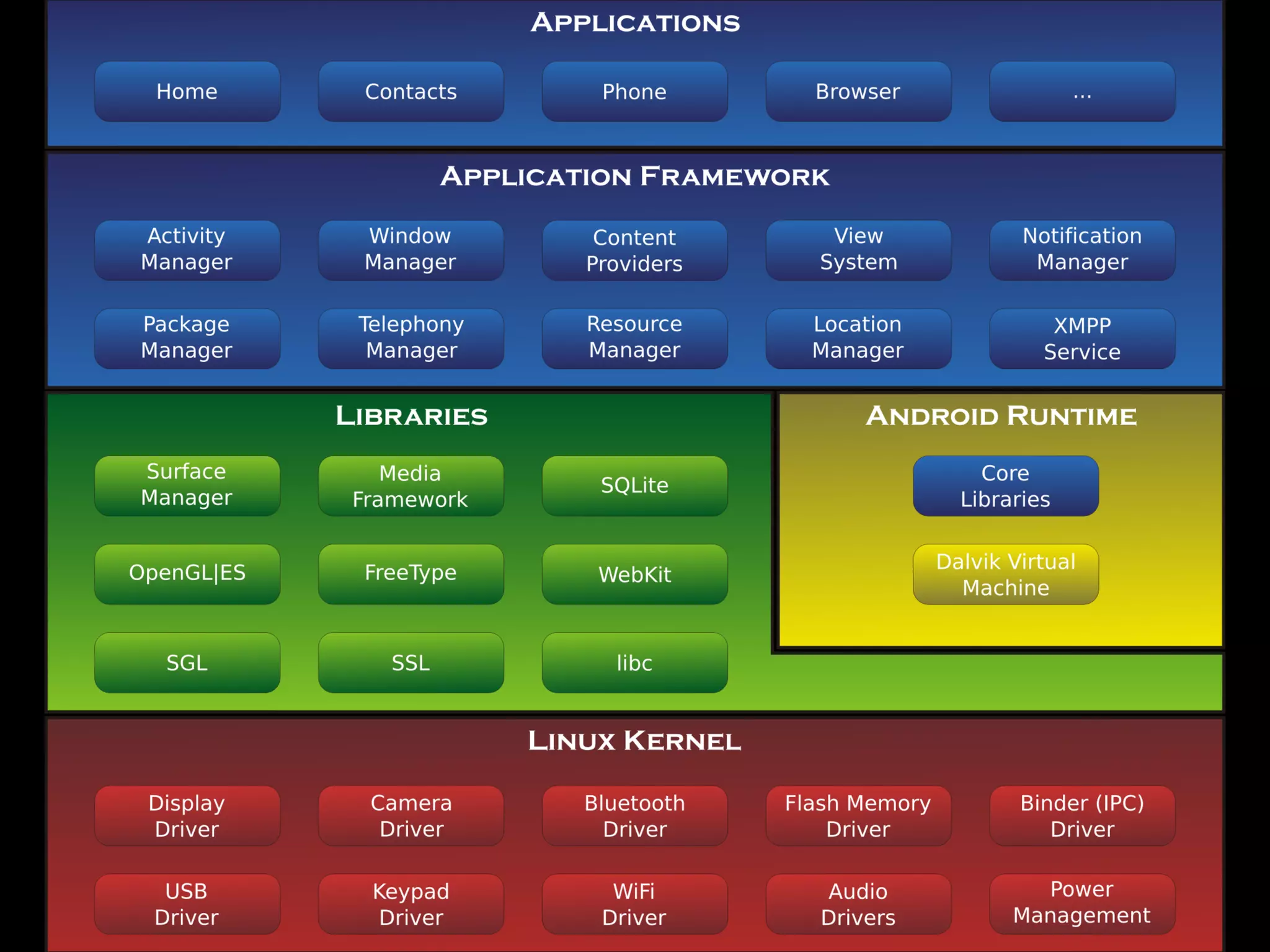
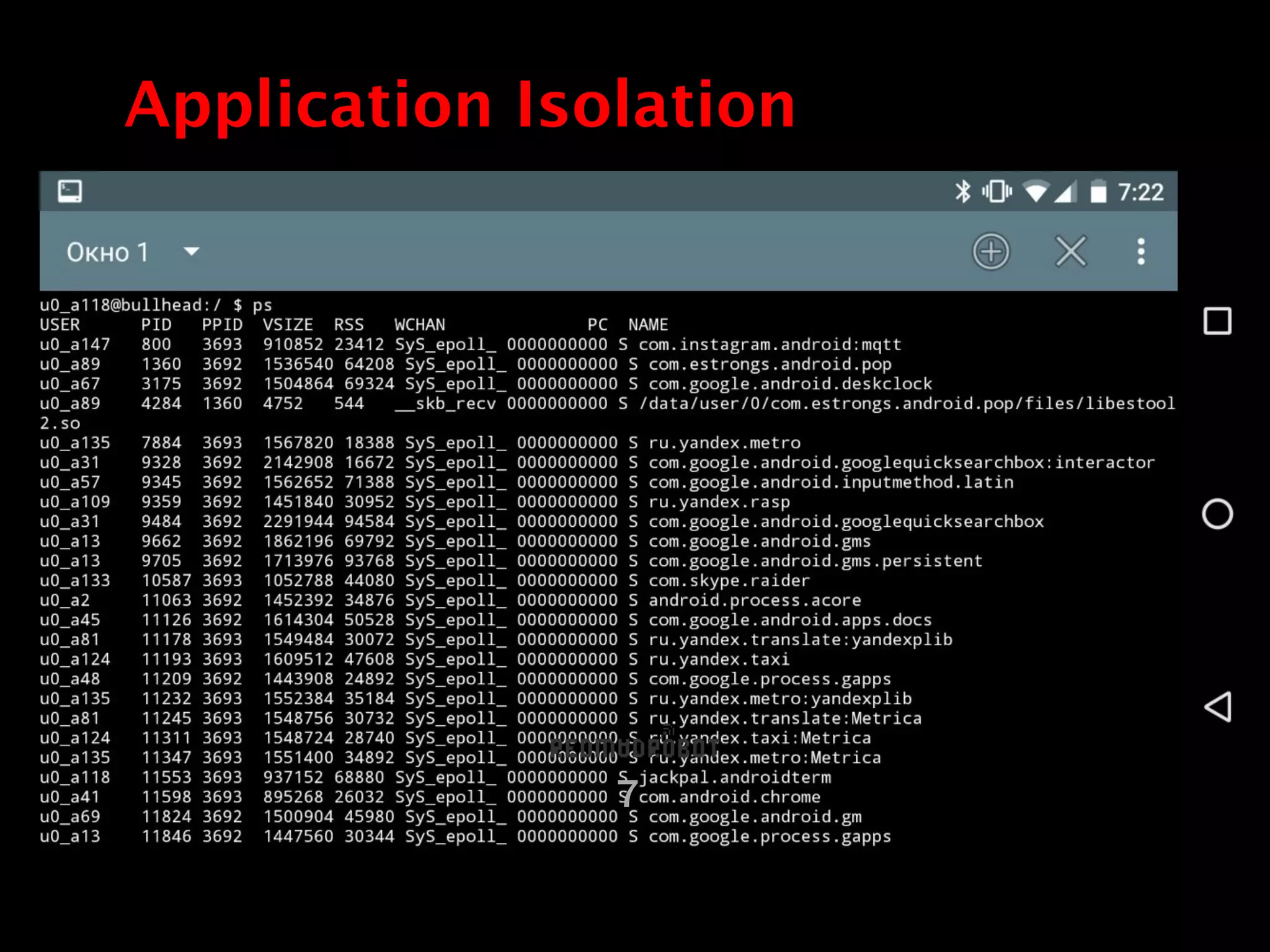
The document discusses security in Android applications. It begins by introducing the author and their background. The agenda then outlines that it will cover the Android security model, realities that differ from the official model, common vulnerabilities, and additional resources. It delves into the official security features like application isolation, permissions, and data storage protections. However, it notes realities like the prevalence of rooting that undermine the official protections. It details several common vulnerabilities in areas like data storage, network traffic, and application intents. It concludes by emphasizing the need for layered security rather than relying solely on the official Android protections.










![- Custom keyboard
- Secure persistent datastore
- No EditText
- No immutable (Strings -> char[])
- Notify if root
Insecure Device
19](https://image.slidesharecdn.com/2smirnov-2-160414073411/75/Security-in-Android-Application-RedMadRobot-19-2048.jpg)