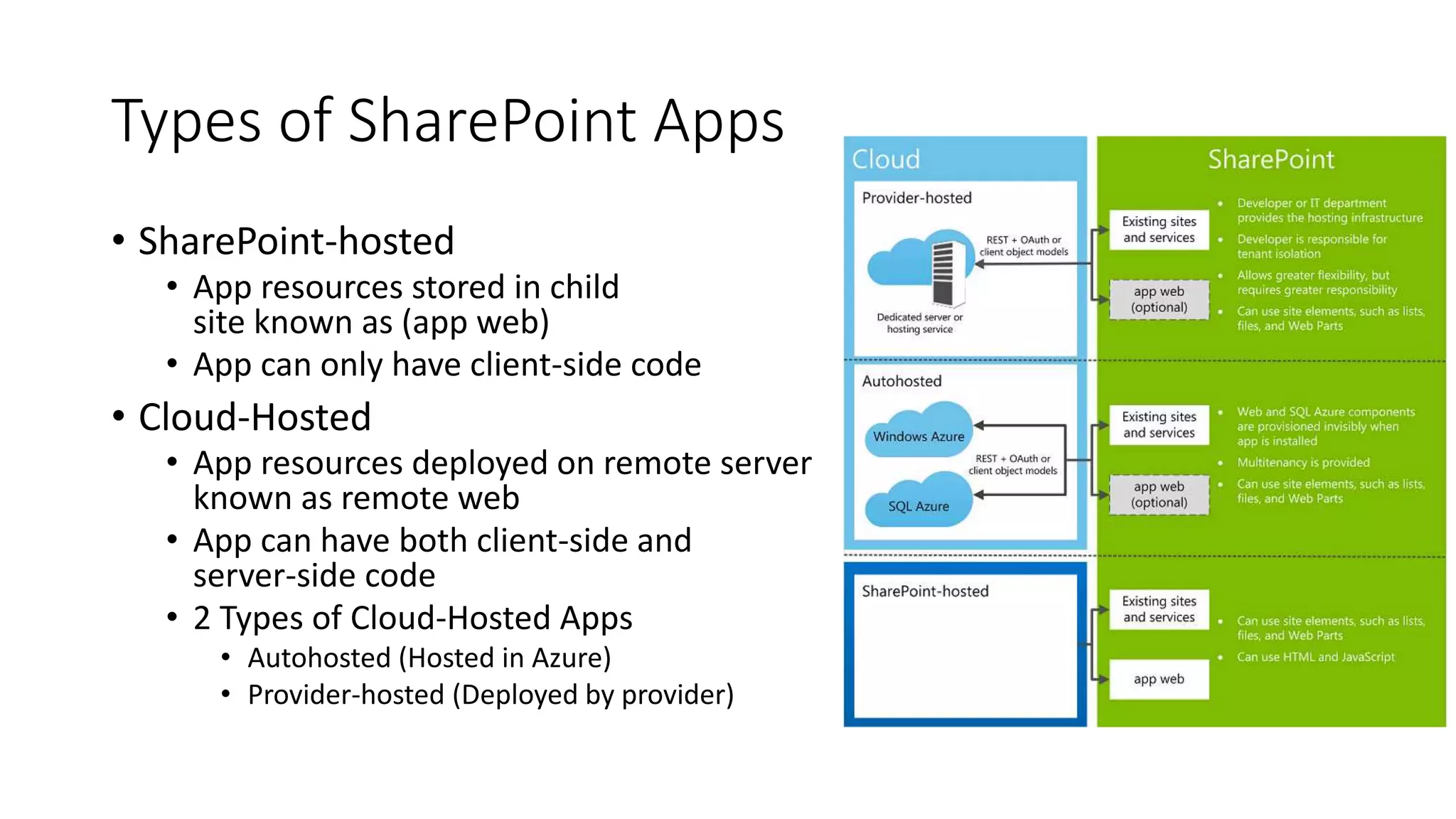
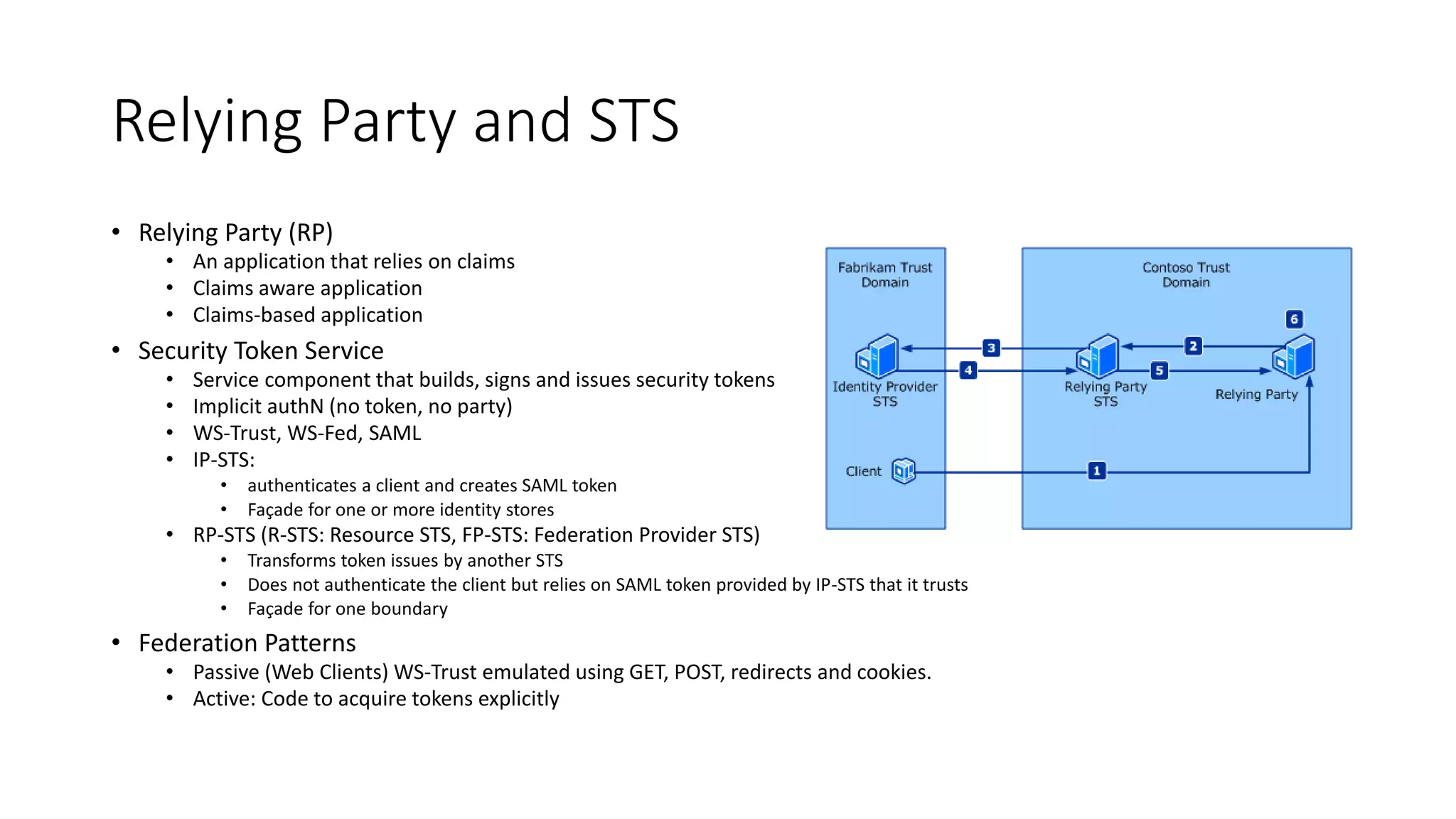
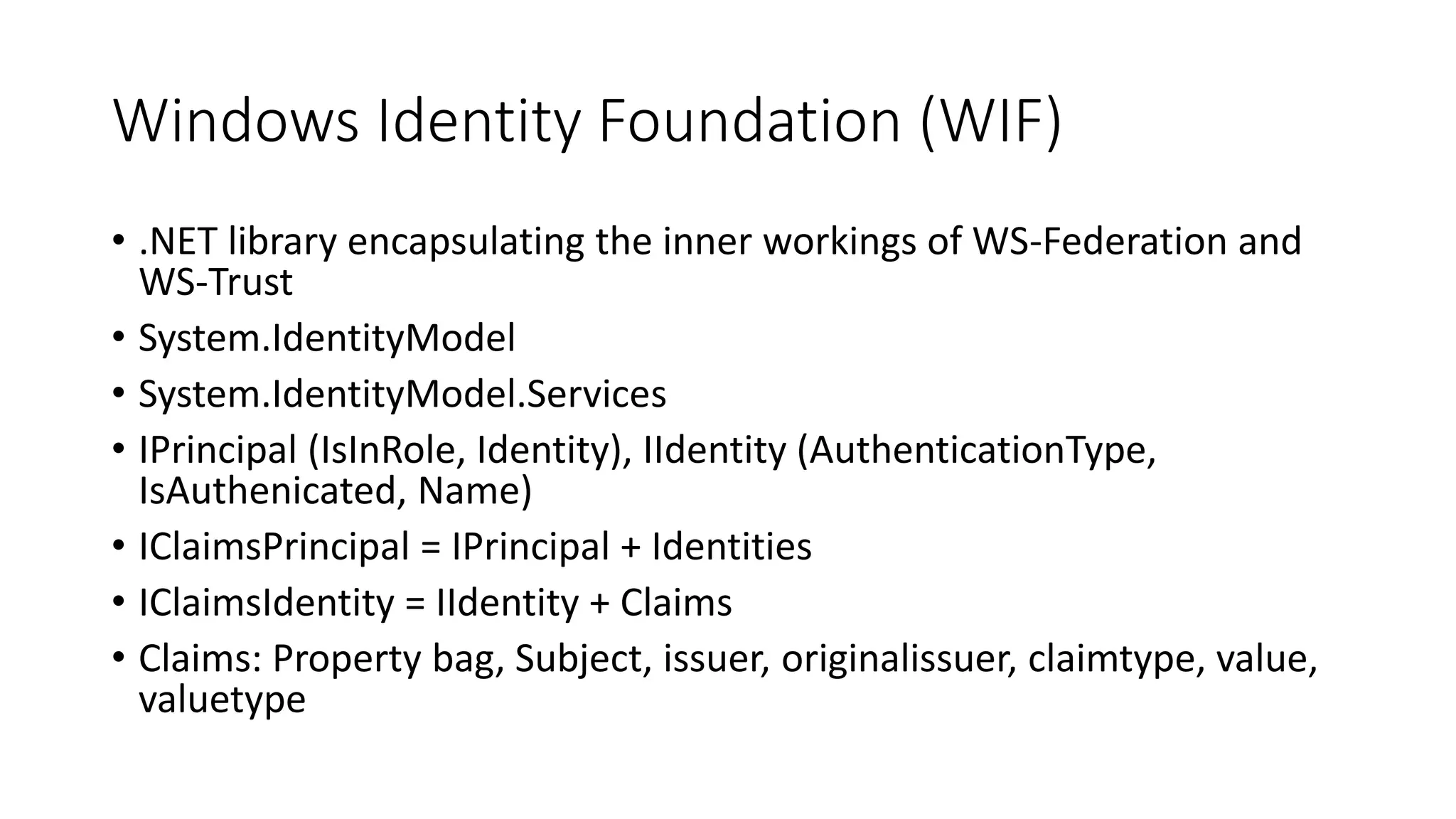
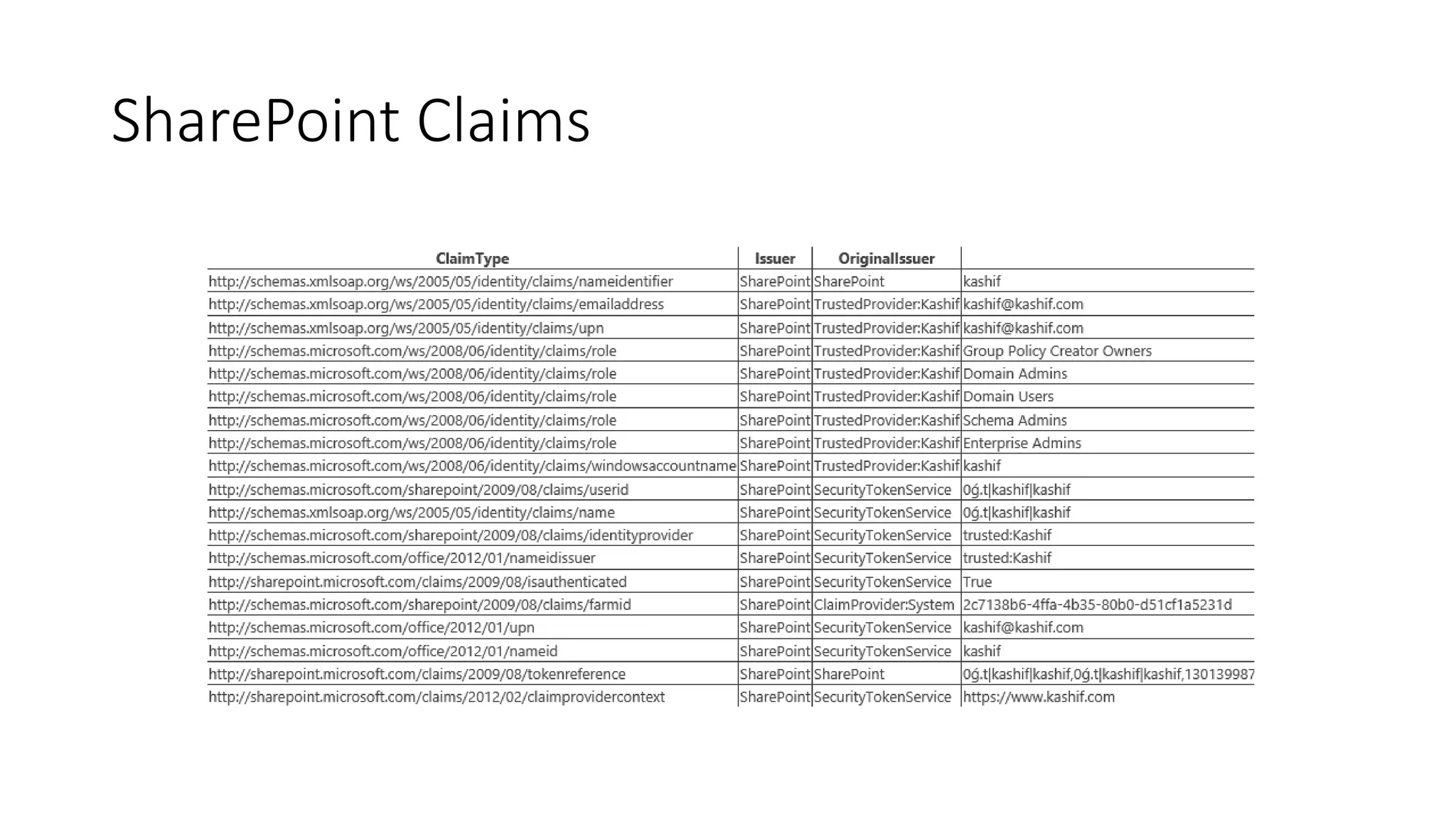
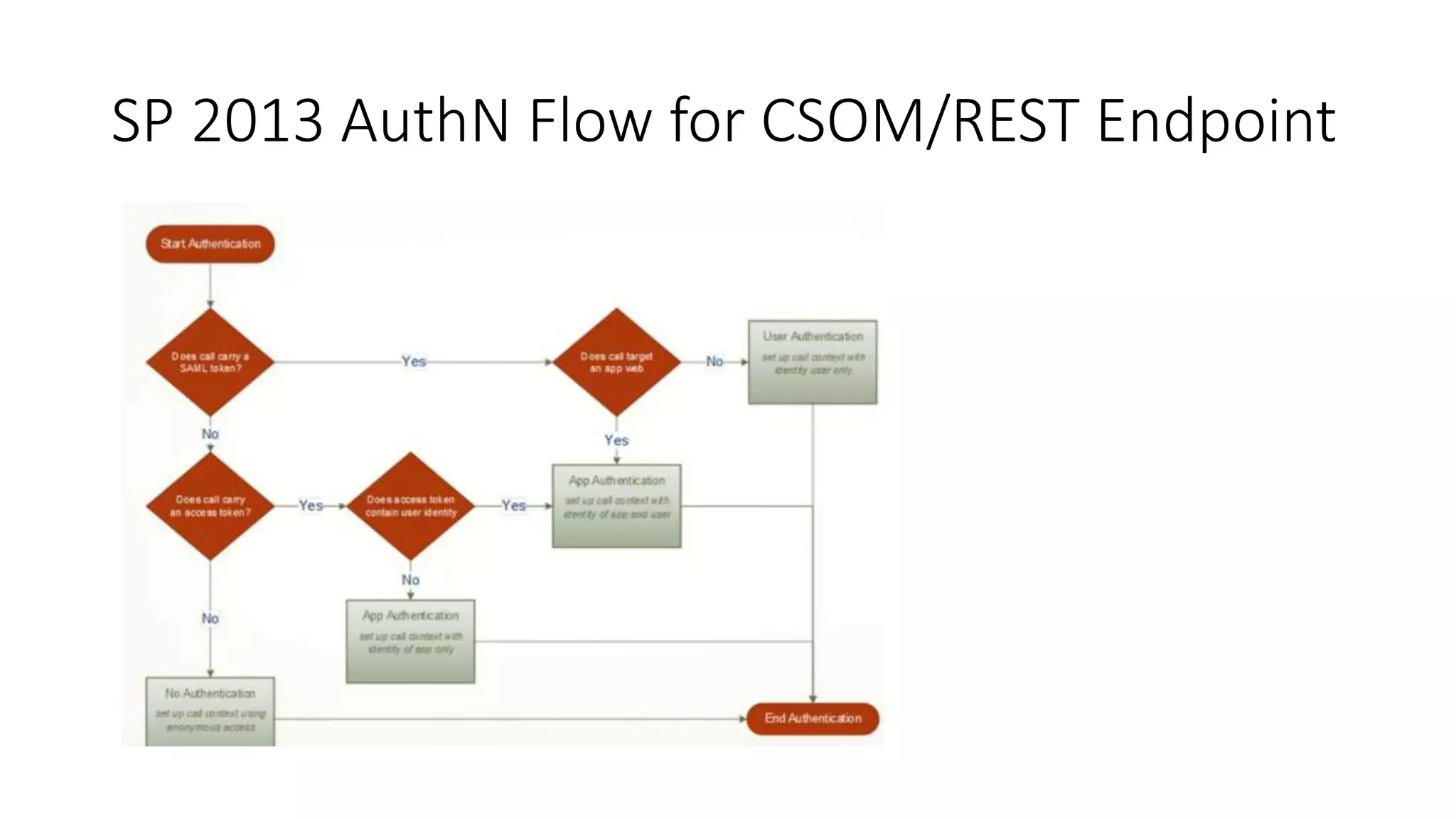
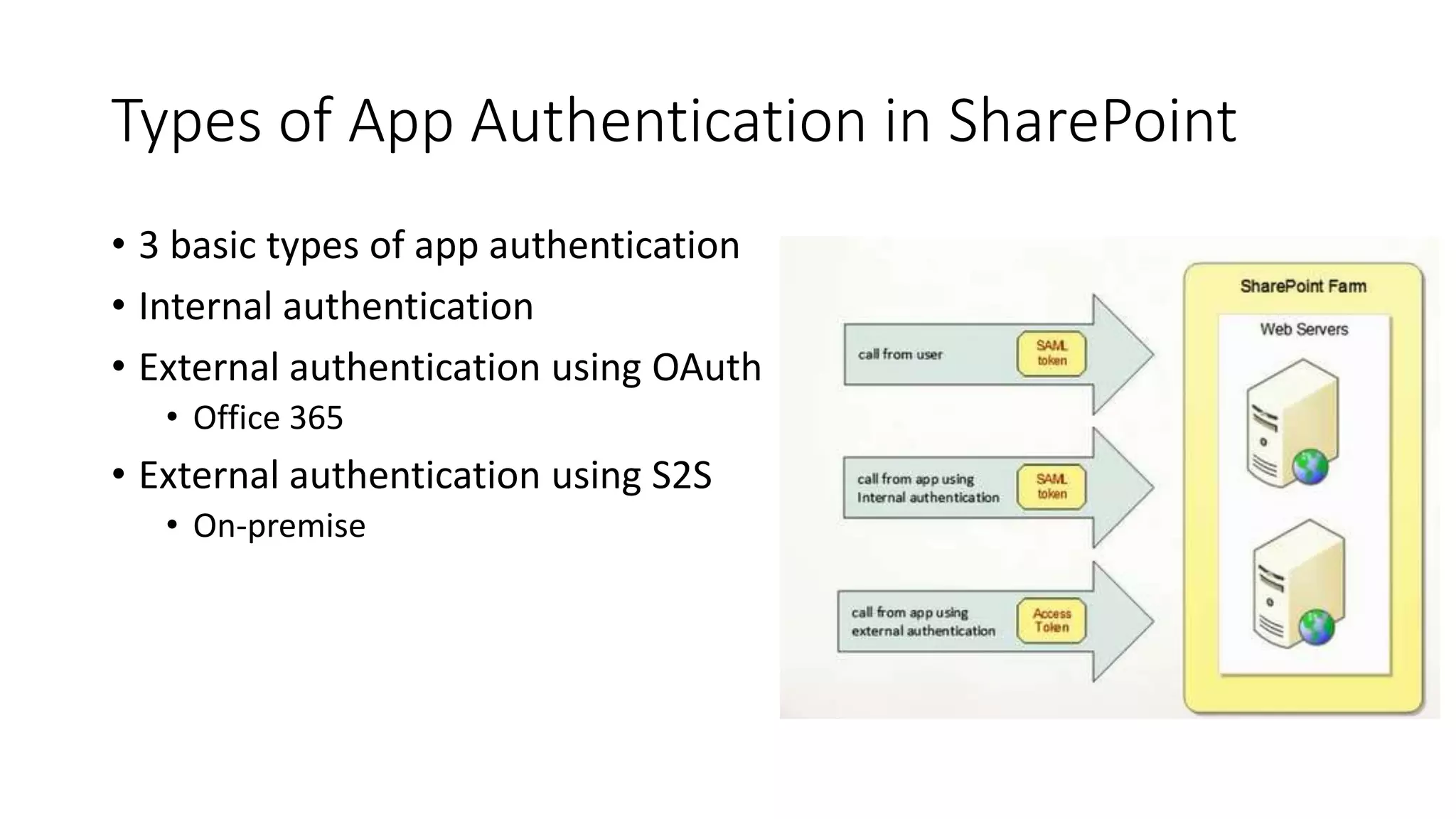
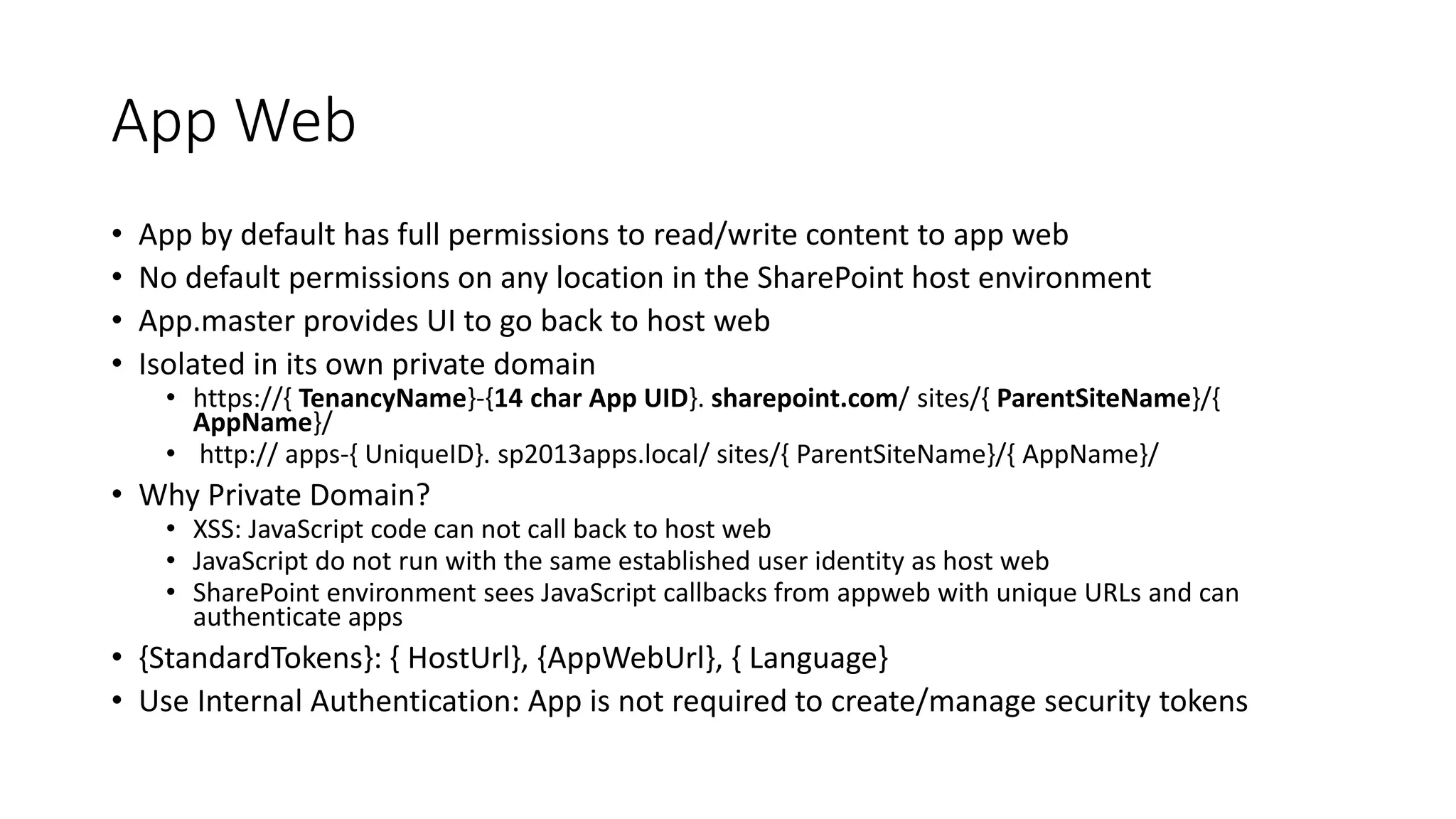
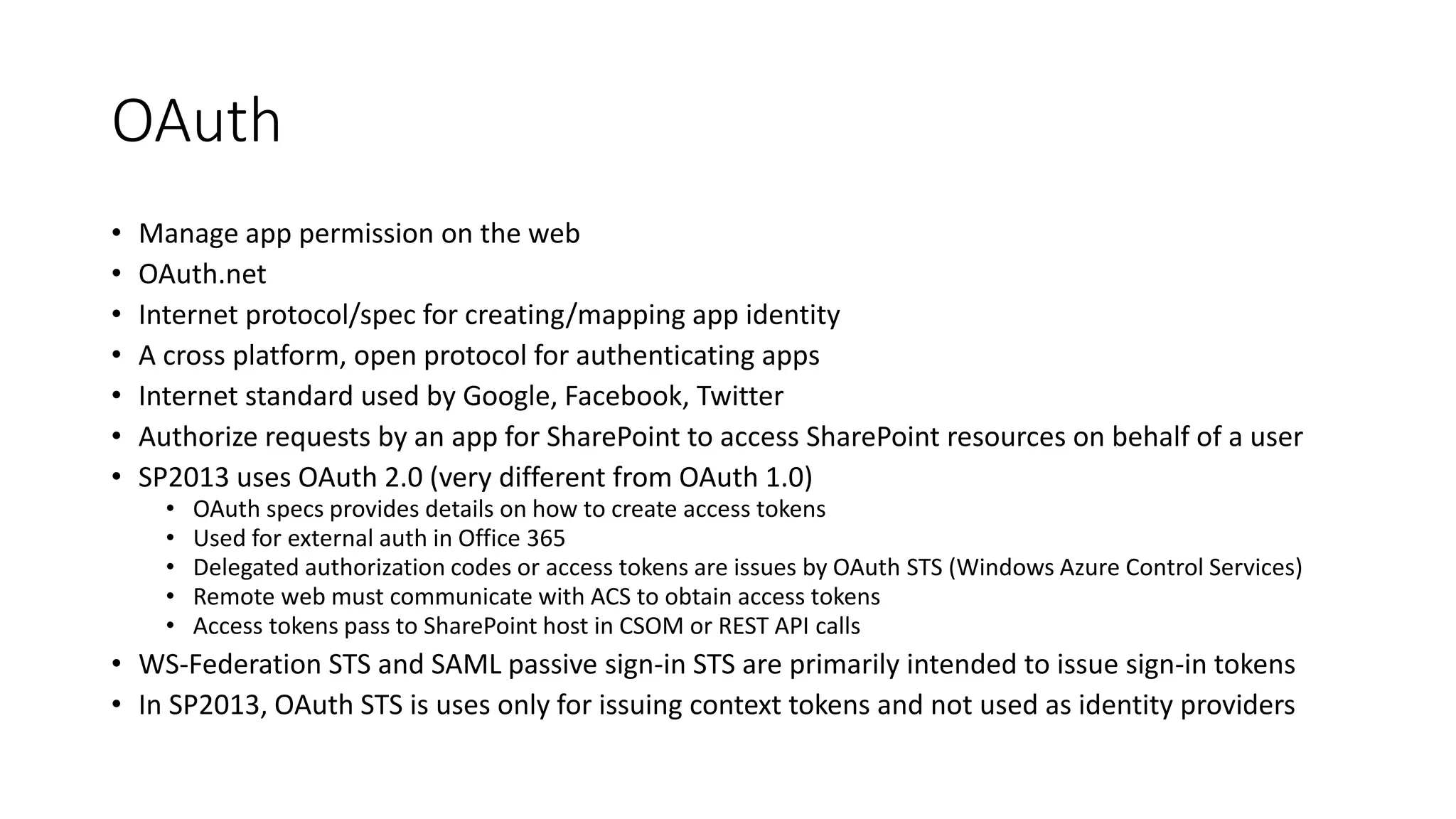
This document discusses securing SharePoint apps using OAuth authentication. It provides an overview of app authentication in SharePoint 2013, including the use of OAuth and app principals. The key points covered are:
- SharePoint 2013 supports app authentication using OAuth or on-premise using security token service.
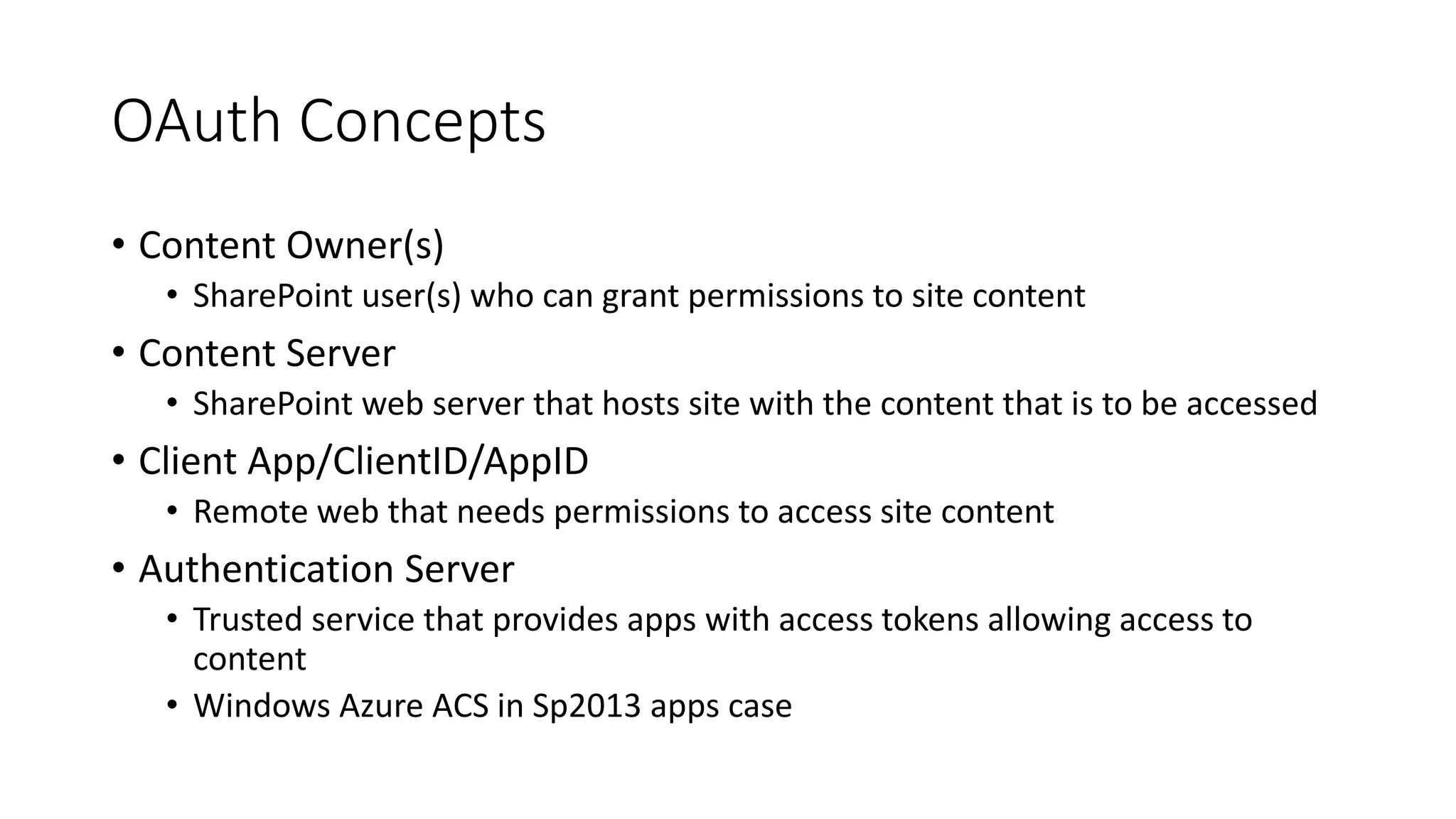
- Apps are assigned a principal that is used to manage app permissions separately from user permissions.
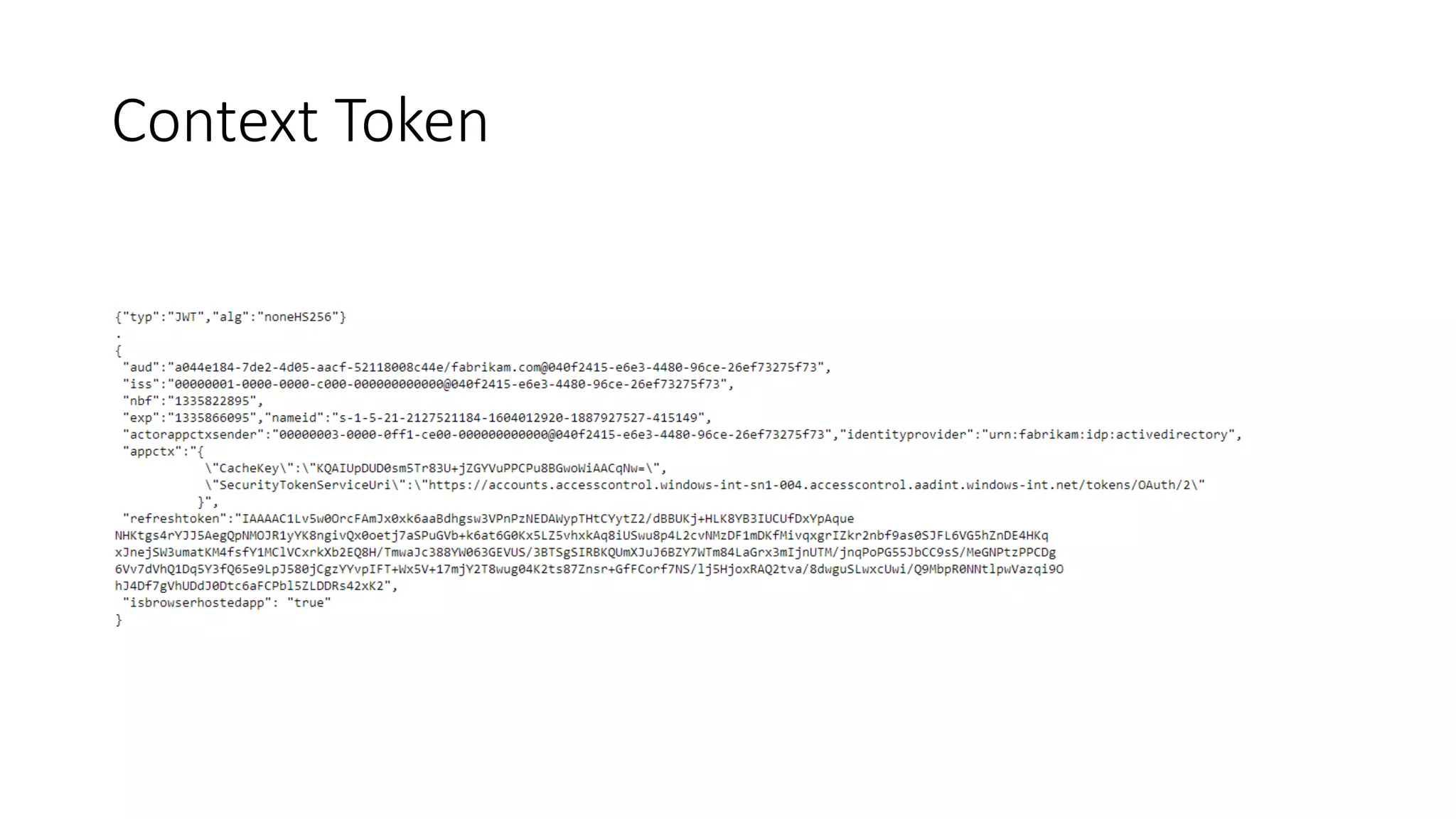
- The OAuth workflow involves apps obtaining access tokens from Azure Access Control Service to make calls to SharePoint on behalf of users.
- App principals must be registered both with SharePoint and ACS, and include a client ID, client secret, and redirect URL.