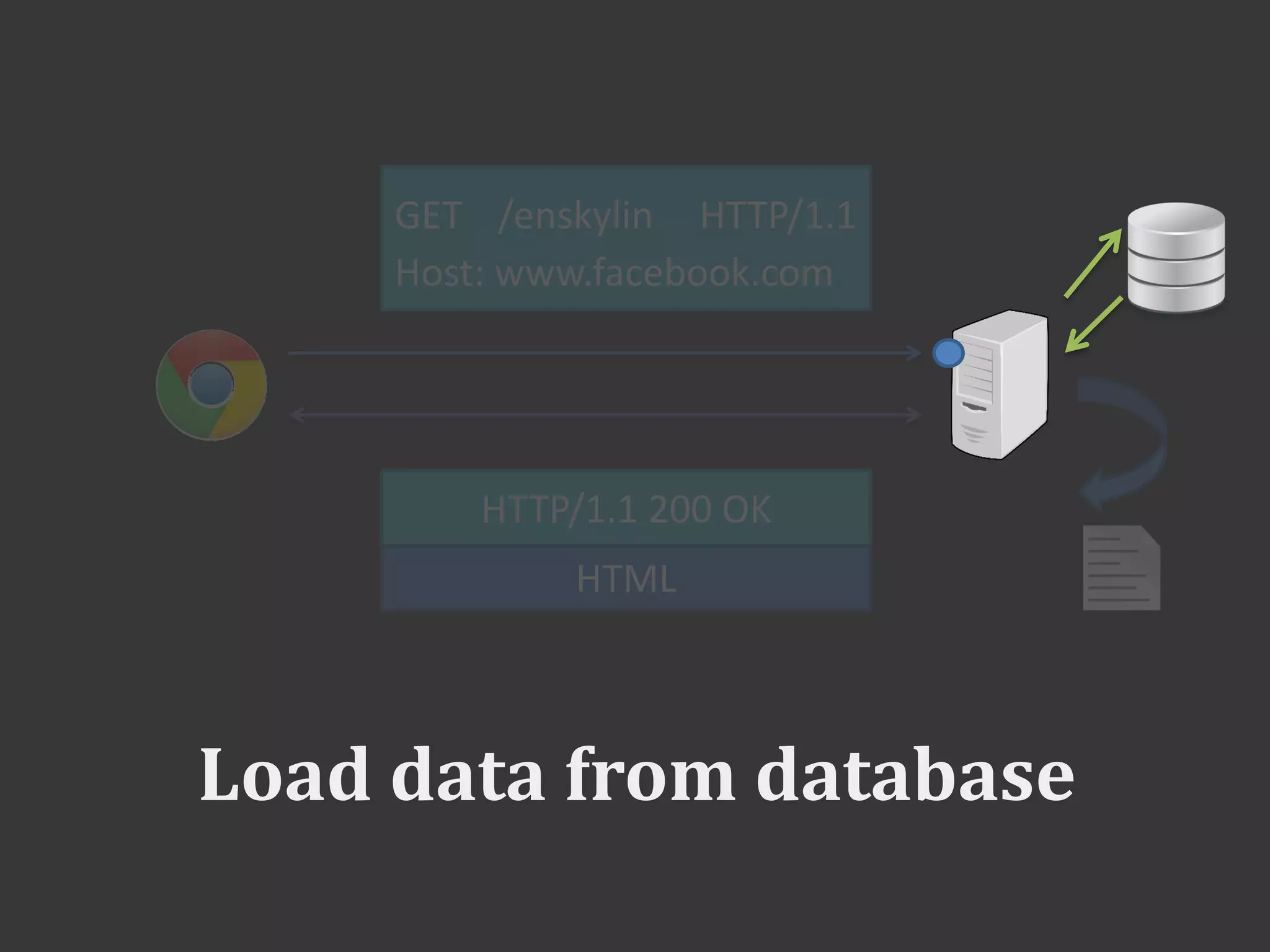
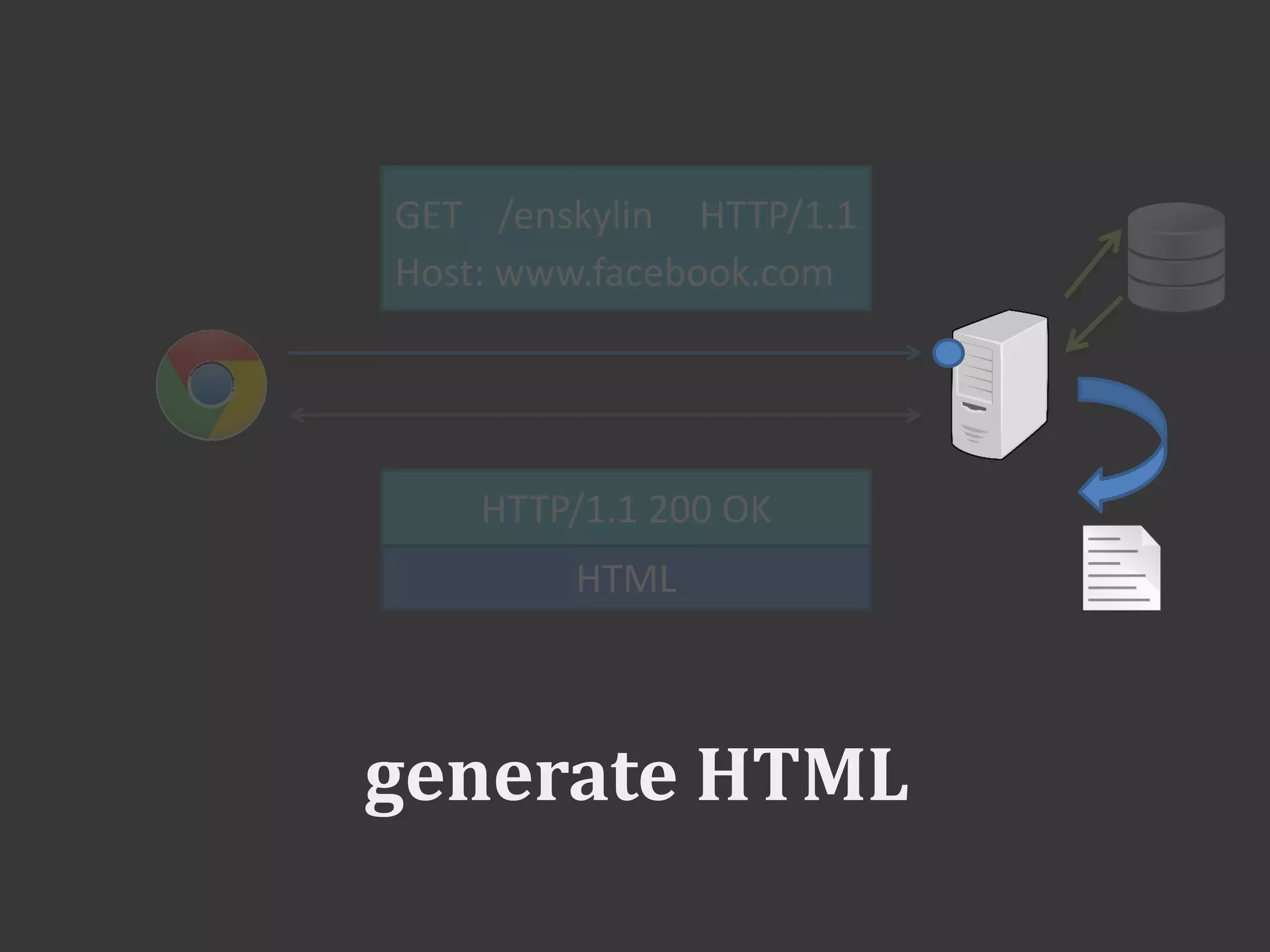
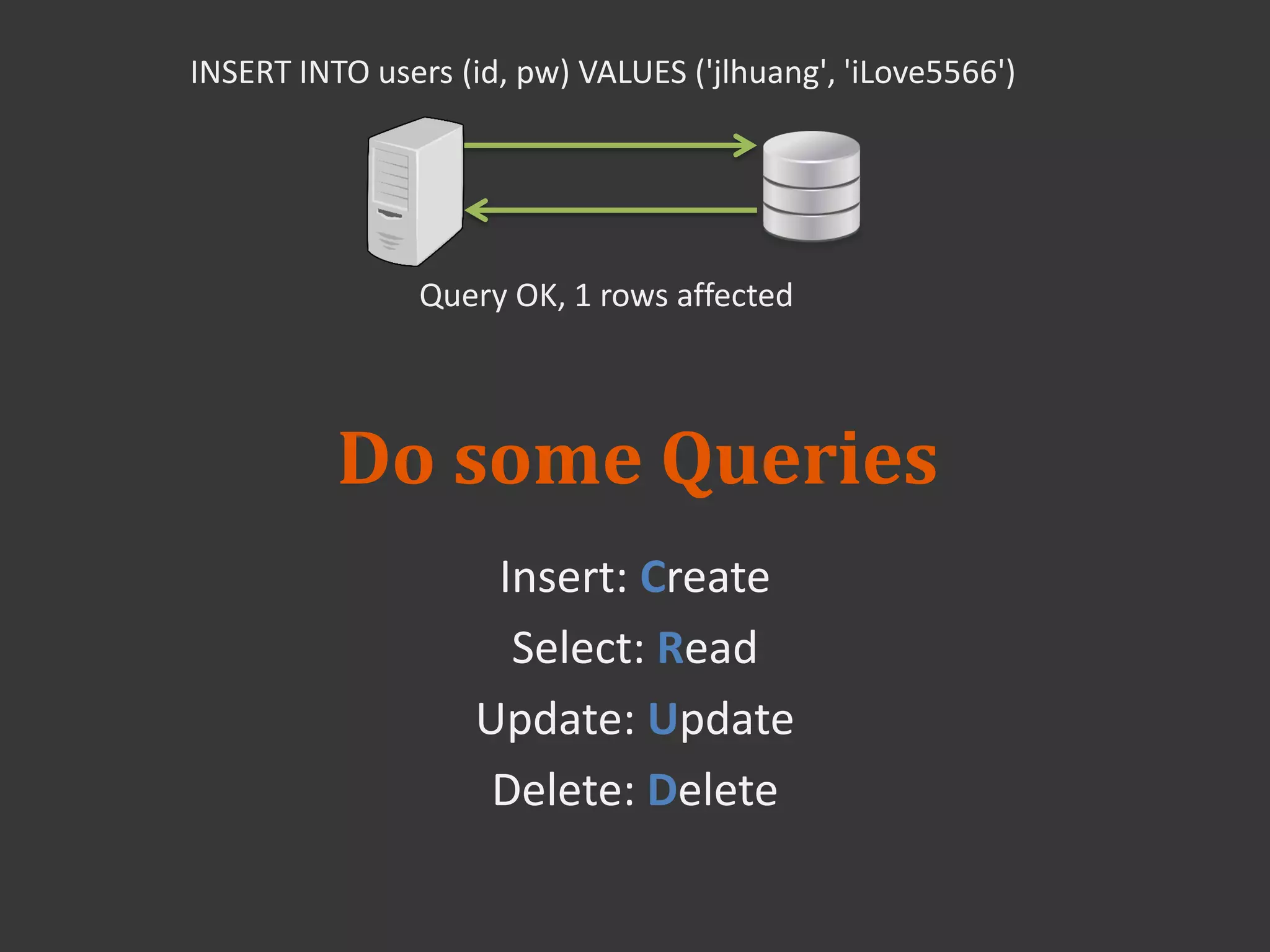
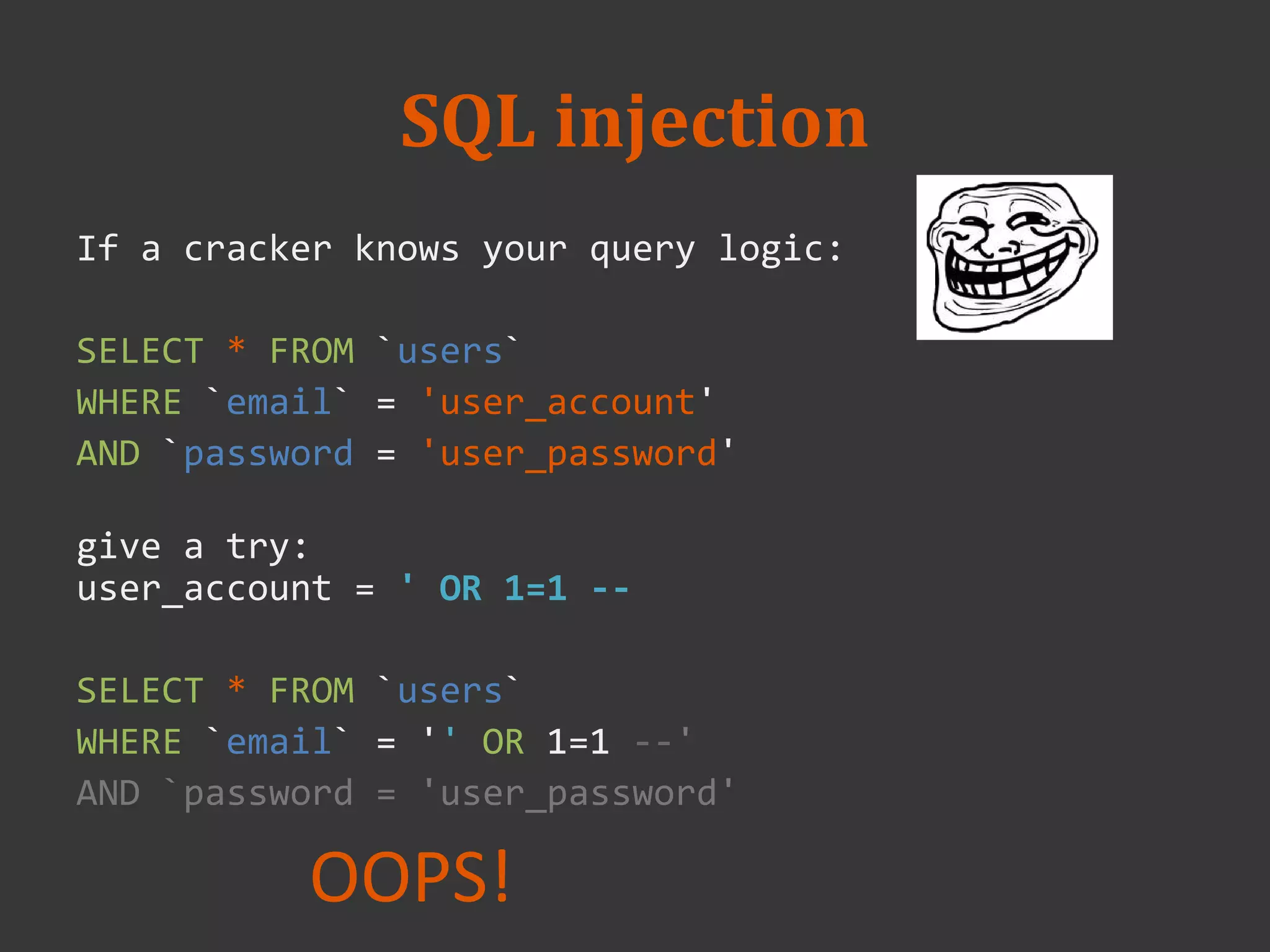
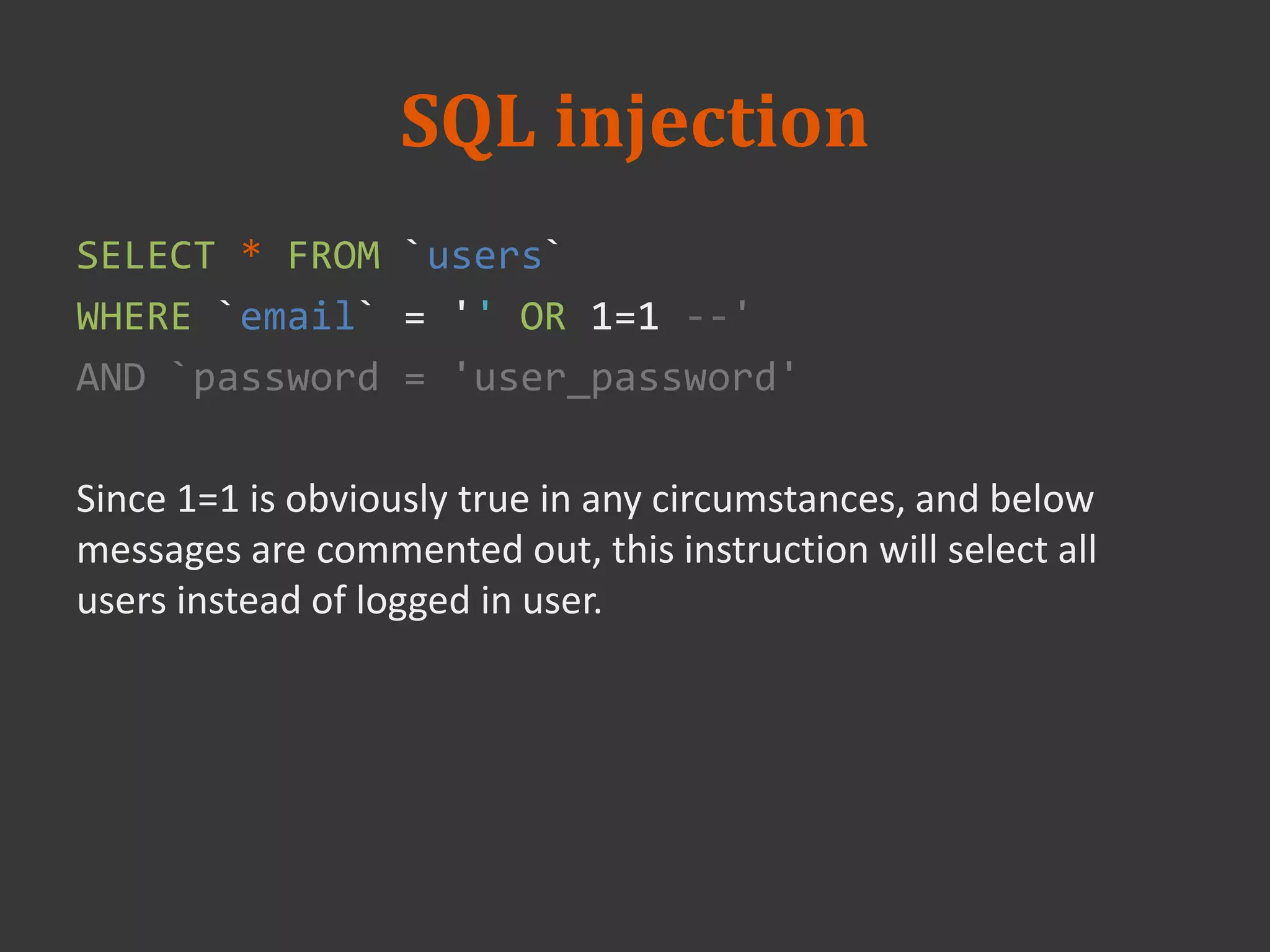
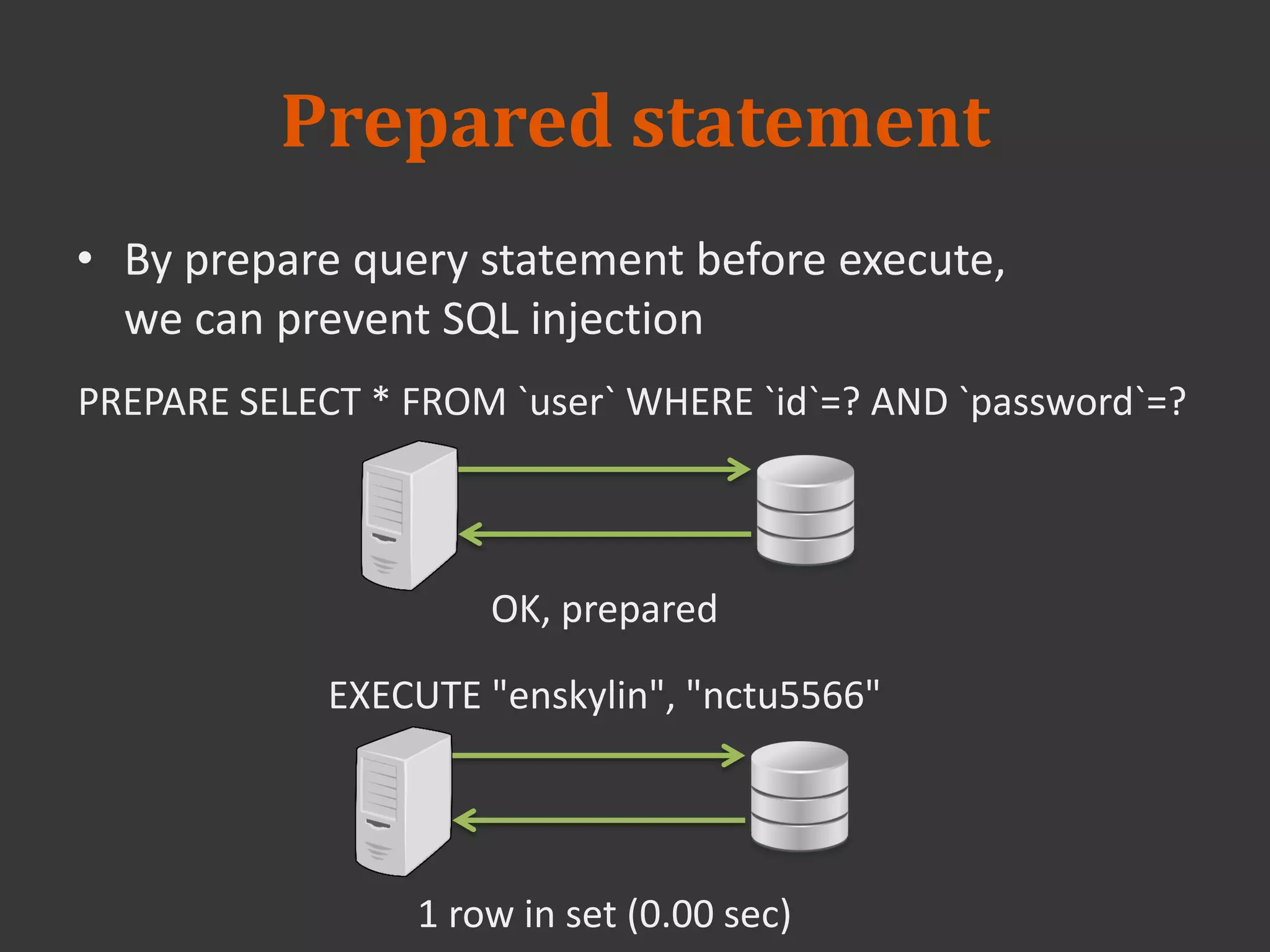
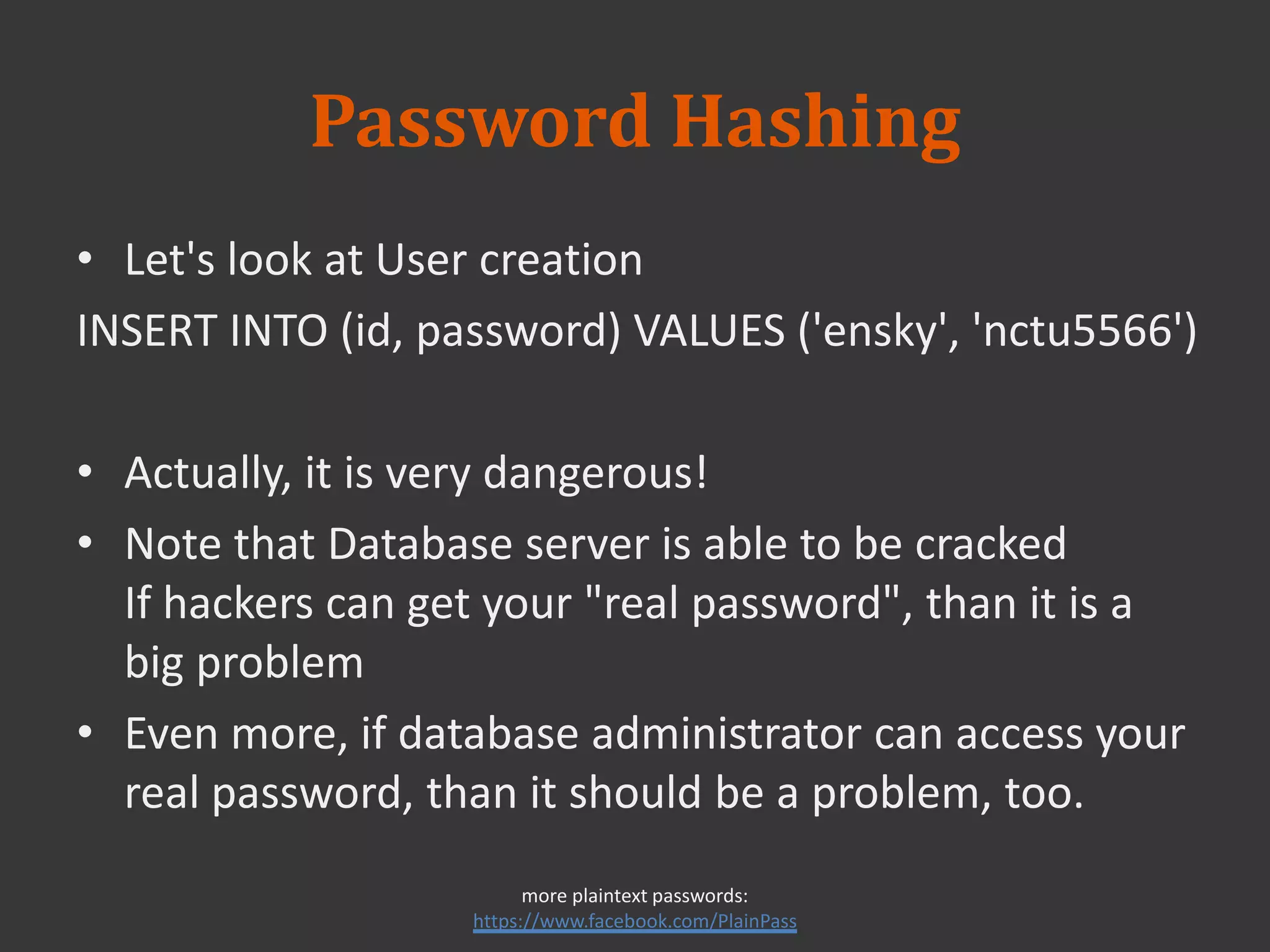
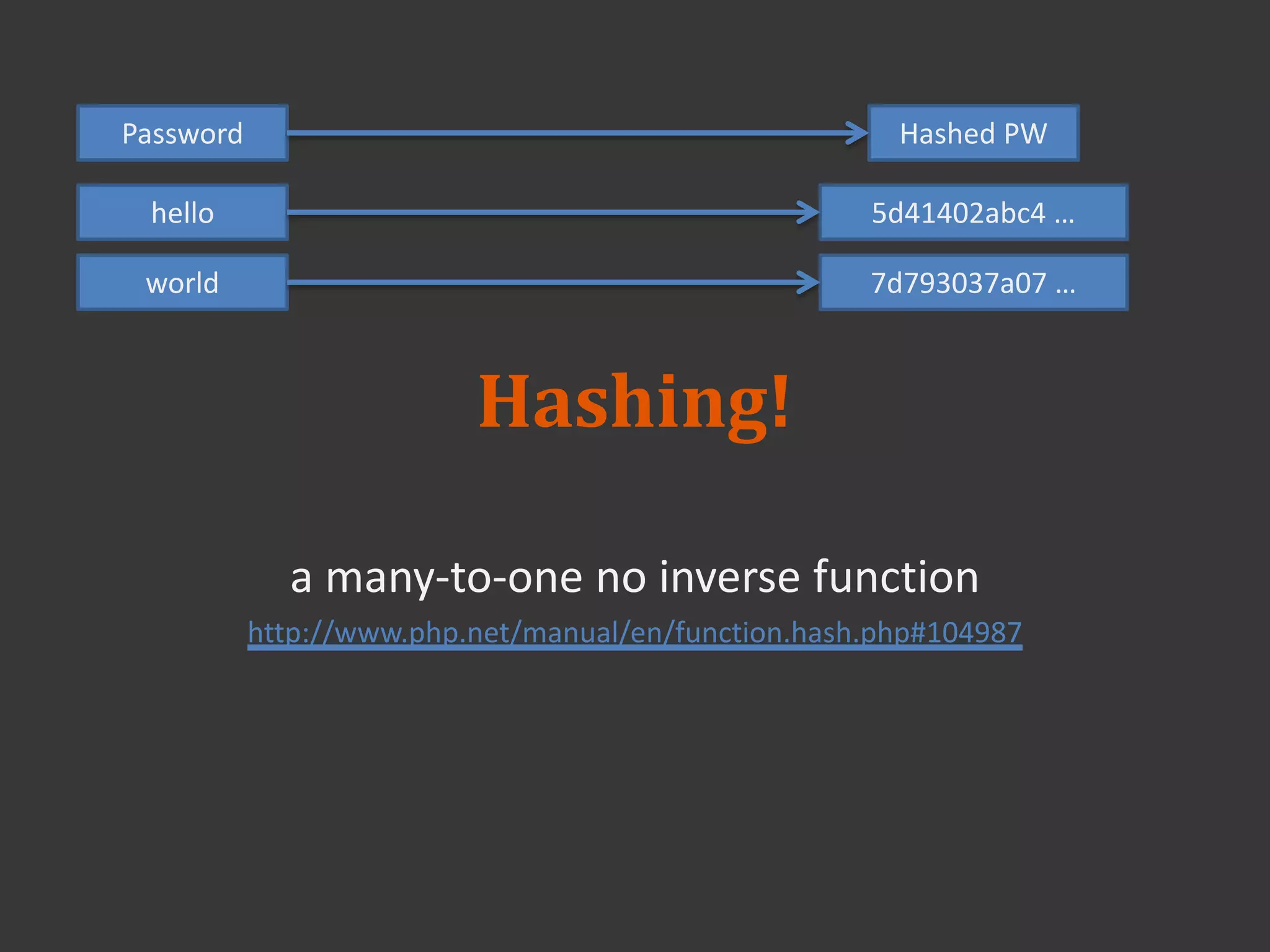
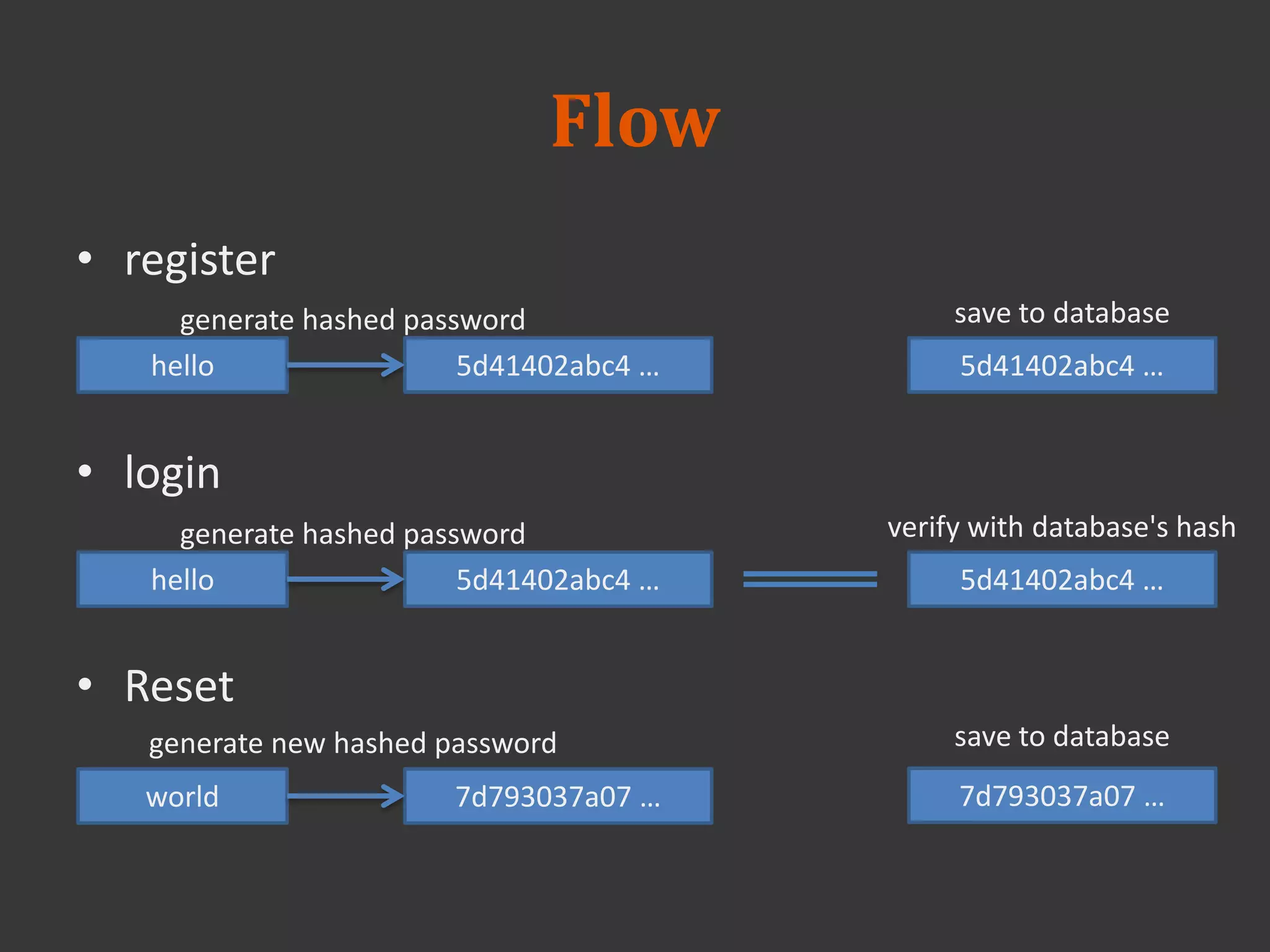
This document discusses connecting to a MySQL database from PHP. It explains how to establish a database connection, perform queries like INSERT, SELECT, UPDATE and DELETE, and handle query results. It emphasizes that using prepared statements prevents SQL injection attacks. It also covers password hashing to securely store passwords in the database by hashing them with a random salt.





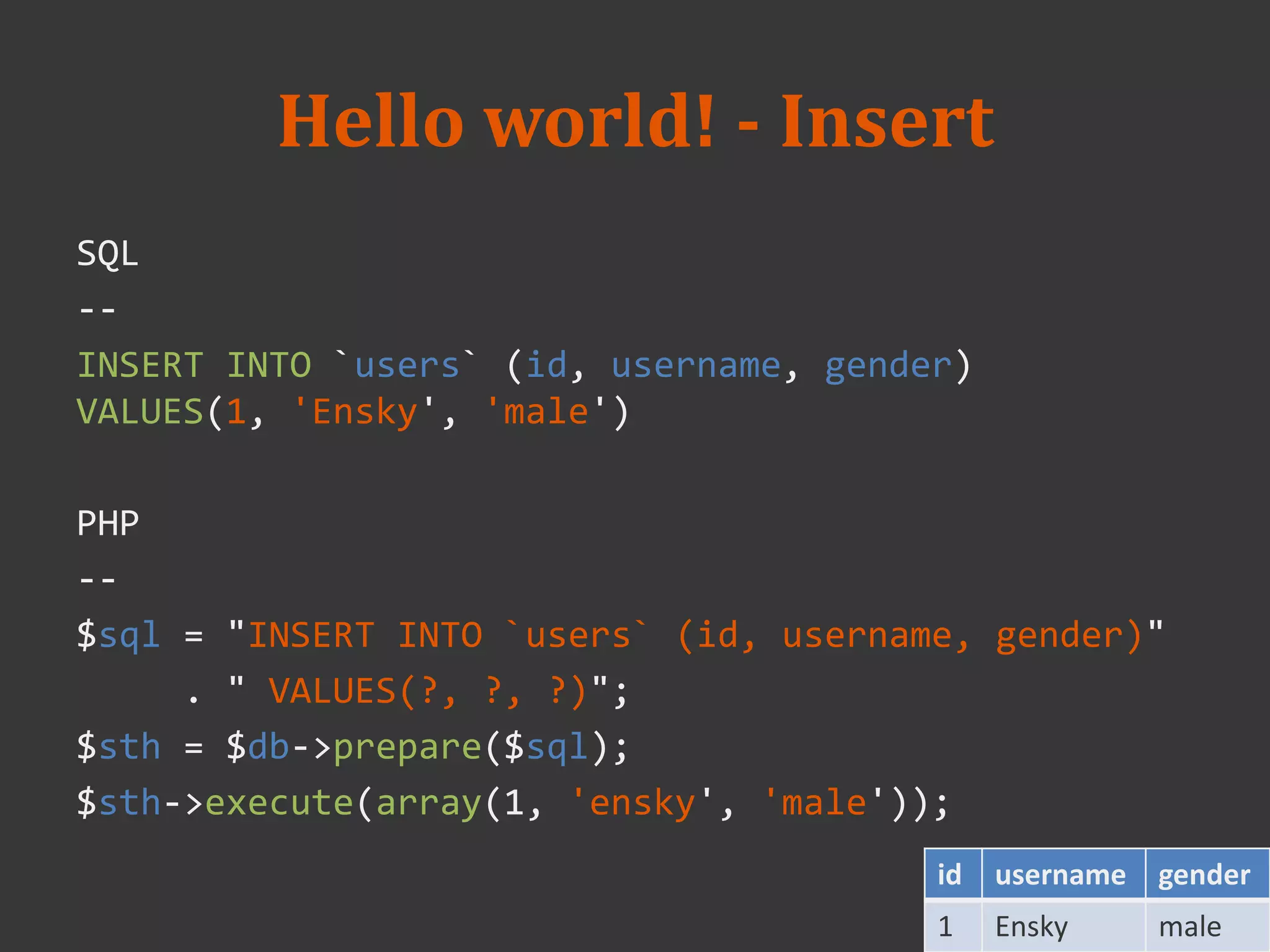

![PHP Data Objects
• PDO is an OO style class
• Classes
– PDO
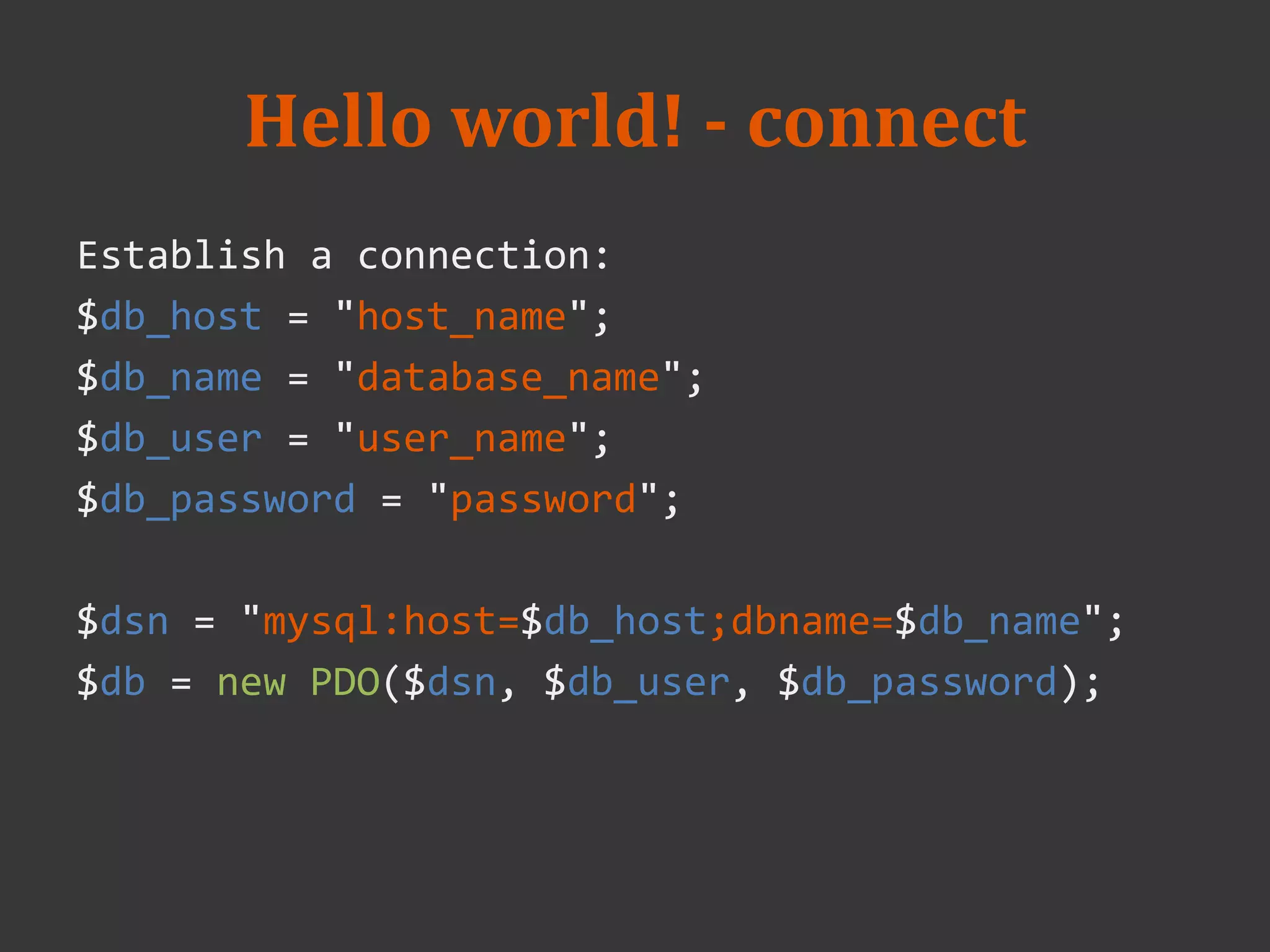
• PDO __construct ( string $dsn, [, string $username [, string
$password ]])
• PDOStatement prepare( string $statement )
• PDOStatement query( string $statement )
– PDOStatement
• bool execute ([ array $input_parameters ] )
• mixed fetchObject ([ string $class_name = "stdClass" [, array
$ctor_args ]] )](https://image.slidesharecdn.com/week3-20-20php-20-20mysql-140312024517-phpapp02/75/2014-database-course-3-PHP-and-MySQL-14-2048.jpg)



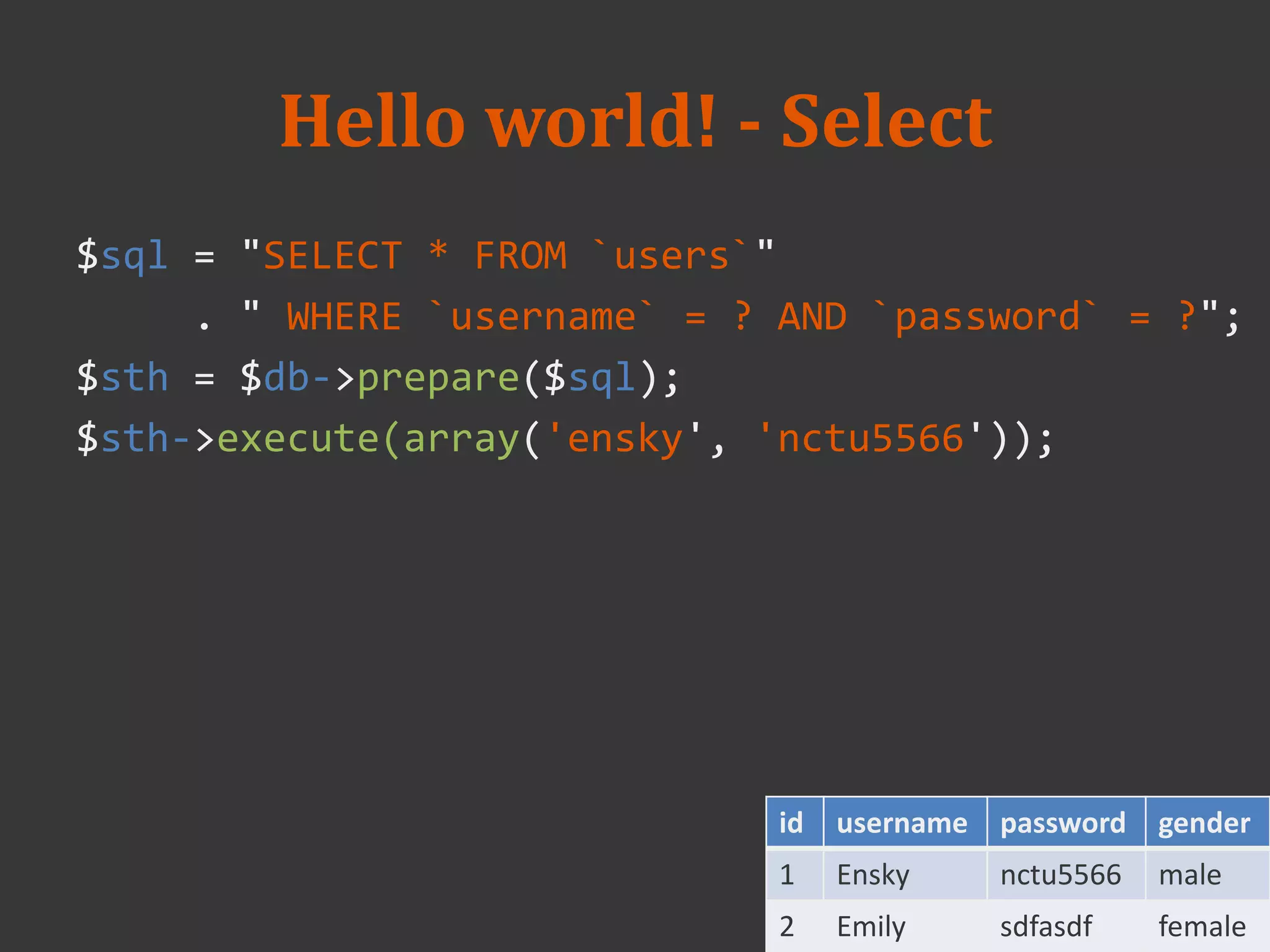
![Simple query(use mysql ext)
login_action.php
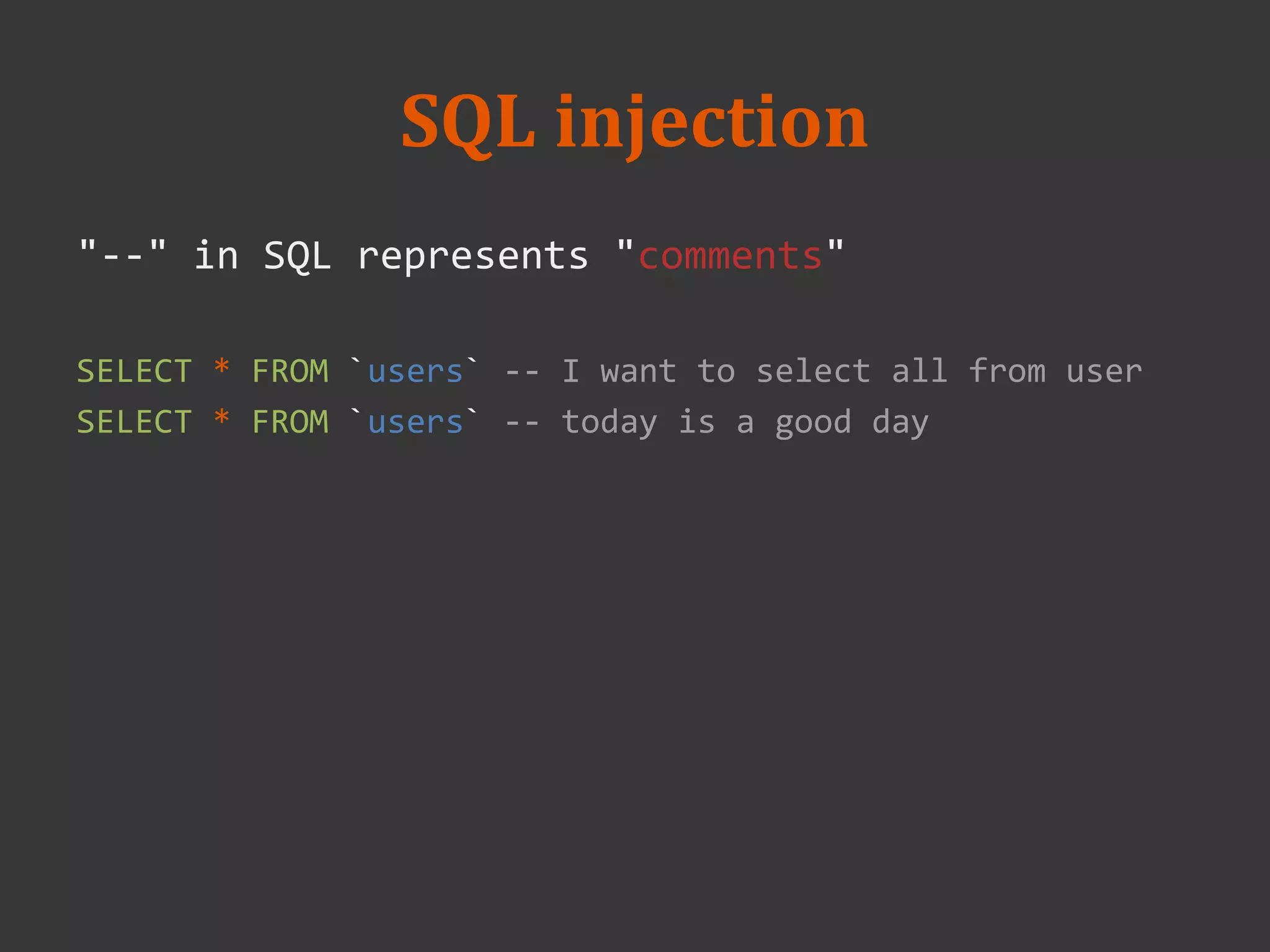
--
<?php
mysql_connect($db_host, $db_user, $db_password);
mysql_select_db($dn_name);
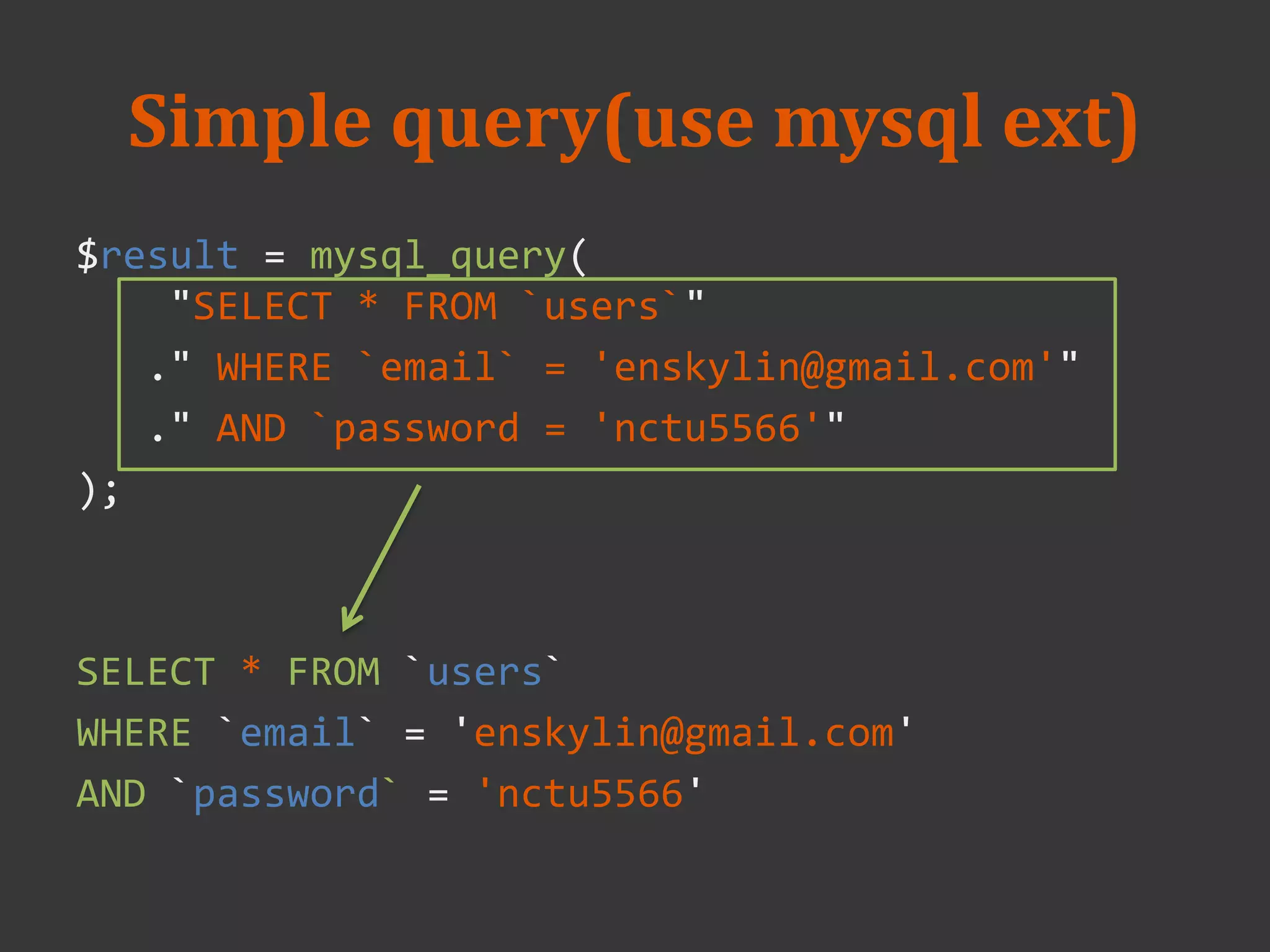
$result = mysql_query(
"SELECT * FROM `users`"
." WHERE `email` = '{$_POST['email']}'"
." AND `password = '{$_POST['password']}'"
);
// …](https://image.slidesharecdn.com/week3-20-20php-20-20mysql-140312024517-phpapp02/75/2014-database-course-3-PHP-and-MySQL-18-2048.jpg)
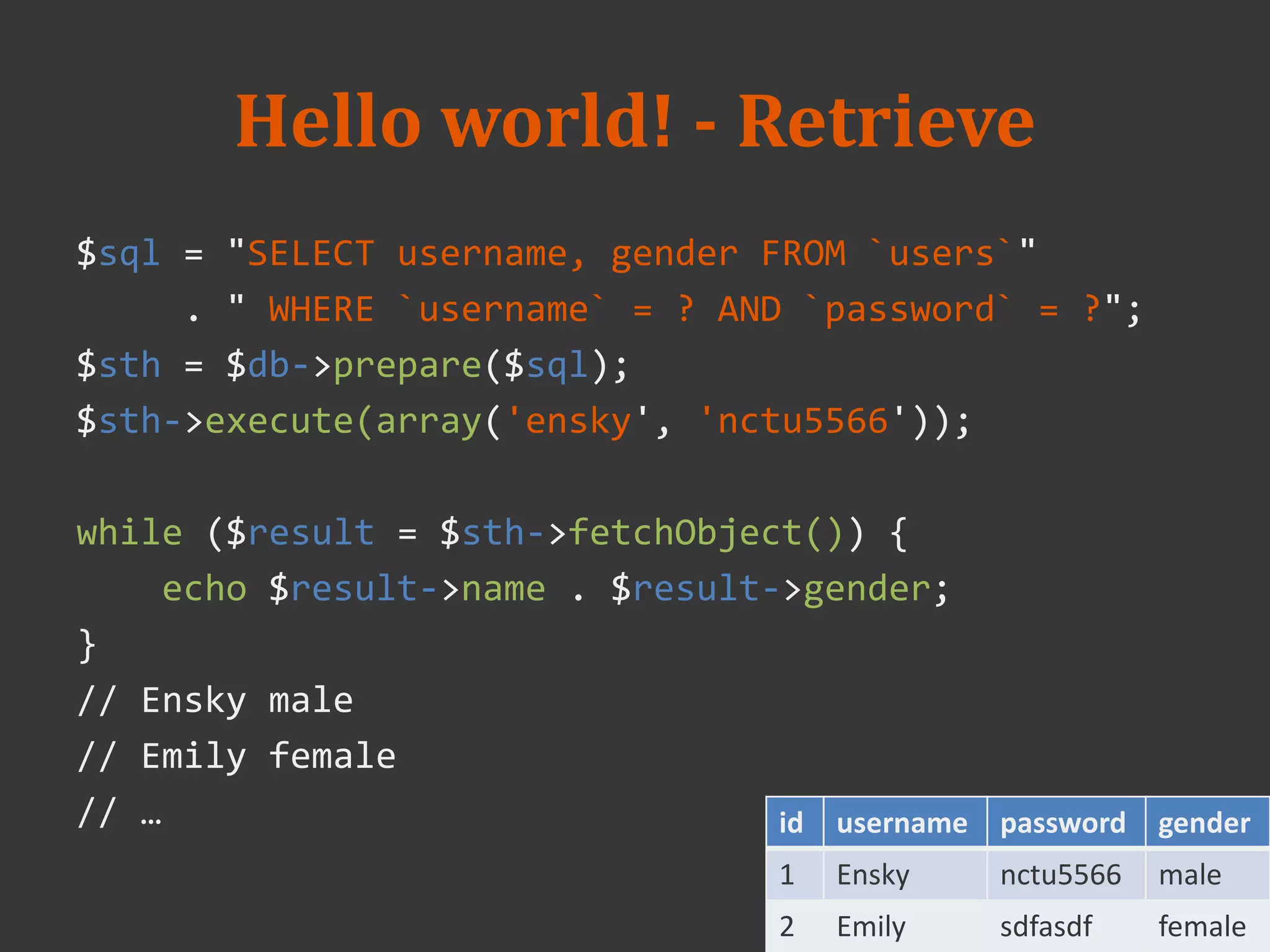
![Simple query(use mysql ext)
login_form.php
login_action.php
--
$result = mysql_query(
"SELECT * FROM `users`"
." WHERE `email` = '{$_POST['email']}'"
." AND `password = '{$_POST['password']}'"
);](https://image.slidesharecdn.com/week3-20-20php-20-20mysql-140312024517-phpapp02/75/2014-database-course-3-PHP-and-MySQL-19-2048.jpg)
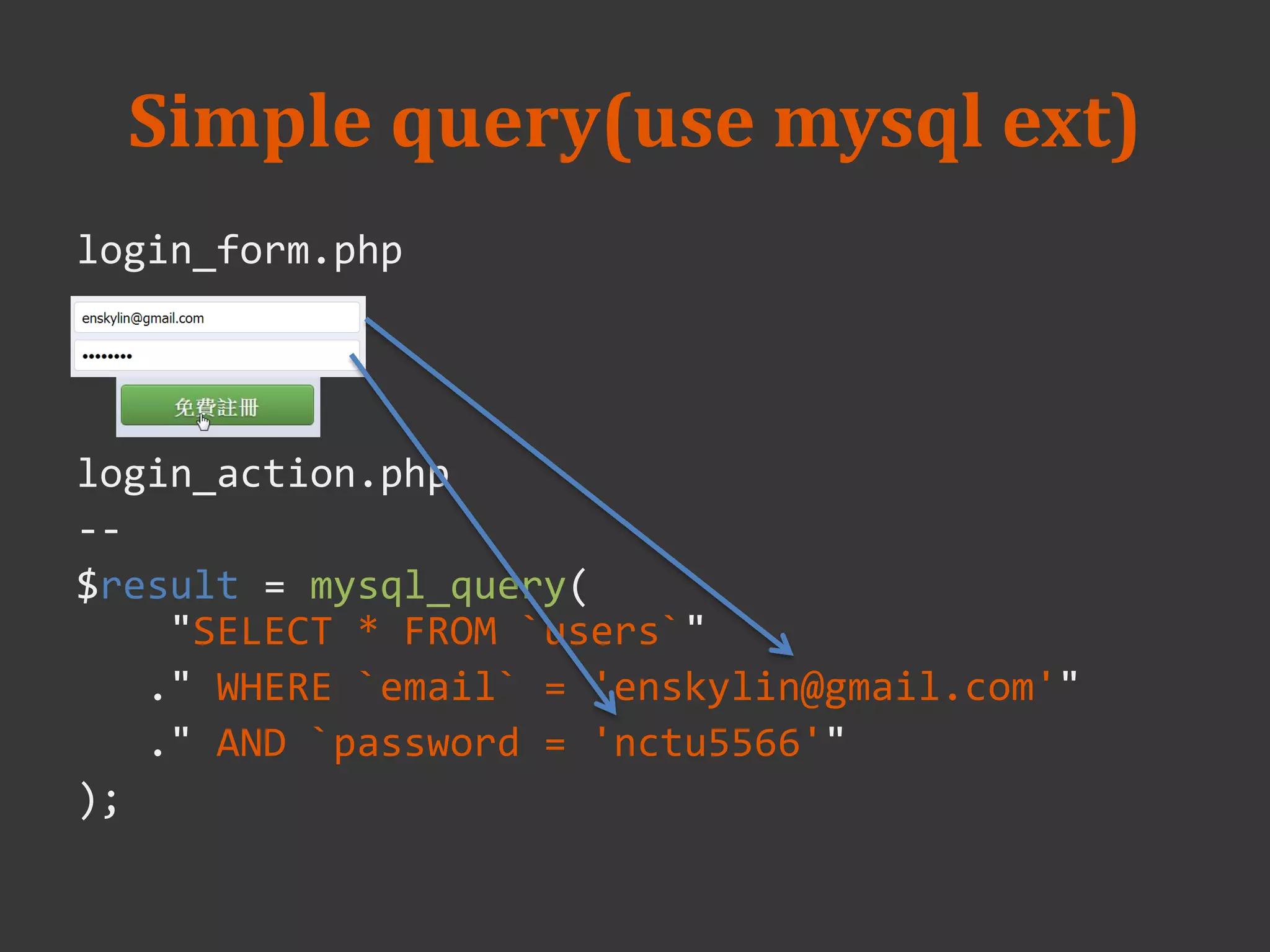




![Usage
// create a hash
$hash = password_hash($_POST['password']);
// verify a hash
if (password_verify($_POST['password'], $hash))
{
echo 'Password is valid!';
} else {
echo 'Invalid password.';
}](https://image.slidesharecdn.com/week3-20-20php-20-20mysql-140312024517-phpapp02/75/2014-database-course-3-PHP-and-MySQL-33-2048.jpg)
