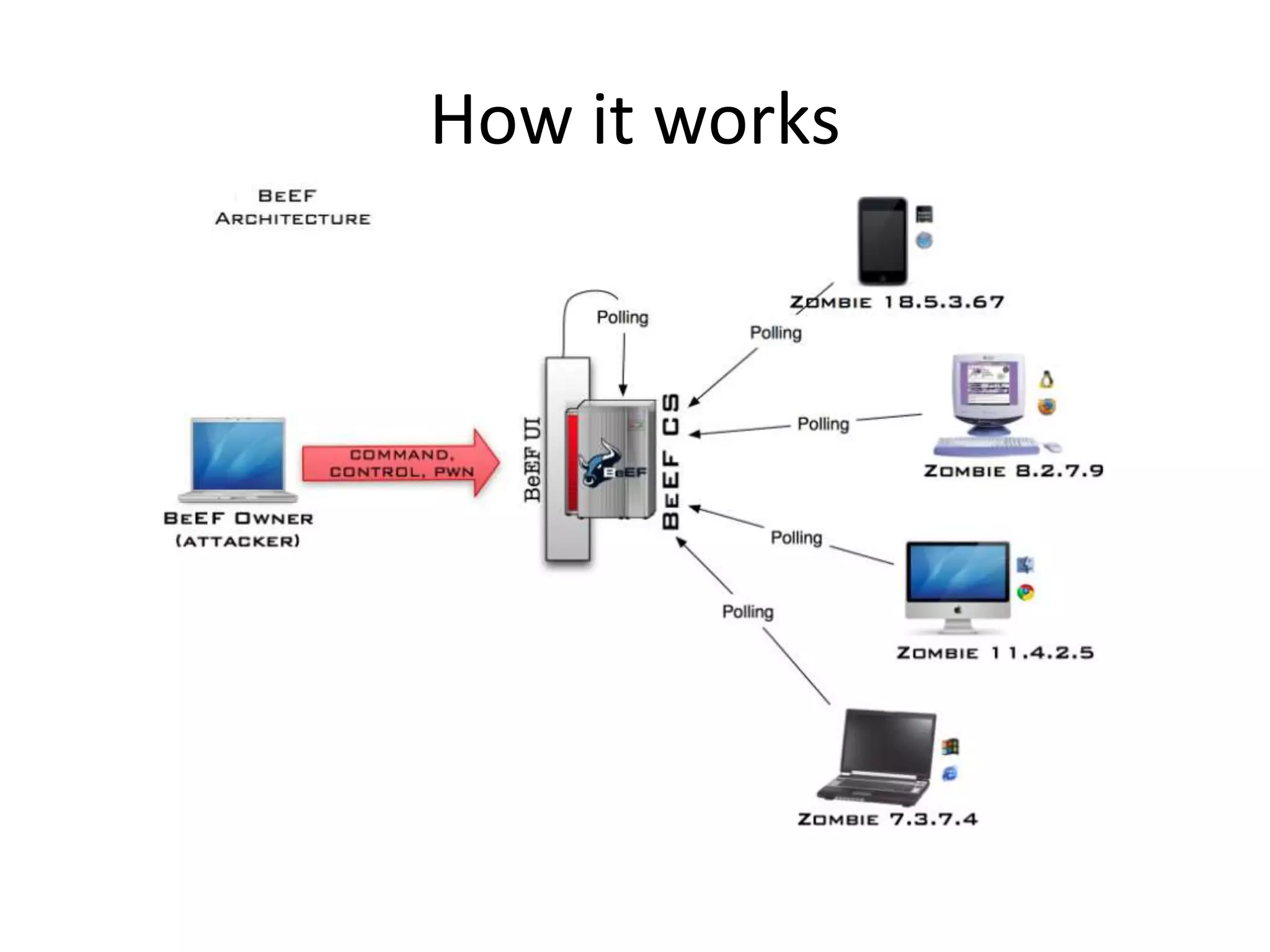
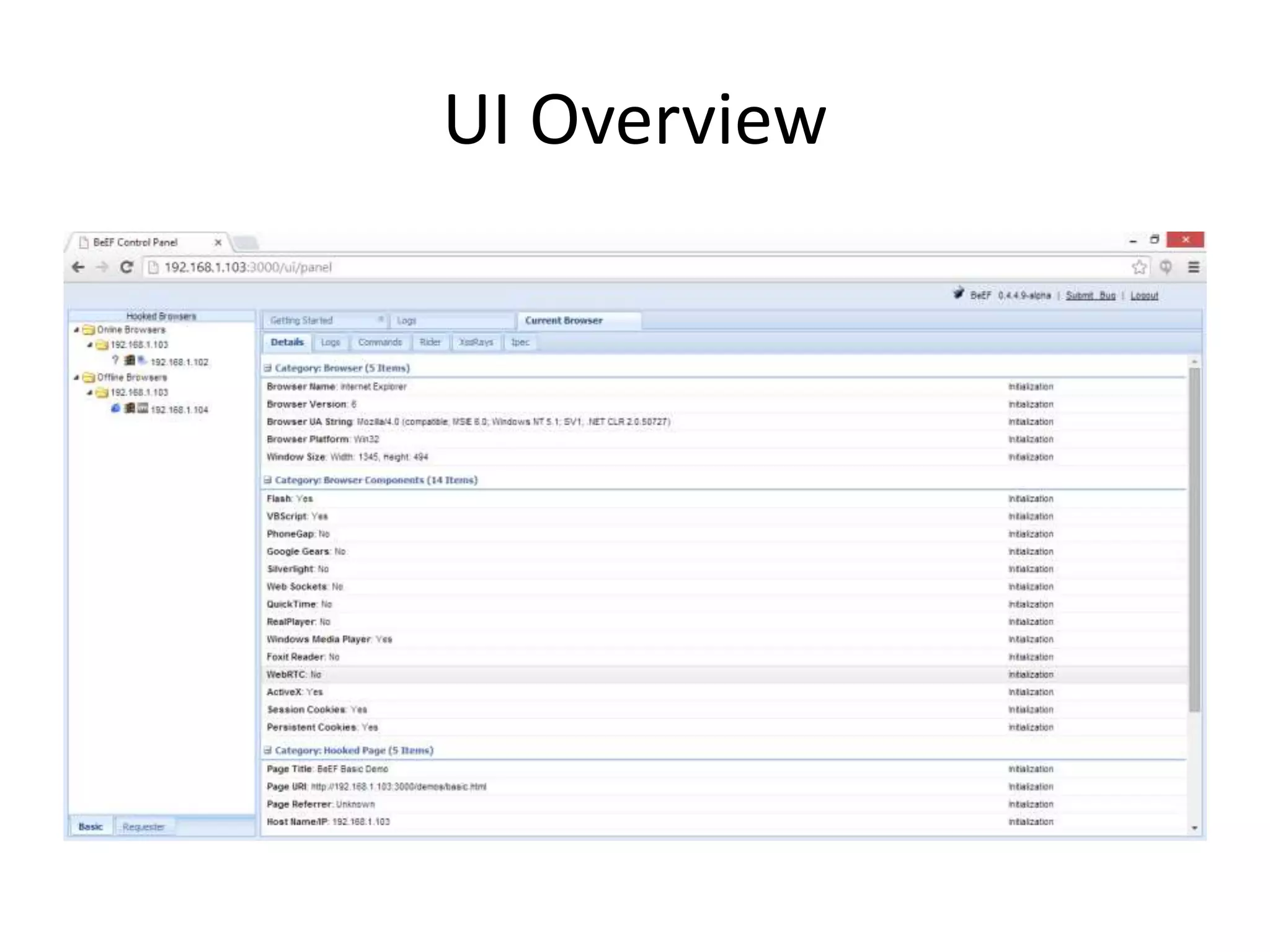
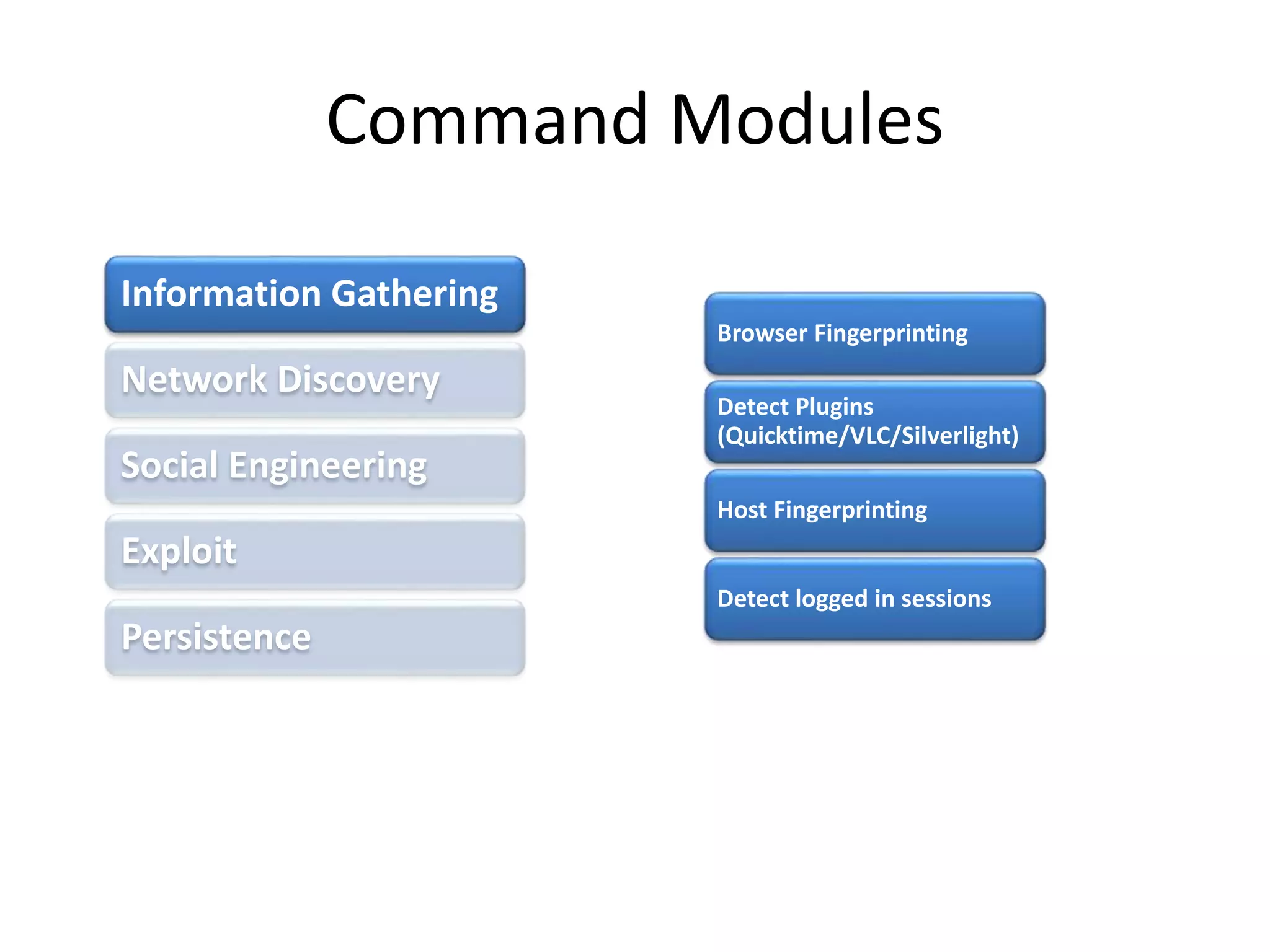
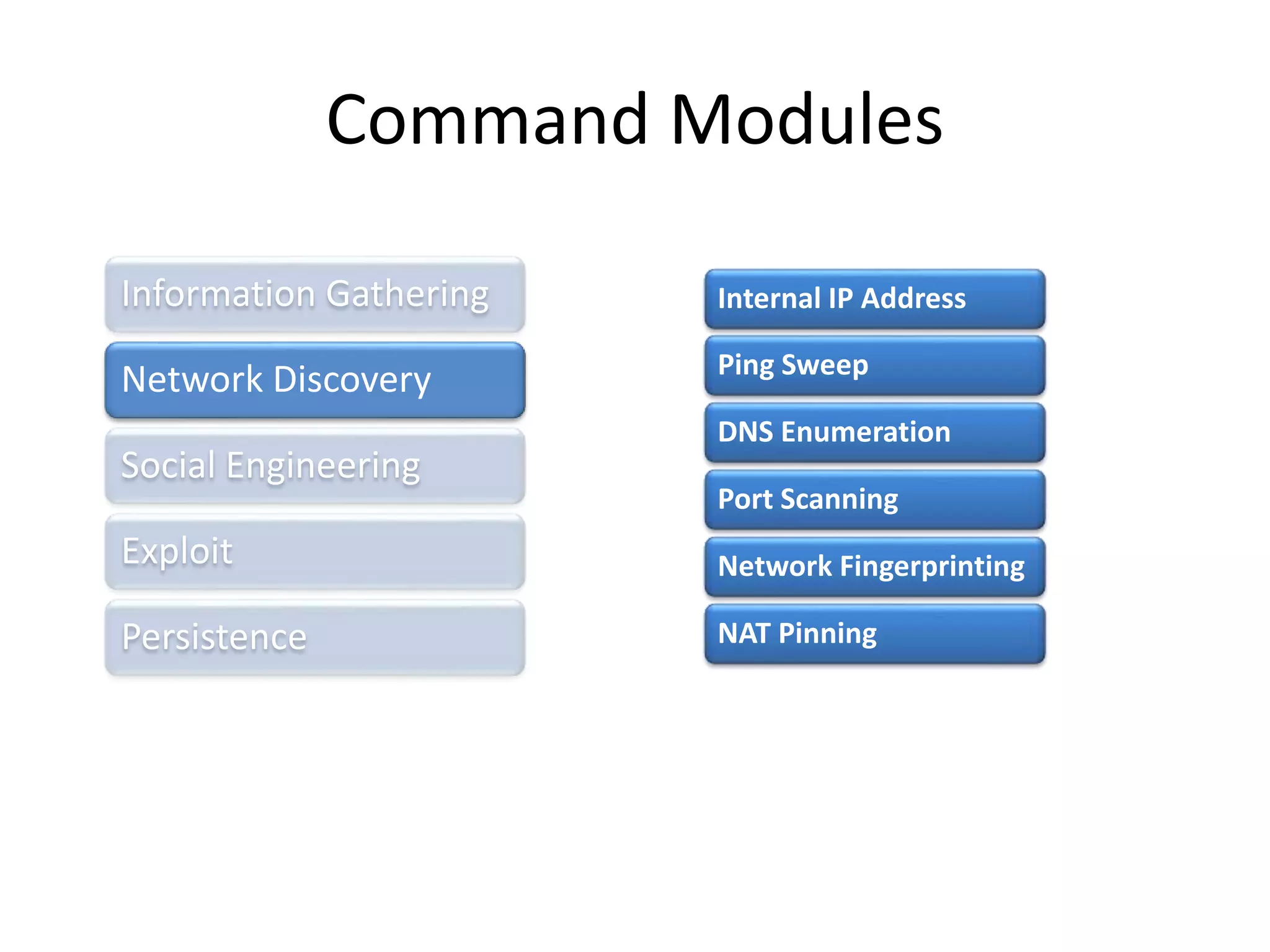
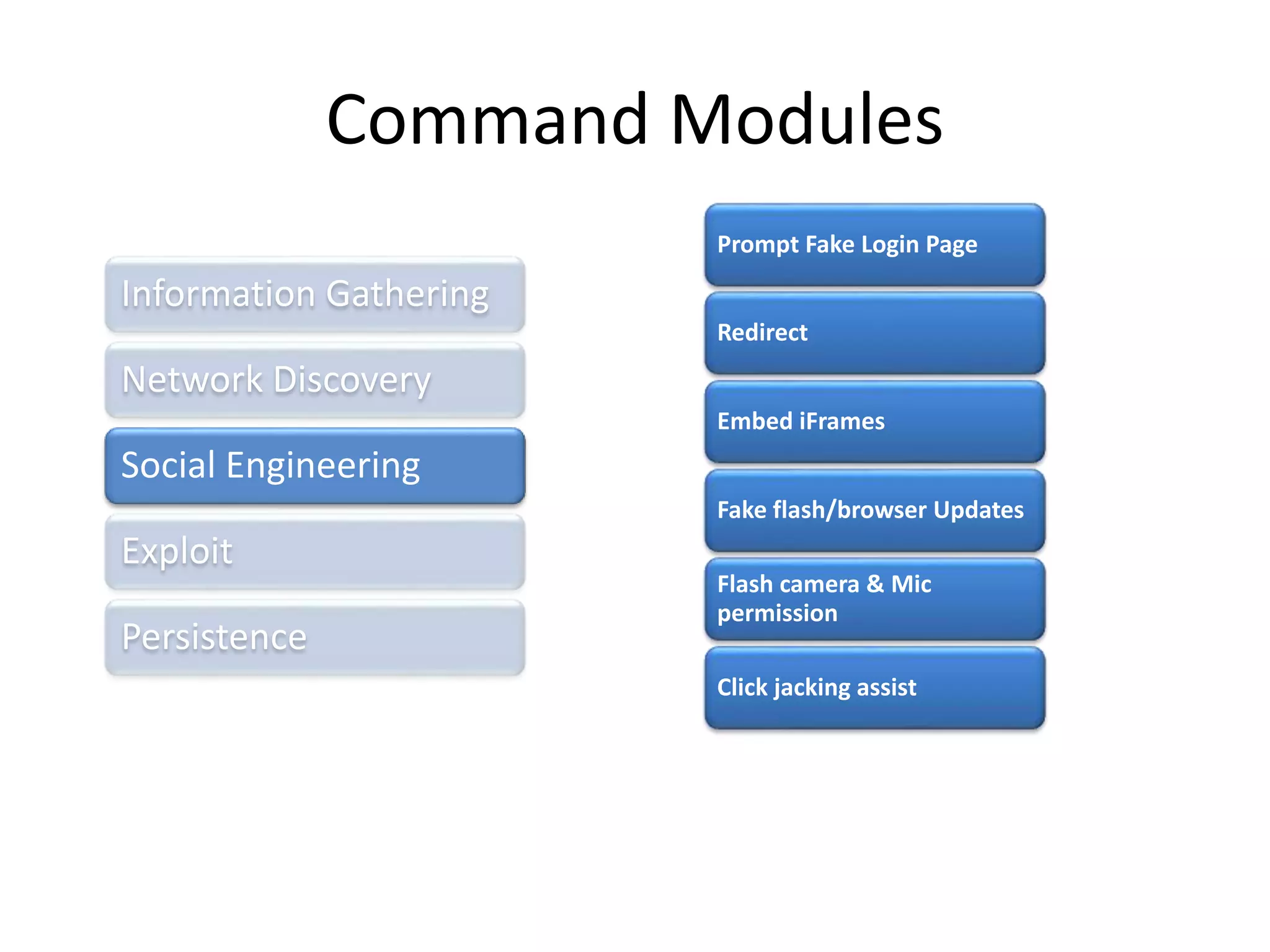
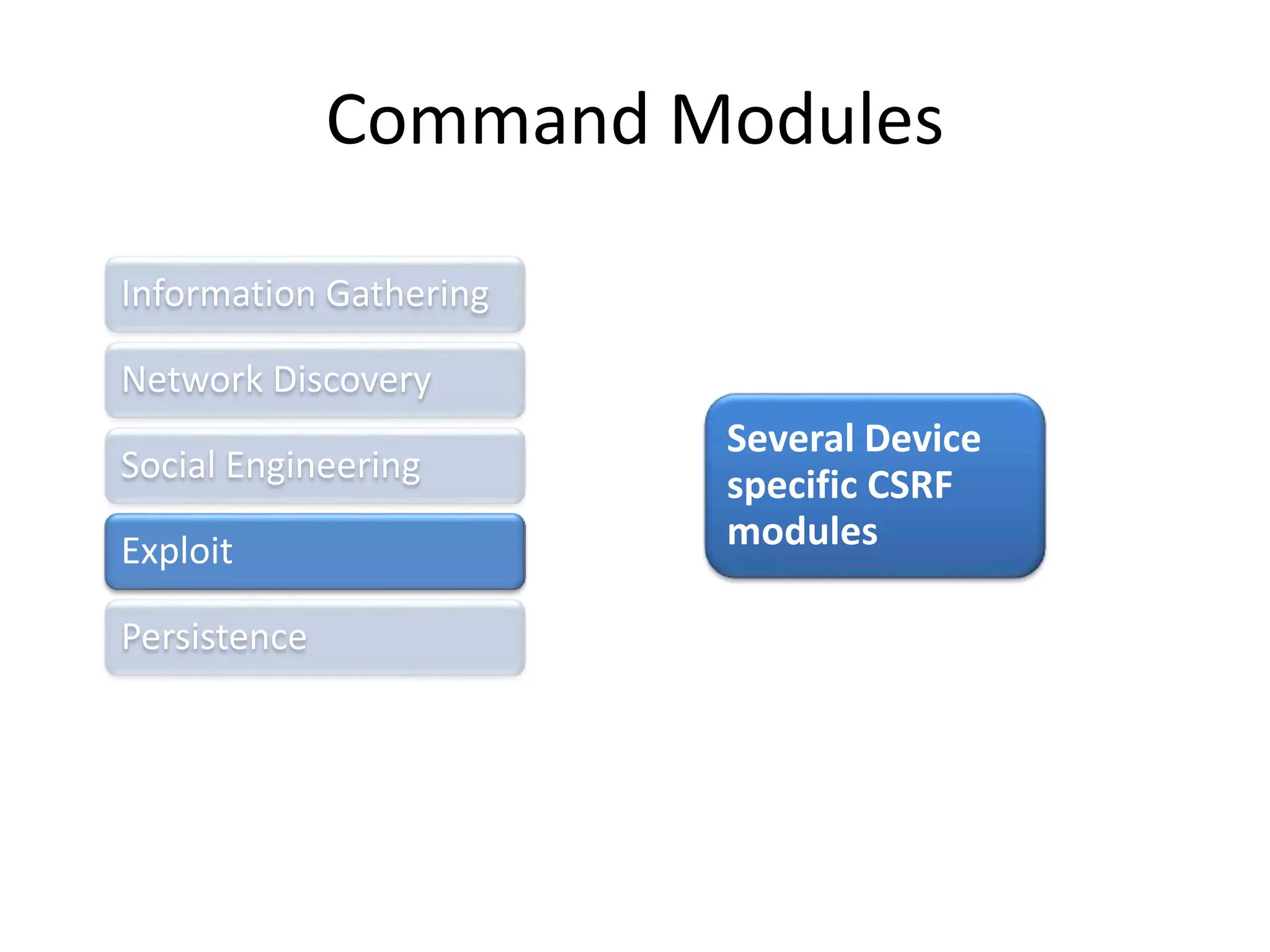
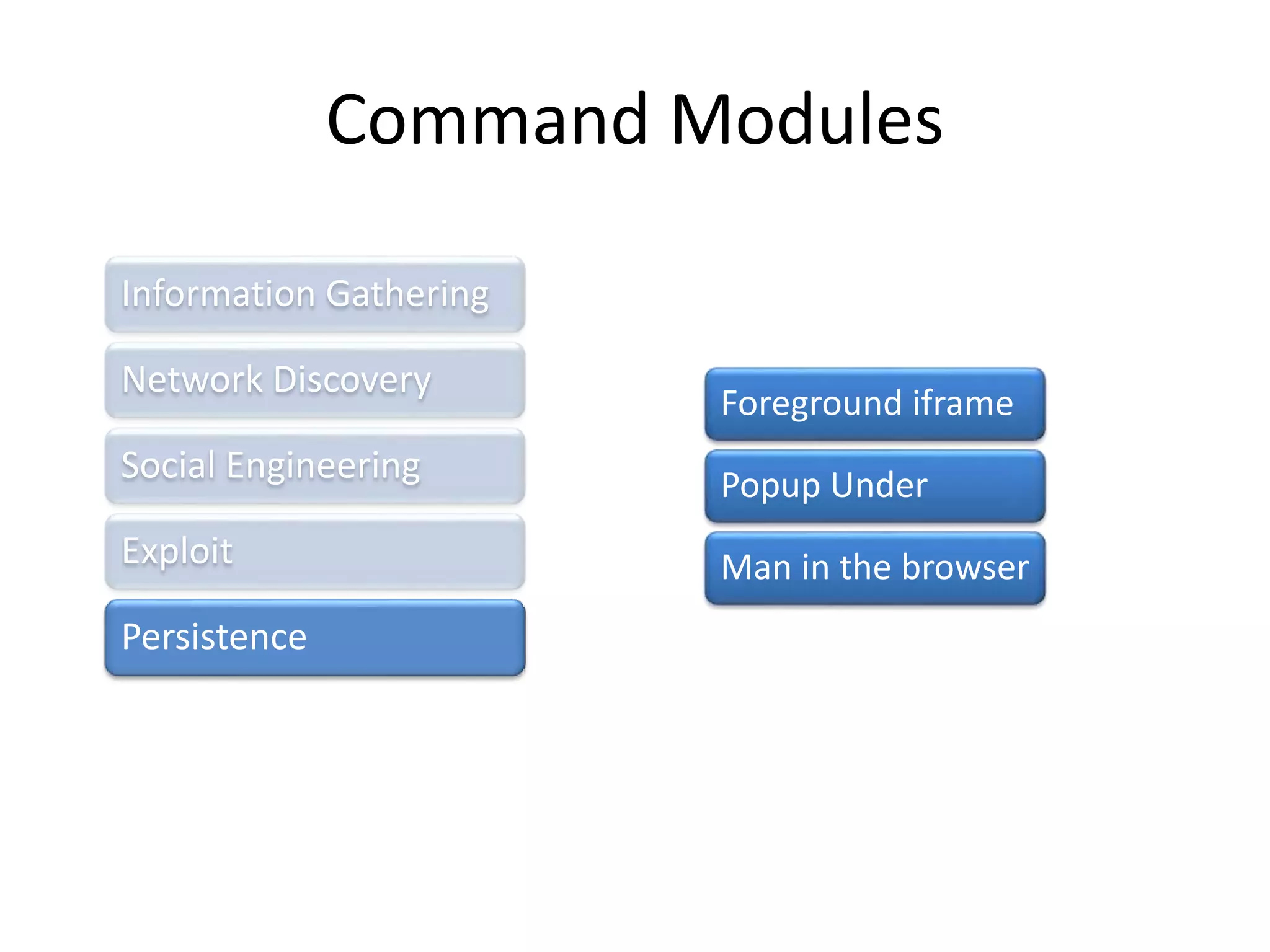
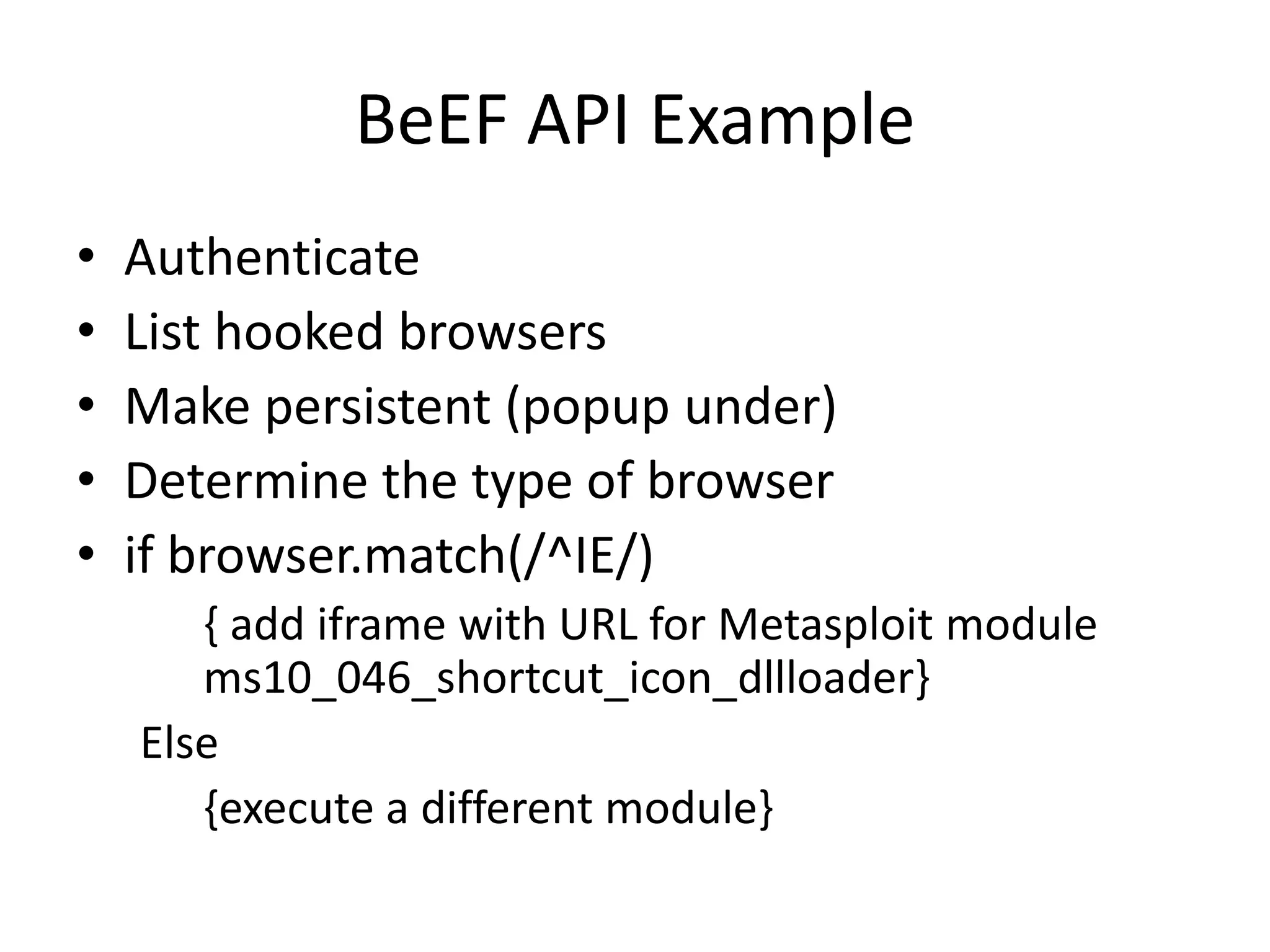
BeEF (Browser Exploitation Framework) is a penetration testing tool that focuses on exploiting vulnerabilities within the web browser. It works by hooking one or more browsers and using them as entry points to launch attacks against the system from within the browser context. This allows penetration testers to assess the security of a target environment by exploiting client-side vectors rather than just focusing on the network perimeter or hardened systems. BeEF gathers information about hooked browsers and systems, performs network discovery, and has command modules for social engineering, exploits, and maintaining persistence within the browser.