0% found this document useful (0 votes)
16 views15 pagesGrafana&Prometheus
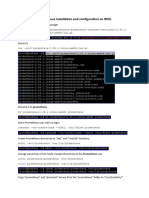
The document outlines the pull-based data collection method used by Prometheus, where the monitoring system retrieves metrics from defined targets via HTTP requests. It details the configuration, scraping process, and advantages of this approach, including centralized control and dynamic target discovery. Additionally, it provides a step-by-step guide for installing and configuring Prometheus and Grafana on a Kubernetes cluster using Helm, including commands for accessing services and managing deployments.
Uploaded by
revanth kandregulaCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
16 views15 pagesGrafana&Prometheus
The document outlines the pull-based data collection method used by Prometheus, where the monitoring system retrieves metrics from defined targets via HTTP requests. It details the configuration, scraping process, and advantages of this approach, including centralized control and dynamic target discovery. Additionally, it provides a step-by-step guide for installing and configuring Prometheus and Grafana on a Kubernetes cluster using Helm, including commands for accessing services and managing deployments.
Uploaded by
revanth kandregulaCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
/ 15