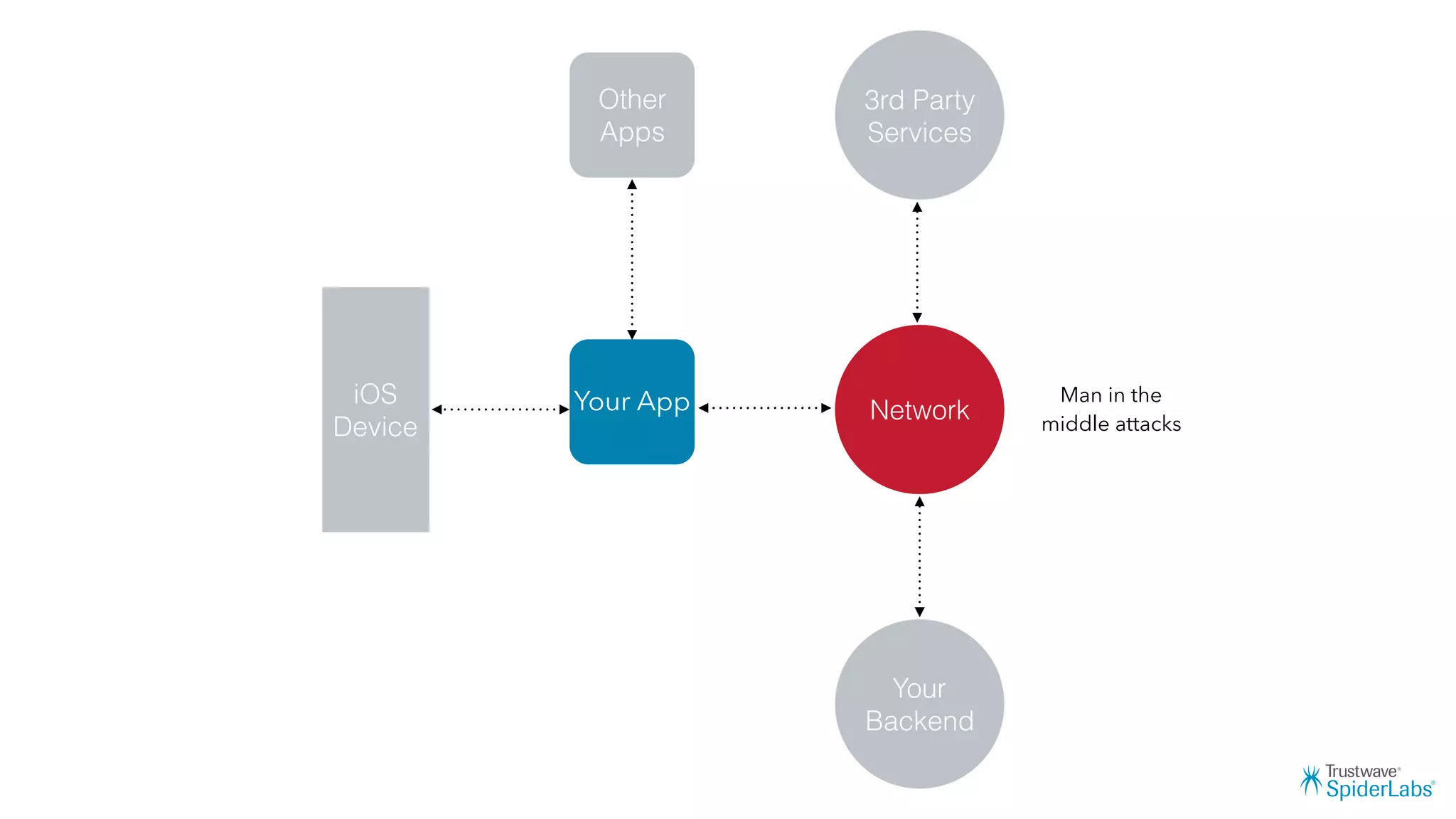
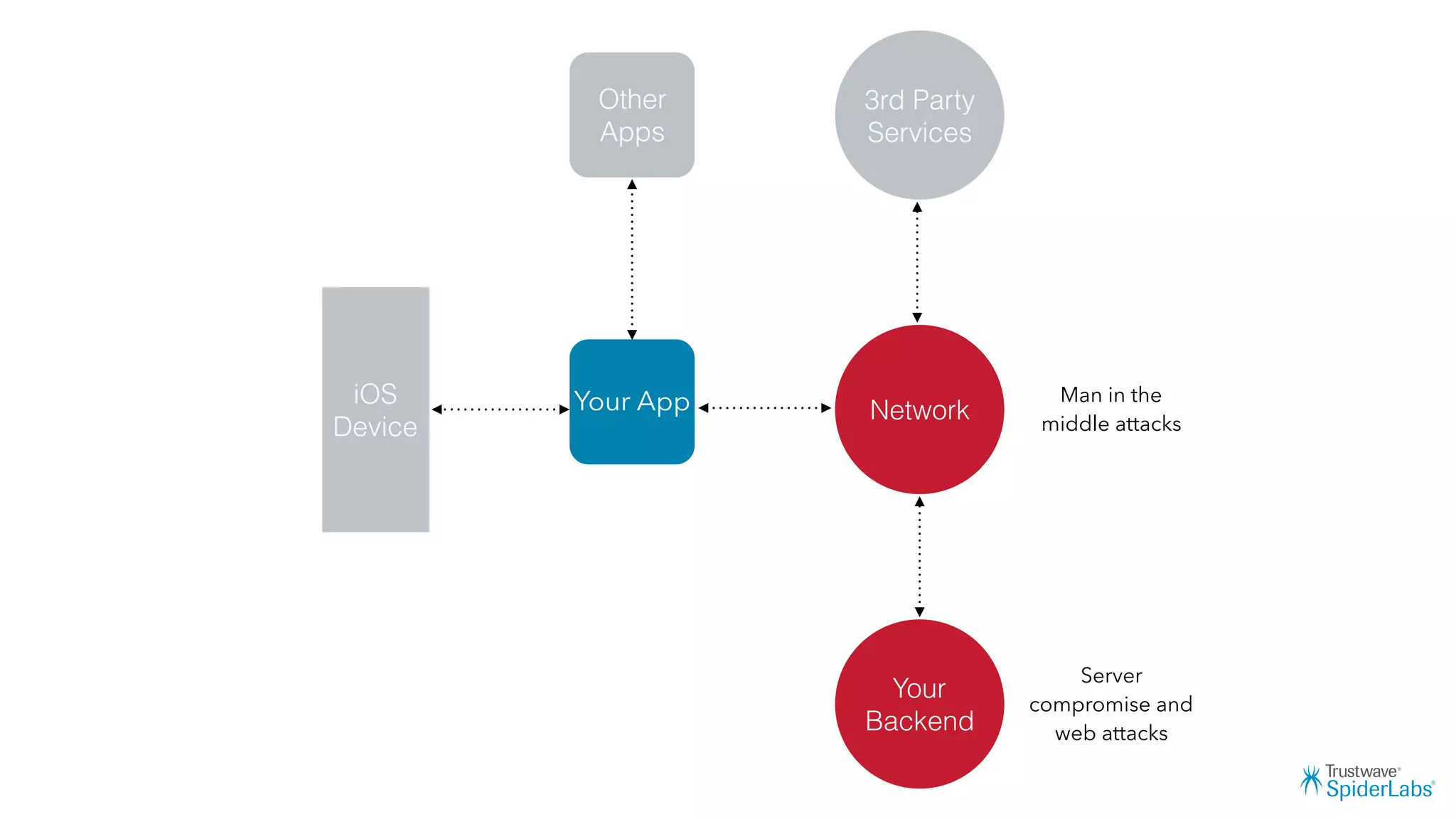
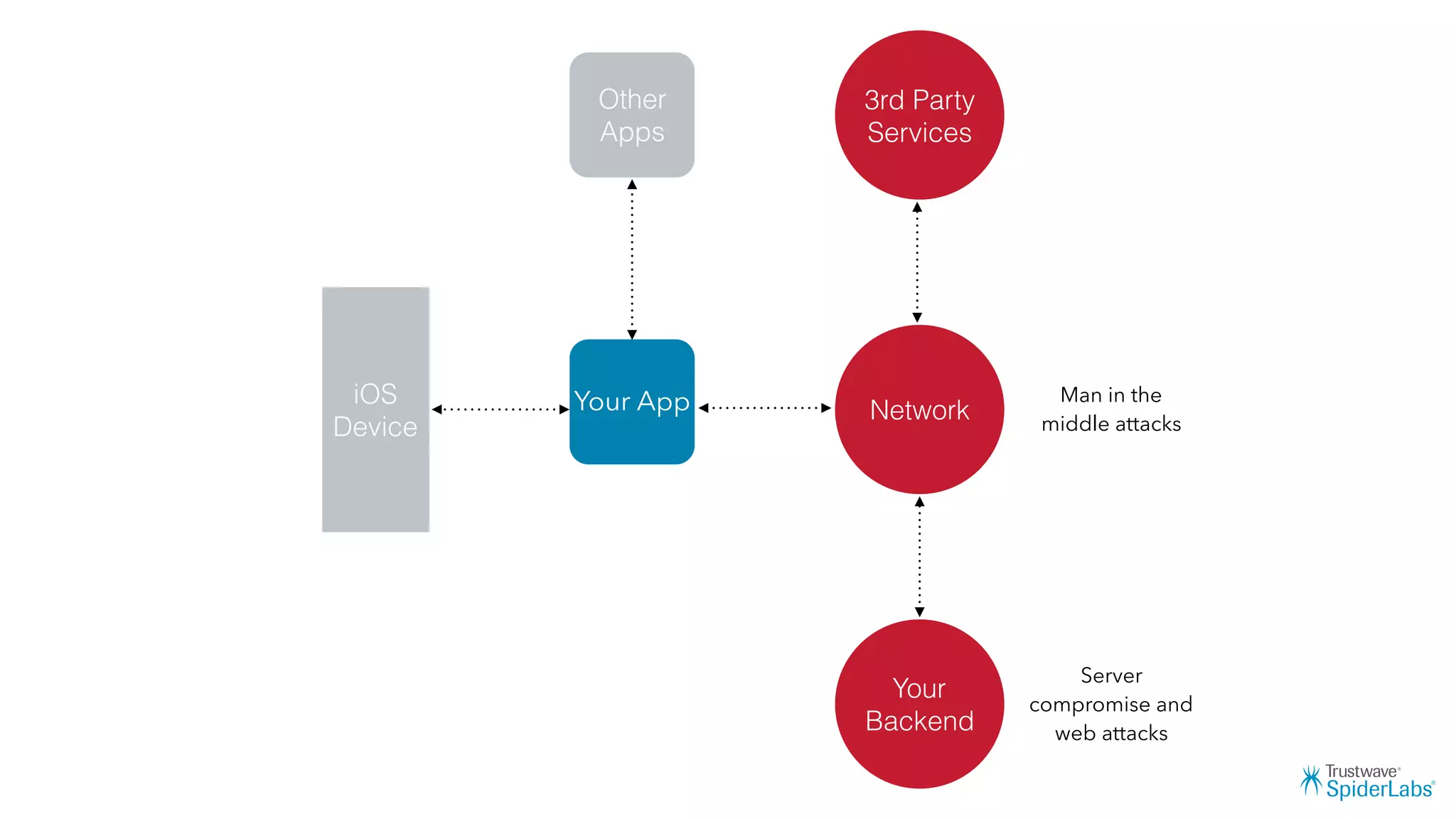
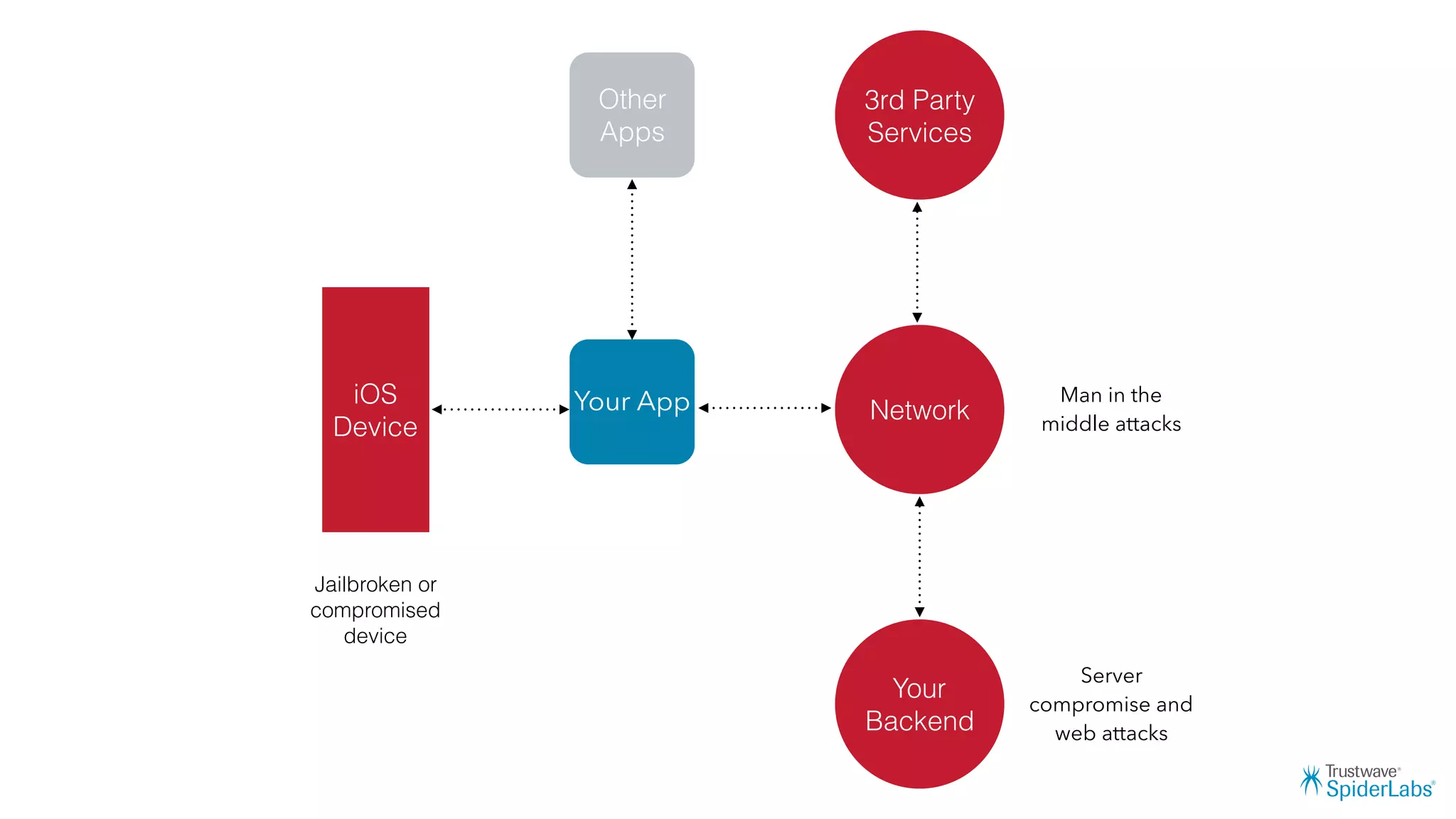
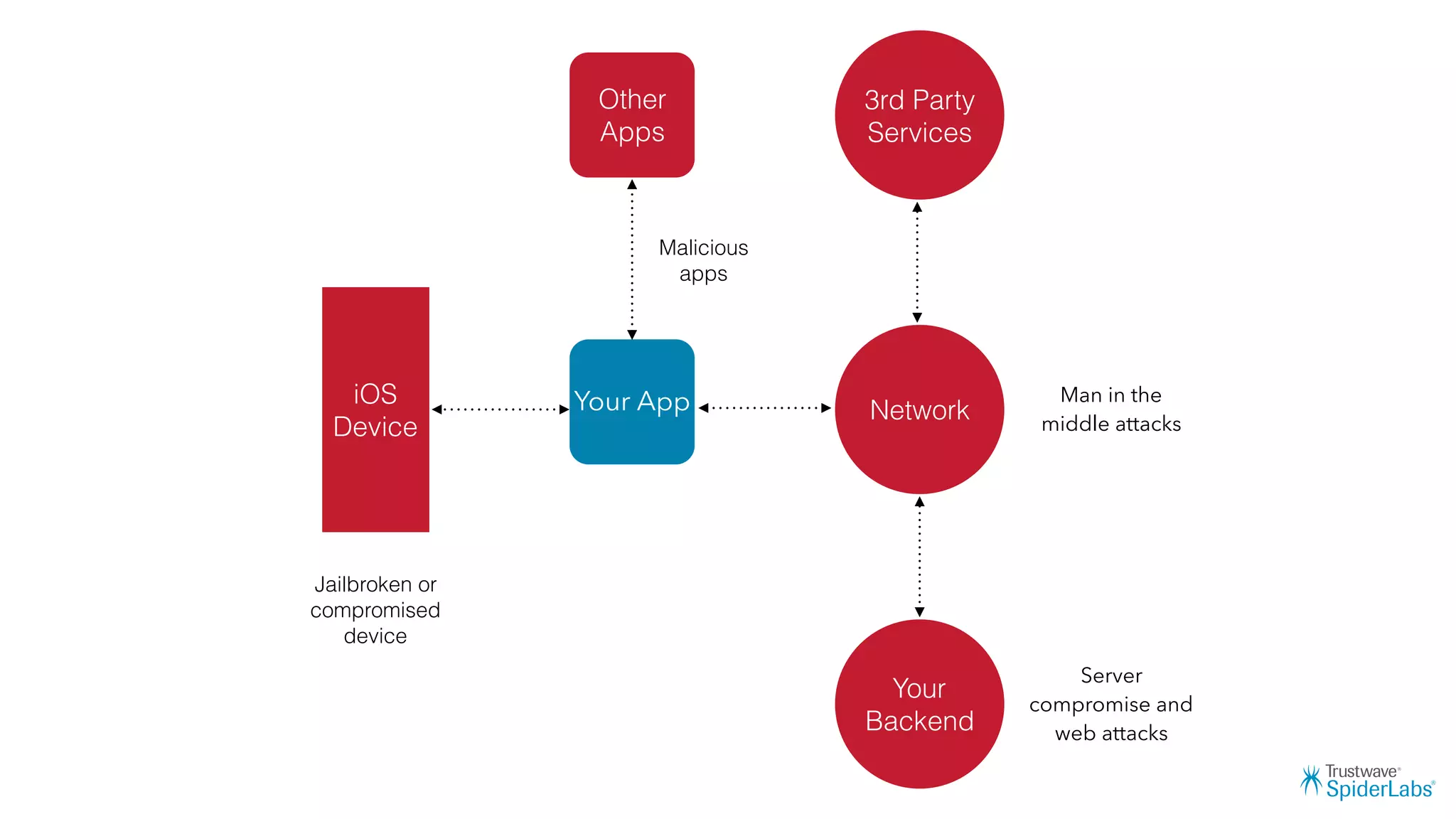
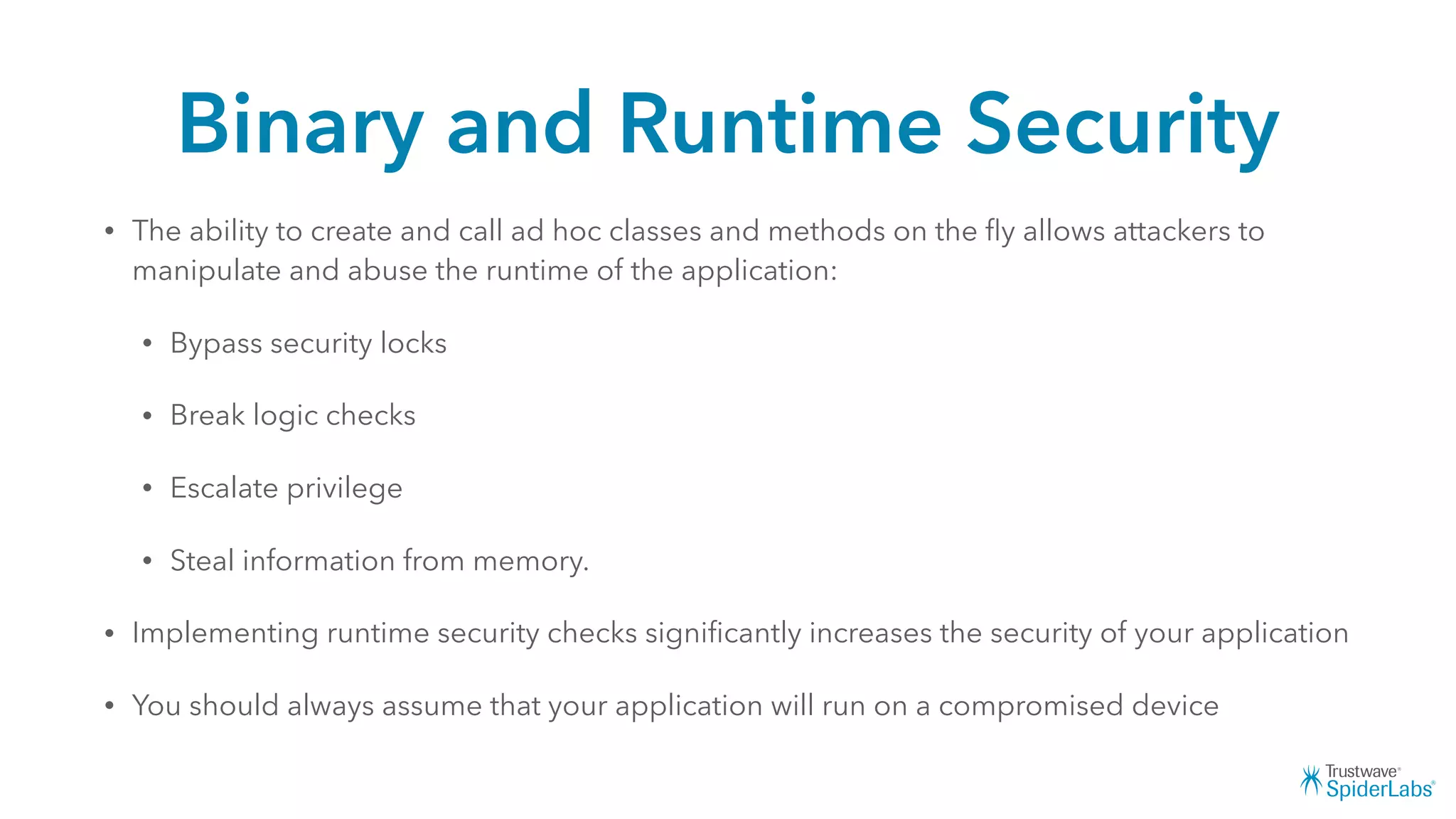
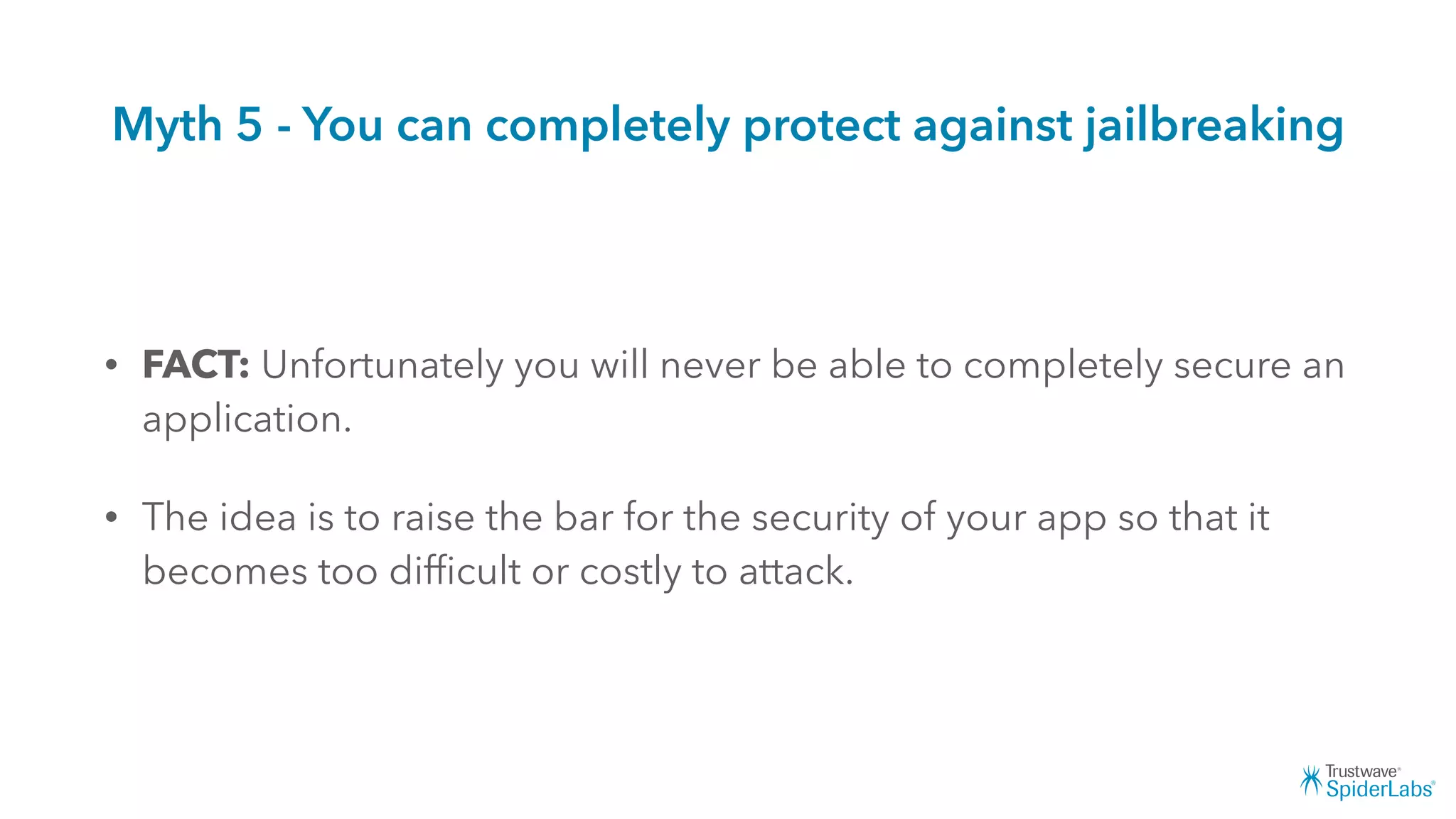
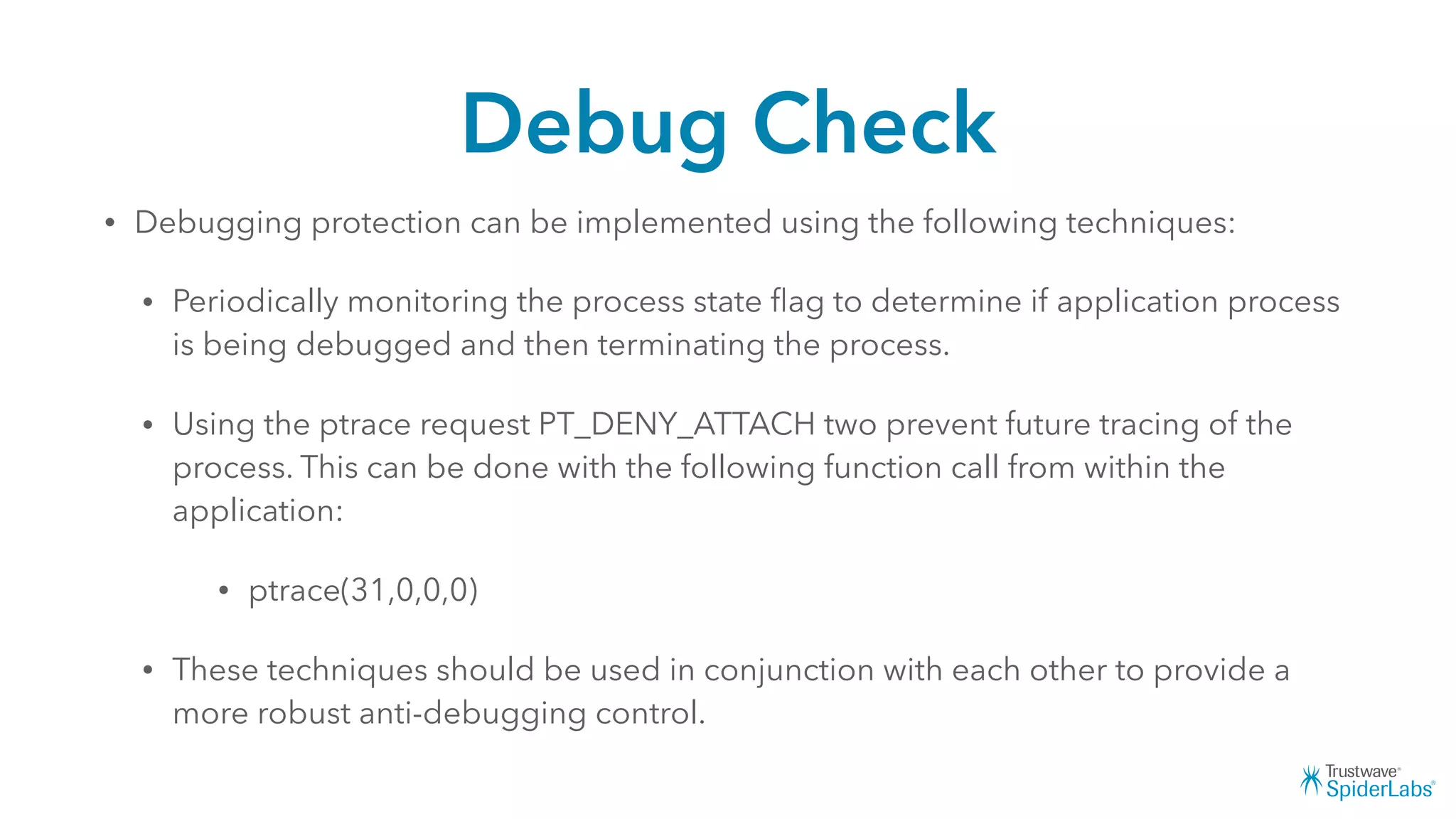
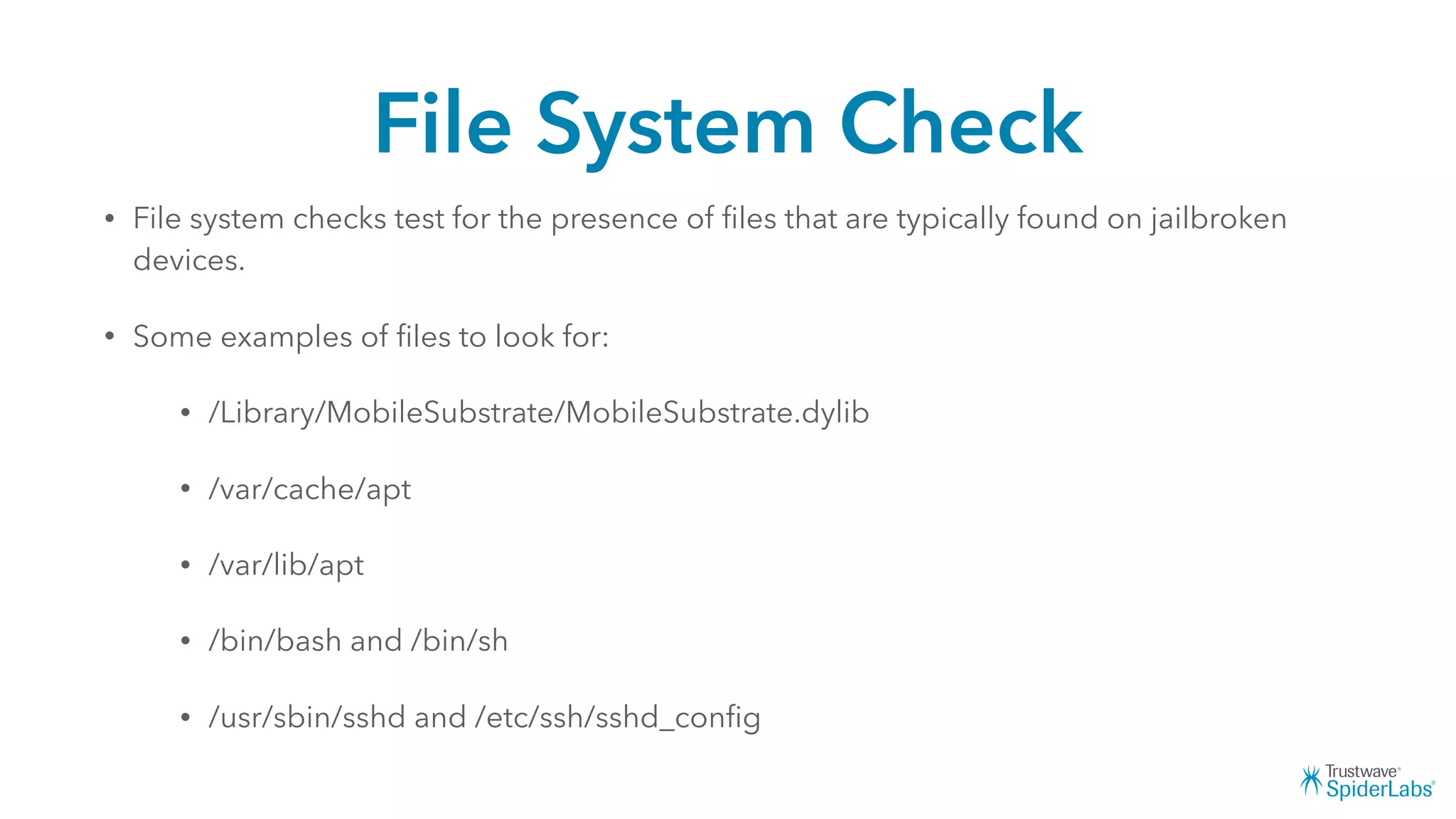
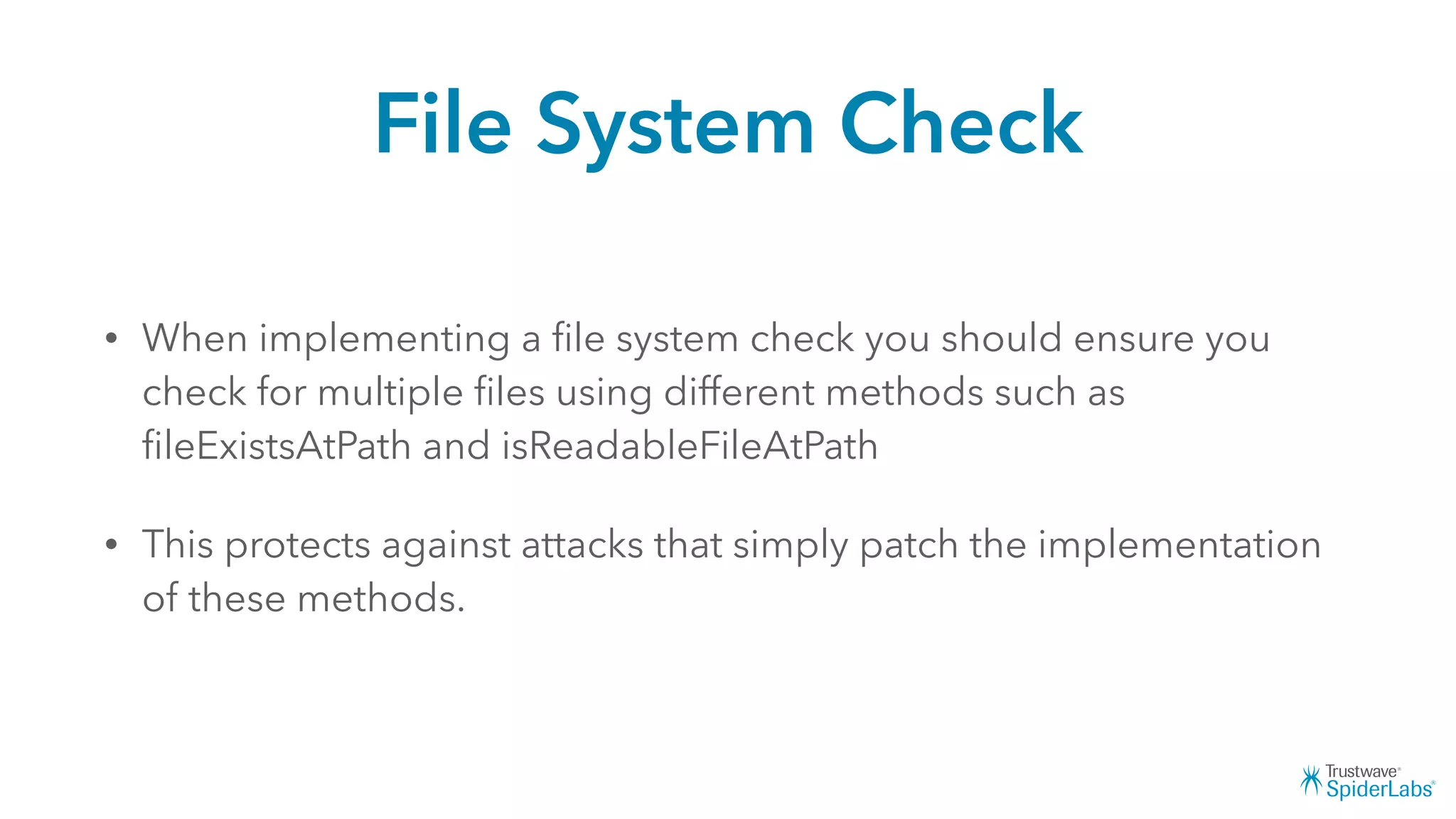
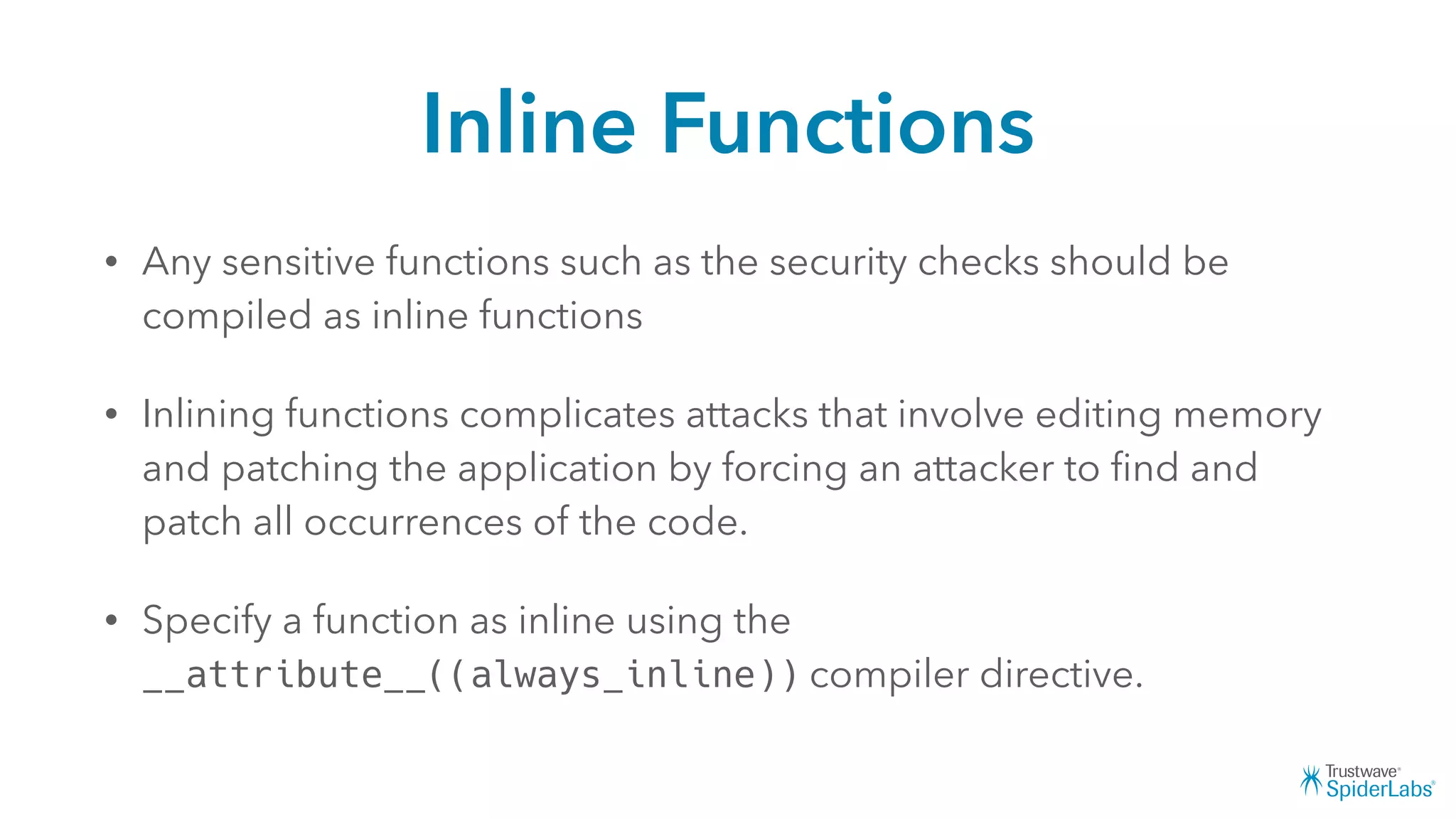
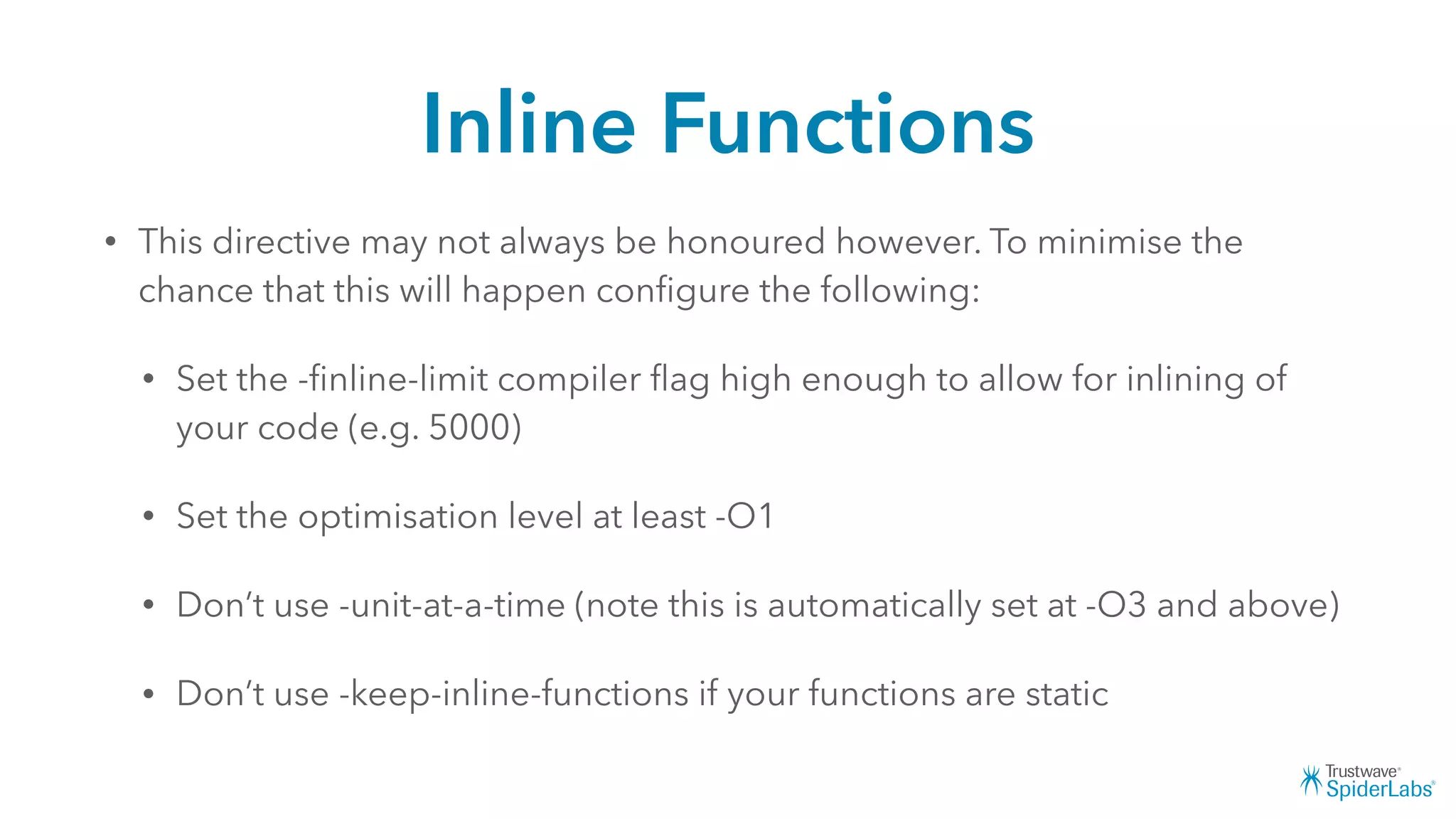
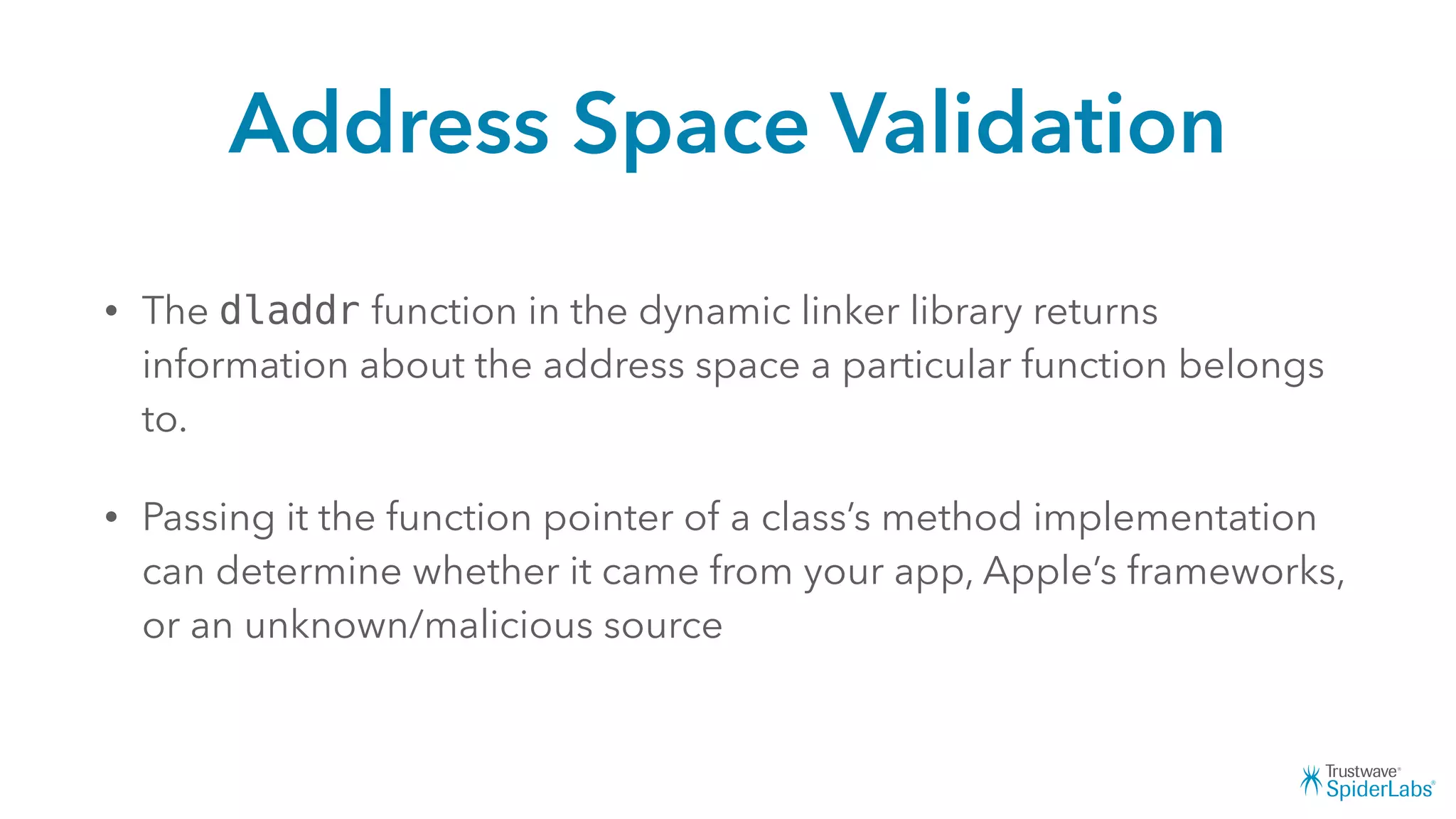
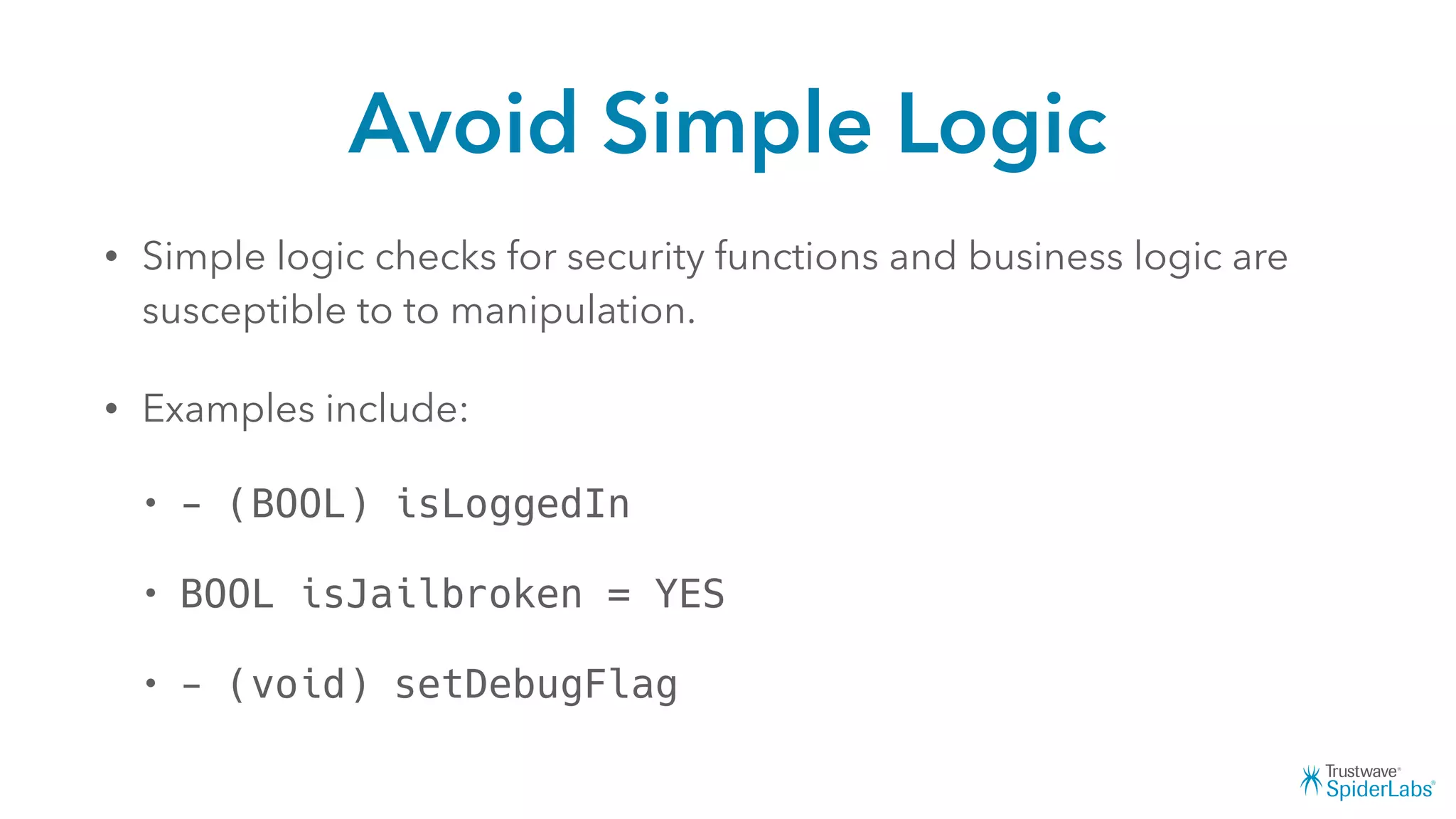
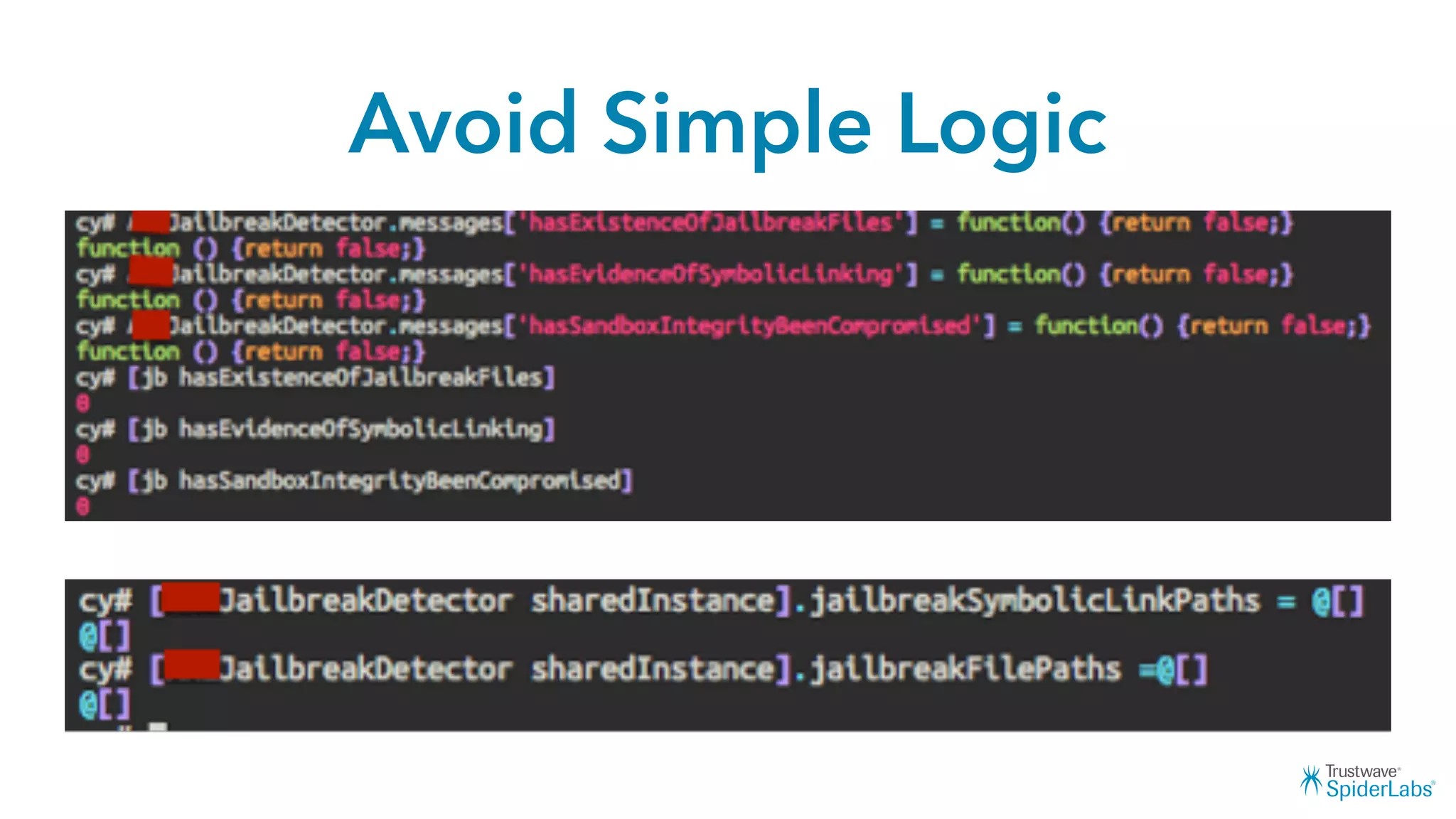
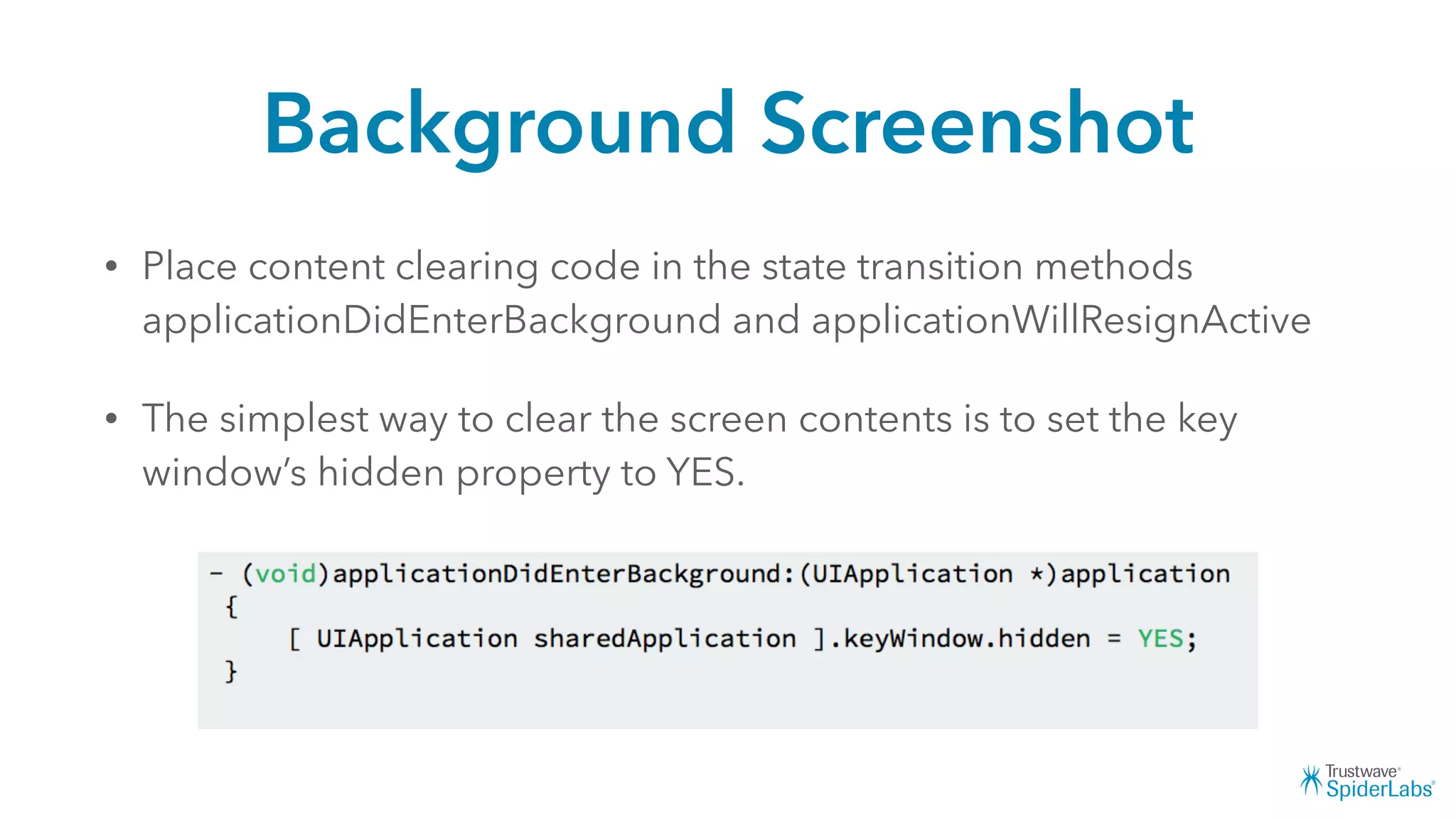
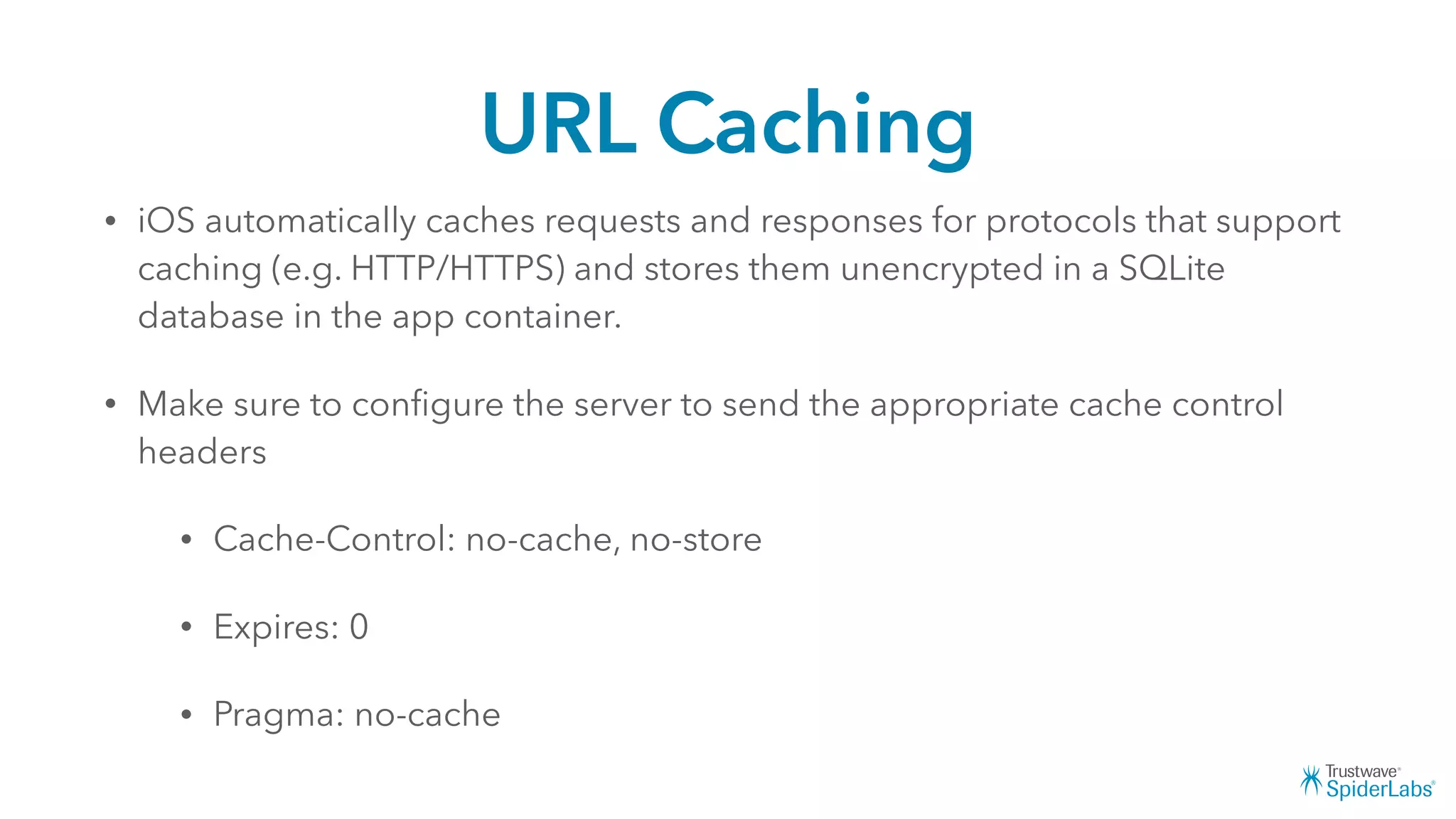
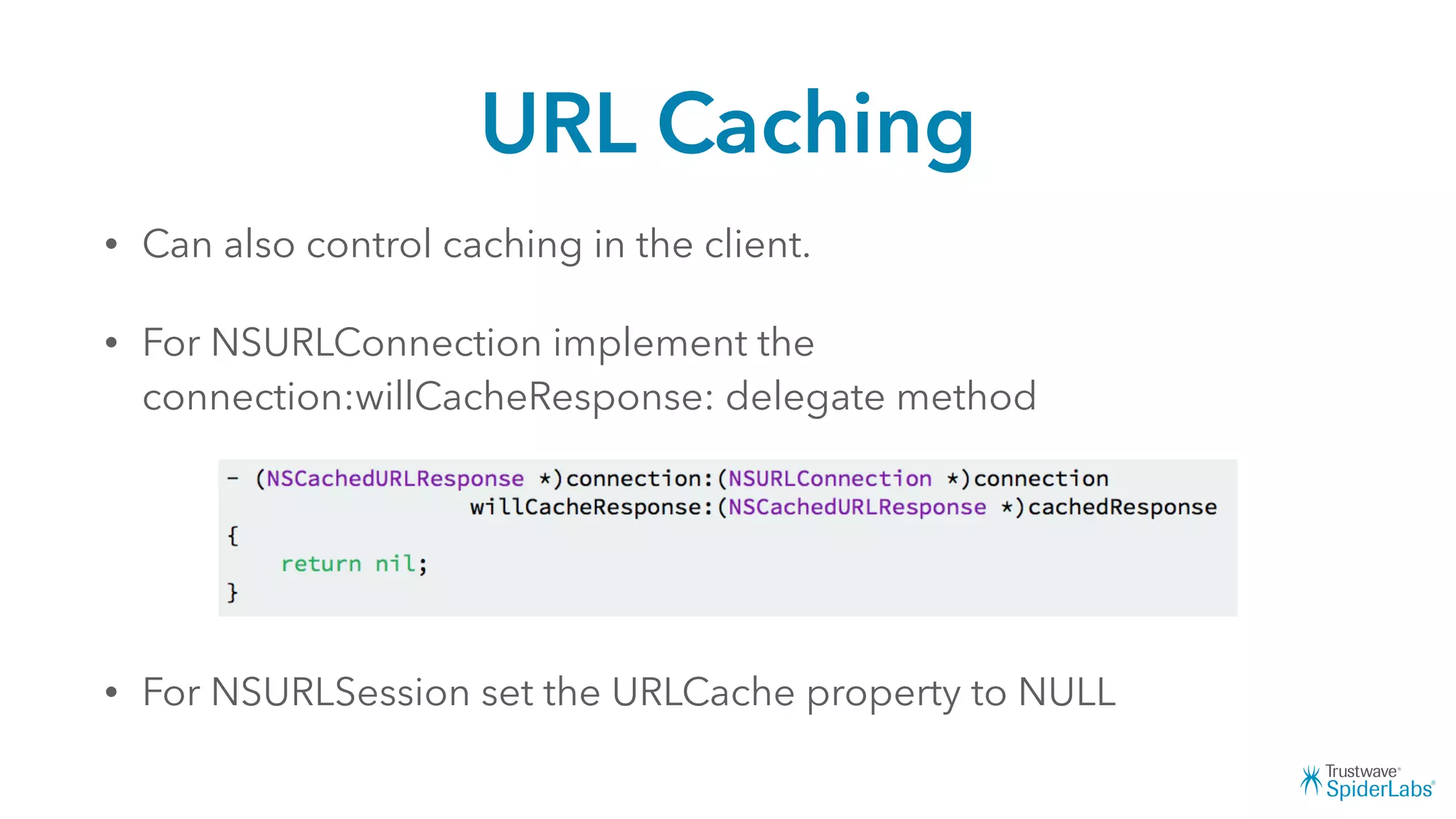
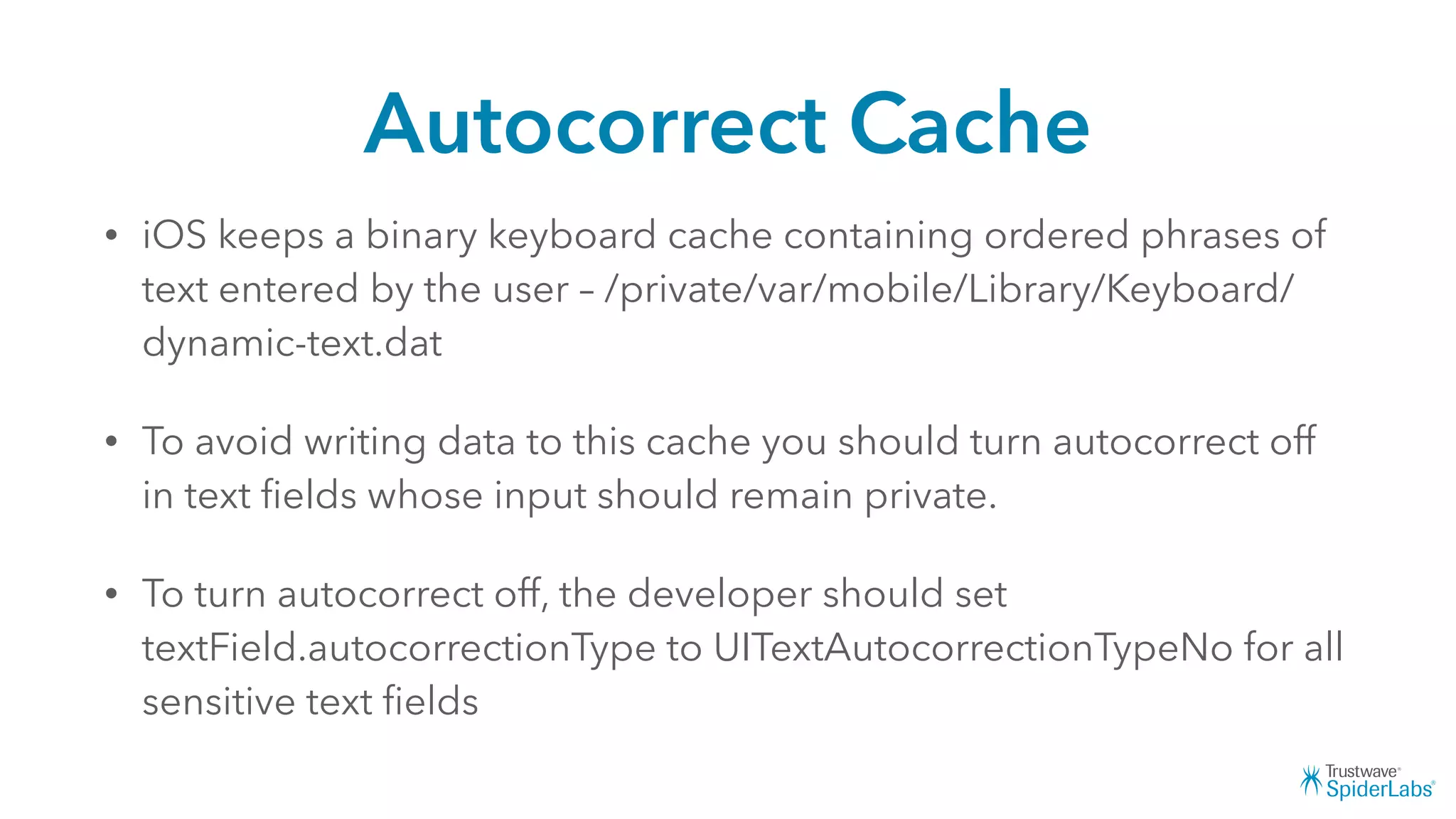
Michael Gianarakis' presentation discusses developing secure iOS applications. It provides an overview of the iOS application attack surface and common security issues. It outlines secure design principles such as not trusting the client/runtime, understanding the app's risk profile, implementing anti-debugging controls, jailbreak detection, and address space validation. The presentation aims to help developers design apps that are secure against common attacks.