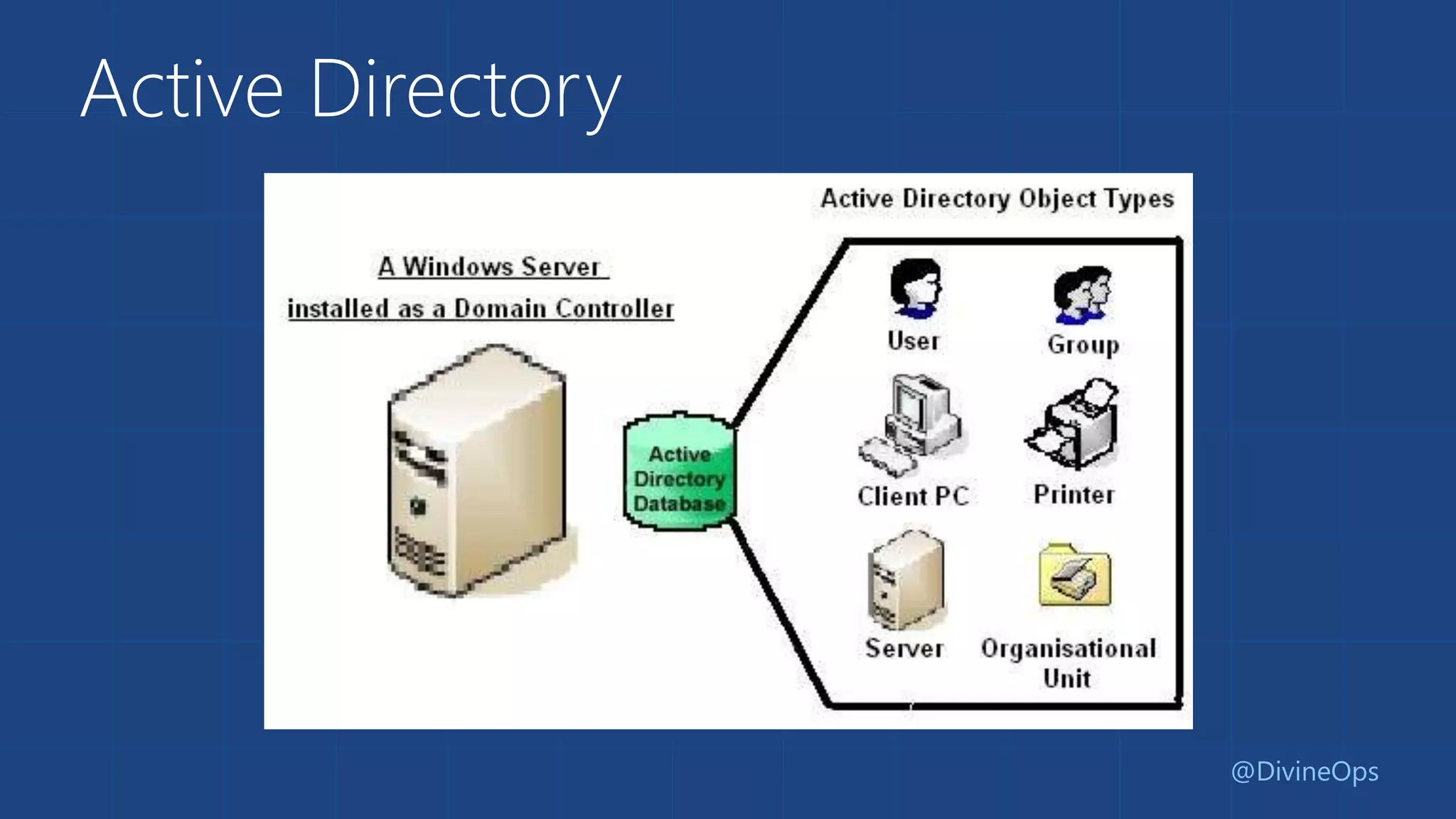
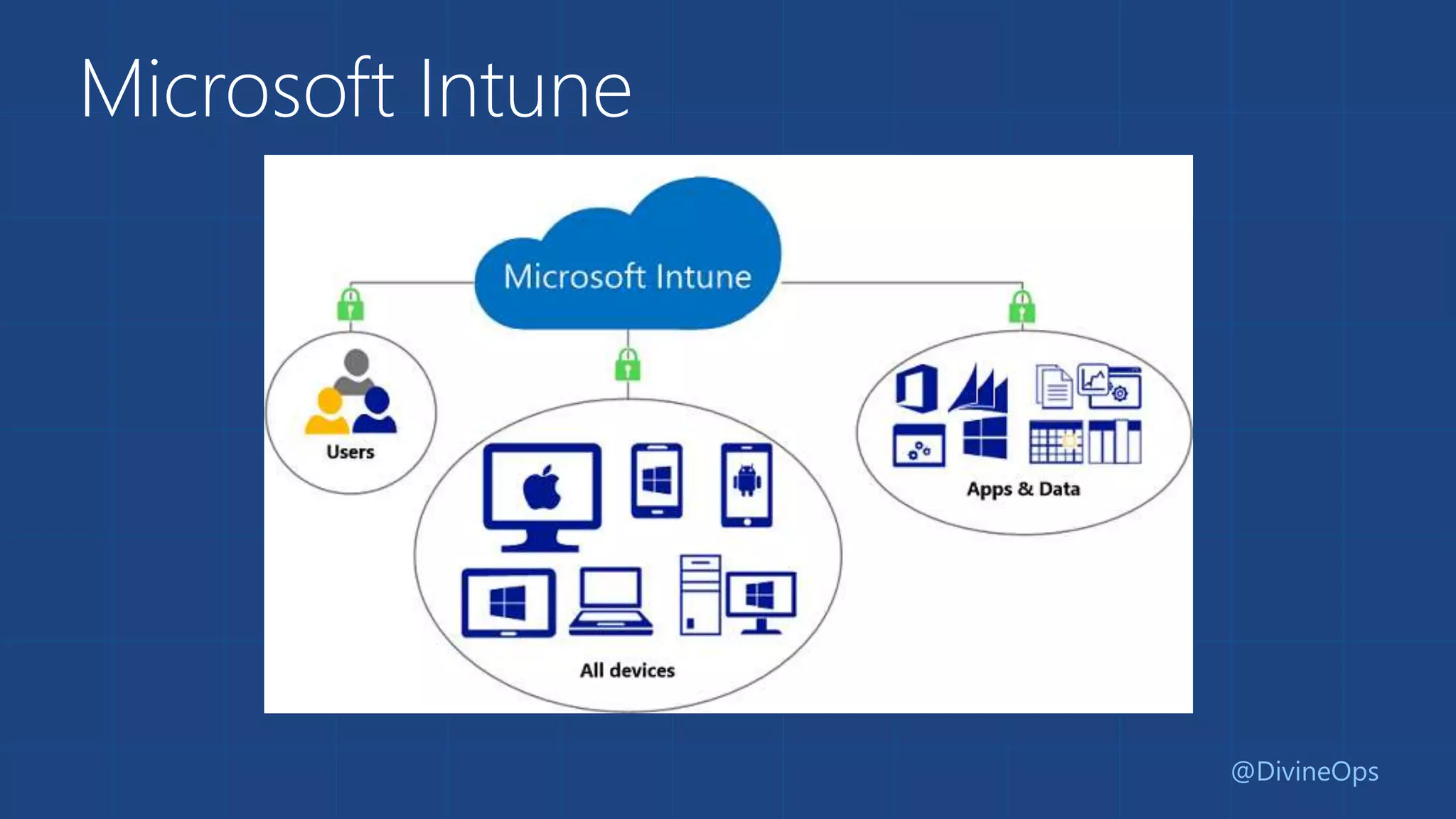
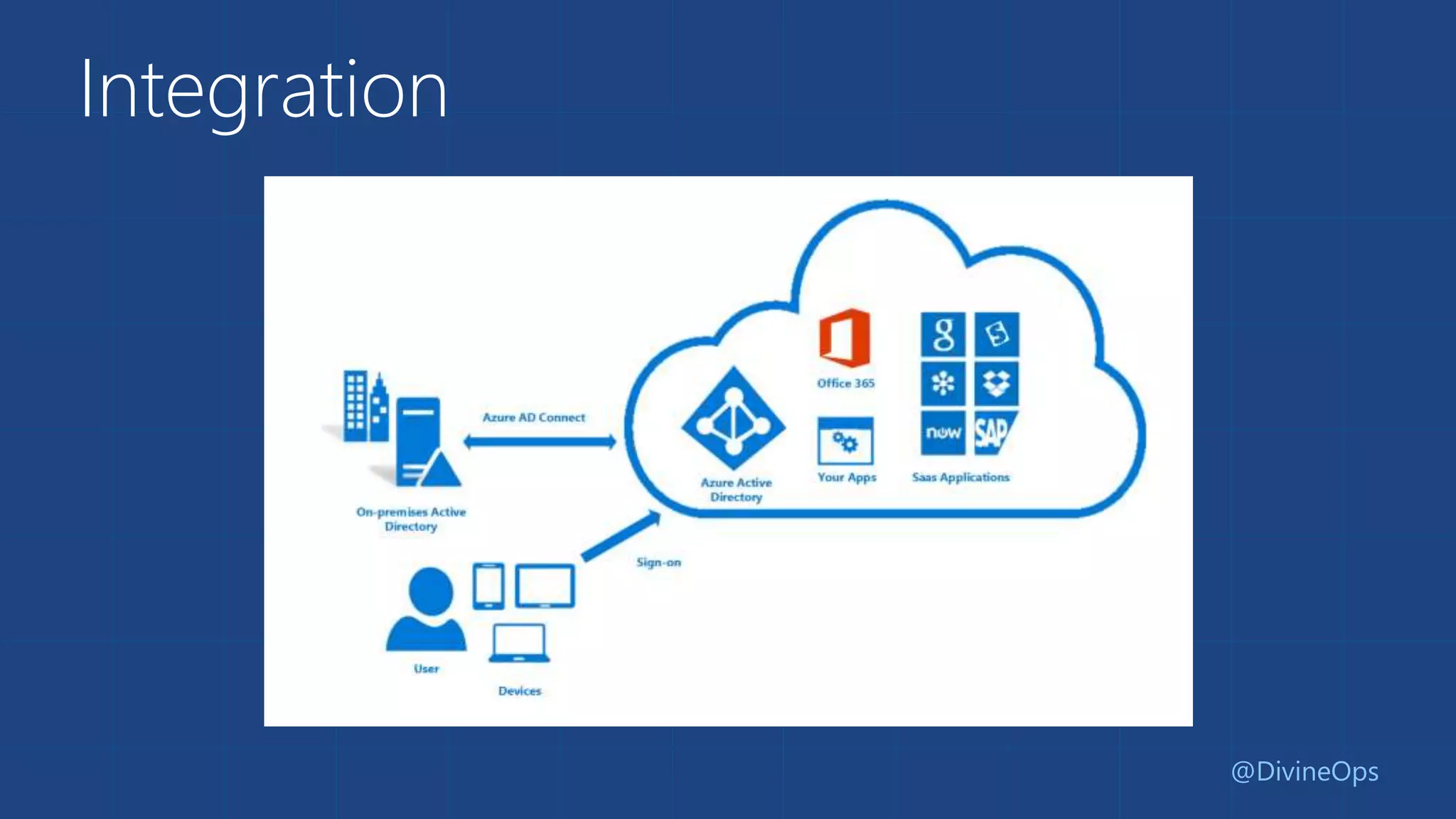
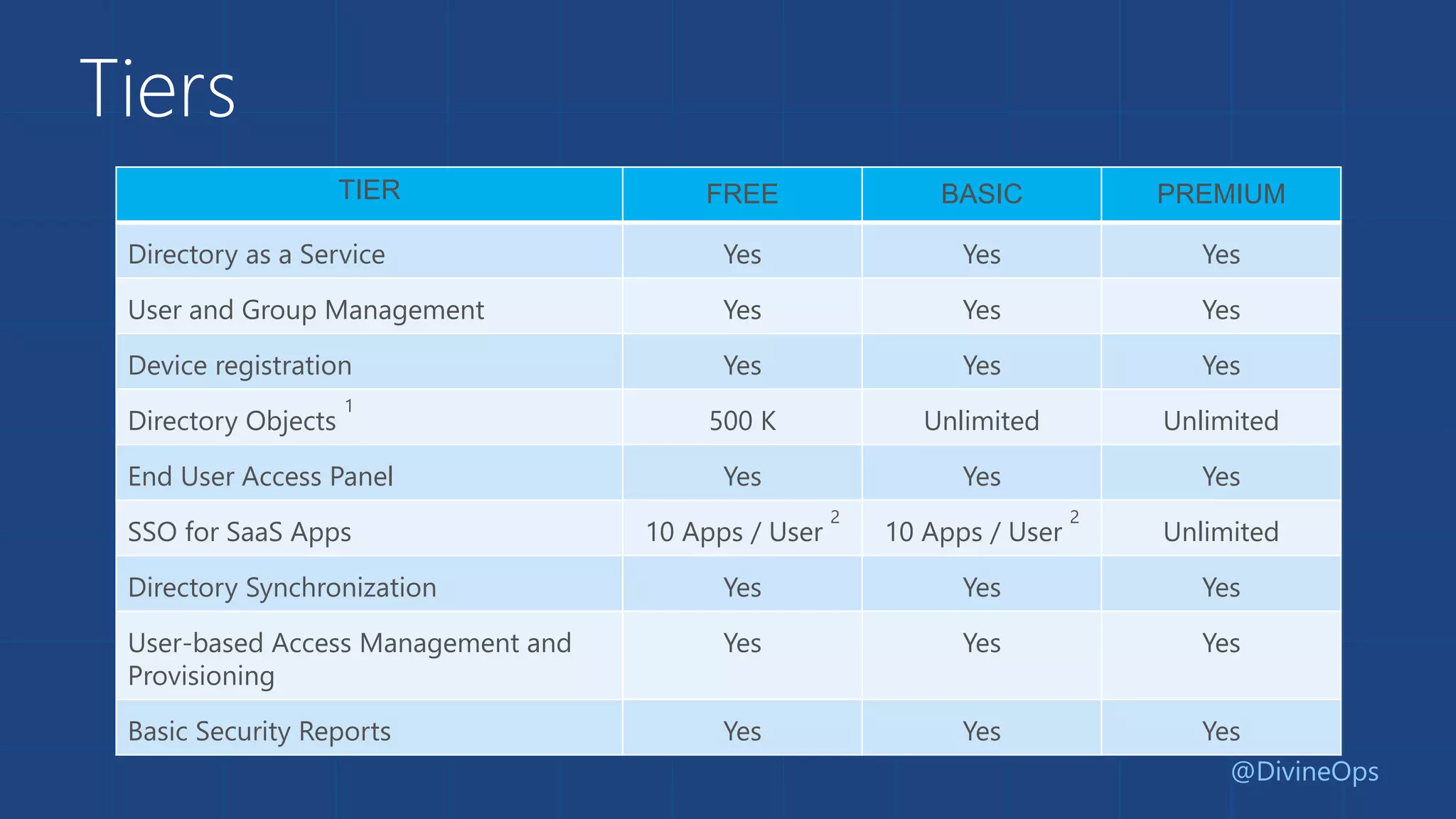
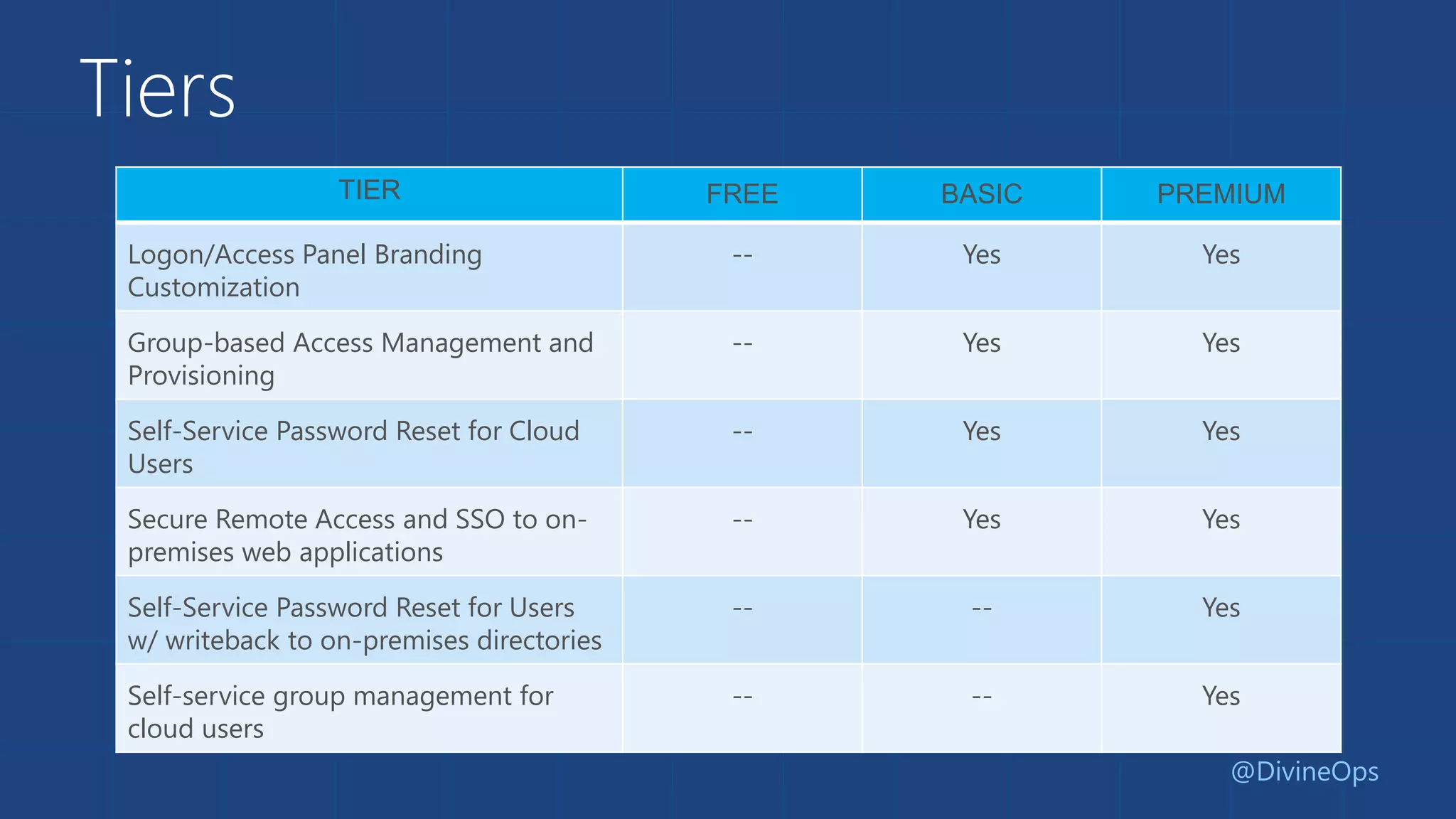
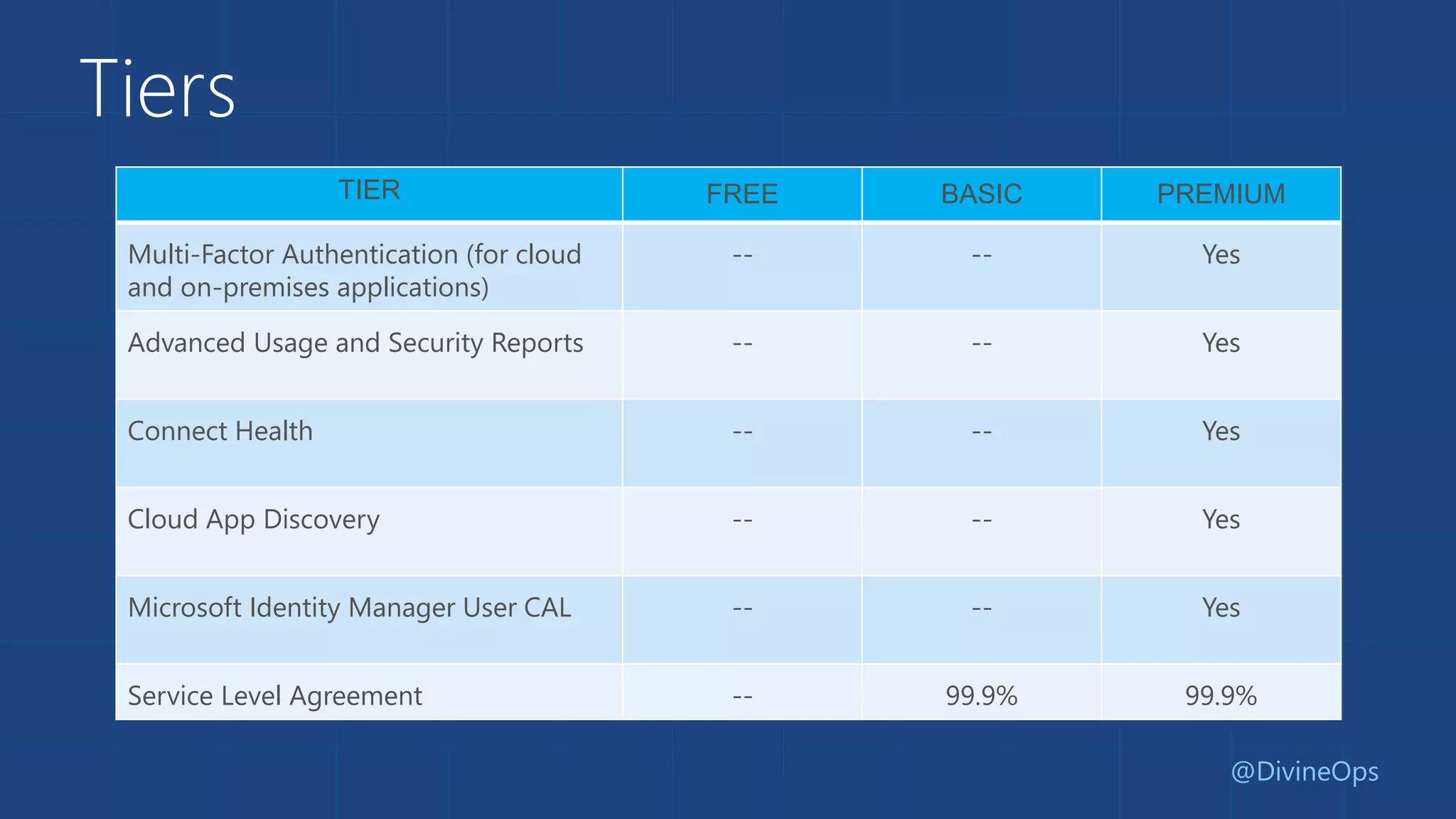
The document provides a comprehensive guide to Azure Active Directory, detailing its origins, features, and the differences between free, basic, and premium tiers for identity management services. It covers integration protocols, application access management, and various scenarios for using Azure AD, including SaaS and on-premise applications. Additionally, it highlights new features and what to expect in the future, particularly in the Business-to-Consumer Azure Active Directory services.