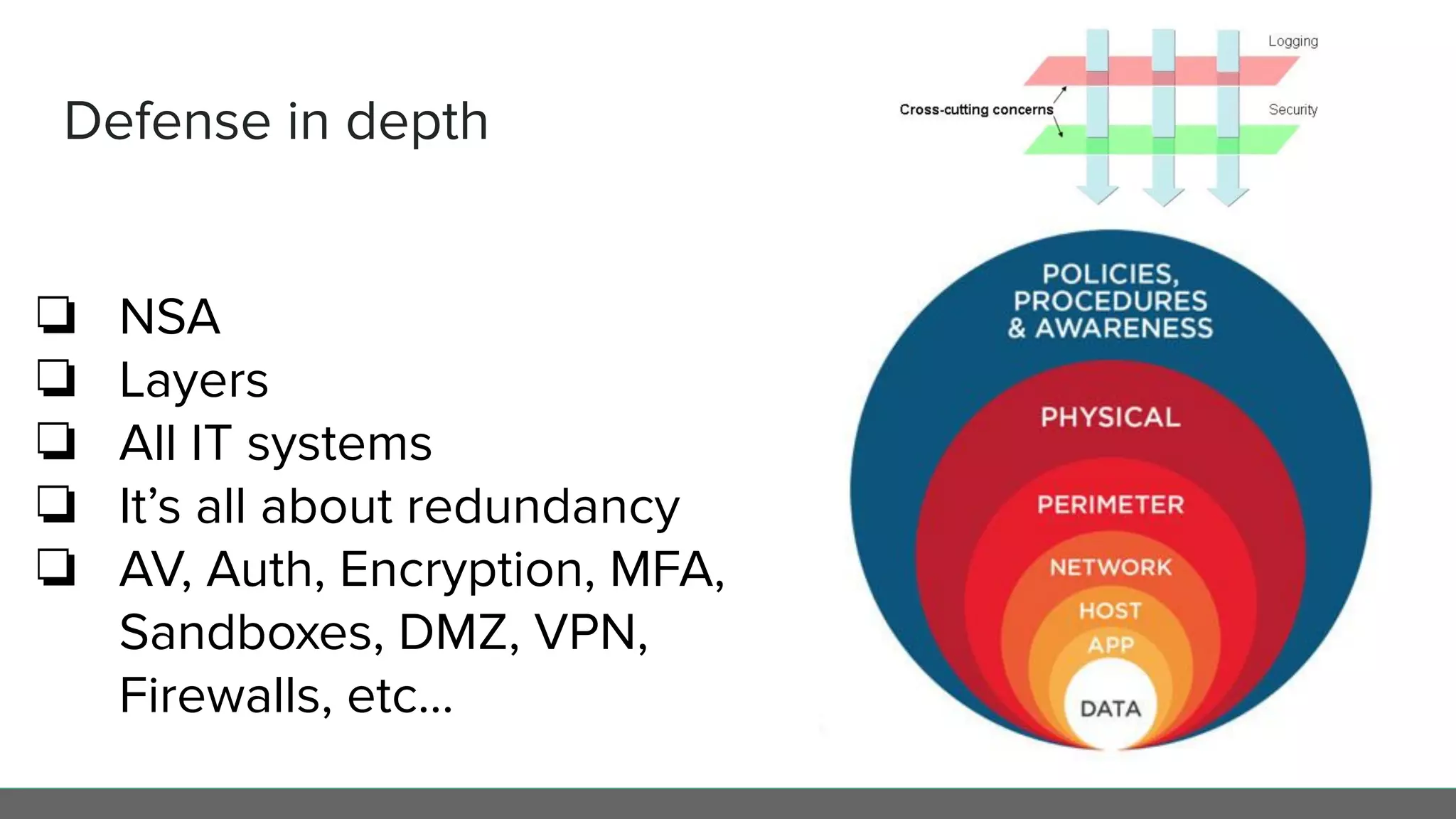
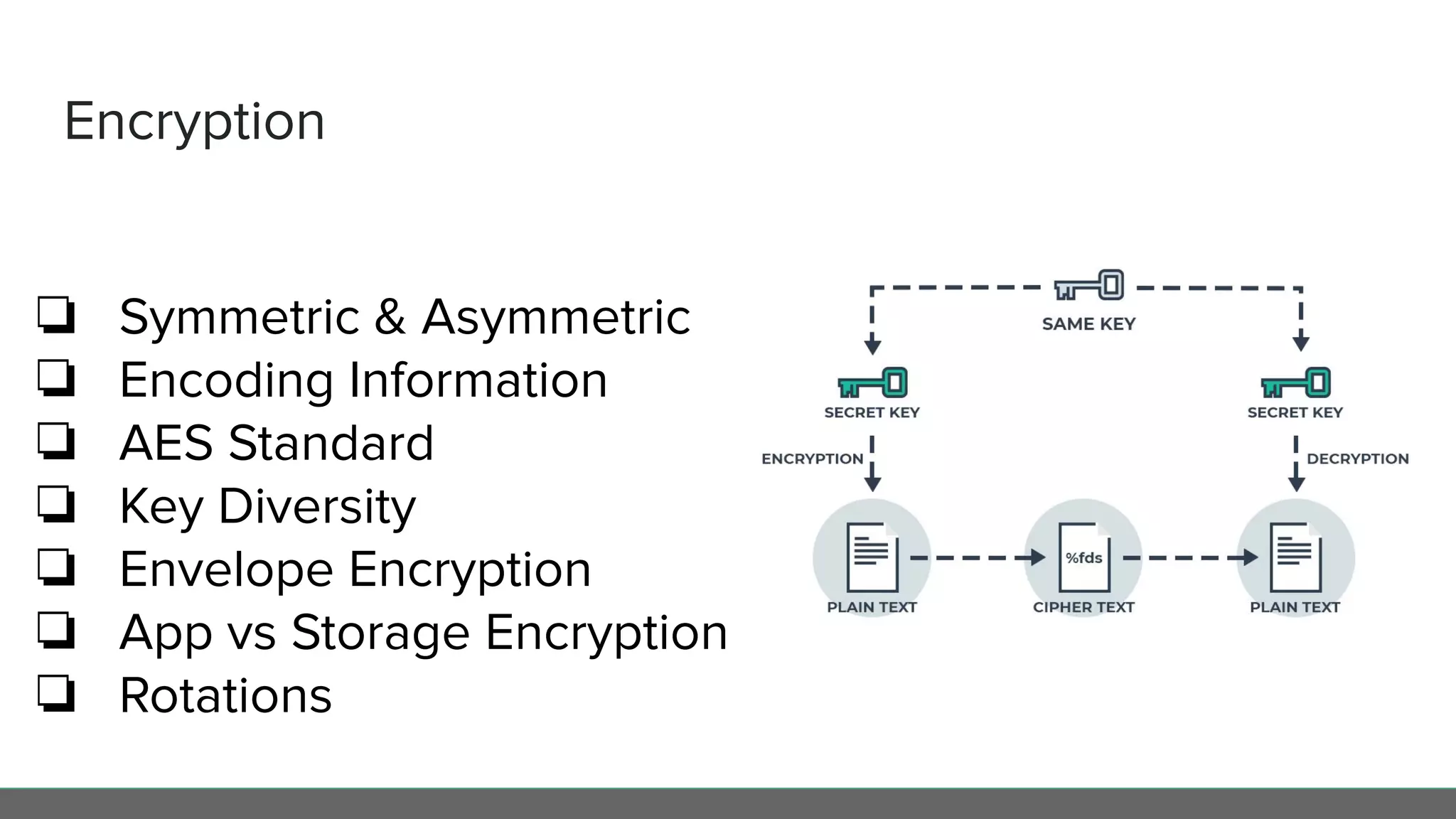
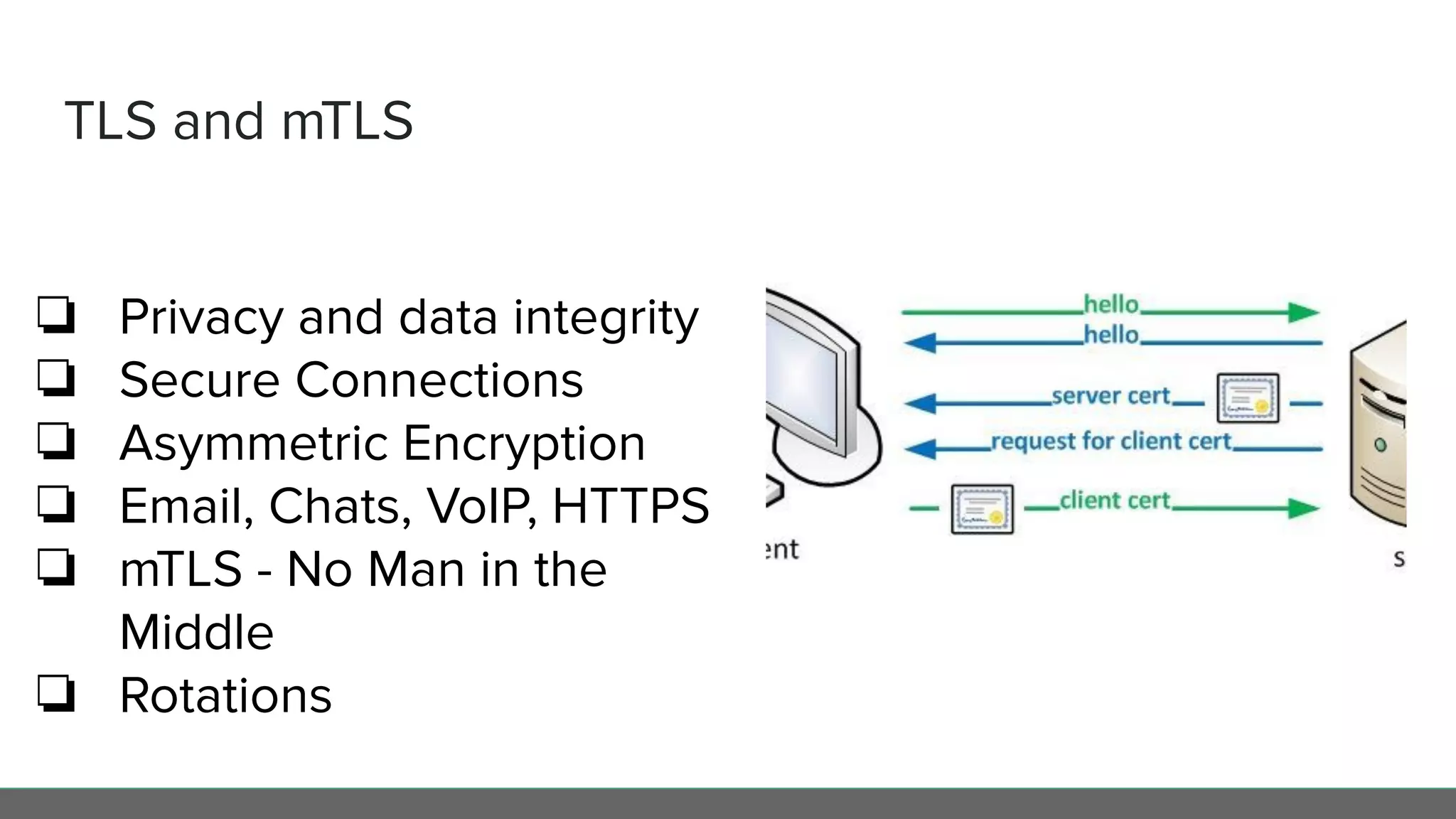
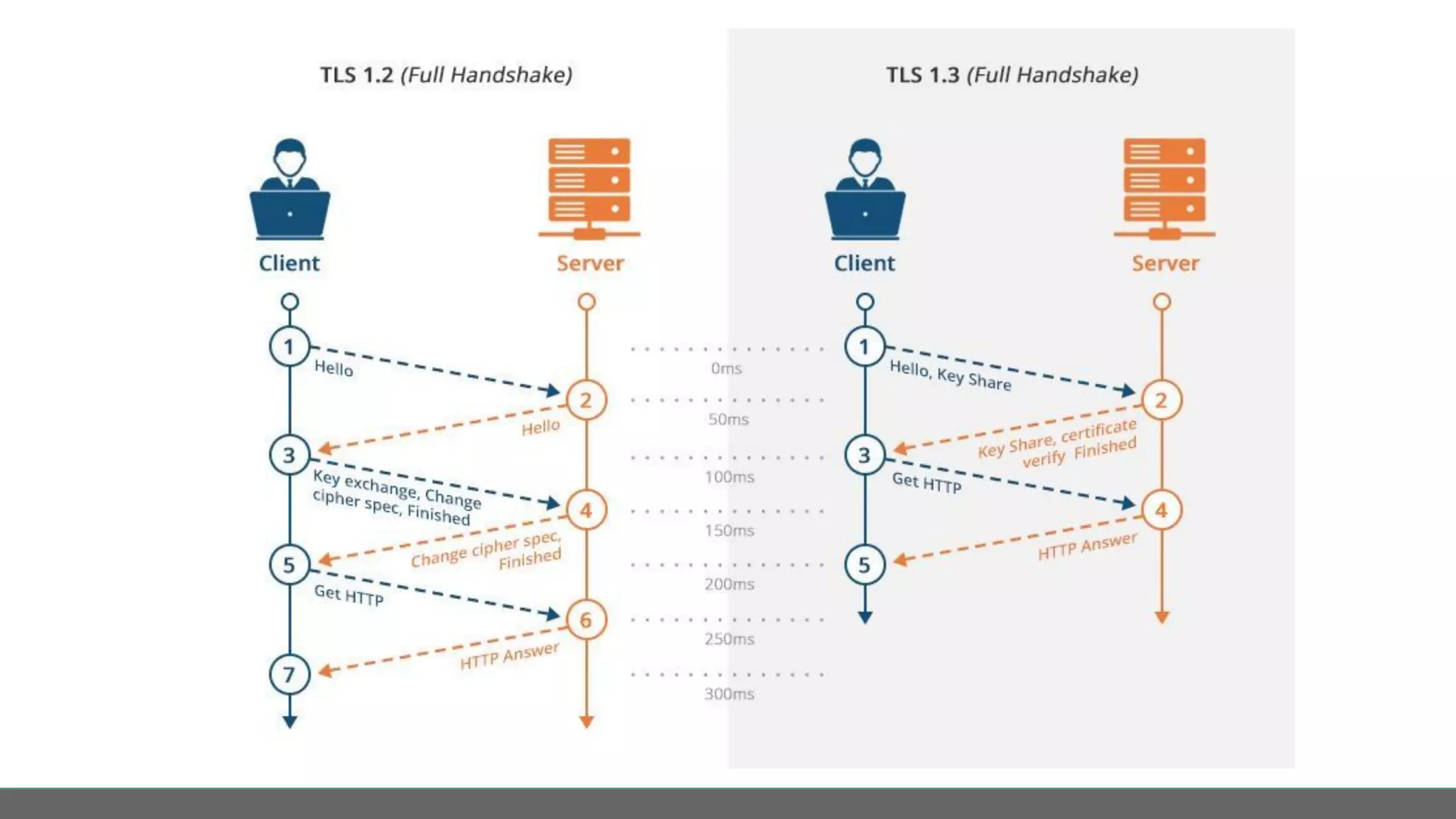
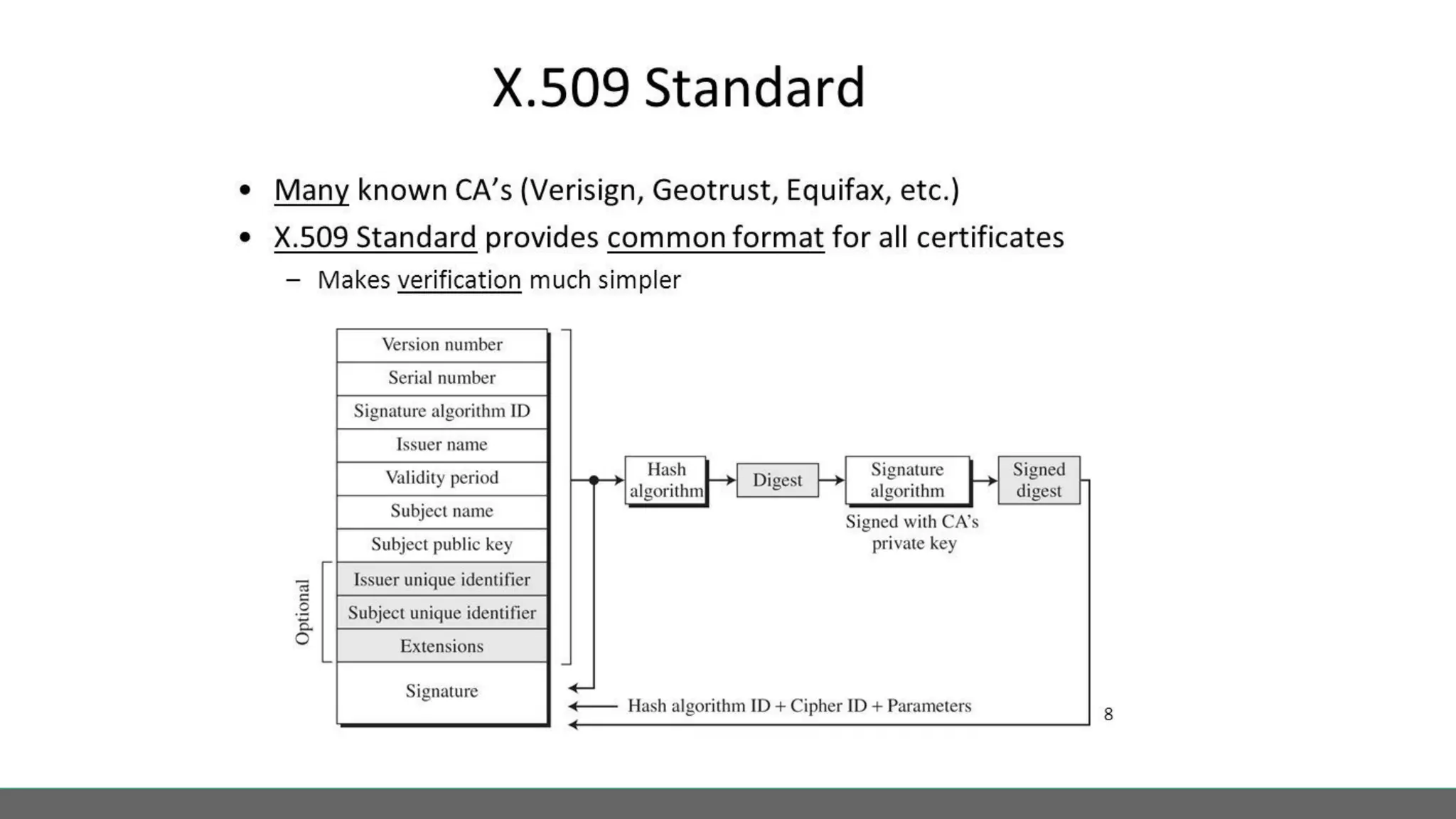
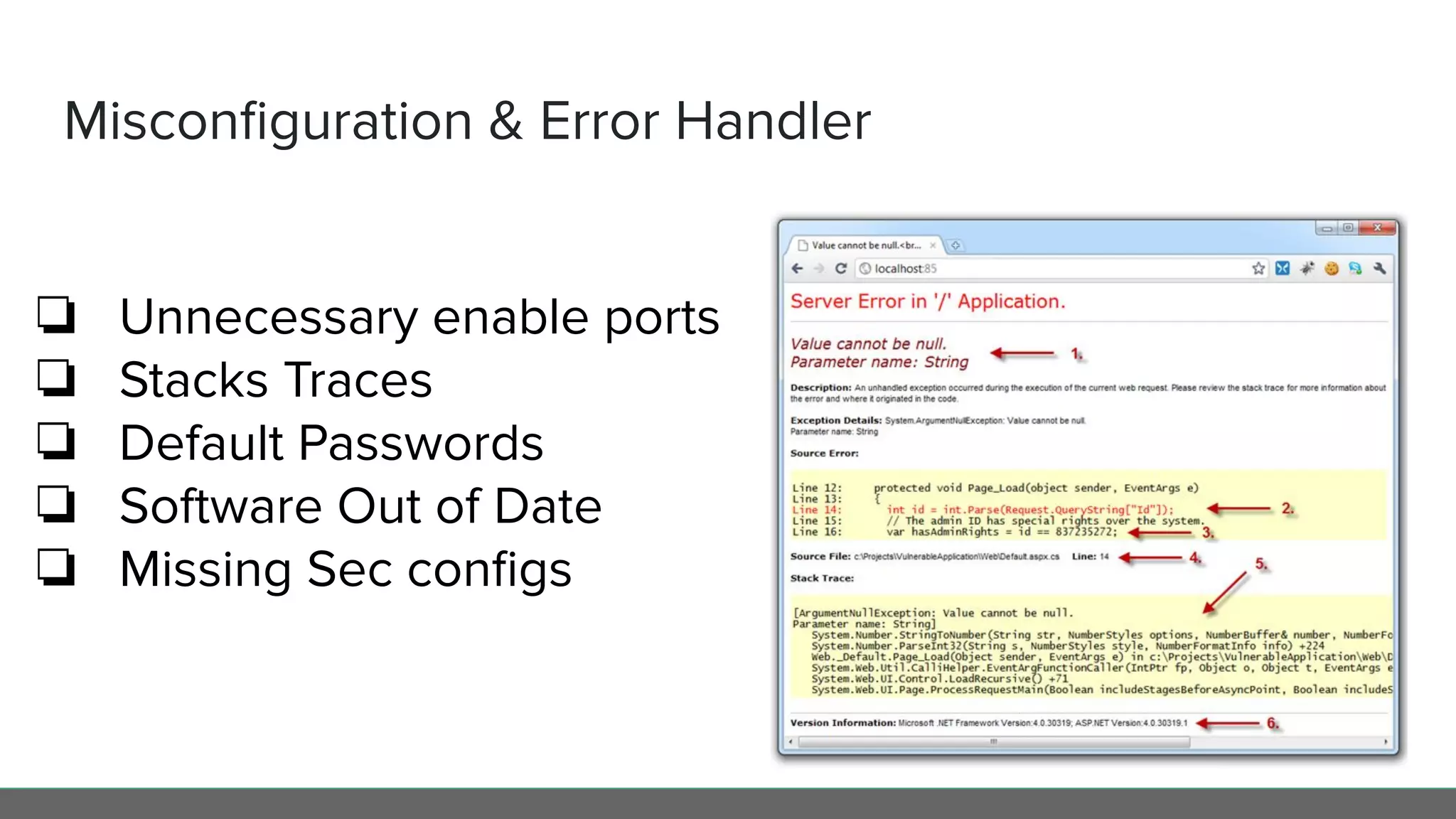
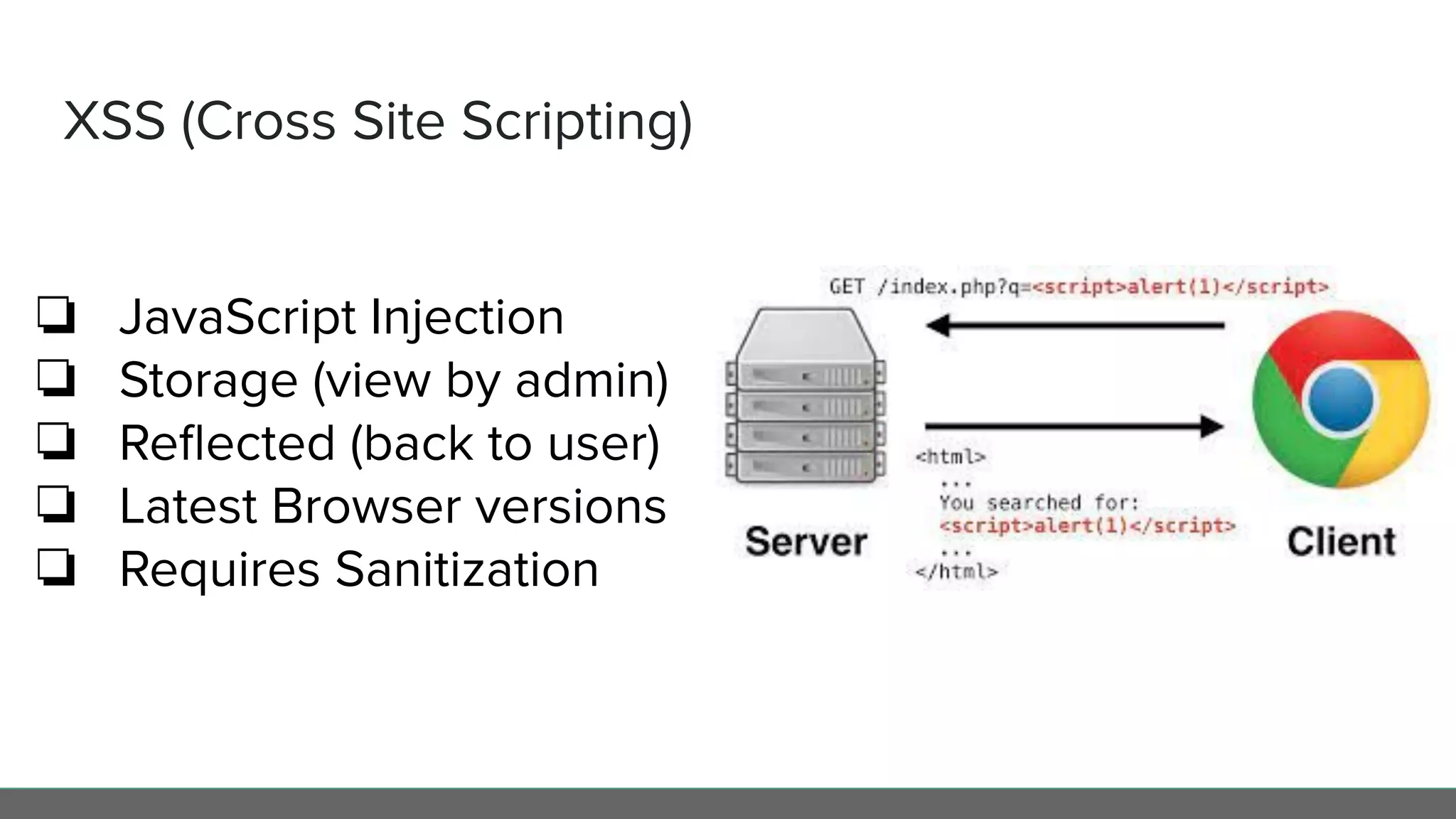
This document profiles Diego Pacheco and provides an overview of key software security principles including defense in depth, the least privilege principle, encryption, TLS and mTLS, misconfiguration and error handling, input sanitization, cross-site scripting (XSS), insecure serialization/deserialization, known vulnerabilities, logging and audit trails, threat analysis, and engineering friction. The document emphasizes applying security best practices to protect customer experience, brand integrity, and compliance while avoiding friction for engineering teams.