0% found this document useful (0 votes)
246 views26 pagesStudy of IoT Protocols
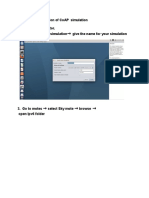
The document discusses several Internet of Things (IoT) protocols. It describes Constrained Application Protocol (COAP) in detail, including its implementation using Contiki and Cooja simulator. COAP is designed for resource constrained IoT devices and uses a request/response interaction model like HTTP. The document also outlines Message Queuing Telemetry Transport (MQTT) and how it was implemented using Node-RED and a mobile app. Other protocols discussed include AMQP, XMPP, and 6LoWPAN.
Uploaded by
Ritesh PatelCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
246 views26 pagesStudy of IoT Protocols
The document discusses several Internet of Things (IoT) protocols. It describes Constrained Application Protocol (COAP) in detail, including its implementation using Contiki and Cooja simulator. COAP is designed for resource constrained IoT devices and uses a request/response interaction model like HTTP. The document also outlines Message Queuing Telemetry Transport (MQTT) and how it was implemented using Node-RED and a mobile app. Other protocols discussed include AMQP, XMPP, and 6LoWPAN.
Uploaded by
Ritesh PatelCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
/ 26