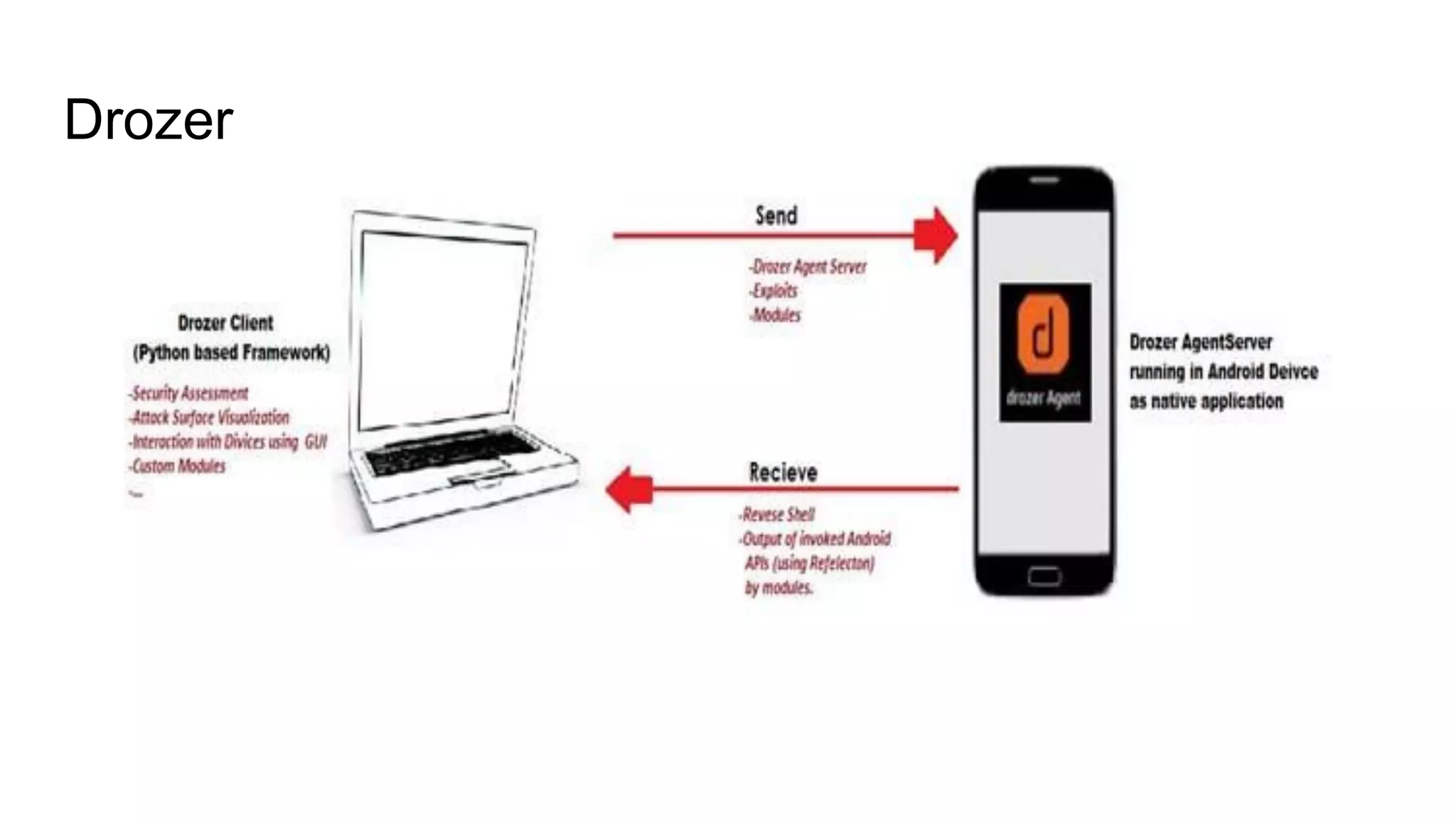
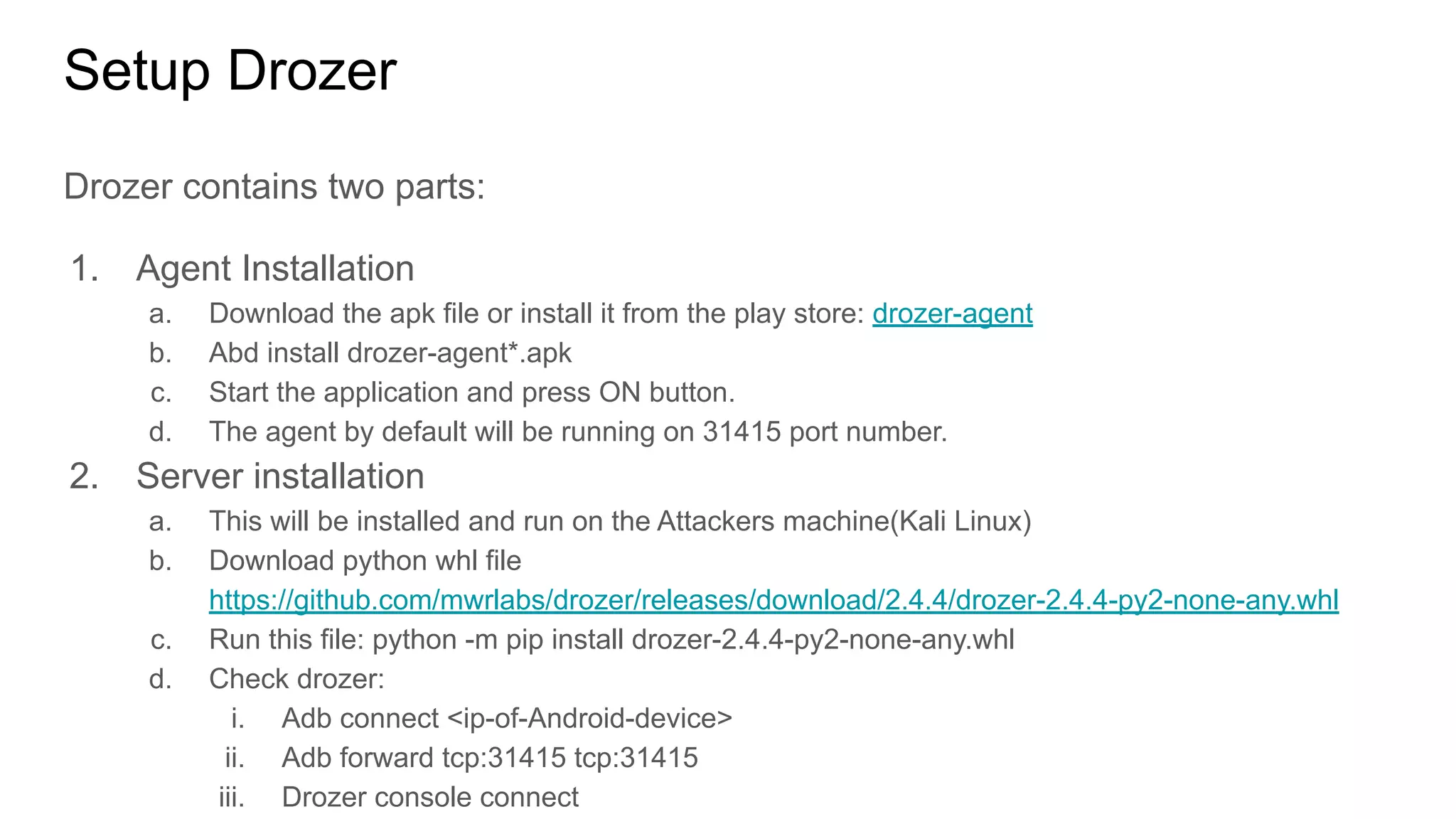
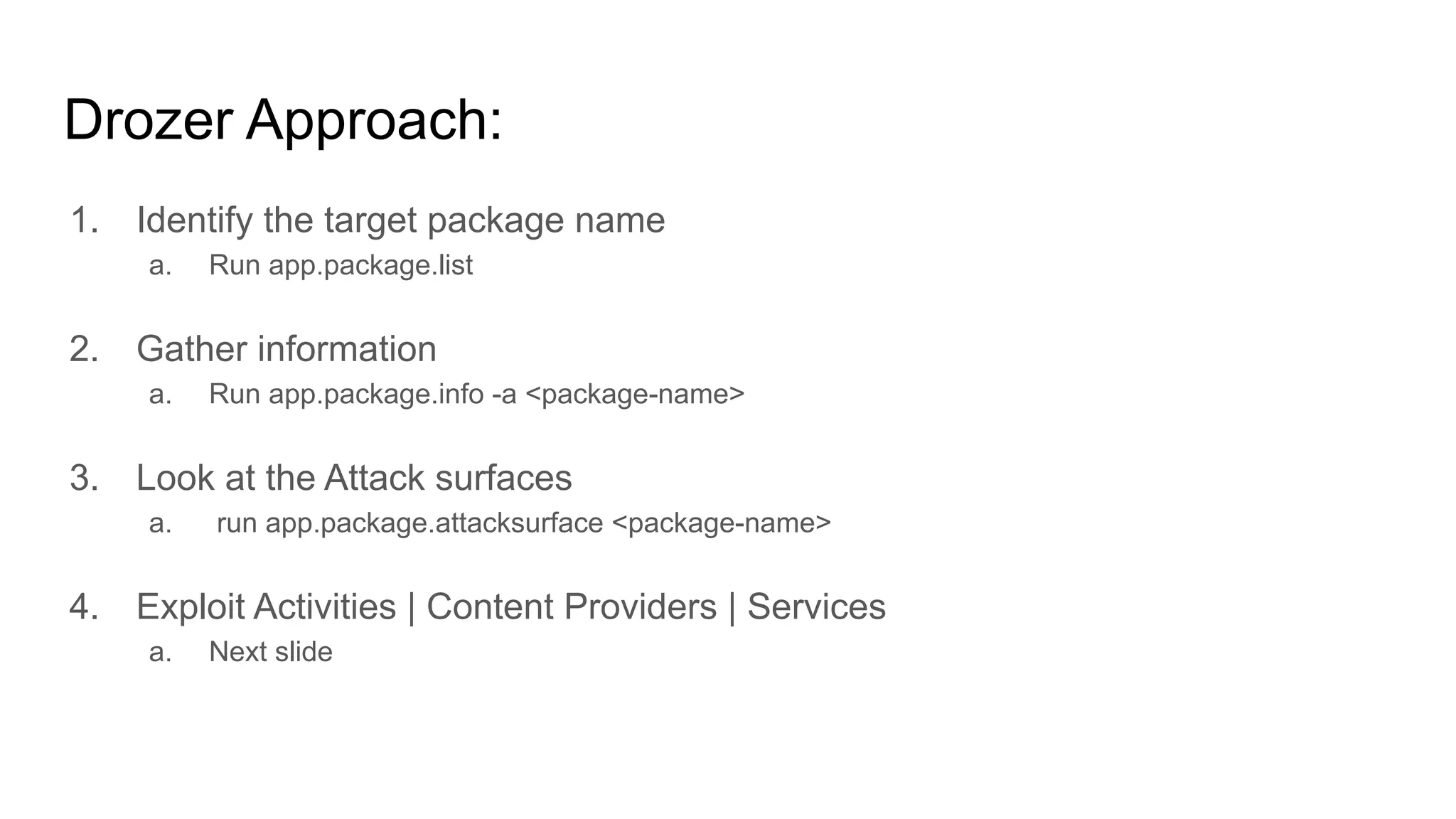
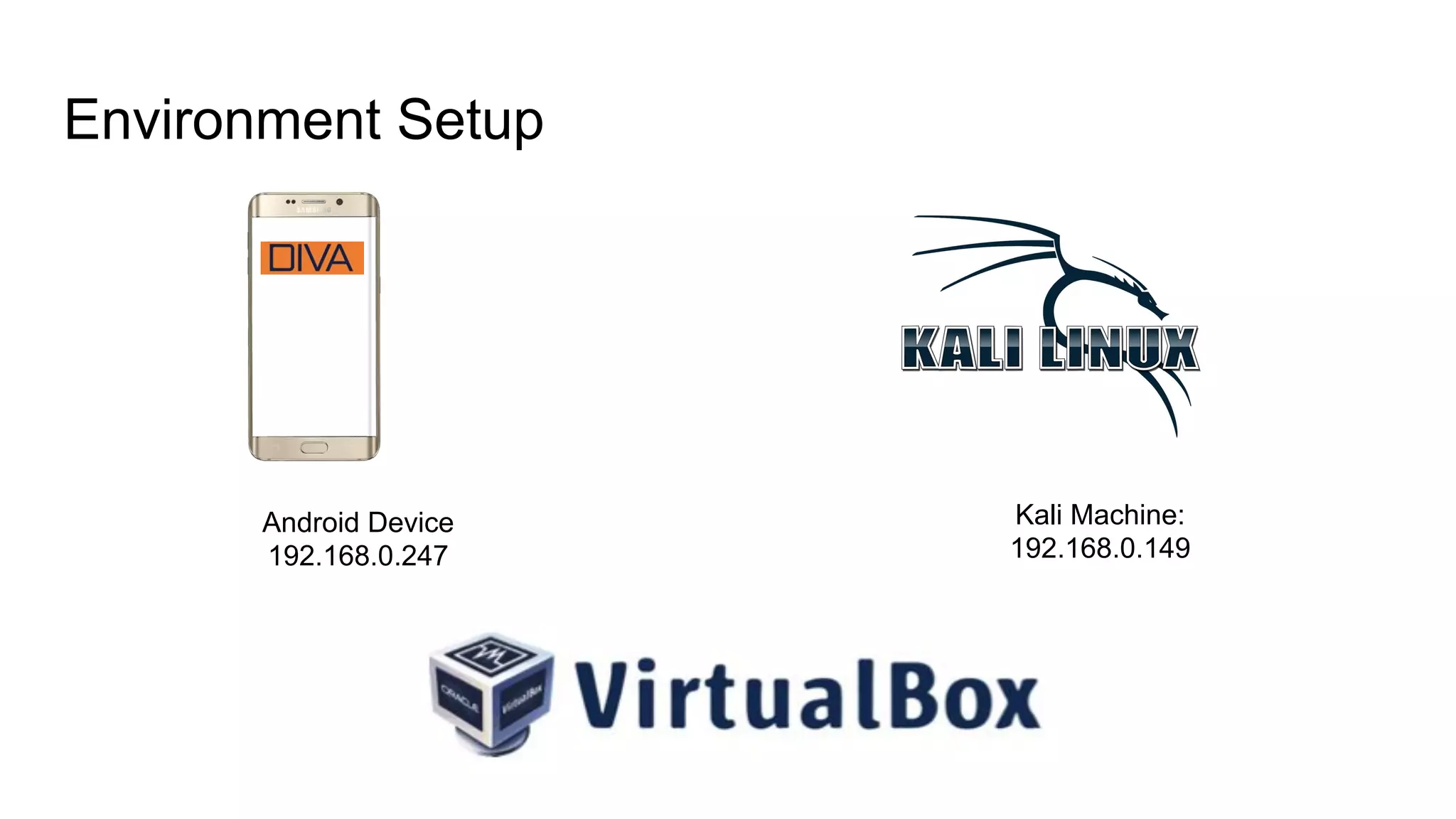
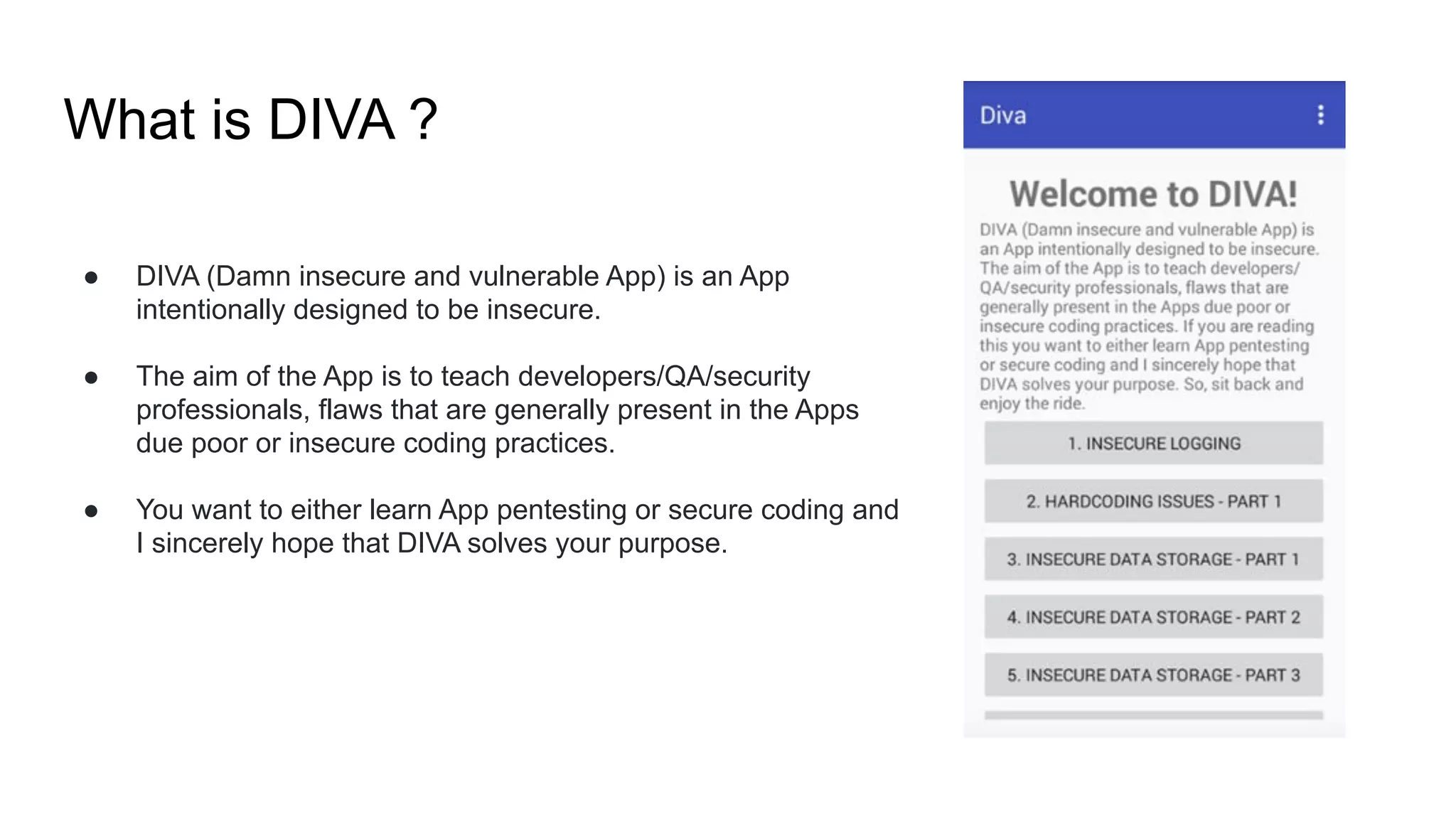
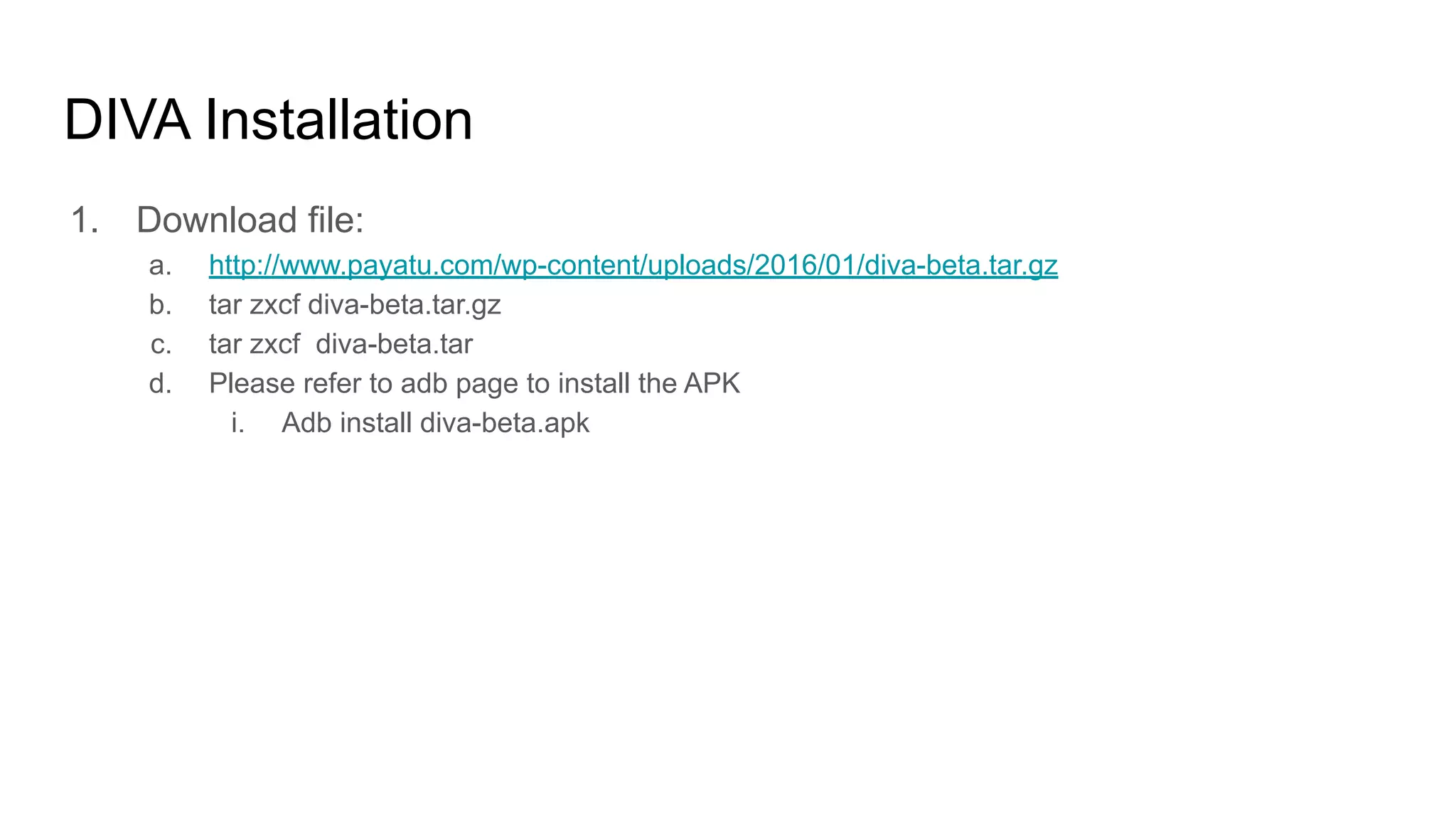
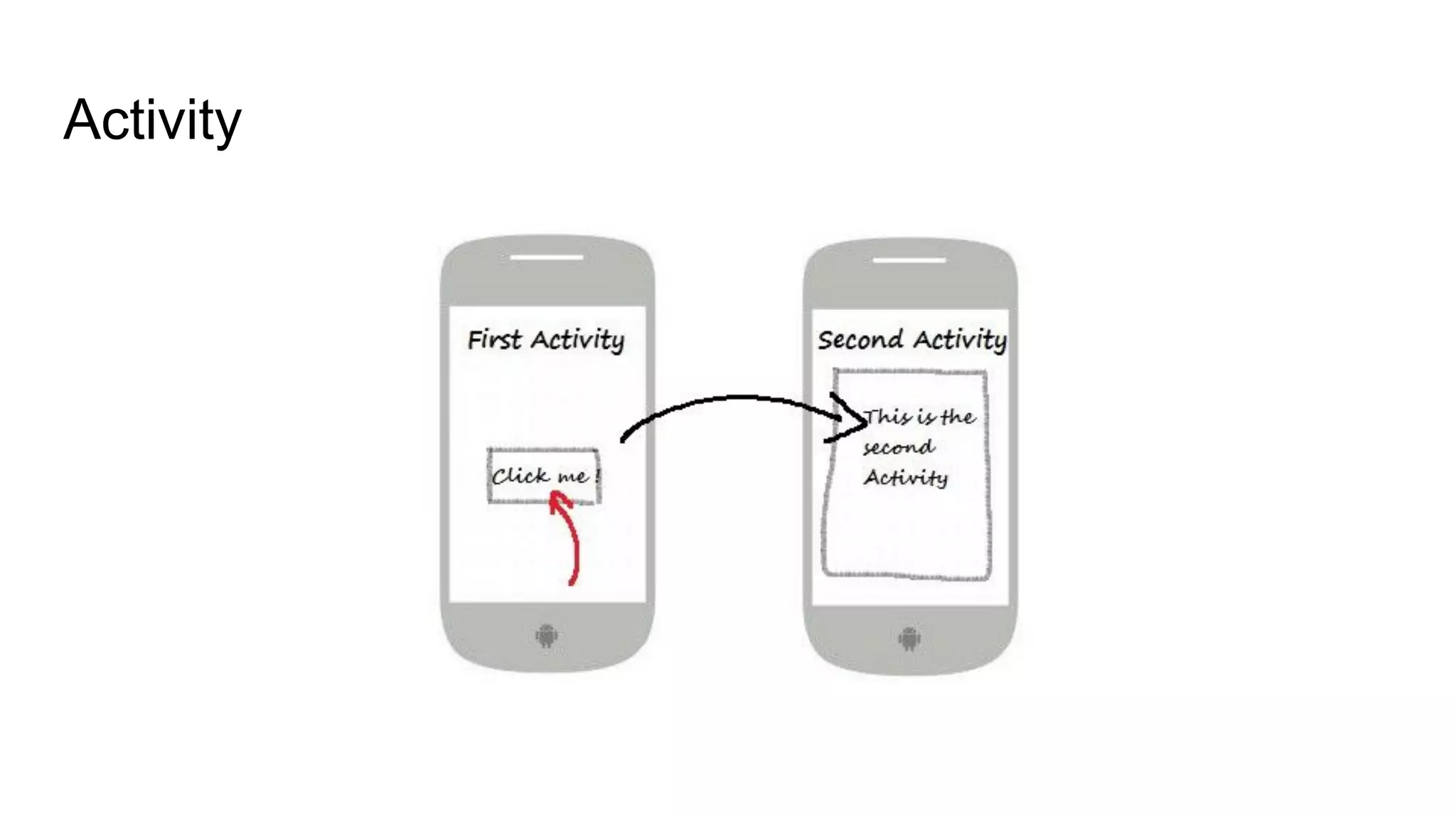
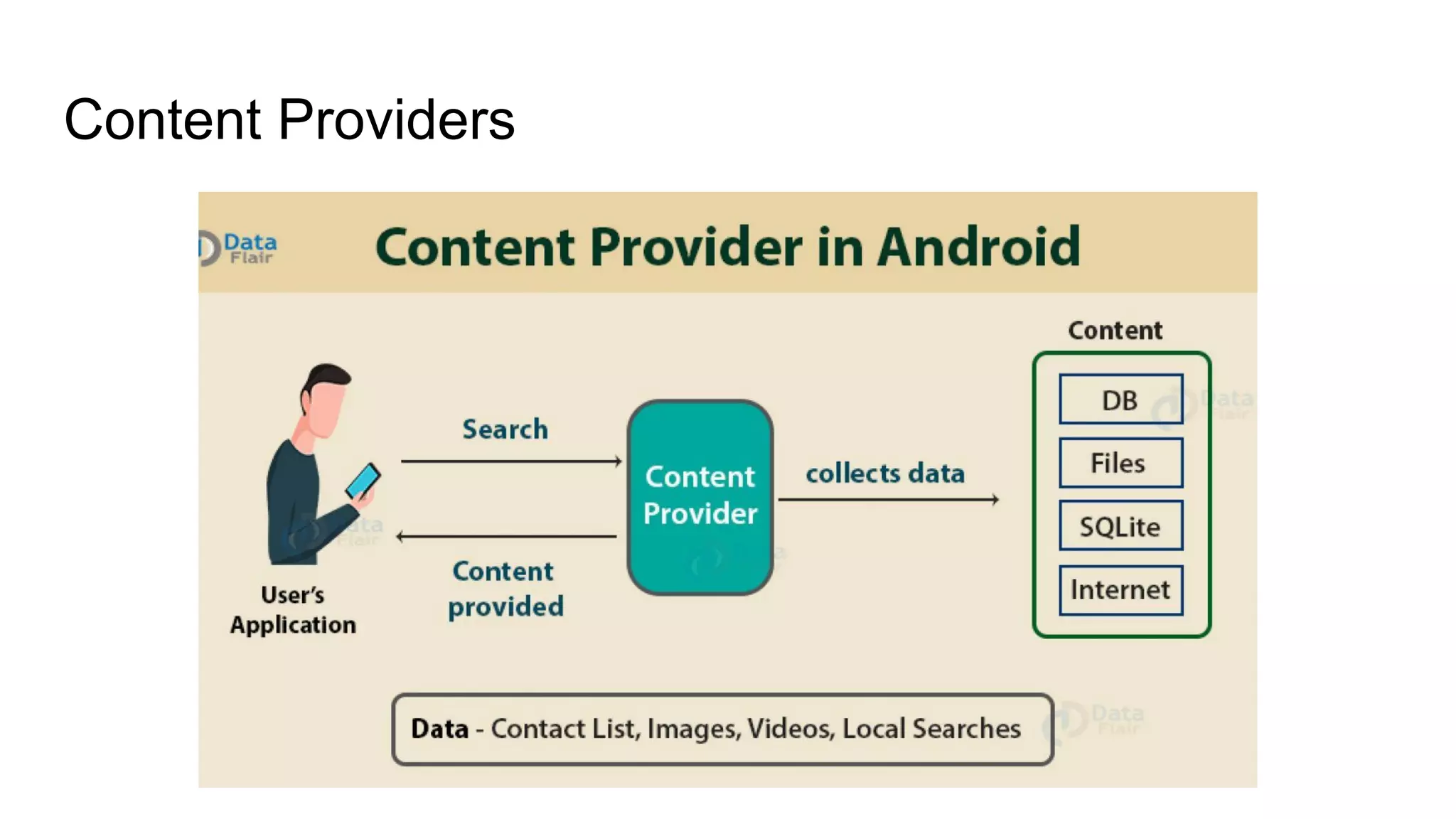
The document outlines tutorials for ethical hacking and penetration testing of Android applications, emphasizing that the information is for educational purposes only and should not be used illegally. It provides setup instructions for using Kali Linux and an Android emulator, as well as tools like Drozer for app testing. Additionally, it details the usage of ADB commands for various operations on Android devices and introduces the Damn Insecure and Vulnerable App (DIVA) for learning about application security flaws.

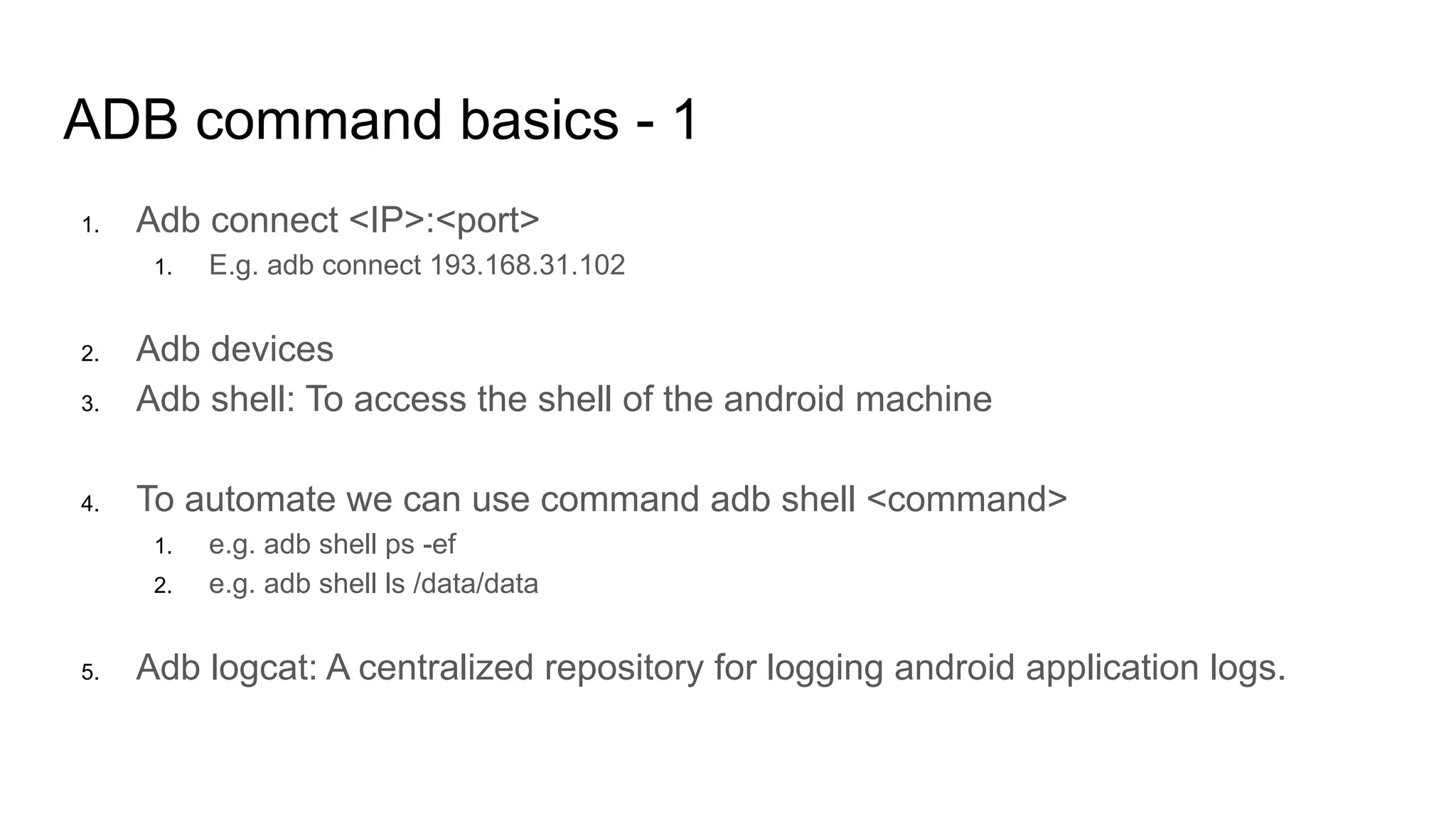
![ADB command basics - 2
1. Adb pull <file-name> : Get a file from the phone to local machine
1. Adb pull /data/app/ssto-pb.apk
2. Adb push <file-name> <mobile location> : To push a file from local machine to
mobile phone.
1. Adb push virus.apk /data/app/
3. Application Installation command:
1. adb install <app name.apk>
2. adb install -r <app name.apk> [The -r option allows you to re-install or update an existing app
on your device]
3. adb install -s <app name.apk> [The -s option lets you install app to SD card if the app supports
move to SD card feature]](https://image.slidesharecdn.com/androidapplicationpenetrationtesting-200901042135/75/Android-application-penetration-testing-12-2048.jpg)