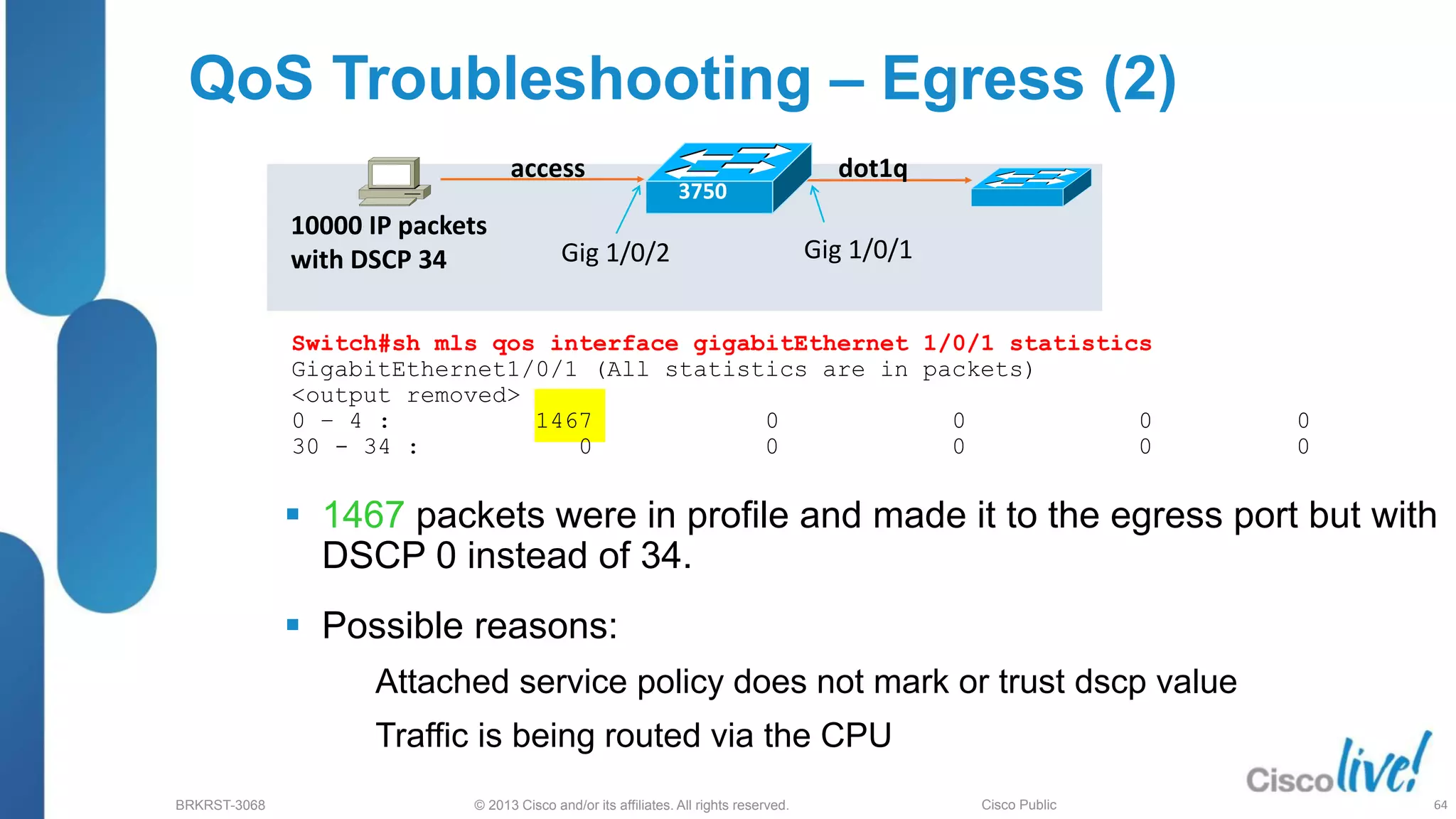
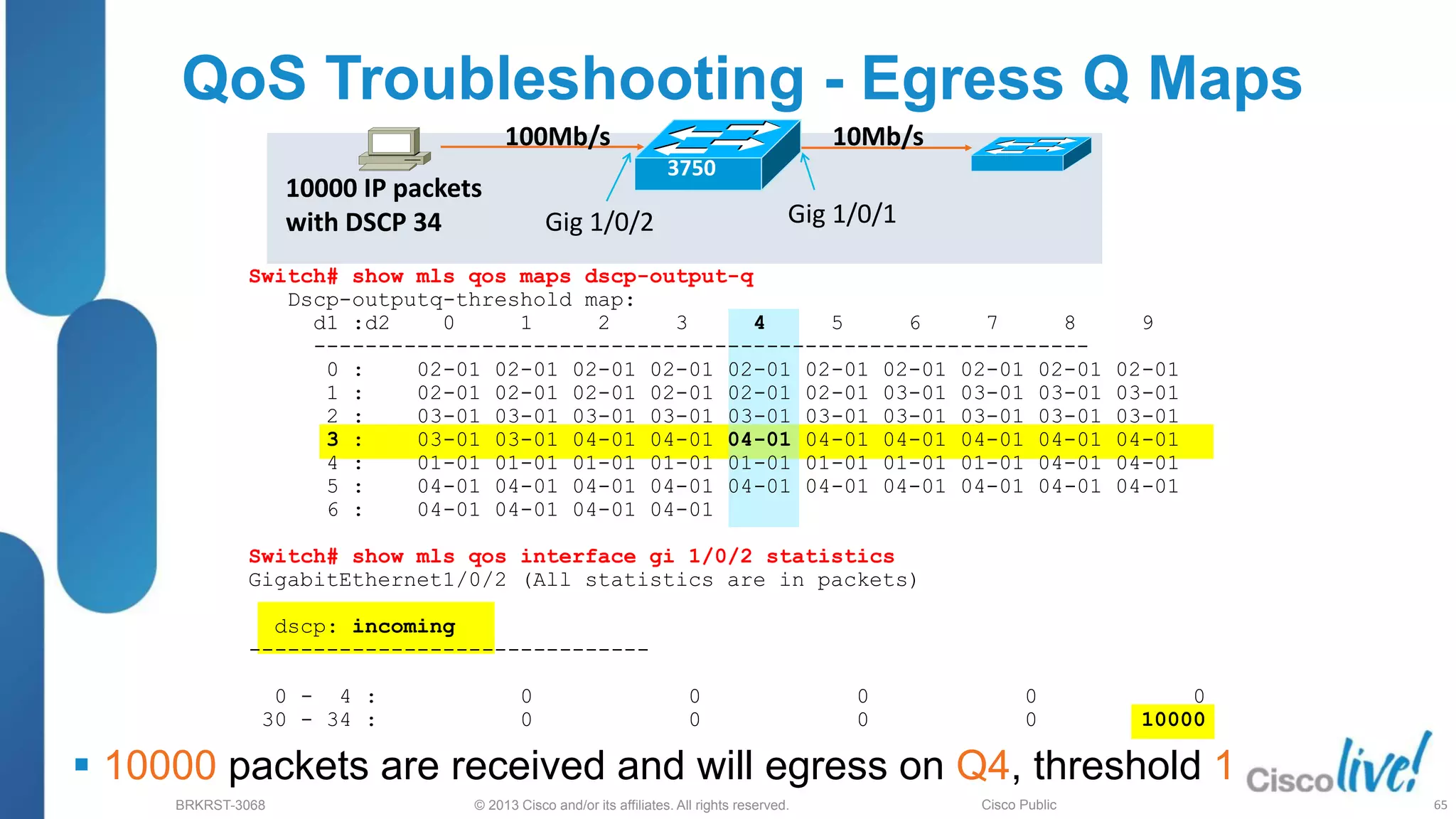
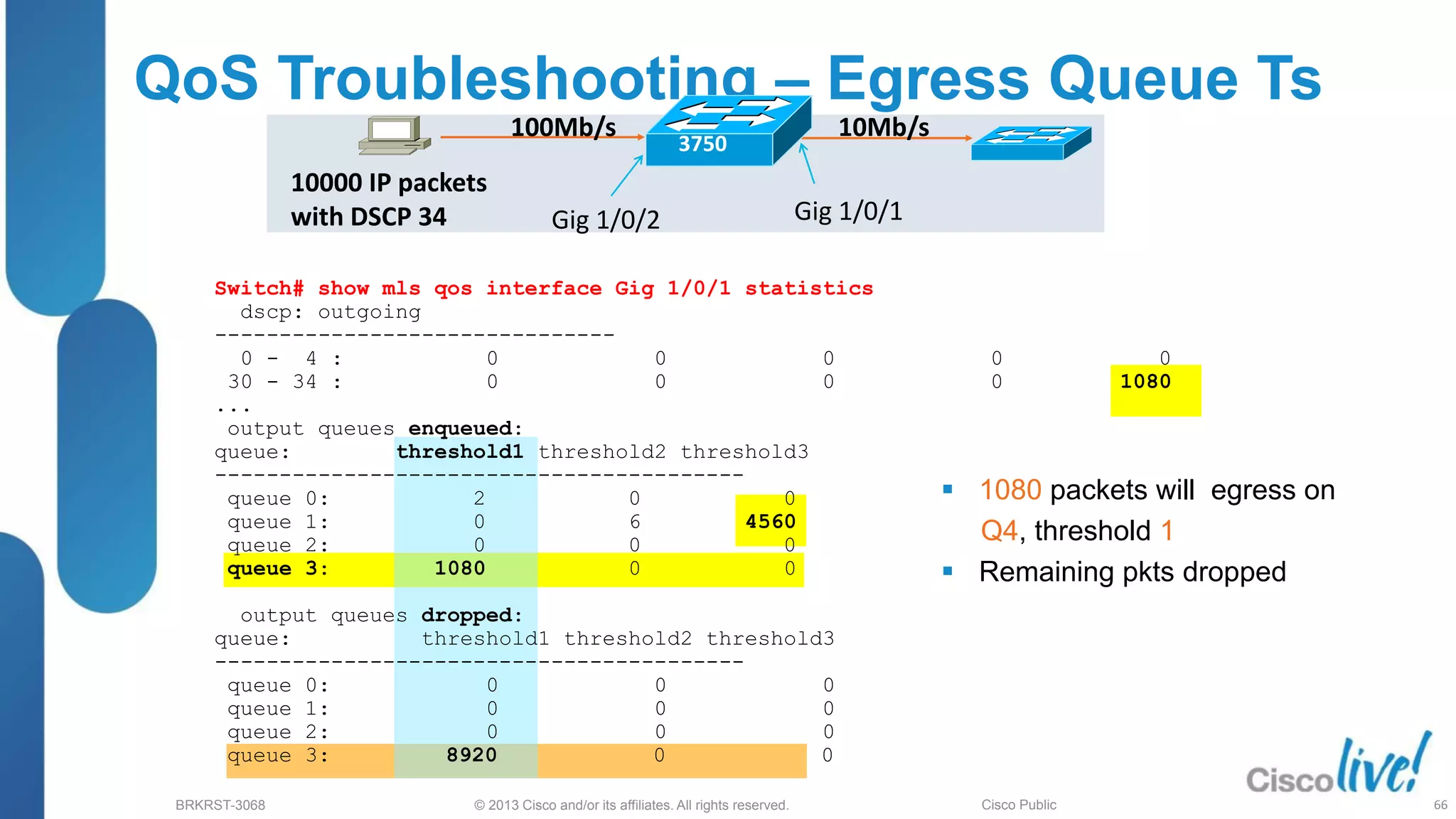
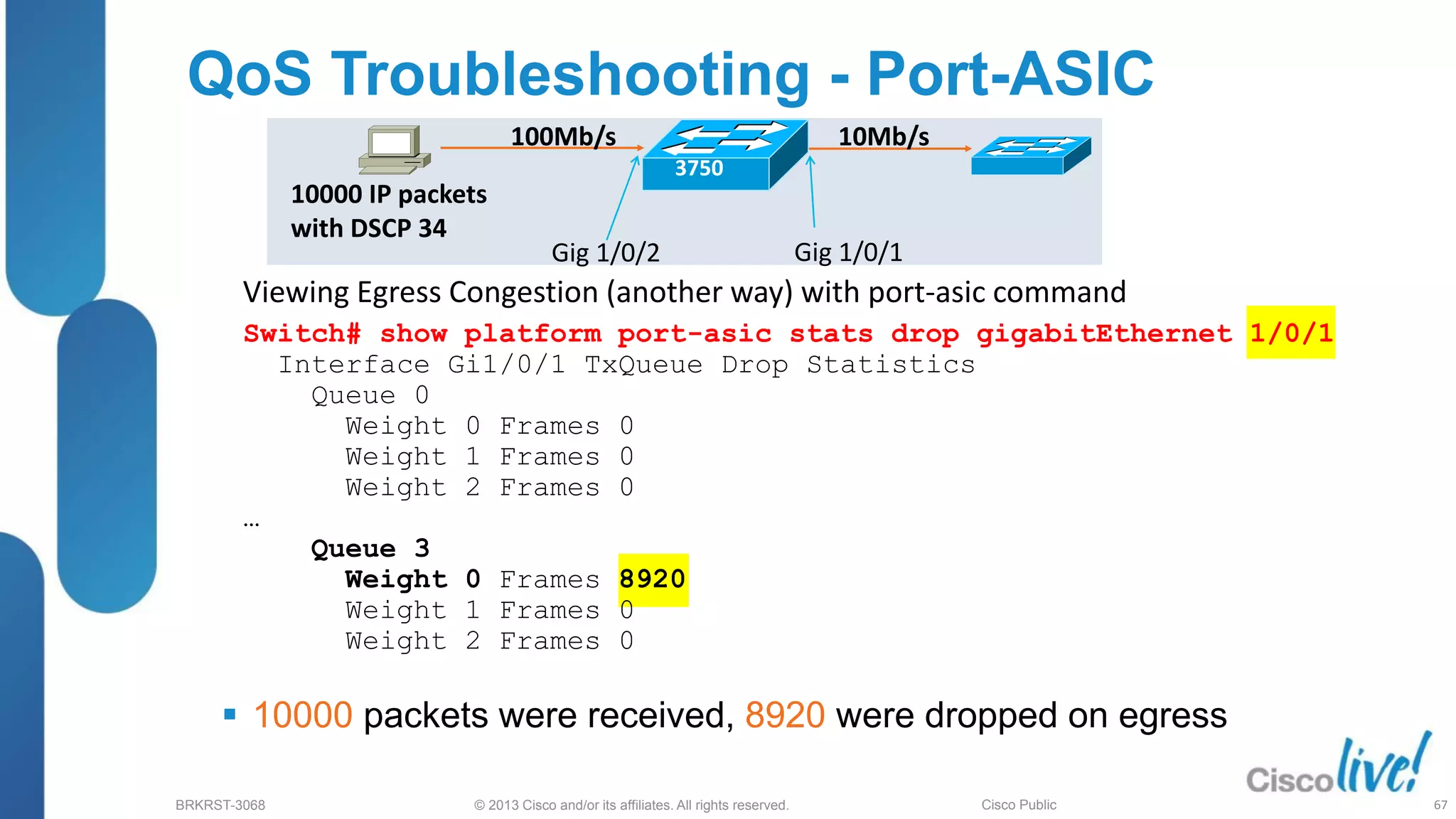
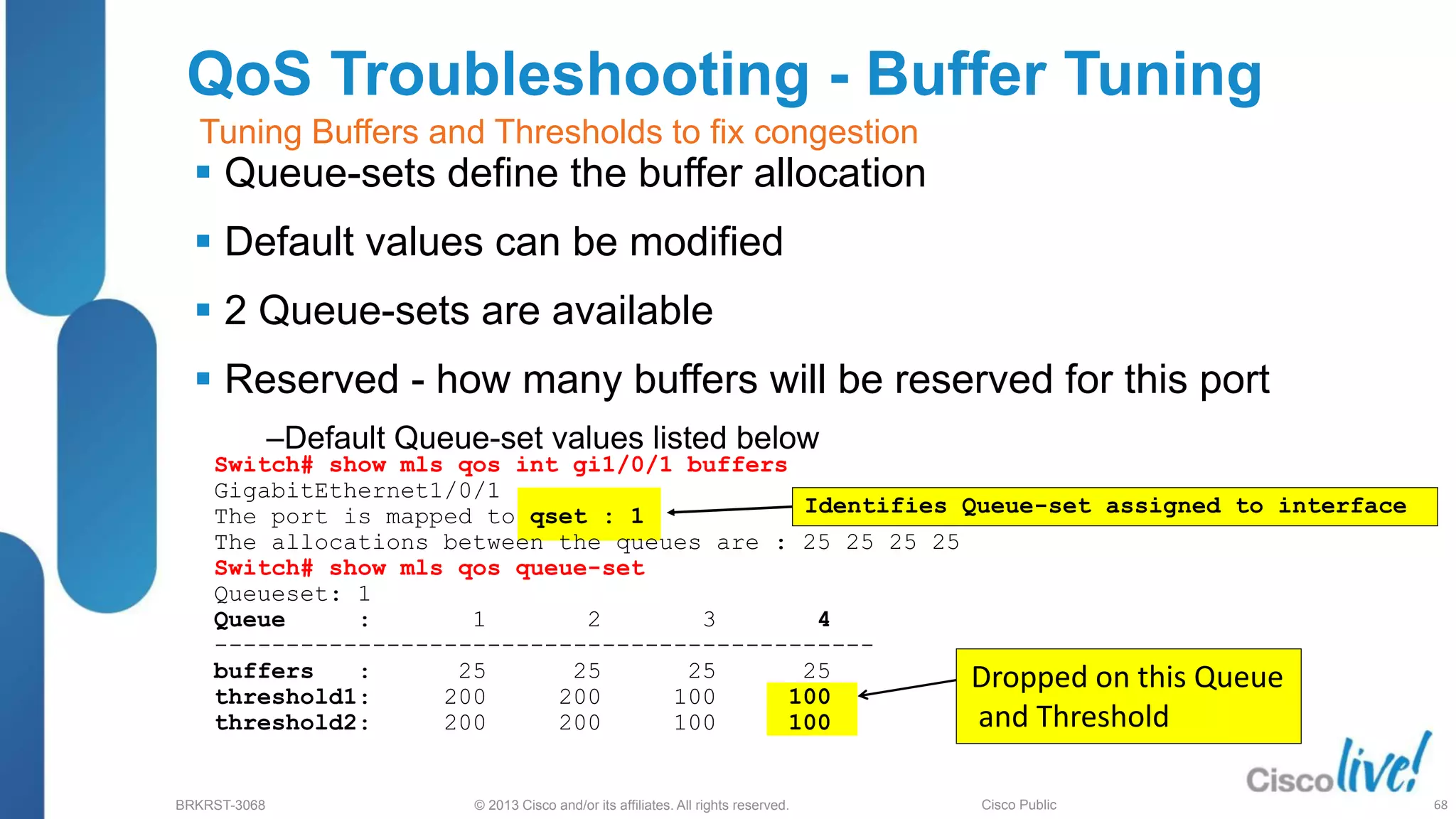
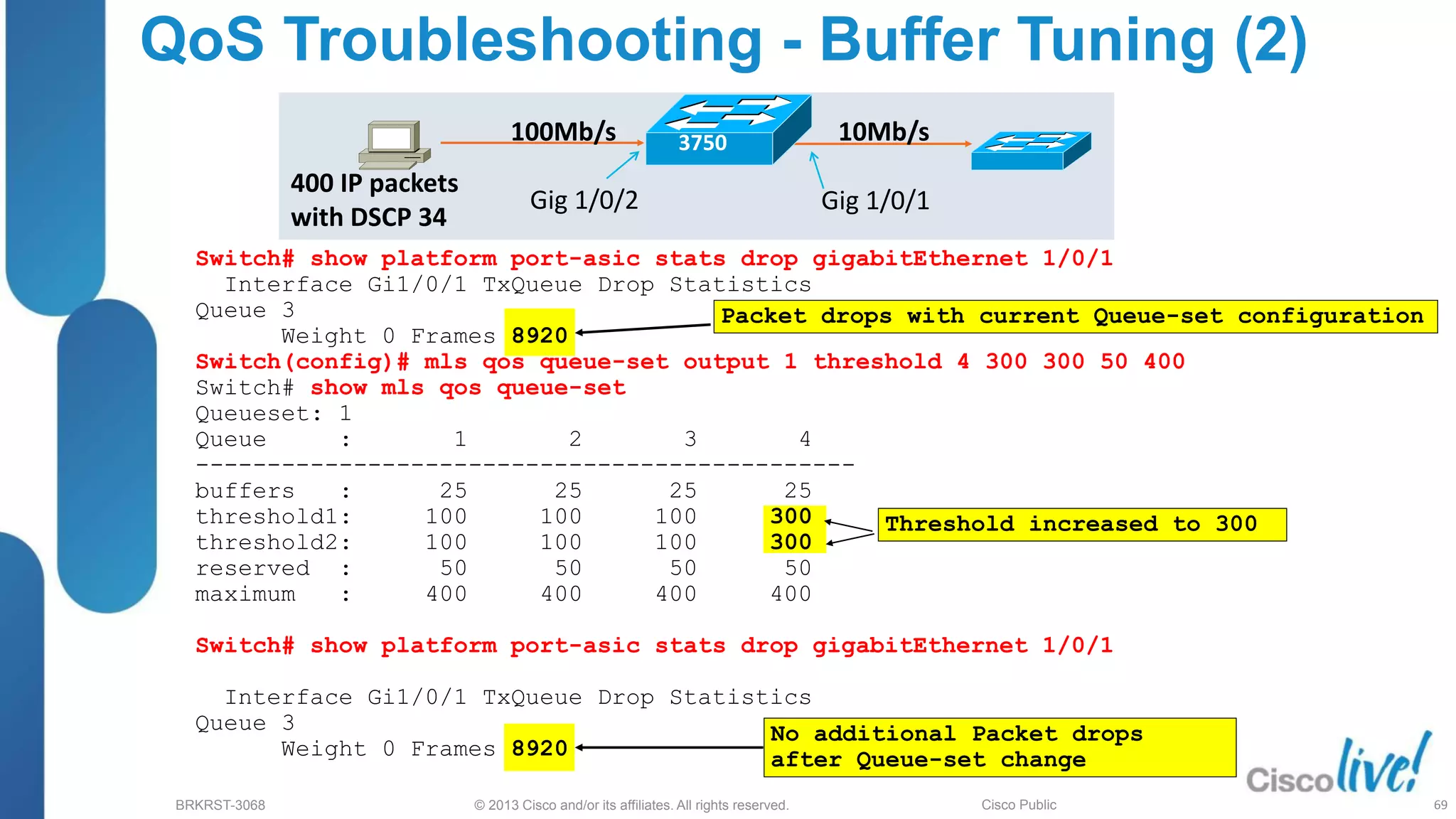
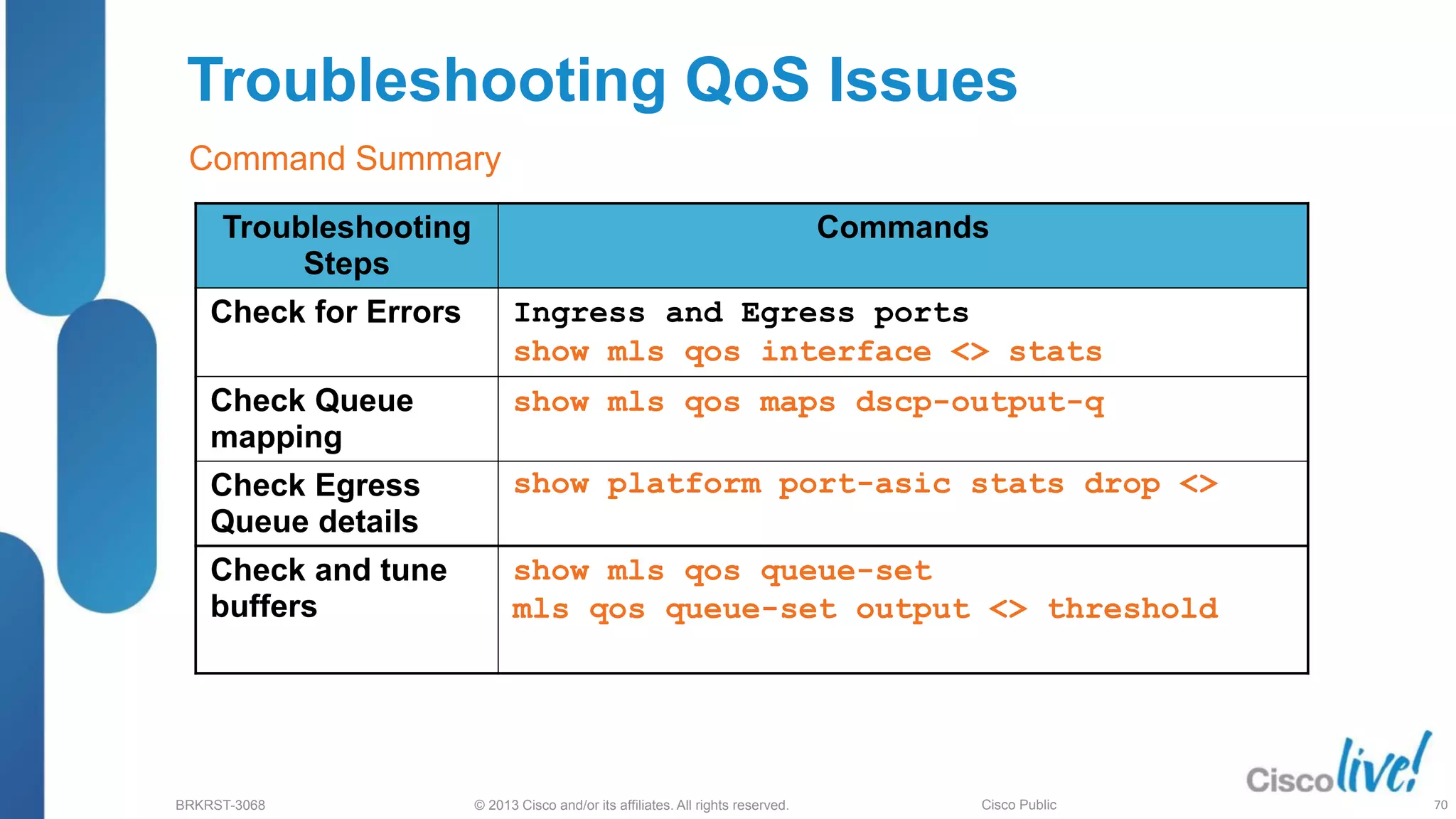
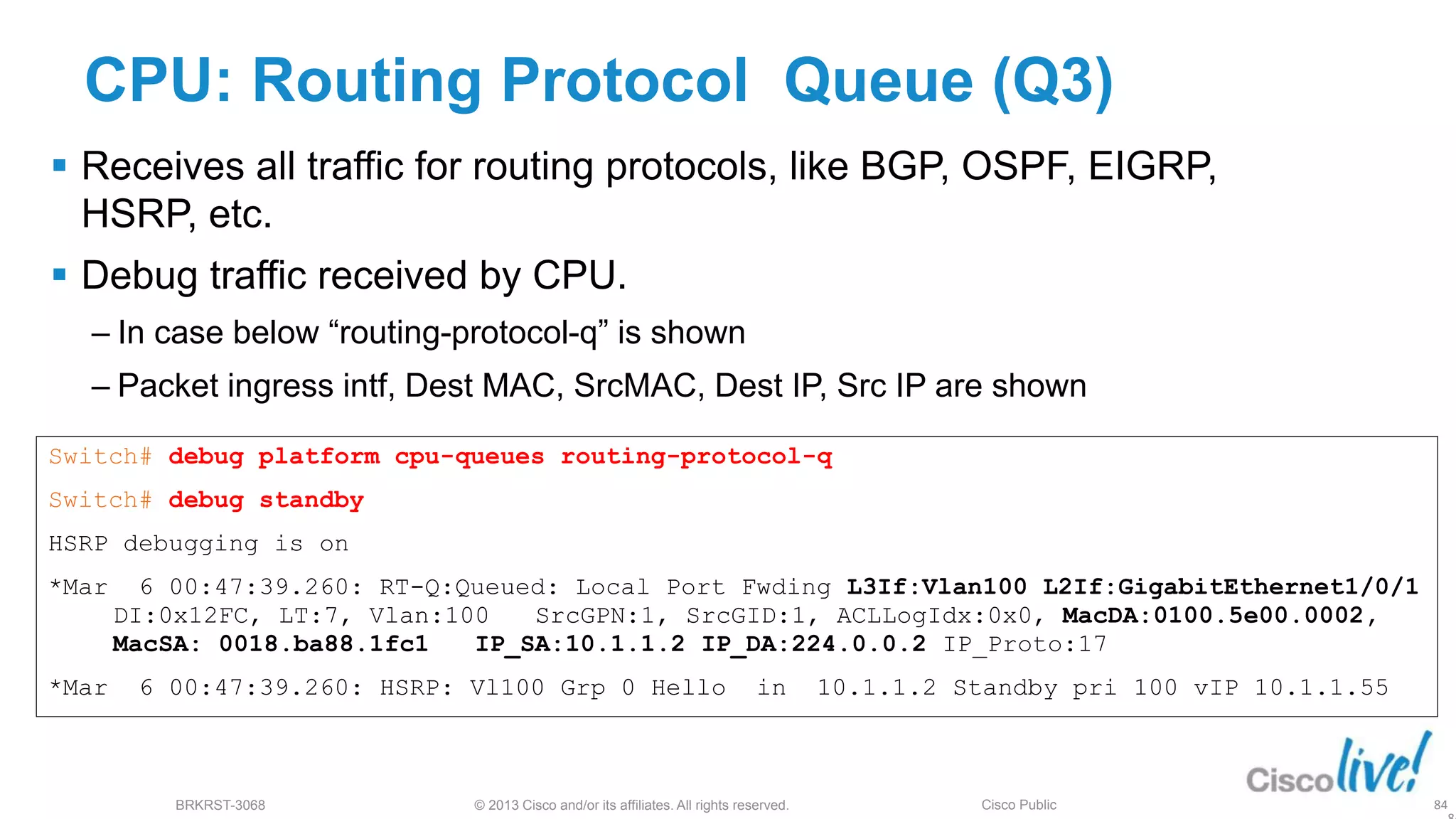
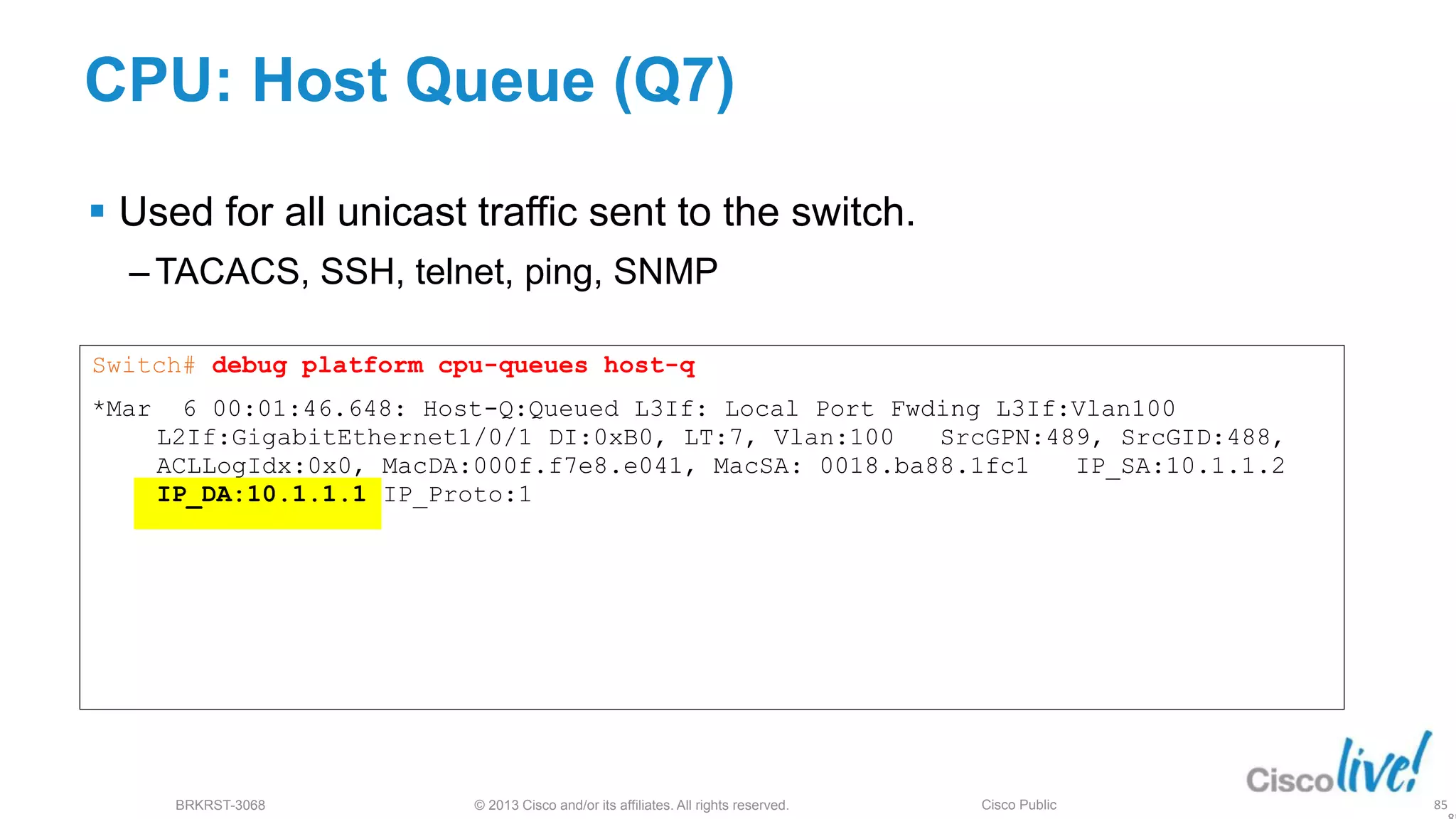
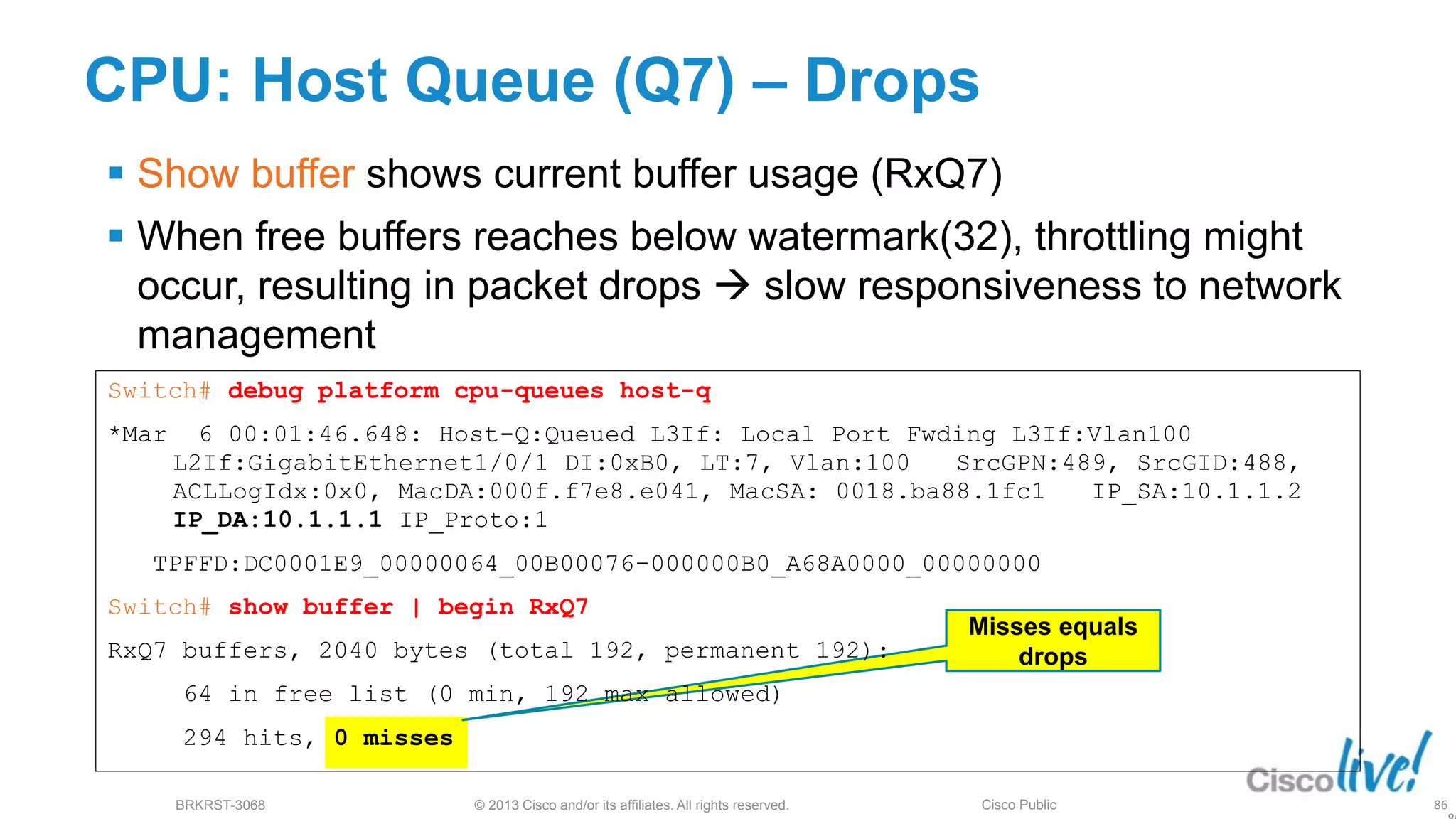
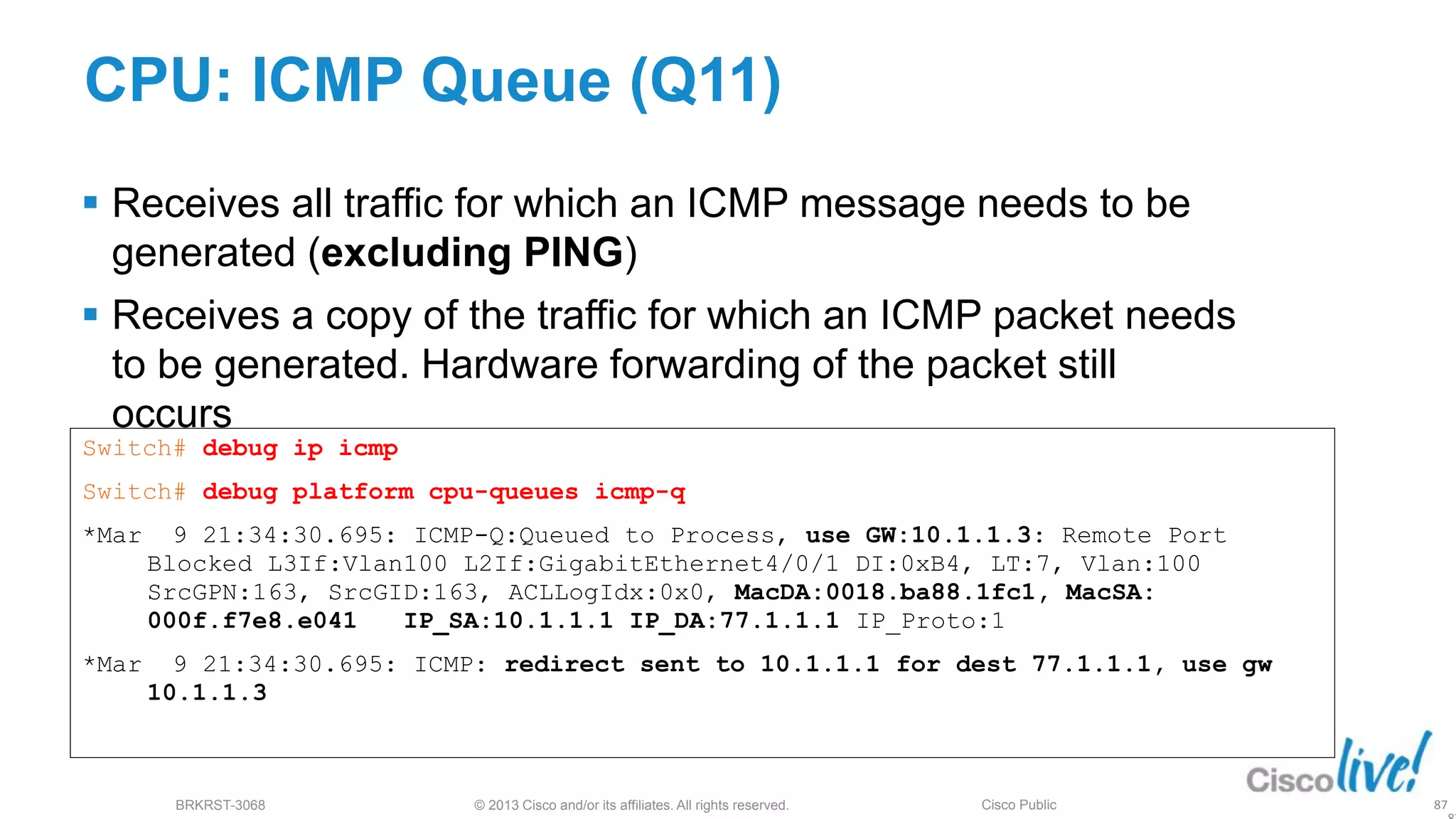
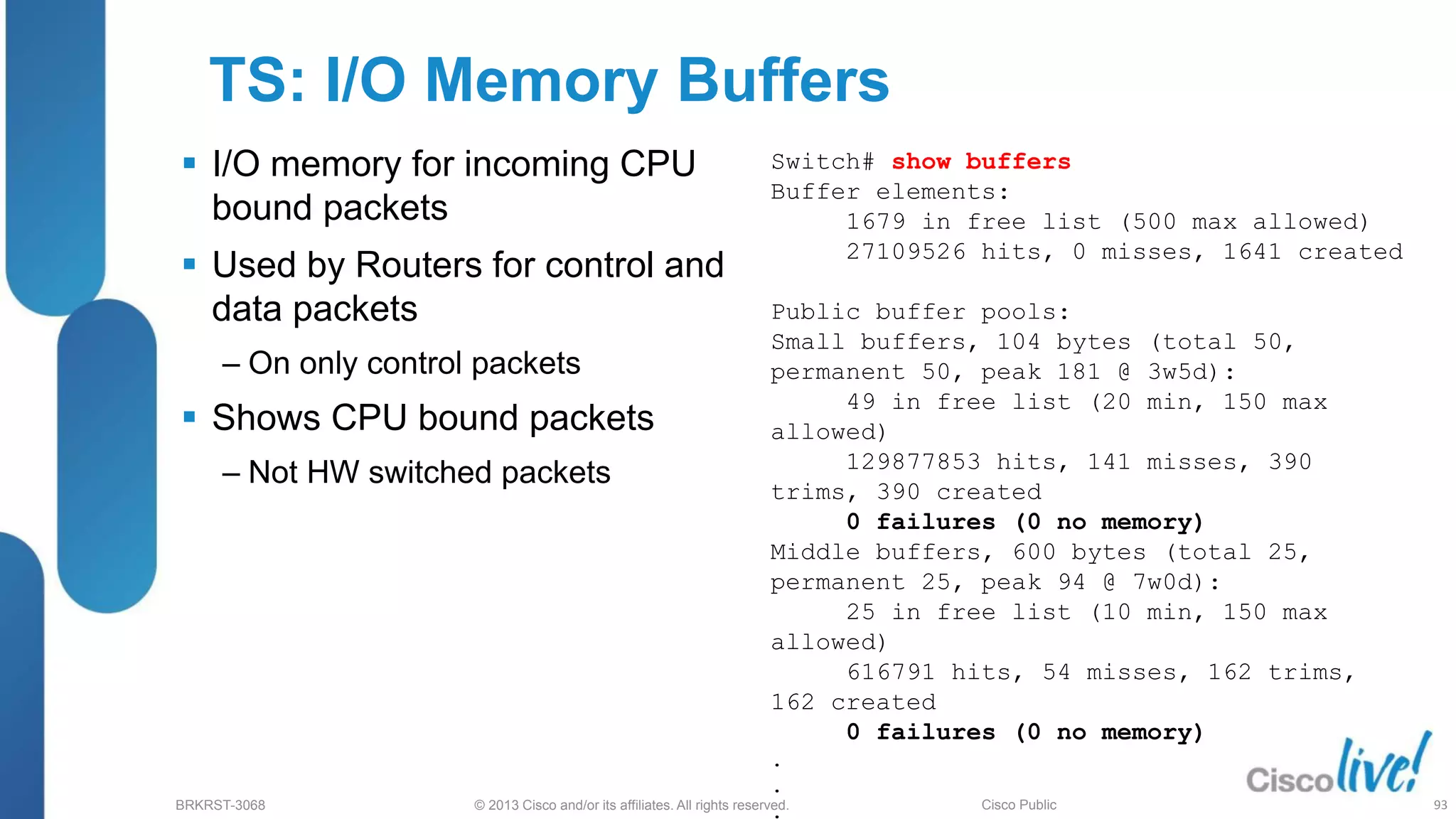
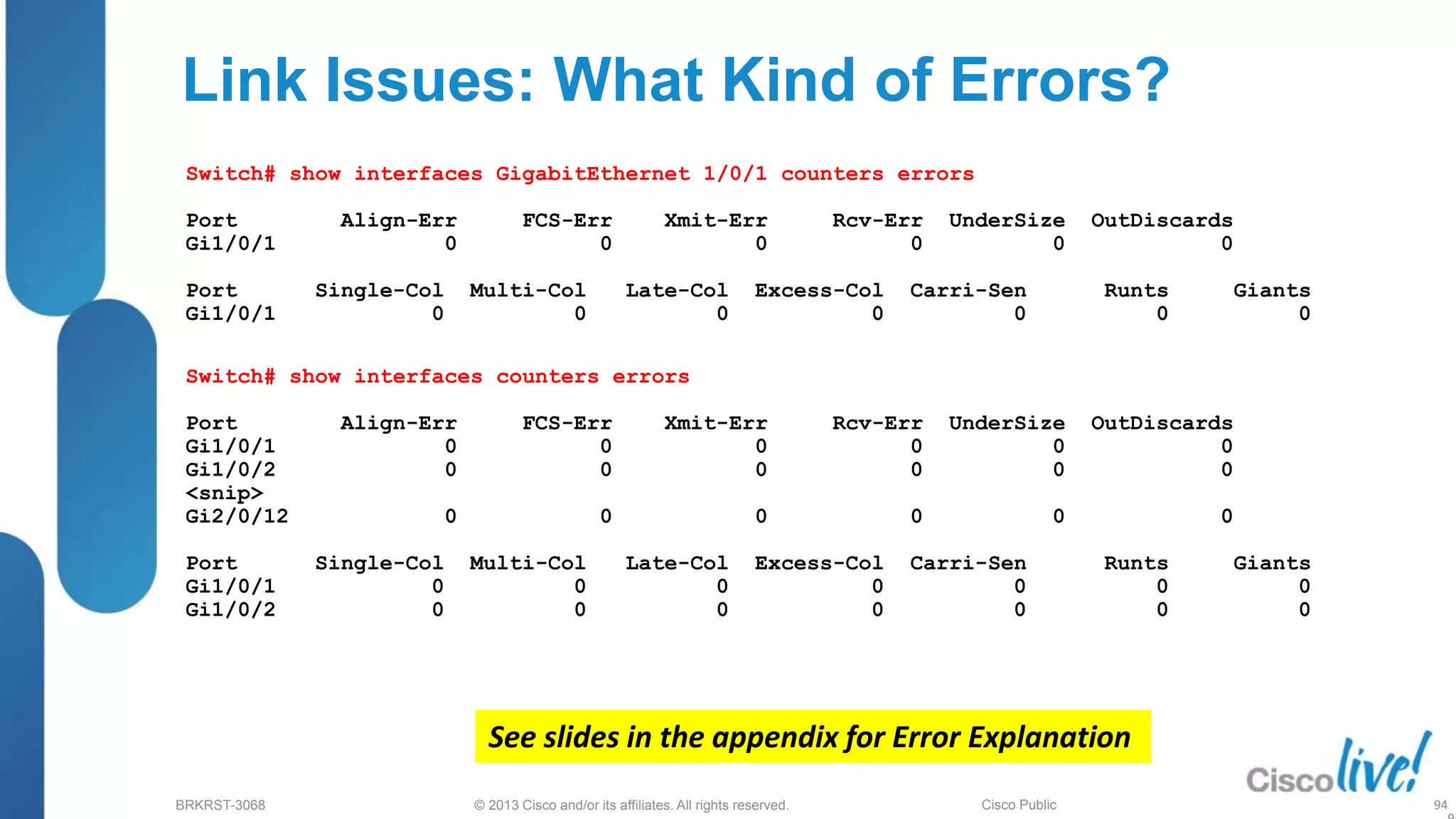
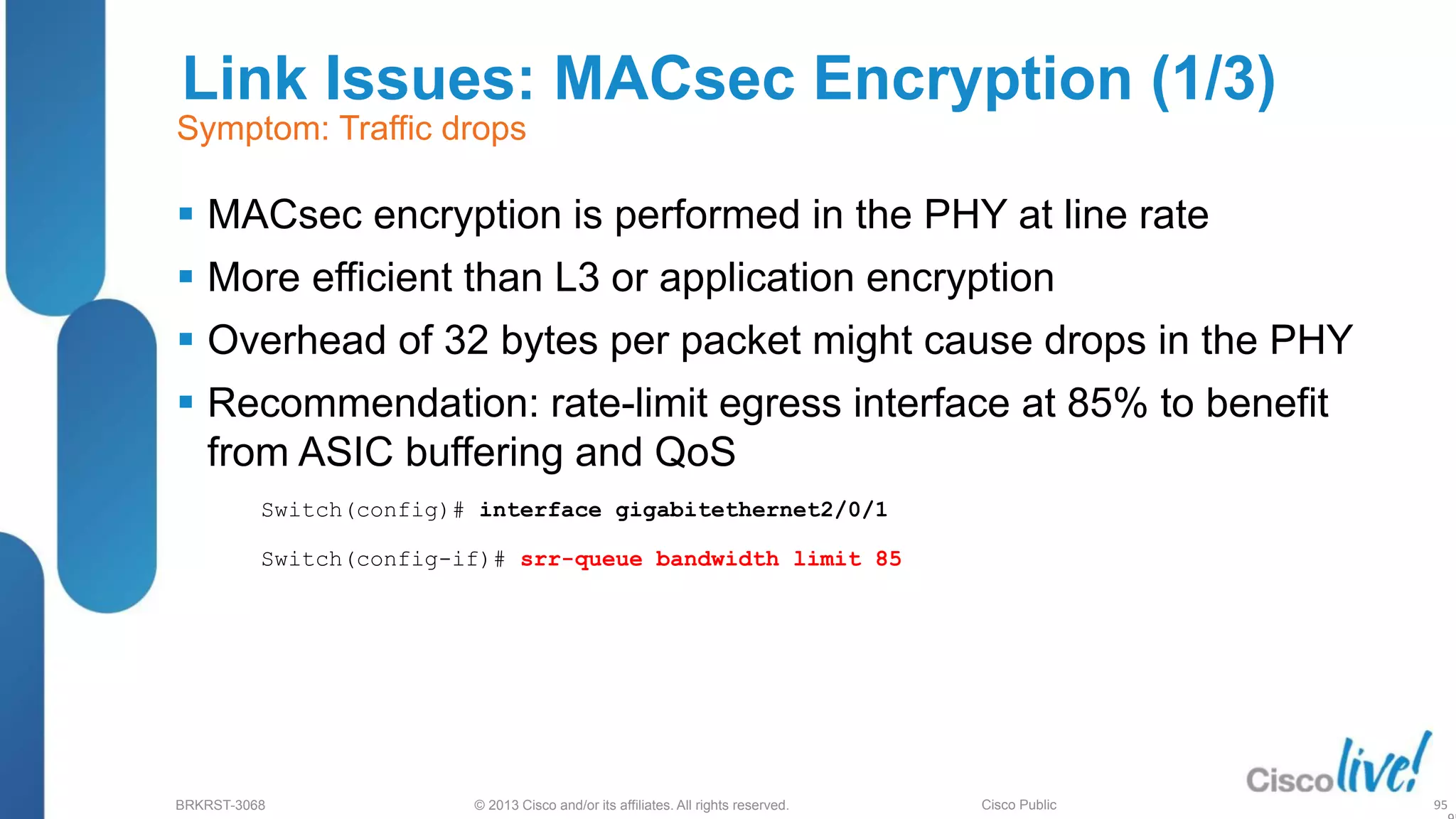
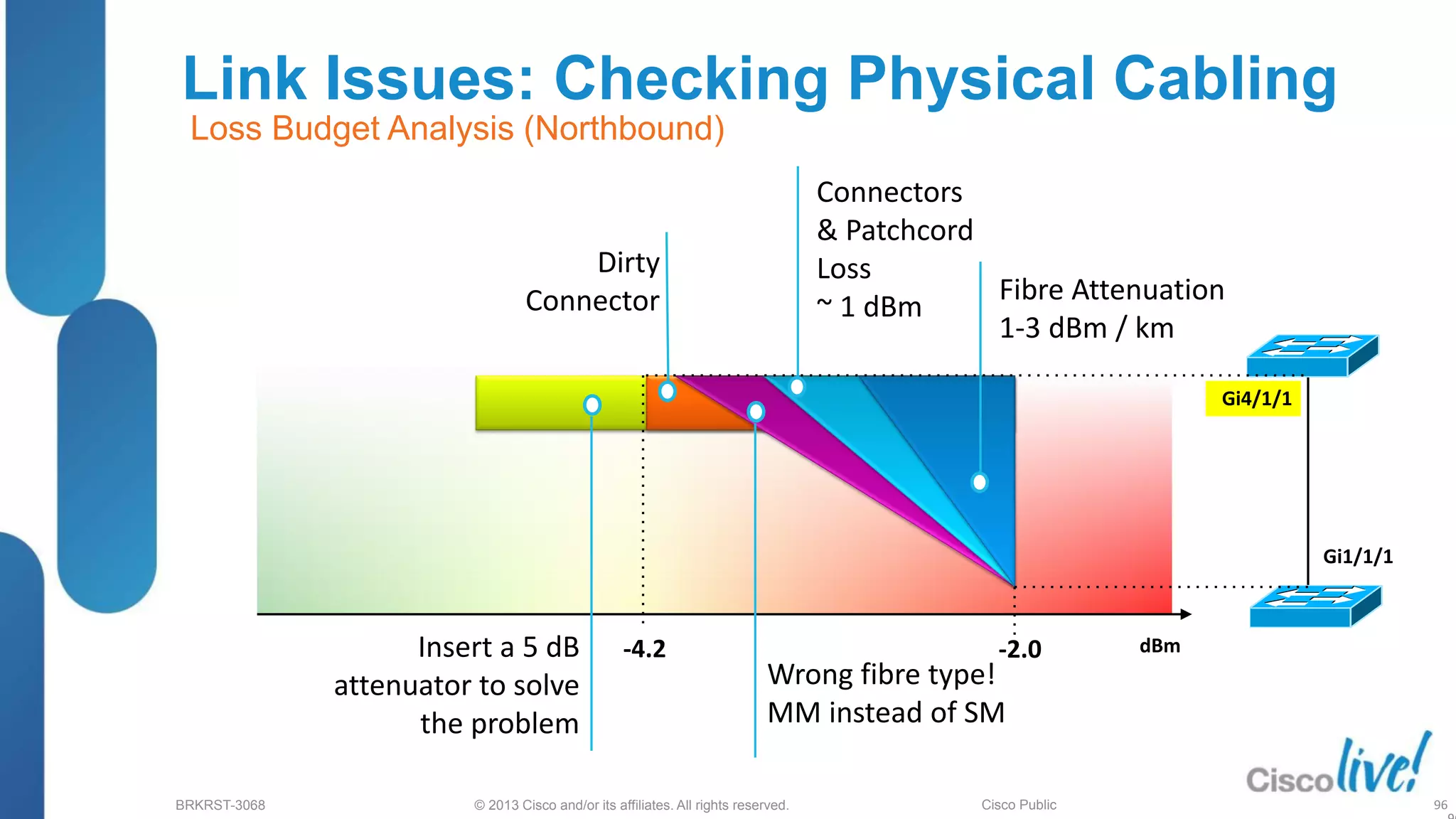
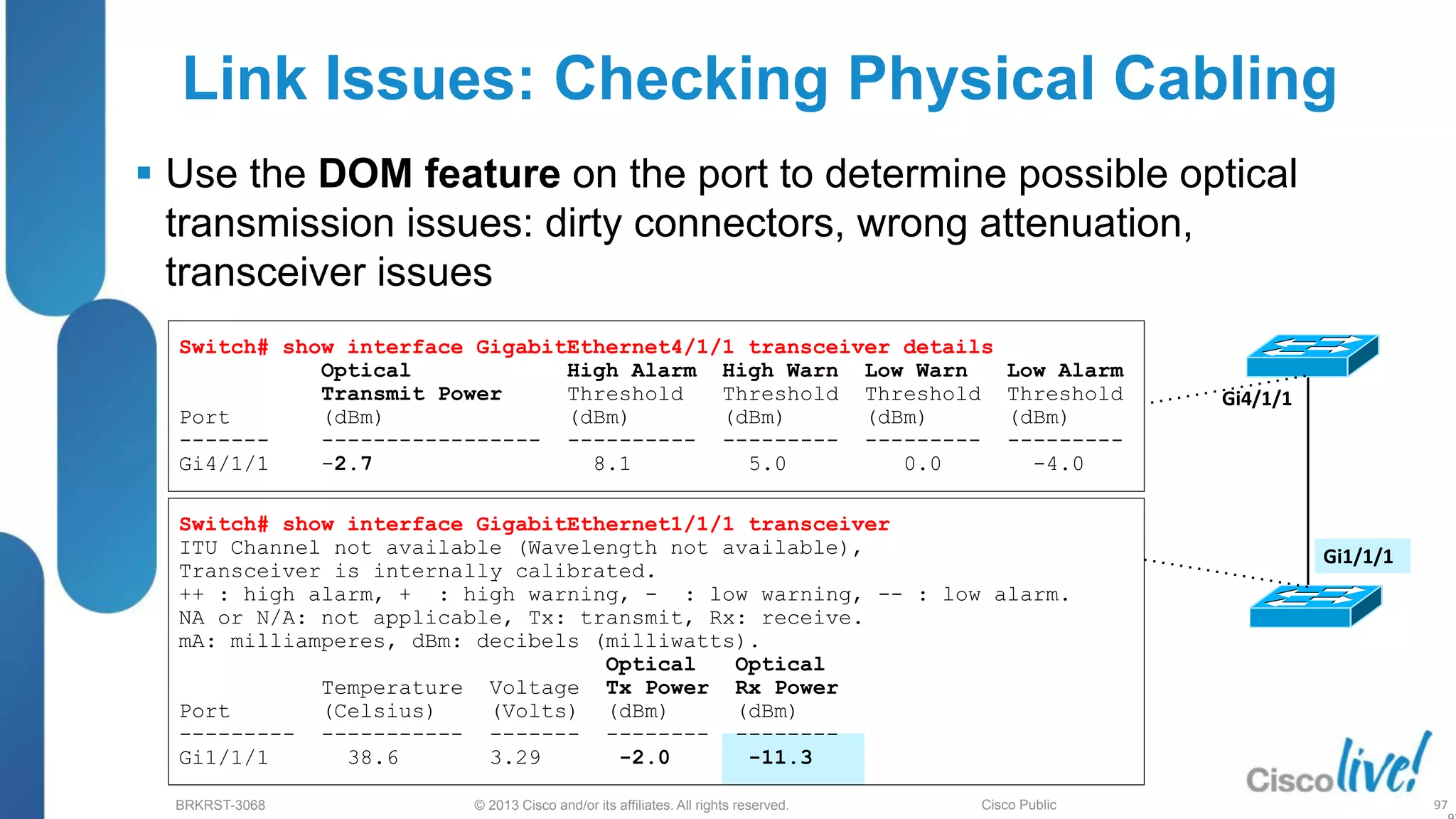
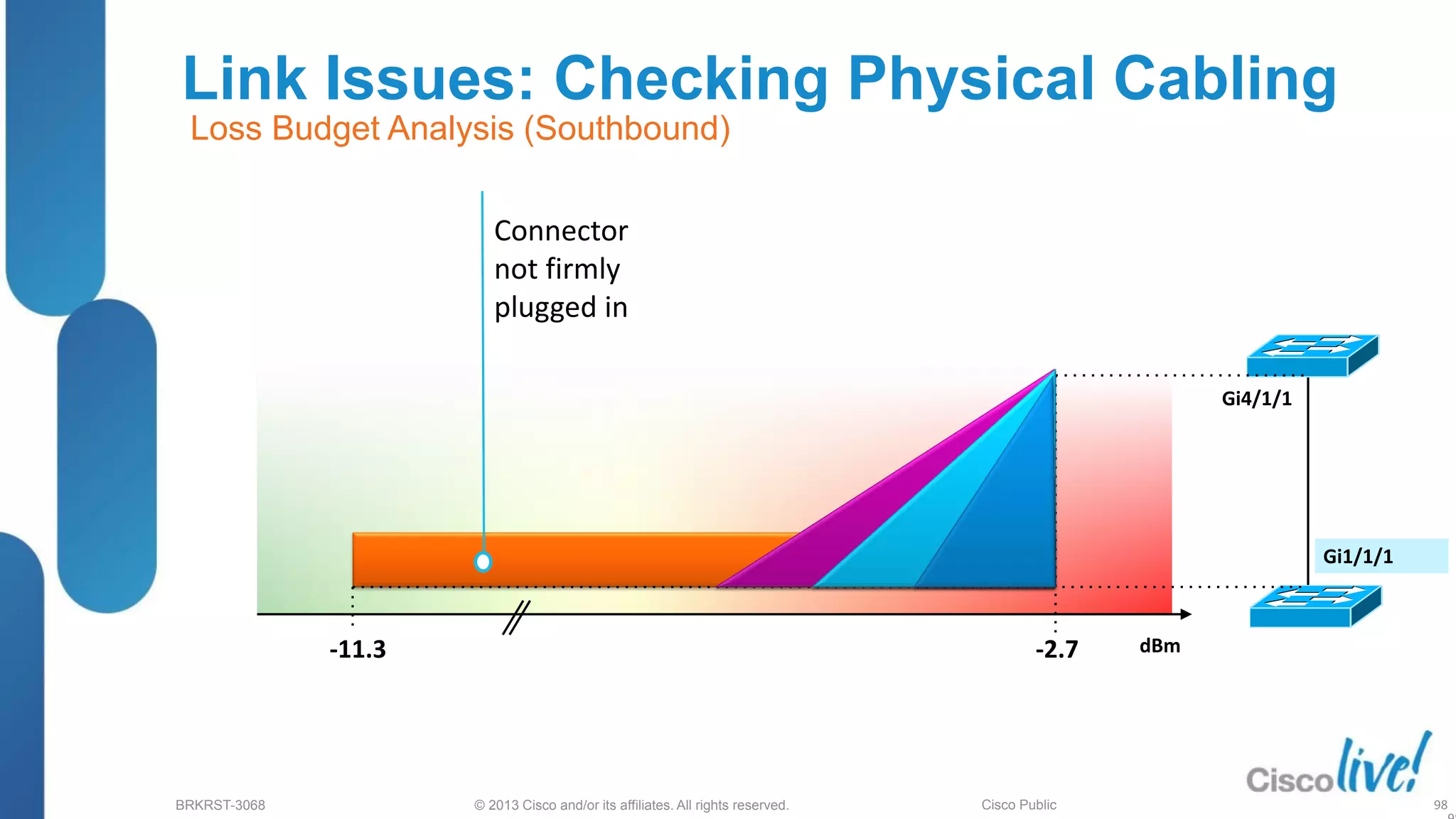
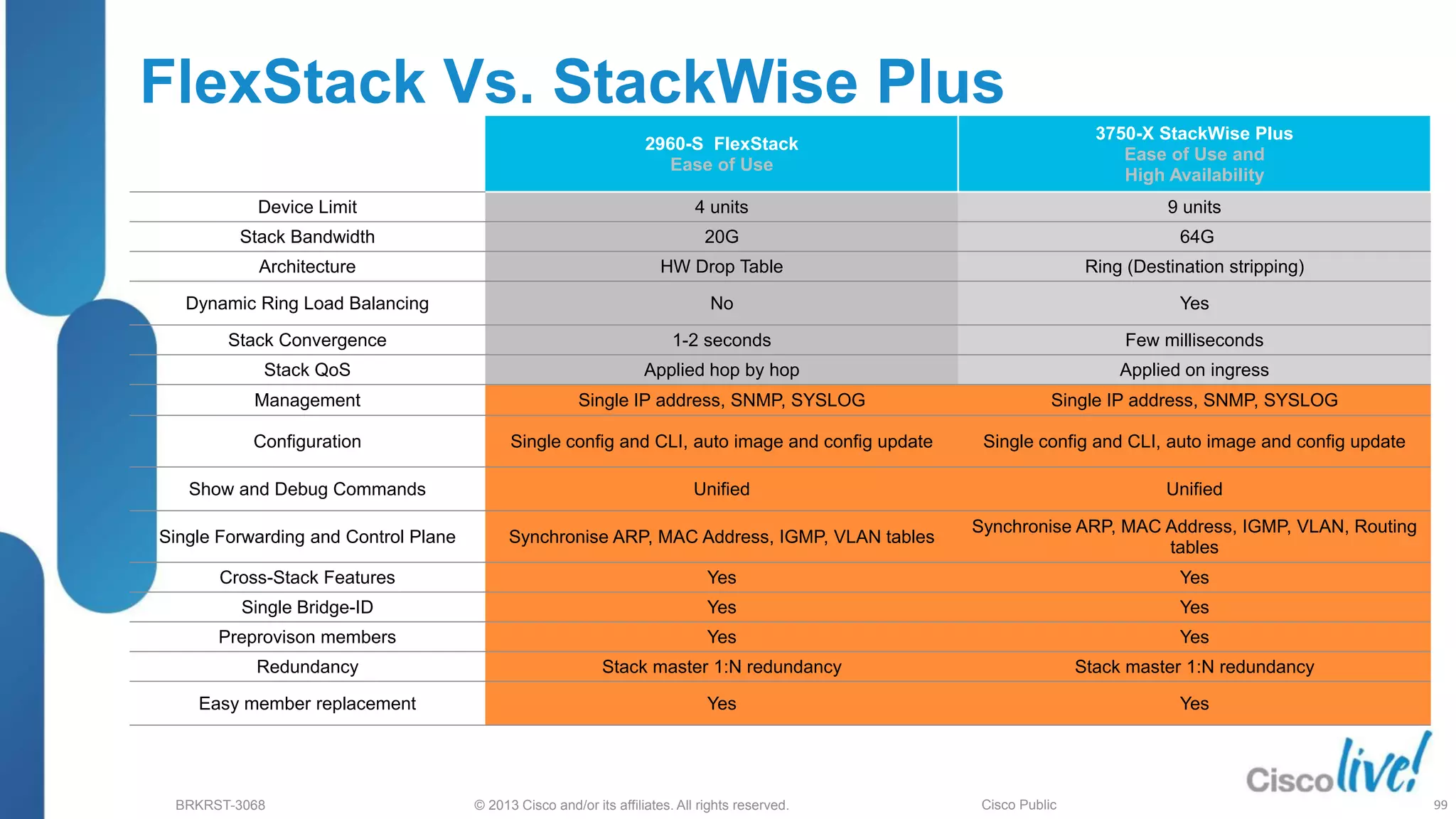
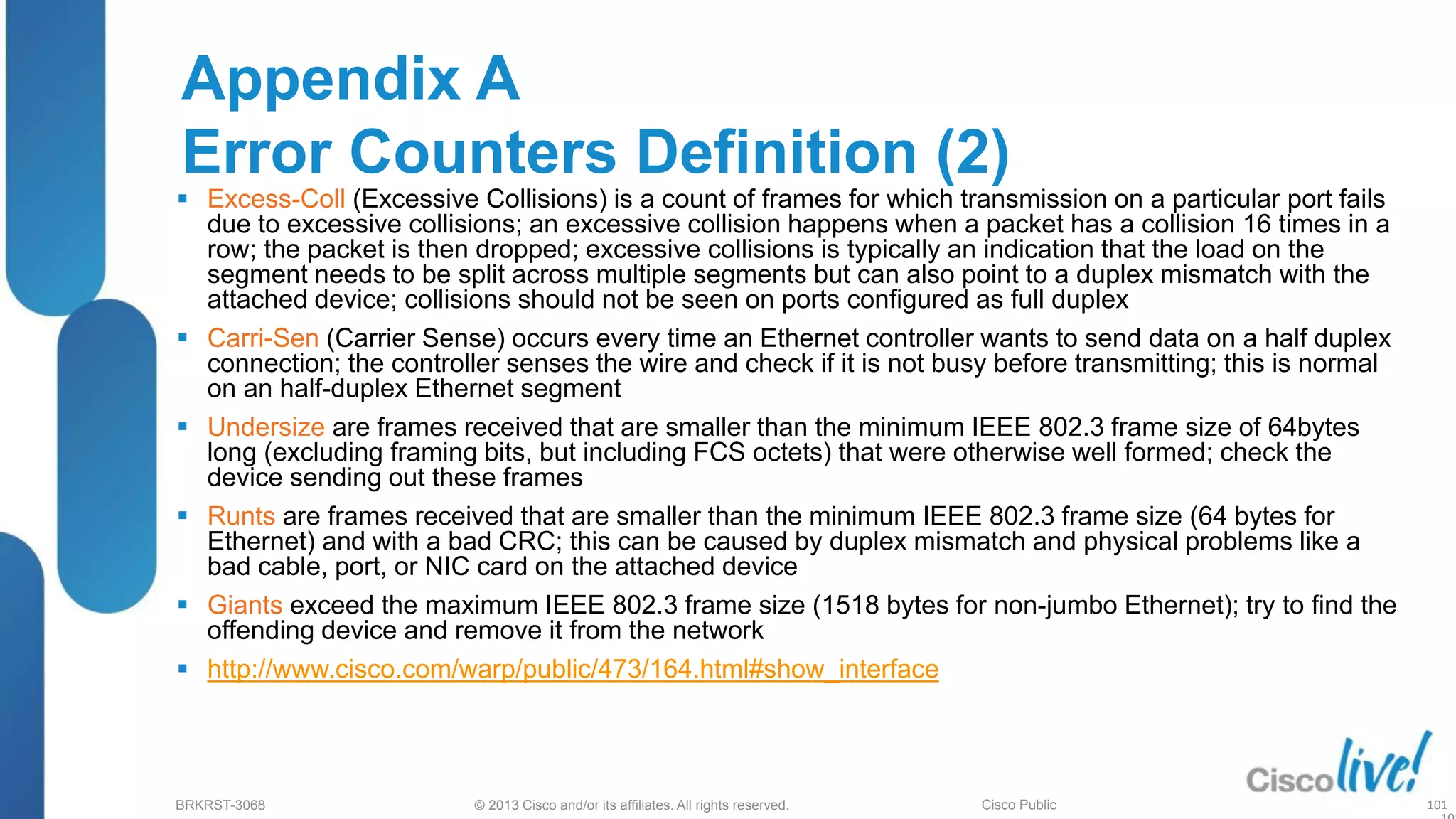
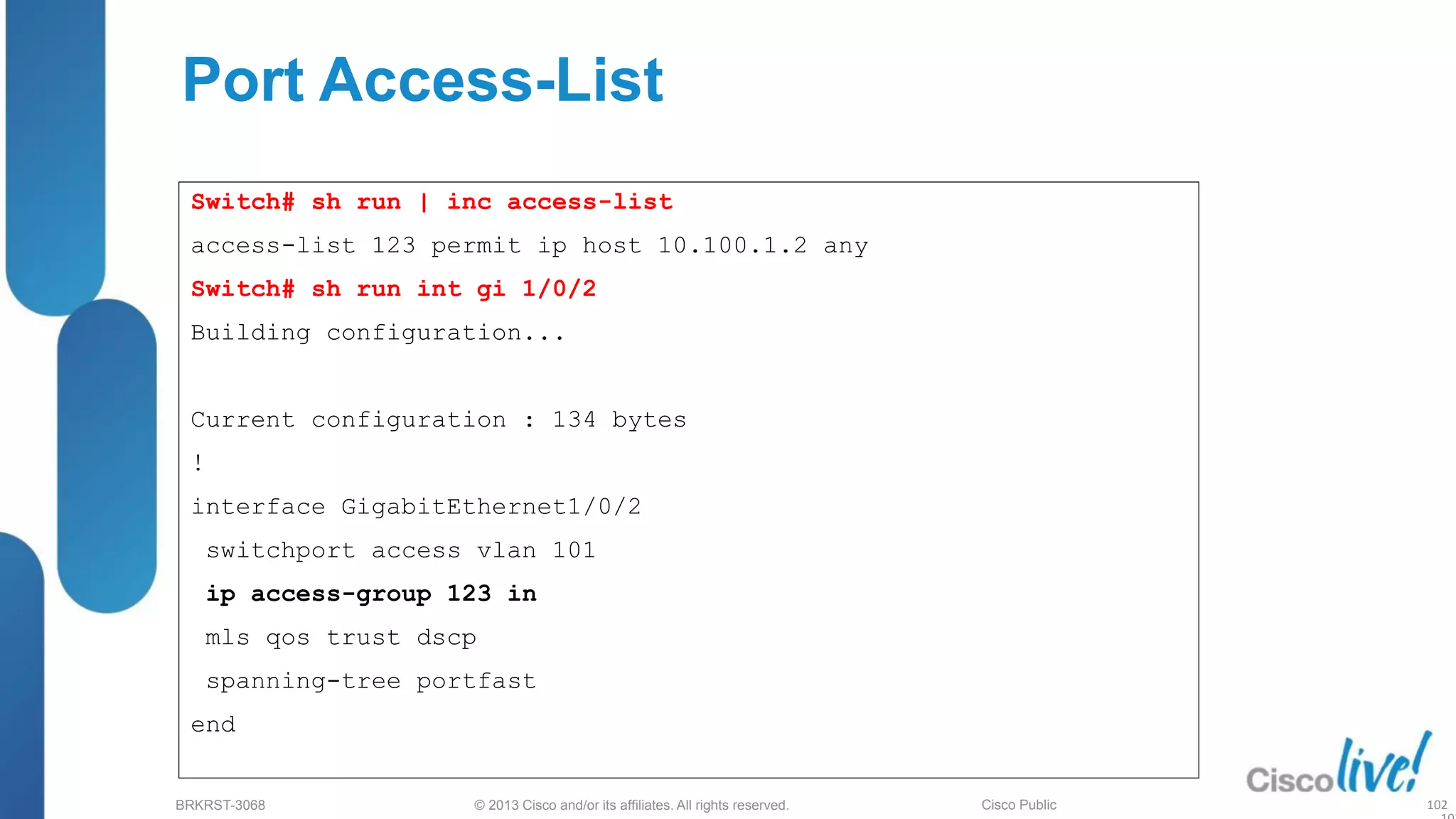
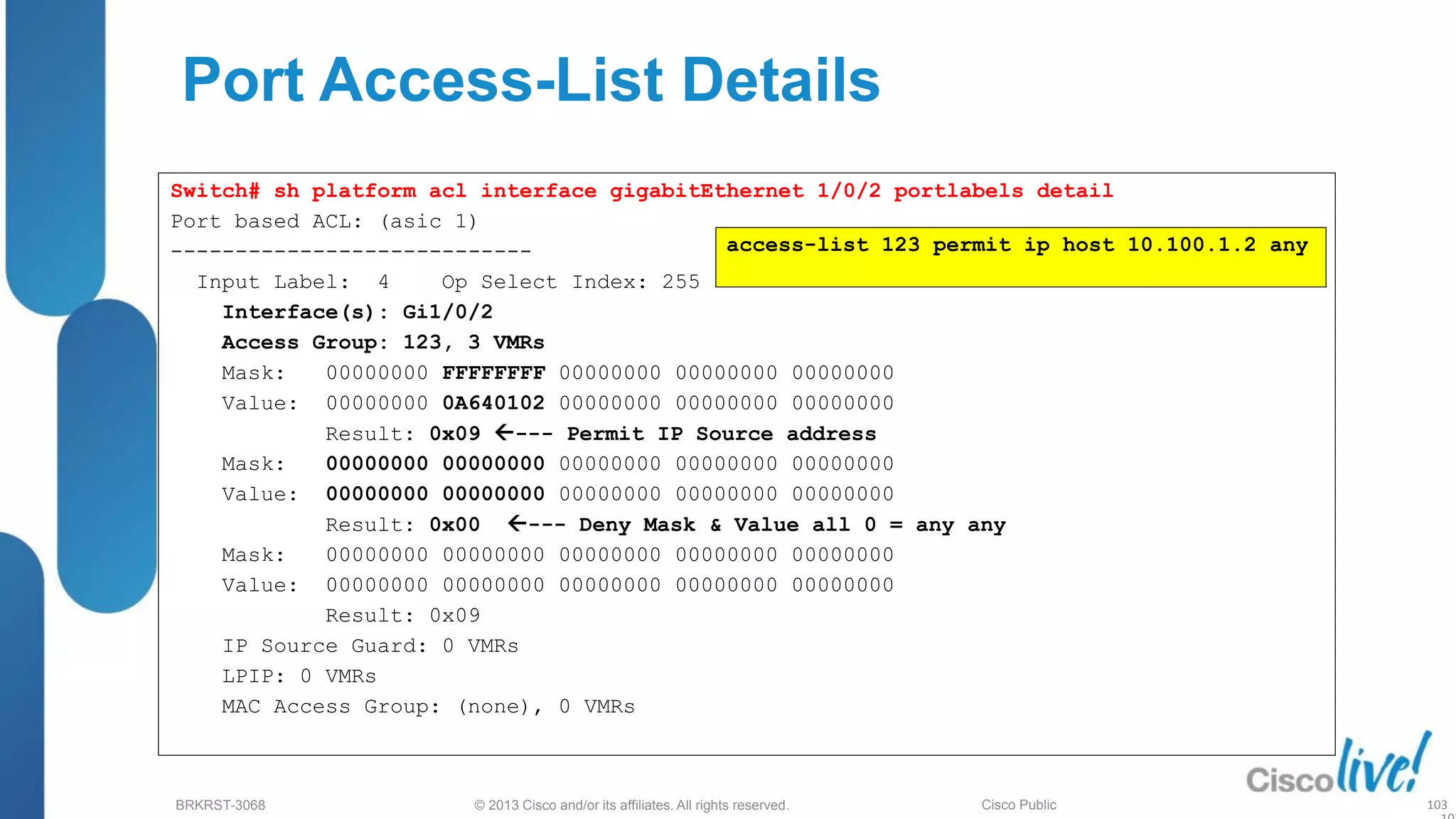
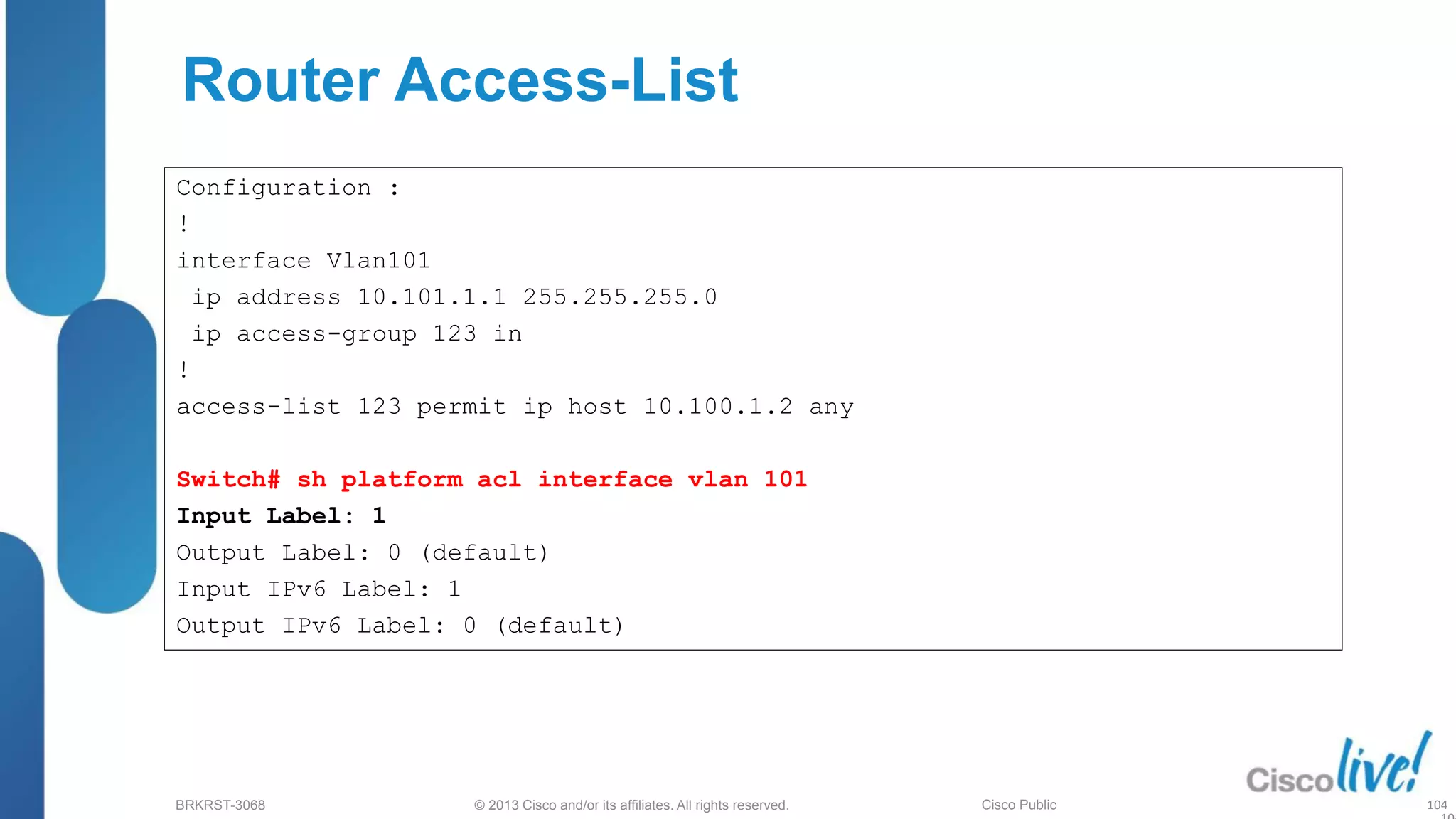
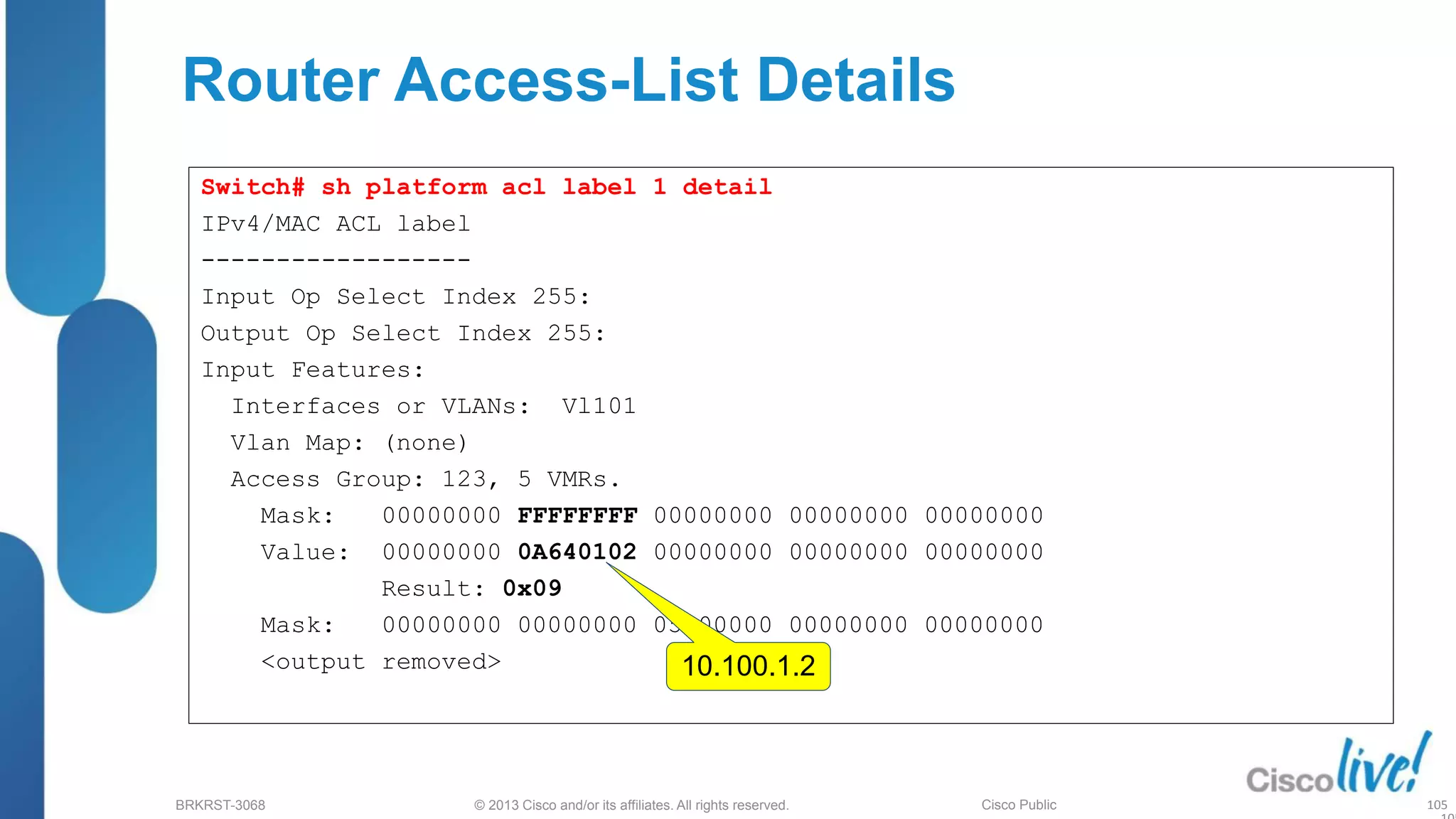
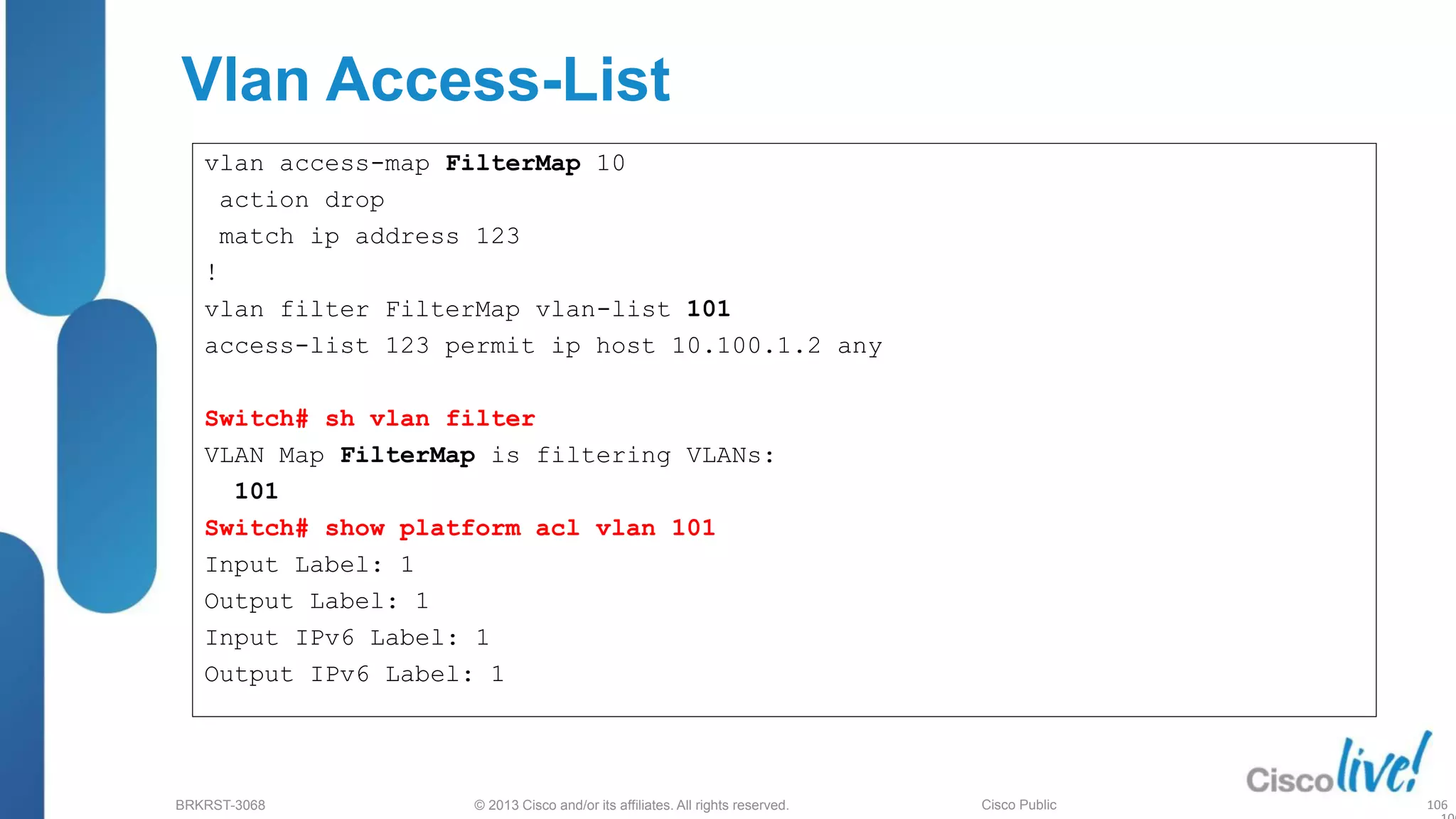
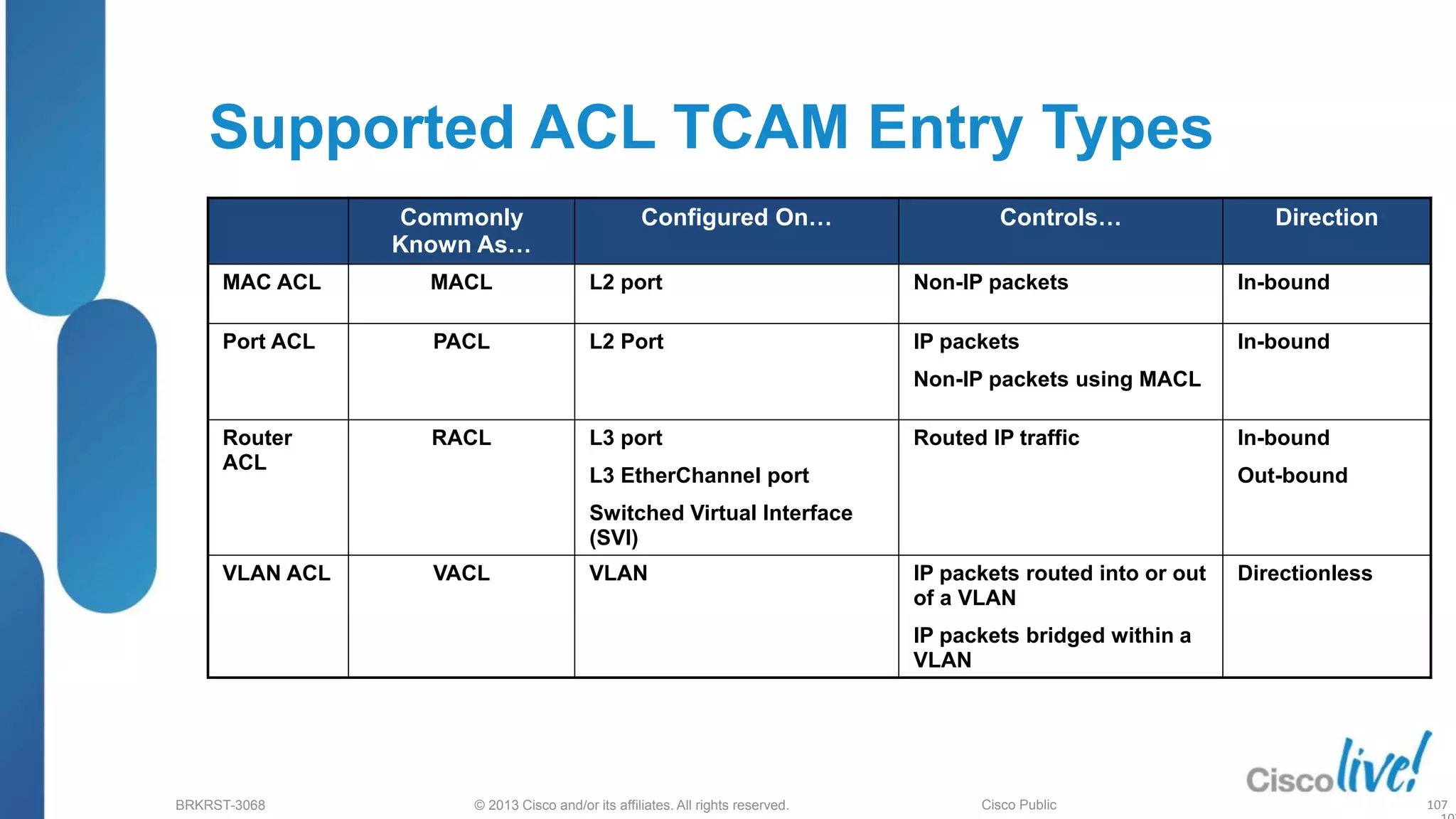
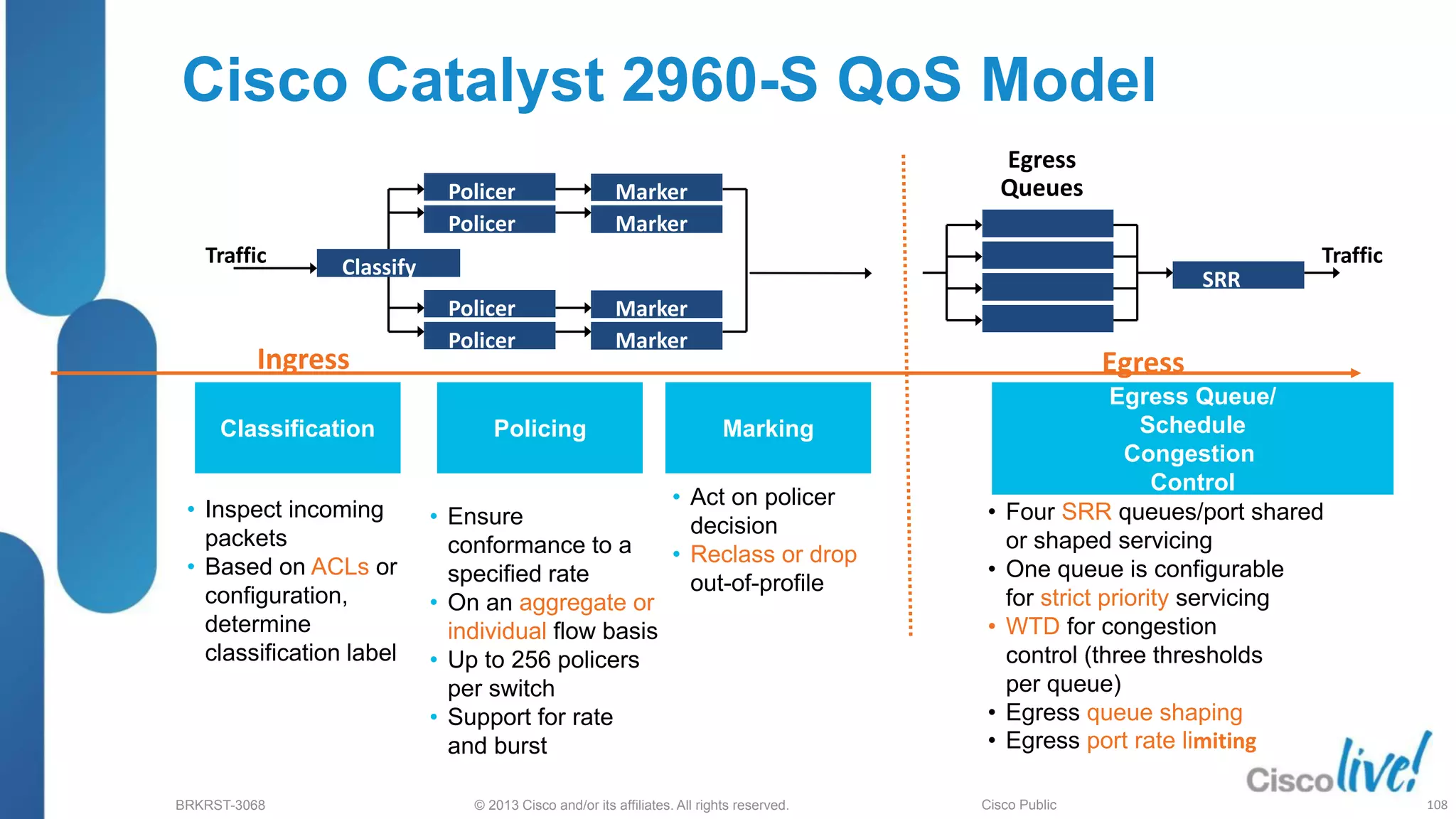
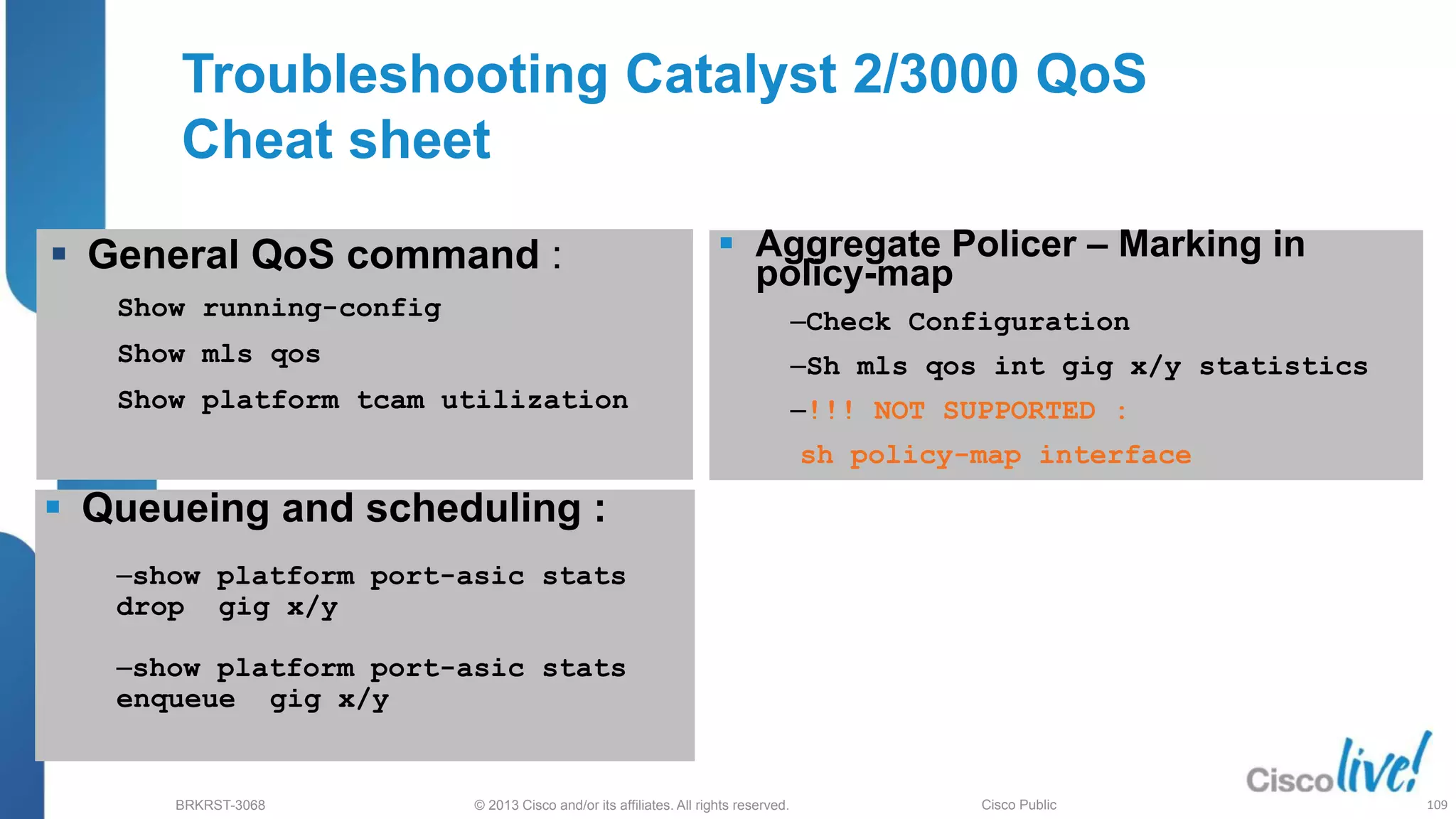
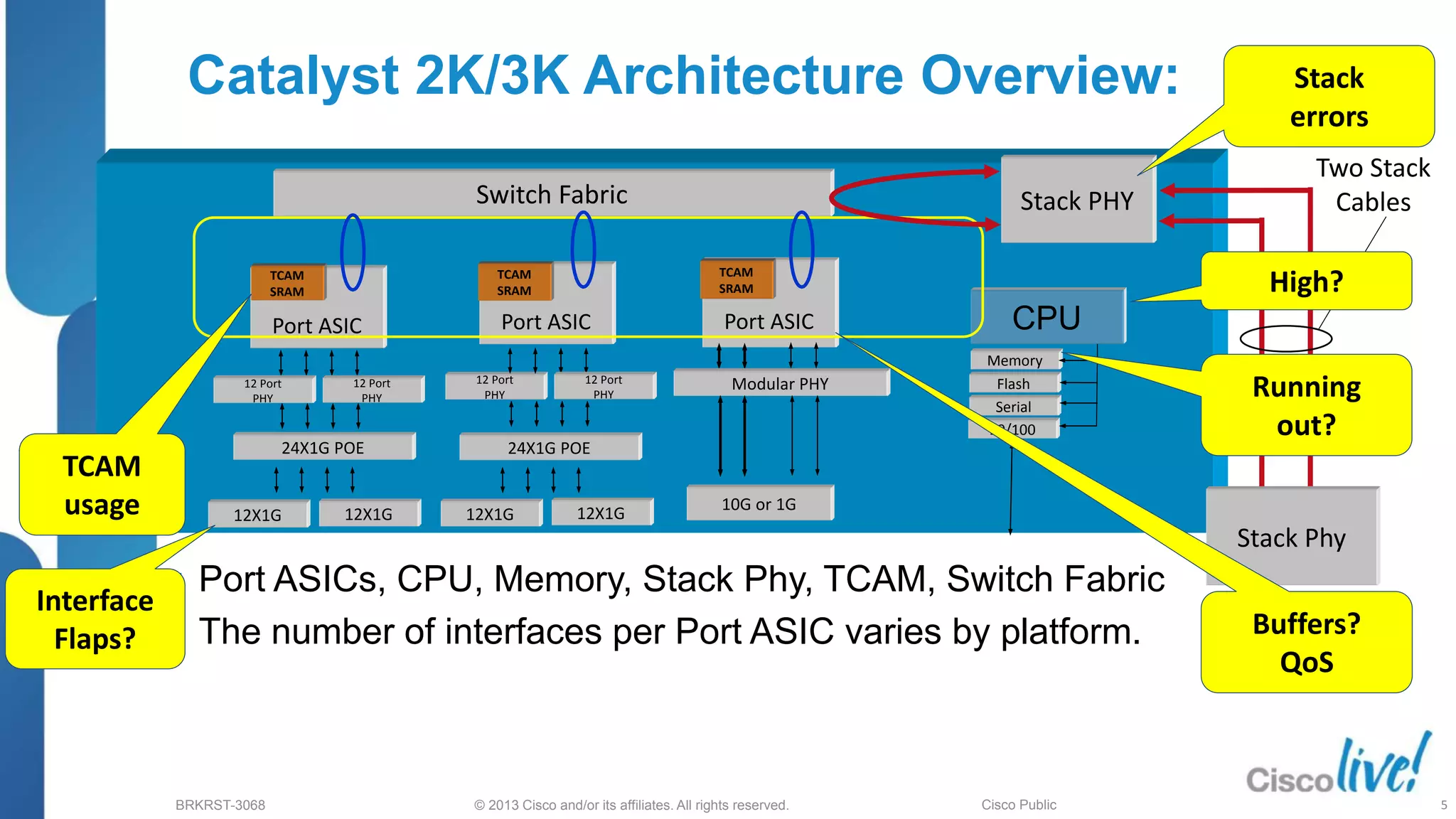
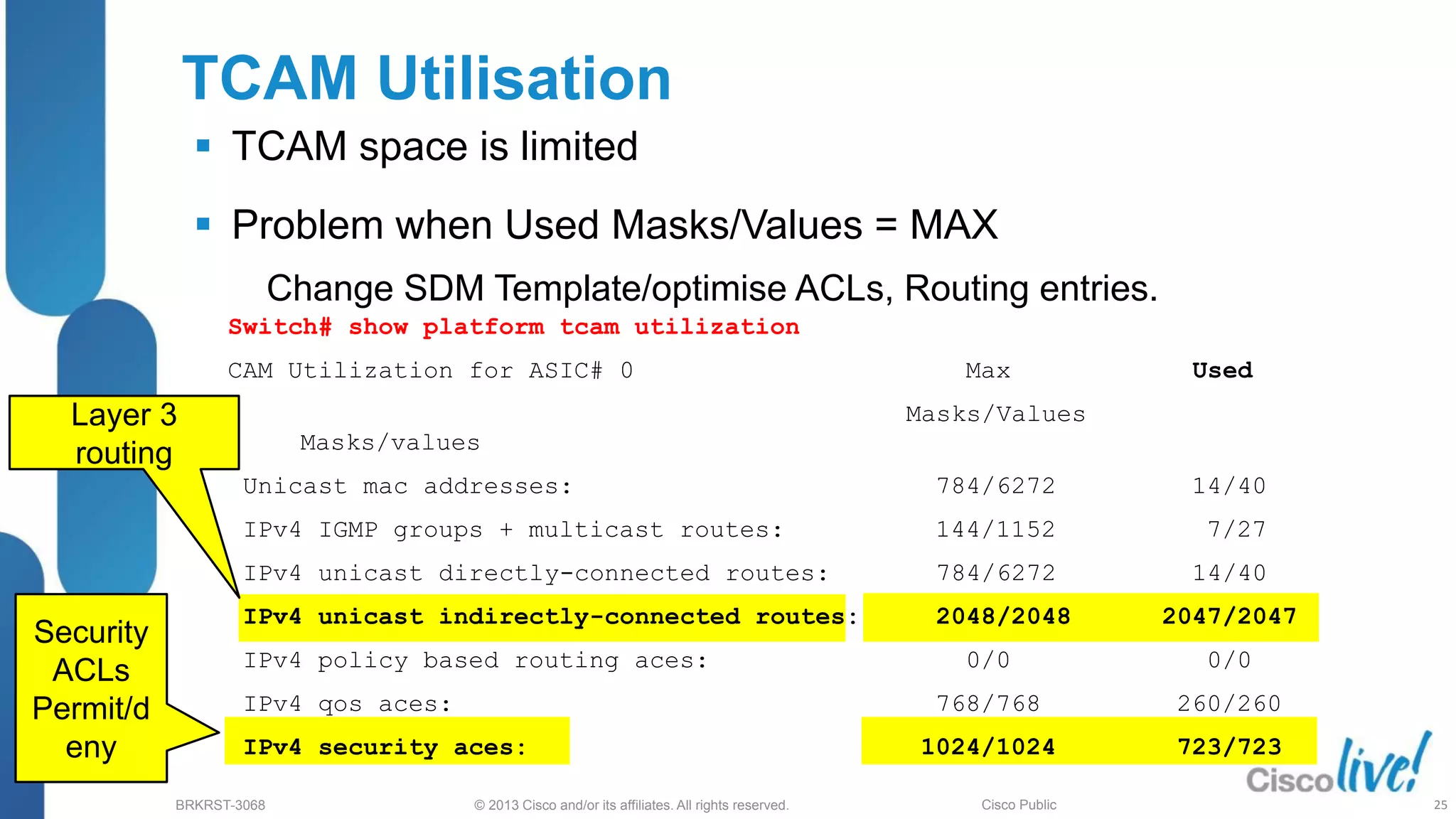
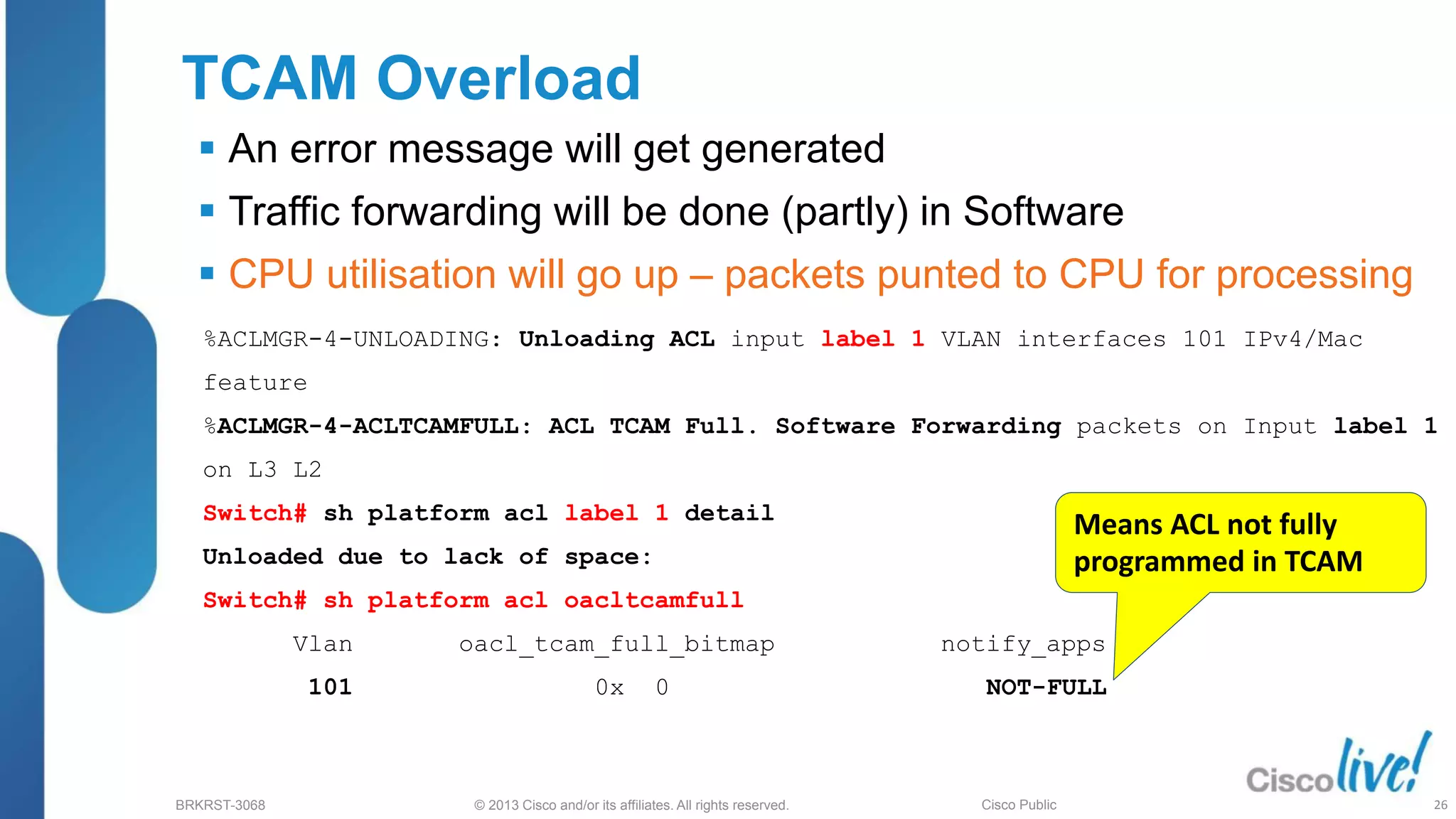
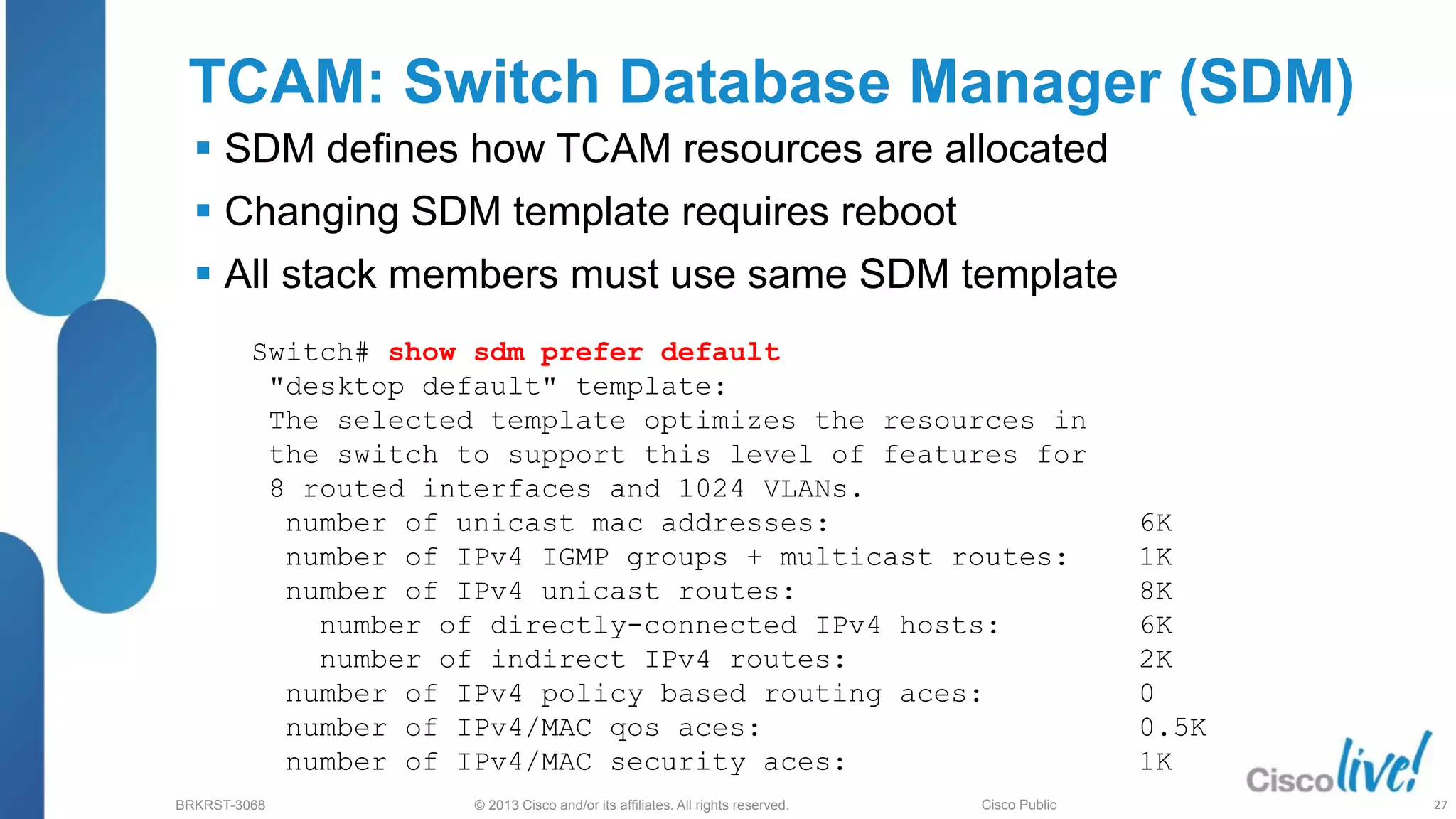
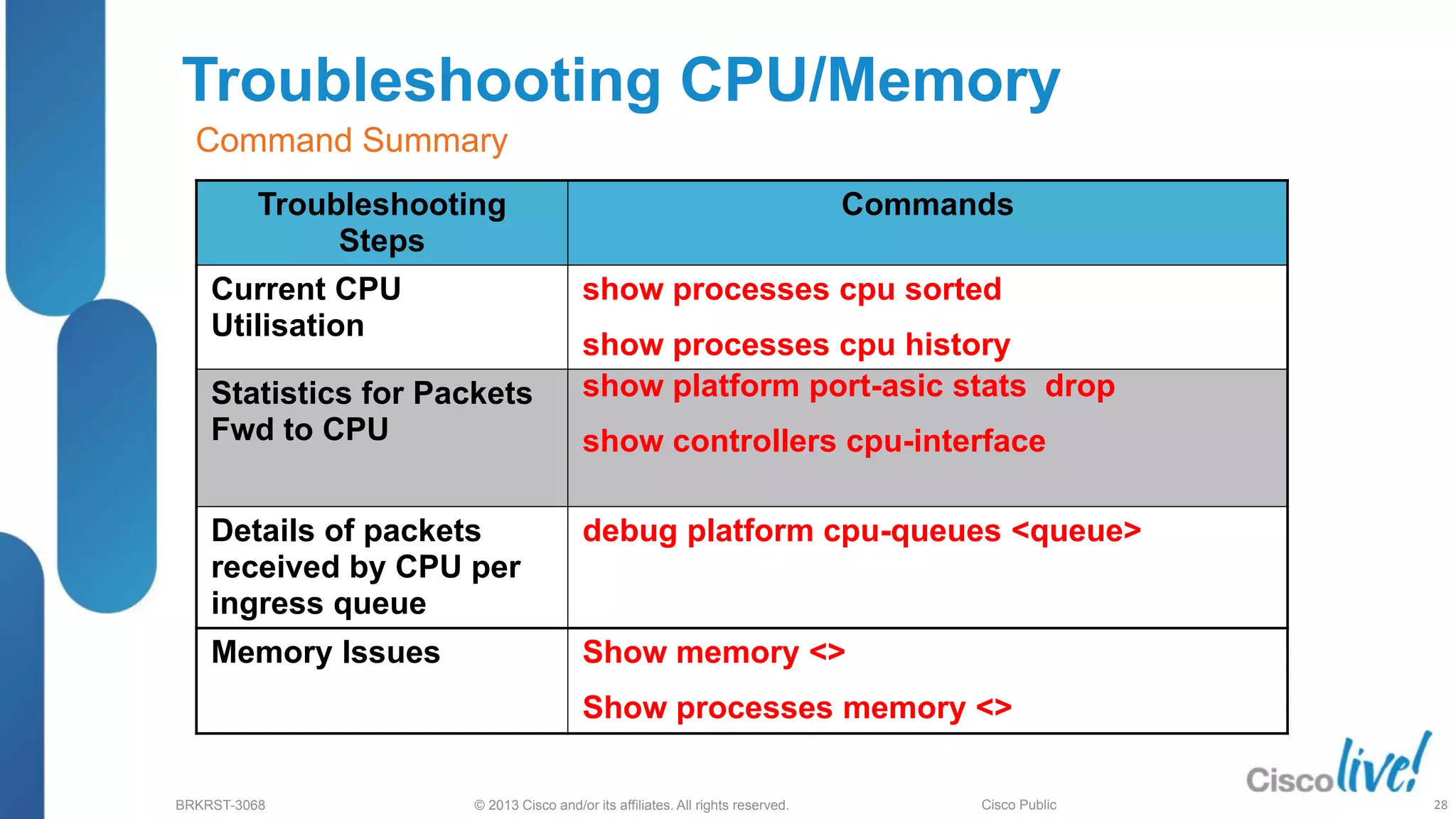
This document provides an overview of troubleshooting Catalyst 2K and 3K switches. It discusses monitoring system resources like CPU usage, port ASICs, memory and TCAM. Common issues covered include link problems, hardware failures, and high CPU. A variety of show commands are provided to monitor resources, analyze errors and diagnose potential causes. The goal is to identify and solve access layer incidents with confidence.



![© 2013 Cisco and/or its affiliates. All rights reserved.
BRKRST-3068 Cisco Public
CPU: Best Practices
Storm Control can help to protect CPU. Configuring Traffic Storm Control to avoid packets
flood the LAN, creating excessive traffic and degrading network performance.
(config-if)#storm-control broadcast level level[.level]
(config-if)#storm-control action ?
shutdown Shutdown this interface if a storm occurs
trap Send SNMP trap if a storm occurs
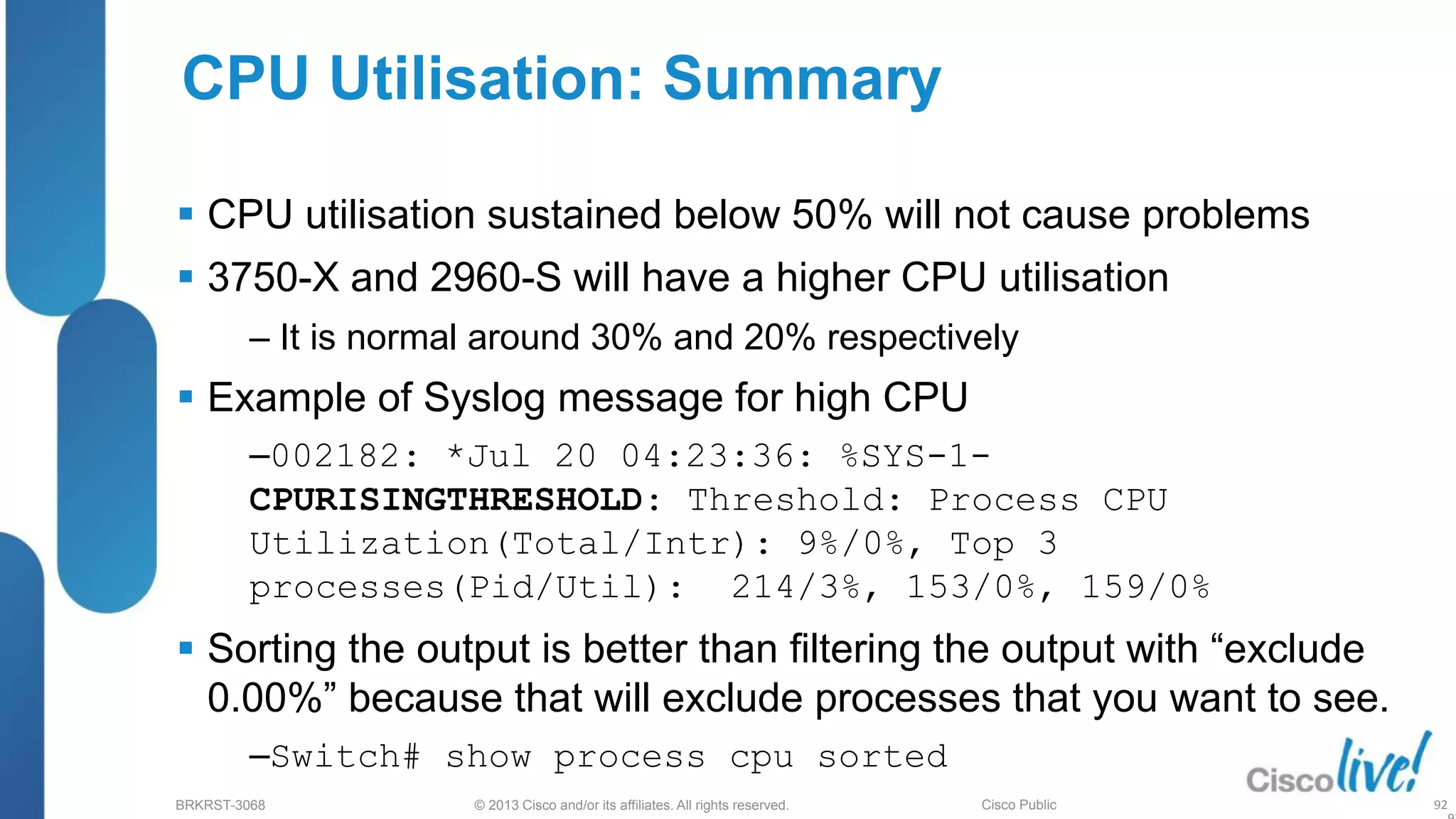
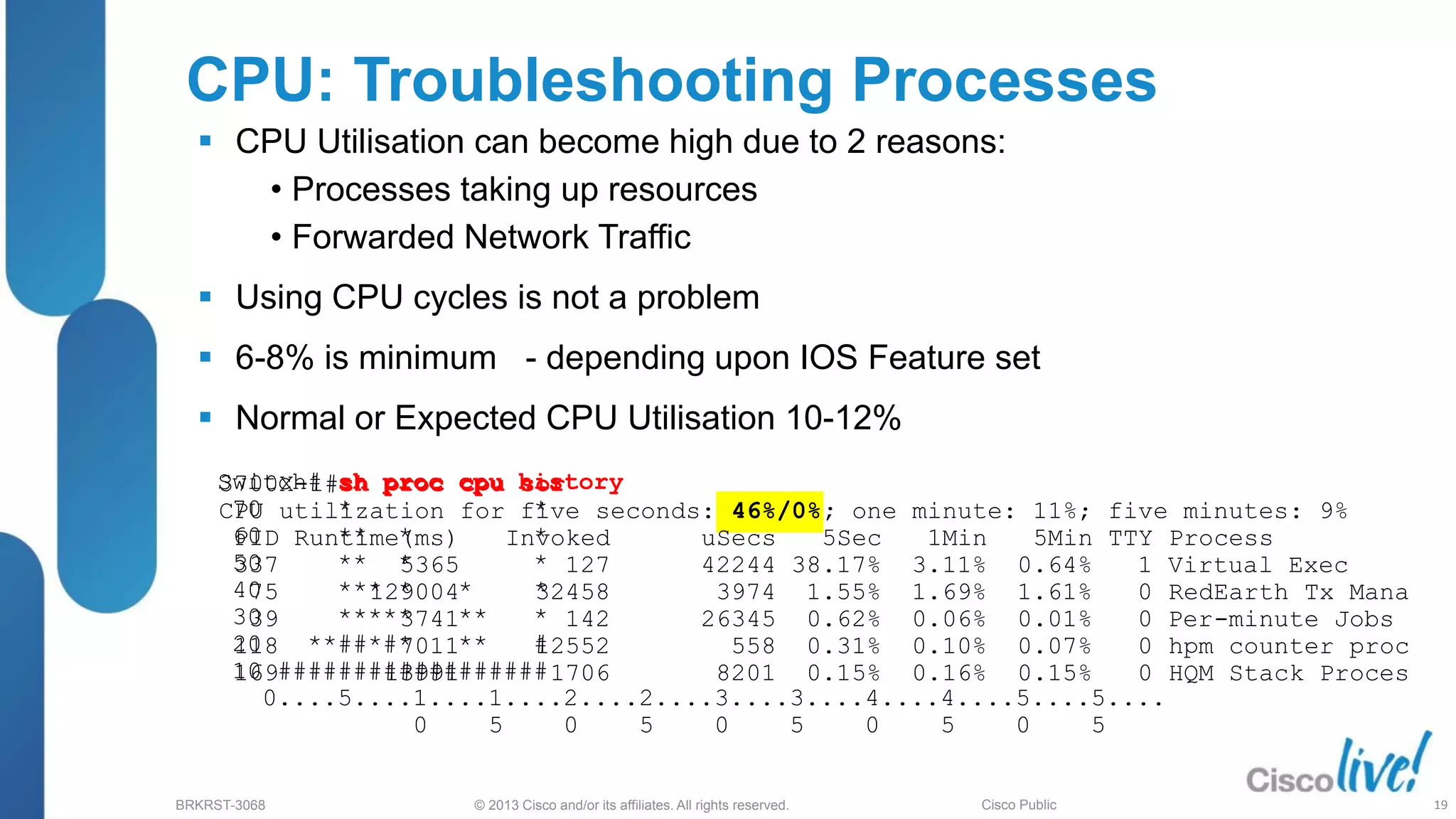
Example of Syslog message for high CPU
*Mar 1 01:03:15.601: %SYS-1-CPURISINGTHRESHOLD: Threshold: Process CPU Utilisation
(Total/Intr): 18%/0%, Top 3 processes(Pid/Util): 4/10%, 75/1%, 164/0%
Configuring the CPU threshold can help you identifying when the CPU
goes over certain limits
Switch(config)# process cpu threshold type {total | process | interrupt}
rising percentage interval seconds [falling fall-percentage interval seconds]
22](https://image.slidesharecdn.com/brkrst-3068troubleshootingcatalyst2kand3k-230406042137-3fedf21f/75/BRKRST-3068-Troubleshooting-Catalyst-2K-and-3K-pdf-20-2048.jpg)
![© 2013 Cisco and/or its affiliates. All rights reserved.
BRKRST-3068 Cisco Public
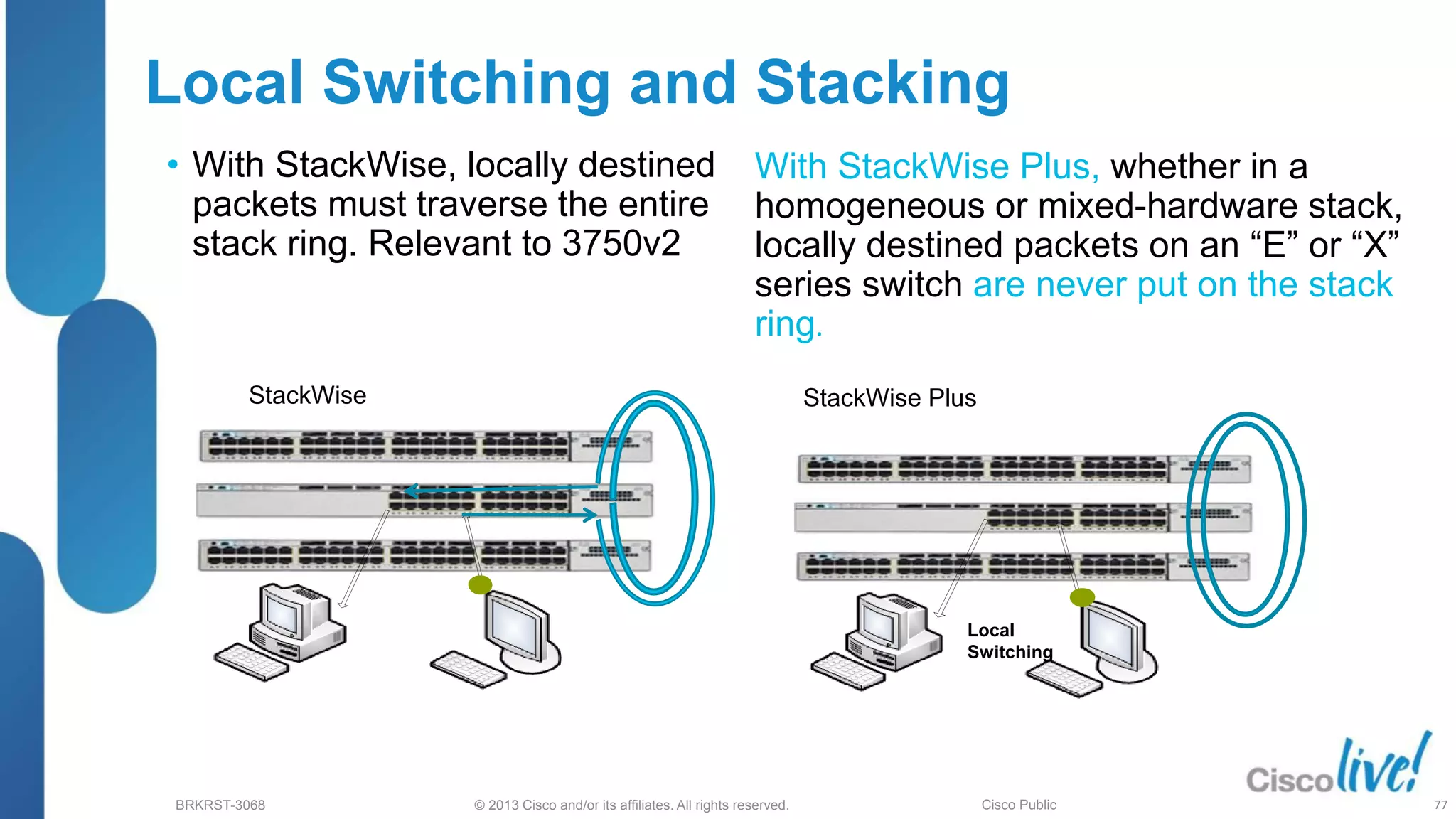
Troubleshooting Stacking
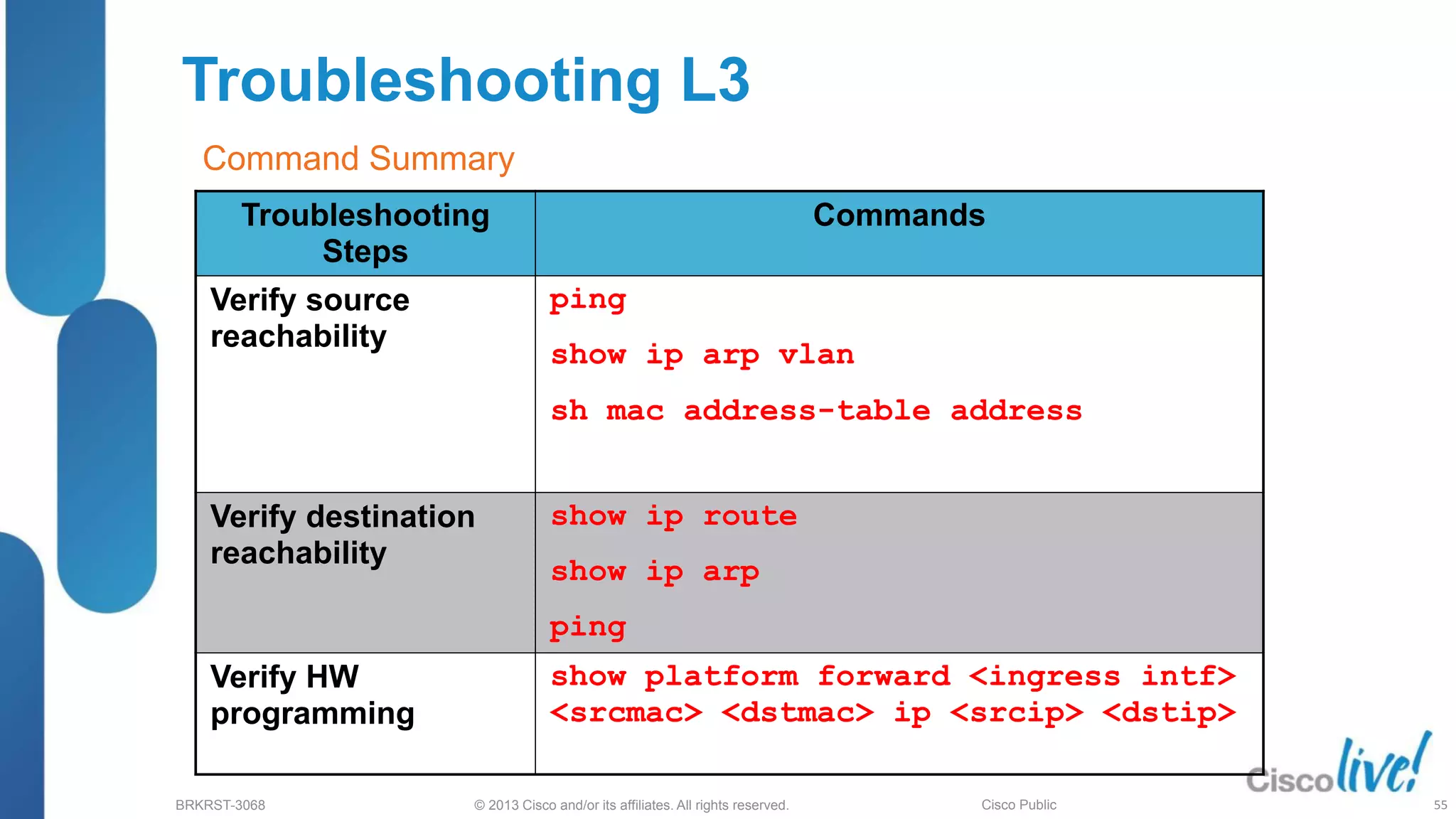
Troubleshooting
Steps
Commands
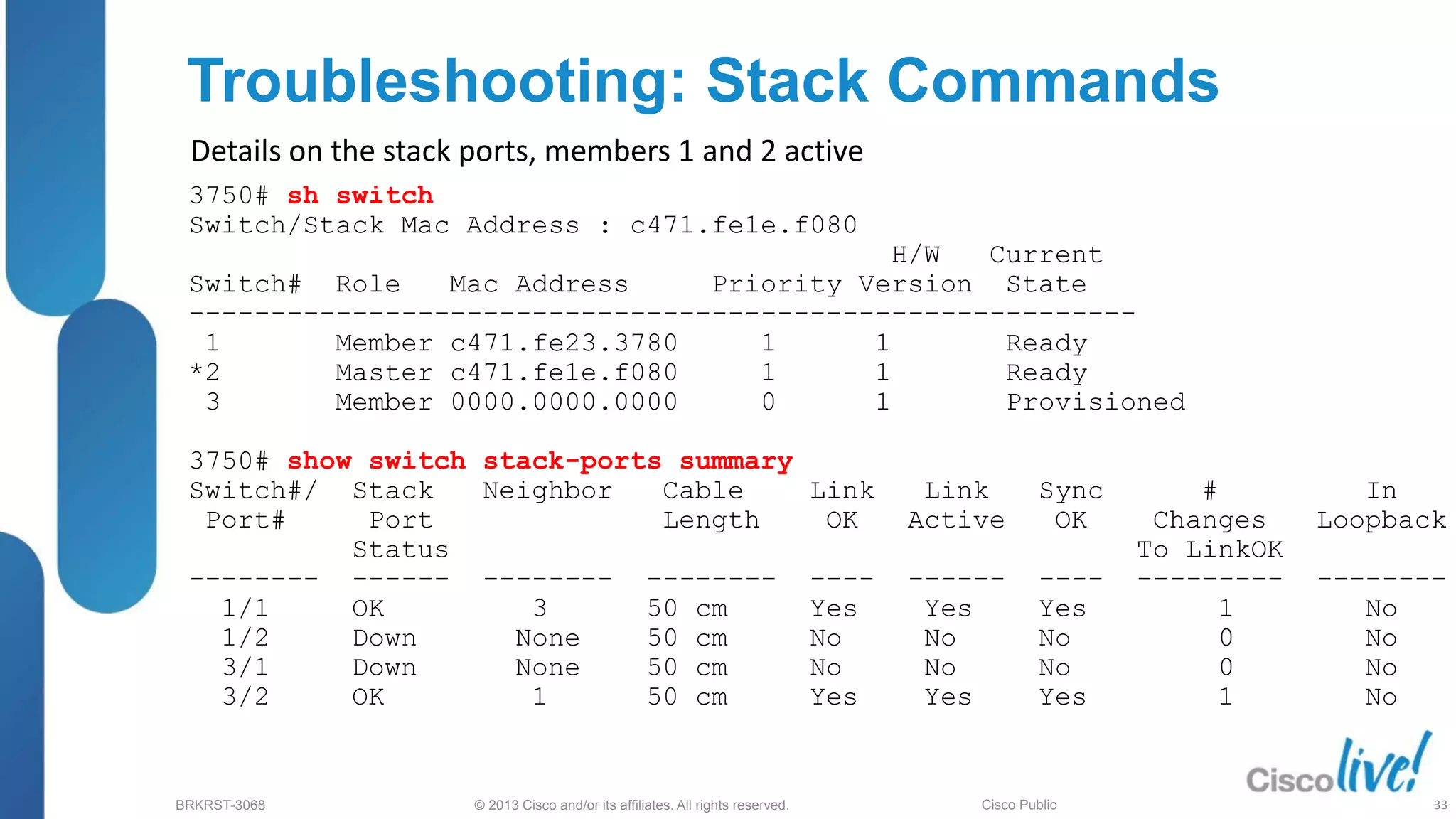
Stack status show switch [detail]
show platform stack manager
show switch stack-ring <>
show controllers utilization
show switch stack-ports summary
(New)
Test Stack Ports switch <> stack port <>
enable/disable
From IOS 12.2(50)
Command Summary
34](https://image.slidesharecdn.com/brkrst-3068troubleshootingcatalyst2kand3k-230406042137-3fedf21f/75/BRKRST-3068-Troubleshooting-Catalyst-2K-and-3K-pdf-32-2048.jpg)
![© 2013 Cisco and/or its affiliates. All rights reserved.
BRKRST-3068 Cisco Public
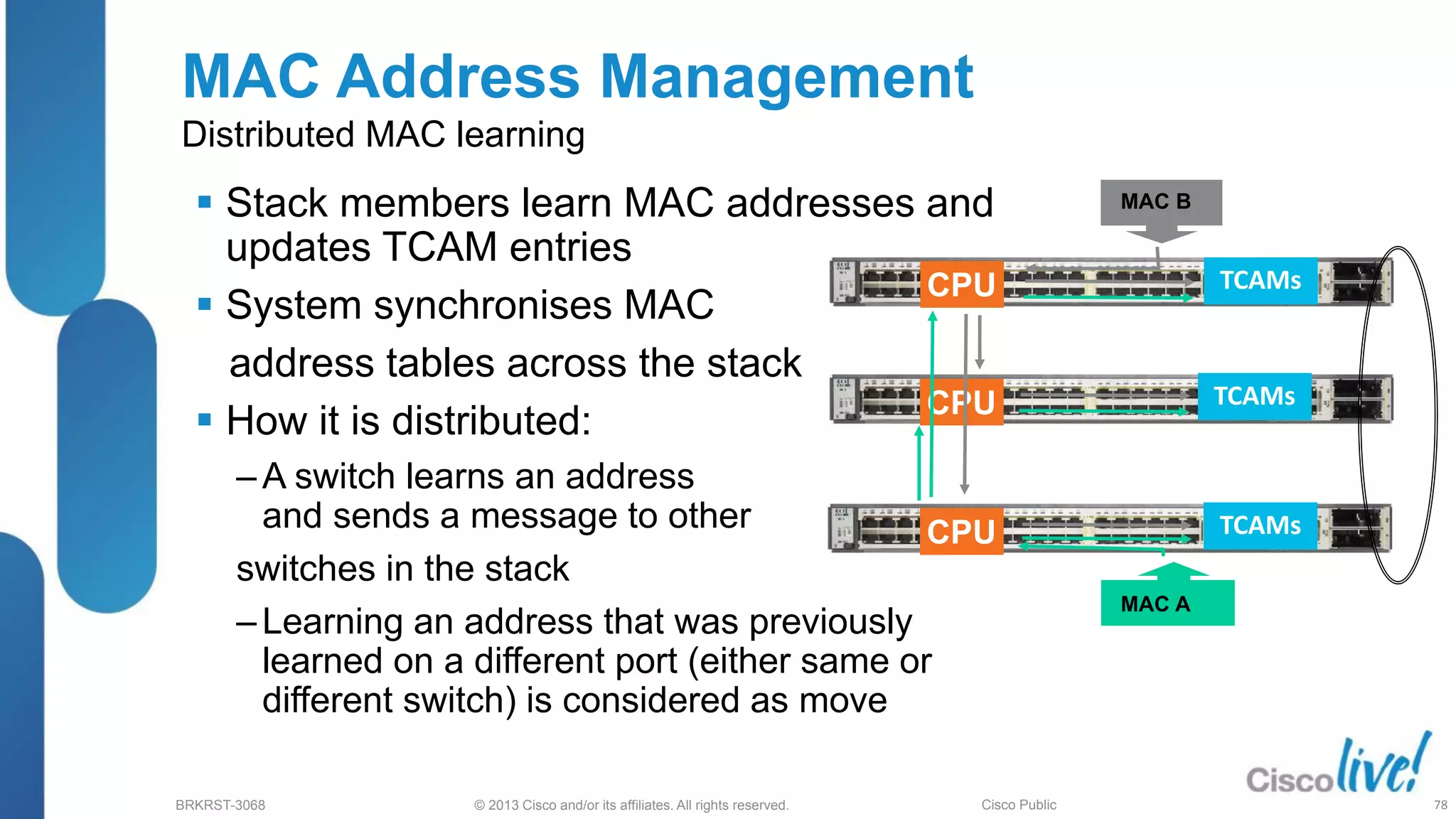
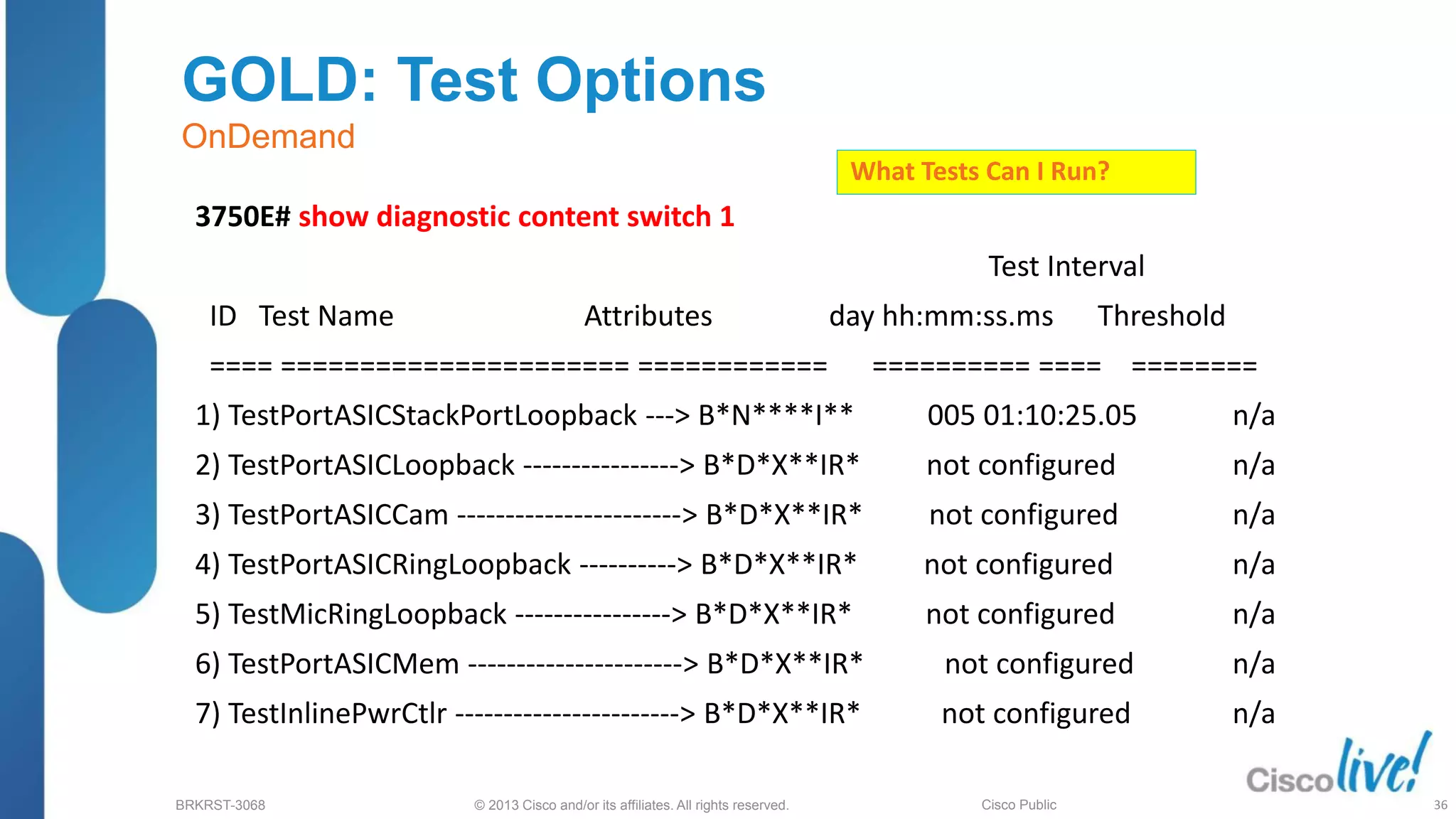
GOLD (Generic Online Diagnostics)
(config)# [no] diagnostic monitor interval { switch <1-9> }
test { test-id | test-id-range | all } hh:mm:ss { ms <0-999> } {
days <0-20> }
diagnostic start {switch <1:9>} test {test-num |
test range | all | basic | non-disruptive }
Switch(config)#[no] diagnostic schedule {
switch <1-9> } test { test-id | test-id-range | all }
daily {hh:mm}
On-Demand
Health-Monitoring
Scheduled
To run Non-disruptive tests in
the background
Serves as HA trigger
All diagnostics tests can be run on
demand, for troubleshooting purposes.
It can also be used as a pre-deployment
tool.
All diagnostic tests can be Scheduled,
for verification and troubleshooting
purposes
Runtime diagnostics
Run During System Bootup,
Makes sure faulty hardware is taken out of
service (POST = Power On Self Test)
Boot-Up diagnostics
show diagnostic post
35](https://image.slidesharecdn.com/brkrst-3068troubleshootingcatalyst2kand3k-230406042137-3fedf21f/75/BRKRST-3068-Troubleshooting-Catalyst-2K-and-3K-pdf-33-2048.jpg)
![© 2013 Cisco and/or its affiliates. All rights reserved.
BRKRST-3068 Cisco Public
GOLD: CLI
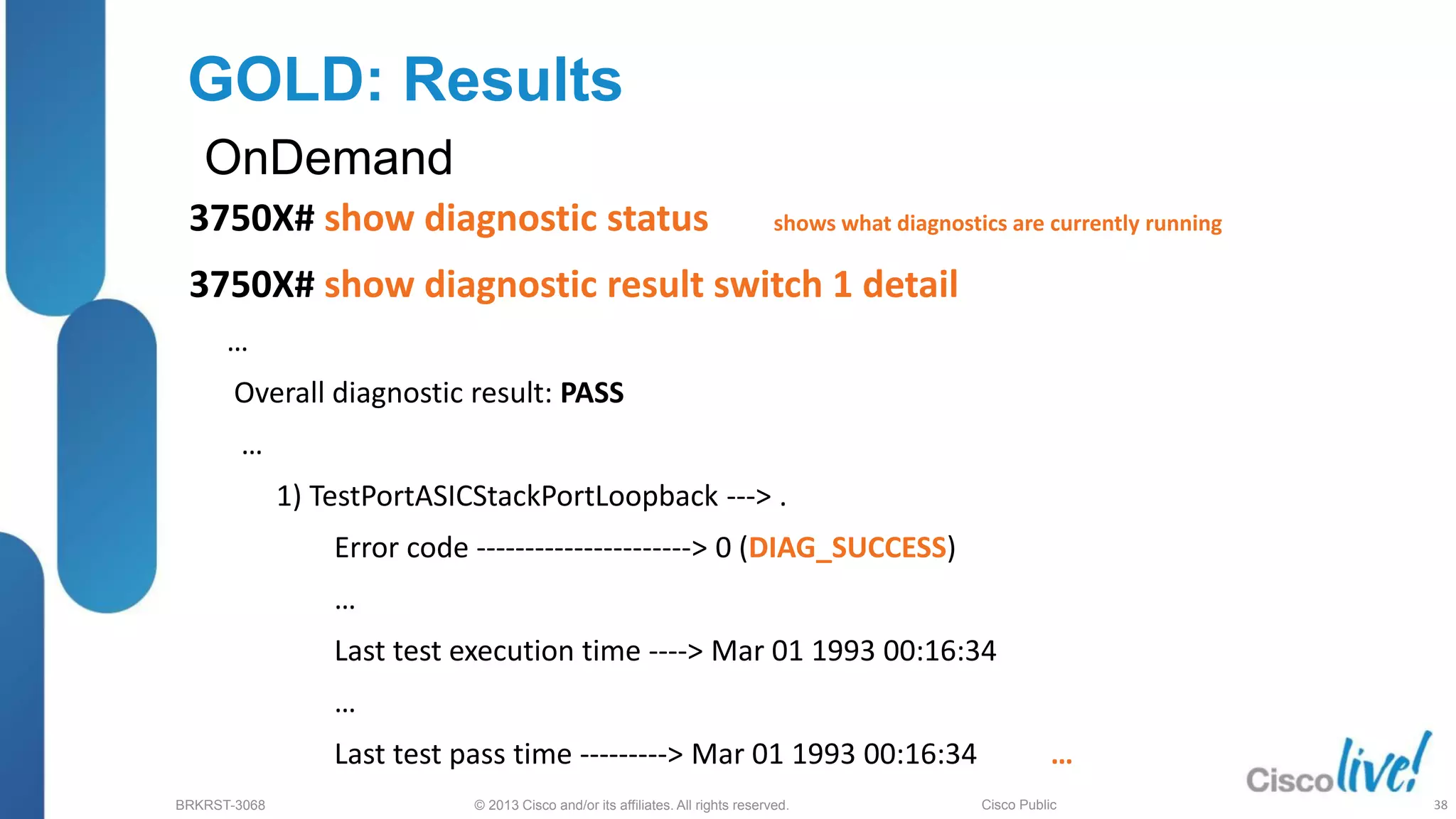
OnDemand
diagnostic start {switch <1:9>} test {test-num | test range | all | basic | non-disruptive }
3700X-1#diagnostic start switch 1 test all
Diagnostic[Switch 1]: Running test(s) 2-6 will cause the switch under test to reload after completion of the test
list.
Diagnostic[Switch 1]: Running test(s) 2-6 may disrupt normal system operation
Do you want to continue? [no]: yes
Disruptive Test:
Users will be prompted if the test causes a lose of stack connectivity:
Switch 3: Running test(s) 2 will cause the switch under test to reload after completion of the test
list.
Switch 3: Running test(s) 2 may disrupt normal system operation Do you want to continue? [no]:
Disruptive Test:
Users will be prompted if the test causes stack partitioning:
Switch 6: Running test(s) 2 will cause the switch under test to reload after completion of the test list.
Switch 6: Running test(s) 2 will partition stack
Switch 6: Running test(s) 2 may disrupt normal system operation Do you want to continue? [no]:
Note: Tests Run to Completion (No Stop Command)
37](https://image.slidesharecdn.com/brkrst-3068troubleshootingcatalyst2kand3k-230406042137-3fedf21f/75/BRKRST-3068-Troubleshooting-Catalyst-2K-and-3K-pdf-35-2048.jpg)