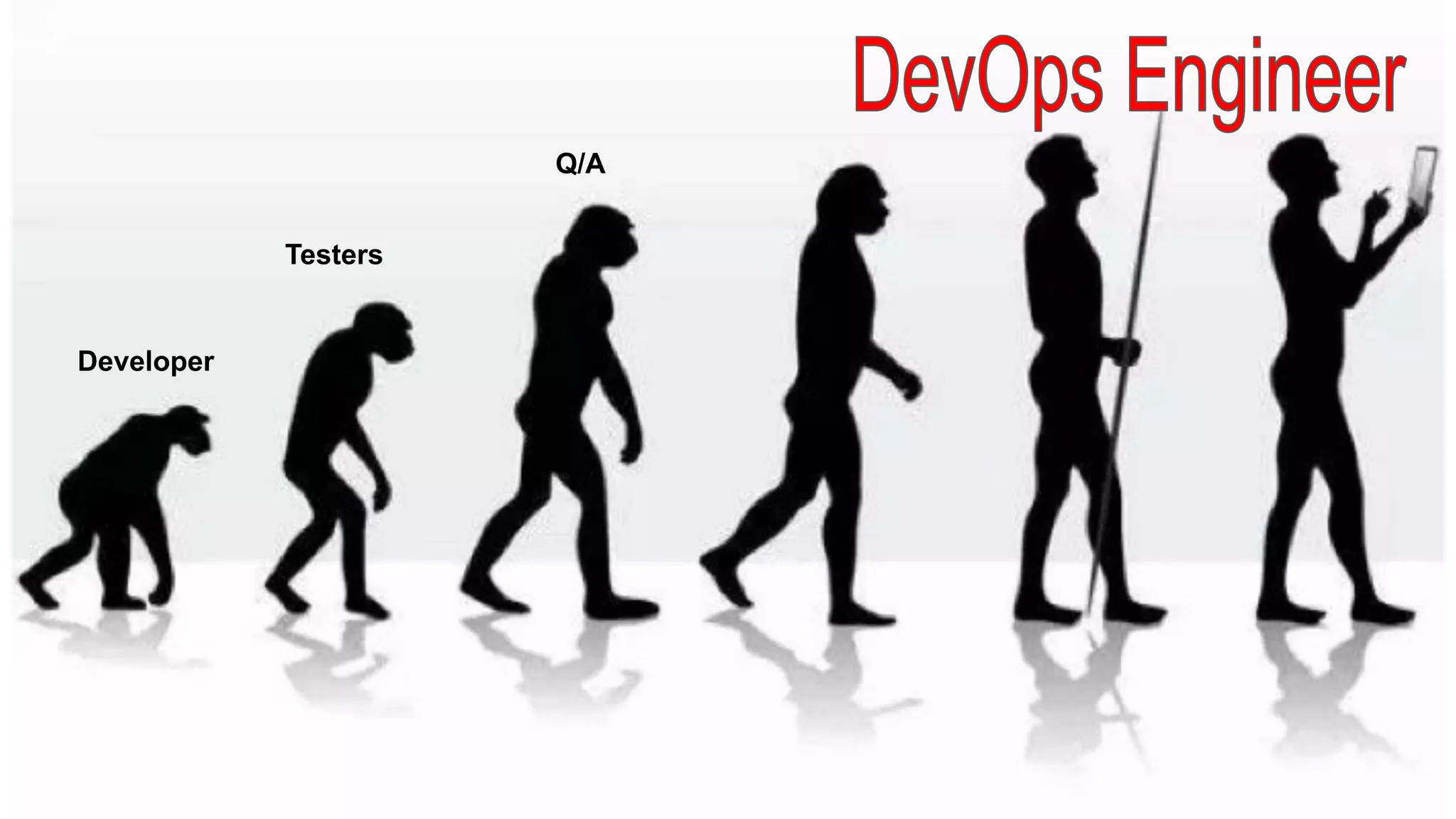
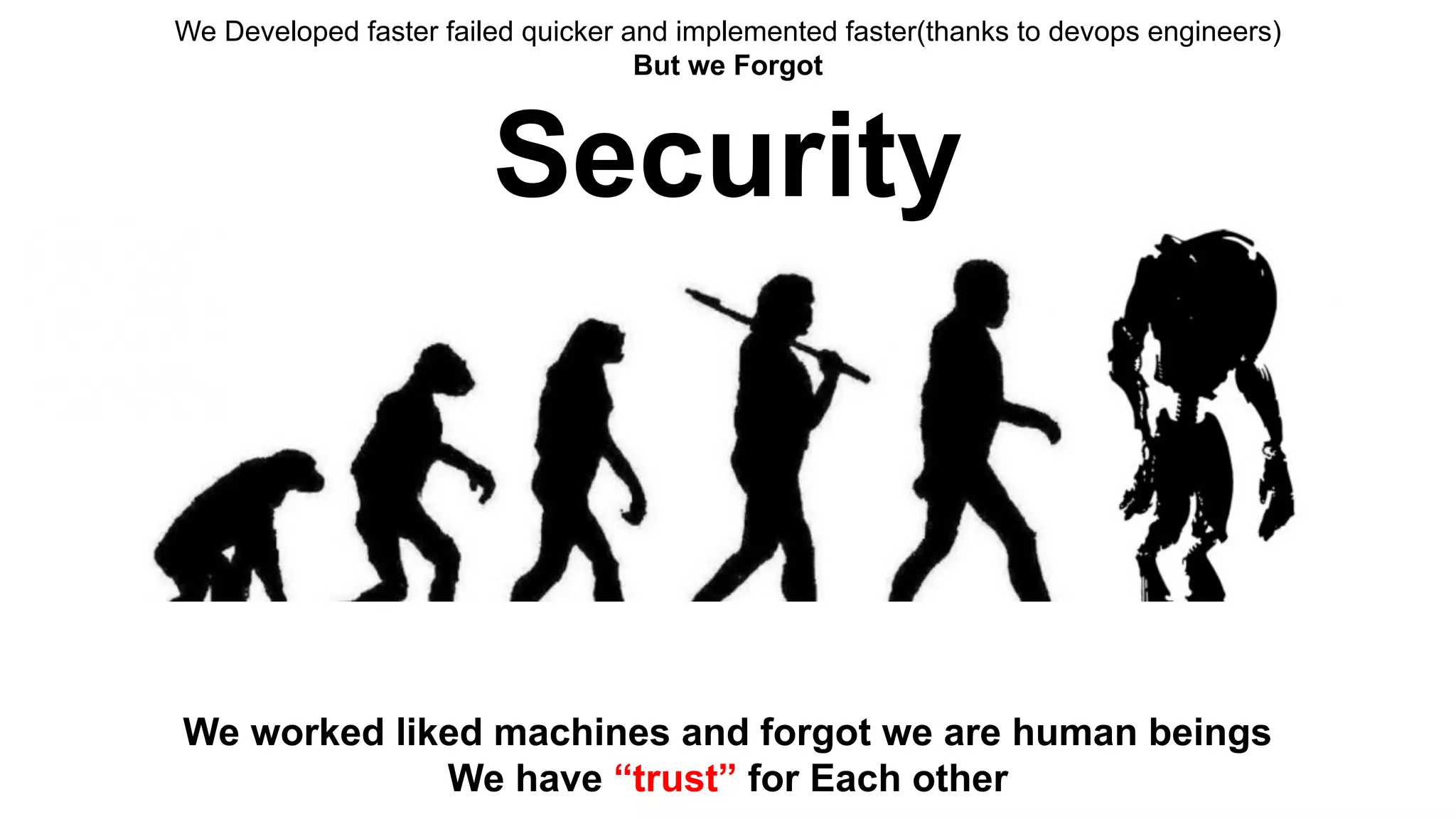
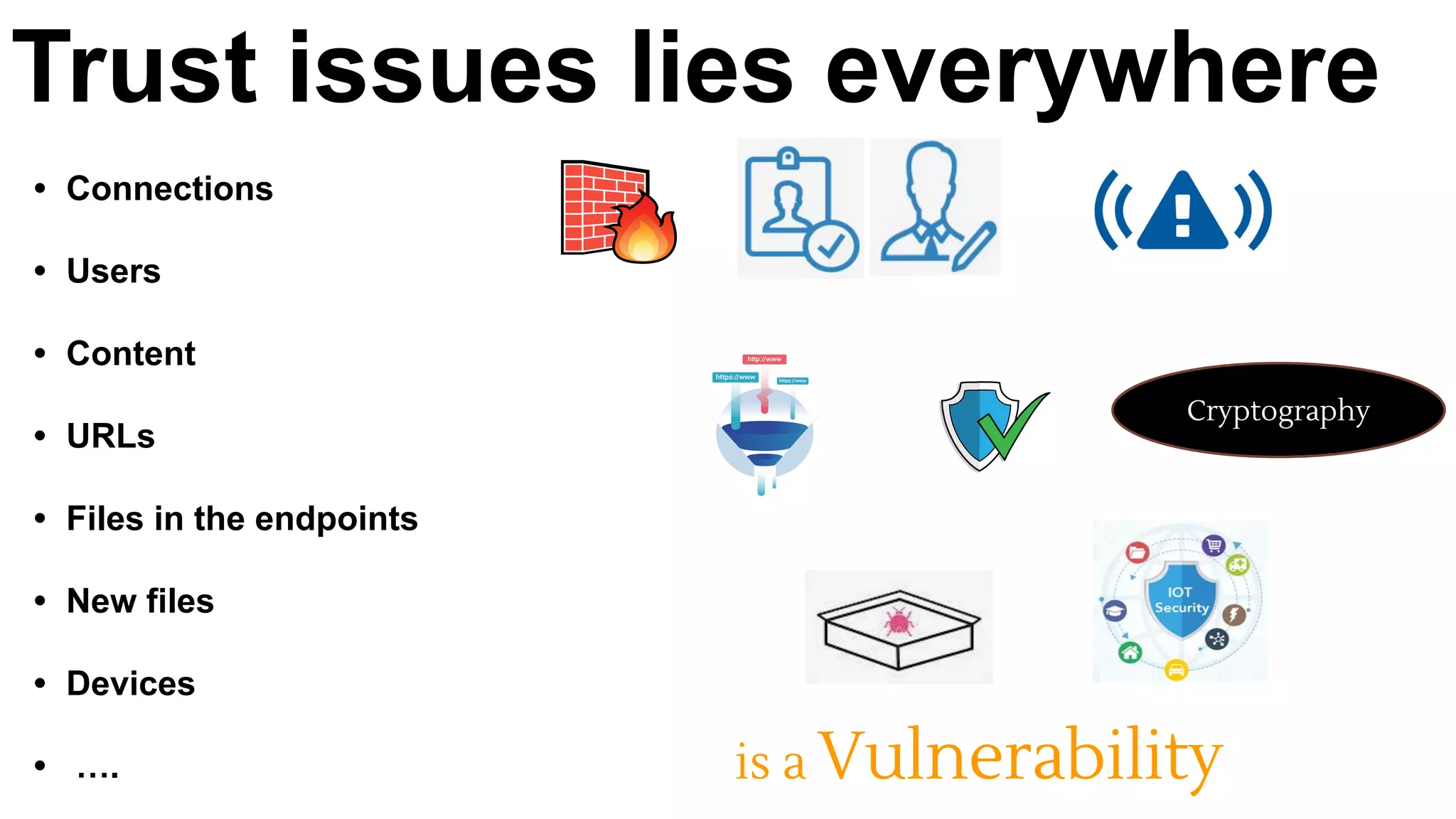
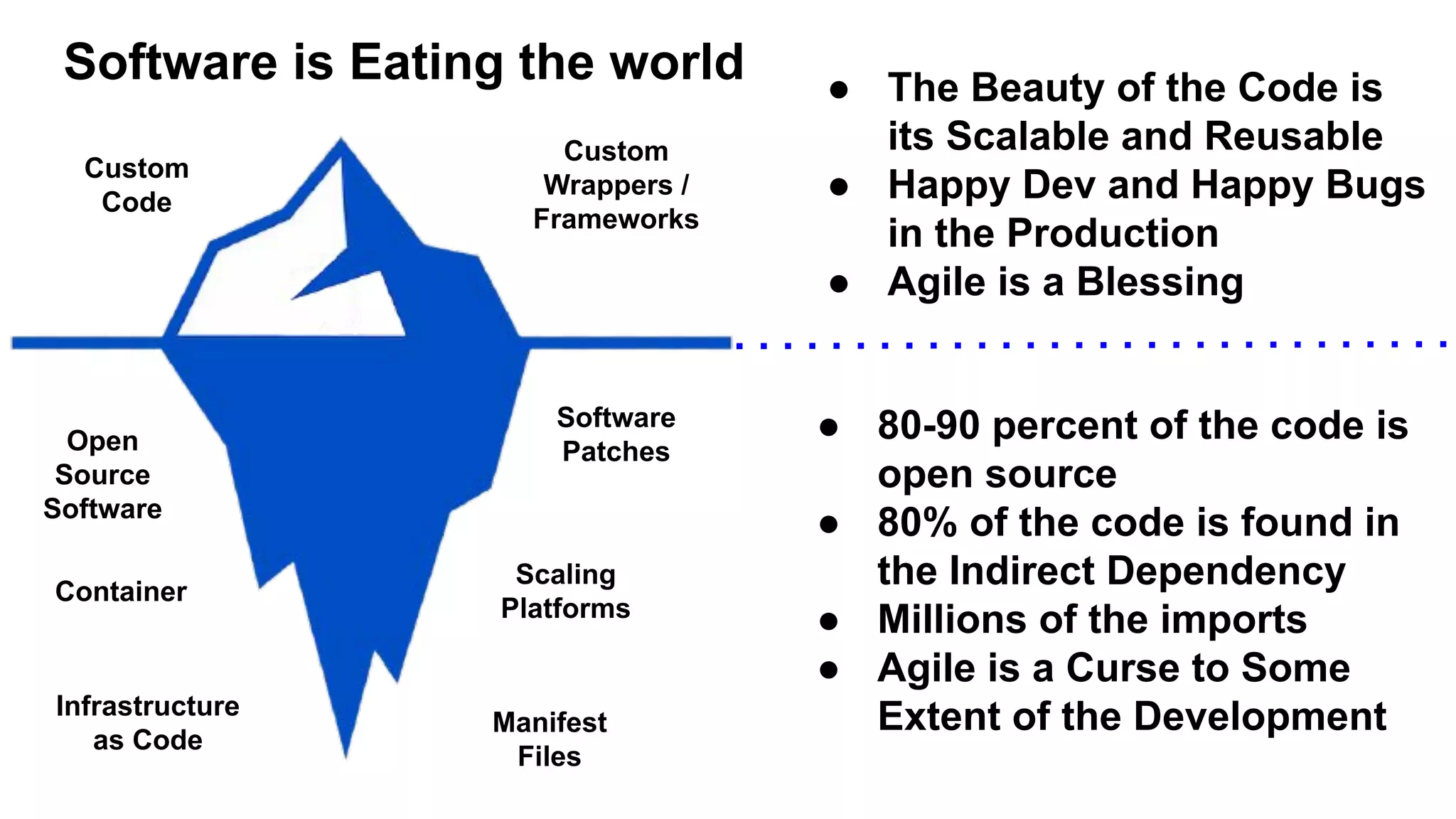
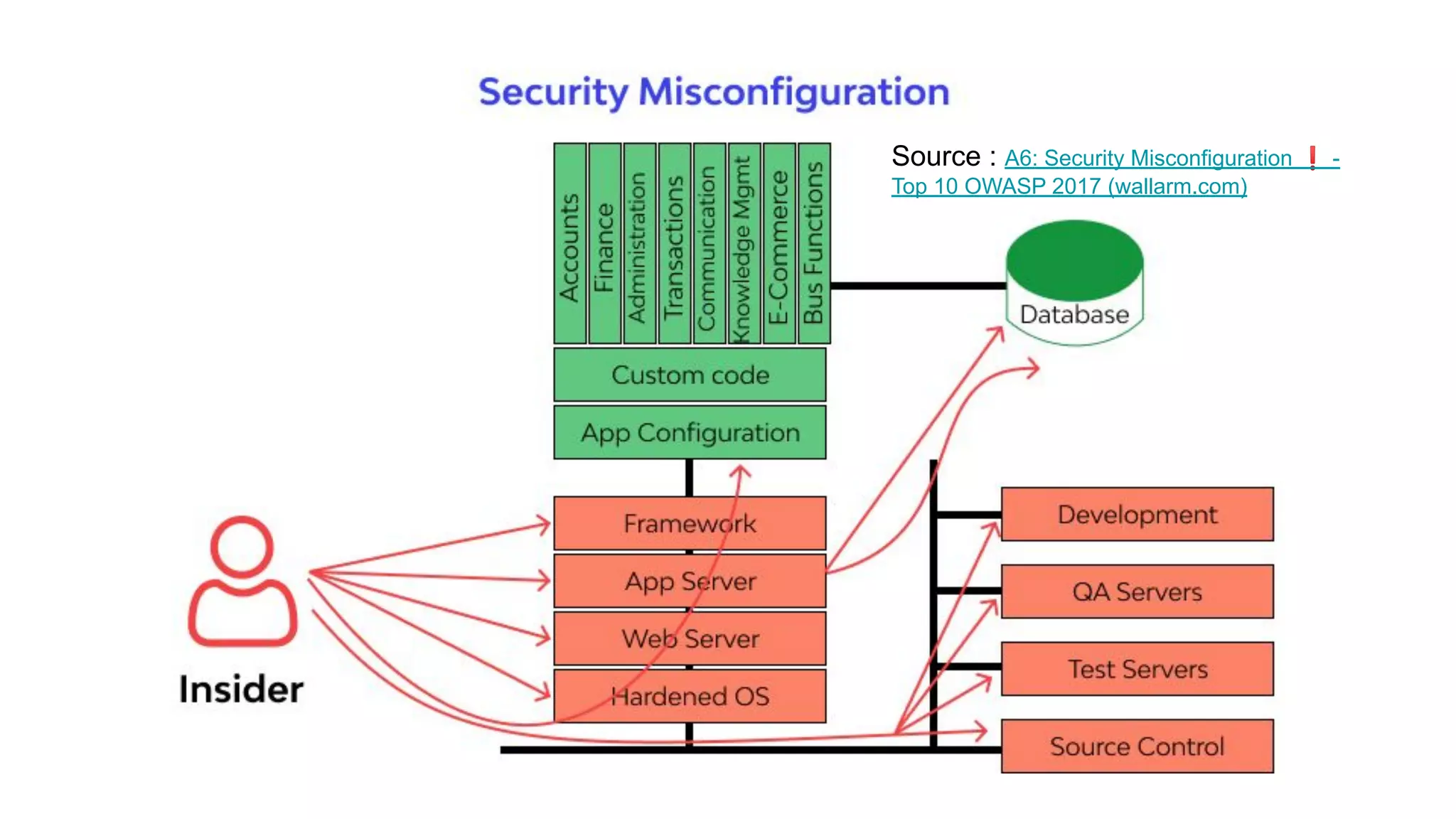
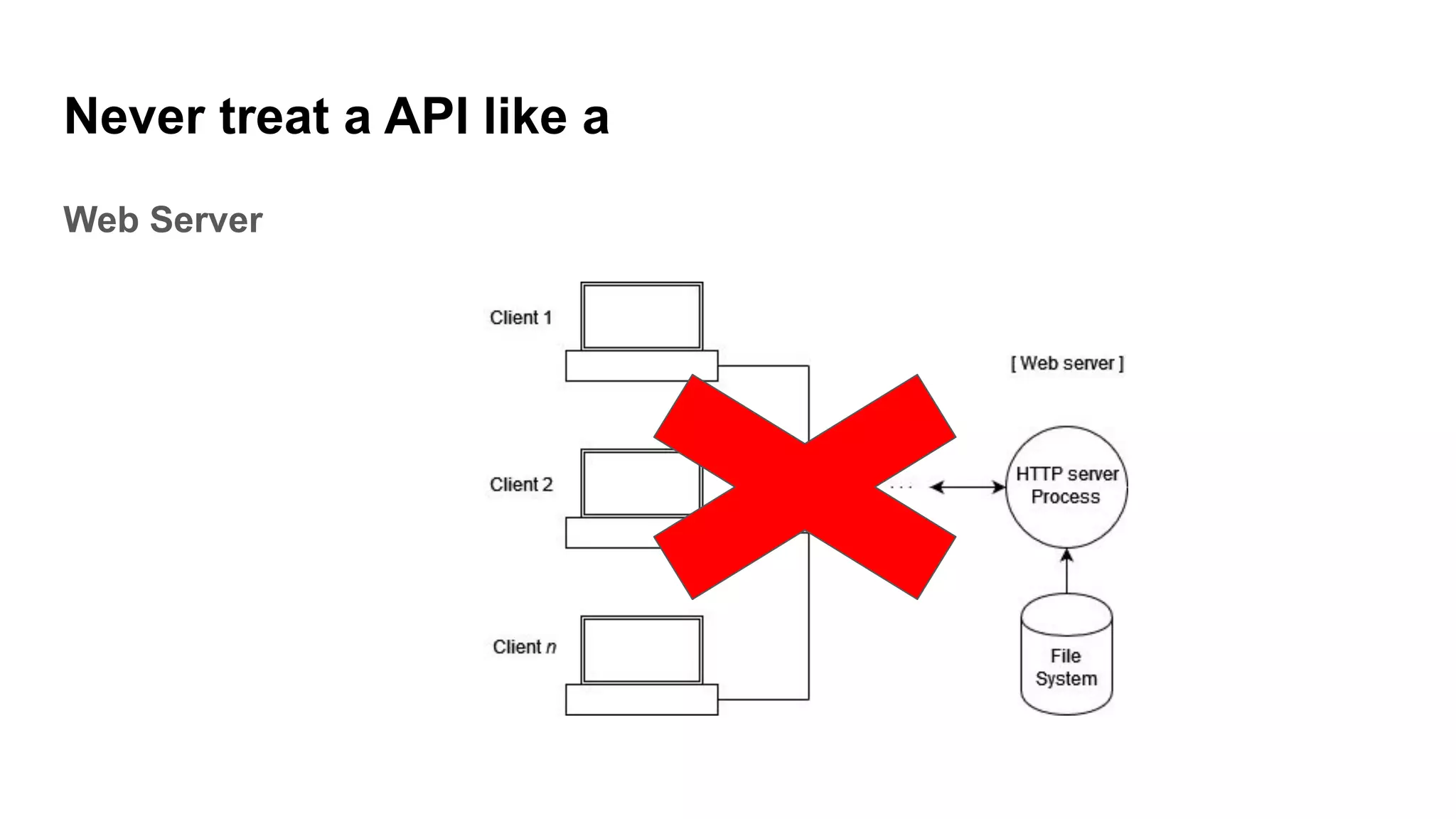
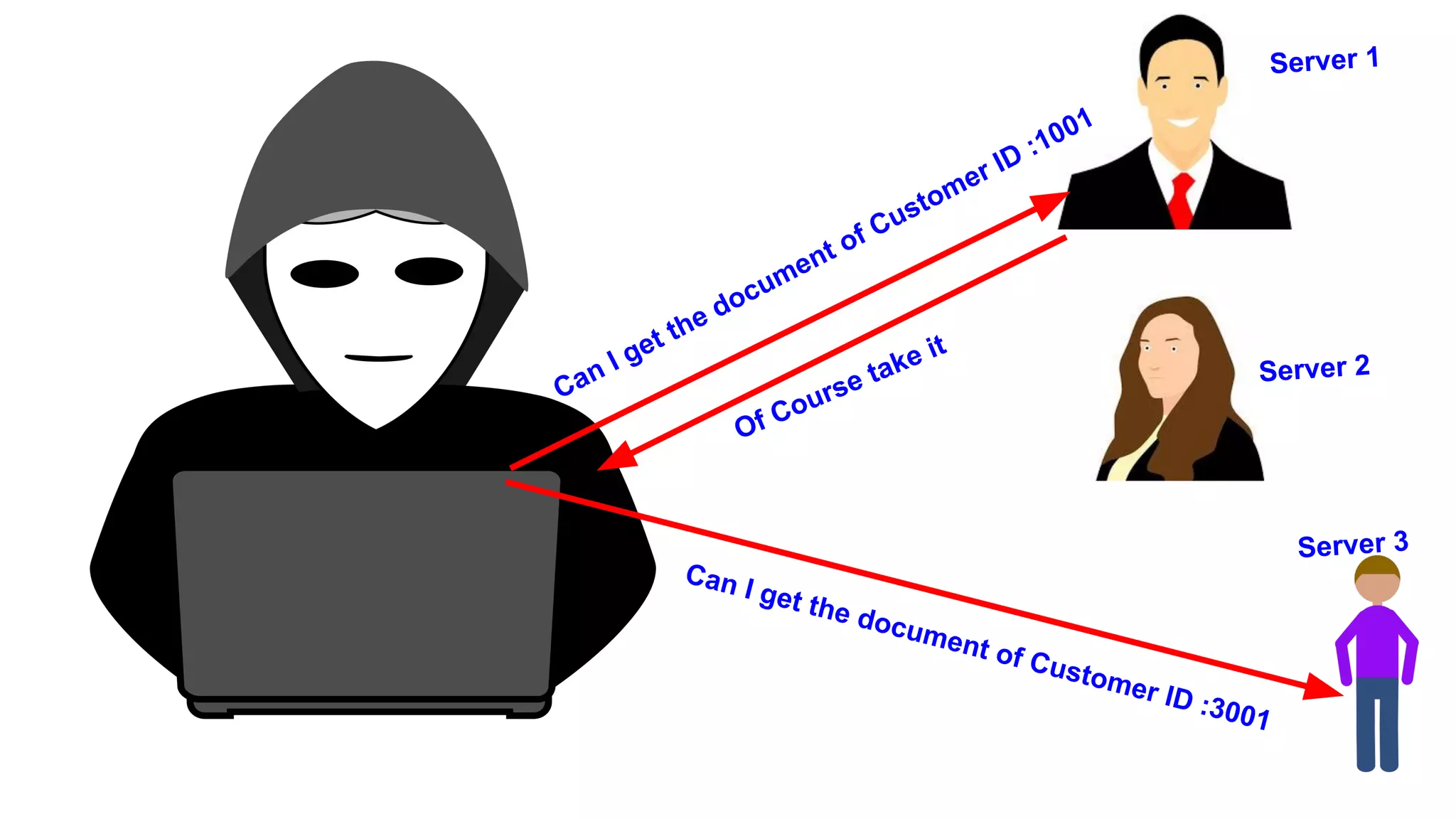
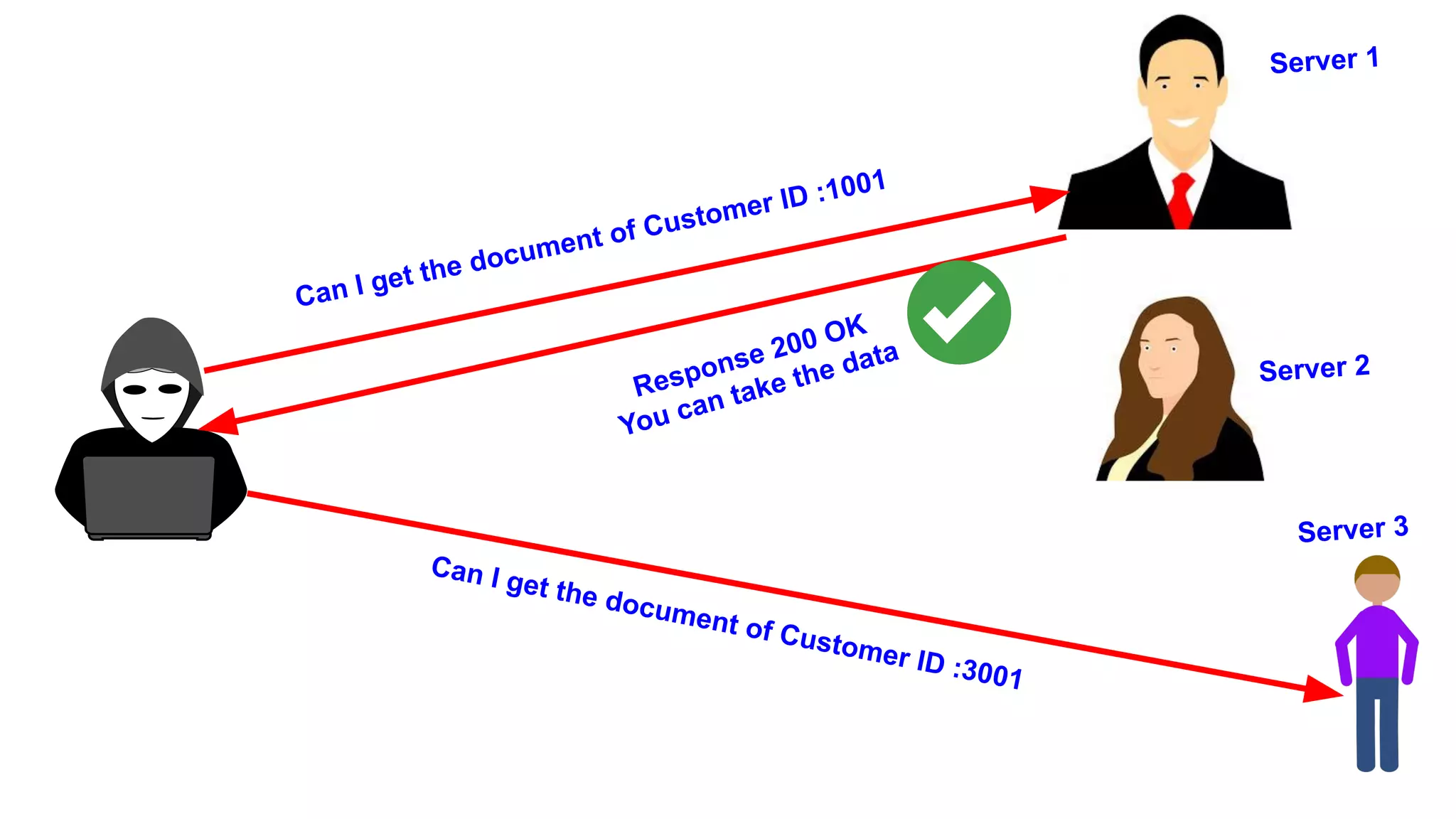
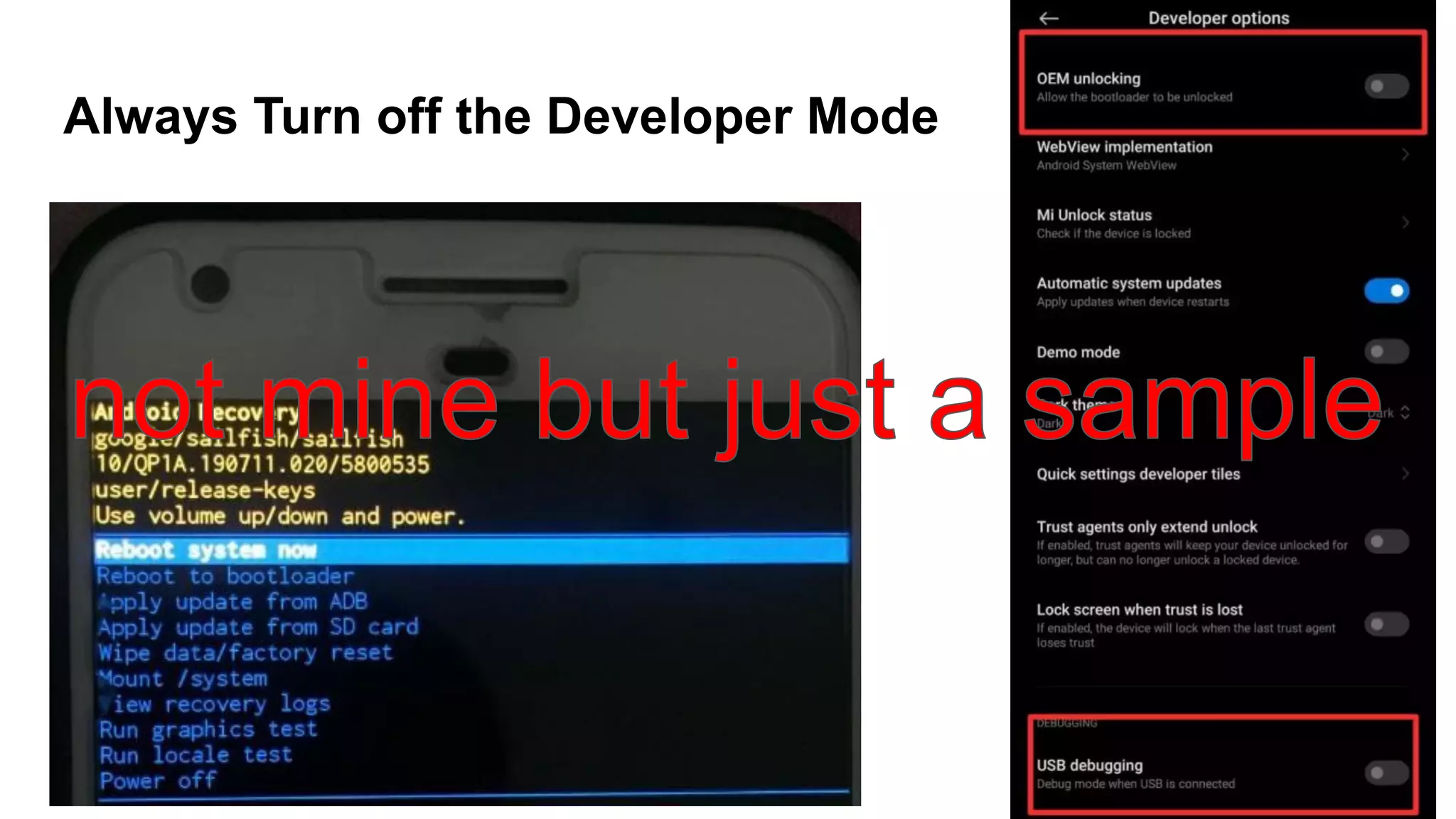
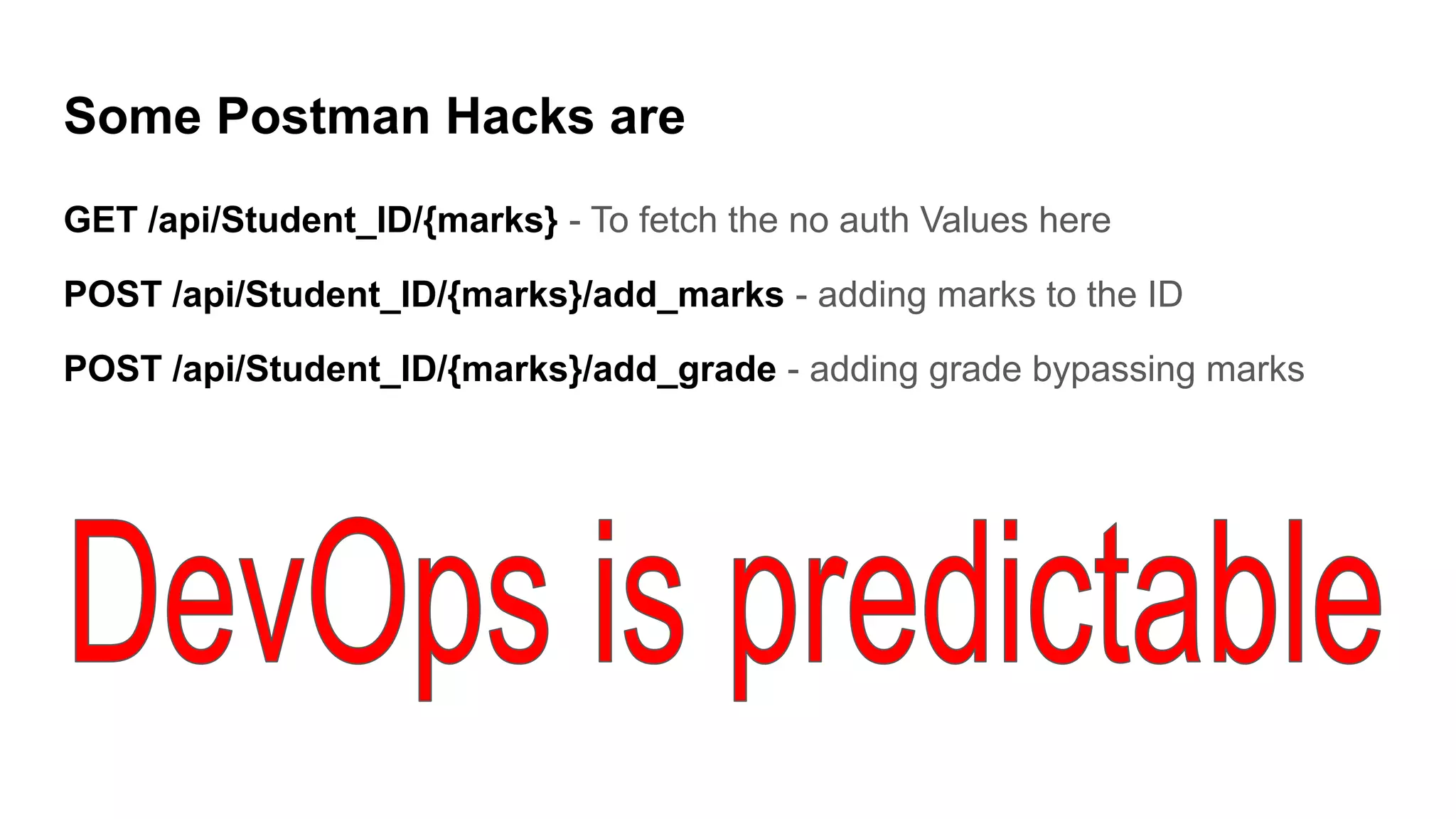
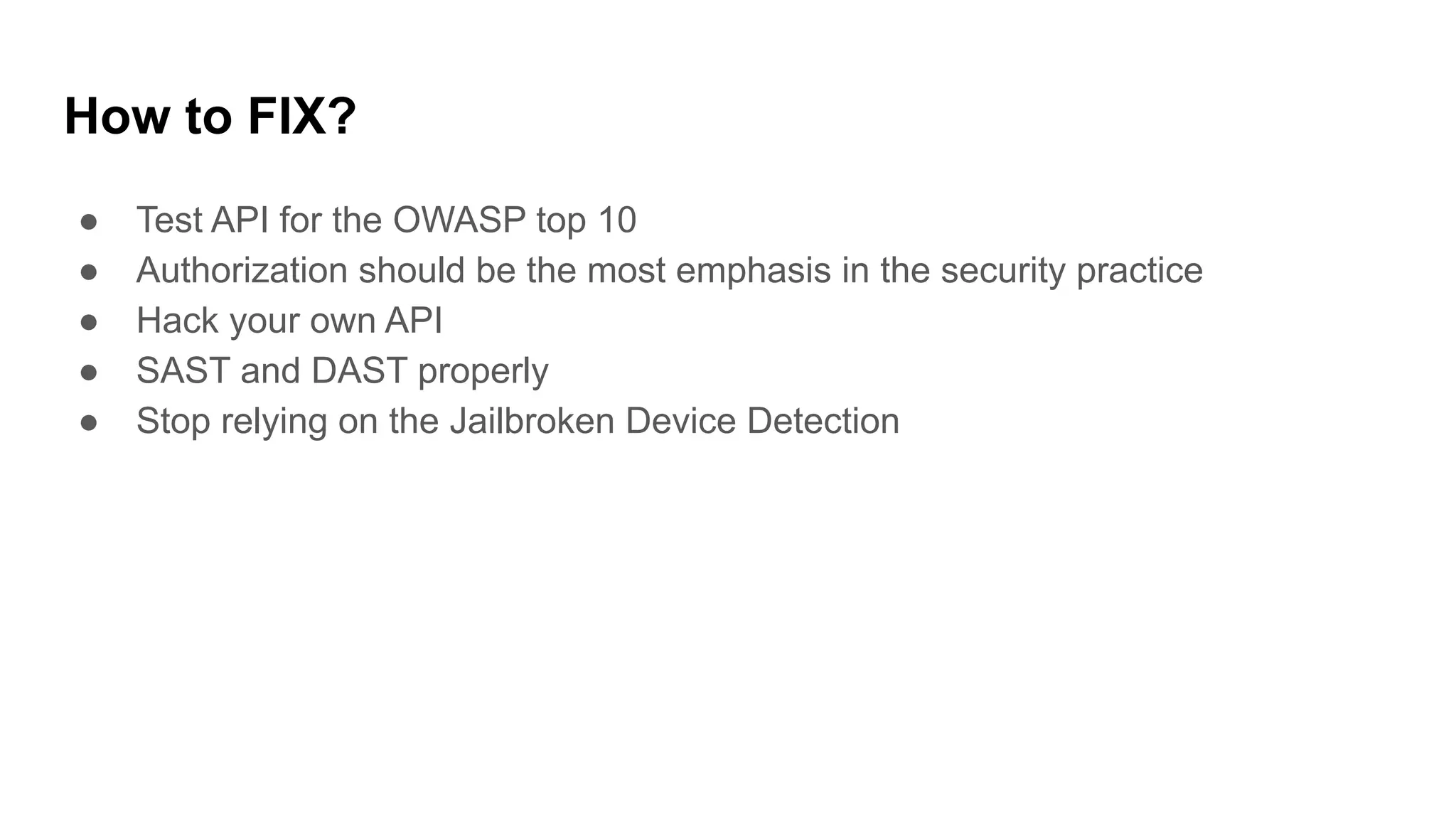
This document discusses API testing and security. It notes that while development has sped up, security has been overlooked. APIs connect many systems and components, so they are vulnerable if not properly secured. The document recommends testing APIs for common vulnerabilities, emphasizing authorization, and "hacking your own API" to identify issues before attackers do. APIs must be developed with security in mind from the start.