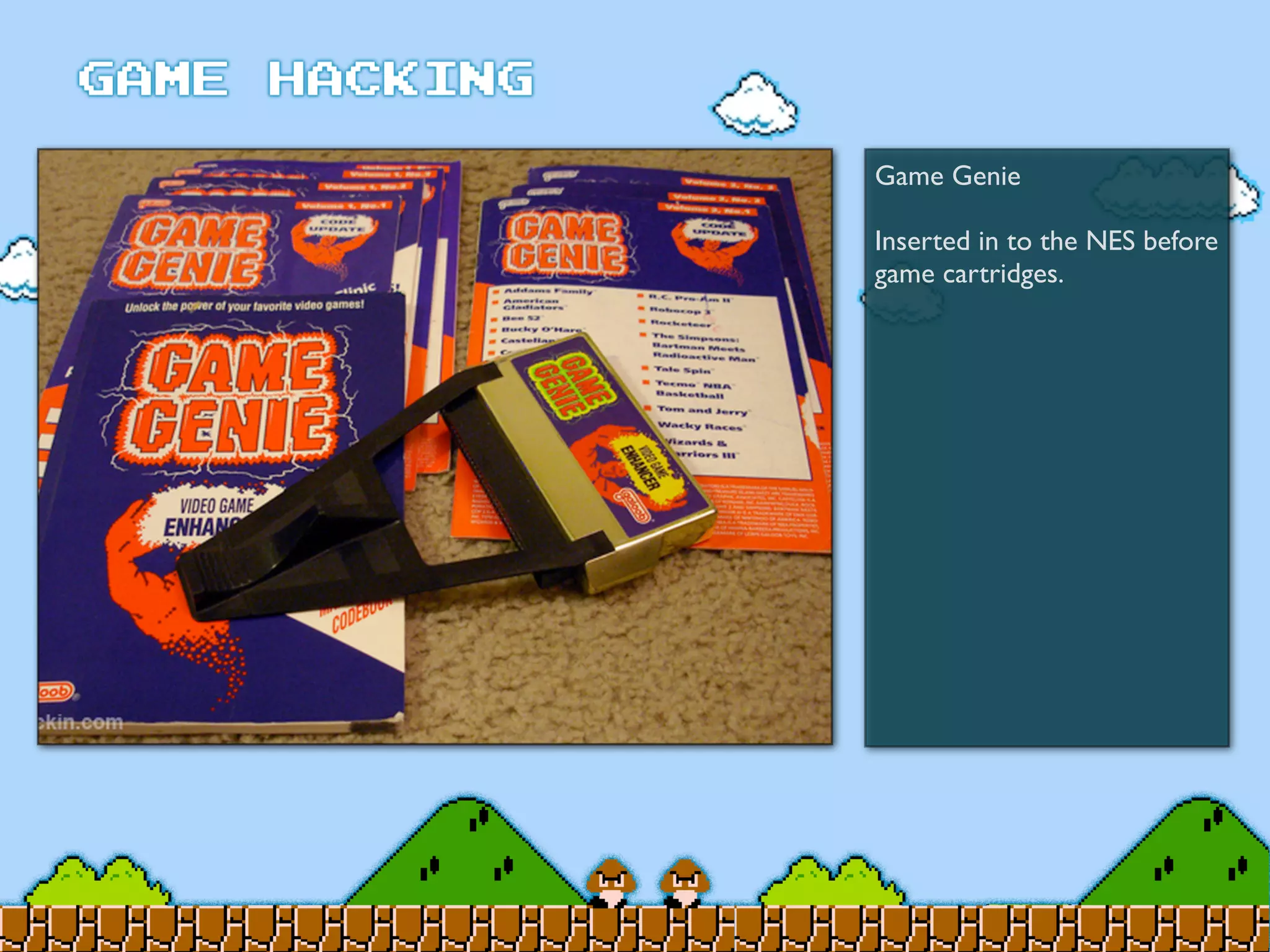
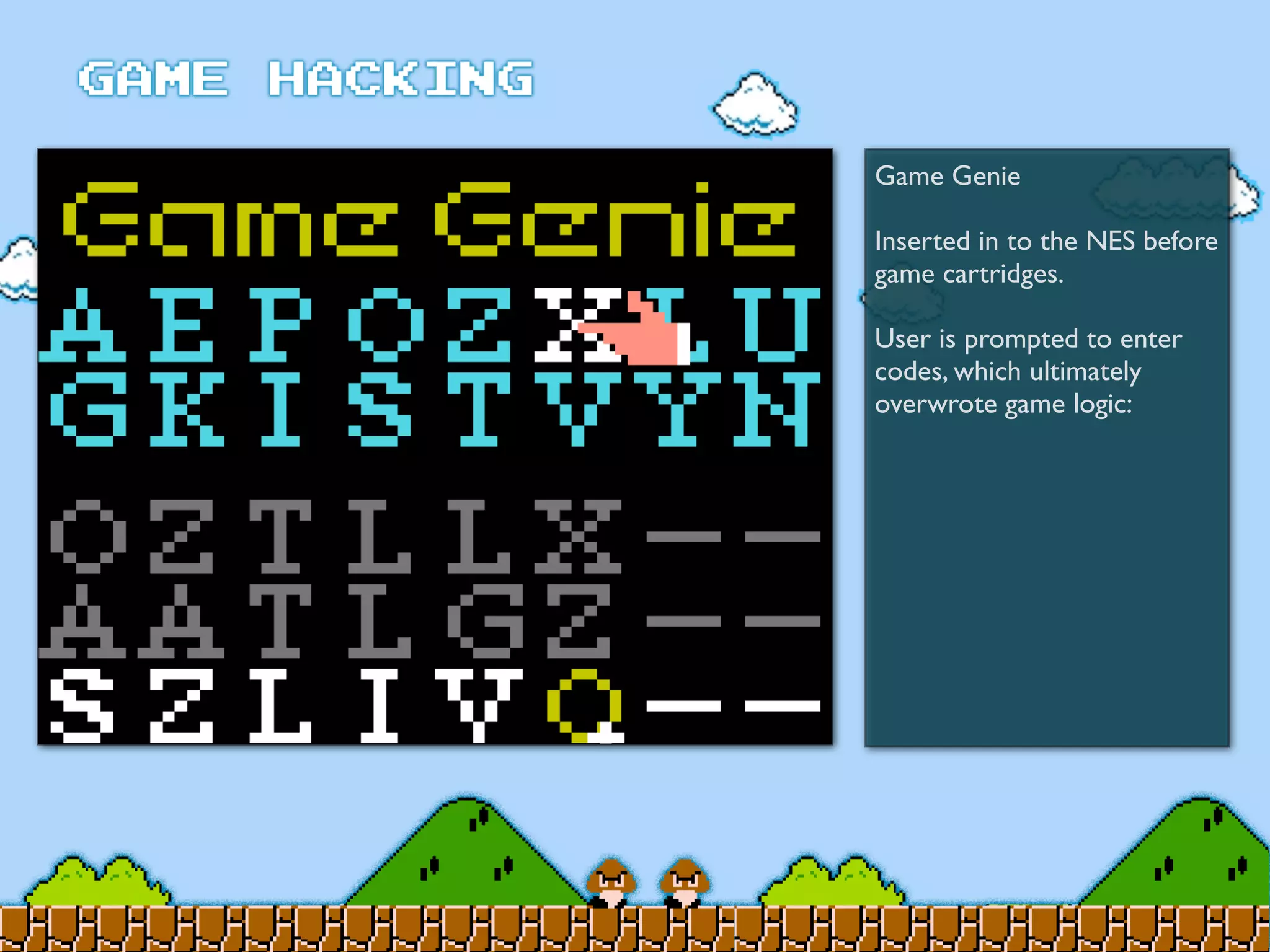
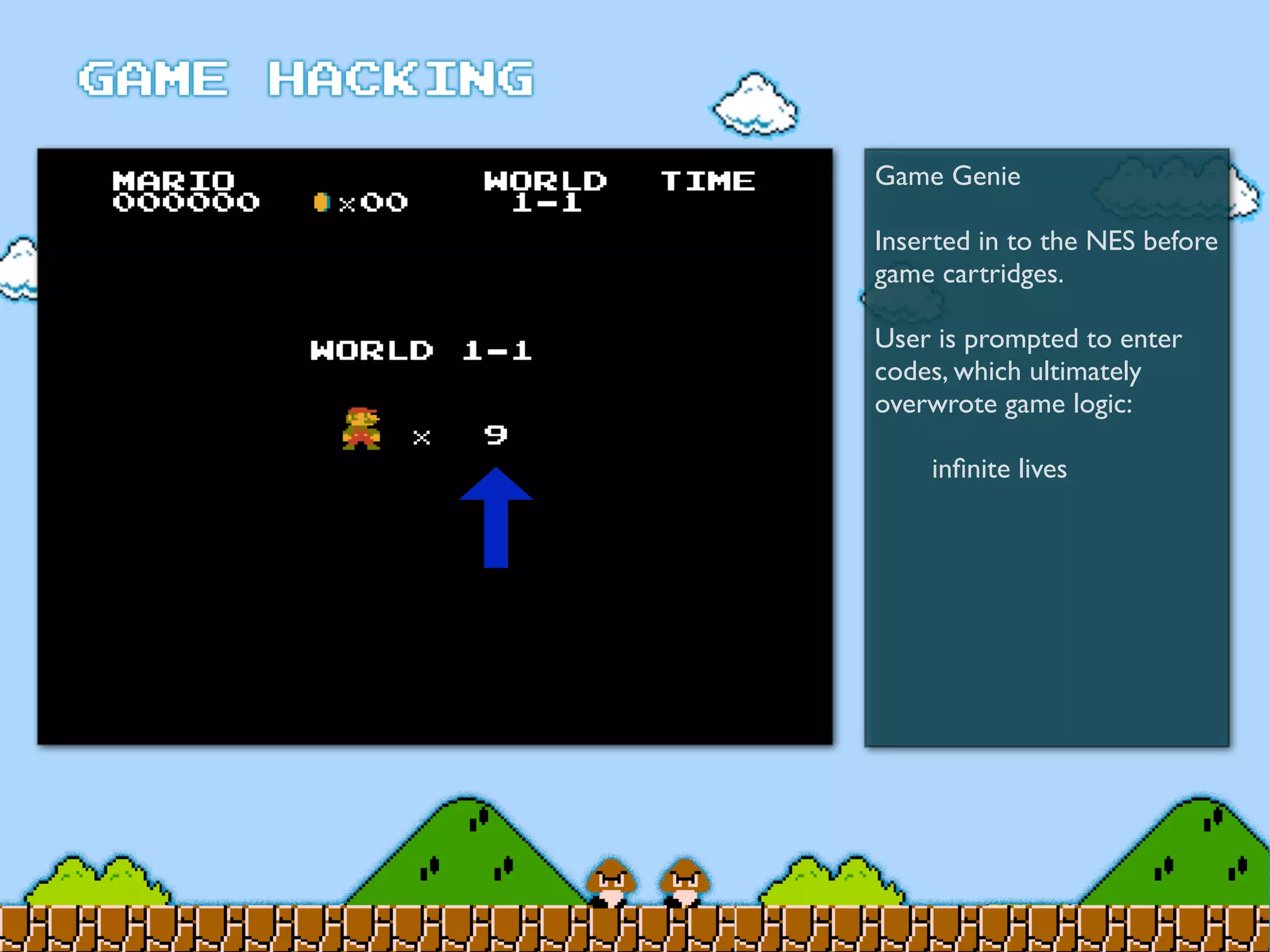
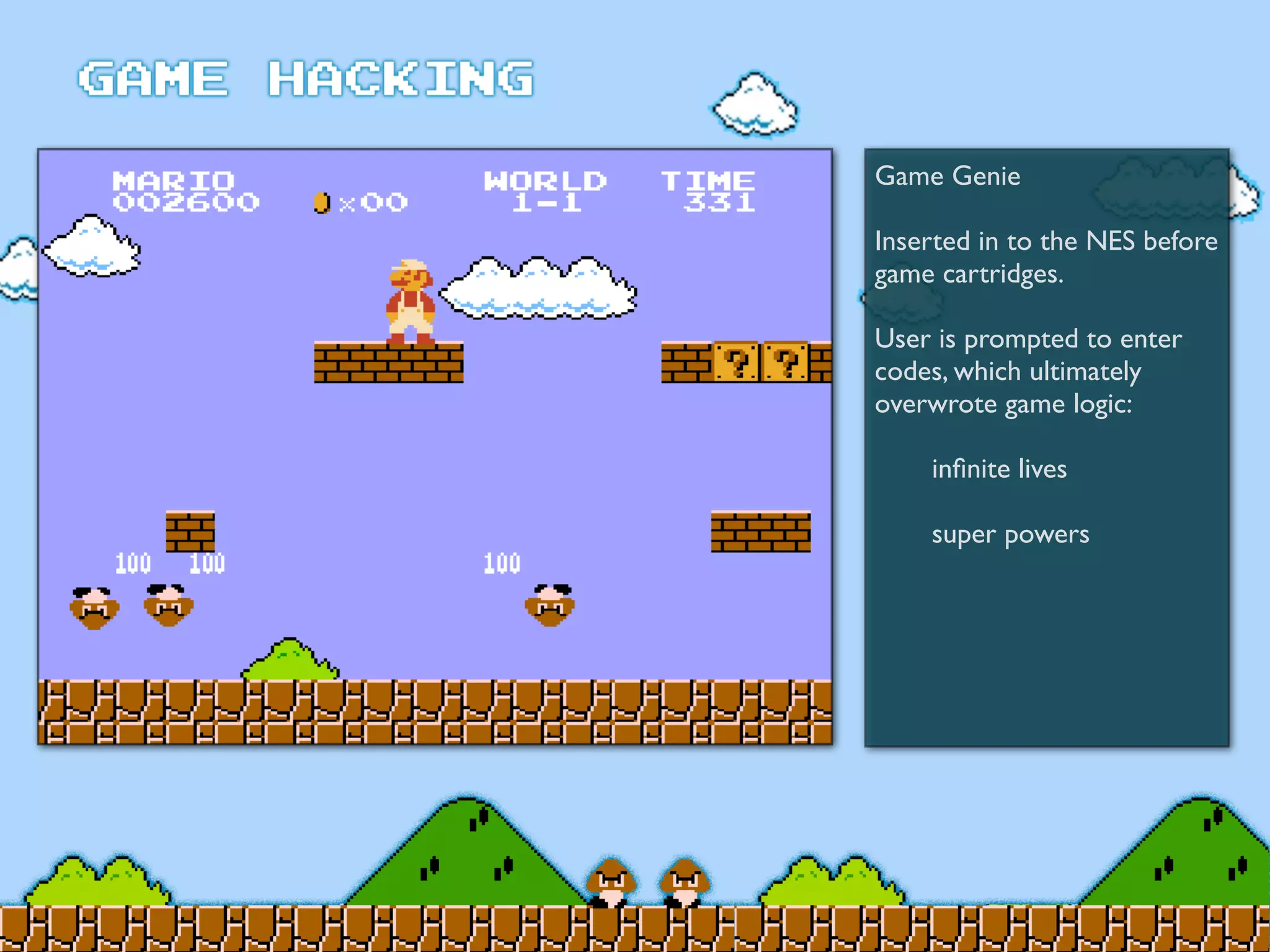
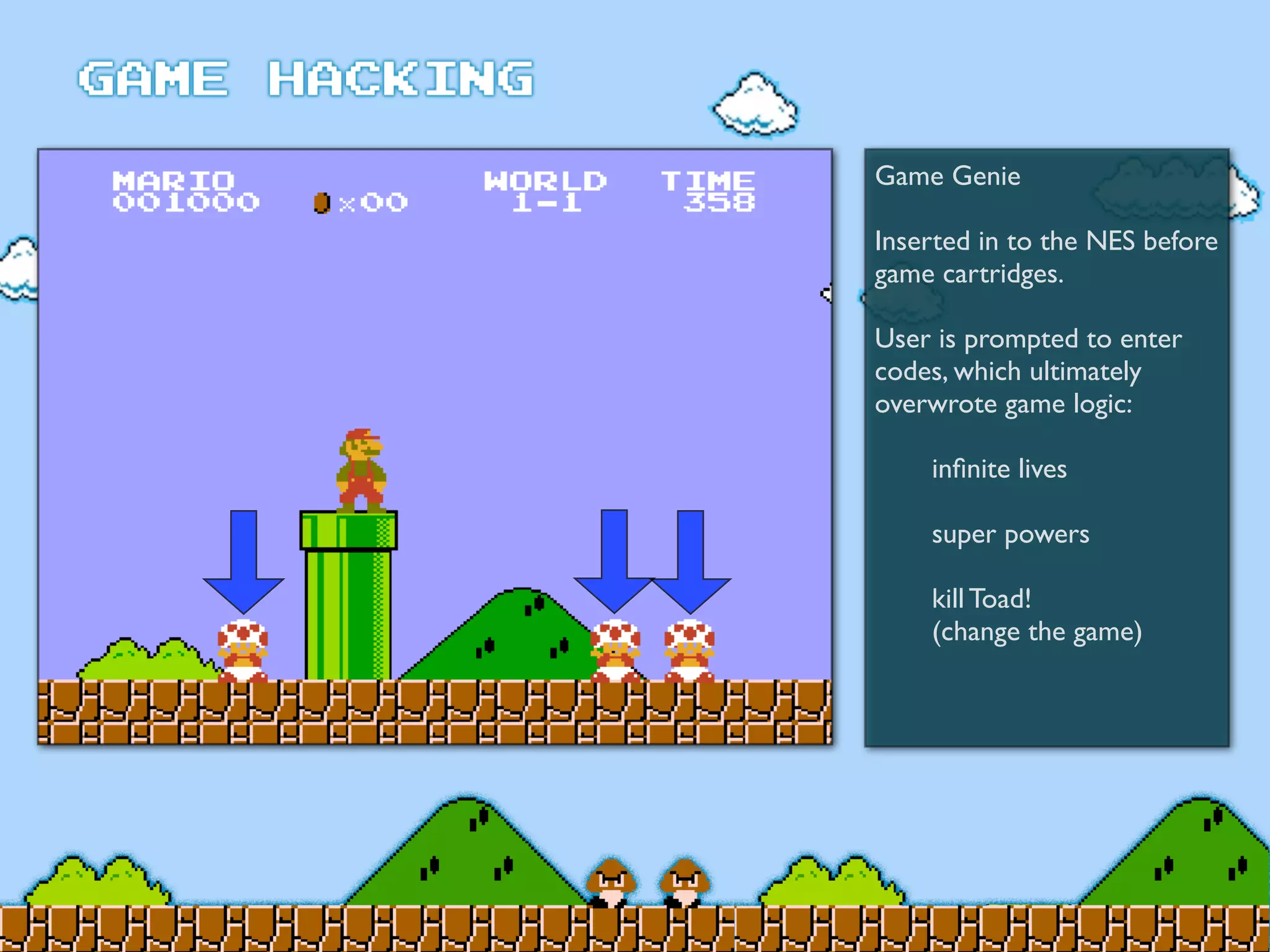
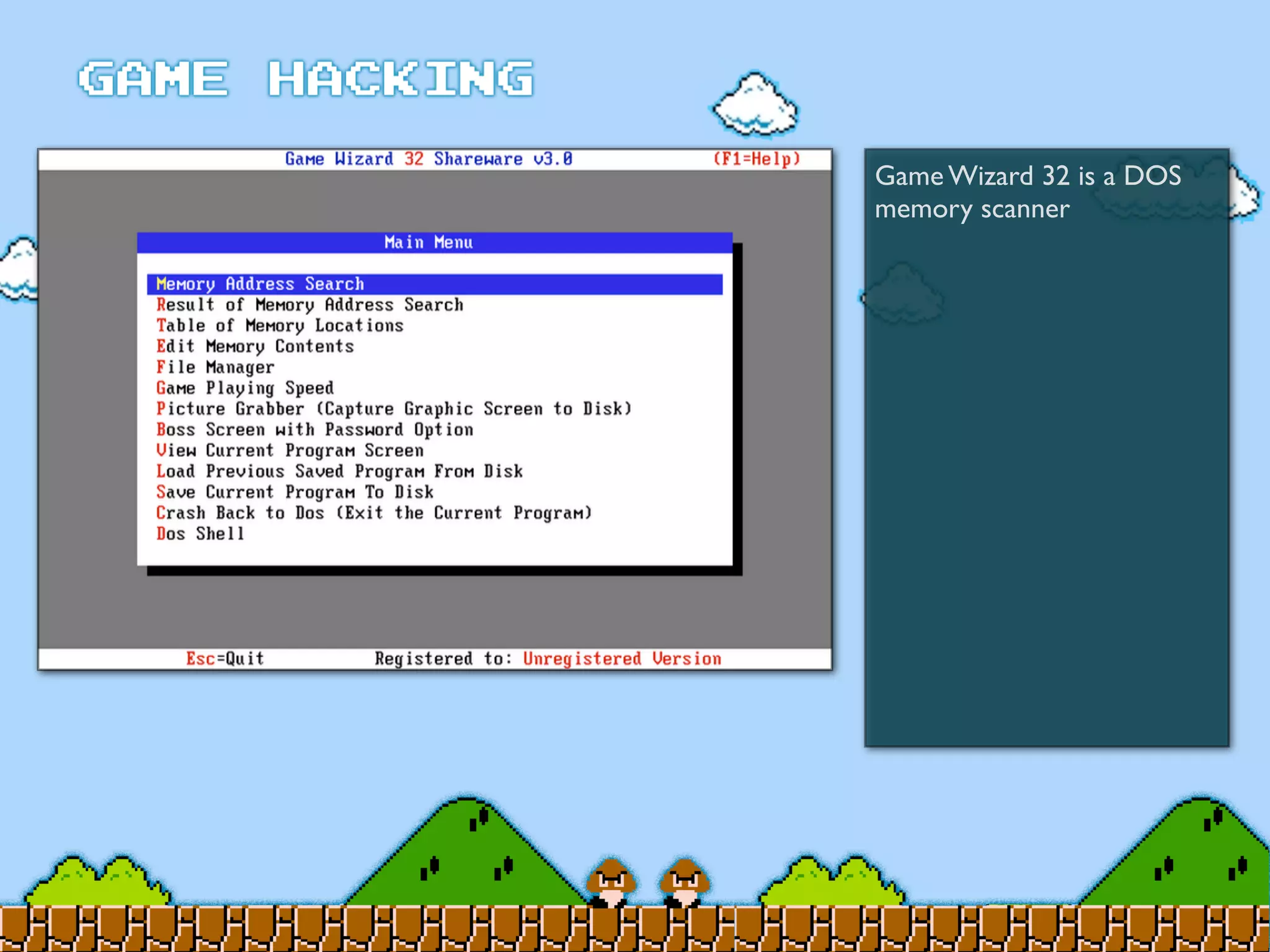
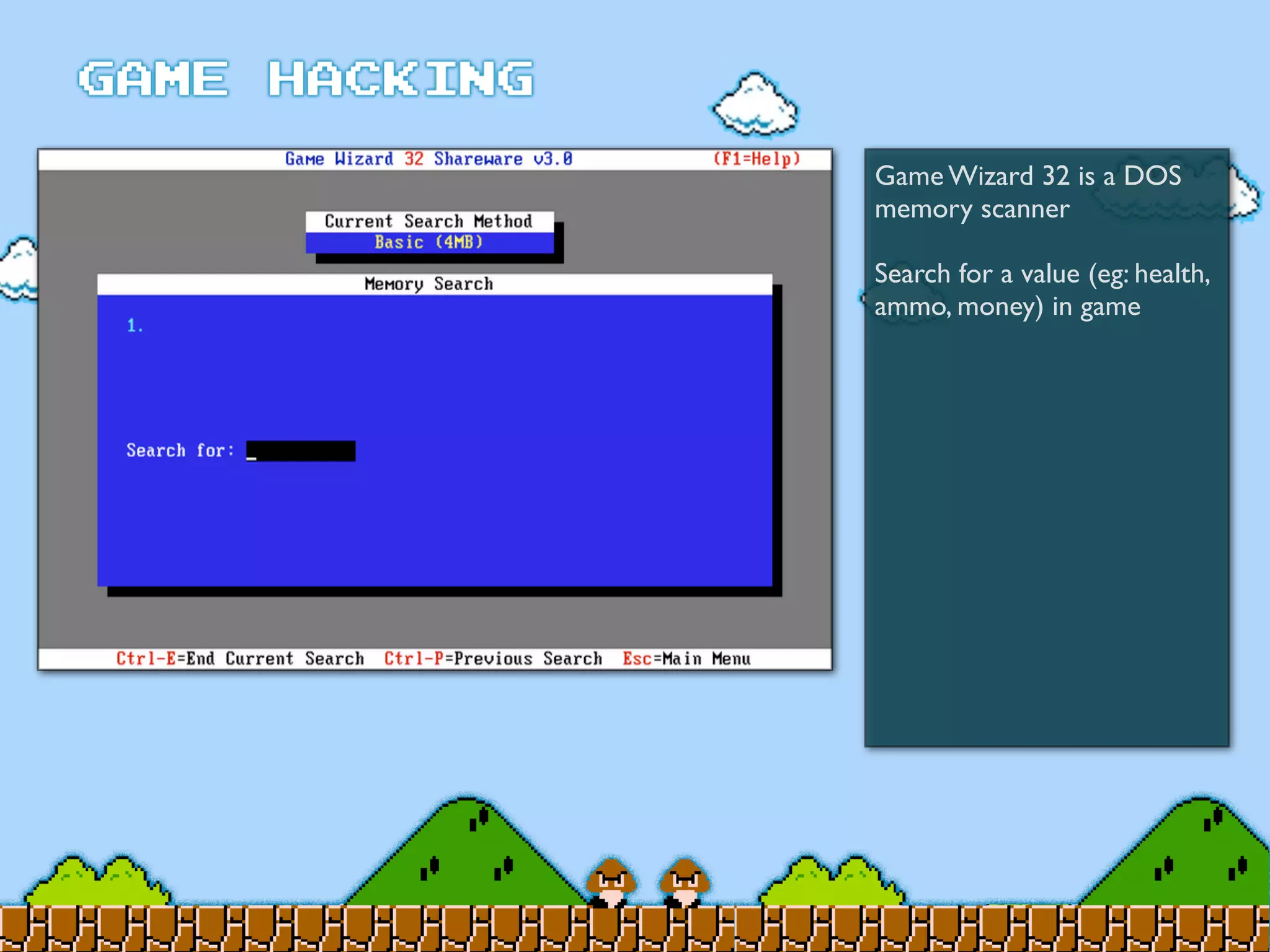
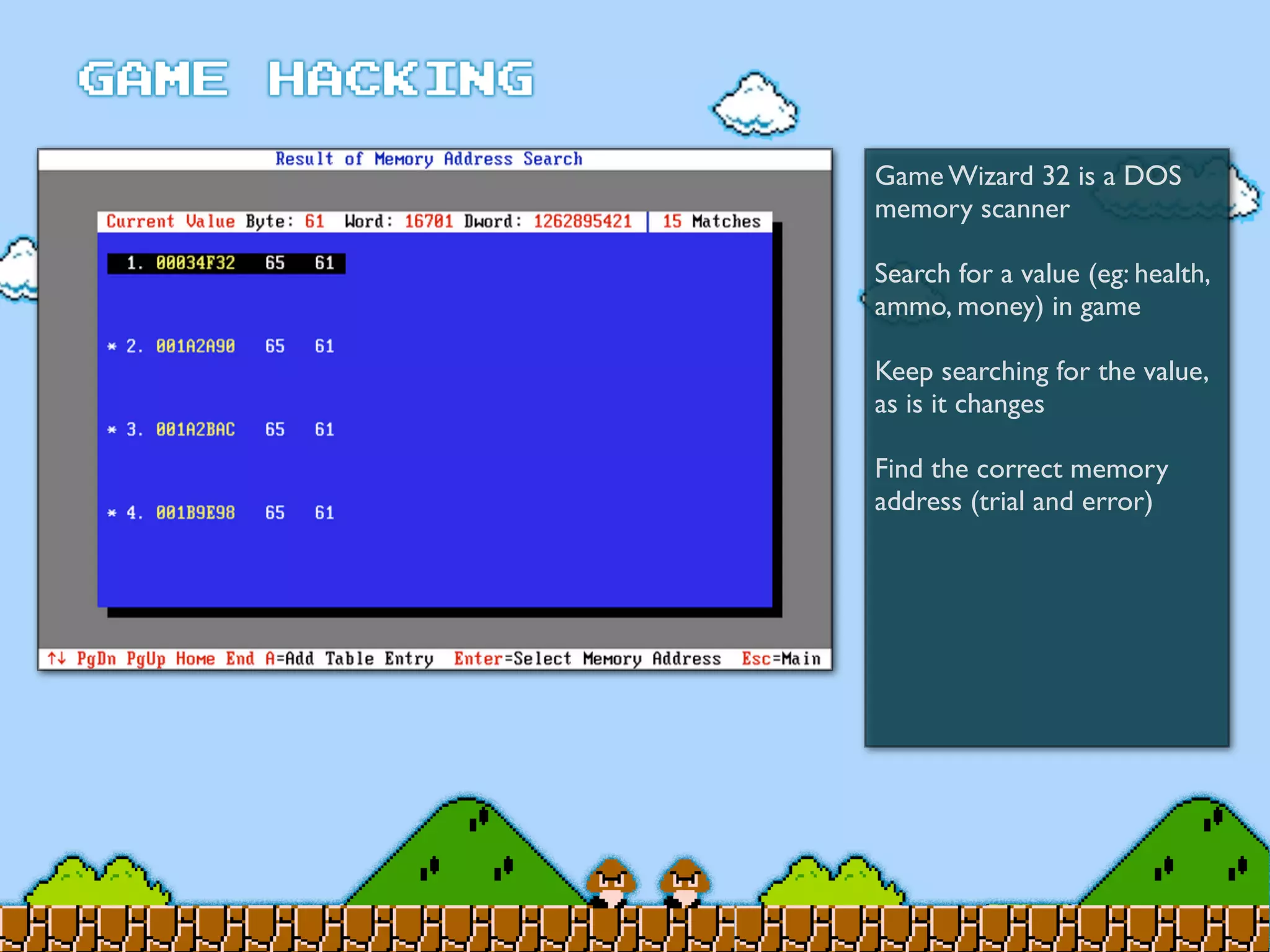
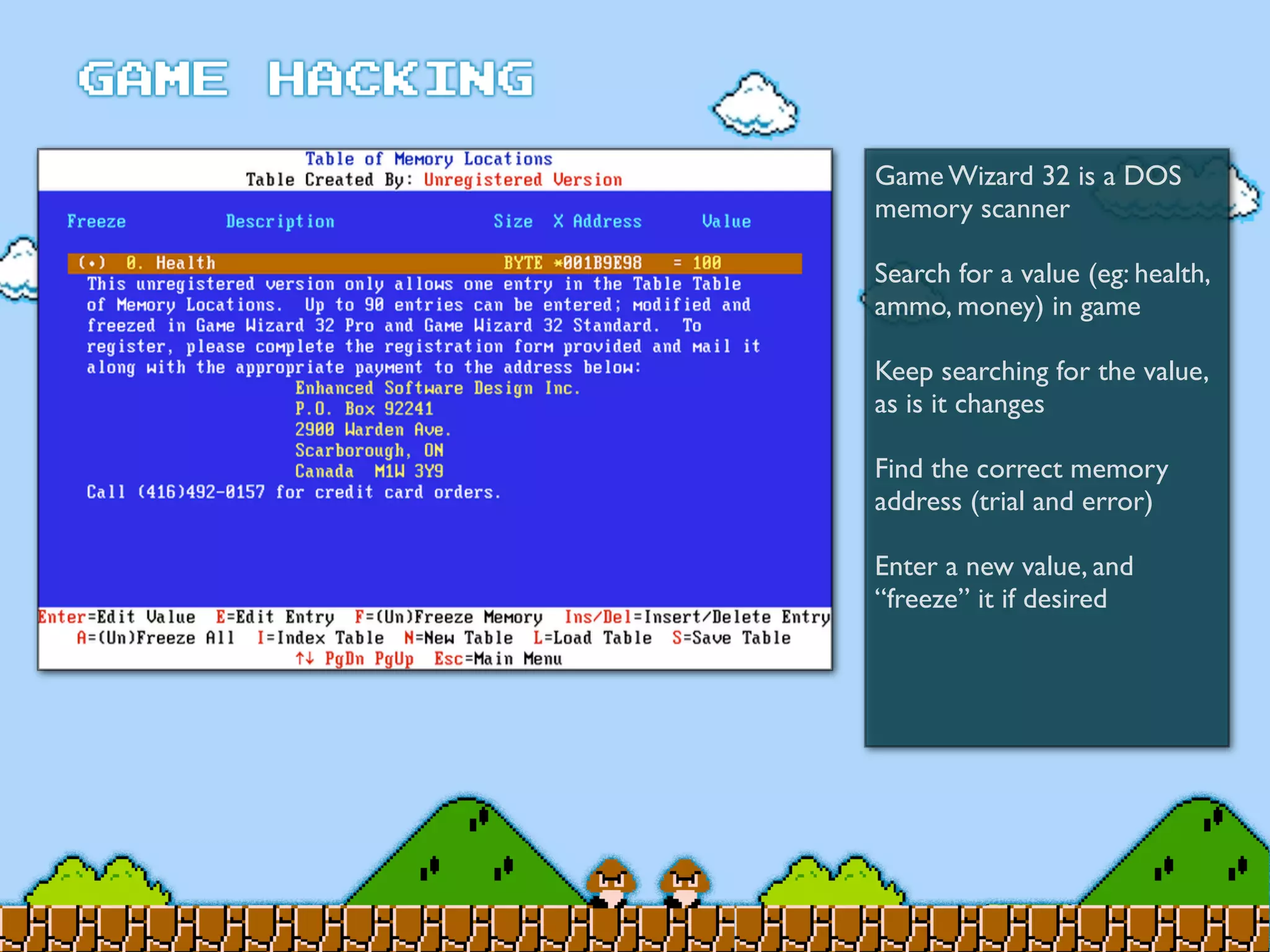
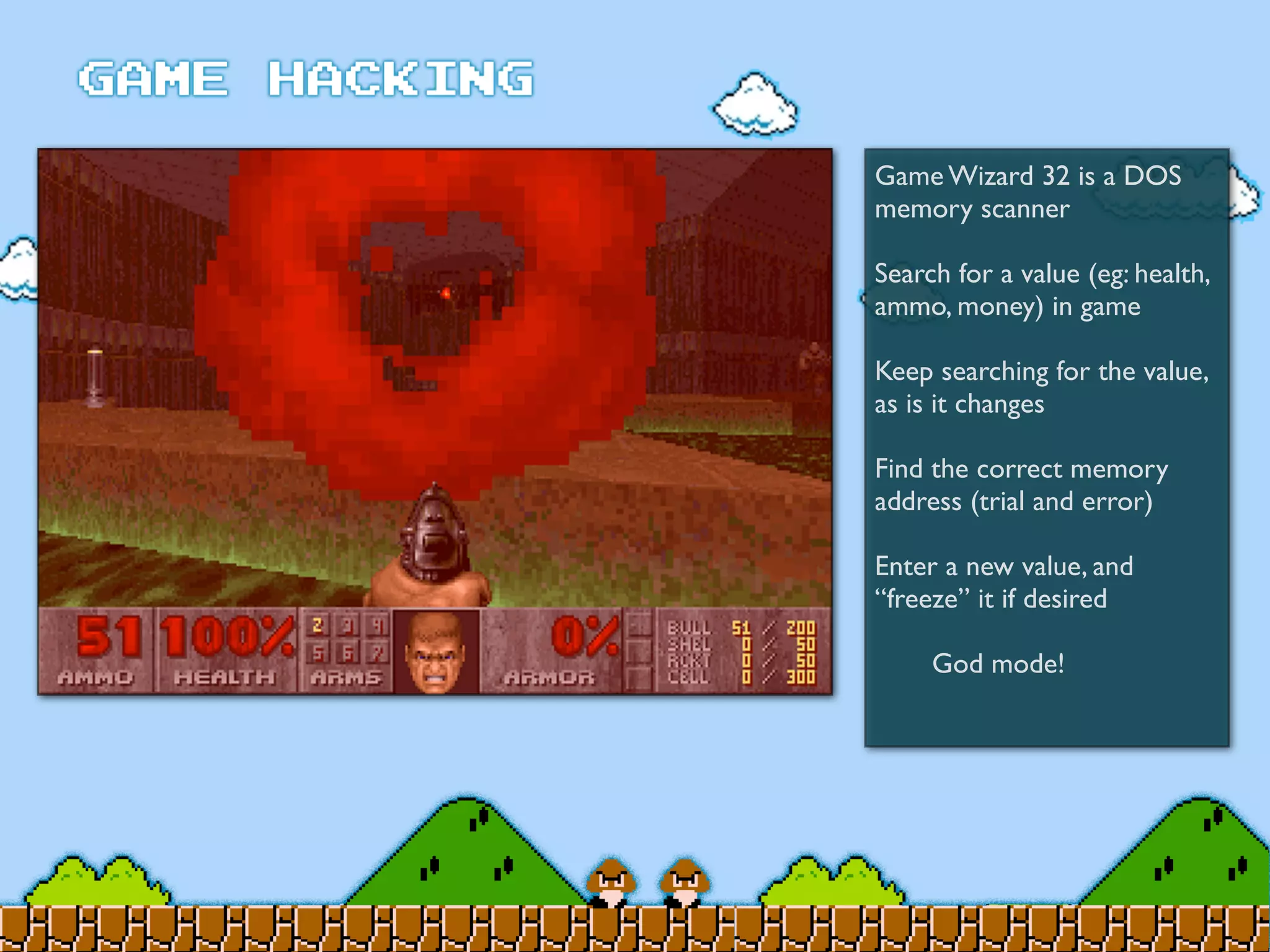
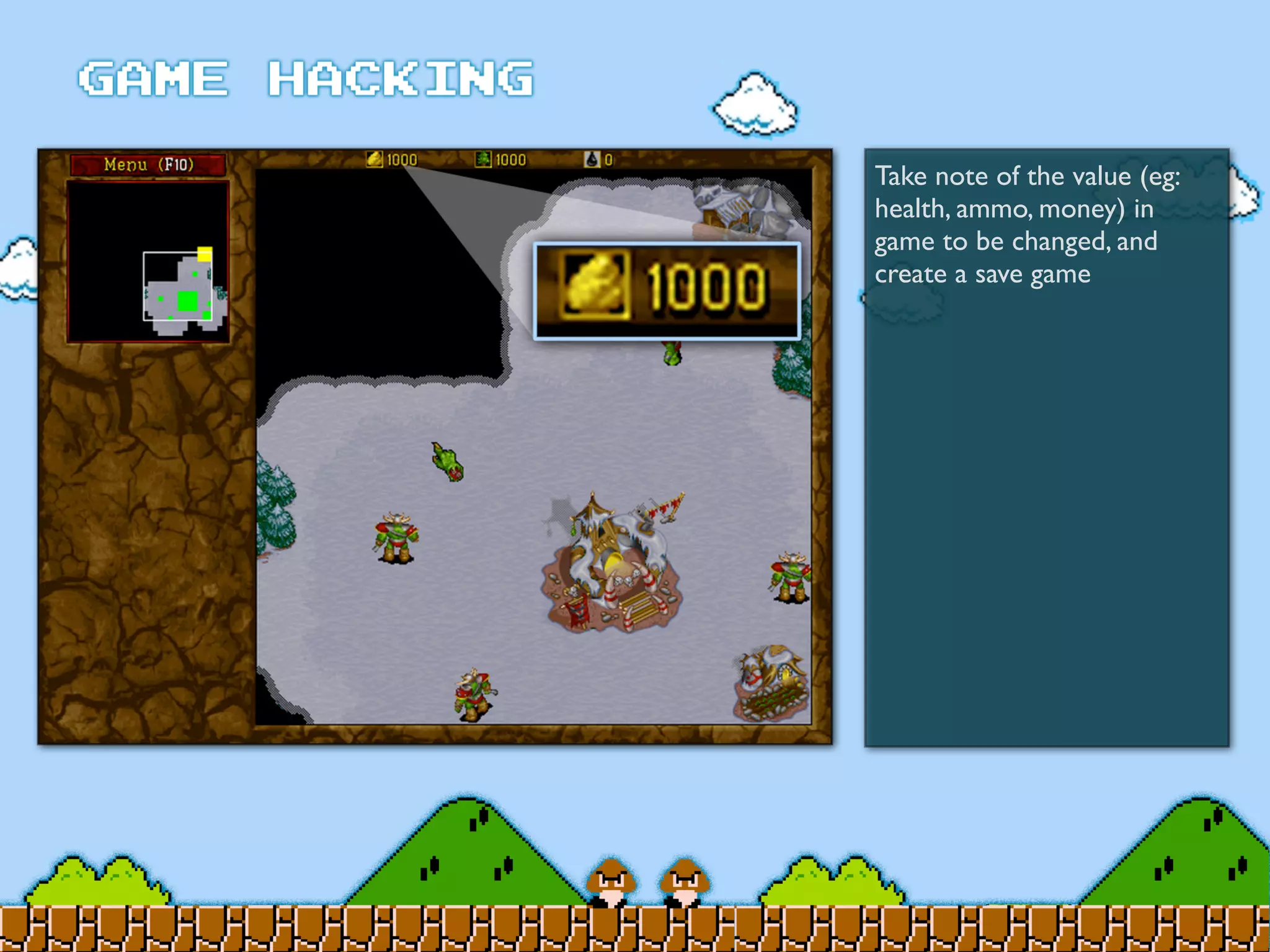
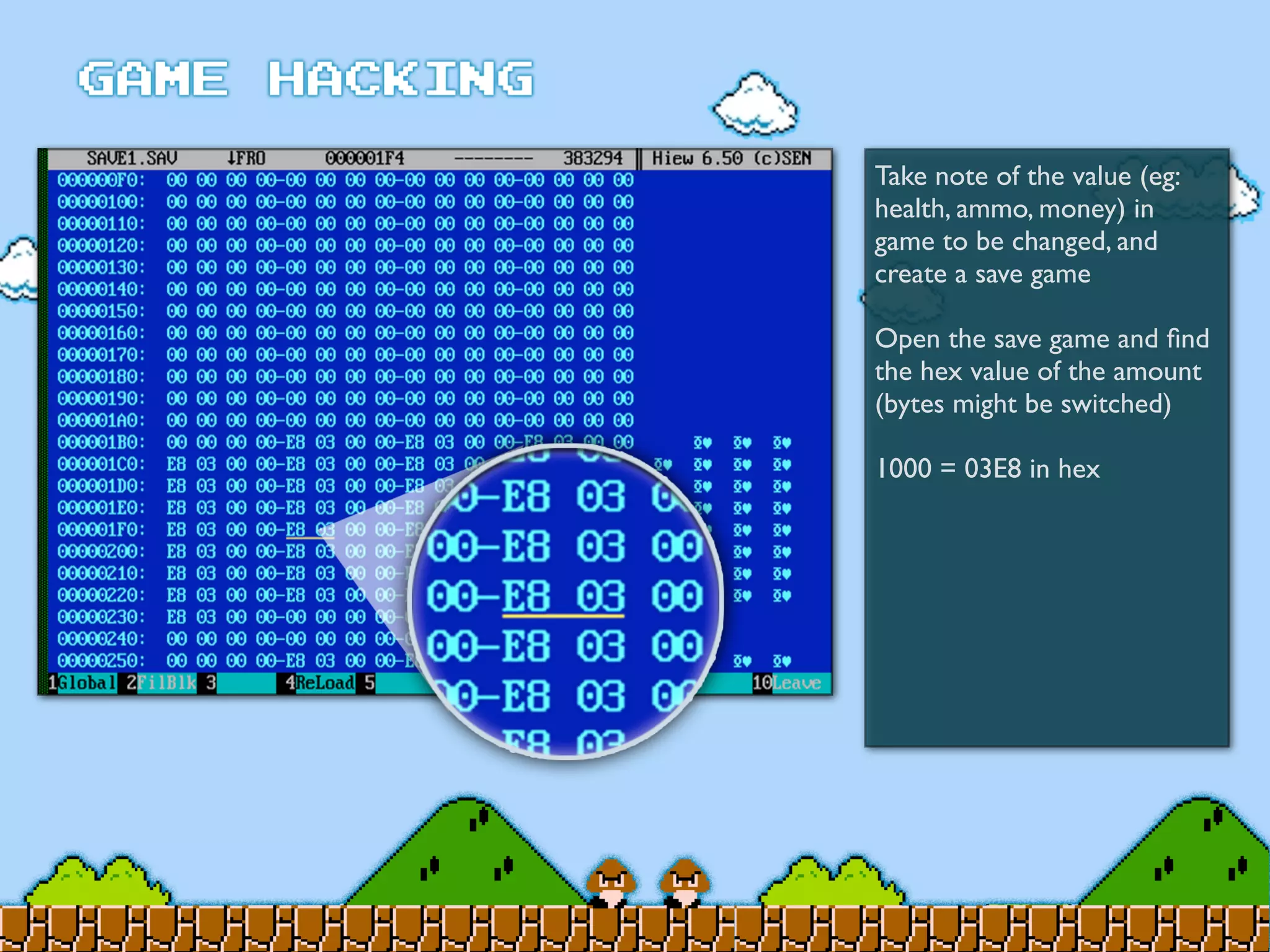
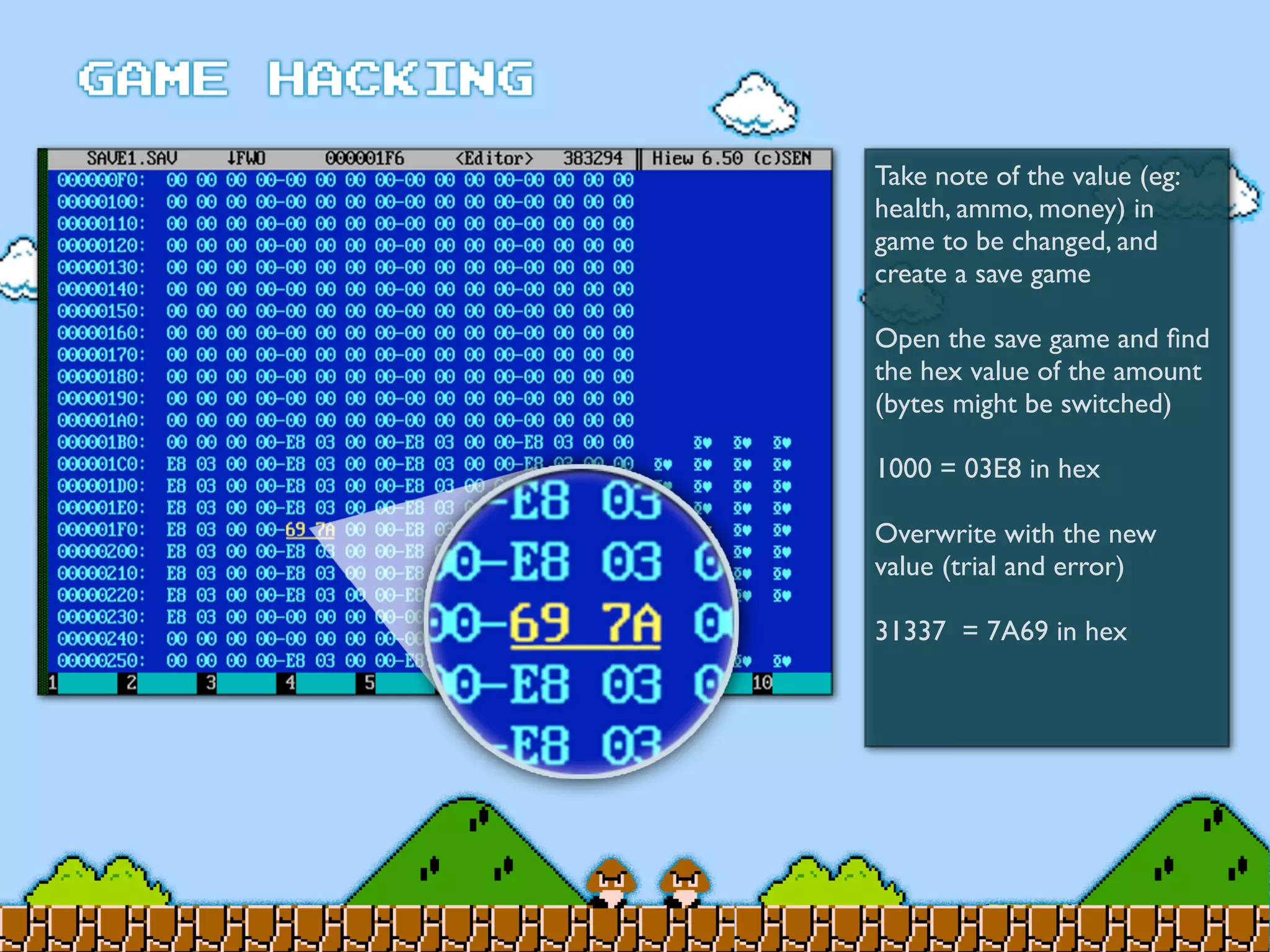
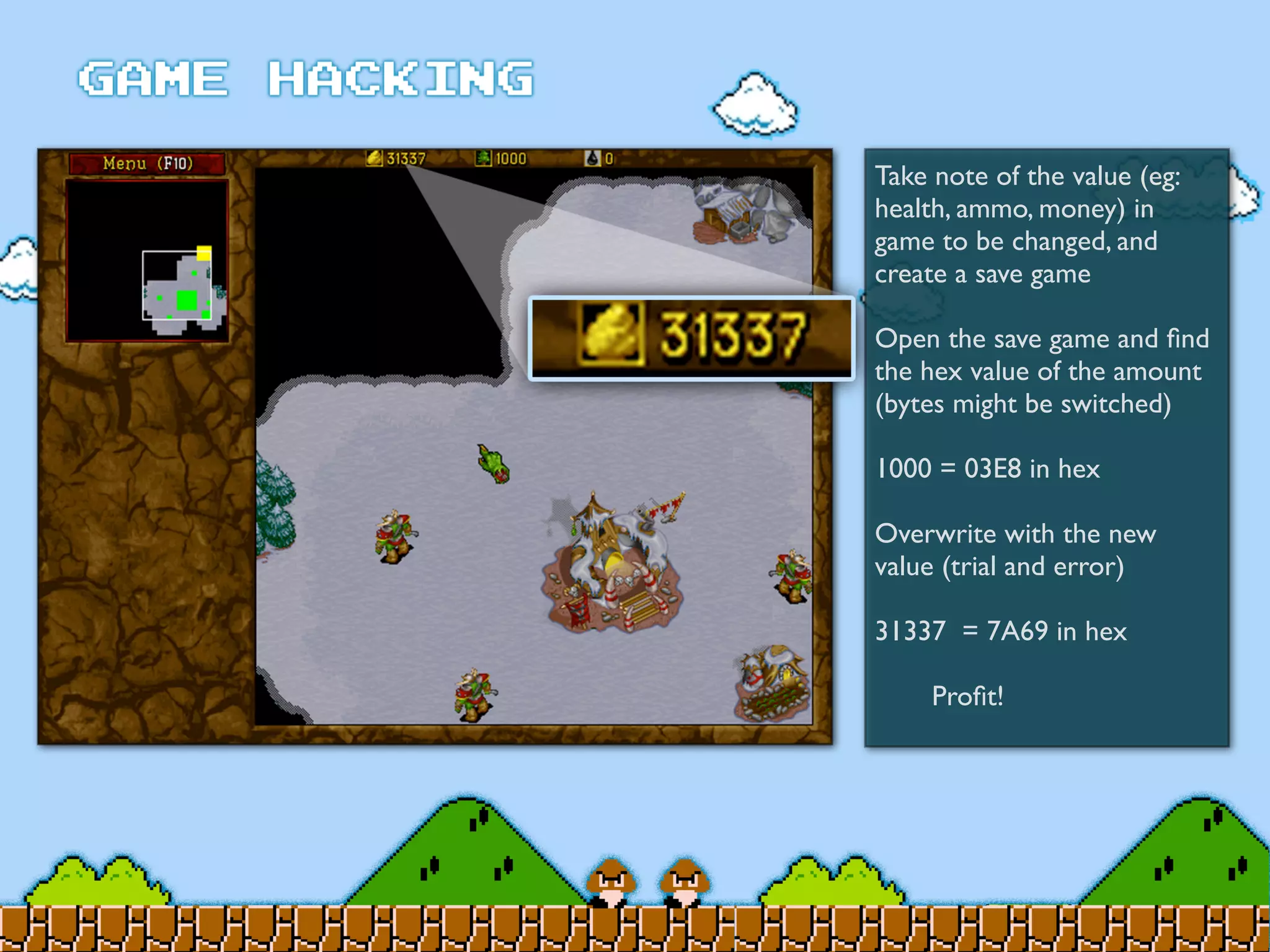
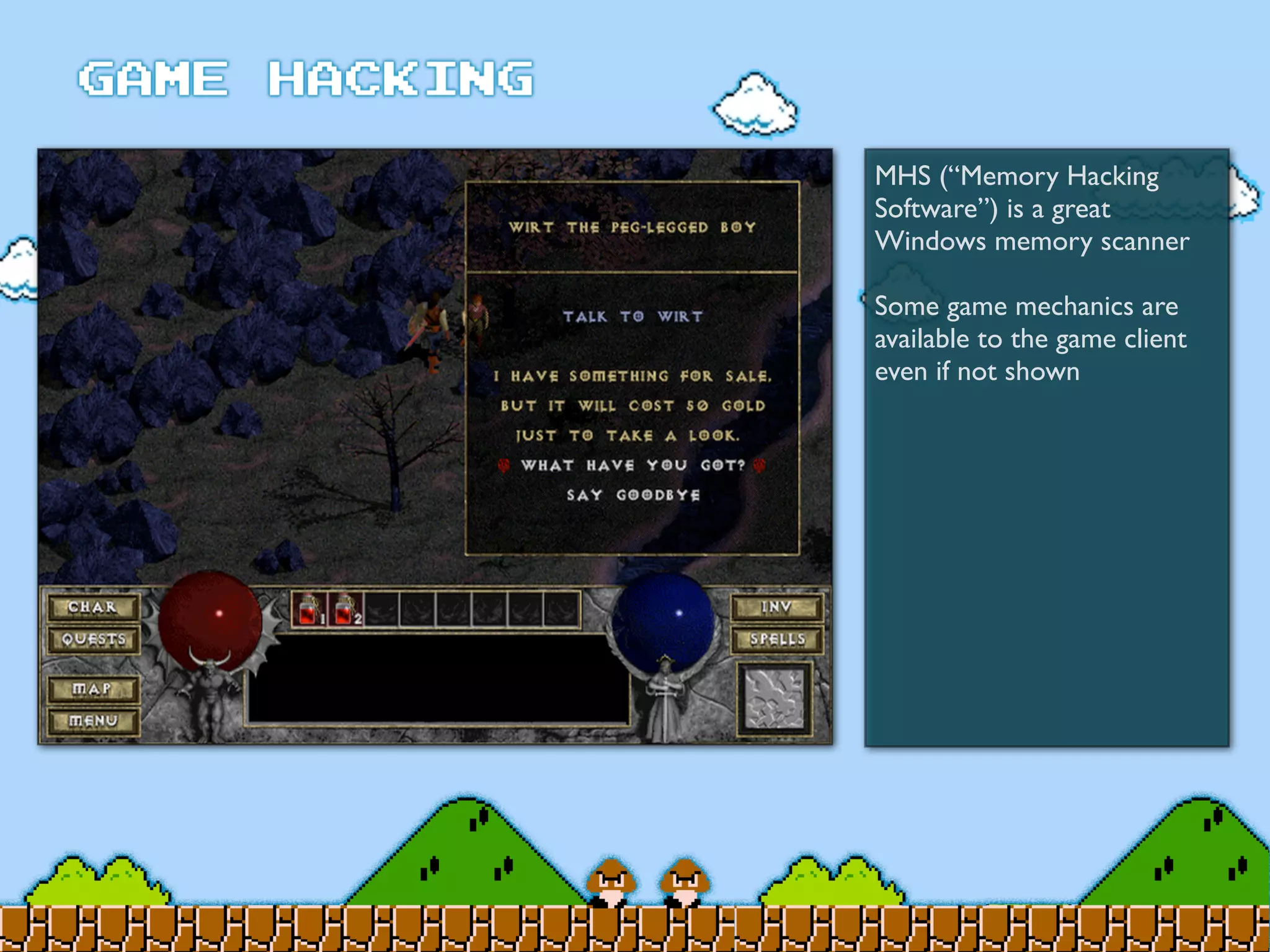
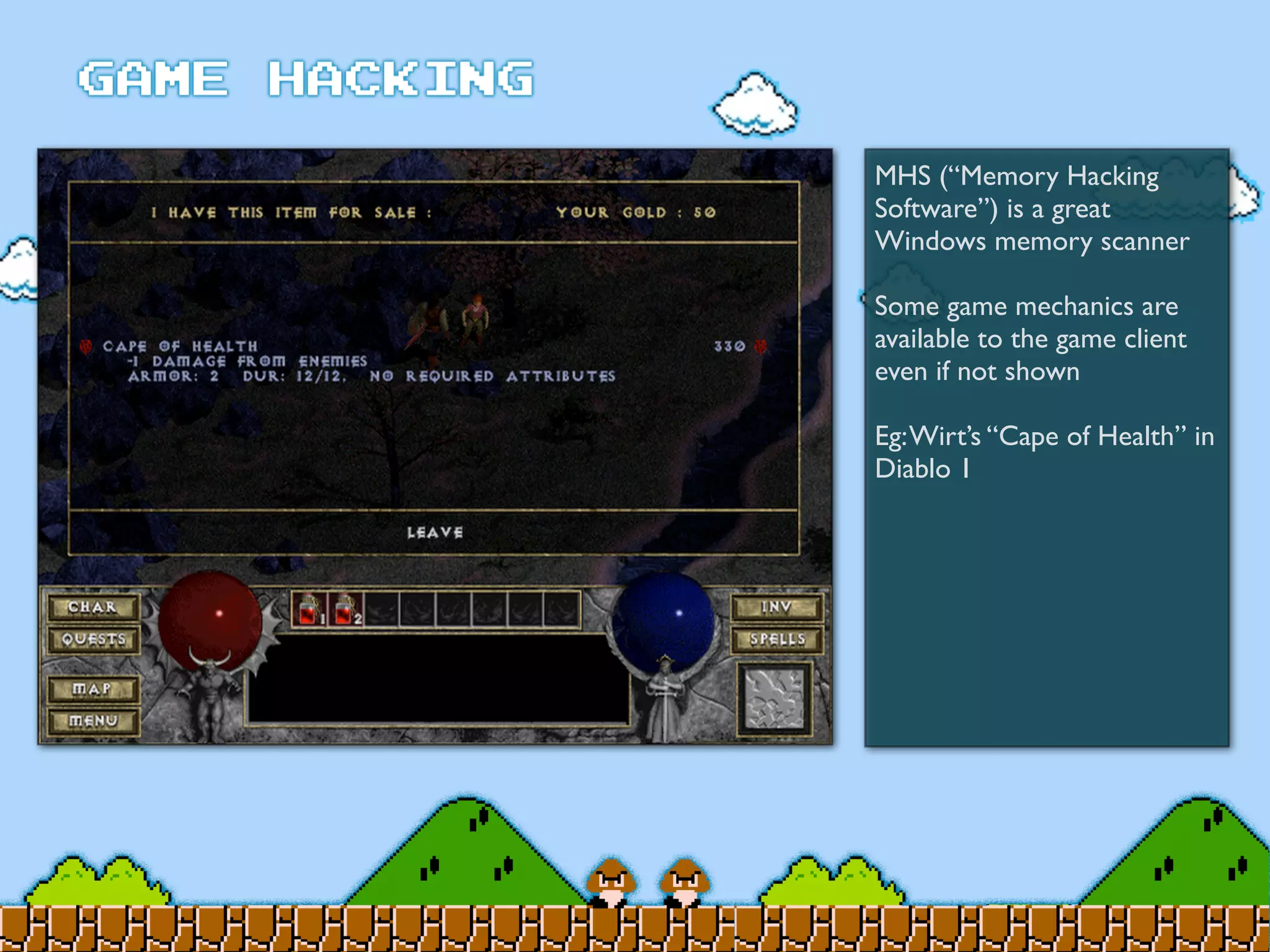
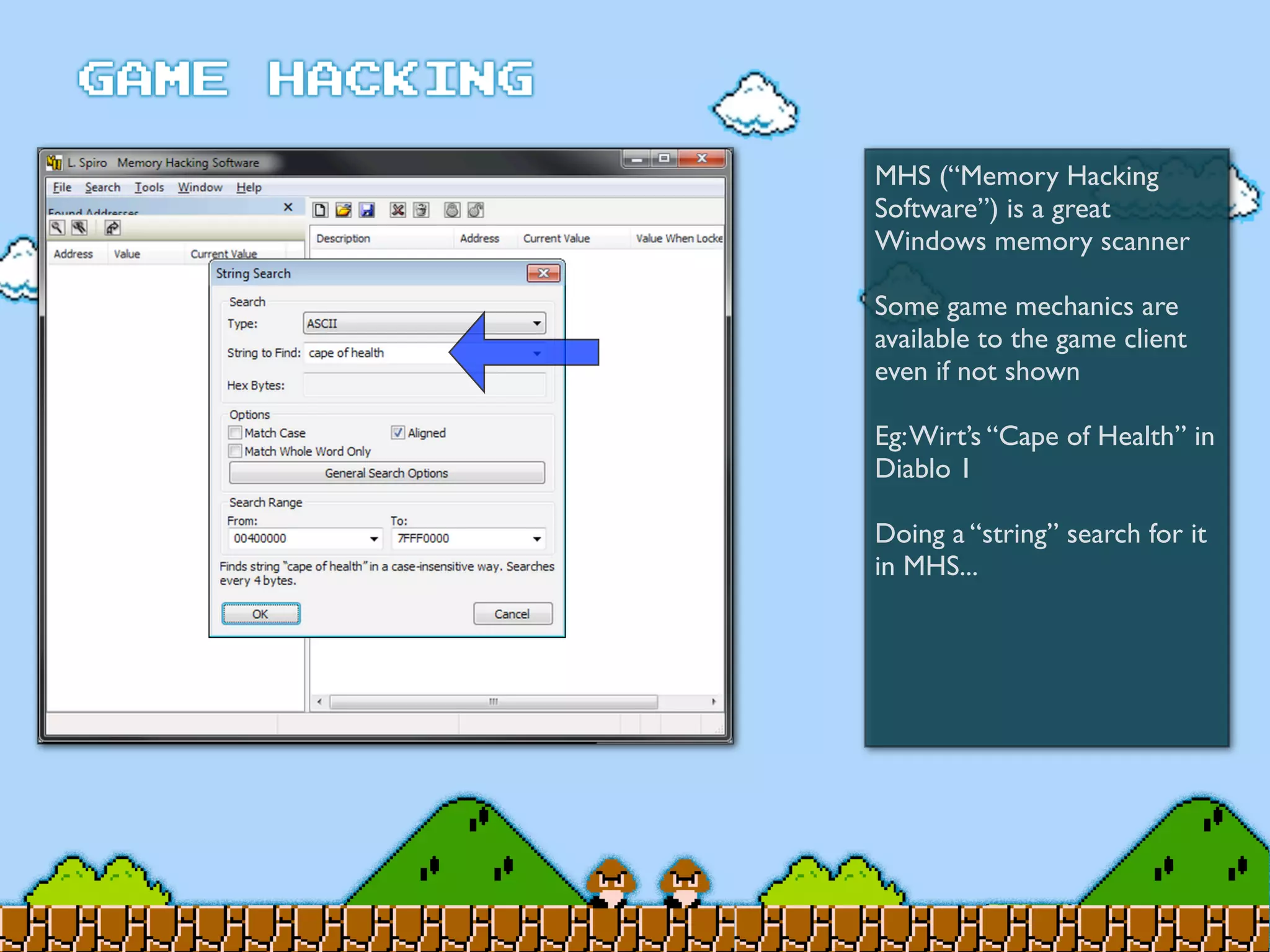
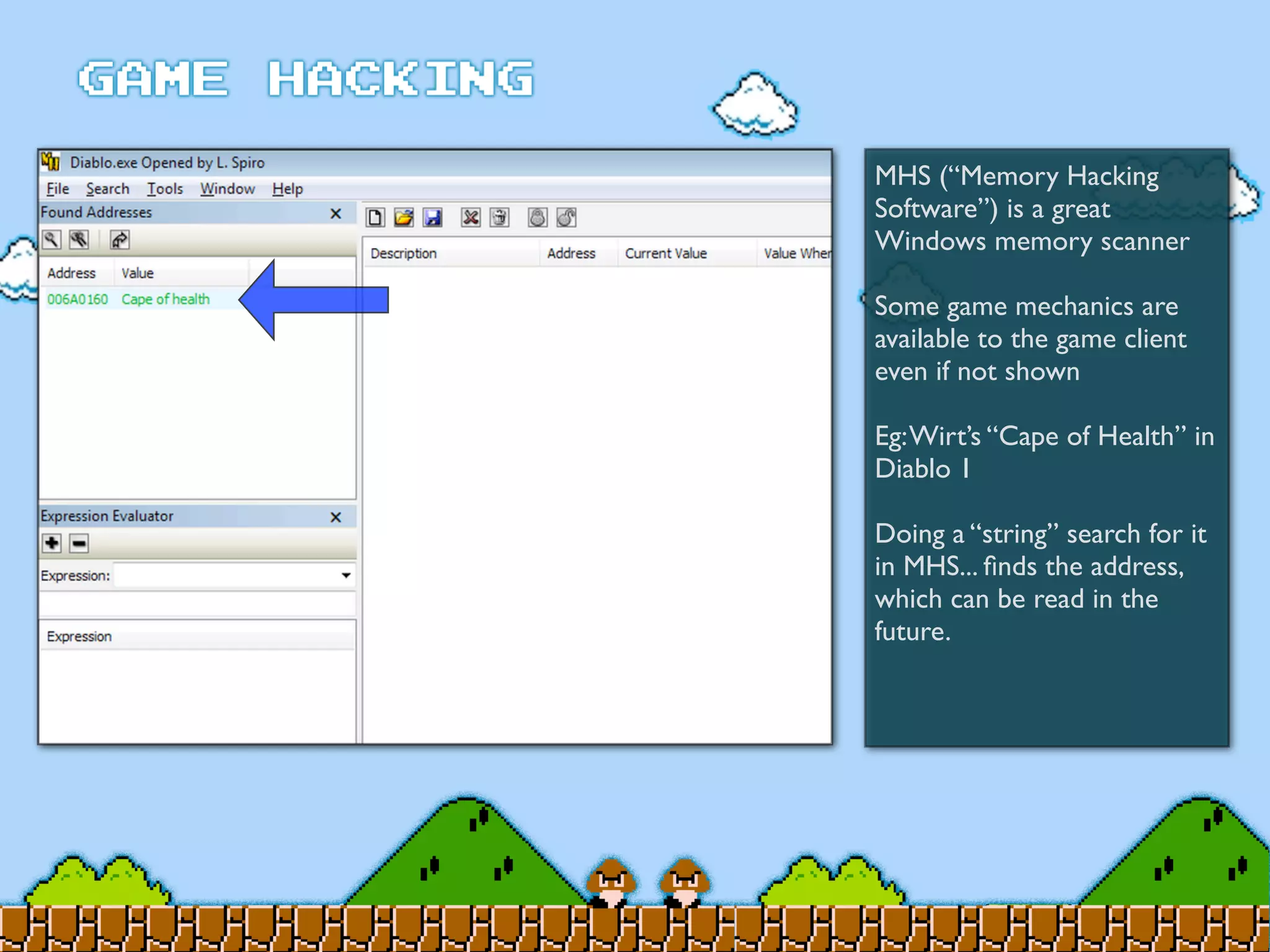
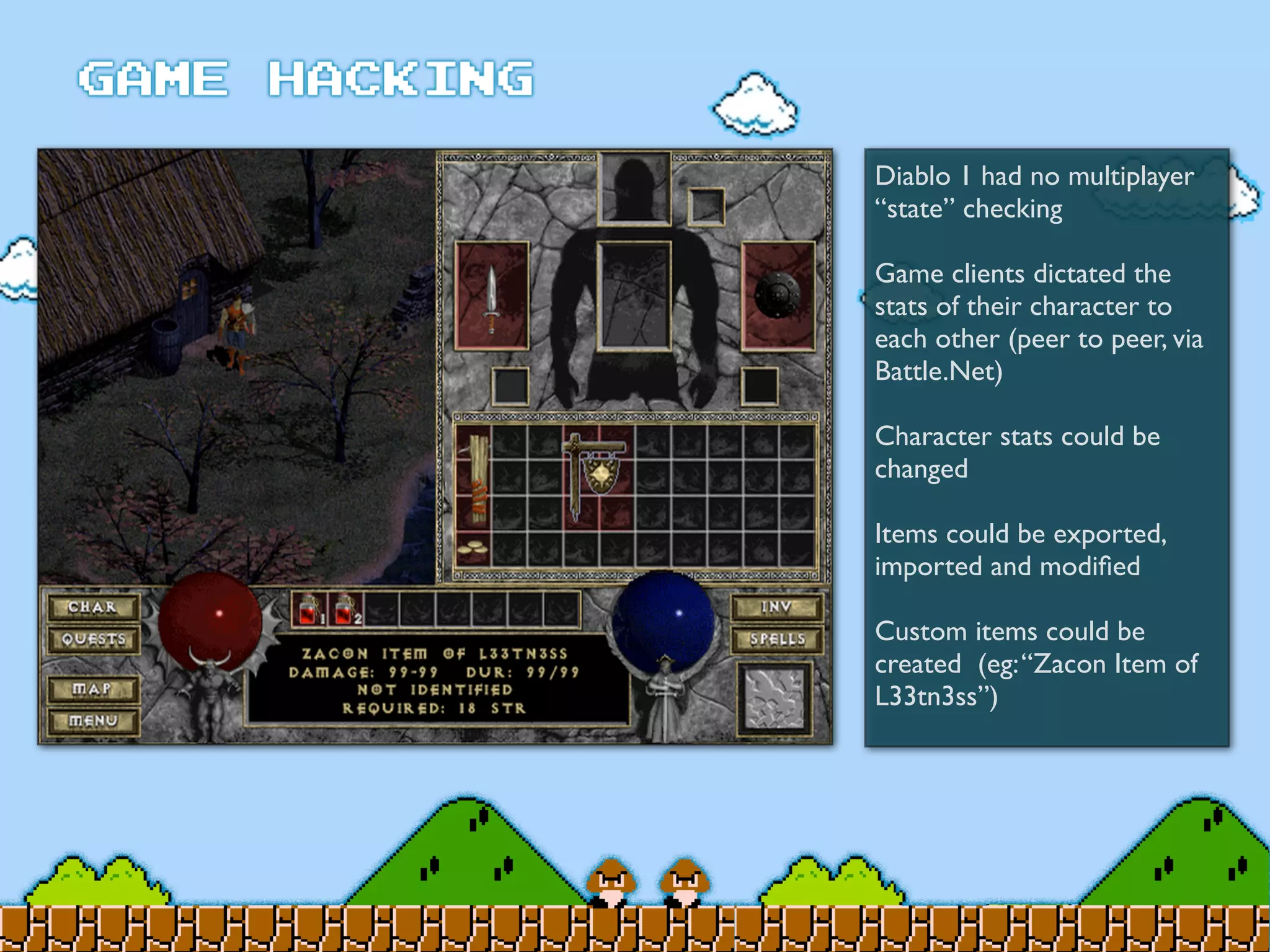
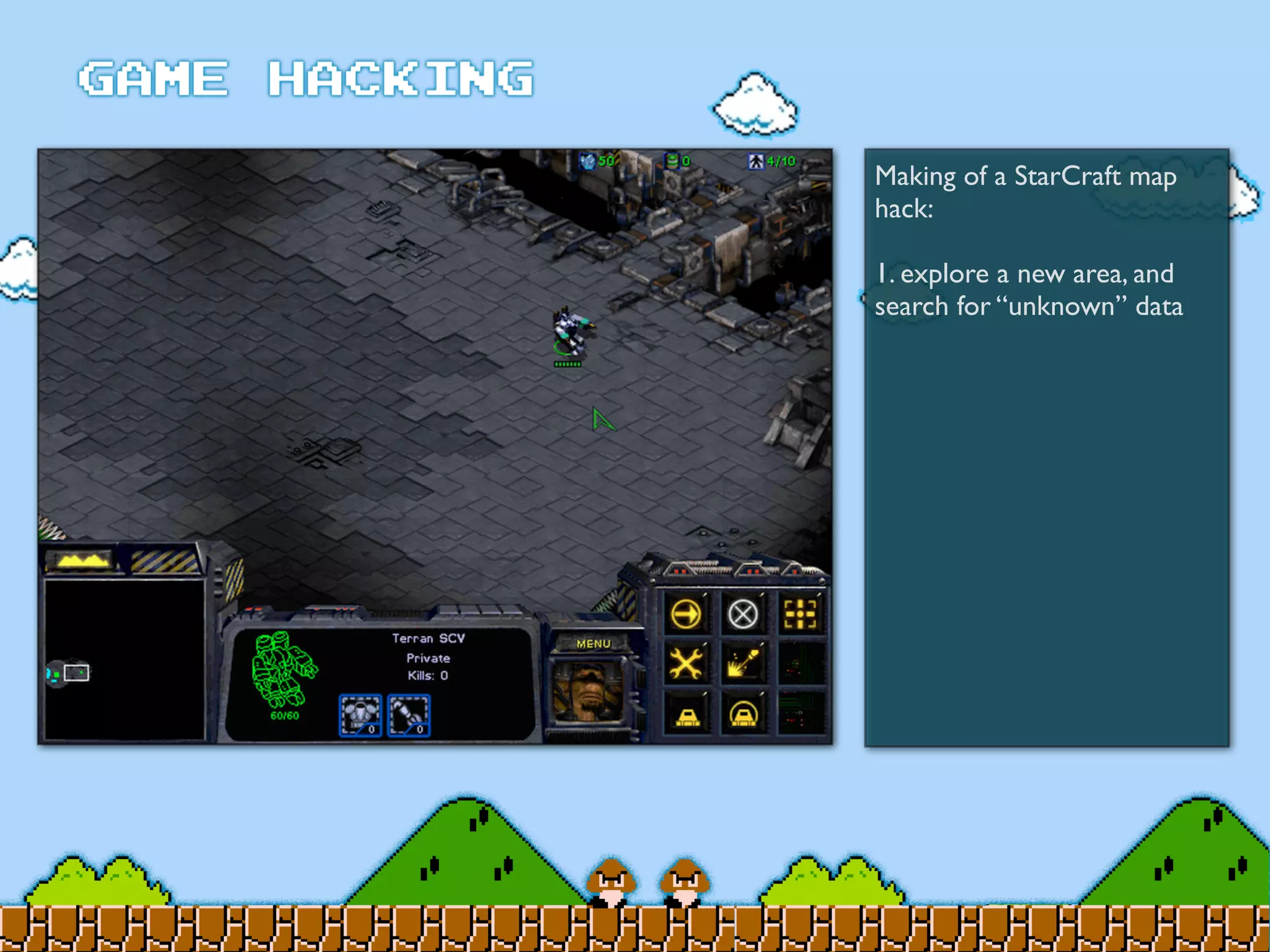
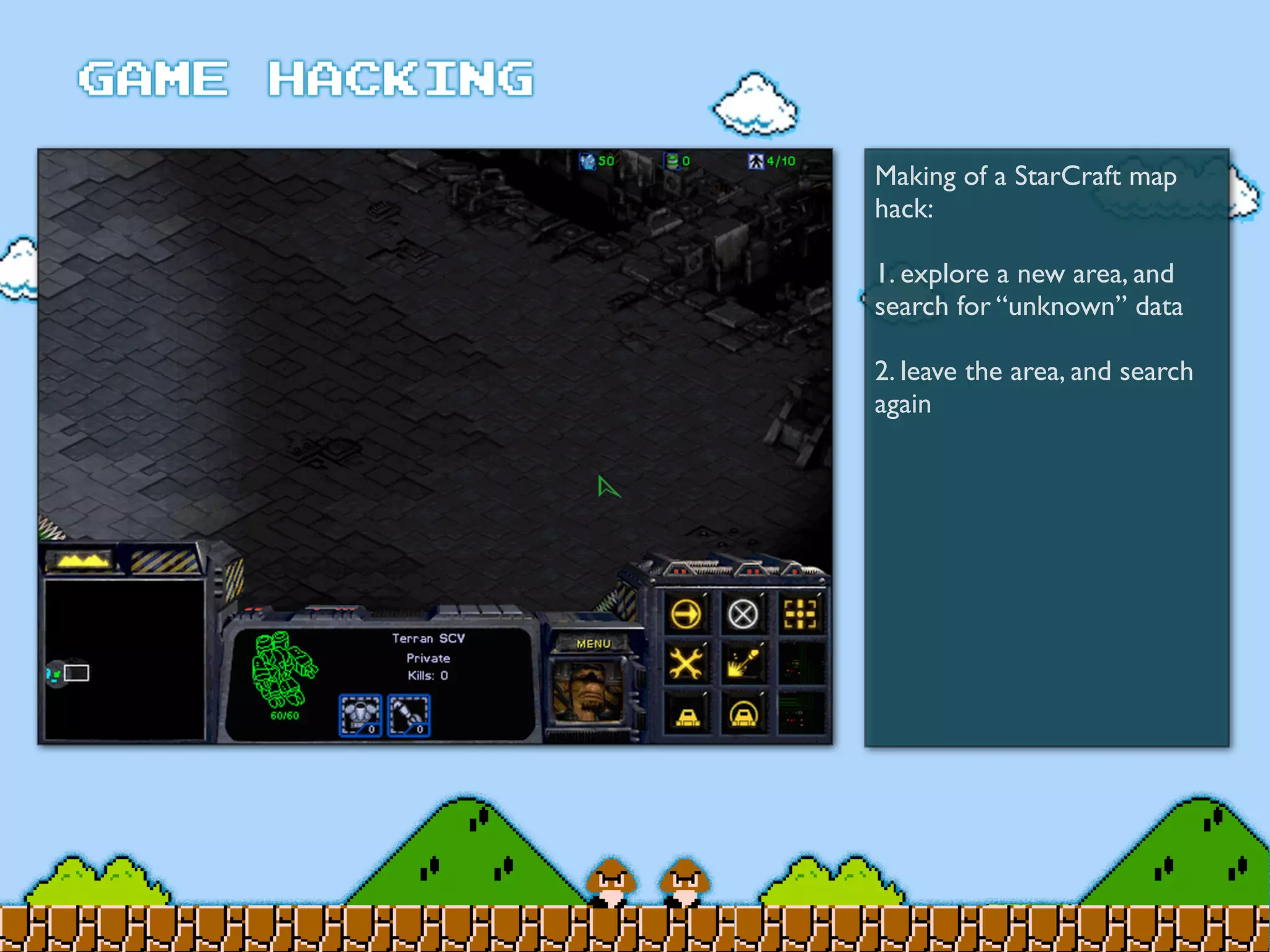
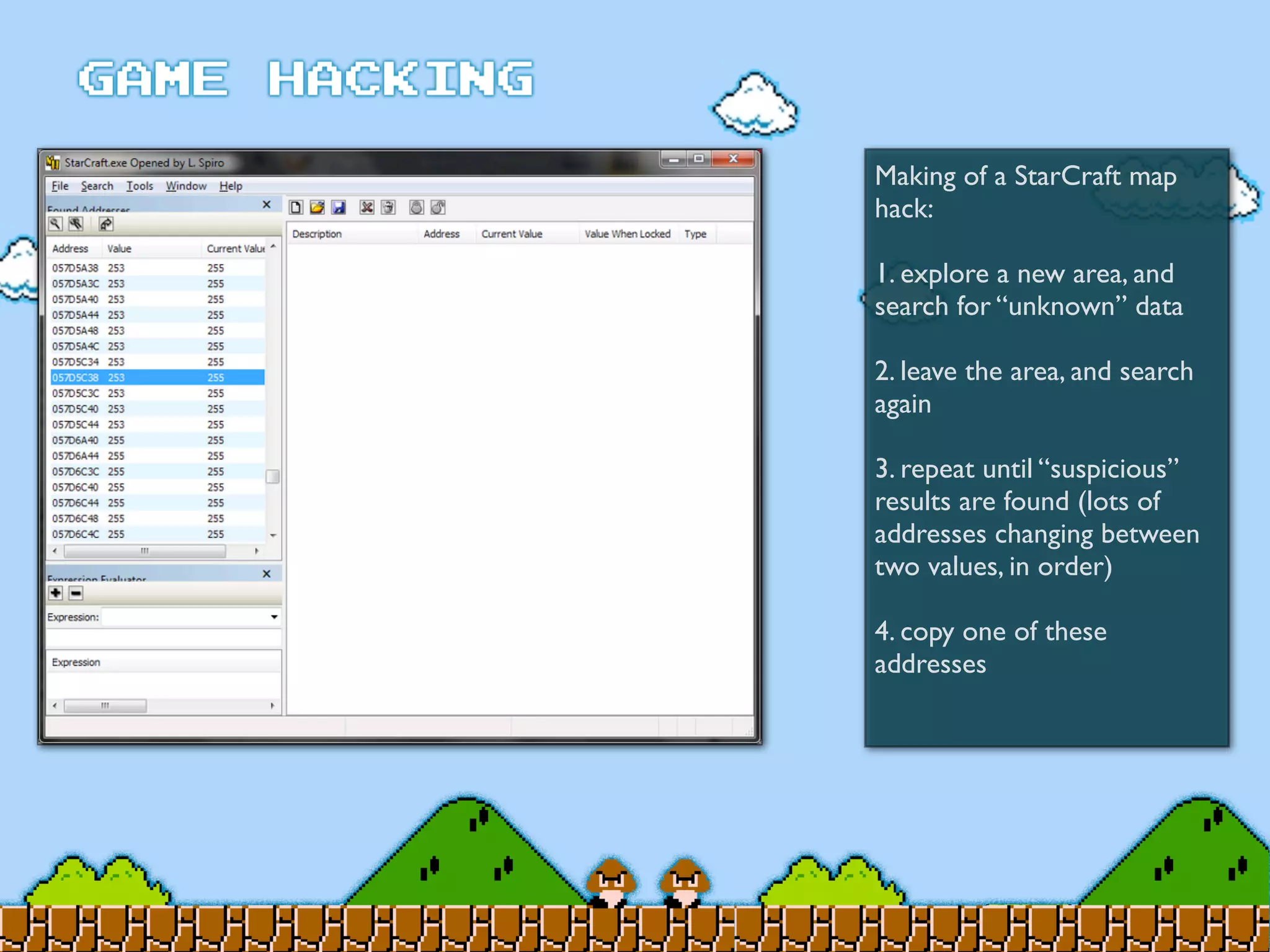
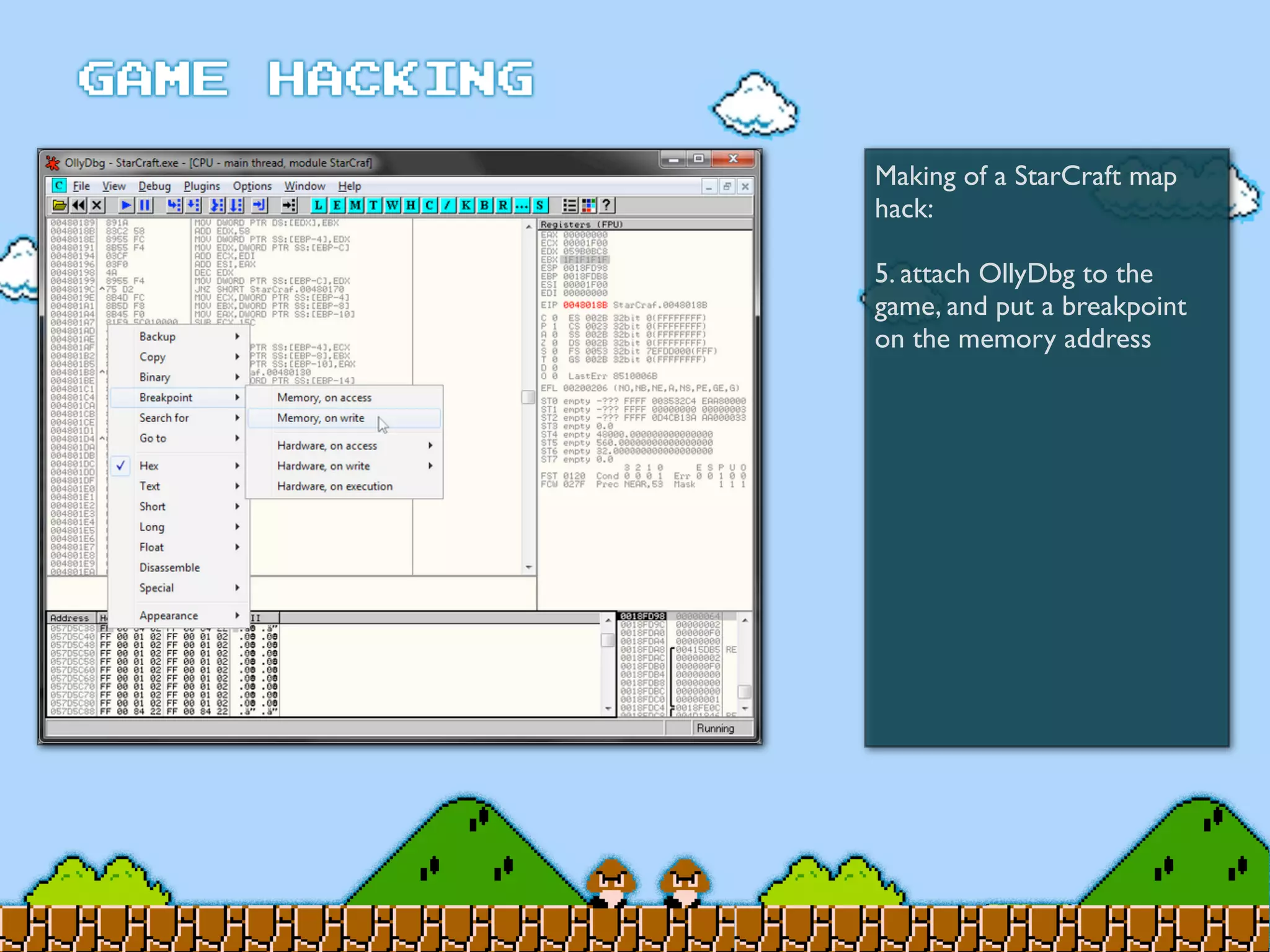
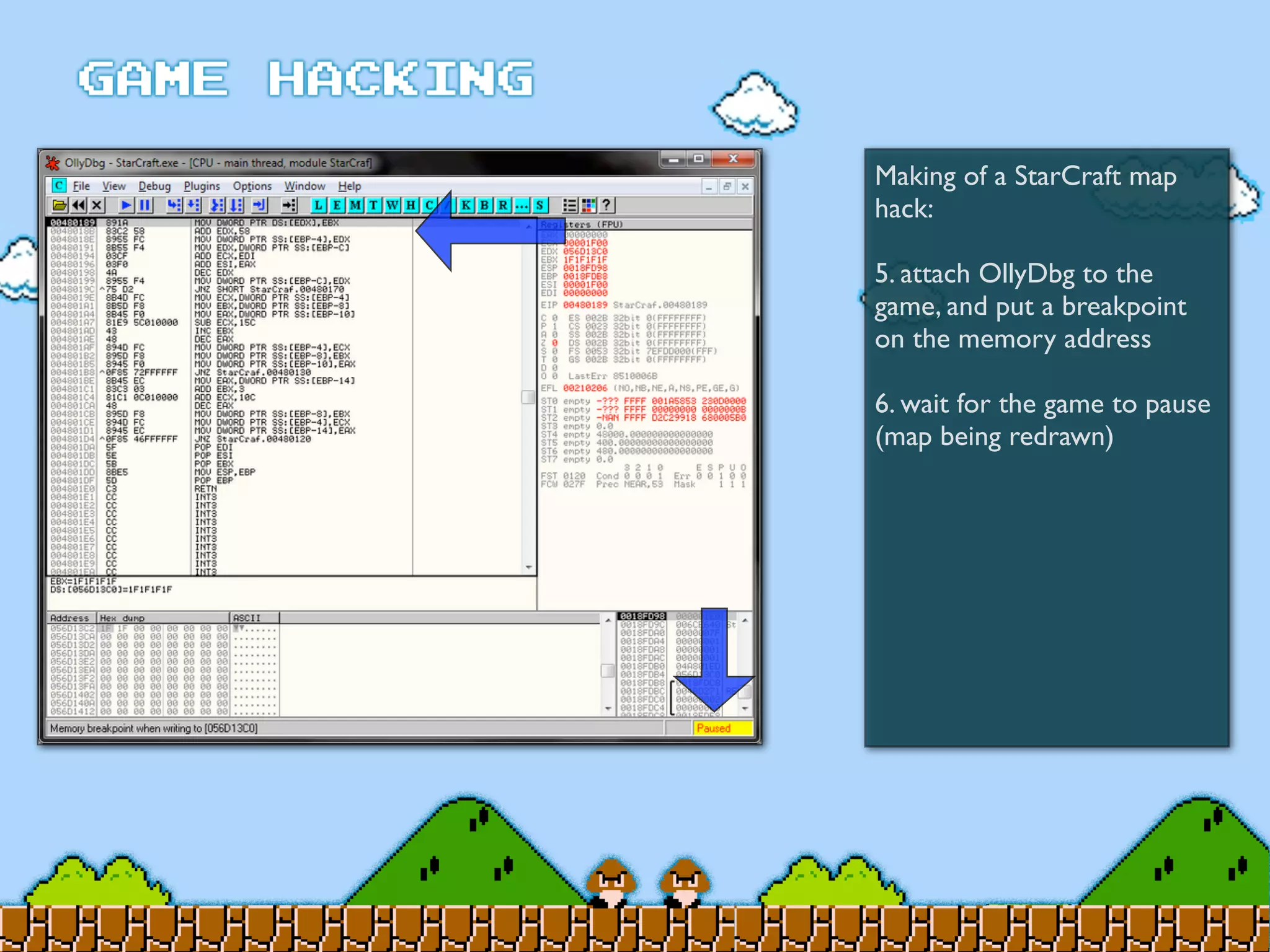
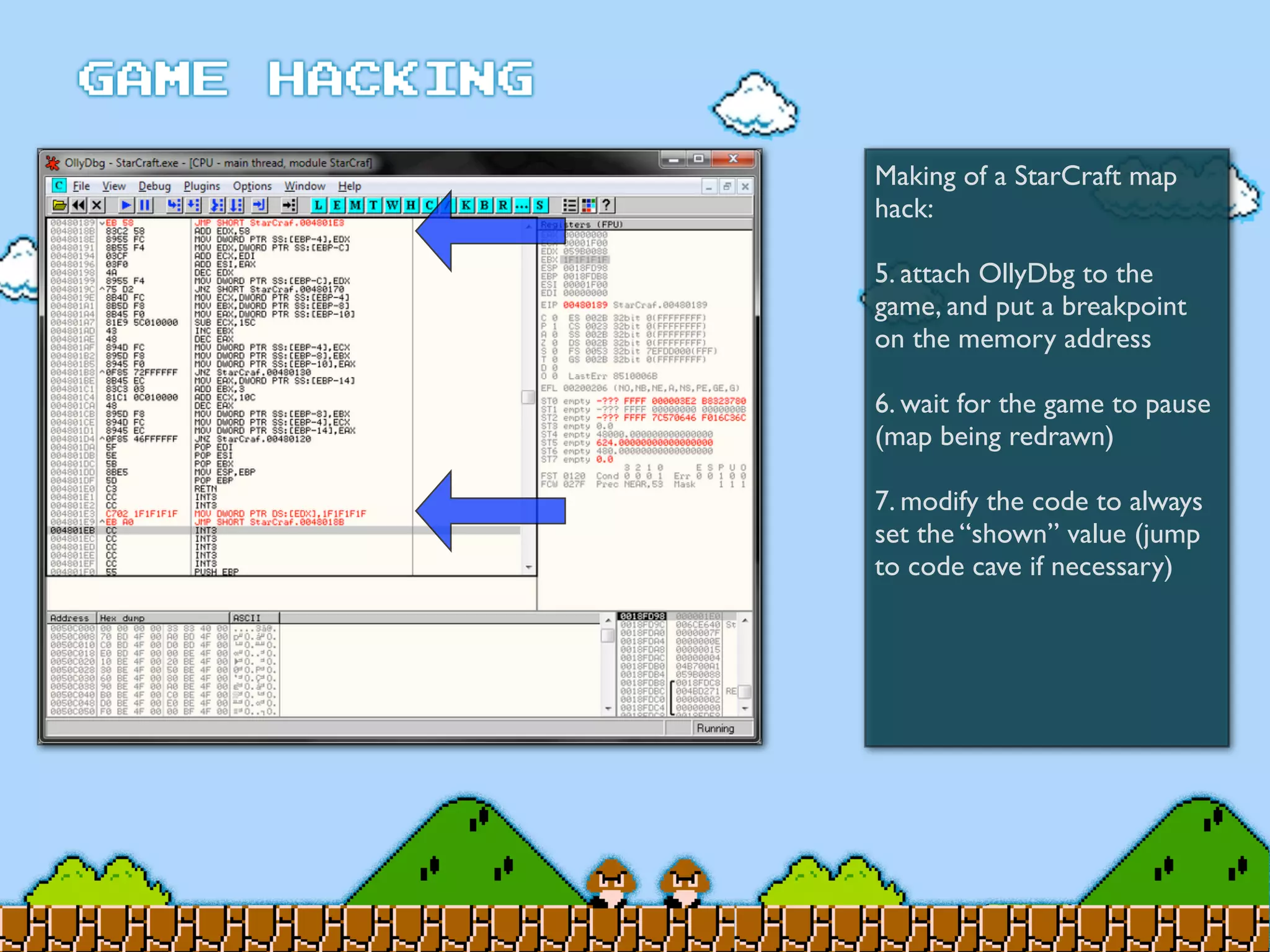
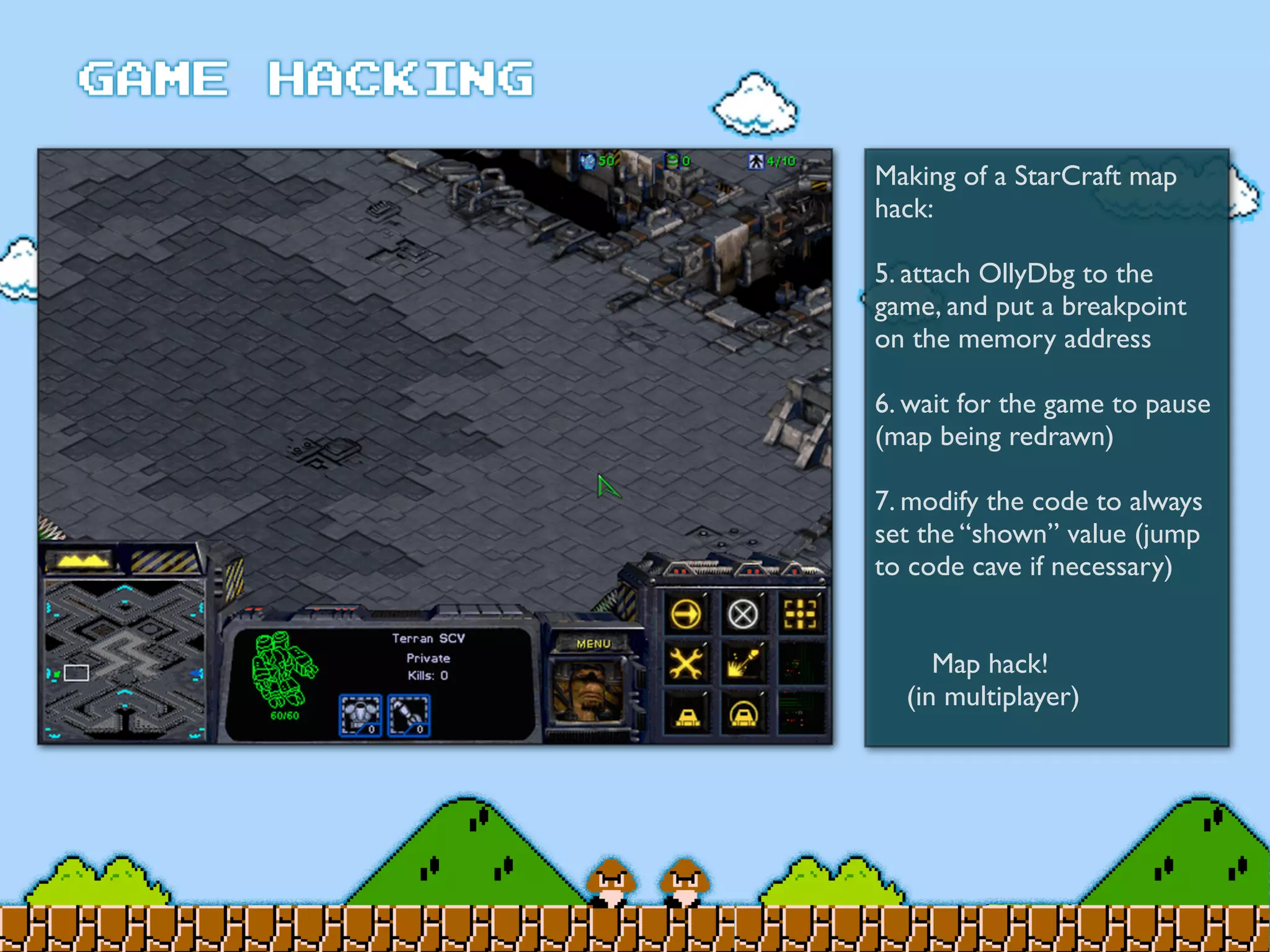
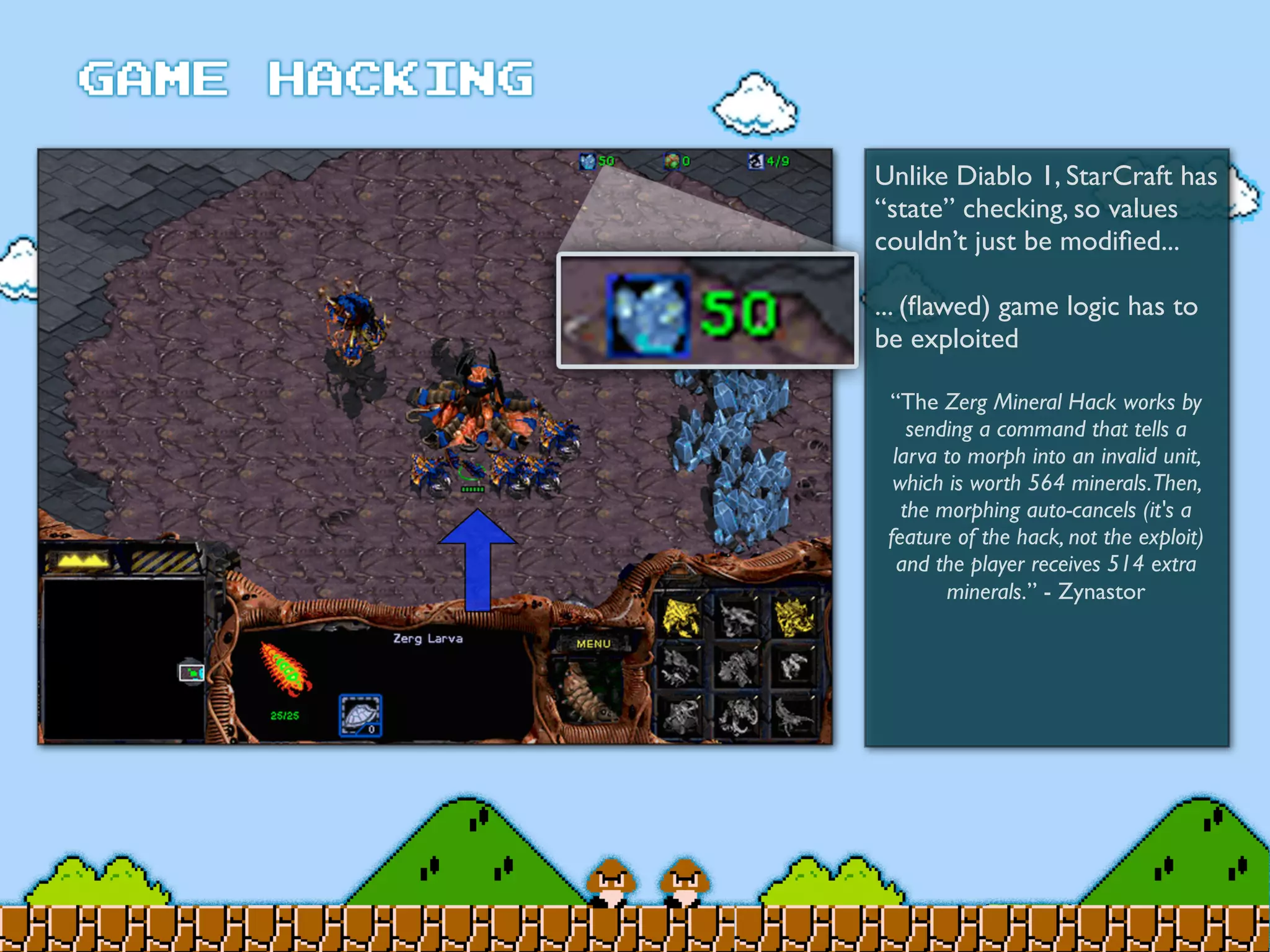
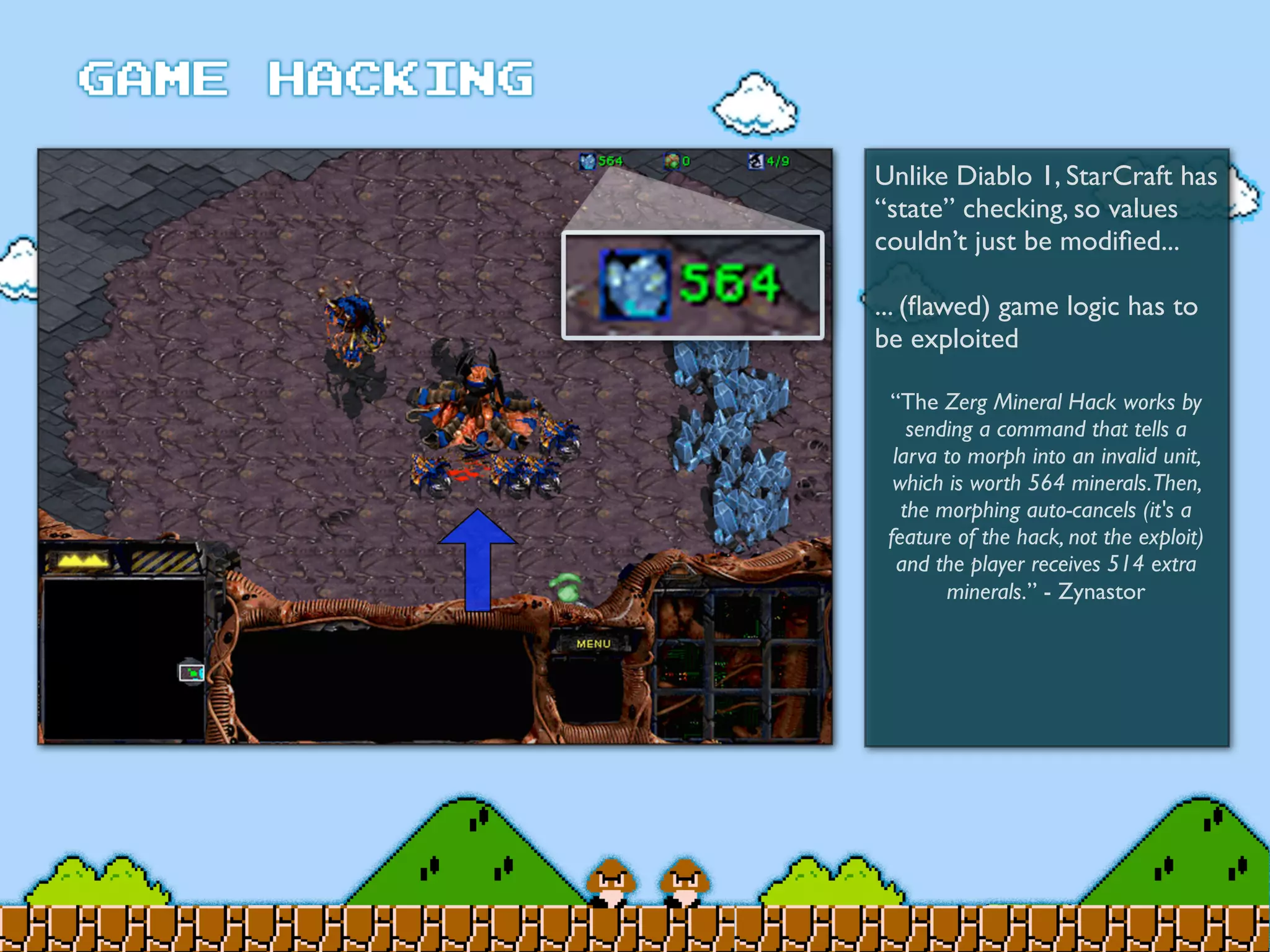
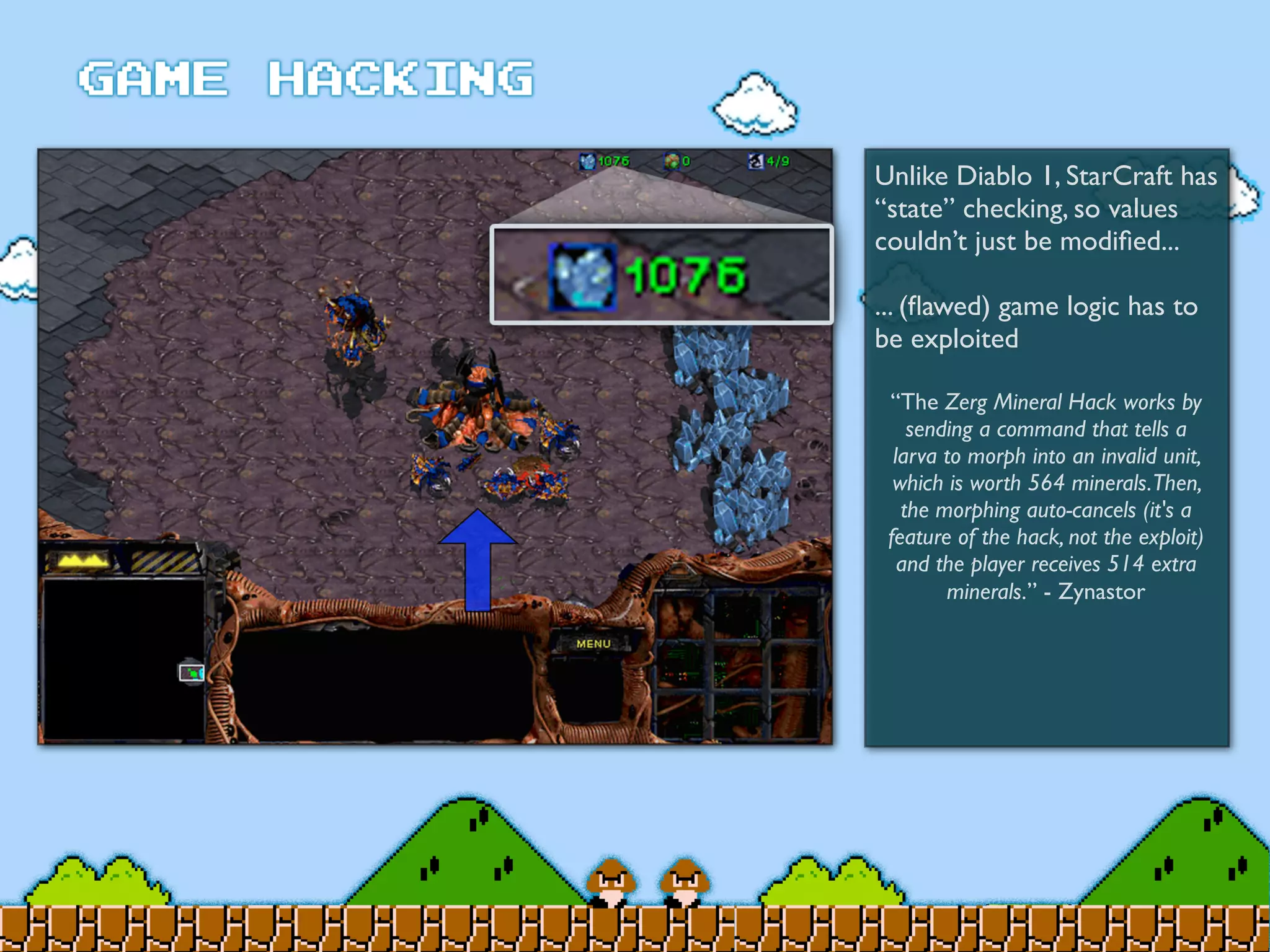
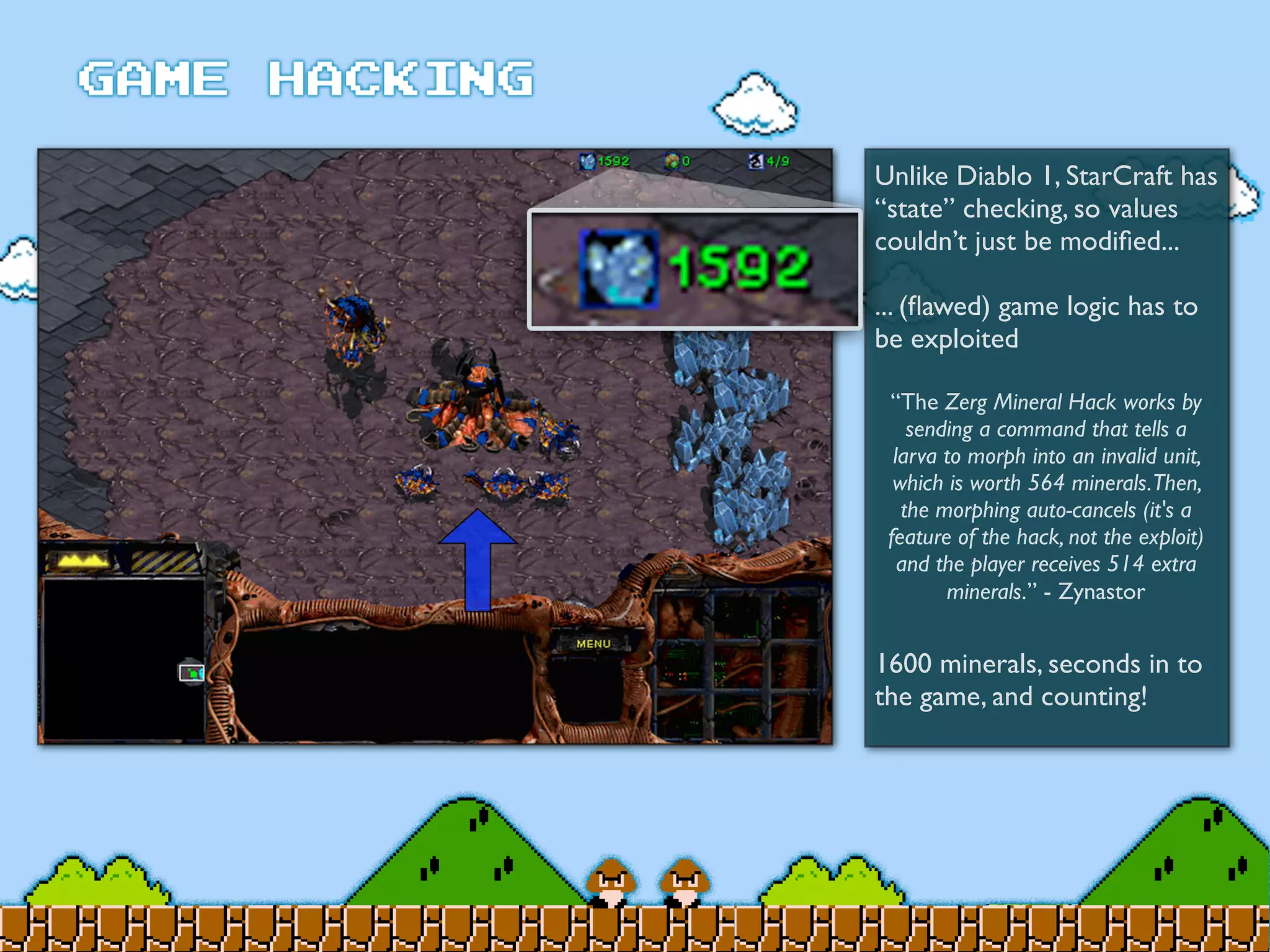
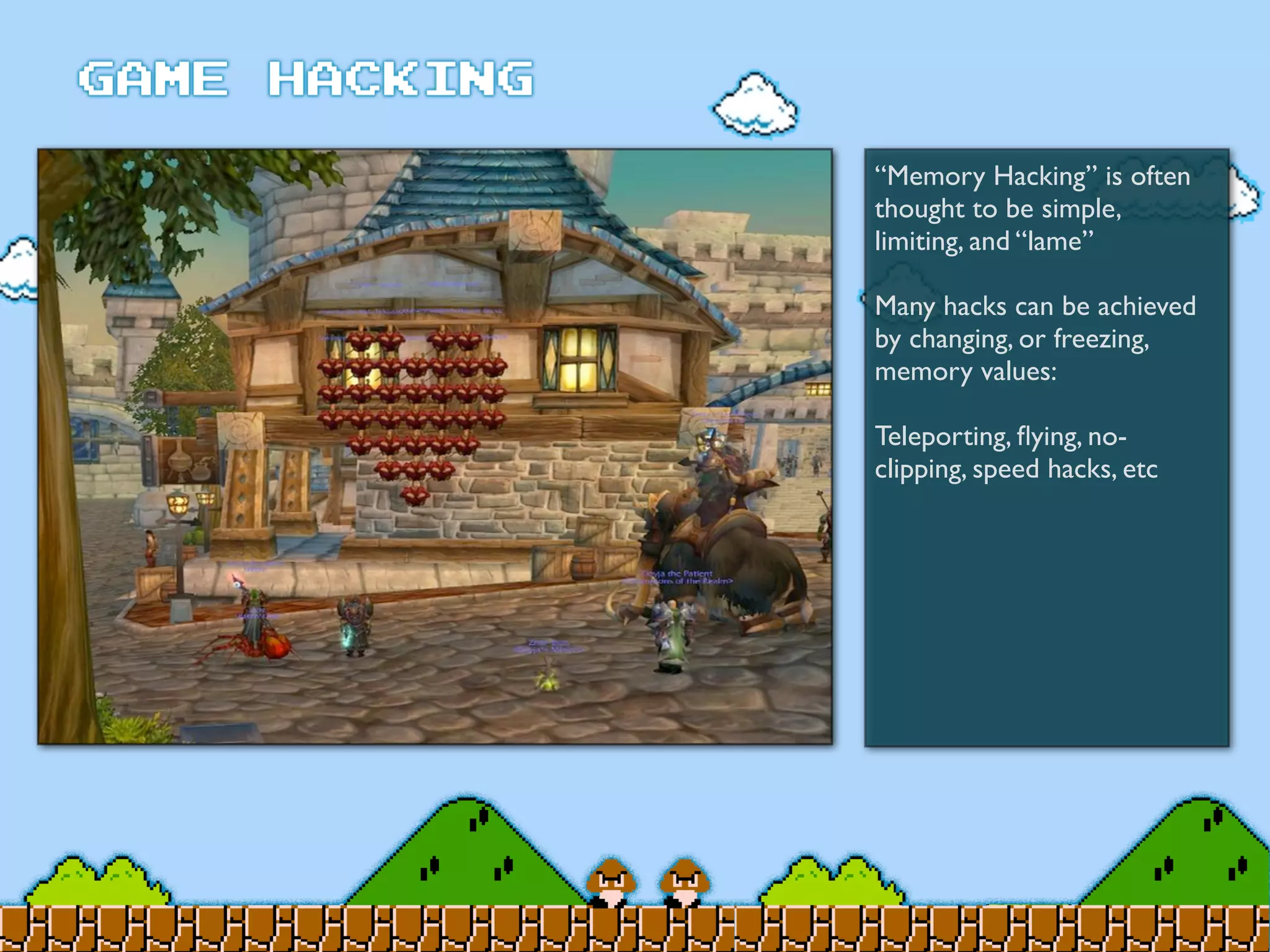
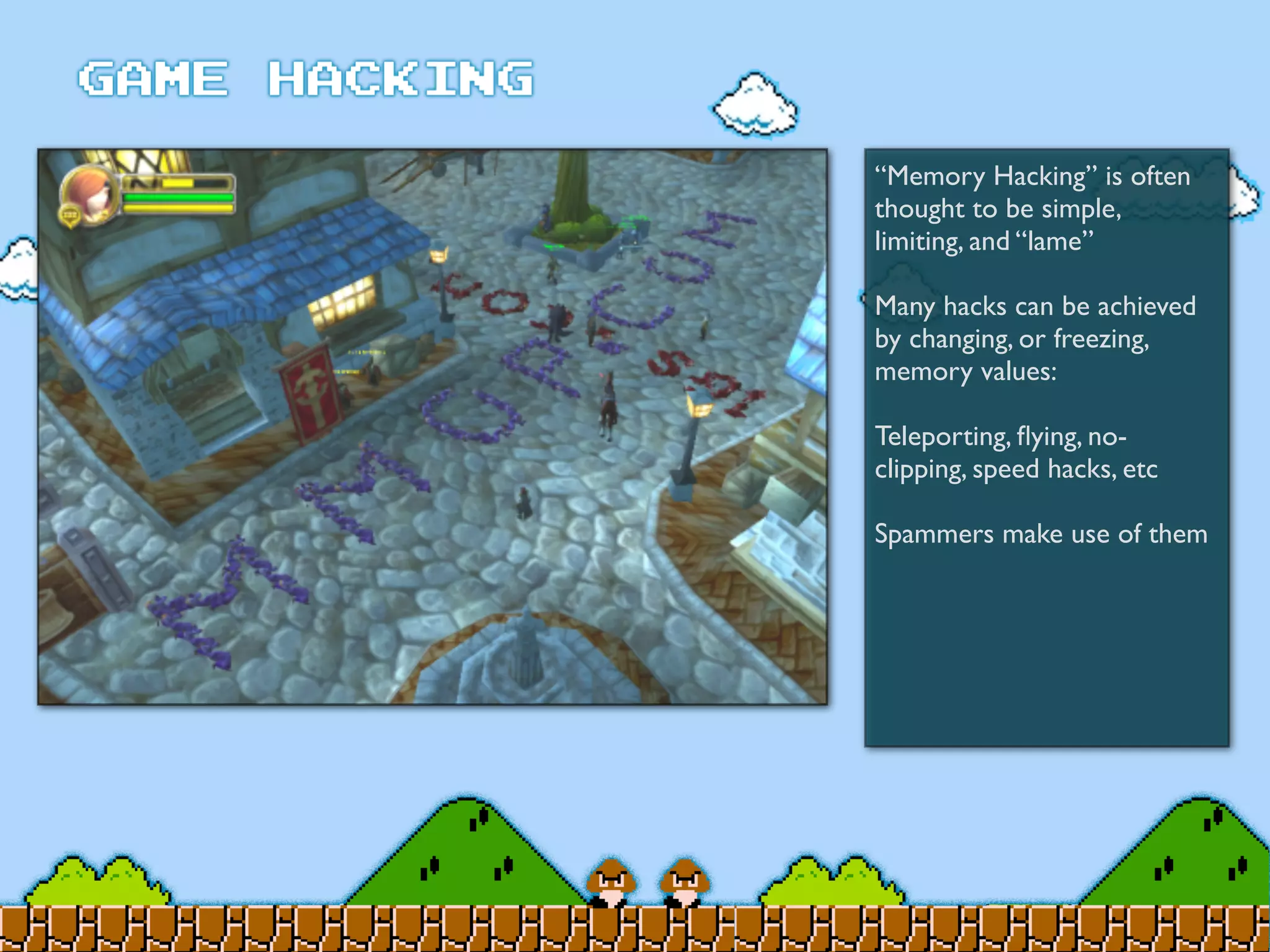
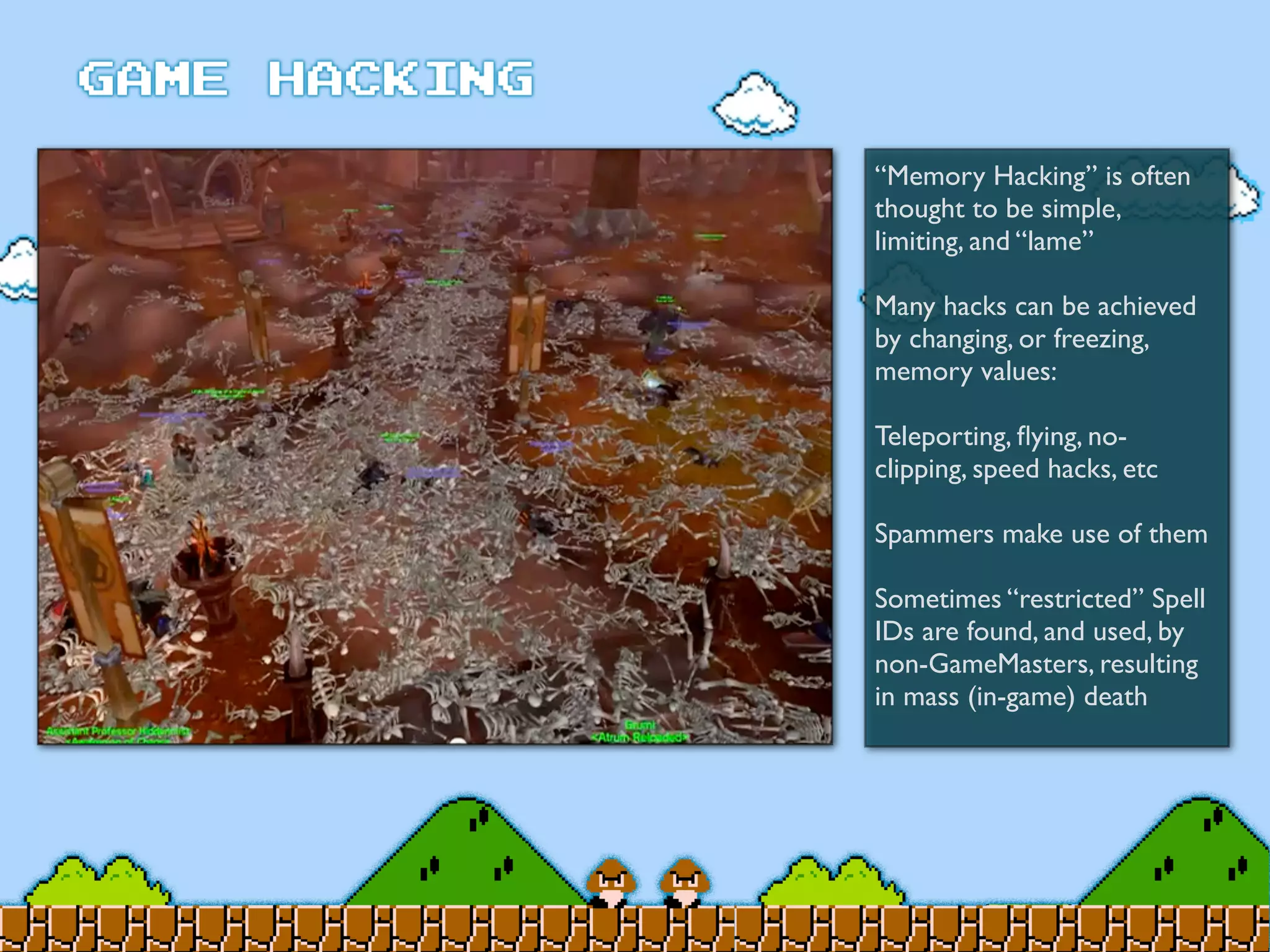
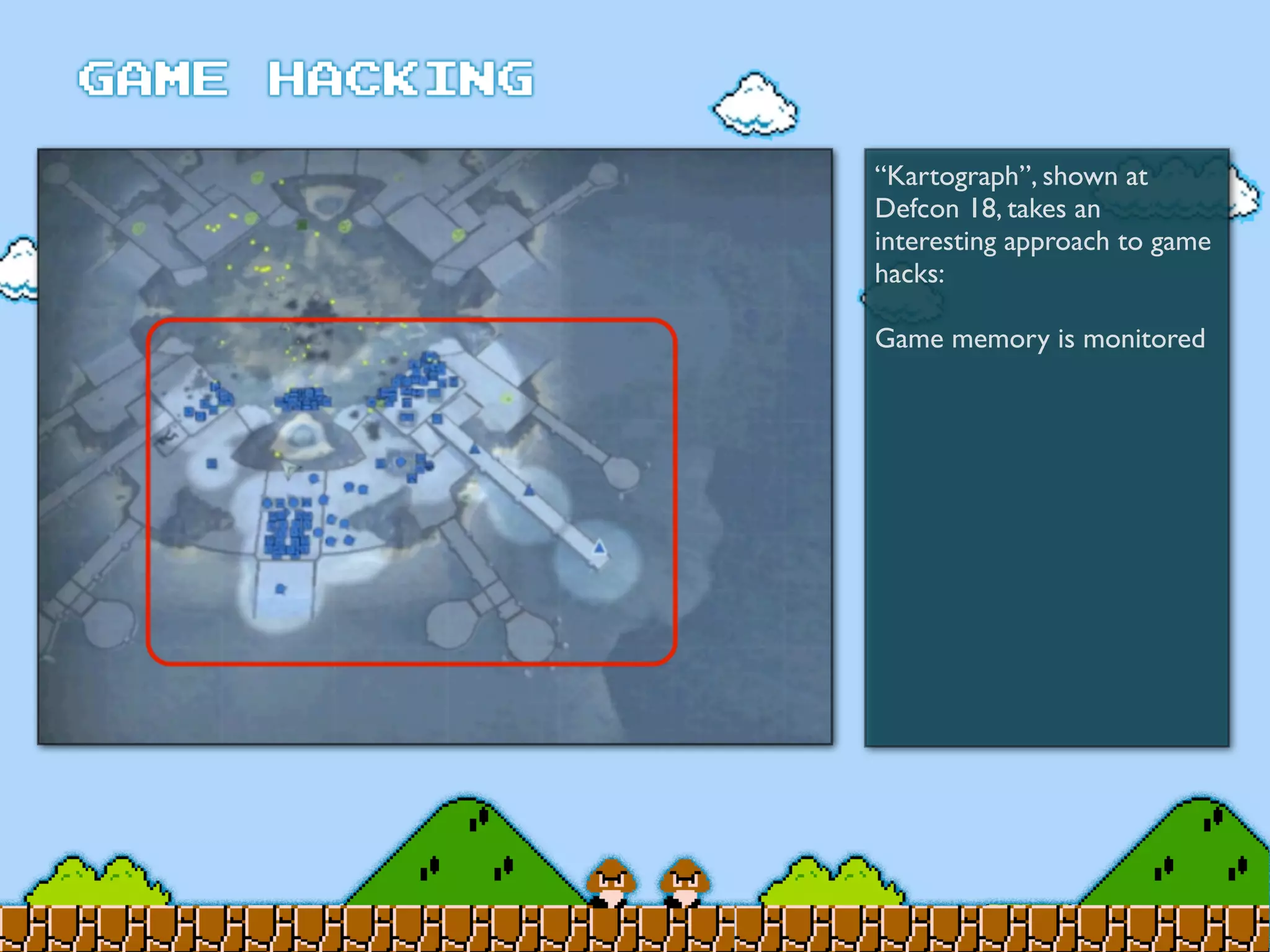
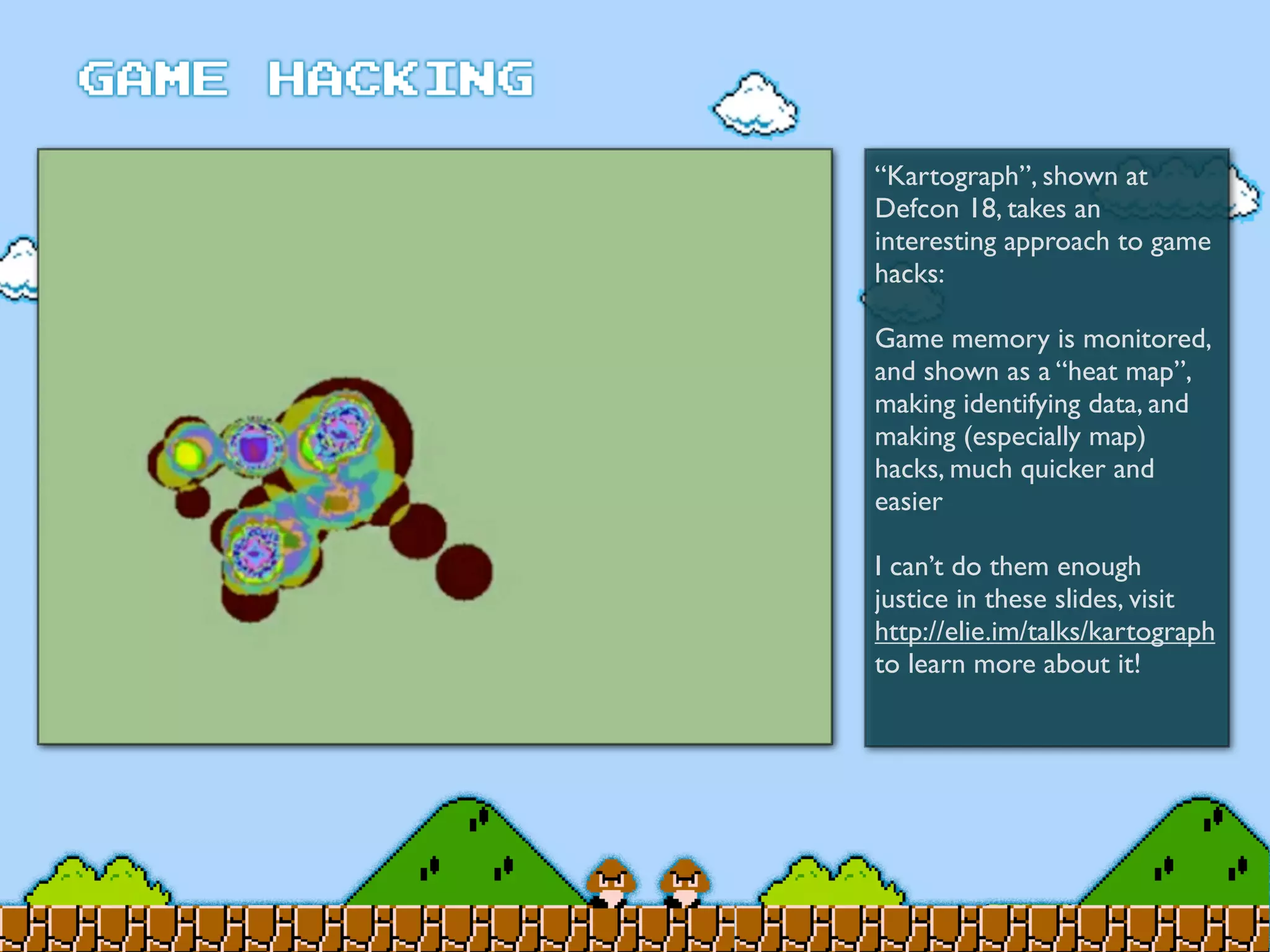
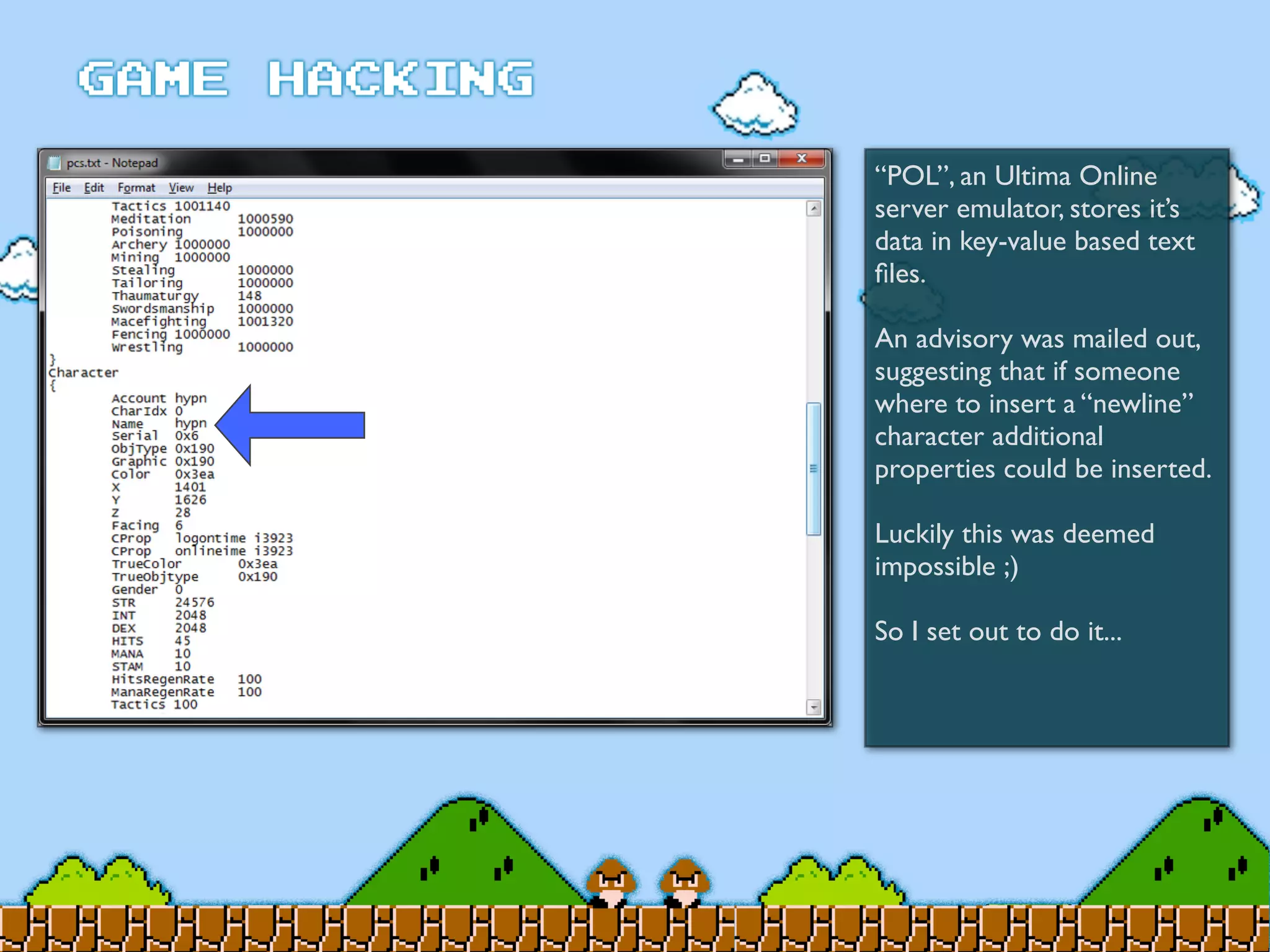
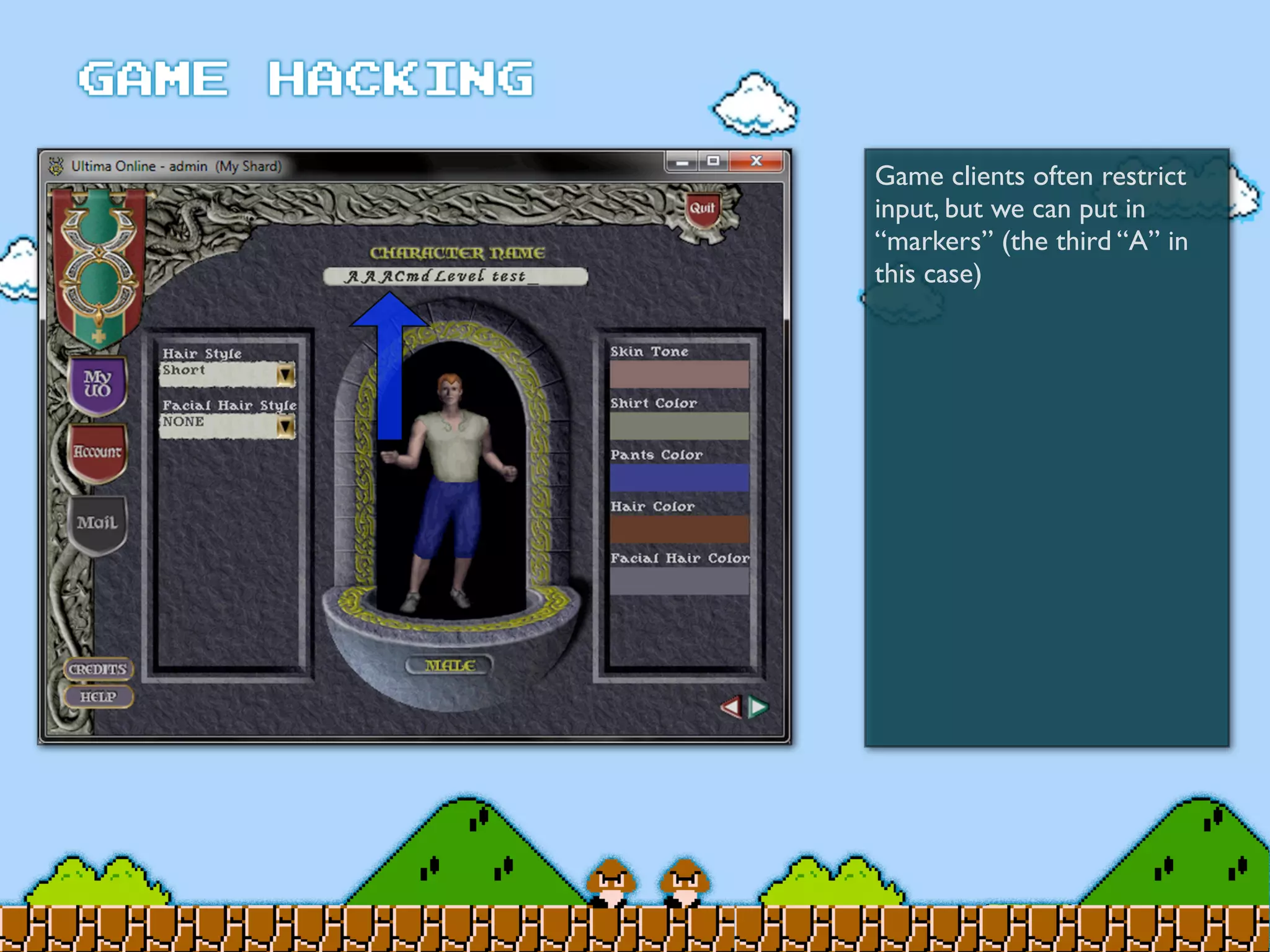
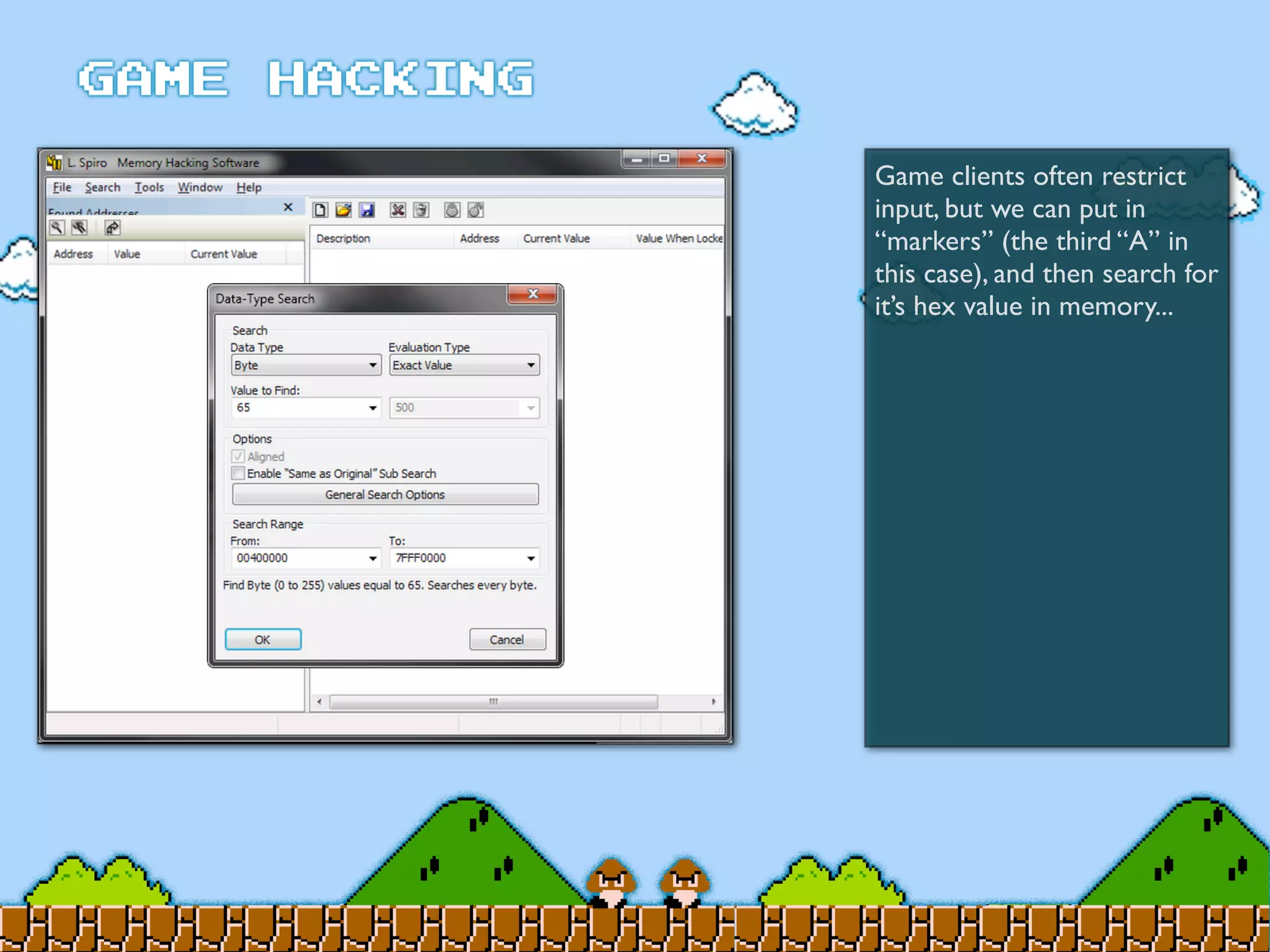
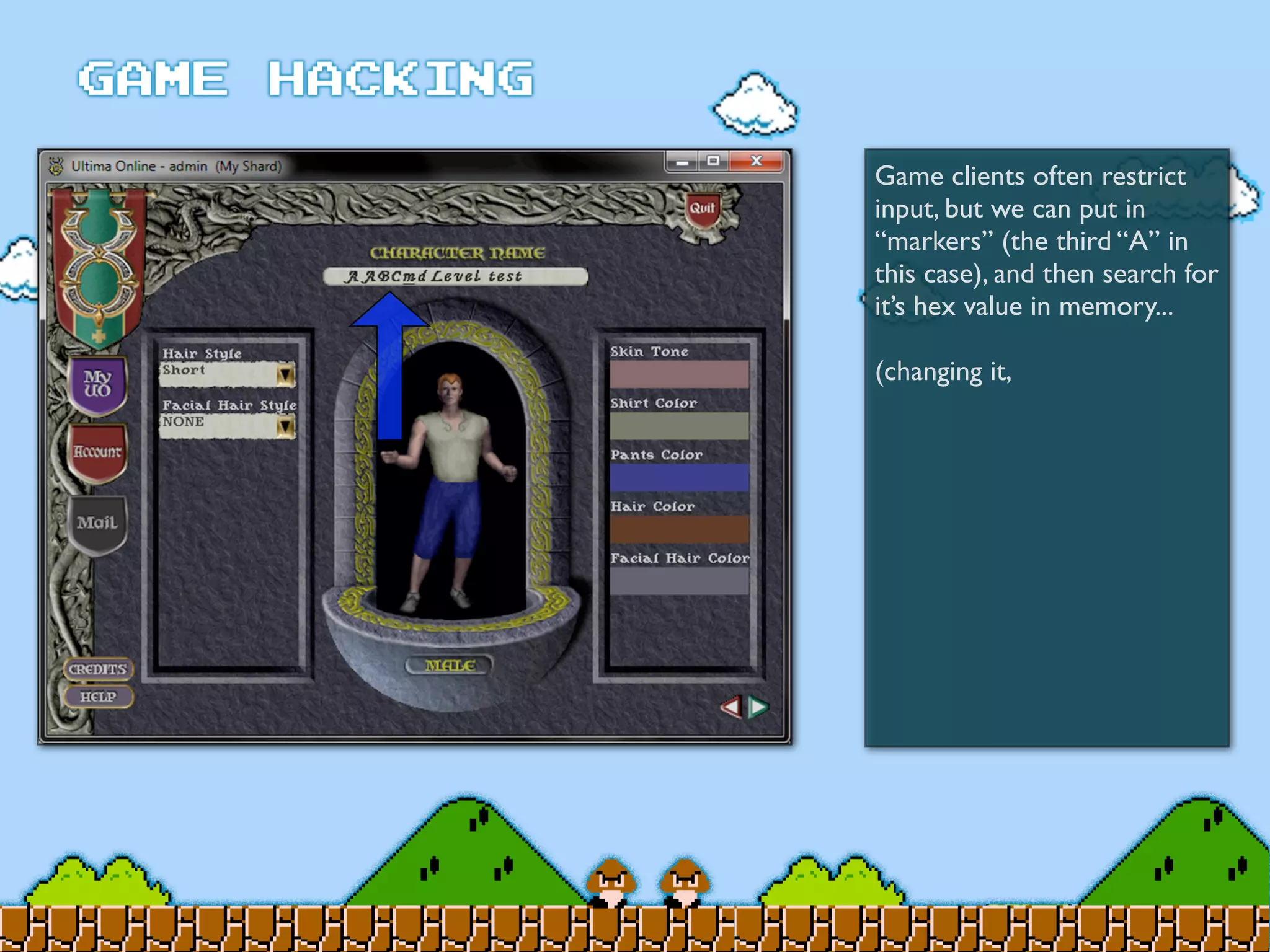
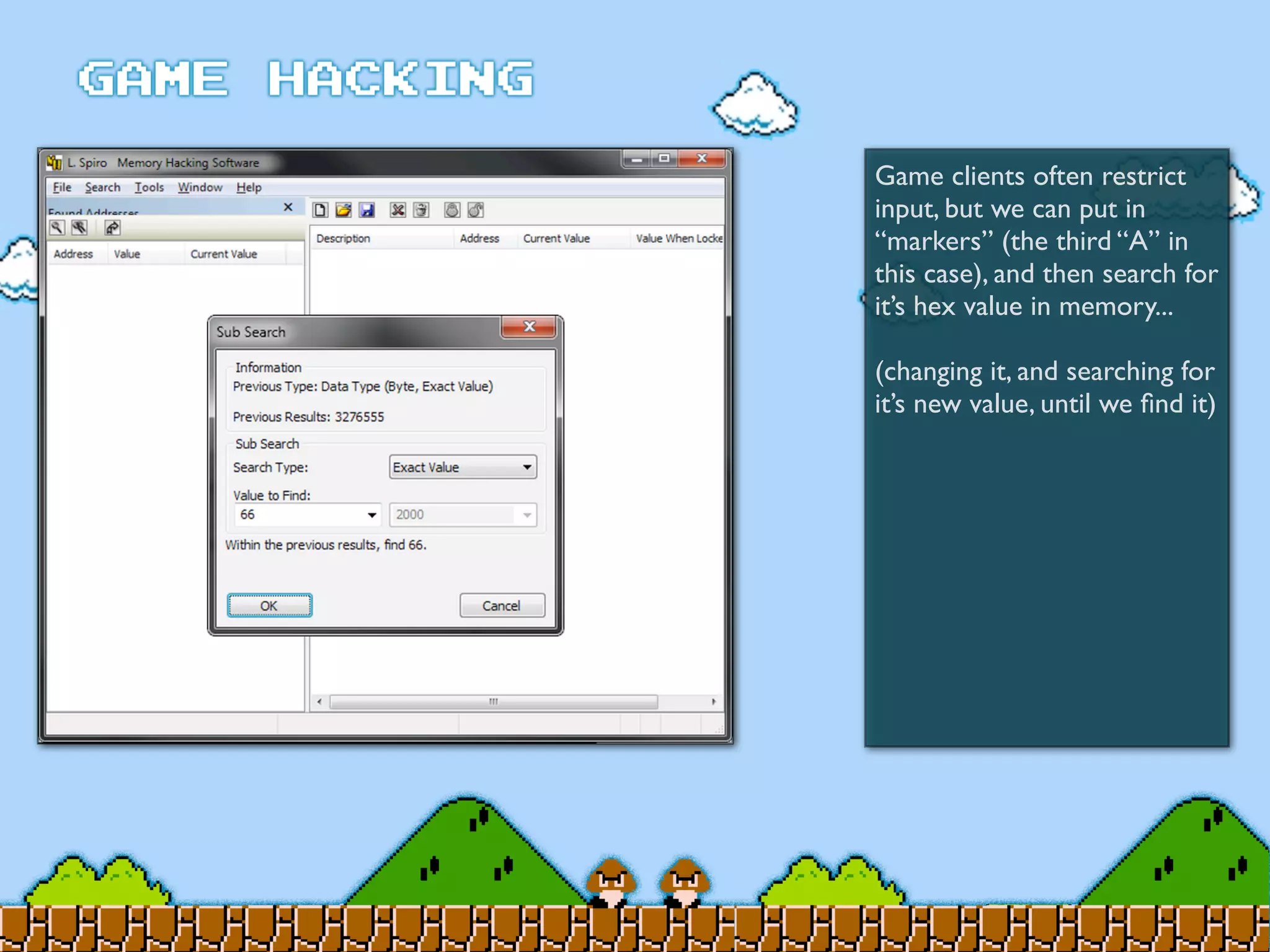
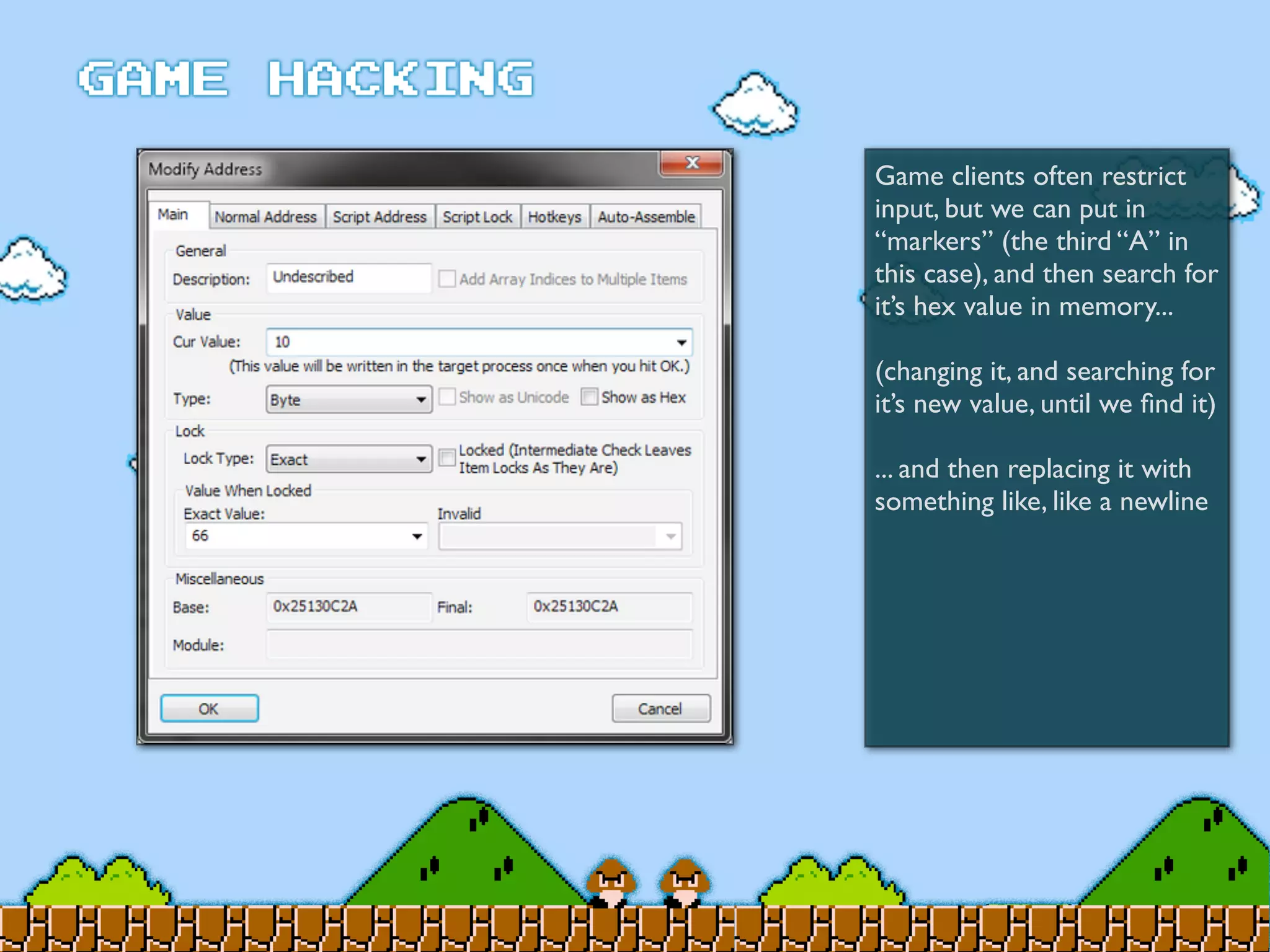
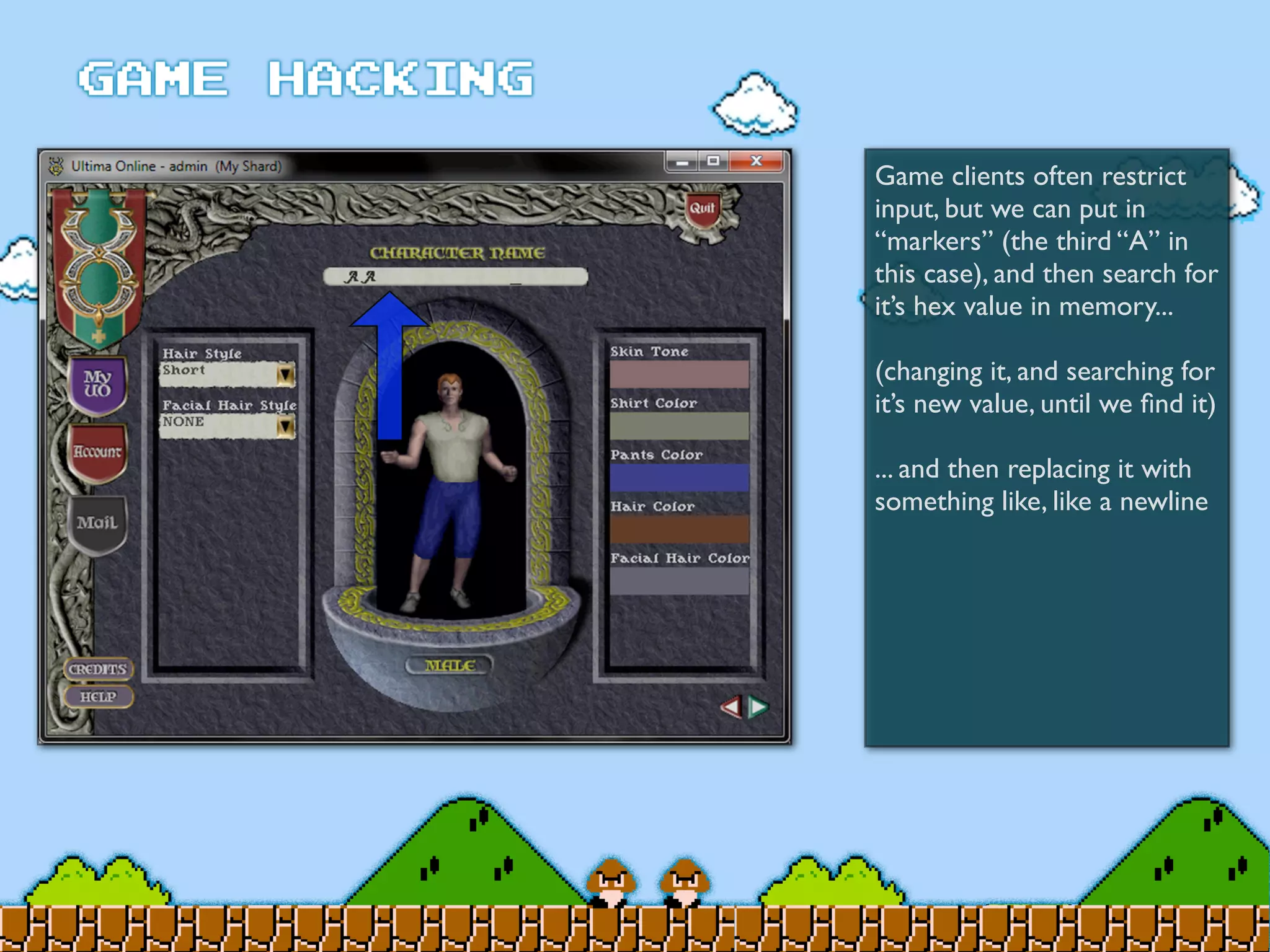
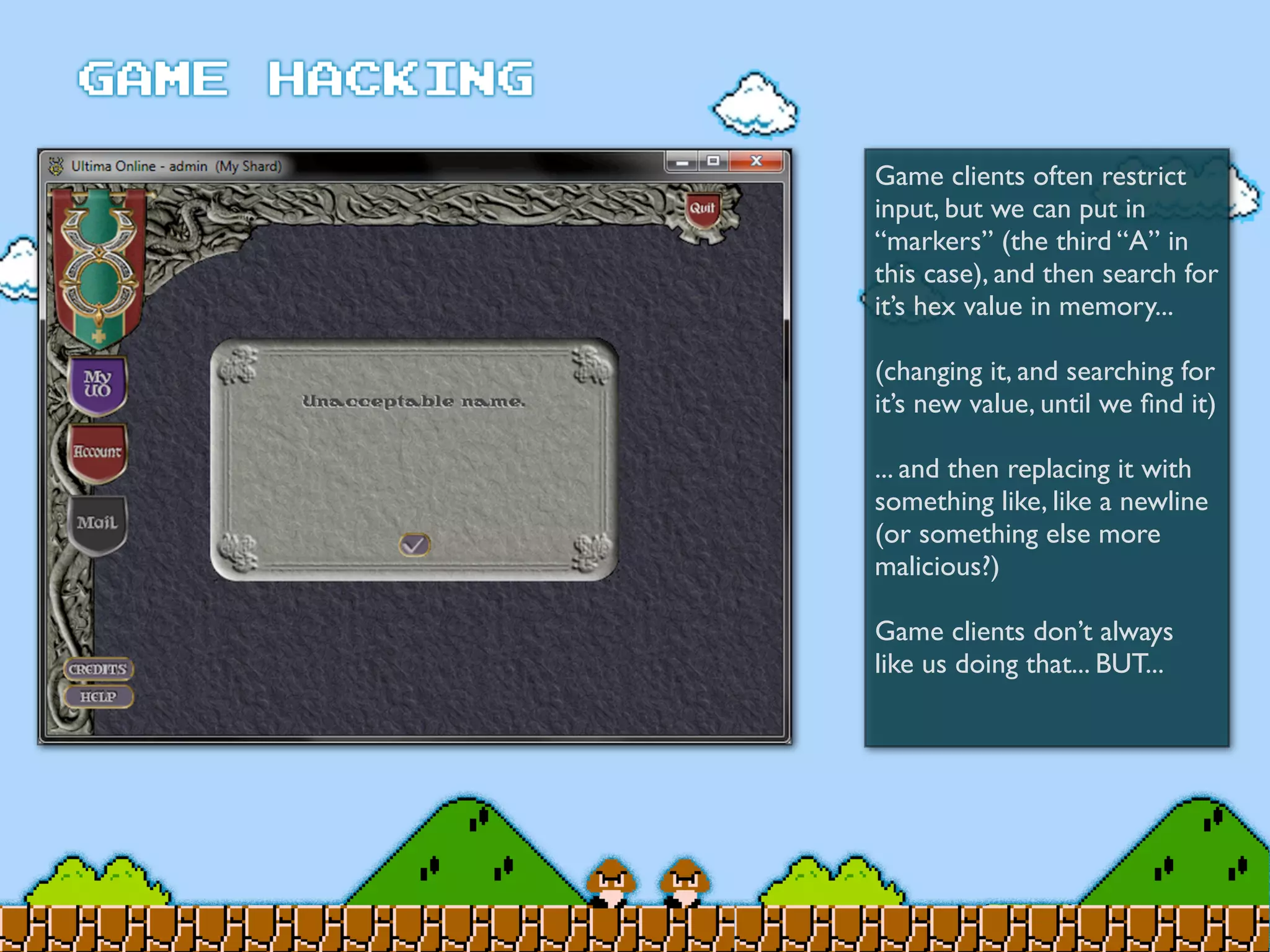
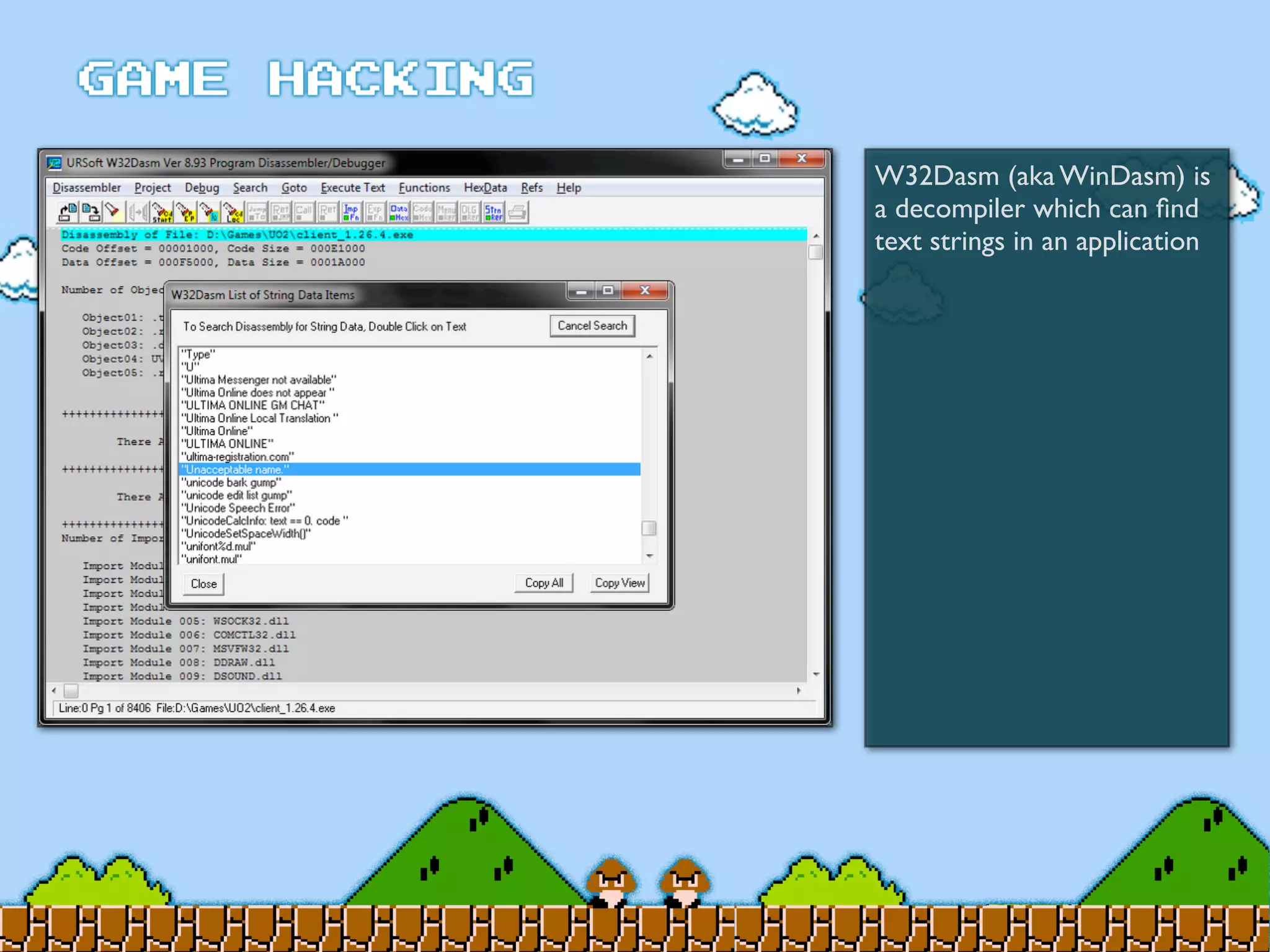
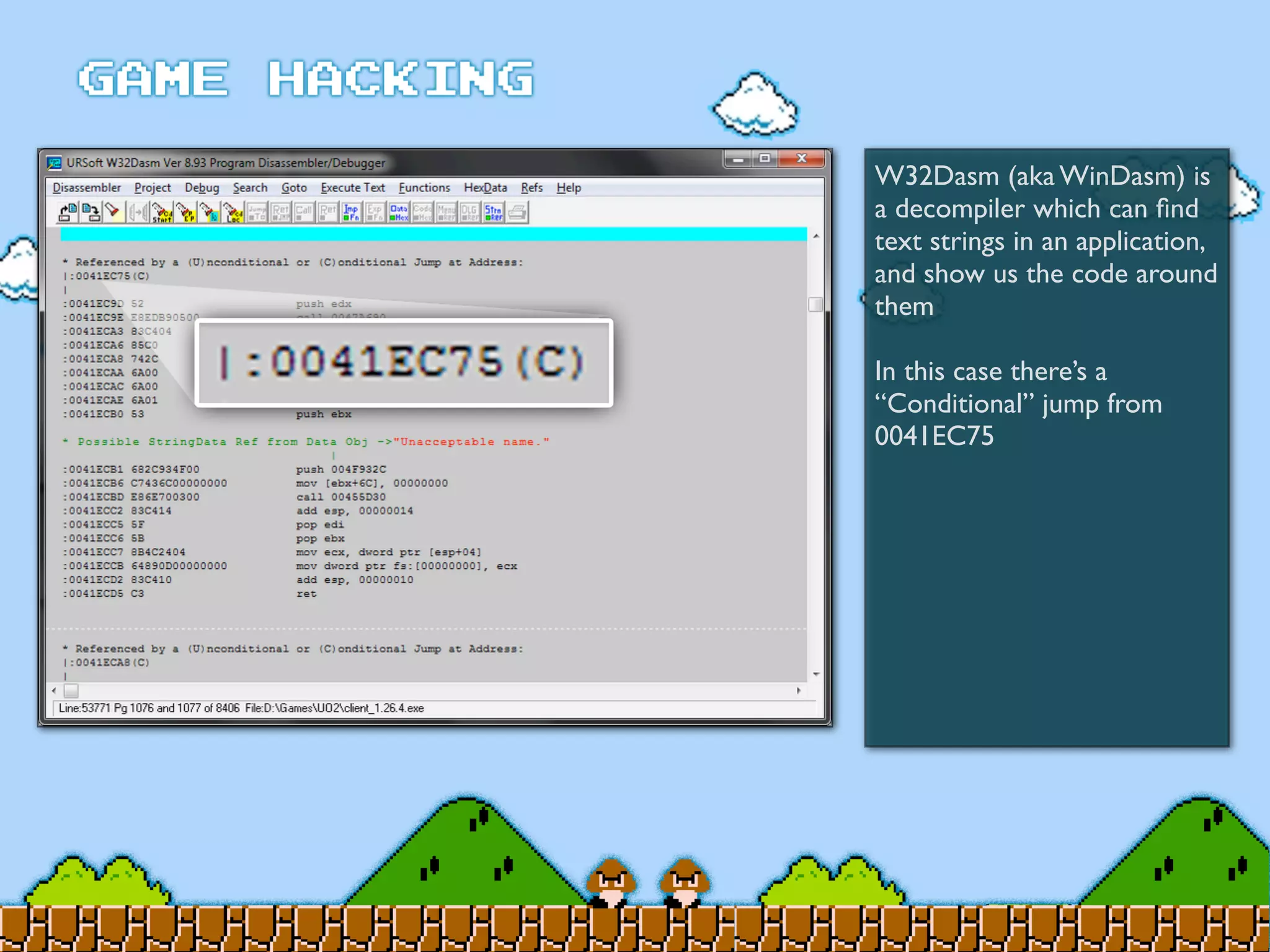
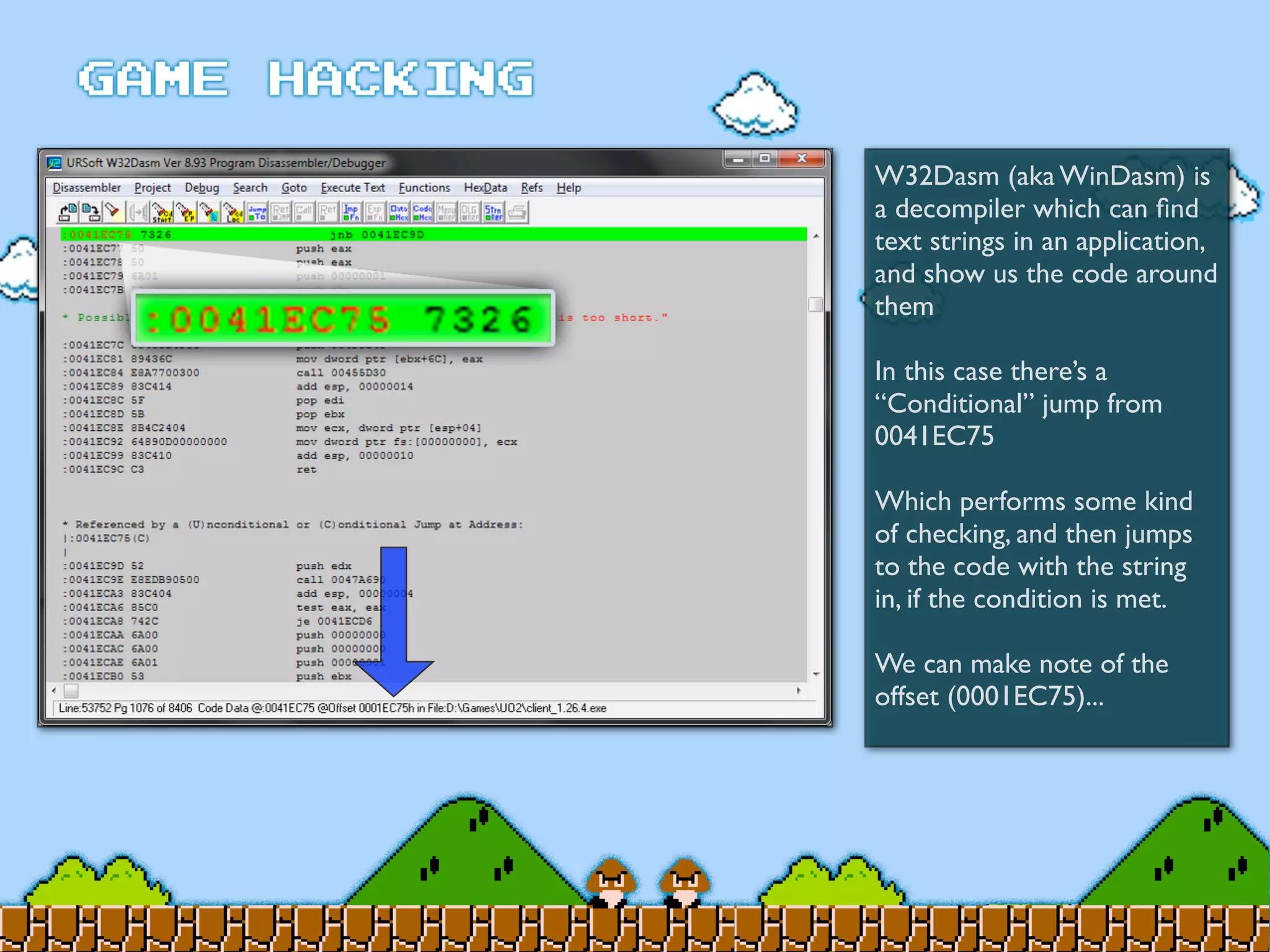
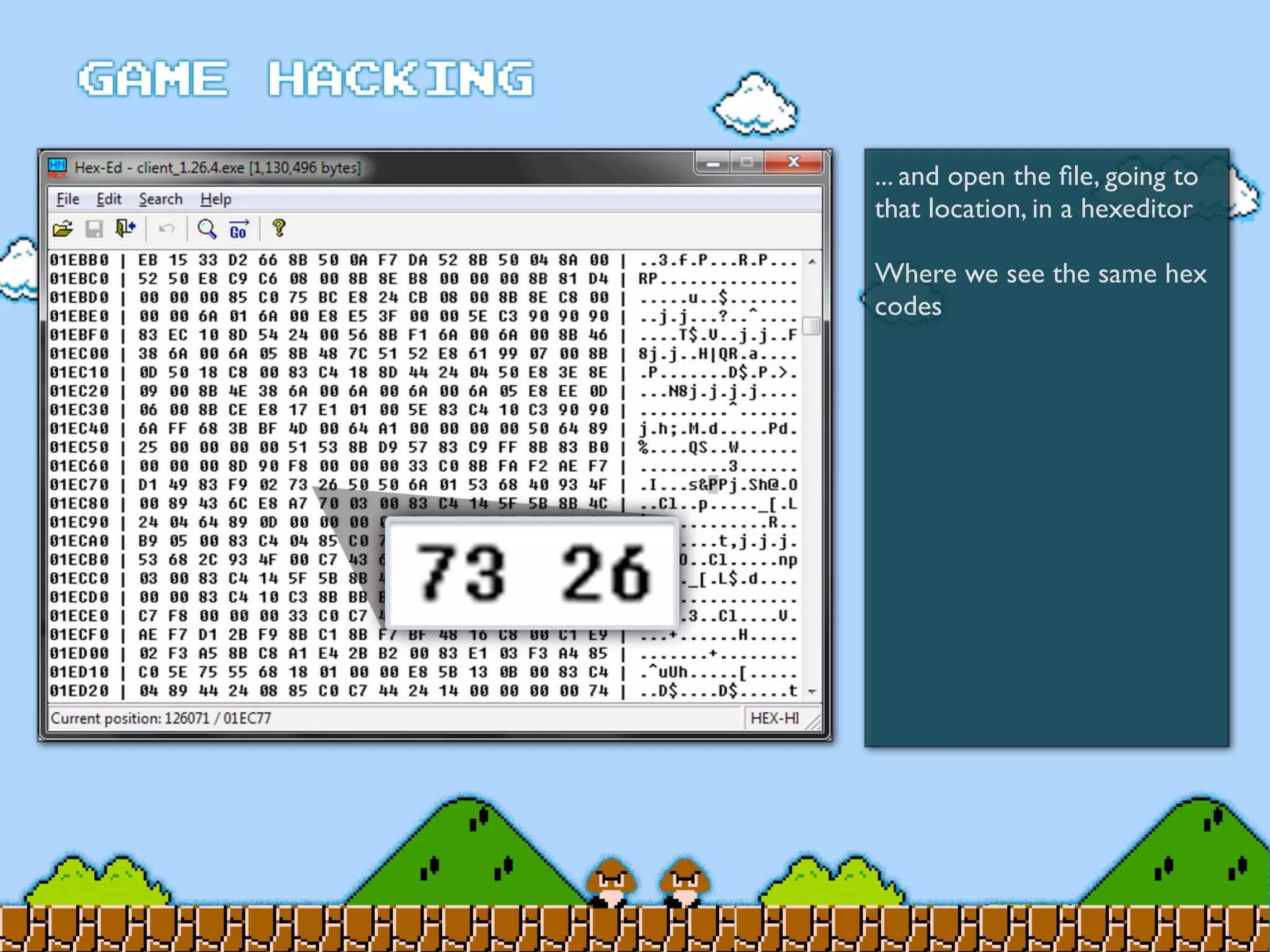
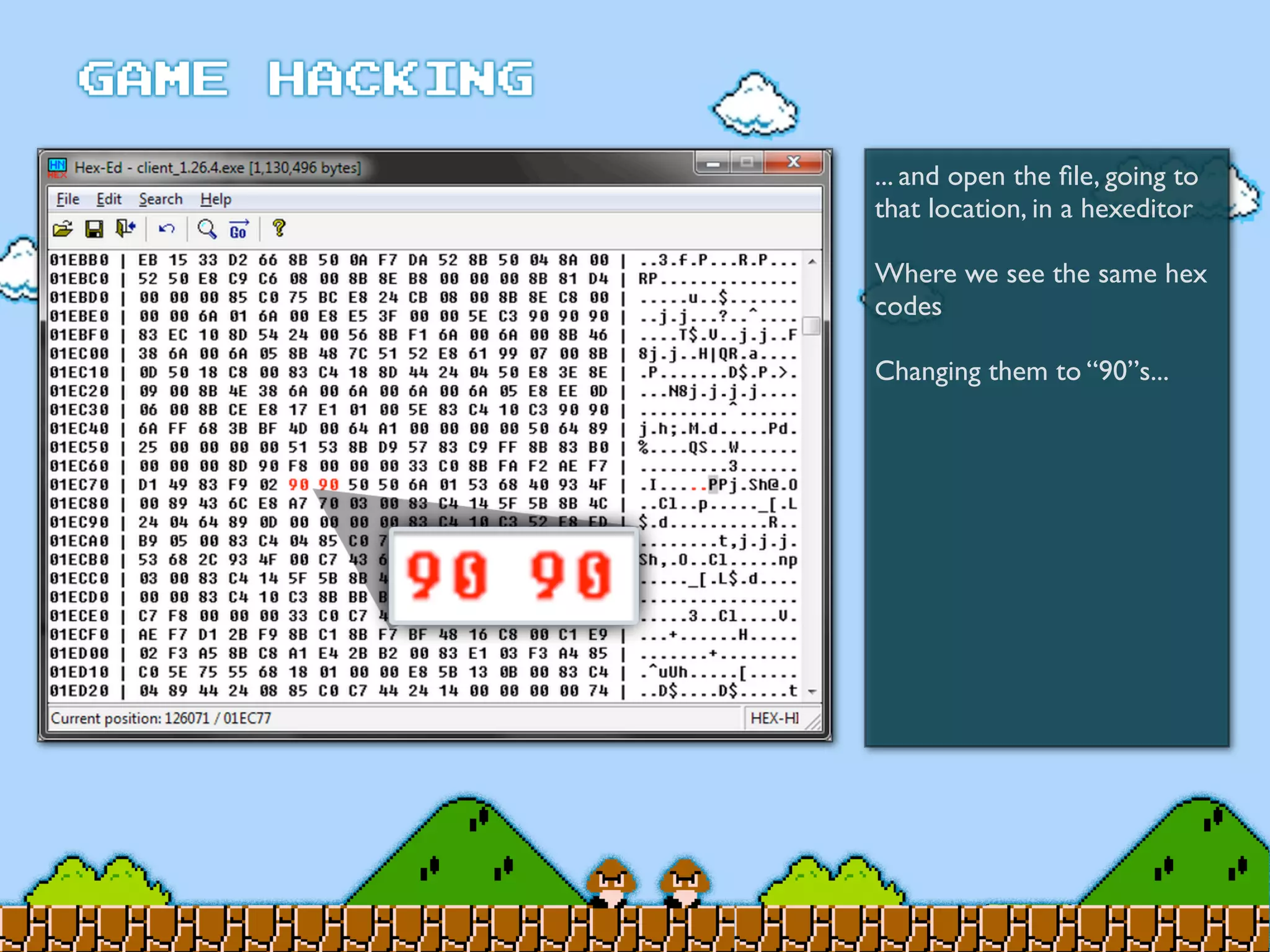
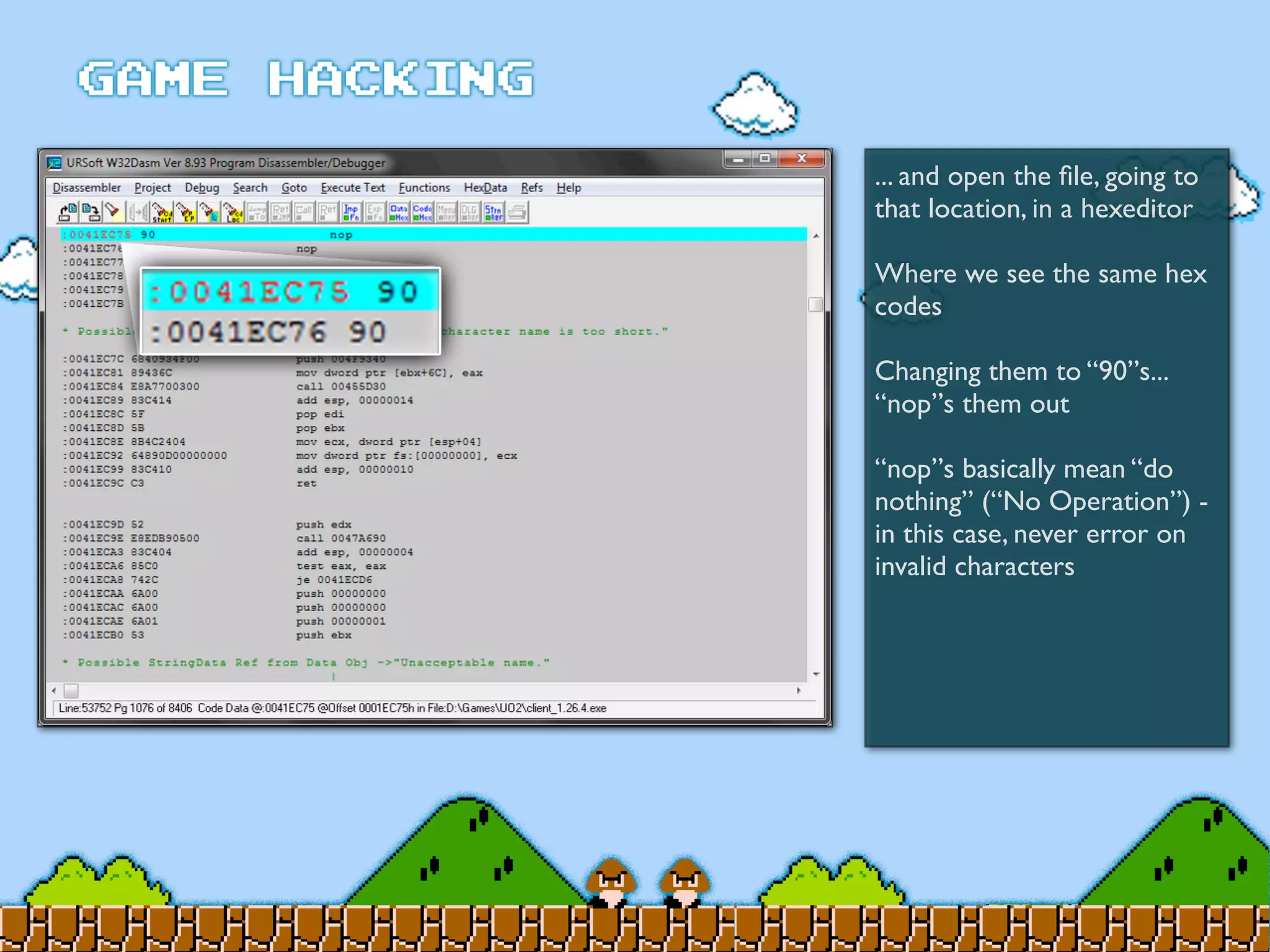
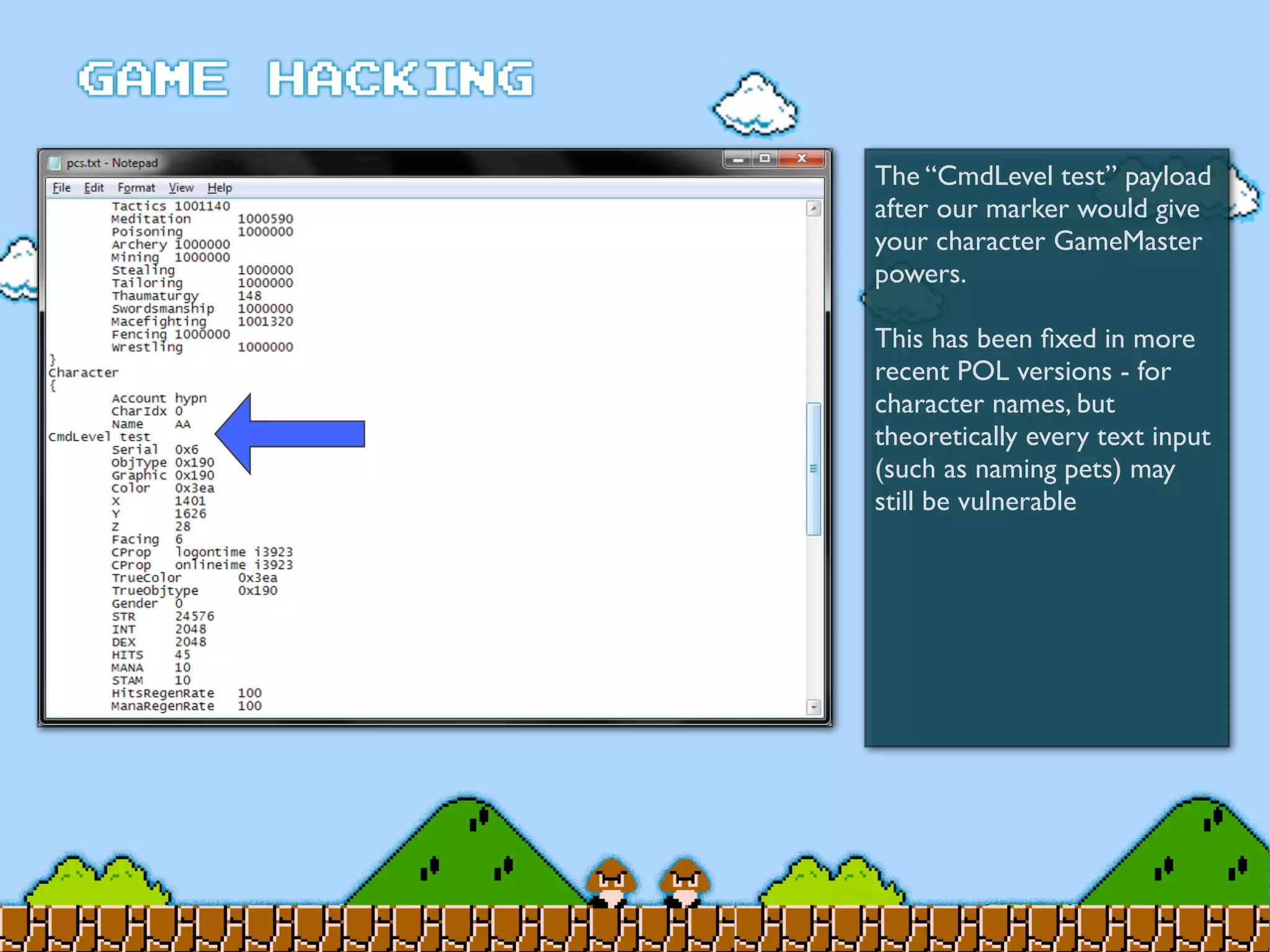
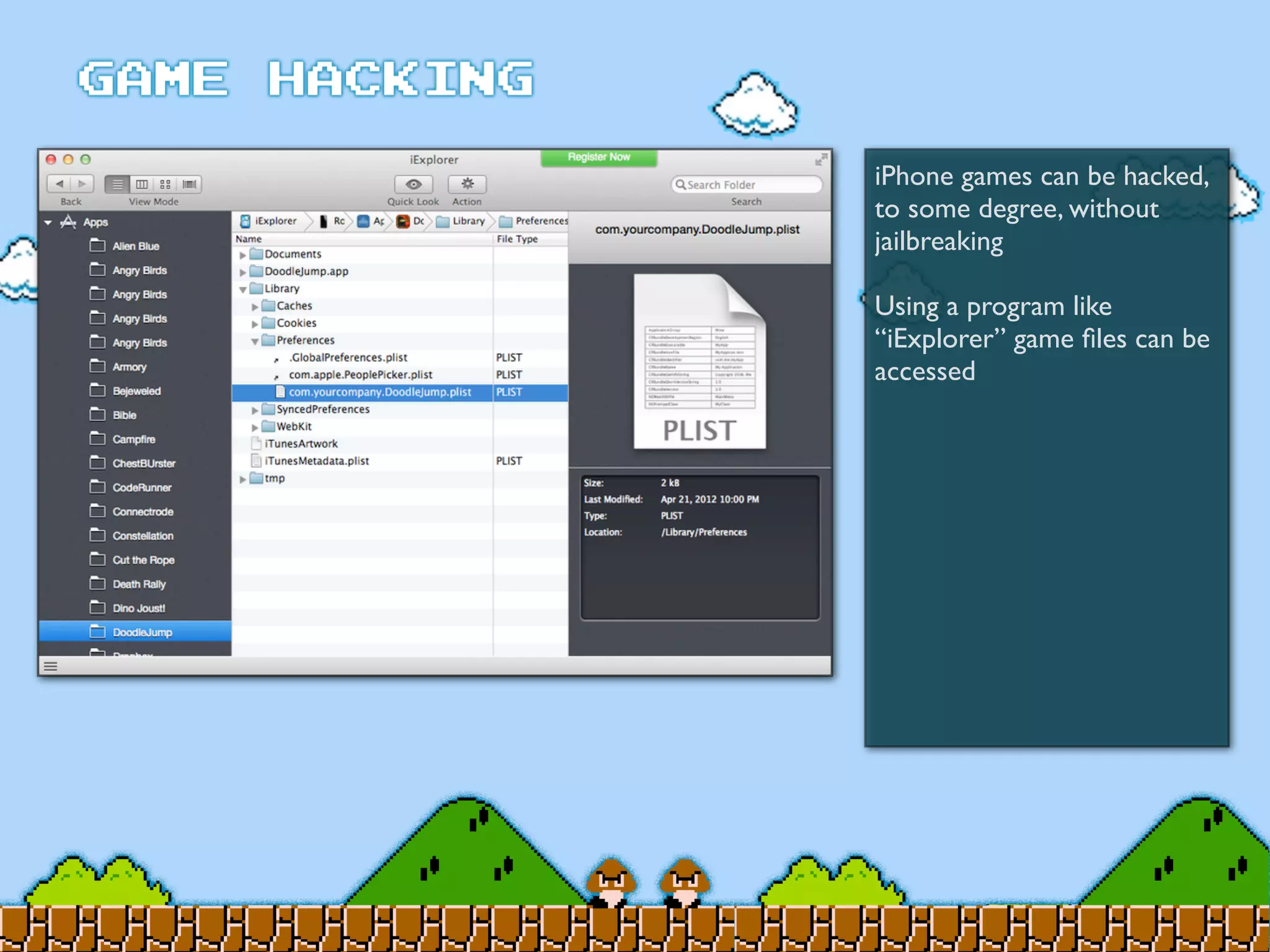
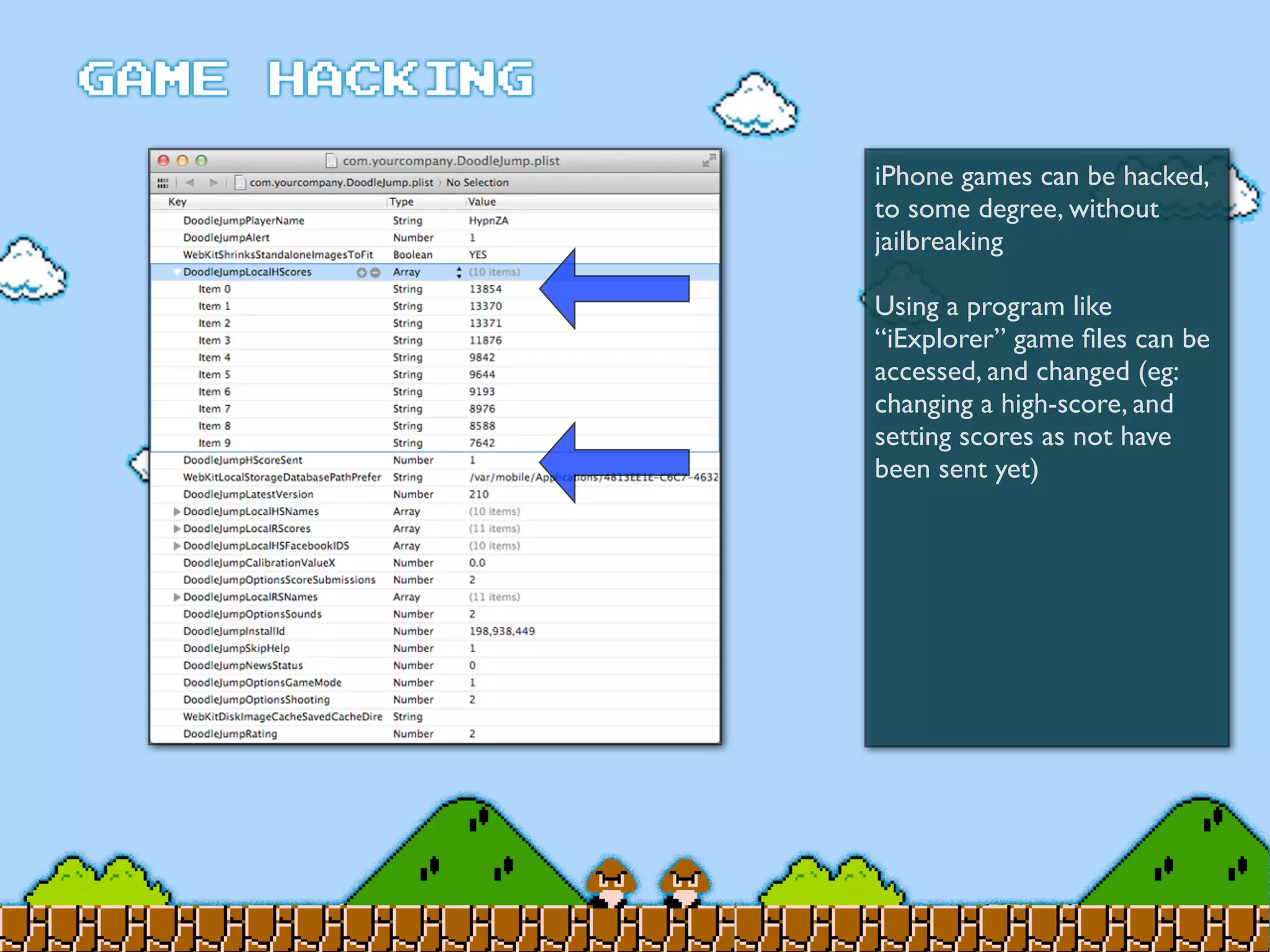
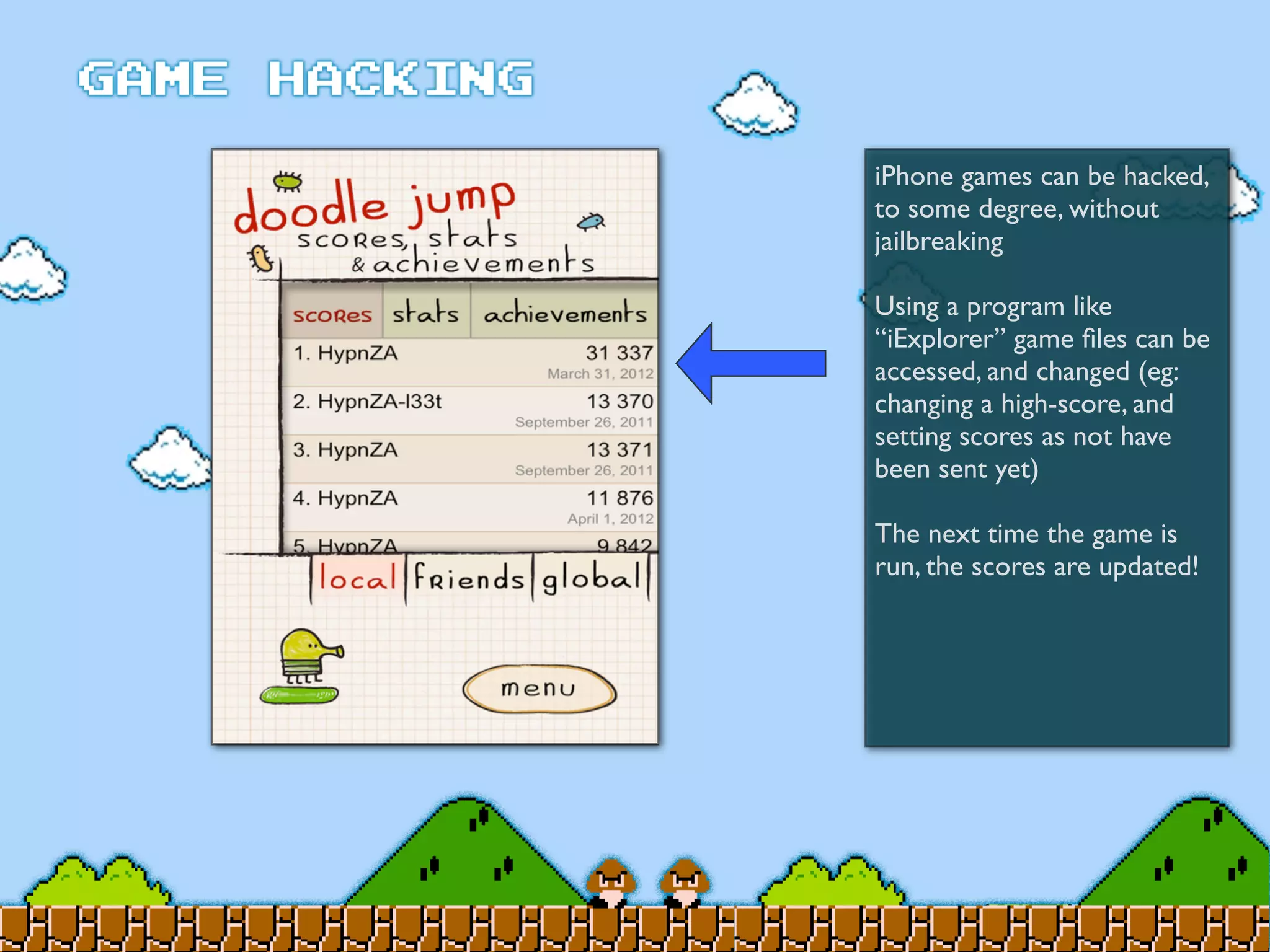
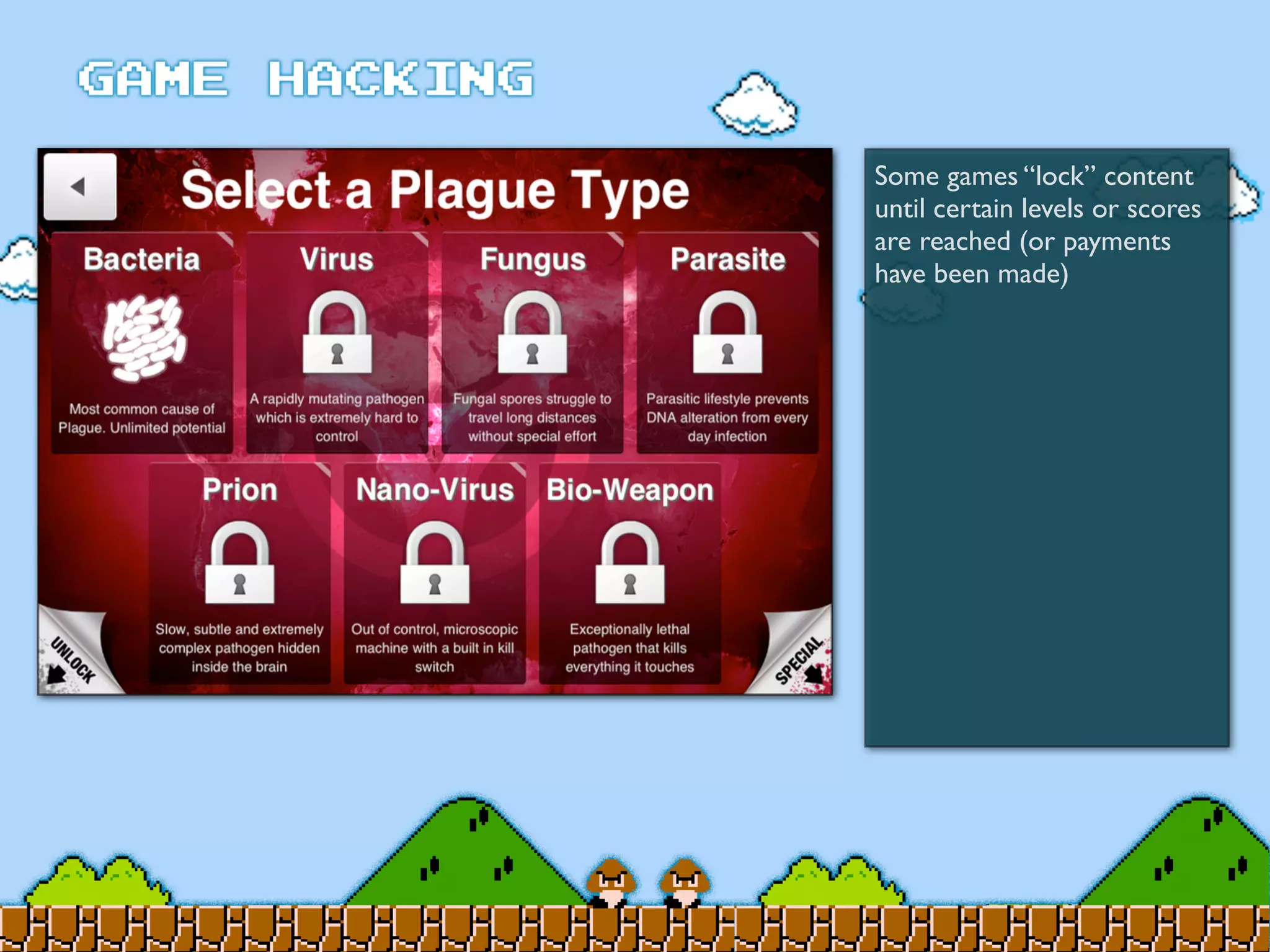
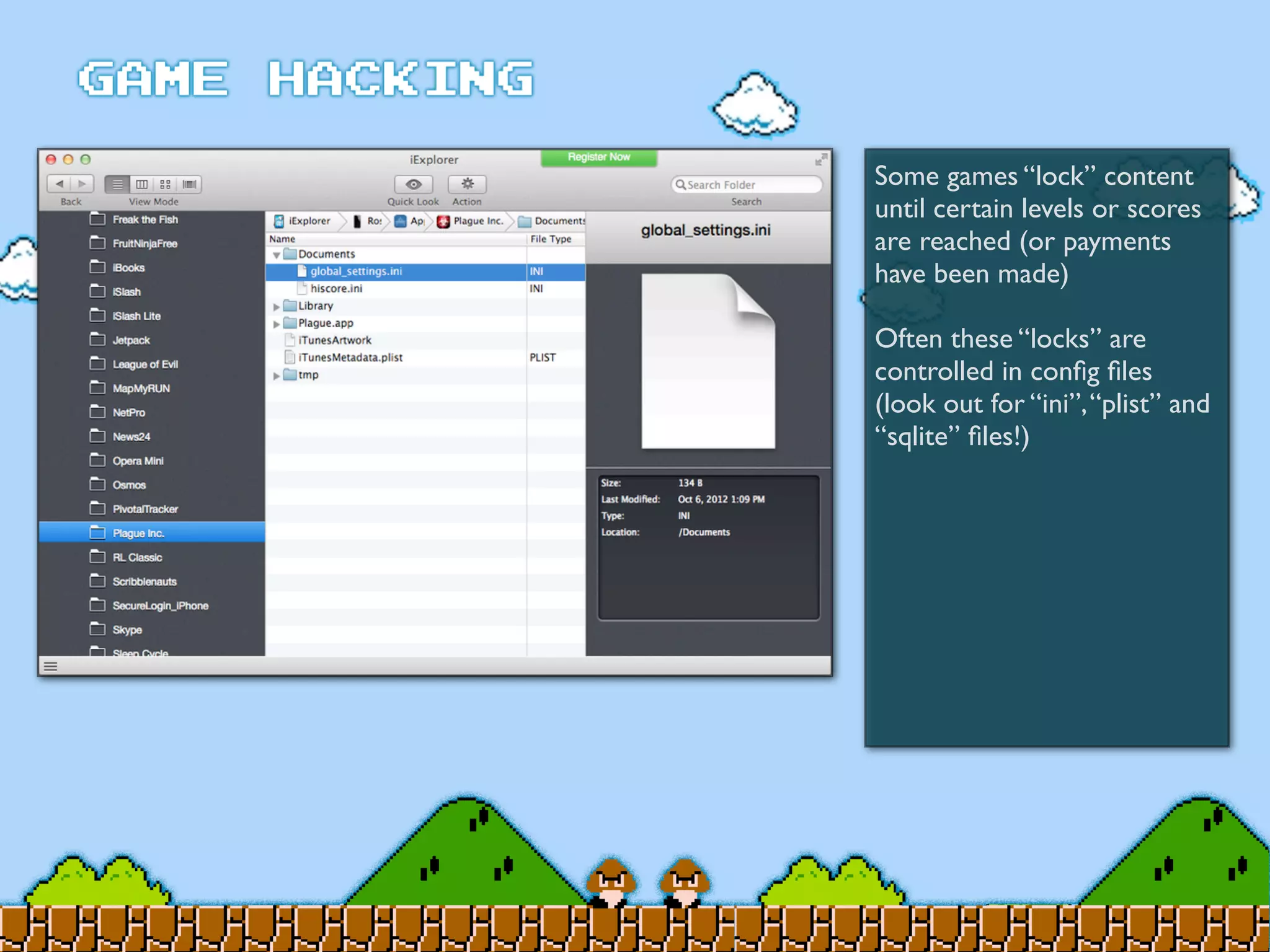
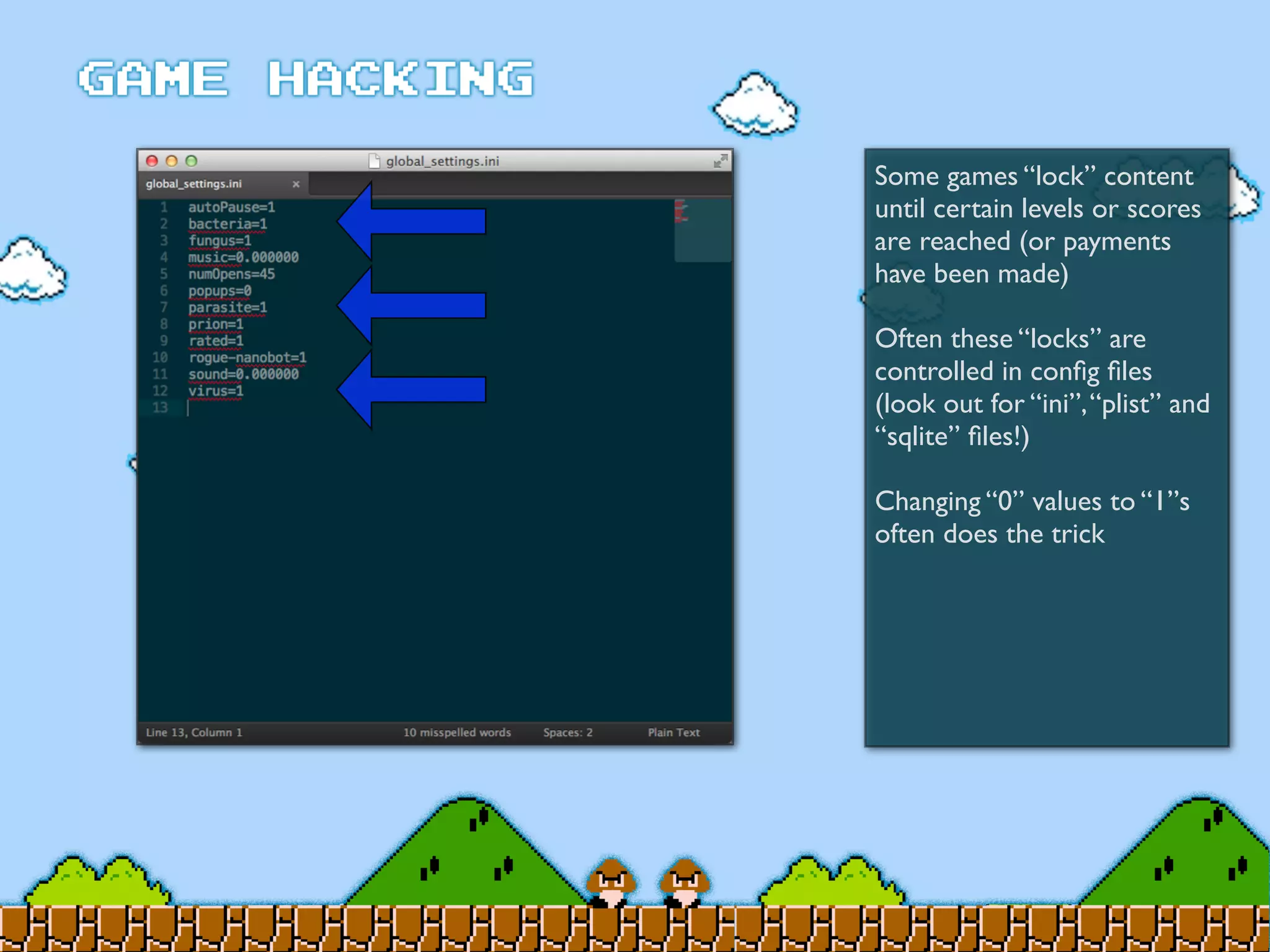
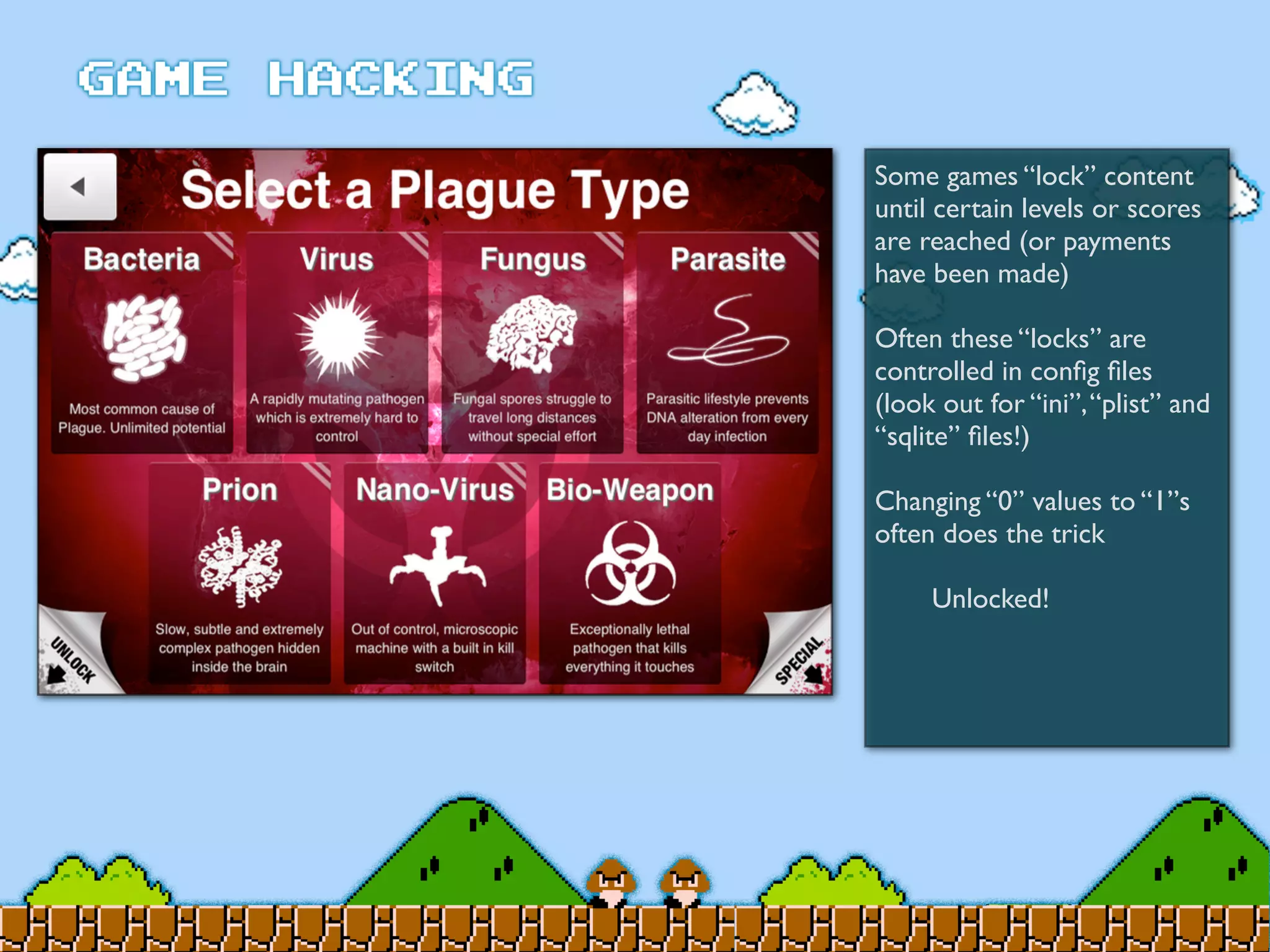
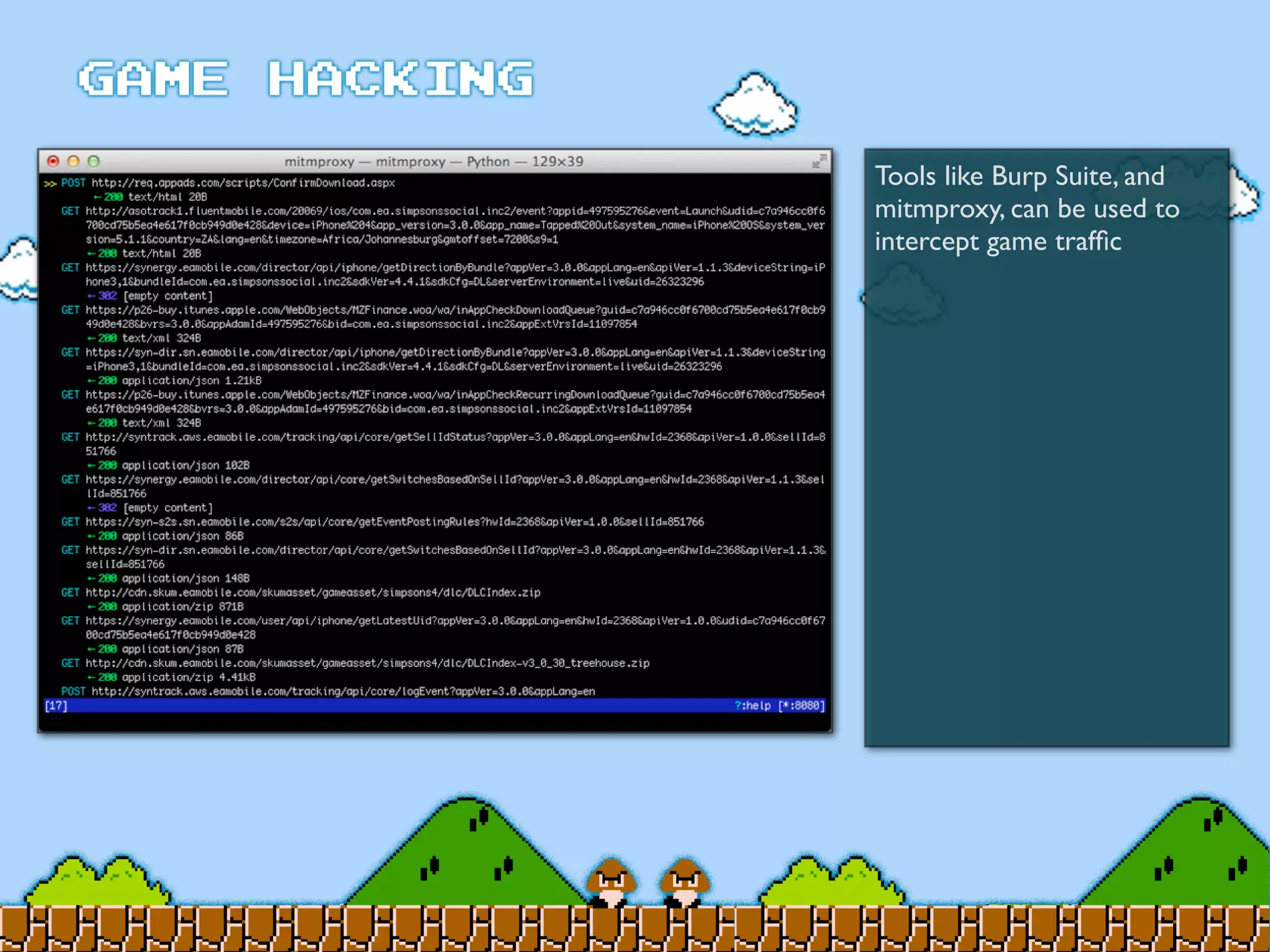
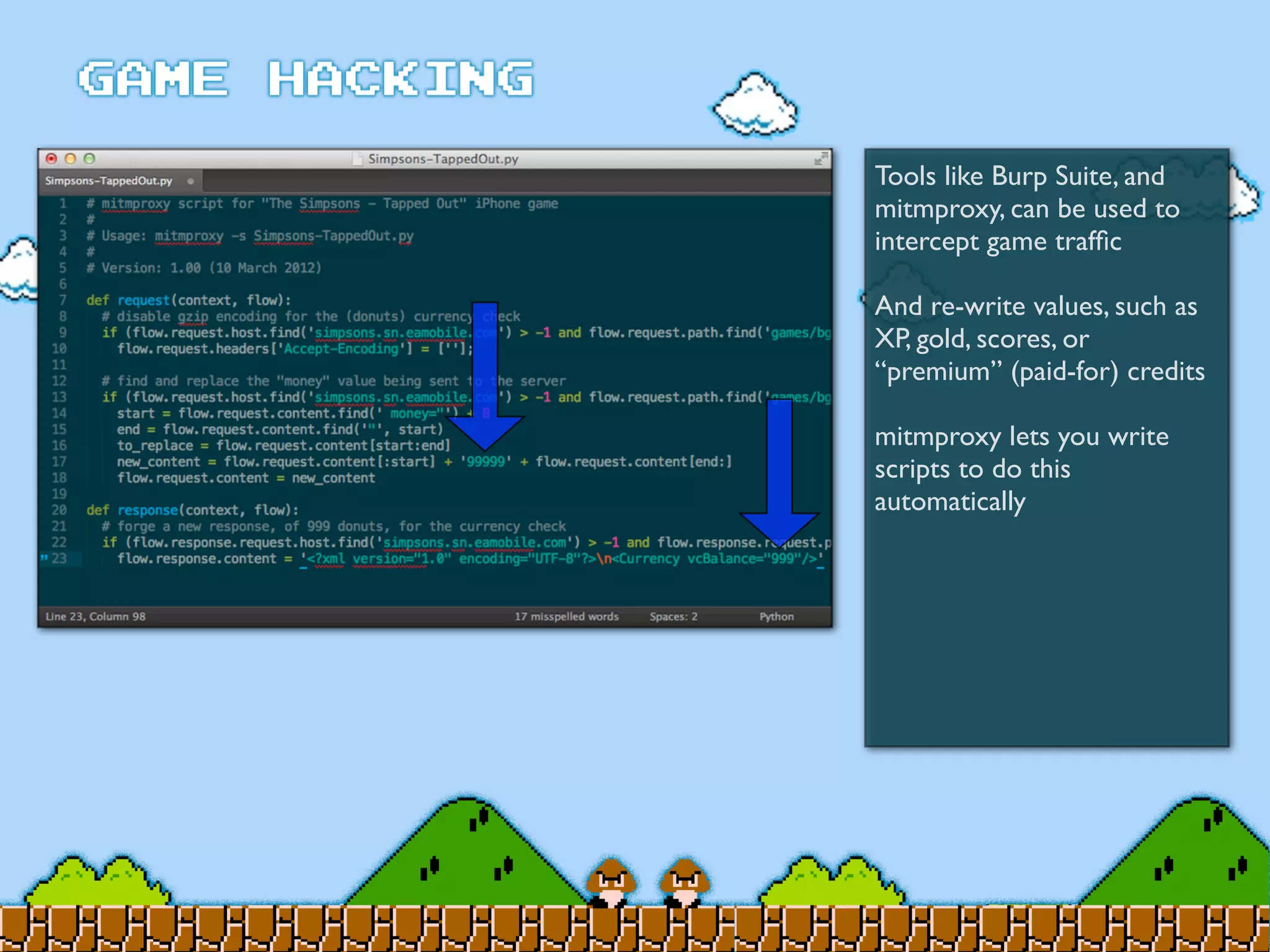
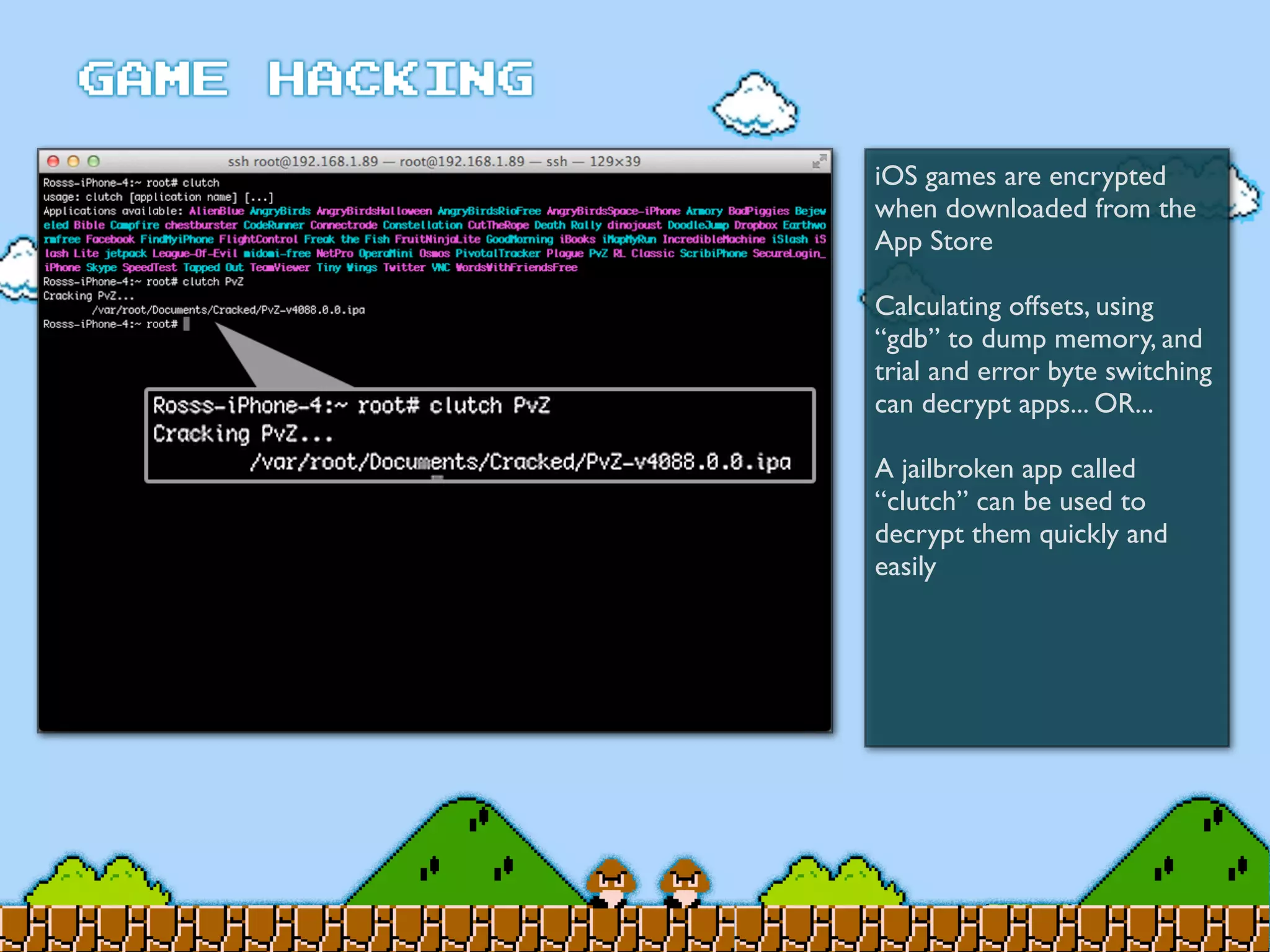
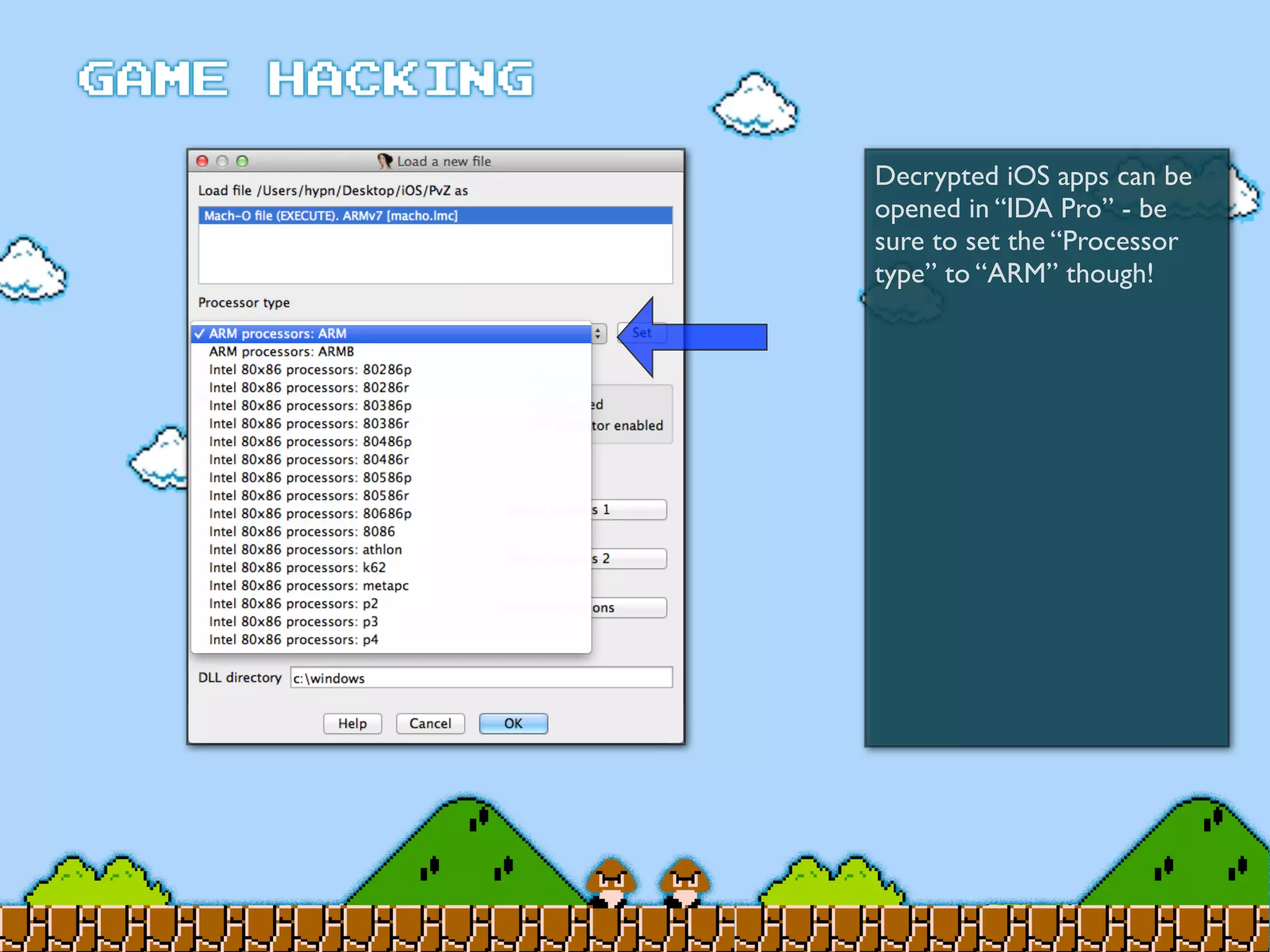
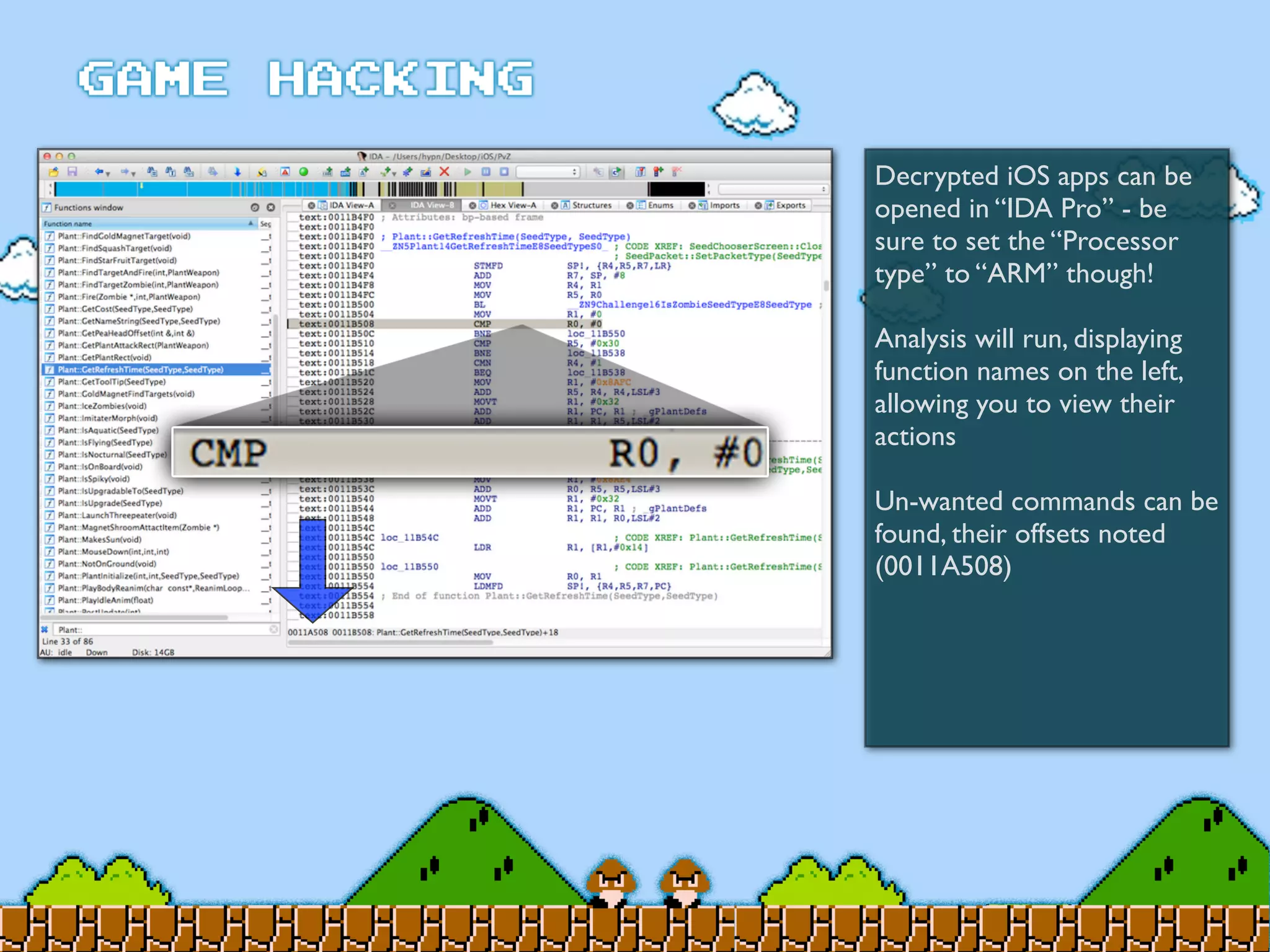
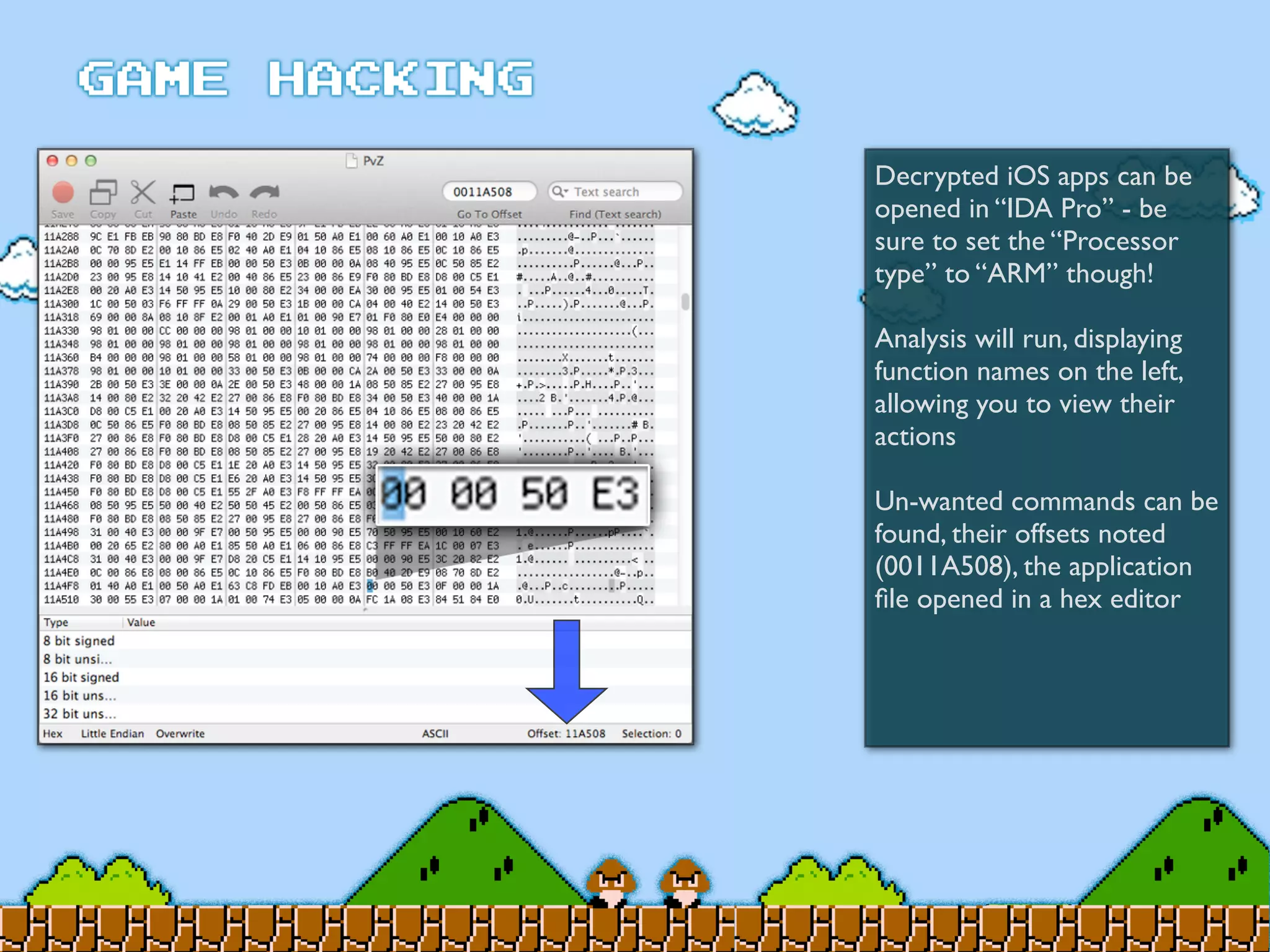
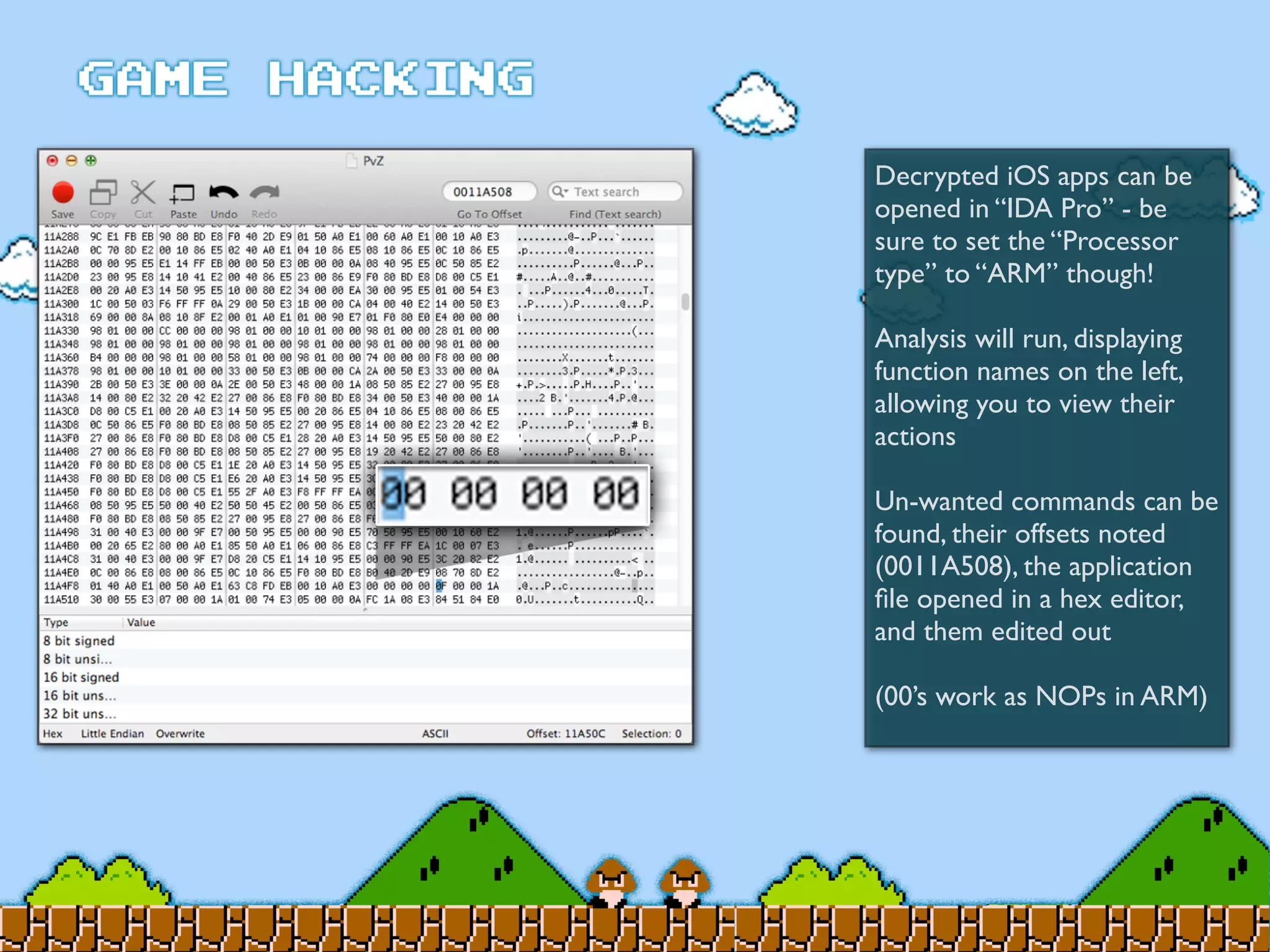
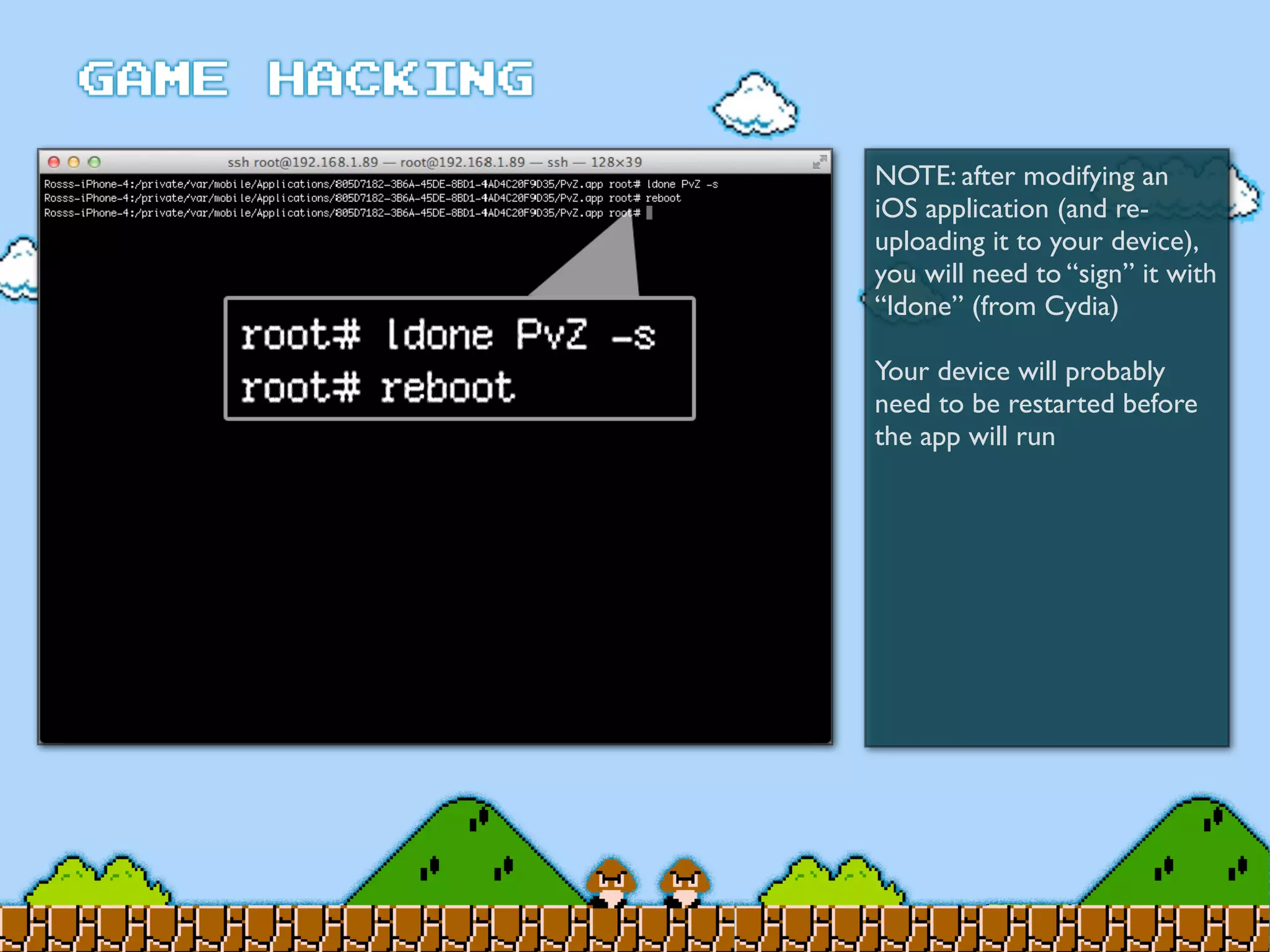
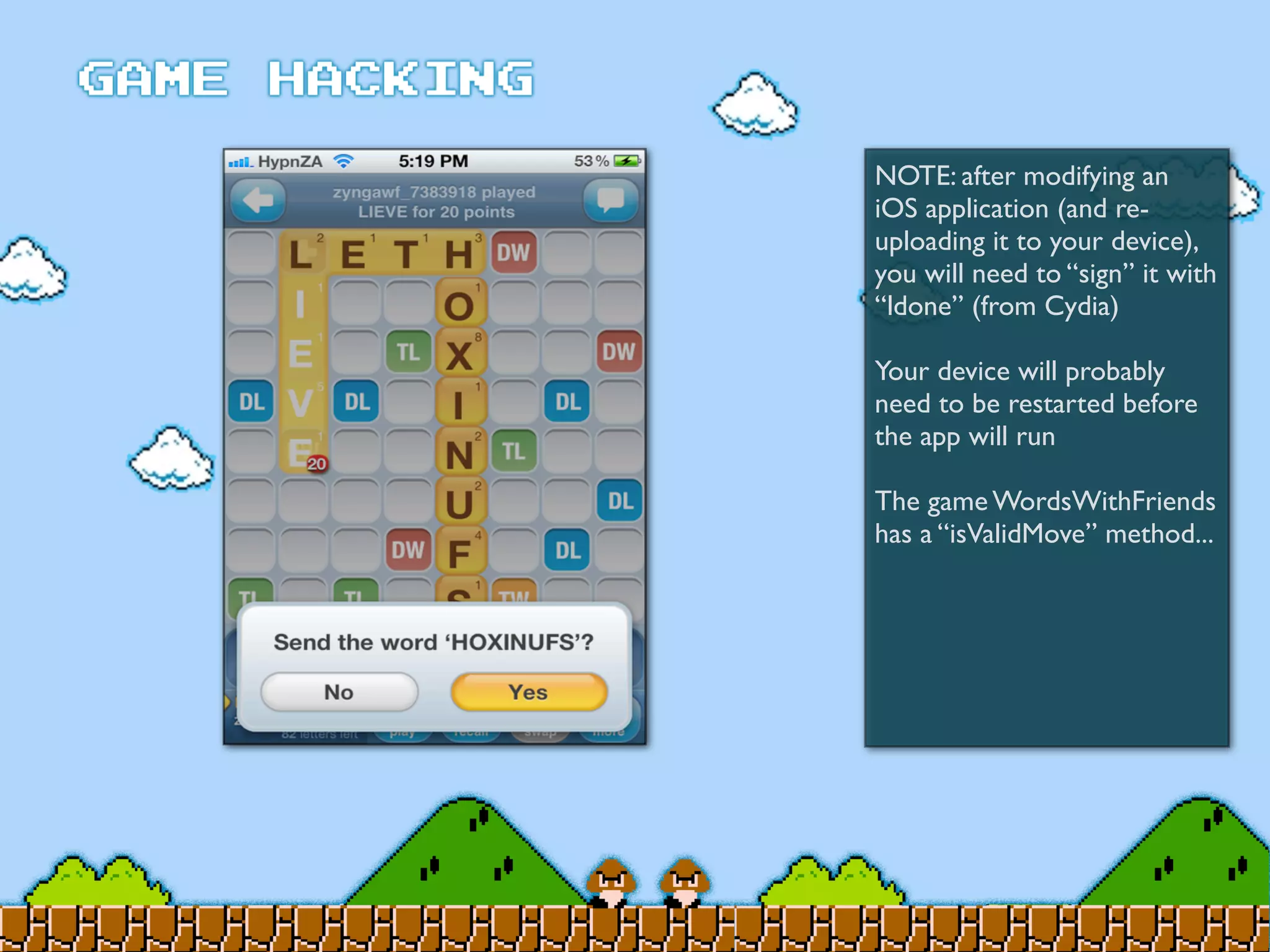
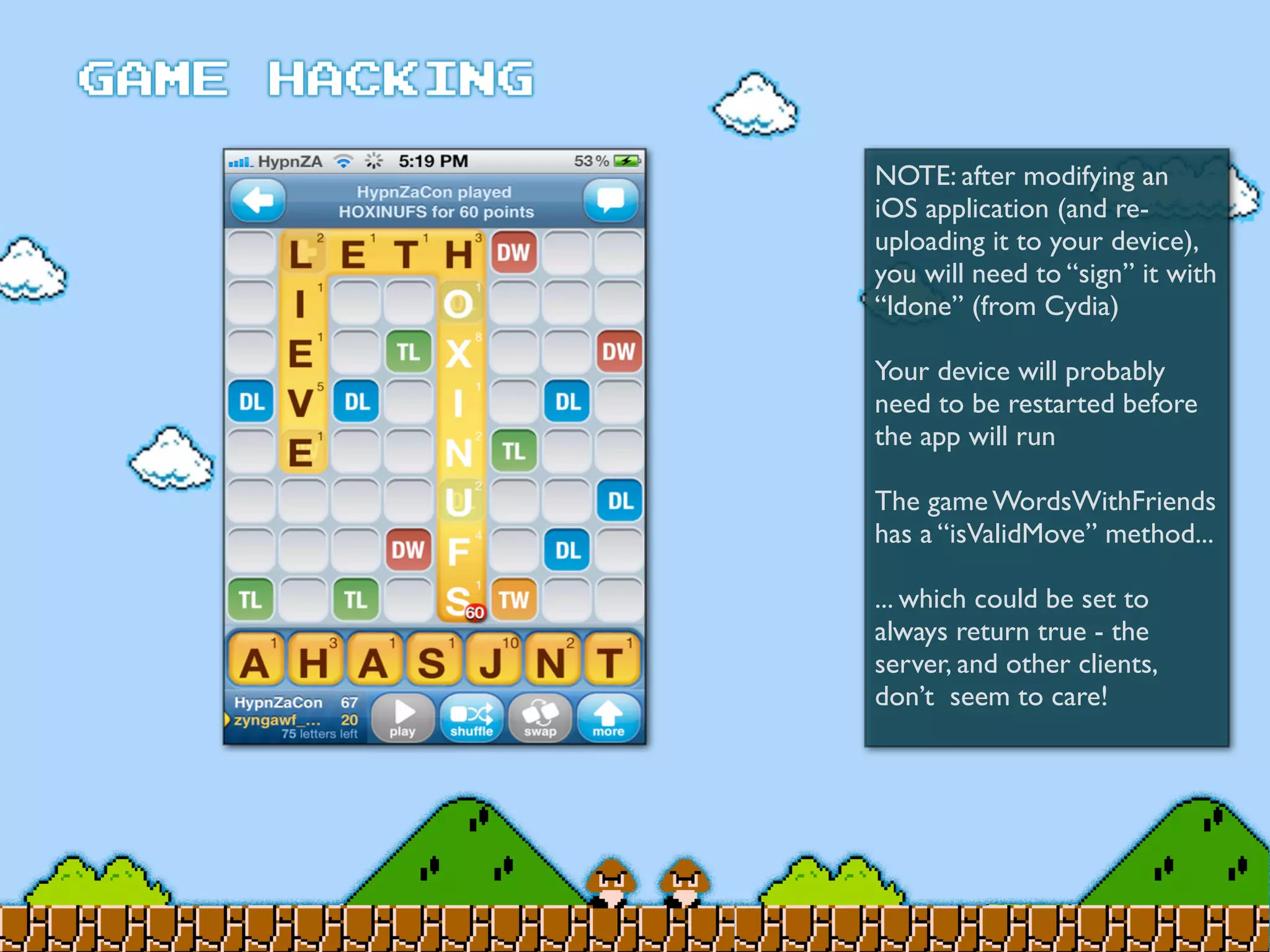
Game Hacking discusses various techniques for hacking console, DOS, and Windows games. These include using devices like Game Genie to modify NES games, memory scanning DOS games to change values like health and ammo, hex editing save files, using debuggers like OllyDbg to modify StarCraft map code, and exploiting flaws in game logic or servers. Memory hacking is described as a common technique to achieve hacks like teleporting or speed increases in games like World of Warcraft.