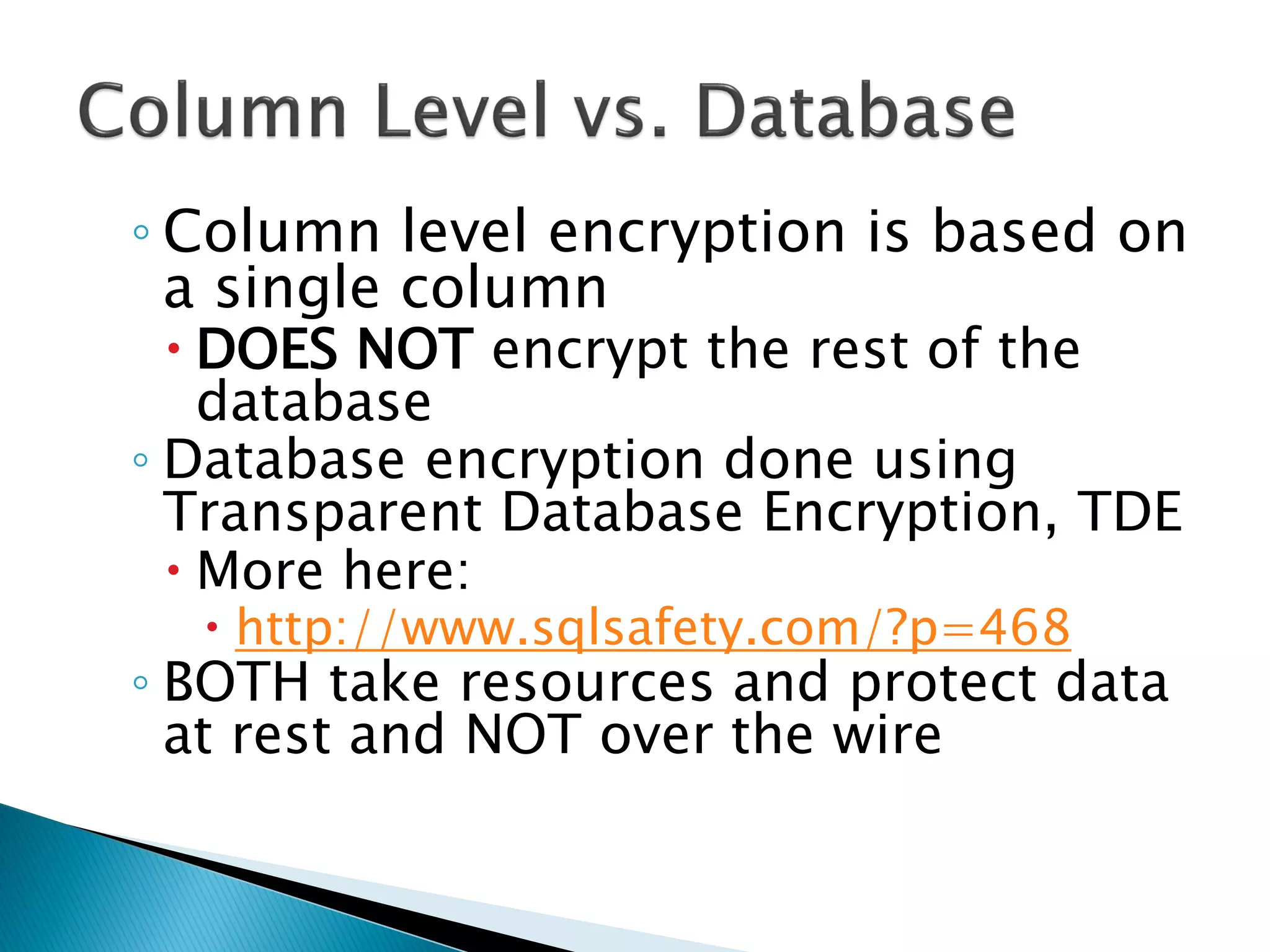
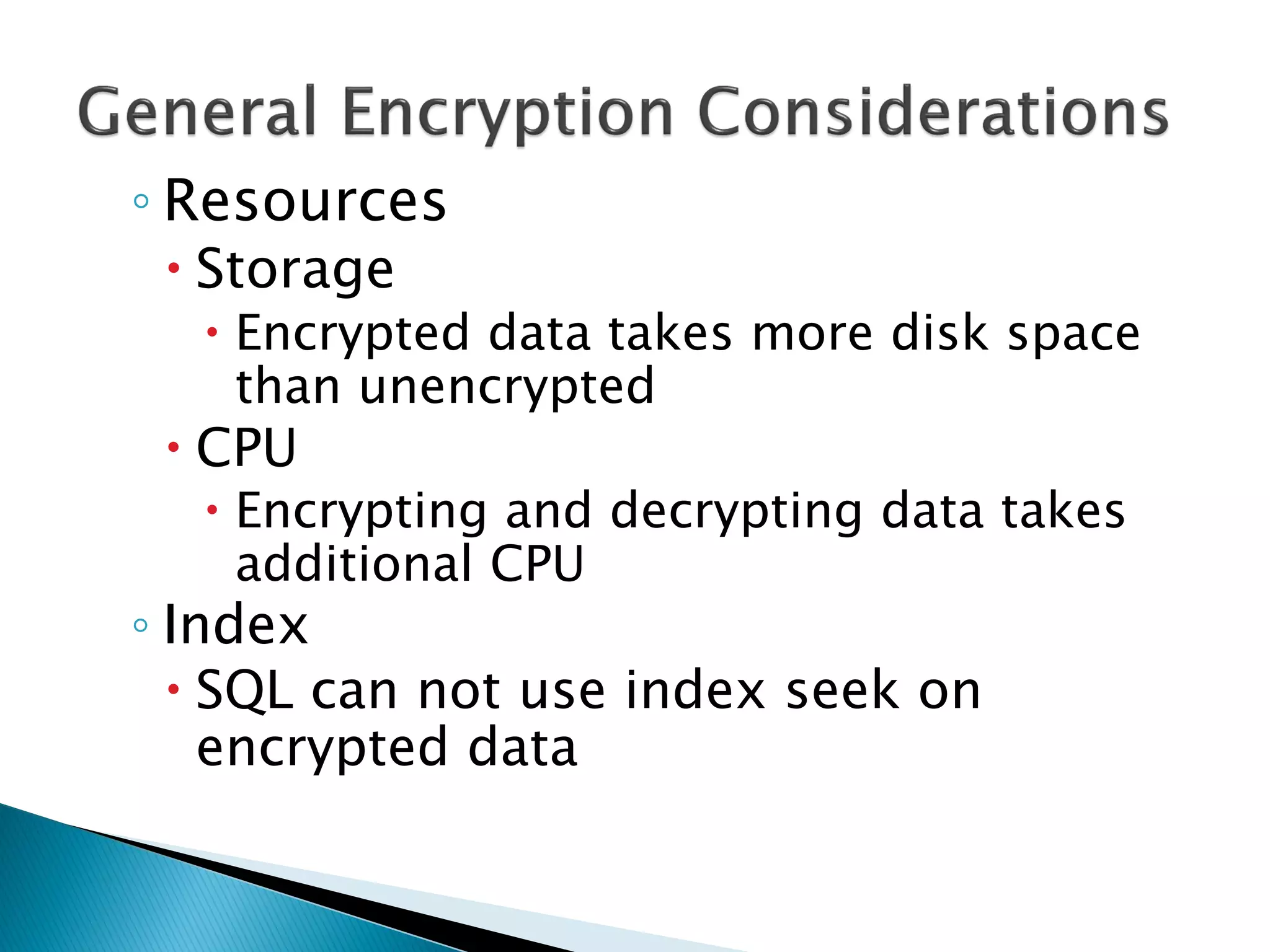
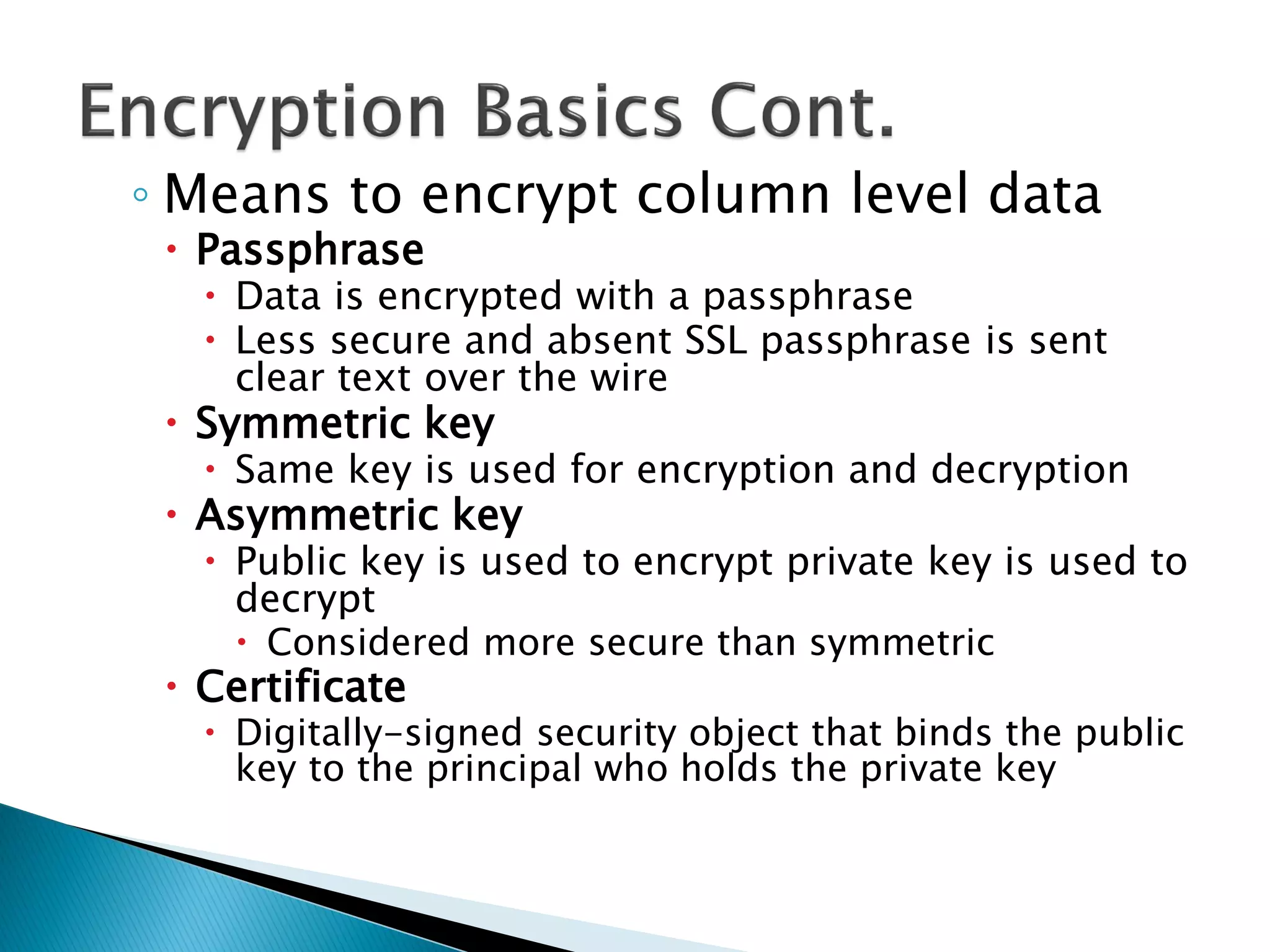
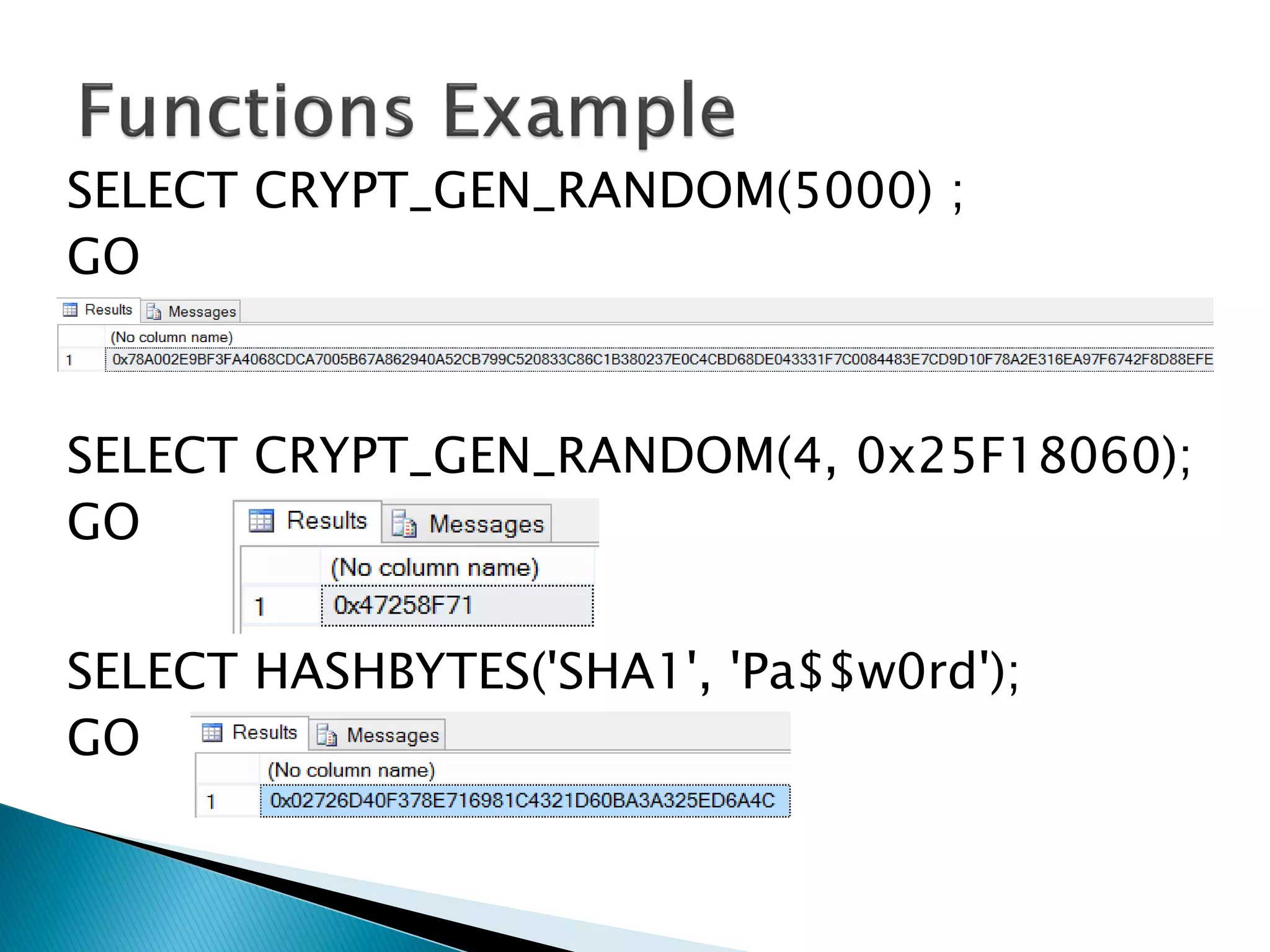
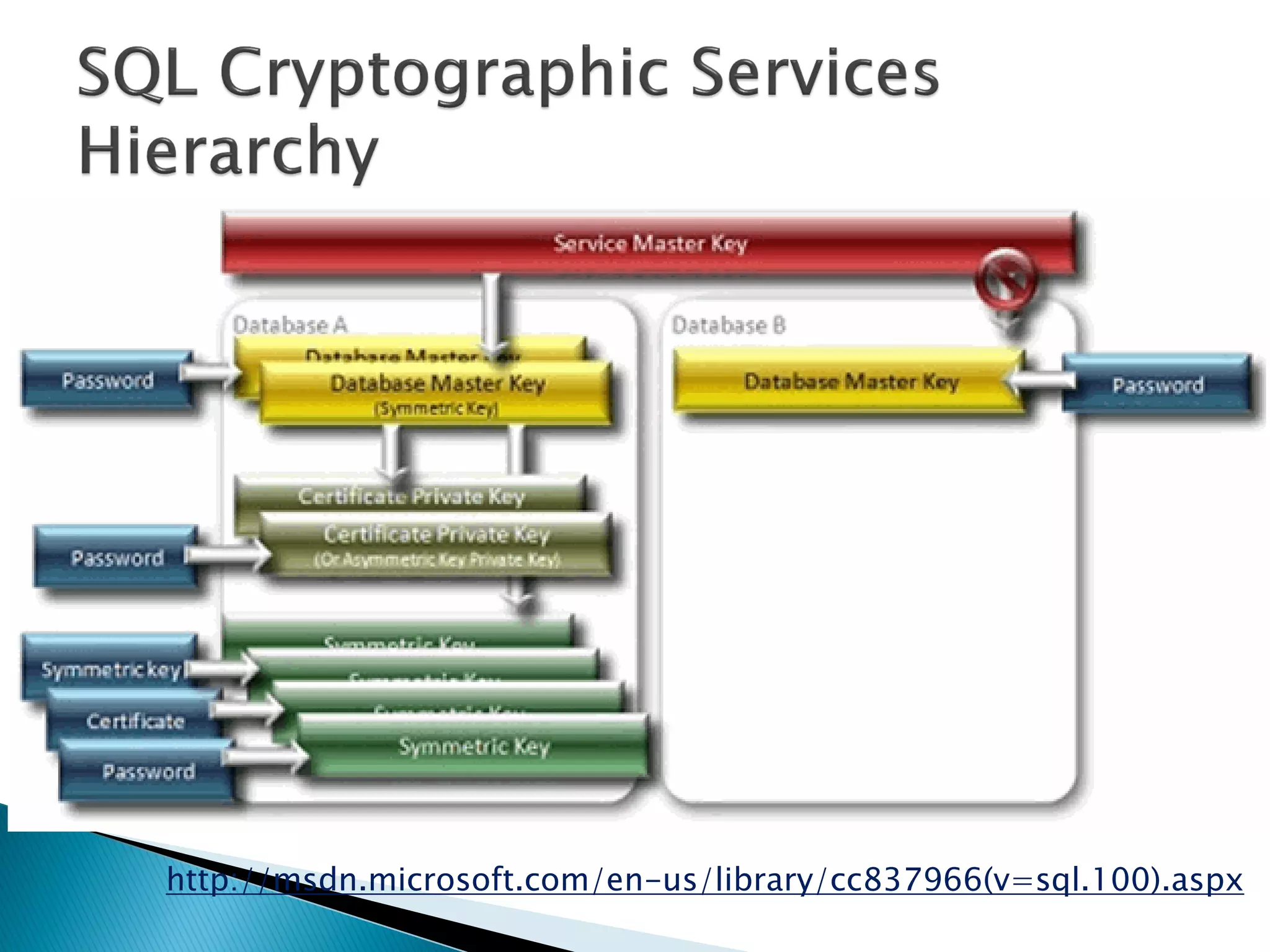
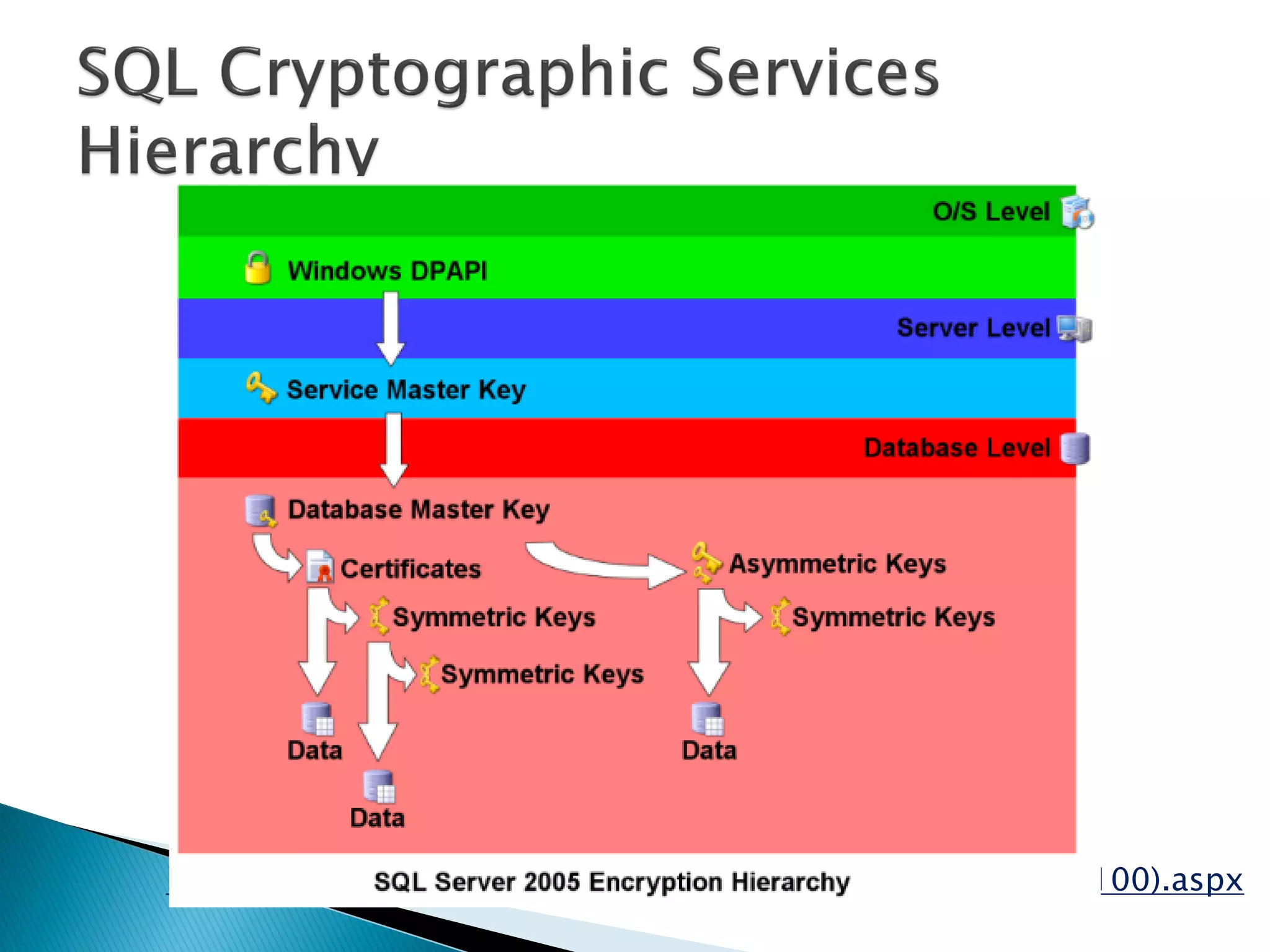
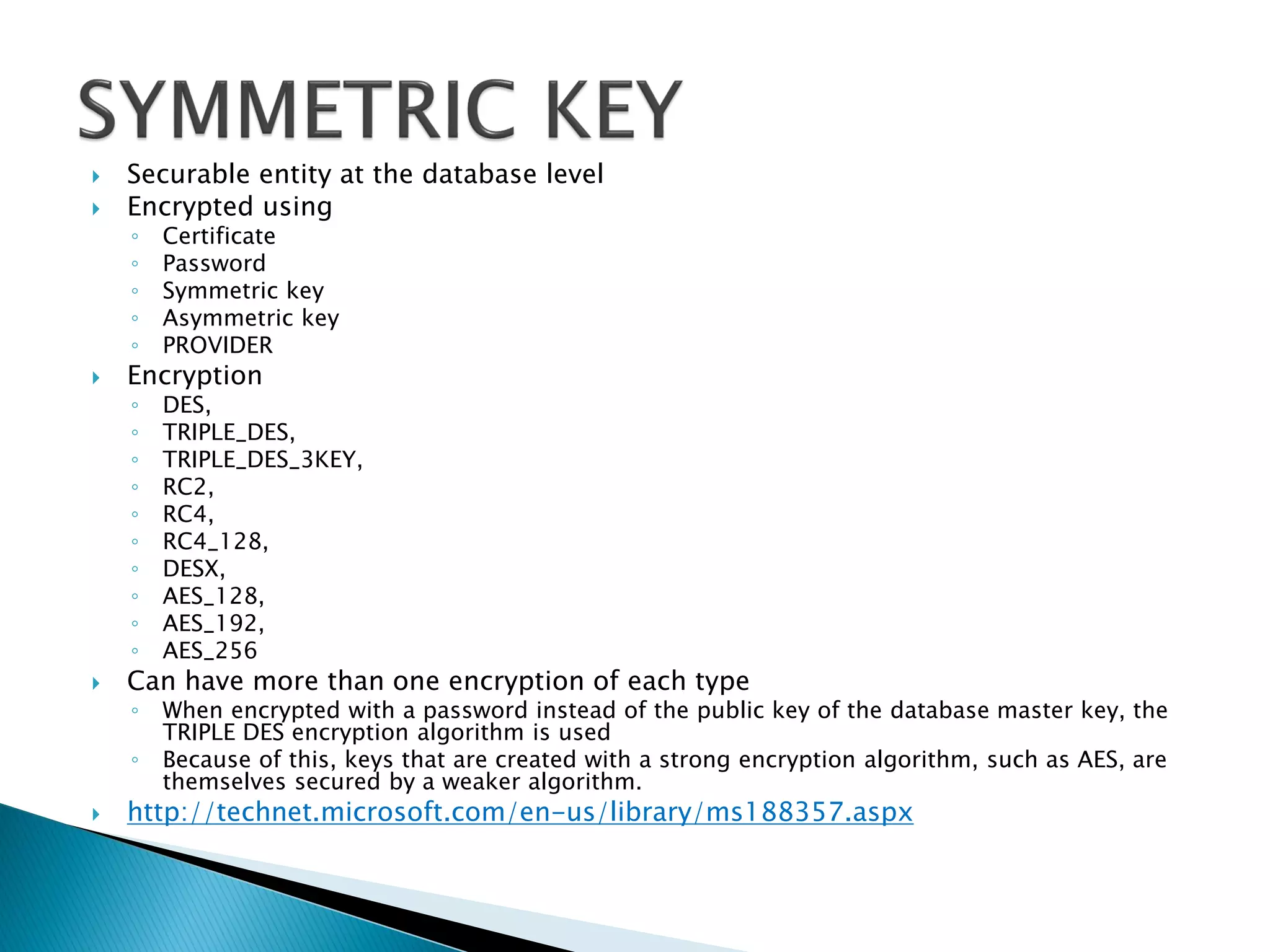
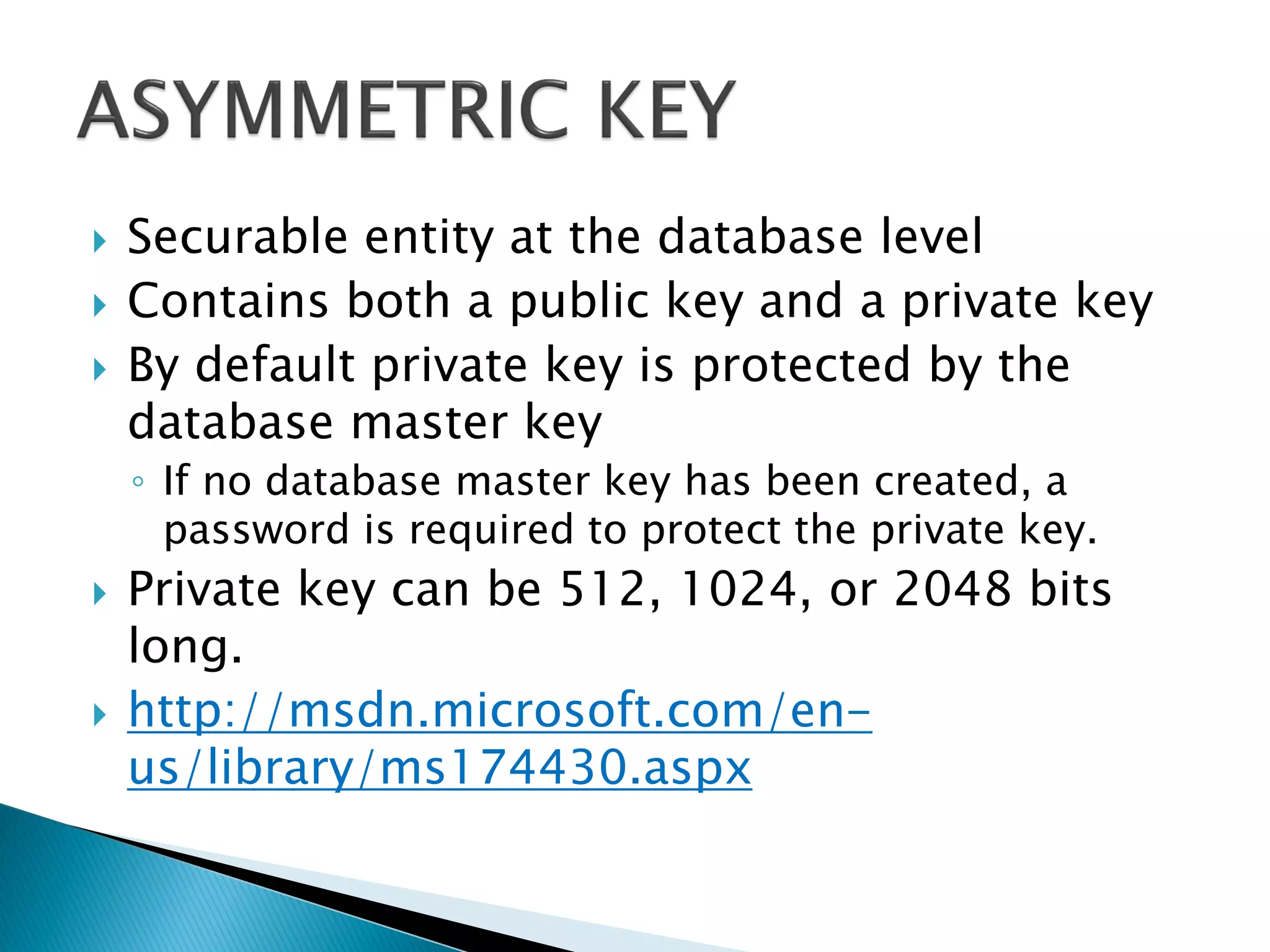
The document discusses cryptographic services in SQL, focusing on various encryption methods, keys, and best practices for securing data. It highlights the implementations of symmetric and asymmetric key encryption, the use of service and database master keys, and the importance of adhering to regulatory standards for data protection. Additionally, it addresses the limitations of encryption methods and the need for careful consideration of data storage and access protocols.