This document discusses buffer overflow exploits. It defines a buffer overflow as when a program overruns a buffer's boundary and overwrites adjacent memory locations. This can allow malicious code to be executed by replacing executable code. A simple C program example is provided to demonstrate this vulnerability. The document also mentions the 1988 Internet worm, which took down 10% of the Internet at the time by exploiting a buffer overflow in the finger program. Safer alternatives to vulnerable functions like gets() that cause buffer overflows are suggested.



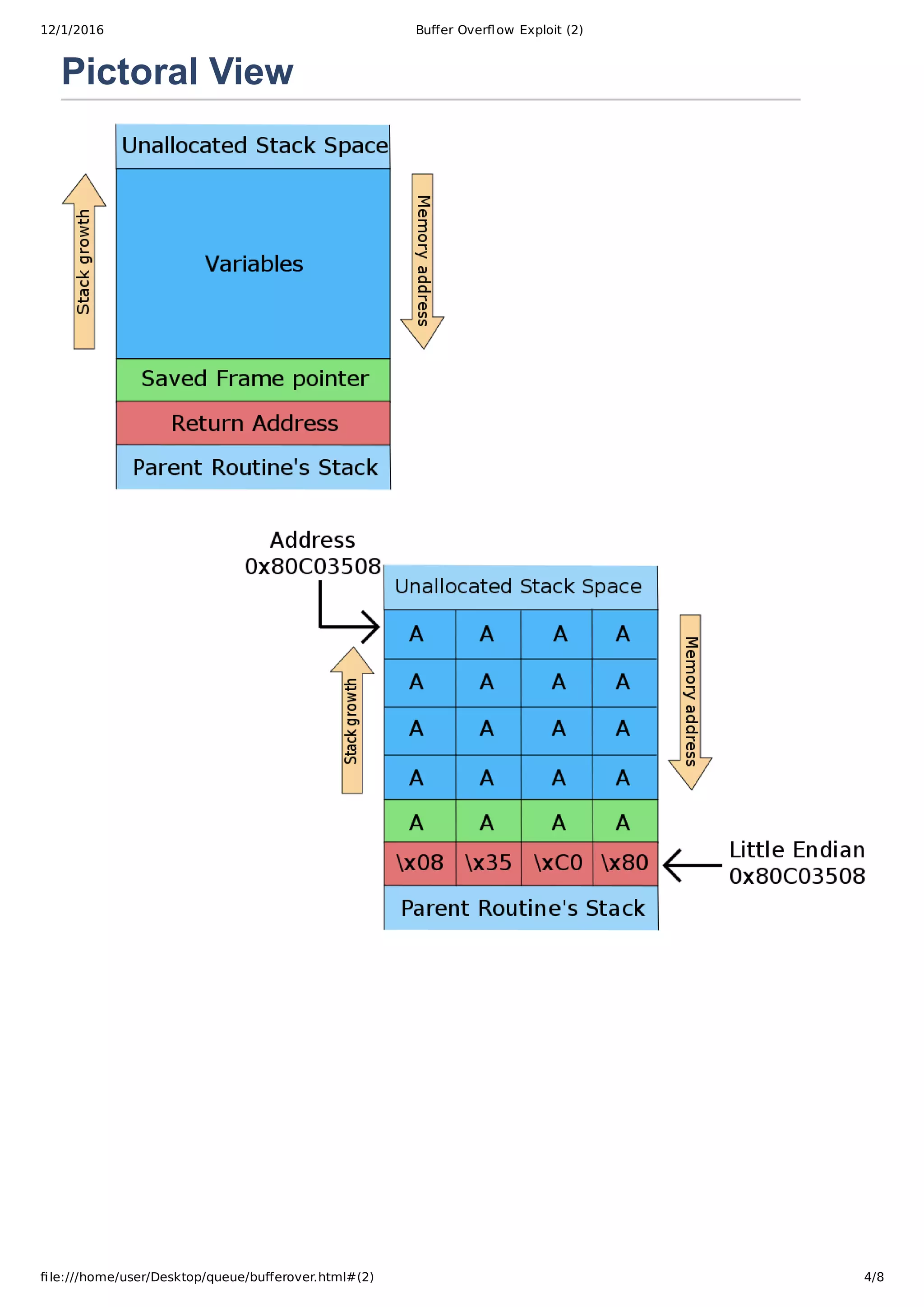
![12/1/2016 Buffer Overflow Exploit (2)
file:///home/user/Desktop/queue/bufferover.html#(2) 5/8
Simple Program
#include <stdio.h>
#include <string.h>
void secretfunction(void)
{
puts("You have been Hacked!!");
}
void pass(void)
{
char pass[10] = "zilogic";
char buff[20];
int flag = 0;
gets(buff);
if (!strcmp(buff, pass))
flag = 1;
if (flag)
puts("Password CorrectnAuthorization
Granted!!");
else
puts("Password Wrong");
}
int main(void)
{
printf("Enter Passwordn");
pass();
return 0;
}](https://image.slidesharecdn.com/bufferoverflowexploit2-161201051634/75/Buffer-OverFlow-Exploit-5-2048.jpg)