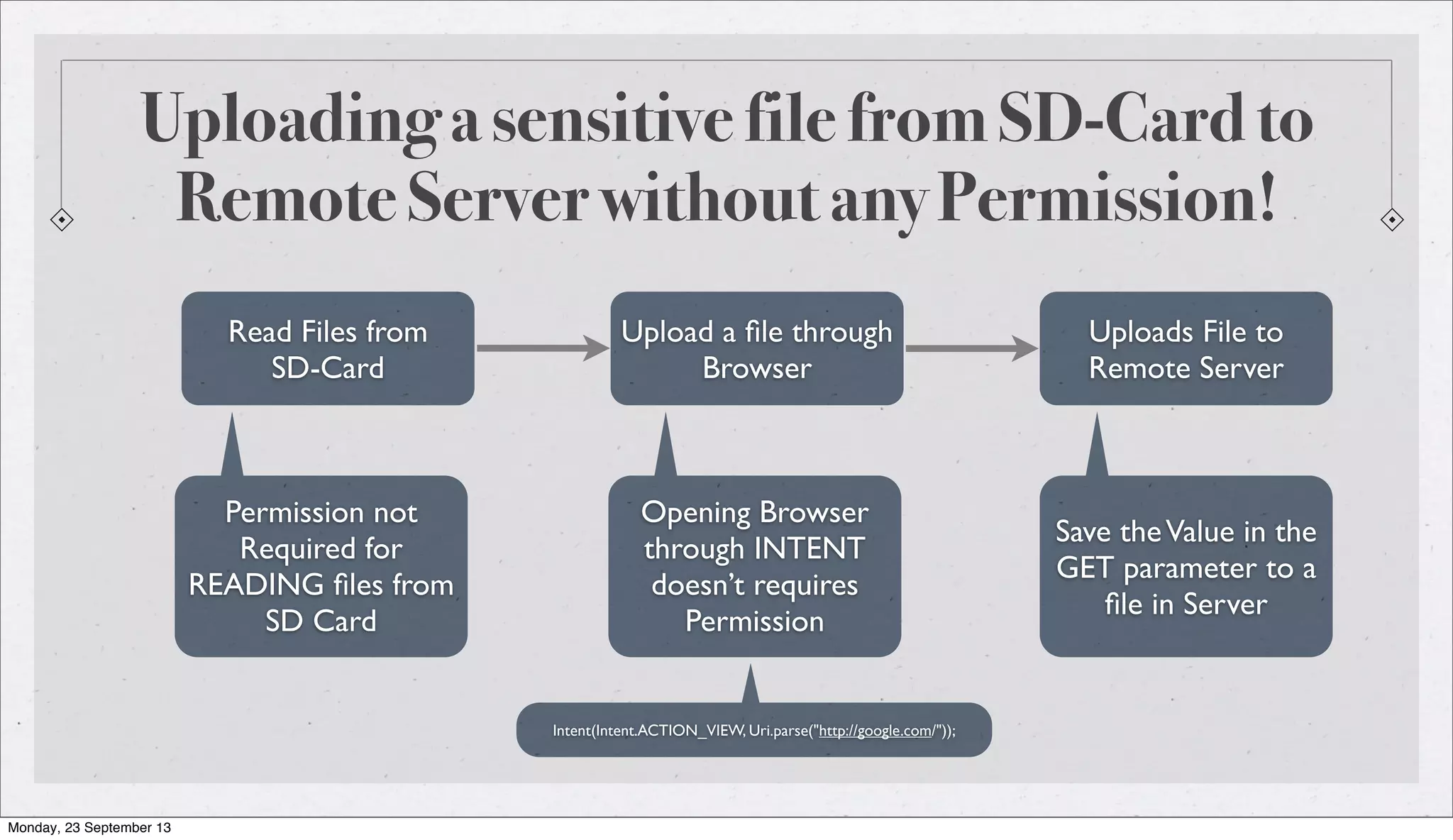
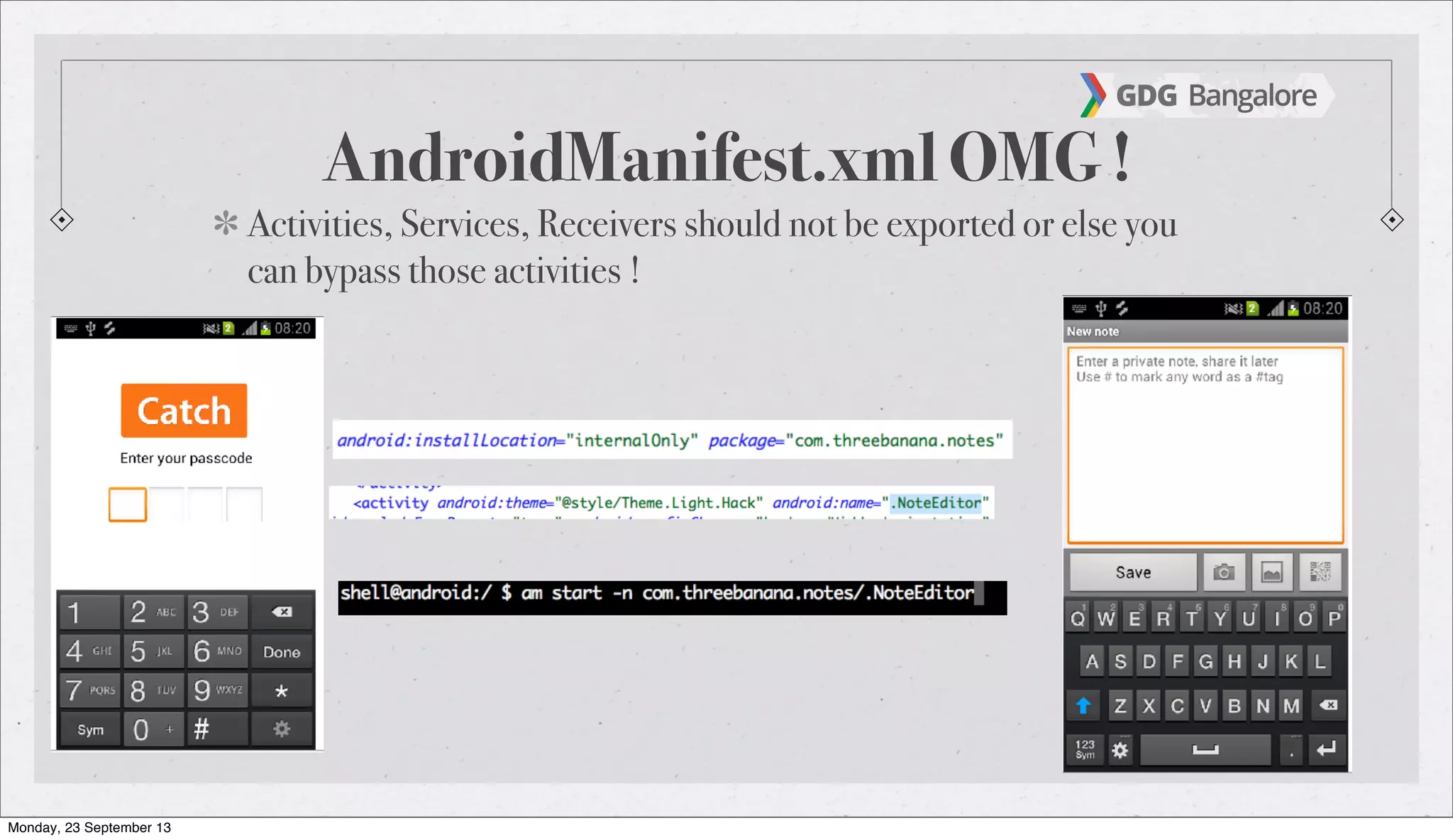
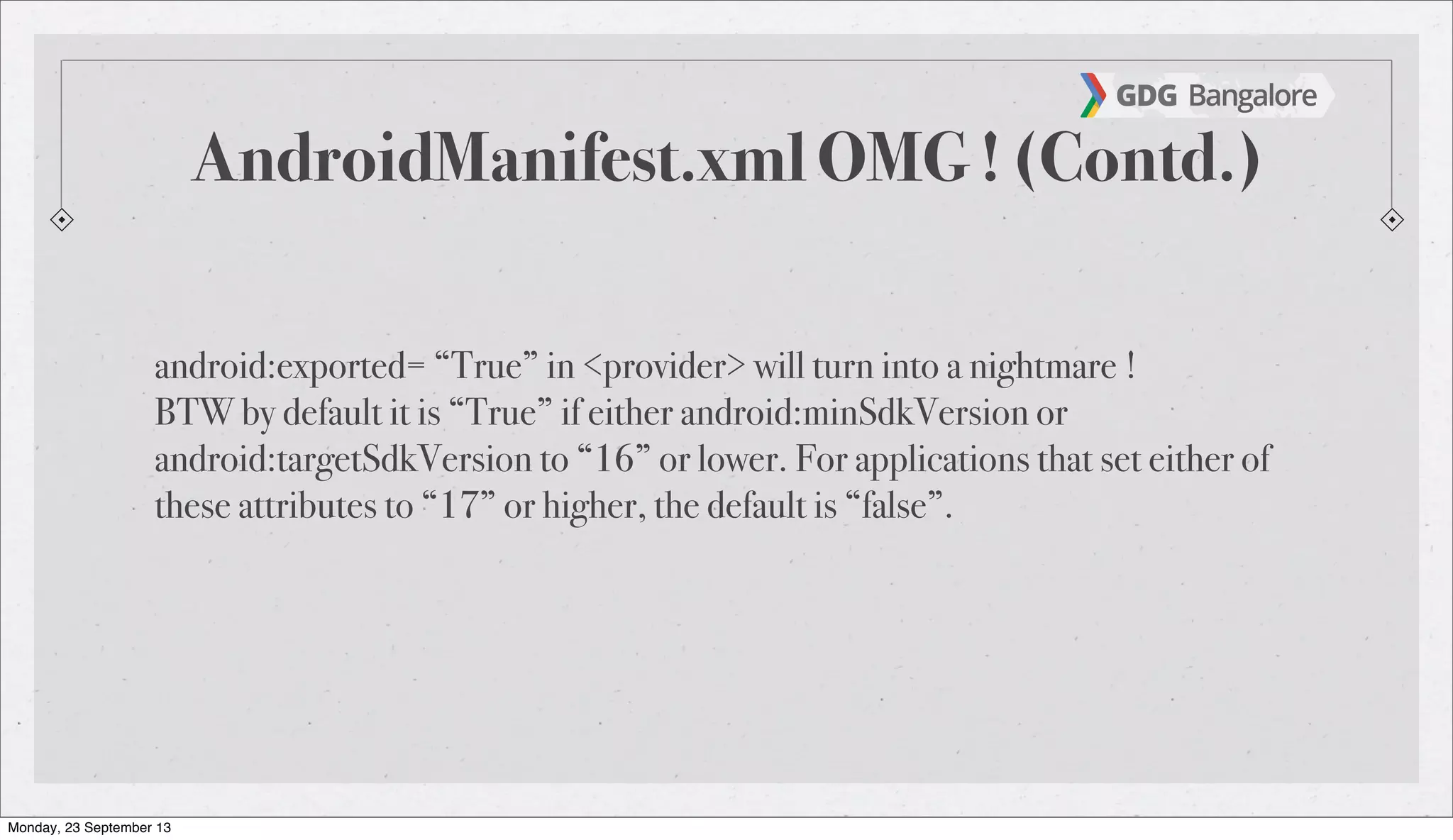
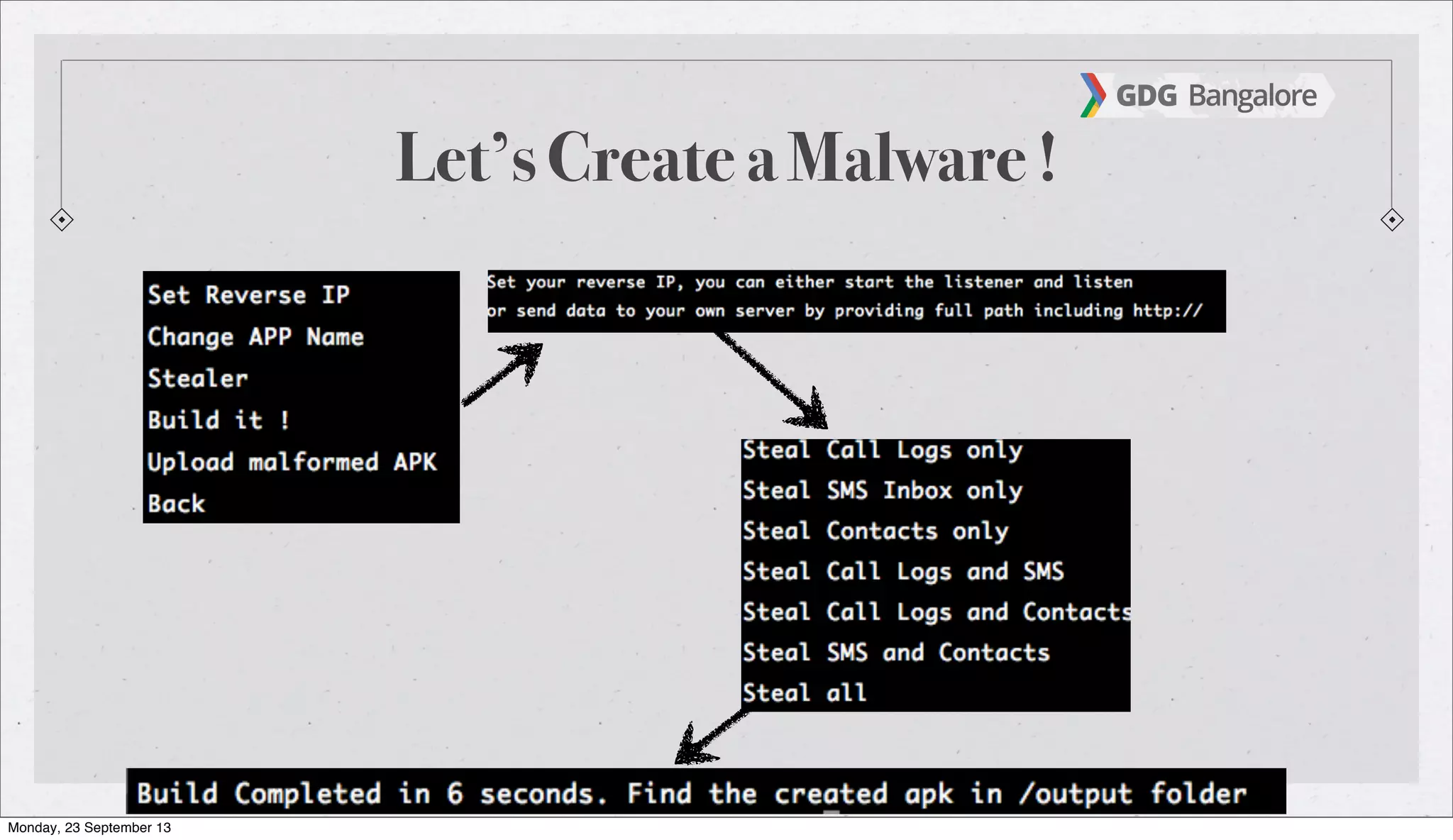
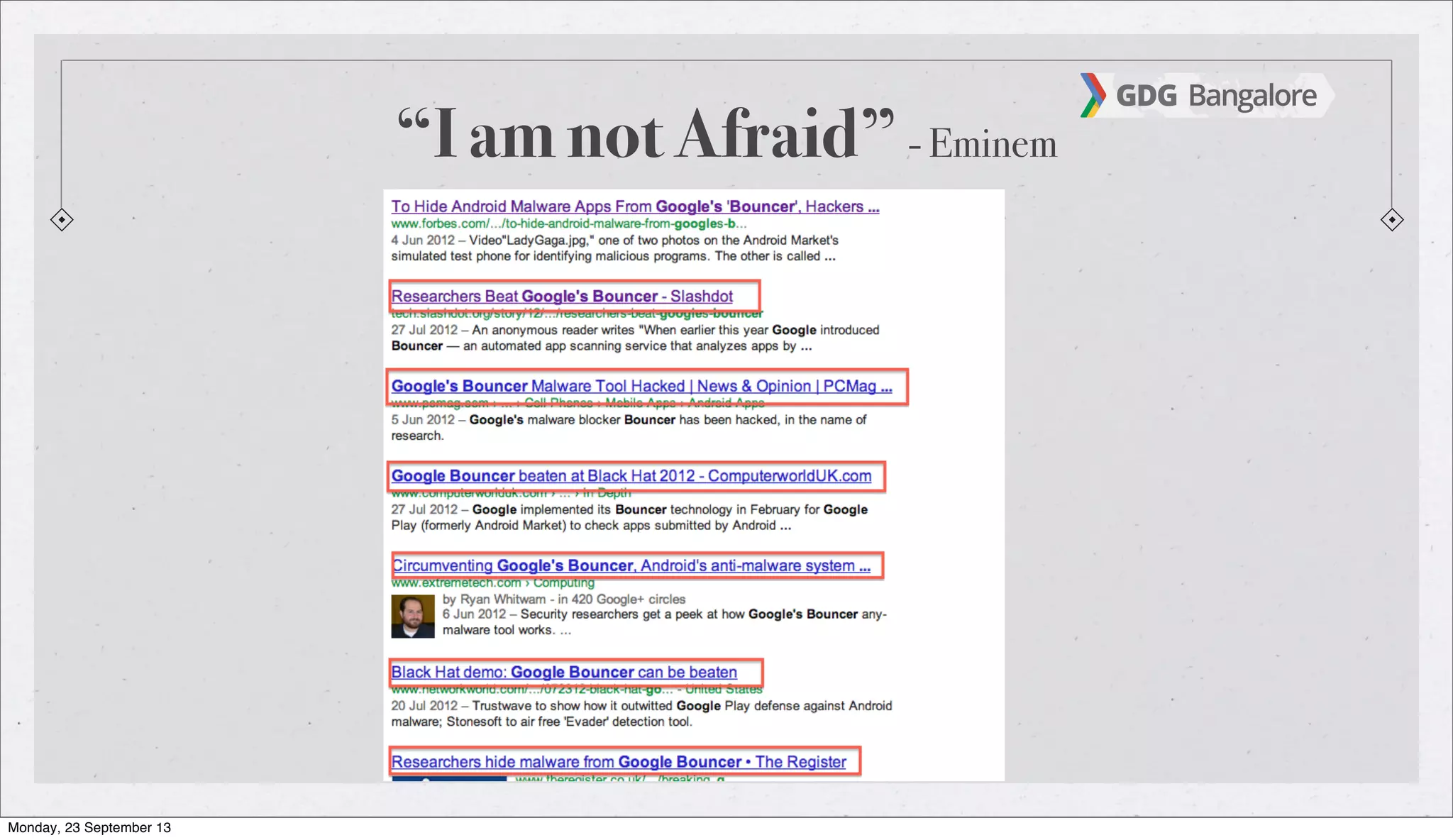
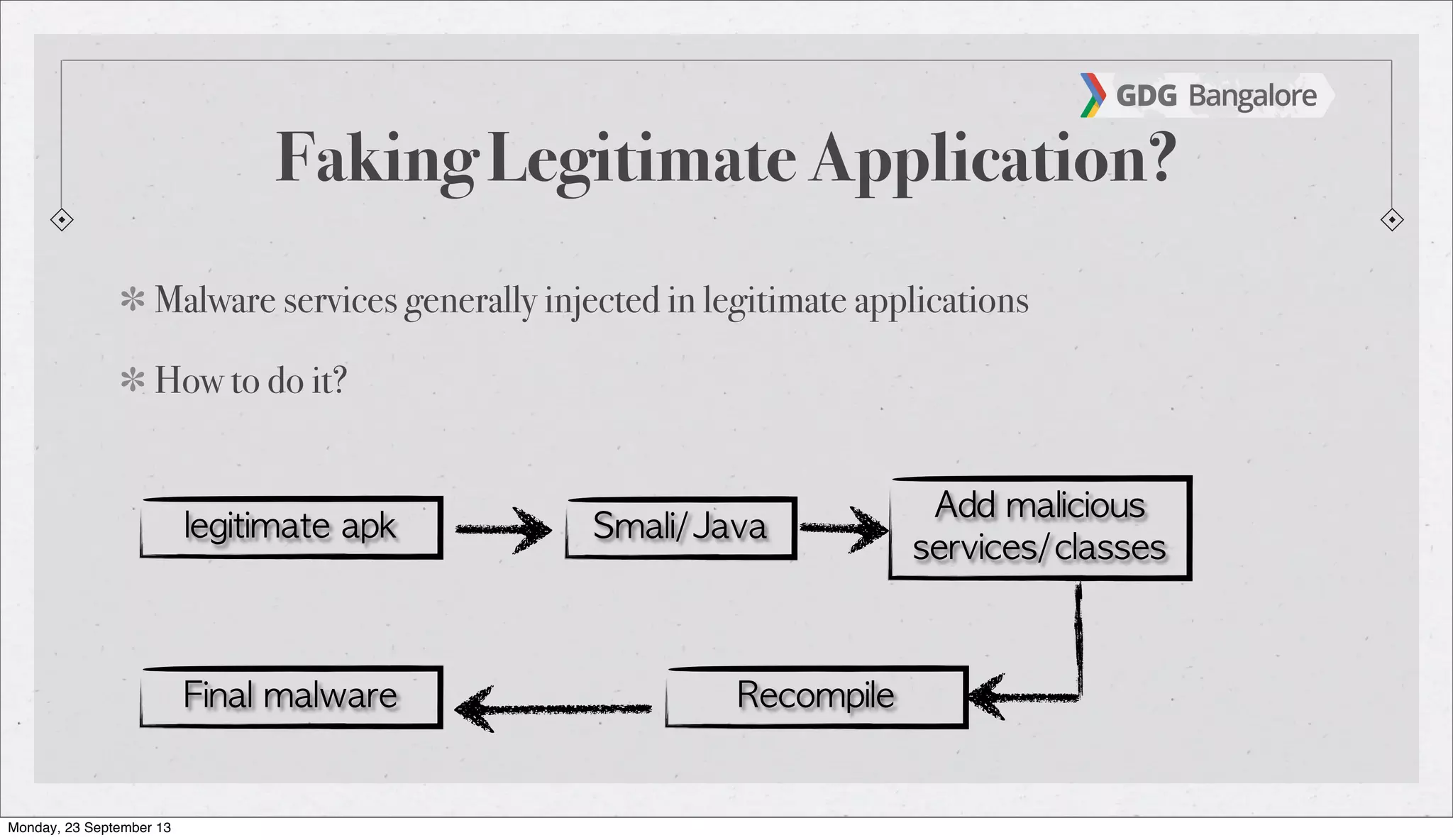
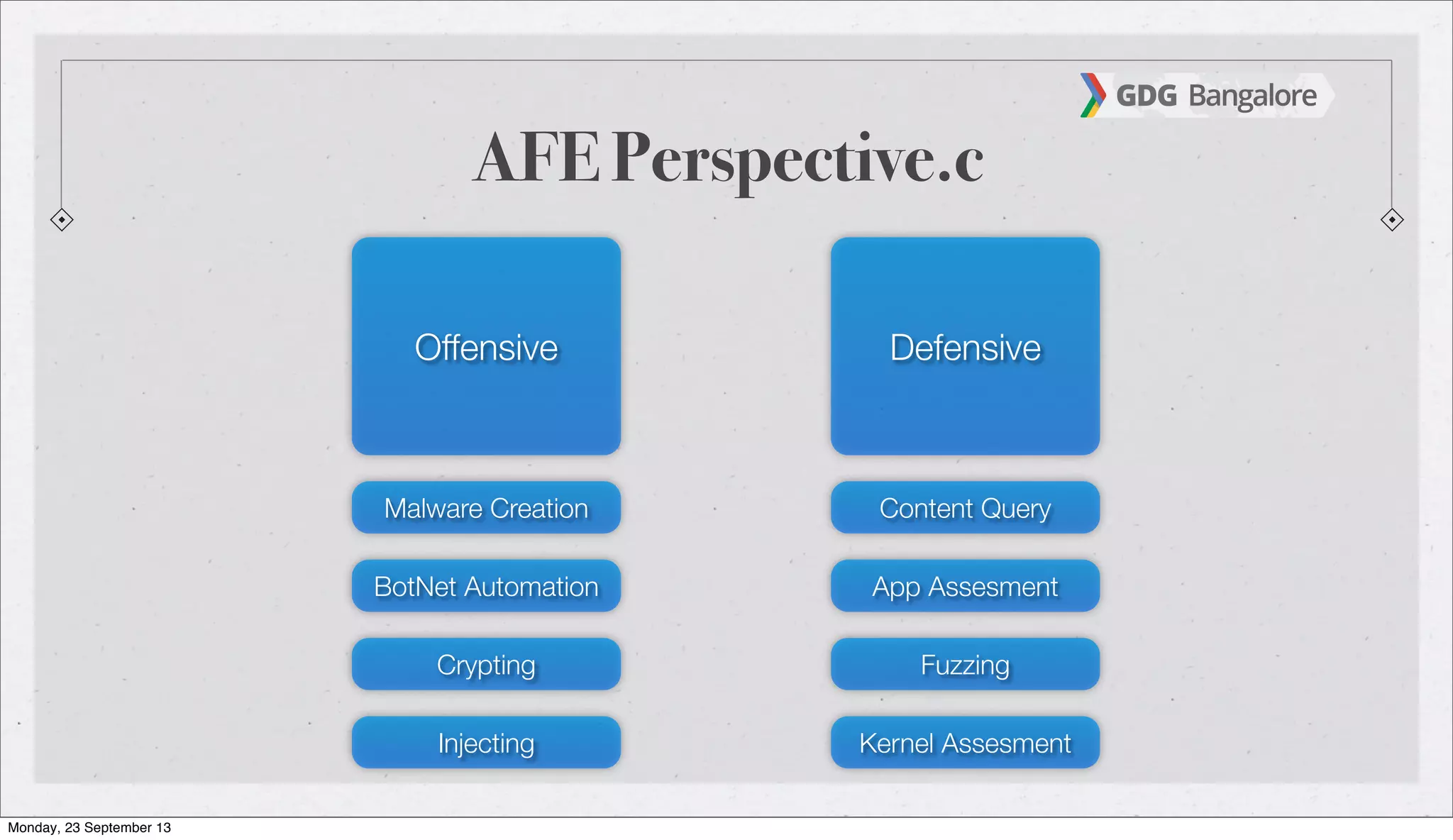
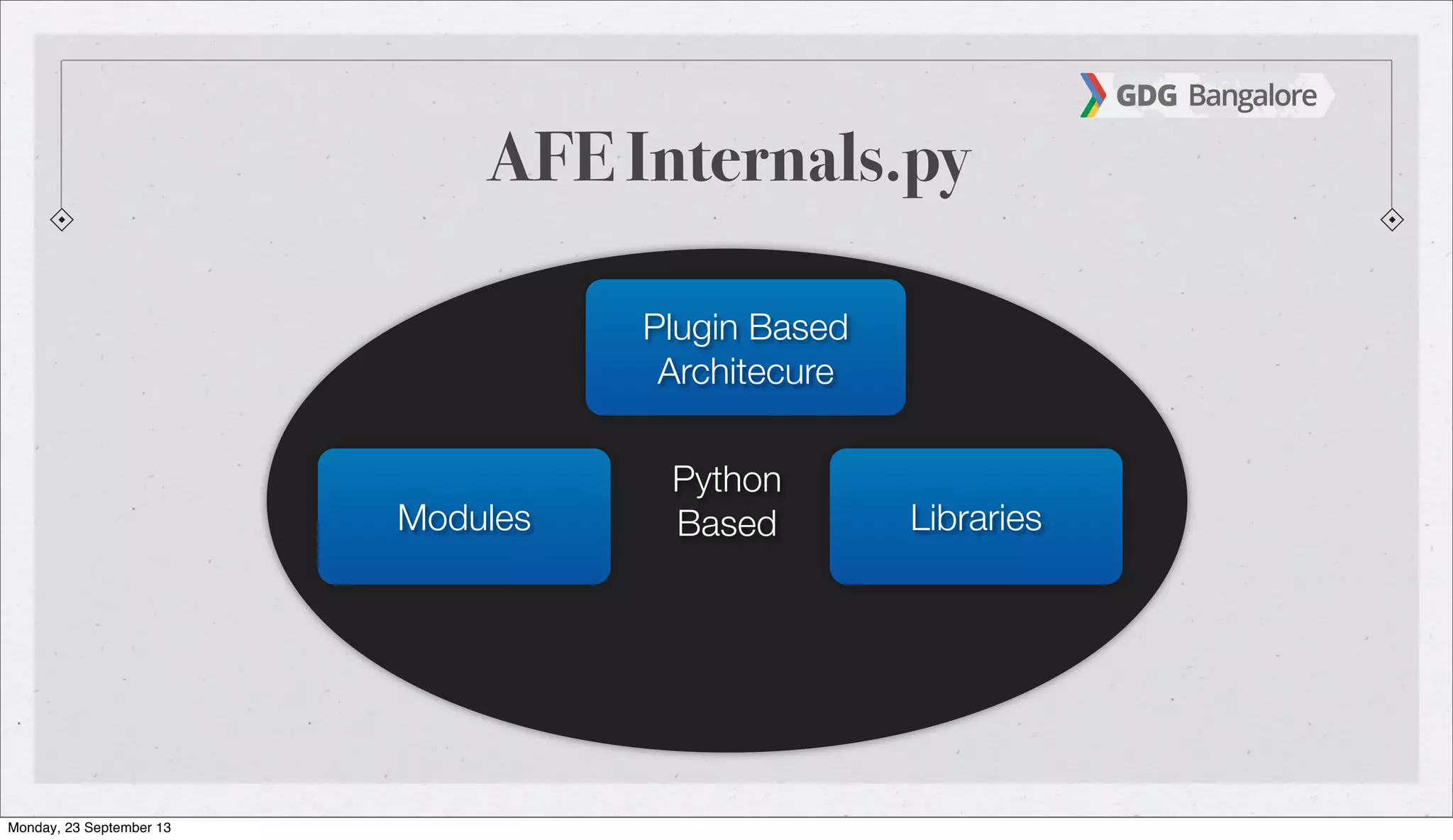
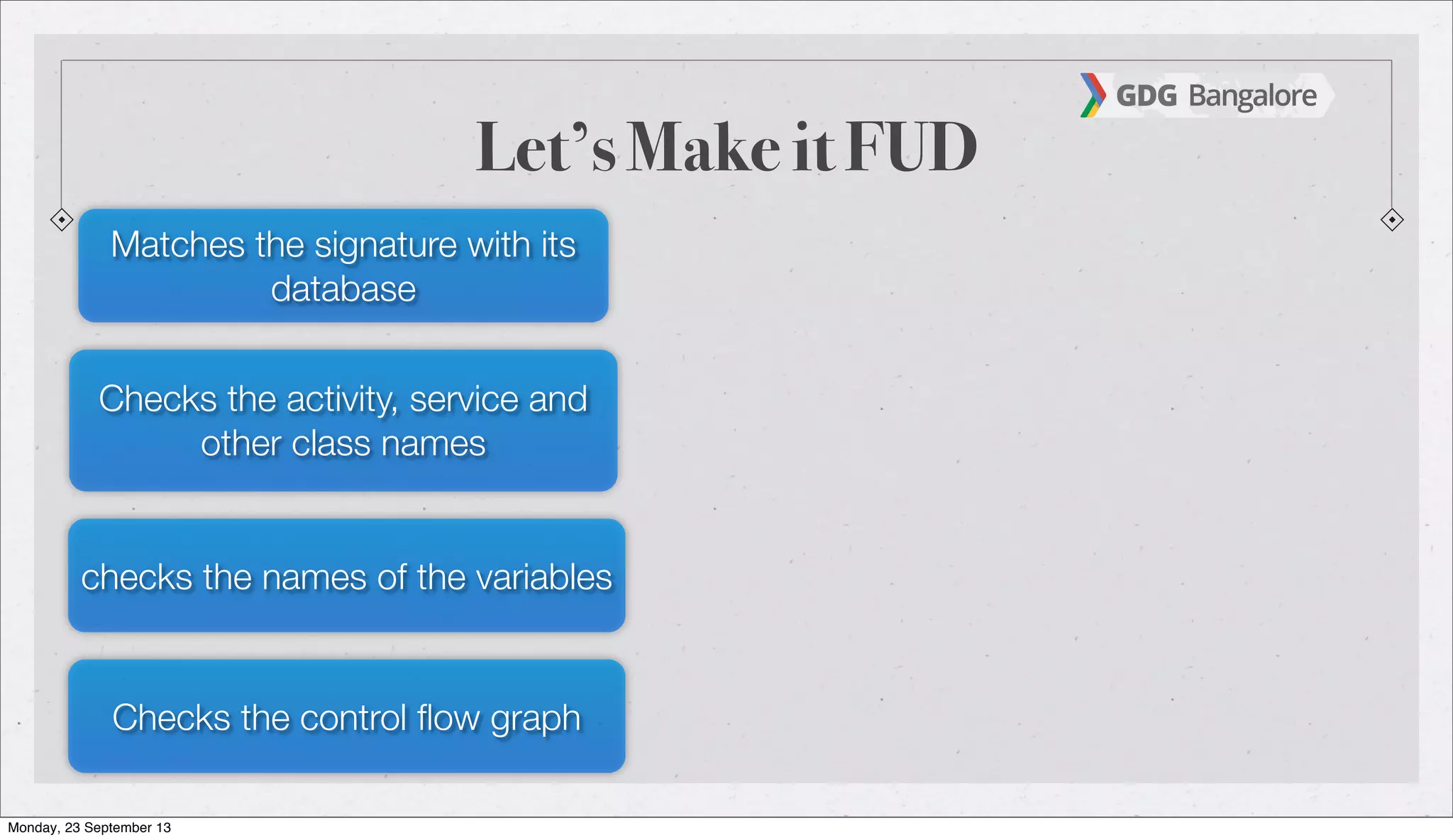
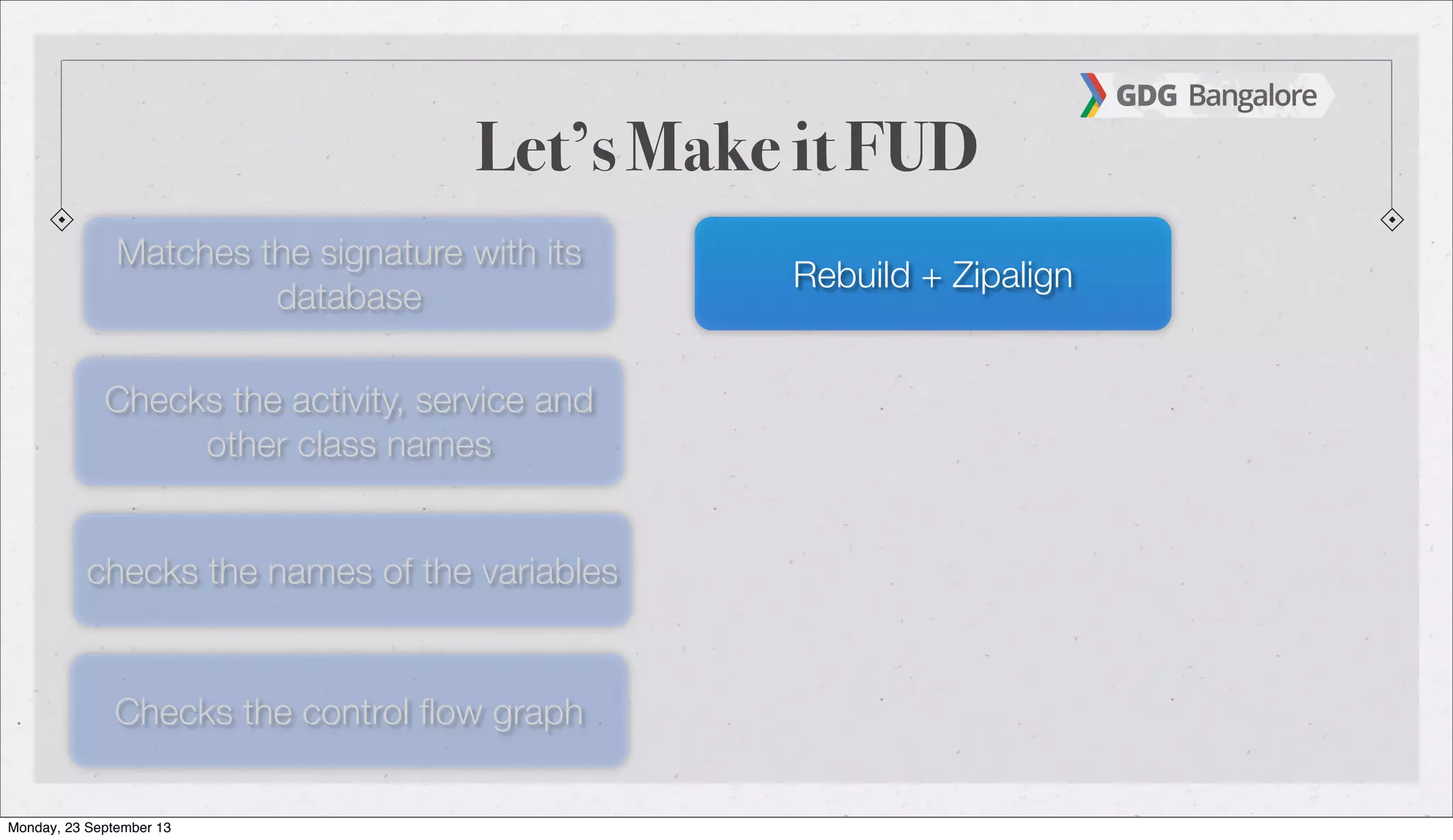
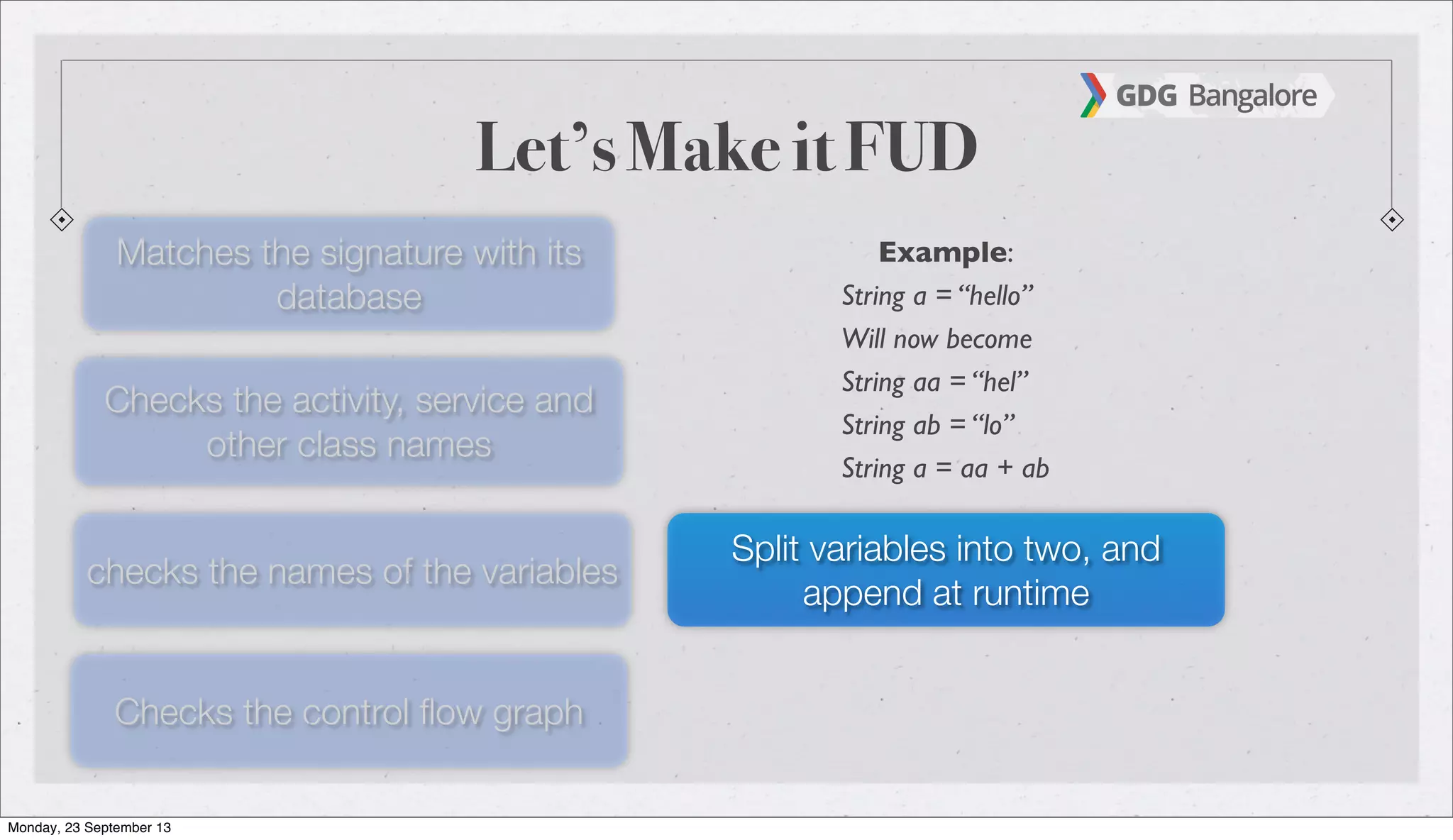
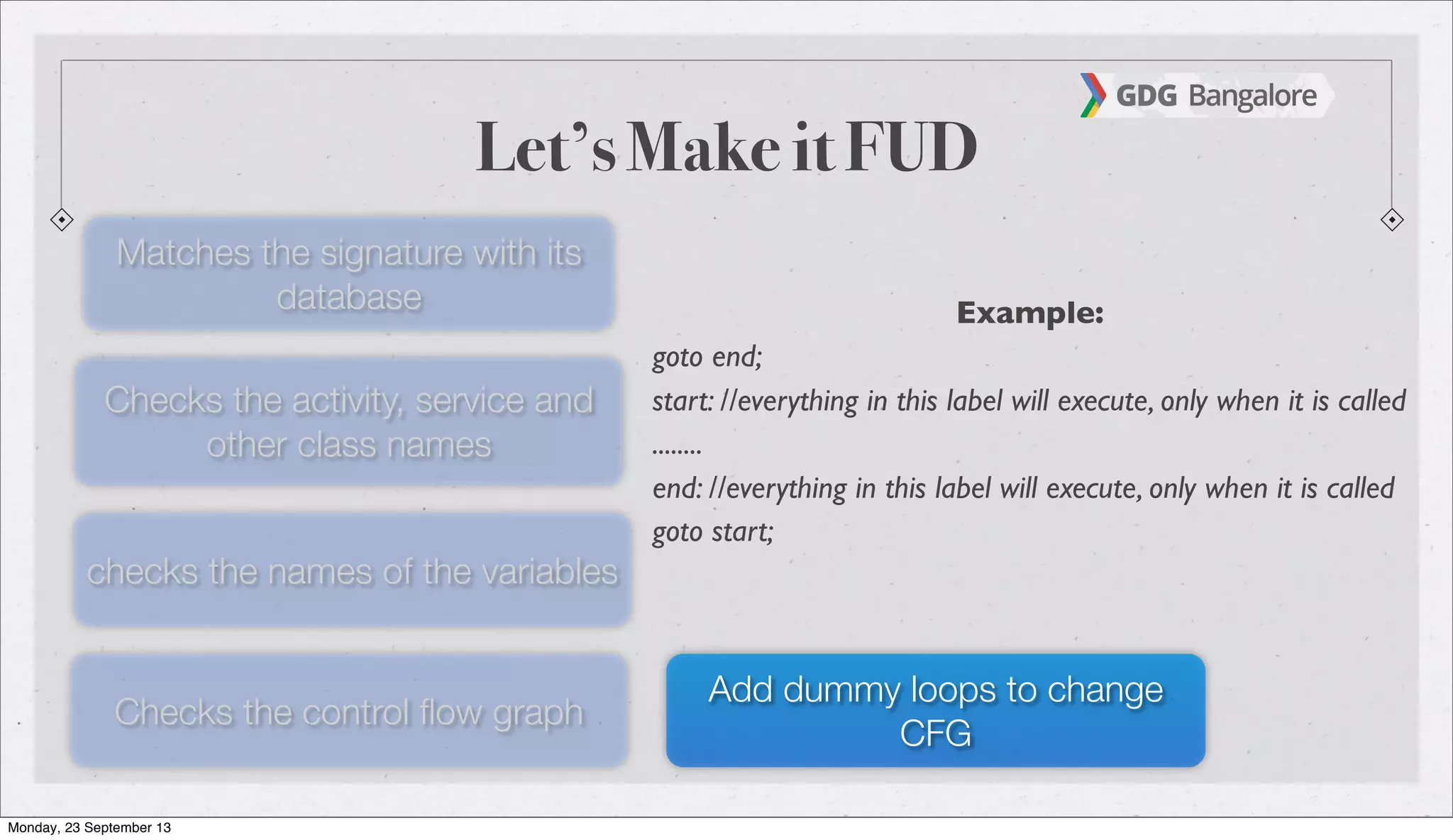
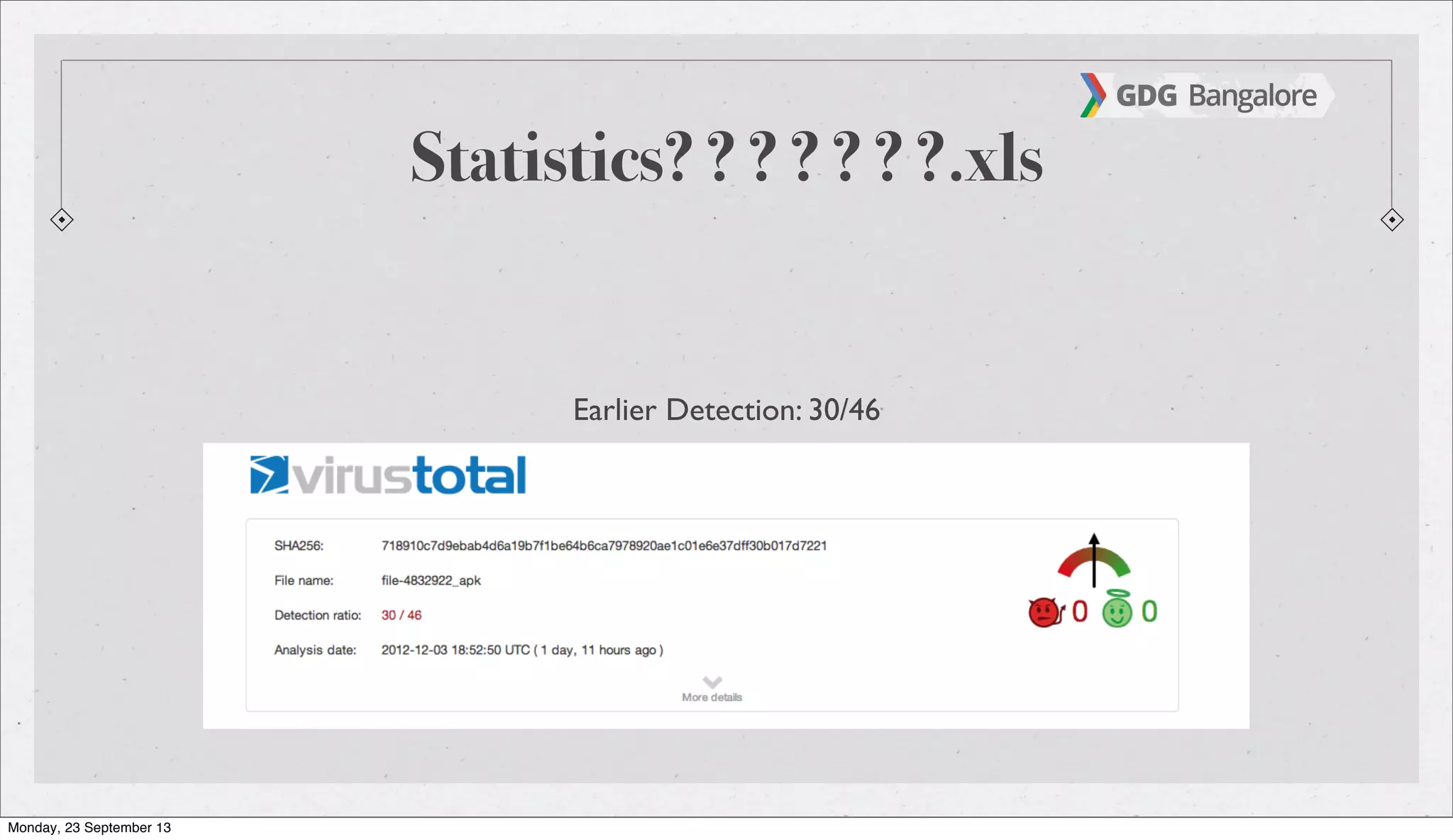
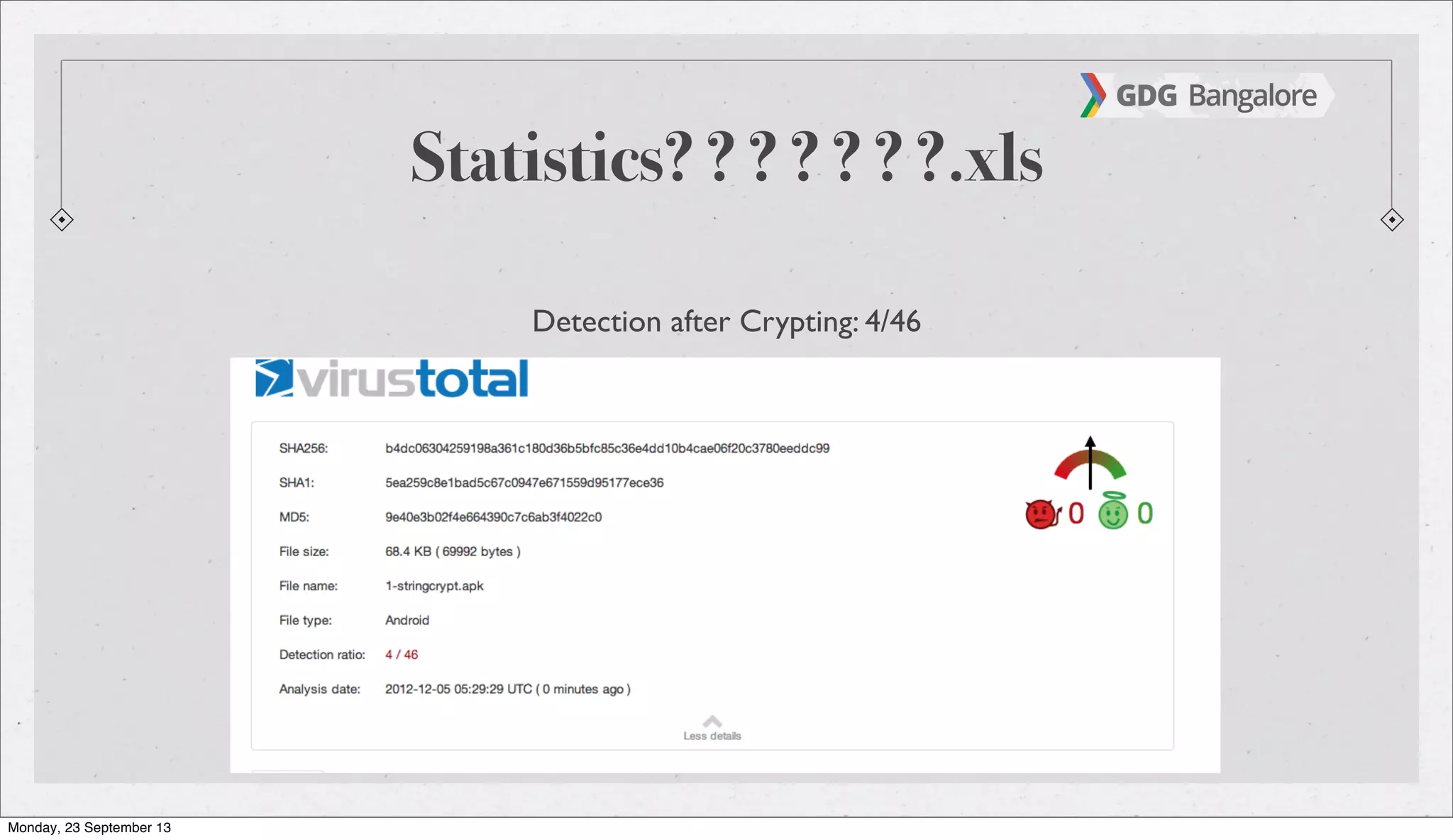
The document is a presentation by Subho Halder on Android security and penetration testing. It covers topics such as Android internals, the security model, best coding practices, and common malware techniques, highlighting vulnerabilities and exploitation methods using the Android Framework for Exploitation (AFE). Additionally, it emphasizes the importance of security measures and dynamic analysis to protect against malware threats.