UNIT 2
THE OPEN SYSTEMS
INTERCONNECTION
(OSI) MODEL AND
NETWORK PROTOCOLS
�2.1 Network Communications
Learning Outcomes
At the end of this topic, student should be able to:
1. Describe the purpose of the OSI Model and each of its layers.
2. Define specific functions belonging to each OSI Model layer.
3. Explain how two network nodes communicate through the
OSI Model.
4. Explain the structure and purpose of data packets and frames.
5. Explain two types of addressing covered by the OSI Model.
�2.1 Describe Network Communications
What is networking?
o
Communication, sharing, delivering
An interconnection of computers and other
devices including:
o
o
o
Client computers
Servers (computers)
Network Devices
Hubs and Switches
Routers
Firewall
etc
�2.1.1 Describe the purpose of the OSI
Model and each of its layers.
In the early 1980s, ISO began work on a universal set of
specifications that would enable computer platforms across the
world to communicate openly.
The result was a helpful model for understanding and
developing computer-to-computer communications over a
network.
This model, called the OSI (Open Systems Interconnection)
model, divides network communications into seven layers:
Physical, Data Link, Network, Transport, Session, Presentation,
and Application. Each layer has their own task and protocol
involved.
OSI or Open Systems Interconnection is a standard reference
model for communication between two end users in a network.
�2.1.1 Describe the purpose of the OSI
Model and each of its layers. (cont.)
While performing those services, the
protocols also interact with protocols in the
layers directly above and below.
In addition, at the top of the OSI model,
Application layer protocols interact with the
software you use (such an e-mail or
spreadsheet program).
At the bottom, Physical layer services act on
the networking cables and connectors to
issue and receive signals.
�Please Do Not Touch Steve Pets Alligator
�1.2 Define specific functions belonging
to each OSI Model layer.
Application
(Layer 7)
Provides interface between
software applications and network
for interpreting applications
request and requirements.
Presentation
(Layer 6)
Allow hosts and applications to
use a common language; perform
data formatting, encryption and
compression
�SESSION
(Layer 5)
TRANSPORT
(Layer 4)
Establishes, maintains and
terminates user connection
Ensure accurate delivery of data
through flow control, segmentation
and reassembly, error correction
and acknowledgment
�NETWORK
(Layer 3)
Establishes network connections;
translate network addresses into
their physical counterparts and
determines routing
DATA LINK
(Layer 2)
Packages data in frames
appropriate to network
transmission method
�Physical
(Layer 1)
Manages signaling to
and form physical
network connections
�Summary
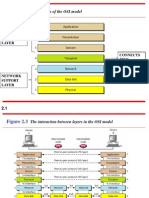
�2.1.3 Explain how two network nodes
communicate through the OSI Model.
The OSI model is a theoretical representation of
what happens between two nodes communicating
on a network.
Every process that occurs during network
communications can be associated with a layer of
the OSI model, so you should be familiar with the
names of the layers and understand the key
services and protocols that belong to each.
��When Data Passes from Host A to Host B :
Application, Presentation and Session layer take
user input and converts it into data
Transport layer adds a segment header converting
the data into segments
Network layer adds a network header and
converts the segments into packets
Data Link layer adds a frame header converting
the packets into frames
MAC sublayer layer converts the frames into a
bits which the Physical layer can put on the wire.
�When the bits stream arrives at the
destination (Host B):
Physical layer takes it of the wire and converts it
into frames.
Each layer will remove their corresponding header
while the data flows up the OSI model until it is
converted back to data and presented to the user.
��2.1.4 Explain the structure and
purpose of data packets and frames.
Data frames are small blocks of data with control,
addressing, and handling information attached to
them.
Frames are composed of several fields. The
characteristics of these fields depend on the type
of network on which the frames run and the
standards that they must follow.
Ethernet and token ring networks use different
frame types, and one type of network cannot
interpret the others frames.
�Frame Specifications
You have learned that frames are composed of several
smaller components, or fields.
The characteristics of these components depend on the
type of network on which the frames run and on the
standards that they must follow.
By far, the most popular type of networking technology in
use today is Ethernet, which uses Ethernet frames.
Youll learn much more about Ethernet in Chapter 5, but
the following serves as an introduction, as well as a
comparison between this favored network type and its
historical rival, token ring.
� Ethernet is a networking technology originally
developed at Xerox in the early 1970s and
improved by Digital Equipment Corporation,
Intel, and Xerox.
There are four different types of Ethernet frames.
The most popular form of Ethernet is
characterized by the unique way in which devices
share a common transmission channel, described
in the IEEE 802.3 standard.
� A much less common networking technology, token
ring, was developed by IBM in the 1980s.
It relies upon direct links between nodes and a ring
topology.
Nodes pass around tokens, special control frames
that indicate to the network when a particular node
is about to transmit data.
Although this networking technology is nearly
obsolete, there is a remote chance that you might
work on a token ring network.
The IEEE has defined token ring technology in its
802.5 standard.
� Ethernet frames are different from token ring
frames, and the two will not interact with each other
on a network.
In fact, most LANs do not support more than one
frame type, because devices cannot support more
than one frame type per physical interface, or NIC.
(NICs can, however, support multiple protocols.)
Although you can conceivably transmit both token
ring and Ethernet frames on a network, Ethernet
interfaces cannot interpret token ring frames, and
vice versa.
Normally, LANs use either Ethernet or token ring,
and almost all contemporary LANs use Ethernet.
�NOTE :
The terms frame, packet, datagram, and protocol data unit
(PDU) are often used interchangeably to refer to a small
piece of data formatted for network transmission.
Technically, however, a packet is a piece of information that
contains network addressing information, and a frame is a
piece of data enclosed by a Data Link layer header and
trailer.
Datagram is synonymous with packet.
PDU generically refers to a unit of data at any layer of the
OSI model.
However, networking professionals often use the term
packet to refer to frames, PDUs, and Transport layer
segments alike.
�2.1.5 Explain two types of addressing
covered by the OSI Model.
Addressing is a system for assigning unique
identification numbers to devices on a network.
Each node has two types of addresses.
�2 Types of Address
Network Address
Physical Address
�Network Address
Network addresses follow a hierarchical addressing
scheme and can be assigned through operating
system software.
They are hierarchical because they contain subsets of data
that incrementally narrow down the location of a node,
just as your home address is hierarchical because it
provides a country, state, ZIP code, city, street, house
number, and persons name.
Network layer address formats differ depending on
which Network layer protocol the network uses.
Example : IP, ICMP, IGMP, IPX/SPX
Network addresses are also called network layer
addresses, logical addresses, or virtual addresses.
�MAC (Media Access Control) Address
The MAC (Media Access Control) sublayer, the
lower sublayer of the Data Link layer, manages access
to the physical medium.
It appends the physical address of the destination
computer onto the data frame.
The physical address is a fixed number associated
with the hosts NIC; it is initially assigned at the
factory and stored in the NICs on-board memory.
Because this address is appended by the MAC
sublayer of the Data Link layer, it is also known as a
MAC address or a Data Link layer address.
Sometimes, its also called a hardware address.
�PHYSICAL ADDRESS
LOGICAL ADDRESS
The 48 bit MAC address that manufactures
encode in their network interface cards
A 32 bit IP address that is not embedded in
the network card
Address is unique, referred to as the
Ethernet or hardware address.
The purpose of routing between networks.
Associated with layer2 of the OSI Model.
Operates at Layer 3 of the OSI Model.
�2.2 Construct a Local Wired Network
Learning Outcomes
Student should be able to:
1. Determine the MAC address of a host using ipconfiq/all command.
2. Build a standard IEEE 802.3 Ethernet Frame based on a given
source and destination devices.
3. Indicate logical address of a computer.
4. Prepare IP address of a computer.
�2.2.1 Determine the MAC address of a
Host using ipconfig /all command.
You will need to know how to find and interpret
MAC addresses when supporting networks. In
this project, you will discover two ways of finding
your computers MAC address, also known as its
physical address, or sometimes, its hardware
address.
�If your workstation is running the Windows XP or Windows Vista operating
system, perform the following steps:
1. Click the Start button, point to All Programs, select Accessories, and
then select Command Prompt. The Command Prompt window opens
with a cursor blinking at the C:\> prompt.
2. Type ipconfig /all then press Enter. A list of your Windows XP or
Windows Vista configuration and Ethernet adapter parameters appears.
This includes your workstations TCP/IP properties, as well as its MAC
address.
3. Search the output for the 12-digit hexadecimal MAC address
currently assigned to your NIC. (Hint: Look for the Physical Address
line.) On a separate piece of paper, write down the MAC address.
4. Type exit and then press Enter to close the Command Prompt
window.
�IEEE Networking Specifications
Apply to connectivity, networking media, error
checking algorithms, encryption, emerging
technologies, and more
Specifications fall under IEEEs Project 802
Effort to standardize physical and logical elements of a network
31
Network+ Guide to Networks, 4e
�IEEE Networking Specifications
(continued)
Table 2-2: IEEE 802 standards
32
Network+ Guide to Networks, 4e
�IEEE Networking Specifications
(continued)
Table 2-2 (continued): IEEE 802 standards
33
Network+ Guide to Networks, 4e
�Summary
Standards are documented agreements containing
precise criteria that are used as guidelines to ensure
that materials, products, processes, and services suit
their purpose
ISOs OSI Model divides networking architecture
into seven layers
Each OSI layer has its own set of functions and
interacts with the layers directly above and below it
Application layer protocols enable software to
negotiate their formatting, procedural, security, and
synchronization with the network
34
Network+ Guide to Networks, 4e
�Summary (continued)
Presentation layer protocols serve as translators
between the application and the network
Session layer protocols coordinate and maintain links
between two devices for the duration of their
communication
Transport layer protocols oversee end-to-end data
delivery
Network layer protocols manage logical addressing
and determine routes based on addressing, patterns
of usage, and availability
35
Network+ Guide to Networks, 4e
�Summary (continued)
Data Link layer protocols organize data they receive
from the Network layer into frames that contain
error checking routines and can then be transmitted
by the Physical layer
Physical layer protocols generate and detect voltage
to transmit and receive signals carrying data over a
network medium
Data frames are small blocks of data with control,
addressing, and handling information attached to
them
36
Network+ Guide to Networks, 4e
�2.2 Comprehend a Local Wired
Network
Determine the MAC address of a Host using
ipconfig /all command
Build a standard IEEE 802.3 Ethernet Frame
based on a given source and destination devices
� Explain logical address of a computer
Appears to reside from the perspective of an executing
application.
Determine the IP address of a computer
Using ipconfig
�2.3 The Importance of Network
Protocols
Learning Outcomes
At the end of this topic, student should be able to:
Identify the characteristics of TCP/IP, IPX/SPX, NetBIOS and
NetBEUI, AppleTalk.
Differentiate how network protocols correlate to layers of the OSI
Model
Explain the functions of the core protocols of the TCP/IP suite
�Introduction to Protocols
Protocols vary according to purpose, speed,
transmission efficiency, utilization of resources,
ease of setup, compatibility, and ability to travel
between different LANs.
Multiprotocol networks: networks running more
than one protocol
Most popular protocol suite is TCP/IP
Others: IPX/SPX, NetBIOS, and AppleTalk
40
Network+ Guide to Networks, 4e
�Networking Protocol Suites:
a) Transmission Control Protocol/Internet
Protocol (TCP/IP)
b) Internetwork Packet Exchange/ Sequenced
Packet Exchange (IPX/SPX)
c) NetBIOS and NetBEUI
d) AppleTalk
�1.Physical
Wireless LAN
(802.11b, a, g)
Internet
(DSL, Cable Modem)
MAN / WAN
(poTS, ISDNT1, SONET,
ATM, Frame Relay
Backbone
(Ethernet, ATM, FDDI)
LAN
(Ethernet)
7.Application
6.Presentation
APPLICATION
LAYER
5.Session
4.Transport
3.Network
INTERNETWORK
LAYER
2.Data Link
HARDWARE
LAYER
�Internetwork Layer
Internetwork layer connect the application
software in the application layer with the
hardware layer that actually move messages from
one computer to another.
�TCP/IP
Transmission Control Protocol/Internet Protocol
Consist of dozens of difference protocols, but
only a few are the core protocol.
Two core protocol the most important : IP
protocol and TCP protocol.
Develop for the US Department of Defenses
Advance Research Project Agency Network
(ARPAnet) by Vinton Cerf and Bob Kahn in
1974.
��TCP/IP
Suite of specialized subprotocols
TCP, IP, UDP, ARP, and many others
De facto standard on Internet
Protocol of choice for LANs and WANs
Protocols able to span more than one LAN are
routable
Can run on virtually any combination of NOSs or
network media
TCP/IP core protocols operate in Transport or
Network layers
46
Network+ Guide to Networks, 4e
�TCP
Transmission Control Protocol
���The TCP Protocols
Provides reliable data delivery services
Operates in Transport layer
Connection-oriented
Establishes a connection before transmitting data.
Three-way handshake
Require acknowledgements from receiver to ensure data was received
correctly.
Ensures reliable data delivery through sequencing and checksums
Checksum for data integrity
Provides flow control
Port hosts address where an application makes itself
available to incoming or outgoing data
50
Network+ Guide to Networks, 4e
�The TCP Protocols (TCP Segment)
Figure 4-1: A TCP segment
51
Network+ Guide to Networks, 4e
�The TCP Protocols (TCP Segment)
Figure 4-2: TCP segment data
52
Network+ Guide to Networks, 4e
��The TCP Protocols (connection)
54
Figure 4-3: Establishing a TCP connection
Network+ Guide to Networks, 4e
� To establish a connection, TCP uses a three-way handshake. Before a client
attempts to connect with a server, the server must first bind to a port to open
it up for connections: this is called a passive open. Once the passive open is
established, a client may initiate an active open. To establish a connection, the
three-way (or 3-step) handshake occurs:
SYN: The active open is performed by the client sending a SYN to the server.
The client sets the segment's sequence number to a random value A.
SYN-ACK: In response, the server replies with a SYN-ACK. The
acknowledgment number is set to one more than the received sequence
number (A + 1), and the sequence number that the server chooses for the
packet is another random number, B.
ACK: Finally, the client sends an ACK back to the server. The sequence
number is set to the received acknowledgement value i.e. A, and the
acknowledgement number is set to one more than the received sequence
number i.e. B.
At this point, both the client and server have received an acknowledgment of
the connection.
����UDP (User Datagram Protocol)
Figure 4-4: A UDP segment
59
Network+ Guide to Networks, 4e
�The UDP Protocols
Provides reliable data delivery services
Operates in Transport layer
Connection-less
Do not establishes a connection before transmitting data.
No handshake.
No effort to ensure data is delivered free of errors.
Faster than conneciton-oriented protocol.
Useful when data must be transferred quickly such as streaming
music or video.
60
Network+ Guide to Networks, 4e
�The TCP Protocols (TCP Segment)
Figure 4-1: A TCP segment
61
Network+ Guide to Networks, 4e
���The TCP/IP Services
��IP
Internet Protocol
�IP (Internet Protocol) Protocol
Provides information about how and where data
should be delivered
Datas source and destination addresses
Network layer protocol
Enables TCP/IP to internetwork
Unreliable, connectionless protocol
IP datagram: packet, in context of TCP/IP
Envelope for data
67
Network+ Guide to Networks, 4e
�IP (continued)
Figure 4-5: An IP datagram
68
Network+ Guide to Networks, 4e
�IP (continued)
Figure 4-6: IP datagram data
69
Network+ Guide to Networks, 4e
��ICMP (Internet Control Message
Protocol)
Network layer protocol that reports on success or
failure of data delivery
Indicates when part of network congested
Indicates when data fails to reach destination
Indicates when data discarded because allotted time for delivery
(TTL) expired
Cannot correct errors it detects
71
Network+ Guide to Networks, 4e
��IGMP (Internet Group Management
Protocol)
Network layer protocol that manages
multicasting
Transmission method allowing one node to send data to defined
group of nodes
Point-to-multipoint method
Teleconferencing or videoconferencing over Internet
Routers use IGMP to determine which nodes
belong to multicast group and to transmit data to
all nodes in that group
73
Network+ Guide to Networks, 4e
�ARP (Address Resolution Protocol)
Network layer protocol
Obtains MAC (physical) address of host
Creates database that maps MAC address to hosts IP (logical) address
ARP table or cache: local database containing
recognized MAC-to-IP address mappings
Dynamic ARP table entries created when client makes ARP
request that cannot be satisfied by data already in ARP table
Static ARP table entries entered manually using ARP utility
74
Network+ Guide to Networks, 4e
��RARP (Reverse Address Resolution
Protocol)
Allows client to broadcast MAC address and receive
IP address in reply
If device doesnt know own IP address, cannot use ARP
RARP server maintains table of MAC addresses and
associated IP addresses
76
Network+ Guide to Networks, 4e
�BOOTP (Bootstrap Protocol)
Uses central list of IP addresses and associated
devices MAC addresses to assign IP addresses to
clients dynamically
Dynamic IP addresses
Application layer protocol
Client broadcasts MAC address, BOOTP server replies with:
Clients IP address
IP address of server
Host name of server
IP address of a default router
77
Network+ Guide to Networks, 4e
�DHCP (Dynamic Host Configuration
Protocol)
Automated means of assigning unique IP address to
every device on a network
Application layer protocol
Reduces time and planning spent on IP address management
Reduces potential for errors in assigning IP addresses
Enables users to move workstations and printers without having to
change TCP/IP configuration
Makes IP addressing transparent for mobile users
Three method in DHCP:
Dynamic allocation
Automatic allocation
Static allocation
78
Network+ Guide to Networks, 4e
�DHCP (continued)
Figure 4-11: The DHCP leasing process
79
Network+ Guide to Networks, 4e
�APIPA (Automatic Private IP Addressing)
Provides computer with IP address automatically
For Windows 98, Me, 2000, XP client and
Windows 2003 server
For situations where DHCP server unreachable
Assigns computers network adapter IP address from predefined
pool of addresses
169.254.0.0 through 169.254.255.255
Computer can only communicate with other nodes using
addresses in APIPA range
80
Network+ Guide to Networks, 4e
�http://pic.dhe.ibm.com/infocenter/zos
/v2r1/index.jsp?topic=%2Fcom.ibm.zo
s.v2r1.hala001%2Fitctcpipcon.htm
TCP Transmission Control Protocol is a transport protocol providing a reliable, full-duplex byte
stream. Most TCP/IP applications use the TCP transport protocol. UDP User Datagram Protocol is
a connectionless protocol providing datagram services. UDP is less reliable because there is no
guarantee that a UDP datagram ever reaches its intended destination, or that it reaches its
destination only once and in the same condition as it was passed to the sending UDP layer by a UDP
application. ICMP Internet Control Message Protocol is used to handle error and control
information at the IP layer. The ICMP is most often used by network control applications that are
part of the TCP/IP software product itself, but ICMP can be used by authorized user processes as
well. PING and TRACEROUTE are examples of network control applications that use the ICMP
protocol. IP Internet Protocol provides the packet delivery services for TCP, UDP, and ICMP. The
IP layer protocol is unreliable (called a best-effort protocol). There is no guarantee that IP packets
arrive, or that they arrive only once and are error-free. Such reliability is built into the TCP
protocol, but not into the UDP protocol. If you need reliable transport between two UDP
applications, you must ensure that reliability is built into the UDP applications. ARP/ND The IPv4
networking layer uses the Address Resolution Protocol (ARP) to map an IP address into a hardware
address. In the IPv6 networking layer, this mapping is performed by the Neighbor Discovery (ND
function). On local area networks (LANs), such an address would be called a media access control
(MAC) address. RARP Reverse Address Resolution Protocol is used to reverse the operation of the
ARP protocol. It maps a hardware address into an IPv4 address. Note that both ARP packets and
RARP packets are not forwarded in IP packets, but are themselves media level packets. ARP and
RARP are not used on all network types, as some networks do not need these protocols
�2.4 Addressing Schemes for TCP/IP
Suite
Learning Outcomes
At the end of this topic, student should be able to:
Understand addressing schemes for TCP/IP suite.
Describe the purpose and implementation of DNS (Domain Name
System) and WINS (Windows Internet Naming Service)
Install protocols on Windows XP clients
�2.4 Addressing Schemes for TCP/IP
Suite
Learning Outcomes
At the end of this topic, student should be able to:
Compare the addressing scheme of TCP/IP: classes, binary, dotted
decimal notation and subnet mask.
Label Public and Private IP address.
Label Unicast, Broadcast and Multicast address.
Relate how IP address are obtained : static address or dynamic address.
��Addressing in TCP/IP (IP address)
Figure 4-8: IP addresses and their classes
85
Network+ Guide to Networks, 4e
����222.32.1.1
____
179.21.9.0
____
90.43.2.1
____
220.11.6.6
____
43.55.45.0
____
126.32.1.0
____
111.45.3.2
____
��������Addressing in TCP/IP (continued)
Many Internet addresses go unused
Cannot be reassigned because they are reserved
IP version 6 (IPv6) will incorporate new addressing scheme
Some IP addresses reserved for special functions
127 reserved for a device communicating with itself
Loopback test
ipconfig: Windows XP command to view IP
information
ifconfig on Unix and Linux
97
Network+ Guide to Networks, 4e
�Binary and Dotted Decimal Notation
Most common way of expressing IP addresses
Decimal number between 0 and 255 represents each binary
octet
Separated by period
Each number in dotted decimal address has
binary equivalent
98
Network+ Guide to Networks, 4e
�Subnet Mask
Every device on TCP/IP-based network identified by subnet
mask
32-bit number that, when combined with devices IP address,
informs rest of network about segment or network to which a
device is attached
Subnetting: subdividing single class of networks into multiple,
smaller logical networks or segments
99
Network+ Guide to Networks, 4e
��1
1
���������������Assigning IP Addresses
Nodes on a network must have unique IP
addresses
Static IP address: manually assigned
Can easily result in duplication of addresses
Most network administrators rely on network
service to automatically assign IP addresses
116
Network+ Guide to Networks, 4e
�����Sockets and Ports
Every process on a machine assigned a port number 0 to
65535
Well Known Ports: in range 0 to 1023
Assigned to processes that only the OS or system administrator can access
Registered Ports: in range 1024 to 49151
Accessible to network users and processes that do not have special
administrative privileges
Dynamic and/or Private Ports: in range 49152 through
65535
Open for use without restriction
Processs port number plus host machines IP address
equals processs socket
Ensures data transmitted to correct application
121
Network+ Guide to Networks, 4e
�http://en.wikipedia.org/wiki/Internet_port
�TCP Segment
123
Network+ Guide to Networks, 4e
�IP datagram
124
Network+ Guide to Networks, 4e
�Addressing in IPv6
IPv6 slated to replace current IP protocol, IPv4
More efficient header, better security, better prioritization
Billions of additional IP addresses
Differences:
Address size
Representation
Distinguishes among different types of network interfaces
Format Prefix
125
Network+ Guide to Networks, 4e
�Comparison between IPv6 and IPv4:
-Larger address space
-Better multicasting
-Better on auto configurations
-Better on security (network layer)
-Better on supporting mobility
�Host Names and DNS (Domain Name
System): Domain Names
Every host can take a host name
Every host is member of a domain
Group of computers belonging to same organization and has part of
their IP addresses in common
Domain name usually associated with company or other type of
organization
Fully qualified host name: local host name plus
domain name
Domain names must be registered with an Internet
naming authority that works on behalf of ICANN
127
Network+ Guide to Networks, 4e
�Host Files
ASCII text file called HOSTS.TXT
Associate host names with IP addresses
Growth of Internet made this arrangement impossible to maintain
Figure 4-13: Example host file
128
Network+ Guide to Networks, 4e
�http://compnetworking.about.com/od/dns_domainnamesystem/f/dns_servers.htm
DNS (Domain Name System)
DNS translates Internet domain and host names to IP addresses.
DNS automatically converts the names we type in our web
browser address bar to the IP addresses of web servers hosting
those sites.
Hierarchical method of associating domain names with IP
addresses
Refers to Application layer service that accomplishes association and organized
system of computers and databases making association possible
Relies on many computers around world
Thirteen root servers
Three components:
Resolvers - a piece of software that's understands how to formulate a DNS query
and is built into practically every Internet-capable application.
Name servers - DNS is a globally connected network of "name servers
Name space - establishes the syntactical rules for creating and structuring legal
DNS names.
129
http://blog.datakl.com/tag/dns-resolver/
Network+ Guide to Networks, 4e