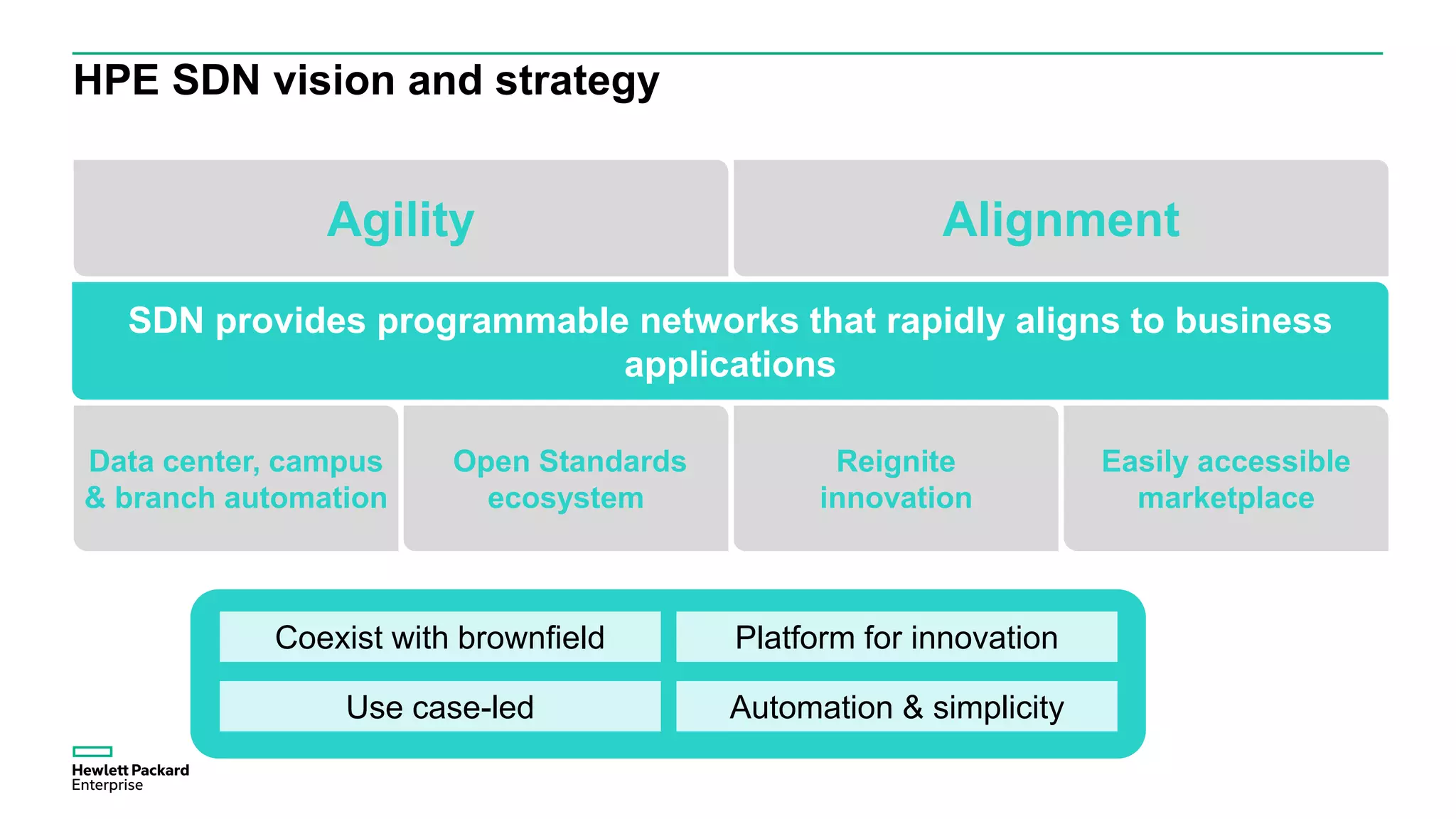
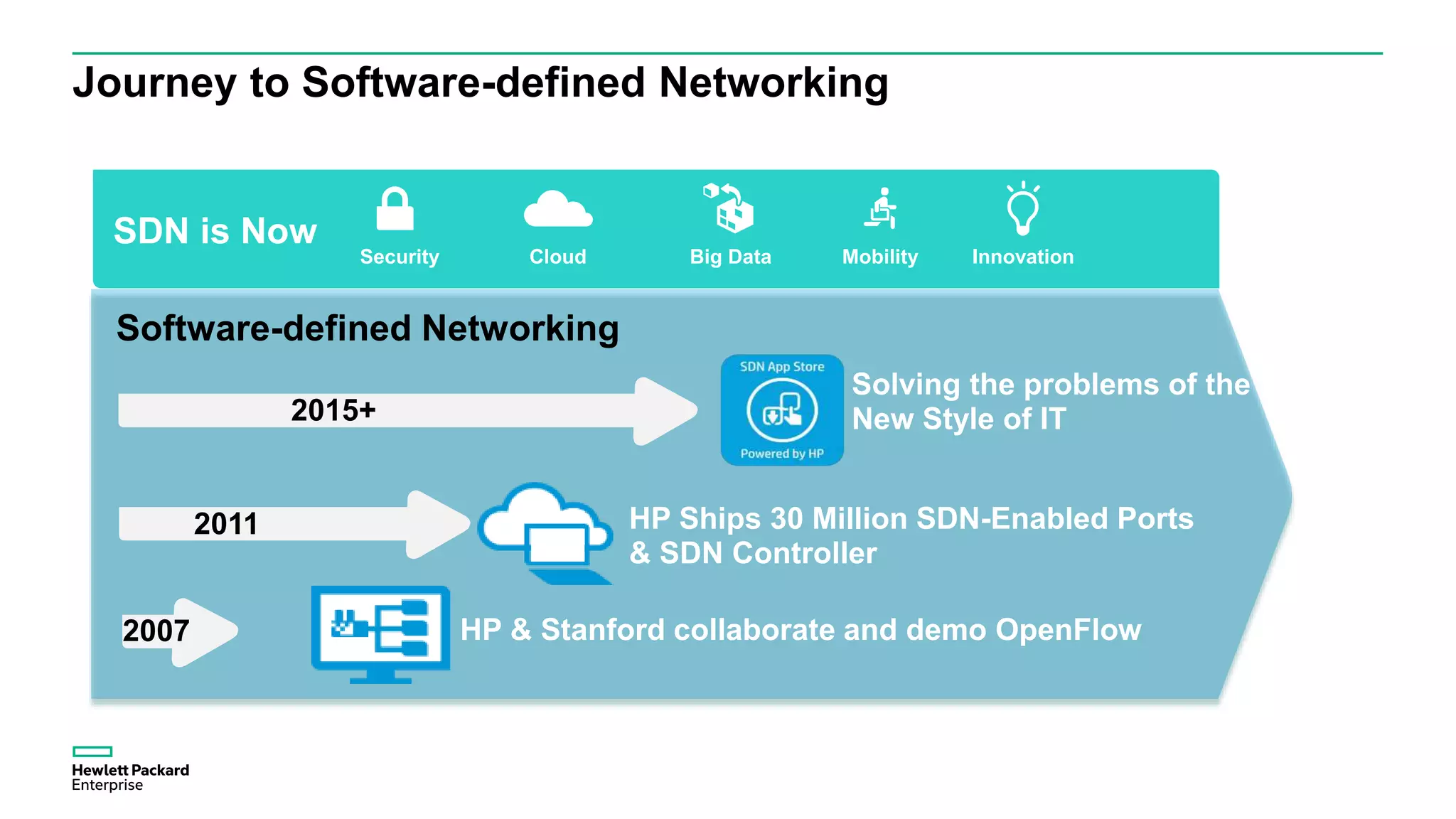
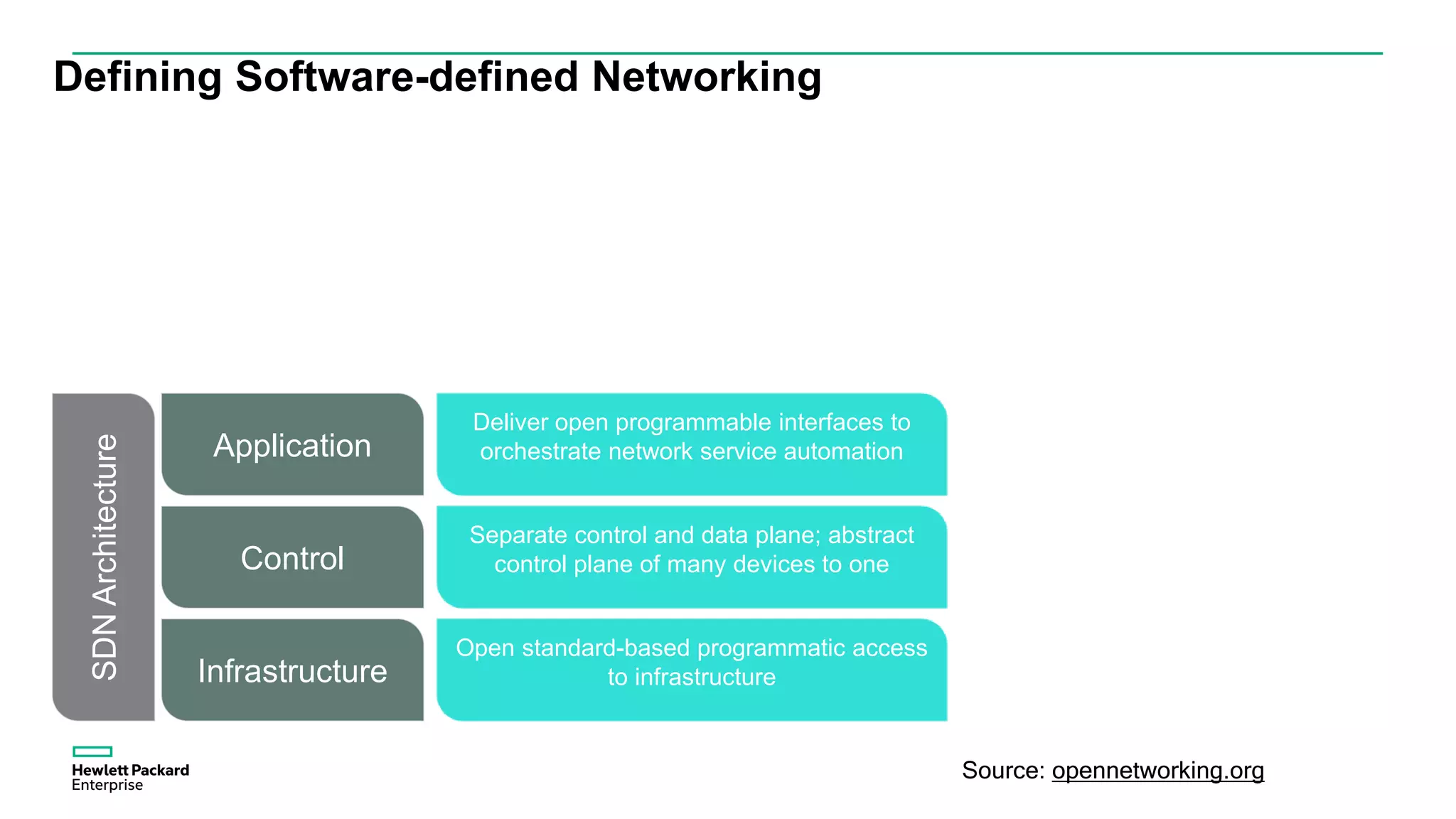
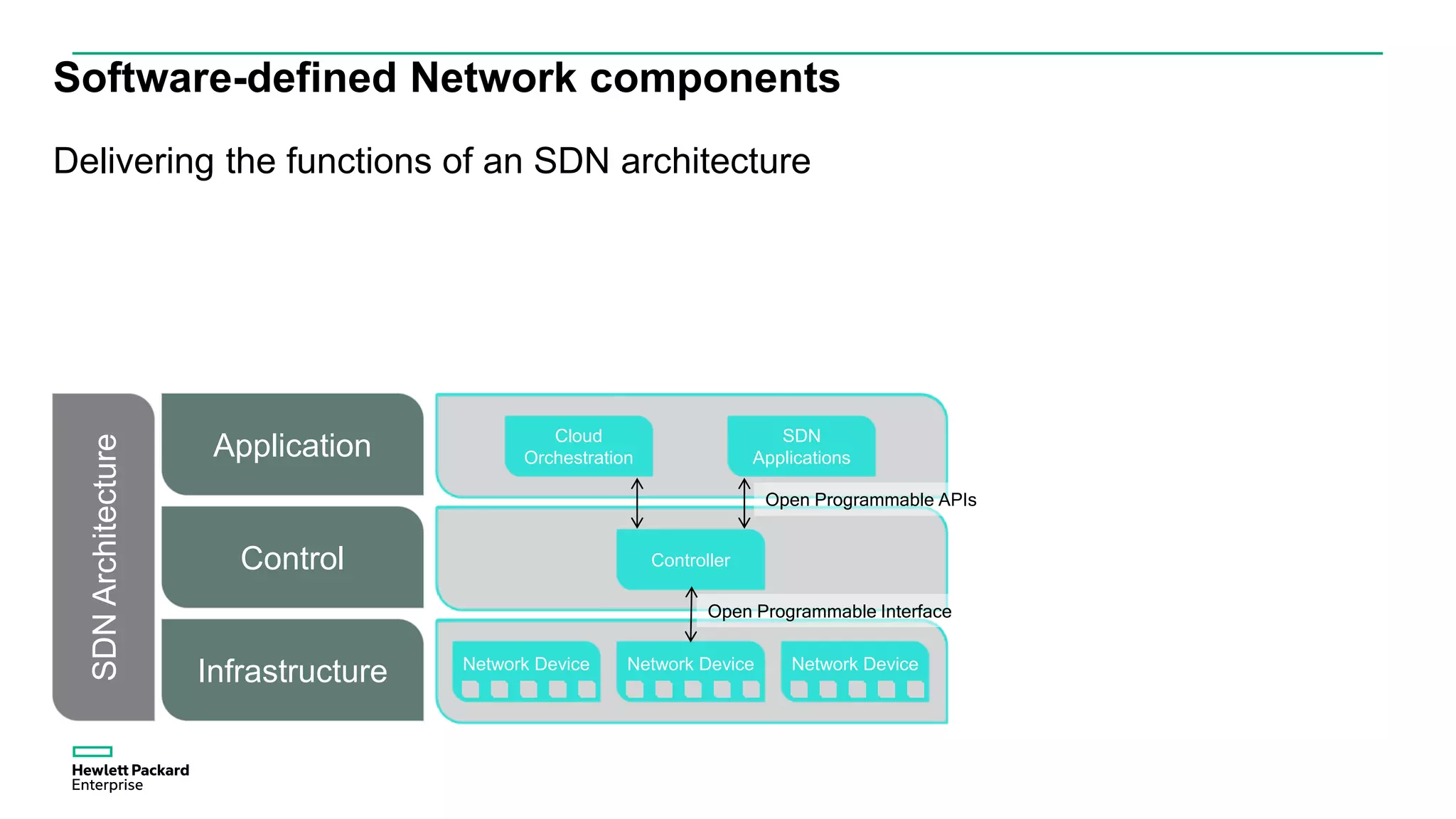
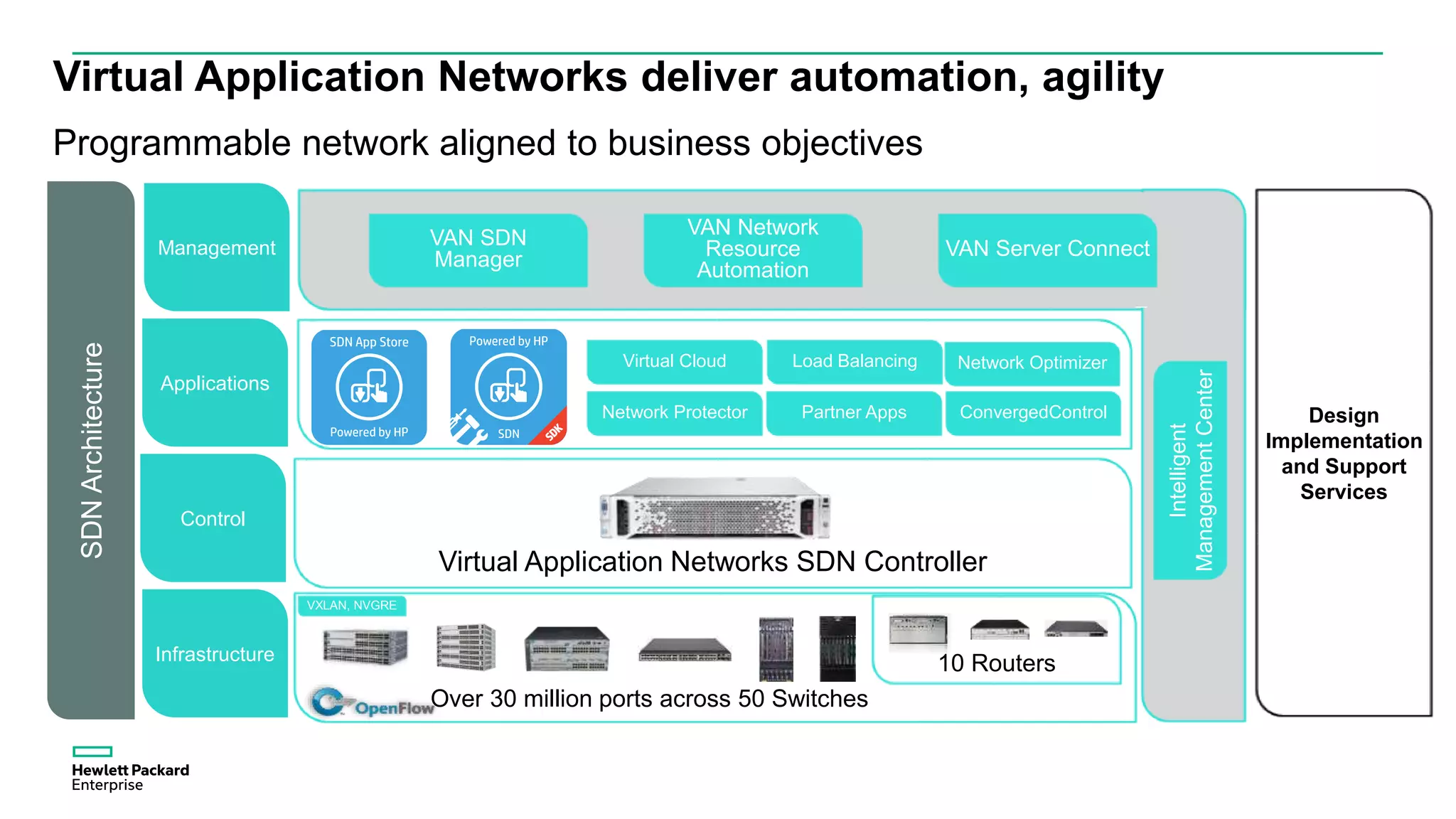
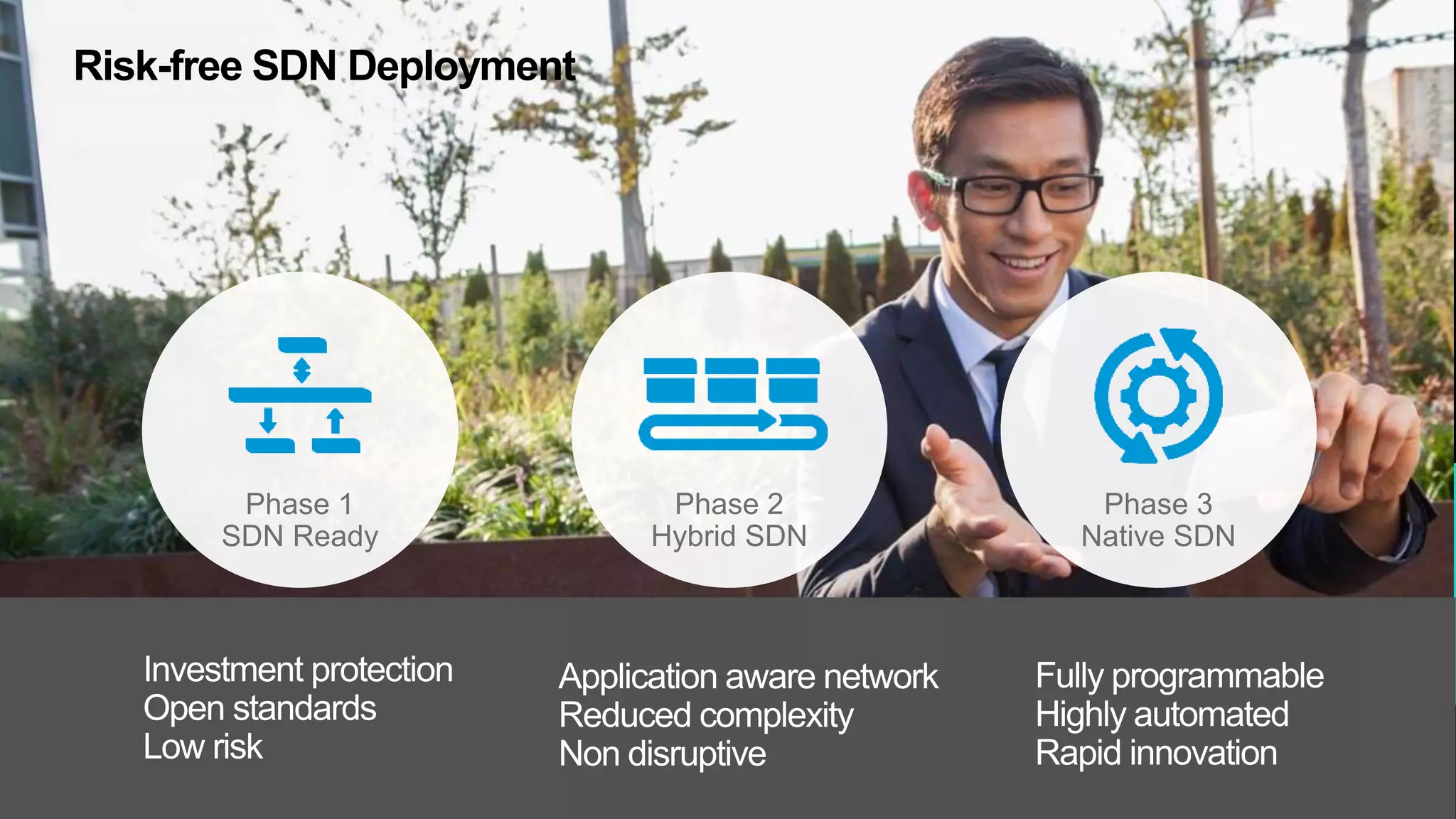
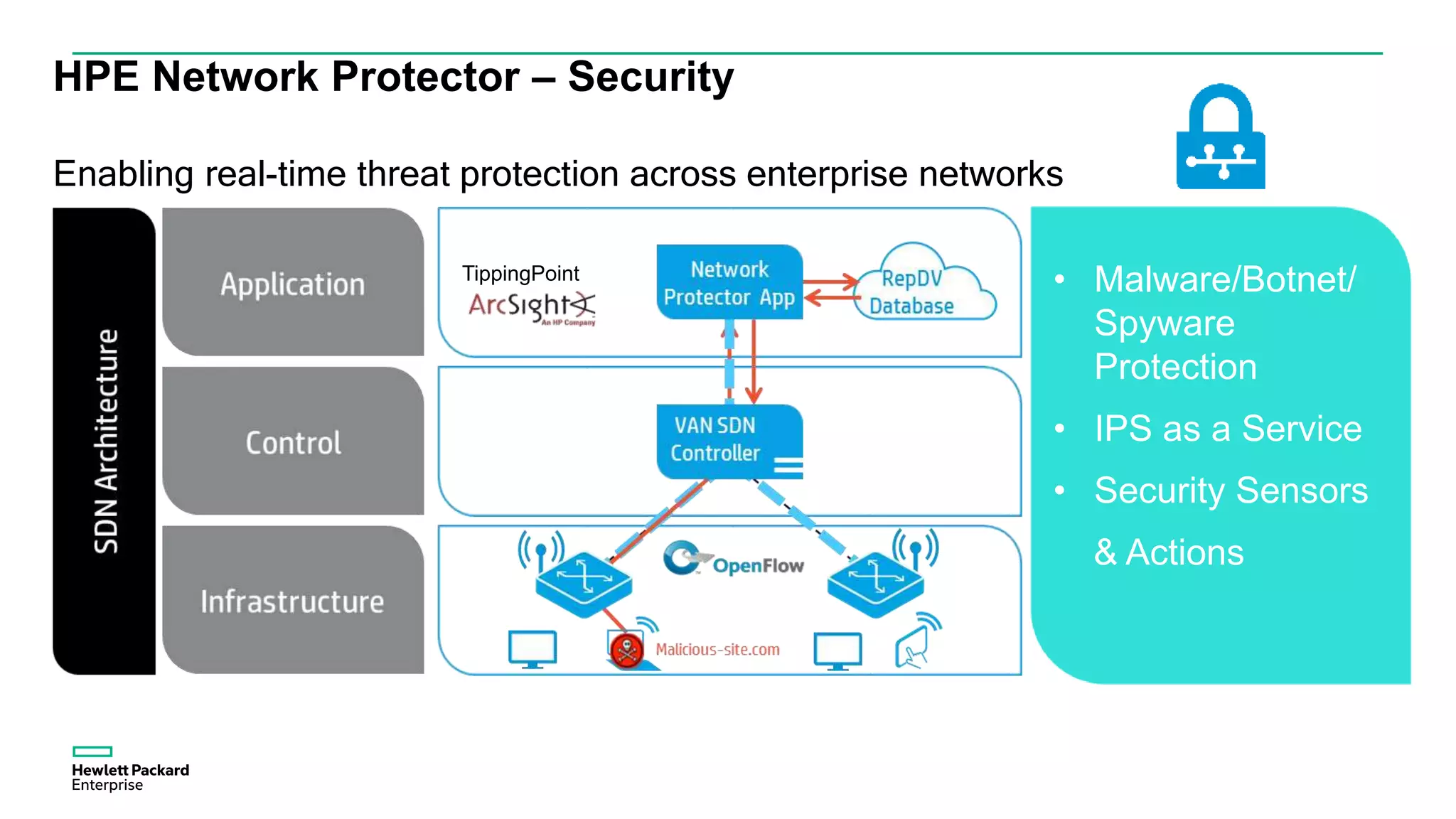
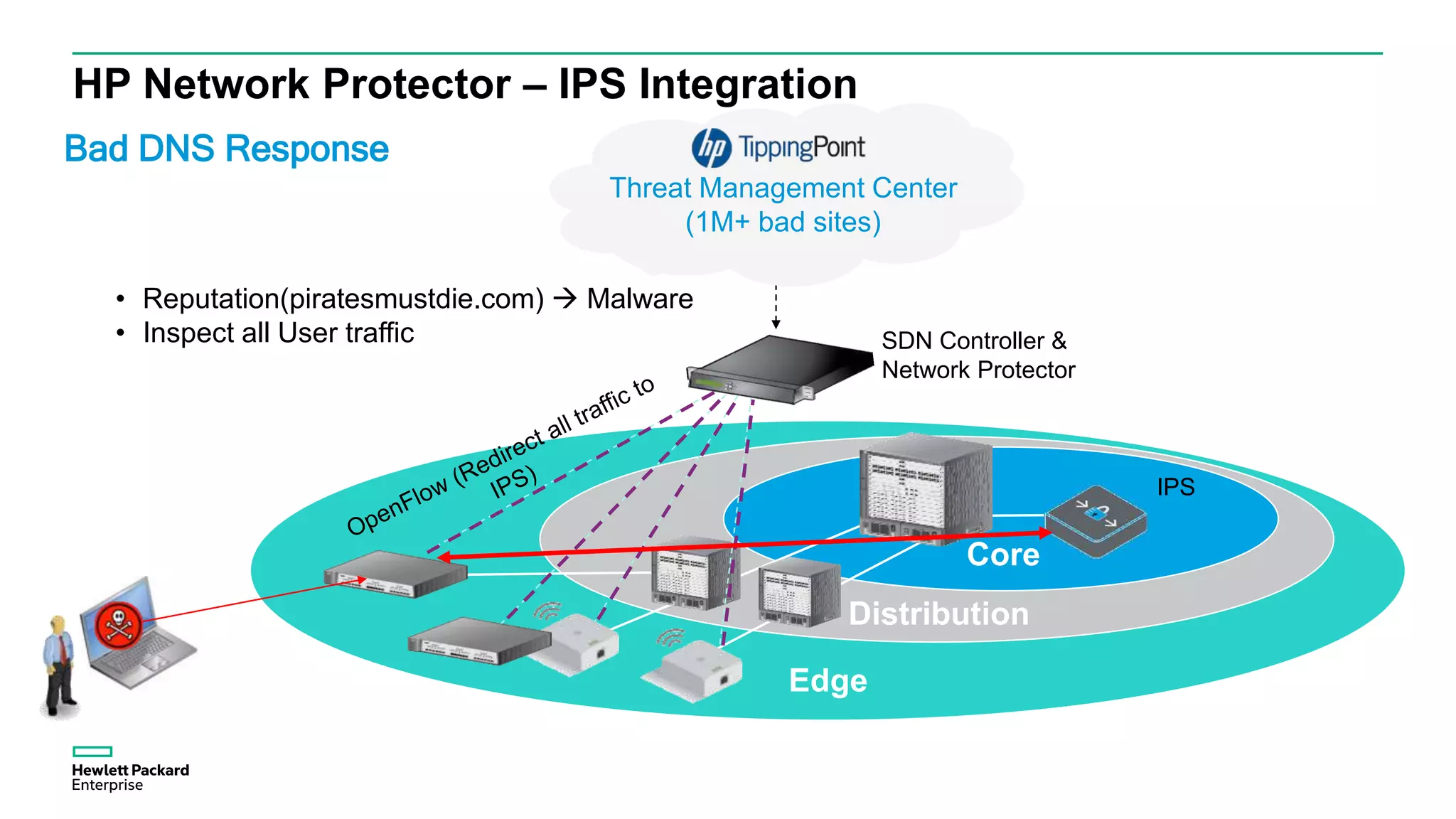
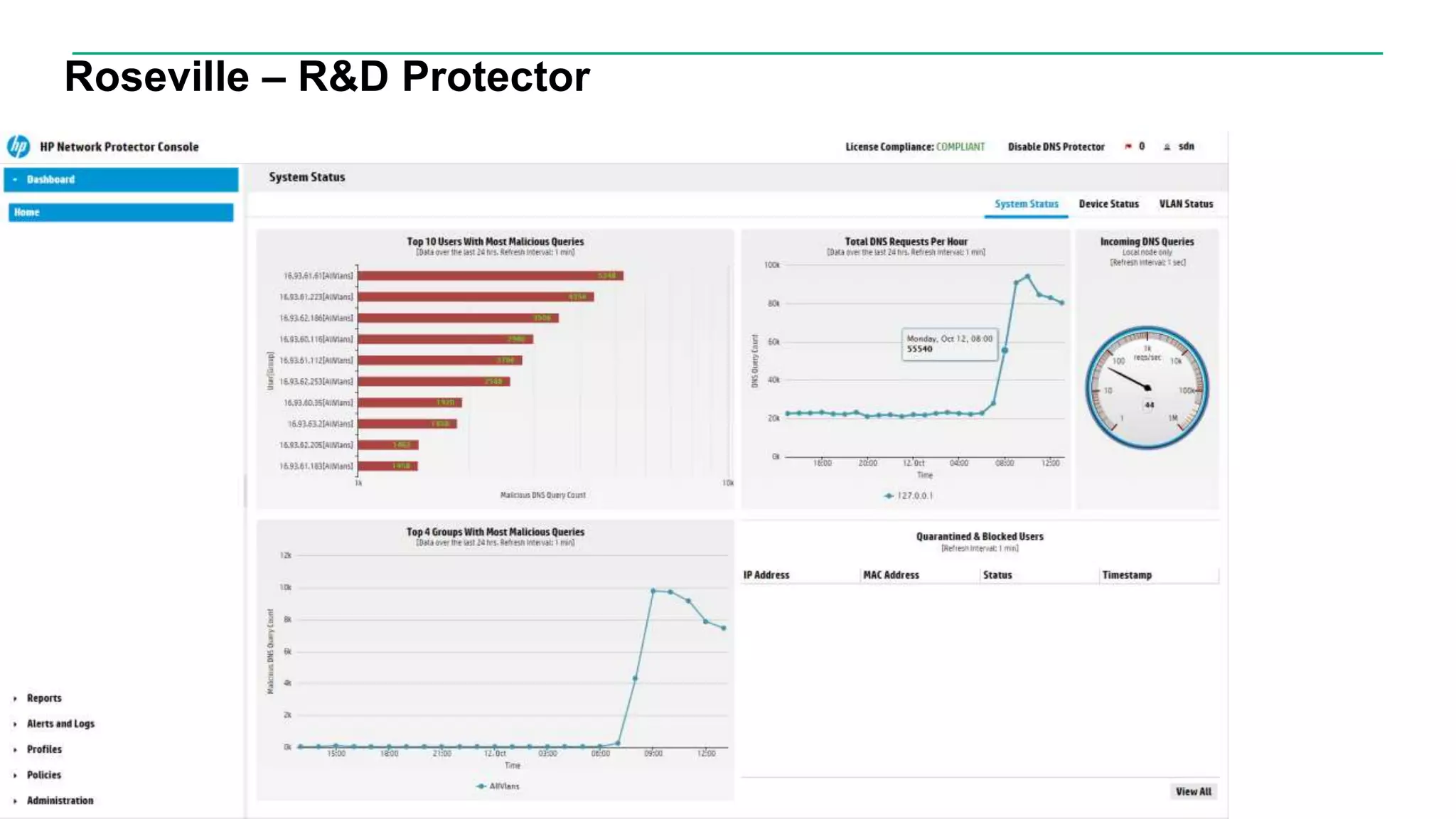
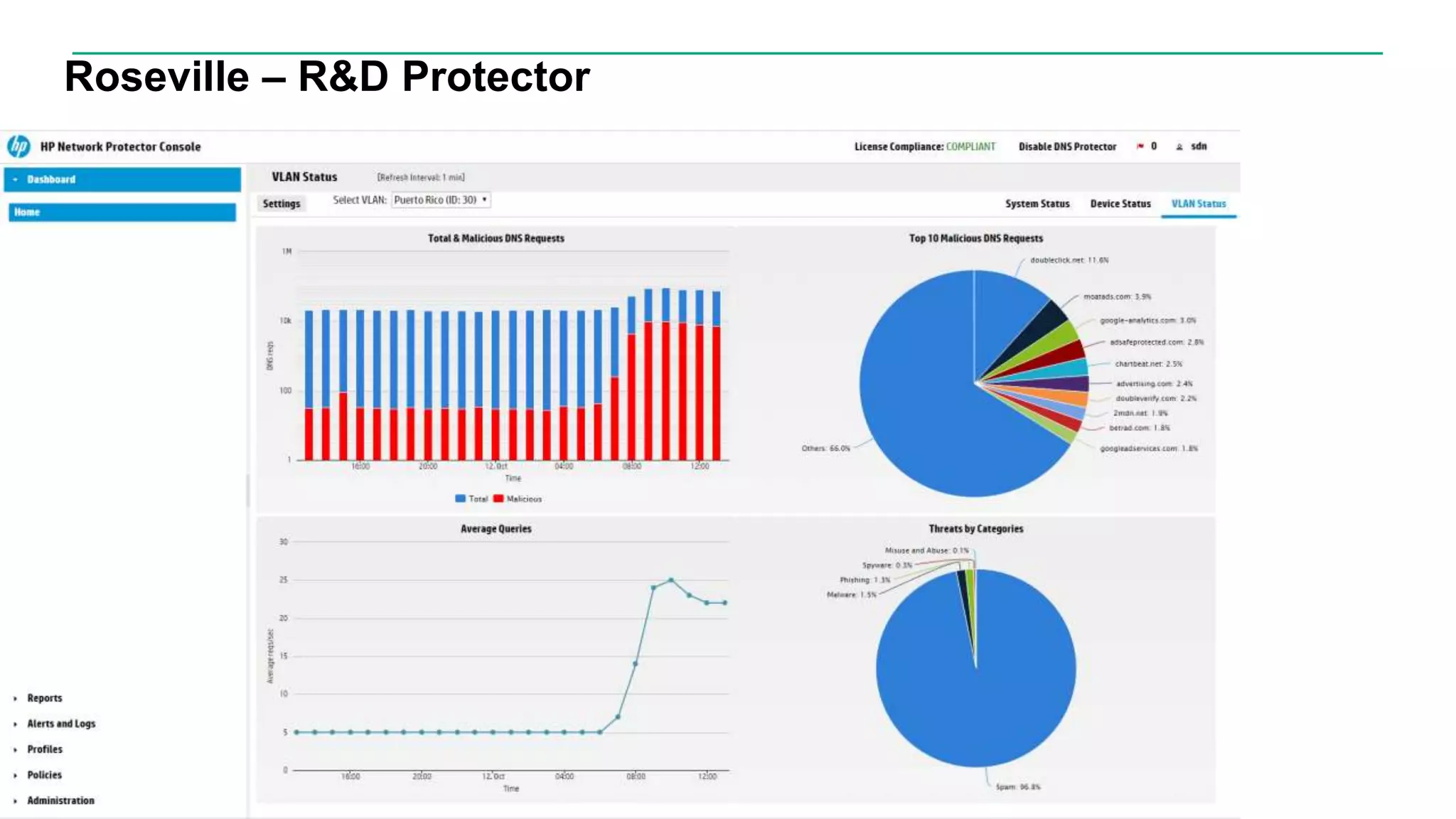
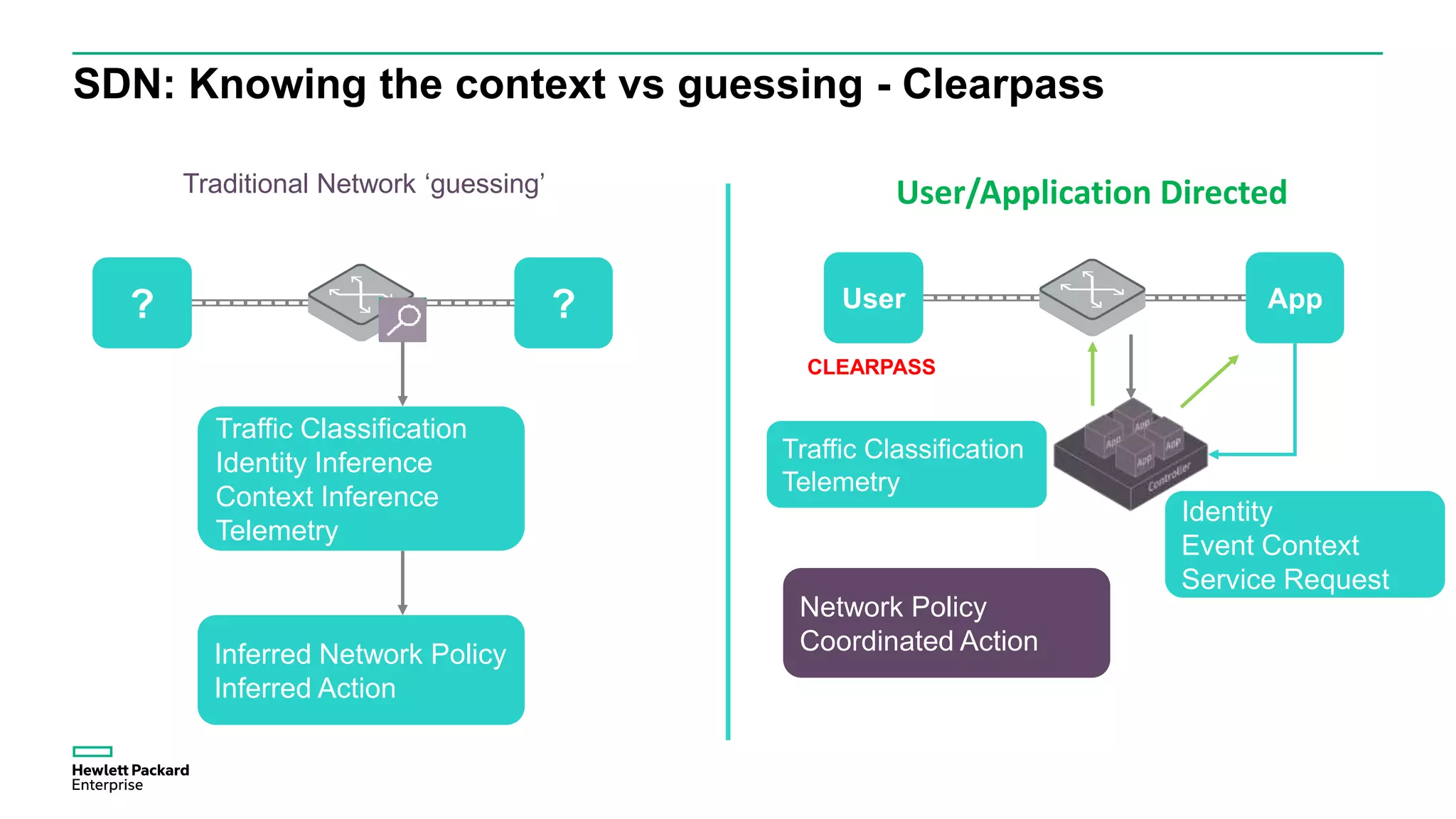
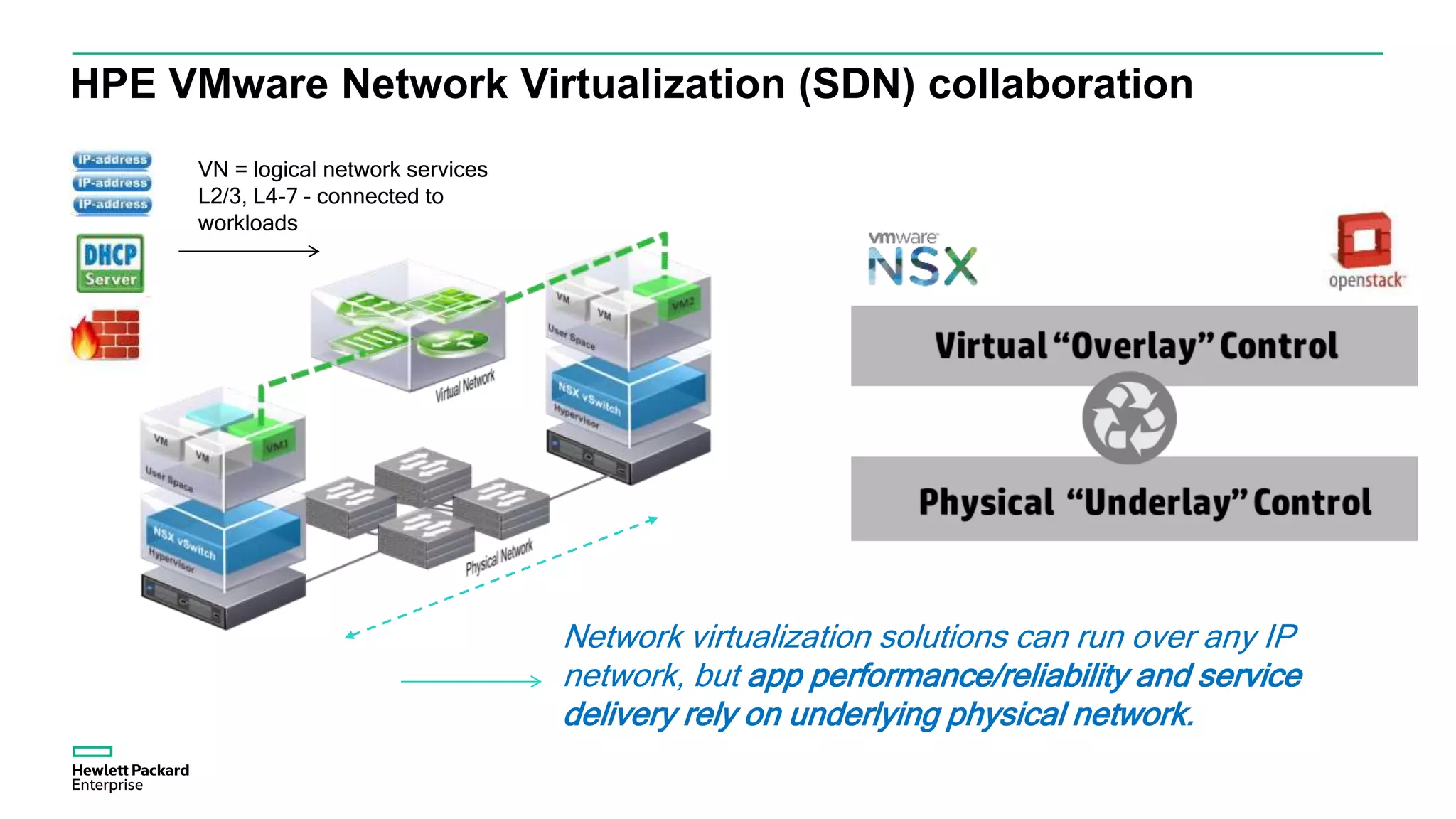
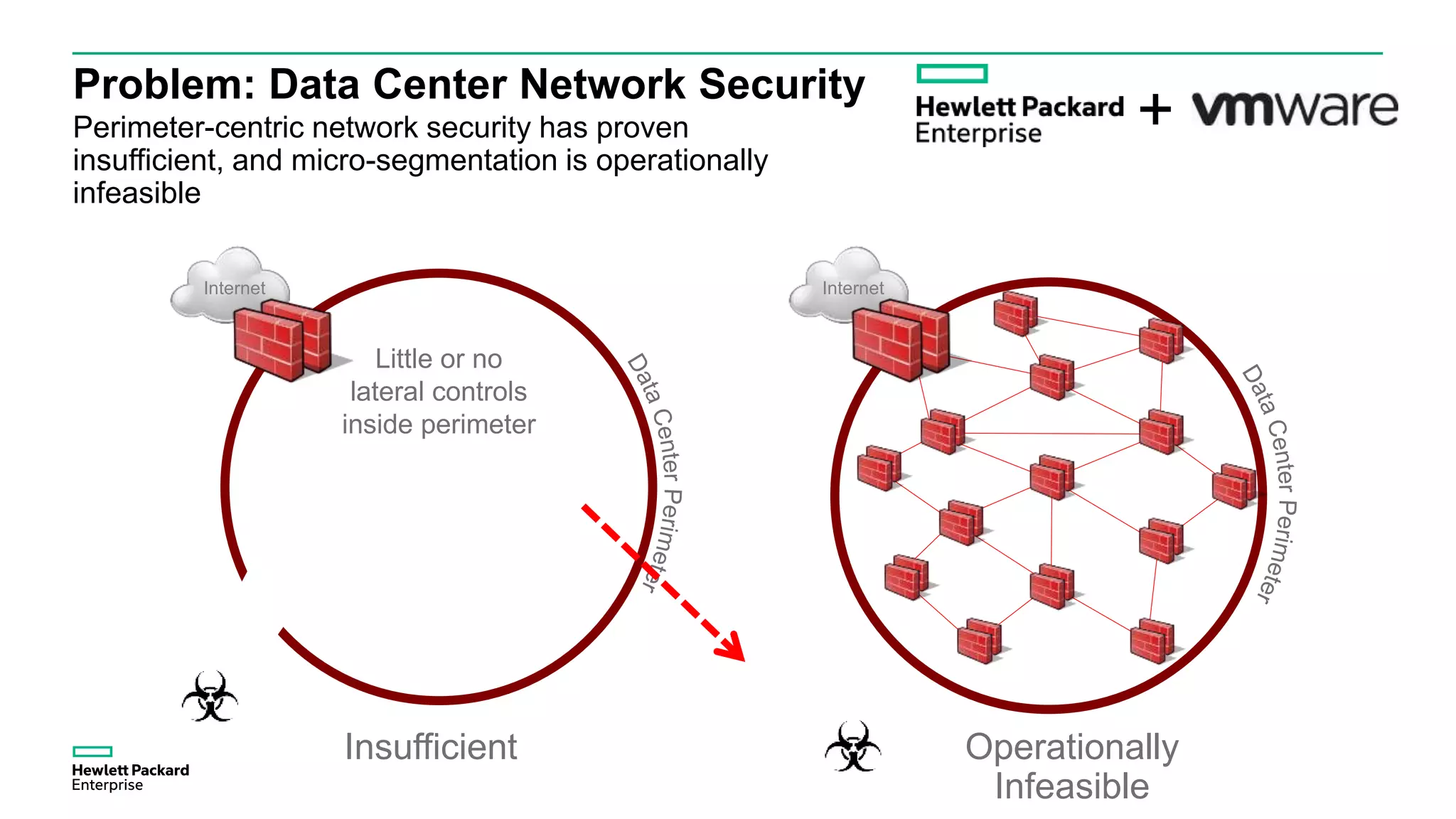
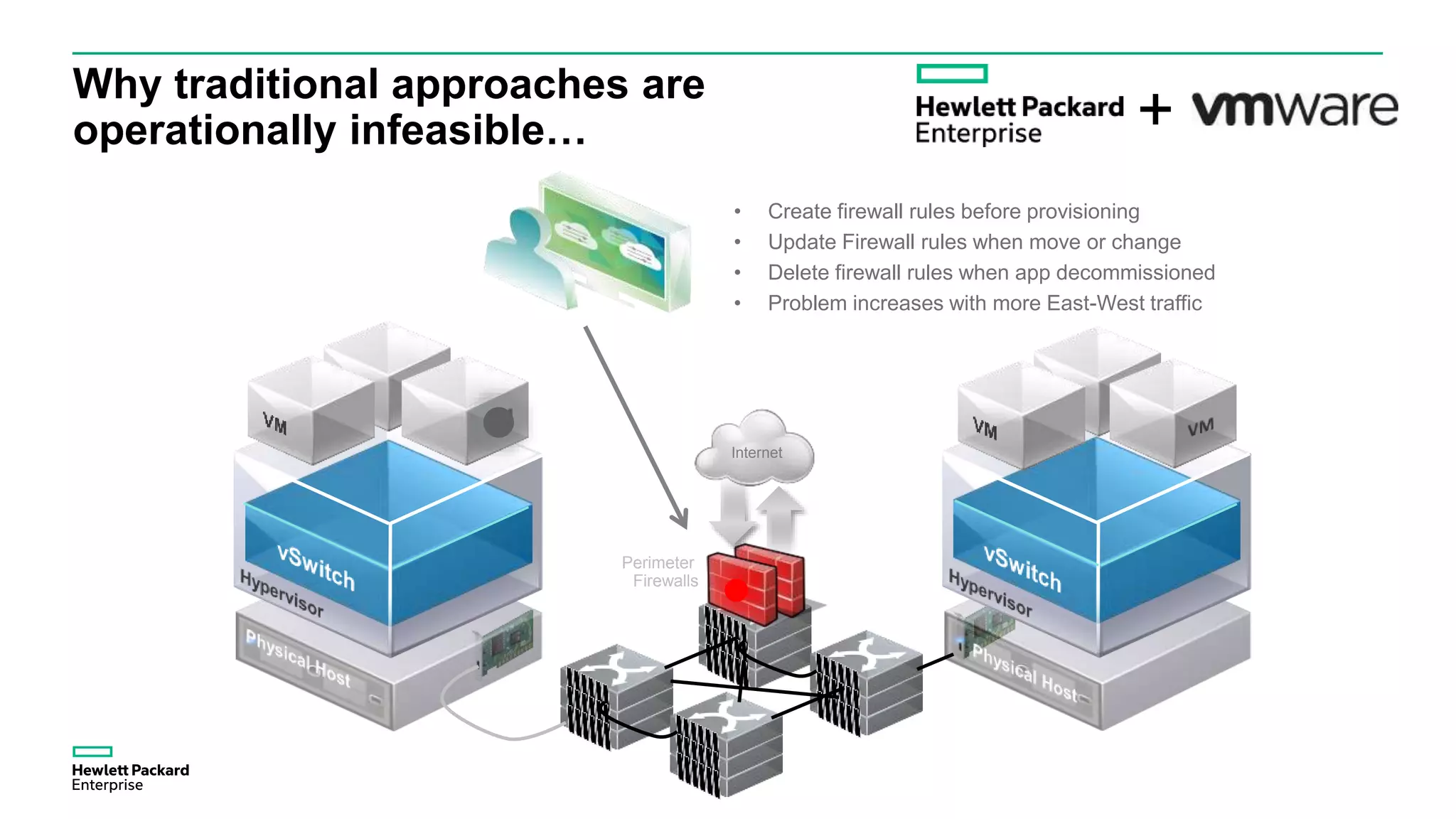
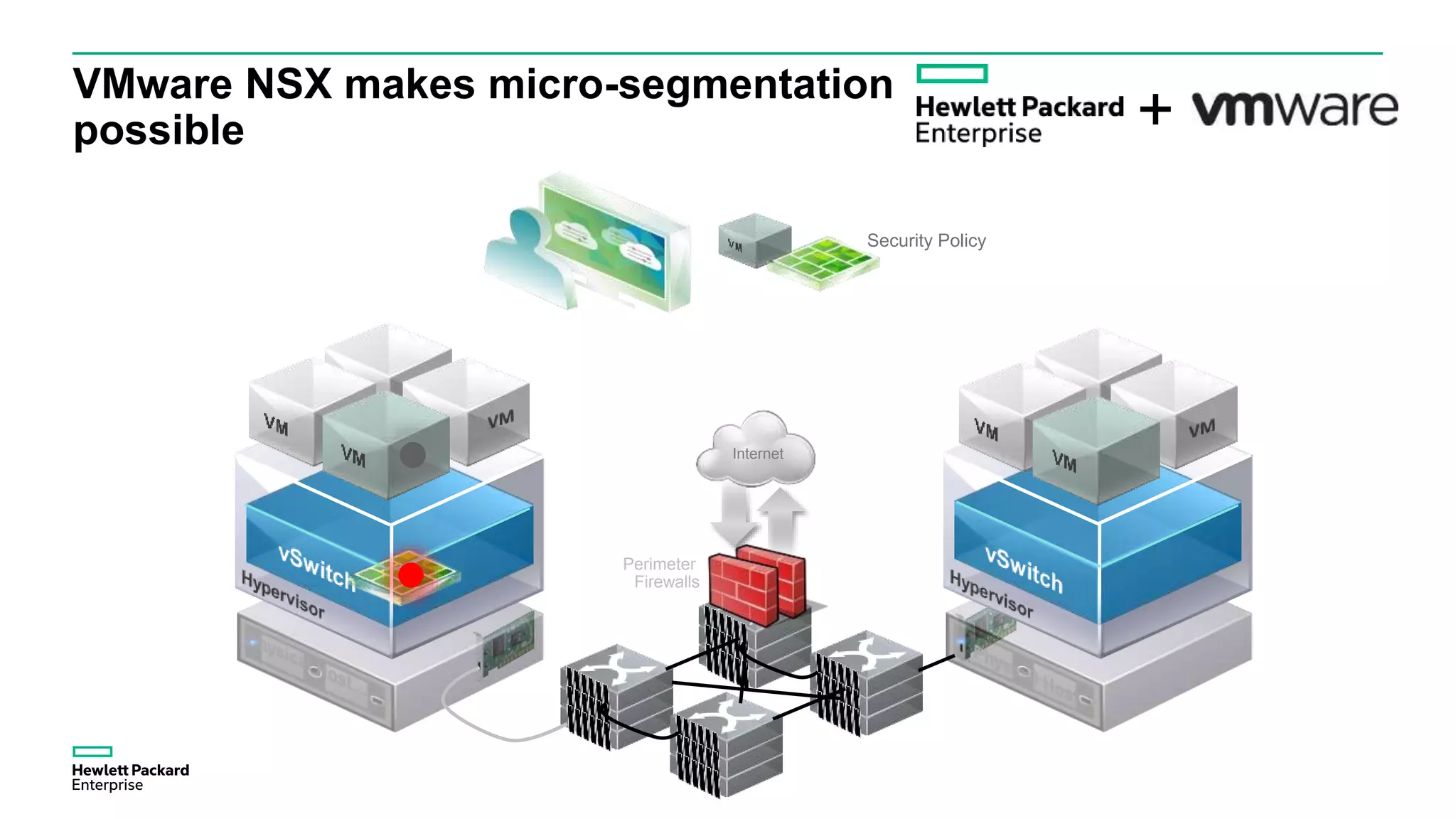
This document discusses how Hewlett Packard Enterprise uses software-defined networking (SDN) to secure campus networks. SDN provides programmable networks that can rapidly align with business applications. HPE delivers the functions of an SDN architecture, including separating the control and data planes and providing open programmable interfaces. This allows for network service automation through virtual application networks and security applications like Network Protector, which provides malware protection and intrusion prevention. The document provides examples of customers using HPE's SDN solutions and the benefits of risk-free SDN deployment.