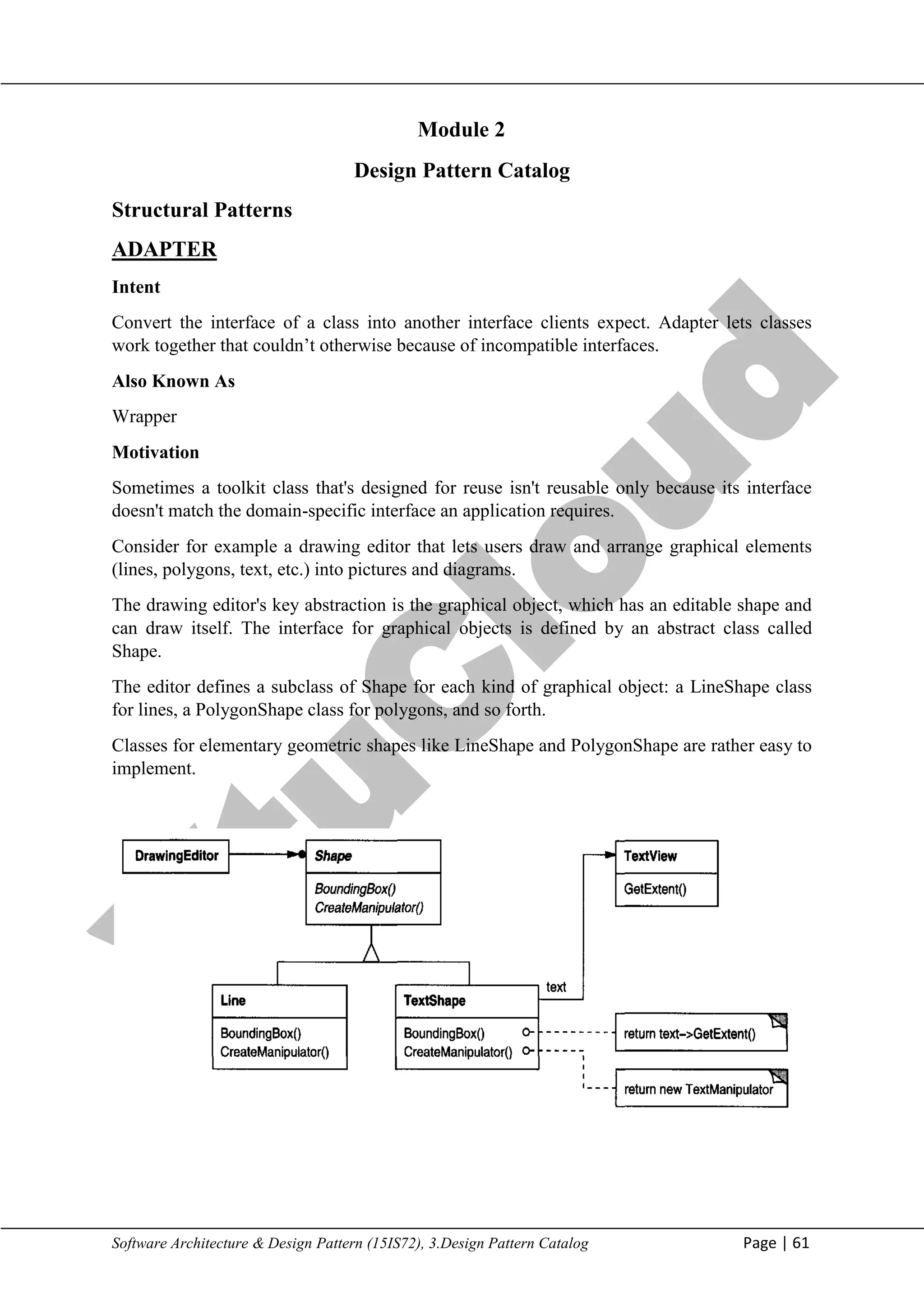
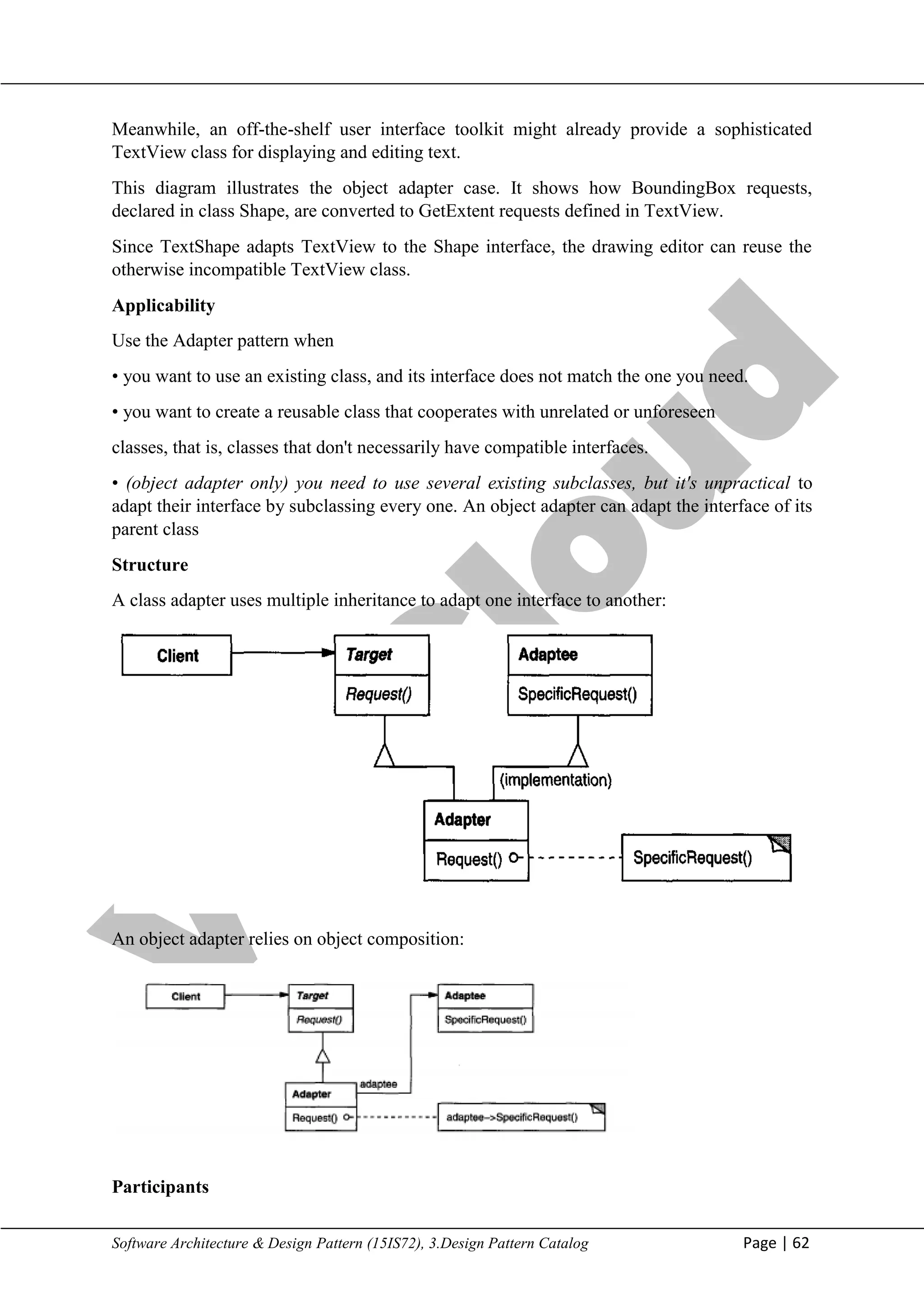
The document discusses the Adapter design pattern, which allows incompatible interfaces to work together by converting one interface into another. It outlines the needs for using the adapter pattern, including reusability and compatibility in various classes, along with the implementation strategies such as class adapters and object adapters. Additionally, the document compares the Adapter pattern with other design patterns like Bridge and Composite, explaining their unique intents and applications.
![V
t
u
C
l
o
u
d
Maharaja Institute of Technology Mysore Department of Information Science & Engineering
Software Architecture & Design Pattern (15IS72), 3.Design Pattern Catalog Page | 63
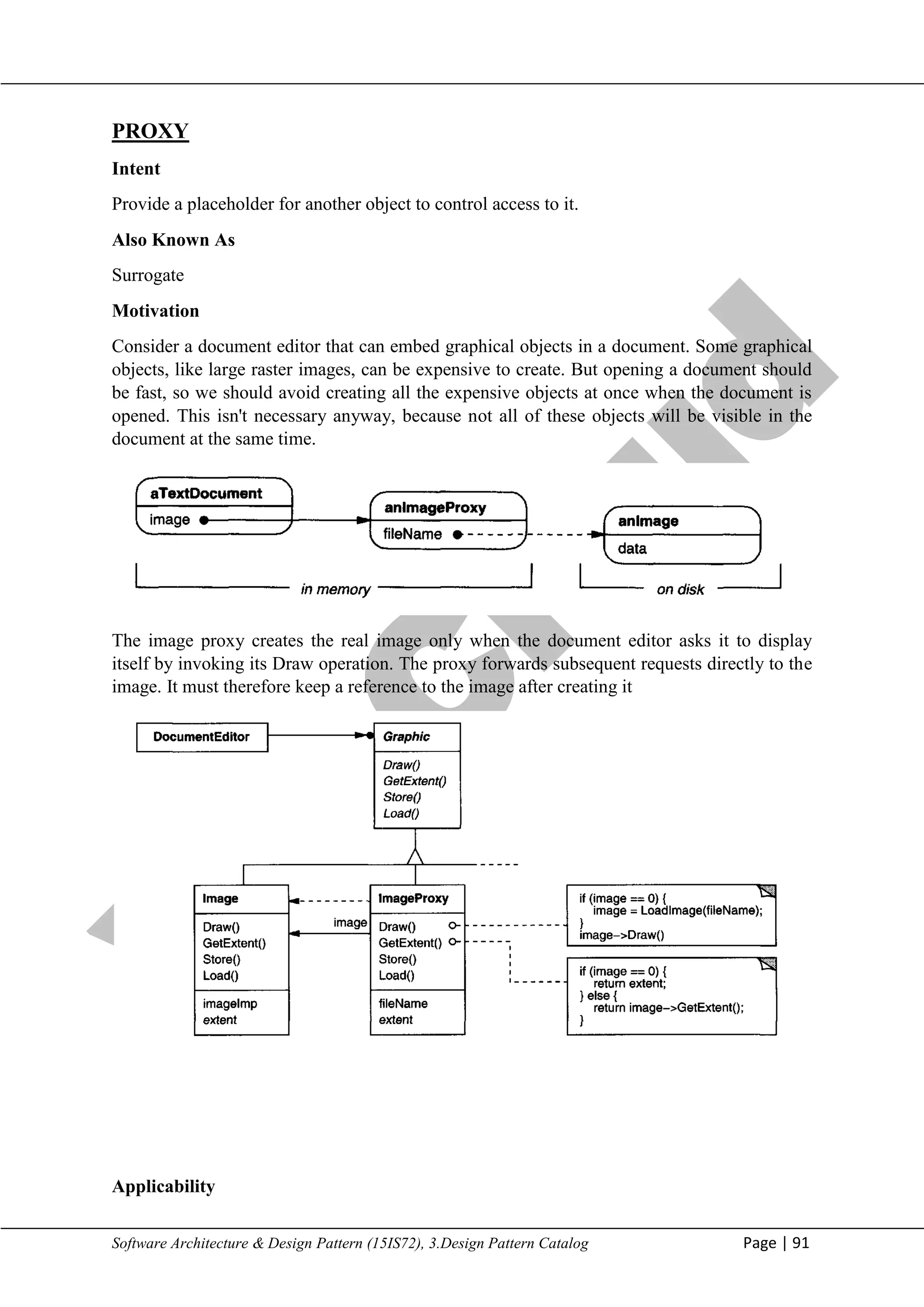
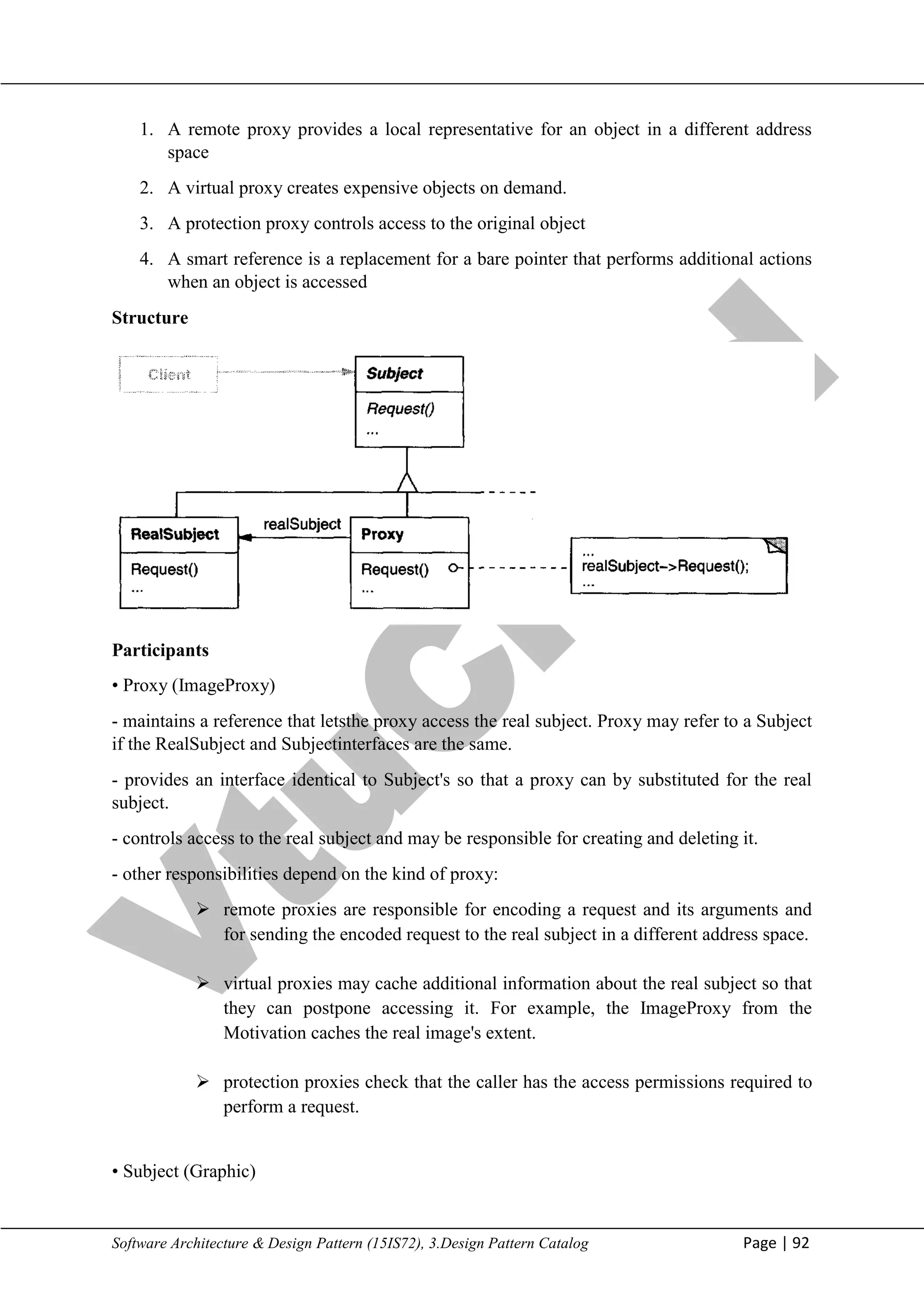
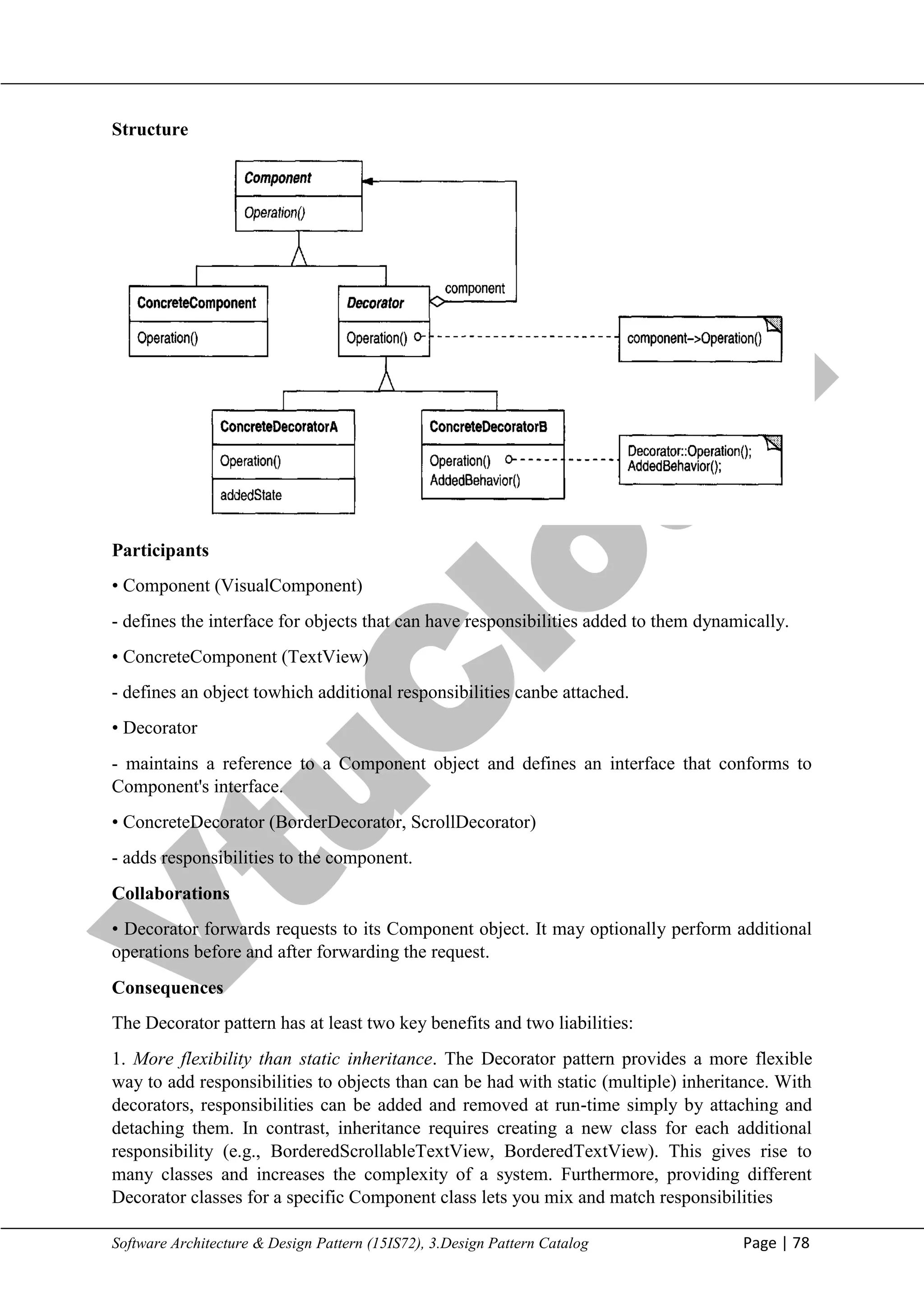
• Target (Shape) - defines the domain-specific interface that Client uses.
• Client (DrawingEditor) – collaborates with objects conforming to the Target interface.
• Adaptec (TextView) - defines an existing interface that needs adapting.
• Adapter (TextShape) - adapts the interface of Adaptec to the Target interface.
Collaborations
• Clients call operations on an Adapter instance. In turn, the adapter calls Adaptec operations
that carry out the request.
Consequences
Class and object adapters have different trade-offs. A class adapter
• adapts Adaptee to Target by committing to a concrete Adaptee class. As a consequence, a
class adapter won't work when we want to adapt a class and all its subclasses.
• lets Adapter override some of Adaptee's behavior, since Adapter is a subclass of Adaptee.
• introduces only one object, and no additional pointer indirection is needed to get to the
adaptee.
An object adapter
• Lets a single Adapter work with many Adaptees—that is, the Adaptee itself and all of its
subclasses (if any). The Adapter can also add functionality to all Adaptees at once.
• Makes it harder to override Adaptee behavior. It will require subclassing Adaptee and
making Adapter refer to the subclass rather than the Adaptee itself.
Here are other issues to consider when using the Adapter pattern:
1. How much adapting does Adapter do? Adapters vary in the amount of work they do to
adapt Adaptee to the Target interface. There is a spectrum of possible work, from simple
interface conversion—for example, changing the names of operations—to supporting an
entirely different set of operations. The amount of work Adapter does depends on how
similar the Target interface is to Adaptee's.
2. Pluggable adapters. A class is more reusable when you minimize the assumptions other
classes must make to use it. By building interface adaptation into a class, you eliminate the
assumption that other classes see the same interface. Put another way, interface adaptation
lets us incorporate our class into existing systems that might expect different interfaces to the
class. Object WorksSmalltalk [Par90] uses the term pluggable adapter to describe classes
with built-in interface adaptation.
3. Using two-way adapters to provide transparency. A potential problem with adapters is that
they aren't transparent to all clients. An adapted object no longer conforms to the Adaptec
interface, so it can't be used as is wherever an Adaptec object can. Two-way adapters can
provide such transparency. Specifically, they're useful when two different clients need to
view an object differently.](https://image.slidesharecdn.com/sadp21cs741-m2-250110081949-4a09db0b/75/Software-and-architecture-design-pattern-3-2048.jpg)
![V
t
u
C
l
o
u
d
Maharaja Institute of Technology Mysore Department of Information Science & Engineering
Software Architecture & Design Pattern (15IS72), 3.Design Pattern Catalog Page | 64
Consider the two-way adapter that integrates Unidraw, a graphical editor framework [VL90],
and QOCA, a constraint-solving toolkit [HHMV92]. Both systems have classes that represent
variables explicitly: Unidraw has StateVariable, and QOCA has ConstraintVariable. To make
Unidraw work with QOCA, ConstraintVariable must be adapted to StateVariable; to let
QOCA propagate solutions to Unidraw, StateVariable must be adapted to ConstraintVariable
The solution involves a two-way class adapter ConstraintStateVariable, a subclass of both
StateVariable and ConstraintVariable that adapts the two interfaces to each other. Multiple
inheritance is a viable solution in this case because the interfaces of the adapted classes are
substantially different. The two-way class adapter conforms to both of the adapted classes
and can work in either system.
Implementation
Although the implementation of Adapter is usually straightforward, here are some issues to
keep in mind:
1. Implementing class adapters in C++.In a C++ implementation of a class adapter, Adapter
would inherit publicly from Target and privately from Adaptec. Thus Adapter would be a
subtype of Target but not of Adaptec.
2. Pluggable adapters. Let's look at three ways to implement pluggable adapters for the
TreeDisplay widget described earlier, which can lay out and display a hierarchical structure
automatically. The first step, which is common to all three of the implementations discussed
here, is to find a "narrow" interface for Adaptec, that is, the smallest subset of operations that
lets us do the adaptation. A narrow interface consisting of only a couple of operations is
easier to adapt than an interface with dozens of operations. For TreeDisplay, the adaptee is
any hierarchical structure. A minimalist interface might include two operations, one that
defines how to present a node in the hierarchical structure graphically, and another that
retrieves the node's children.
The narrow interface leads to three implementation approaches:
(a) Using abstract operations. Define corresponding abstract operations for the narrow
Adaptee interface in the TreeDisplay class. Subclasses must implement the abstract
operations and adapt the hierarchically structured object. For example, a
DirectoryTreeDisplay subclass will implement these operations by accessing the directory
structure.](https://image.slidesharecdn.com/sadp21cs741-m2-250110081949-4a09db0b/75/Software-and-architecture-design-pattern-4-2048.jpg)
![V
t
u
C
l
o
u
d
Maharaja Institute of Technology Mysore Department of Information Science & Engineering
Software Architecture & Design Pattern (15IS72), 3.Design Pattern Catalog Page | 65
(b) Using delegate objects. In this approach, TreeDisplay forwards requests for accessing the
hierarchical structure to a delegate object. TreeDisplay can use a different adaptation strategy
by substituting a different delegate.
For example, suppose there exists a DirectoryBrowser that uses a TreeDisplay.
DirectoryBrowser might make a good delegate for adapting TreeDisplay to the hierarchical
directory structure. In dynamically typed languages like Smalltalk or Objective C, this
approach only requires an interface for registering the delegate with the adapter. Then
TreeDisplay simply forwards the requests to the delegate. NEXTSTEP [Add94] uses this
approach heavily to reduce subclassing.
(c) Parameterized adapters. The usual way to support pluggable adapters in Smalltalk is to
parameterize an adapter with one or more blocks. The block construct supports adaptation
without subclassing. A block can adapt a request, and the adapter can store a block for each
individual request. In our example, this means TreeDisplay stores one block for converting a
node into a GraphicNode and another block for accessing a node's children.
Known Uses](https://image.slidesharecdn.com/sadp21cs741-m2-250110081949-4a09db0b/75/Software-and-architecture-design-pattern-5-2048.jpg)

![V
t
u
C
l
o
u
d
Maharaja Institute of Technology Mysore Department of Information Science & Engineering
Software Architecture & Design Pattern (15IS72), 3.Design Pattern Catalog Page | 68
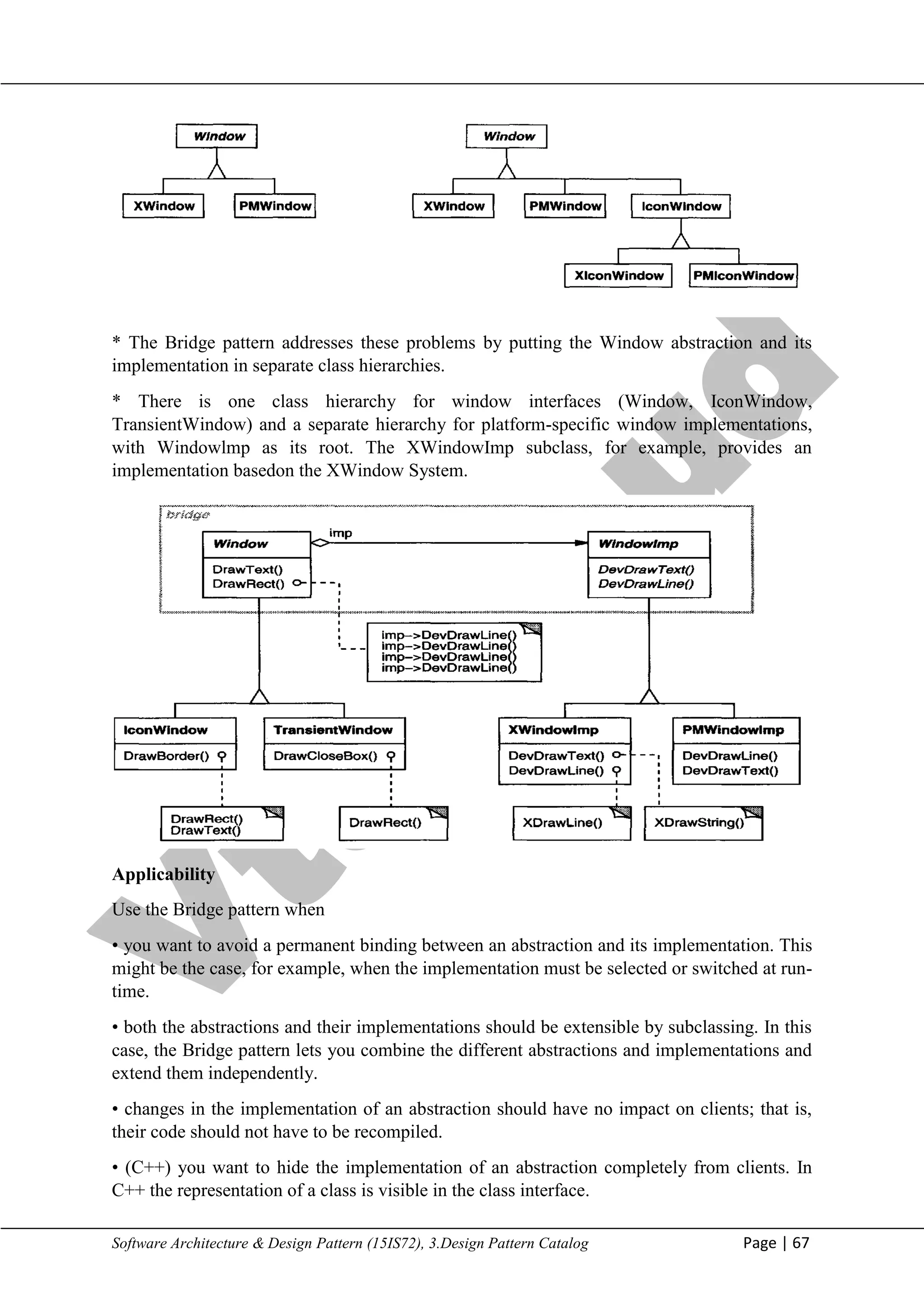
• you have a proliferation of classes as shown earlier in the first Motivation diagram. Such a
class hierarchy indicates the need for splitting an object into two parts. Rumbaugh uses the
term "nested generalizations" [RBP+91] to refer to such class hierarchies.
• you want to share an implementation among multiple objects(perhaps using reference
counting), and this fact should be hidden from the client. A simple example is Coplien's
String class, in which multiple objects can share the same string representation (StringRep).
Structure
Participants
• Abstraction (Window) - defines the abstraction's interface. - maintains a reference to an
object of type Implementor.
• RefmedAbstraction (IconWindow) – Extends the interface defined by Abstraction.
• Implementor (Windowlmp) - defines the interface for implementation classes. This
interface doesn't have to correspond exactly to Abstraction's interface; in fact the two
interfaces can be quite different. Typically the Implementor interface provides only primitive
operations, and Abstraction defines higher-level operations based on these primitives.
• Concretelmplementor (XWindowImp, PMWindowImp) - implements the Implementor
interface and defines its concrete implementation.
Collaborations
• Abstraction forwards client requests to its Implementor object.
Consequences
The Bridge pattern has the following consequences:
1. Decoupling interface and implementation. An implementation is not bound permanently to
an interface. The implementation of an abstraction can be configured at run-time. It's even
possible for an object to change its implementation at run-time. Decoupling Abstraction and
Implementor also eliminates compile-time dependencies on the implementation. Changing an
implementation class doesn't require recompiling the Abstraction class and its clients. This
property is essential when you must ensure binary compatibility between different versions of
a class library. Furthermore, this decoupling encourages layering that can lead to a better](https://image.slidesharecdn.com/sadp21cs741-m2-250110081949-4a09db0b/75/Software-and-architecture-design-pattern-8-2048.jpg)
![V
t
u
C
l
o
u
d
Maharaja Institute of Technology Mysore Department of Information Science & Engineering
Software Architecture & Design Pattern (15IS72), 3.Design Pattern Catalog Page | 69
structured system. The high-level part of a system only has to know about Abstraction and
Implementor.
2. Improved extensibility. You can extend the Abstraction and Implementor hierarchies
independently.
3. Hiding implementation details from clients. You can shield clients from implementation
details, like the sharing of implementor objects and the accompanying reference count
mechanism (if any).
Implementation
Consider the following implementation issues when applying the Bridge pattern:
1. Only one Implementor. In situations where there's only one implementation, creating an
abstract Implementor class isn't necessary. This is a degenerate case of the Bridge pattern;
there's a one-to-one relationship between Abstraction and Implementor. Nevertheless, this
separation is still useful when a change in the implementation of a class must not affect its
existing clients— that is, they shouldn't have to be recompiled just relinked.
2. Creating the right Implementor object.
How, when, and where do you decide which Implementor class to instantiate when there's
more than one?
If Abstraction knows about all Concretelmplementor classes, then it can instantiate one of
them in its constructor; it can decide between them based on parameters passed to its
constructor. If, for example, a collection class supports multiple implementations, the
decision can be based on the size of the collection. A linked list implementation can be used
for small collections and a hash table for larger ones.
Another approach is to choose a default implementation initially and change it later according
to usage. For example, if the collection grows bigger than a certain threshold, then it switches
its implementation to one that's more appropriate for a large number of items
3. Sharing implementors.
Coplien illustrates how the Handle/Body idiom in C++ can be used to share implementations
among several objects [Cop92]. The Body stores a reference count that the Handle class
increments and decrements. The code for assigning handles with shared bodies has the
following general form:
4. Using multiple inheritance.
You can use multiple inheritance in C++ to combine an interface with its implementation .For
example, a class can inherit publicly from Abstraction and privately from a Concretelmplementor. But
because this approach relies on static inheritance, it binds an implementation permanently to its](https://image.slidesharecdn.com/sadp21cs741-m2-250110081949-4a09db0b/75/Software-and-architecture-design-pattern-9-2048.jpg)
![V
t
u
C
l
o
u
d
Maharaja Institute of Technology Mysore Department of Information Science & Engineering
Software Architecture & Design Pattern (15IS72), 3.Design Pattern Catalog Page | 70
interface. Therefore you can't implement a true Bridge with multiple inheritances—at least not in
C++.
Known Uses
The Window example above comes from ET++ [WGM88]. In ET++, Windowlmp is called
"WindowPort" and has subclasses such as XWindowPortand SunWindowPort. The Window
object creates its corresponding Implementor object by requesting it from an abstract factory
called "WindowSystem." WindowSystem provides an interface for creating platform-specific
objects such as fonts, cursors, bitmaps, and so forth.
The ET++ Window/WindowPort design extends the Bridge pattern in that the WindowPort
also keeps a reference back to the Window. The WindowPort implementor class uses this
reference to notify Window about WindowPort-specific events: the arrival of input events,
window resizes, etc.
Related Patterns
An Abstract Factory can create and configure a particular Bridge.
The Adapter pattern is geared toward making unrelated classes work together. It is usually
applied to systems after they're designed. Bridge, on the other hand, is used up-front in a
design to let abstractions and implementations vary independently.
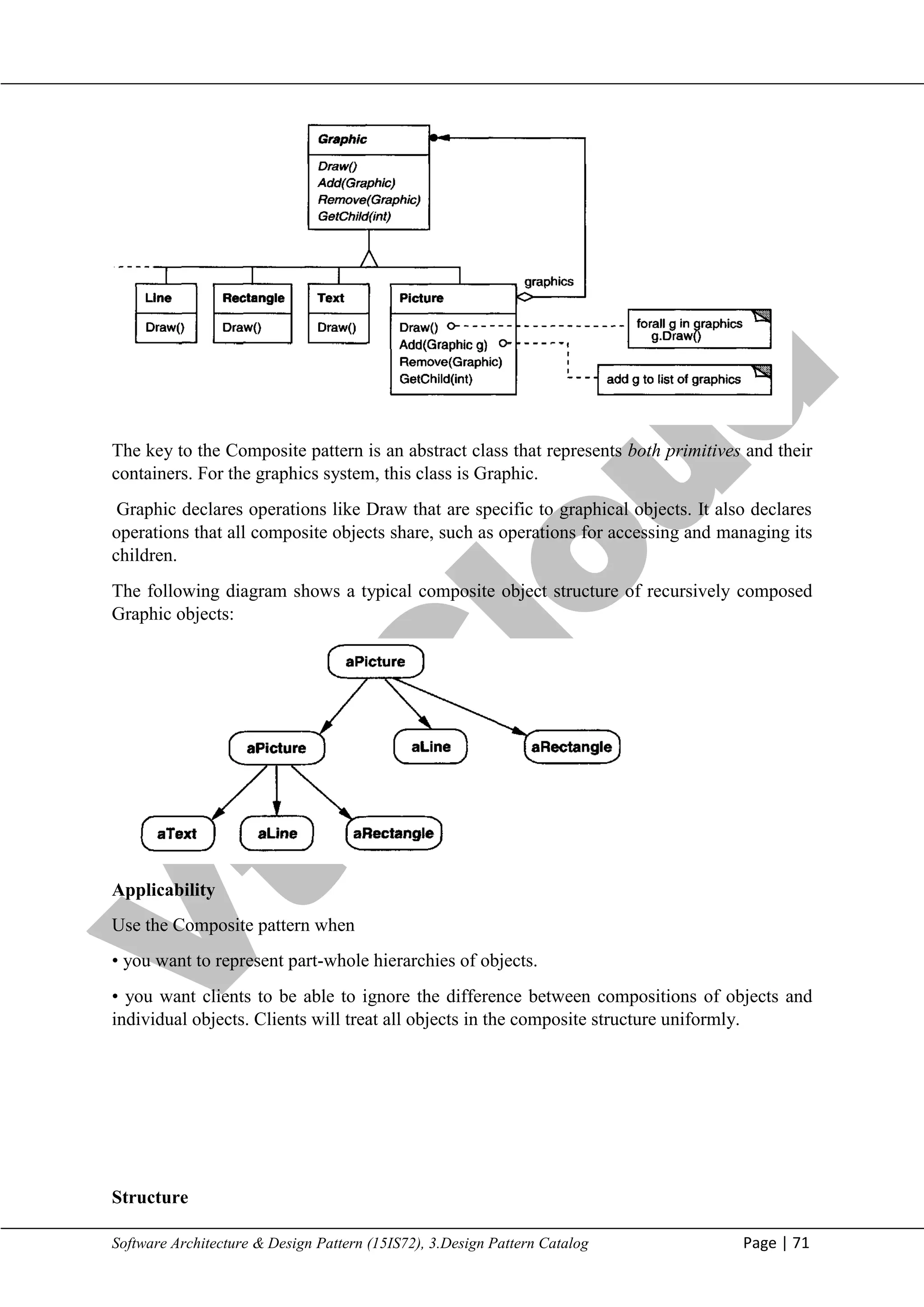
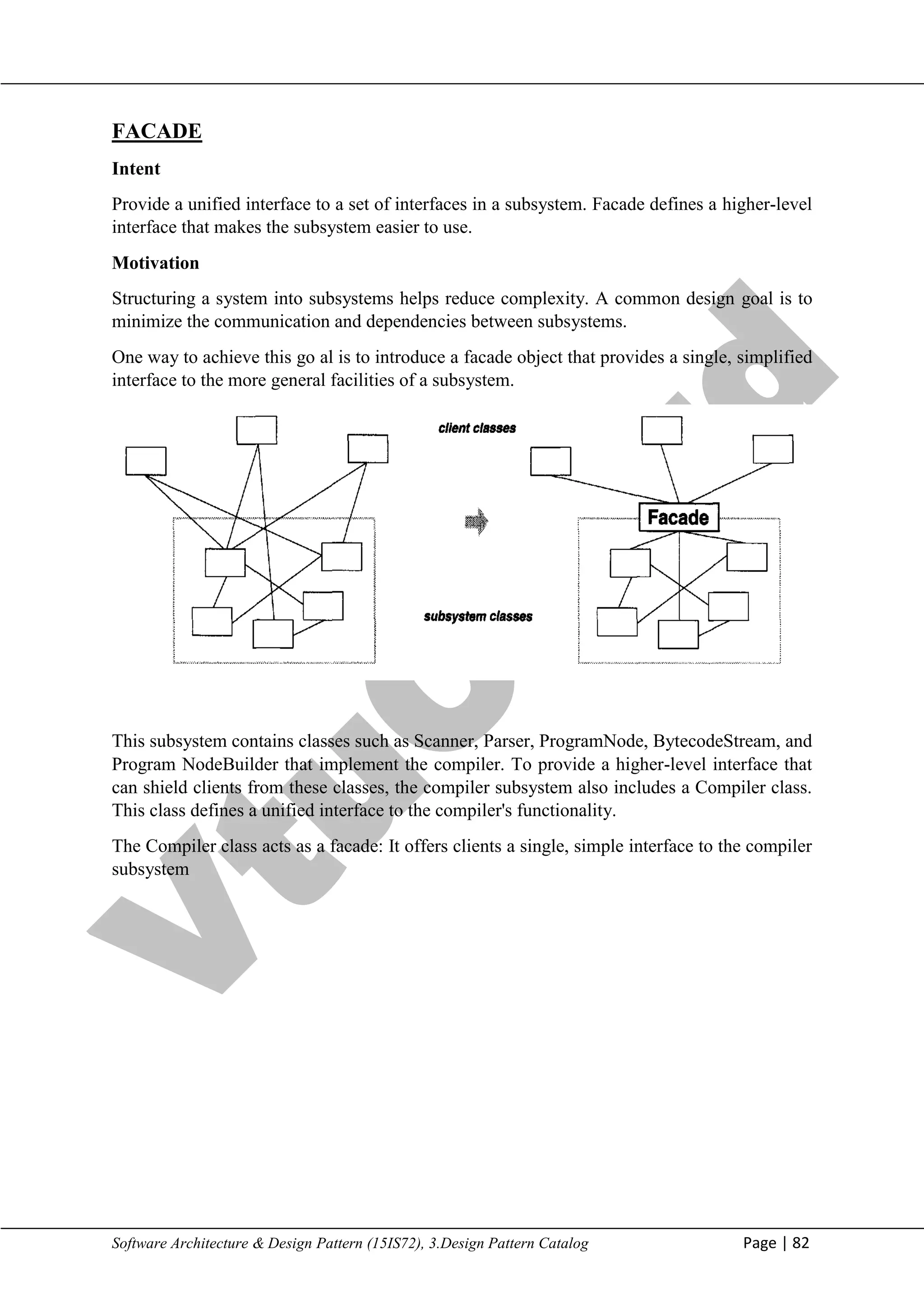
COMPOSITE
Intent
Compose objects into tree structures to represent part-whole hierarchies. Composite lets
clients treat individual objects and compositions of objects uniformly.
Motivation
Graphics applications like drawing editors and schematic capture systems let users build
complex diagrams out of simple components. The user can group components to form larger
components, which in turn can be grouped to form still larger components.
A simple implementation could define classes for graphical primitives such as Text and Lines
plus other classes that act as containers for these primitives.](https://image.slidesharecdn.com/sadp21cs741-m2-250110081949-4a09db0b/75/Software-and-architecture-design-pattern-10-2048.jpg)


![V
t
u
C
l
o
u
d
Maharaja Institute of Technology Mysore Department of Information Science & Engineering
Software Architecture & Design Pattern (15IS72), 3.Design Pattern Catalog Page | 75
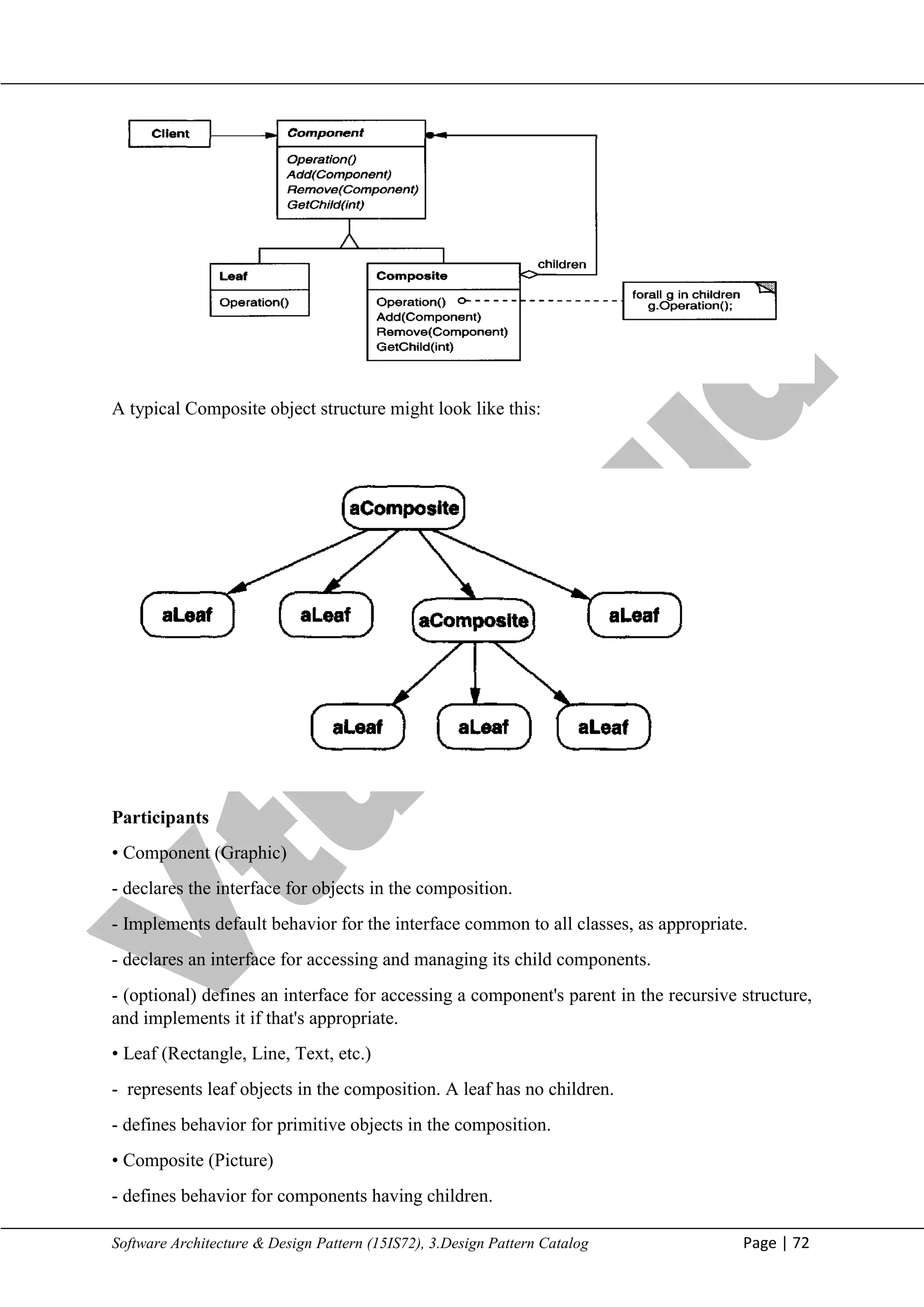
5. Should Component implement a list of Components? You might be tempted to define the
set of children as an instance variable in the Component class where the child access and
management operations are declared. But putting the child pointer in the base class incurs a
space penalty for every leaf, even though a leaf never has children. This is worthwhile only if
there are relatively few children in the structure.
6. Child ordering. Many designs specify an ordering on the children of Composite. In the
earlier Graphics example, ordering may reflect front-to-back ordering. If Composites
represent parse trees, then compound statements can be instances of a Composite whose
children must be ordered to reflect the program. When child ordering is an issue, you must
design child access and management interfaces carefully to manage the sequence of children.
The Iterator pattern can guide you in this.
7. Caching to improve performance. If you need to traverse or search compositions
frequently, the Composite class can cache traversal or search information about its children.
The Composite can cache actual results or just information that lets it short-circuit the
traversal or search. For example, the Picture class from the Motivation example could cache
the bounding box of its children. During drawing or selection, this cached bounding box lets
the Picture avoid drawing or searching when its children aren't visible in the current window.
Changes to a component will require invalidating the caches of its parents. This works best
when components know their parents. So if you're using caching, you need to define an
interface for telling composites that their caches are invalid.
8. Who should delete components? In languages without garbage collection, it's usually best
to make a Composite responsible for deleting its children when it's destroyed. An exception
to this rule is when Leaf objects are immutable and thus can be shared.
9. What's the best data structure for storing components? Composites may use a variety of
data structures to store their children, including linked lists, trees, arrays, and hash tables. The
choice of data structure depends (as always) on efficiency.
Known Uses
The RTL Smalltalk compiler framework [JML92] uses the Composite pattern extensively.](https://image.slidesharecdn.com/sadp21cs741-m2-250110081949-4a09db0b/75/Software-and-architecture-design-pattern-15-2048.jpg)


![V
t
u
C
l
o
u
d
Maharaja Institute of Technology Mysore Department of Information Science & Engineering
Software Architecture & Design Pattern (15IS72), 3.Design Pattern Catalog Page | 80
component. If a view has any adorners attached, then it gives them a chance to draw
additional embellishments. MacApp and Bedrock must use this approach because the
Viewclass is heavyweight. It would be too expensive to use a full-fledged View just to add a
border.
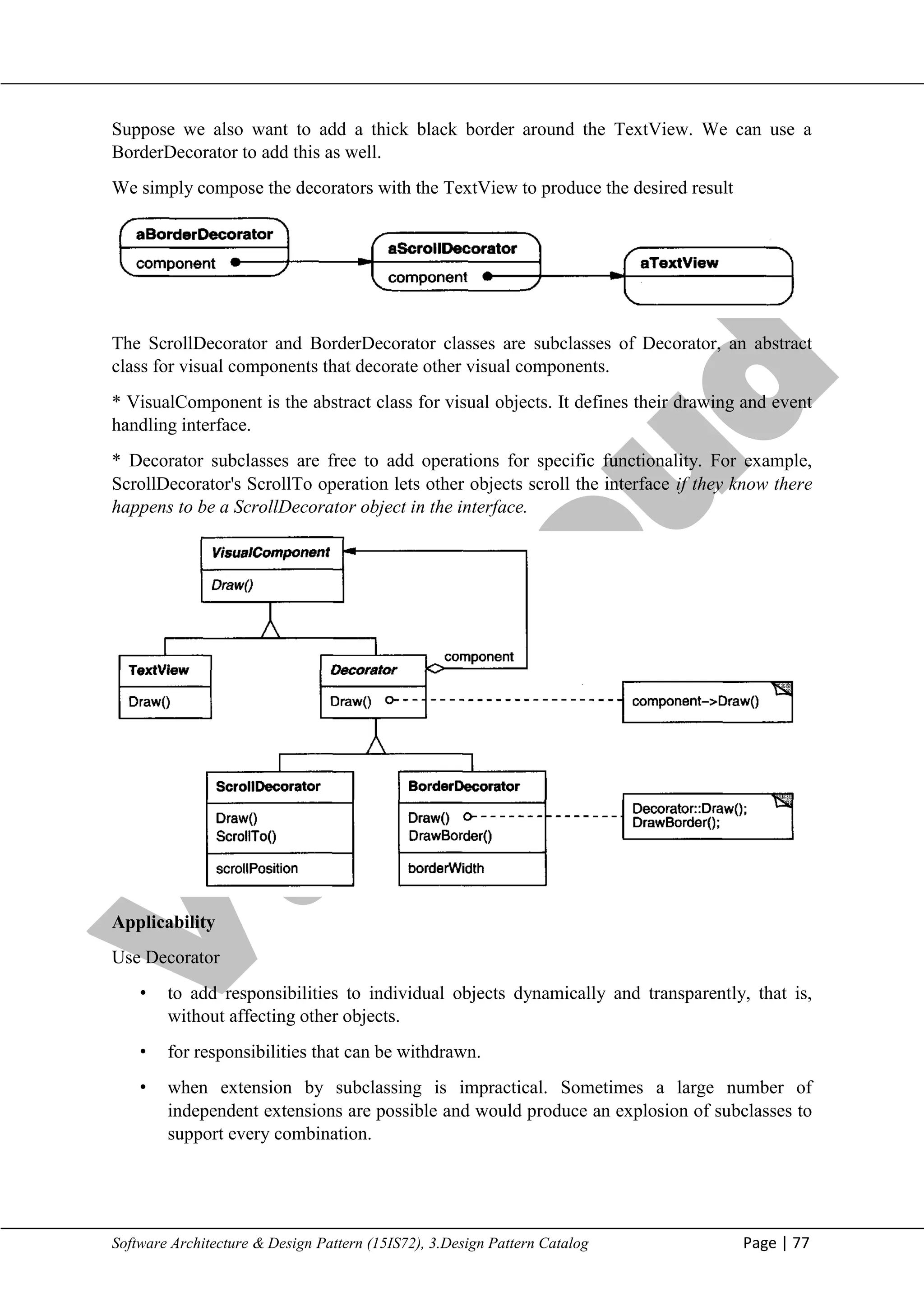
Since the Decorator pattern only changes a component from the outside, the component
doesn't have to know anything about its decorators; that is, the decorators are transparent to
the component:
With strategies, the component itself knows about possible extensions. So it has to reference
and maintain the corresponding strategies:
Known Uses
Many object-oriented user interface toolkits use decorators to add graphical embellishments
to widgets. Examples include Interviews [LVC89, LCI+92], ET++ [WGM88], and the Object
WorksSmalltalkclass library [Par90]. More exotic applications of Decorator are the
DebuggingGlyph from Interviews and the PassivityWrapper from ParcPlace Smalltalk.
Streams are a fundamentalabstractionin most I/O facilities. Astream can provide an interface
for converting objects into a sequence of bytes or characters. That lets us transcribe an object
to a file or to a string in memory for retrieval later. A straightforward way to do this is to
define an abstractStream class with subclasses MemoryStream and FileStream. But suppose
we also want to be able to do the following:
• Compress the stream data using different compression algorithms (runlength encoding,
Lempel-Ziv, etc.).
• Reduce the stream data to 7-bit ASCII characters so that it can be transmitted over an ASCII
communication channel.
The Decorator pattern gives us an elegant way to add these responsibilities to streams. The
diagram below shows one solution to the problem:](https://image.slidesharecdn.com/sadp21cs741-m2-250110081949-4a09db0b/75/Software-and-architecture-design-pattern-20-2048.jpg)


![V
t
u
C
l
o
u
d
Maharaja Institute of Technology Mysore Department of Information Science & Engineering
Software Architecture & Design Pattern (15IS72), 3.Design Pattern Catalog Page | 85
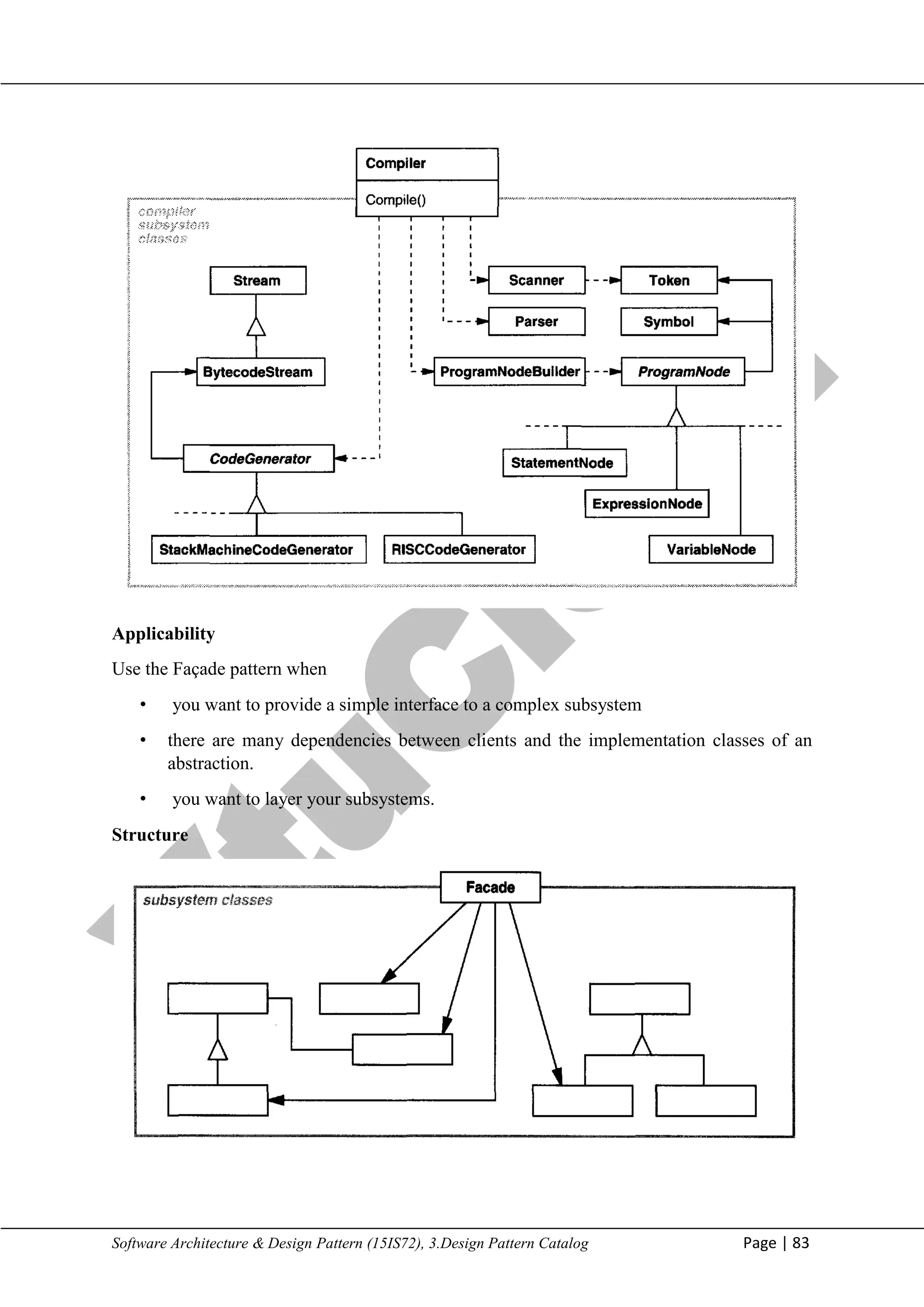
2. Public versus private subsystem classes. A subsystem is analogous to a class in that both
have interfaces, and both encapsulate something—a class encapsulates state and operations,
while a subsystem encapsulates classes. And just as it's useful to think of the public and
private interface of a class, we can think of the public and private interface of a subsystem.
The public interface to a subsystem consists of classes that all clients can access; the
private interface is just for subsystem extenders. For example, the classes Parser and Scanner
in the compiler subsystem are part of the public interface
Known Uses
The compiler example in the Sample Code section was inspired by the Object
WorksSmalltalk compiler system
In the ET++ application framework [WGM88], an application can have built-in browsing
tools for inspecting its objects at run-time. These browsing tools are implemented in a
separate subsystem that includes a Facade class called "ProgrammingEnvironment." This
facade defines operations such as InspectObject and InspectClass for accessing the browsers.
The Choices operating system [CIRM93] uses facades to compose many frameworks into
one. The key abstractions in Choices are processes, storage, and address spaces. For each of
these abstractions there is a corresponding subsystem, implemented as a framework, that
supports porting Choices to a variety of different hardware platforms. Two of these
subsystems have a "representative" (i.e., facade). These representatives are
FileSystemlnterface (storage) and Domain (address spaces).
For example, the virtual memory framework has Domain as its facade. A Domain represents
an address space. It provides a mapping between virtual addresses and offsets into memory
objects, files, or backing store. The main operations on Domain support adding a memory
object at a particular address, removing a memory object, and handling a page fault.](https://image.slidesharecdn.com/sadp21cs741-m2-250110081949-4a09db0b/75/Software-and-architecture-design-pattern-25-2048.jpg)



![V
t
u
C
l
o
u
d
Maharaja Institute of Technology Mysore Department of Information Science & Engineering
Software Architecture & Design Pattern (15IS72), 3.Design Pattern Catalog Page | 90
Implementation
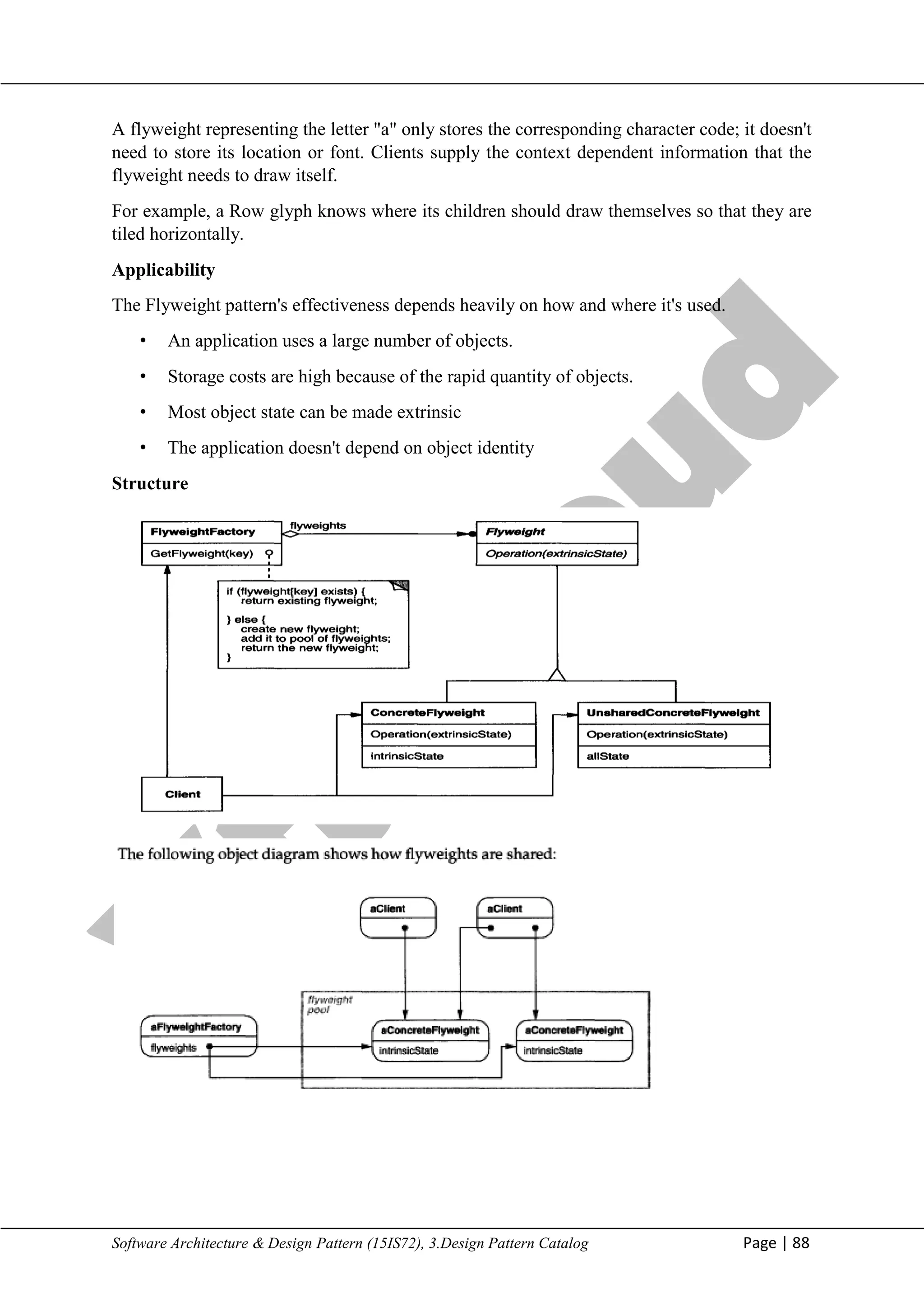
Consider the following issues when implementing the Flyweight pattern:
1. Removing extrinsic state. The pattern's applicability is determined largely by how easy it is
to identify extrinsic state and remove it from shared objects. Removing extrinsic state won't
help reduce storage costs if there are as many different kinds of extrinsic state as there are
objects before sharing. Ideally, extrinsic state can be computed from a separate object
structure, one with far smaller storage requirements.
In our document editor, for example, we can store a map of typographic information
in a separate structure rather than store the font and type style with each character object. The
map keeps track of runs of characters with the same typographic attributes. When a character
draws itself, it receives its typographic attributes as a side-effect of the draw traversal.
Because documents normally use just a few different fonts and styles, storing this information
externally to each character object is far more efficient than storing it internally.
2. Managing shared objects. Because objects are shared, clients shouldn't instantiate them
directly. FlyweightFactory lets clients locate a particular flyweight. FlyweightFactory objects
often use an associative store to let clients look up flyweights of interest. For example, the
flyweight factory in the document editor example can keep a table of flyweights indexed by
character codes. The manager returns the proper flyweight given its code, creating the
flyweight if it does not already exist.
Known Uses
ET++ [WGM88] uses flyweights to support look-and-feel independence. The look-and-feel
standard affects the layout of user interface elements (e.g., scroll bars, buttons, menus—
known collectively as "widgets") and their decorations (e.g., shadows, beveling). A widget
delegates all its layout and drawing behavior to a separate Layout object. Changing the
Layout object changes the look and feel, even at run-time.
The Layout objects are created and managed by Look objects. The Look class is an Abstract
Factory that retrieves a specific Layout object with operations like GetButtonLayout,
GetMenuBarLayout, and so forth. For each look-and-feel standard there is a corresponding
Looksubclass (e.g., MotifLook, OpenLook)that supplies the appropriate Layoutobjects.
By the way, Layout objects are essentially strategies (see Strategy). They are an
example of a strategy object implemented as a flyweight.
Related Patterns
The Flyweight pattern is often combined with the Composite pattern to implement a logically
hierarchical structure in terms of a directed-acyclic graph with shared leaf nodes.
It's often best to implement State and Strategy objects as flyweights.](https://image.slidesharecdn.com/sadp21cs741-m2-250110081949-4a09db0b/75/Software-and-architecture-design-pattern-30-2048.jpg)