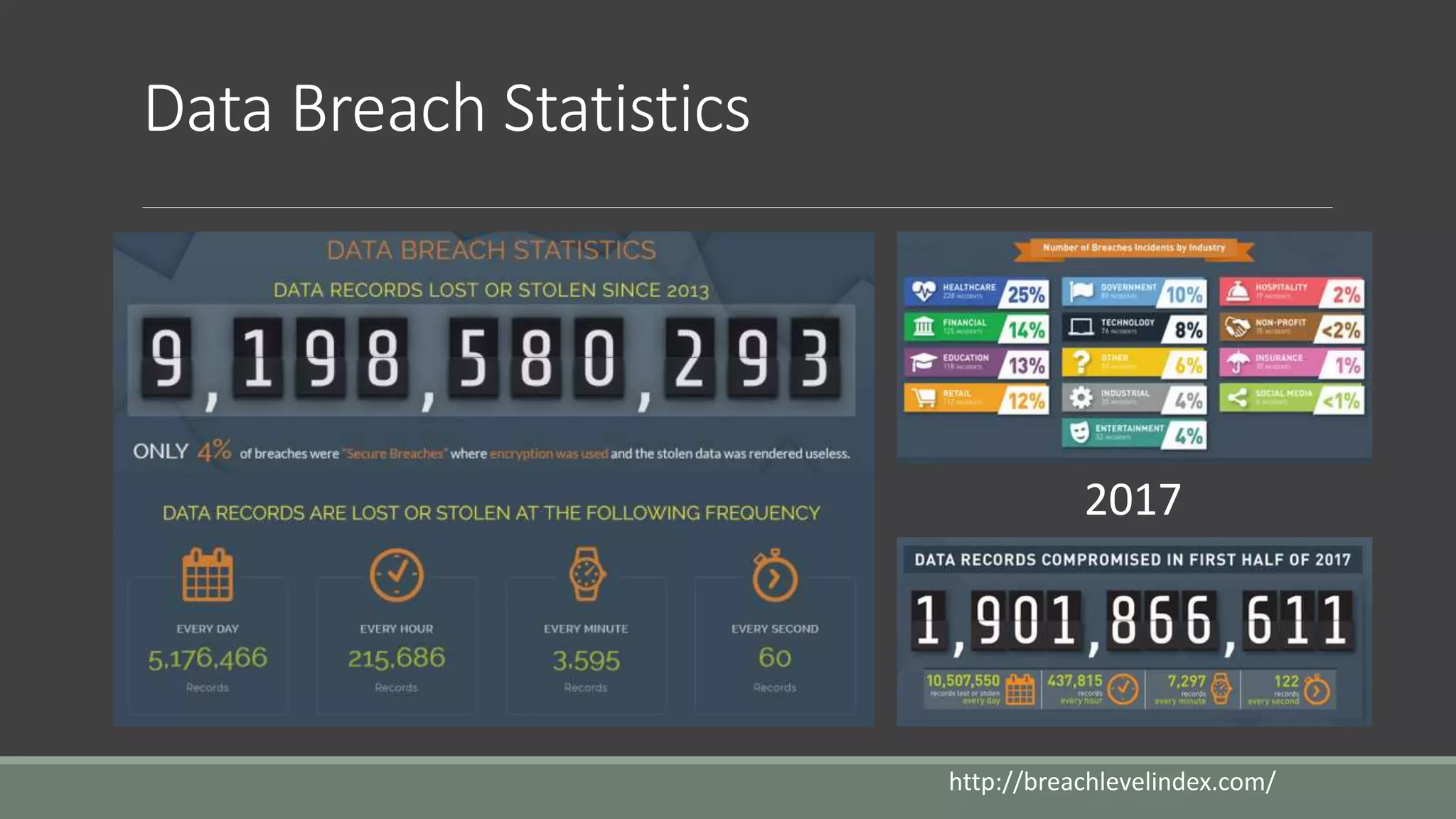
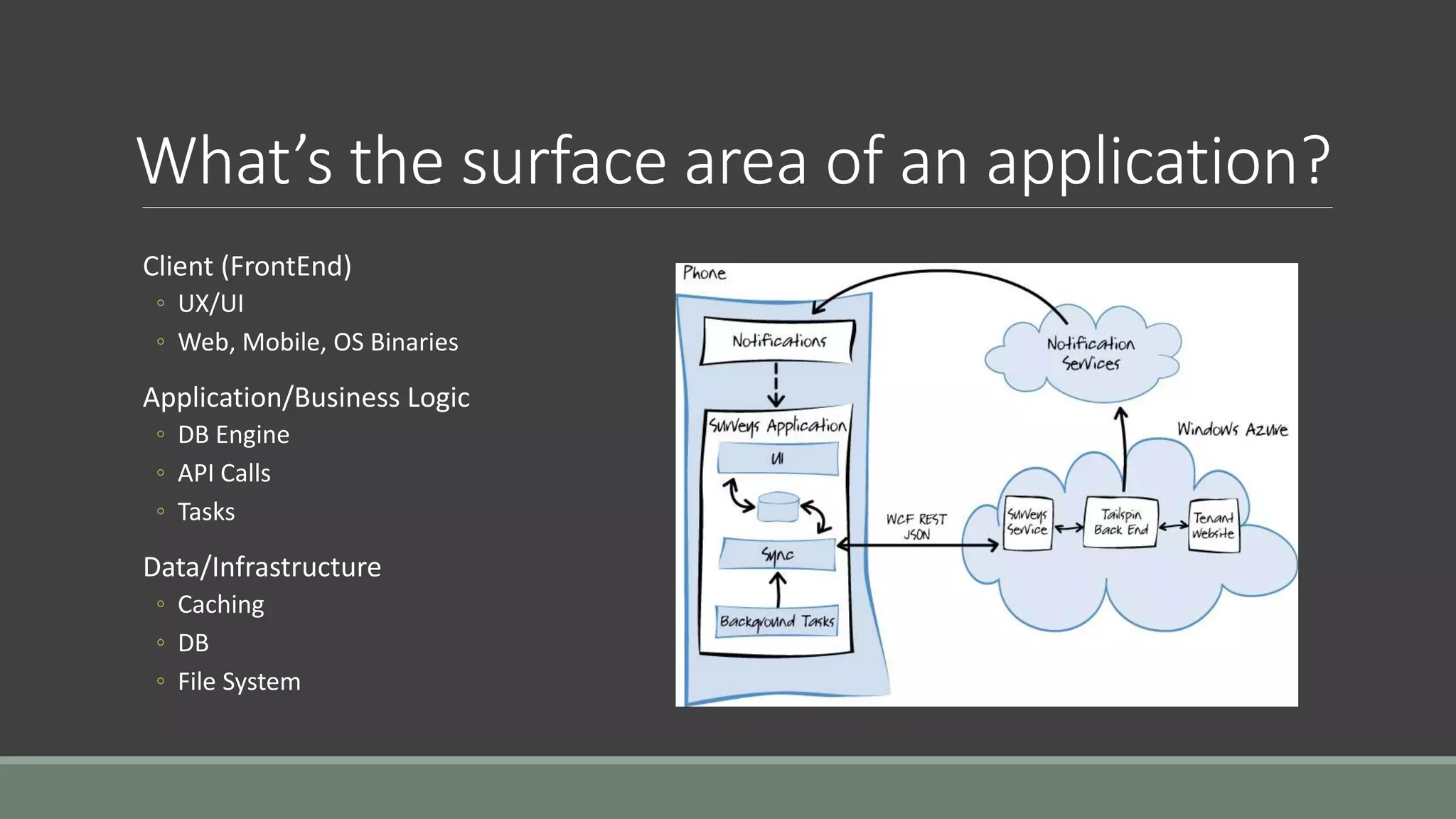
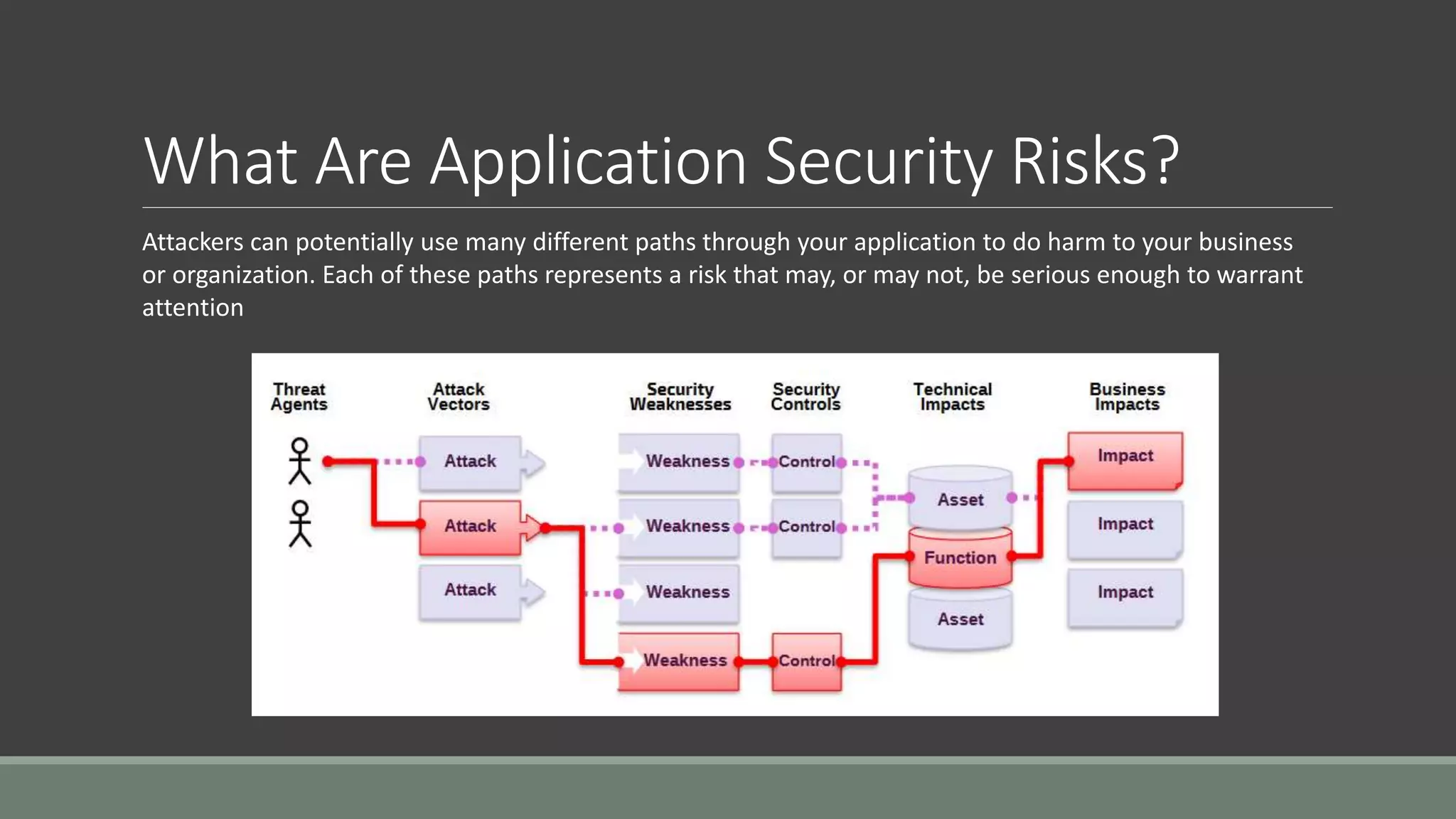
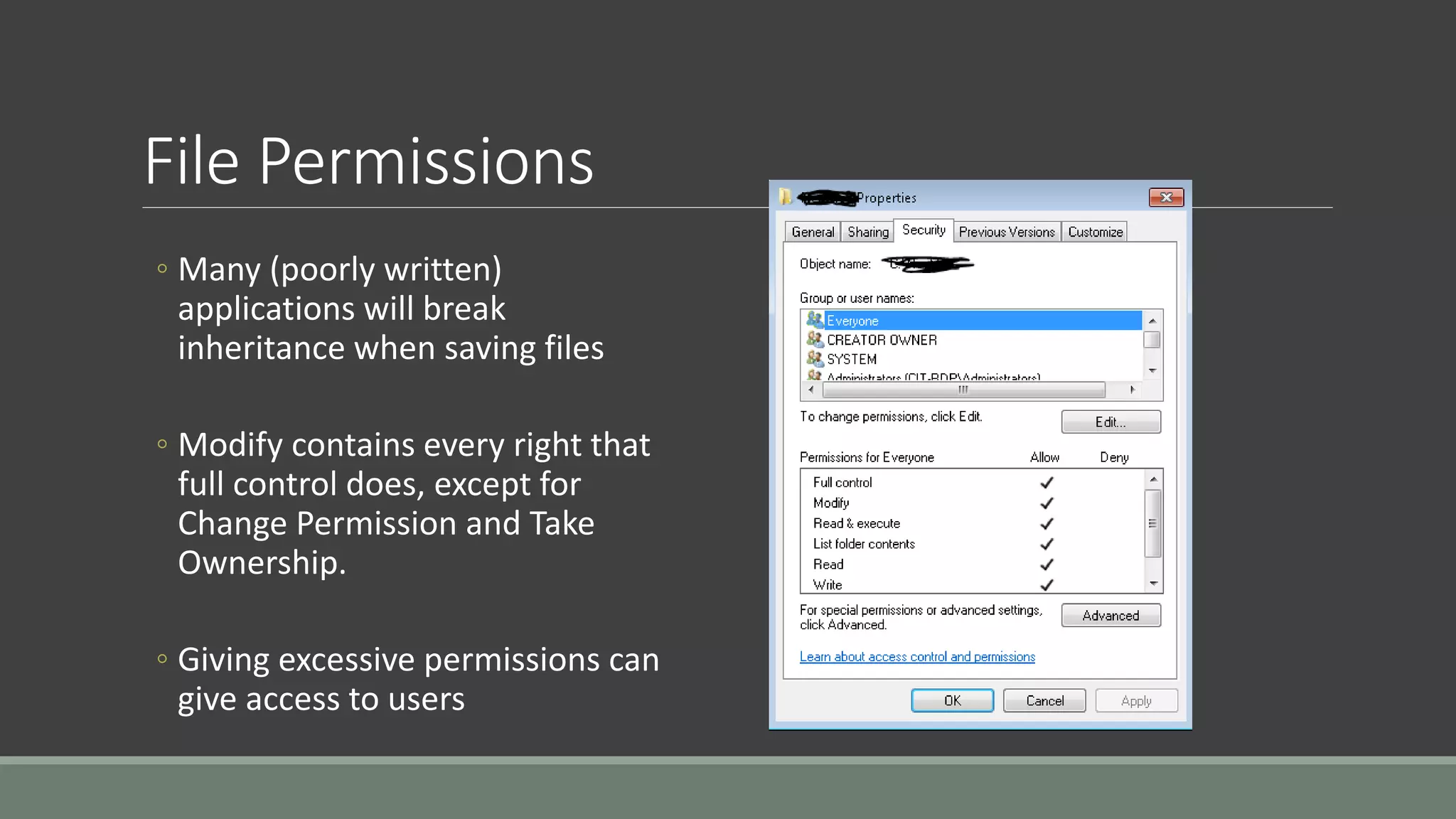
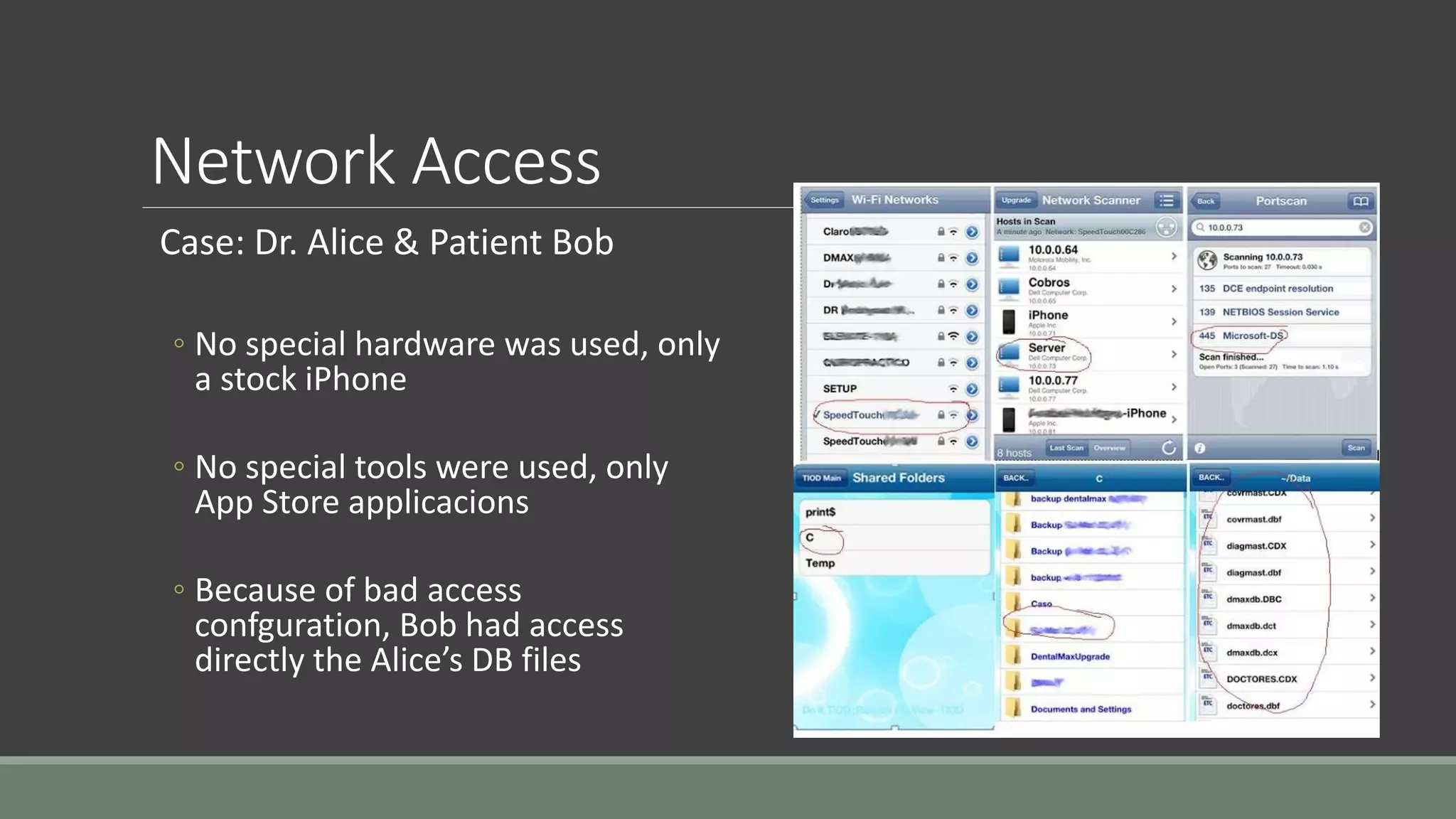
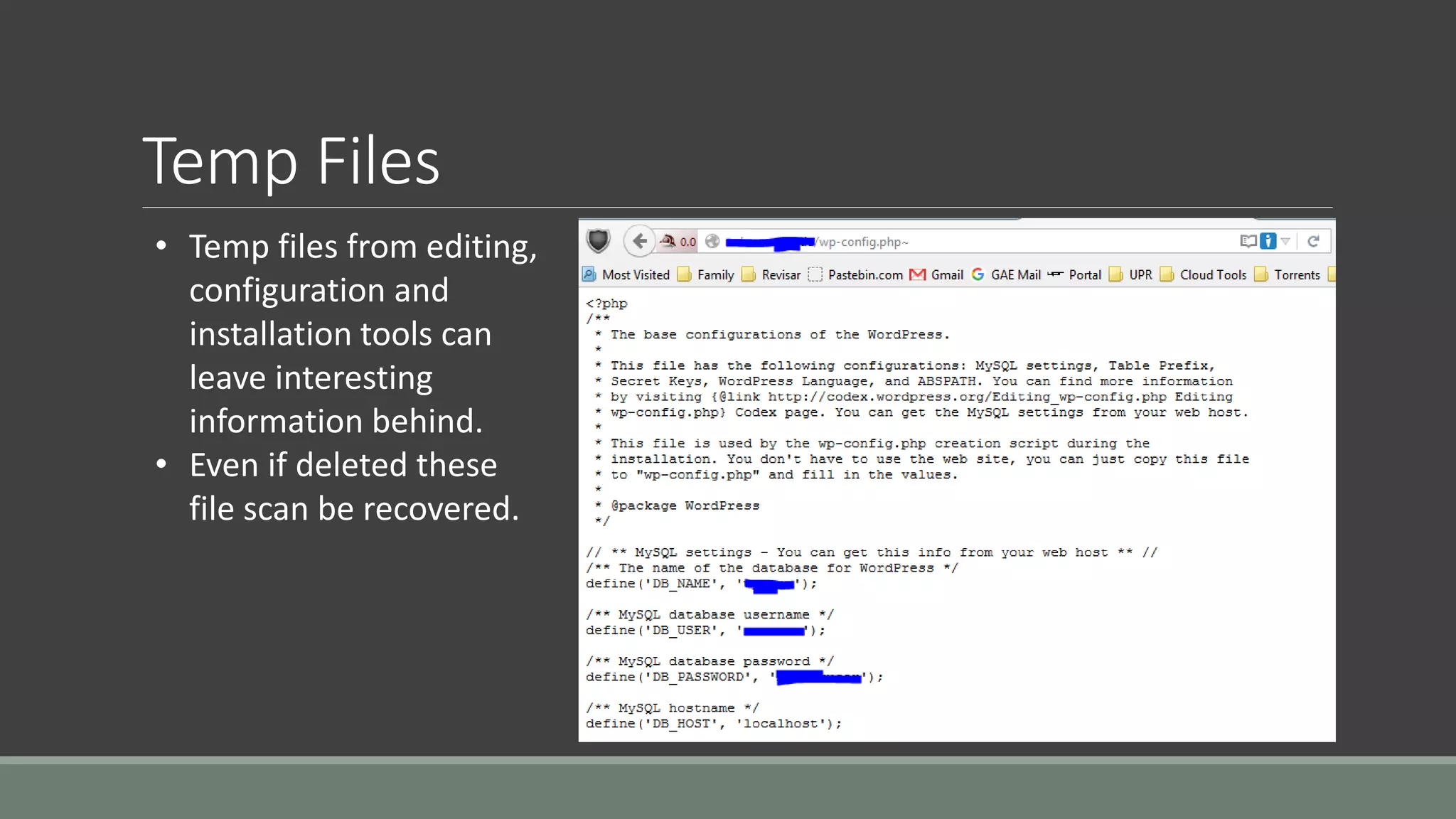
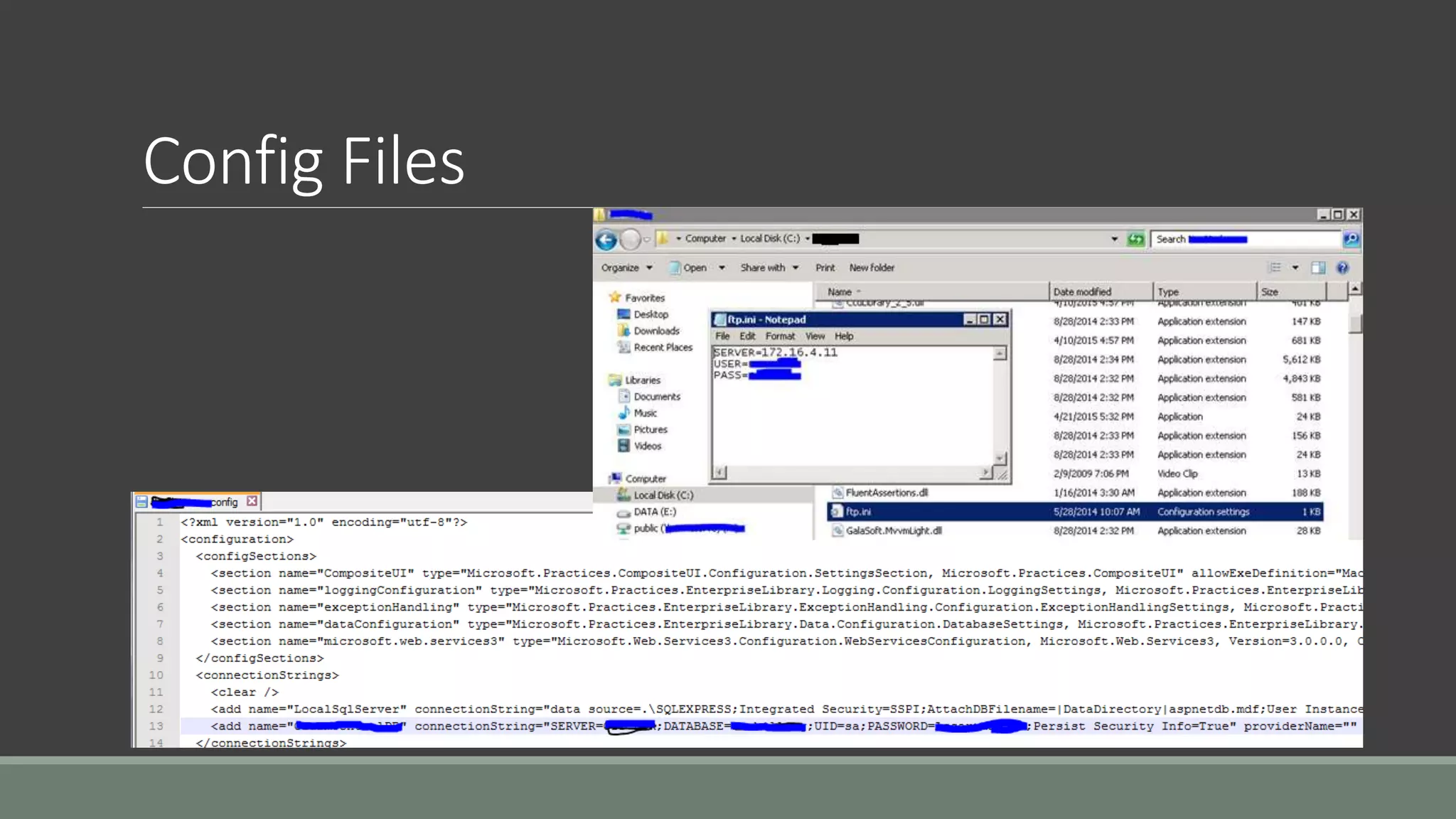
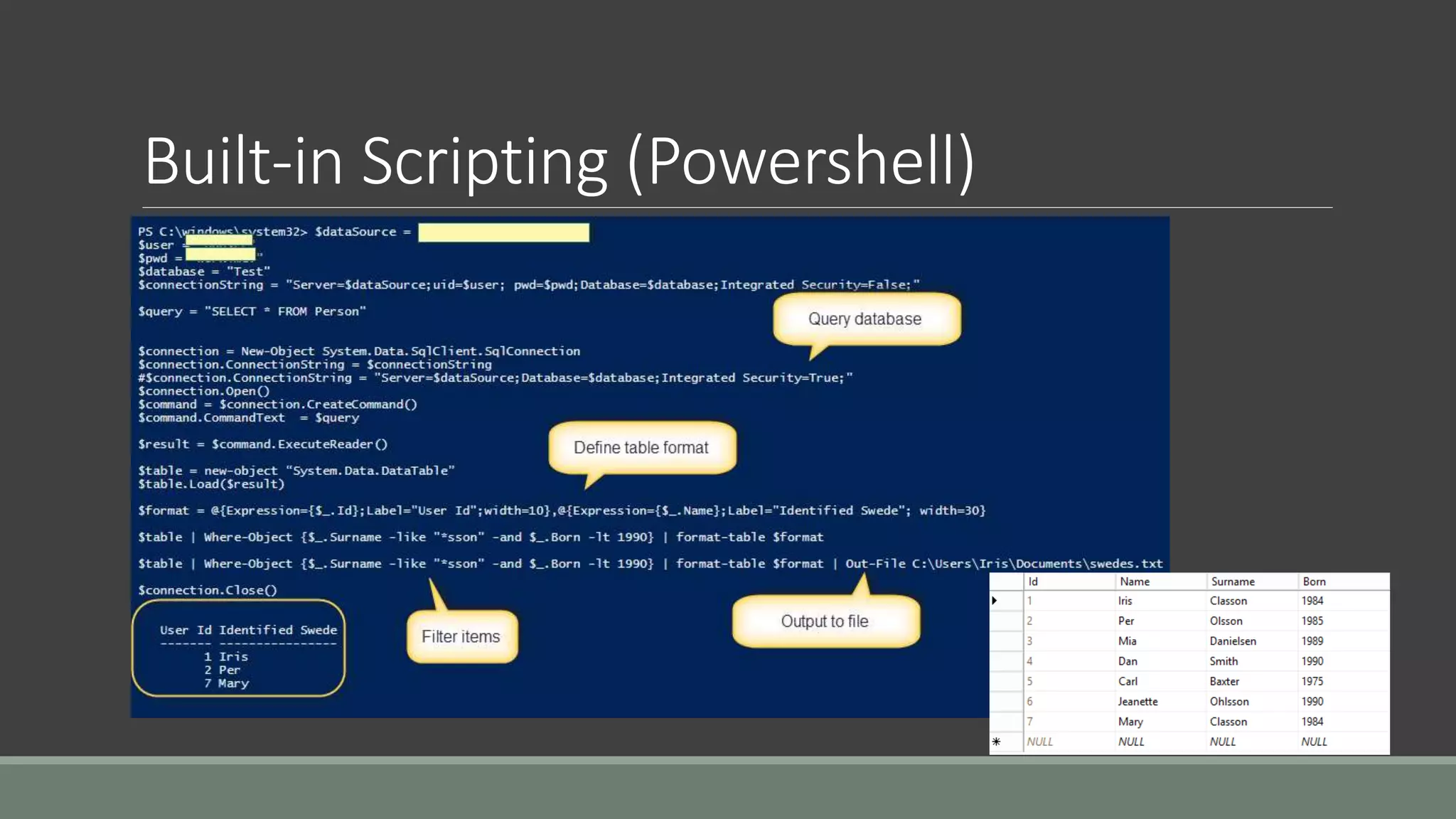
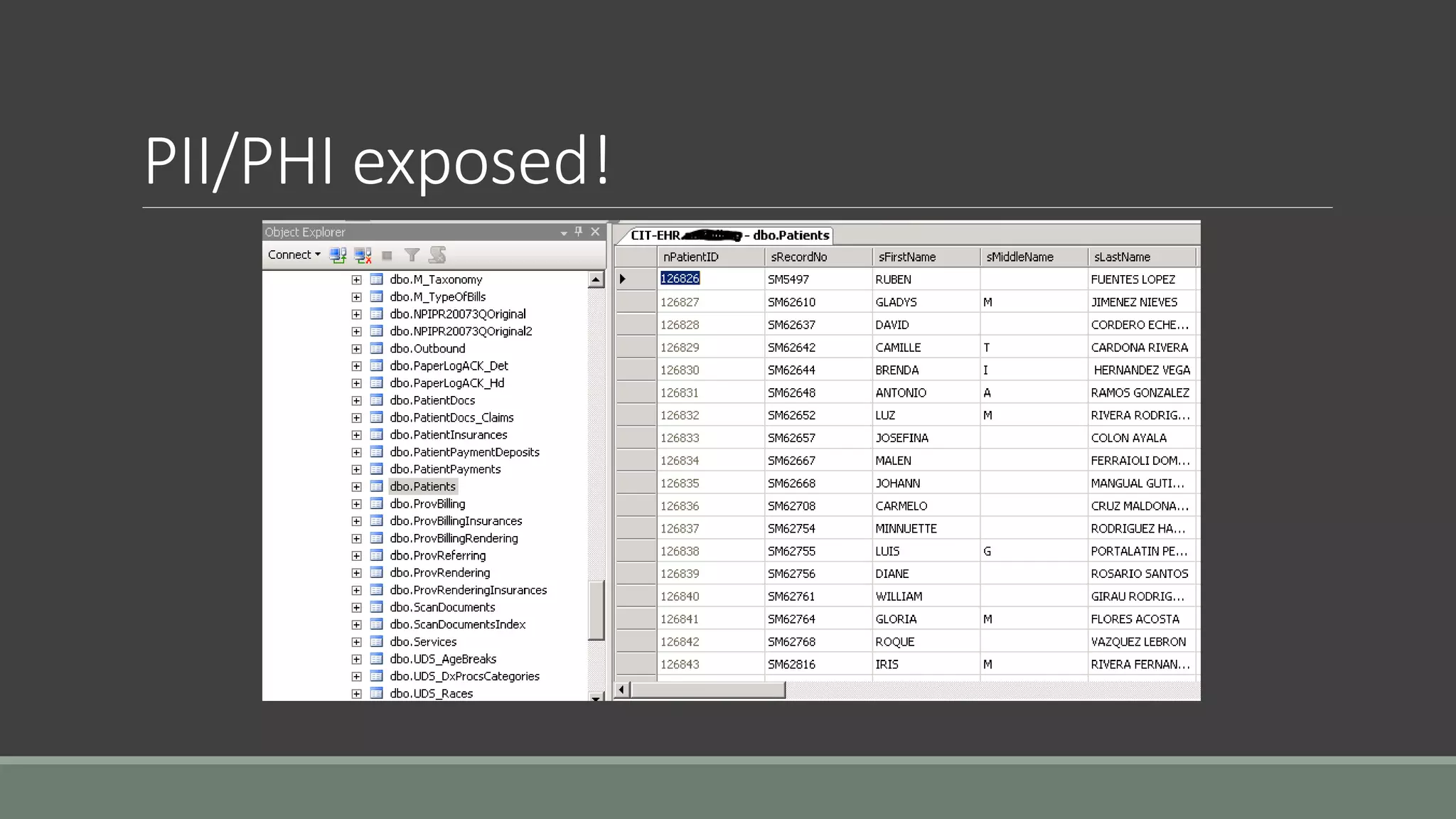
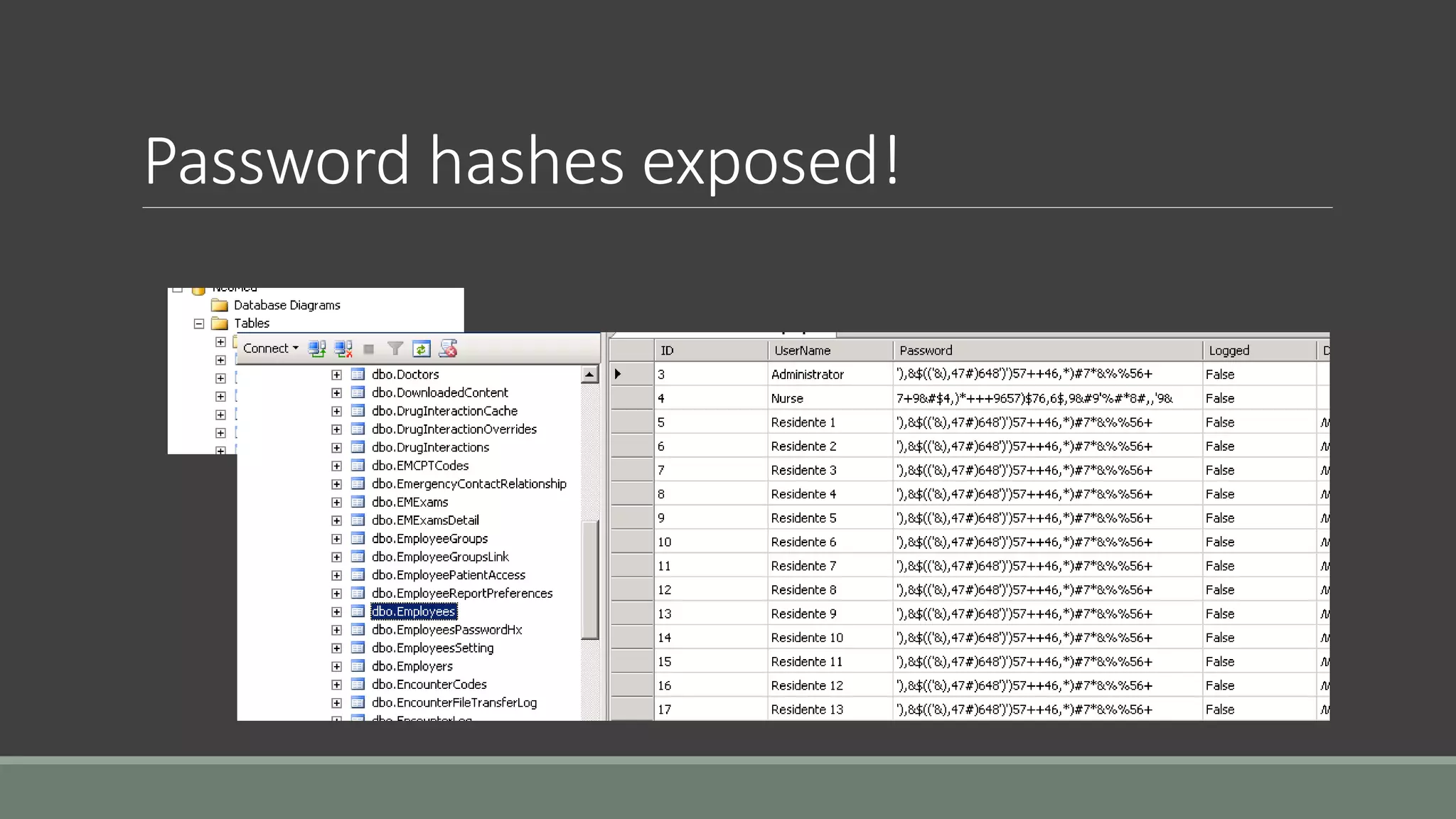
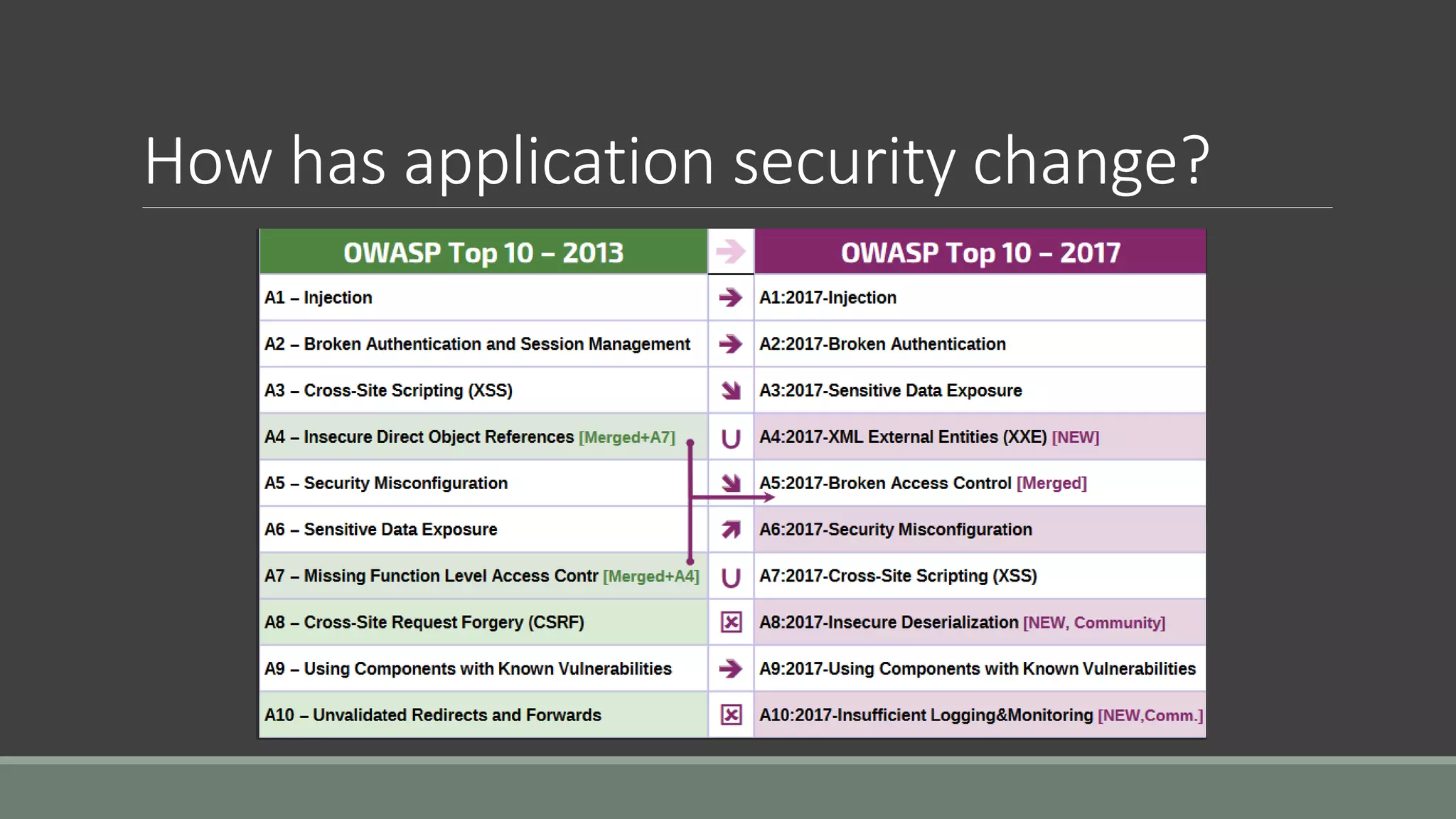
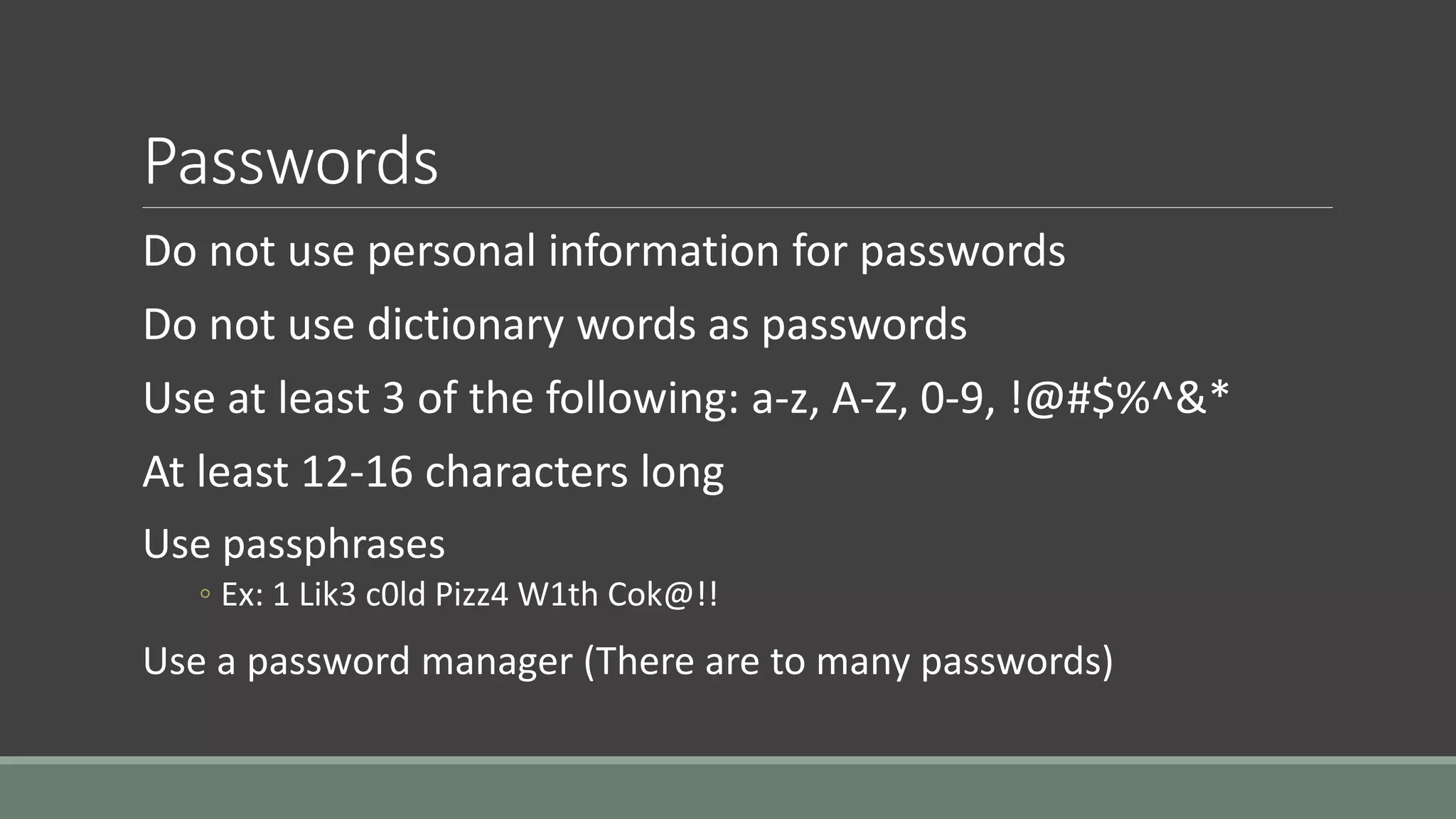
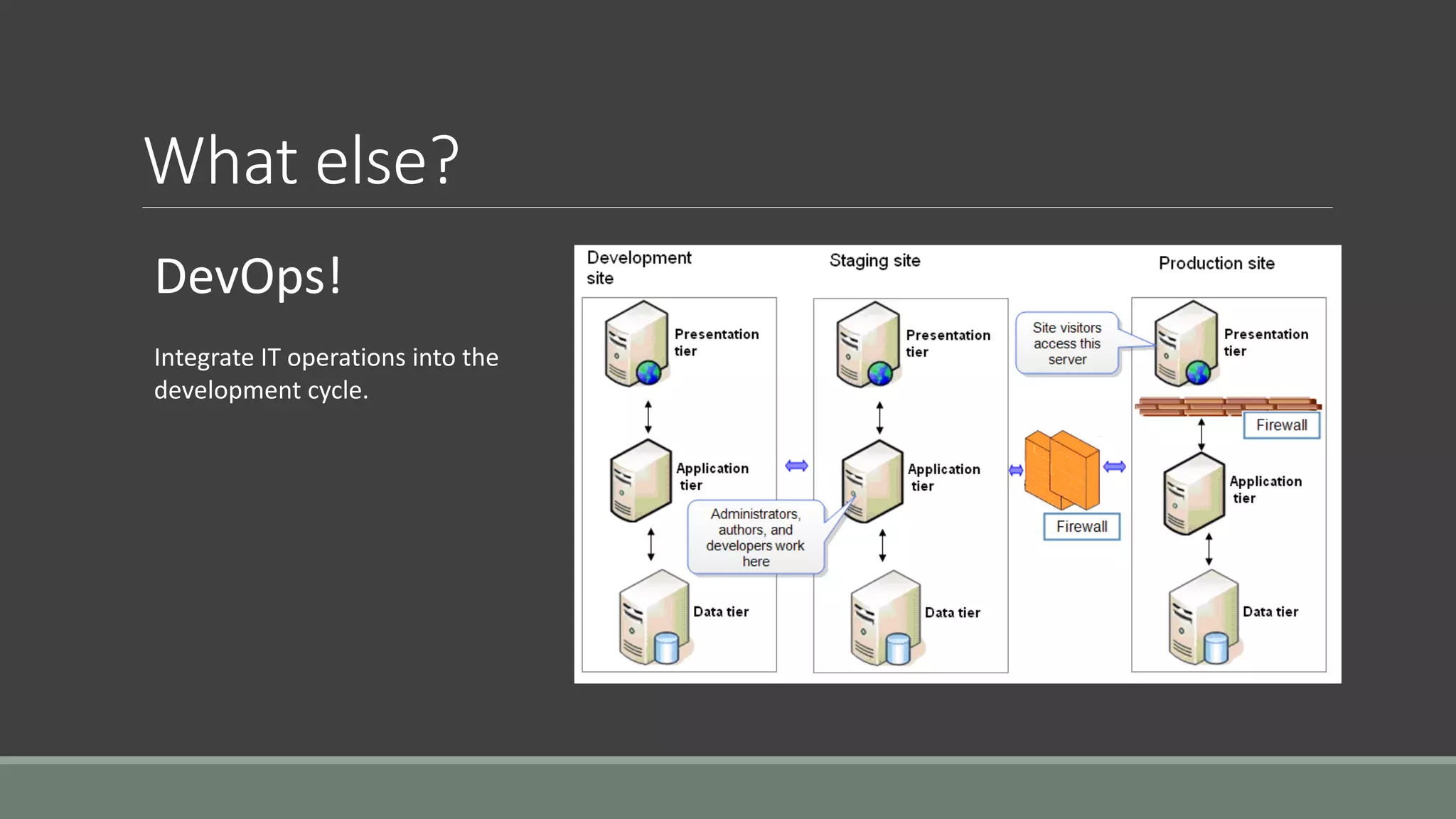
The document discusses application security from the perspective of an IT director with experience in healthcare and education. It highlights common vulnerabilities and risks associated with application development, stressing the importance of securing data and using strong passwords, encryption, and user awareness to prevent breaches. The presentation emphasizes the necessity for continuous communication with developers and integrating IT operations into the development cycle for better security practices.