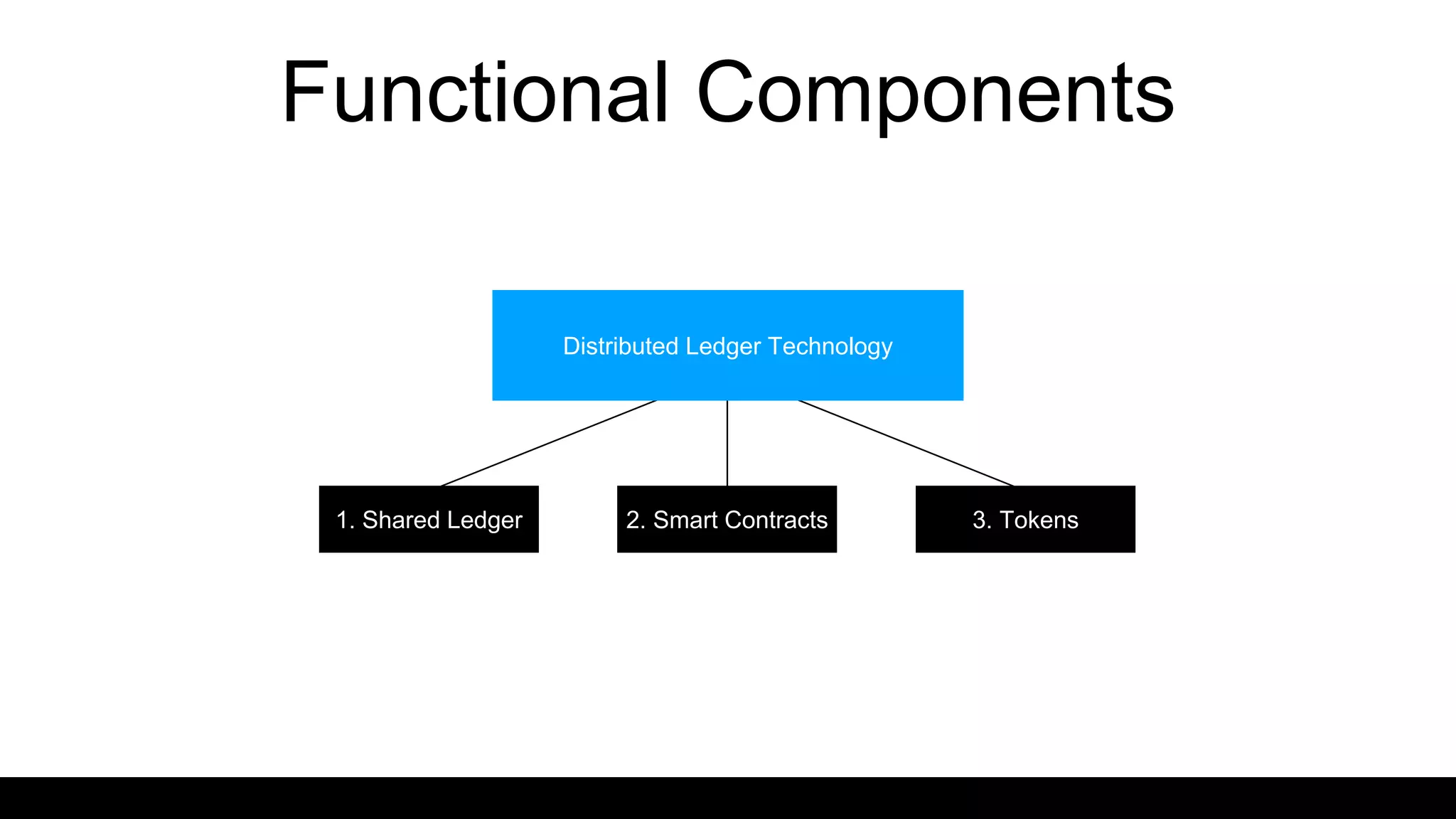
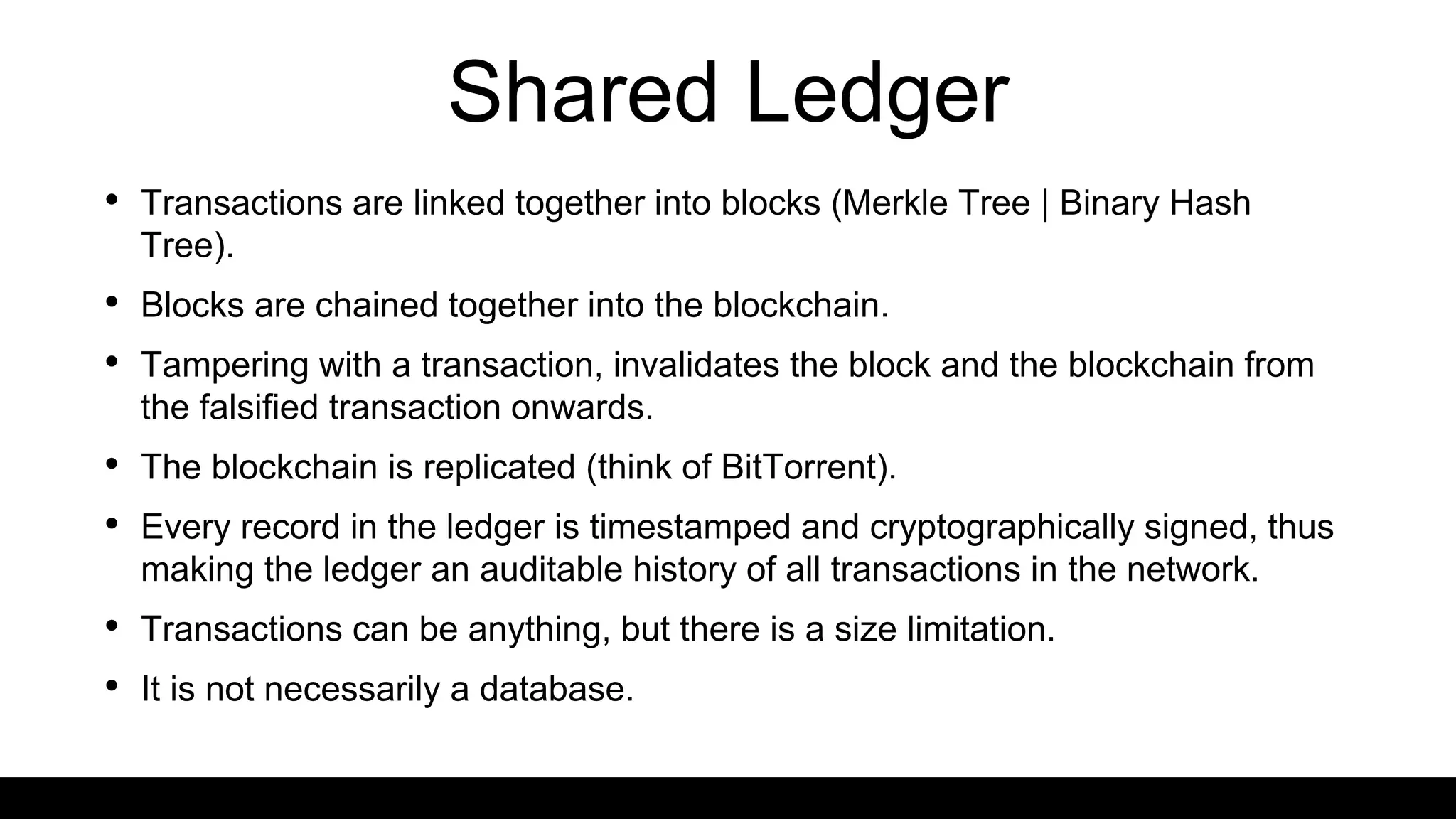
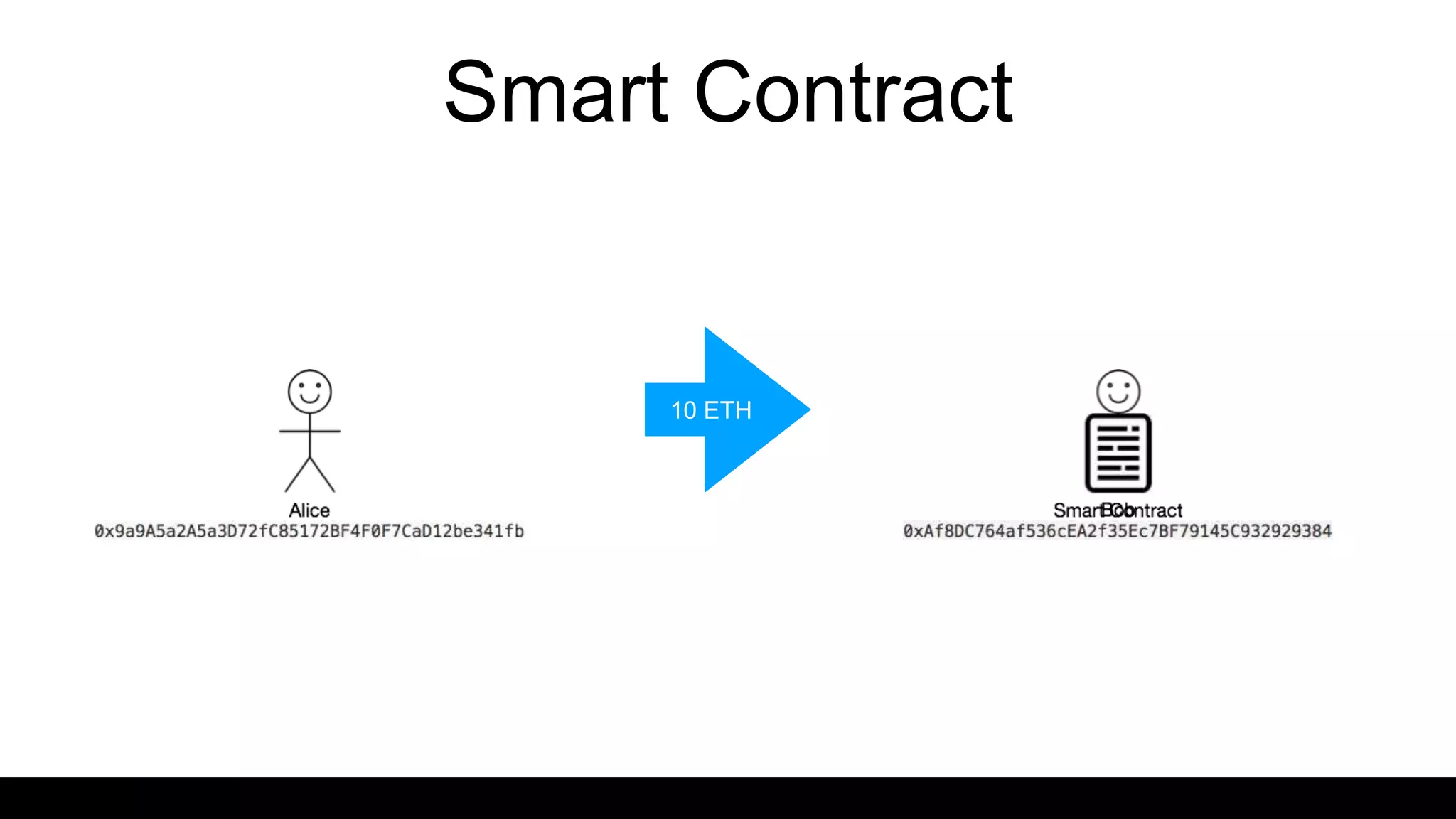
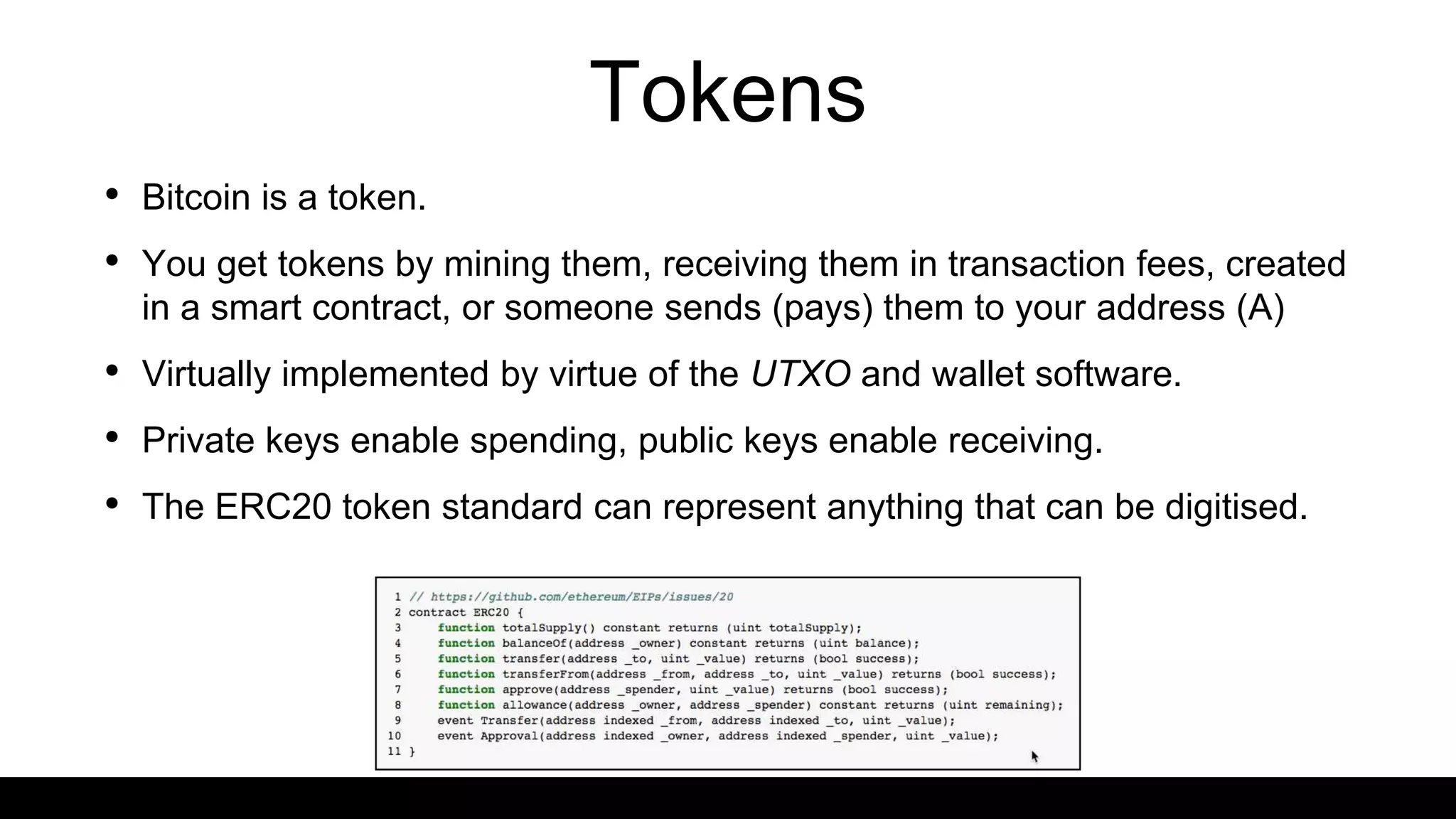
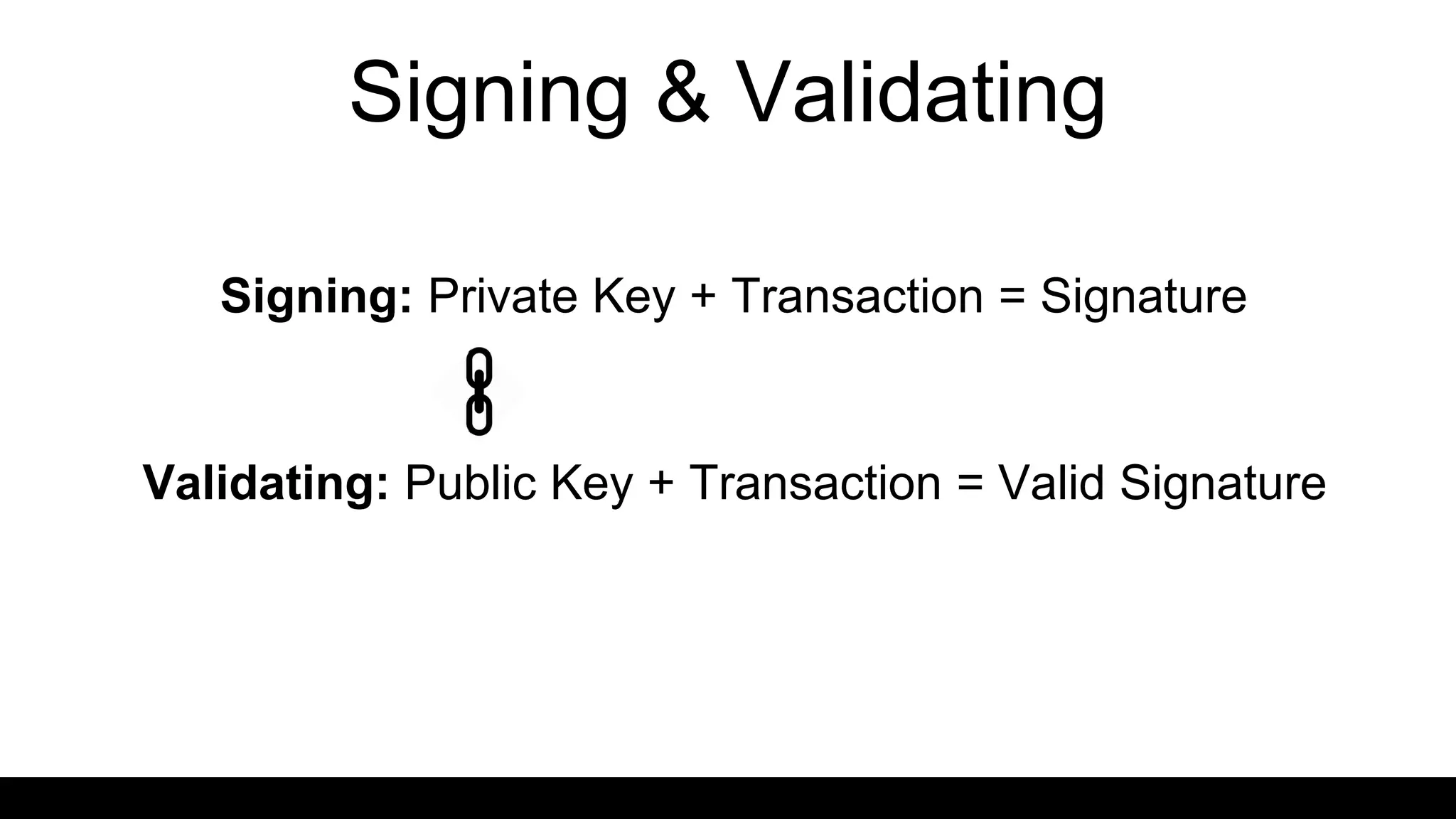
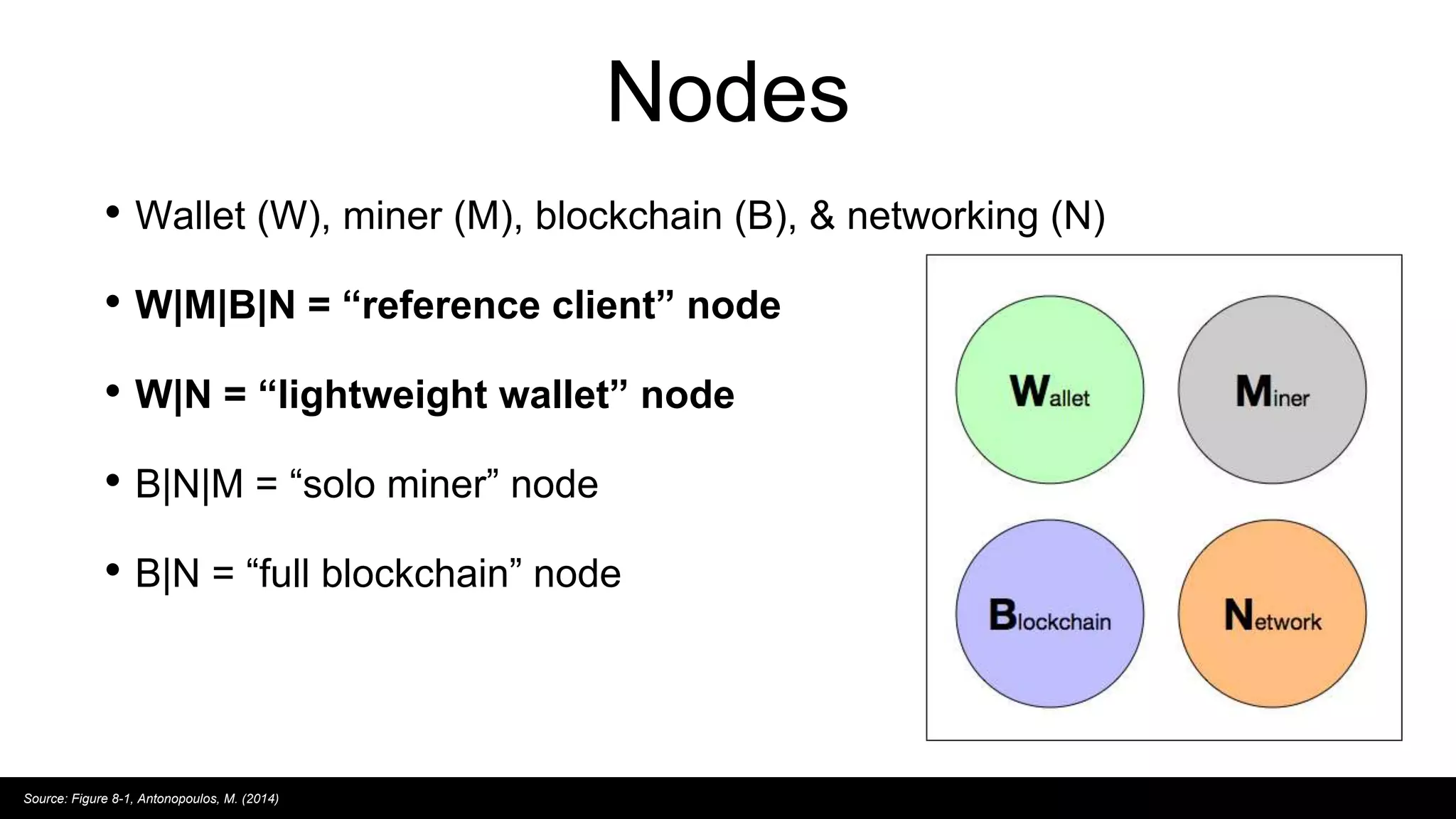
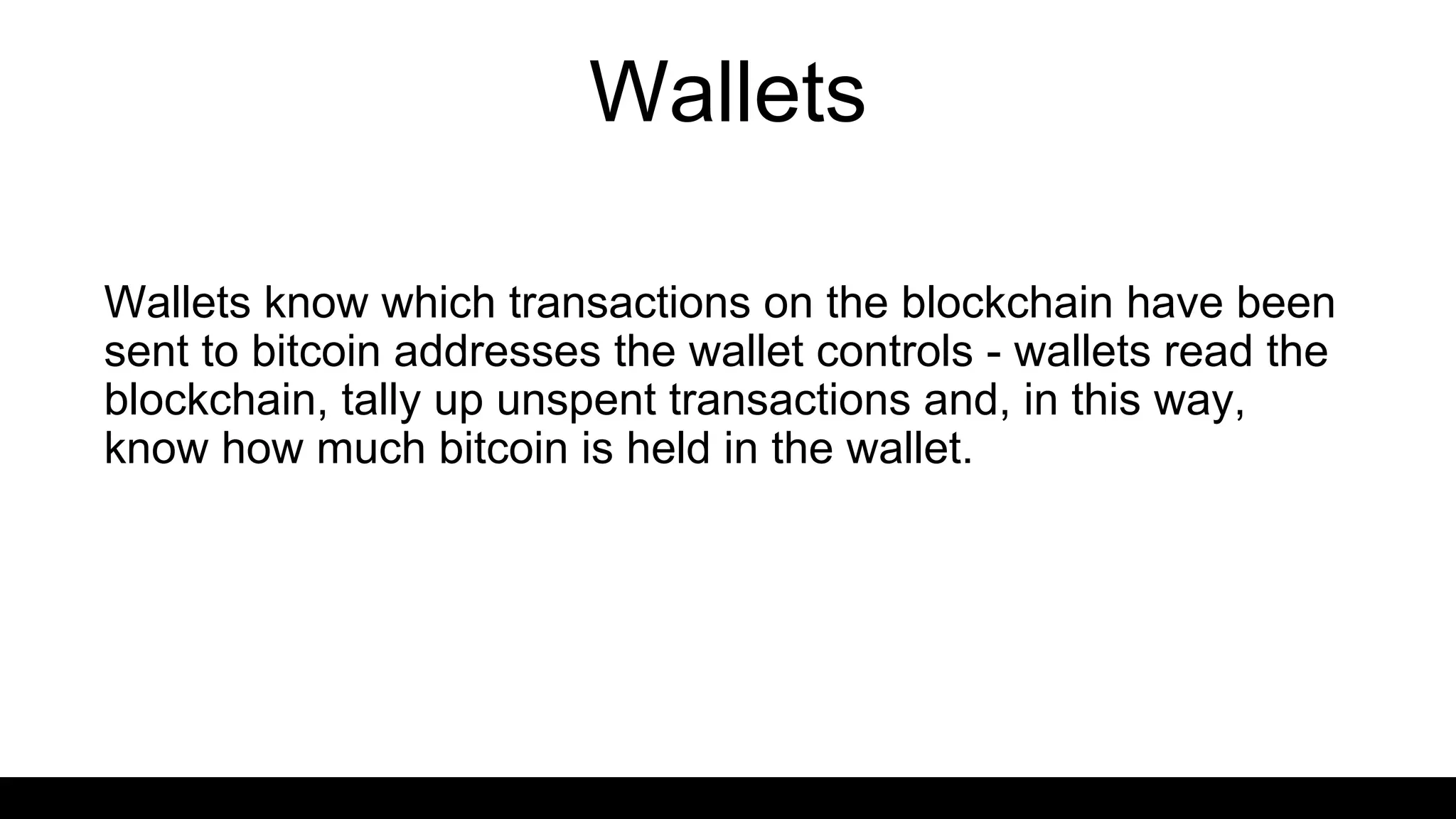
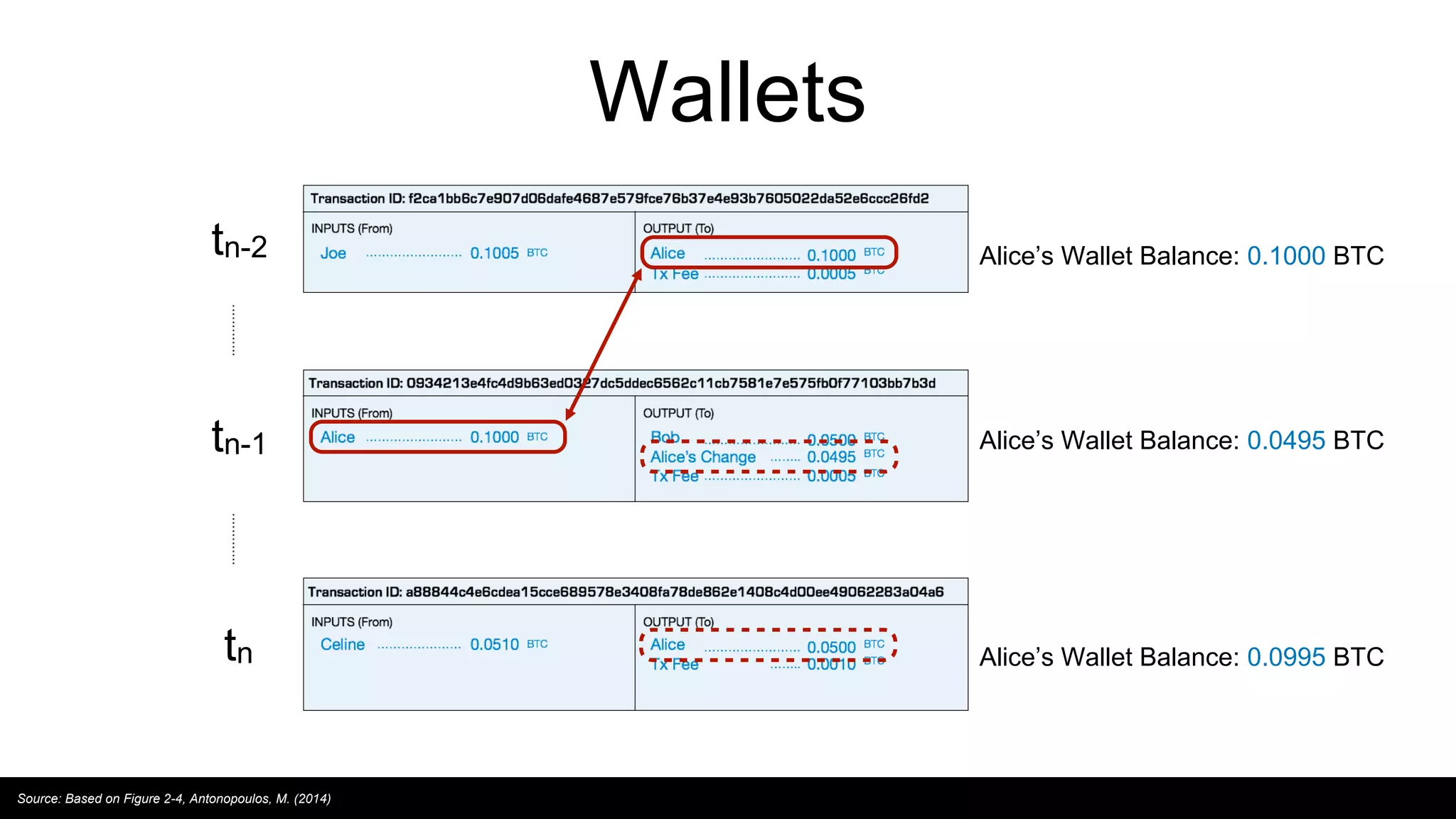
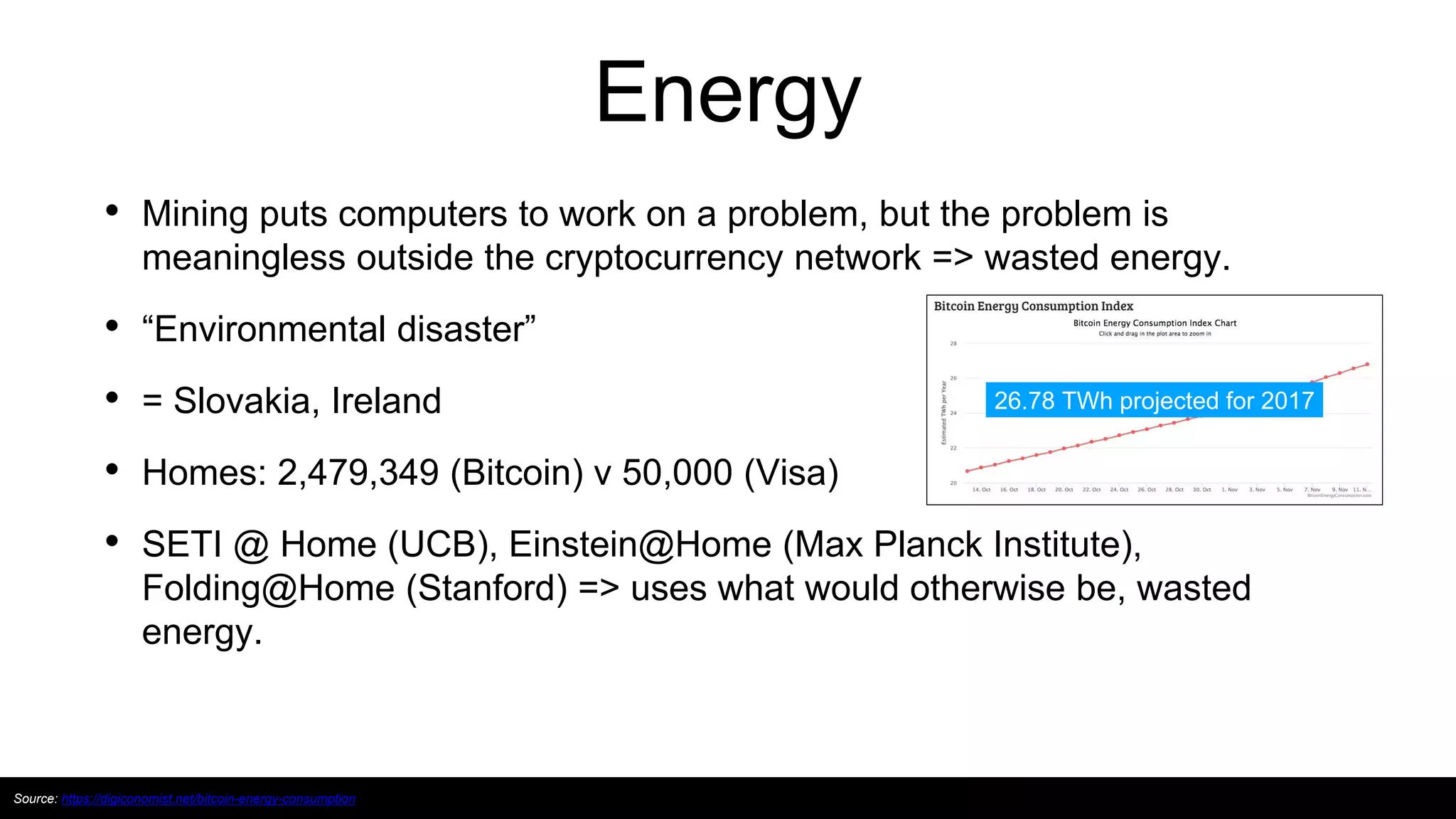
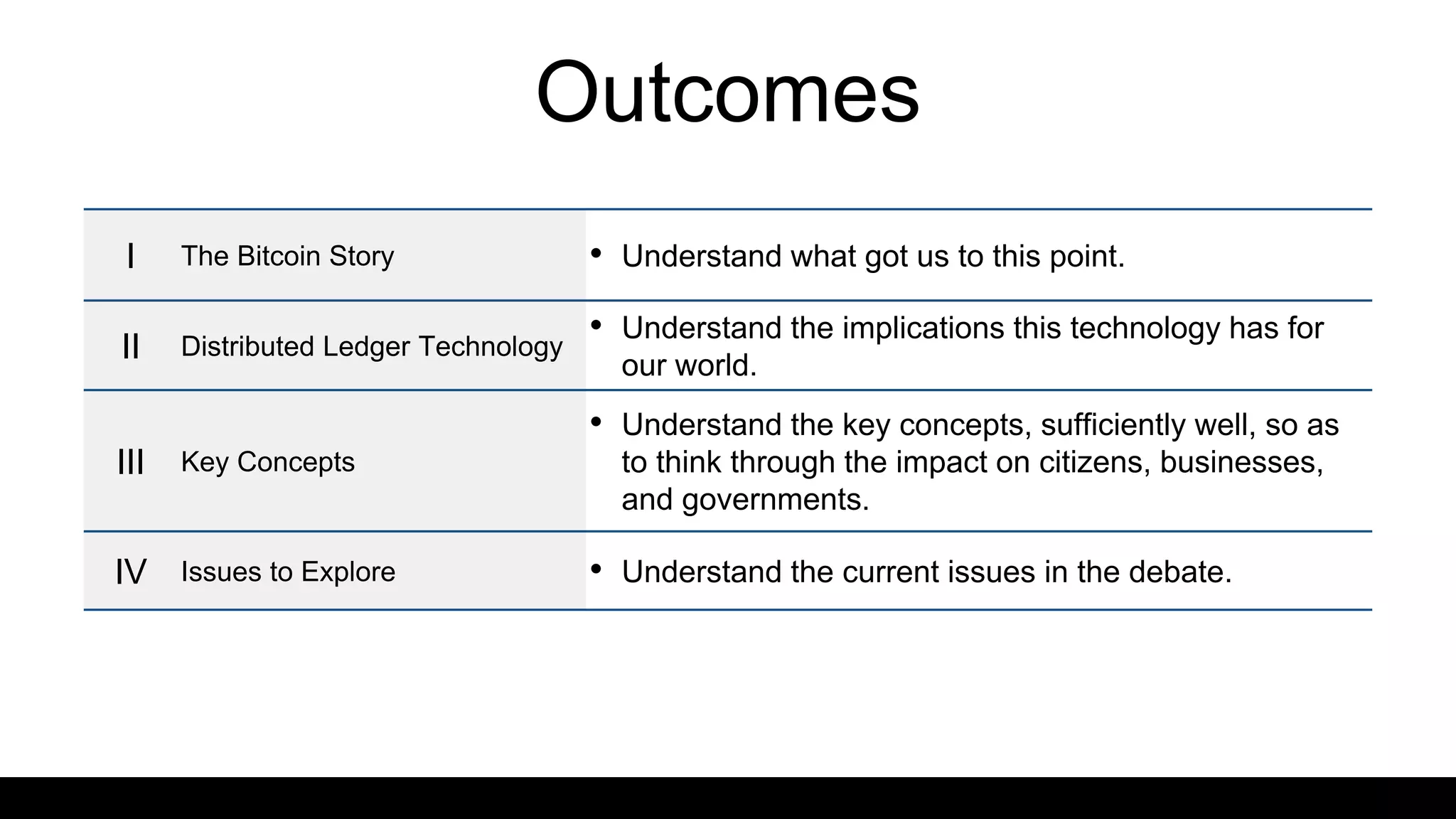
This document provides an overview of blockchain technology and distributed ledgers. It begins with the story of Bitcoin's origins in response to the 2008 financial crisis. It then explains key concepts like distributed ledgers, smart contracts, tokens, proof-of-work, private-public keys, and addresses. Issues discussed include classification of cryptocurrencies, identity, complexity challenges, legal issues, capital raising, data ownership, and energy consumption concerns related to mining. The goal is to help understand implications of this technology for citizens, businesses, and governments.









![DLT
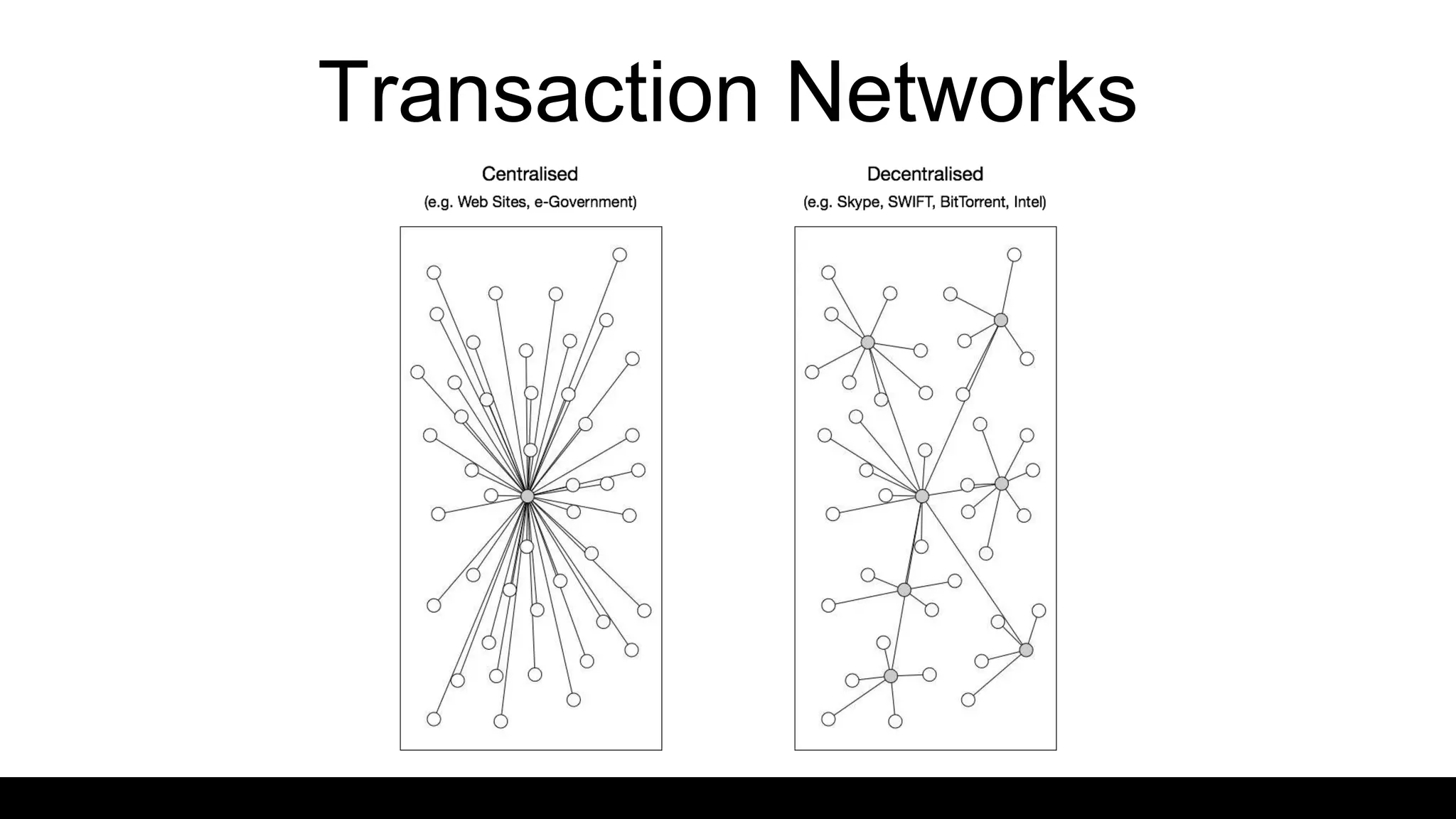
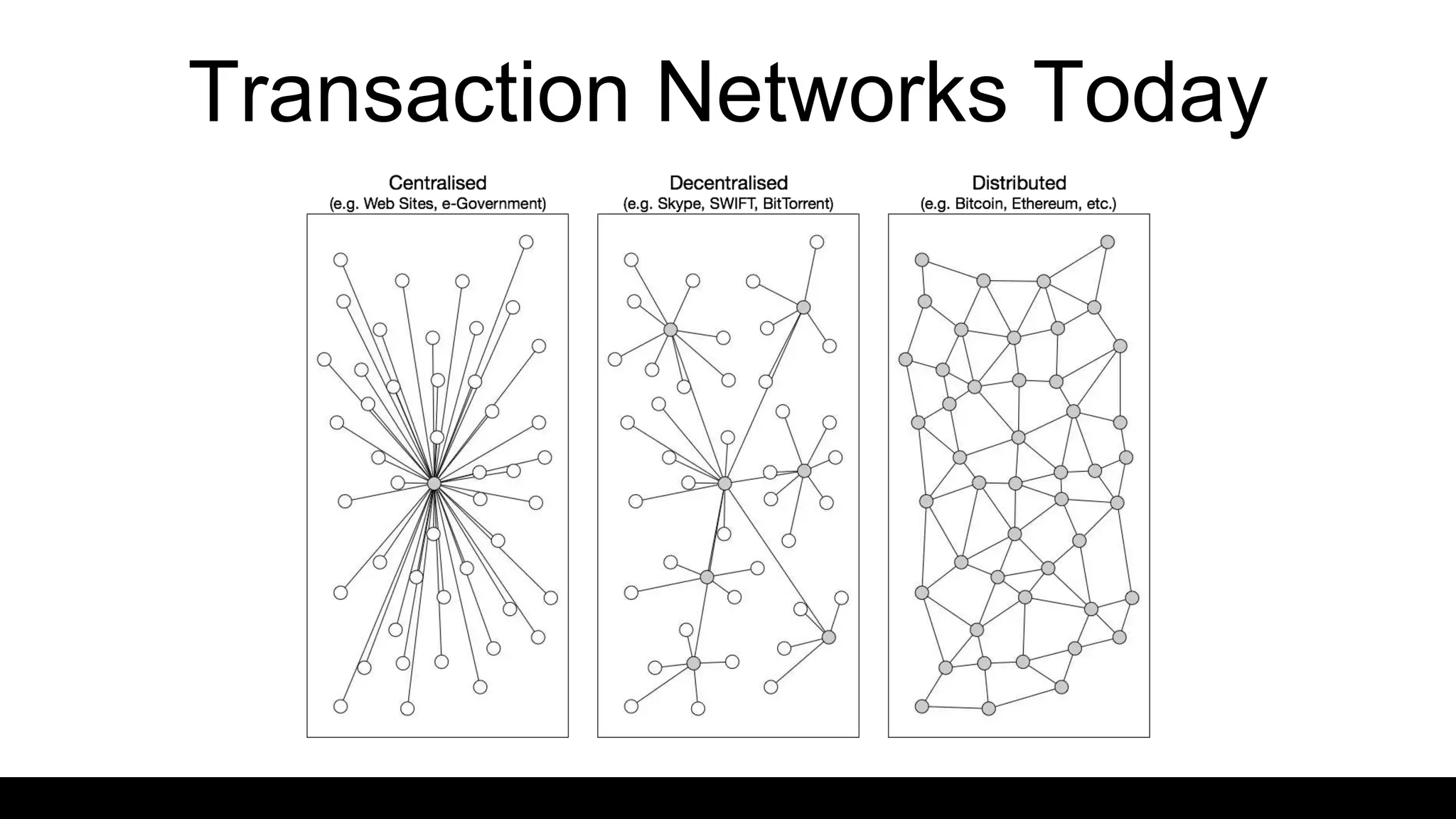
Source: Based on Birch (2016) cited in “Distributed Ledger Technology: Beyond Blockchain”, Government Office for Science, Government of the United Kingdom.
How many copies?
Who can use the copies?
Who integrates the ledger?
[anyone]
[group of owners] e.g. a clearing and settlement
network
[one]
e.g. personal bank account
[many]
[any user, by untrusted consensus]
[trusted ledger owners or by validation] e.g. Ripple (XPR) (a global
financial transactions system),
consortium chains
Bitcoin (BTC), Ethereum (ETH), Litecoin
(LTC), Monero (XMR)](https://image.slidesharecdn.com/financewatch-171117160541/75/Understanding-Blockchain-21-2048.jpg)