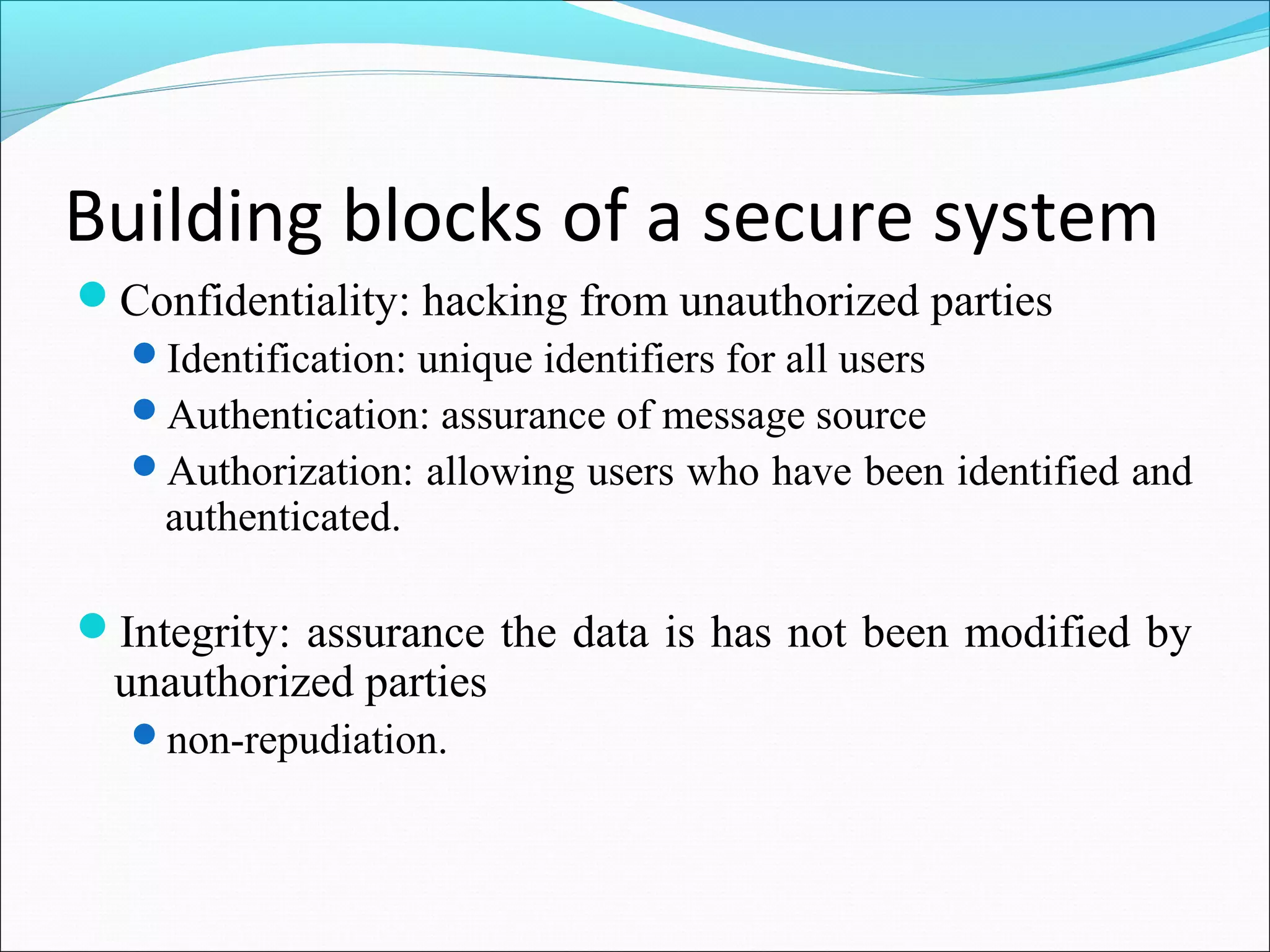
This document provides an overview of information security basics. It discusses how information security aims to prevent unauthorized use, disclosure, alteration or substitution of electronic data through measures that ensure confidentiality, integrity and availability of information. It also outlines some key building blocks of secure systems like identification, authentication, authorization, and integrity. The document describes security processes, attacks against systems, and approaches for prevention, detection and response to security incidents.