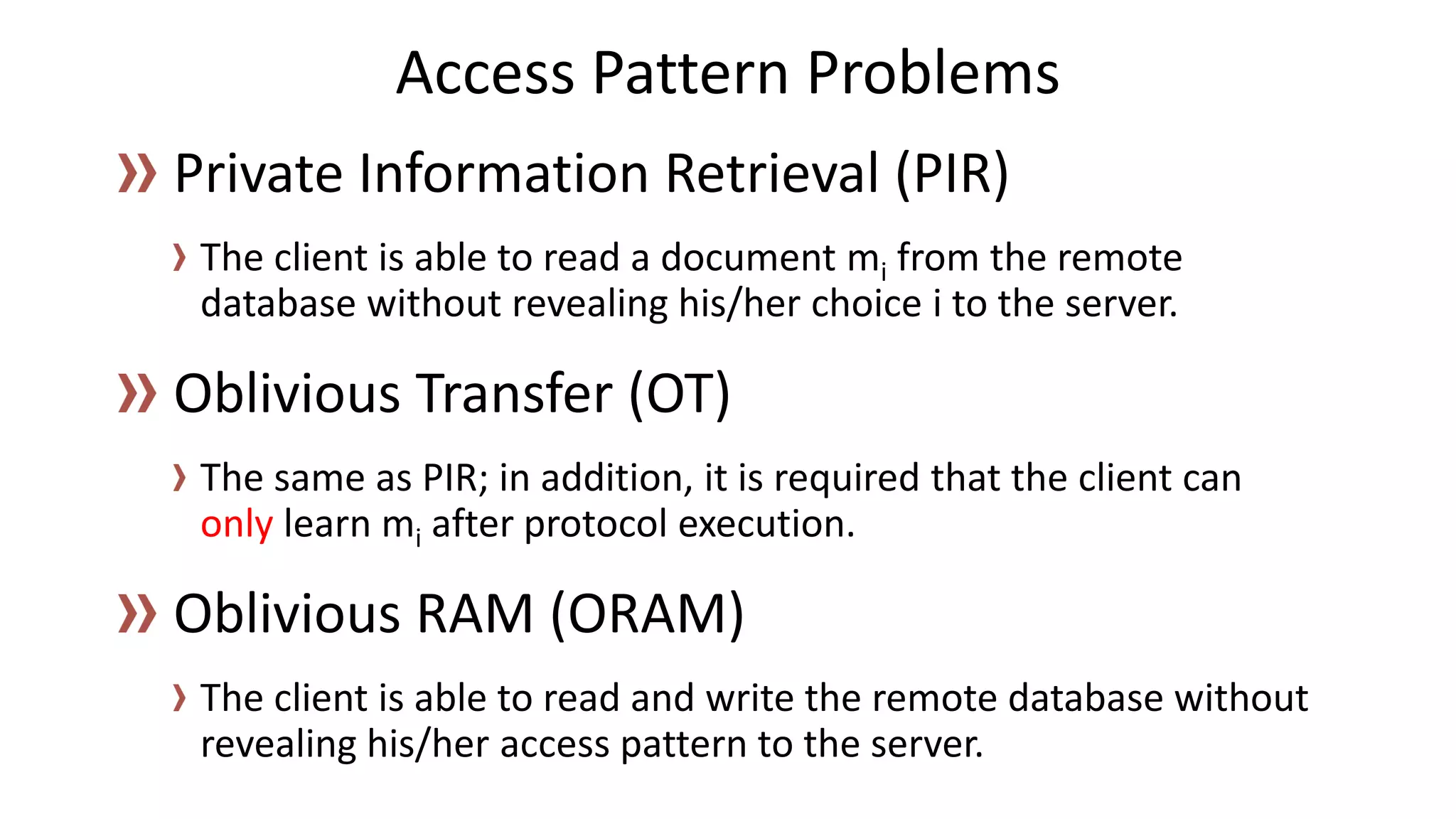
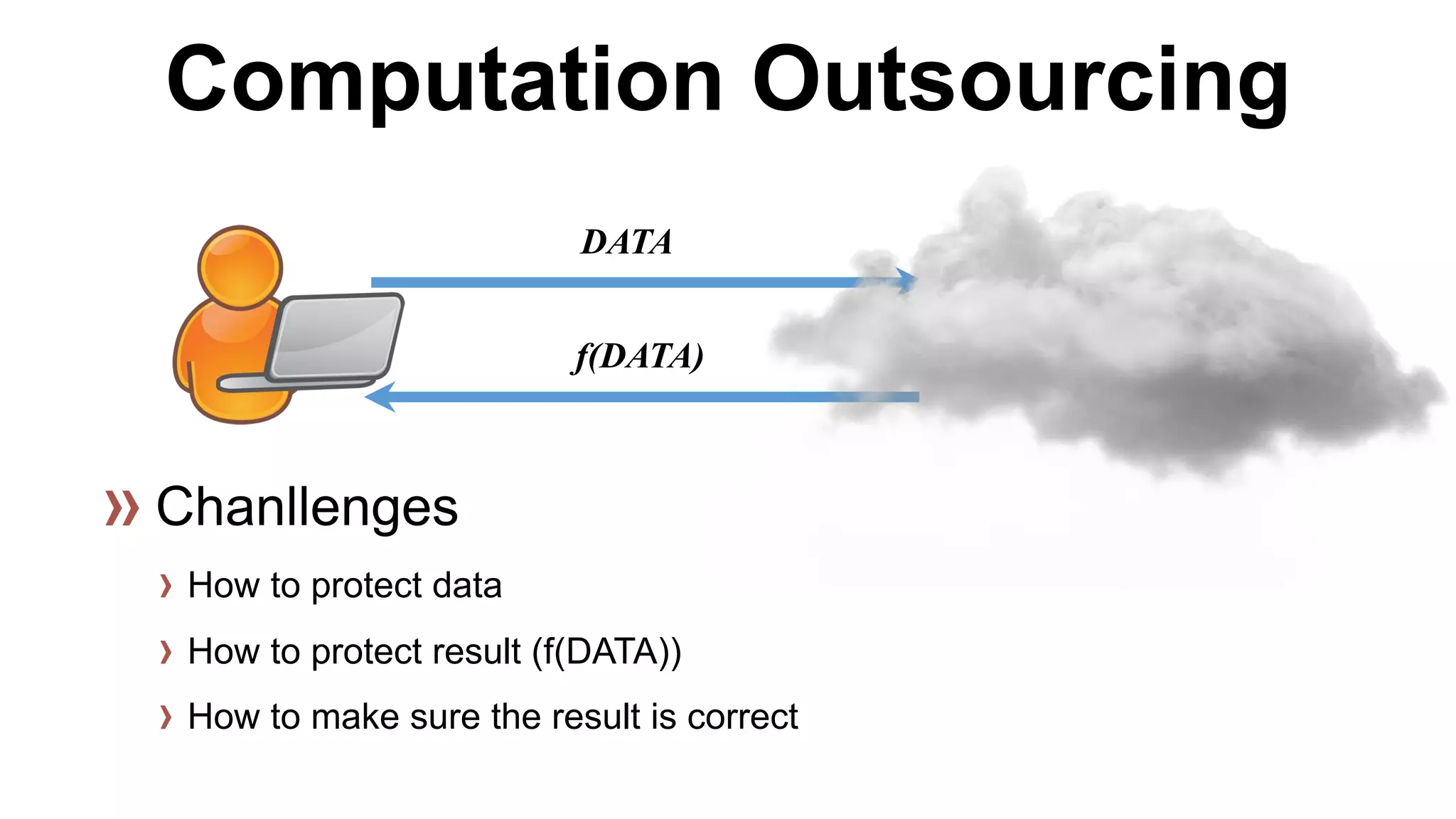
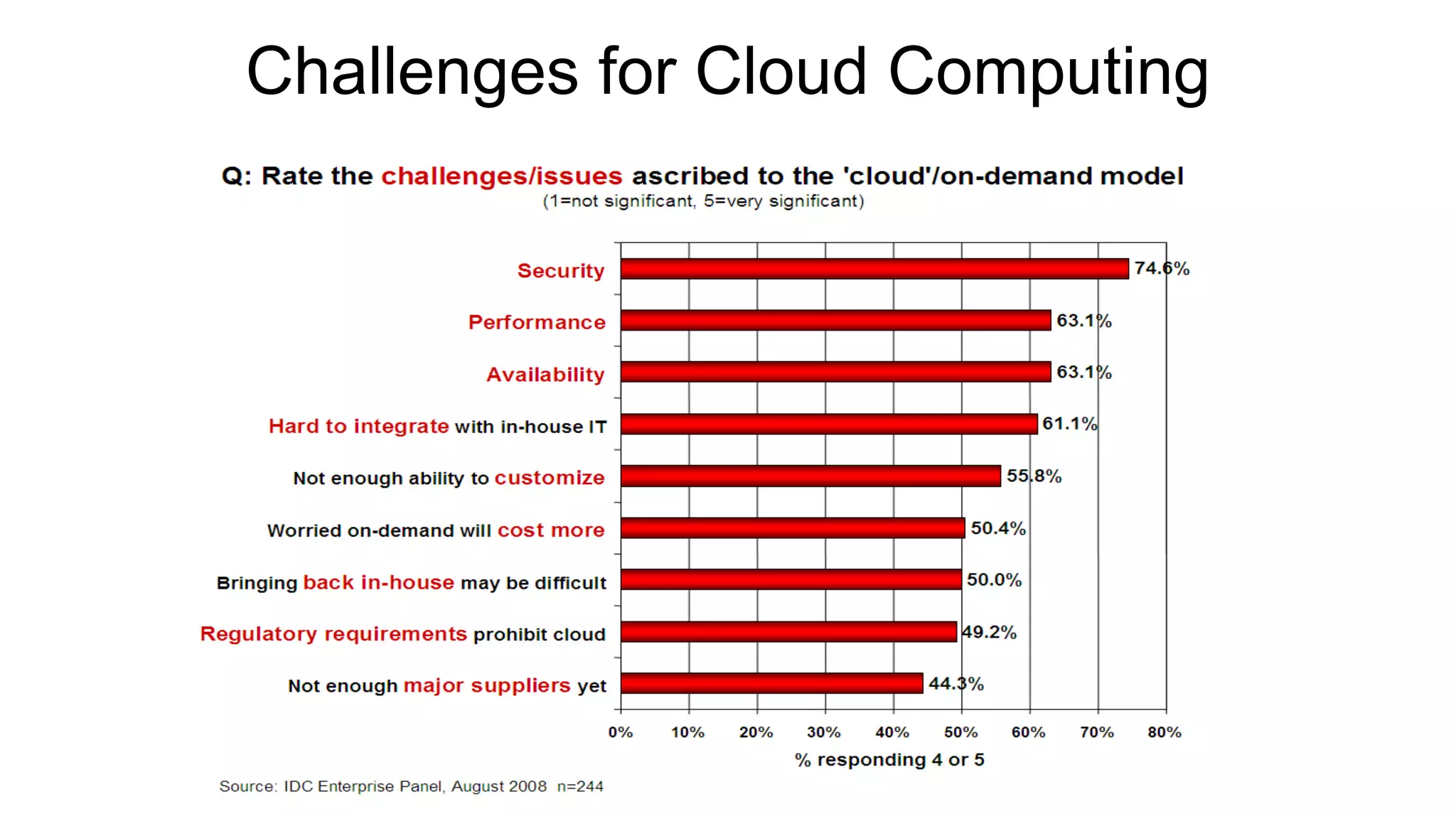
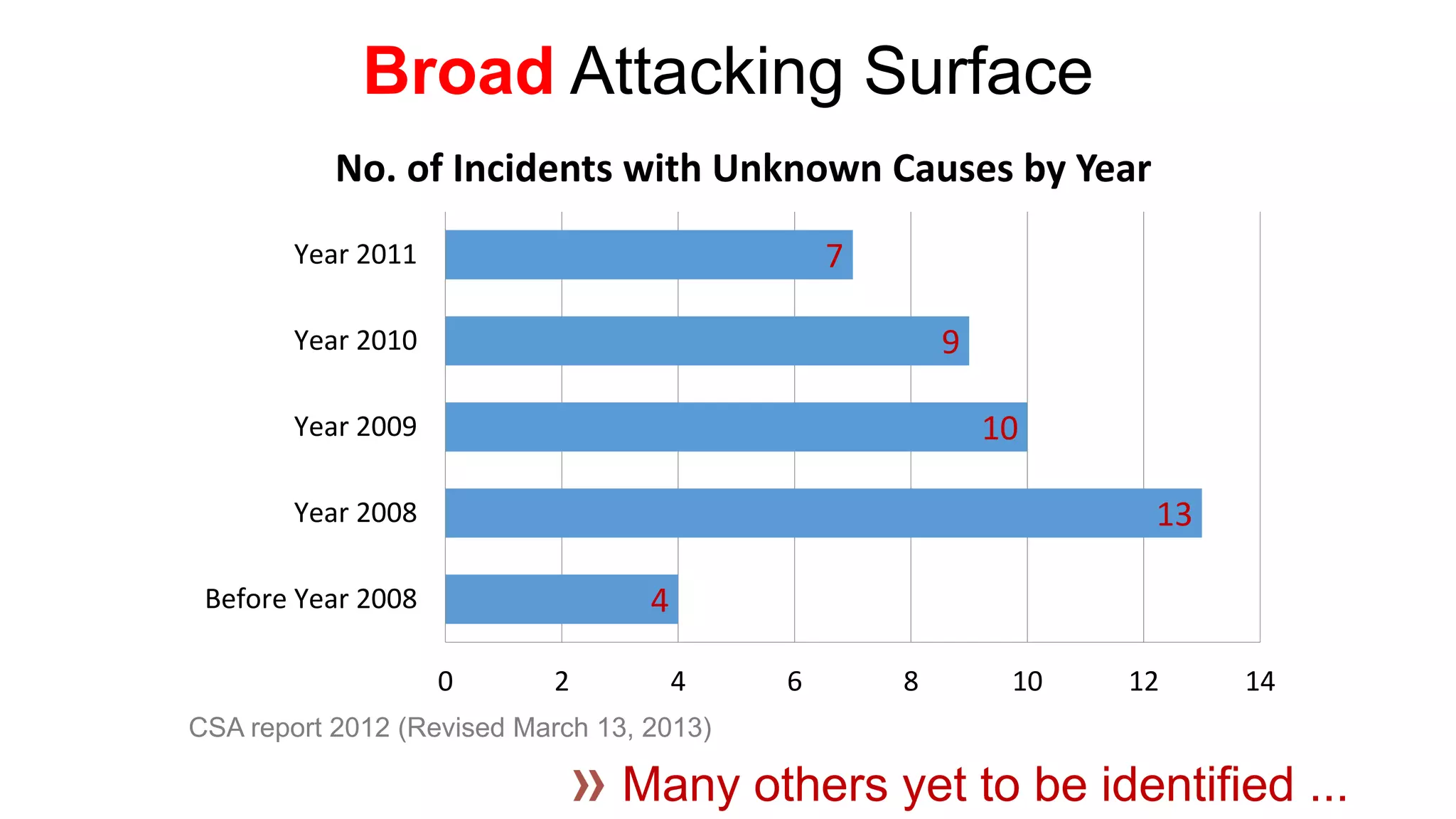
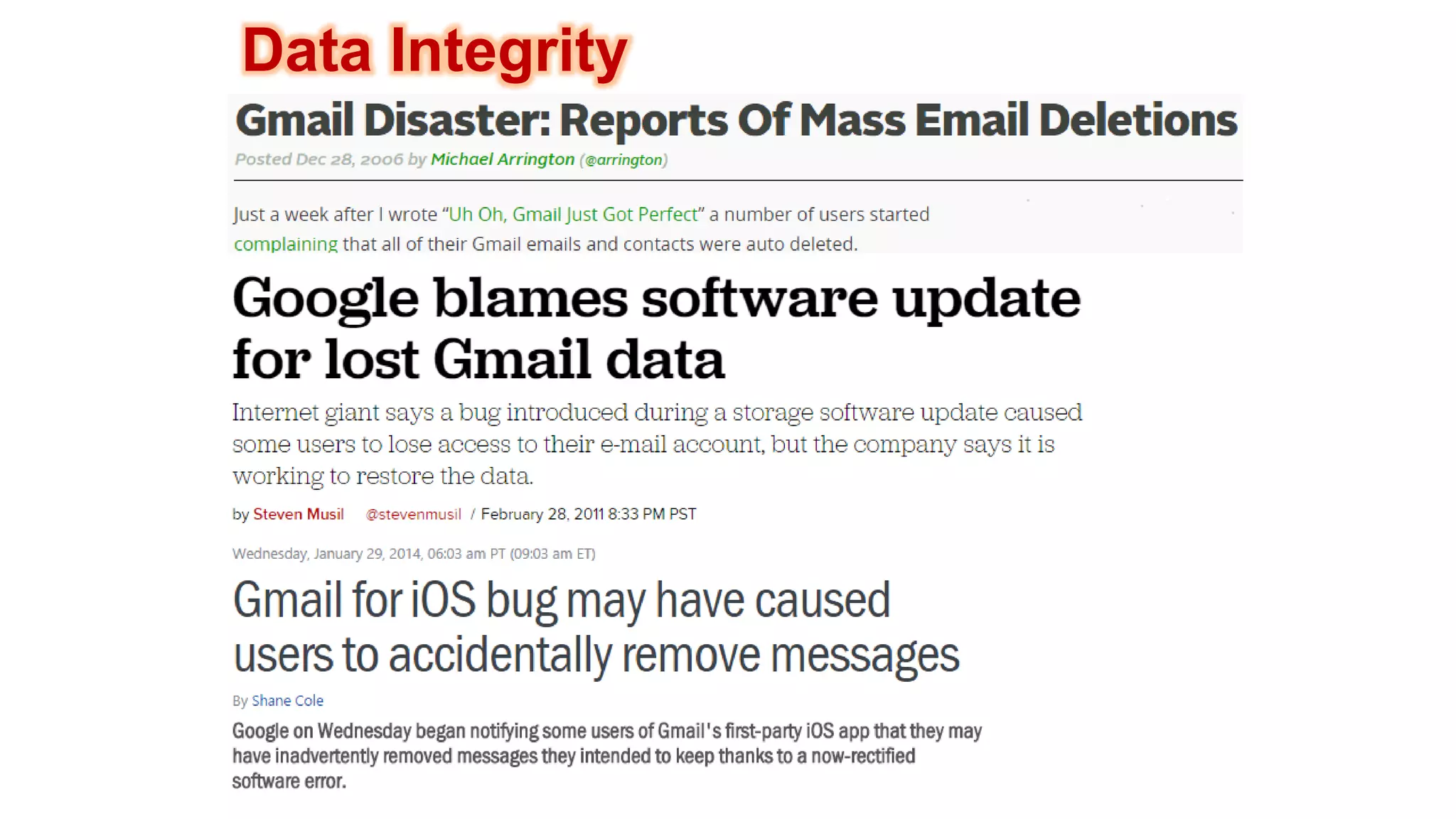
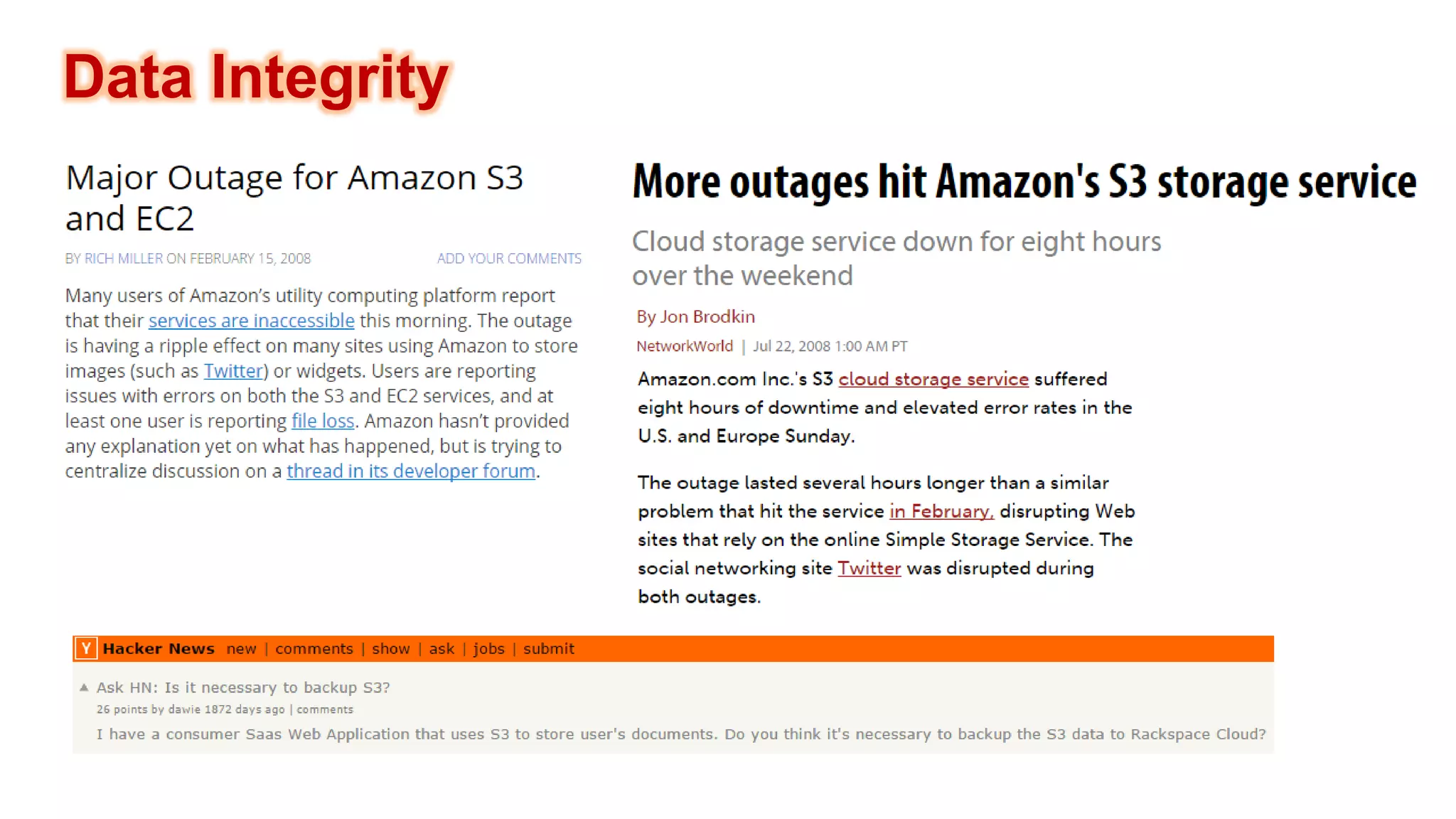
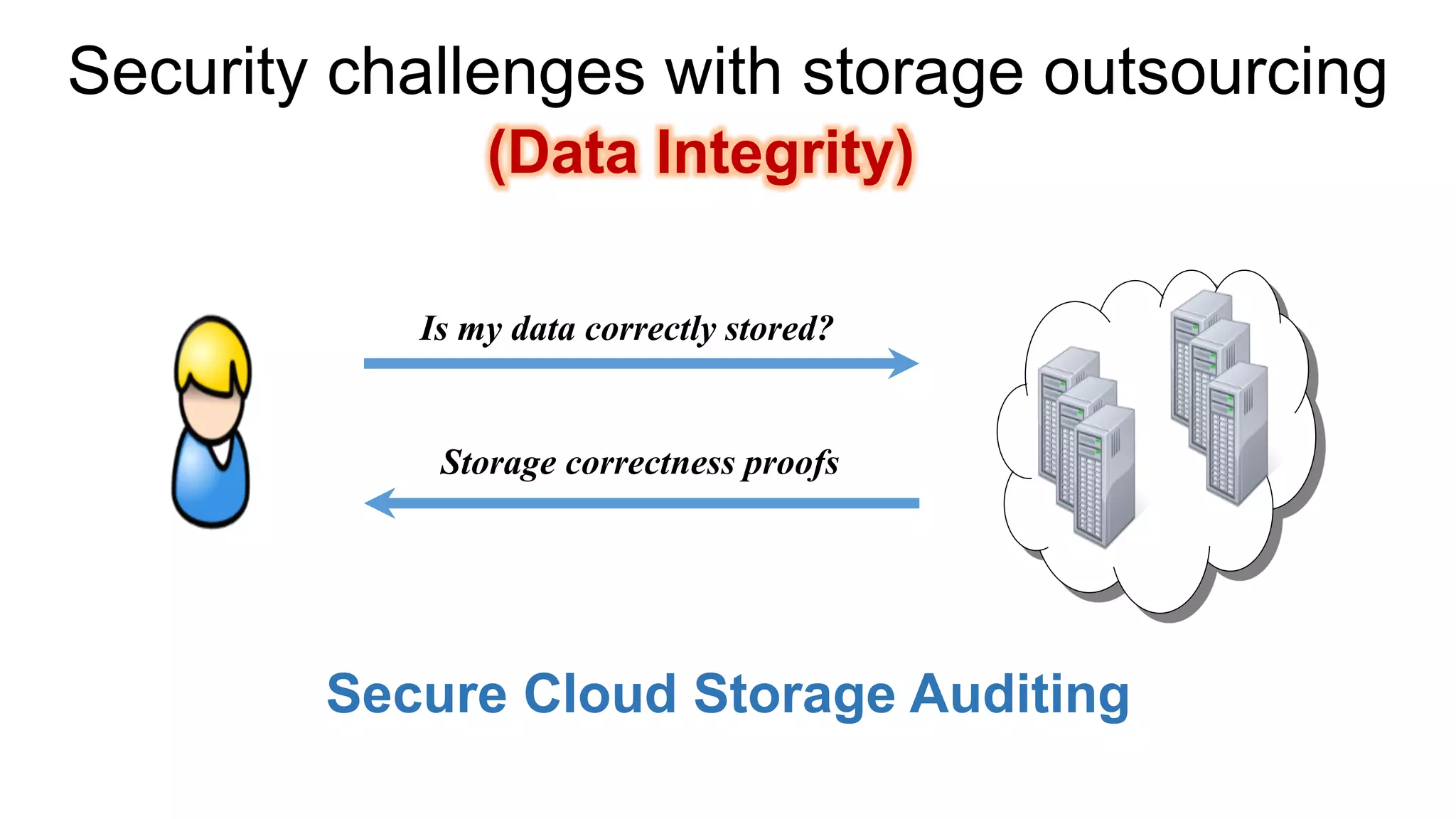
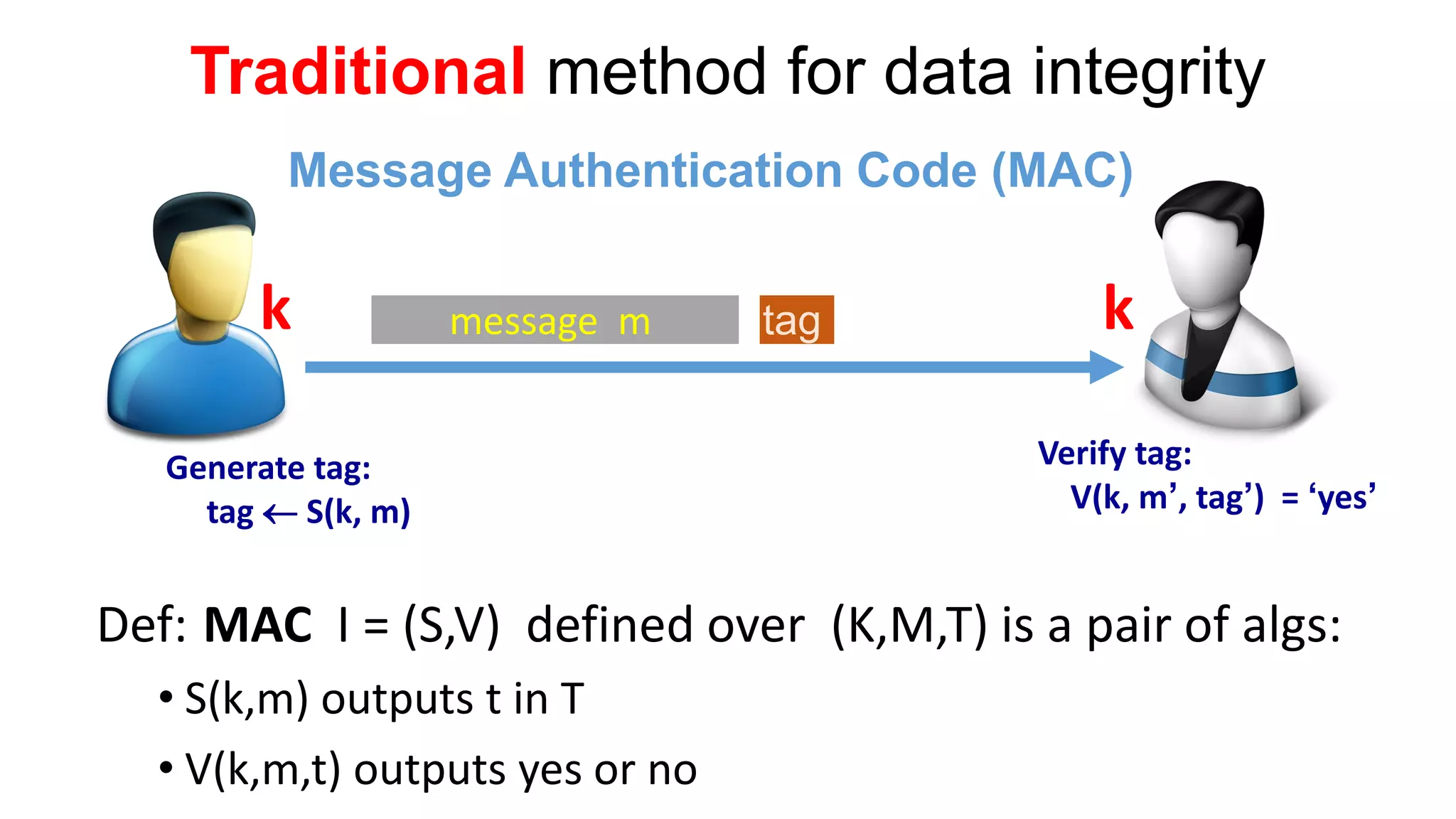
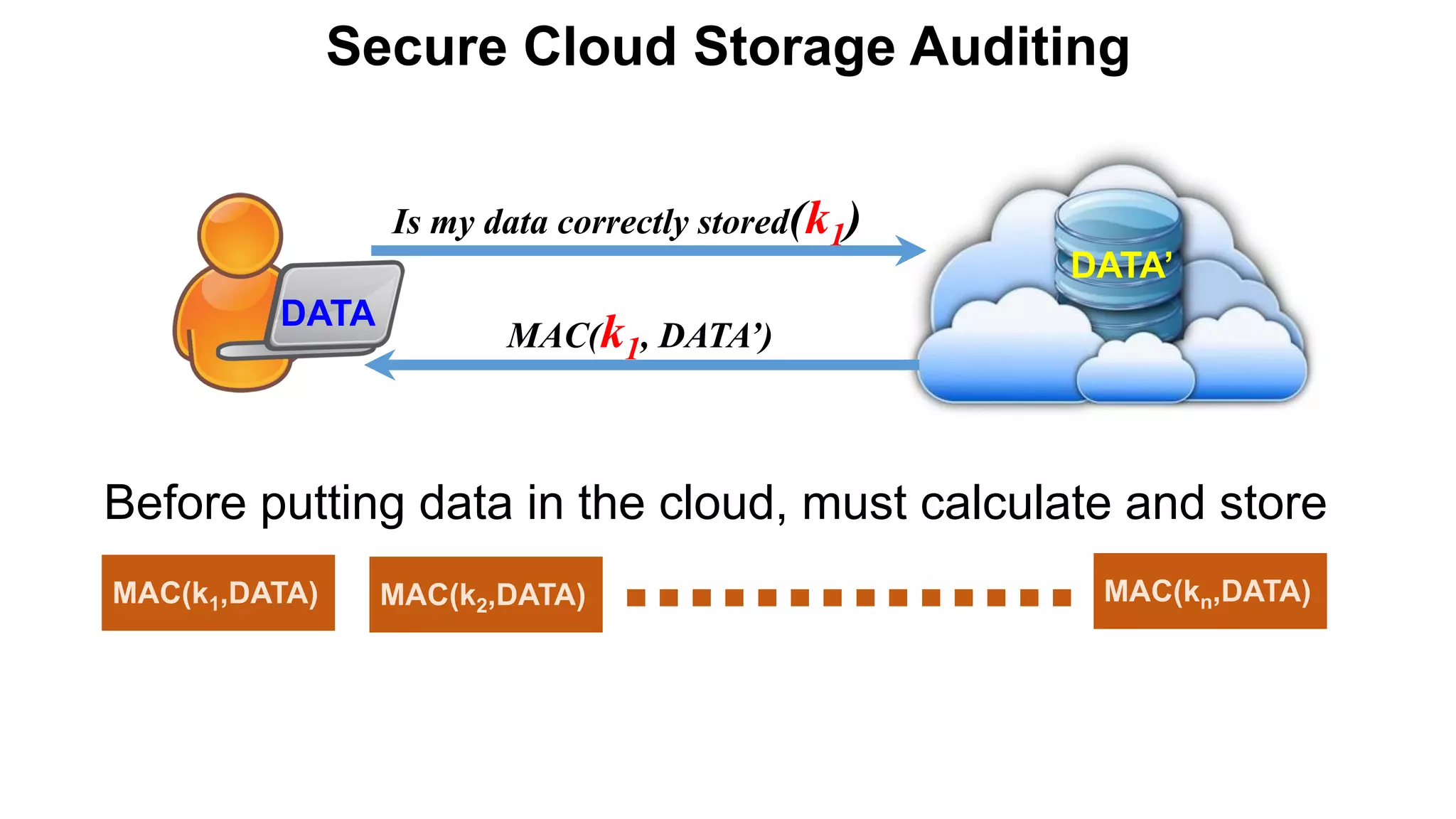
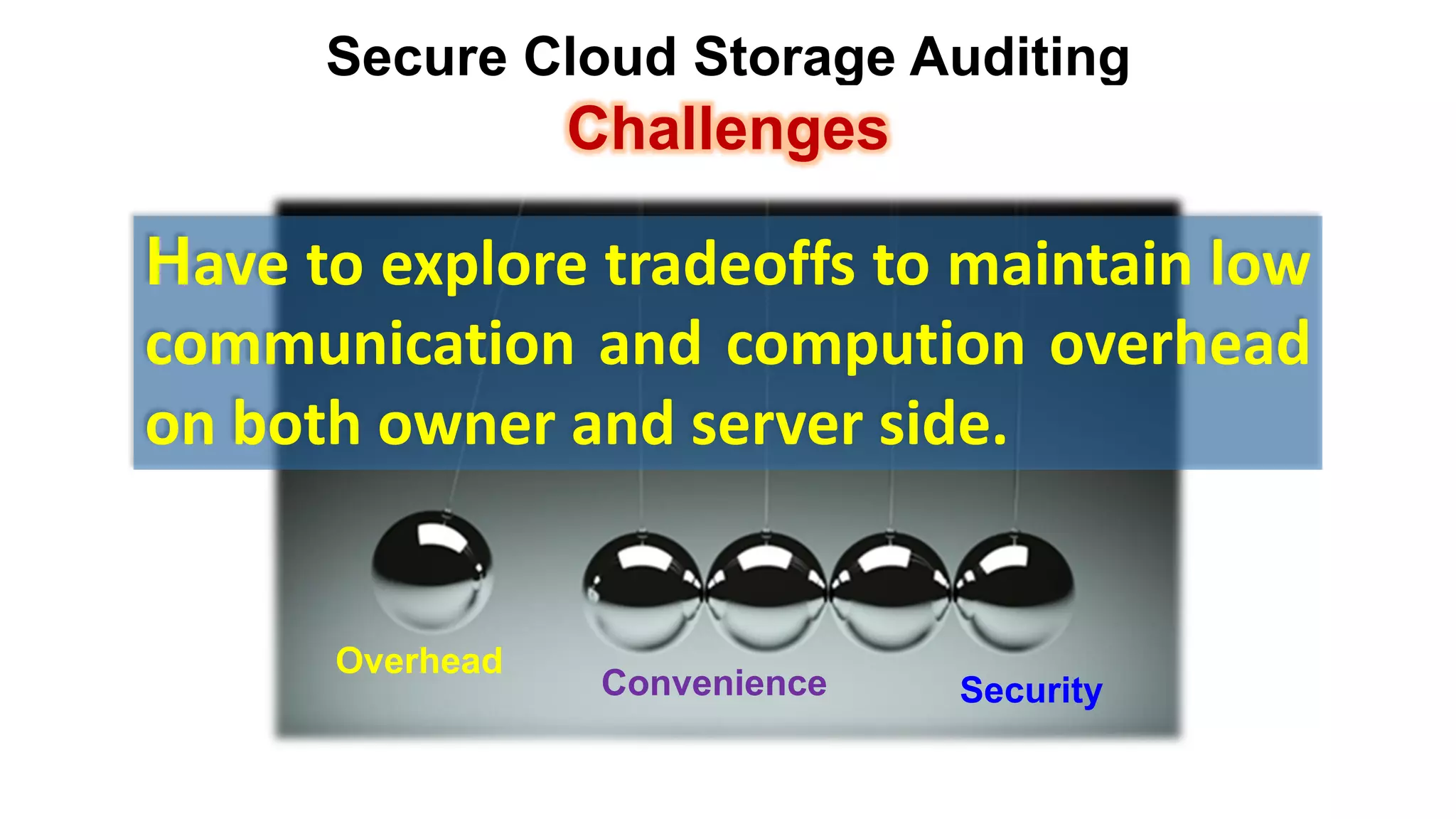
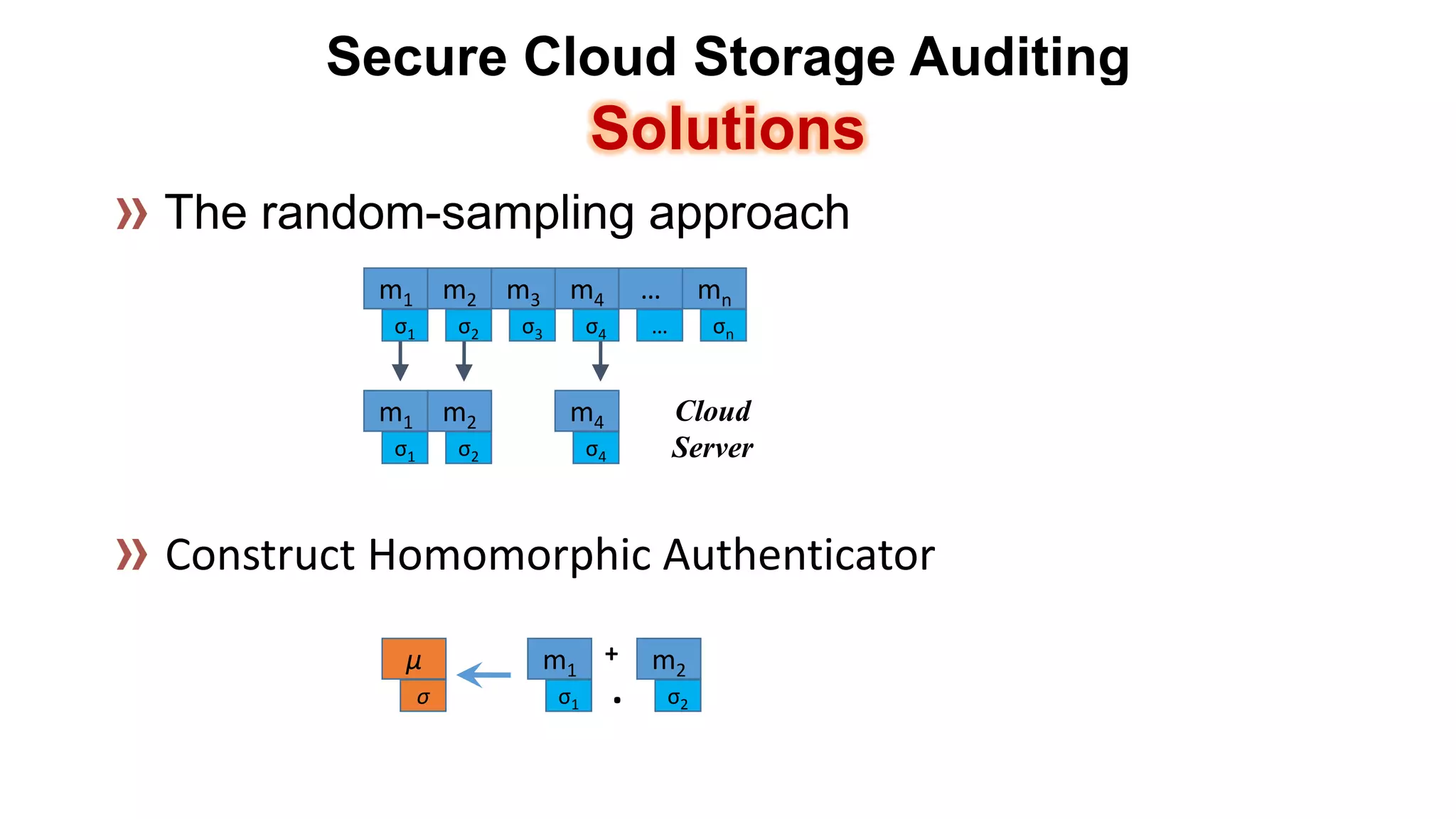
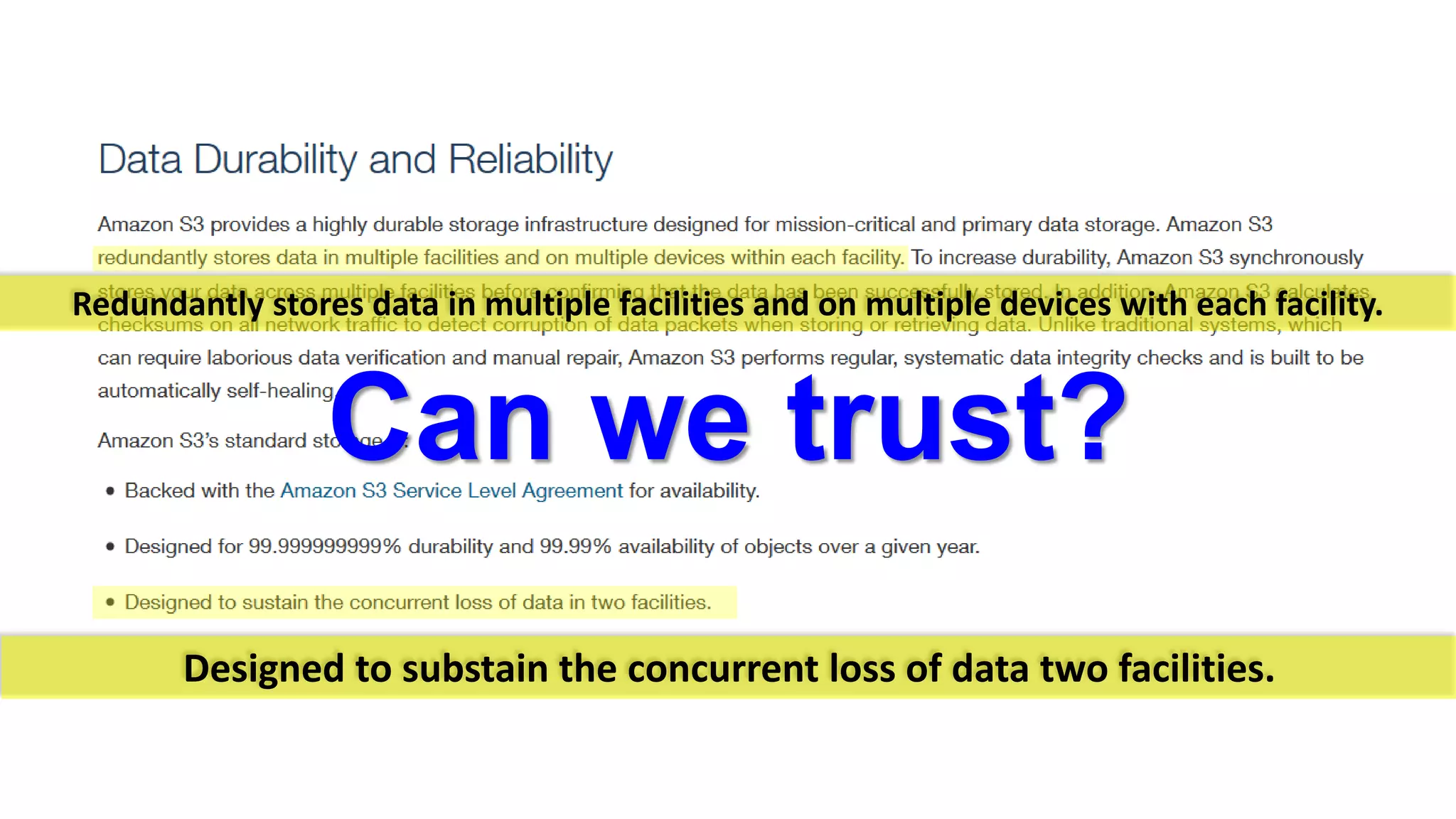
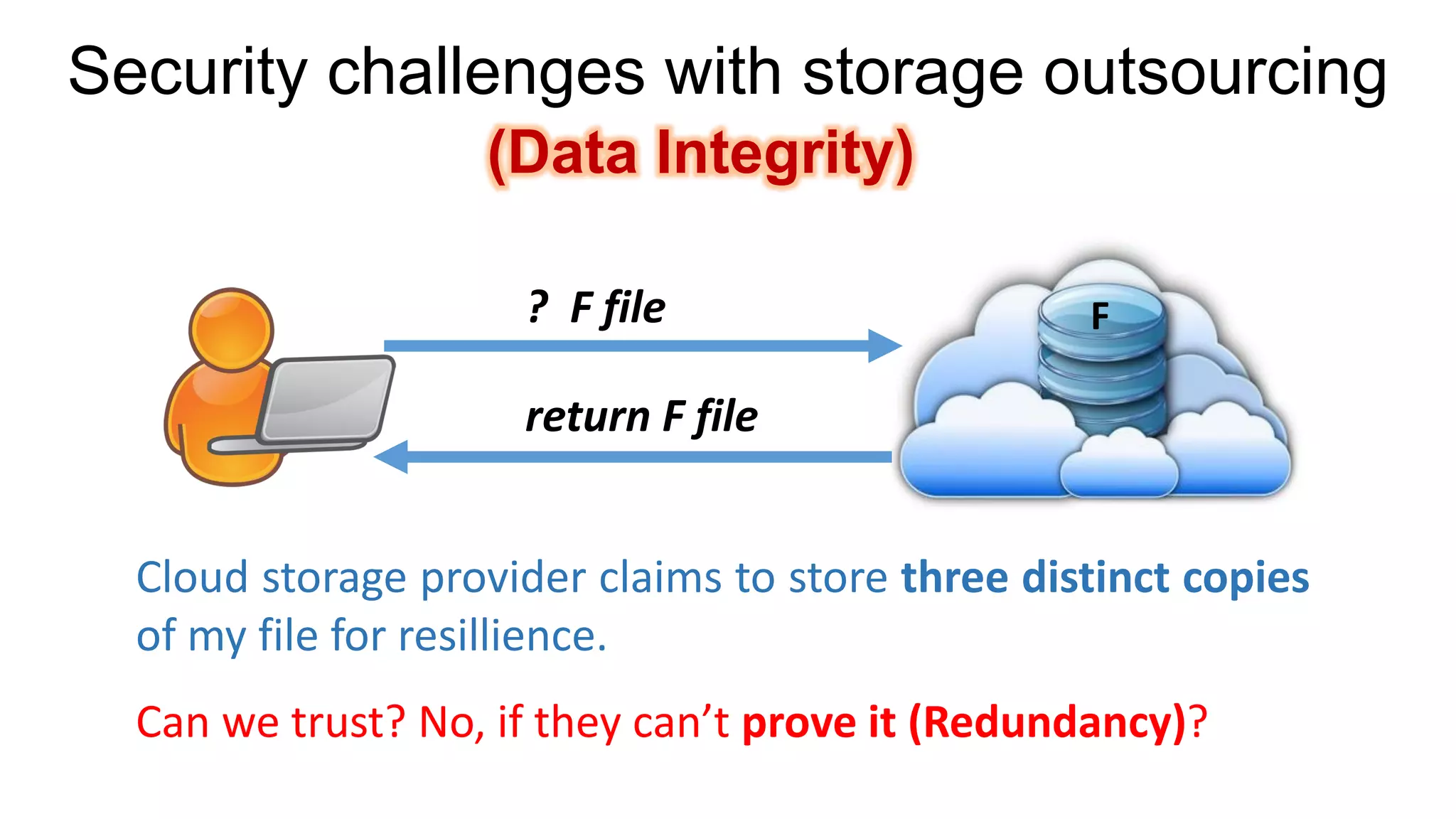
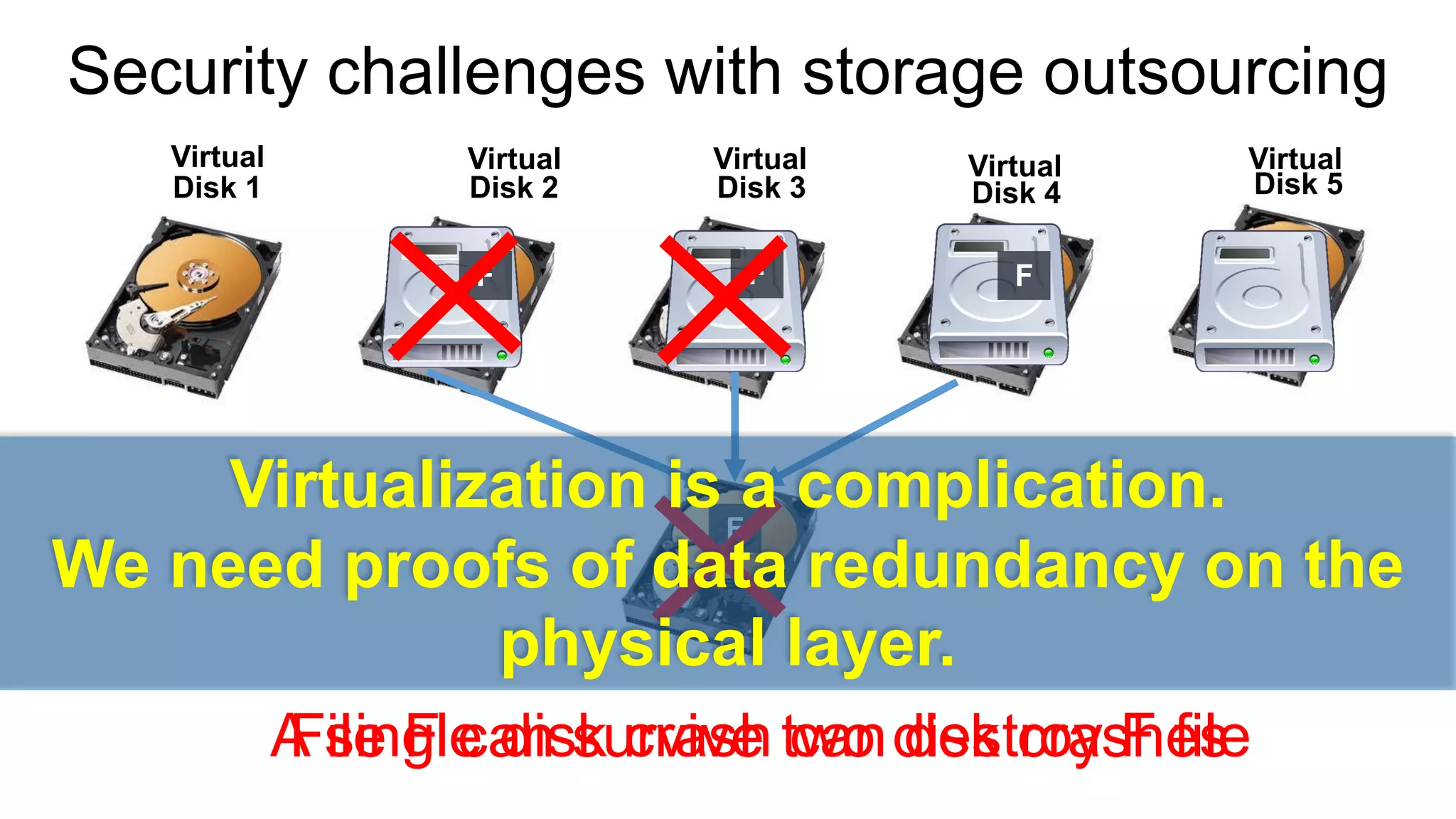
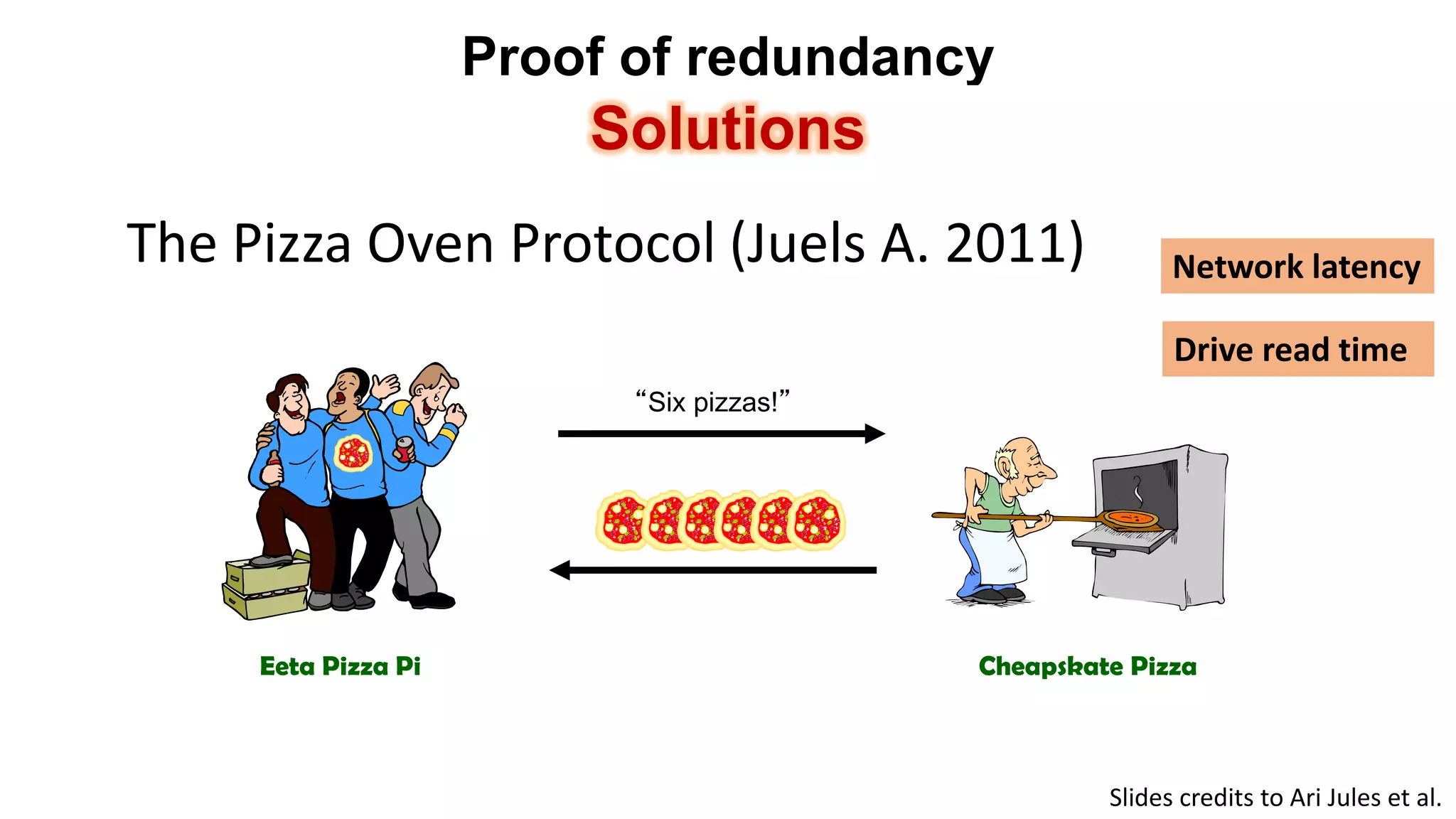
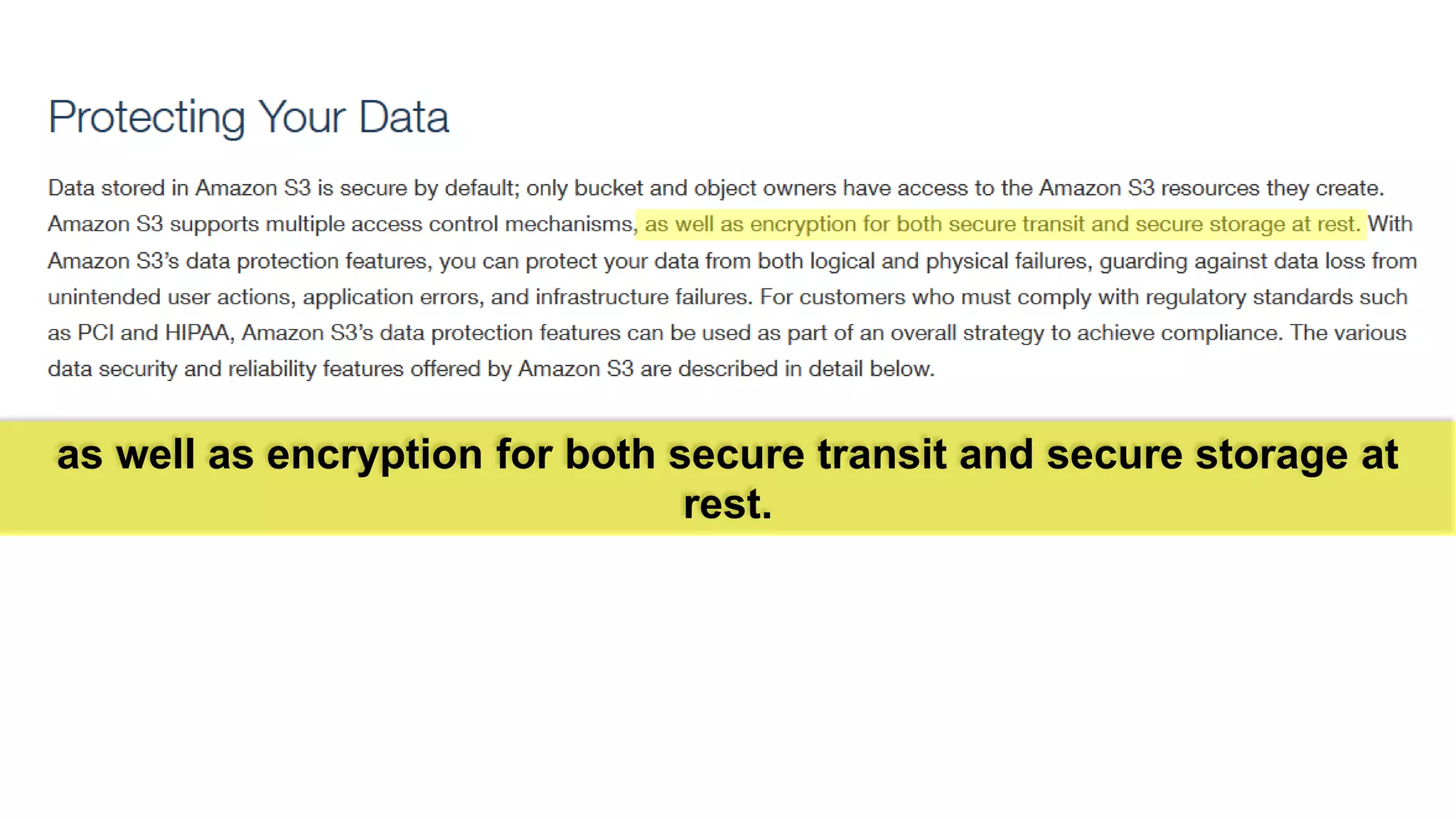
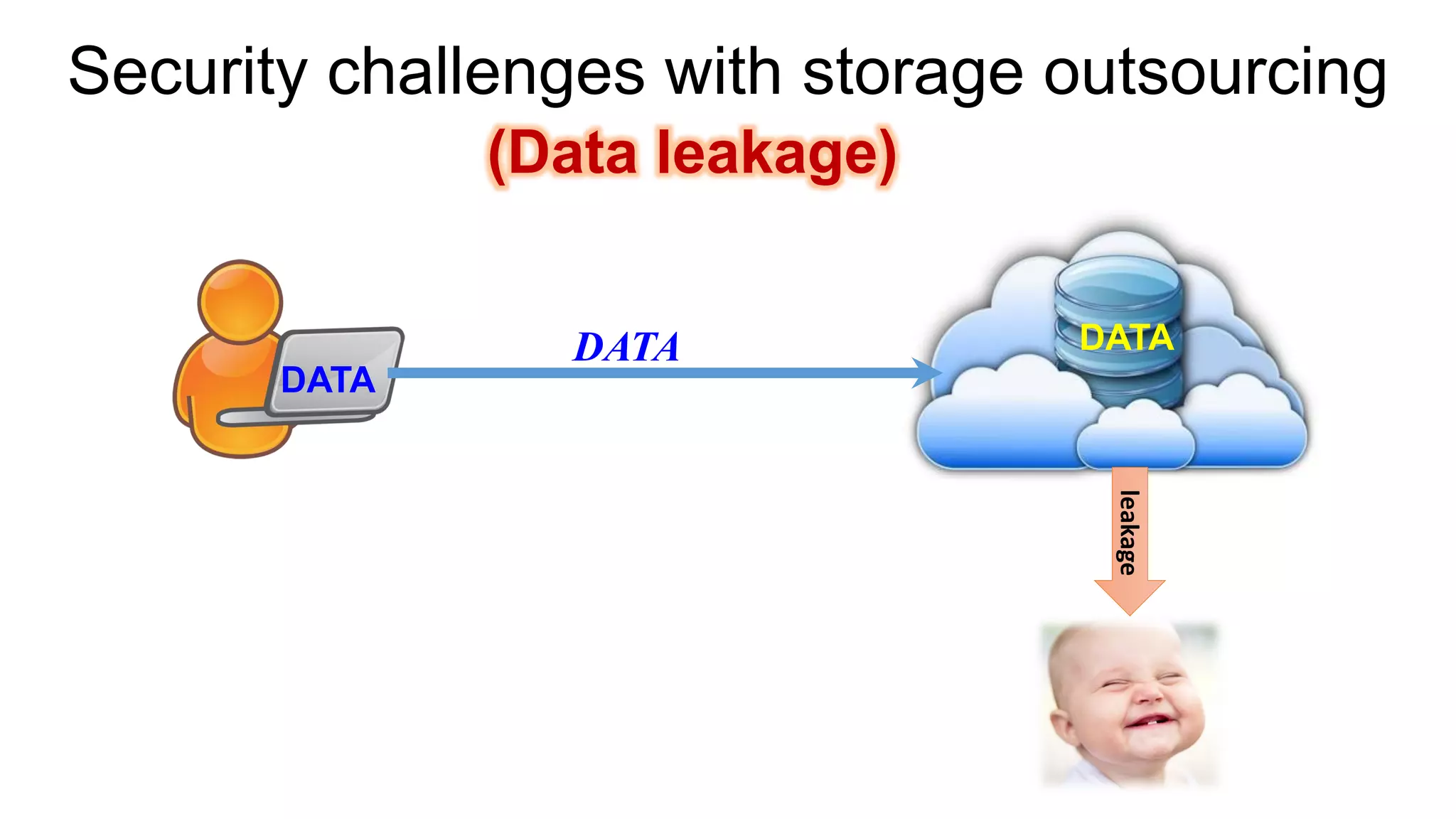
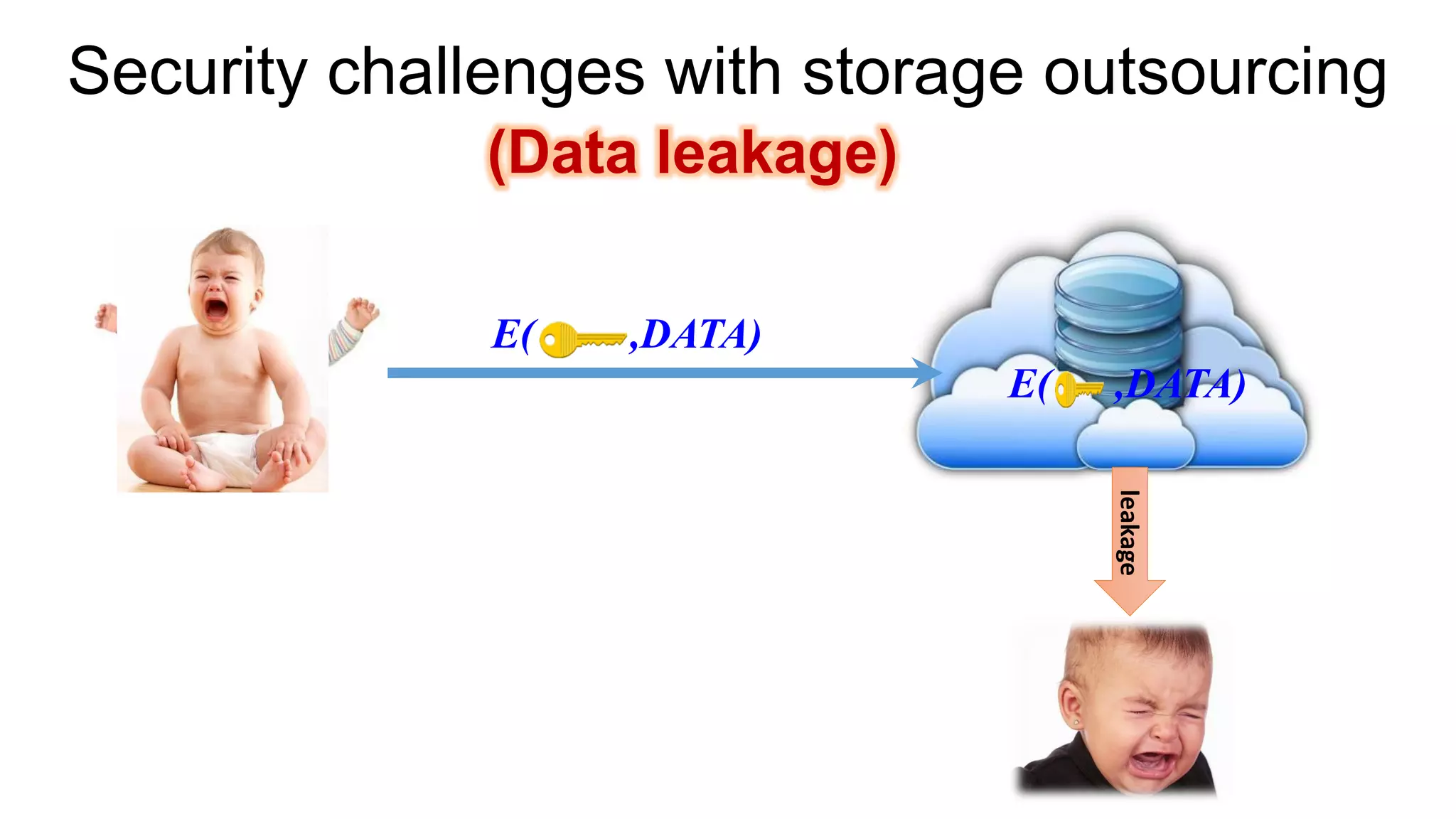
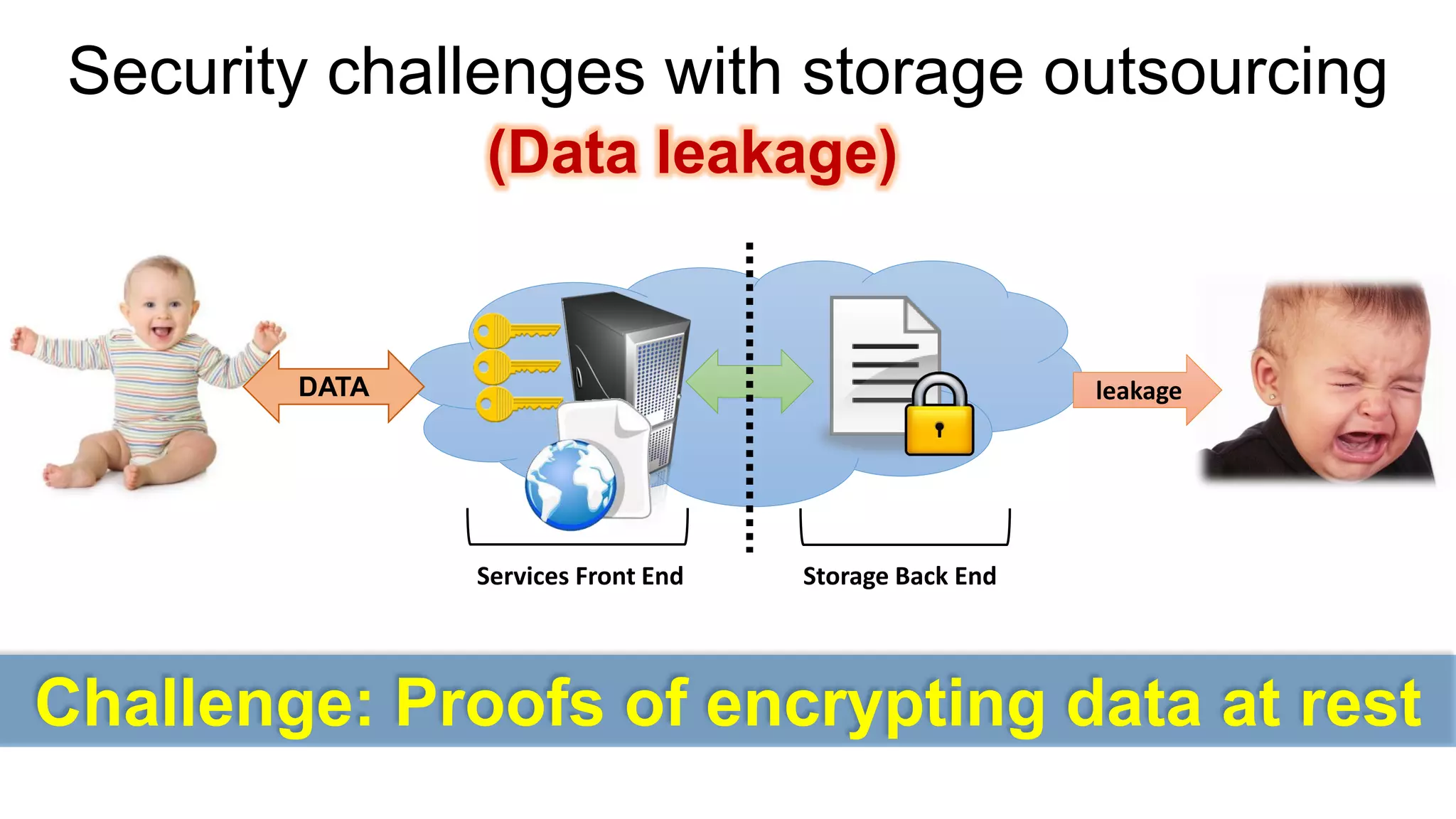
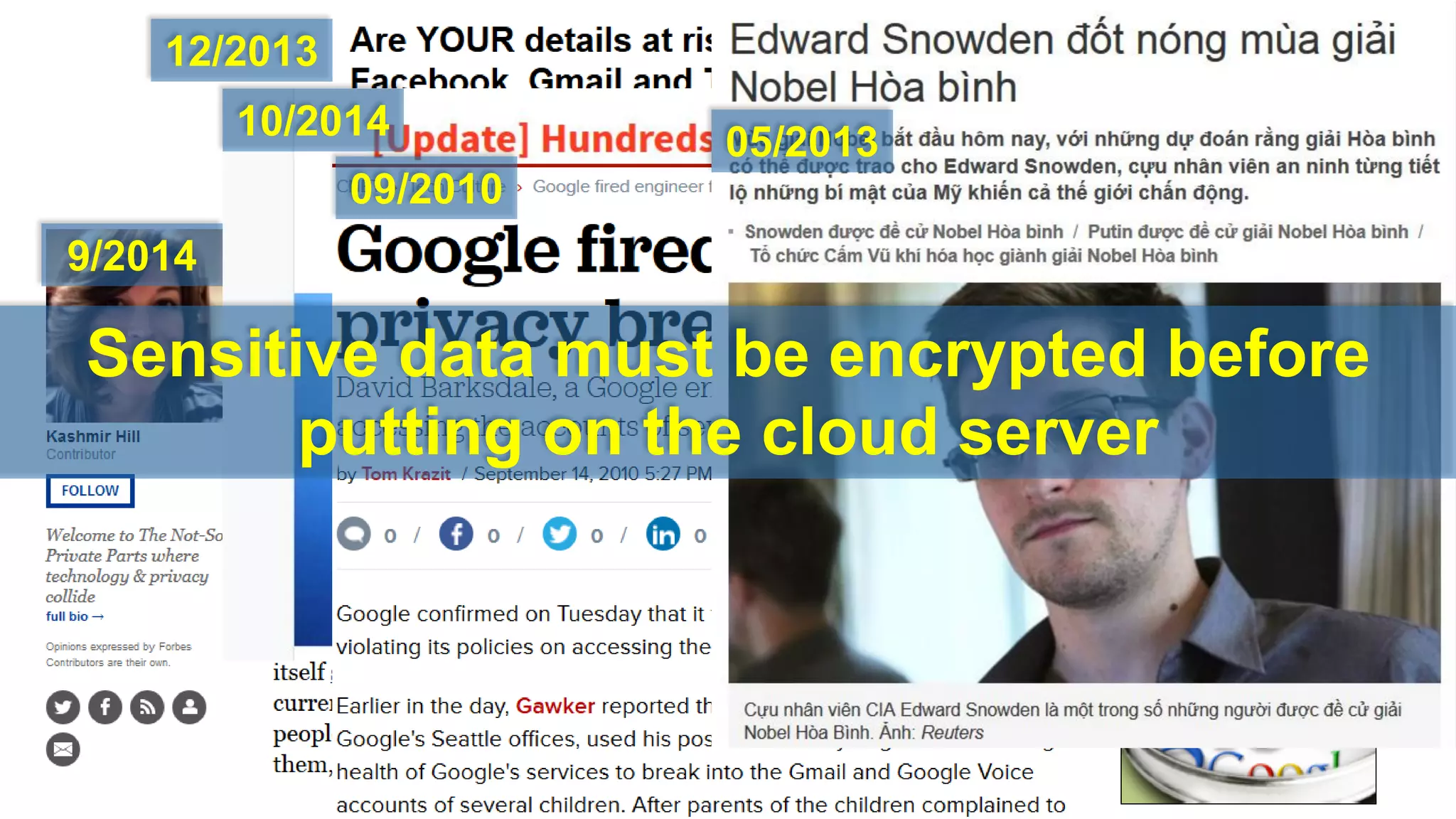
There are several security challenges with cloud computing including issues of trust, broad attacking surfaces, and data breaches. Ensuring data integrity and privacy is difficult when data is outsourced to cloud storage. Techniques like encryption, secure auditing, and proofs of data redundancy can help address some of these challenges, but protecting access patterns and enabling secure computation outsourcing remain open problems.






















![Data Encryption vs Data UtilizationSolutions
[Goldreich-Ostrovsky92]
[Song-Wagner-Perrig-S&P00][Goh-ePrint-03, Chang-Mitzenmacher-ACNS05] [Curtmola-Garay-Kamara-Ostrovsky-ccs06]
[Boneh et al. EUROCRYPT’04]](https://image.slidesharecdn.com/t1-141201202519-conversion-gate02/75/SOME-SECURITY-CHALLENGES-IN-CLOUD-COMPUTING-46-2048.jpg)