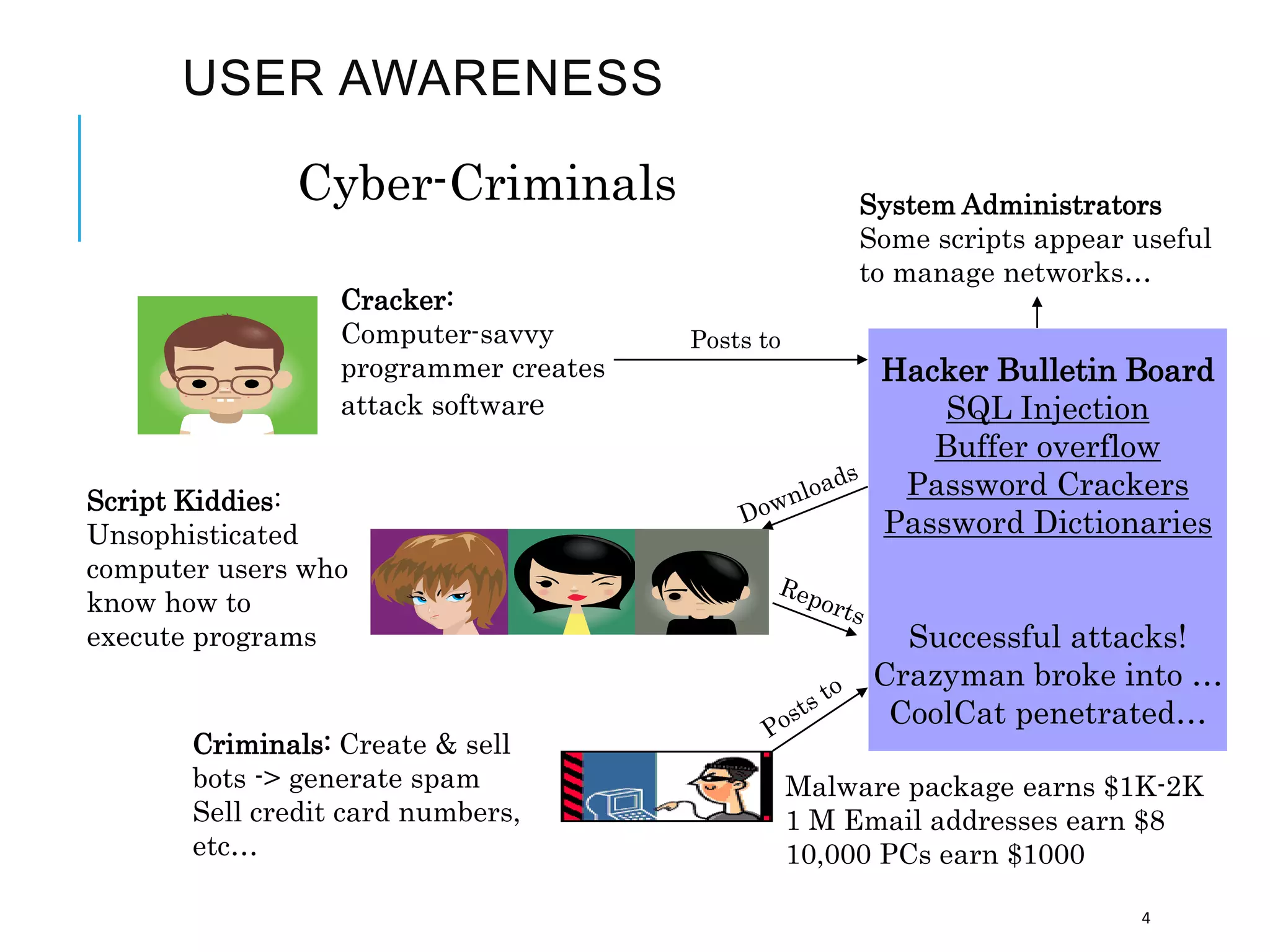
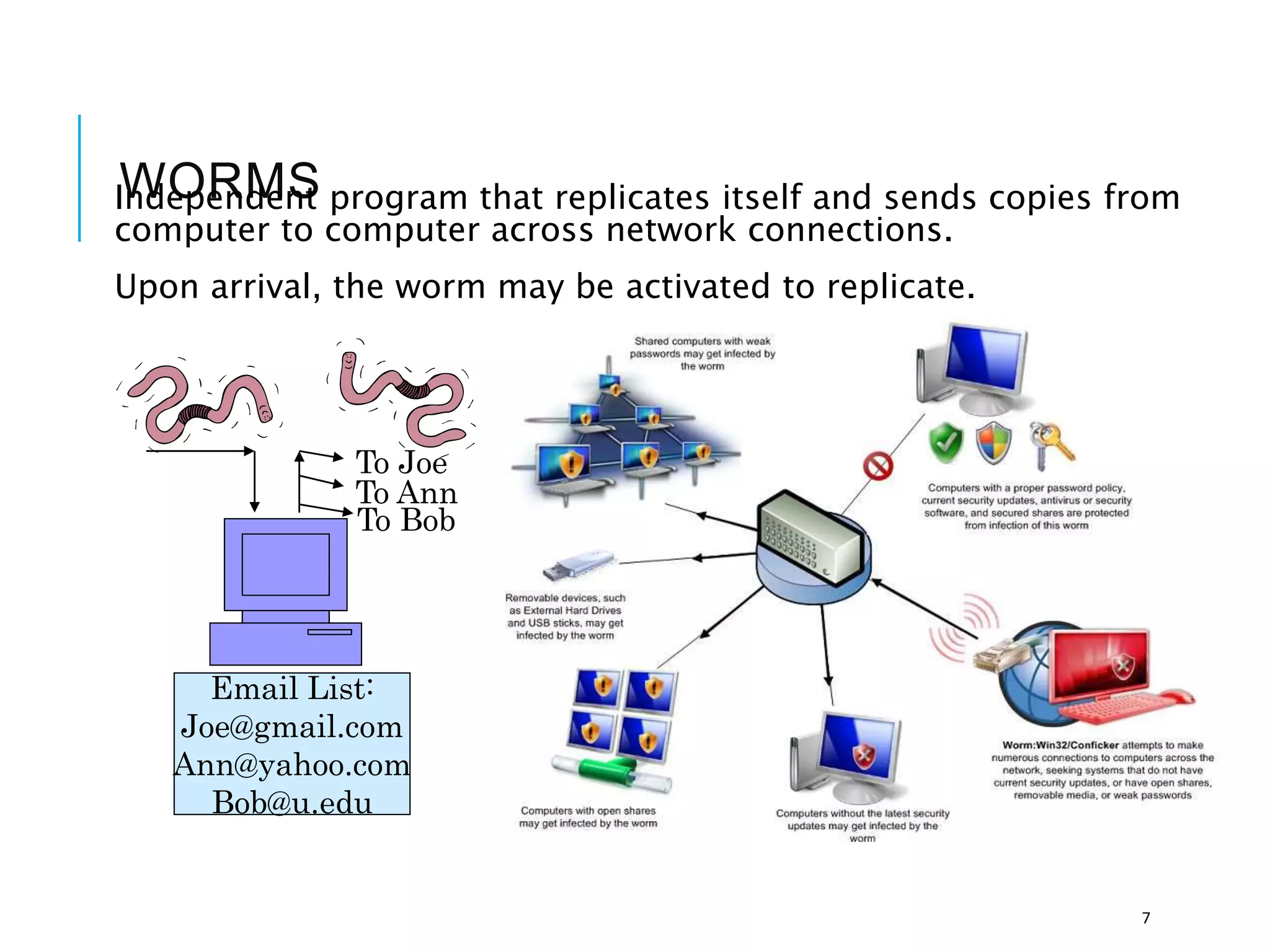
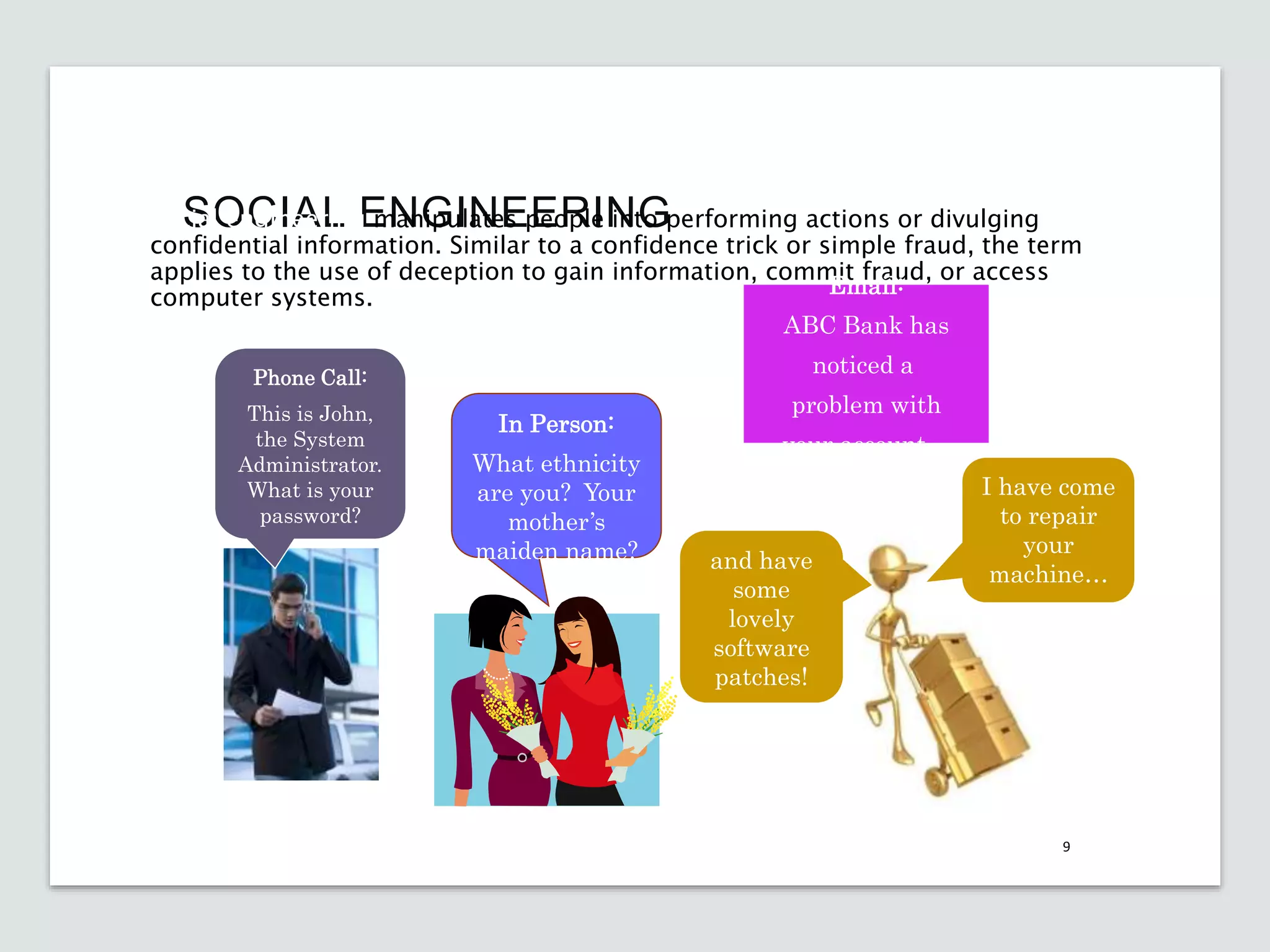
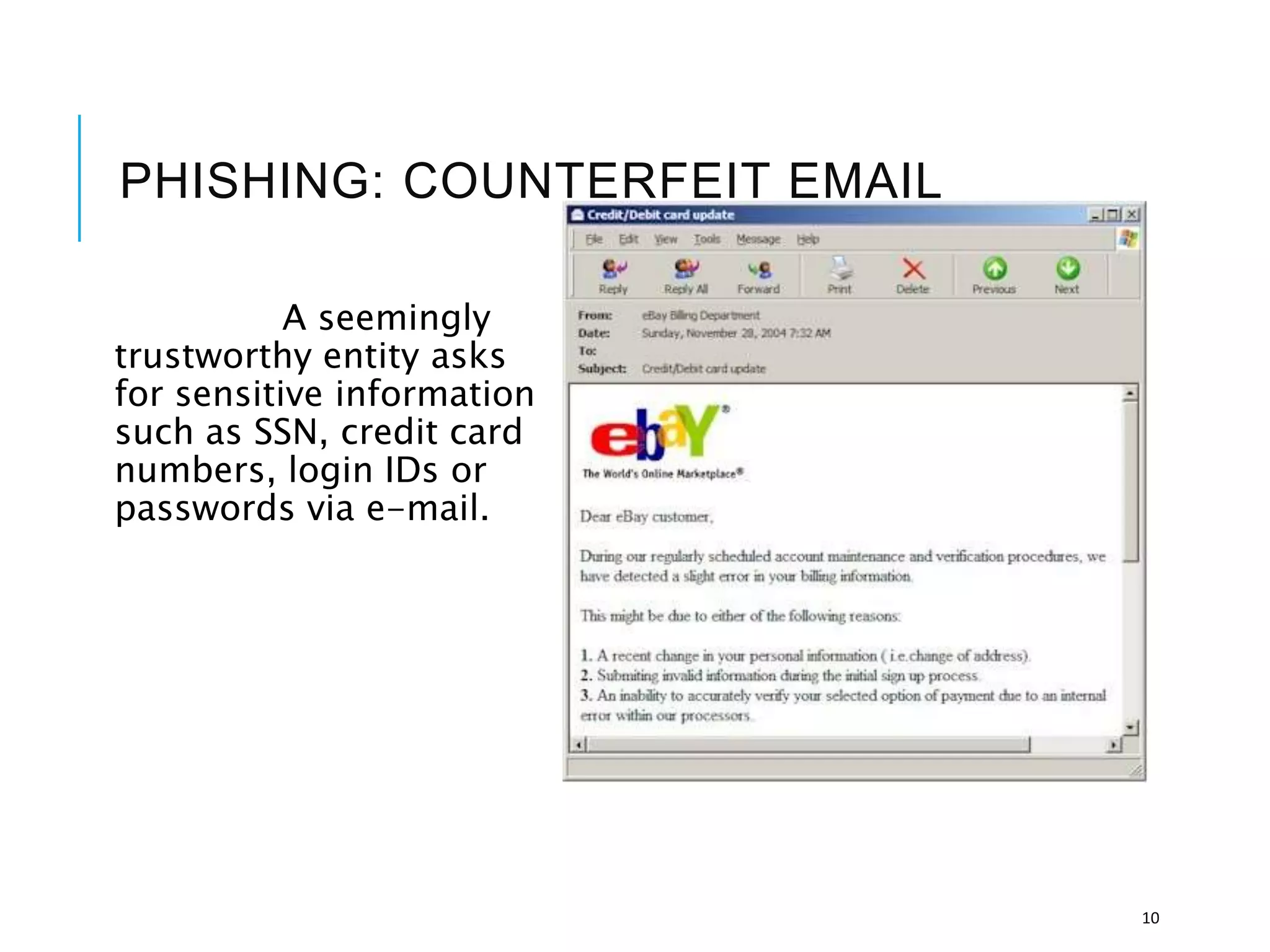
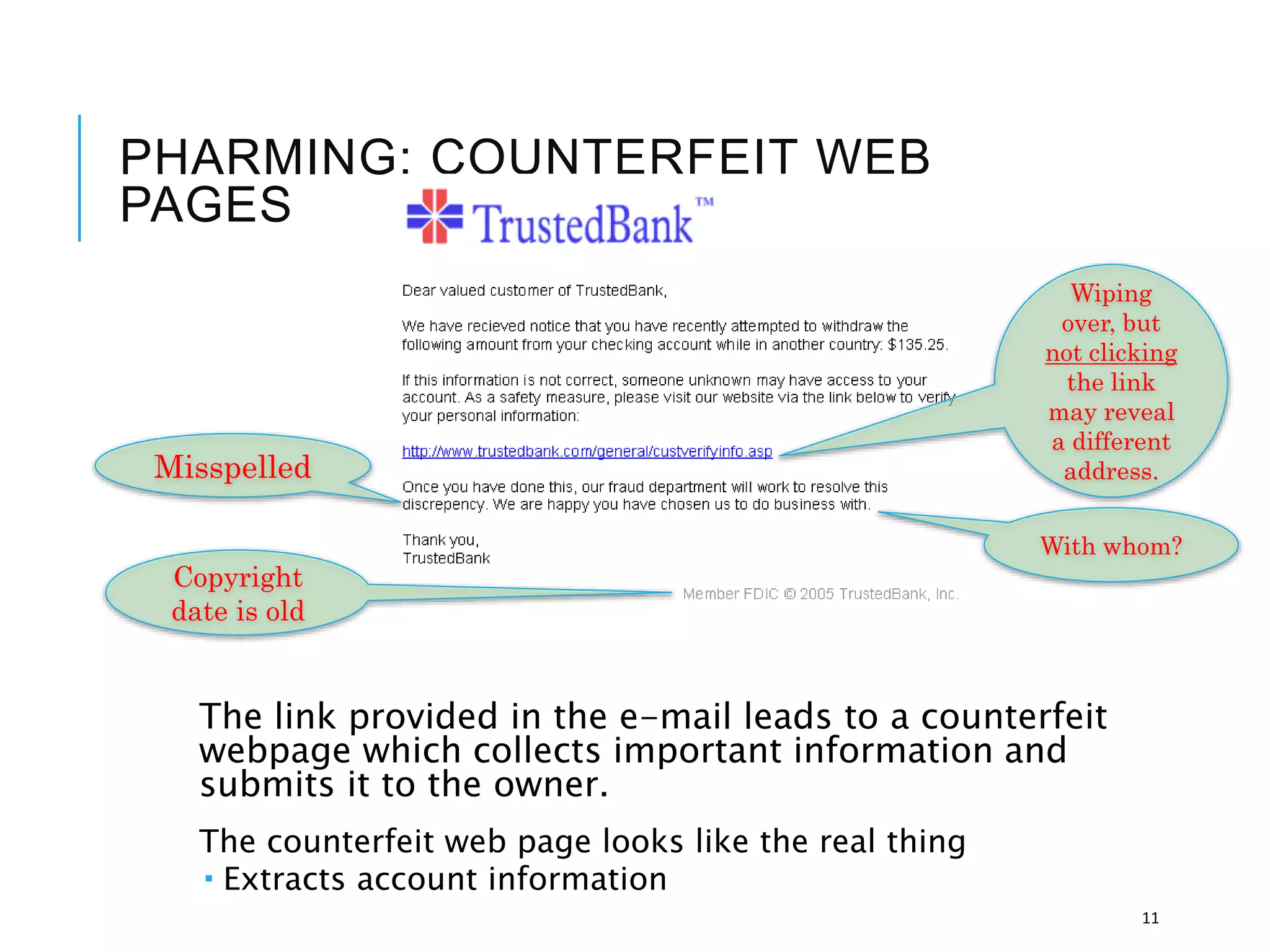
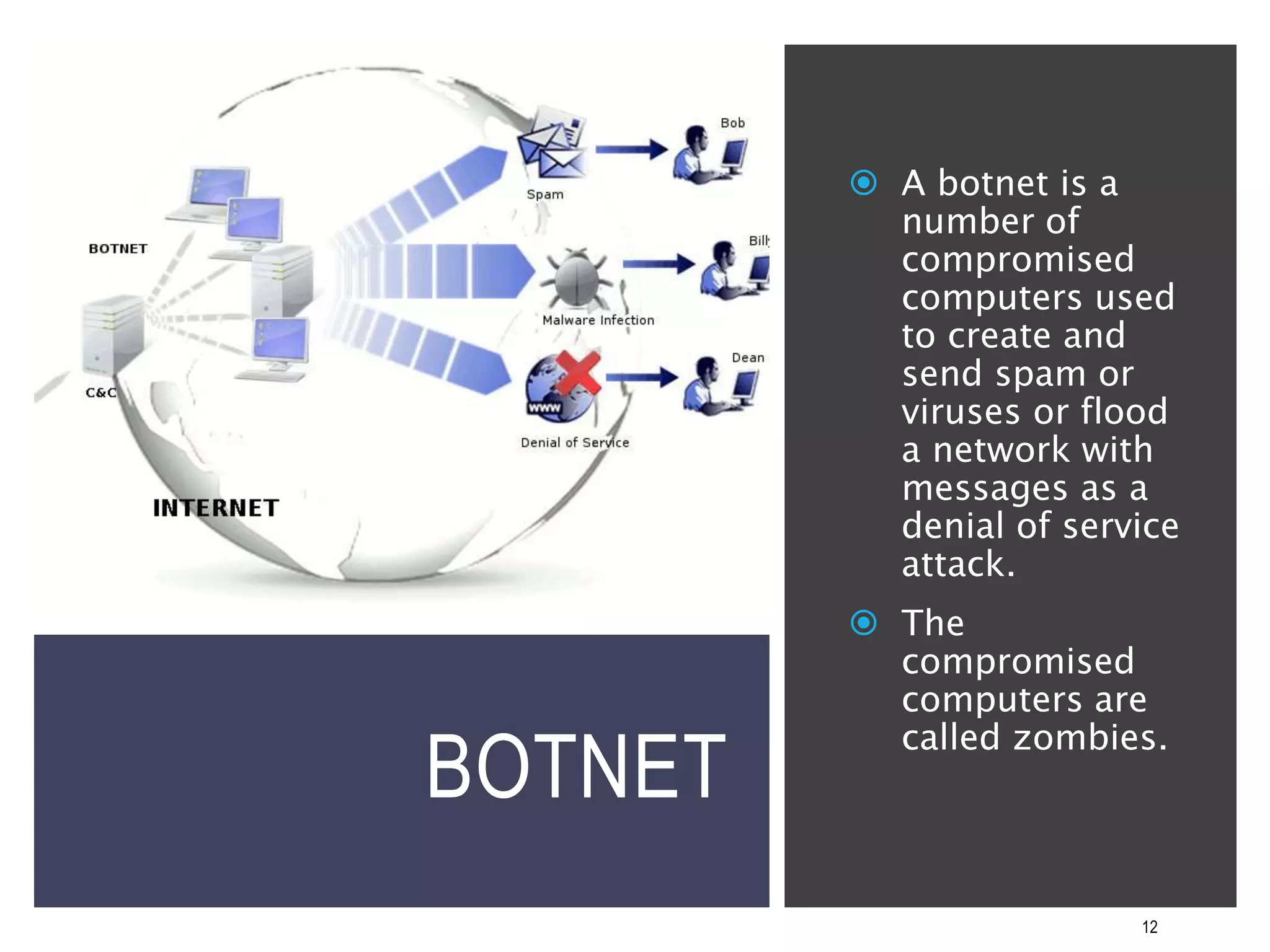
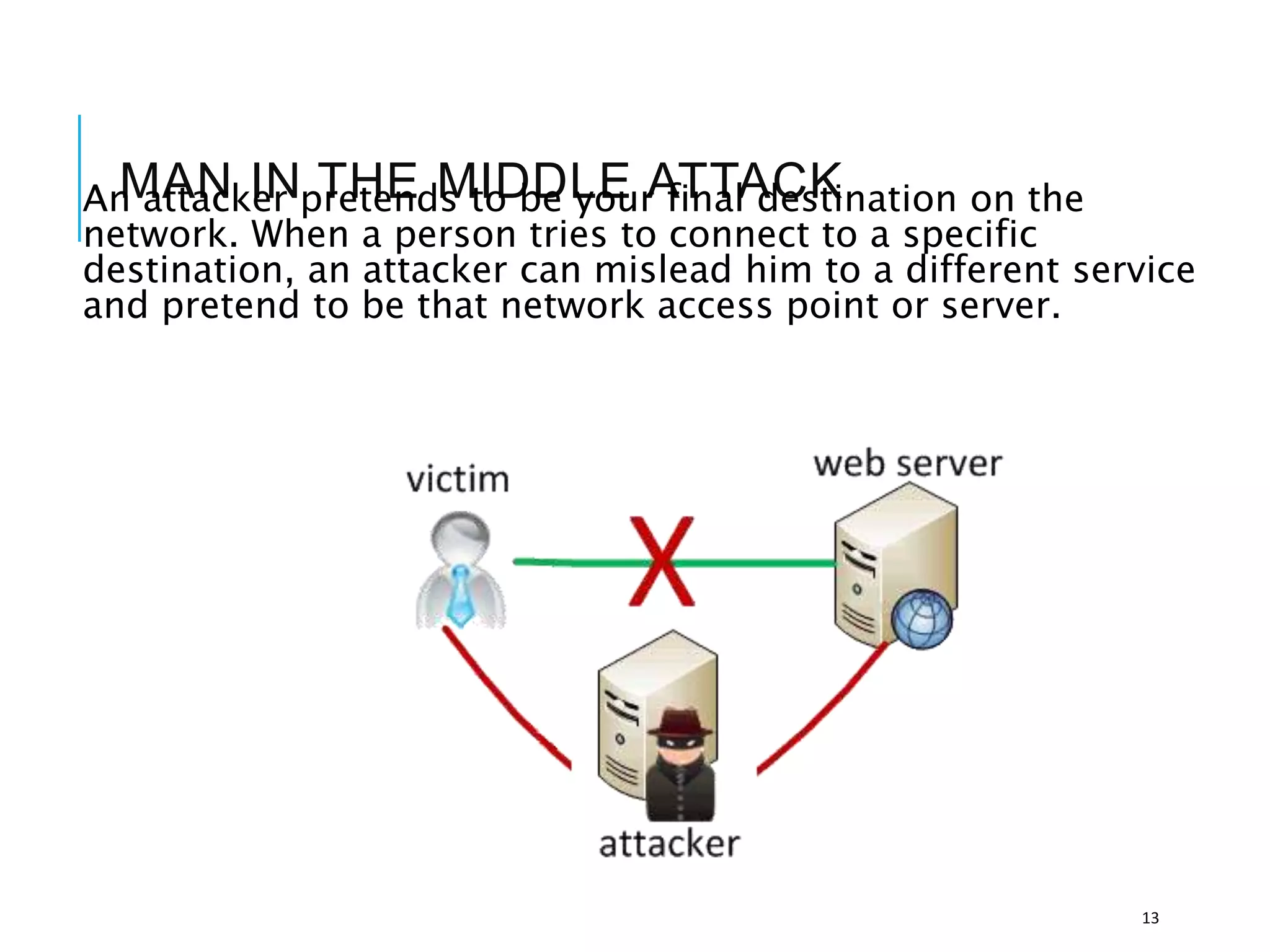
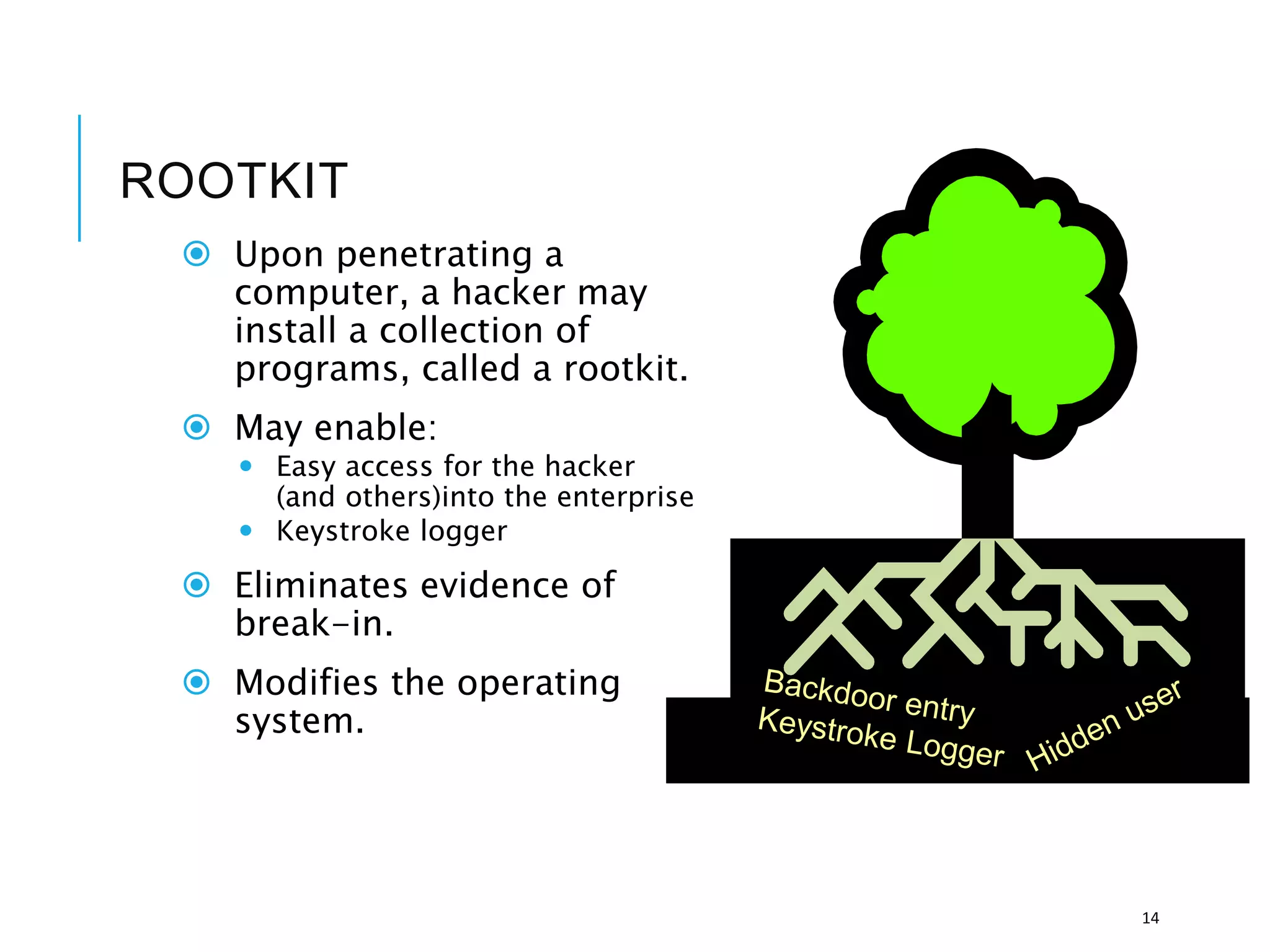
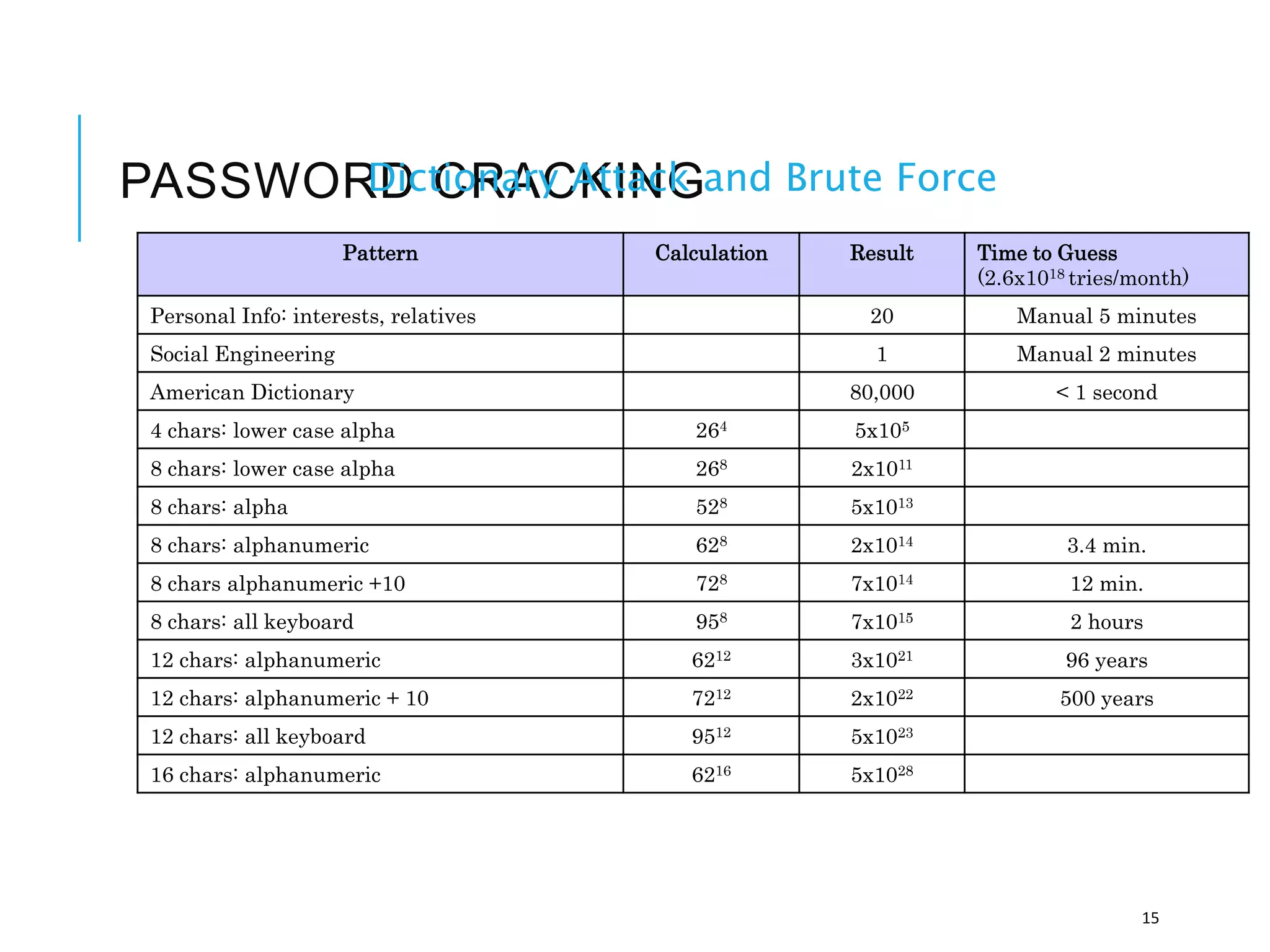
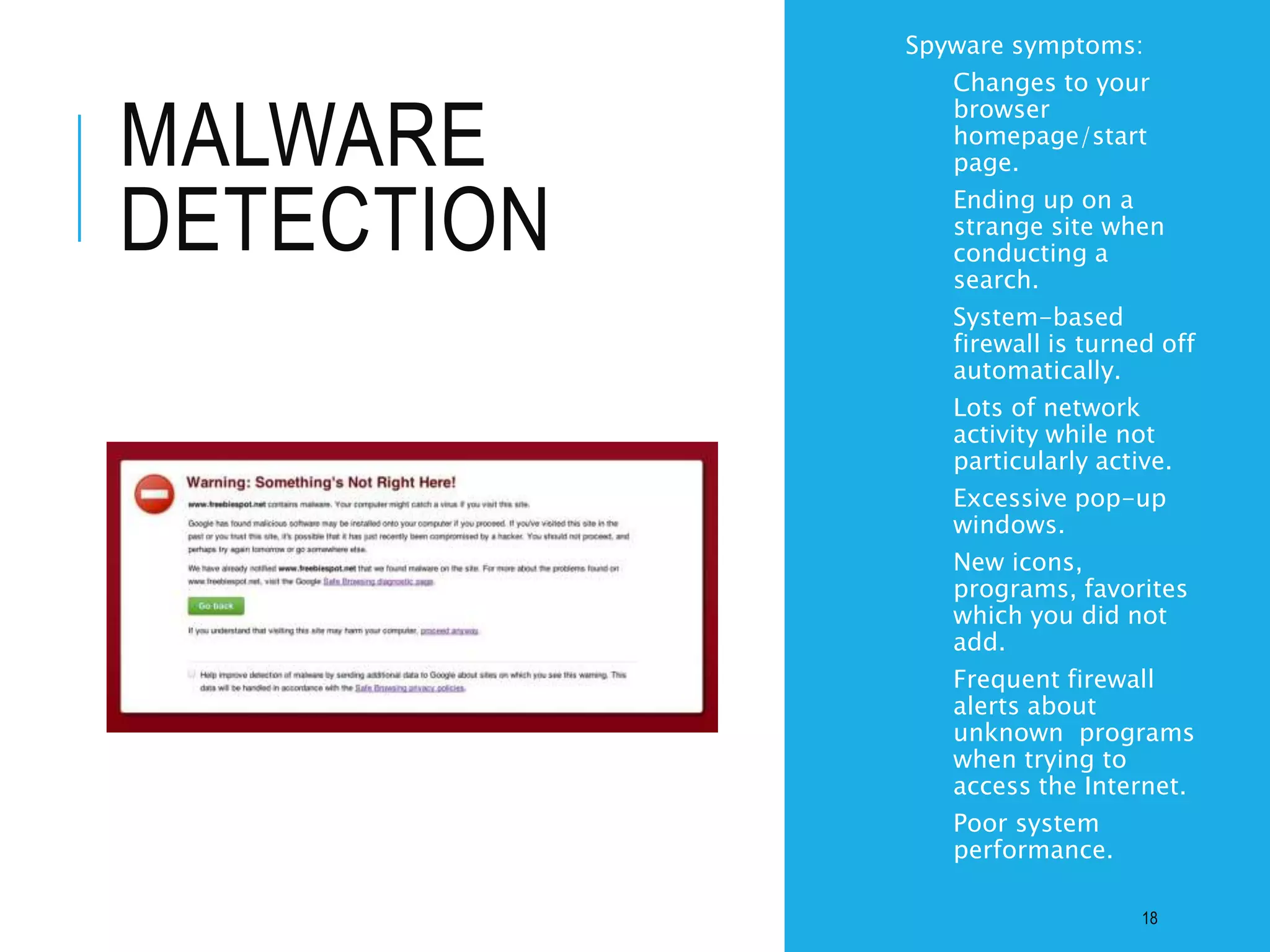
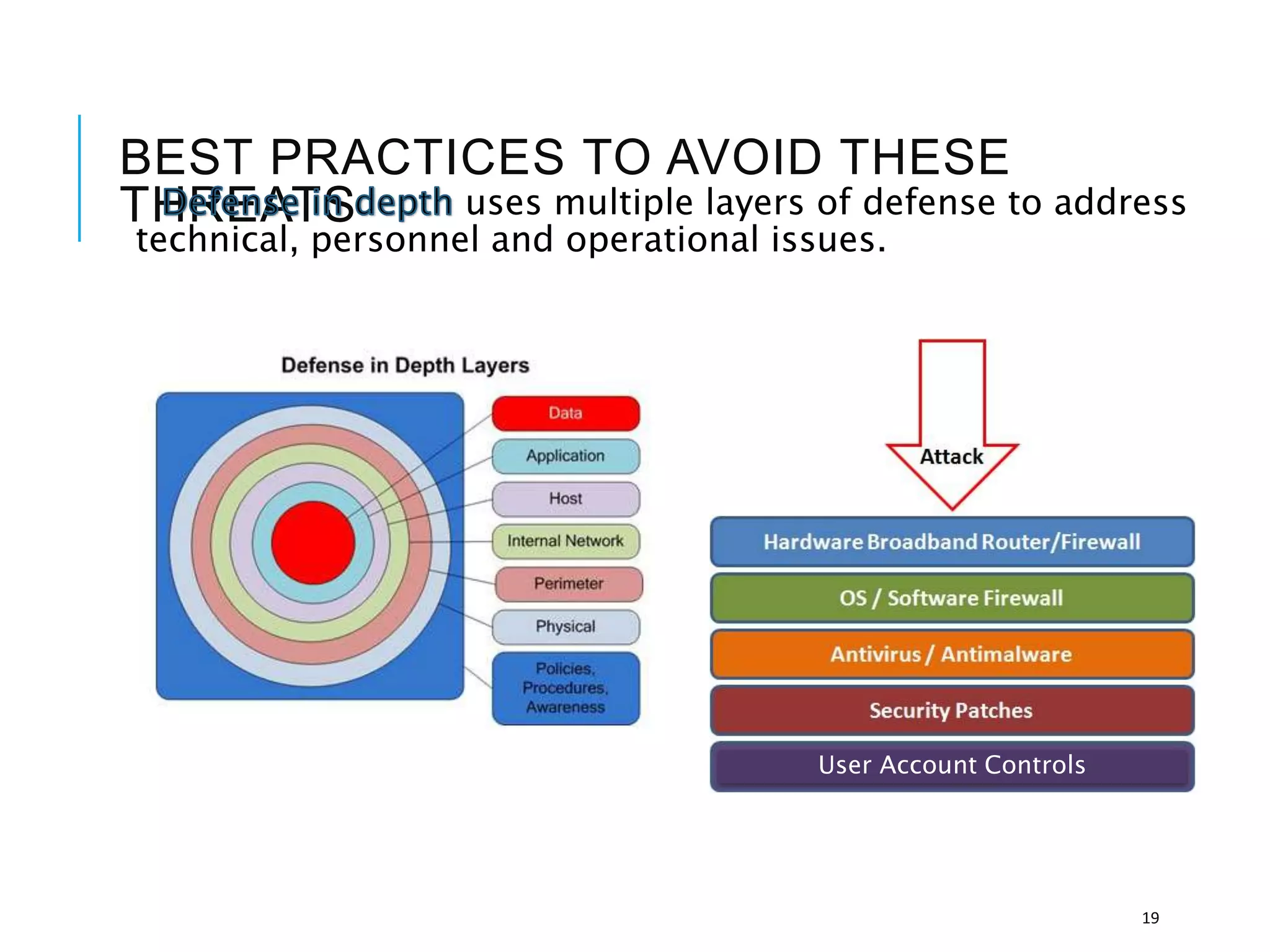
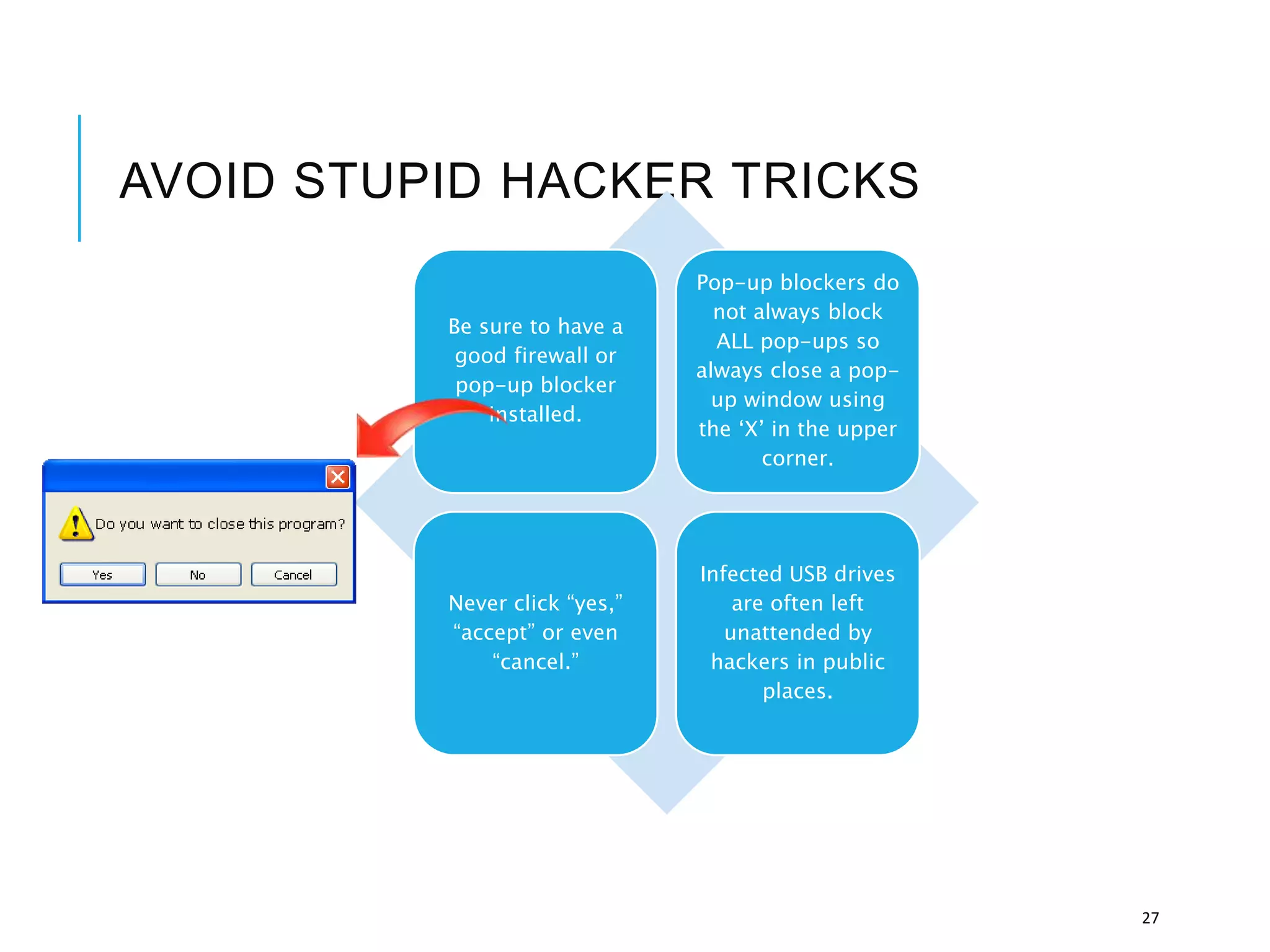
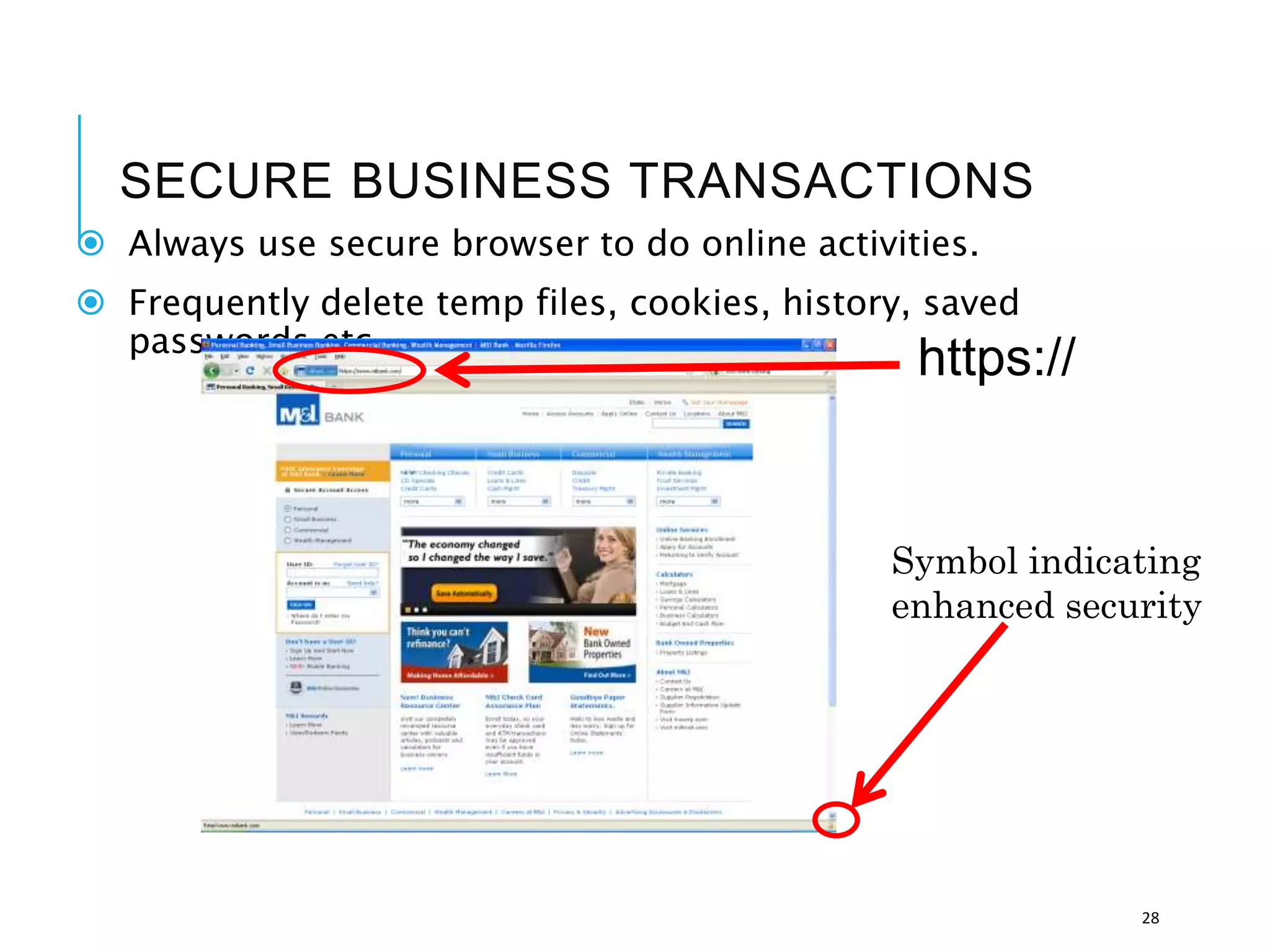
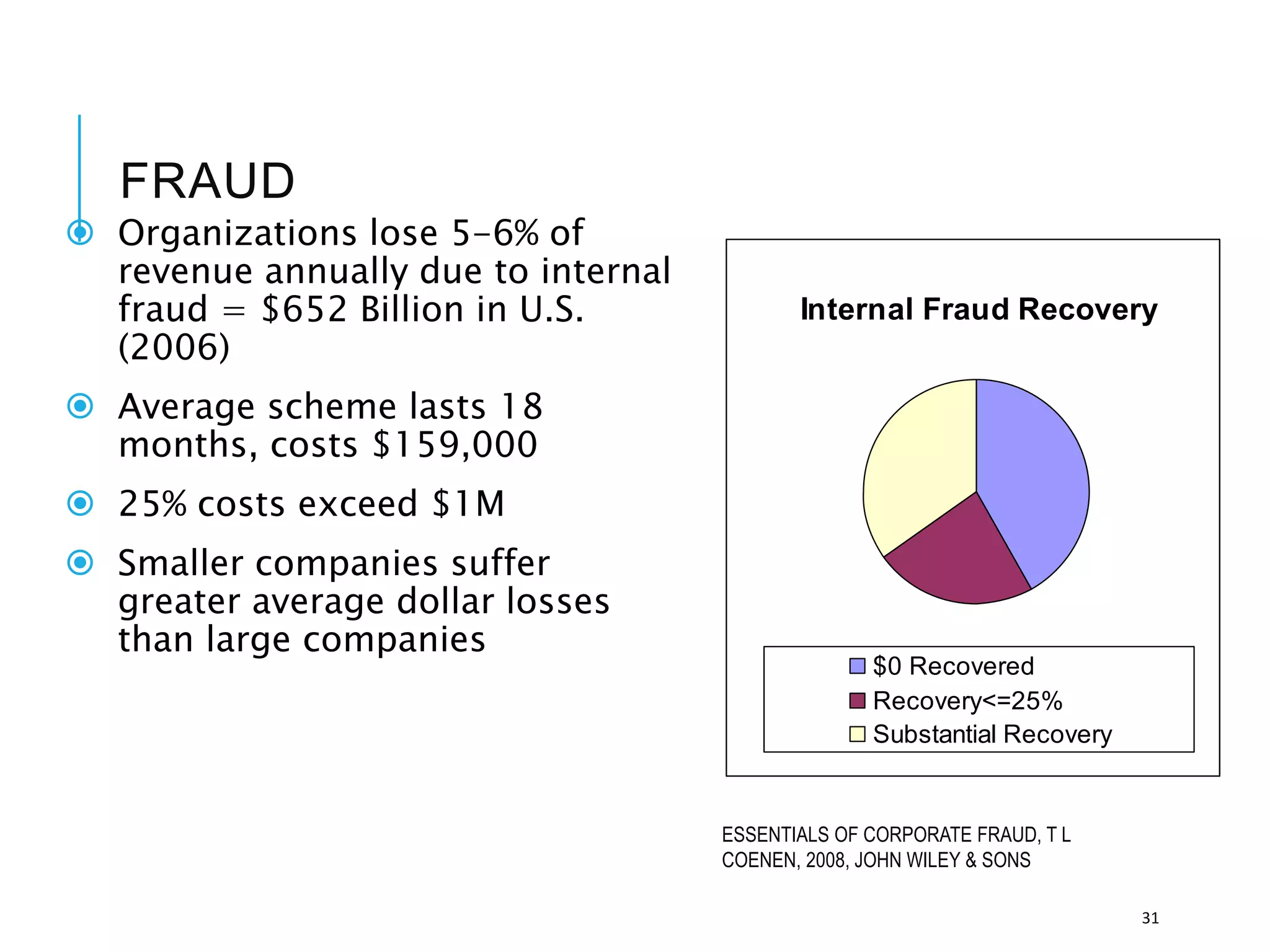
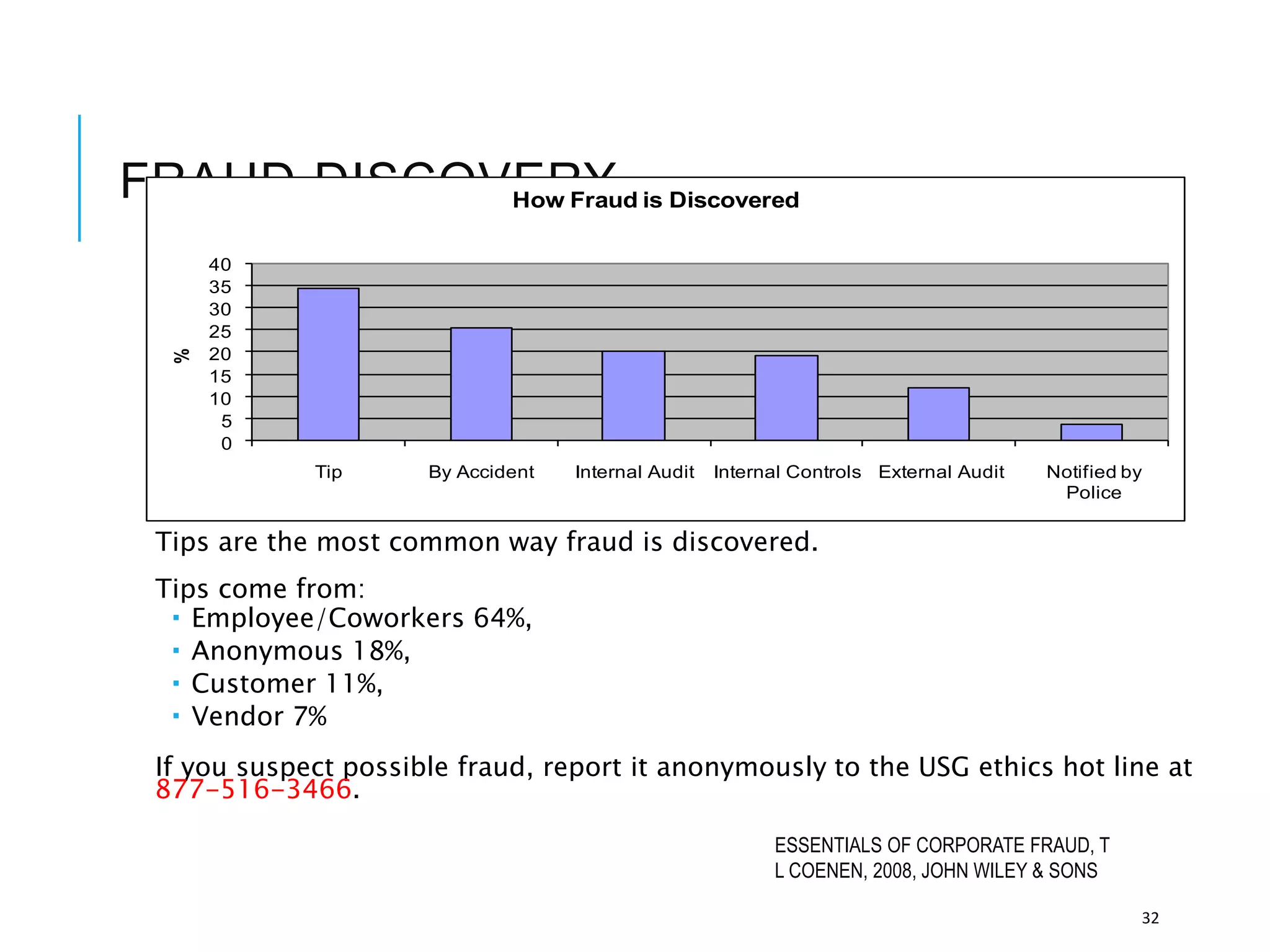
This document discusses the importance of cybersecurity and provides best practices to protect against common cyber threats. It begins by outlining the risks of identity theft, monetary theft, and legal ramifications from poor cybersecurity practices. It then describes common vectors for vulnerabilities like web browsers and excess user rights. The document summarizes several leading cyber threats like viruses, worms, Trojan horses, and social engineering. It provides examples of these threats and recommends practices like using antivirus software, firewalls, strong passwords, and regular backups to help avoid security compromises. The summary emphasizes implementing multiple layers of defense to address technical, personnel, and operational cybersecurity issues.