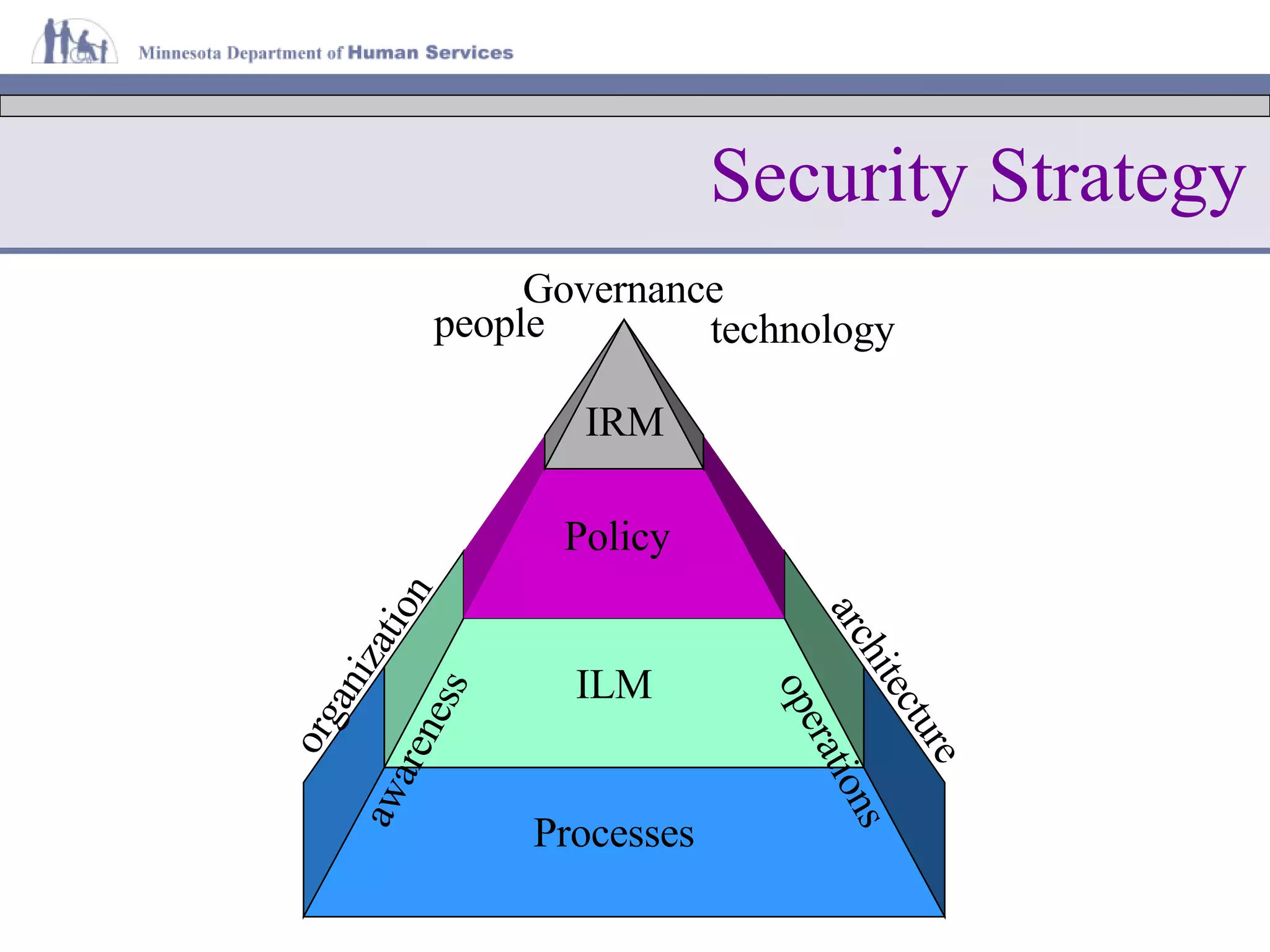
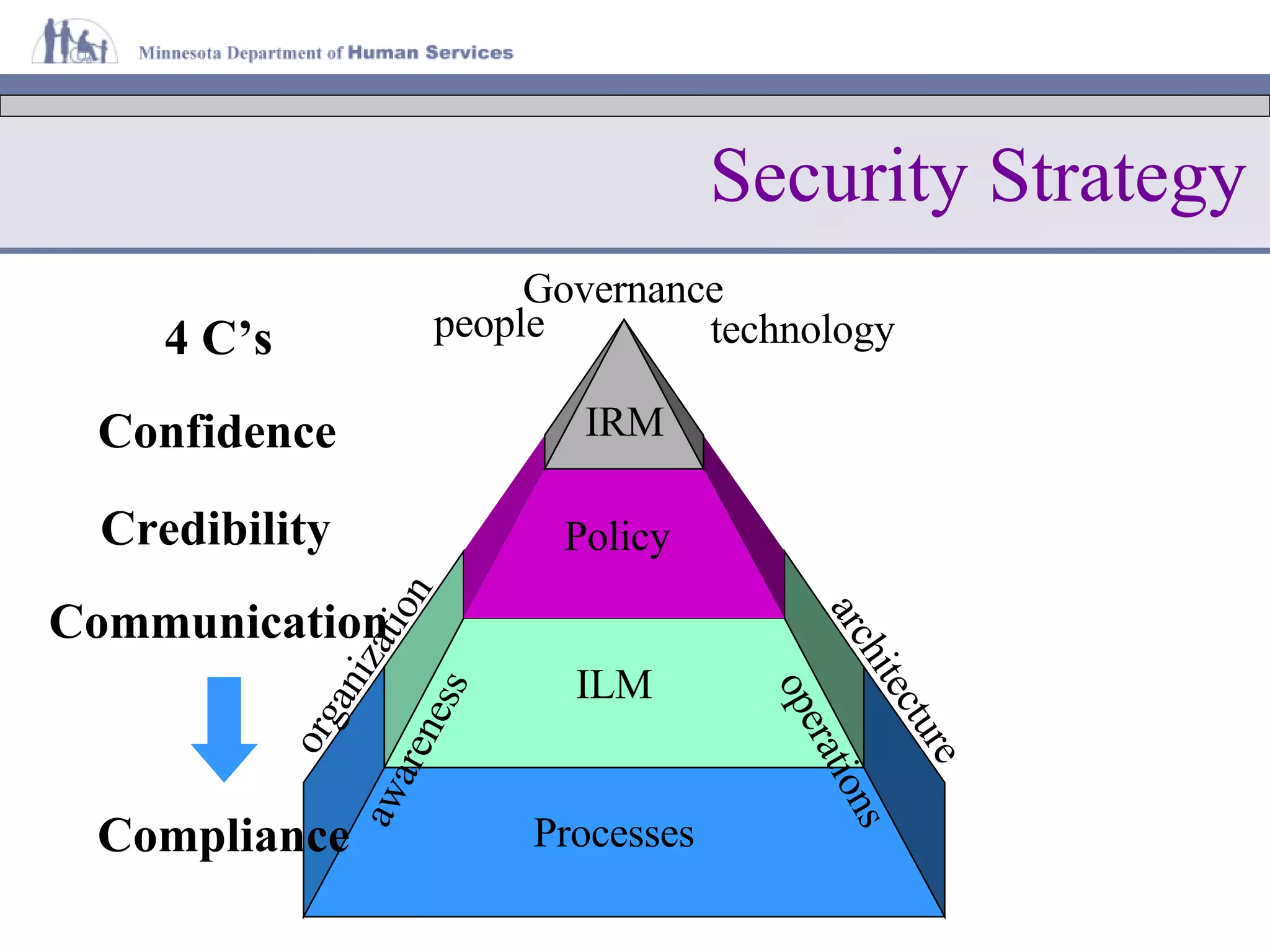
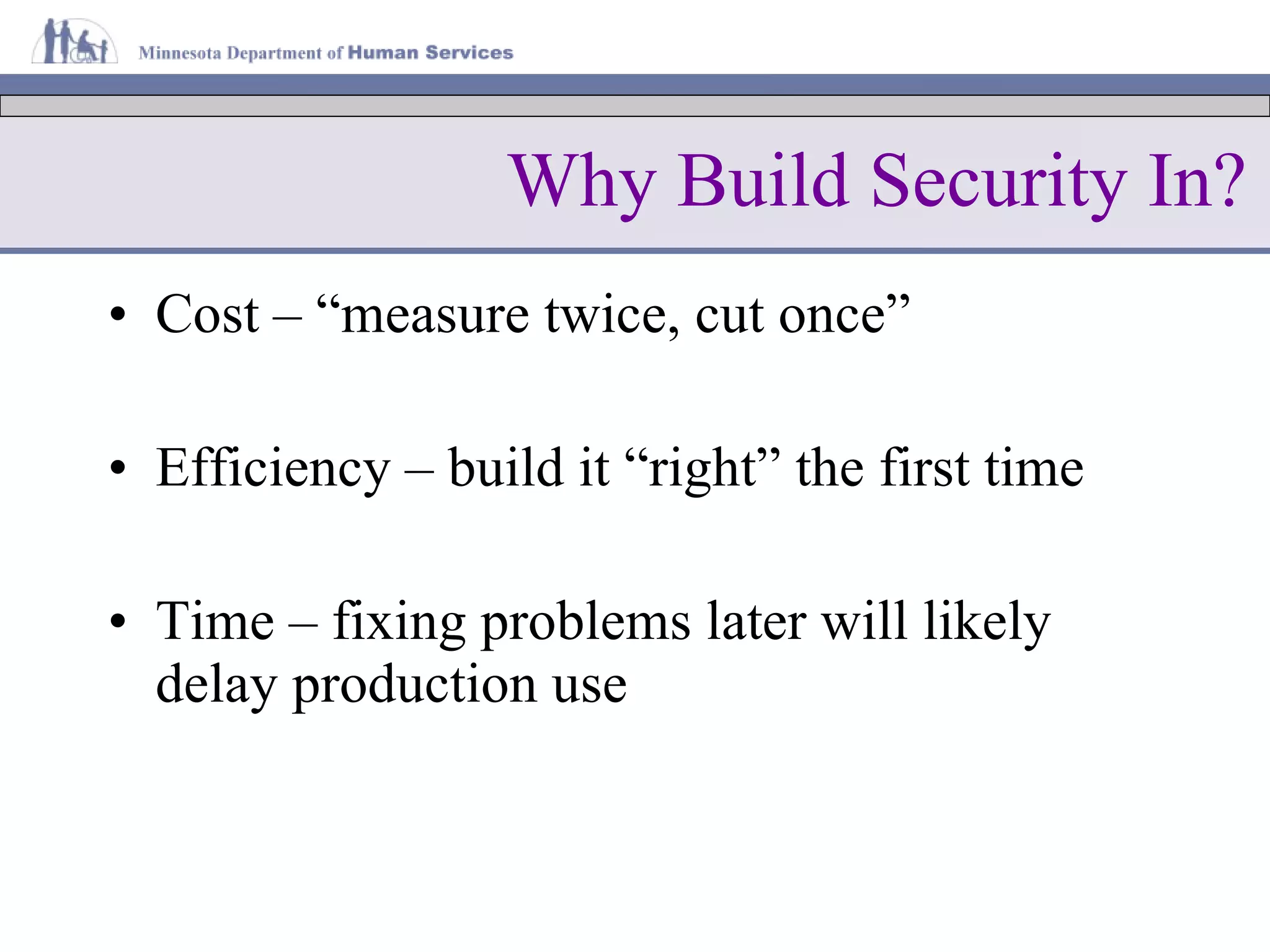
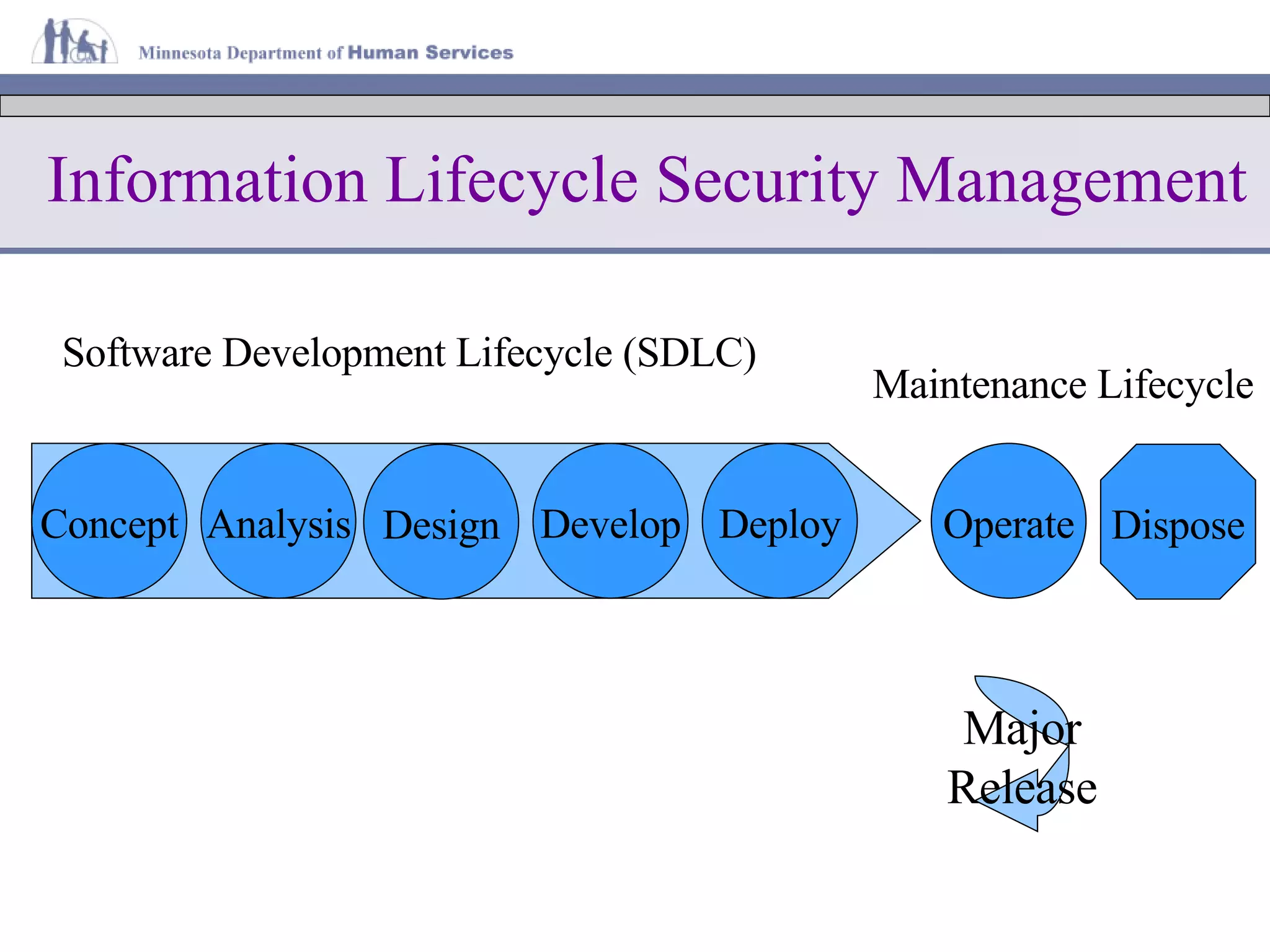
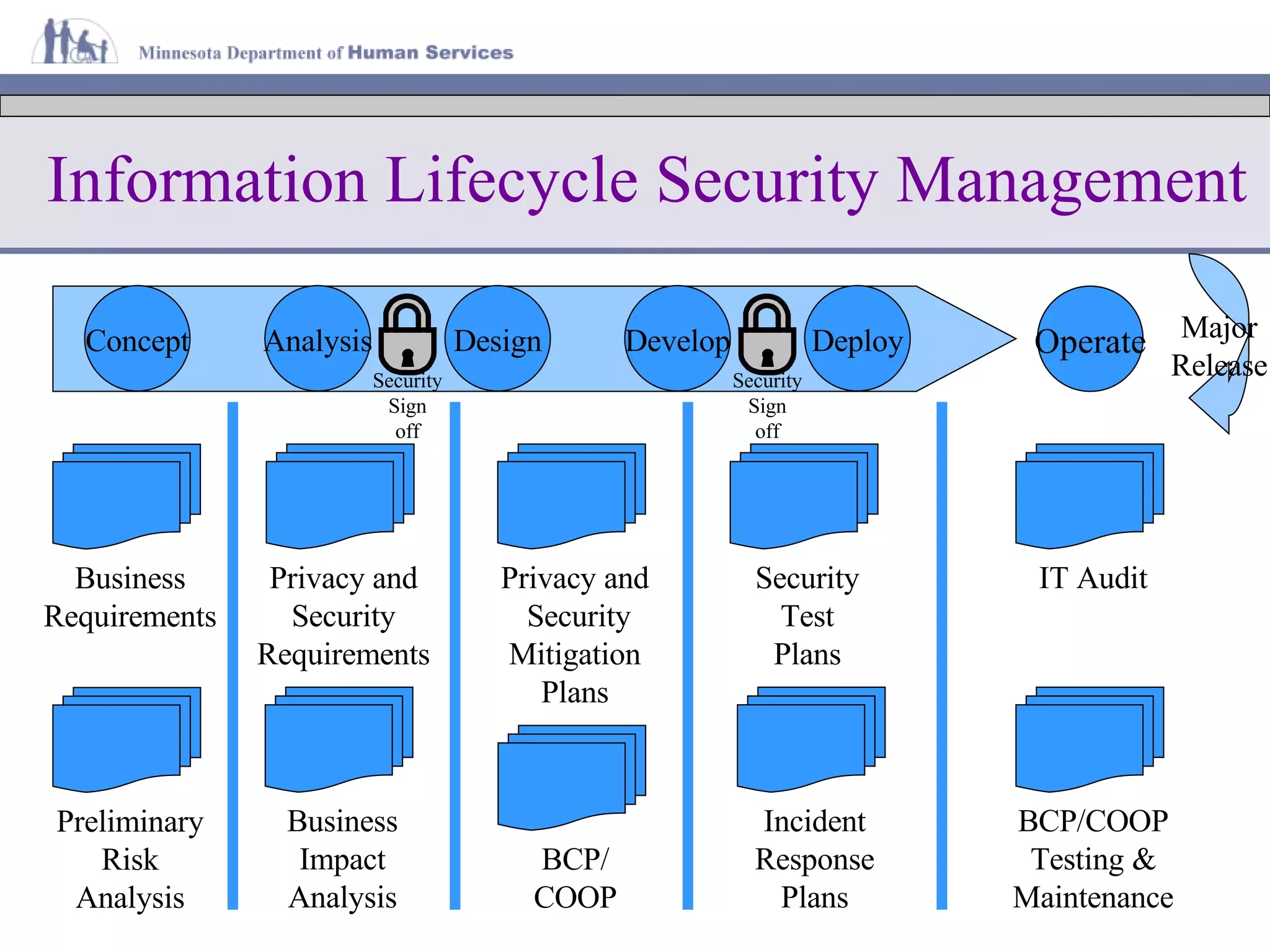
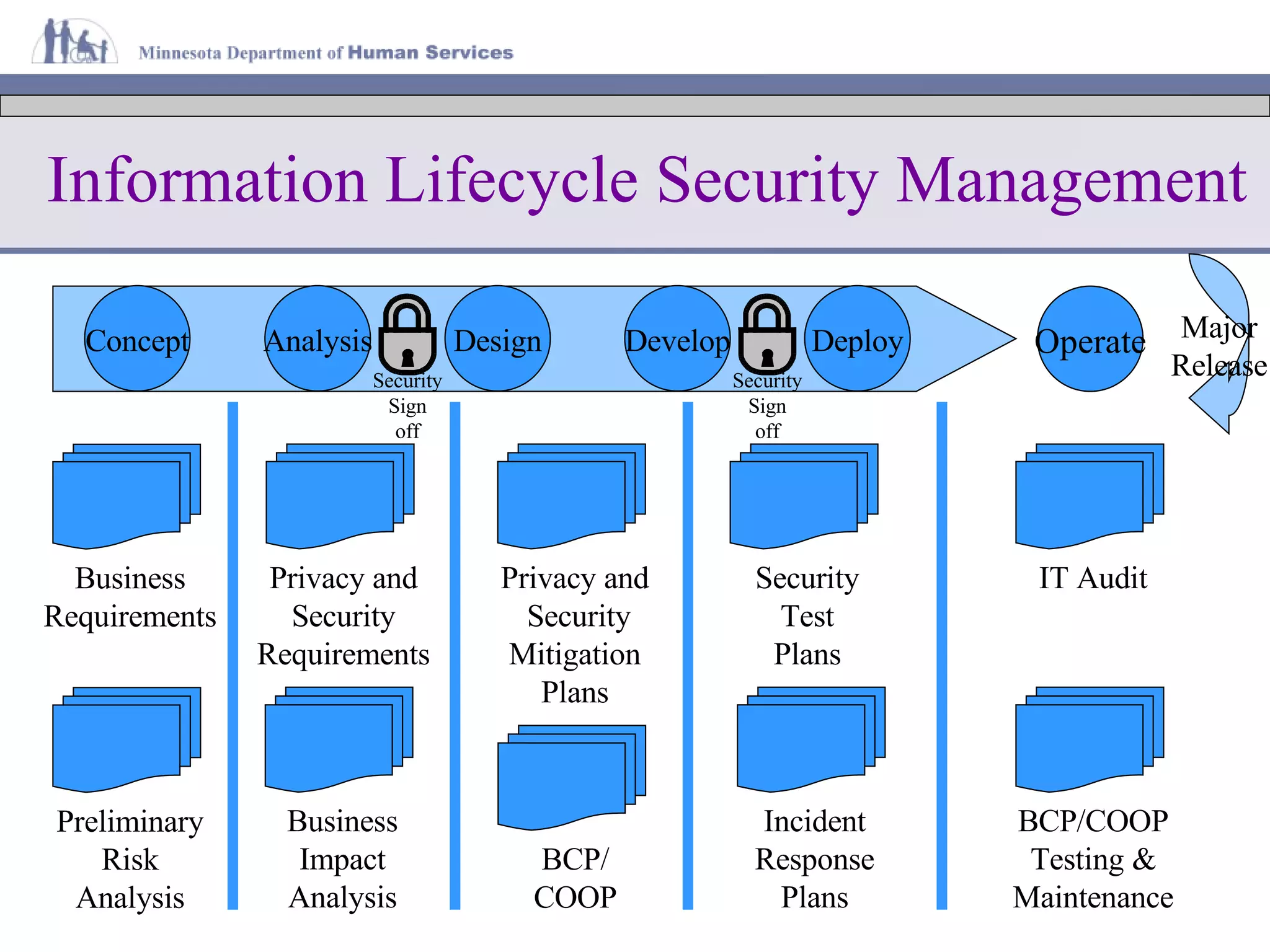
The document discusses information lifecycle security management (ILSM) and outlines the key steps in the process. It begins with an overview of the Minnesota Department of Human Services (DHS) and its mission to help citizens meet basic needs. It then describes the DHS enterprise security strategy and emphasizes building security into systems from the beginning. Finally, it details the ILSM process which incorporates security activities at each stage of the system development lifecycle from concept through disposal.
![ISM in the ILM (Information Lifecycle Security Management) Barry Caplin Chief Information Security Officer Minnesota Department of Human Services [email_address] May 18, 2006 10:00-11:00 a.m. Secure360](https://image.slidesharecdn.com/security-lifecycle-management-852/75/Security-Lifecycle-Management-1-2048.jpg)