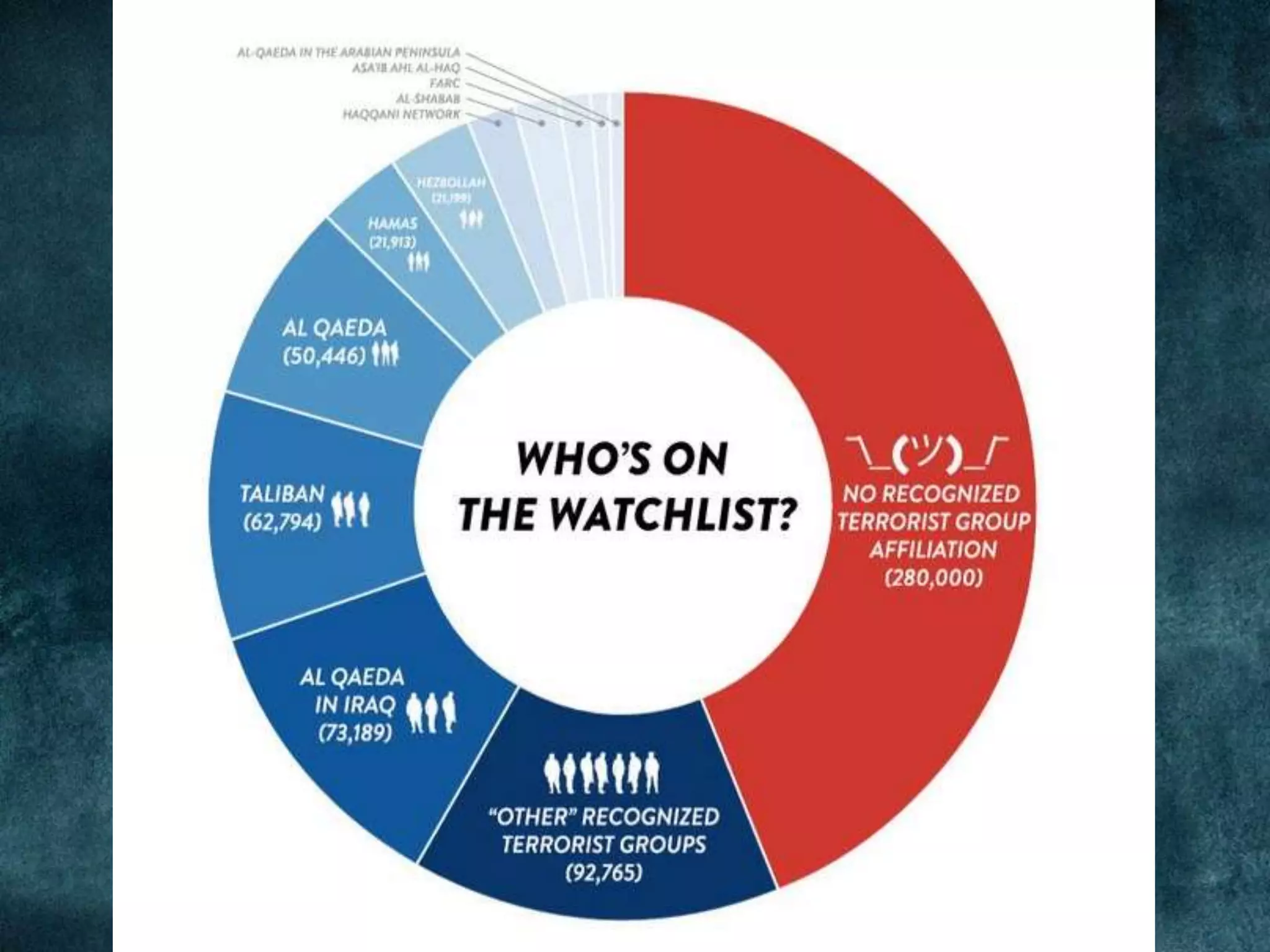
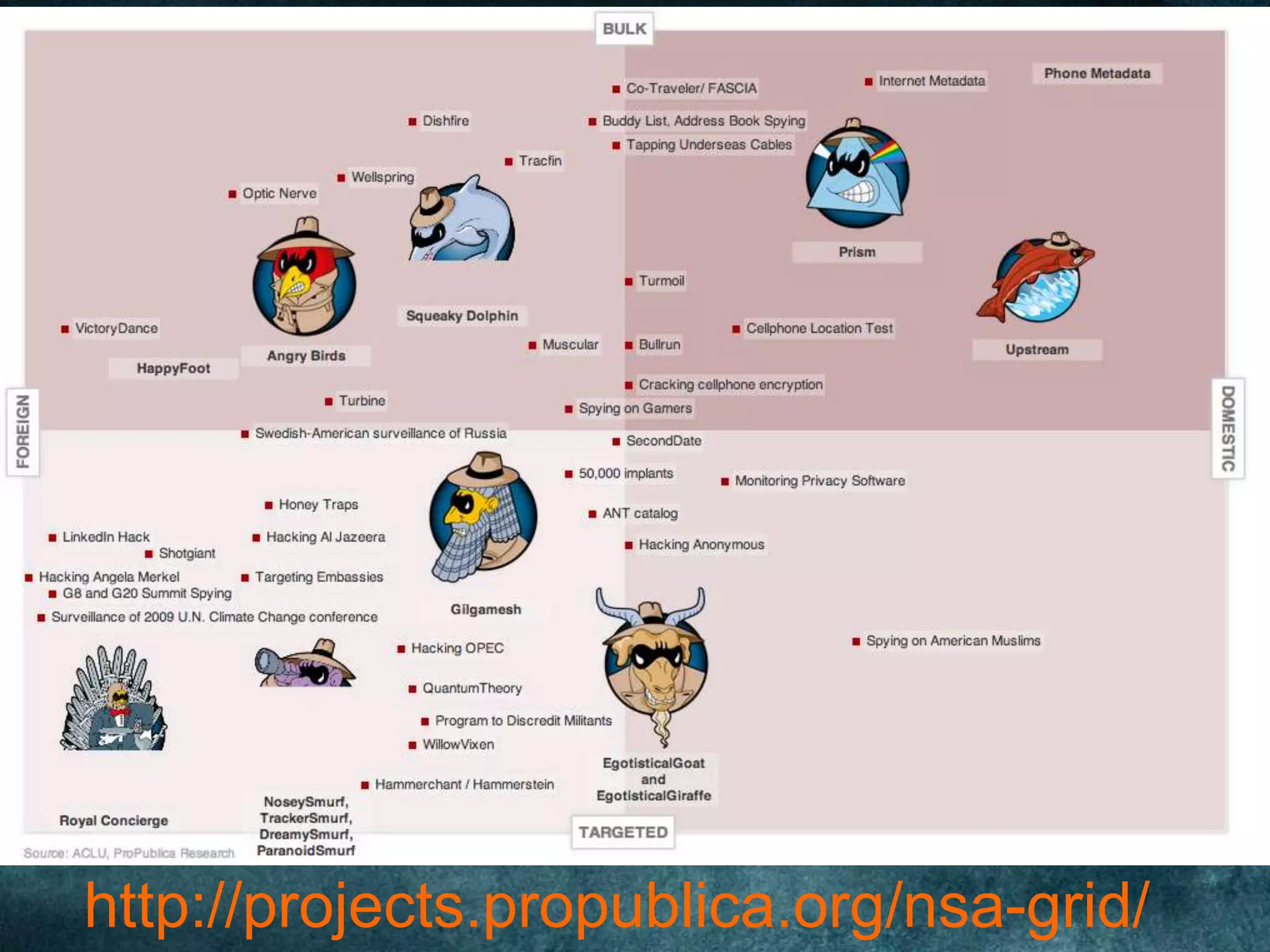
The document outlines various surveillance programs and tools used by the NSA, providing a comprehensive list of their codenames and functions. It highlights controversial practices such as extensive monitoring of communication methods, including email, SMS, and VoIP services. Key figures quoted in the document raise concerns about the implications of mass surveillance and unauthorized data access.















• W
WEALTHYCLUSTER - Program to hunt down tips on terrorists in
cyberspace (2002- )
WEBCANDID - NSA tool or database
WHITEBOX -
• X
XCONCORD - Program for finding key words in foreign language
documents
XKEYSCORE (XKS) - Program for analysing SIGINT traffic
• Z
ZARF - Compartment of TALENT KEYHOLE for ELINT satellites](https://image.slidesharecdn.com/snowden-140814123155-phpapp01/75/Summarising-Snowden-and-Snowden-as-internal-threat-16-2048.jpg)