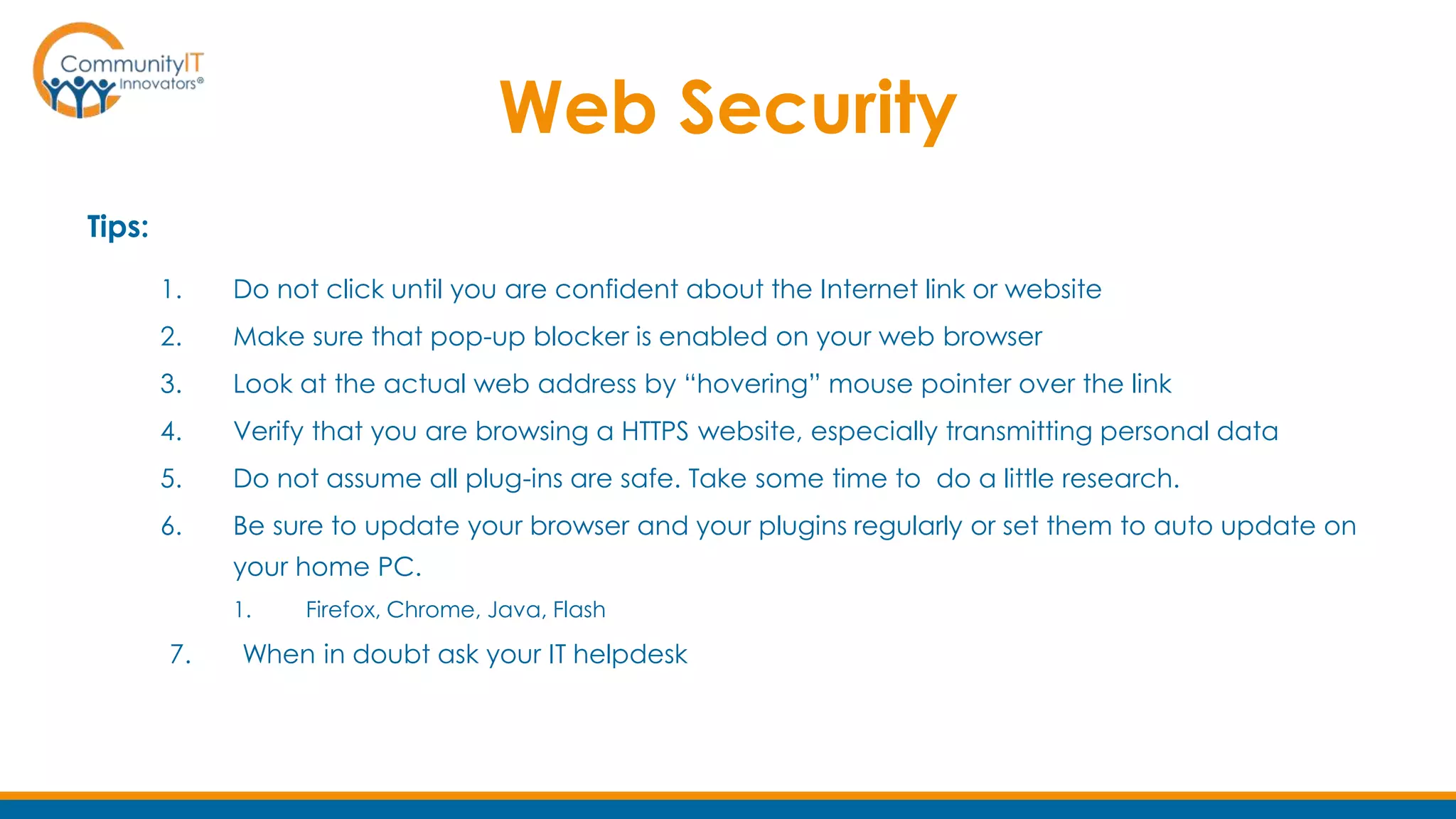
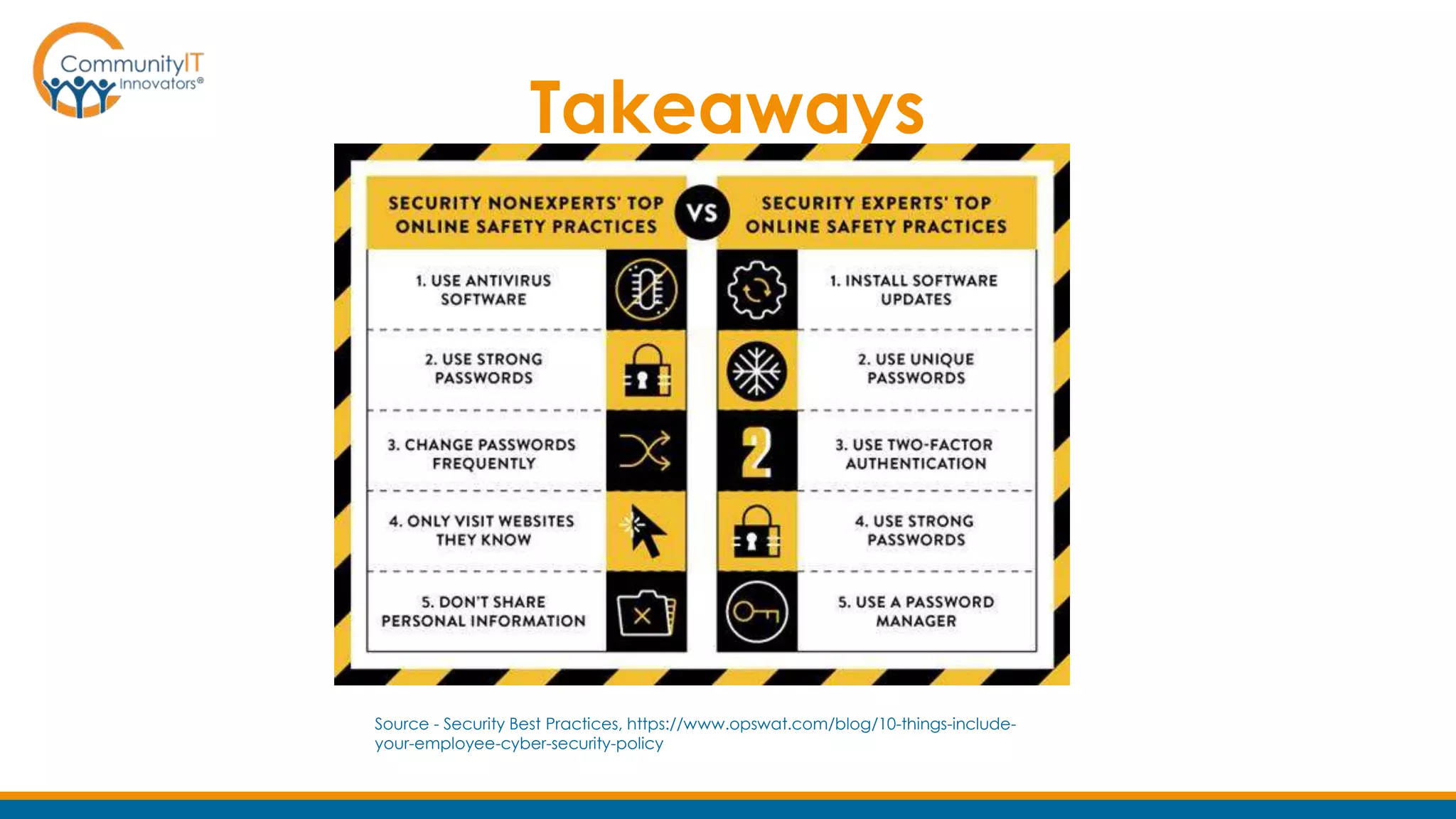
The document outlines a webinar on training nonprofit staff in end-user IT security, emphasizing the importance of awareness and education to safeguard against various digital threats. Key topics include password security, email and web threats, and mobile security tips, highlighting practical measures for maintaining security. Additionally, the document promotes an upcoming webinar on nonprofit IT budgeting and mentions feedback opportunities for participants.