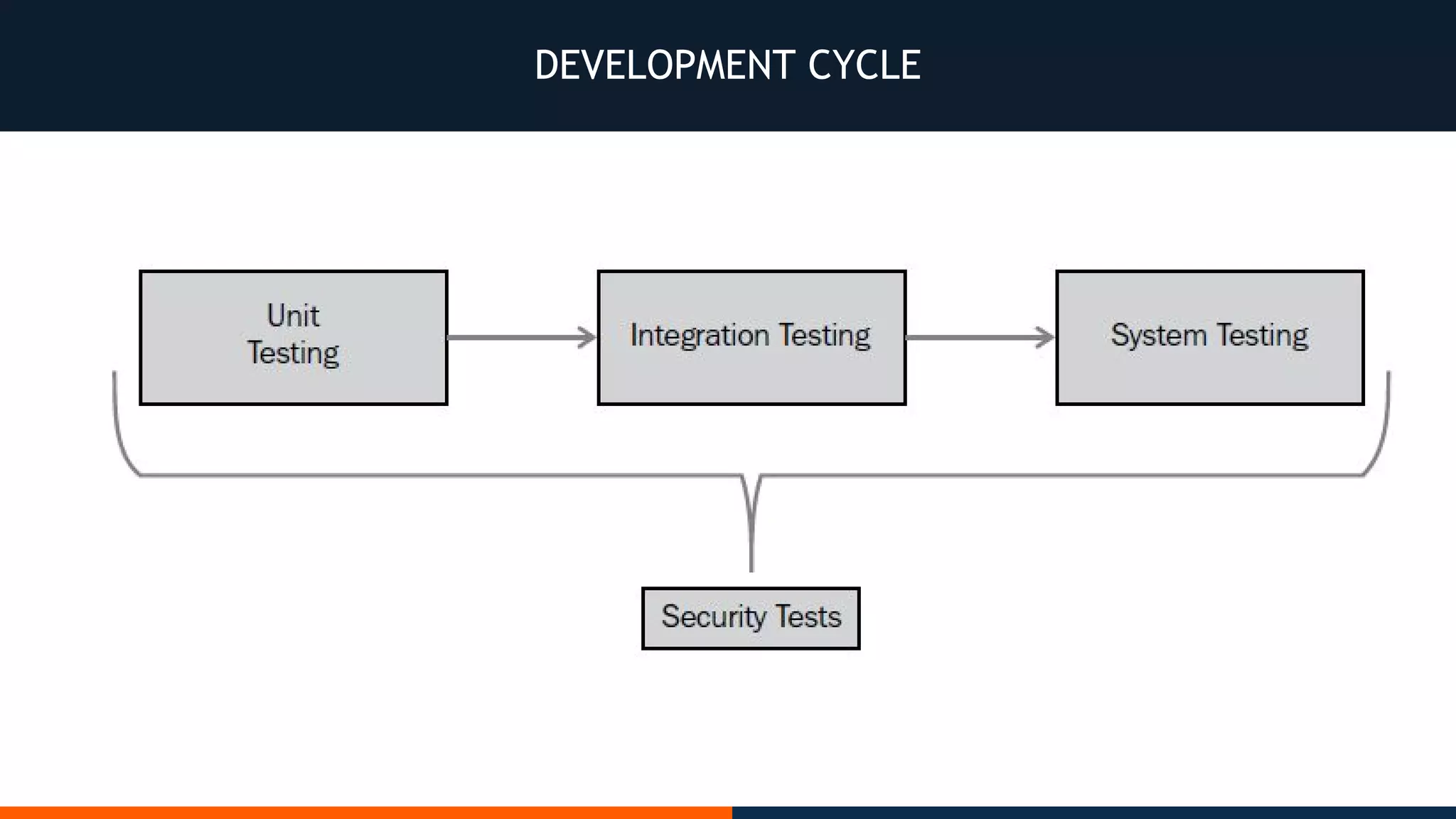
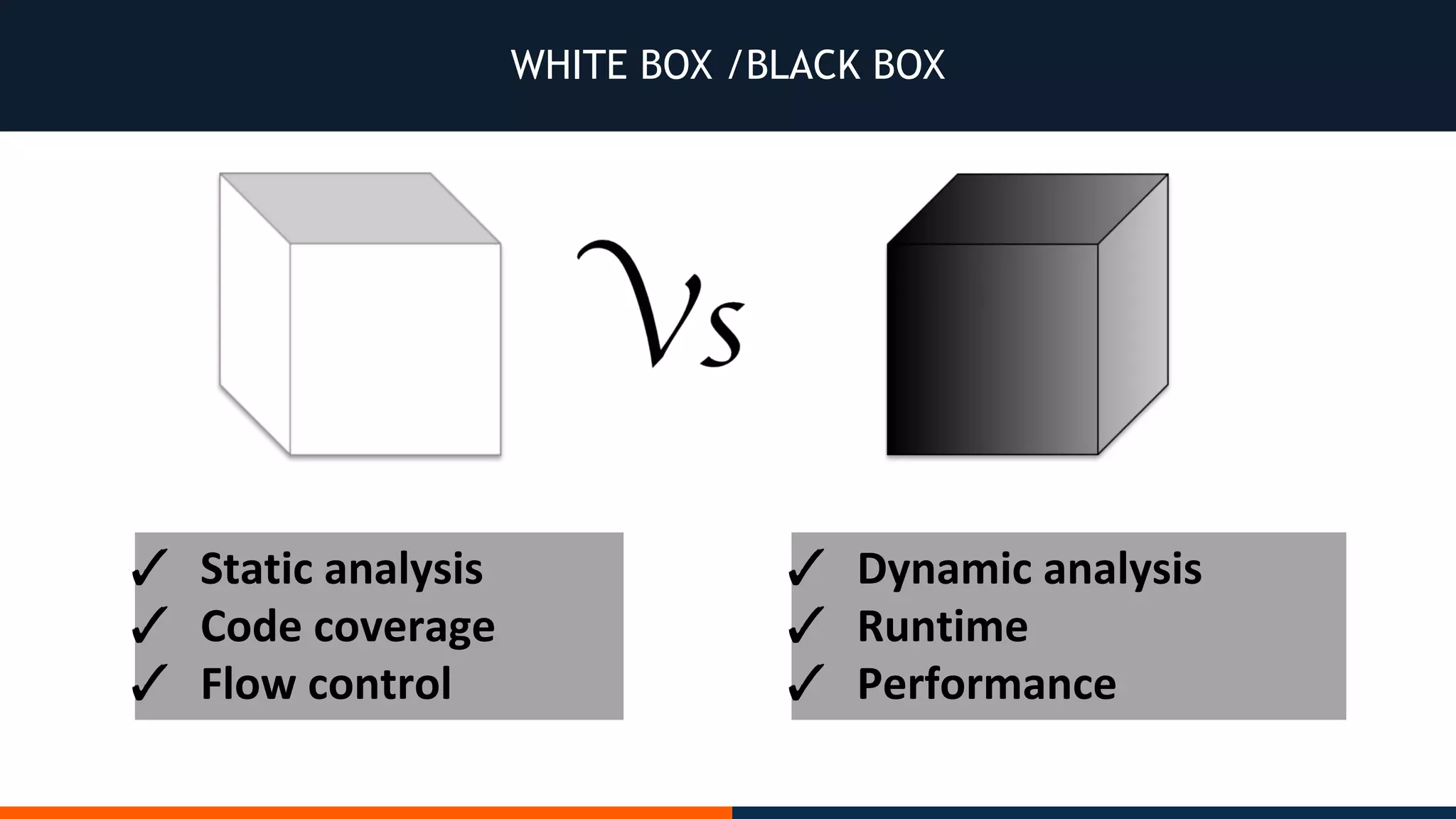
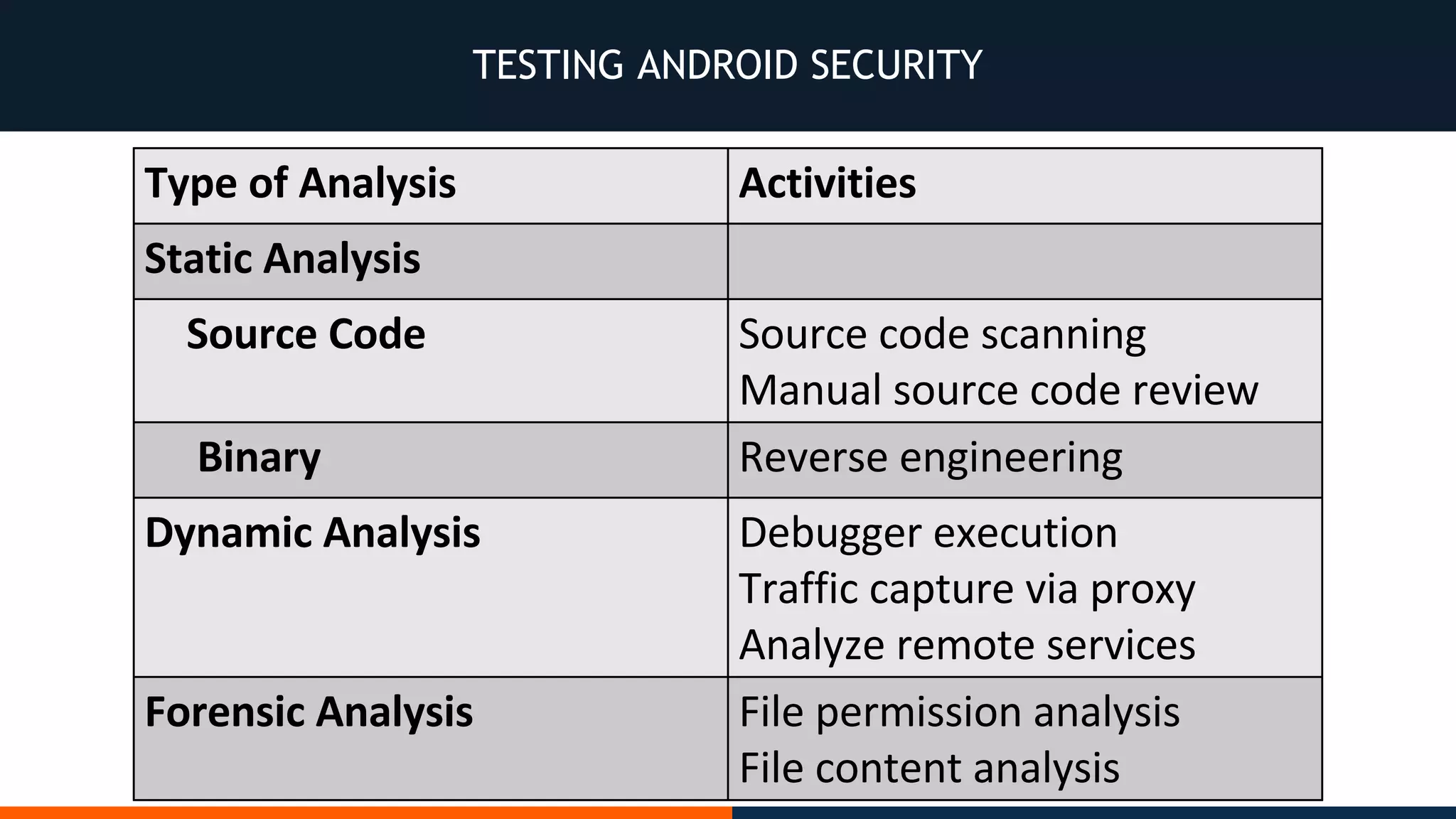
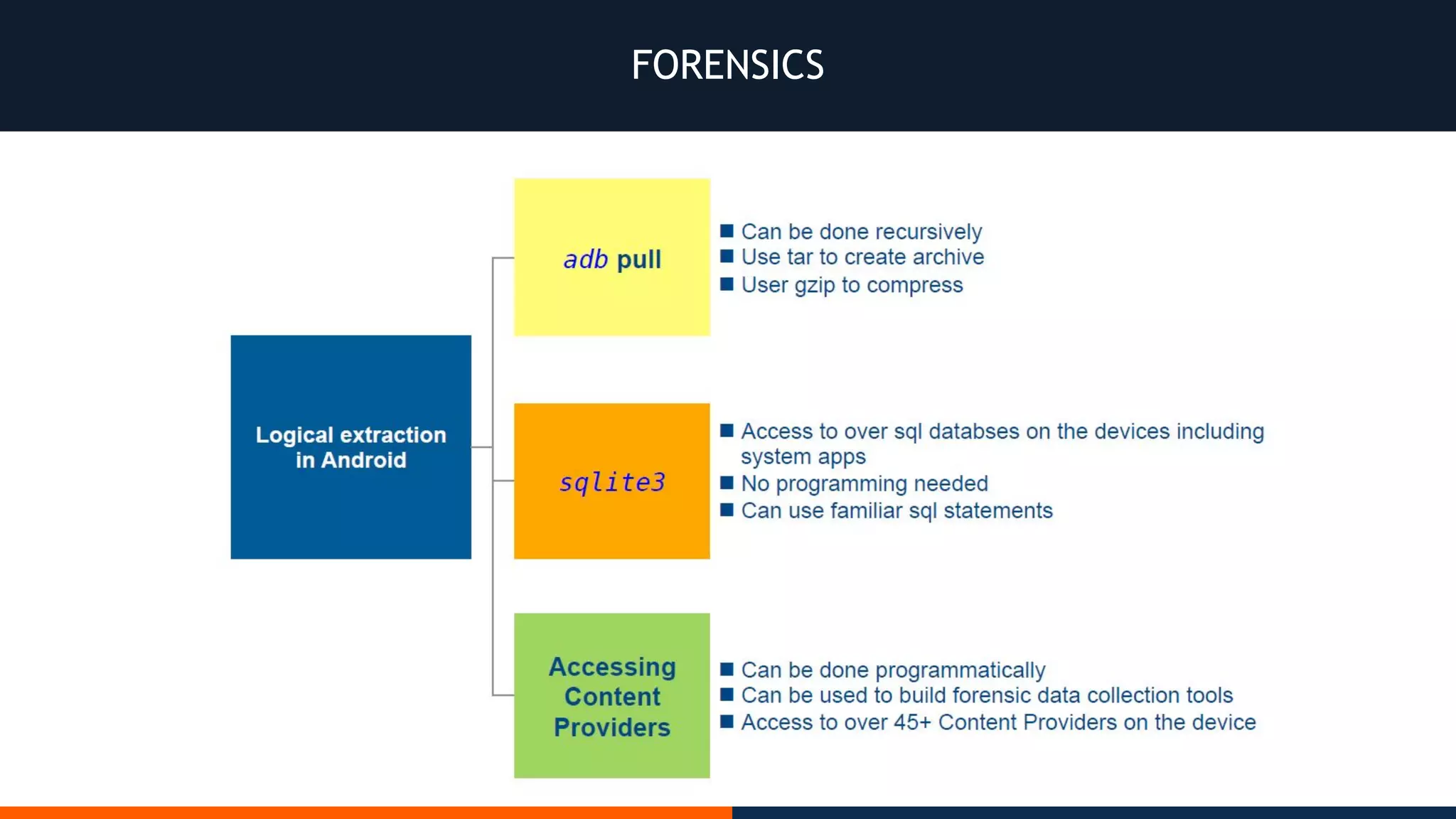
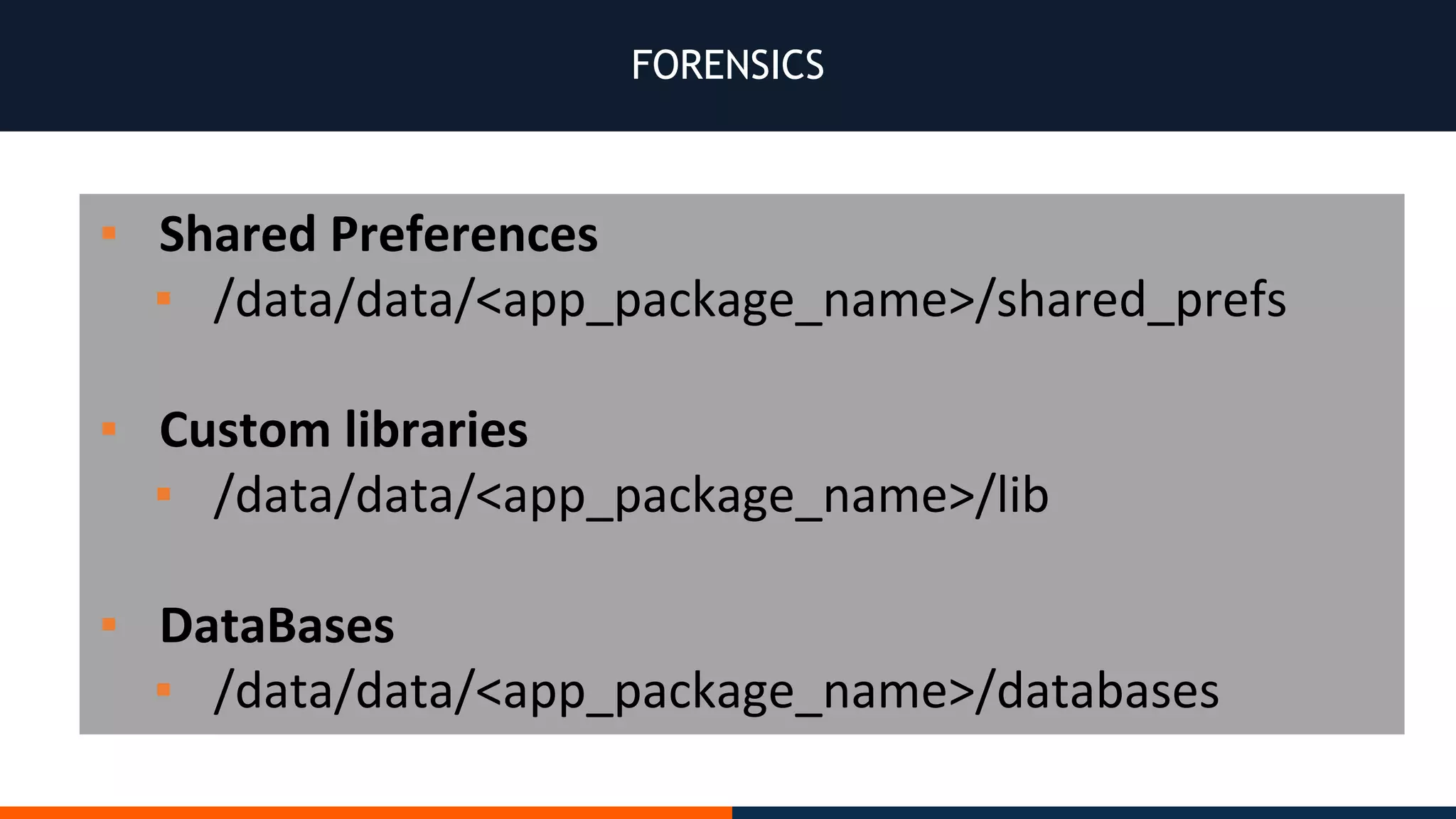
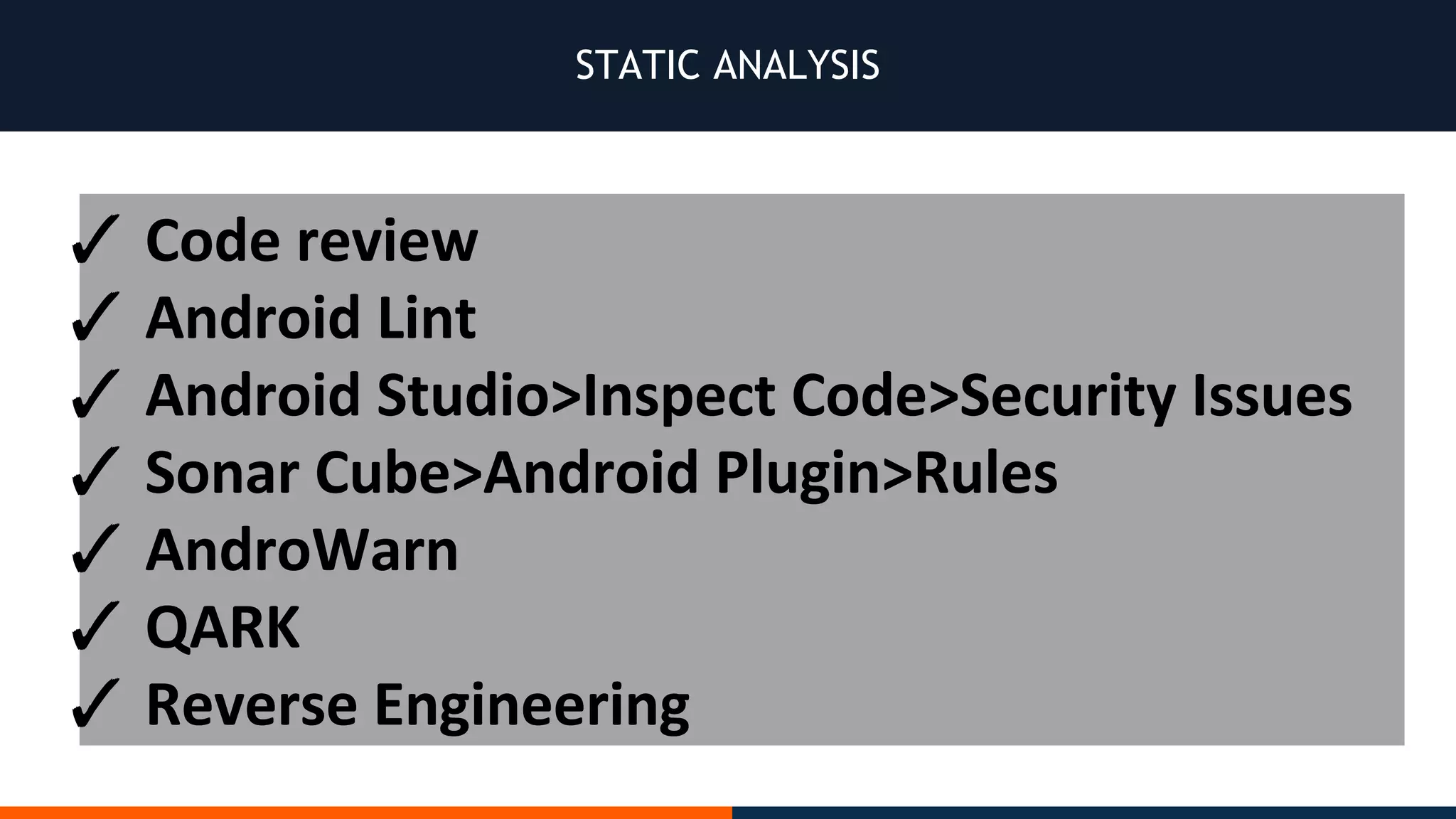
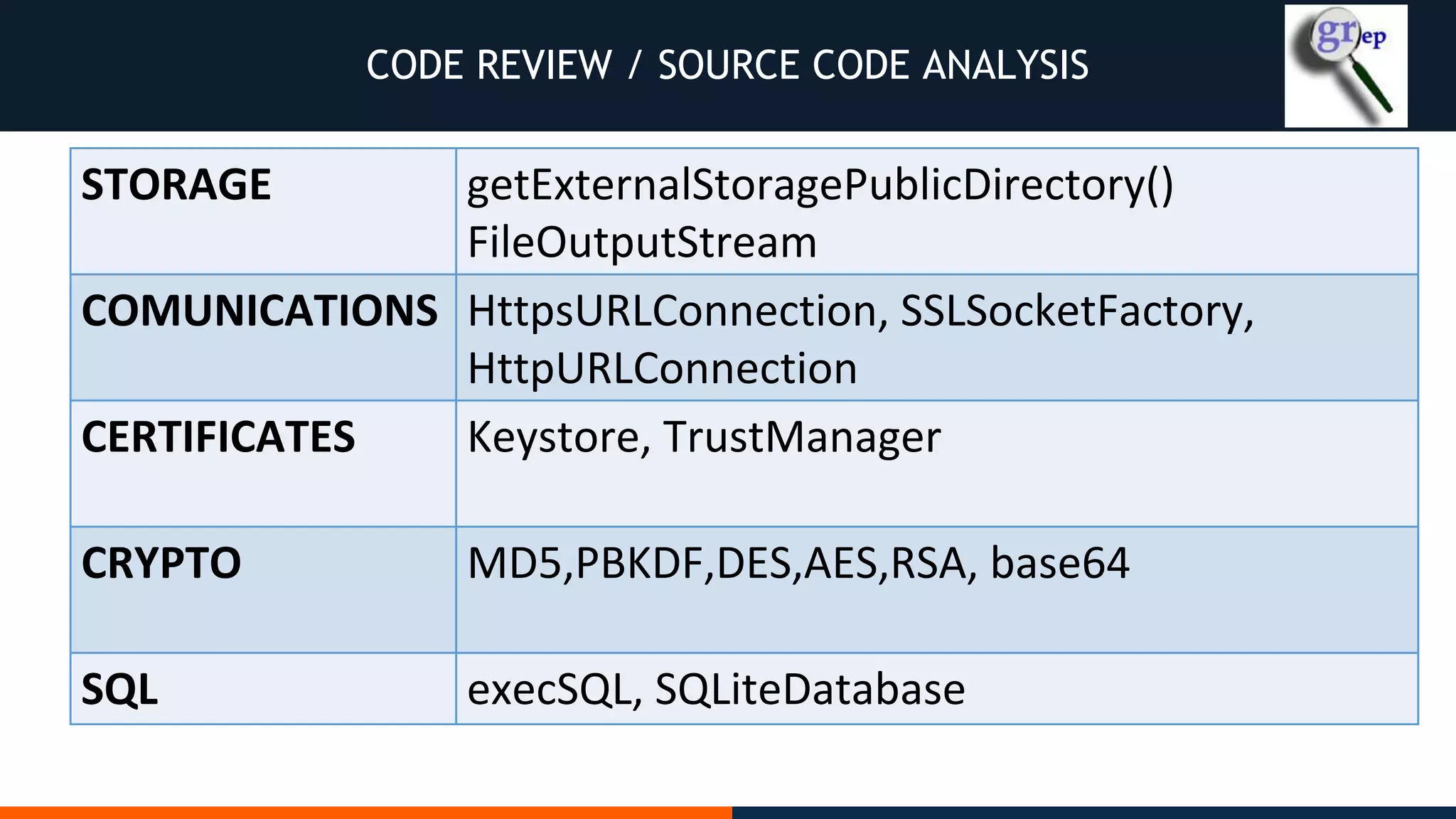
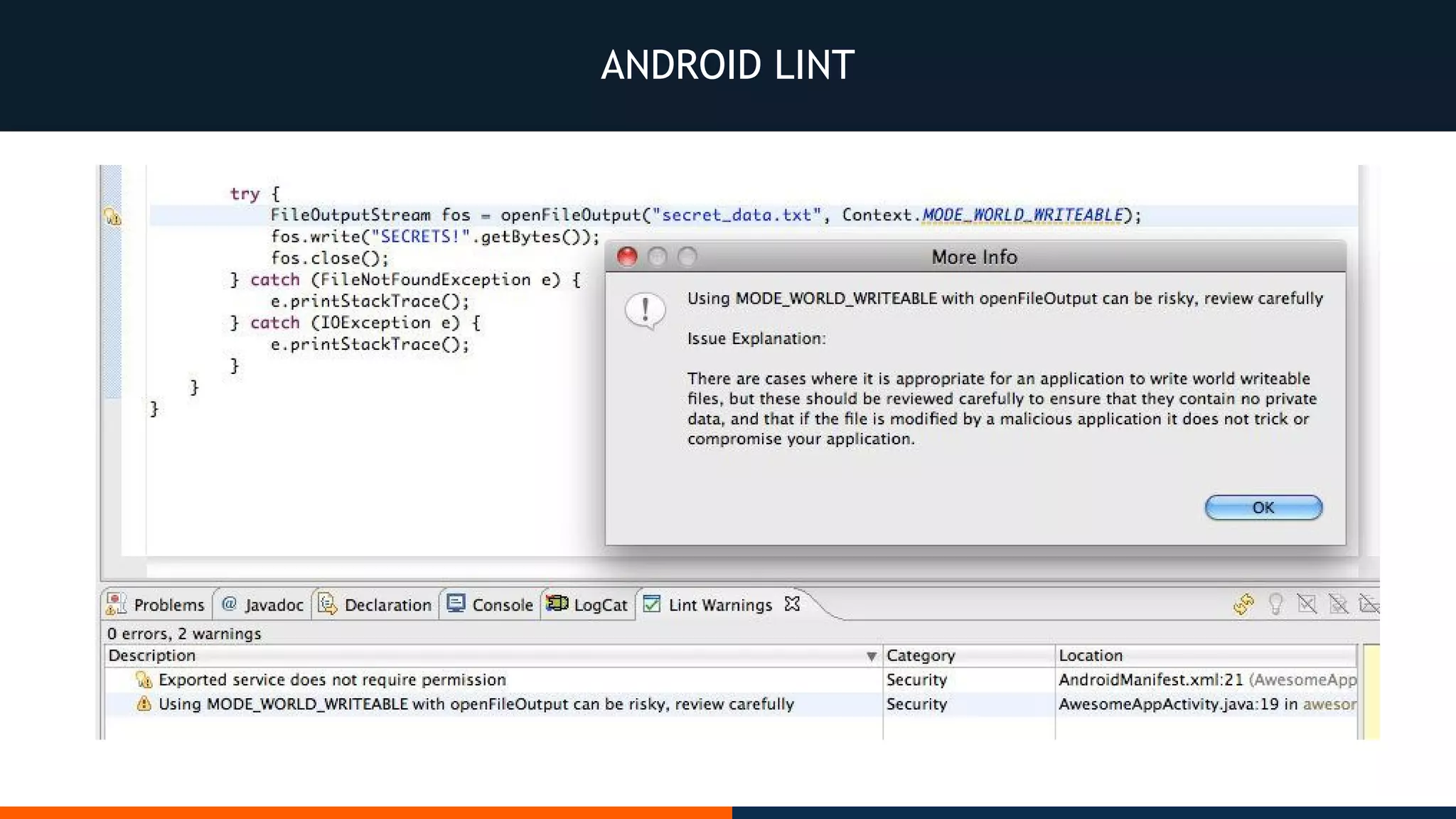
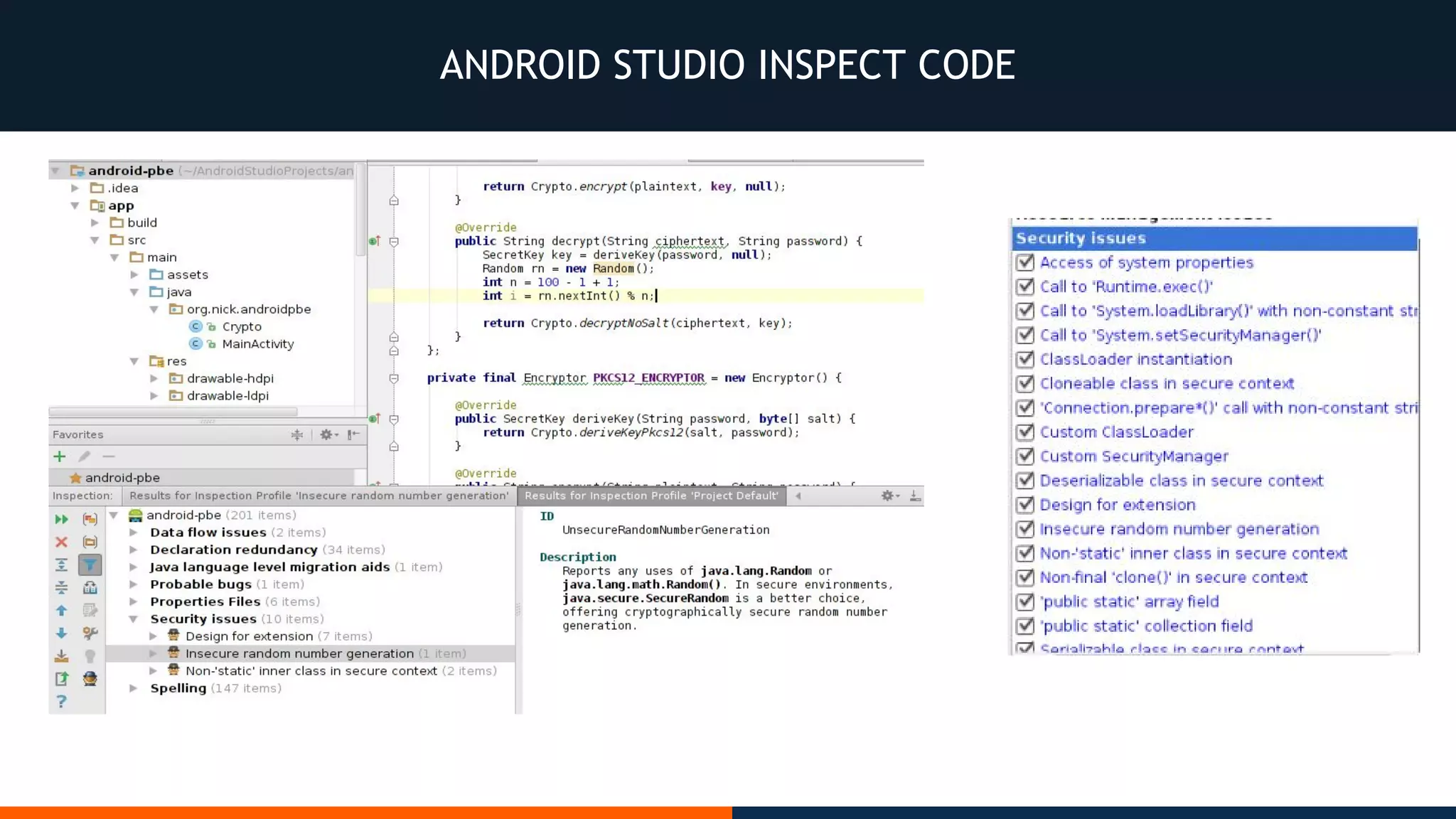
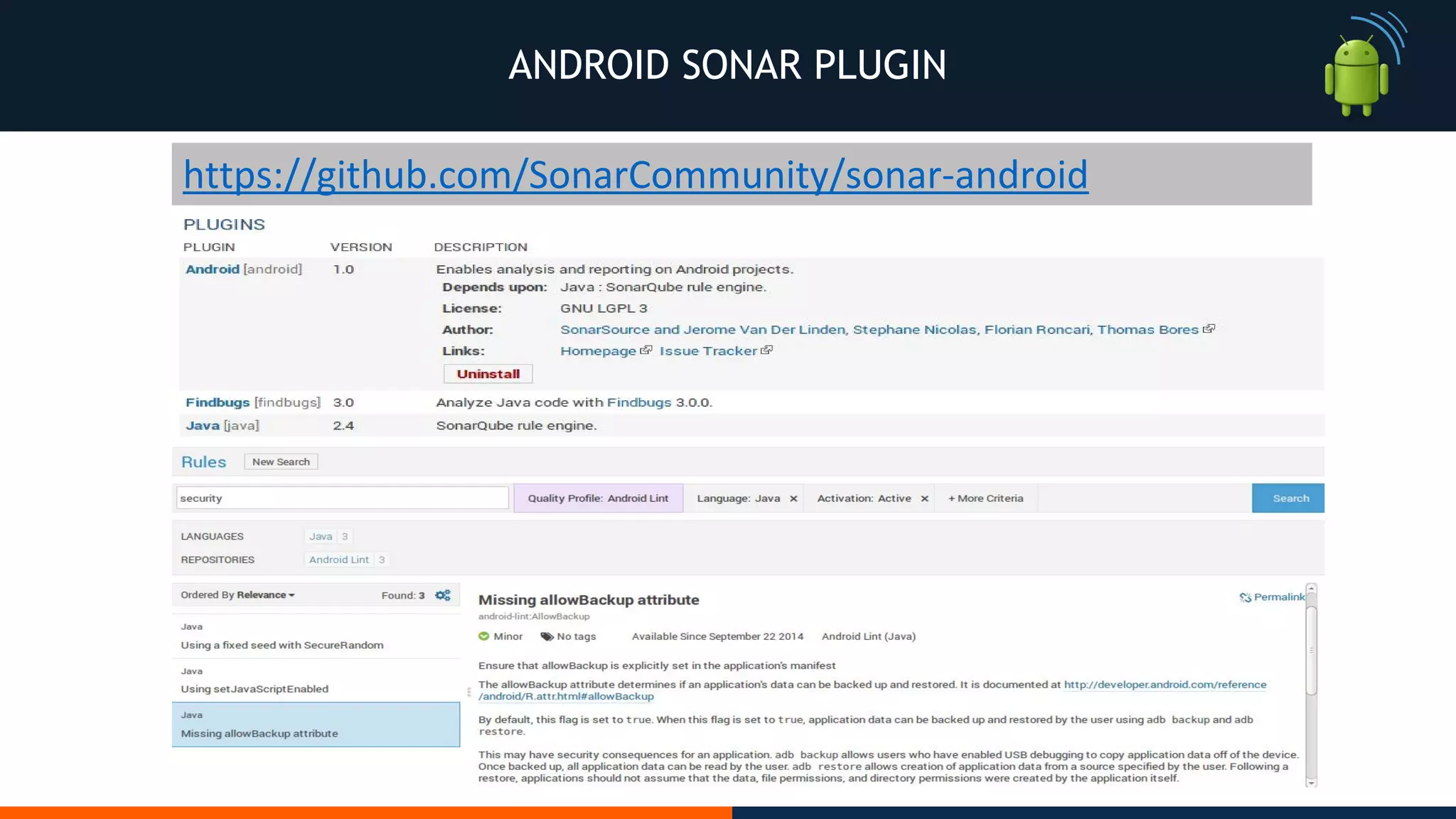
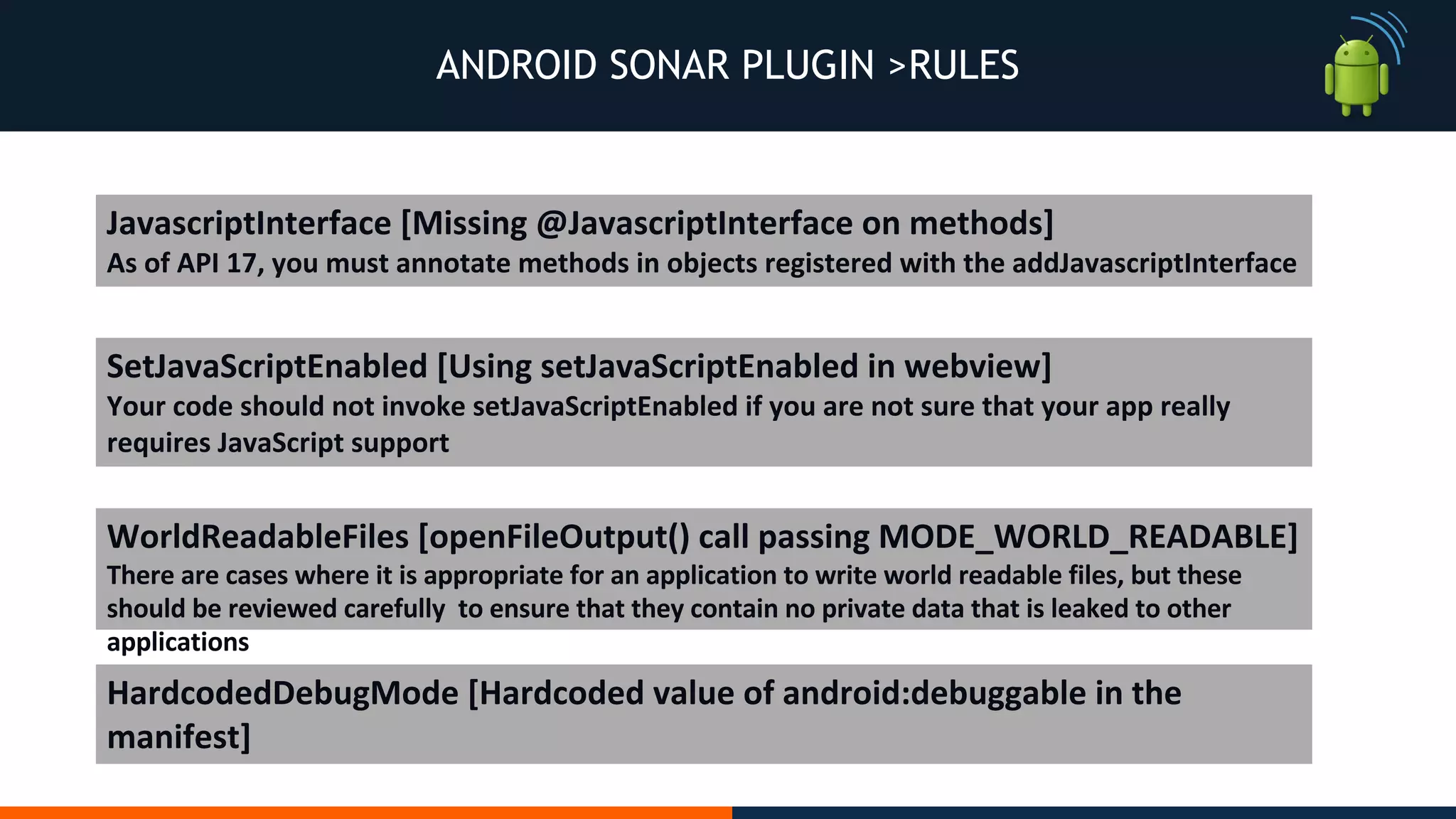
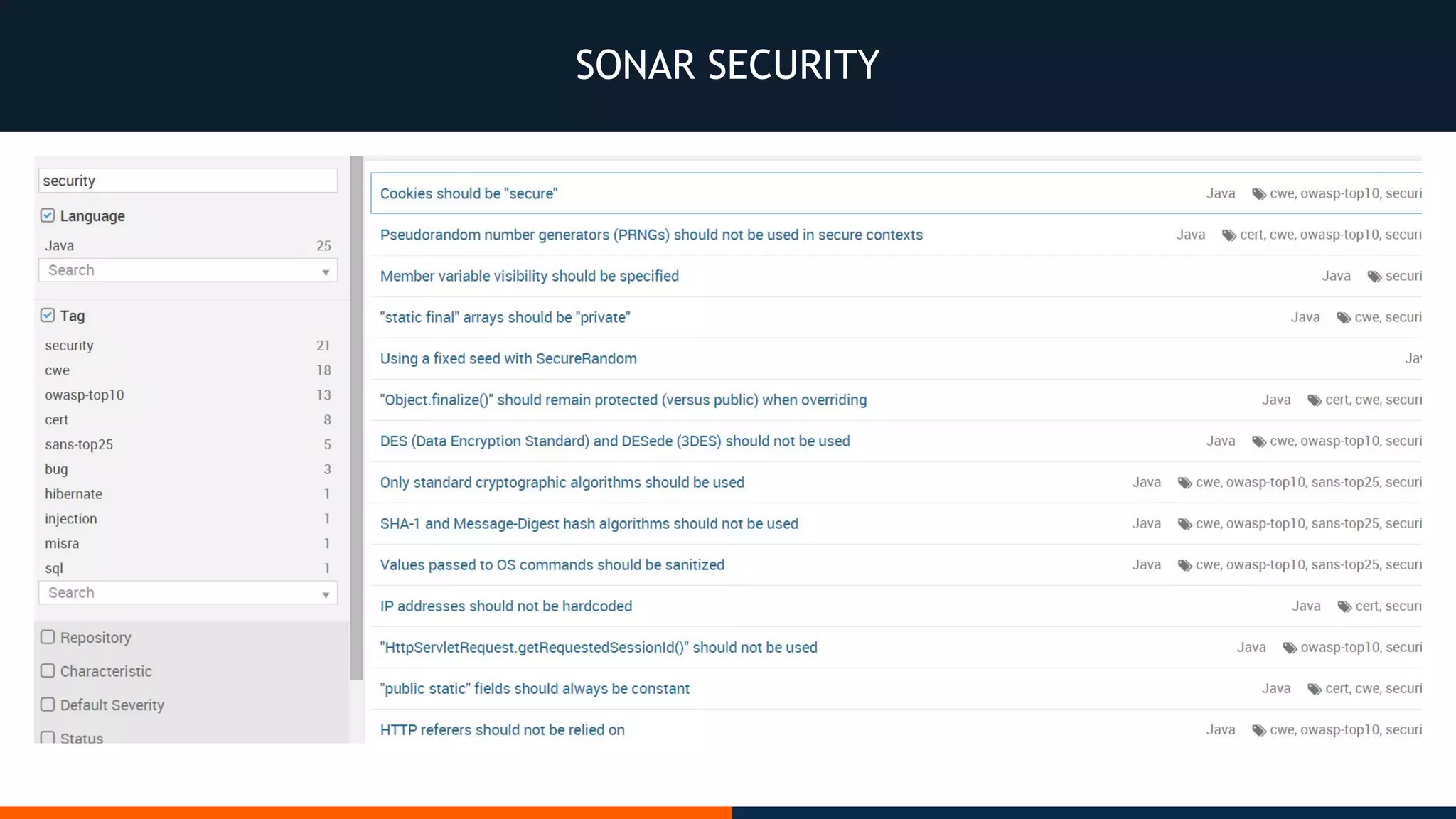
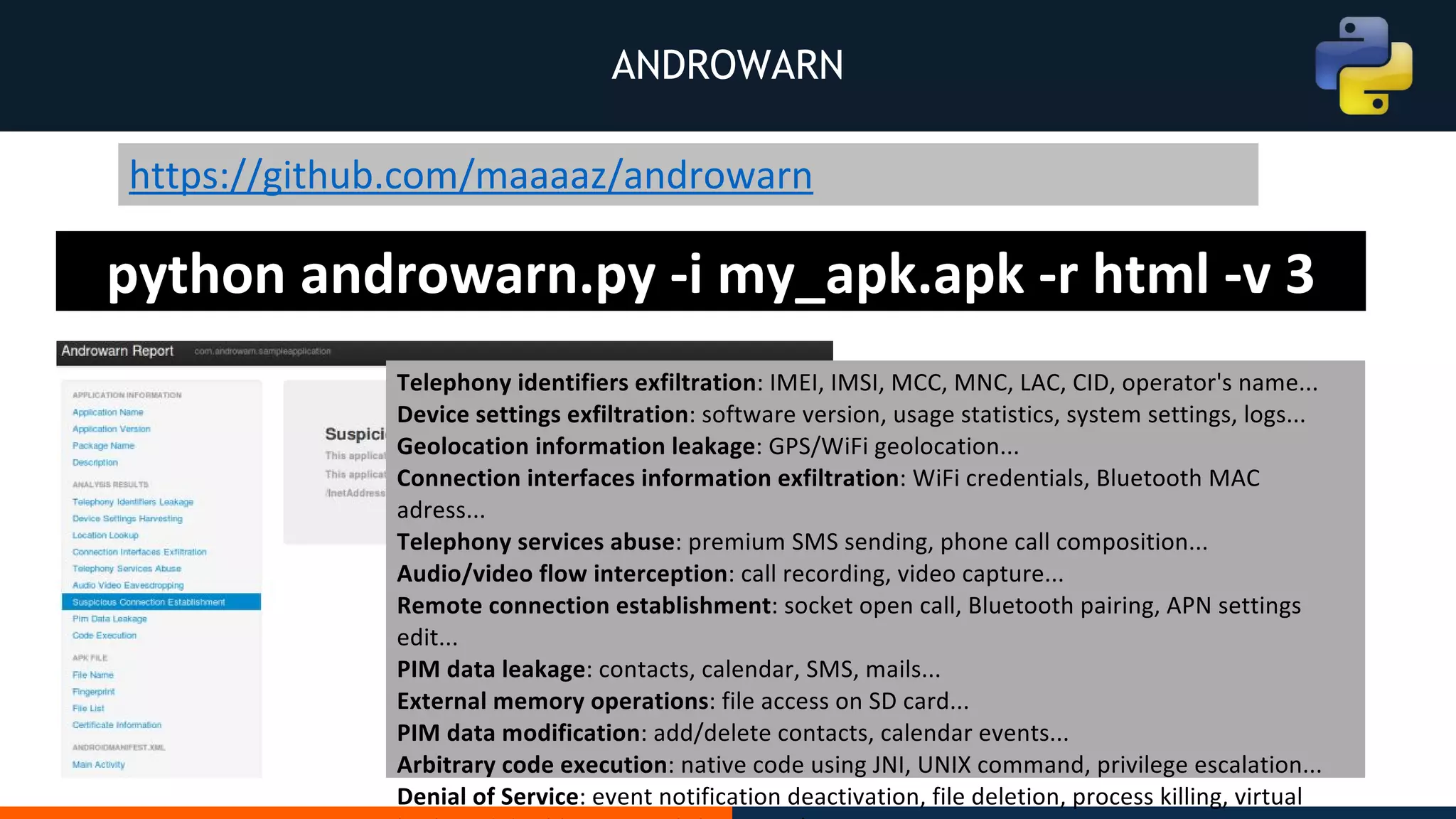
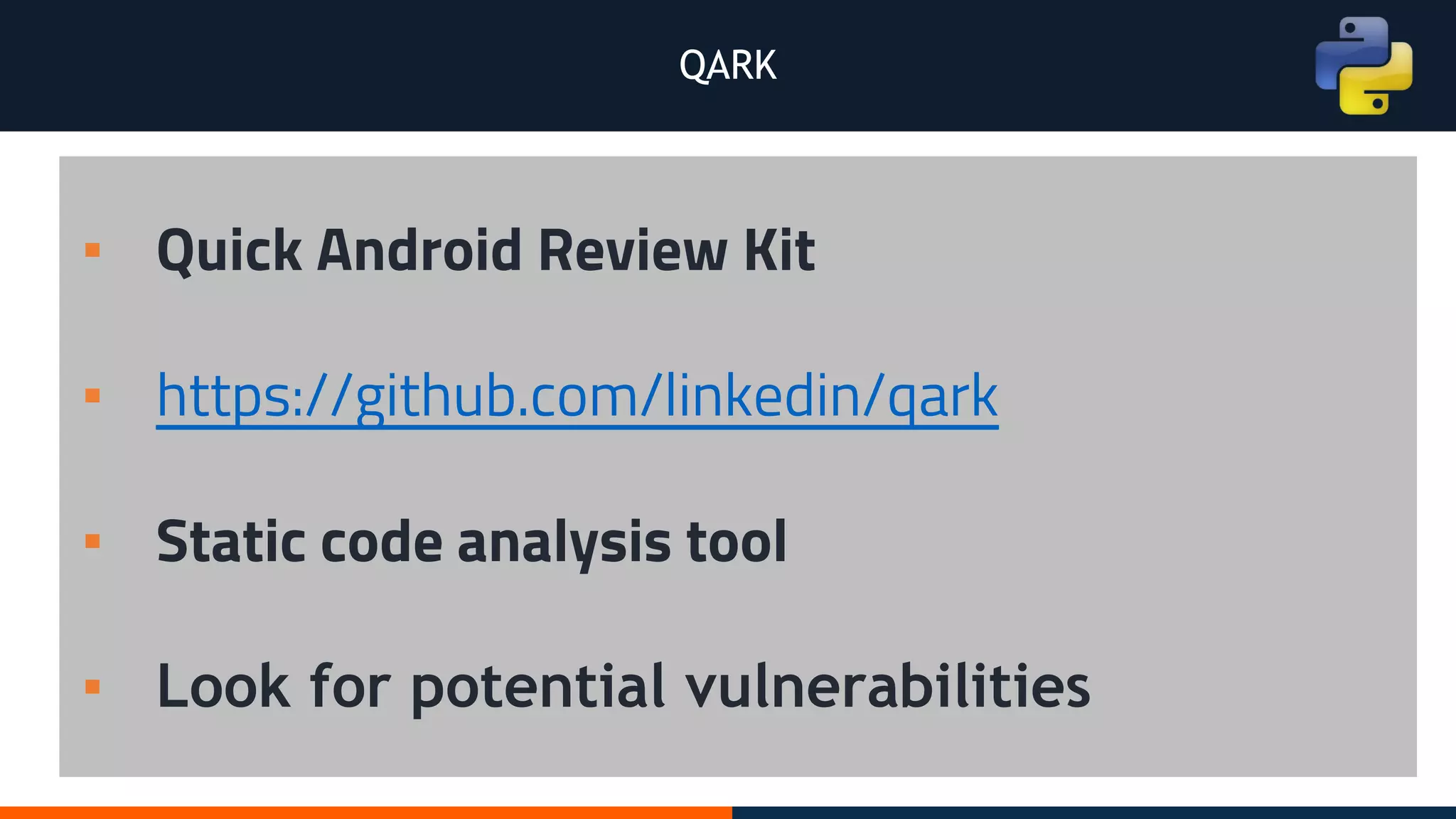
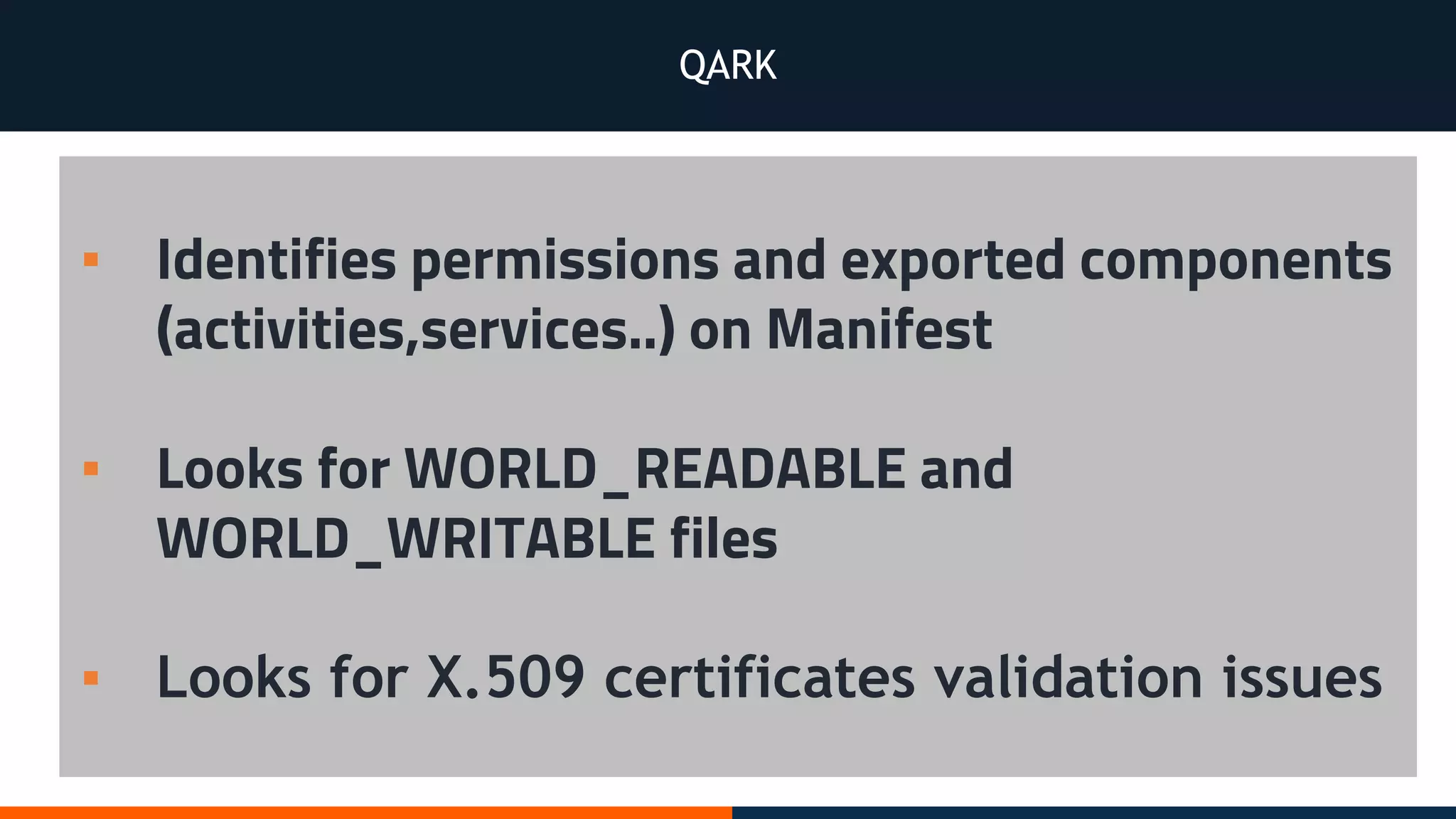
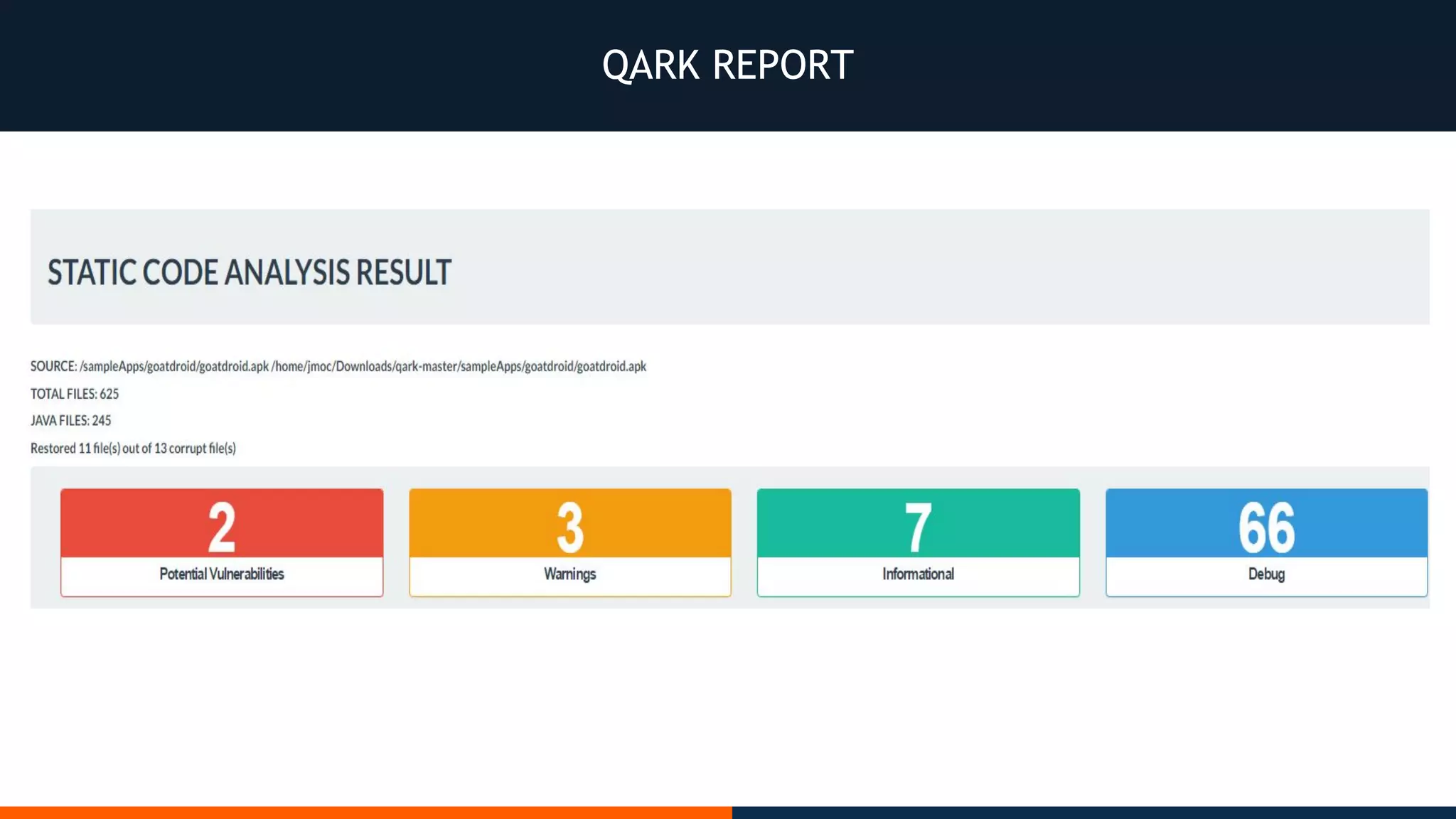
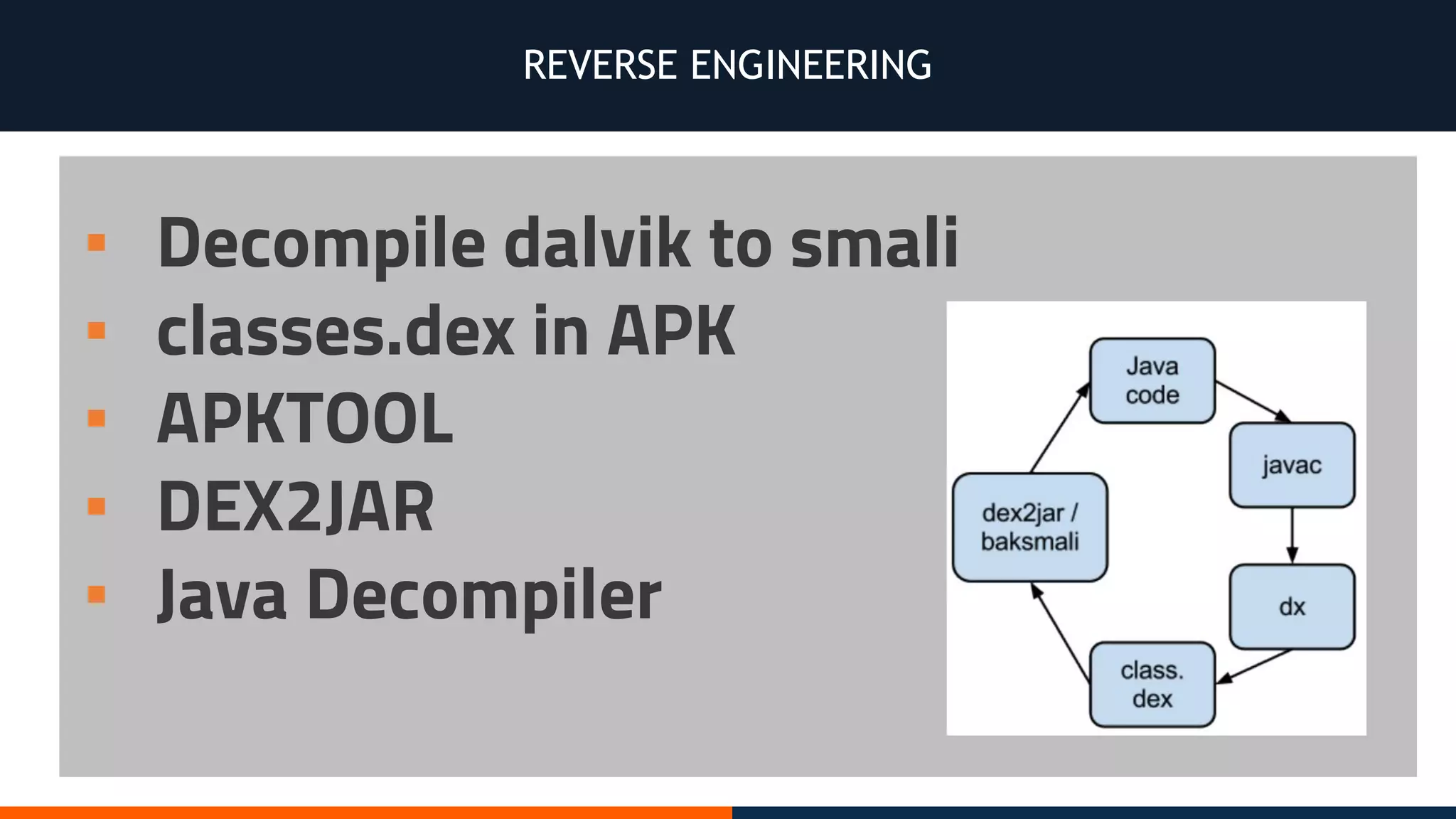
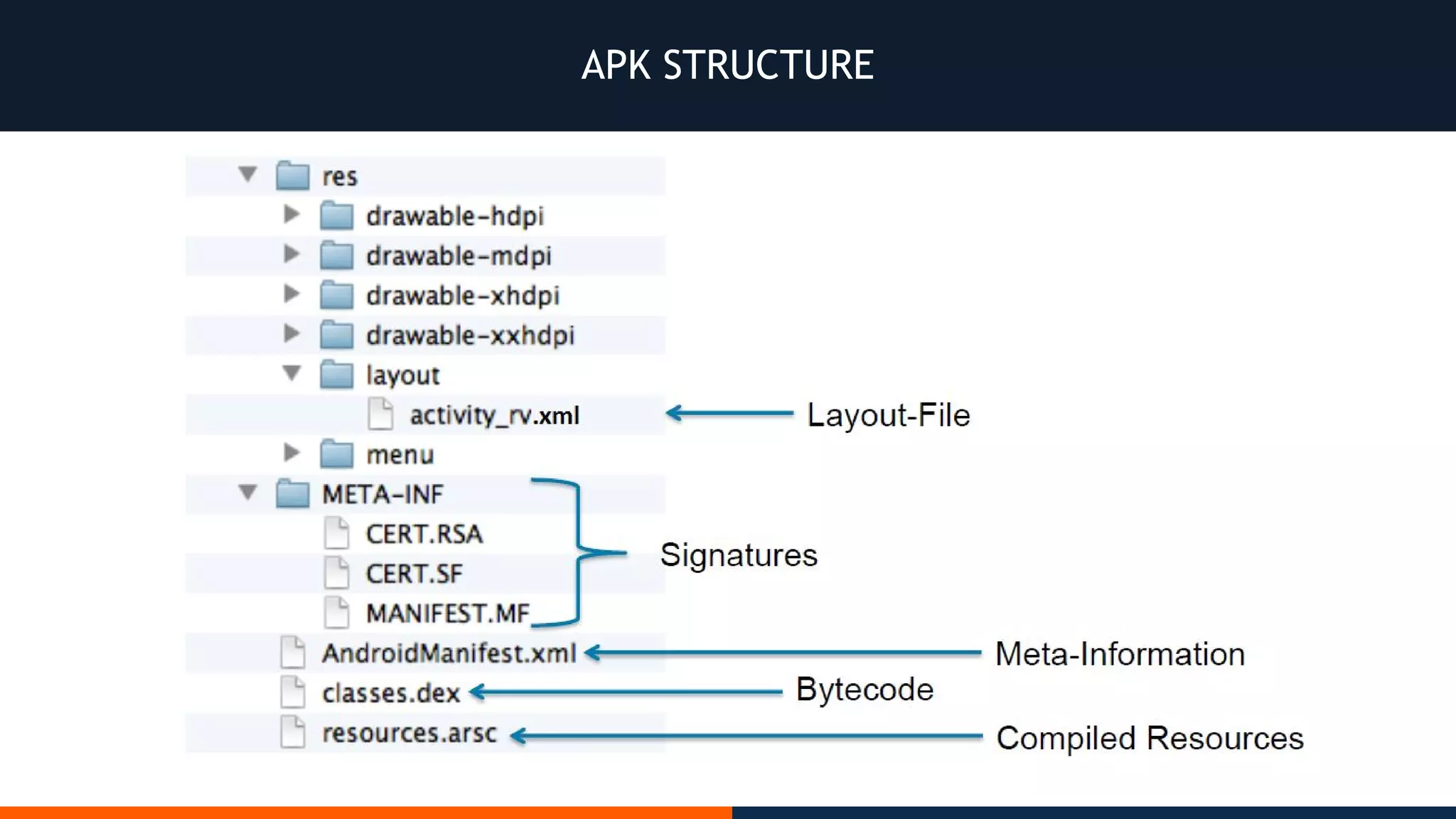
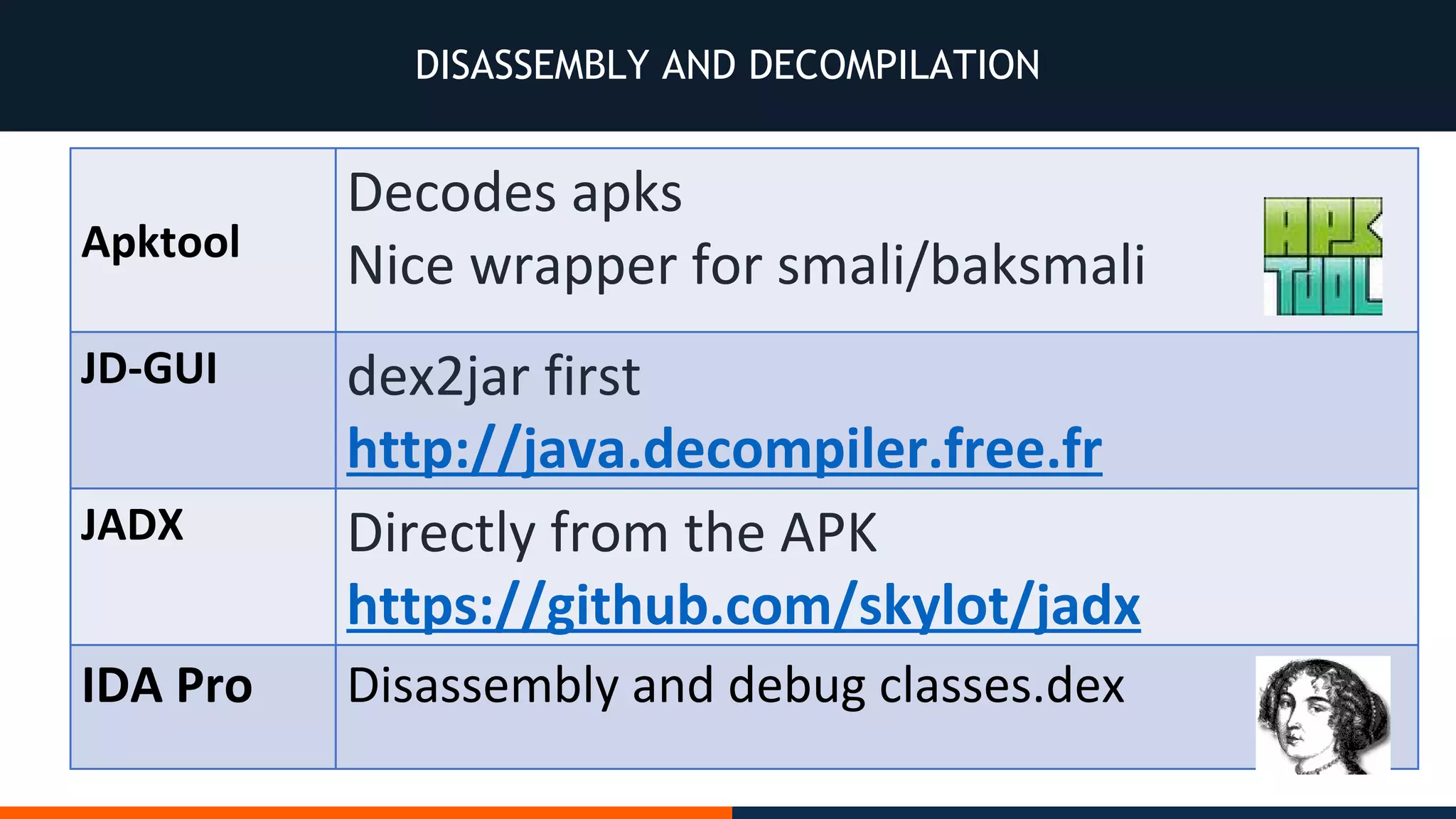
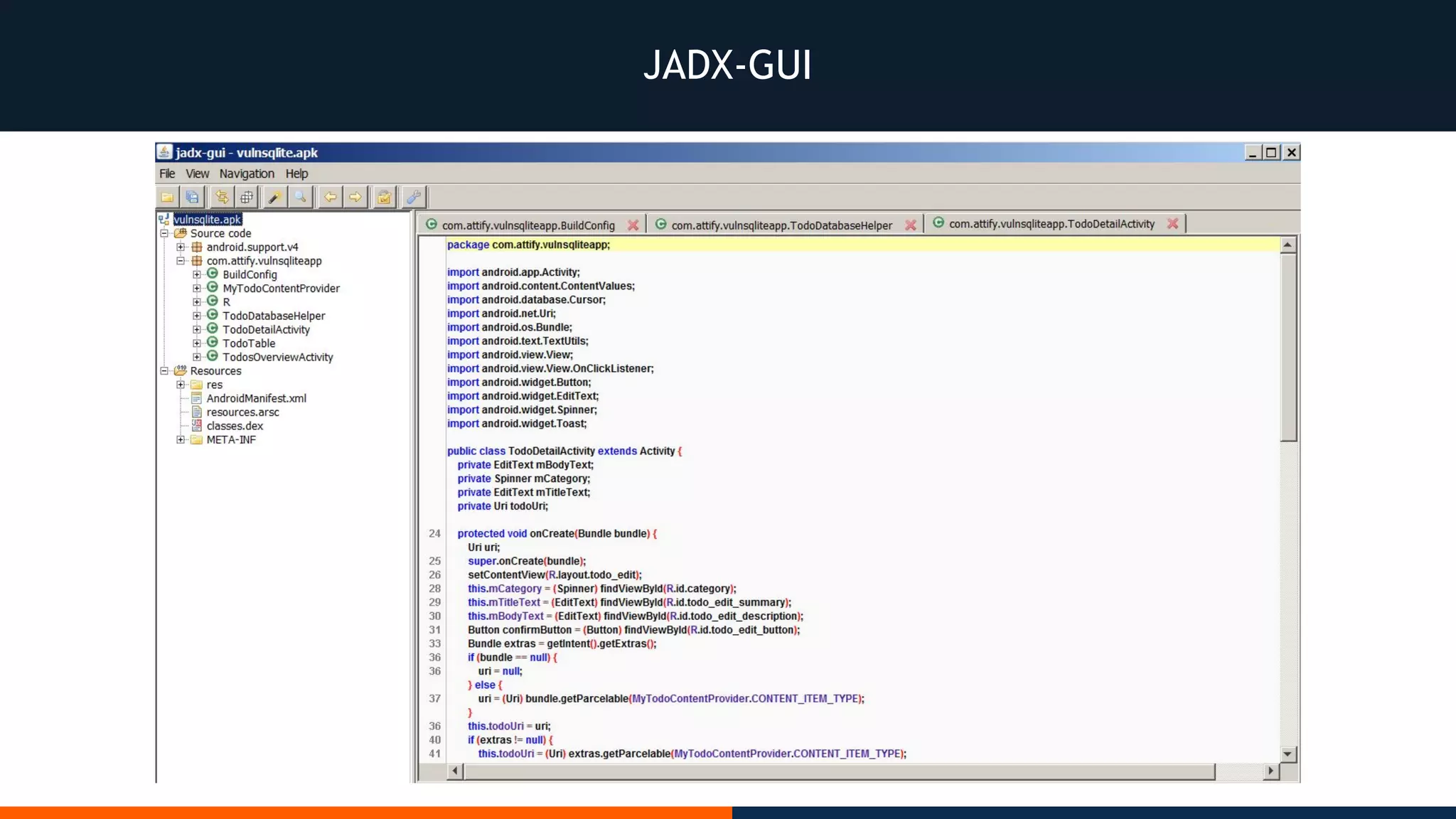
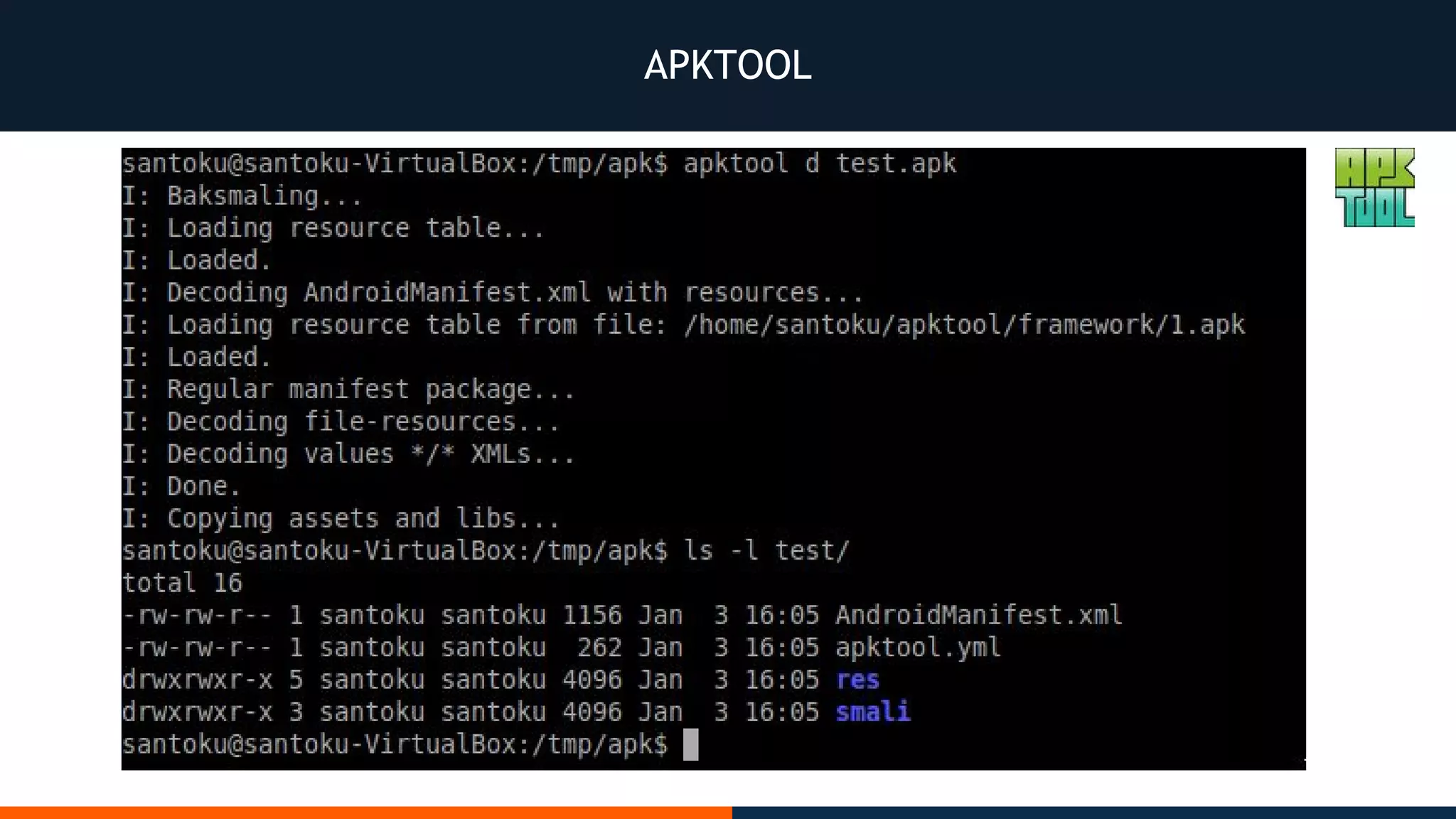
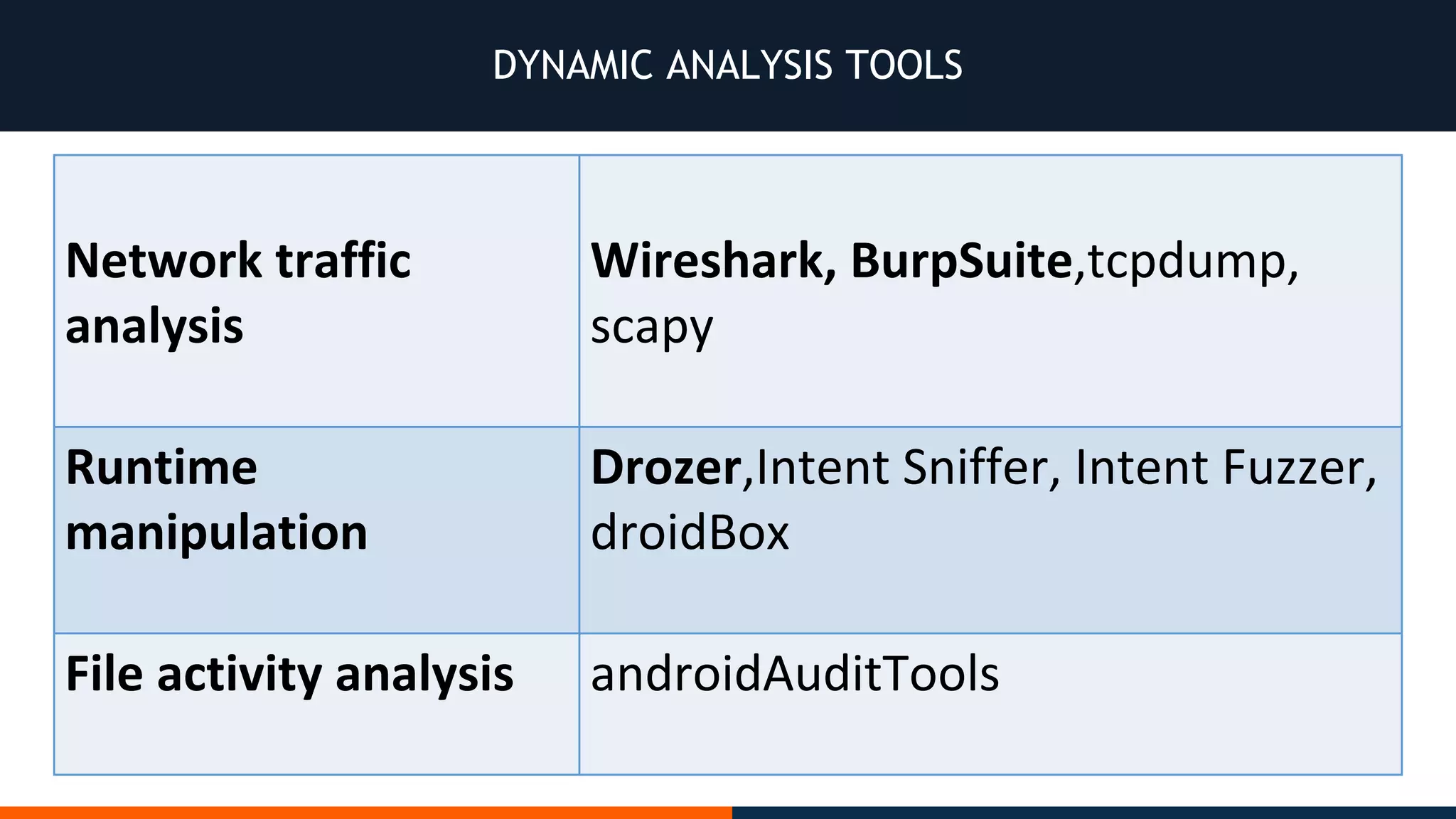
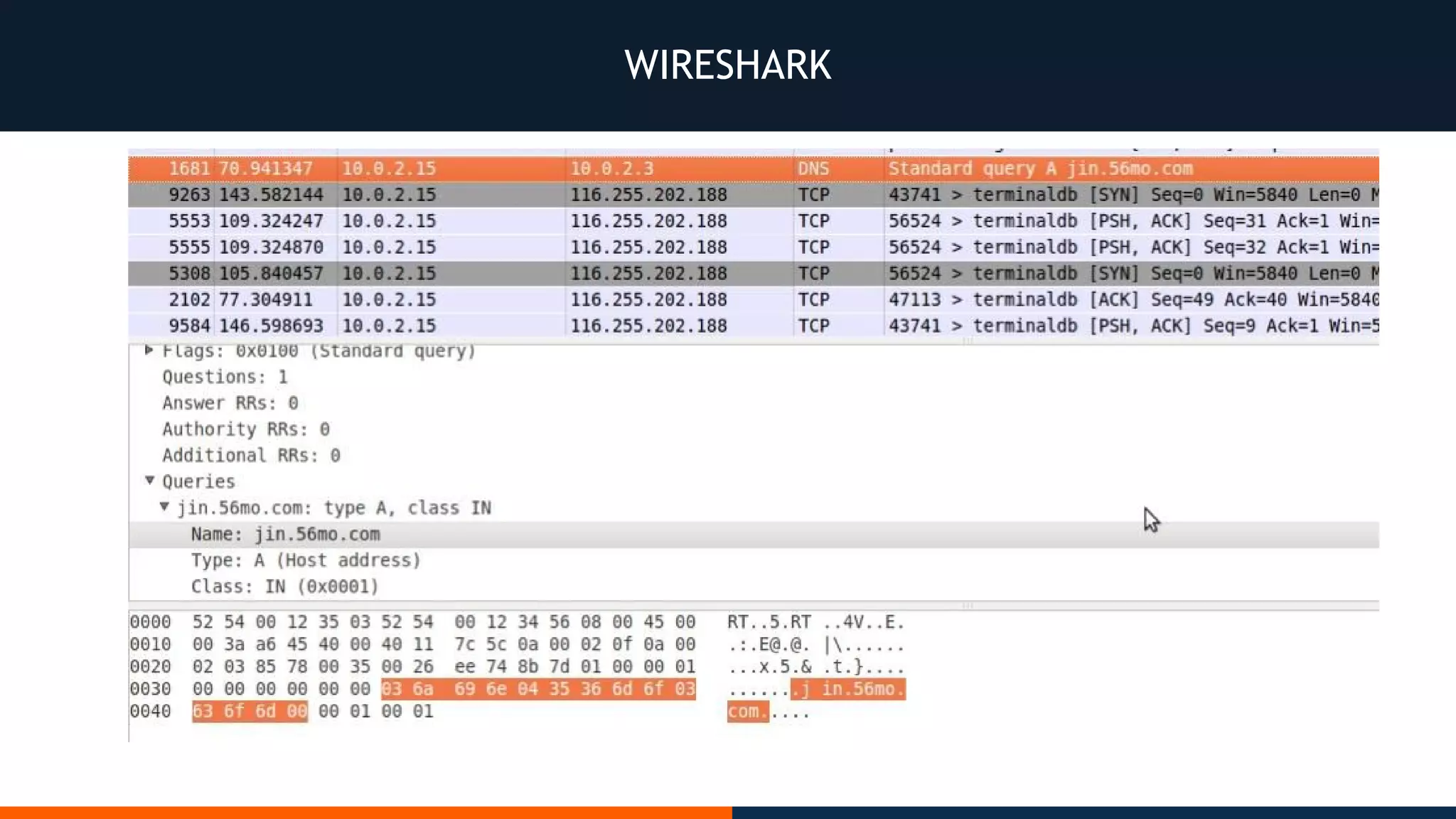
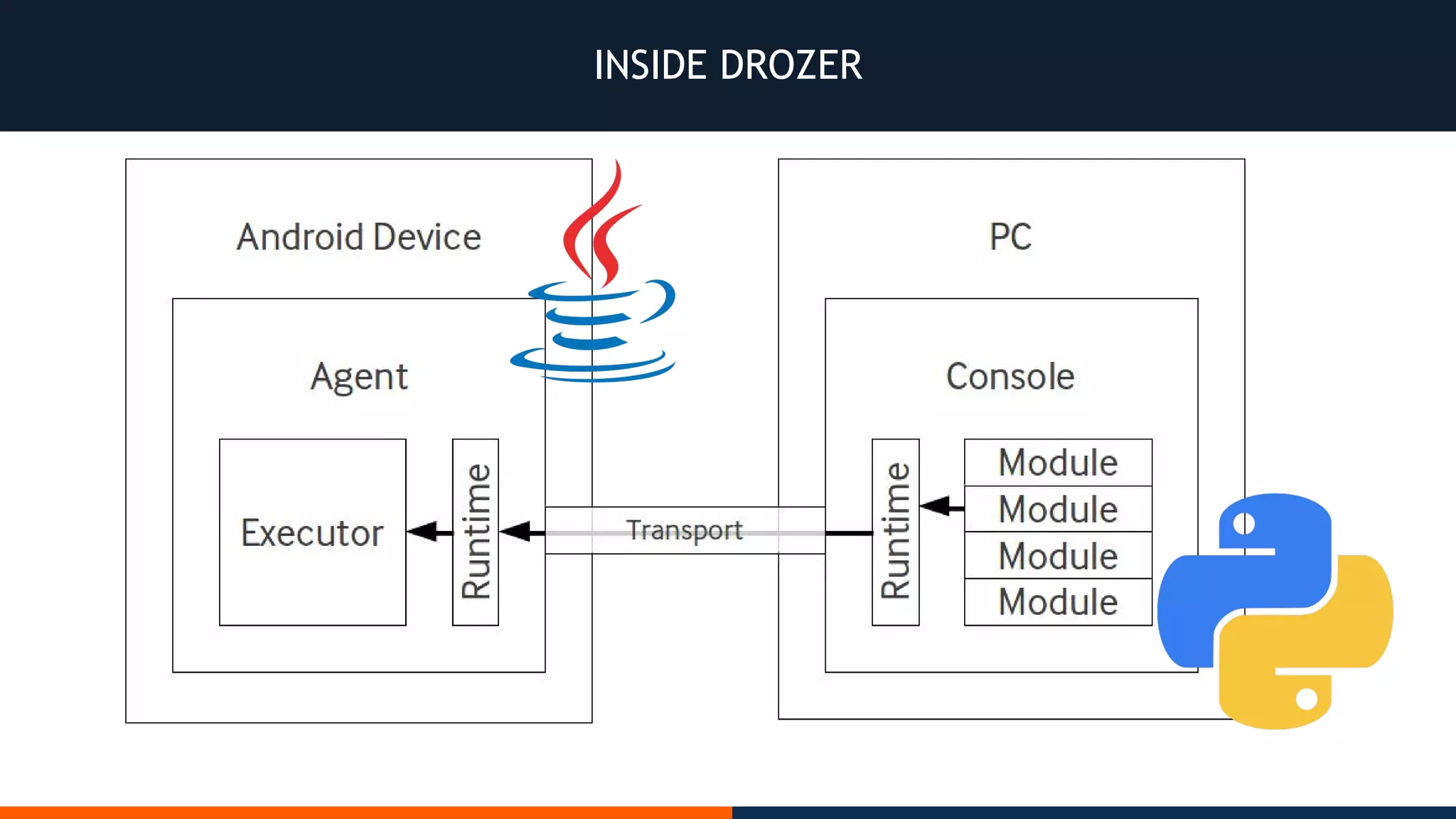
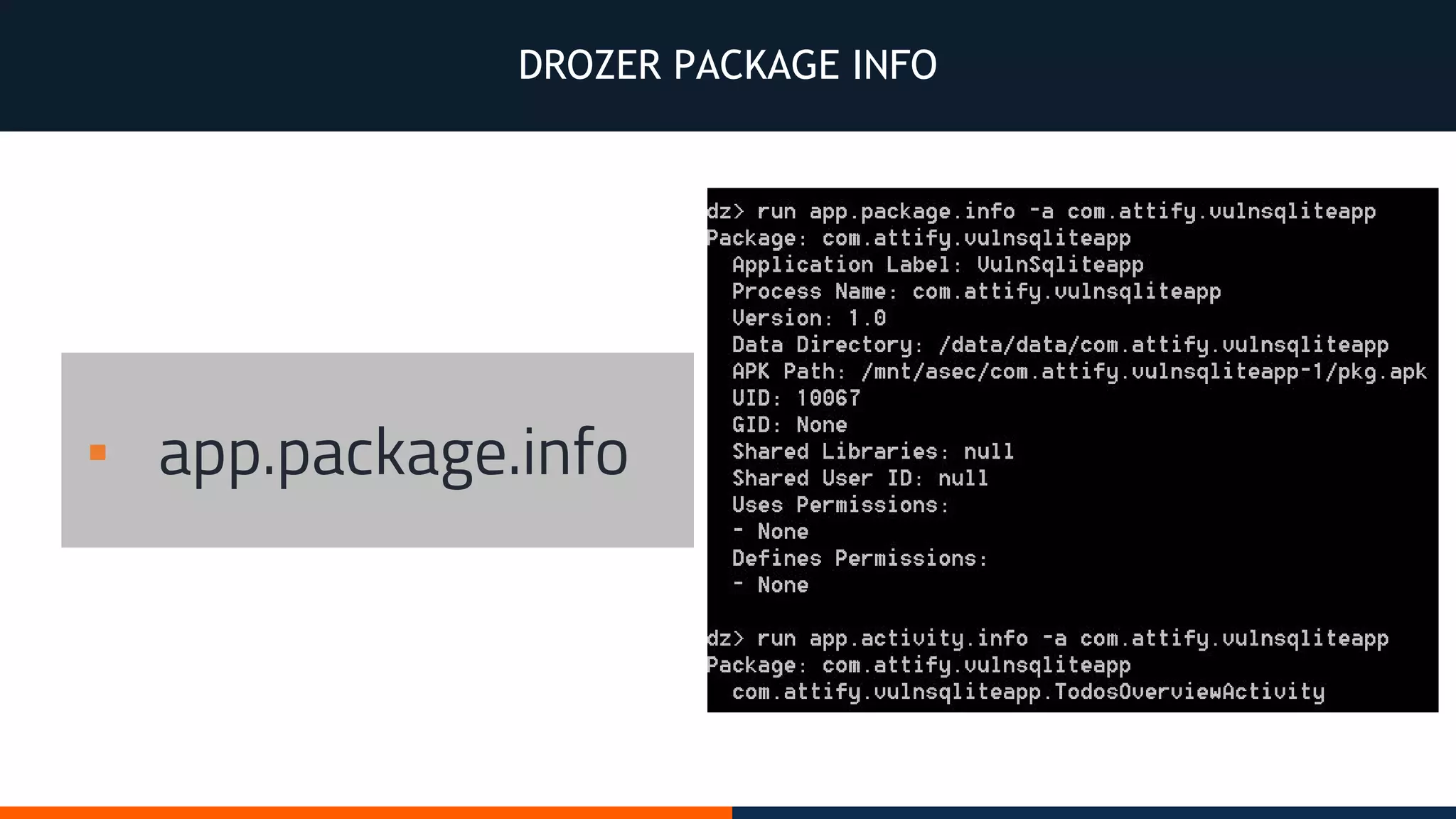
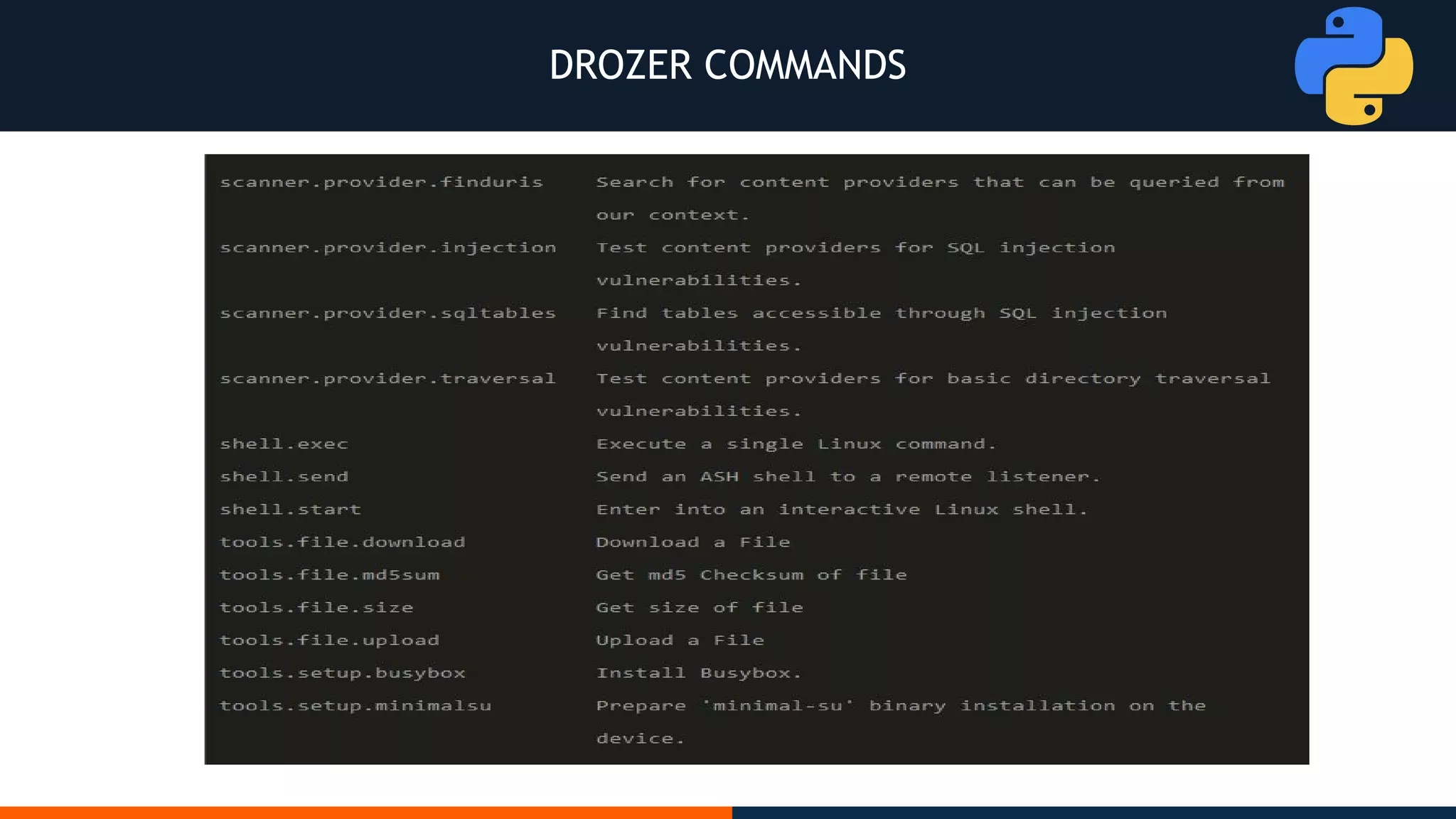
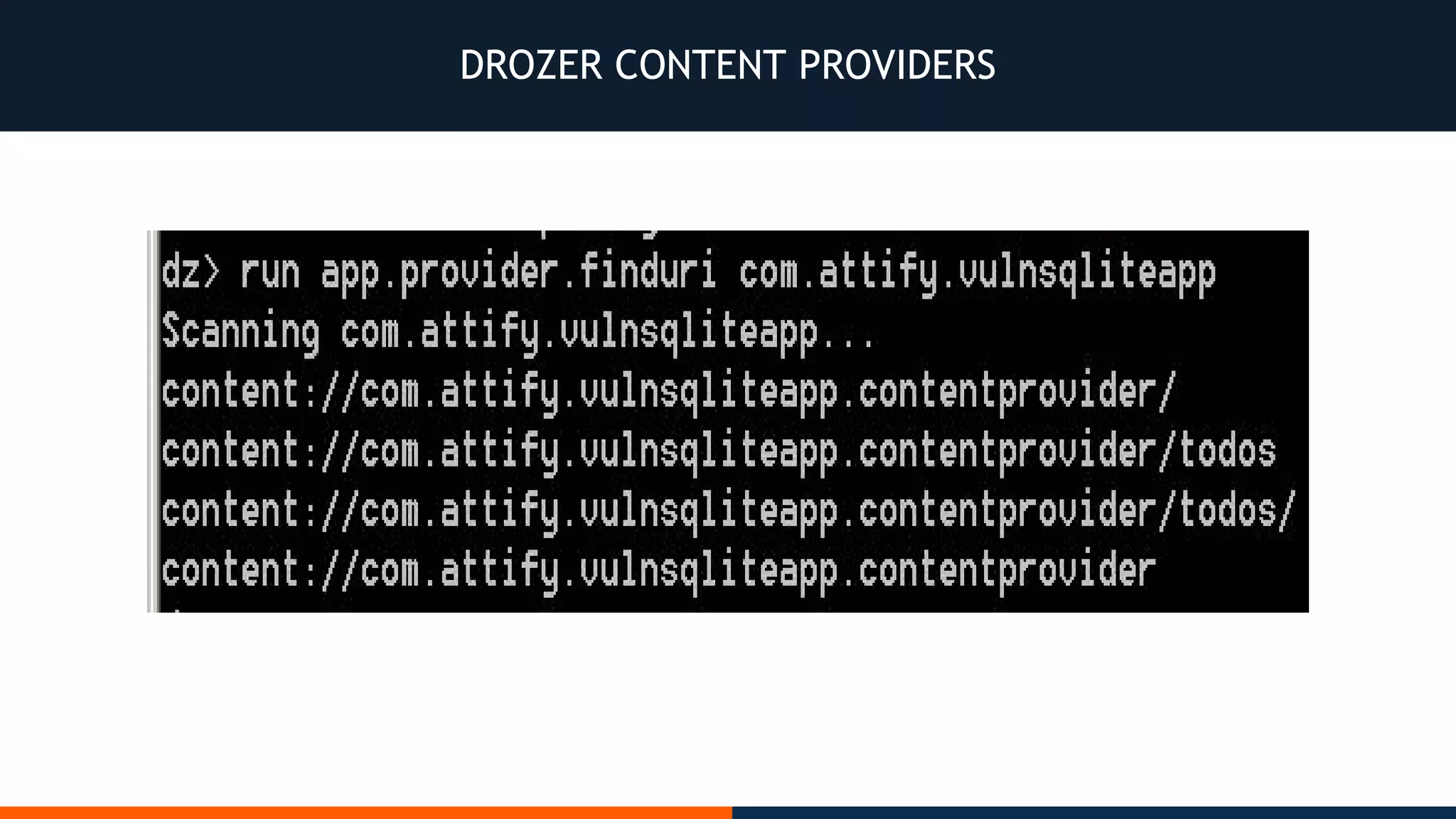
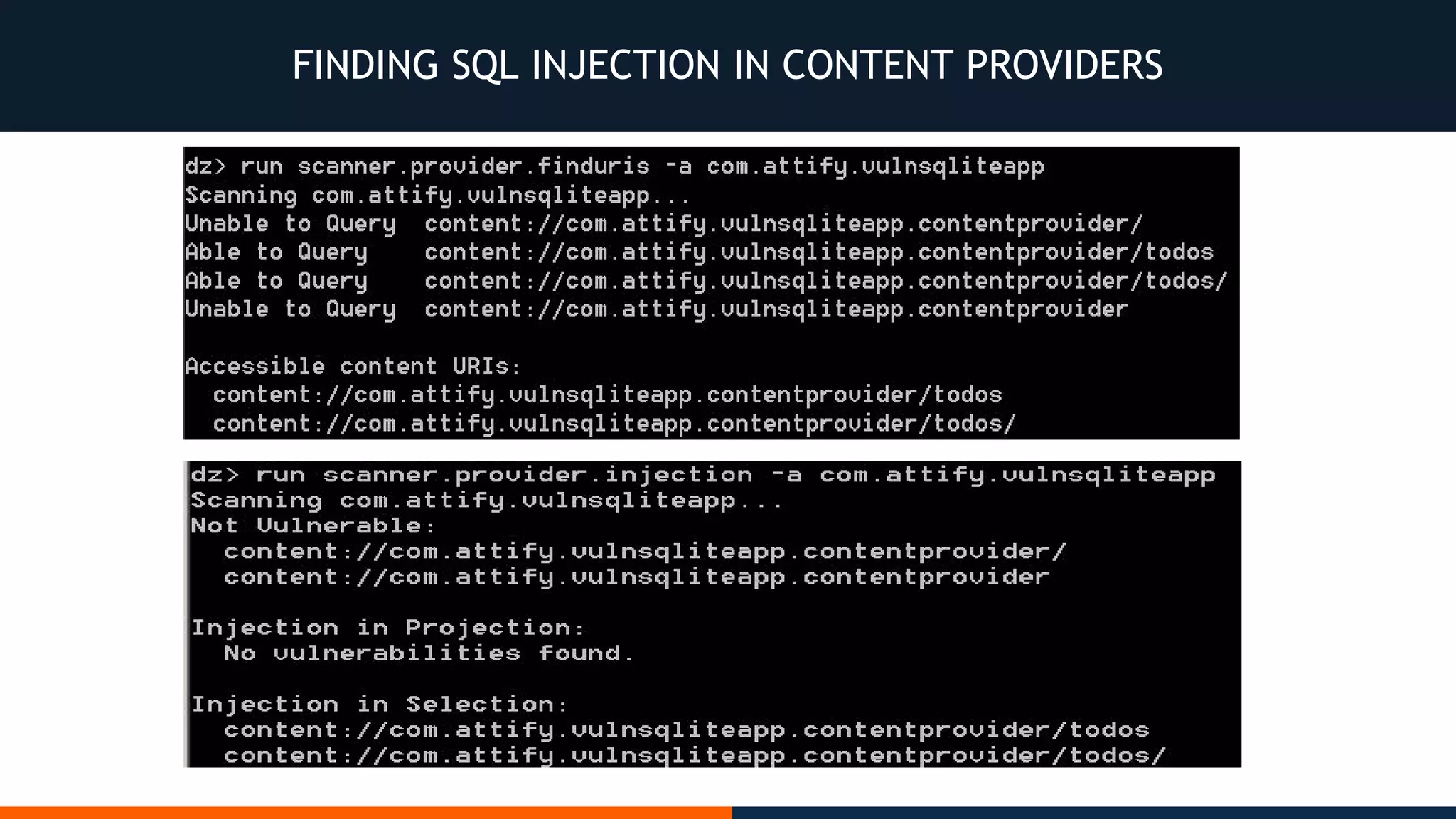
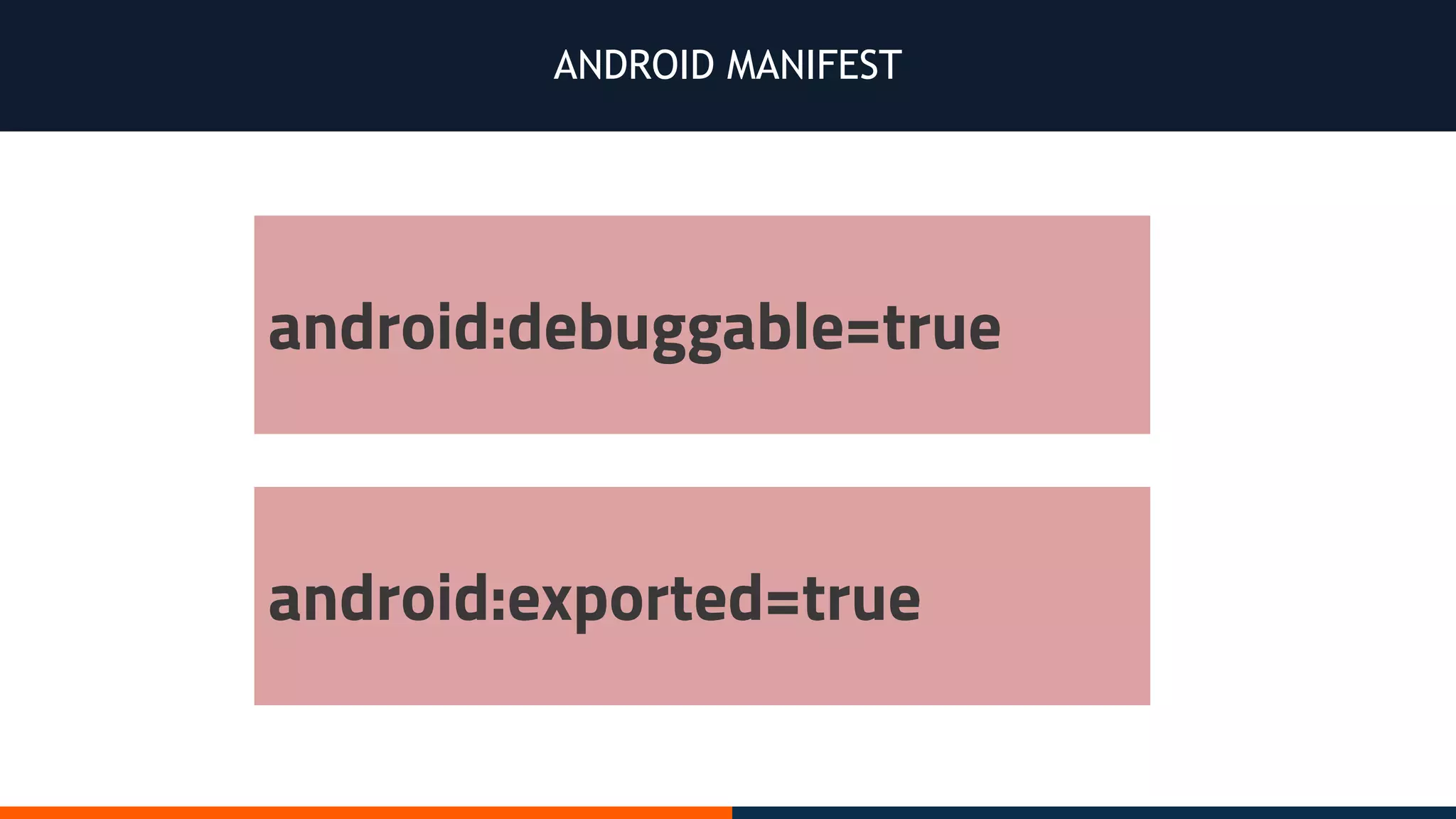
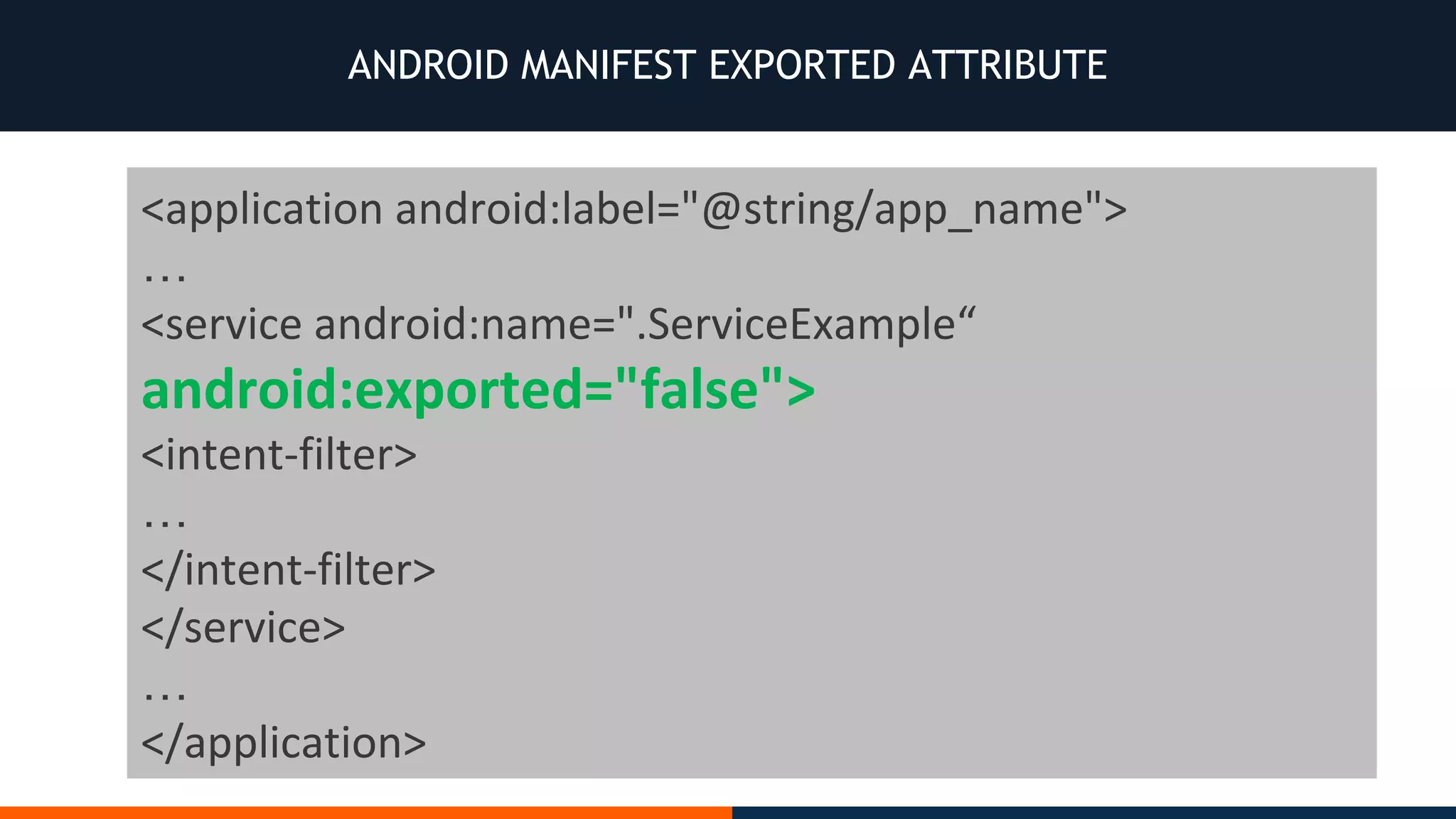
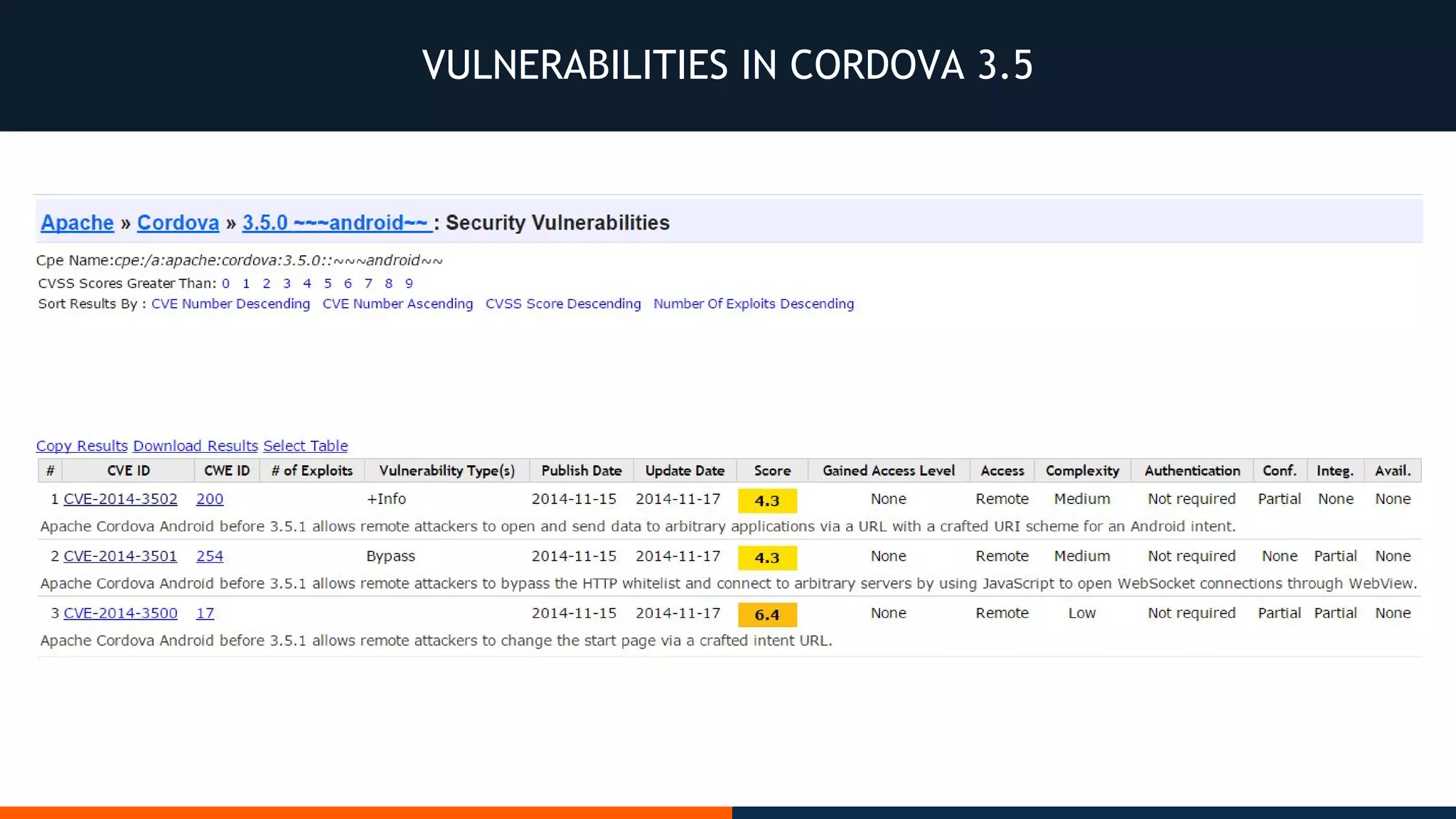
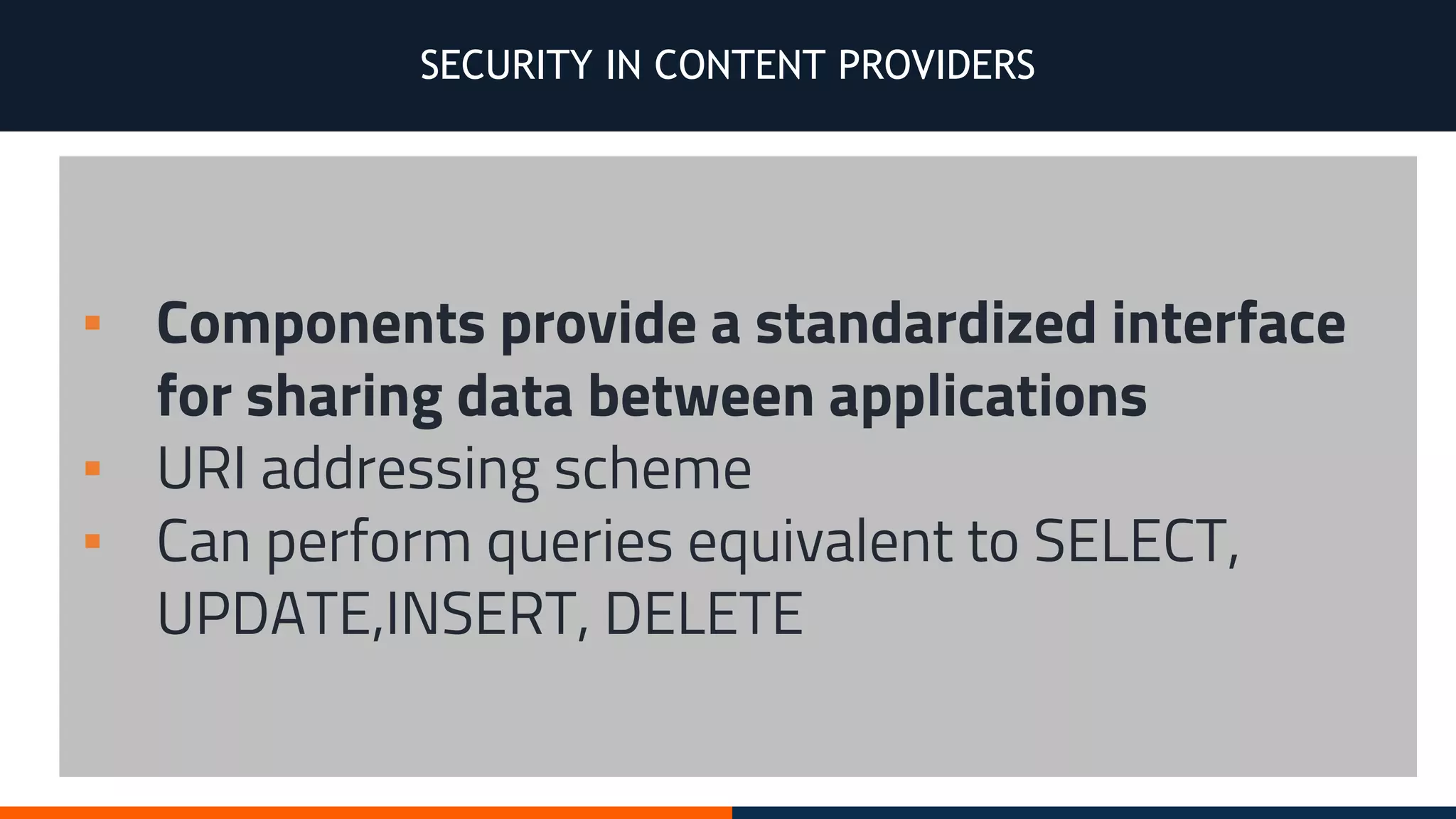
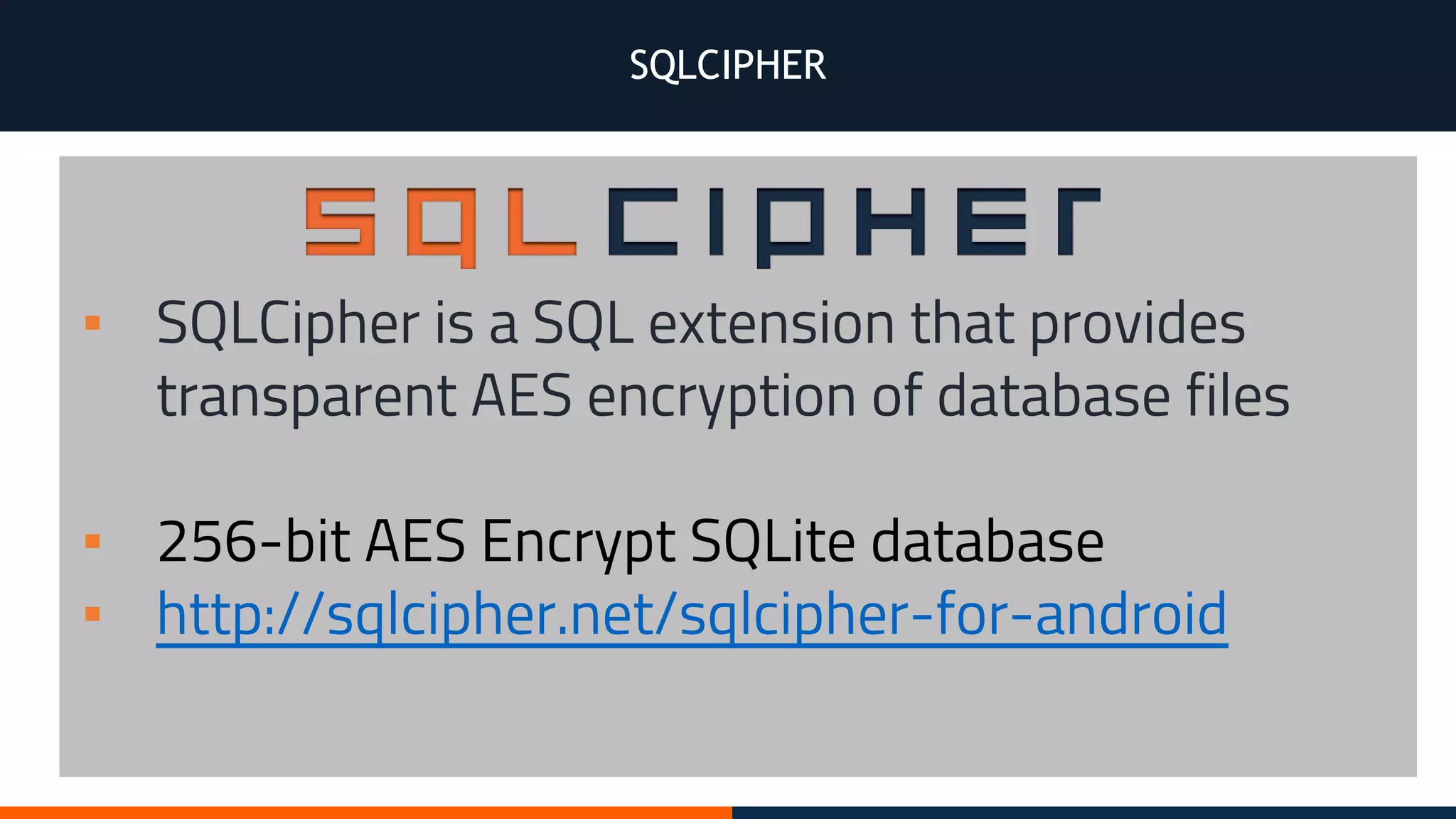
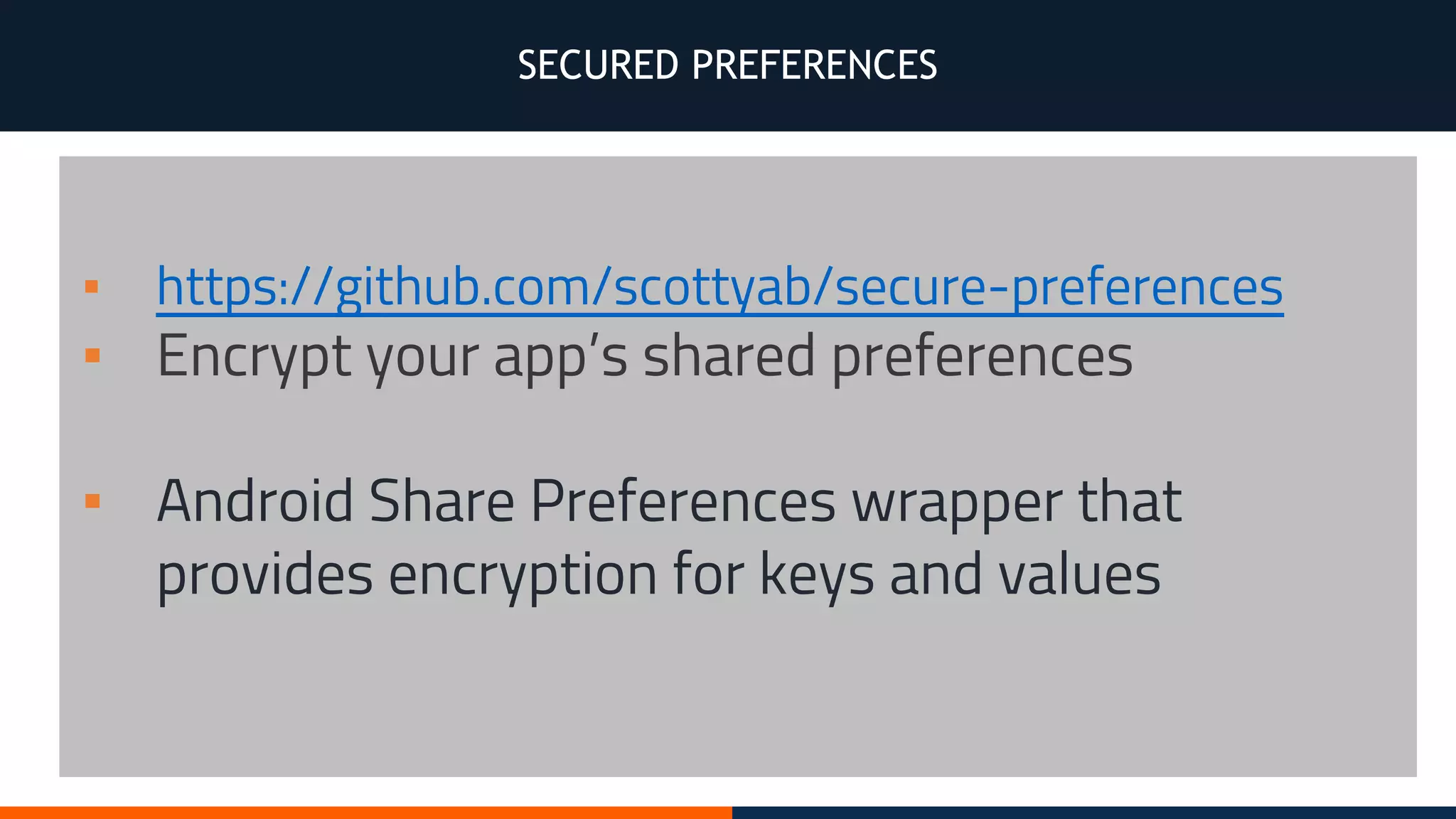
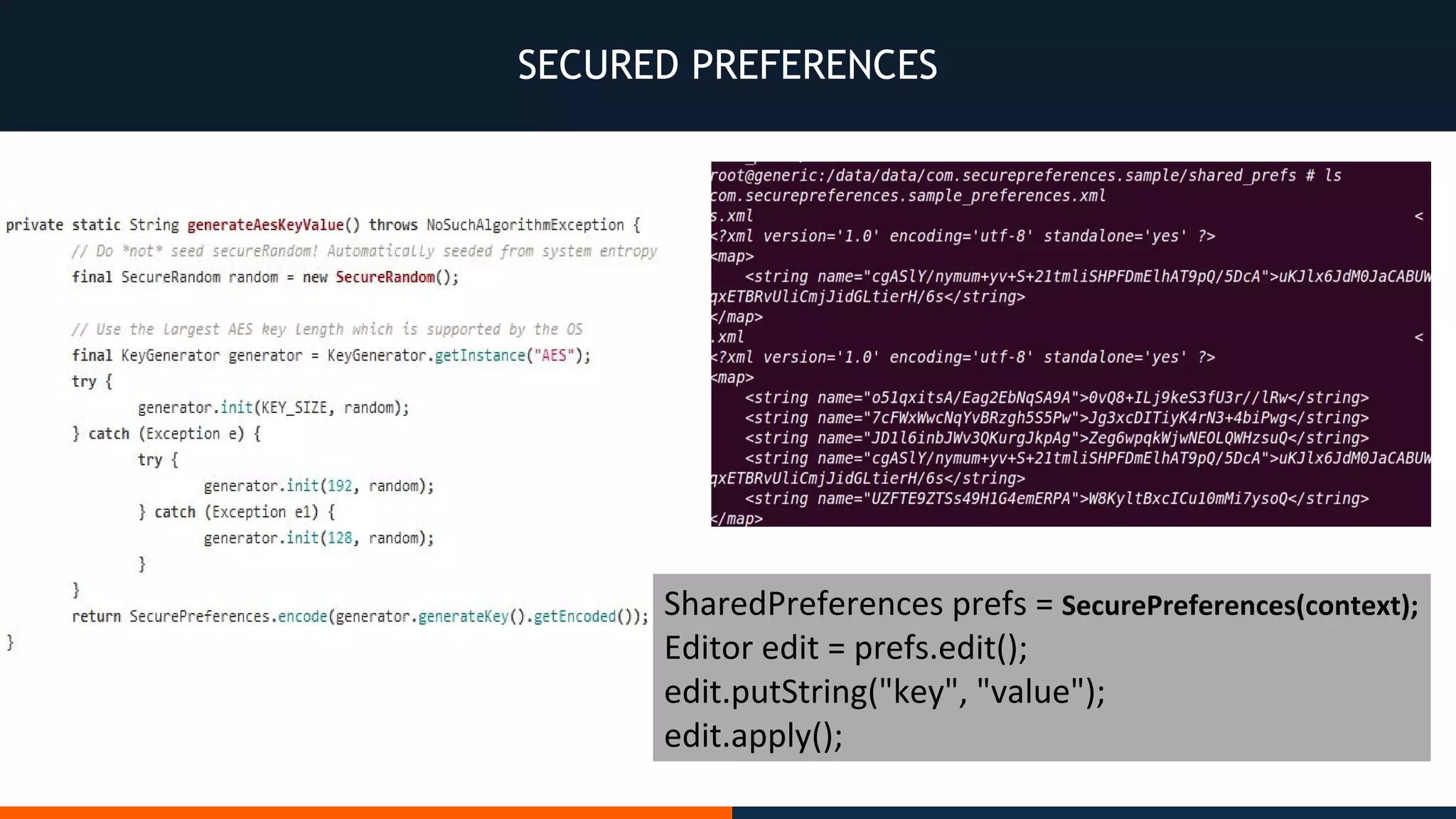
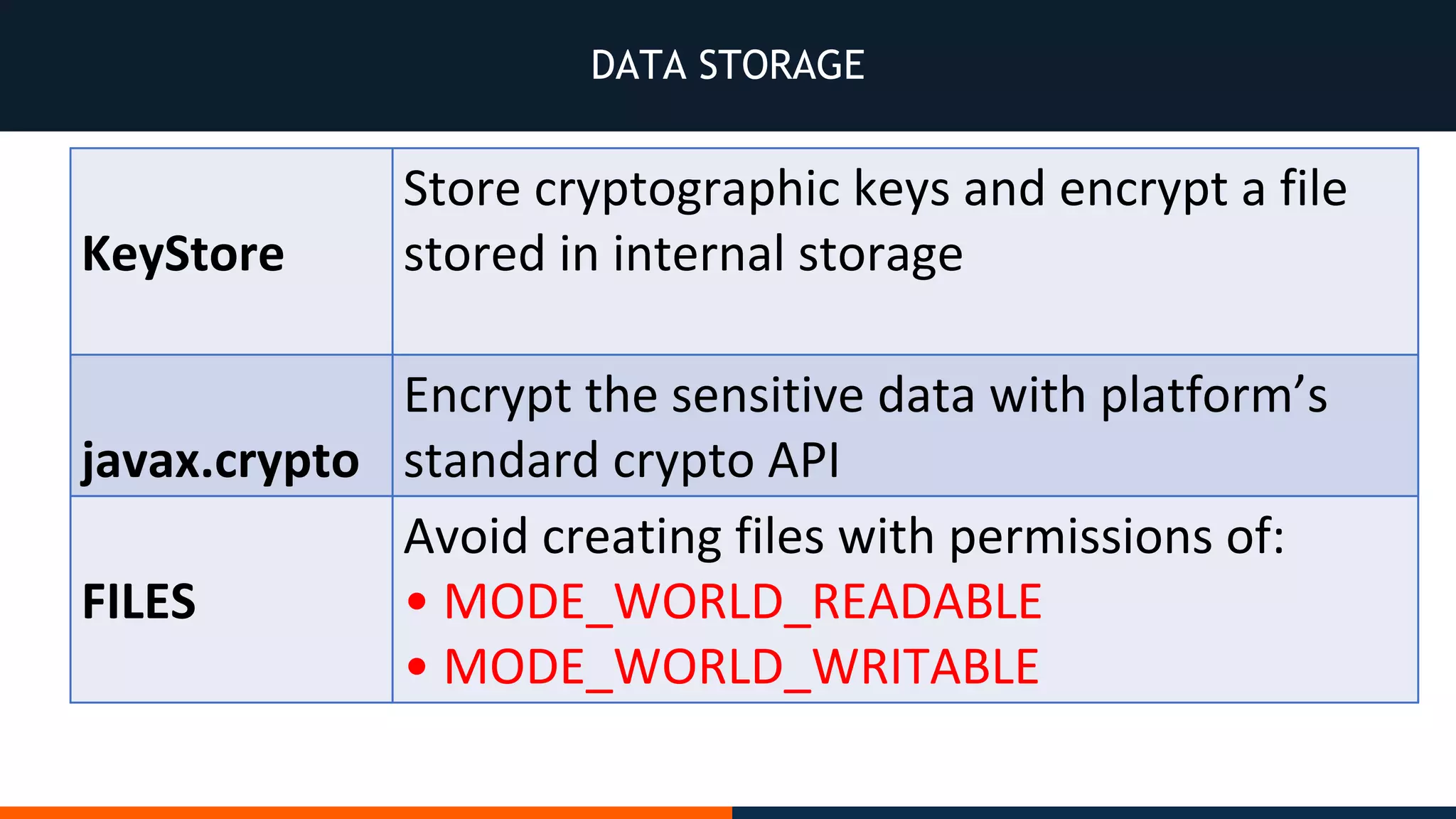
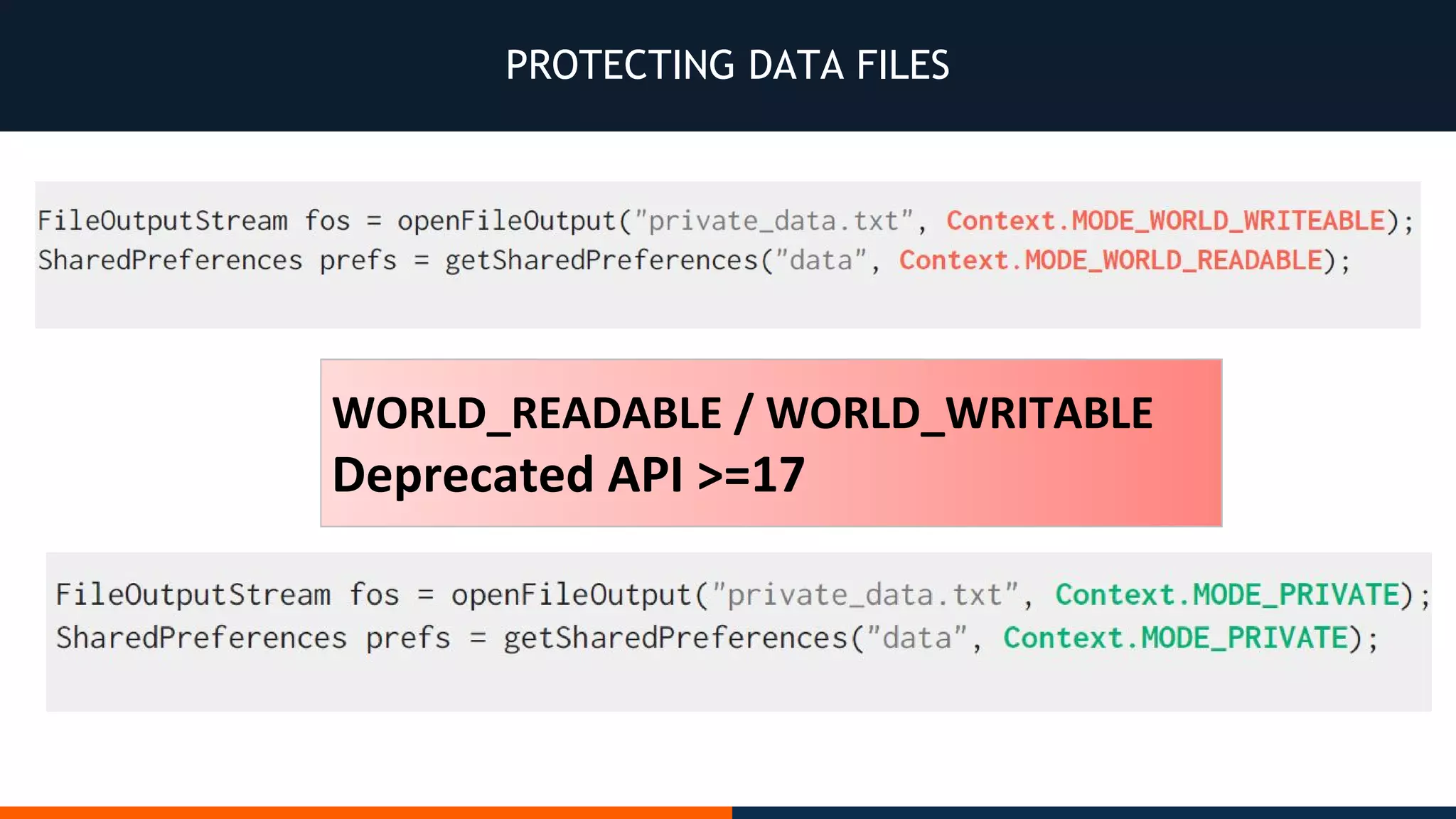
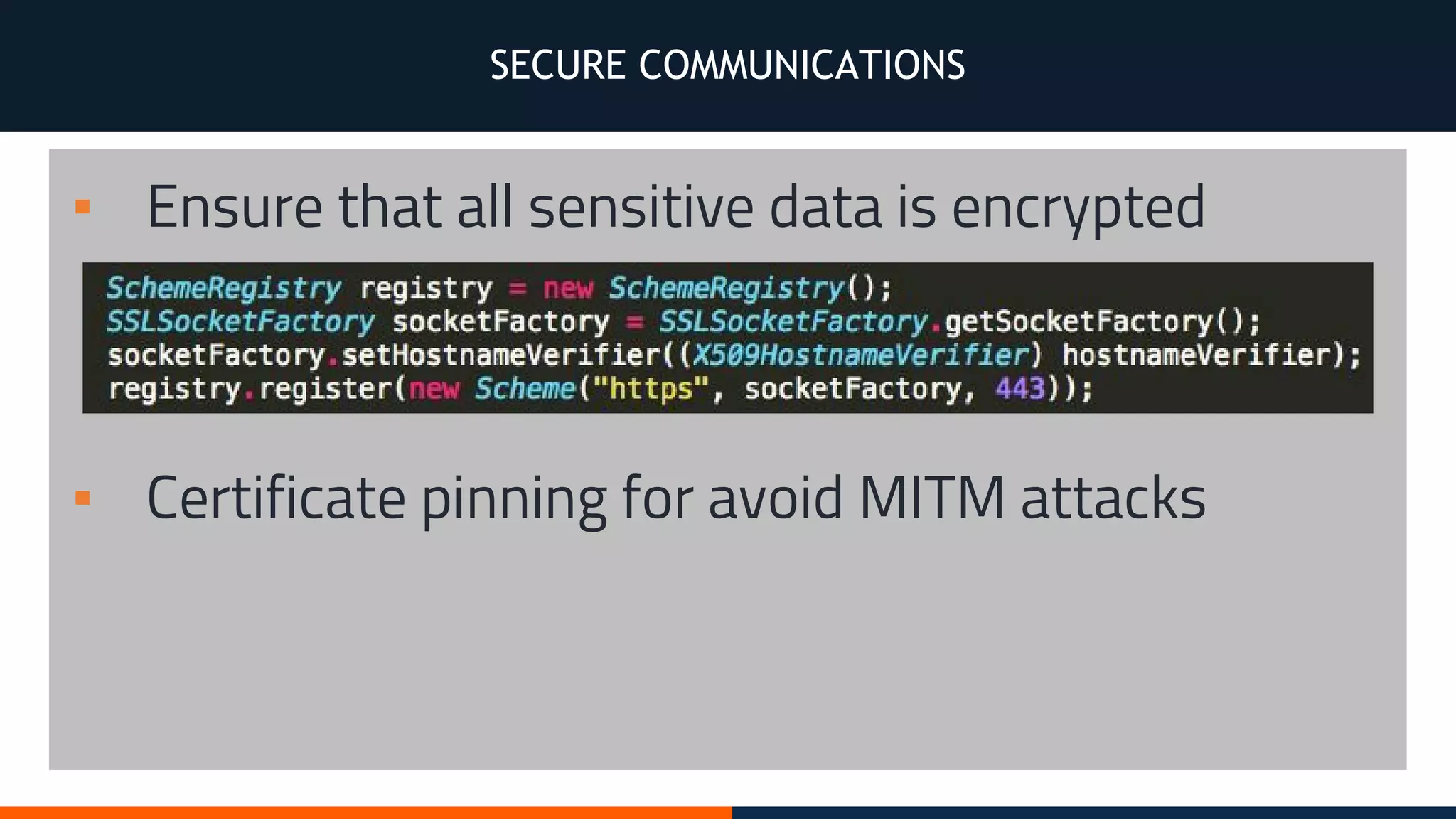
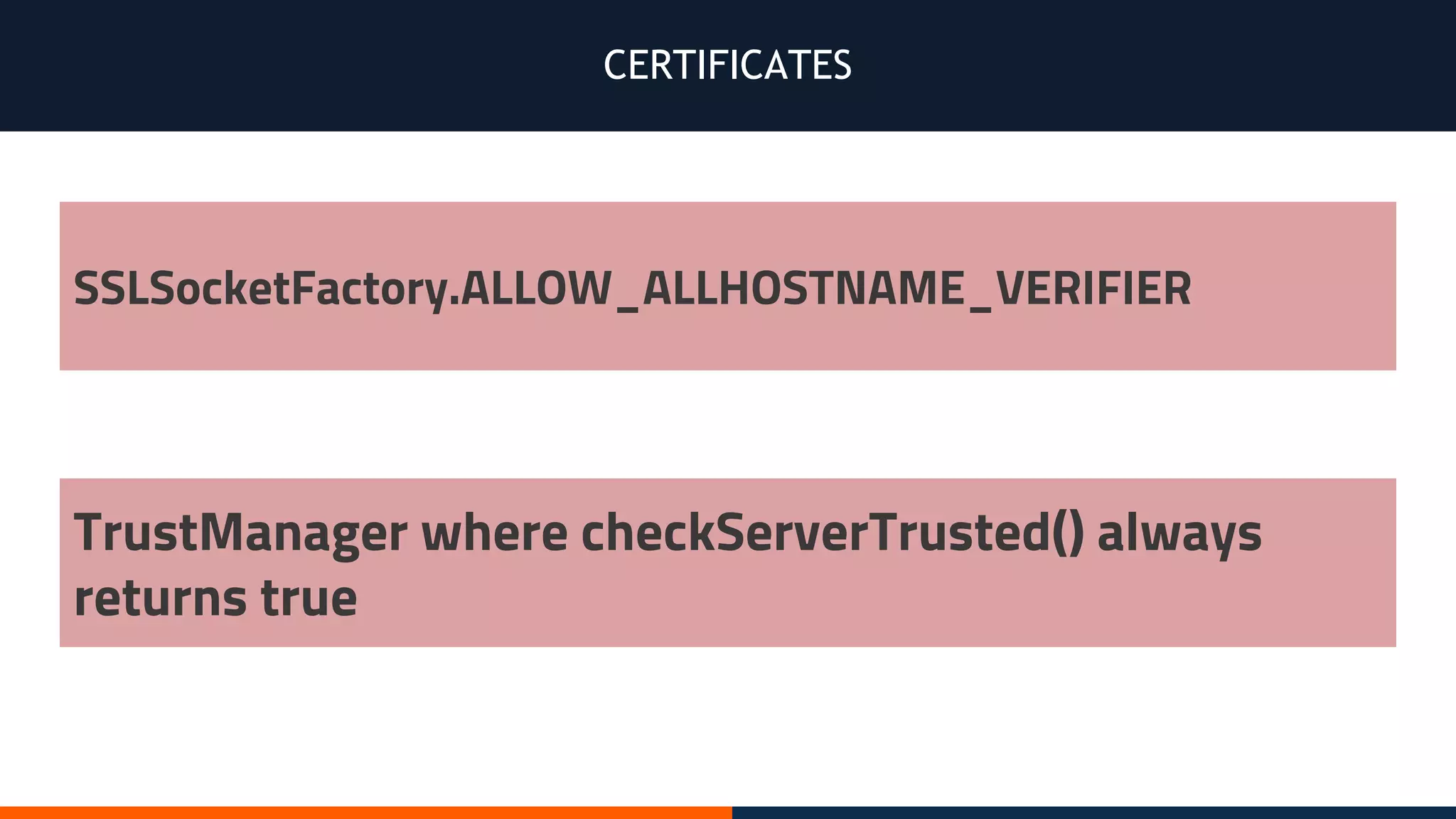
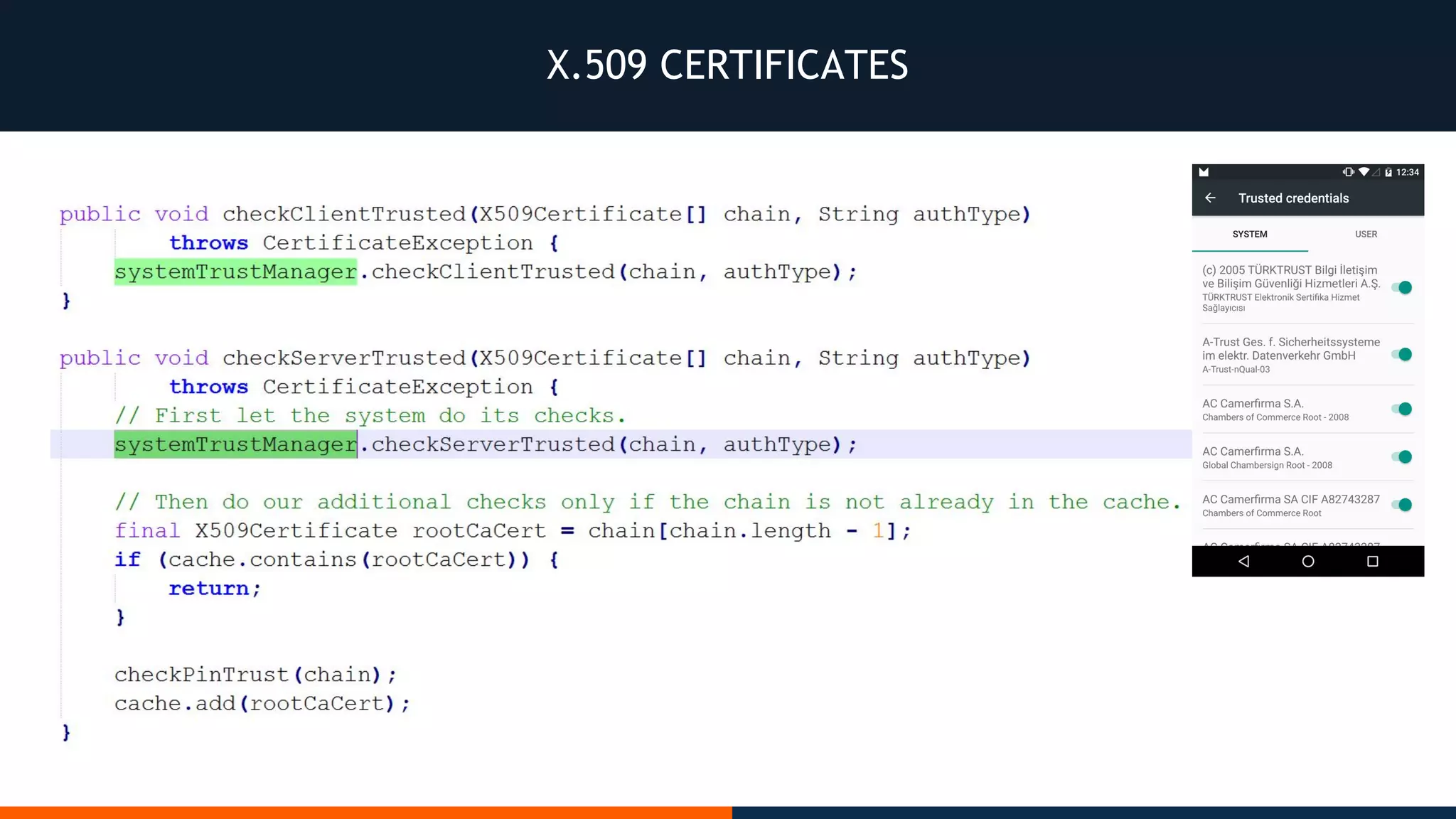
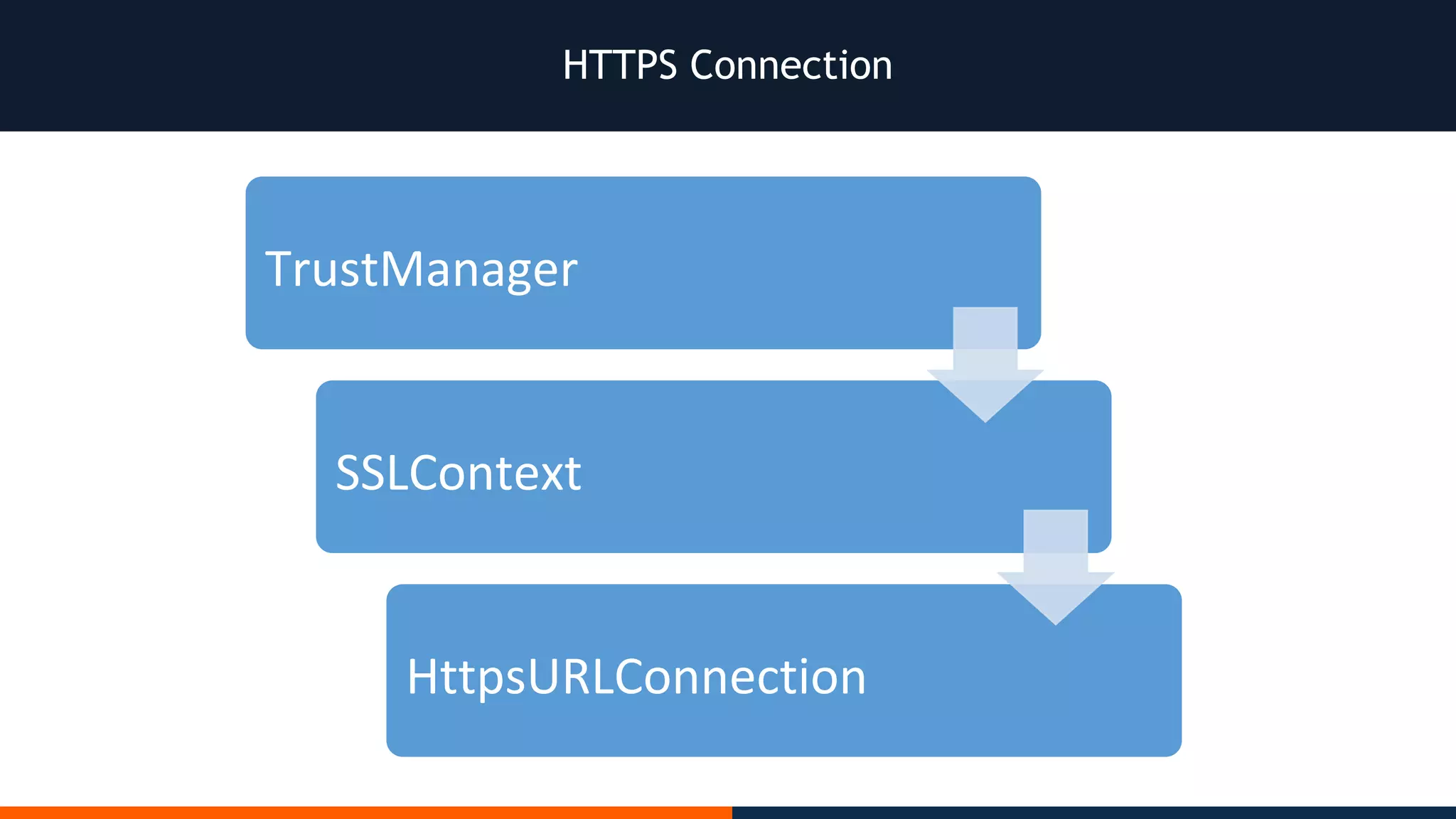
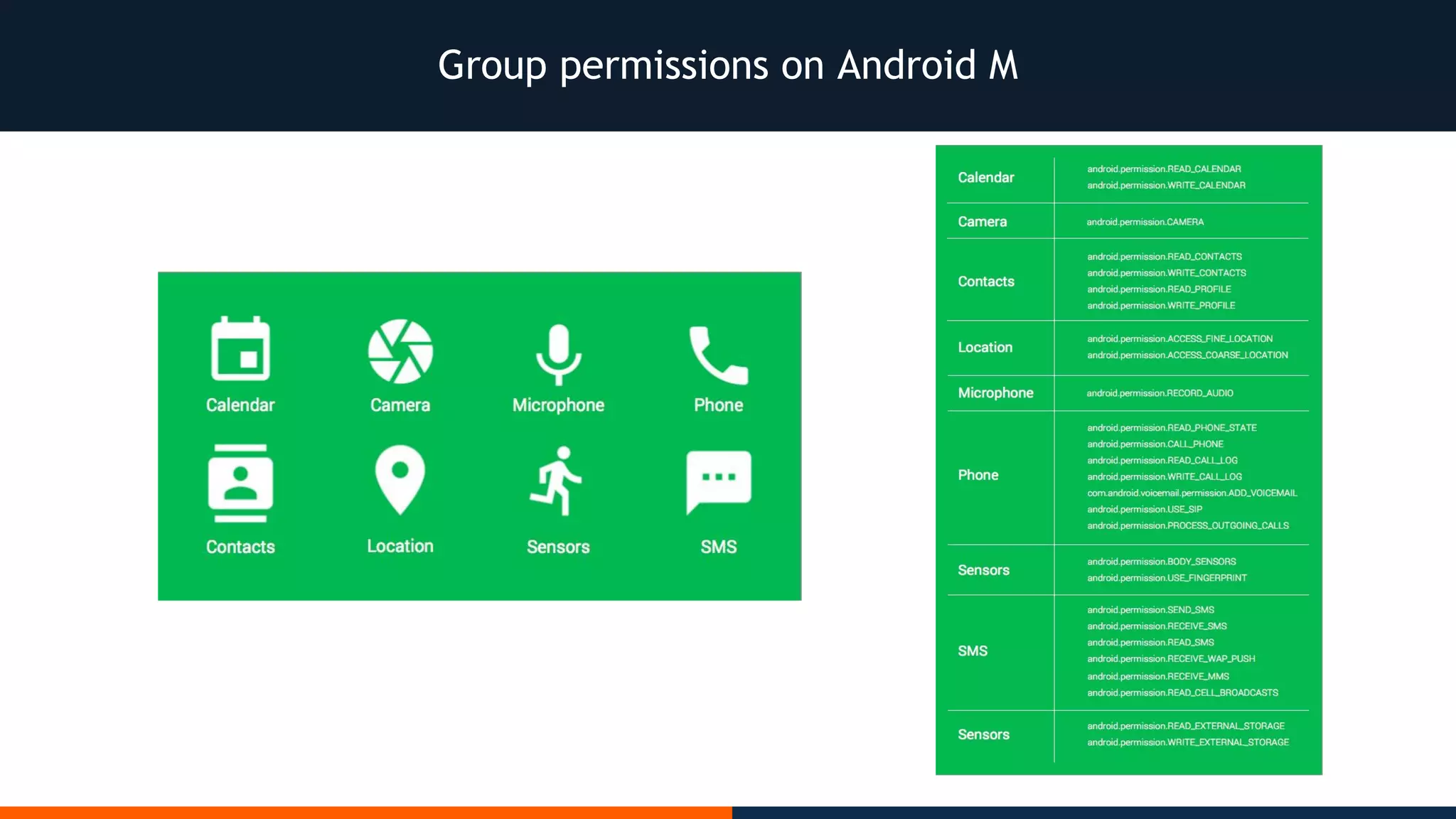
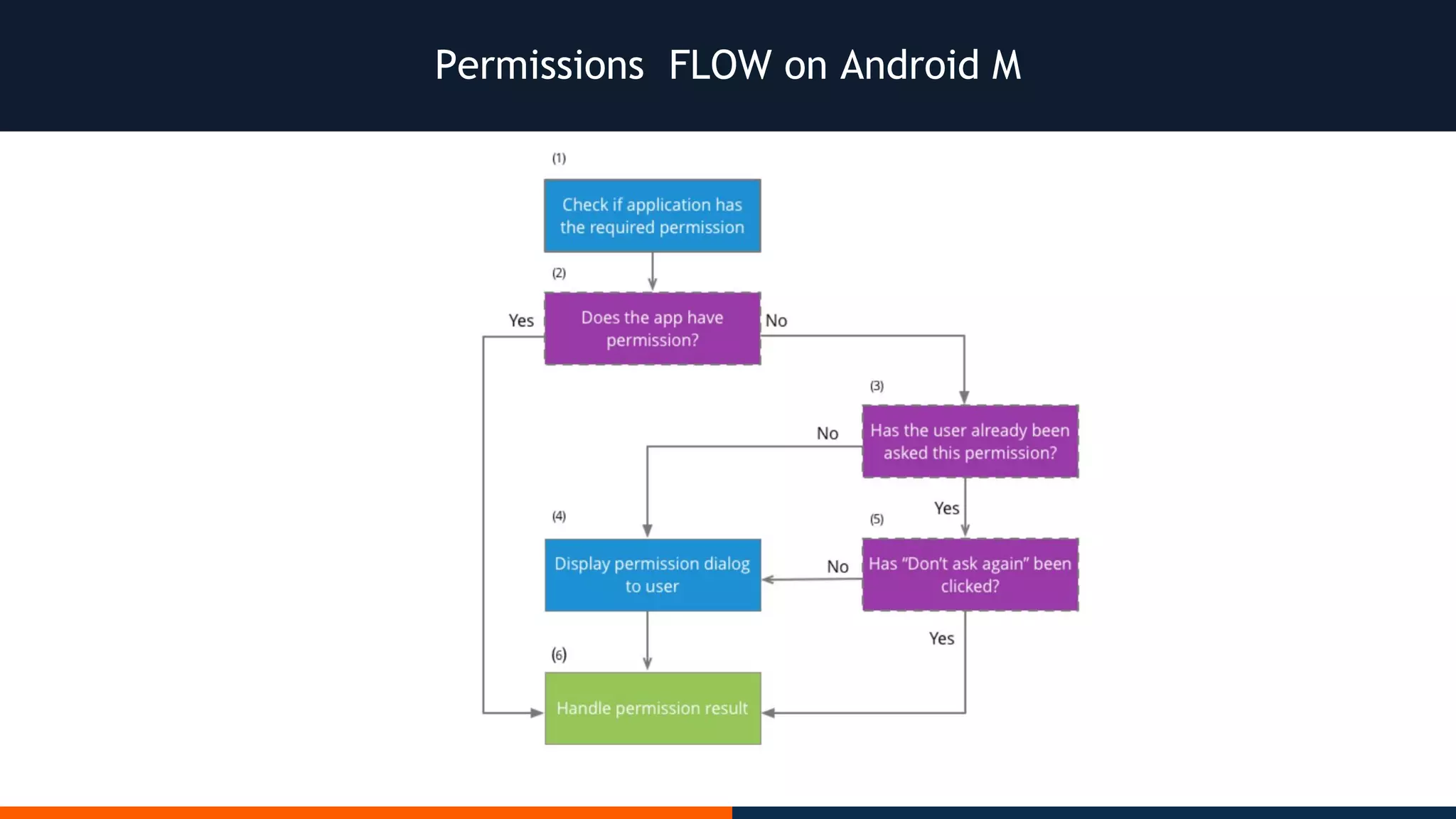
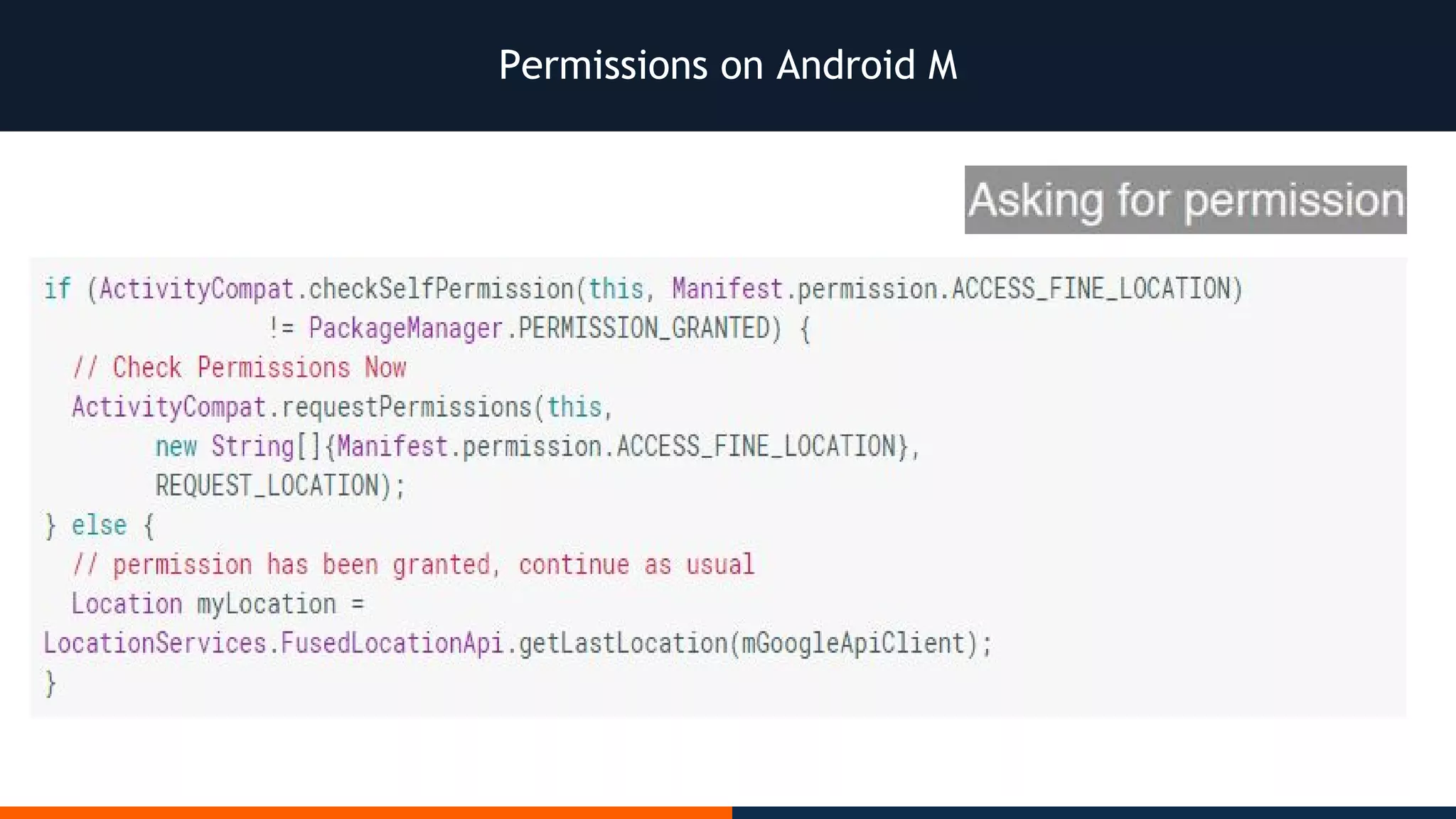
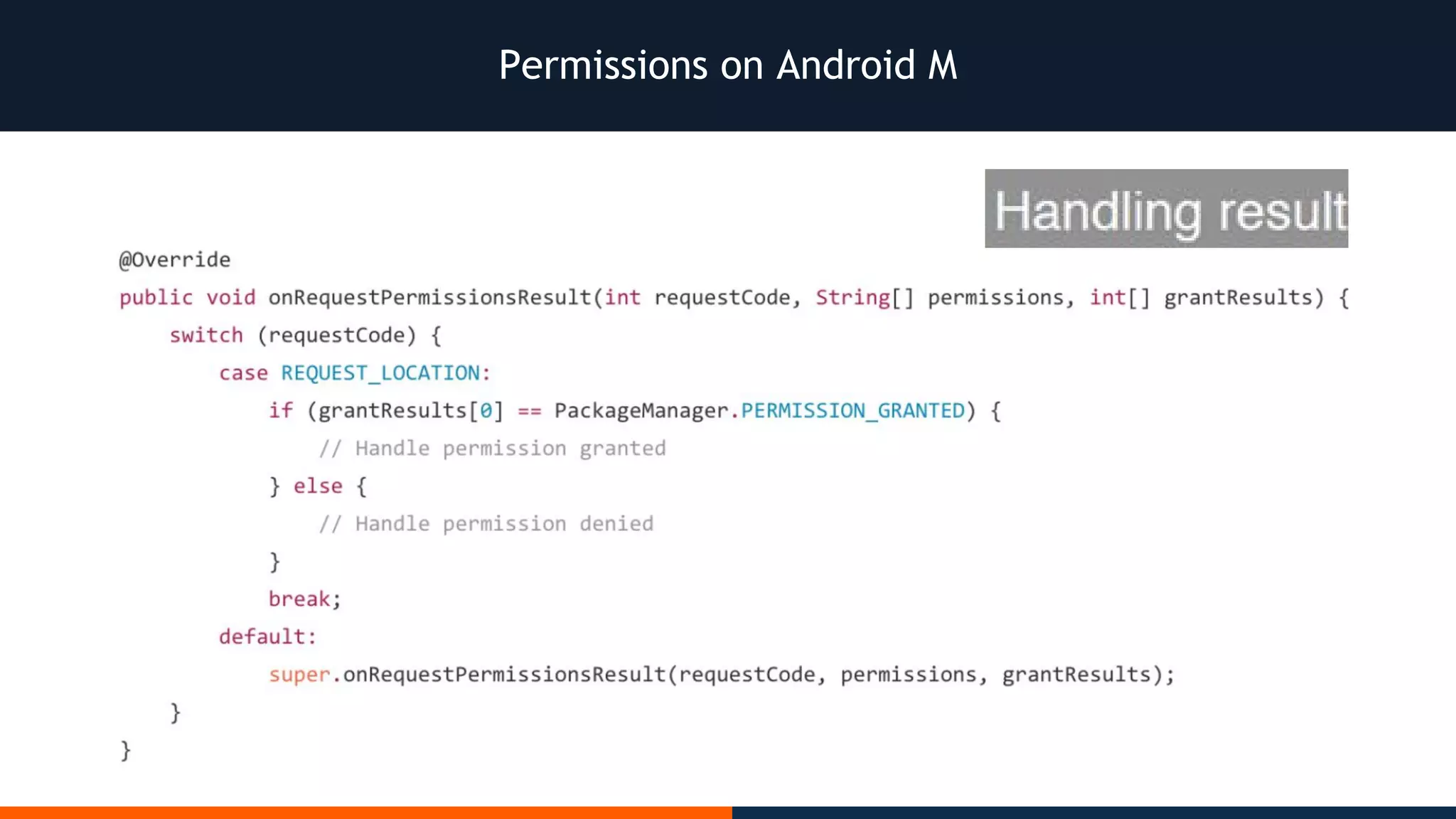
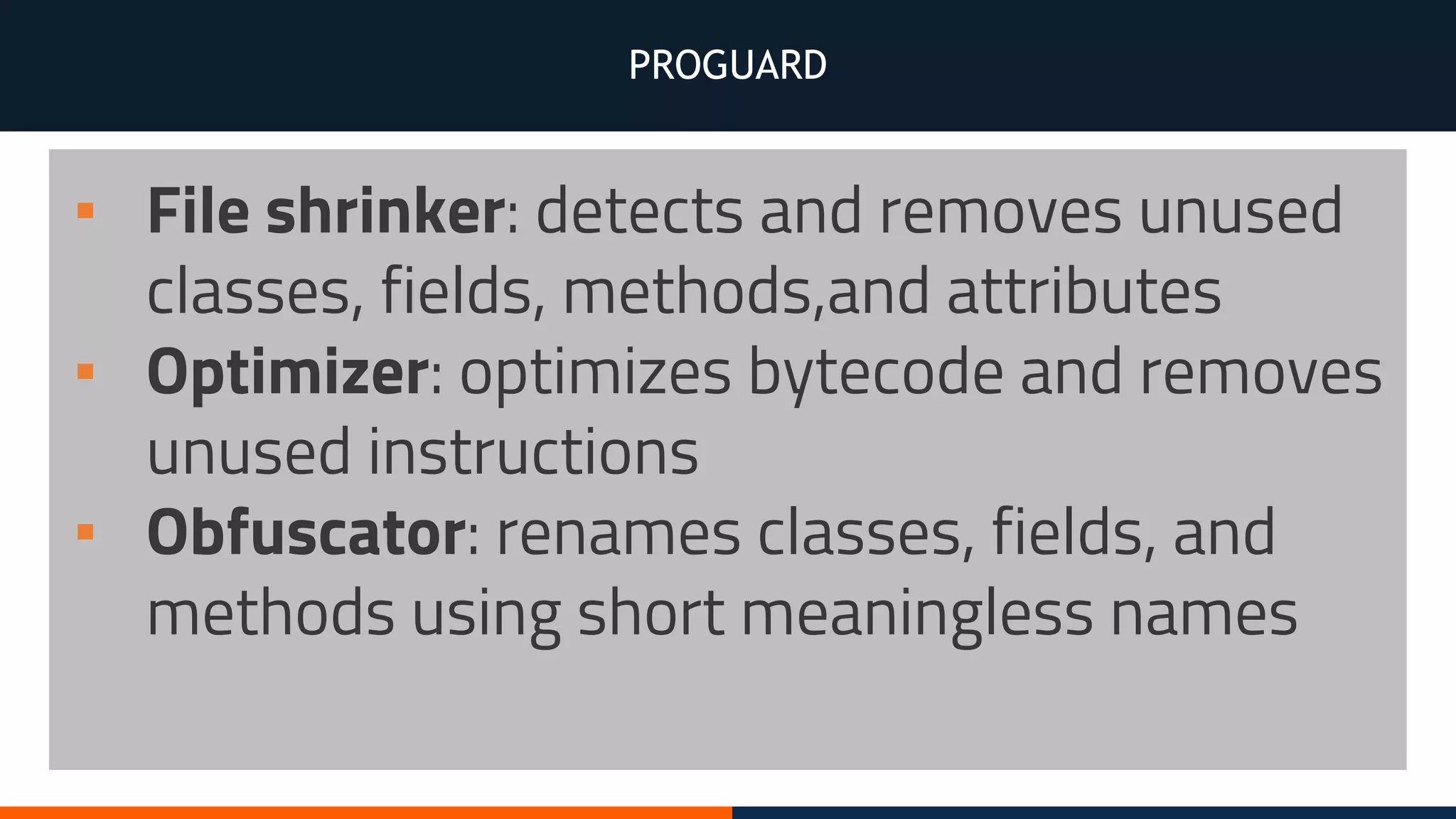
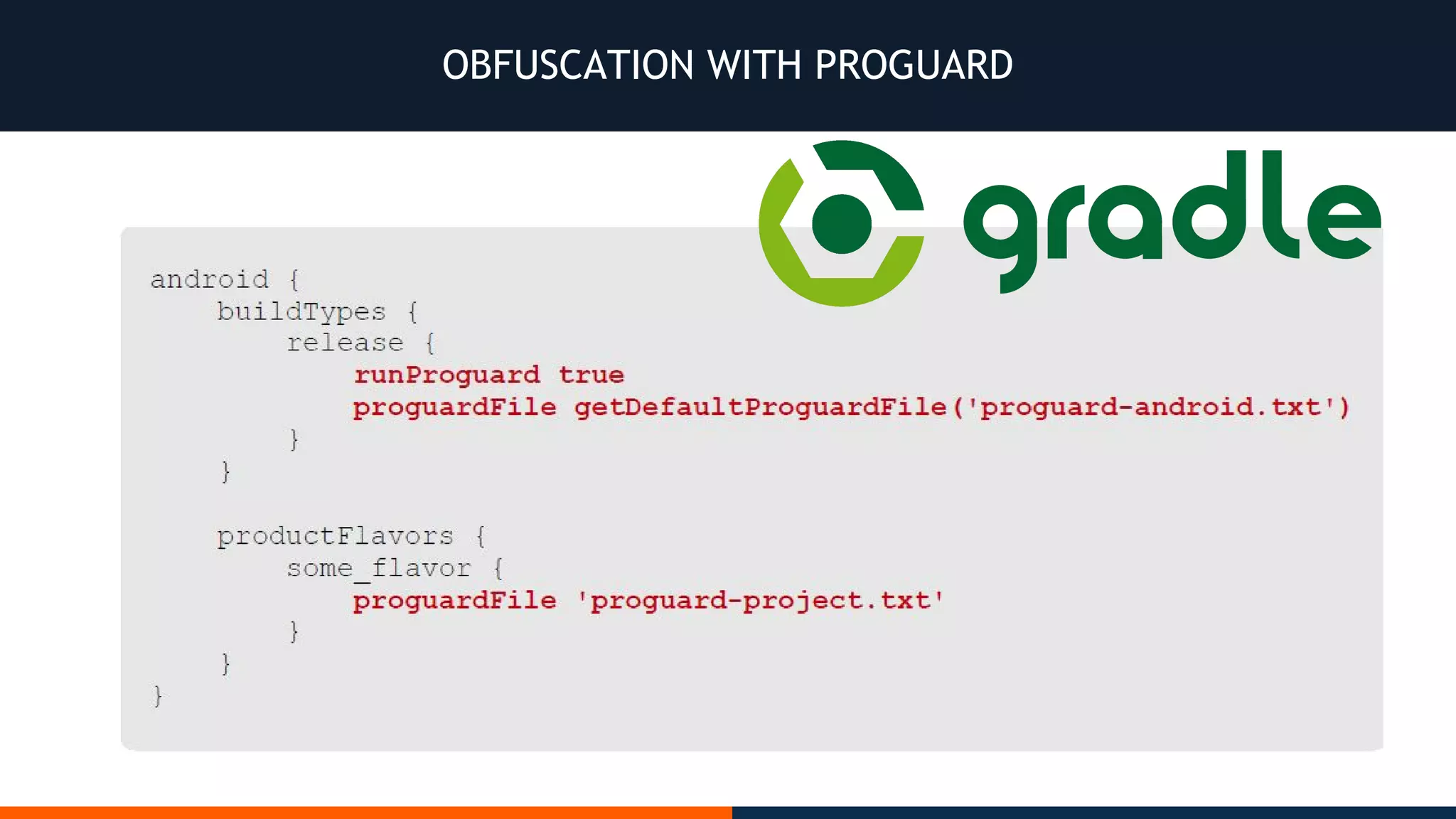
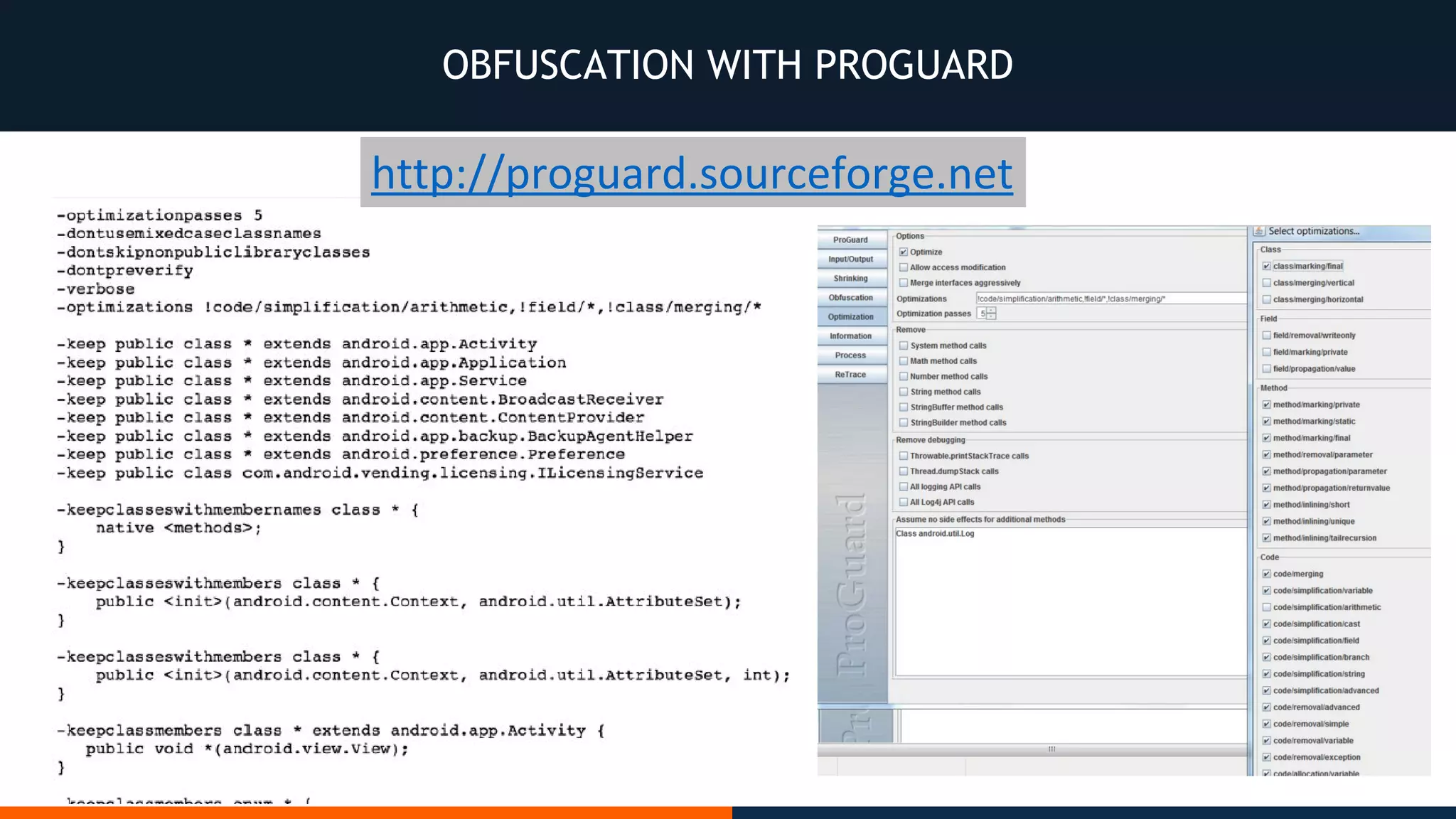
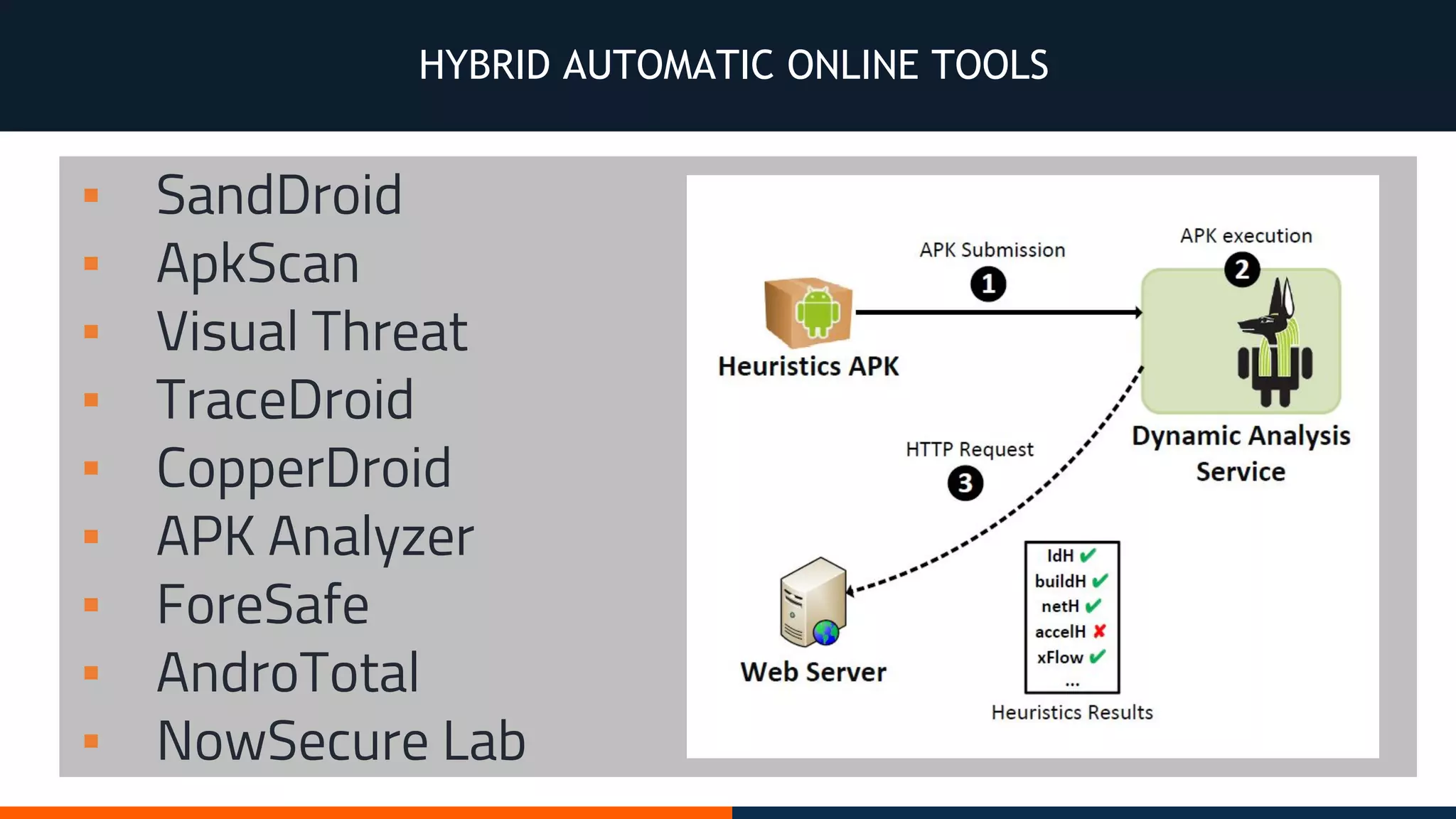
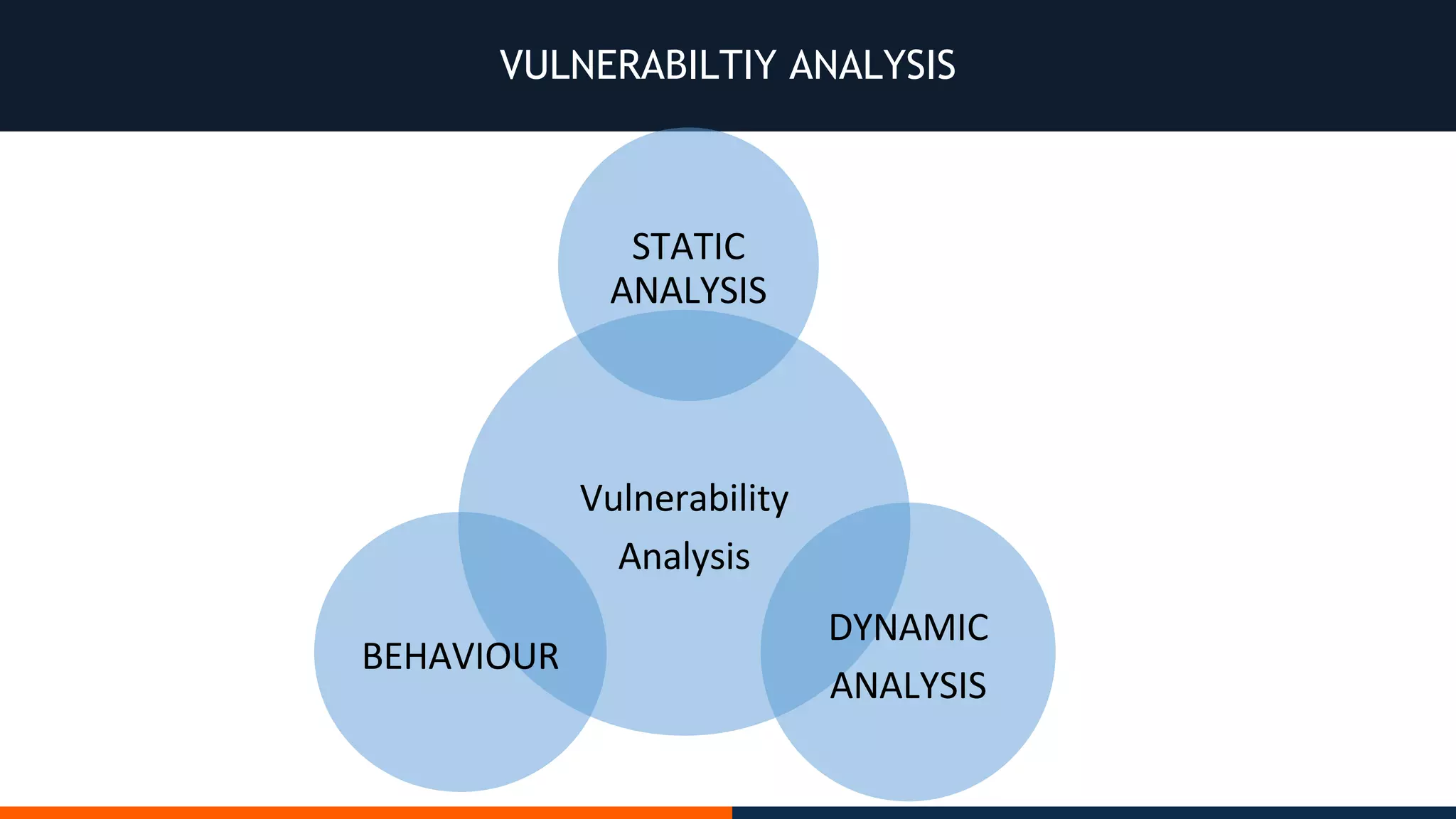
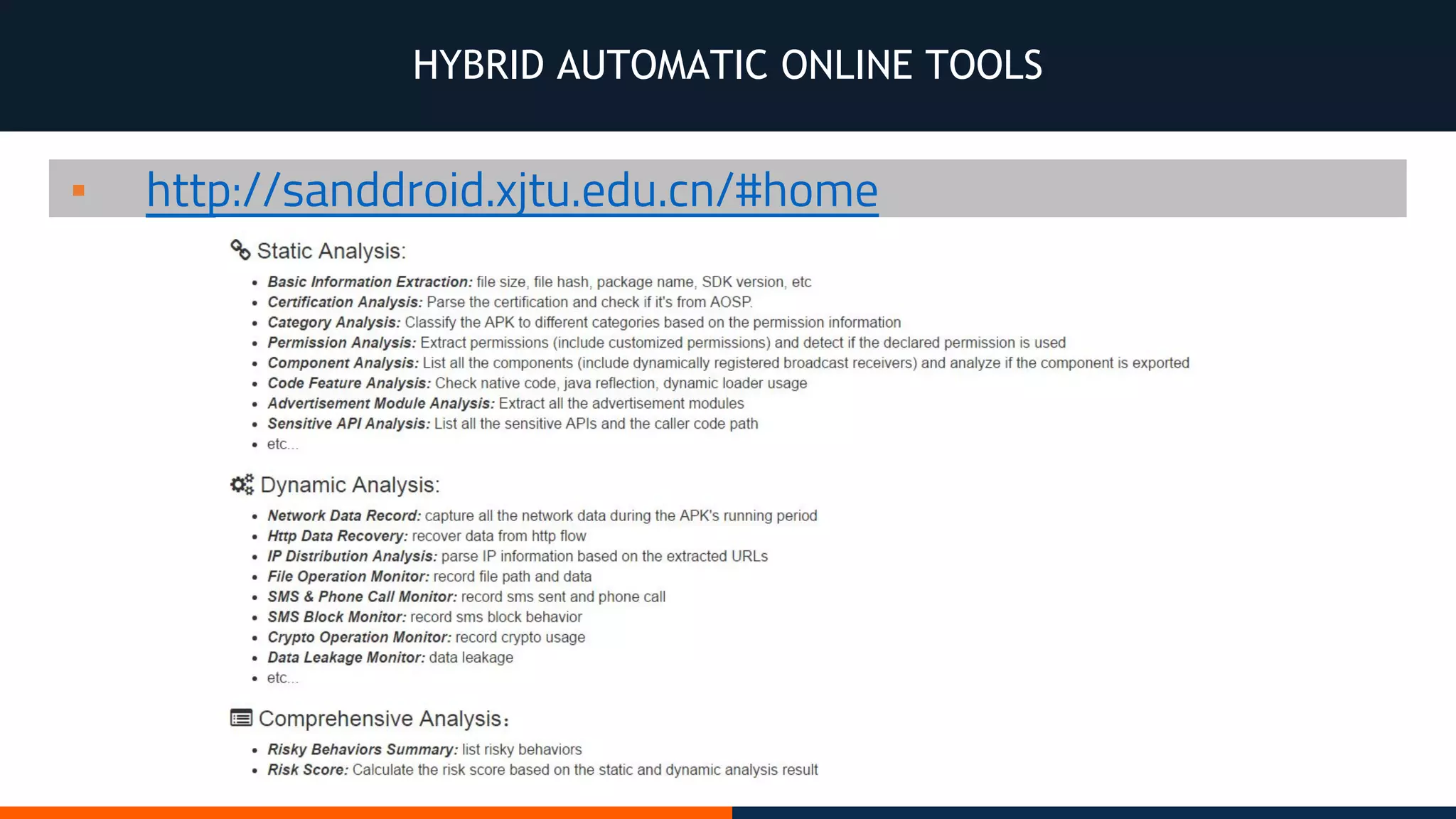
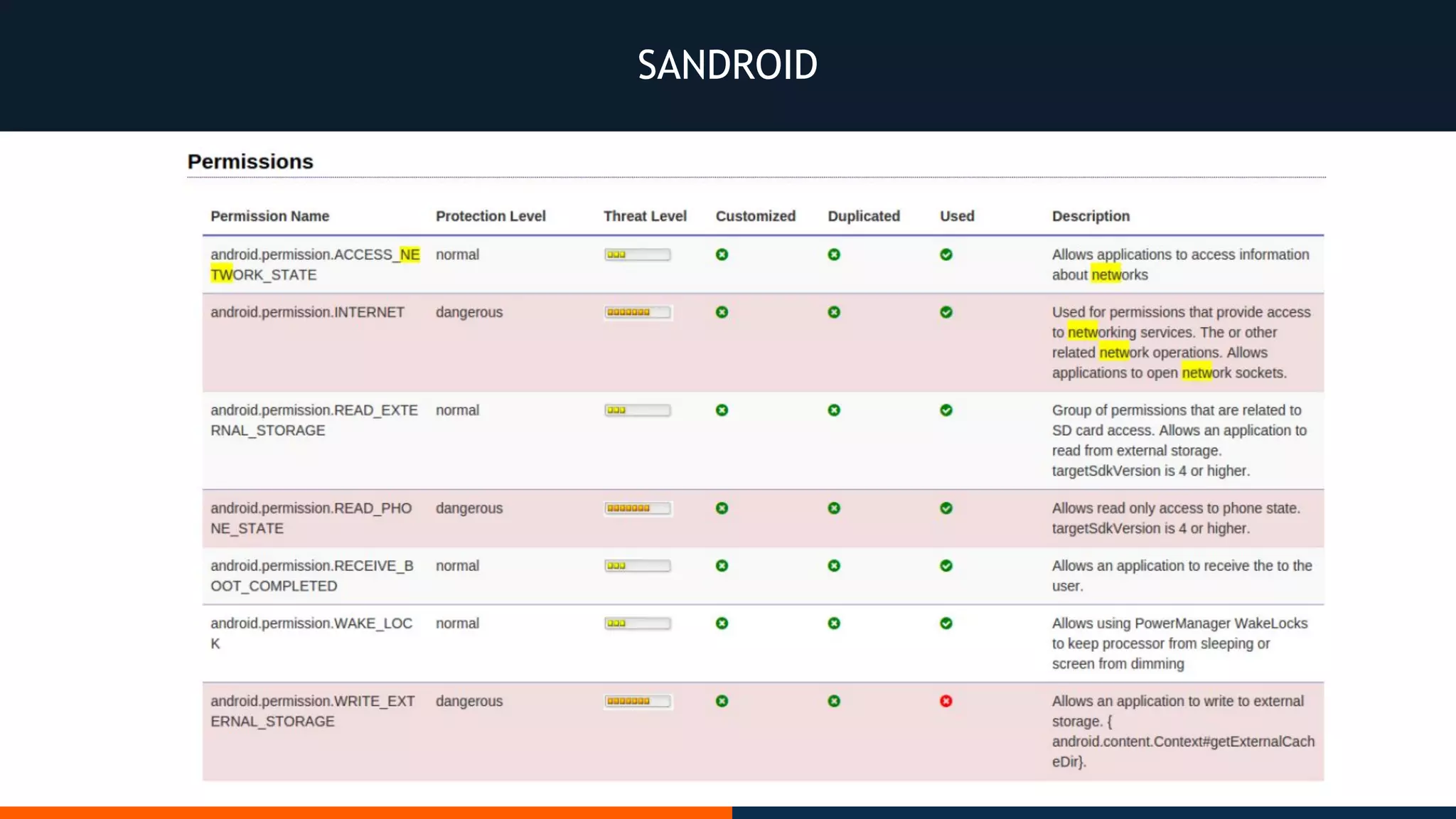
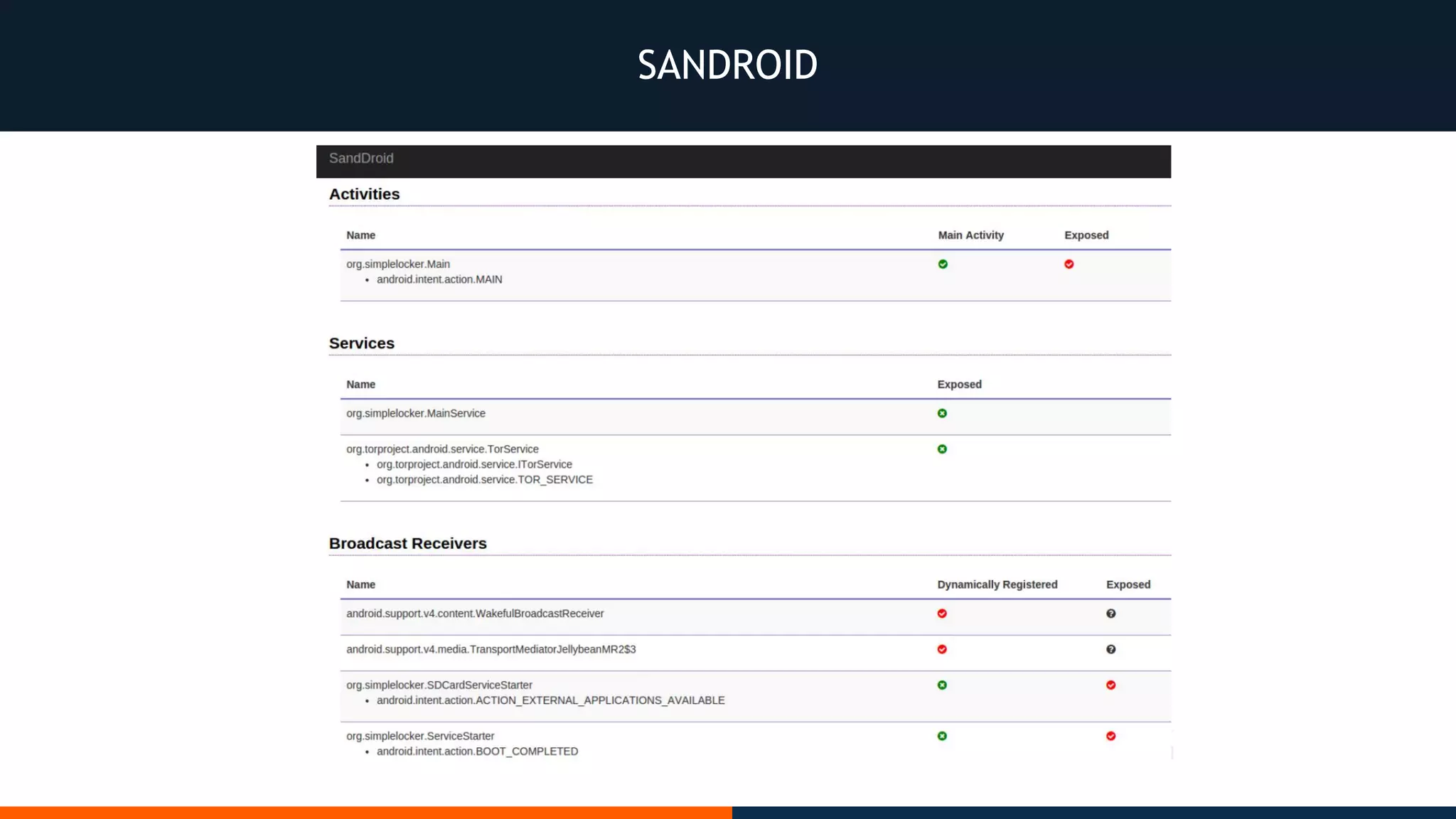
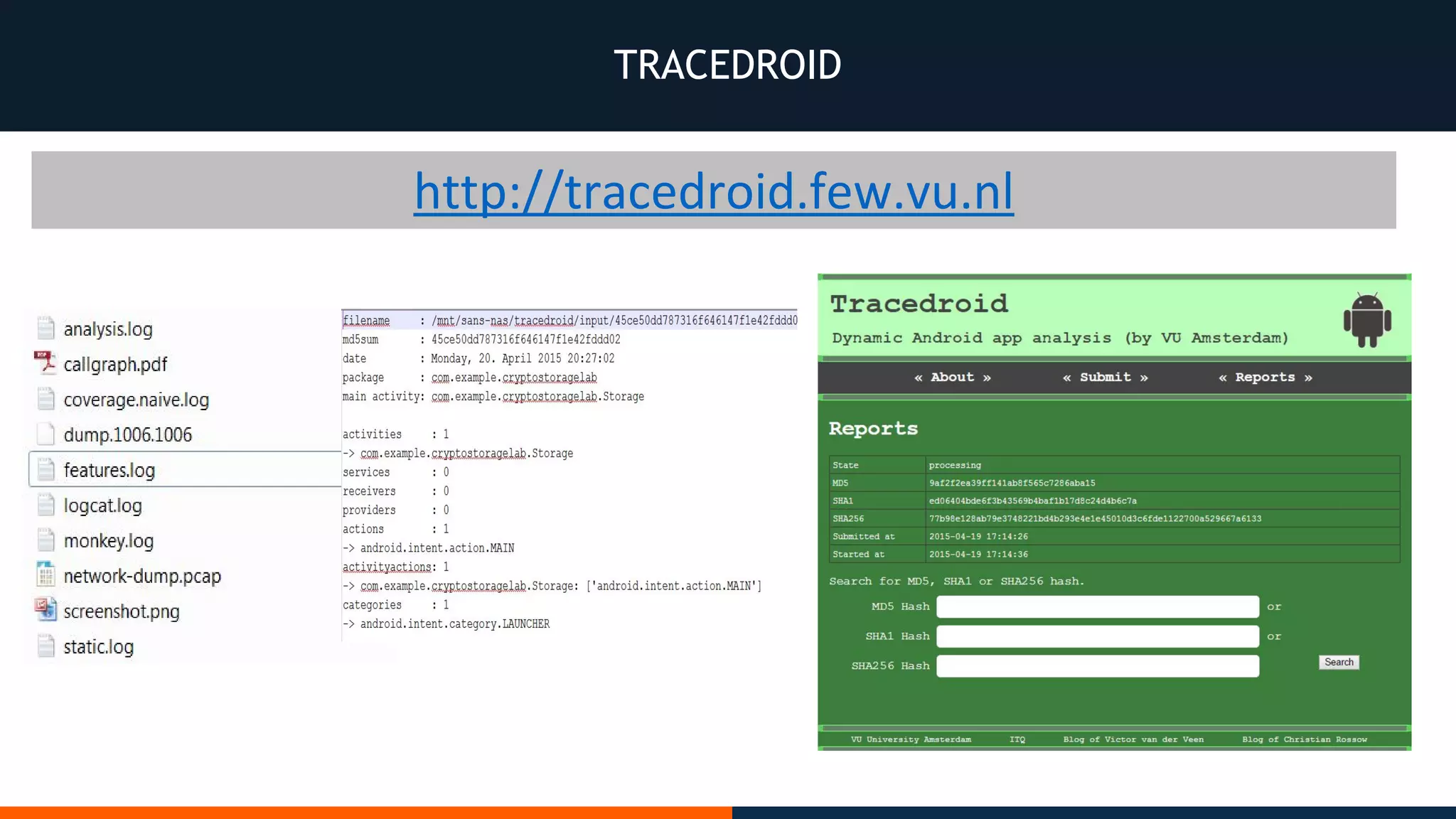
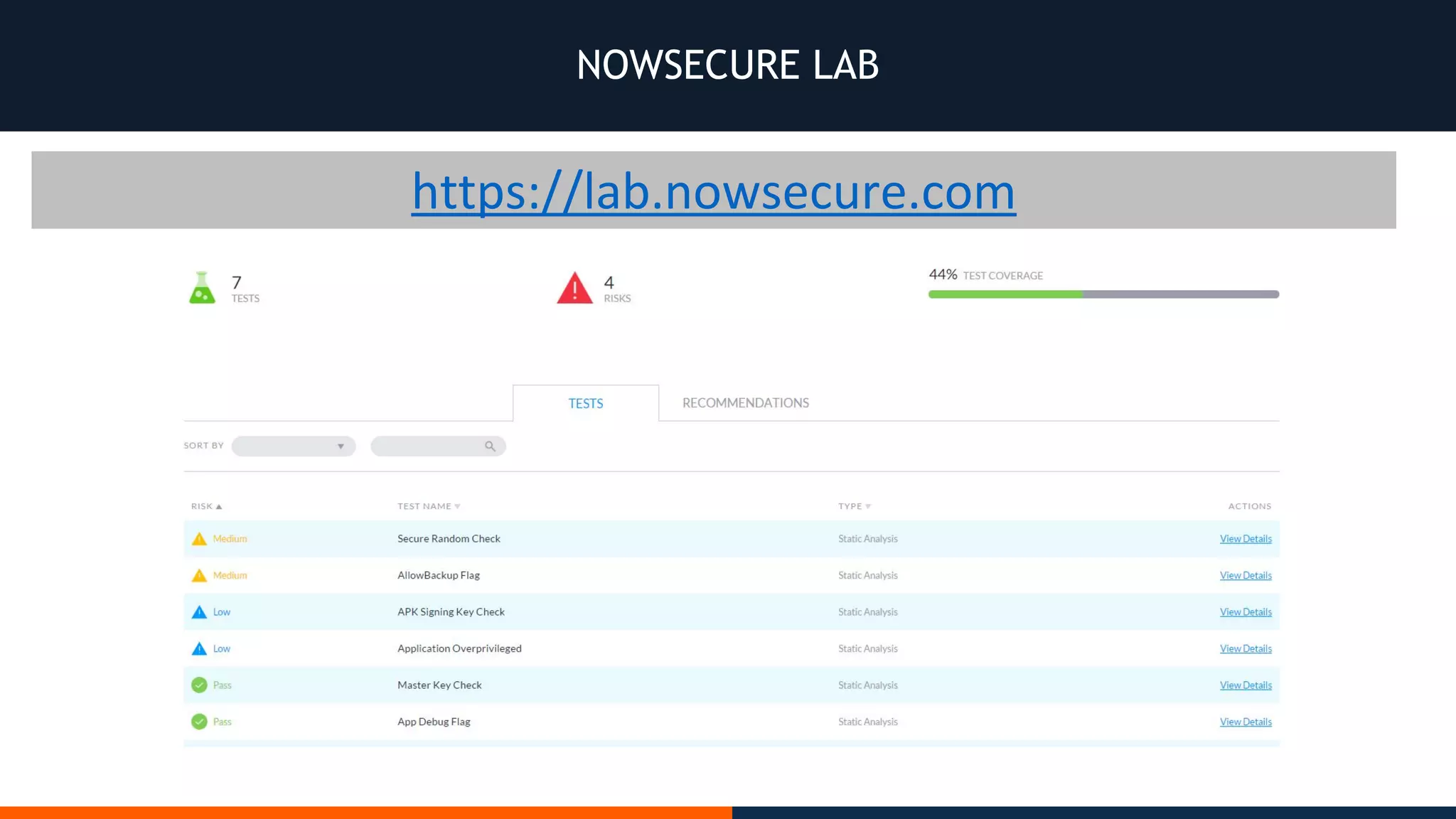
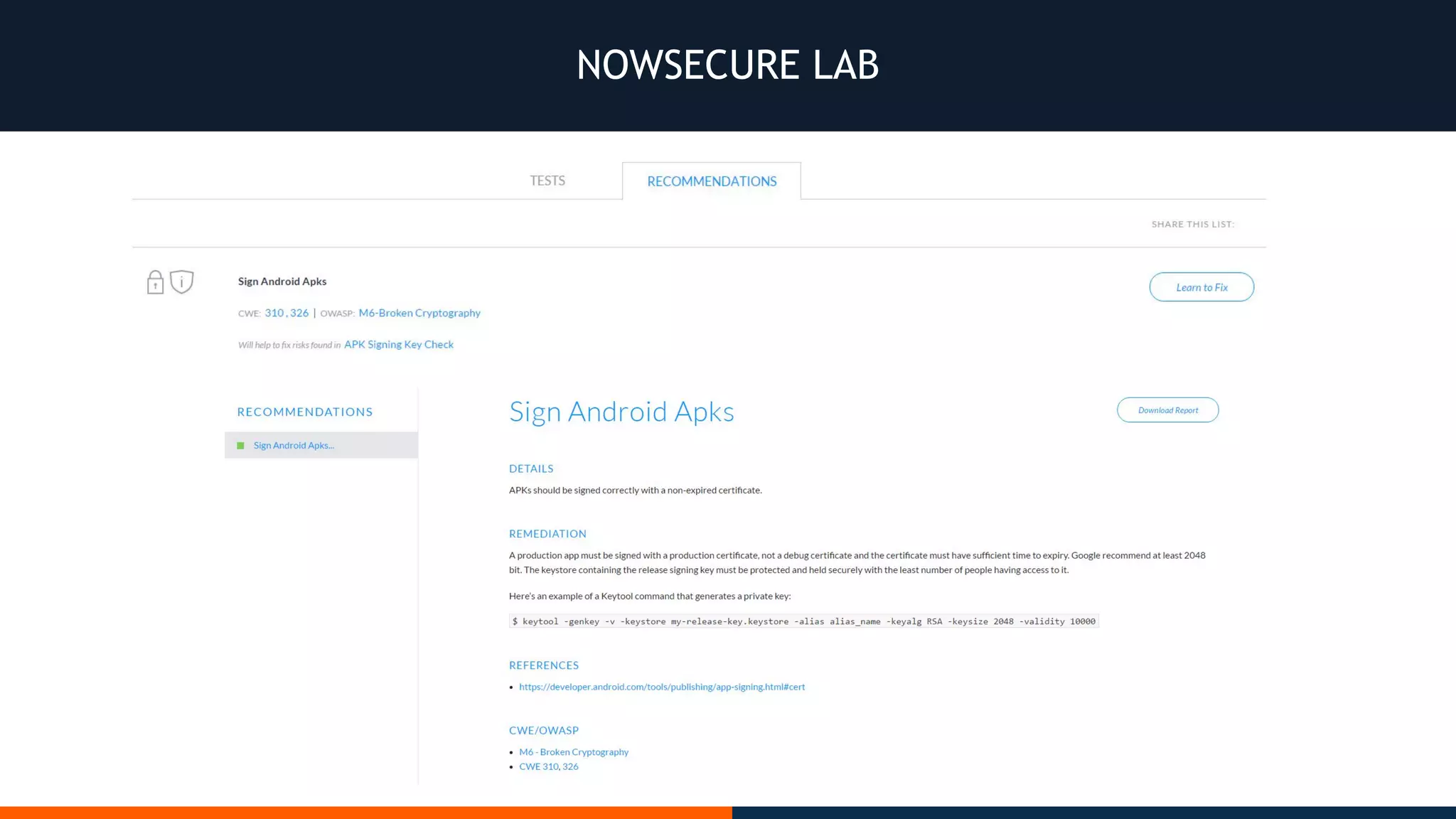
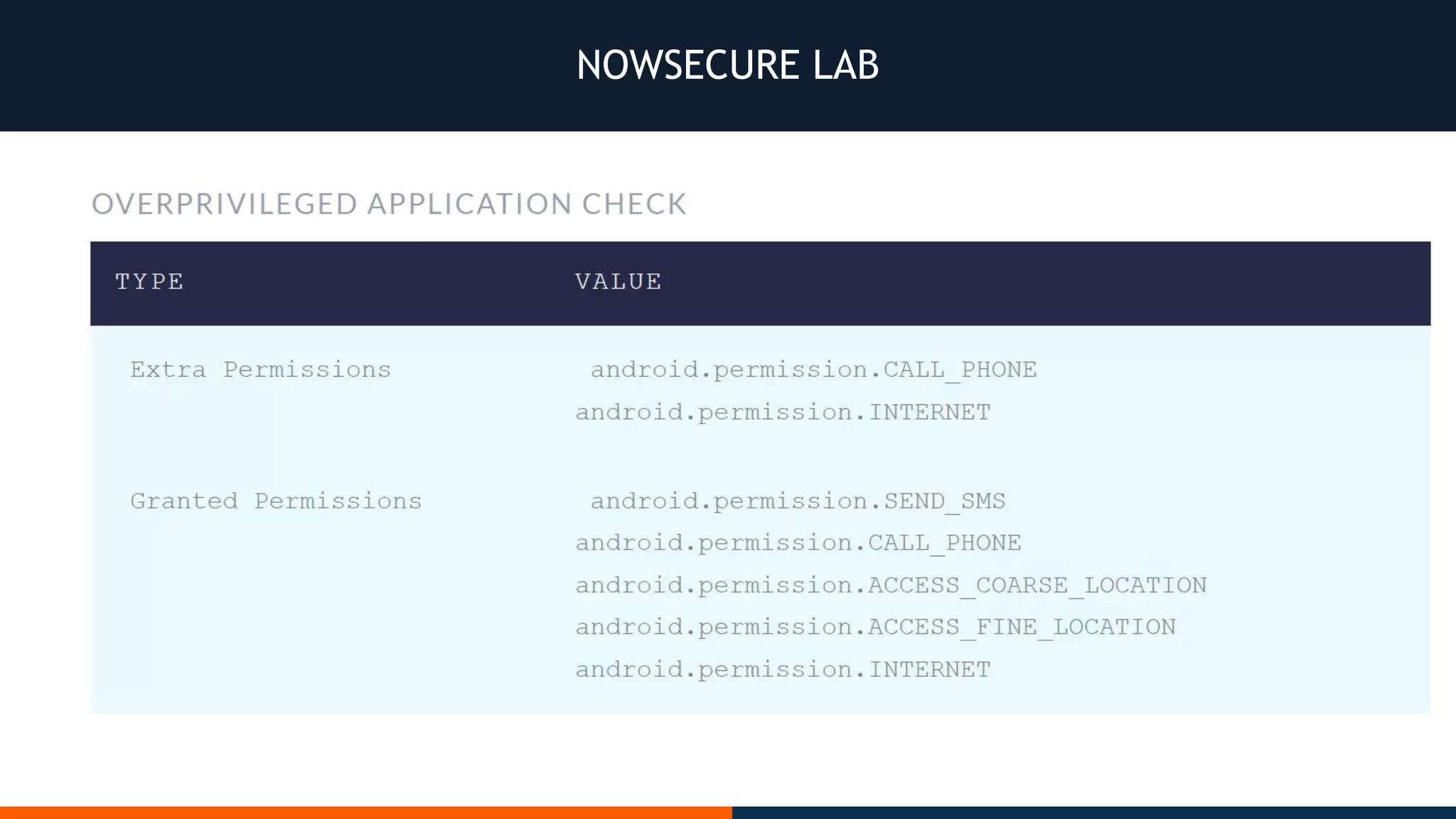
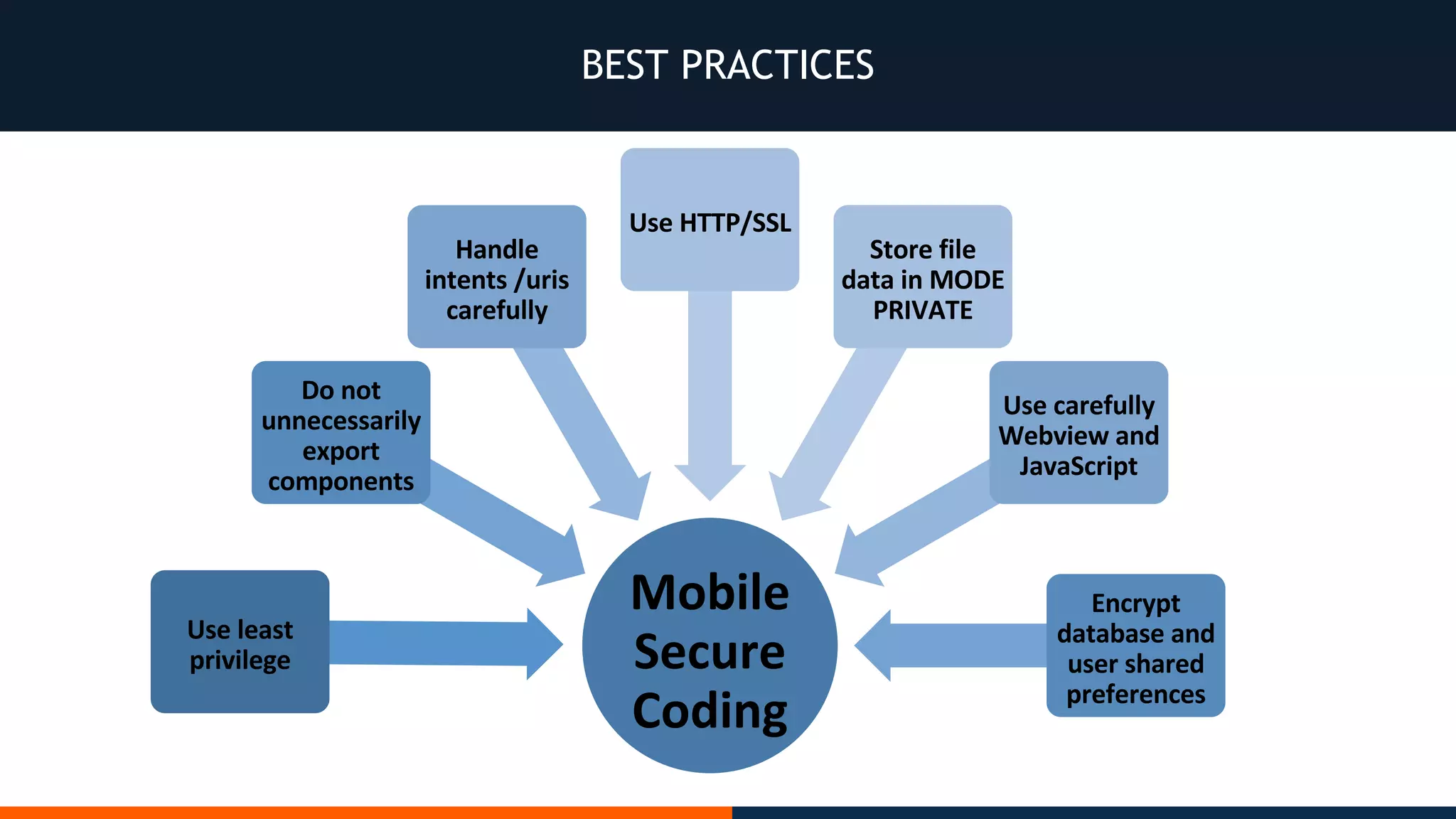
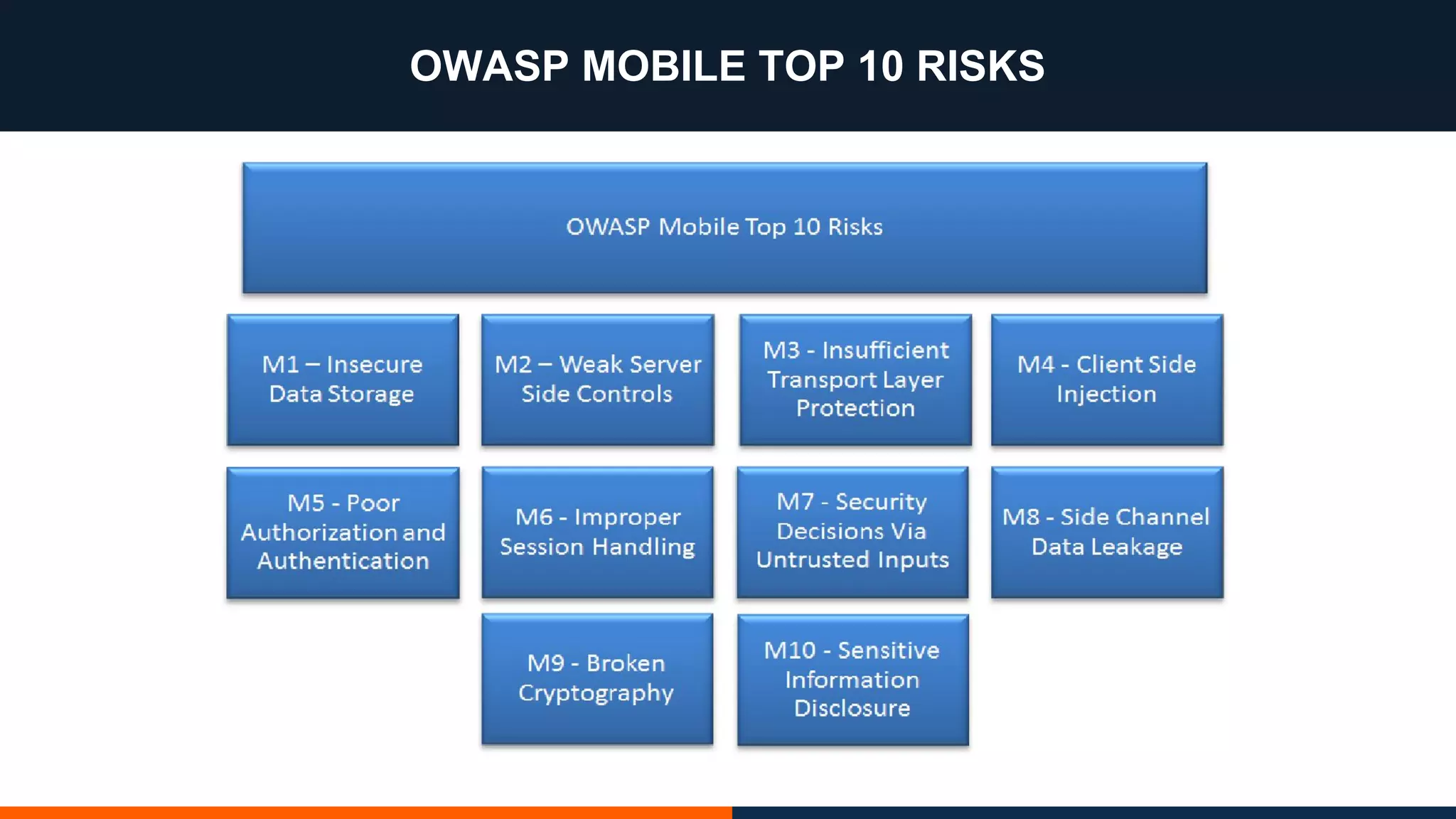
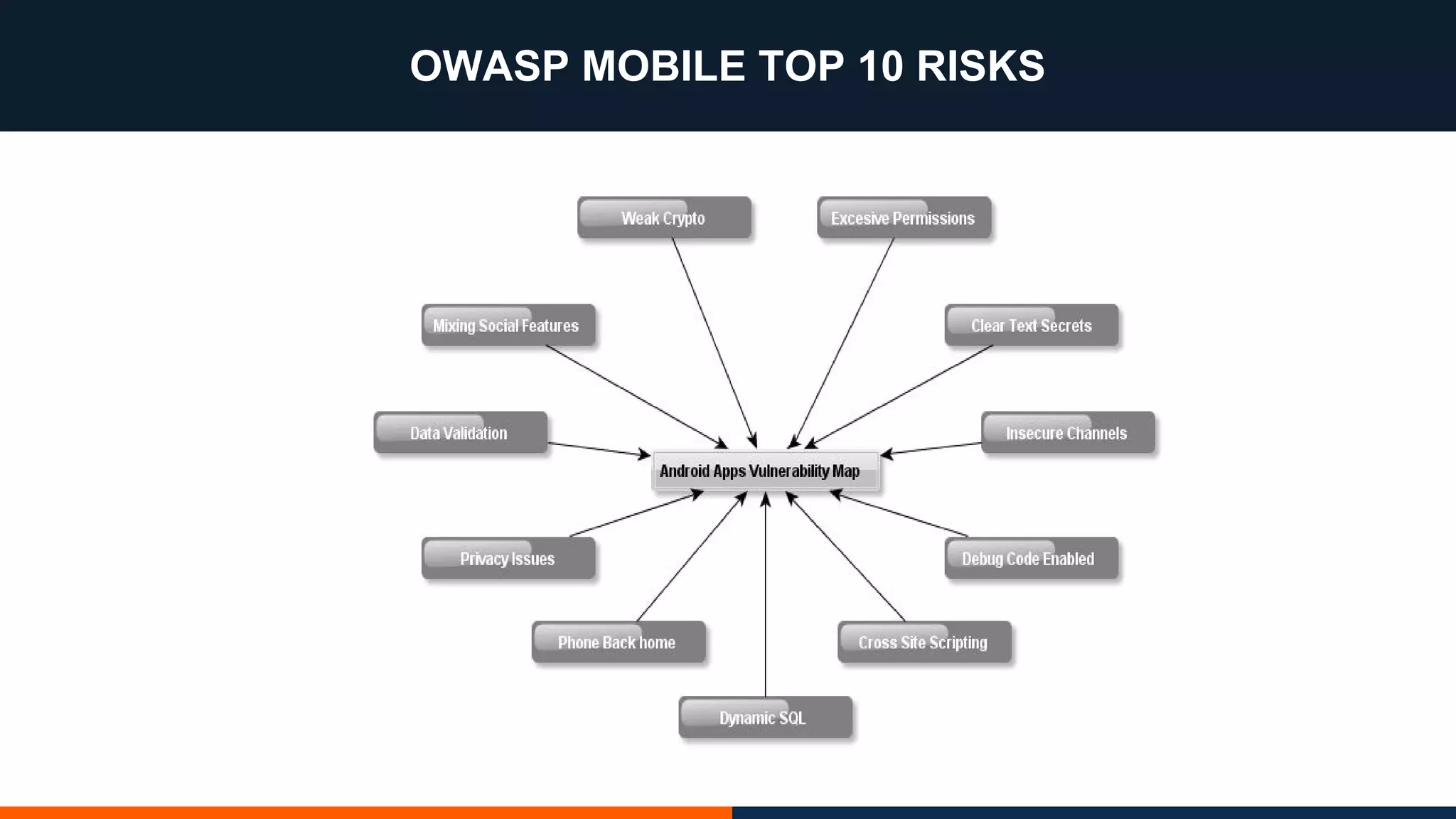
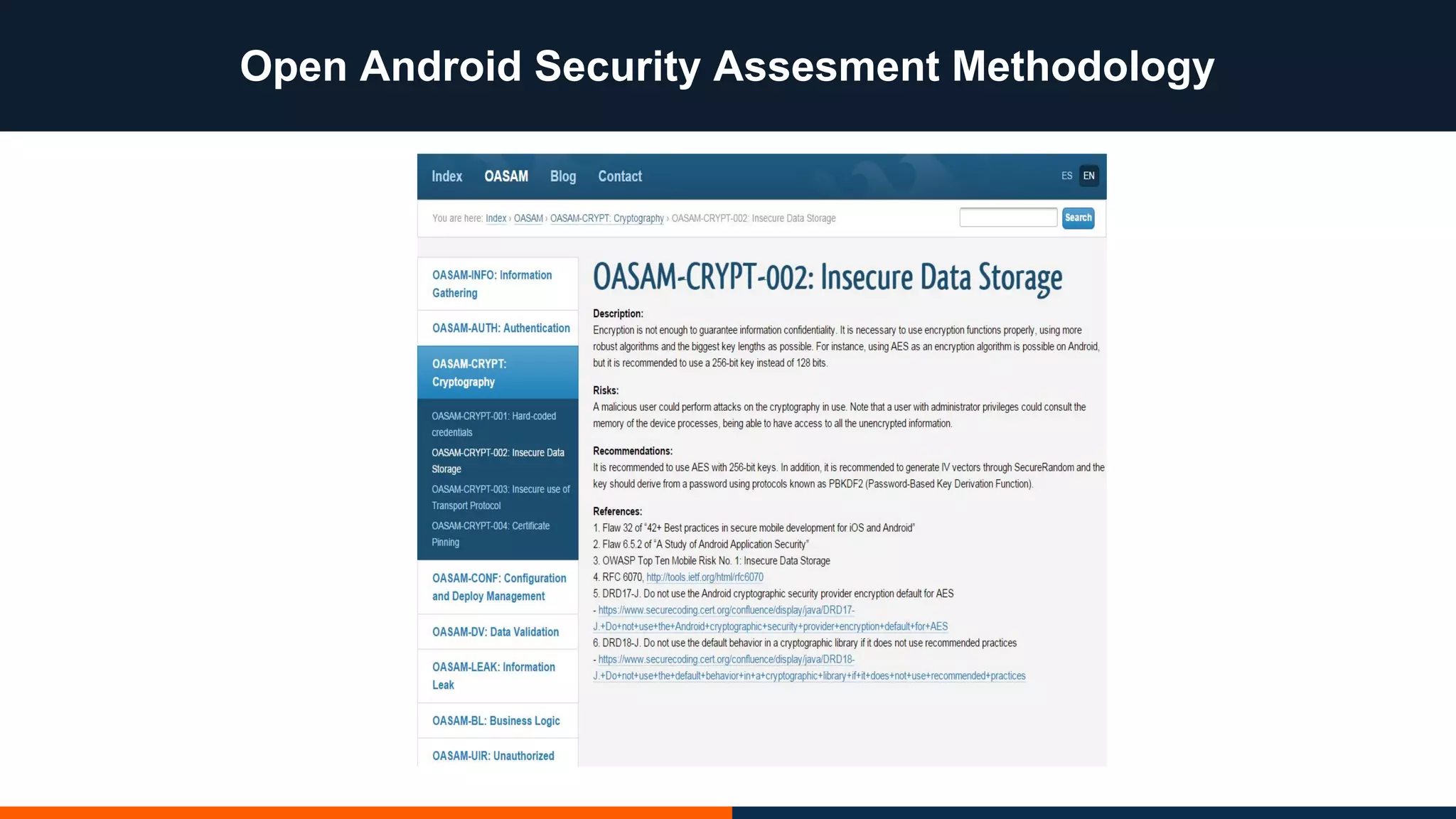
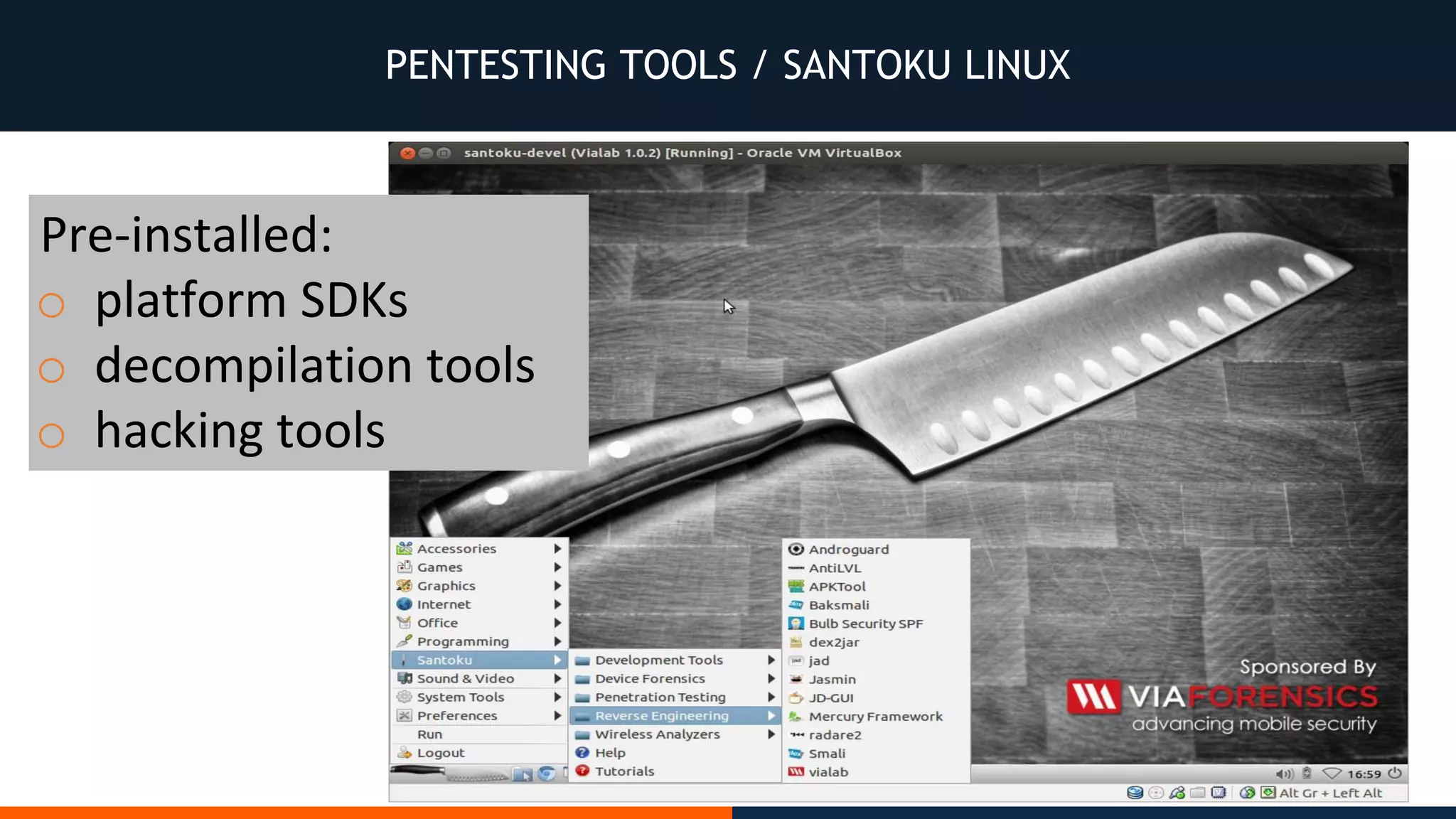
This document outlines an agenda for testing Android security. It discusses various stages of the development cycle and security testing approaches, including static and dynamic analysis, component security, and best practices. Automatic and hybrid tools are presented for analyzing apps through decompilation, emulation, and network traffic inspection. Specific tools are explained like Android Lint, QARK, Drozer, and SQLCipher. The document concludes with recommendations around permissions, encryption, input validation, and references.