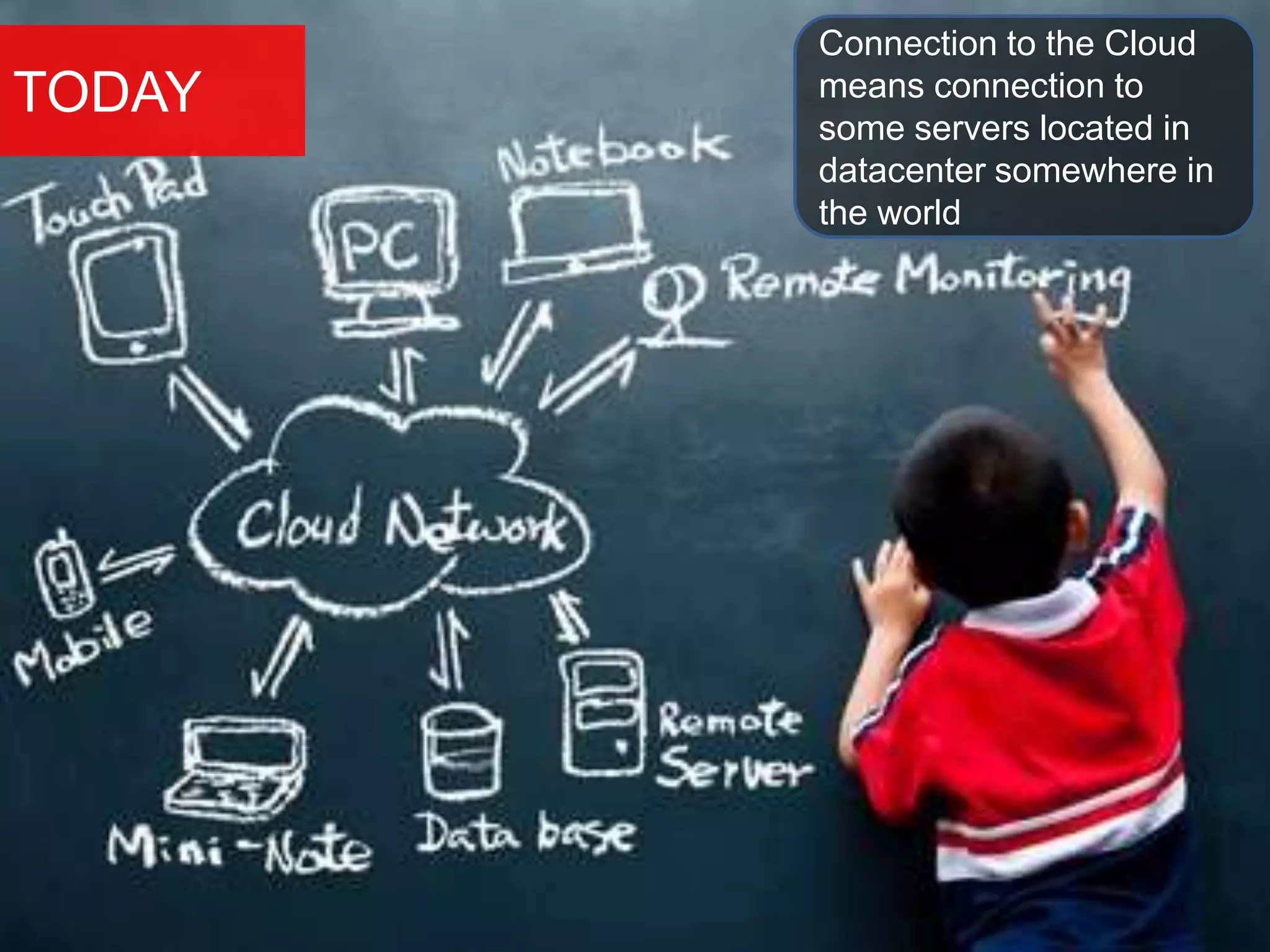
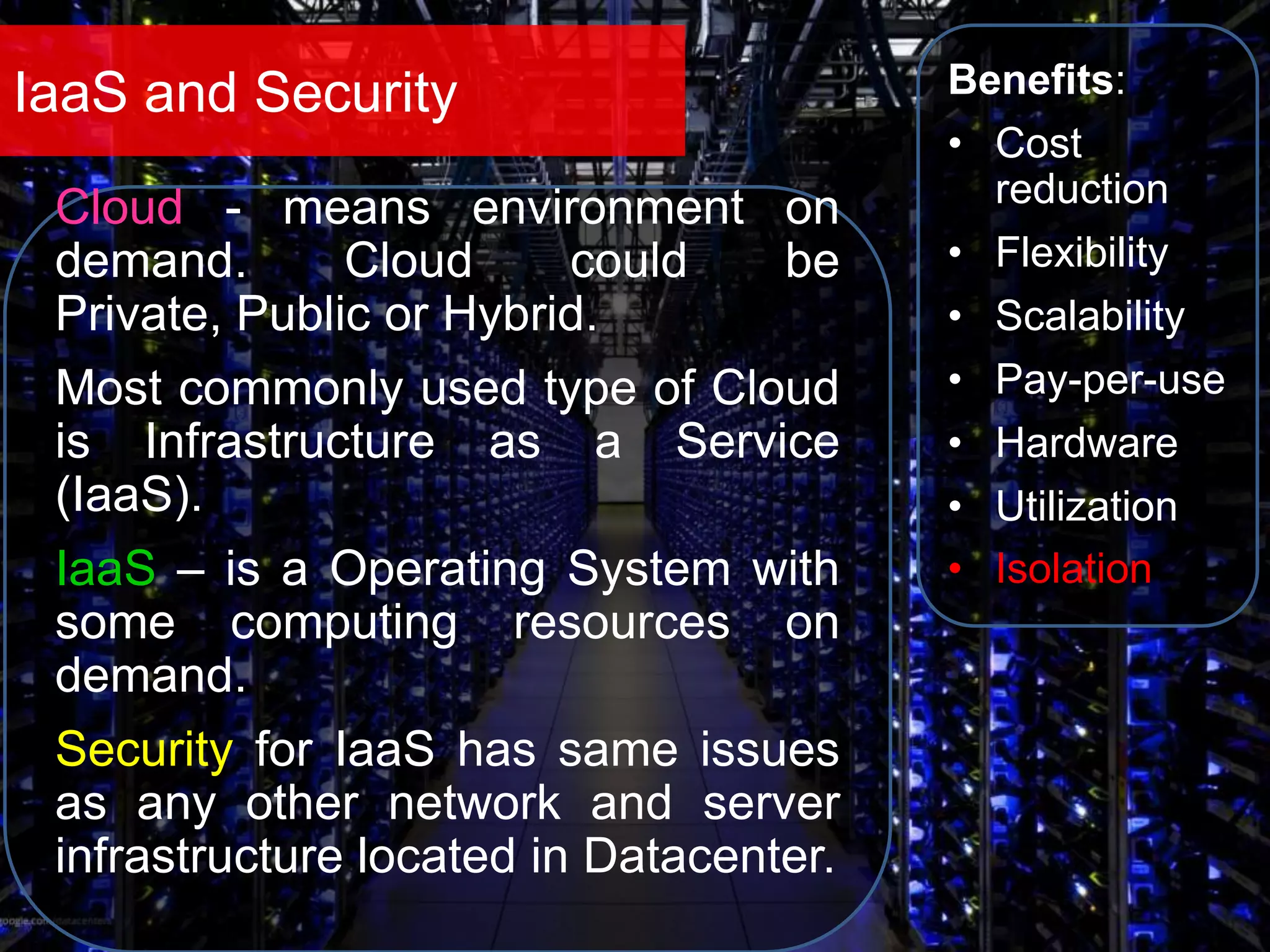
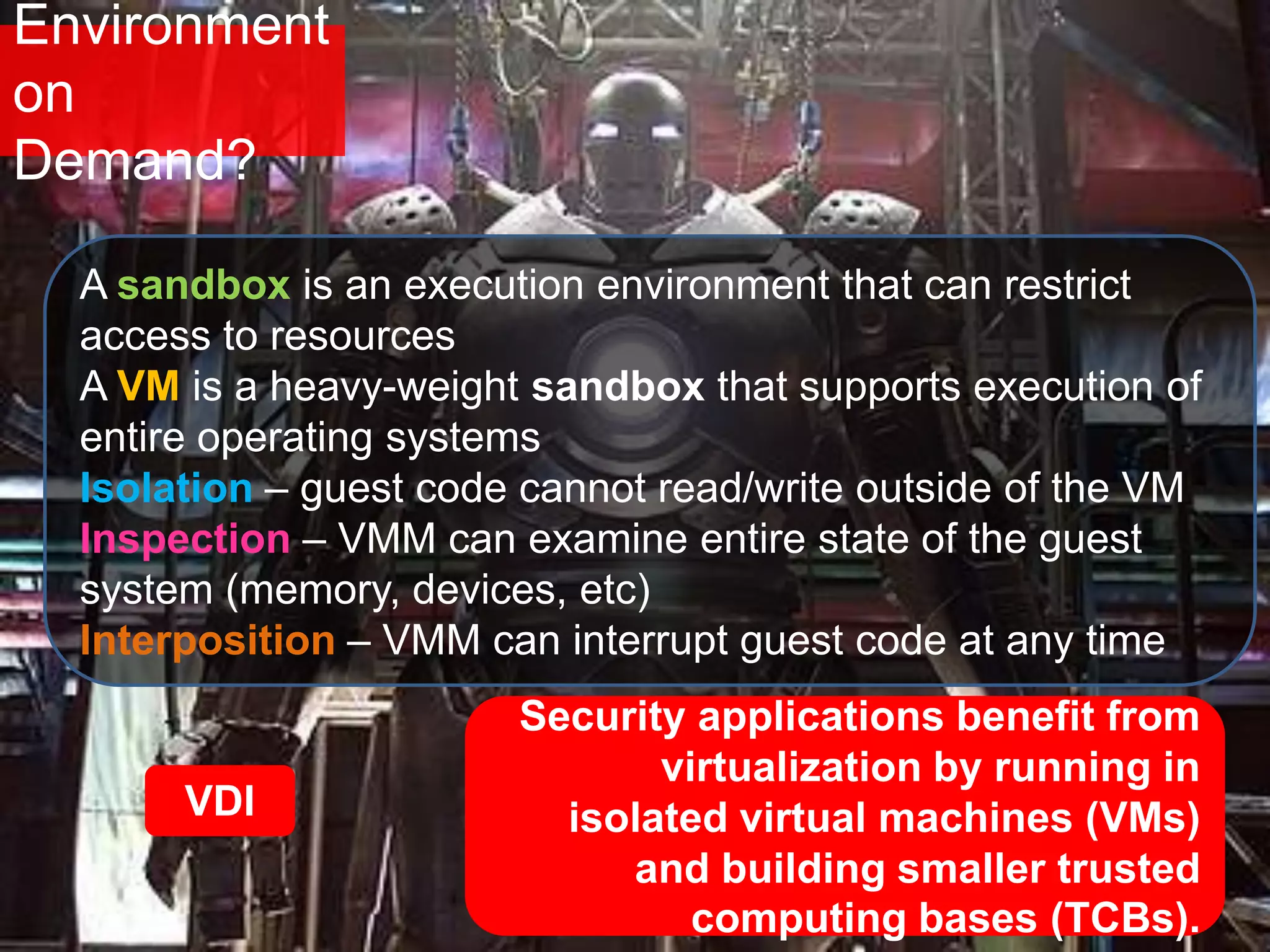
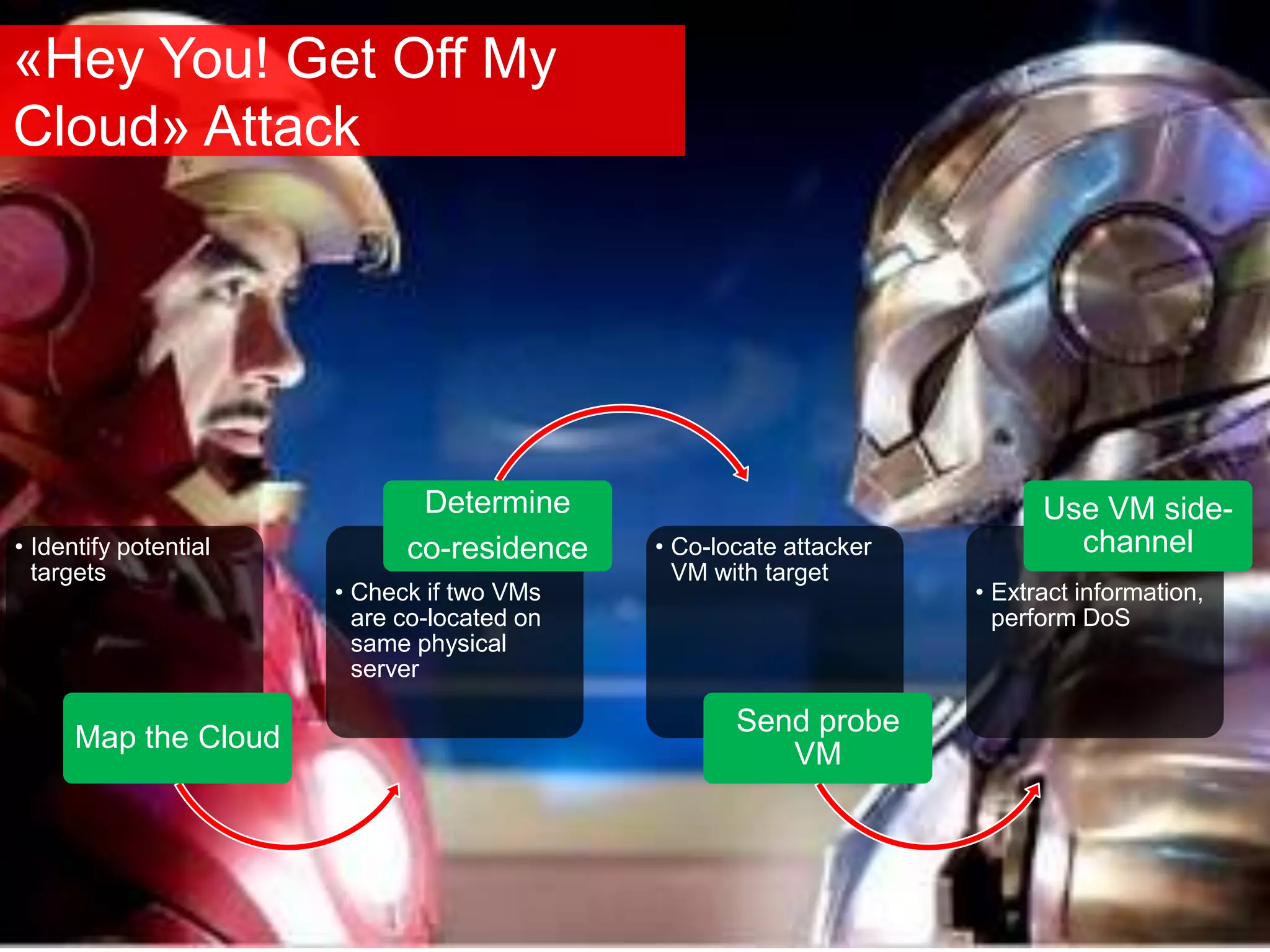
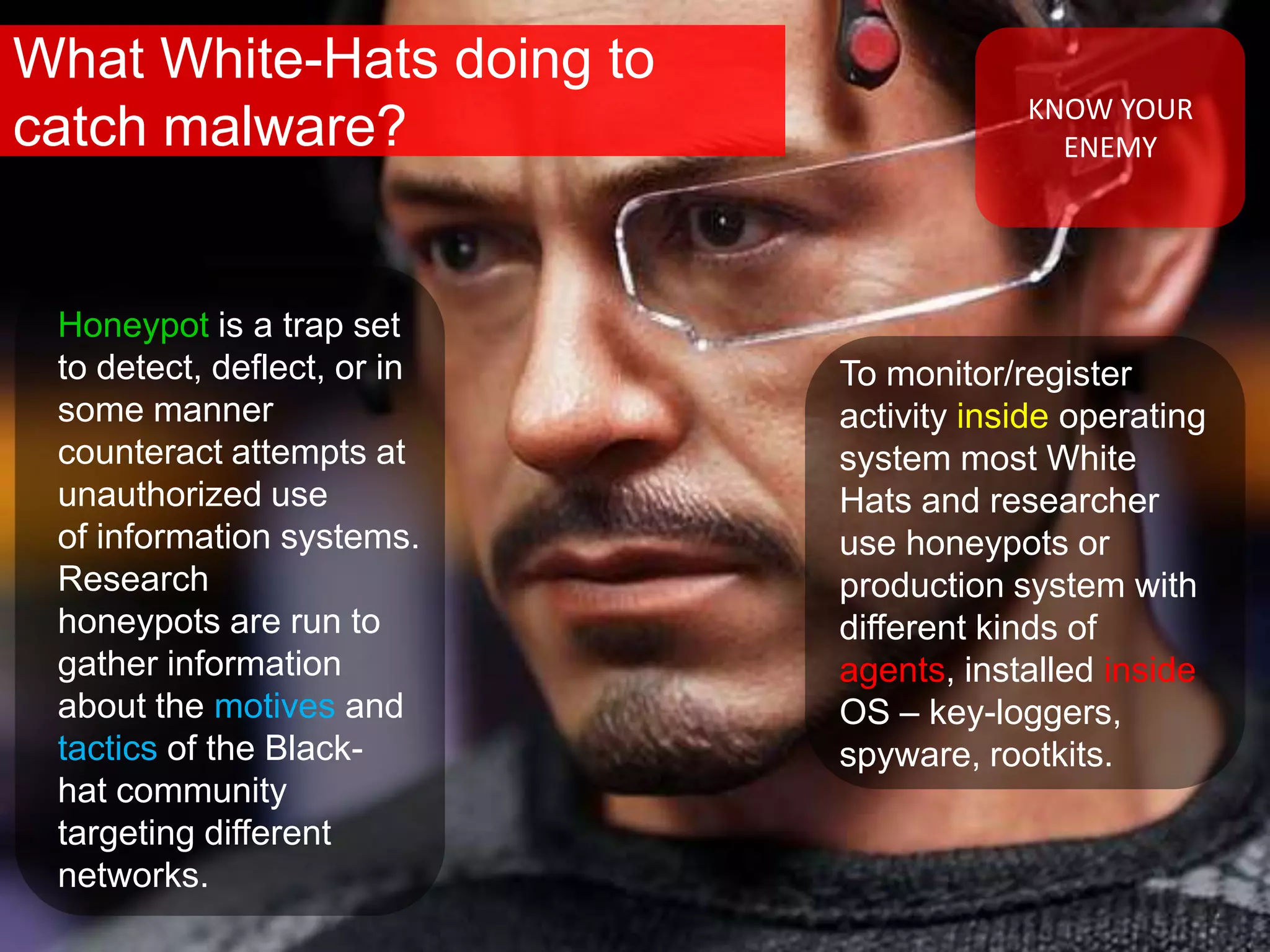
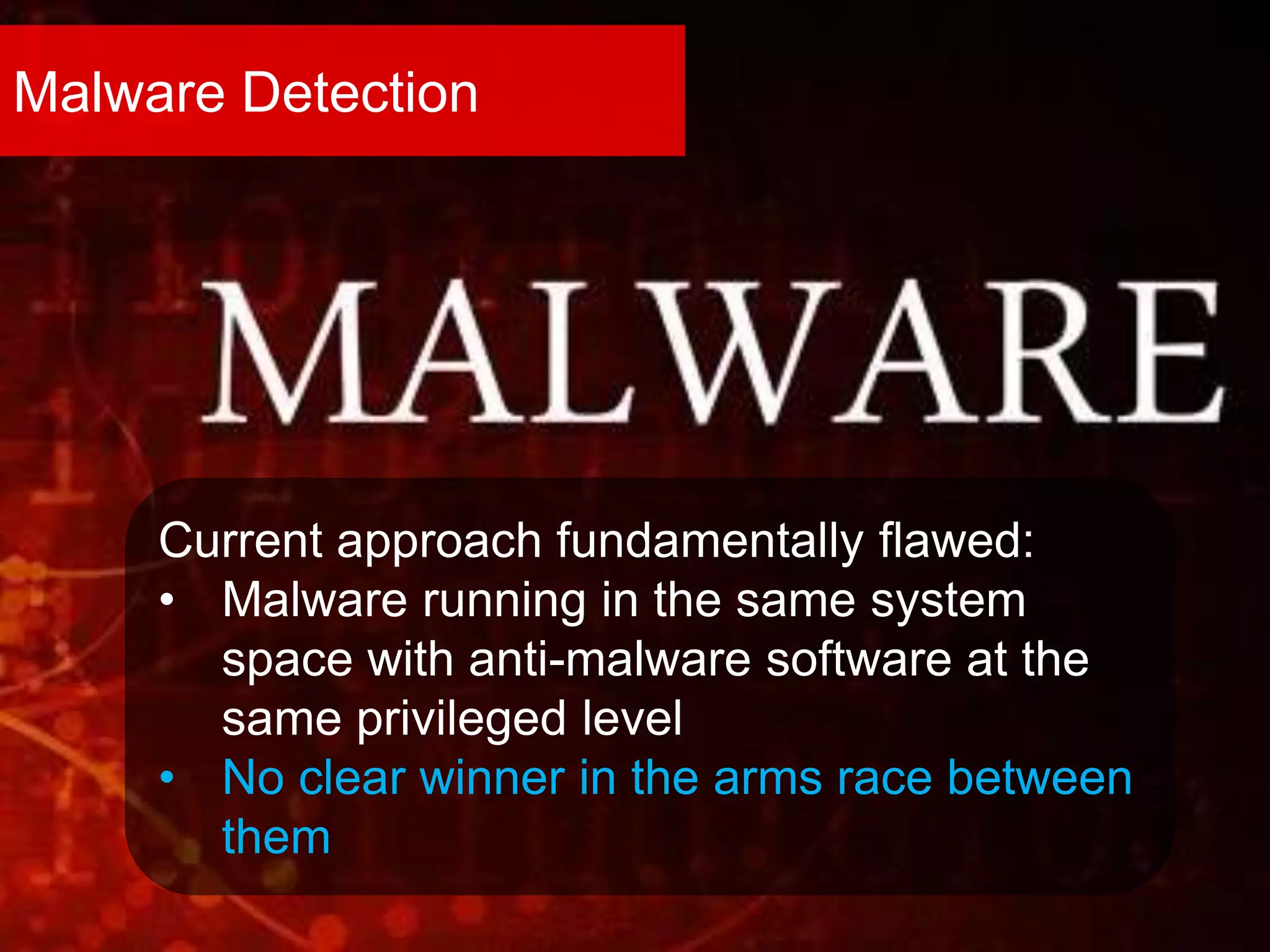
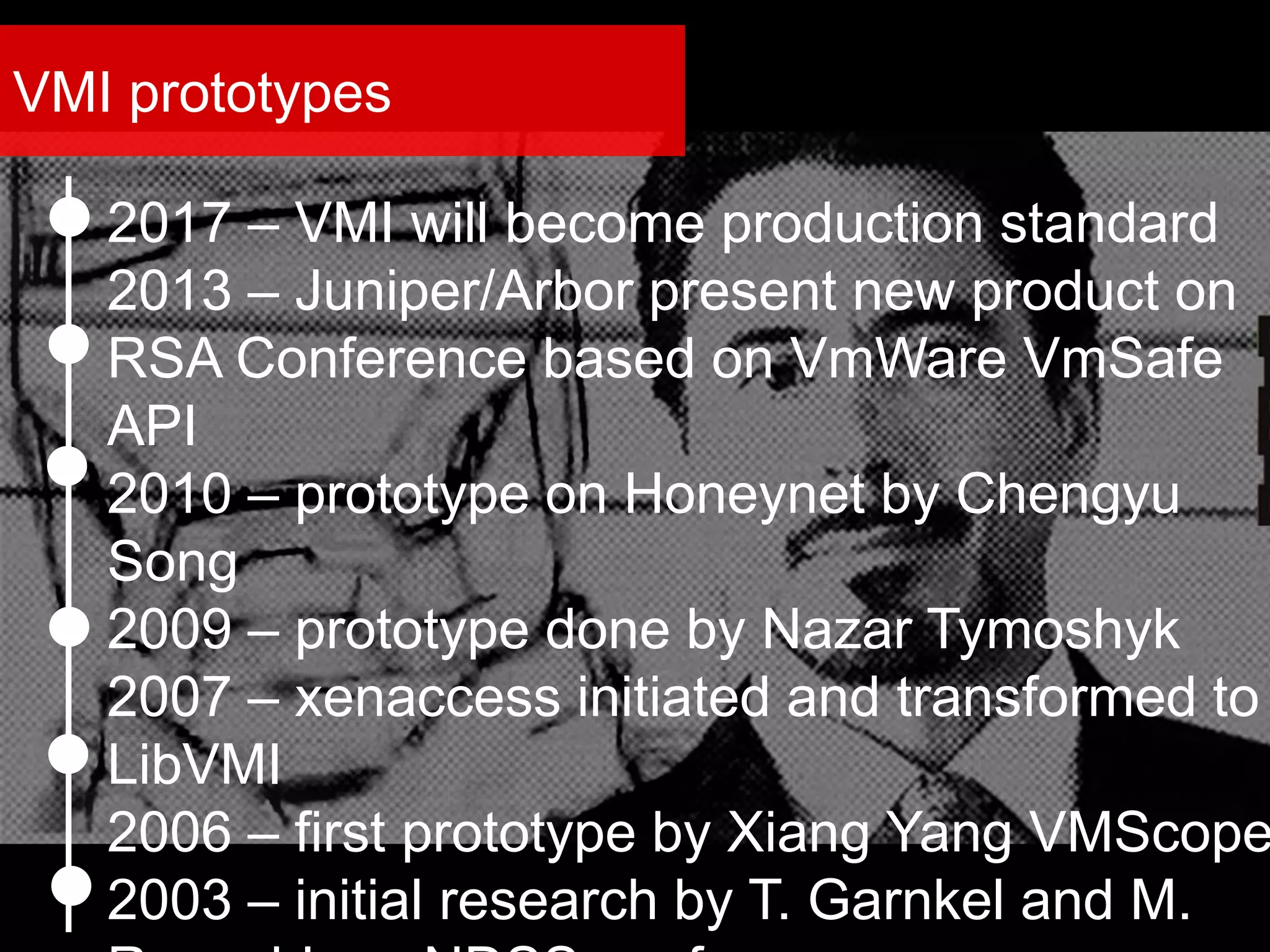
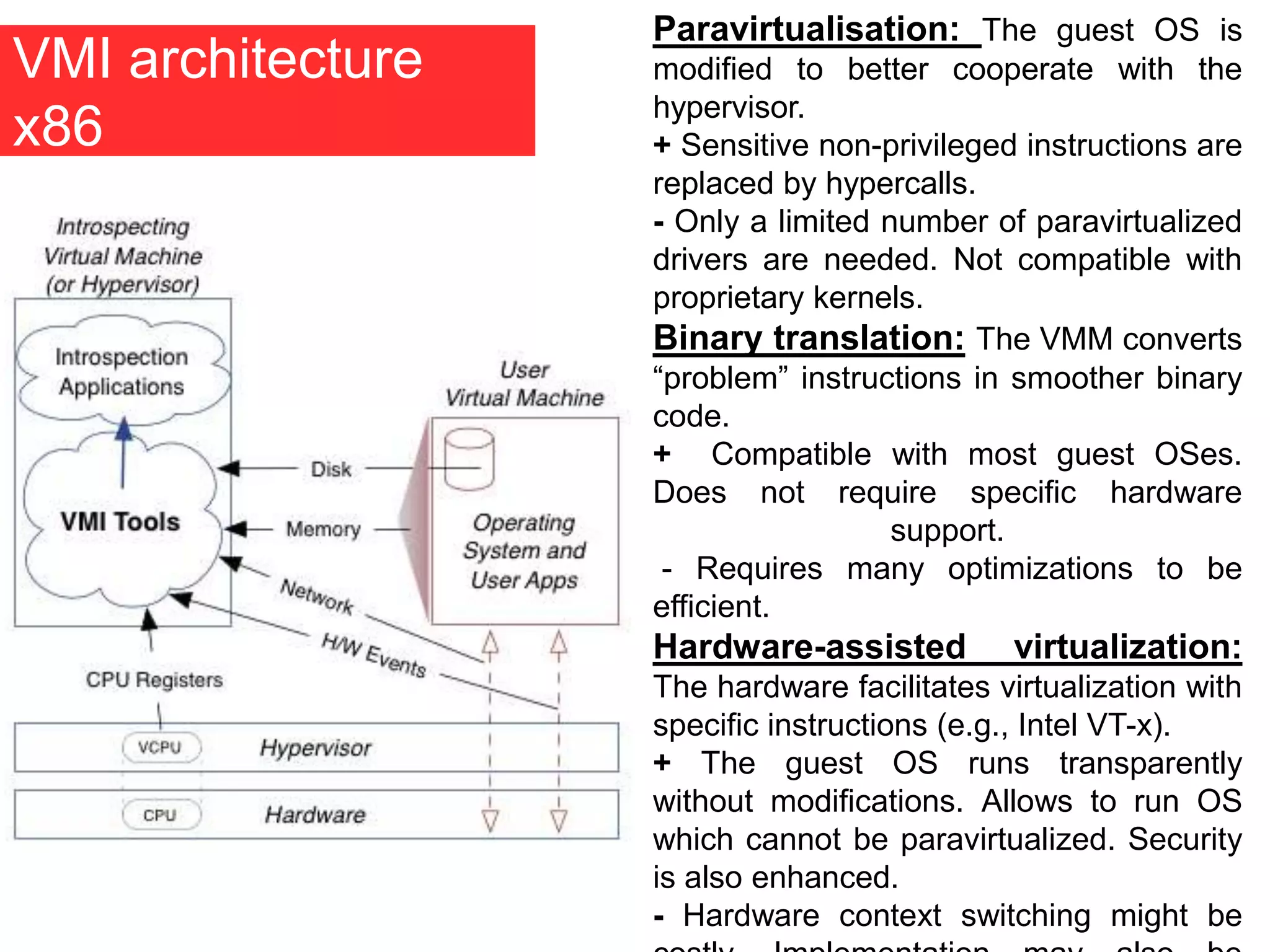
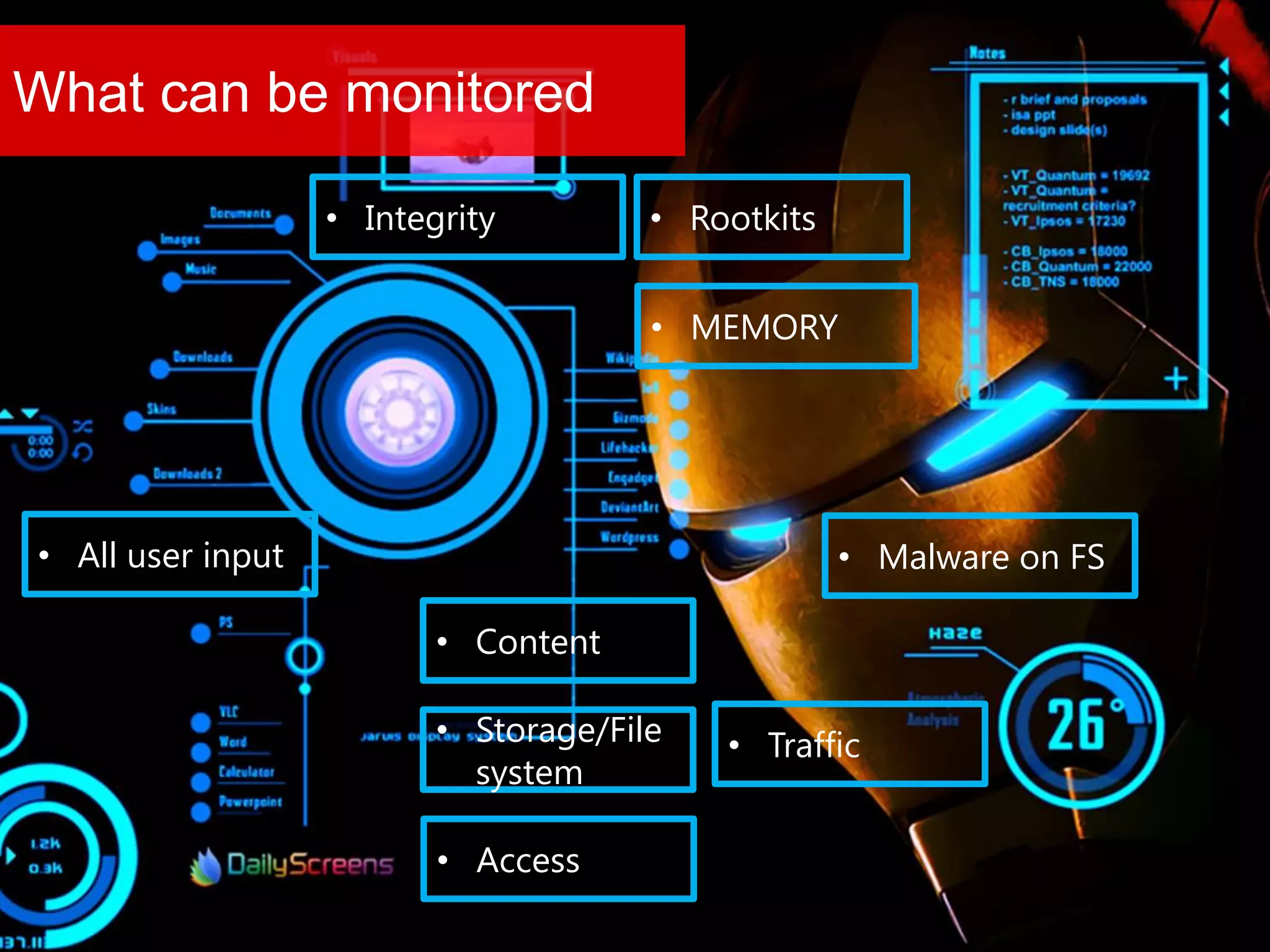
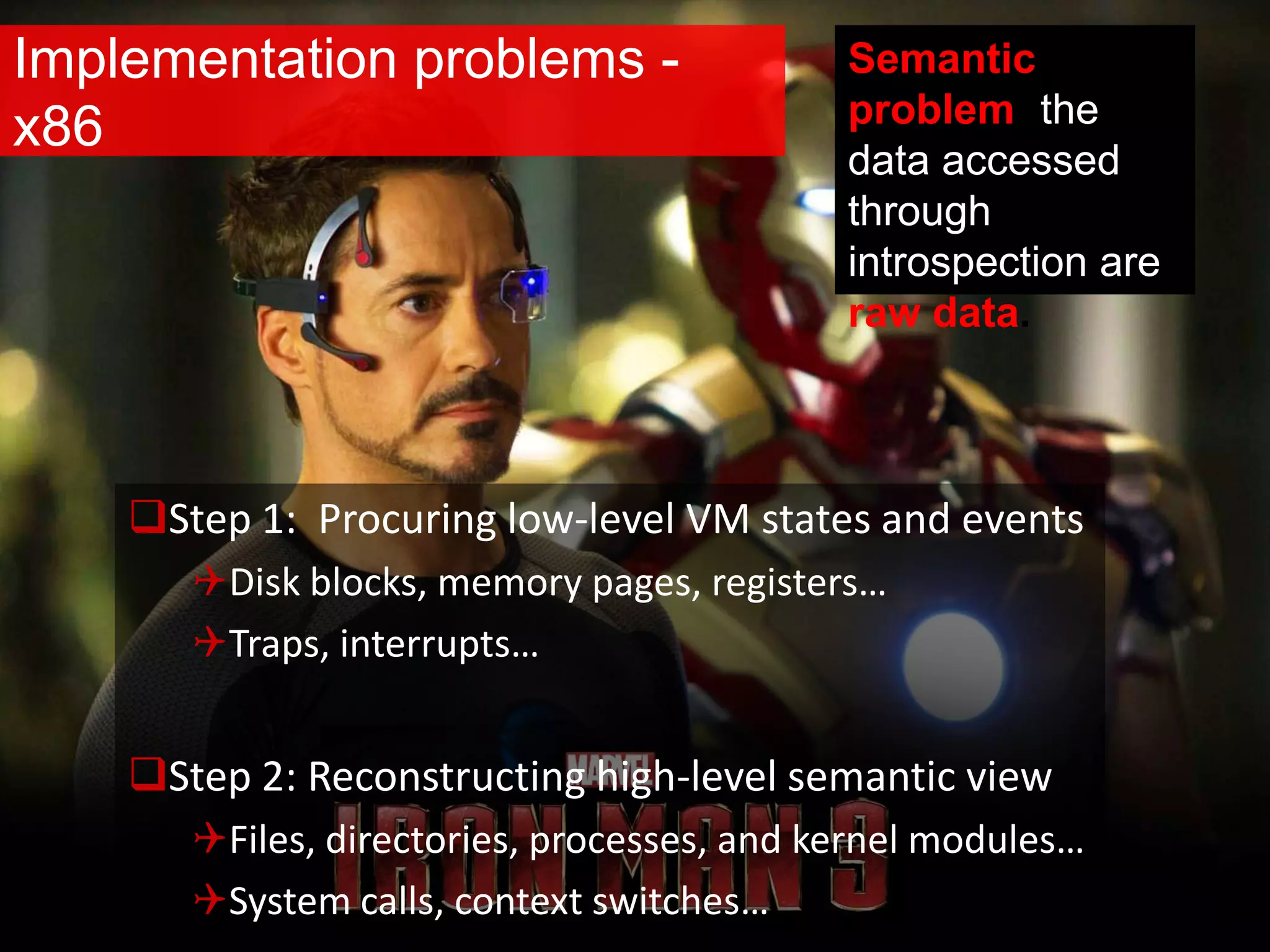
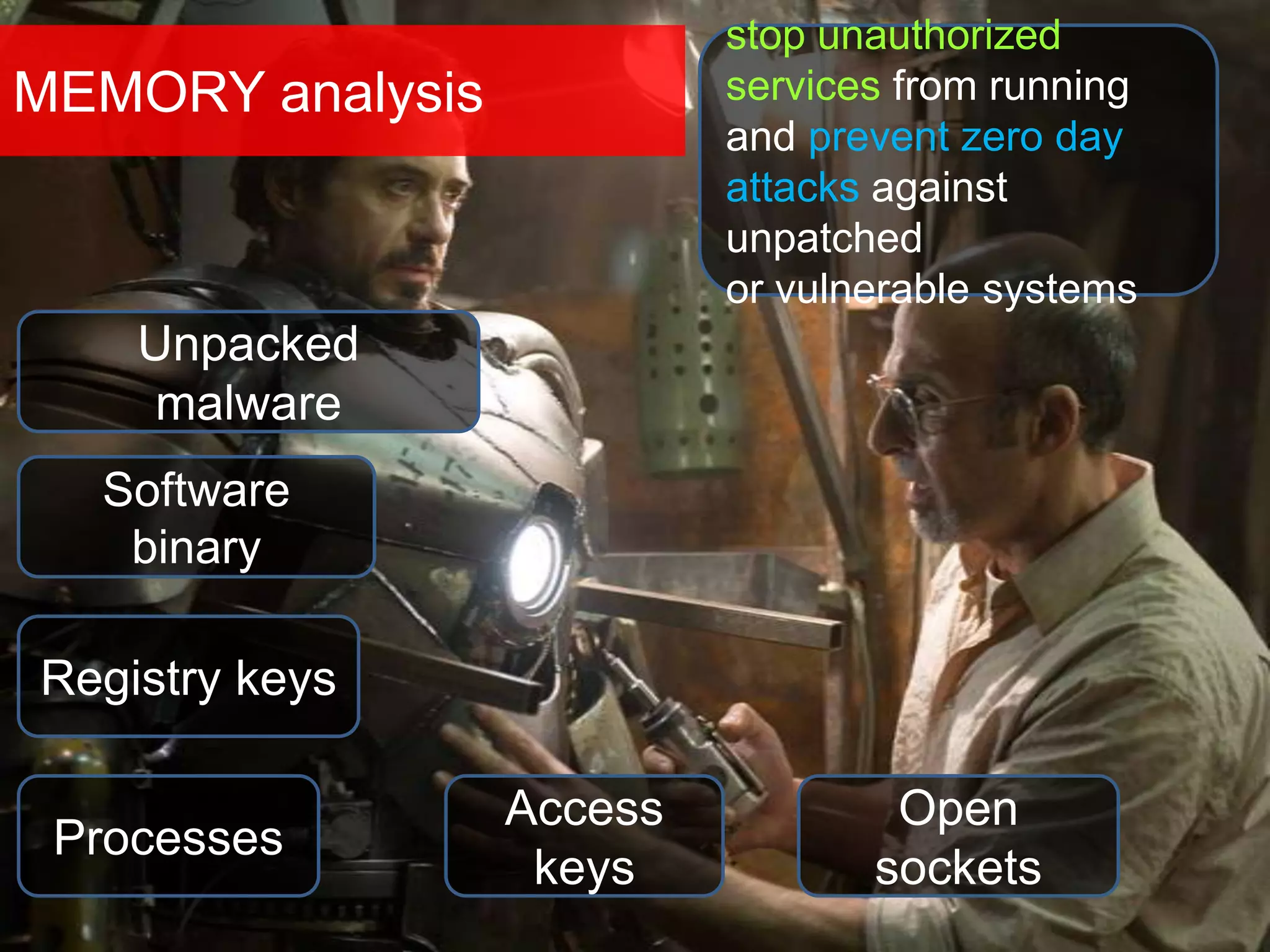
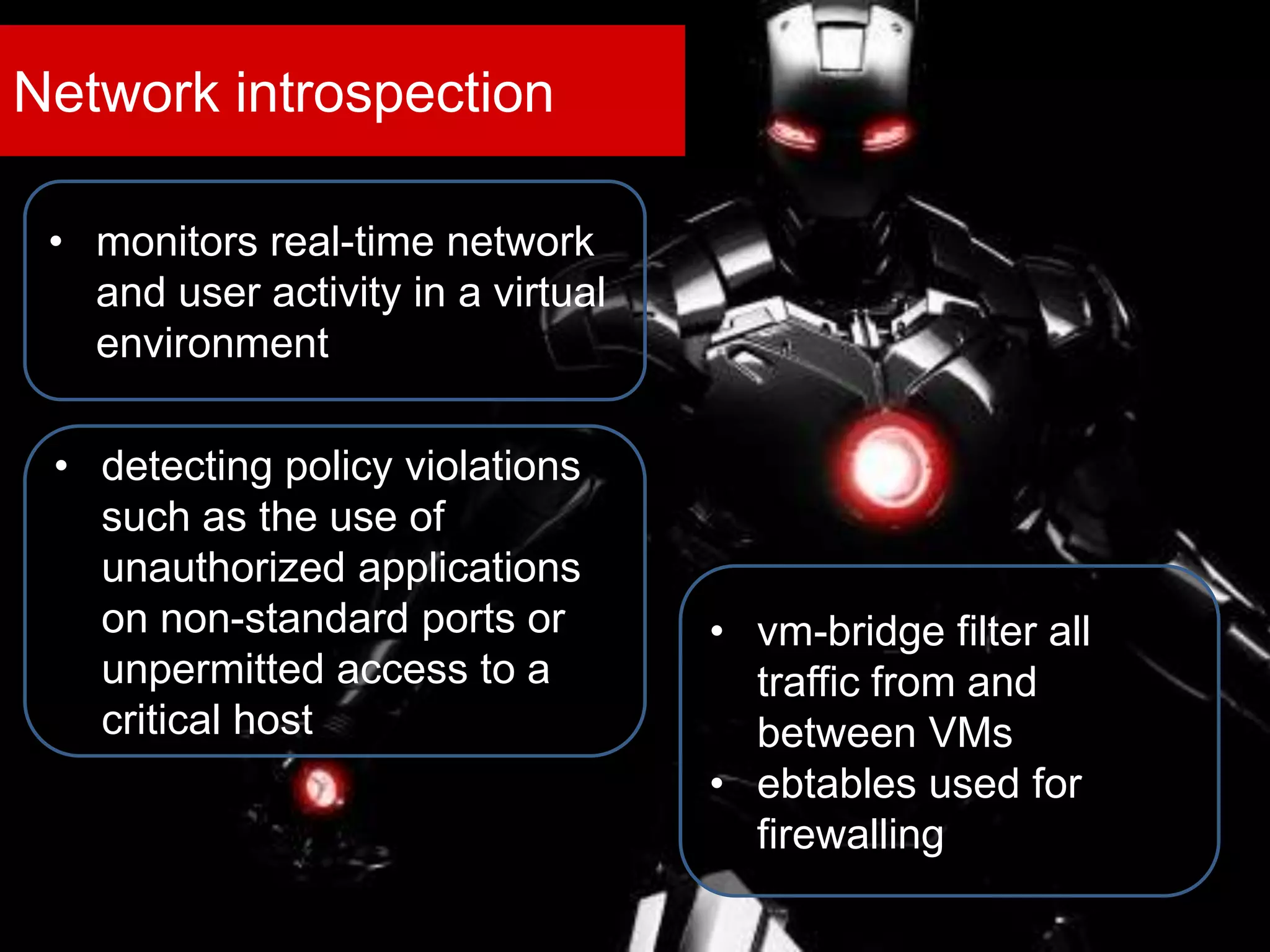
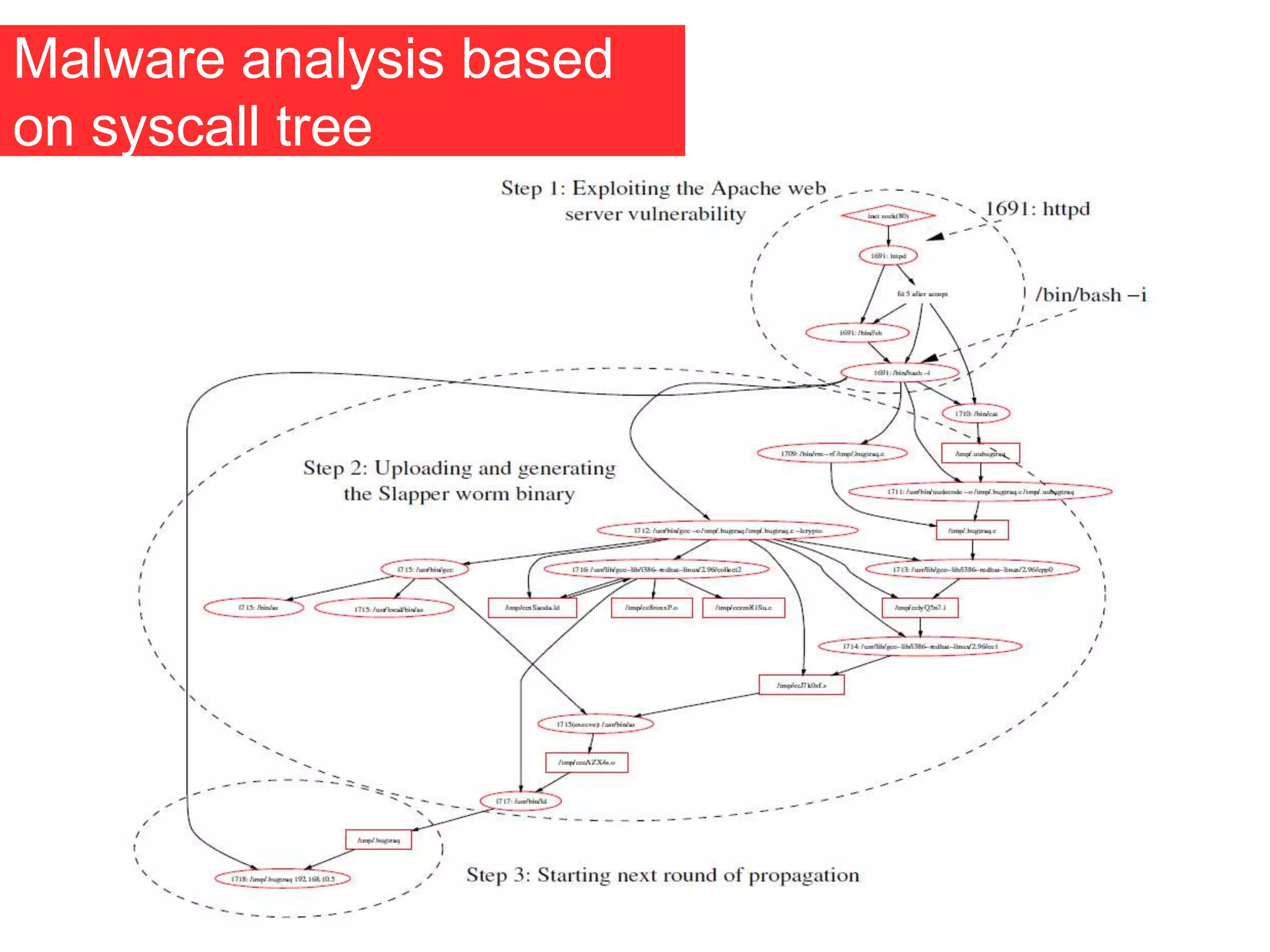
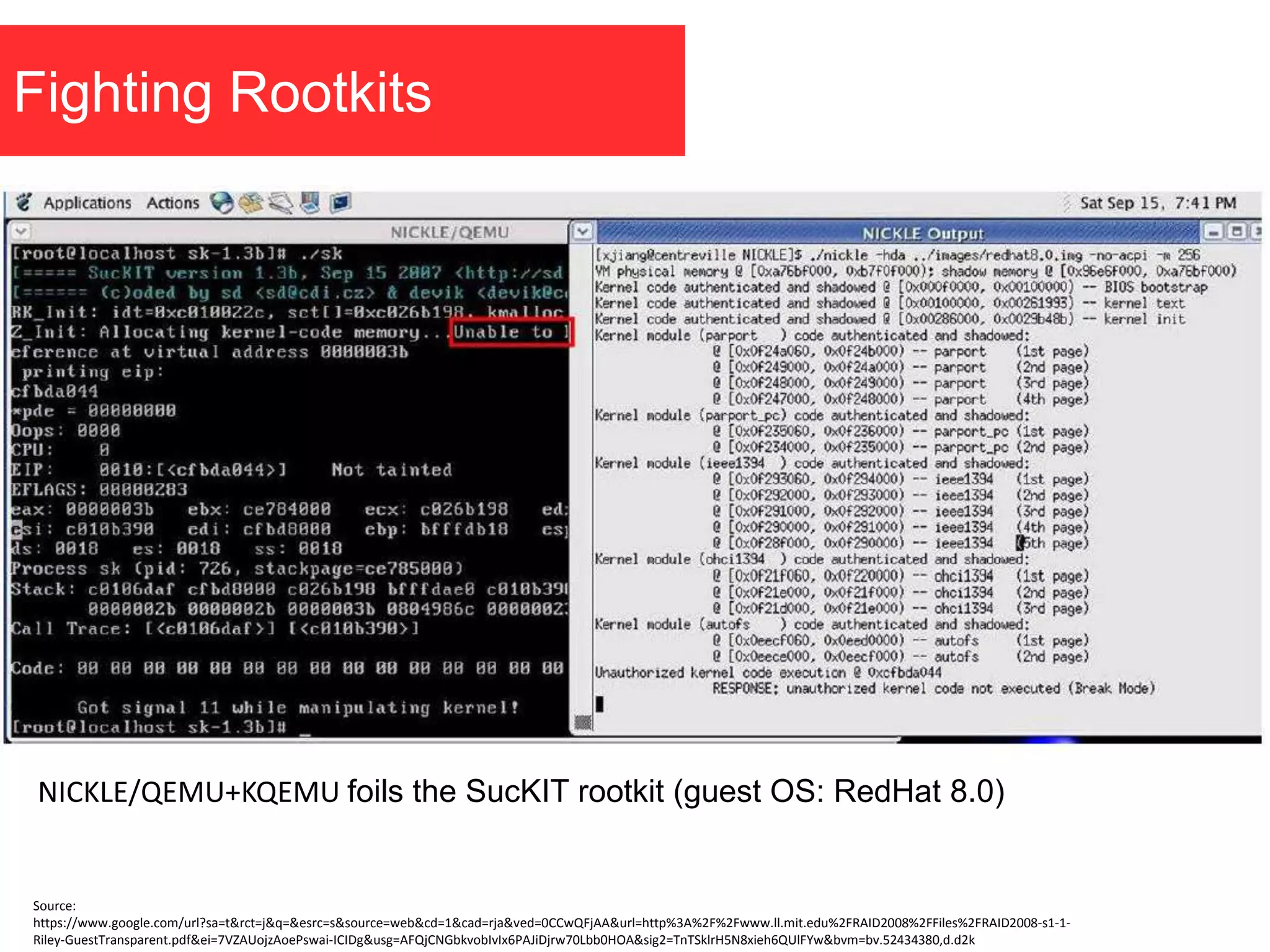
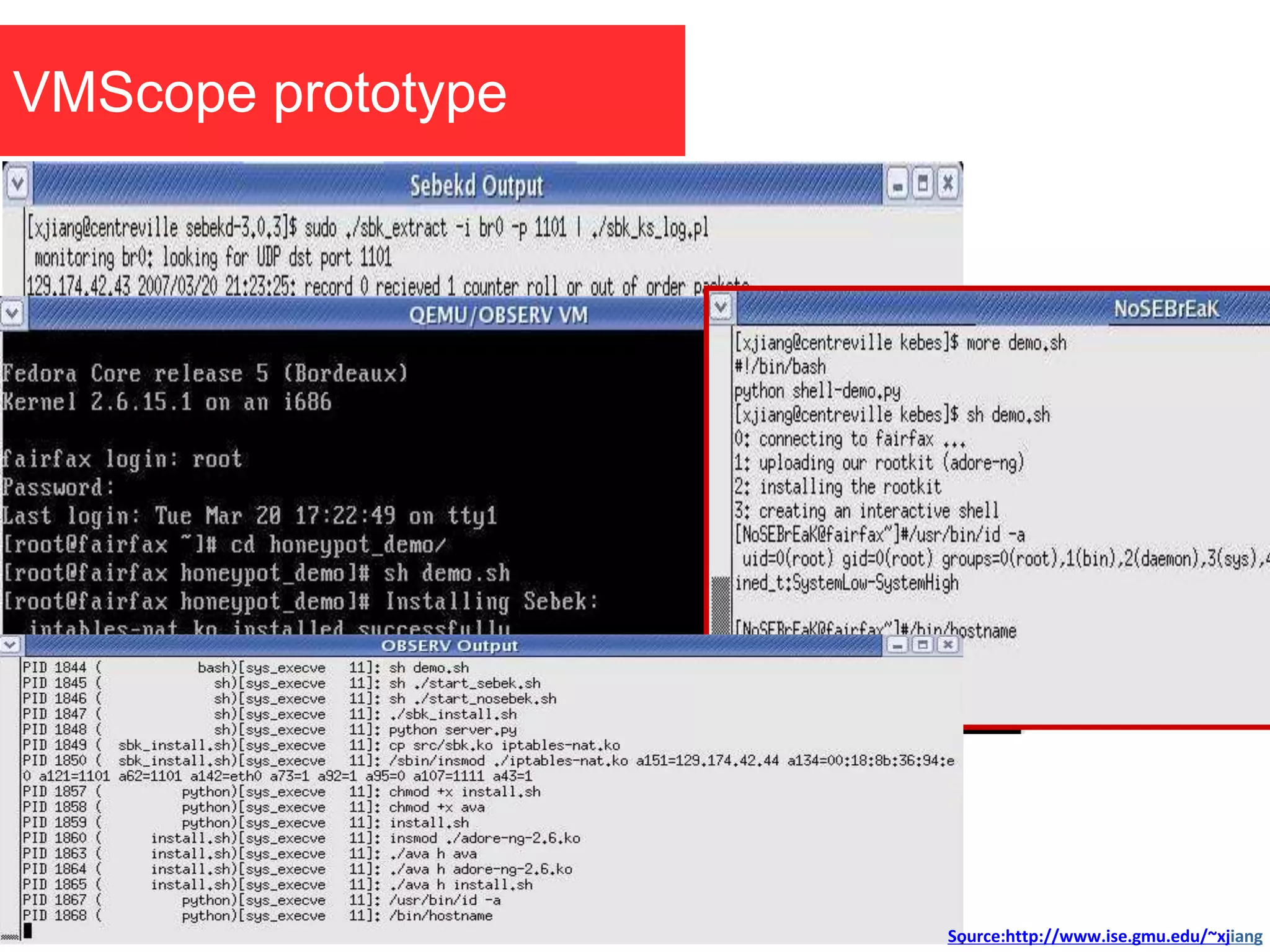
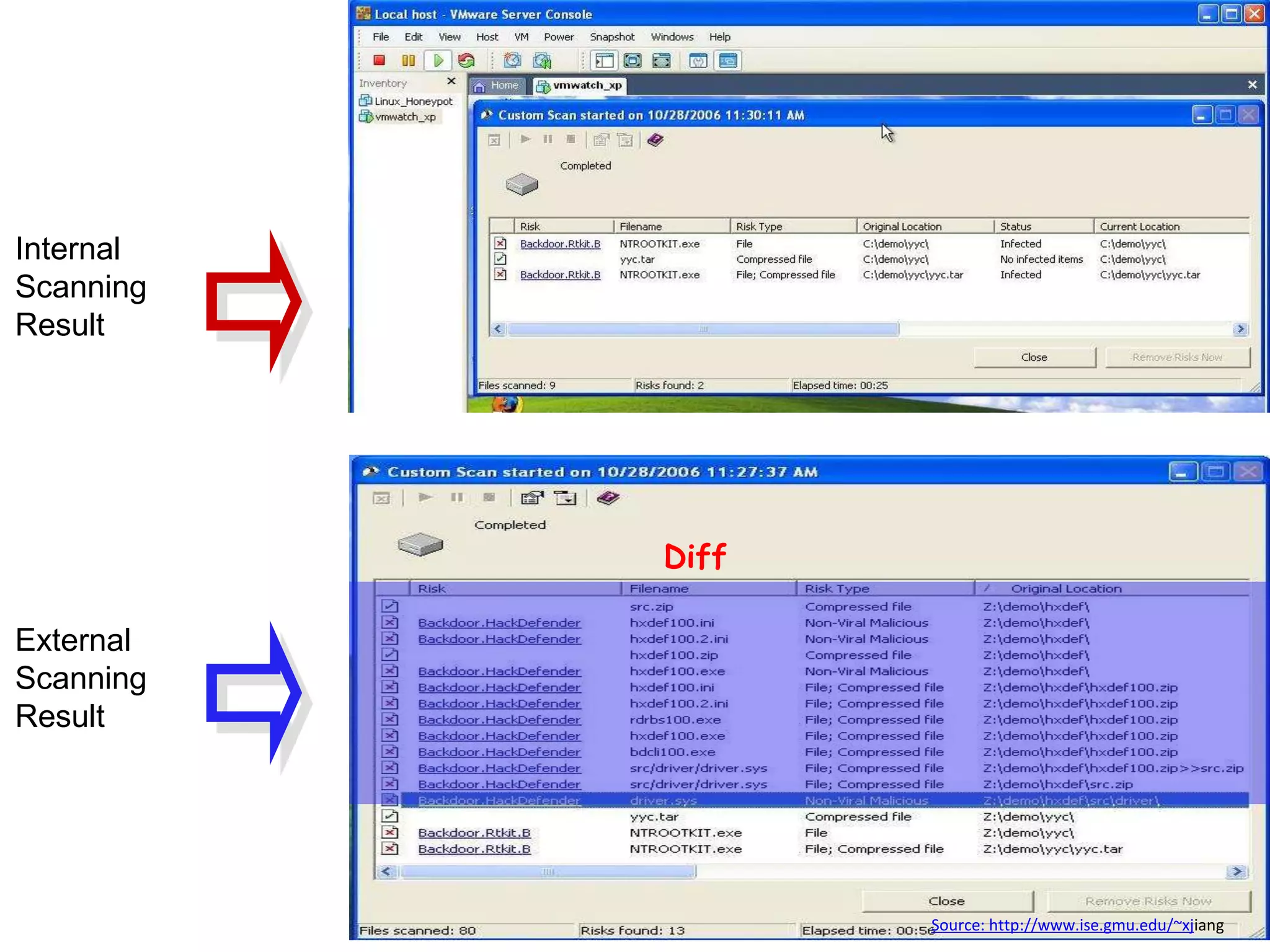
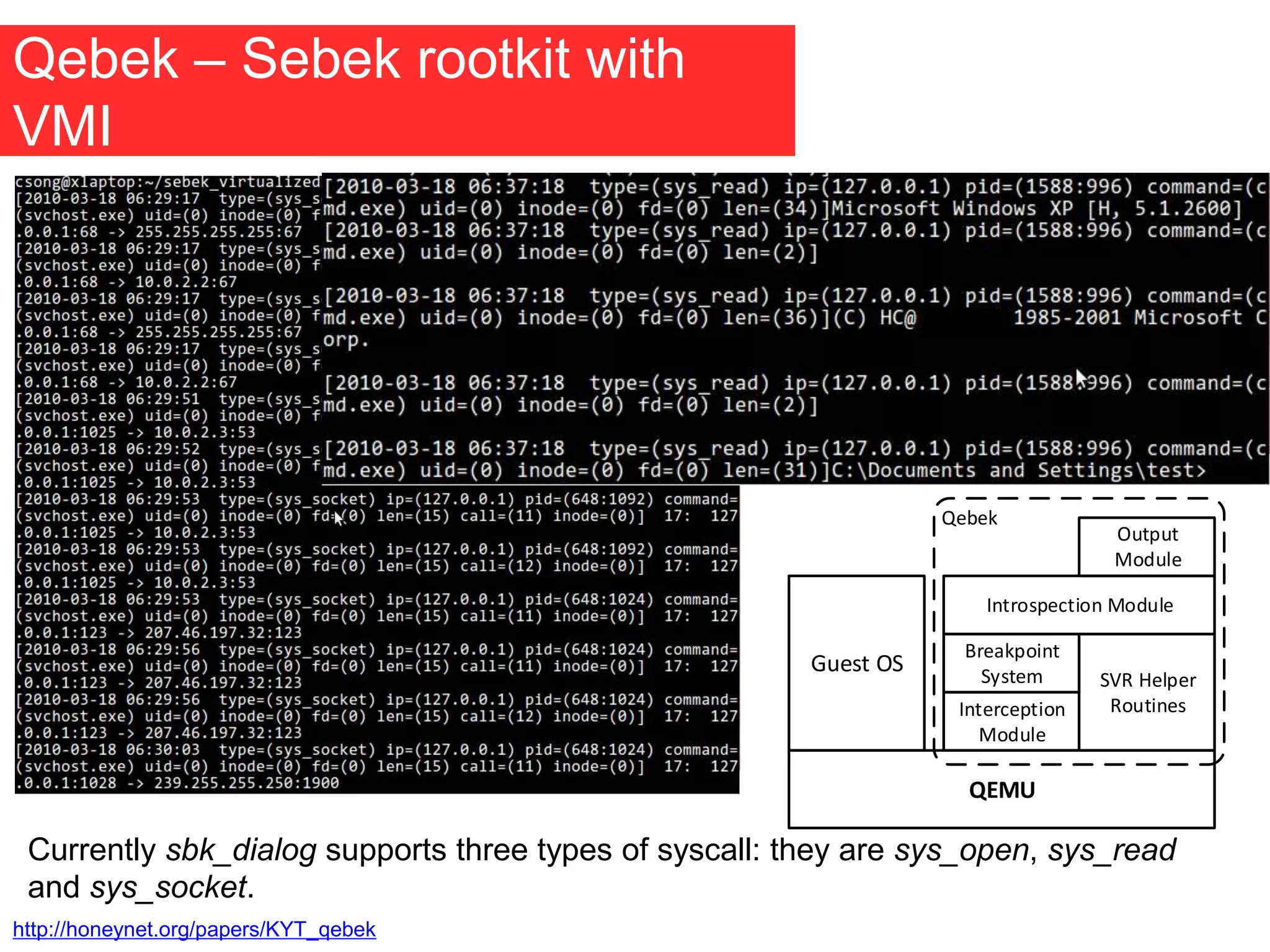
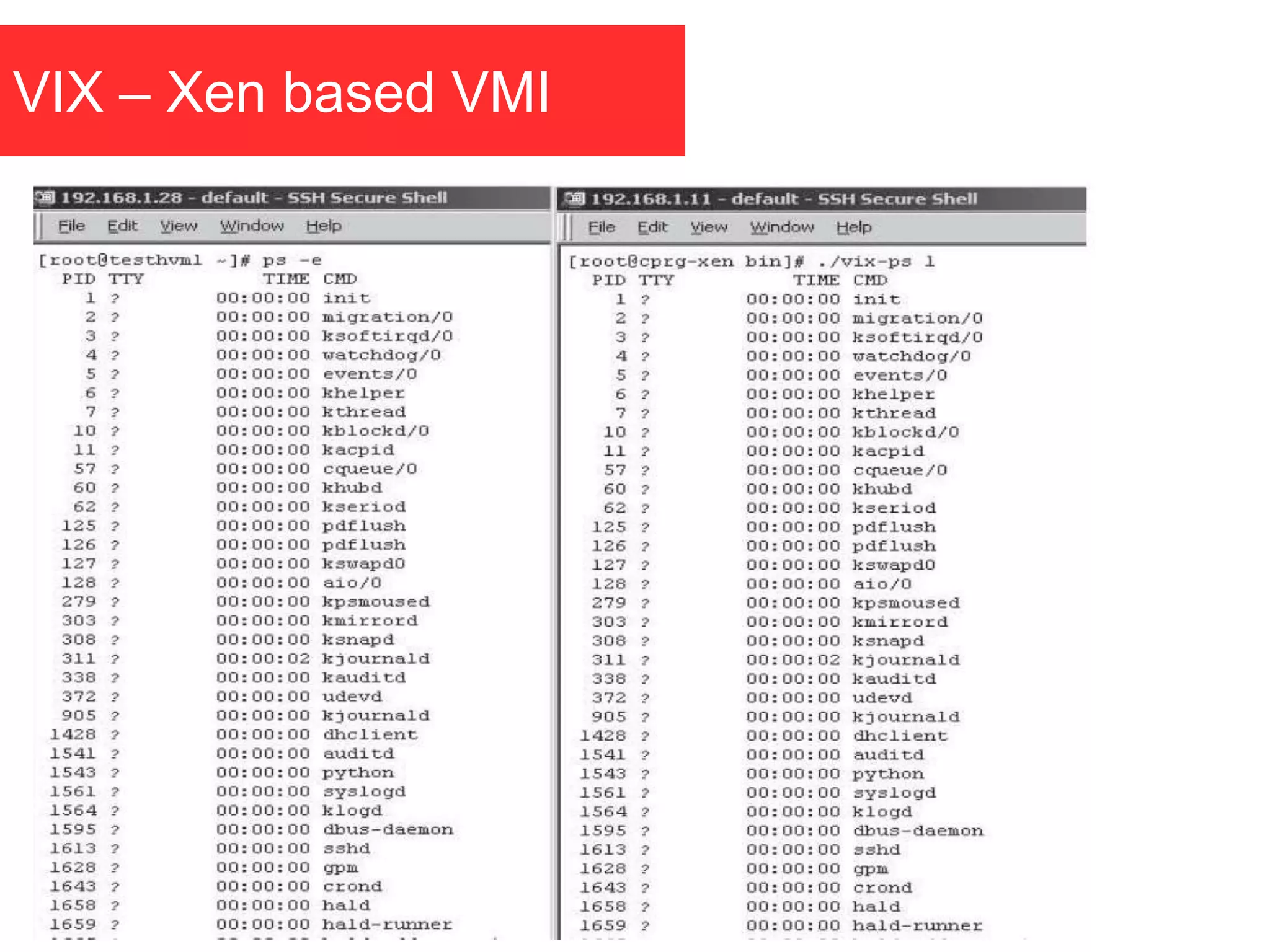
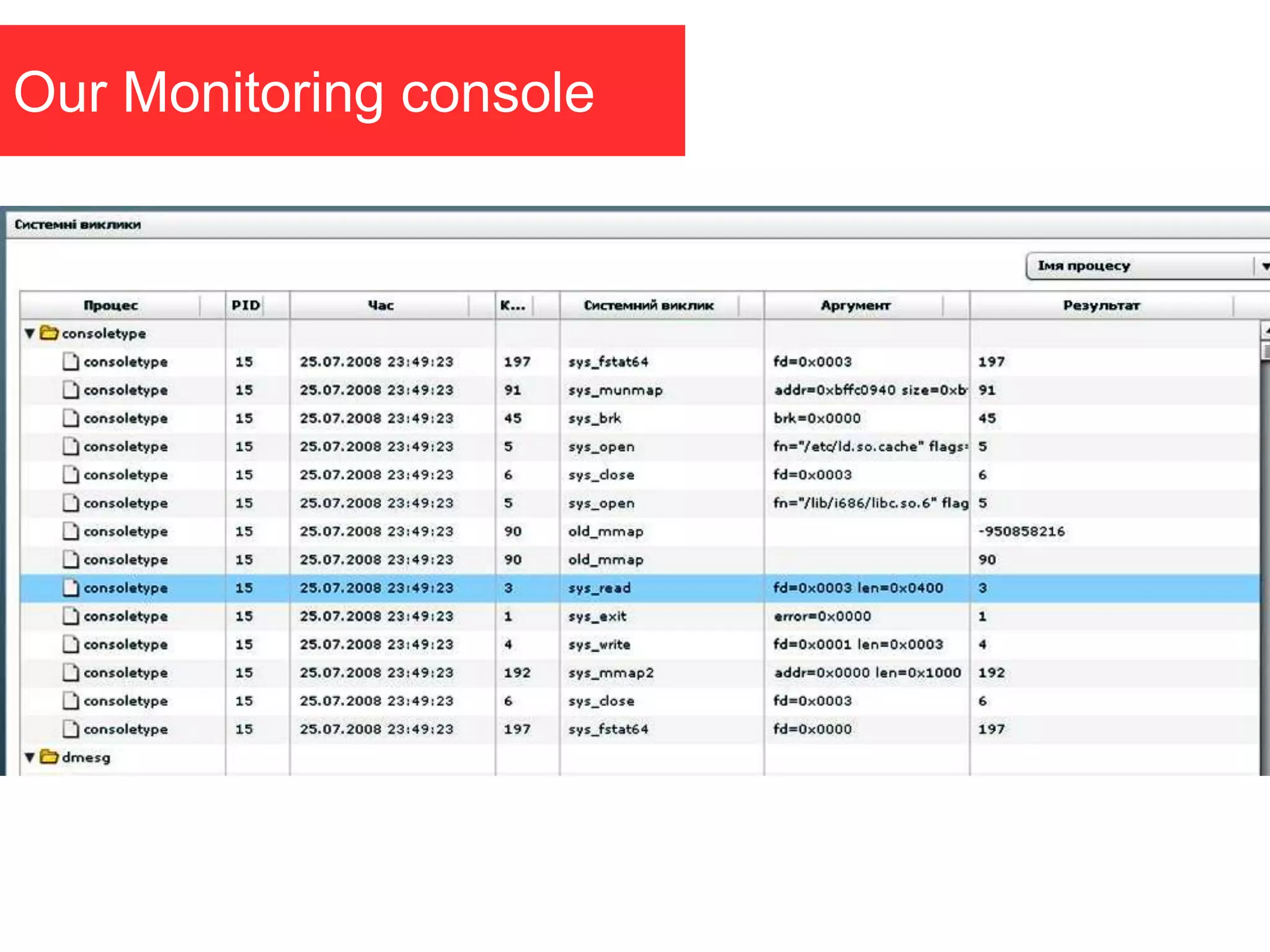
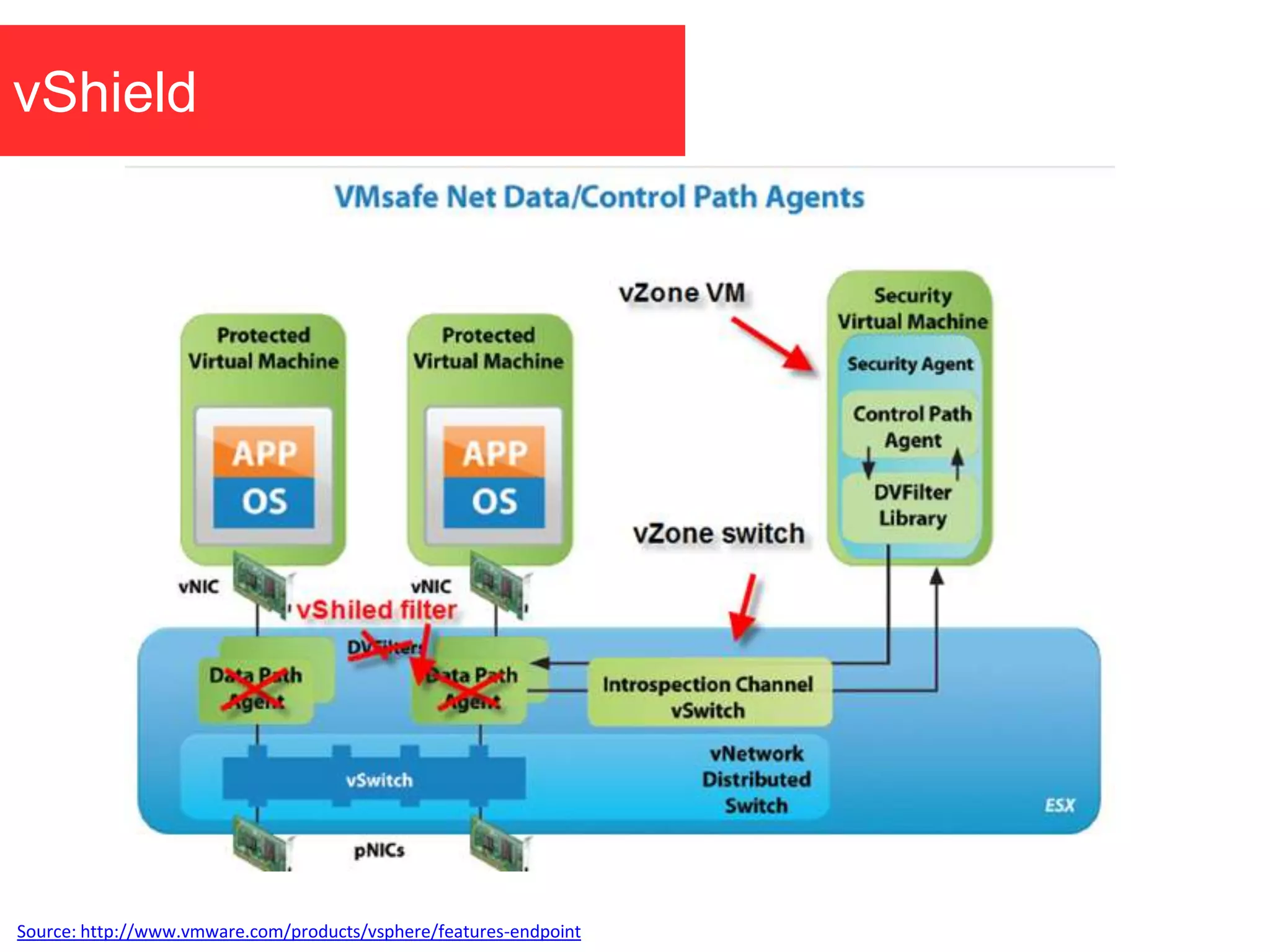
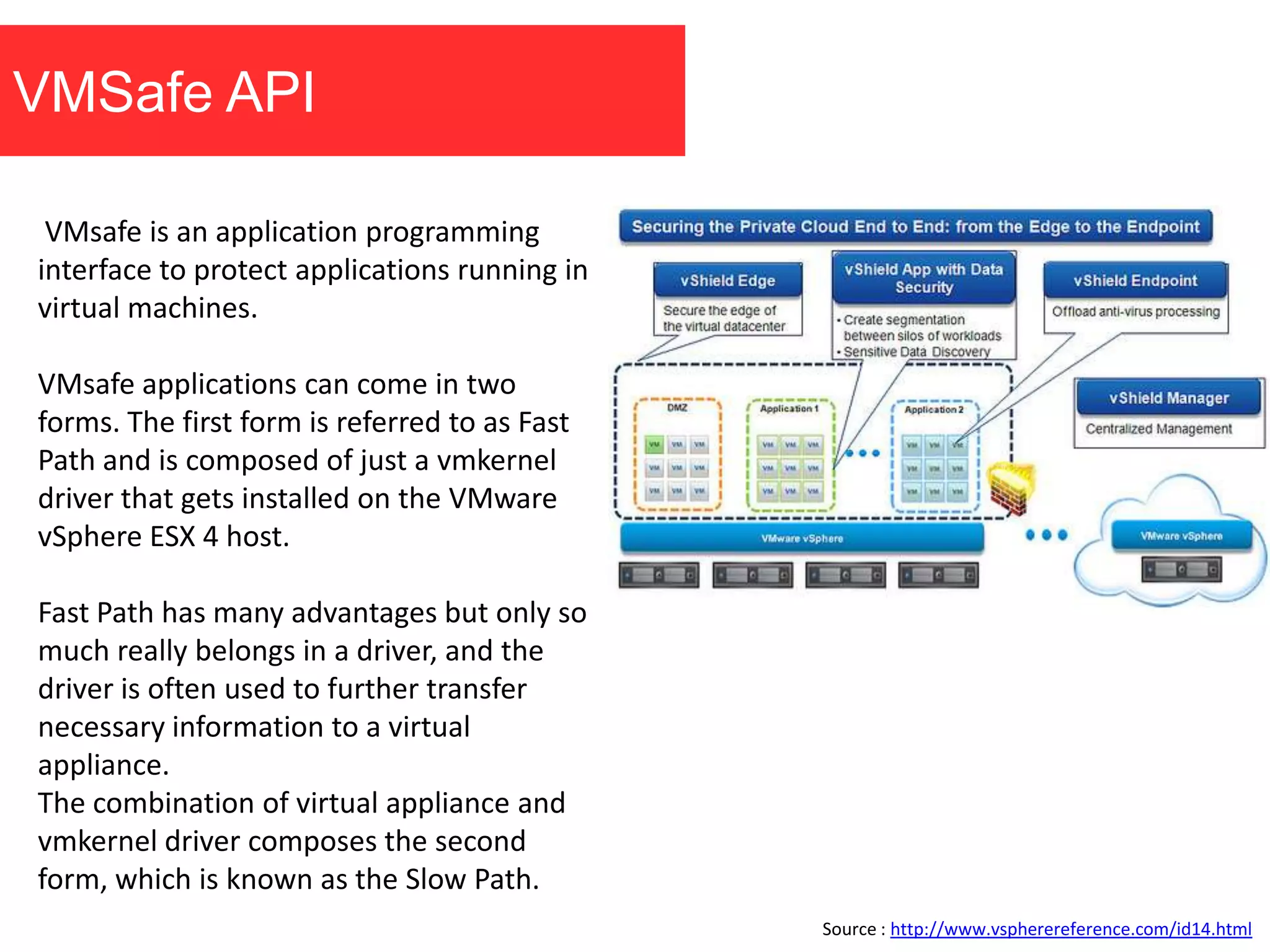
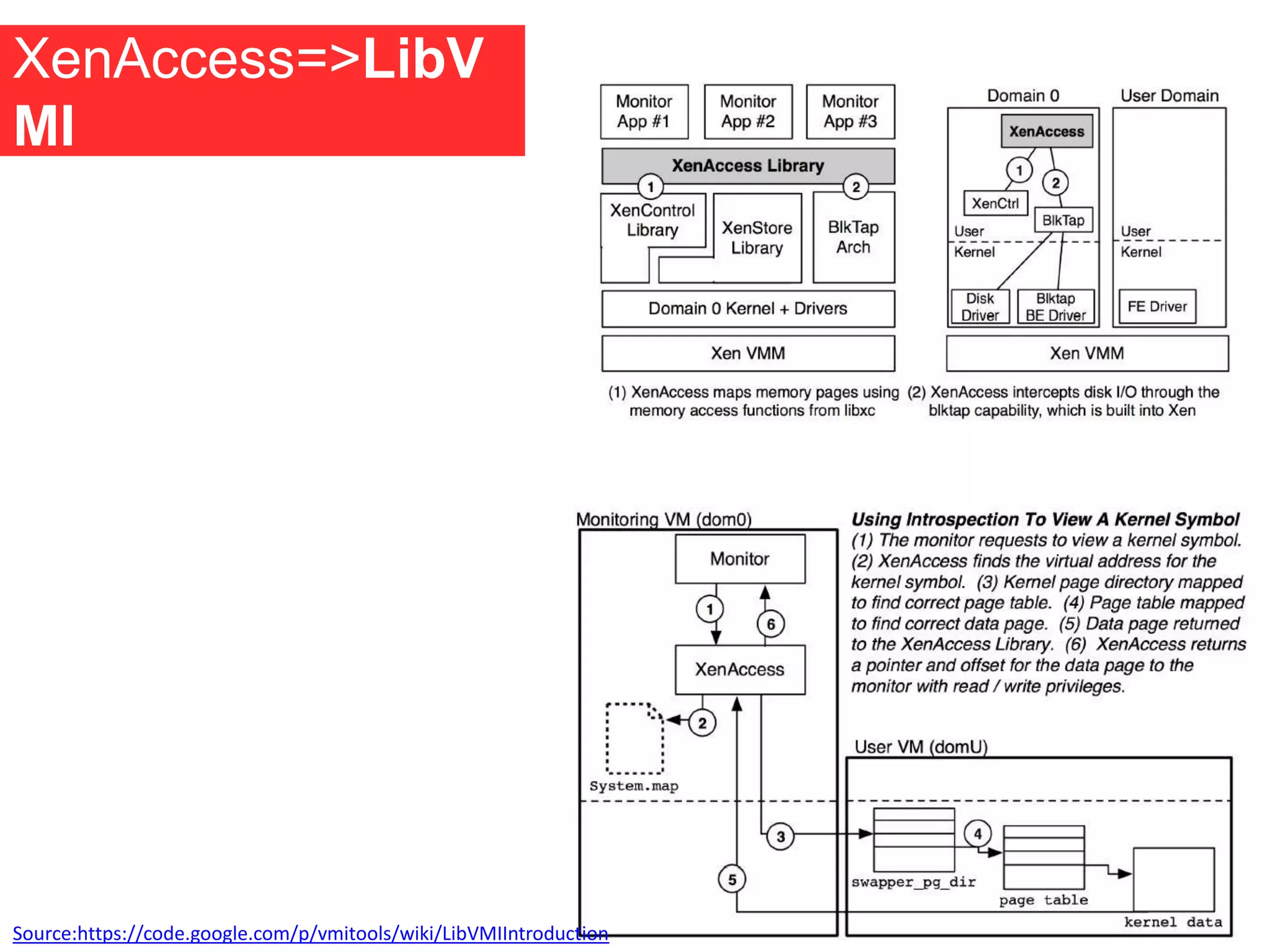
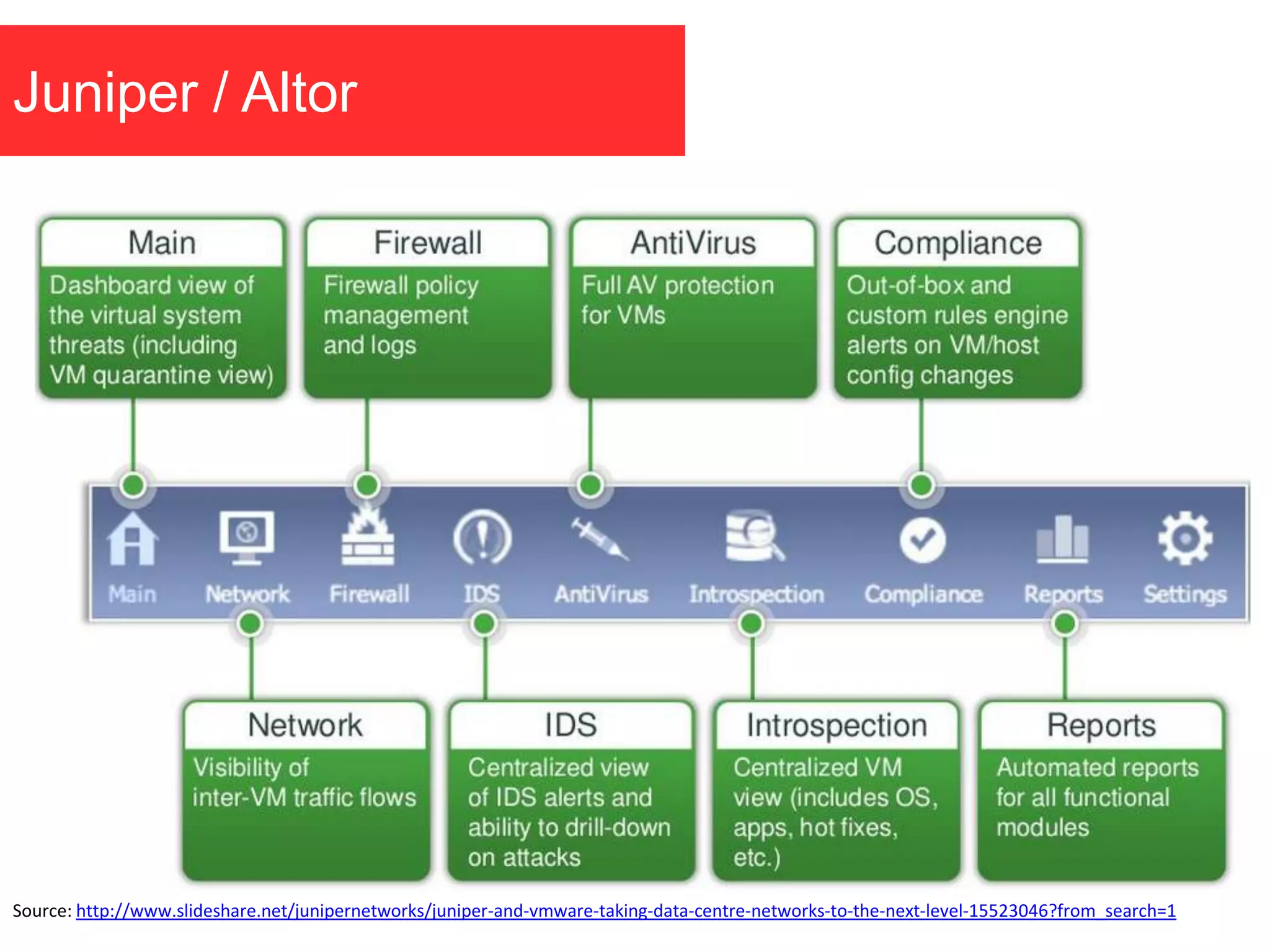
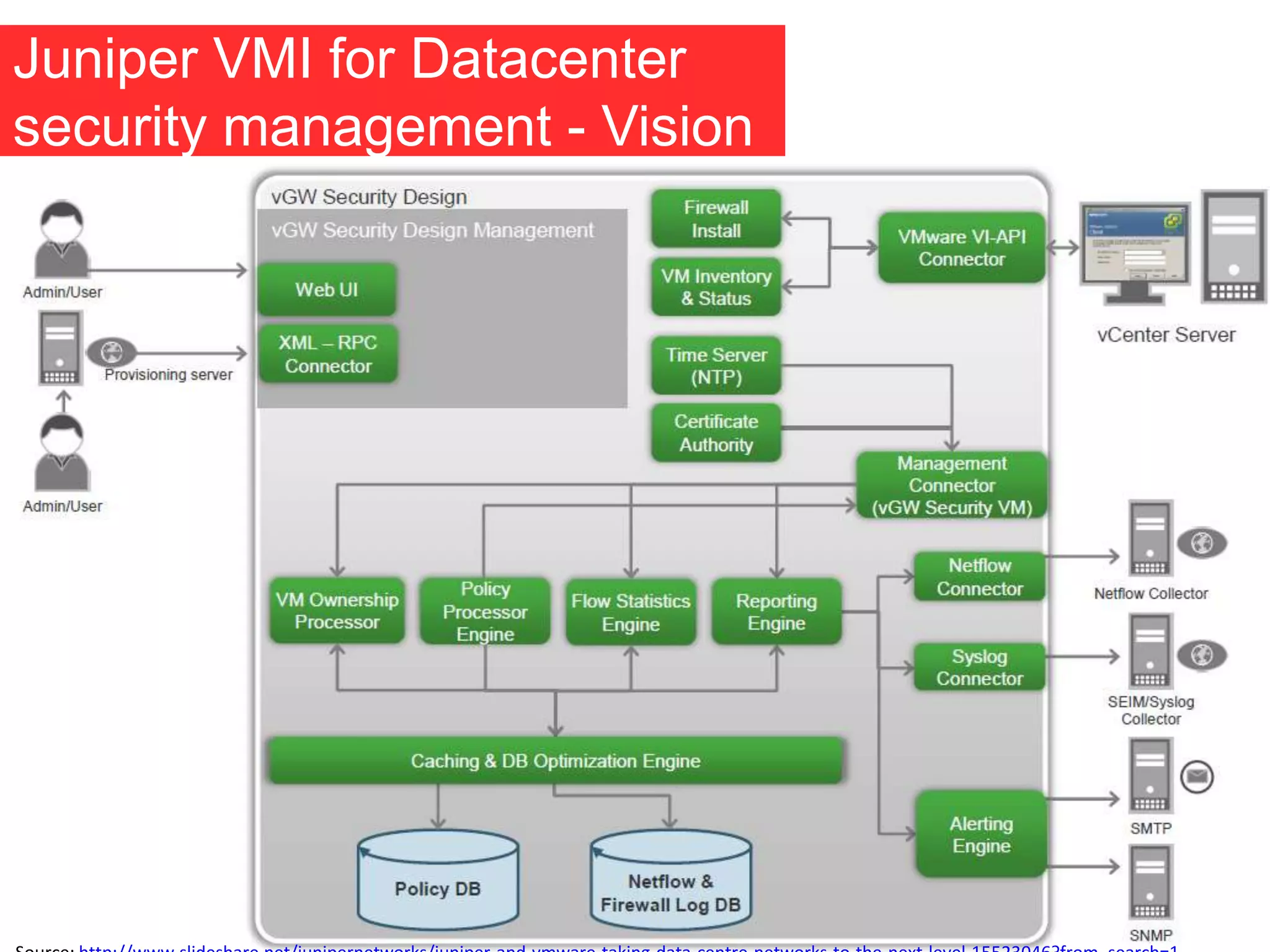
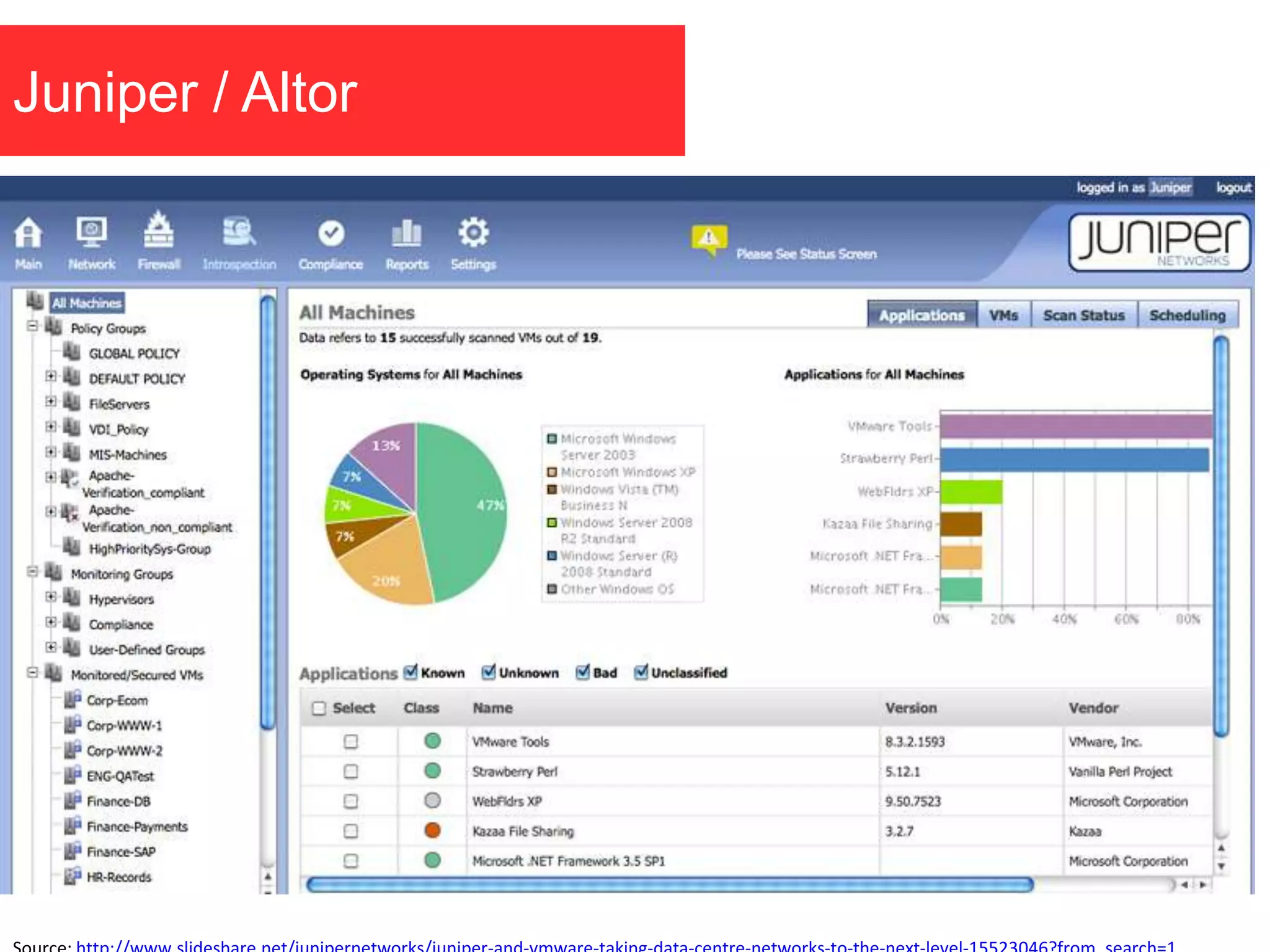
The document discusses the role of virtual machine introspection (VMI) in enhancing cloud security, focusing on its benefits, challenges, and technological evolution. VMI enables improved monitoring, malware detection, and security compliance for virtual environments by leveraging hypervisor capabilities to inspect virtual machine states. It also addresses the complexities of securing cloud architecture, including the need for transparency and the mitigation of specific threats like isolation breakouts and malware propagation.