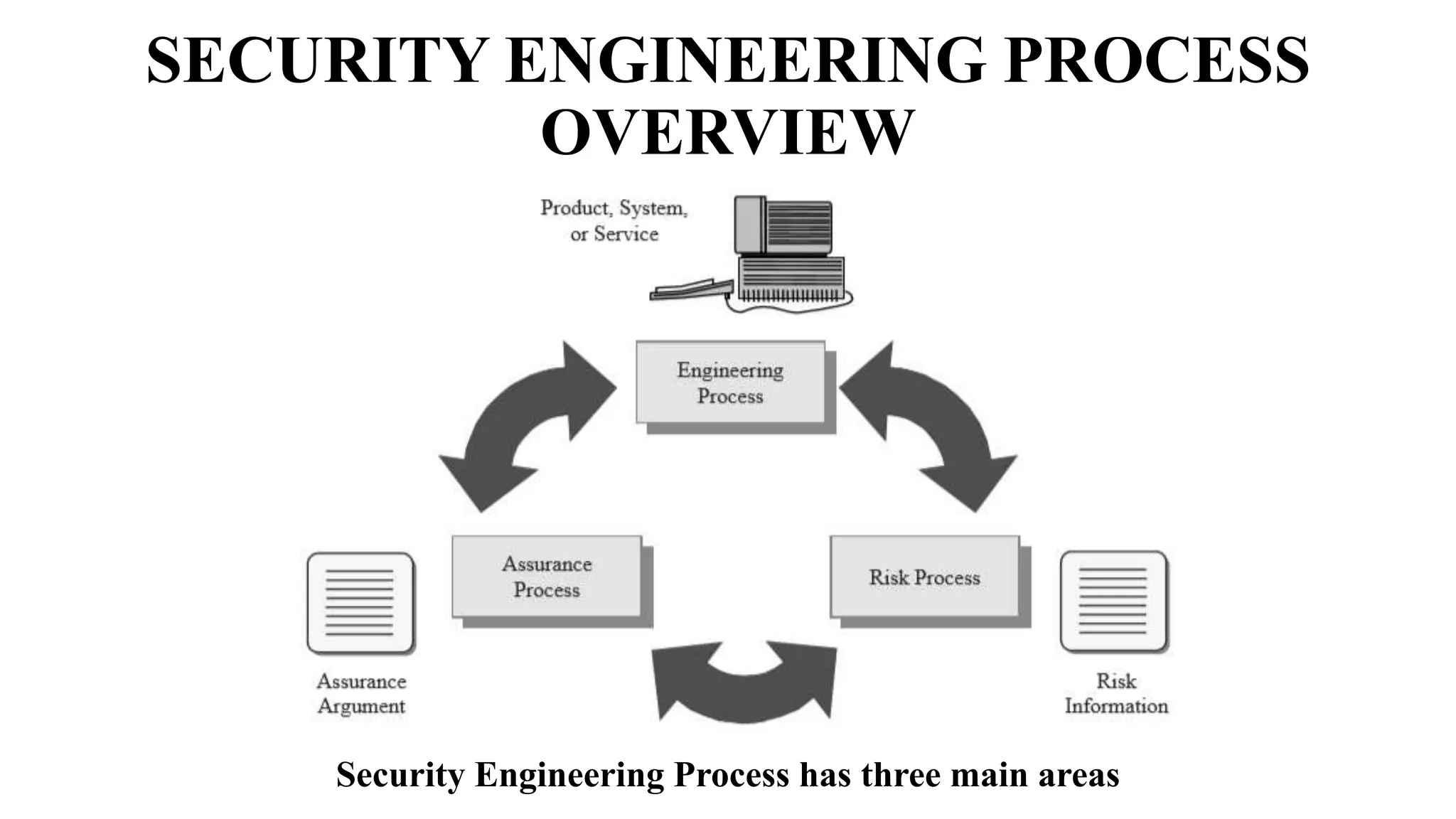
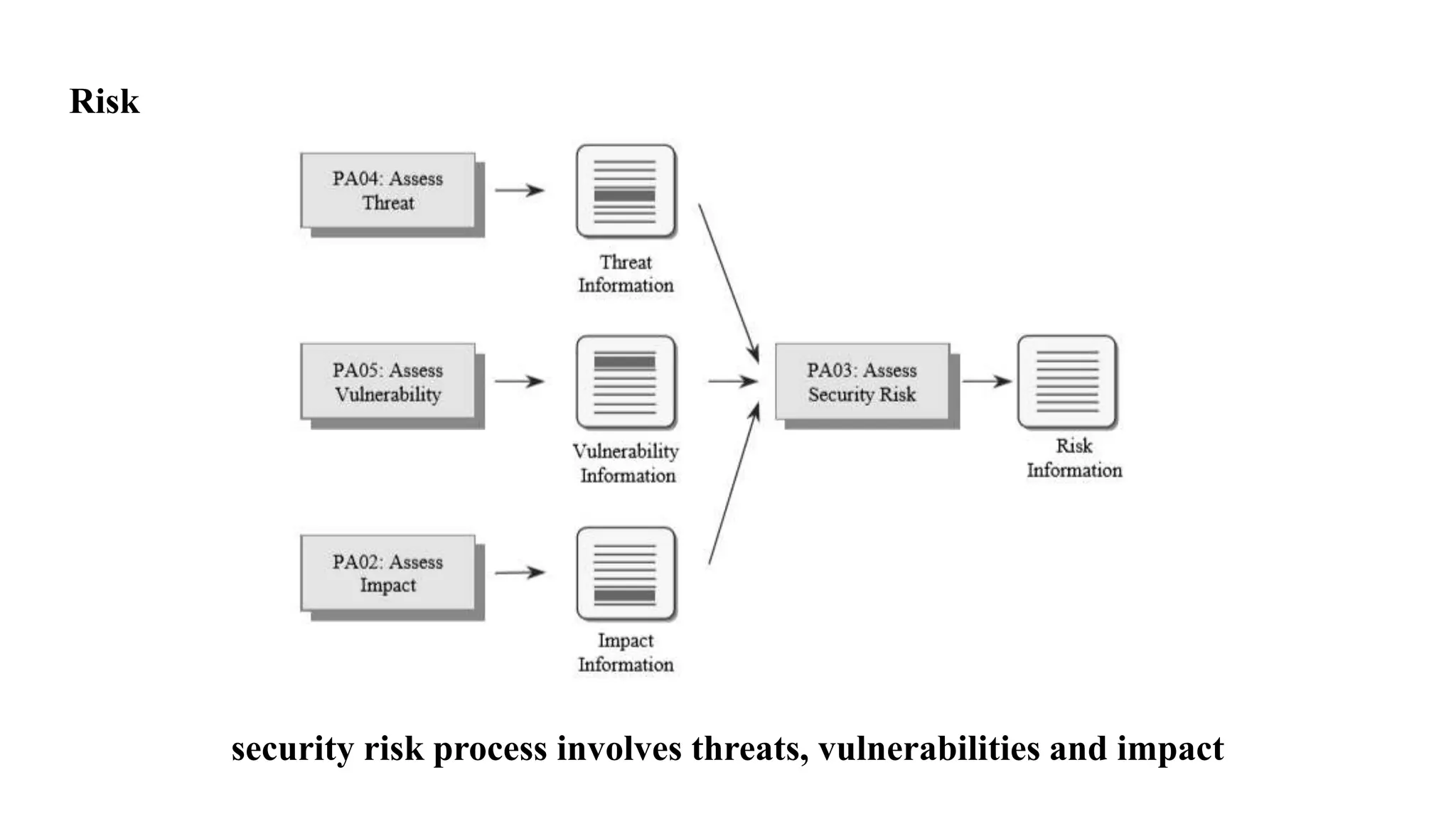
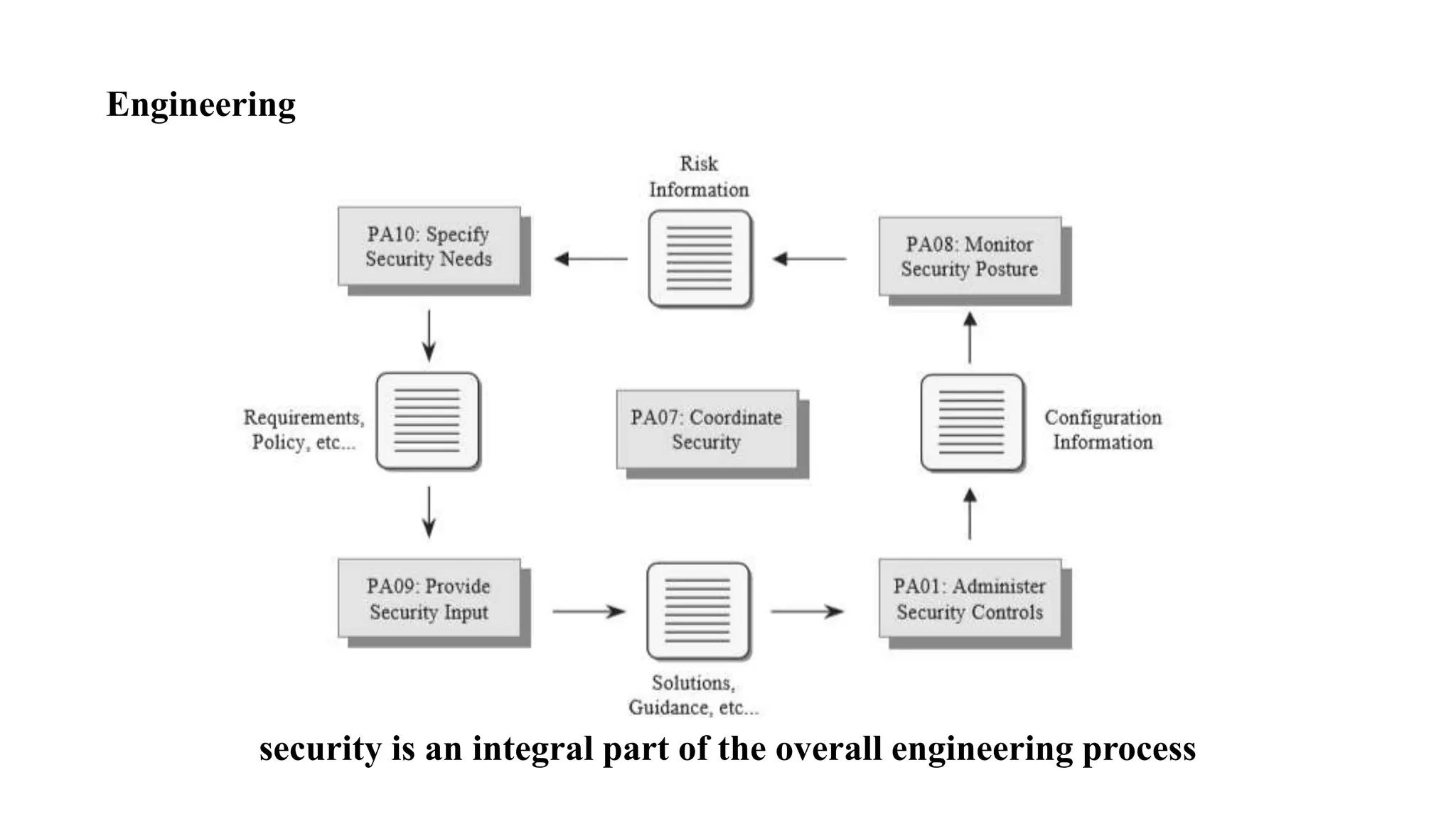
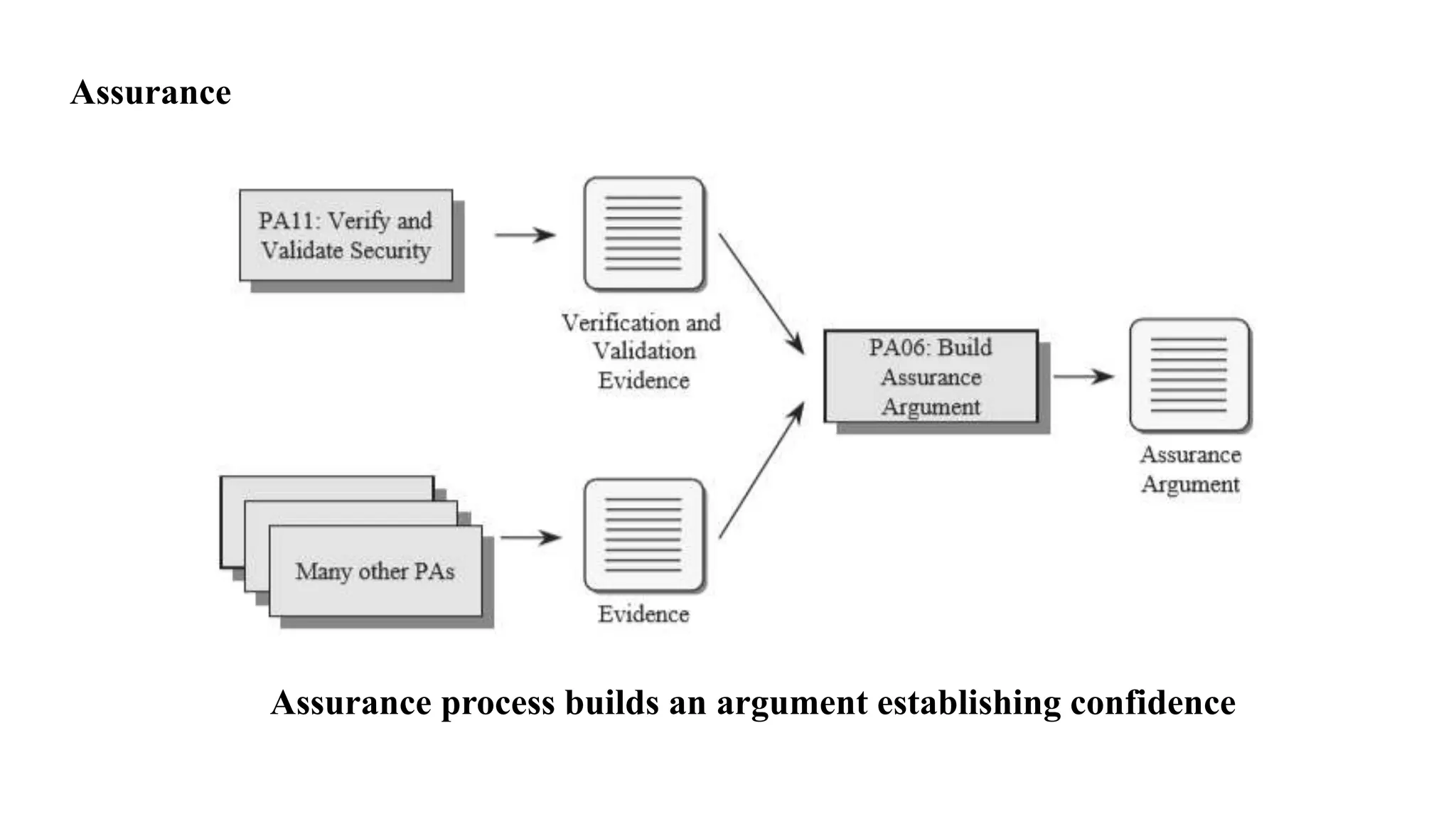
The document discusses several key concepts in information security management including:
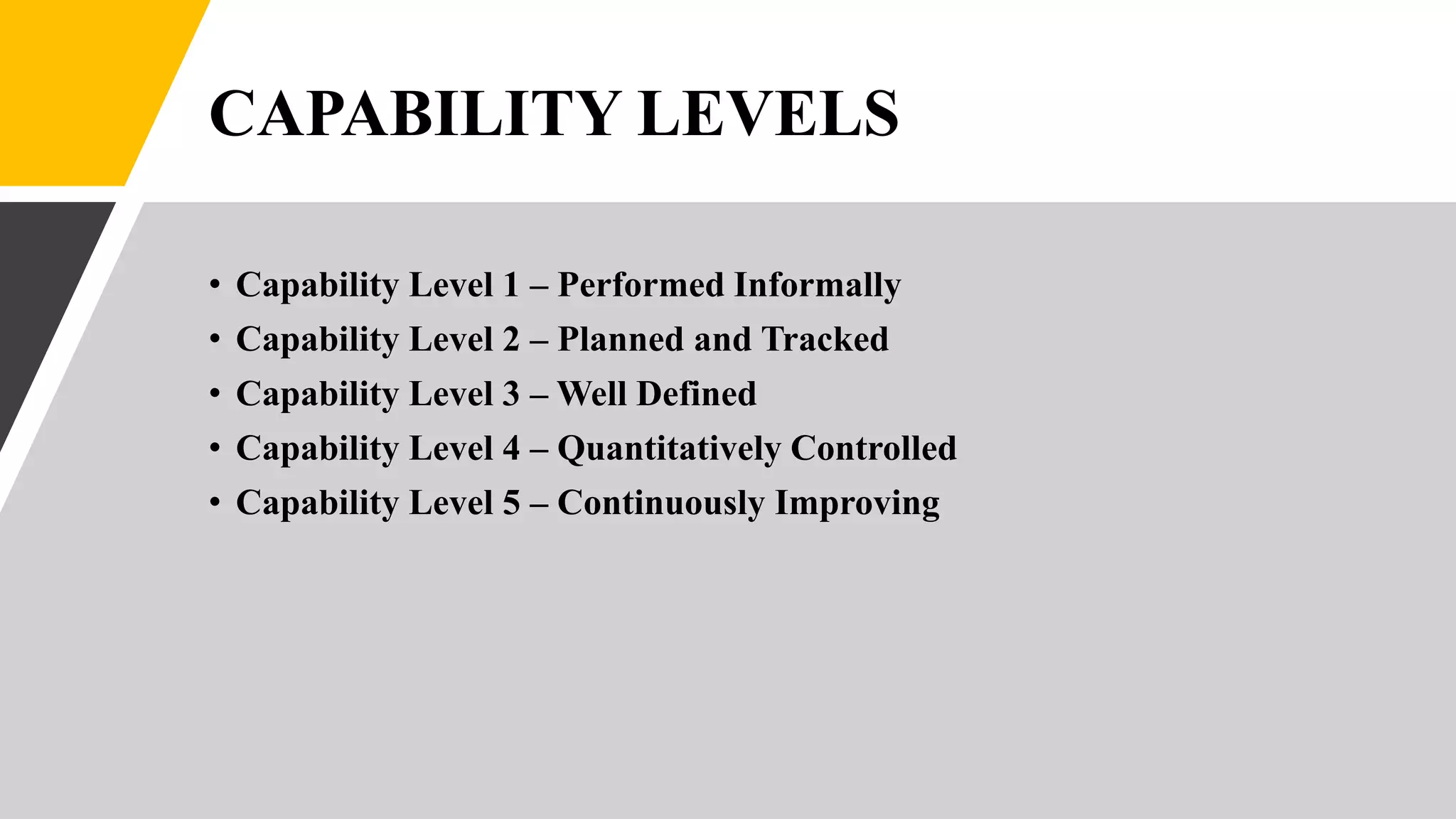
1. The Systems Security Engineering Capability Maturity Model (SSE-CMM) describes essential security engineering practices across the system lifecycle and aims to advance security as a mature discipline. It defines 5 capability levels.
2. Configuration management is important for securely managing changes to an organization's IT infrastructure and systems. It involves identifying configuration items, controlling changes, and reporting status.
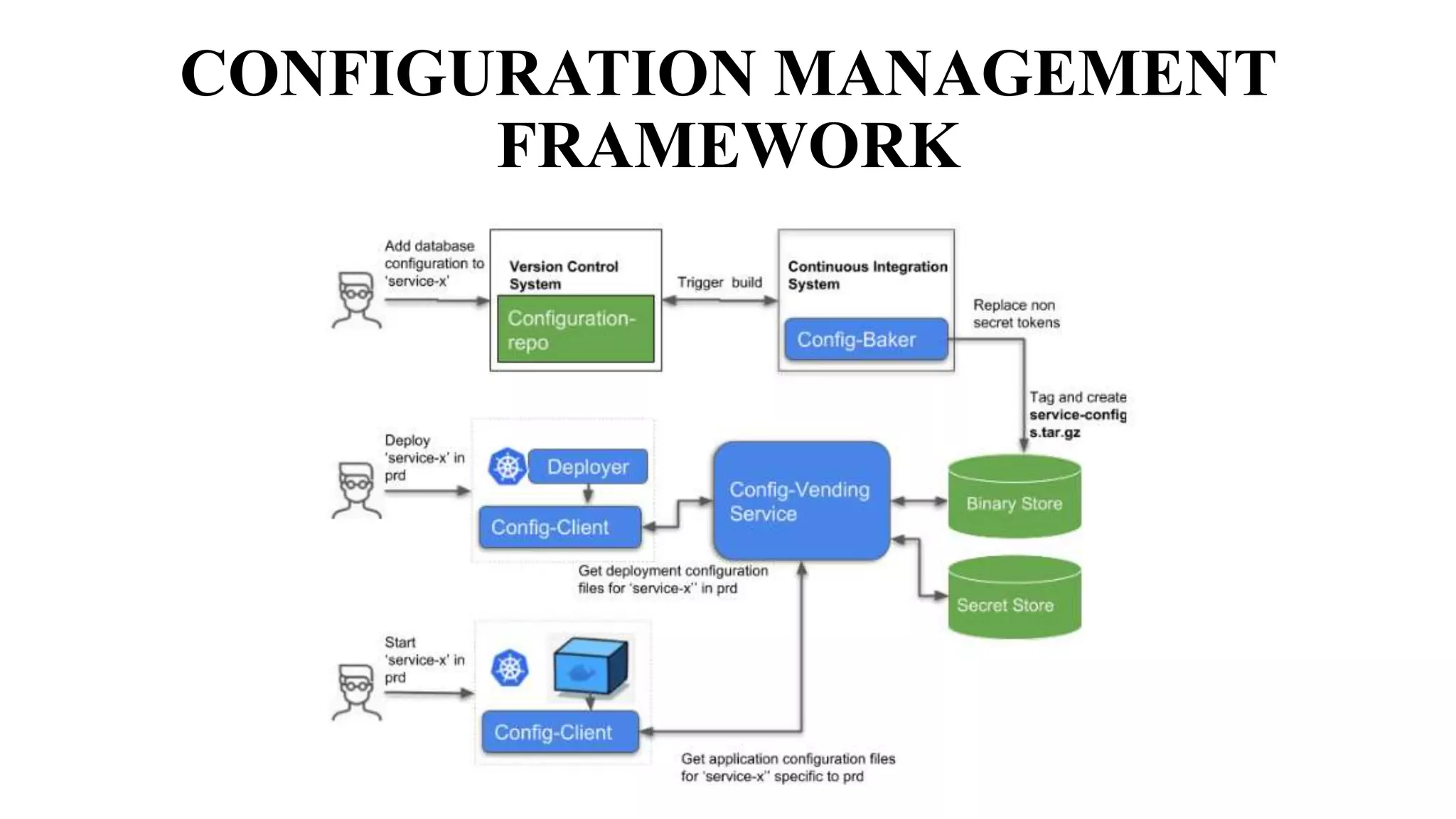
3. The configuration management framework includes configuration items, change control, status reporting, and protection of items from unauthorized changes.