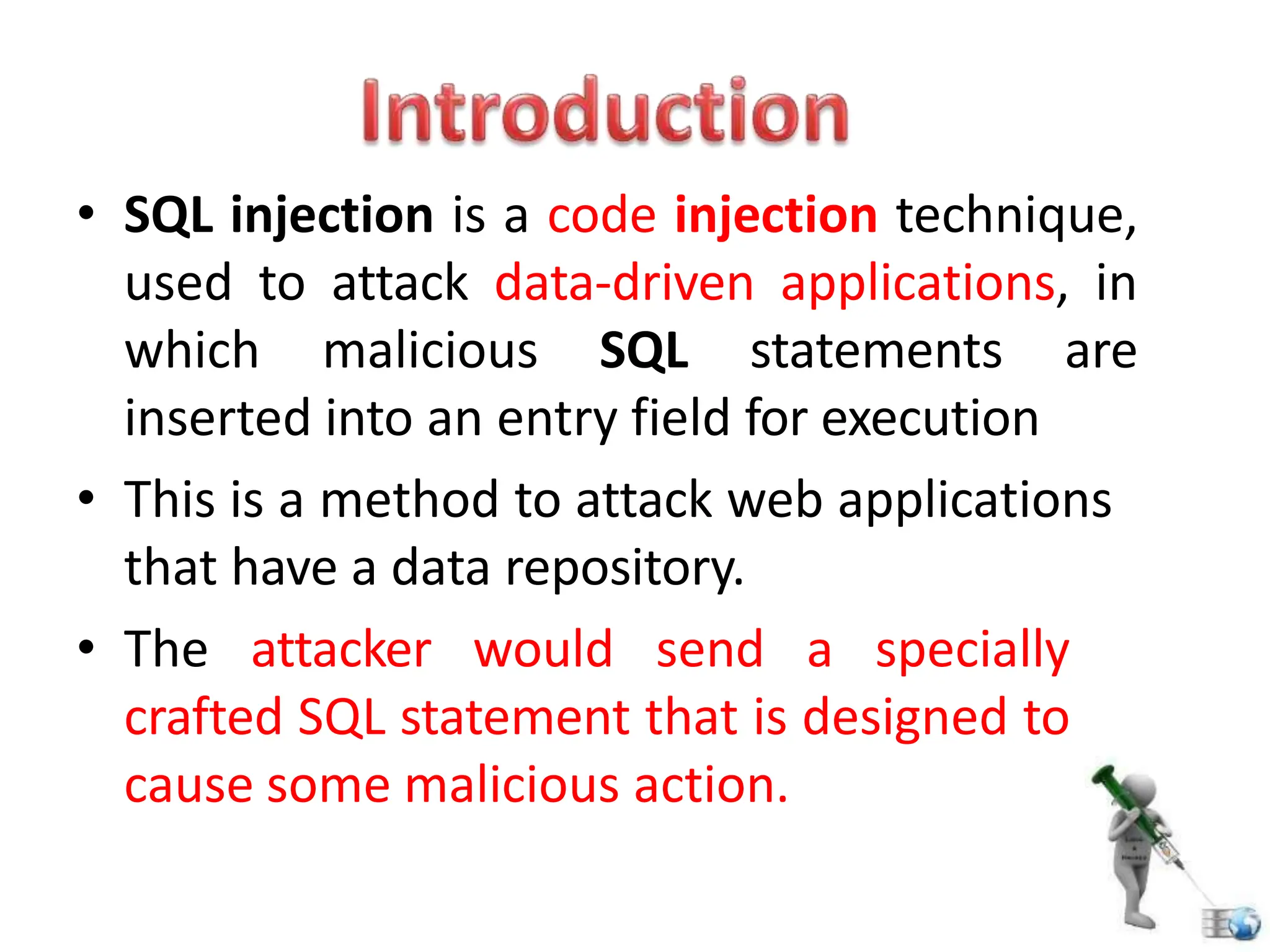
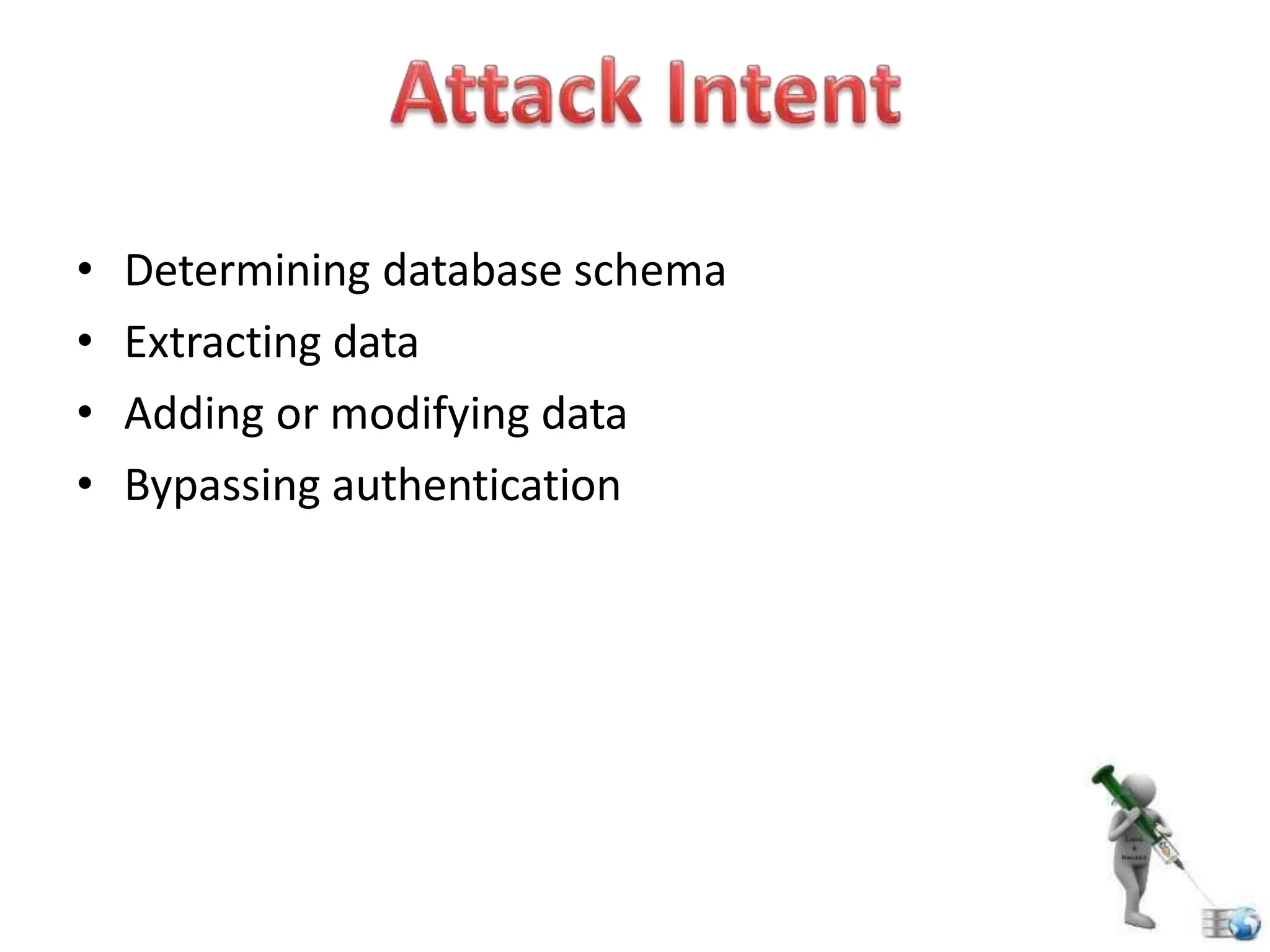
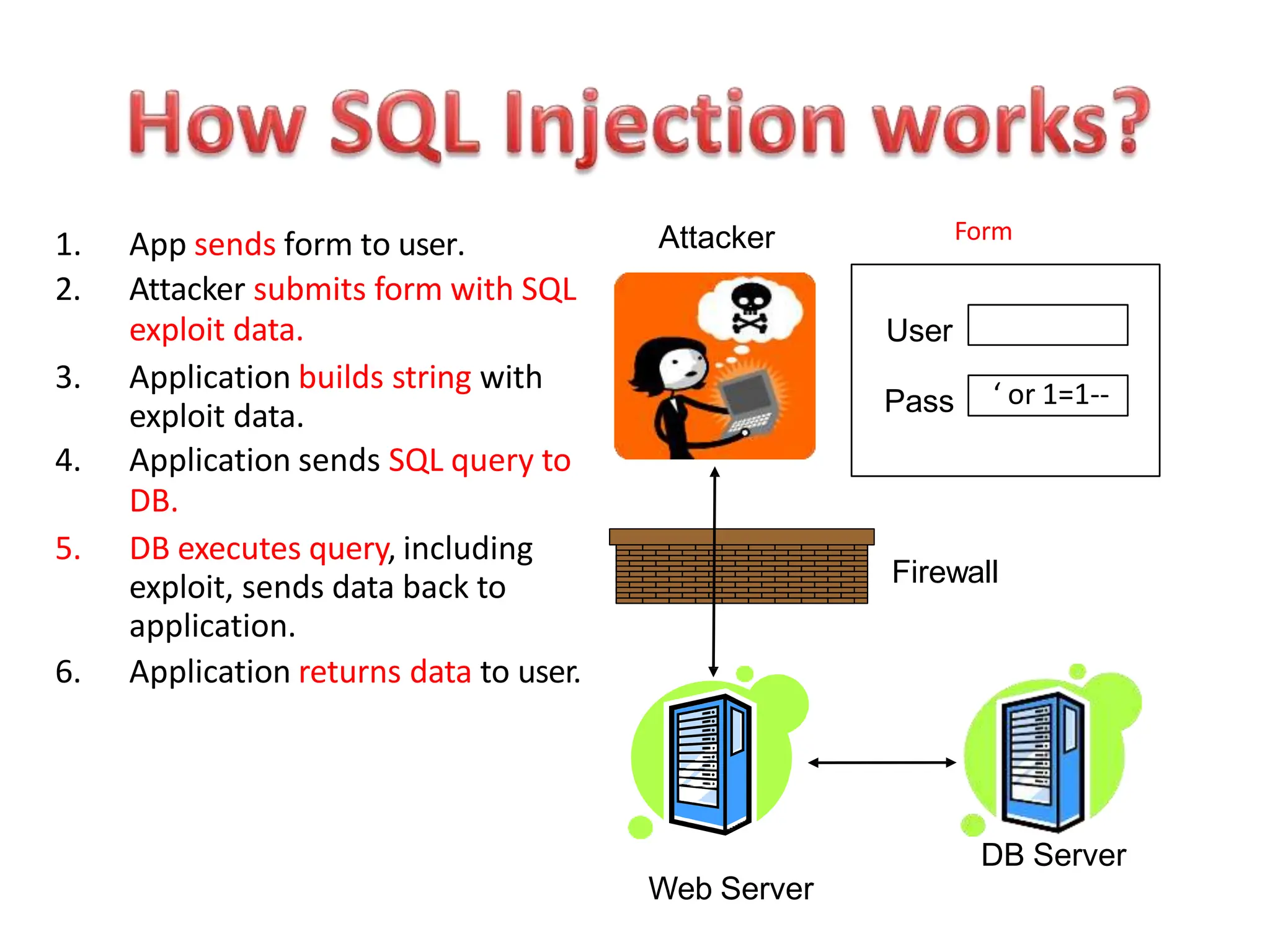
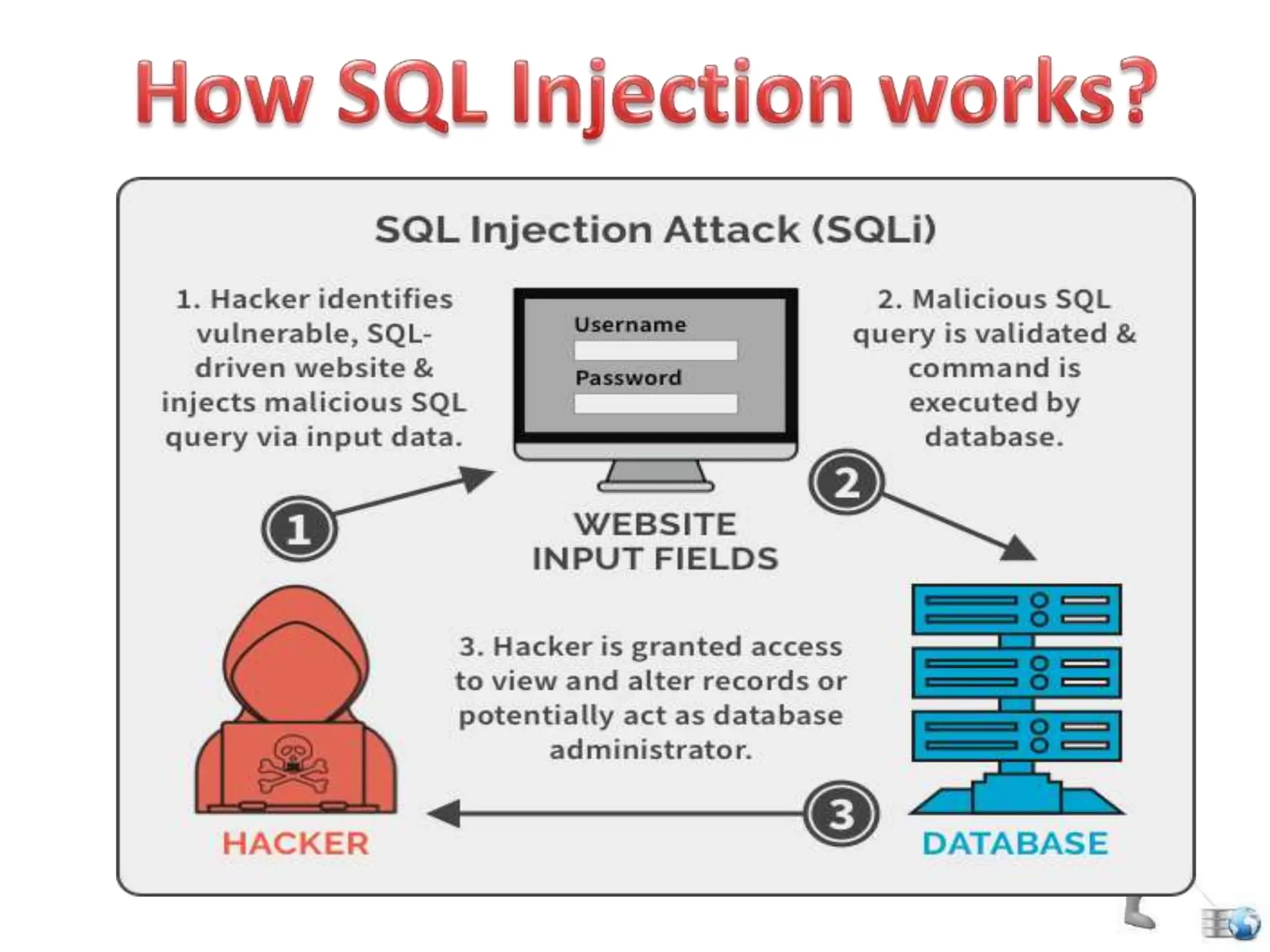
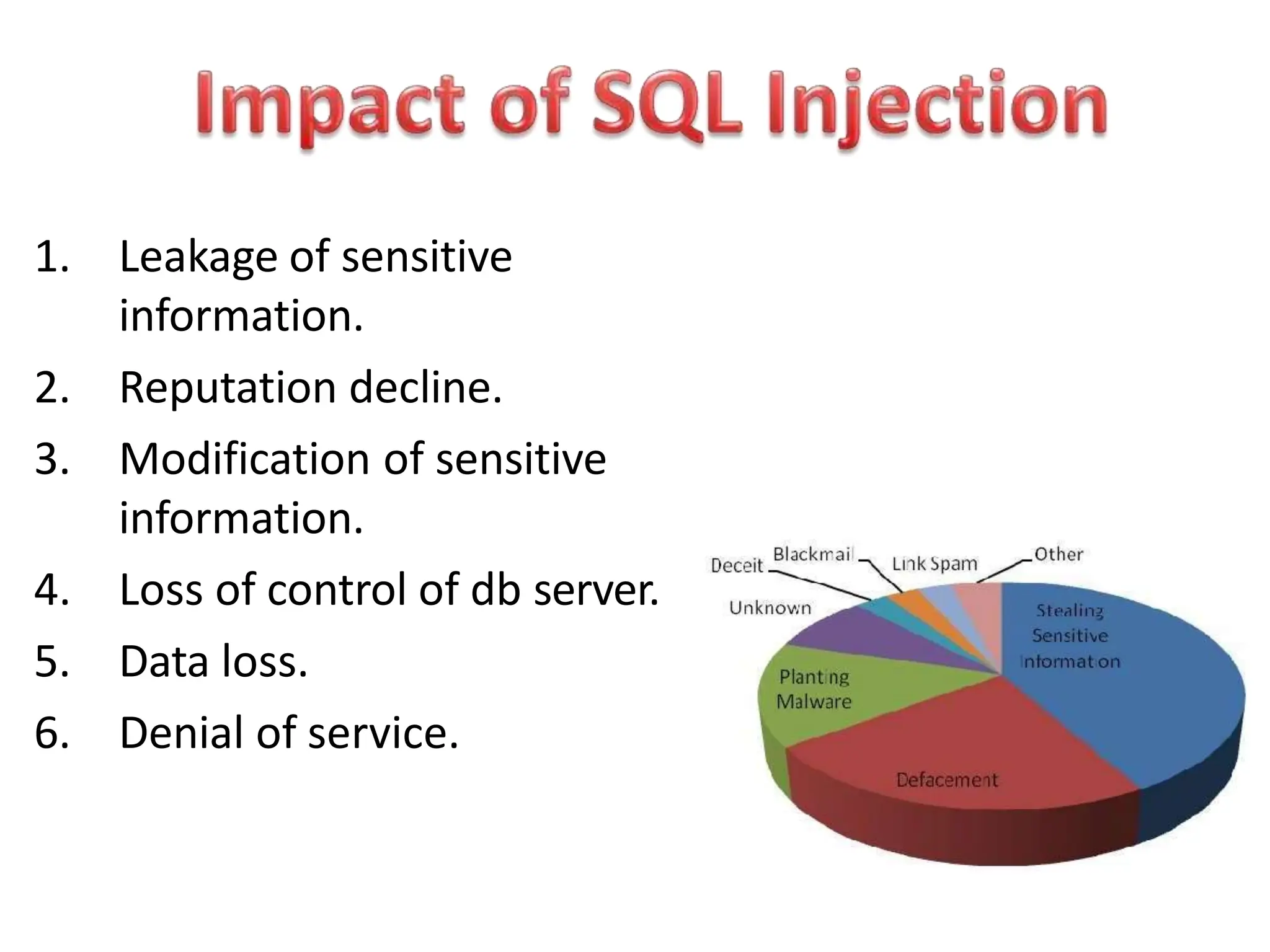
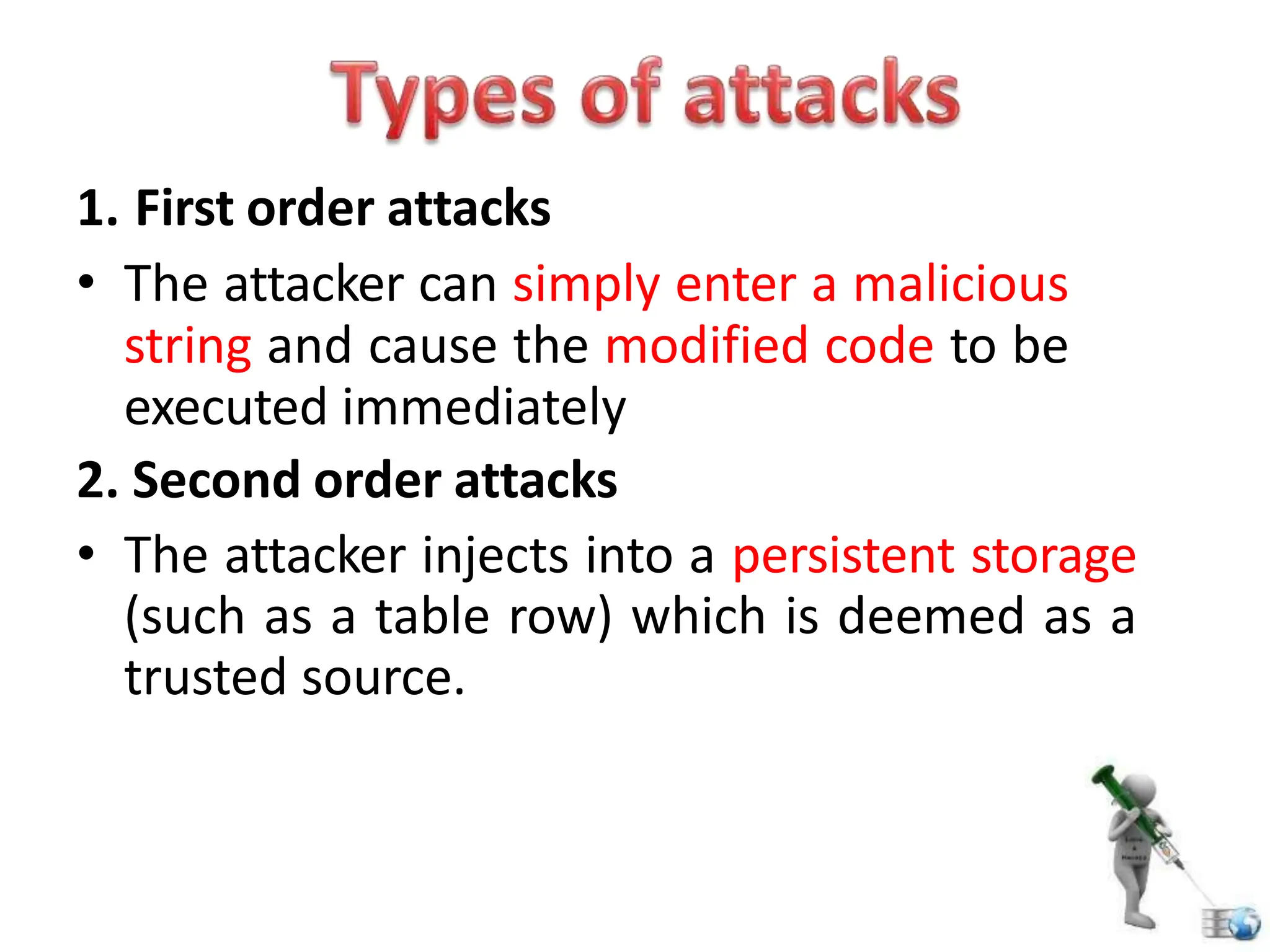
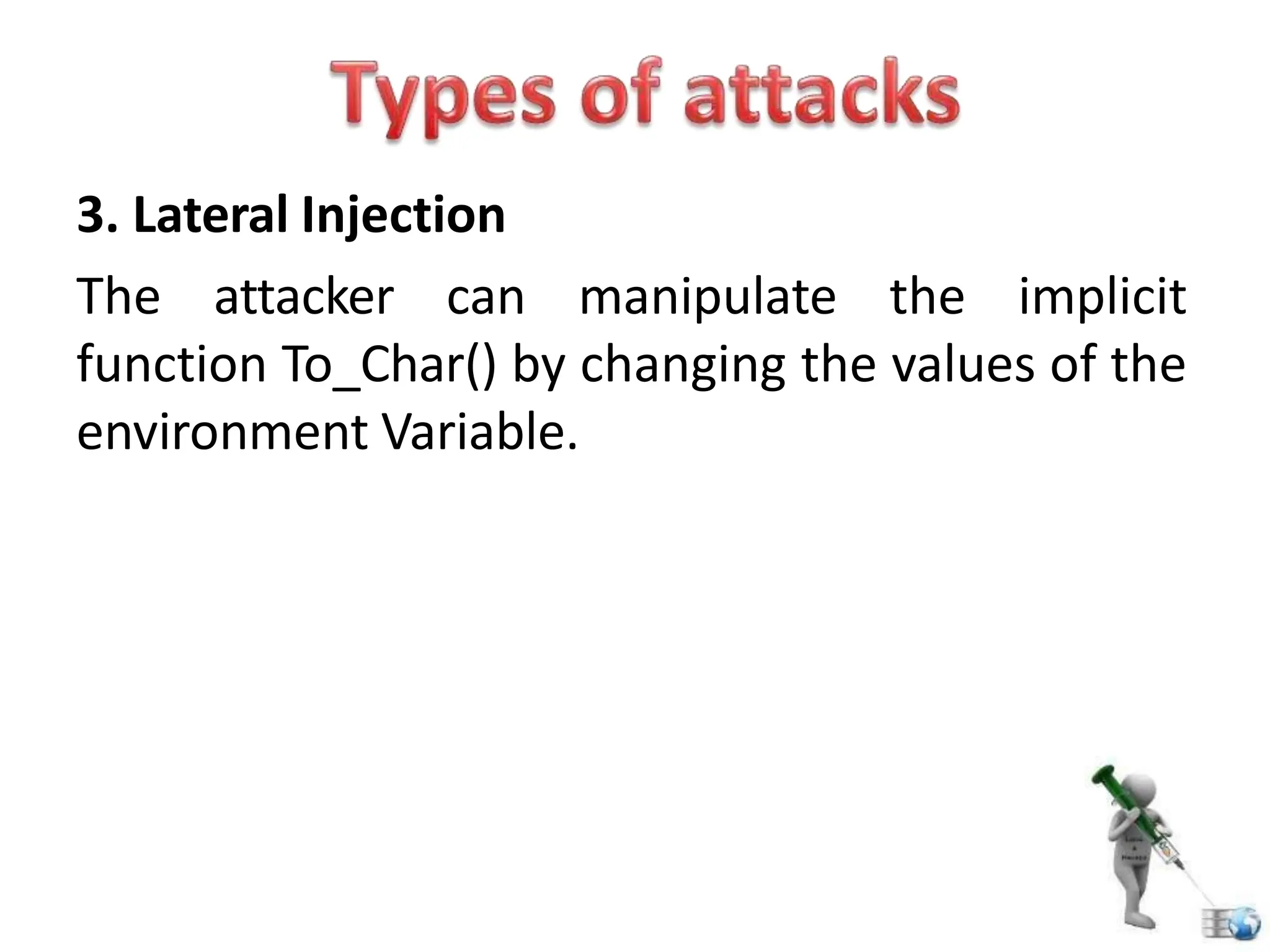
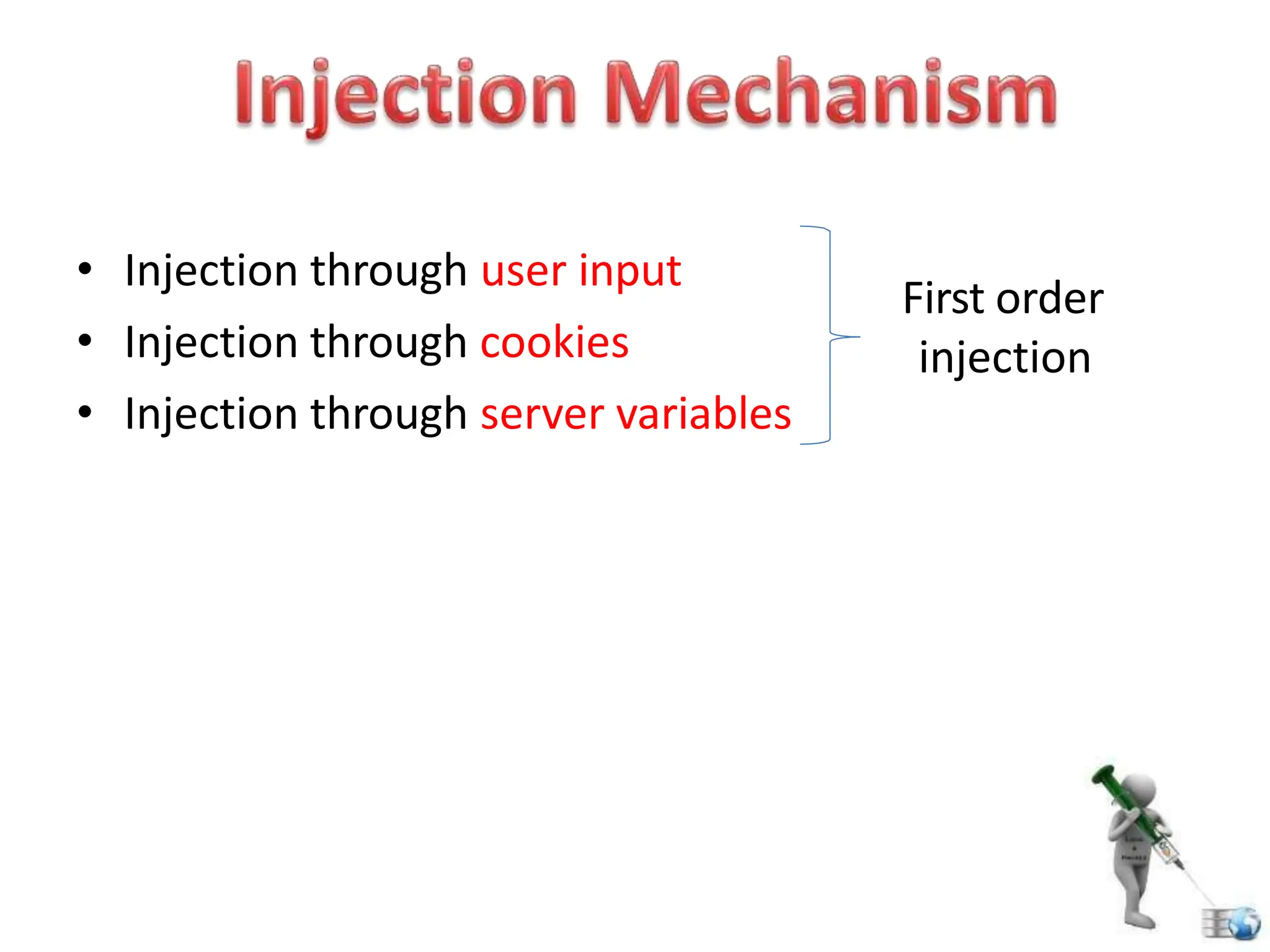
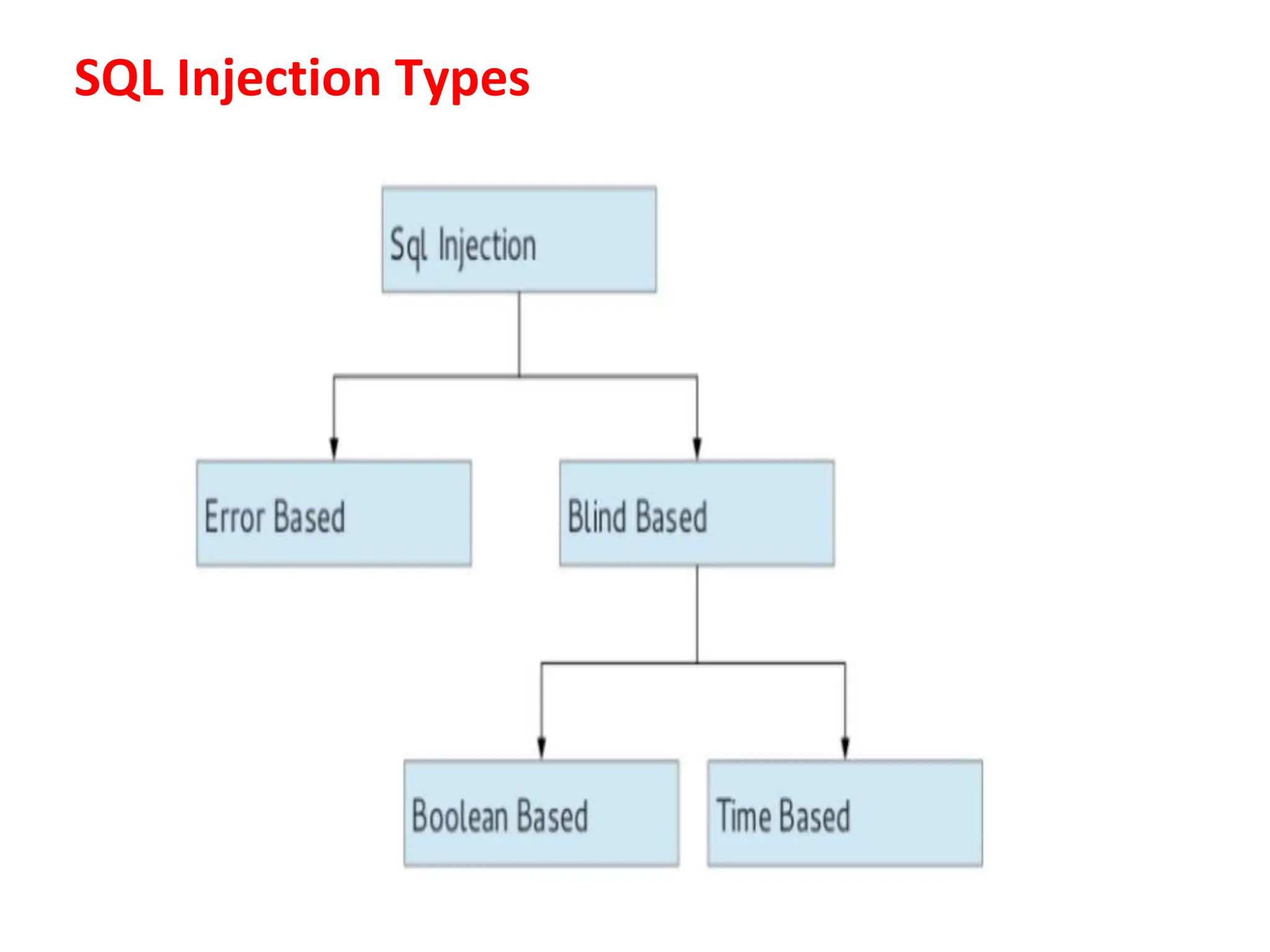
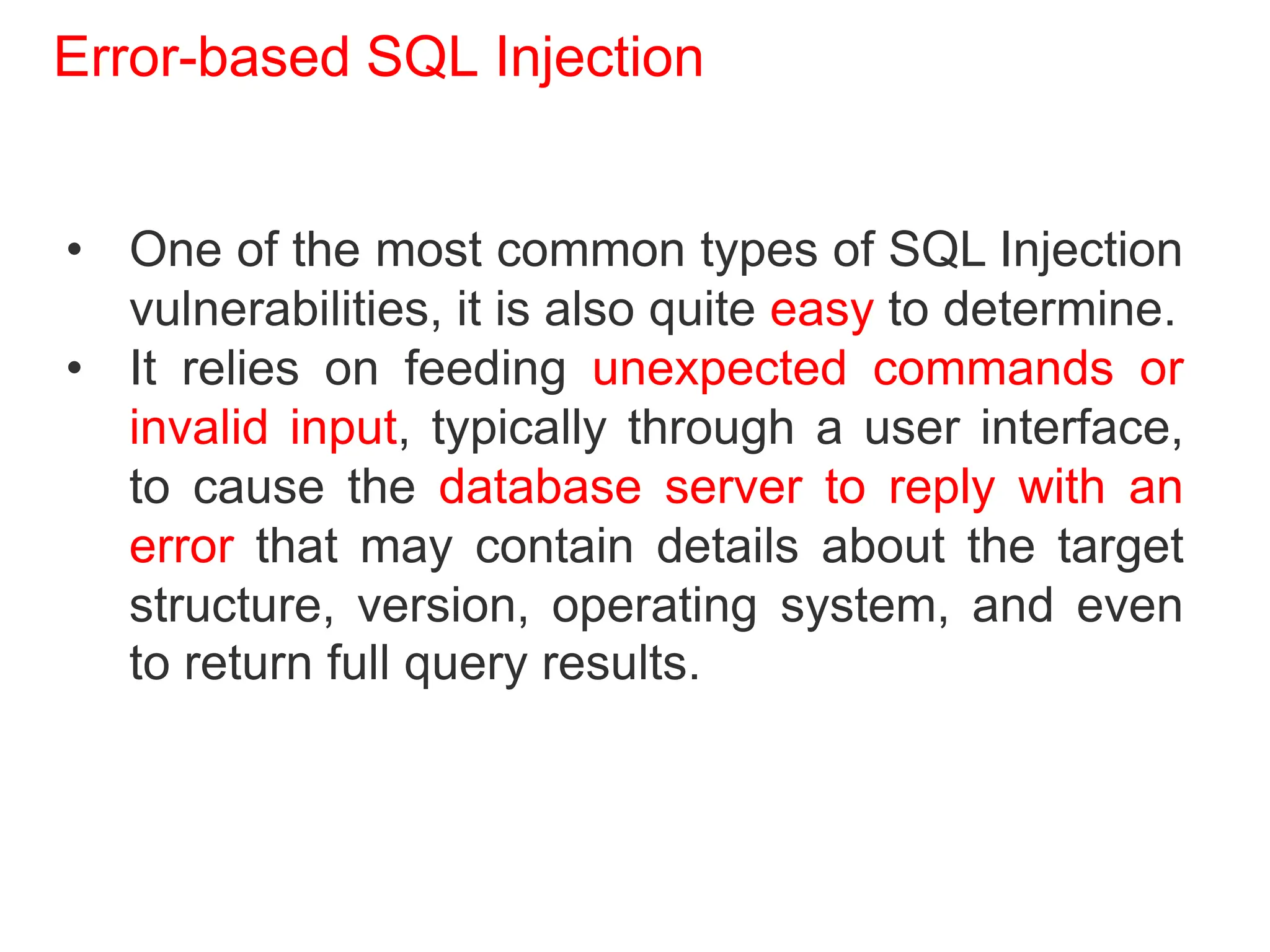
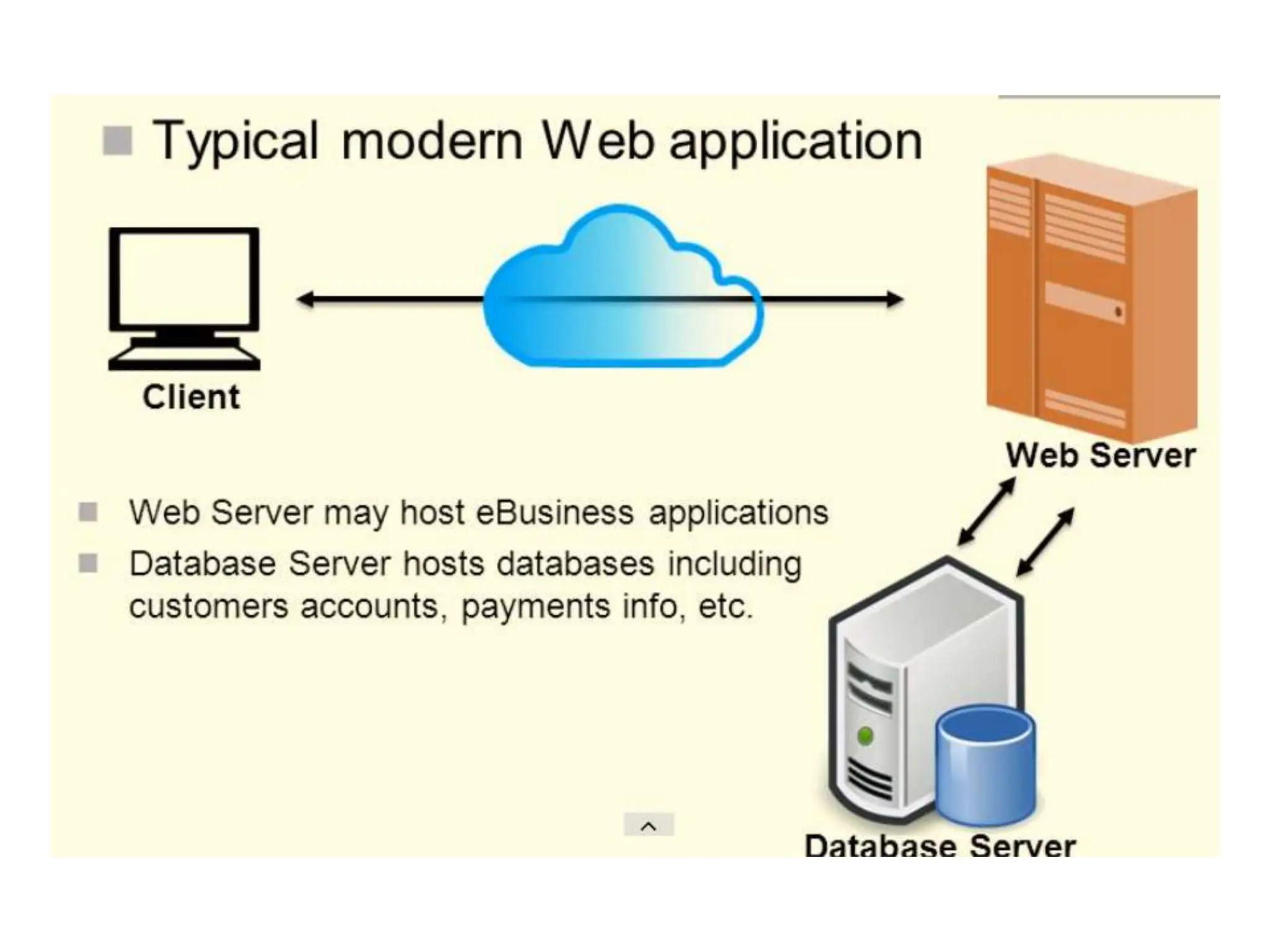
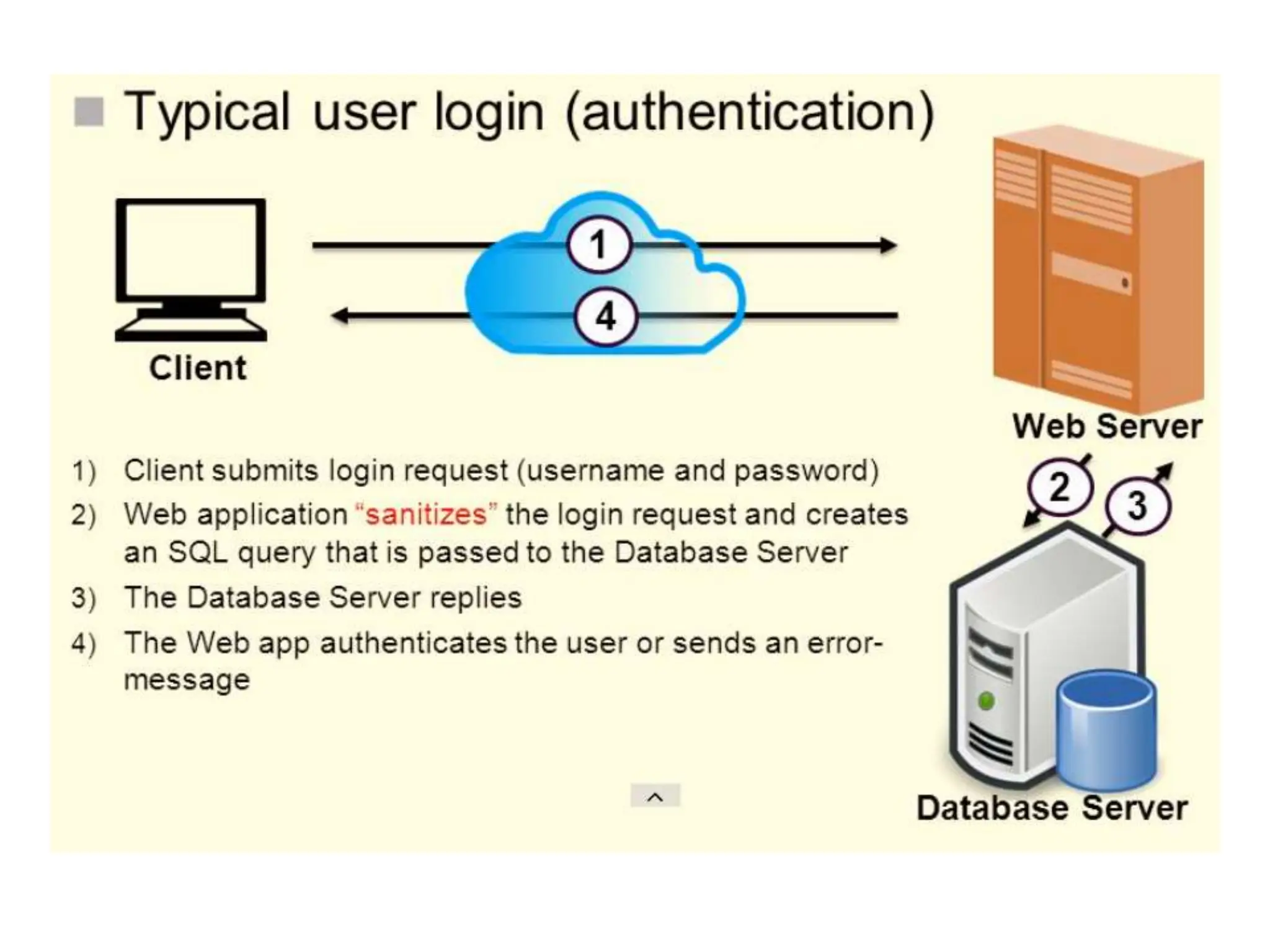
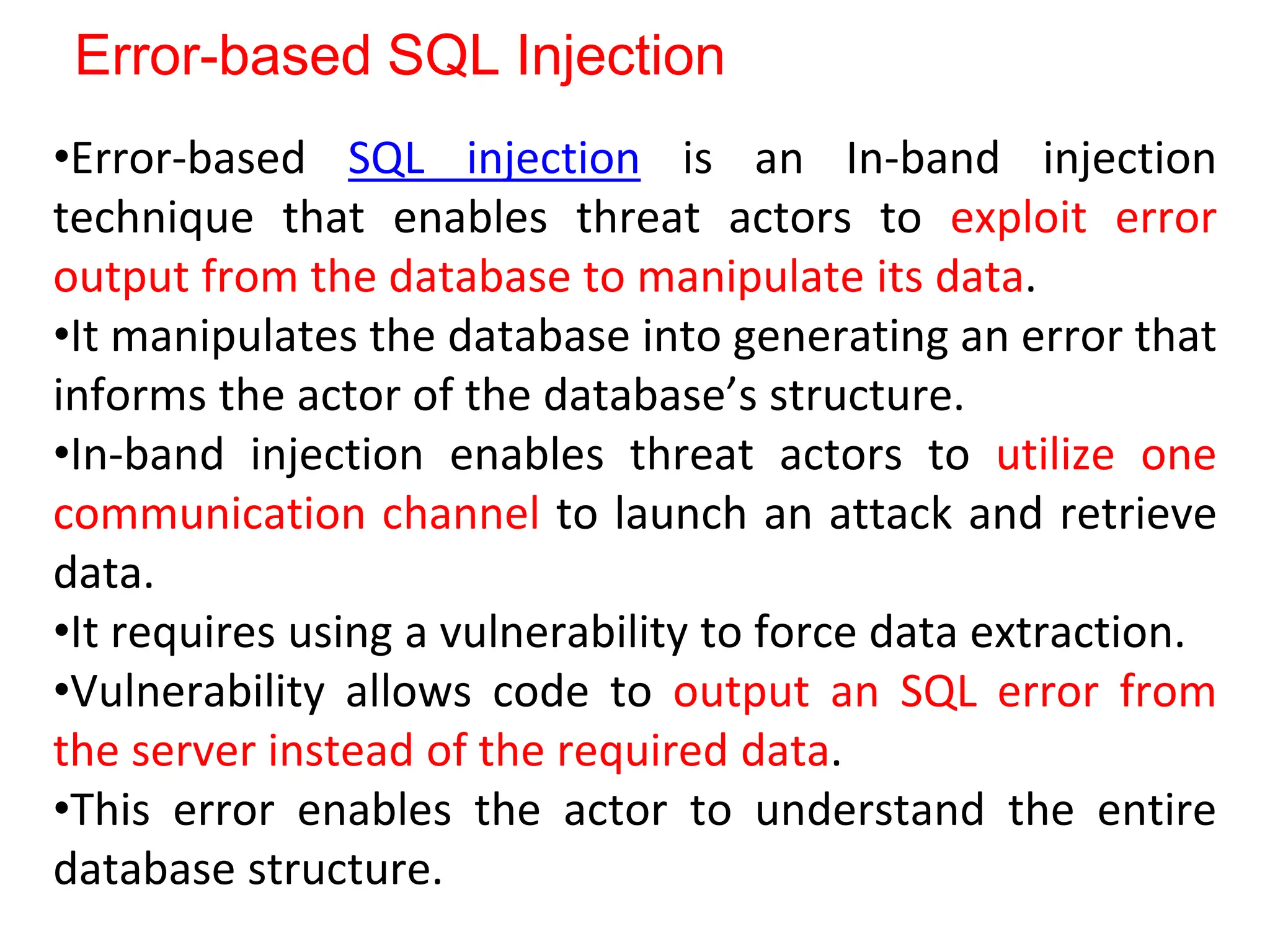
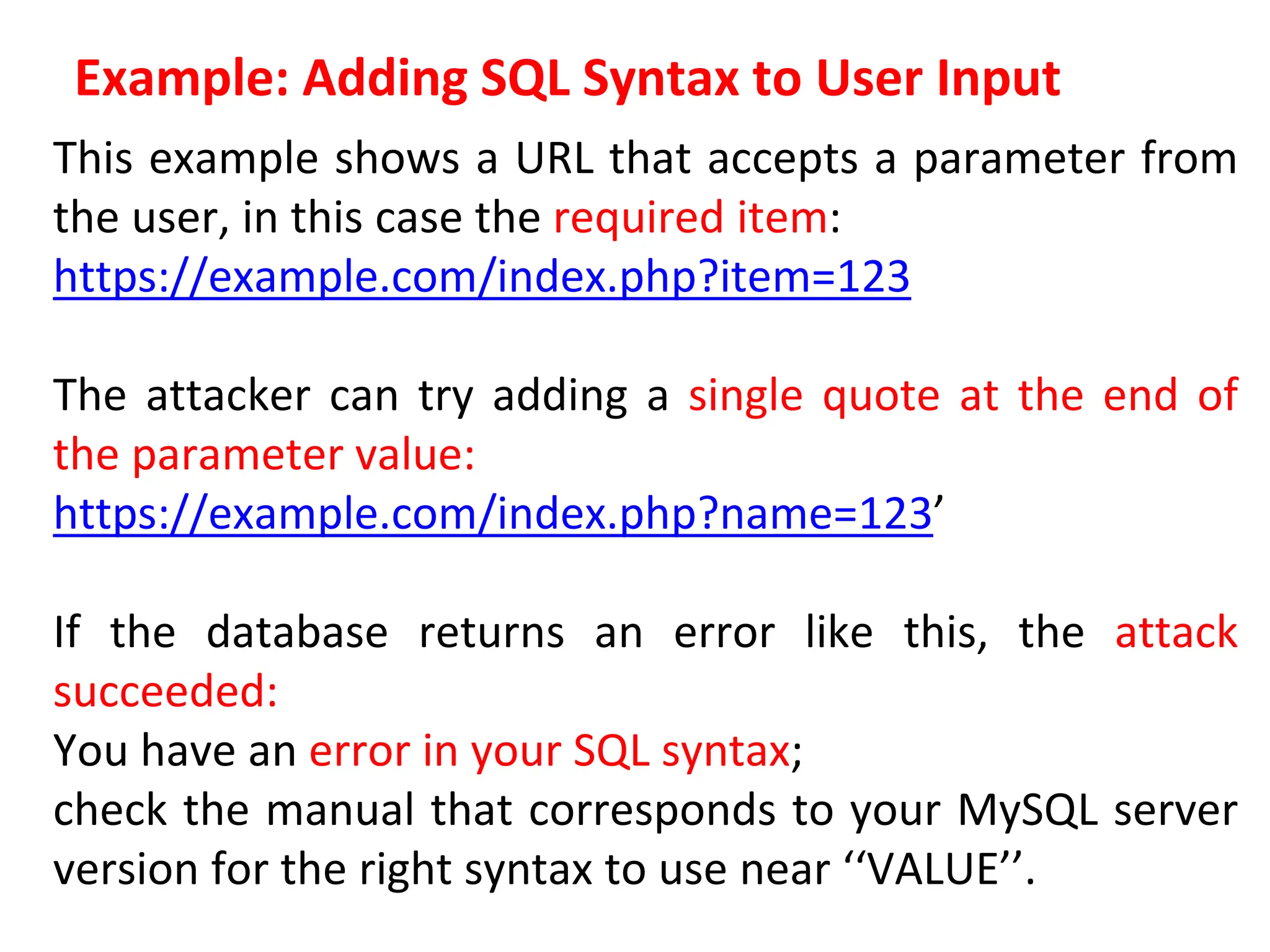
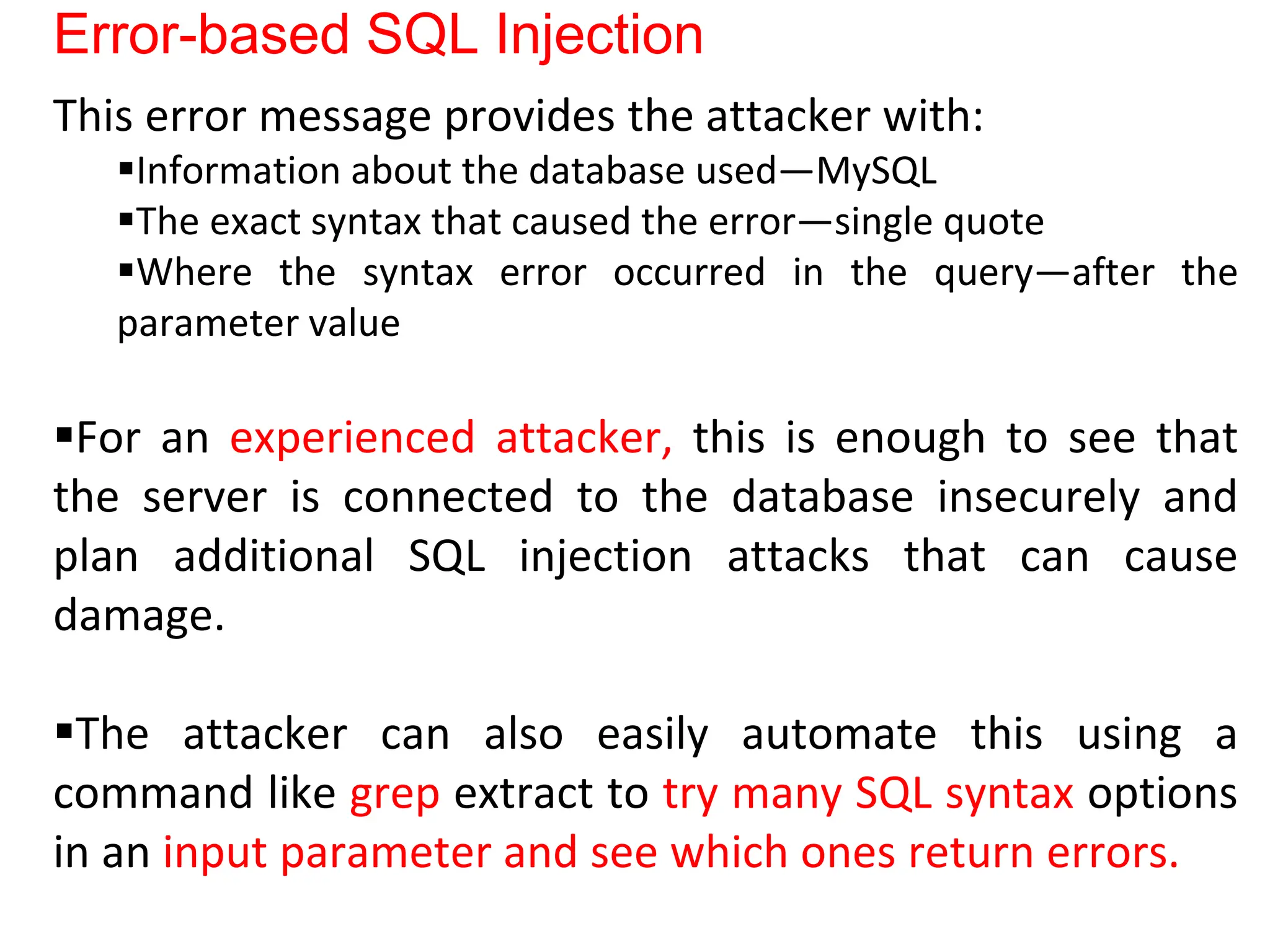
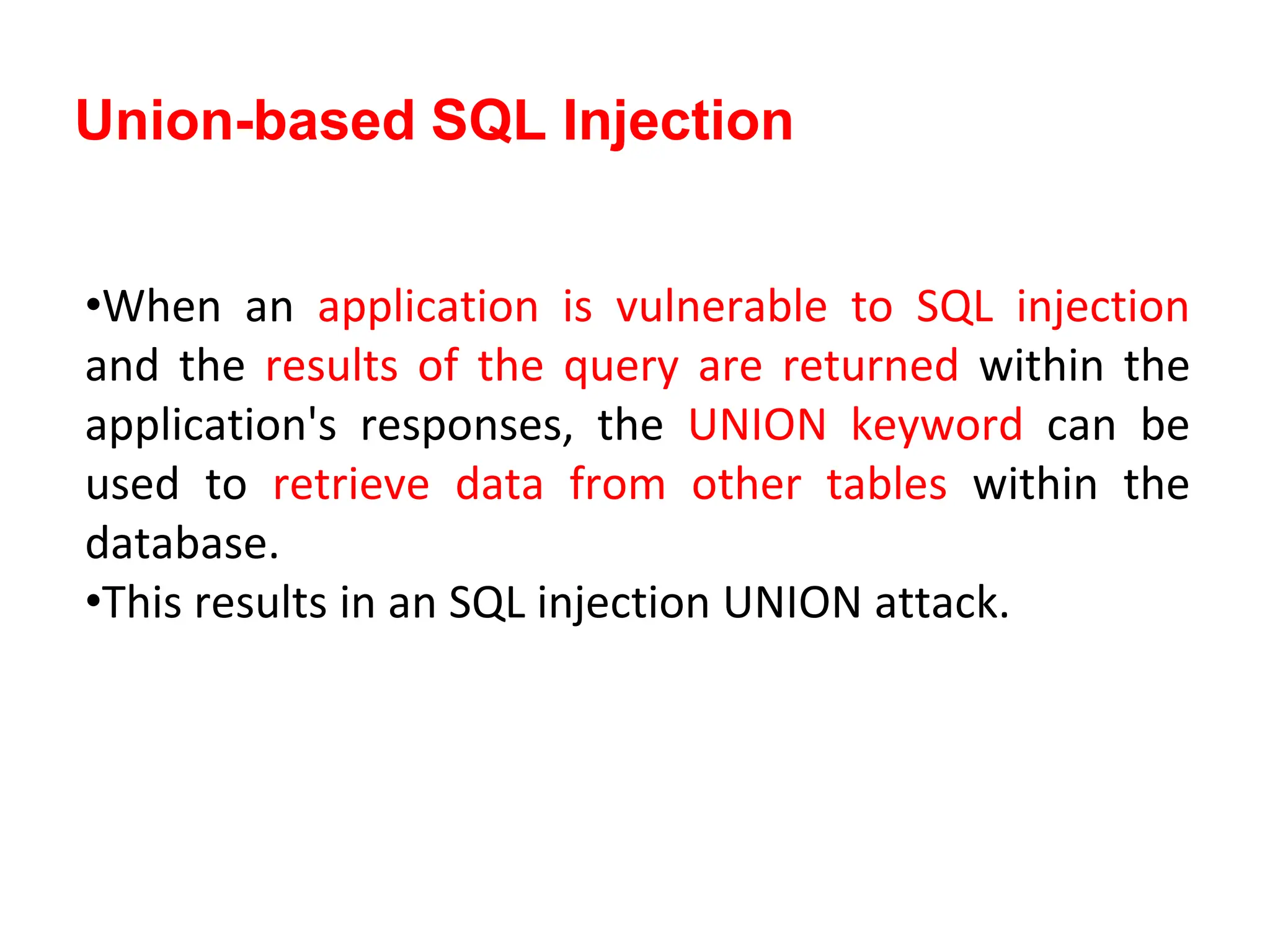
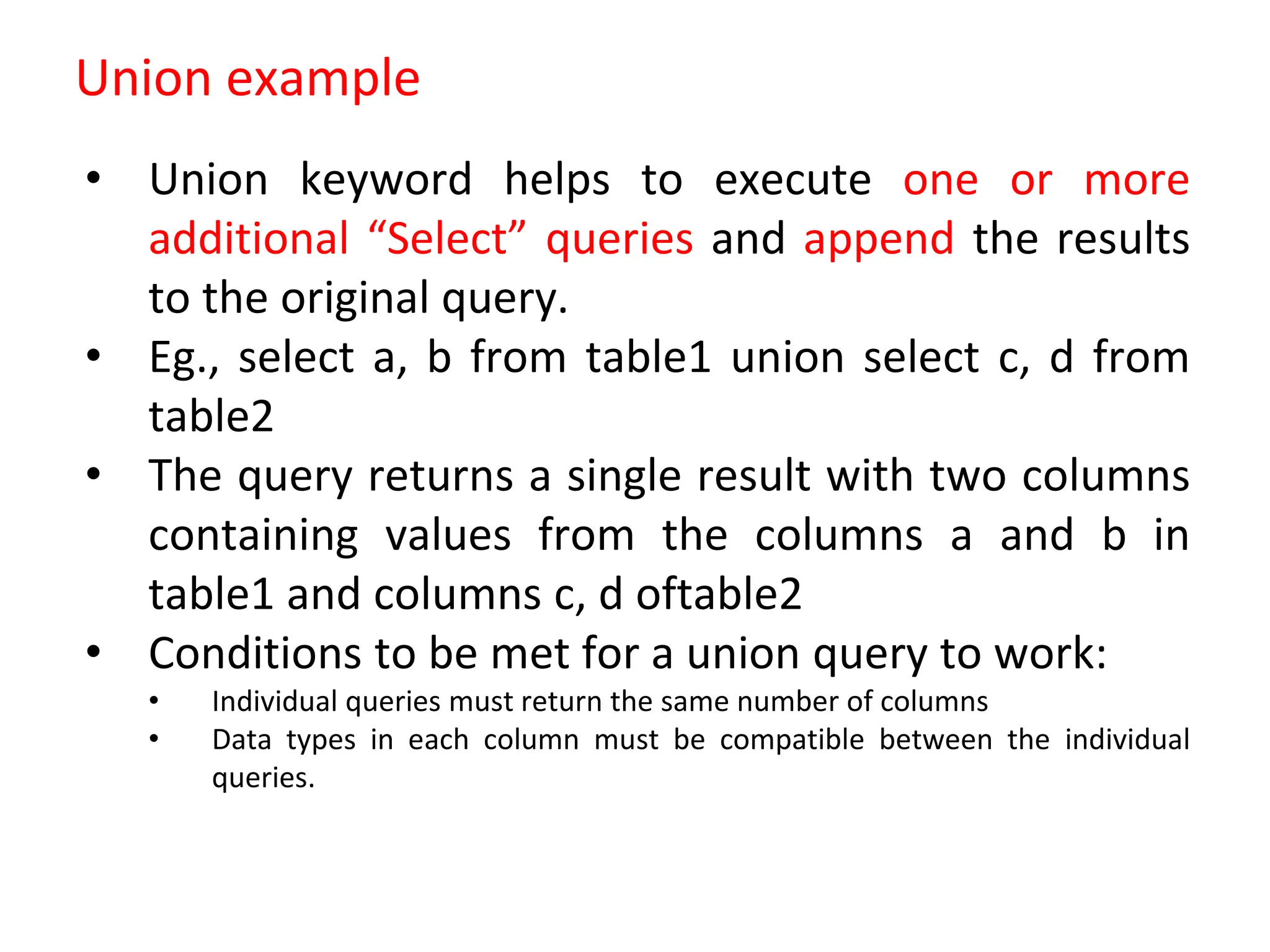
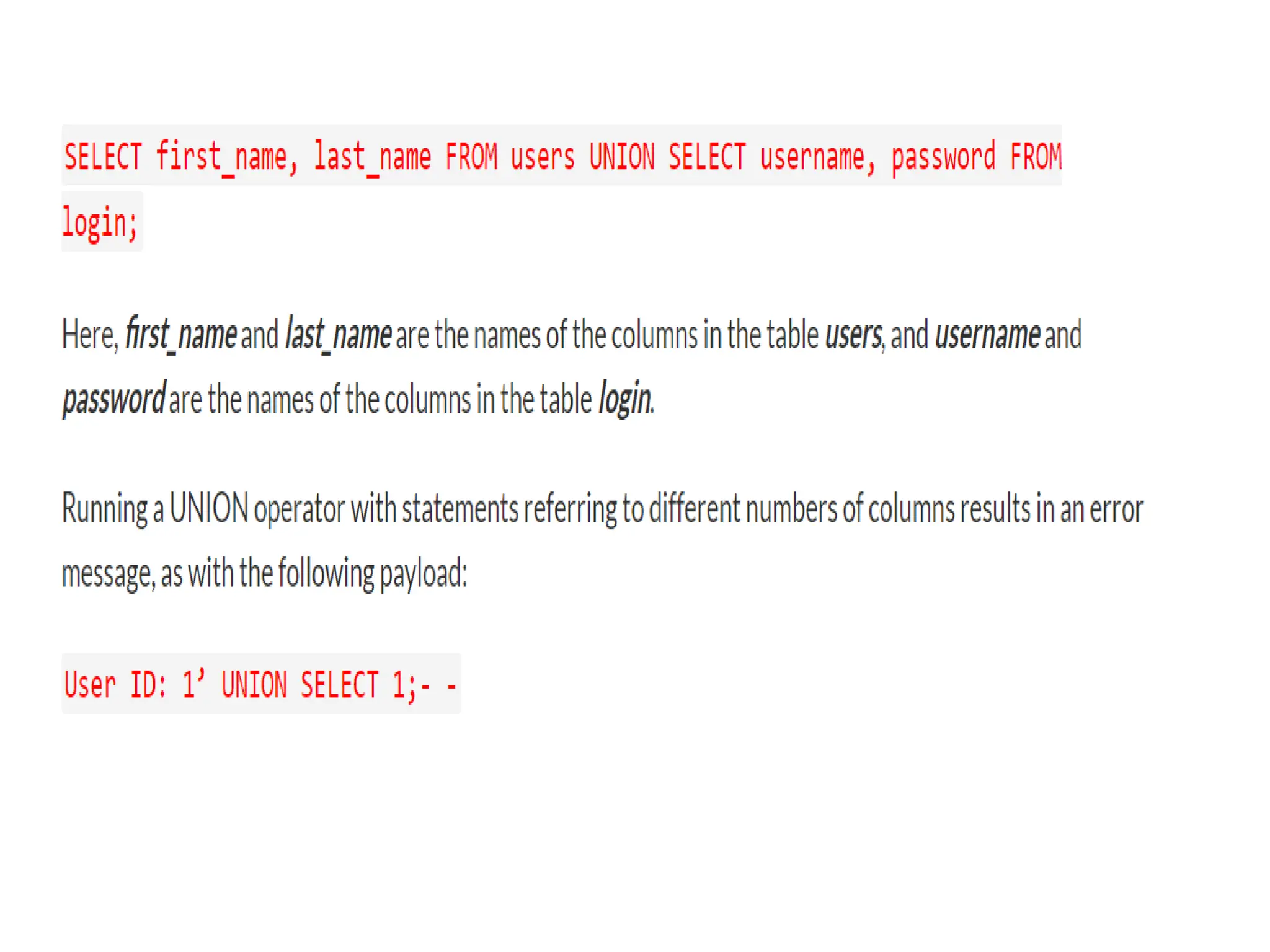
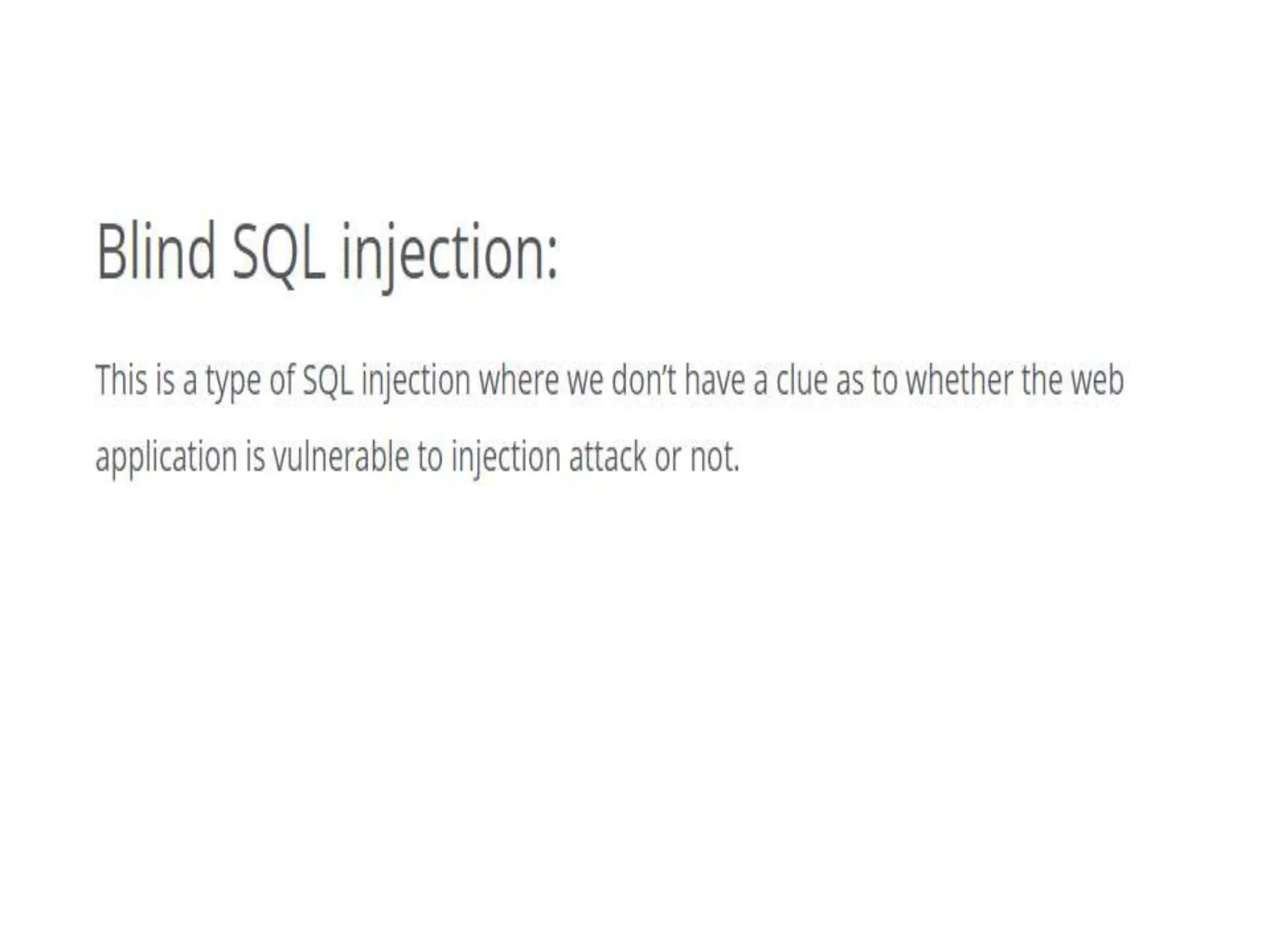
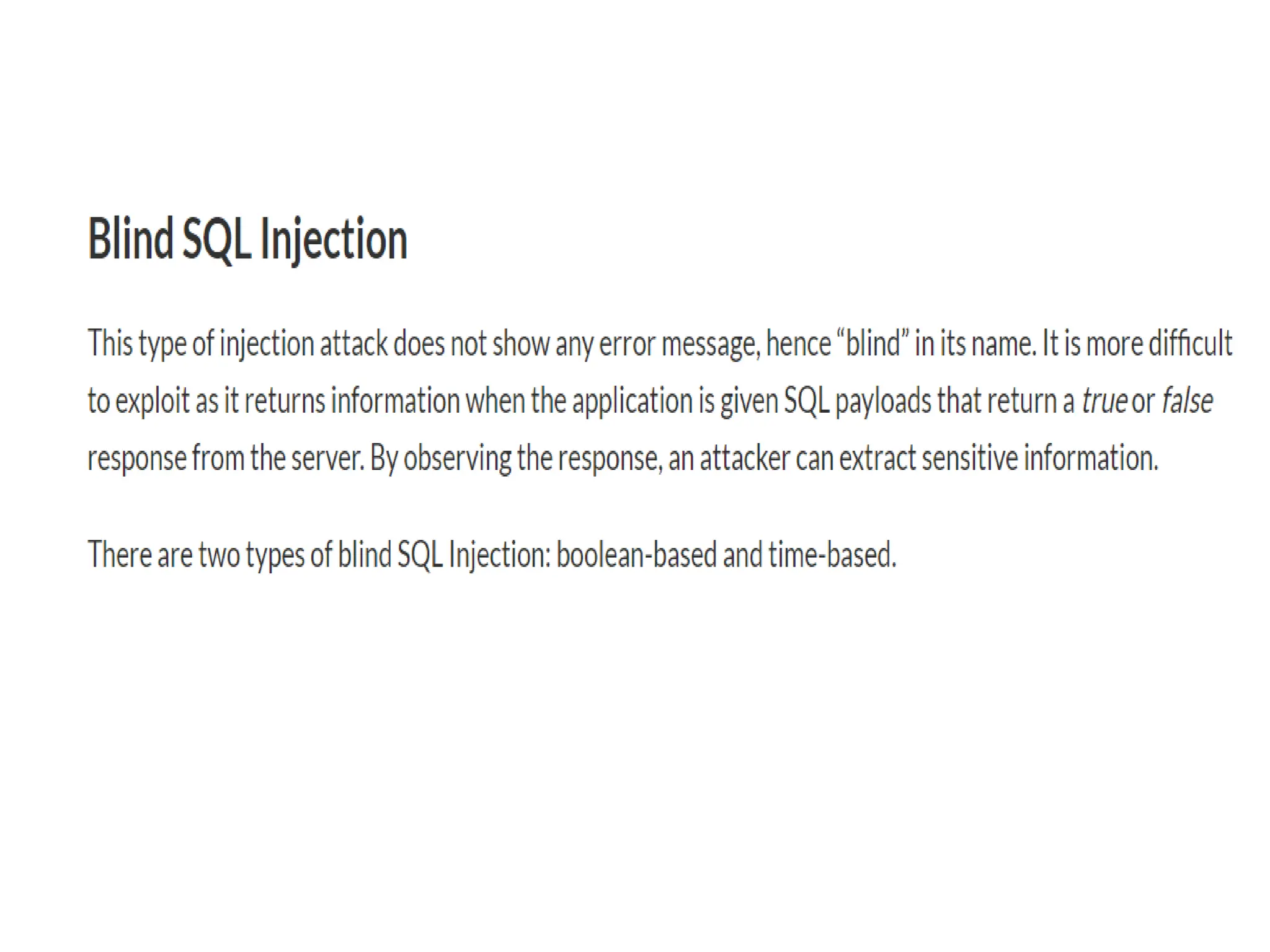
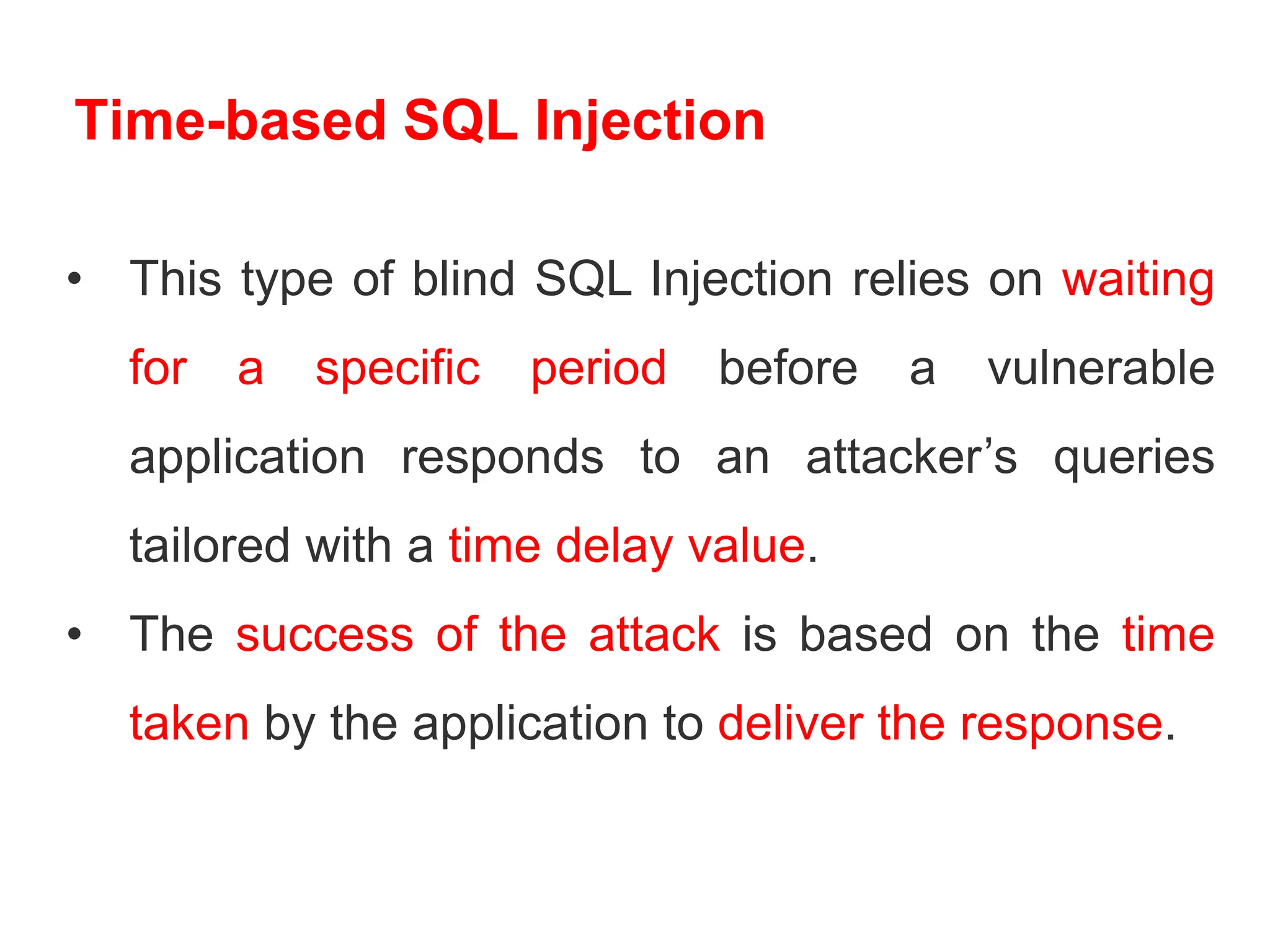
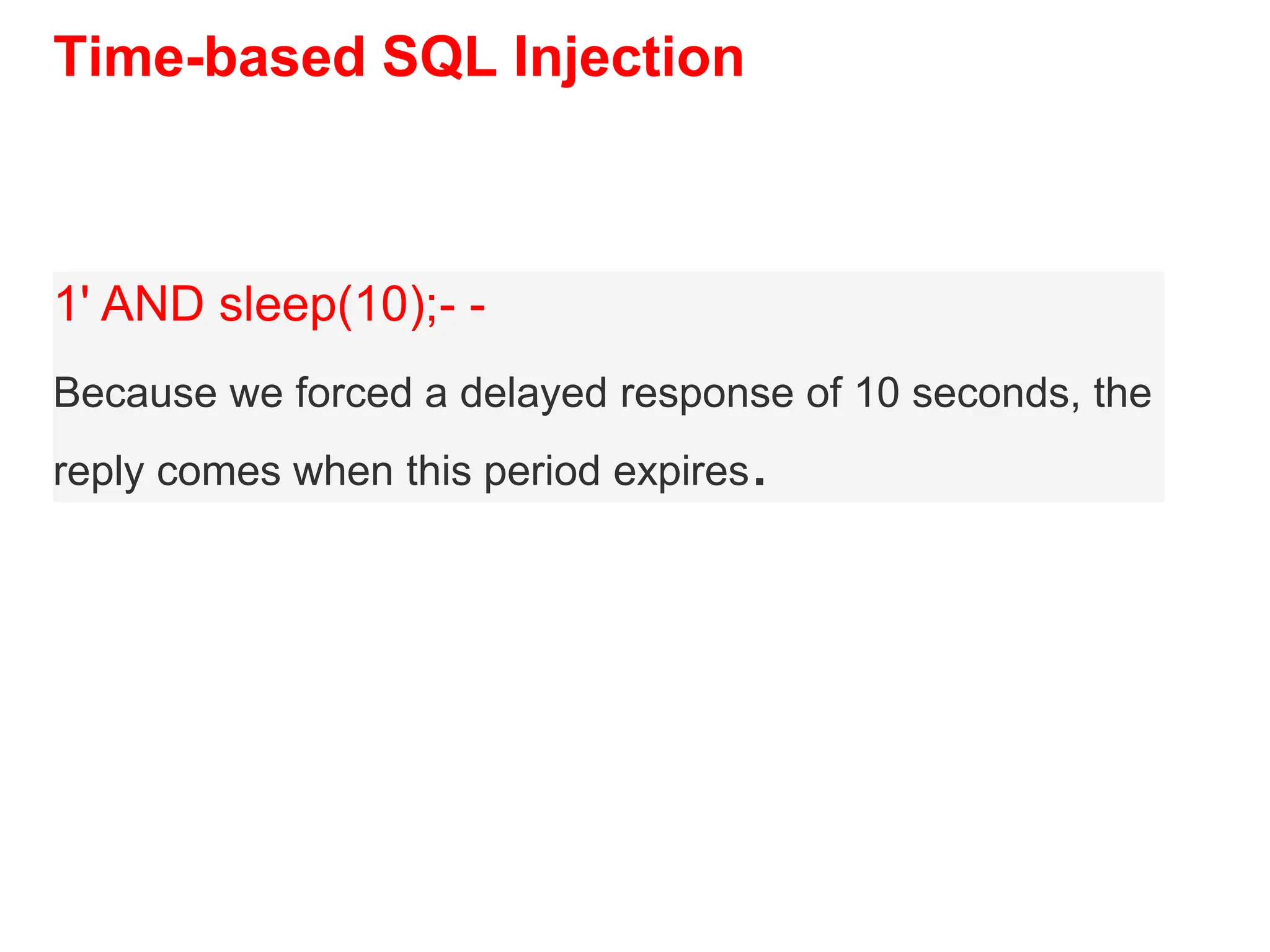
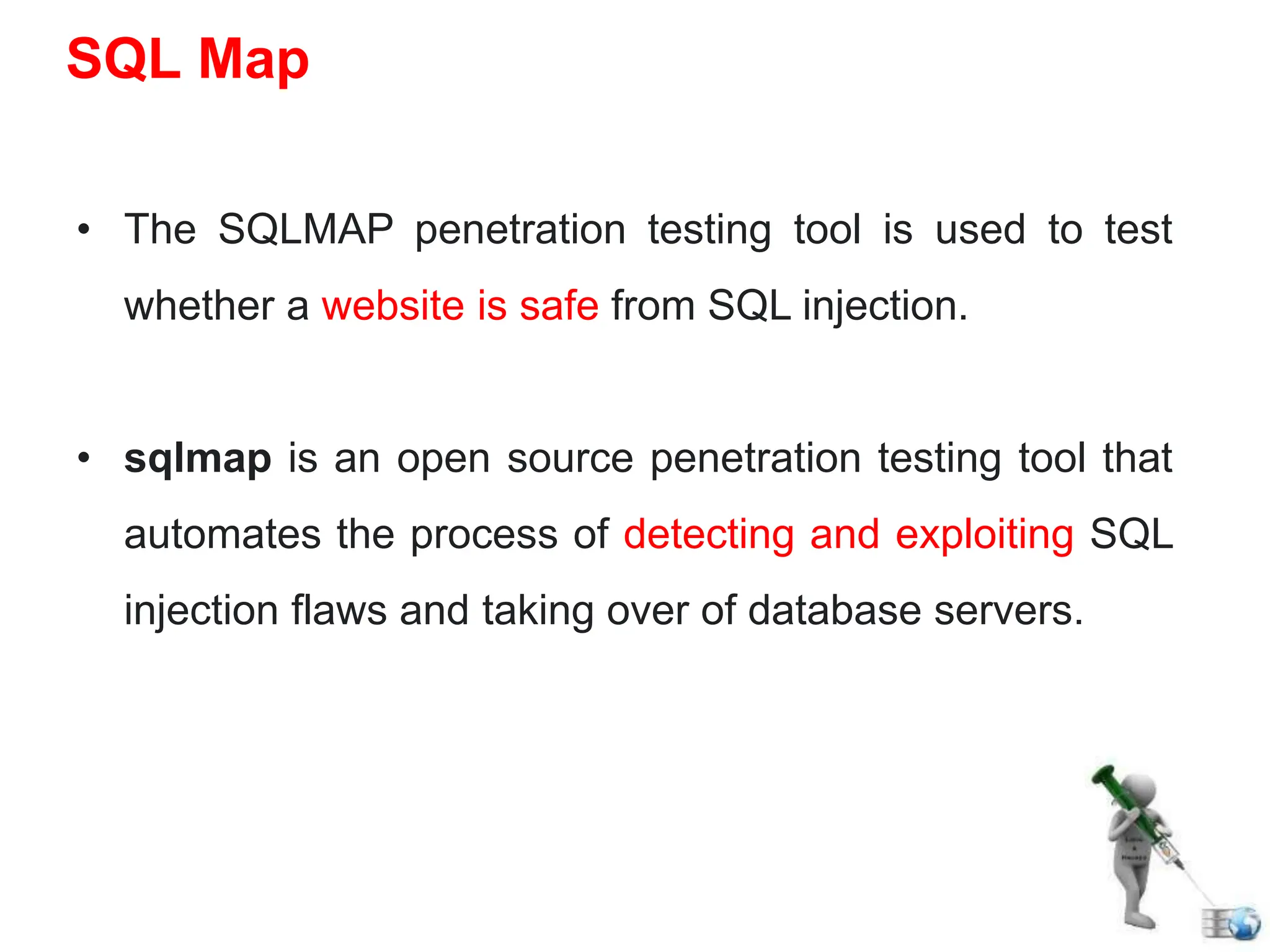
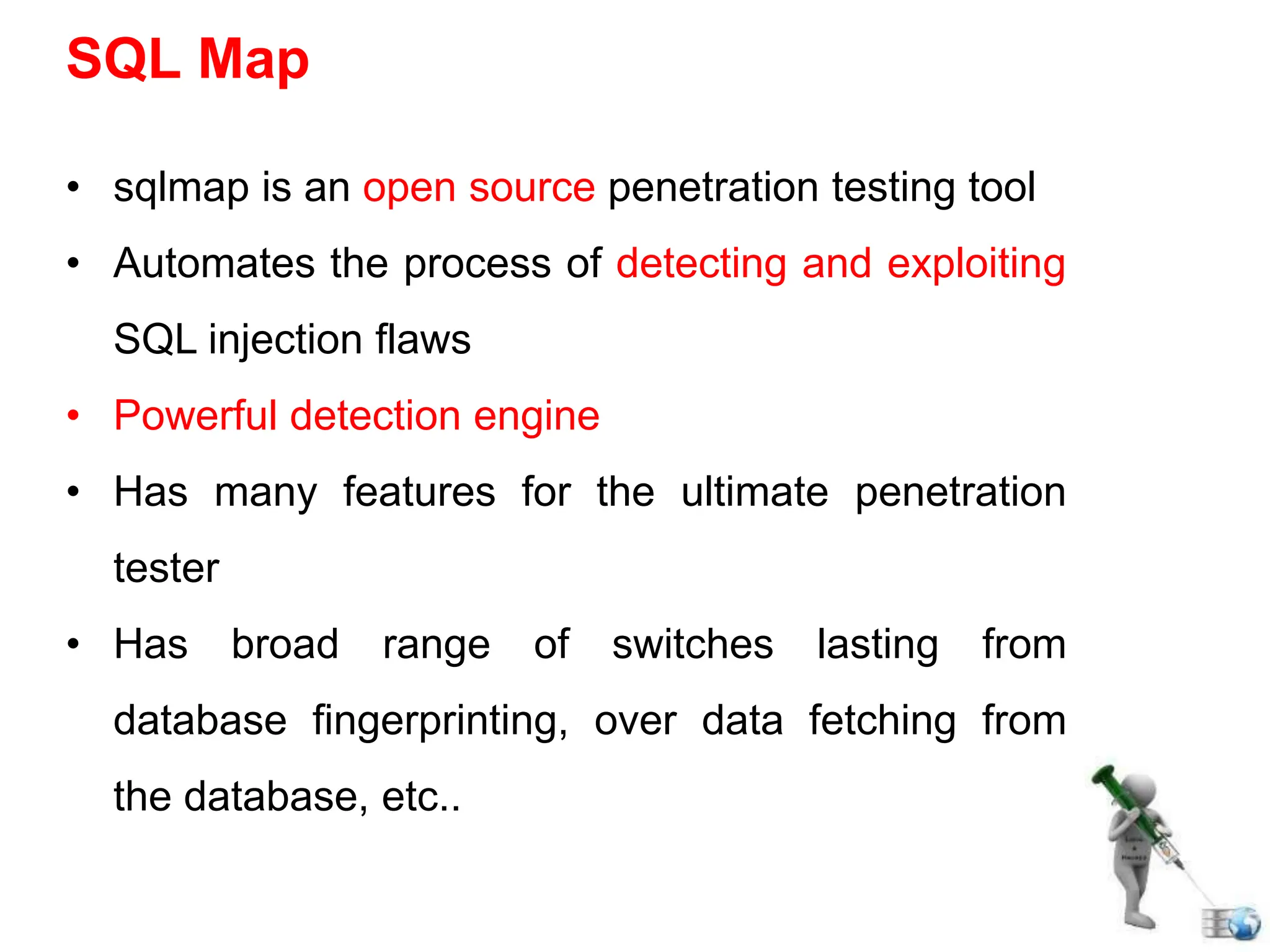
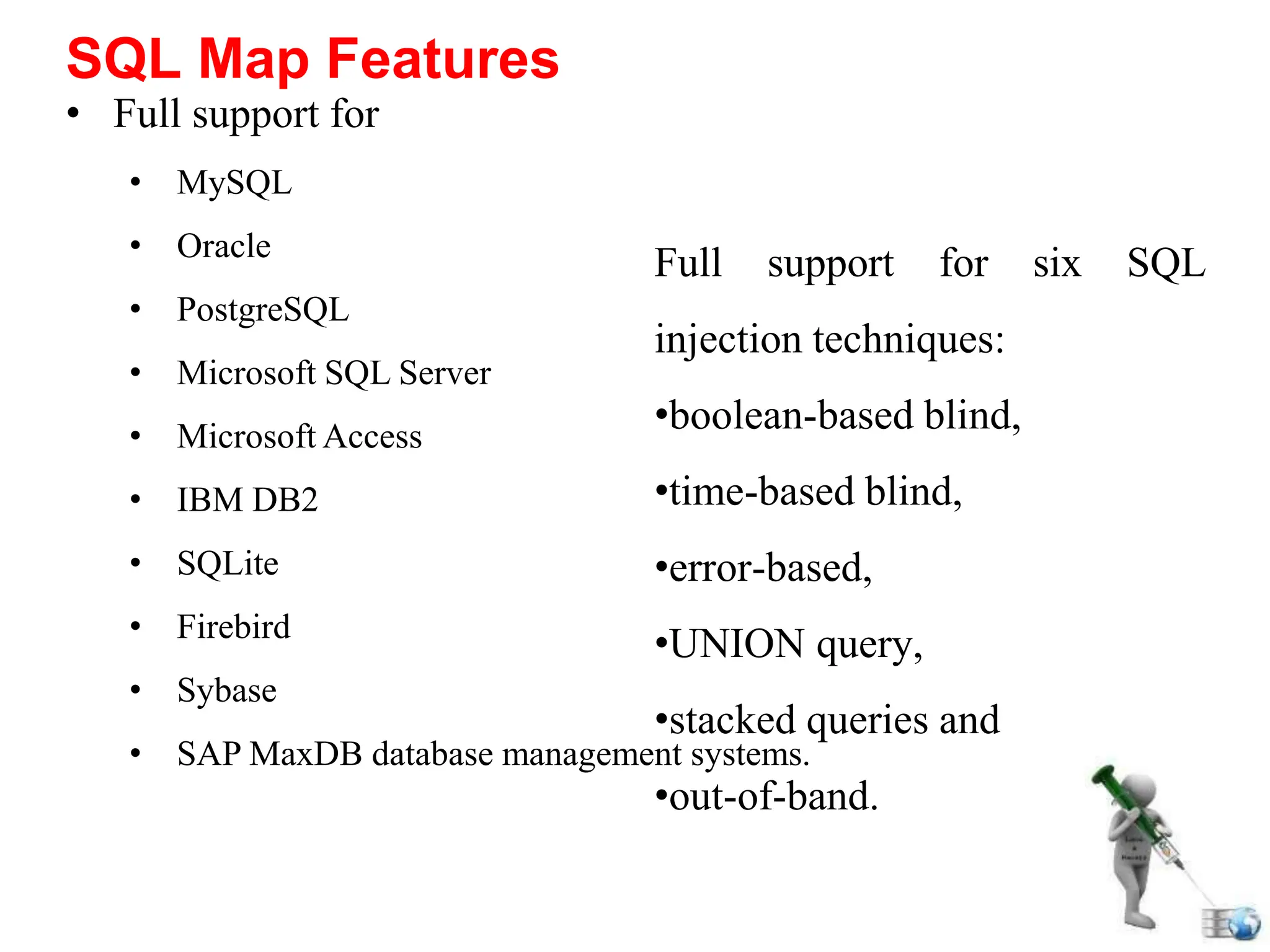
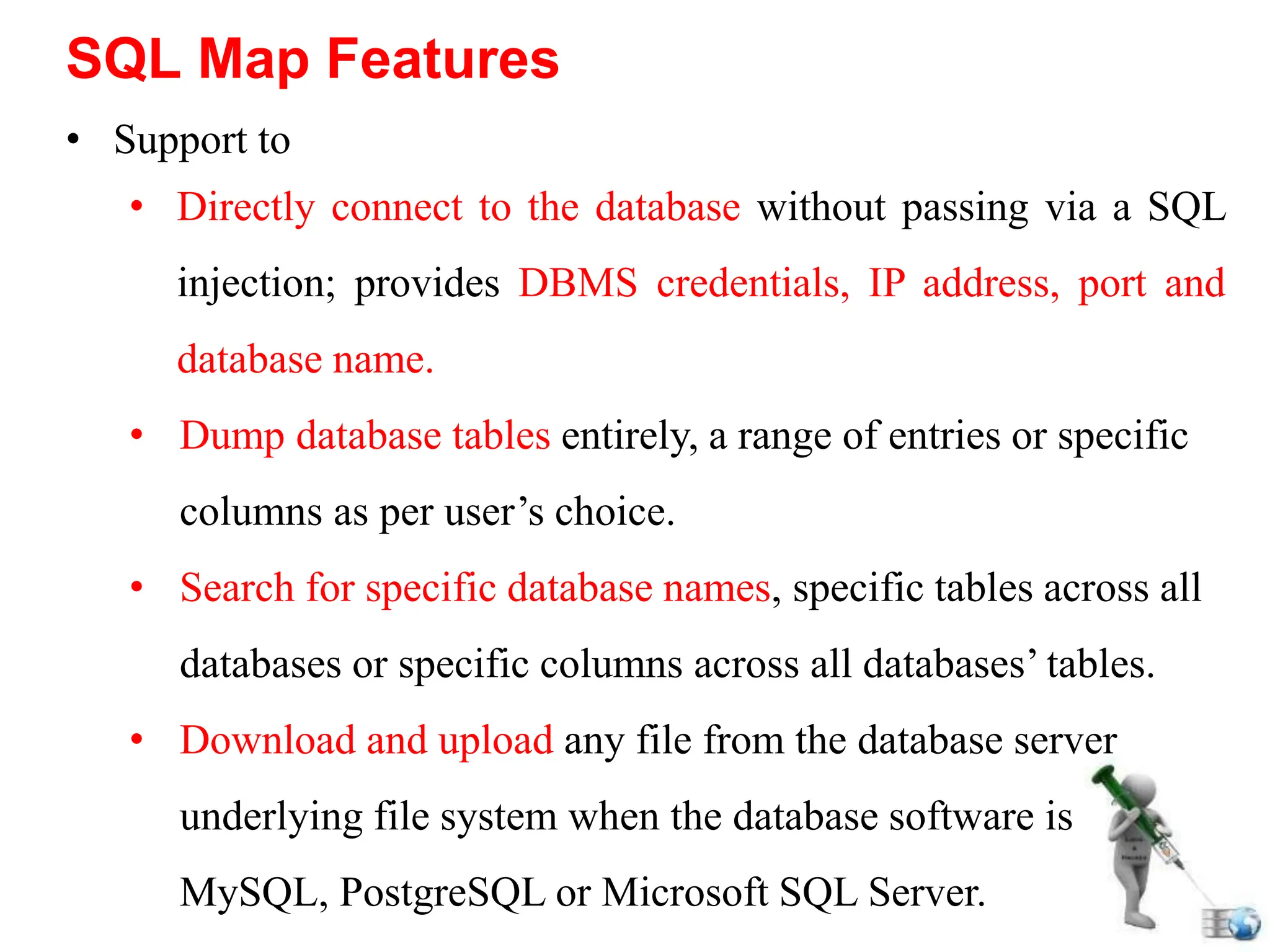
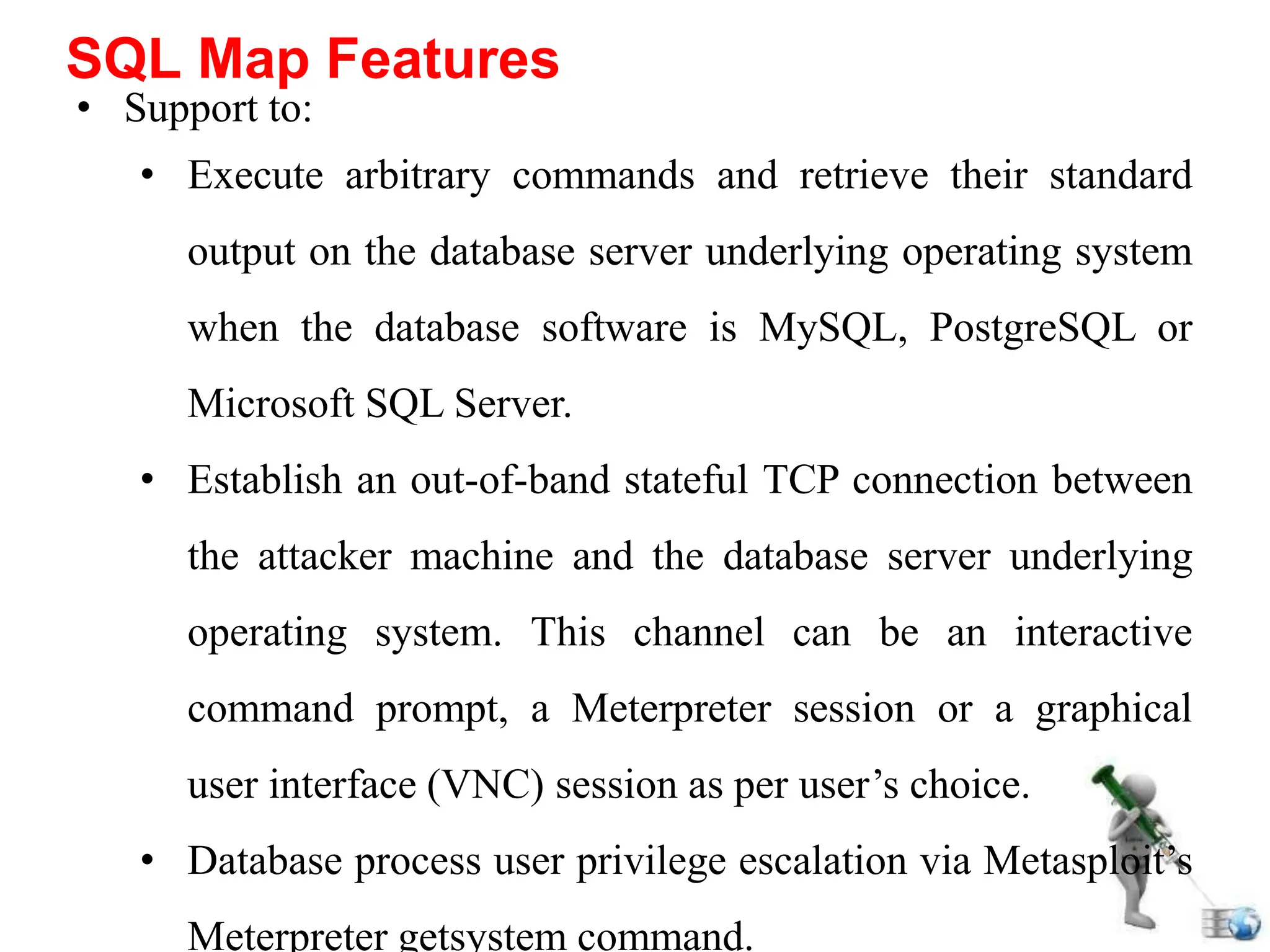
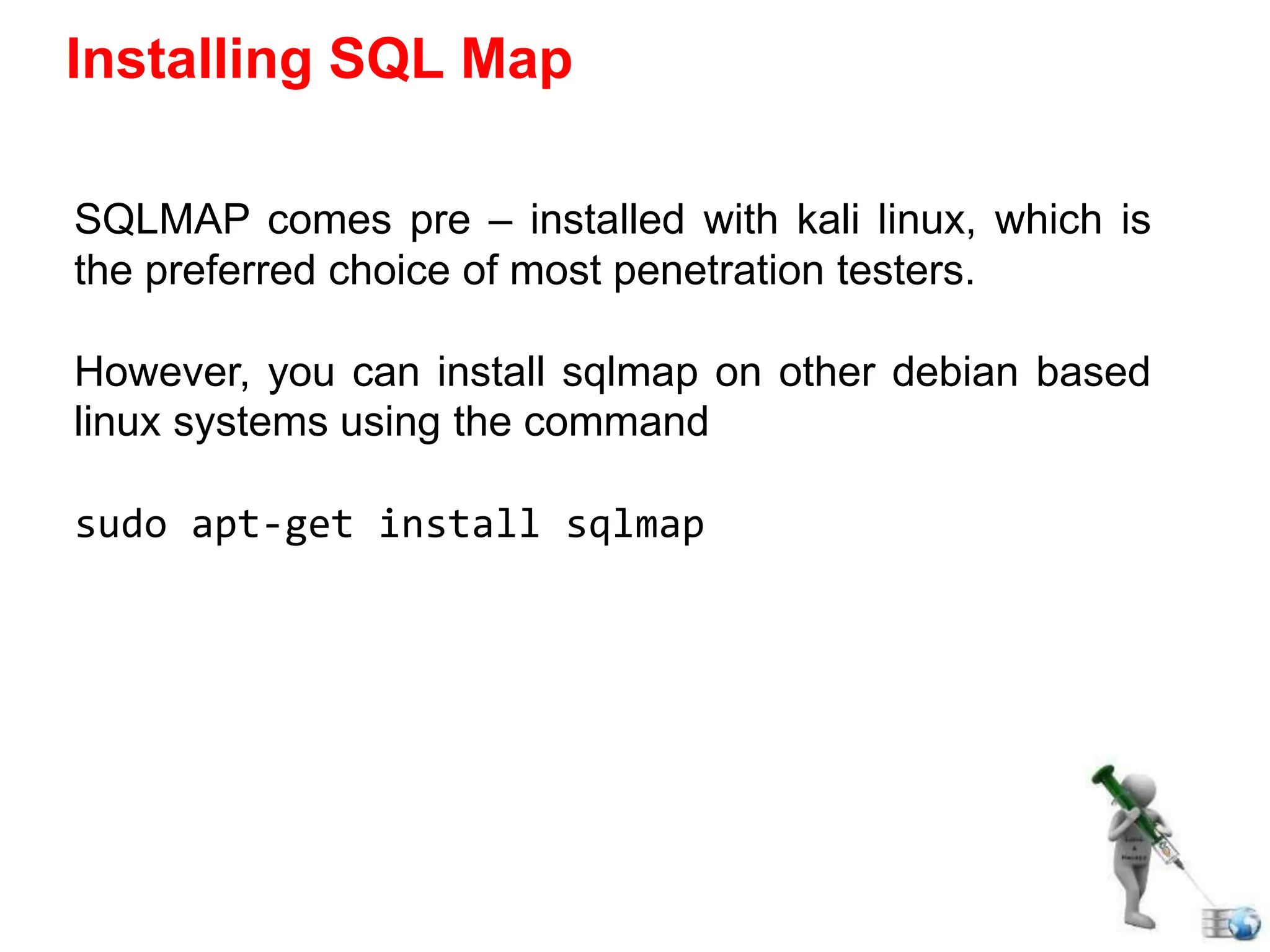
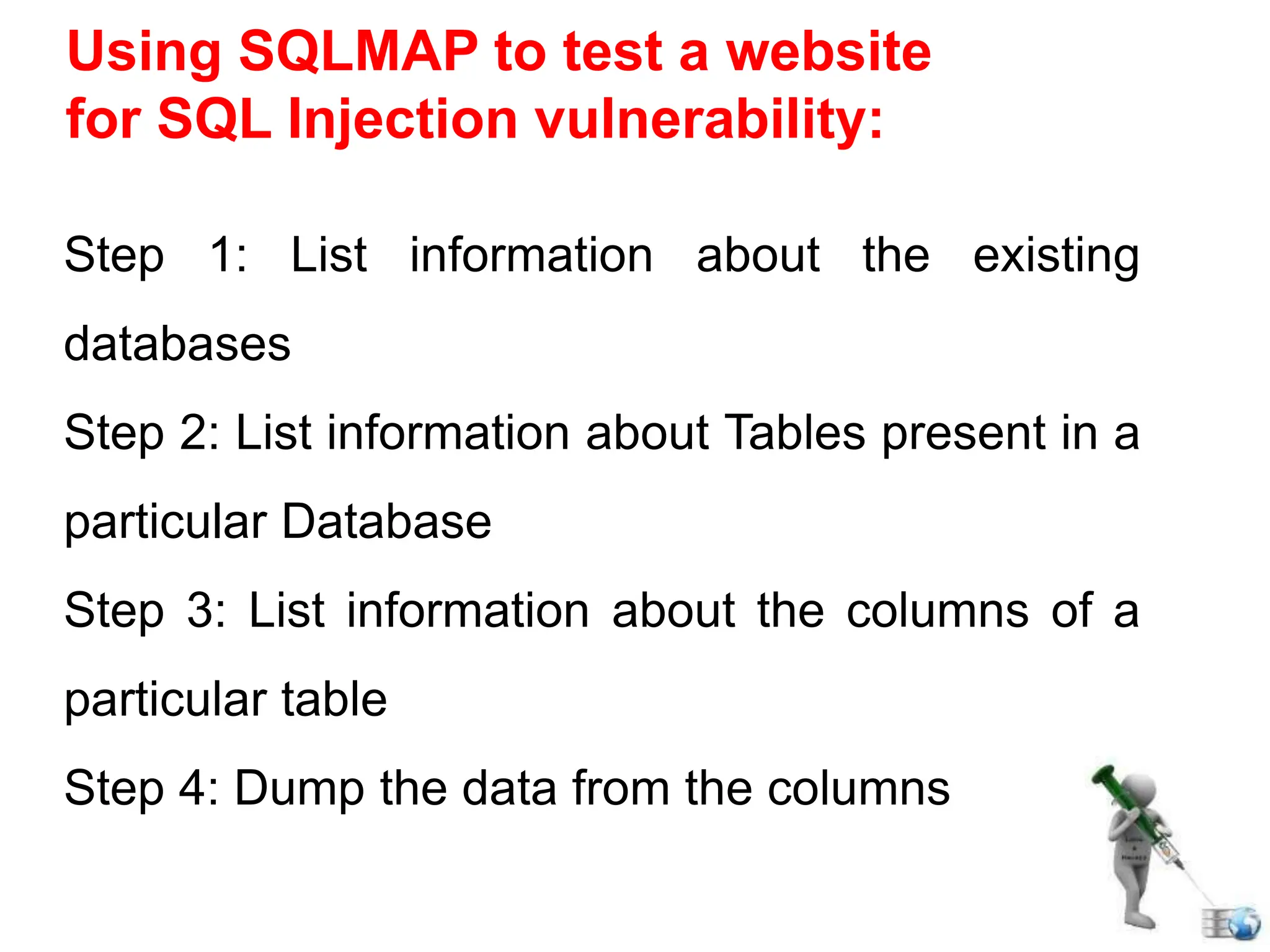
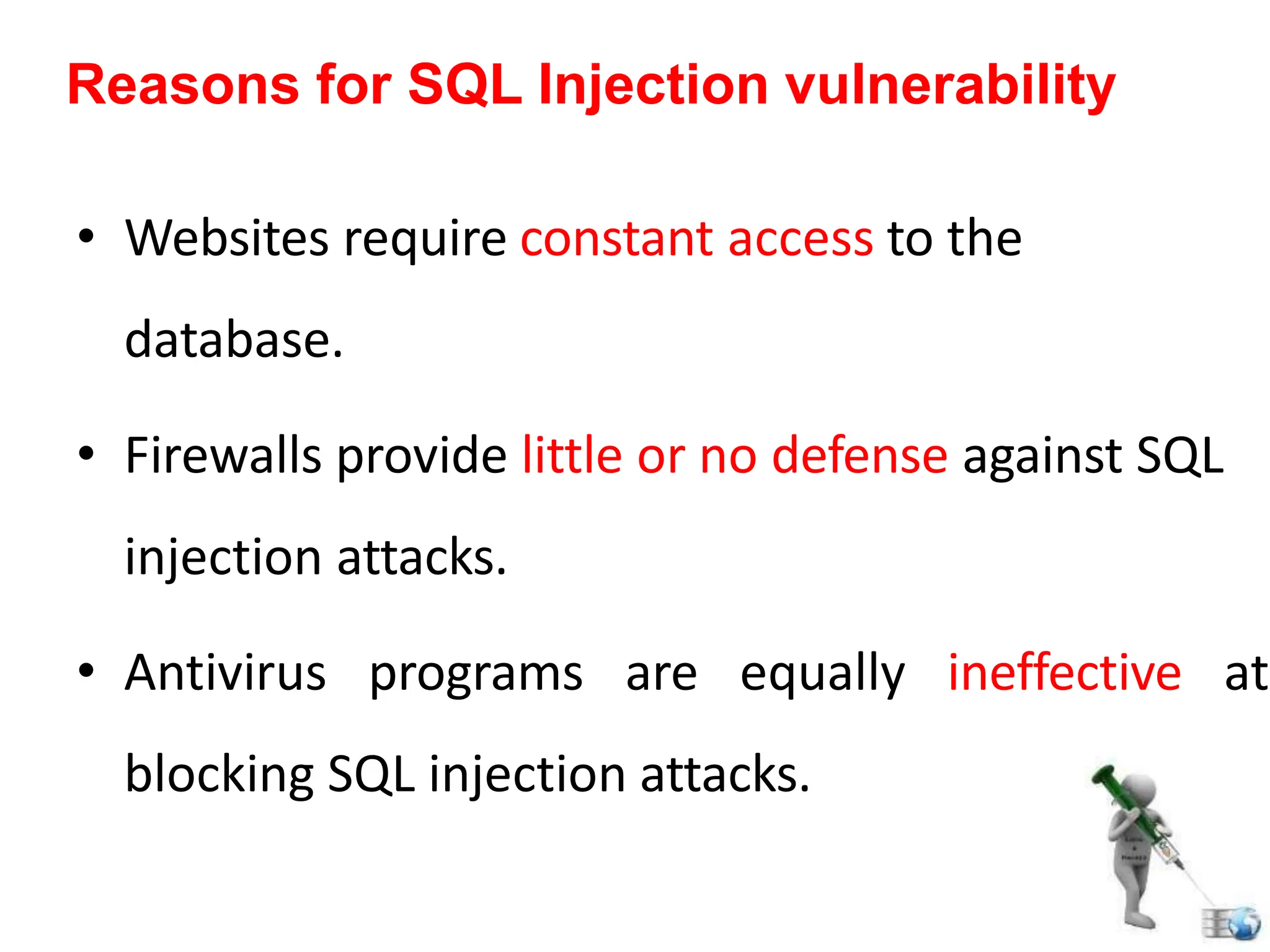
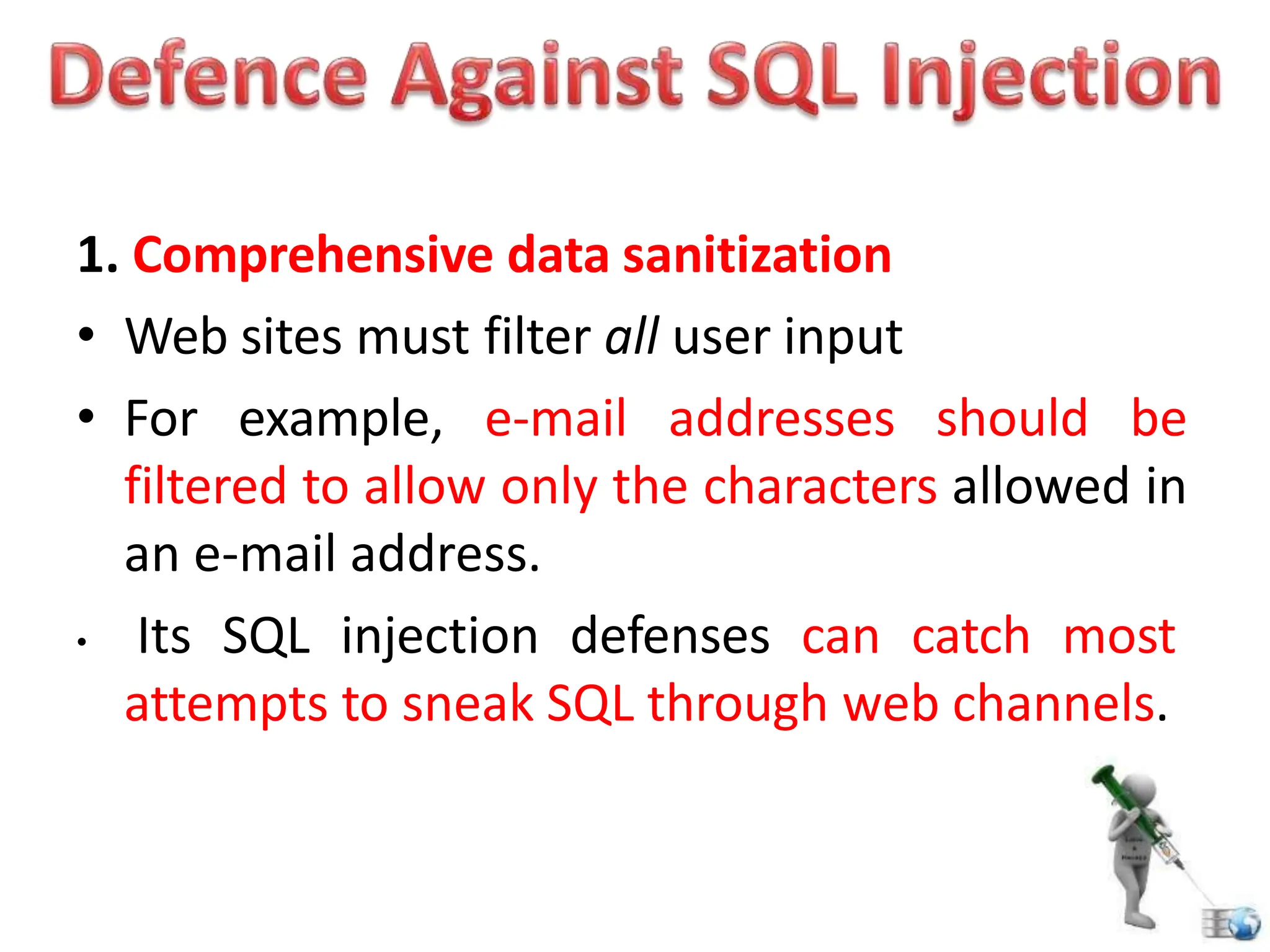
SQL injection is a code injection technique used to exploit vulnerabilities in data-driven applications by inserting malicious SQL statements. This technique allows attackers to execute unauthorized actions such as extracting, modifying, or deleting data. Notable cases include the theft of 130 million credit card numbers in 2009 and widespread attacks on Microsoft's SQL server in 2008, highlighting the critical need for prevention measures like input validation and the use of web application firewalls.























![Text Steganography Methods
Text Steganography in Markup Languages[HTML]
Text Steganography in Specific characters in words
Line shifting Method
Word shifting
Open spaces
Semantic methods
Character Encoding](https://image.slidesharecdn.com/sqlinjection-stegnography-1-240621183803-80c17f63/75/SQL-Injection-Stegnography-in-Pen-Testing-69-2048.jpg)